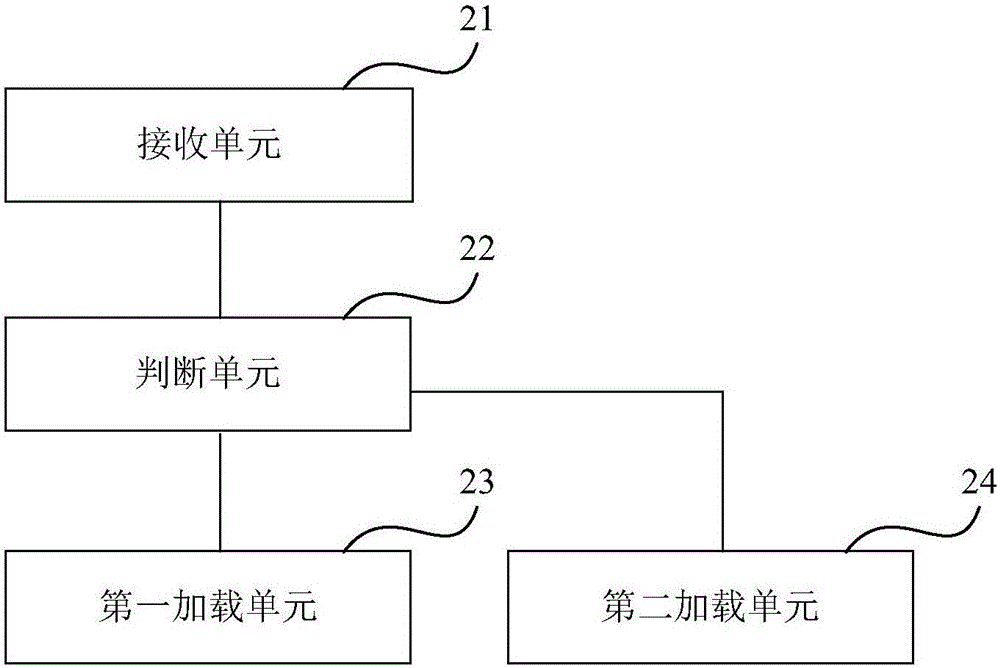
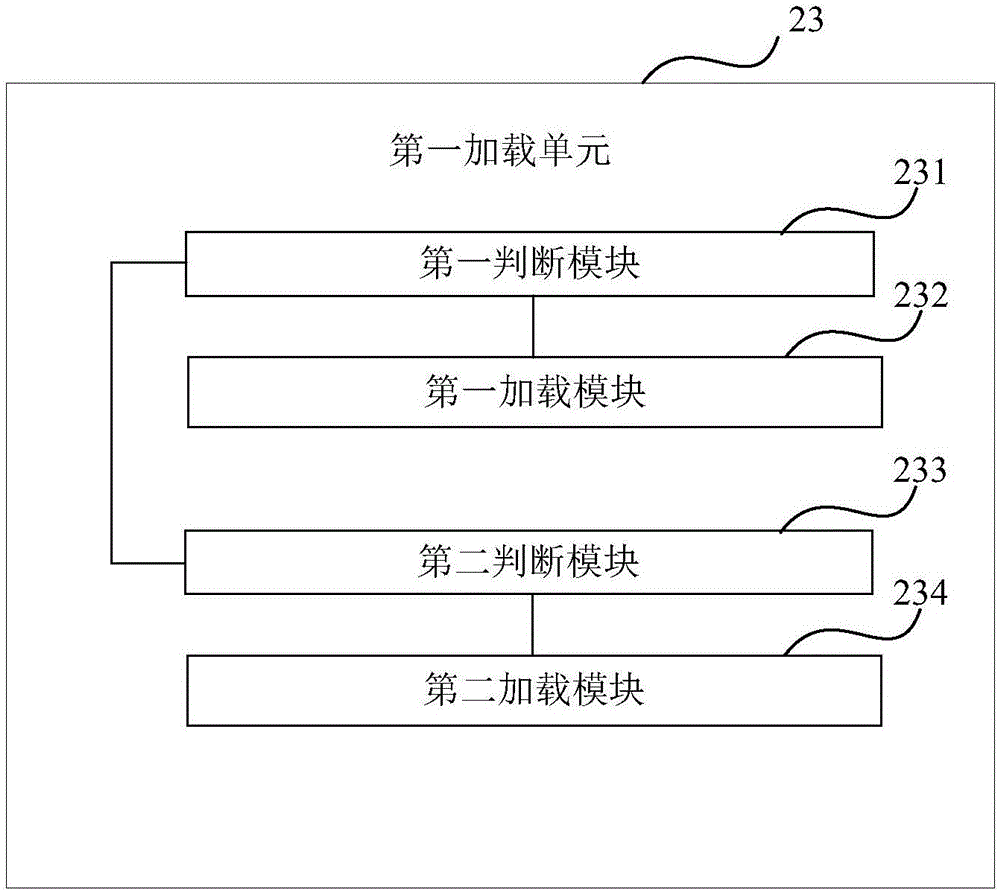
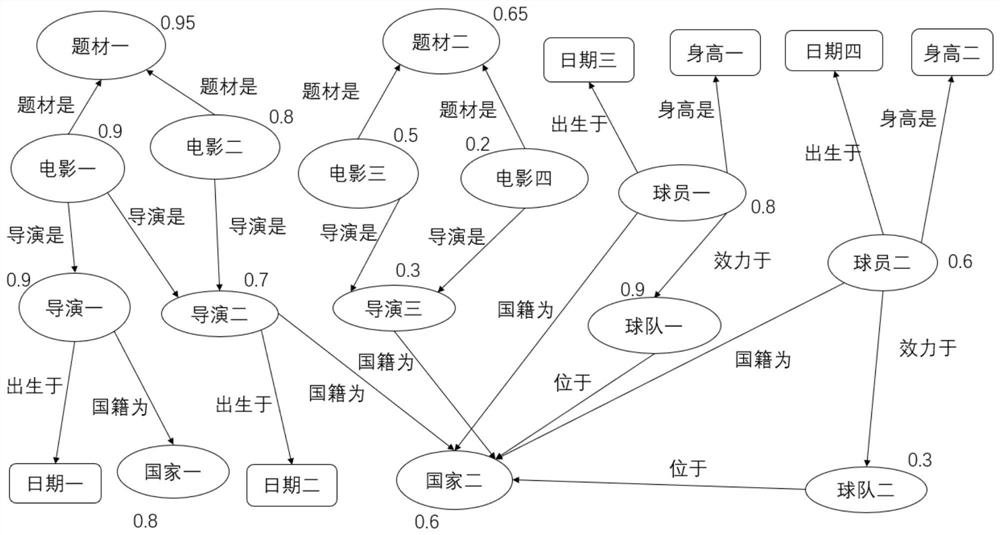
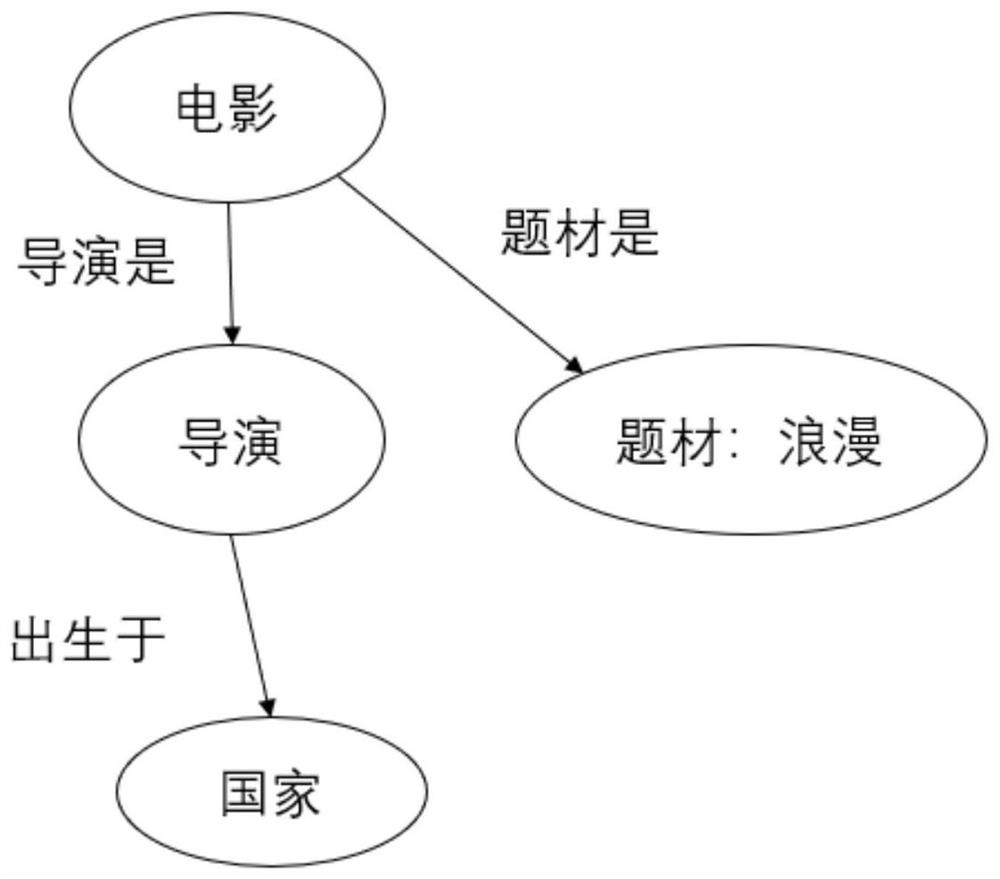
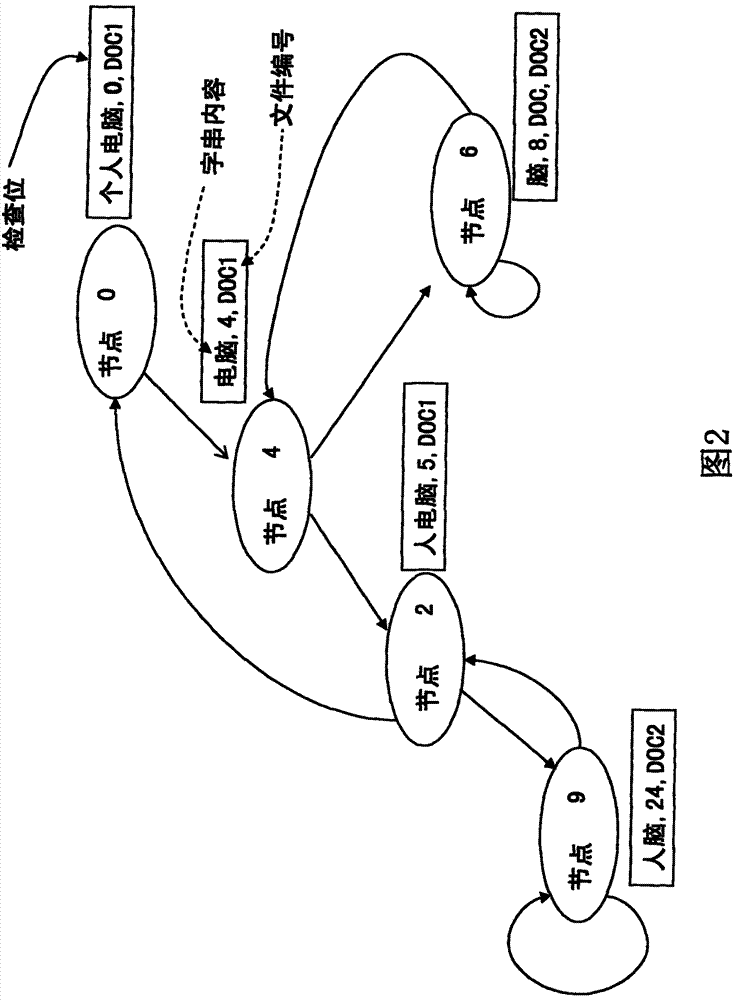
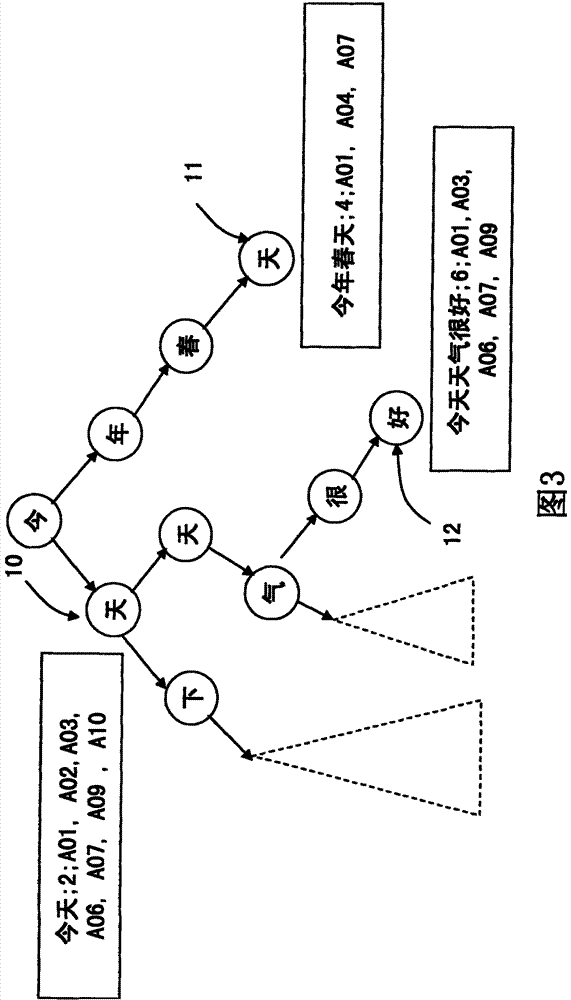
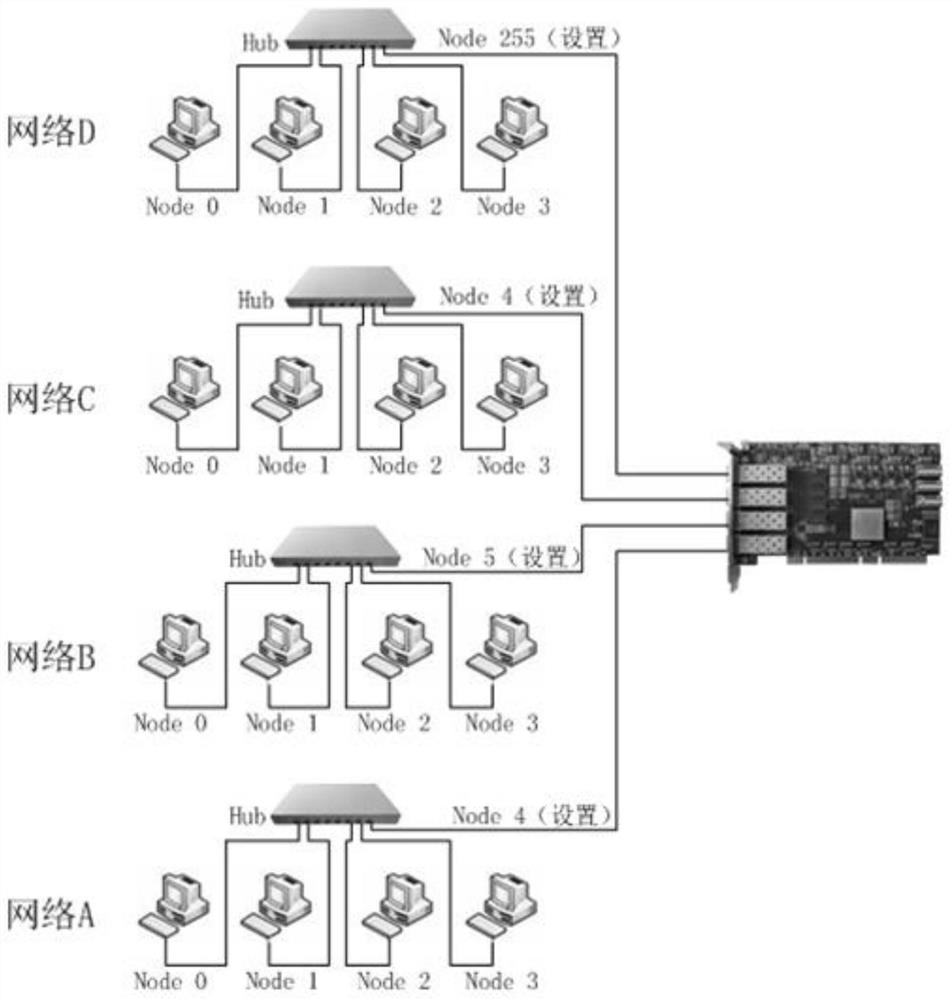
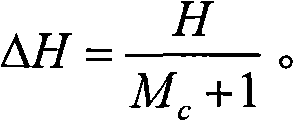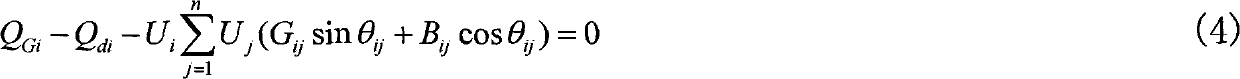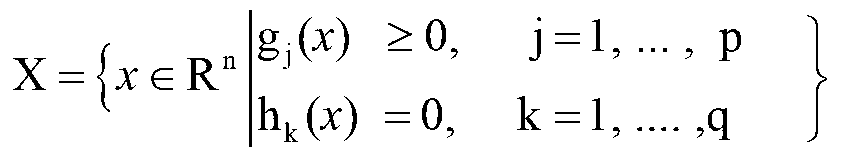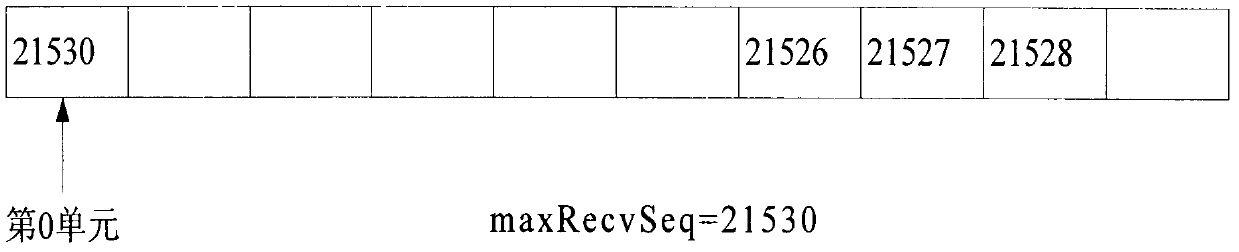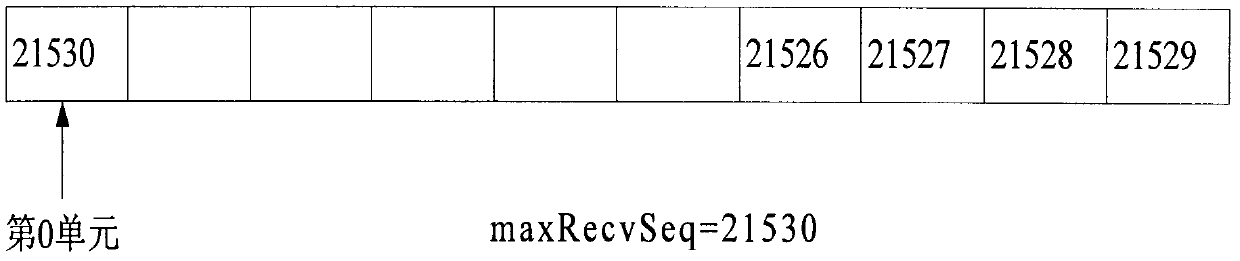Patents
Literature
59results about How to "Resolve duplication" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Method for resolving duplication of terminal identifiers in a wireless communication system
InactiveUS7075897B2Resolve duplicationEasy to resolveNetwork traffic/resource managementNetwork topologiesCommunications systemIp address
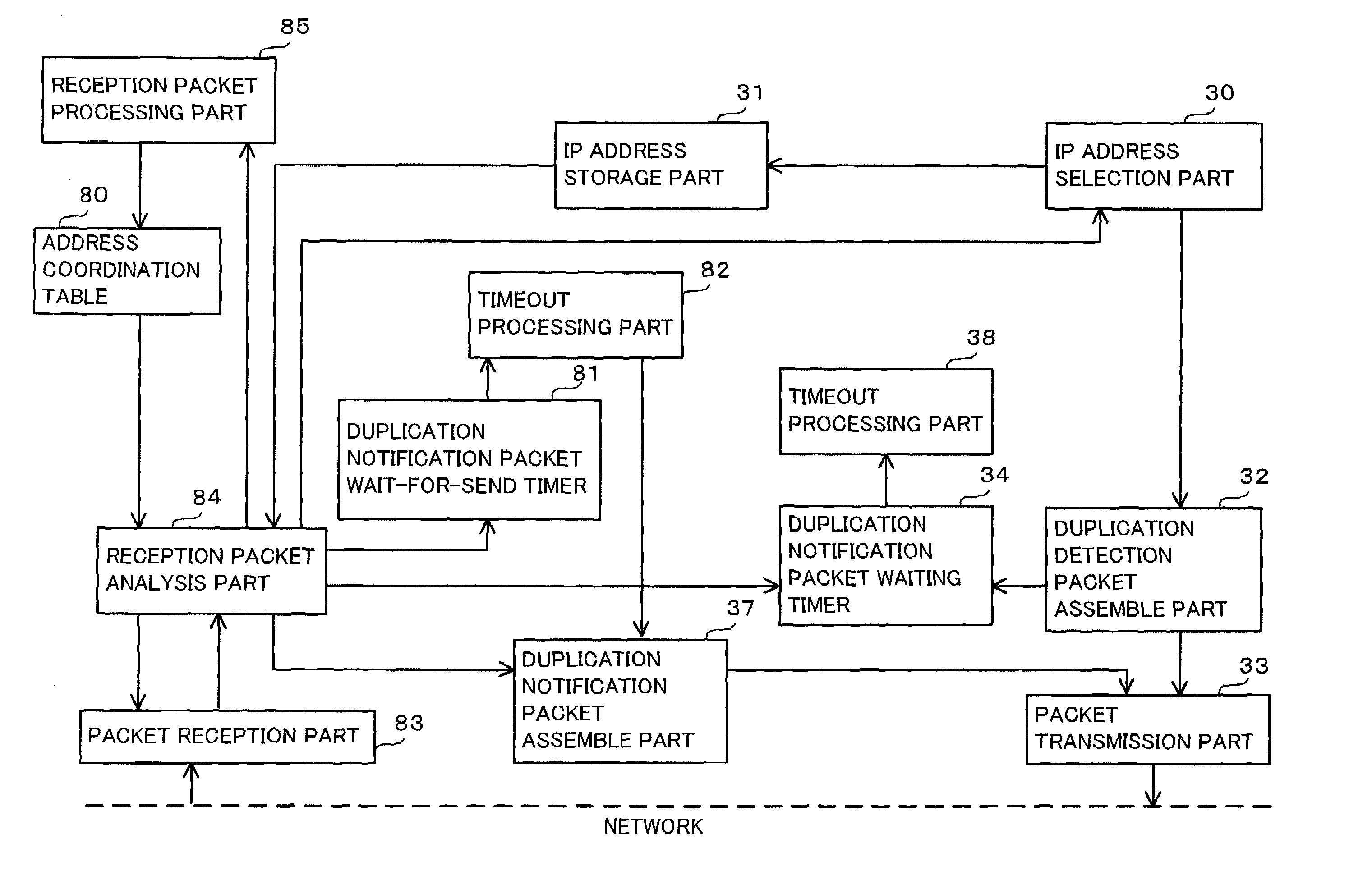
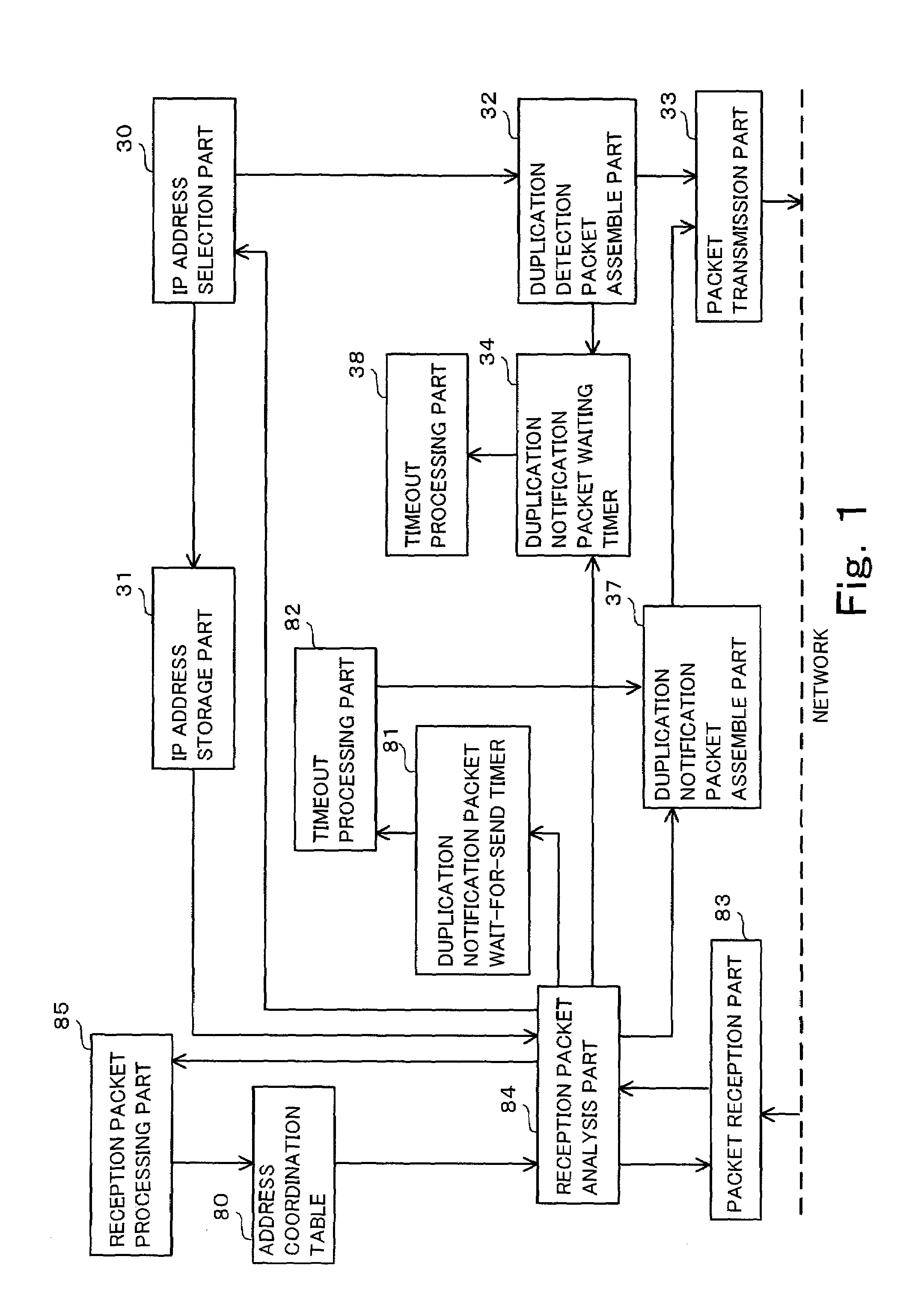
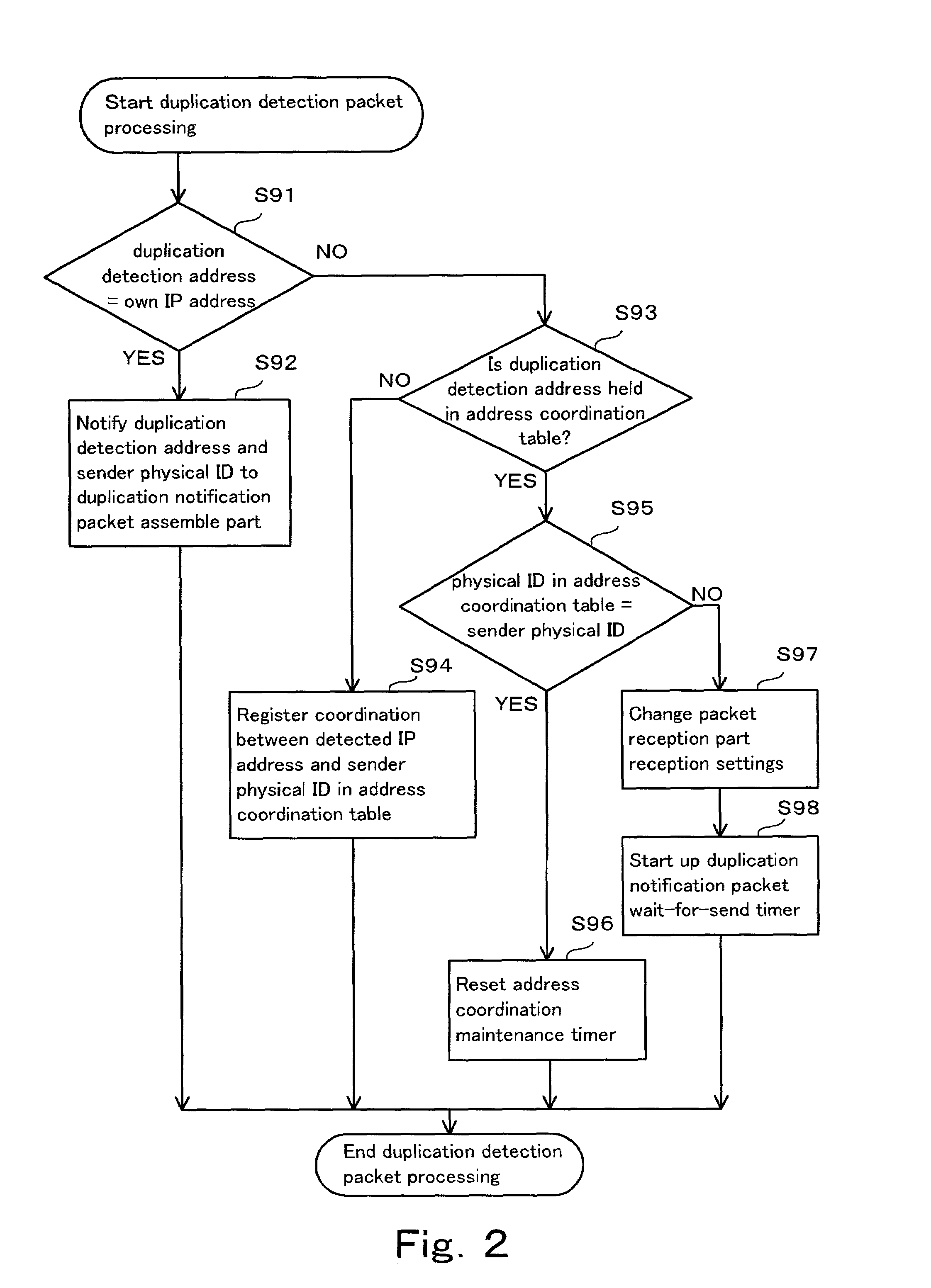
A wireless communication system wherein if a terminal receives an address duplication detection packet that terminal compares the duplication detection address with the IP address of itself and if those addresses are similar, sends a duplication notification packet, however if those addresses are not similar, the terminal investigates whether or not the duplicated address is being held in an address coordination table. If the duplicated address is not being held in that table, the terminal makes a new registration of that address in the table while if that duplicated address is held in that table, the terminal compares the combination of that duplicated address and the sender physical identifier of the duplication detection packet with the combinations inside the coordination table. If those combinations are equivalent, the terminal resets an address coordination maintenance timer while if they are not equivalent, the terminal changes the reception settings of packet reception part 83 to enable reception of packets each of which includes the duplication detection address and the sender physical identifier of the duplication inspection packet as the destination physical identifier, and starts up duplication notification packet wait-for-send timer 81 however if timer 81 times out, a duplication notification packet is sent.
Owner:NEC CORP
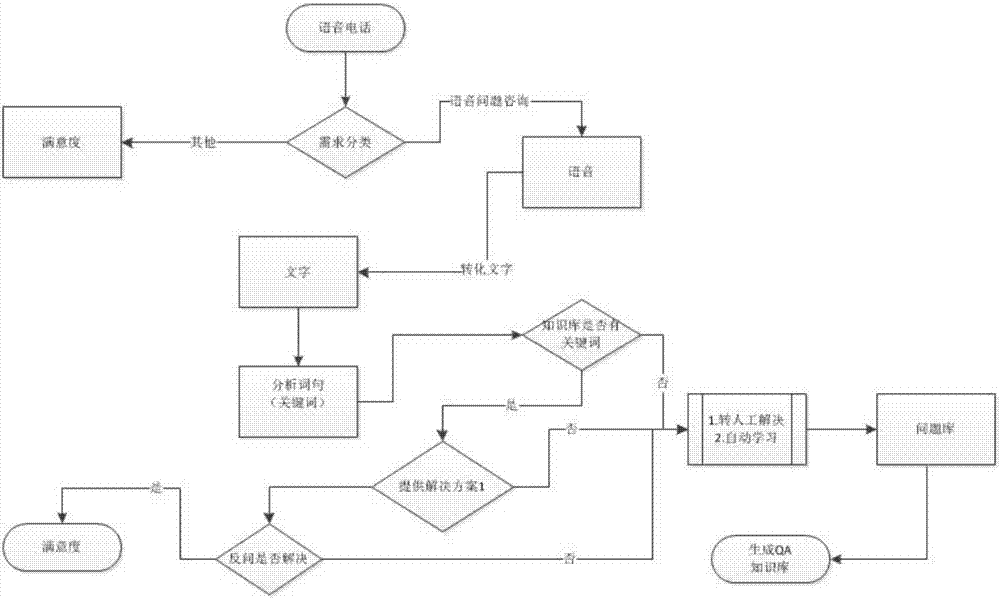
Multi-terminal intelligent customer service solution method
InactiveCN107153965AReduce repetitive labor timeImprove work efficiencySpeech recognitionCommerceProblem listSolution plan
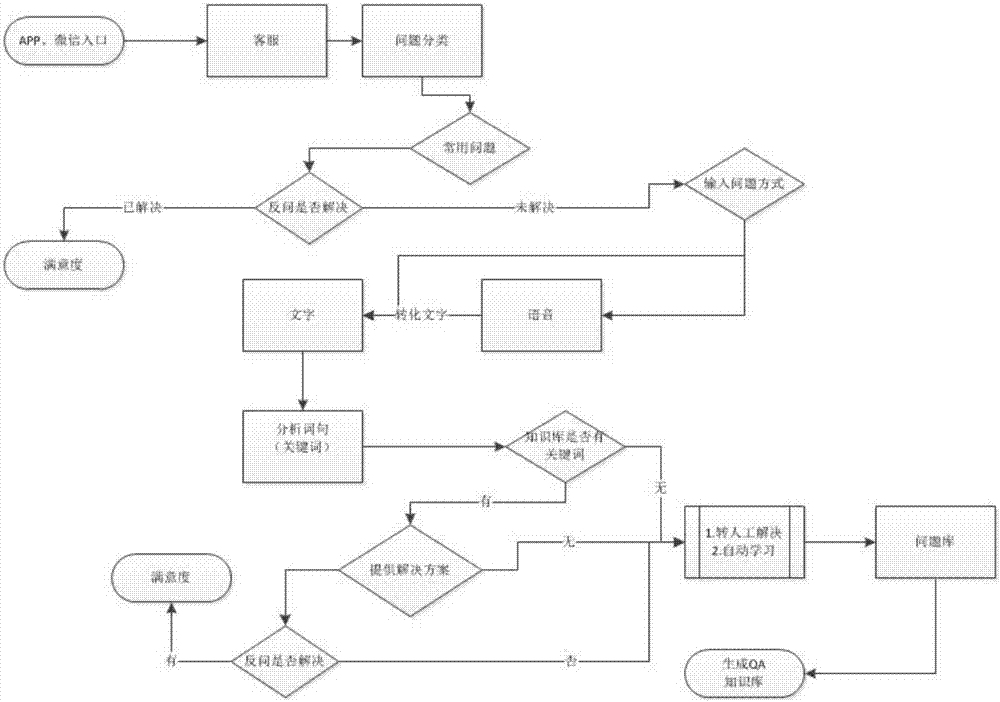
The invention relates to the technical field of intelligent customer service system, particularly to a multi-terminal intelligent customer service solution method. The method comprises: a customer enters a customer terminal for page consultation; a system automatically displays common problems, the user makes confirmation, and if the problem of the user has been solved, the user makes confirmation and gives a score for satisfaction; if the problem of the user is not solved, the user can submit the problem in a voice and text manner; a key word is extracted by a voice transform technique; key work information matching is carried out by an intelligent customer service problem processing center; a solution plane is sent if matching is done successfully; if matching fails, transferring to the customer service system is carried out for processing; the customer service system obtains user information and a problem content, and thus the problem is solved manually and an order record is generated; and an unsolved problem list is generated, the customer service system sets key words and solution plans, and the information is recorded and inputted into a QA knowledge base. Therefore, 80% of repeated problems of the users can be solved, so that the repeated labor time of the customer service staff can be reduced substantially and thus the work efficiency can be improved. Besides, the queuing time for consultation by the user can be reduced and the solution plans of the problems can be obtained timely.
Owner:WUHU HENGTIAN YIKAI SOFTWARE TECH CO LTD
Reactive power optimization method of enterprise distribution network based on genetic algorithm
ActiveCN101950971AExpand selectionSolve too much concentrationEnergy industryReactive power adjustment/elimination/compensationPopulationCapacitance
The invention discloses a reactive power optimization method of an enterprise distribution network based on a genetic algorithm, comprising the following steps: (1) building the reactive power optimization model of an enterprise distribution network; (2) determining the final reactive power optimization point to be compensated of the enterprise distribution network; (3) carrying out chromosome coding on the compensation capacitance of a compensation capacitor, the transformation ratio of an adjustable transformer and generator end voltage in the enterprise distribution network, and forming an initial population; (4) calculating the fitness value of an individual satisfying constraint check in the initial population; (5) according to the fitness value of each individual in the initial population, adaptively crossing and varying to generate new generation of population; (6) if the maximum fitness value of the individual of new generation of population and the maximum fitness value of the individual of the previous generation of population satisfy a relation, carrying out chromosome decoding on the individual with the maximum fitness value in the new generation of population, obtaining the reactive power optimization result of the enterprise distribution network, and outputting; and otherwise, returning to step (4).
Owner:广东立胜综合能源服务有限公司 +1
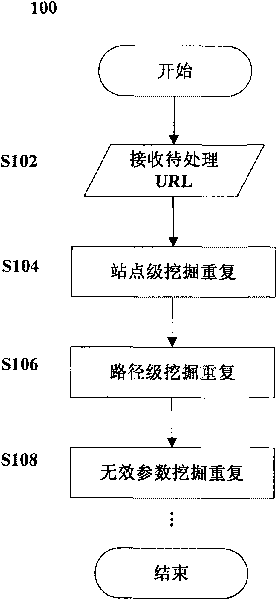
Method and device for removing duplication from data mining
The invention discloses a method, a device and a system for removing duplication from data mining. The method comprises the following steps: receiving two or more characteristic values of identification information; confirming that the two or more identification information are duplicated when the characteristics values thereof are identical; and selecting one piece of duplicated identification information to represent the duplicated identification information.
Owner:BAIDU ONLINE NETWORK TECH (BEIJIBG) CO LTD
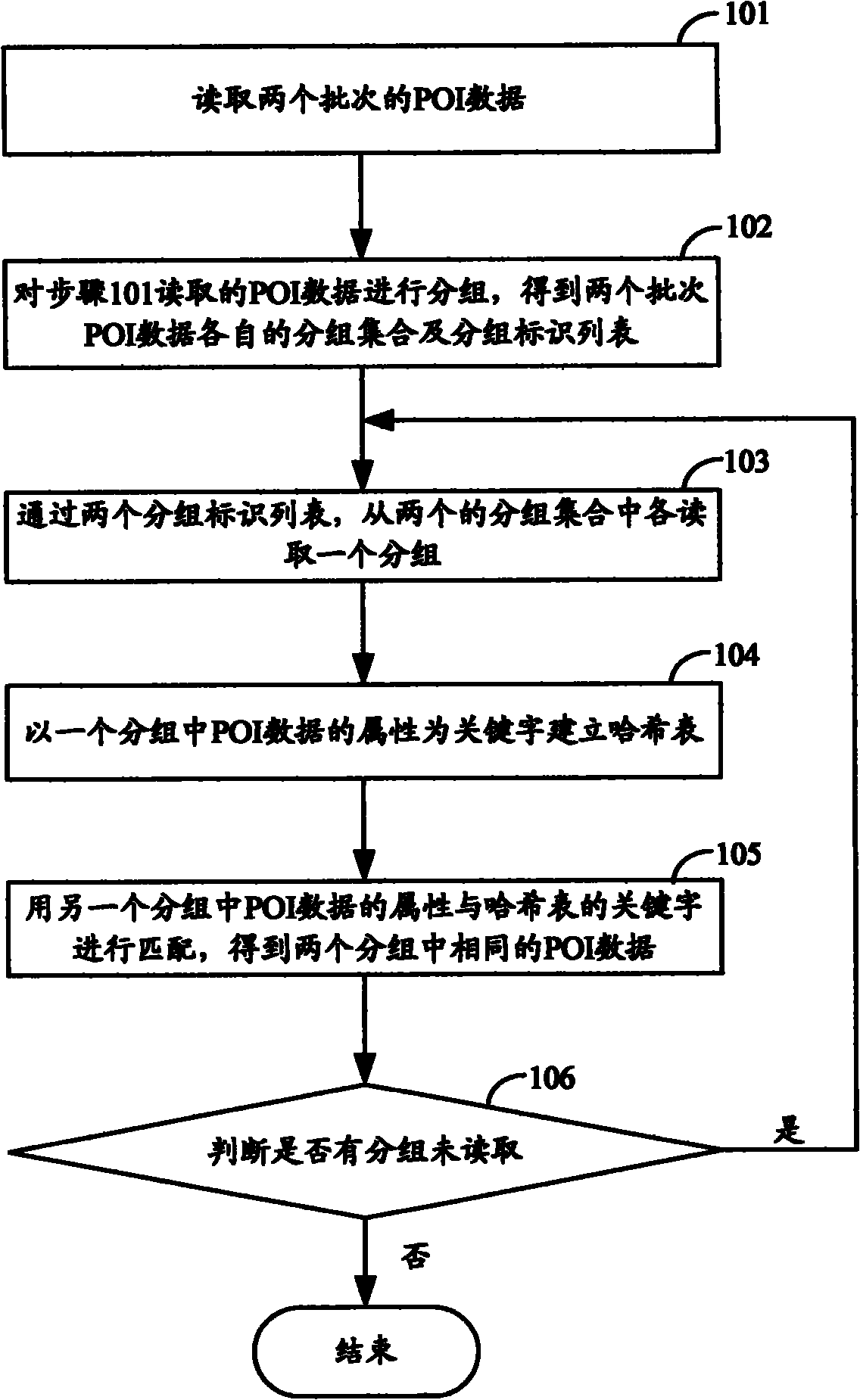
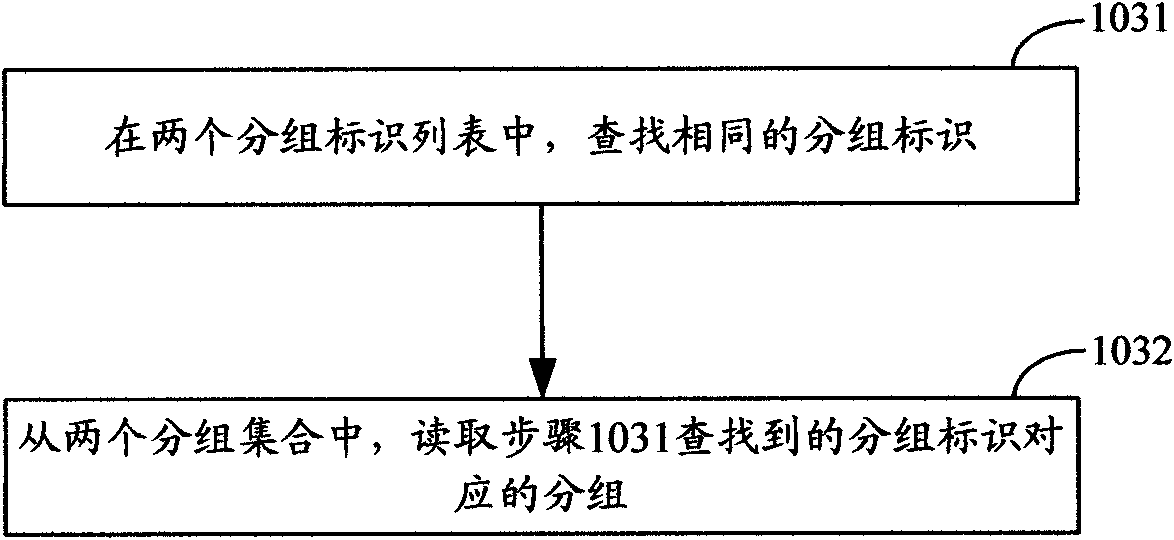
Interest point data correlation method and device therefor
The embodiment of the invention provides an interest point data correlation method and a device therefor. The method comprises the following steps: reading two batches of interest point data; grouping the interest point data to obtain grouping sets and grouping identification lists of the two batches of interest point data; respectively reading a group from the two grouping sets by the two grouping identification lists; establishing a hash table with the attribute of interest point data of a group being the keyword; matching the attribute of another group of interest point data with the keyword of the hash table to obtain two samely grouped interest point data. Correspondingly, the embodiment of the invention provides an interest point data correlation device. With the method or the device of the embodiment of the invention, repetitive data of different batches of POI data can be effectively correlated.
Owner:ALIBABA (CHINA) CO LTD
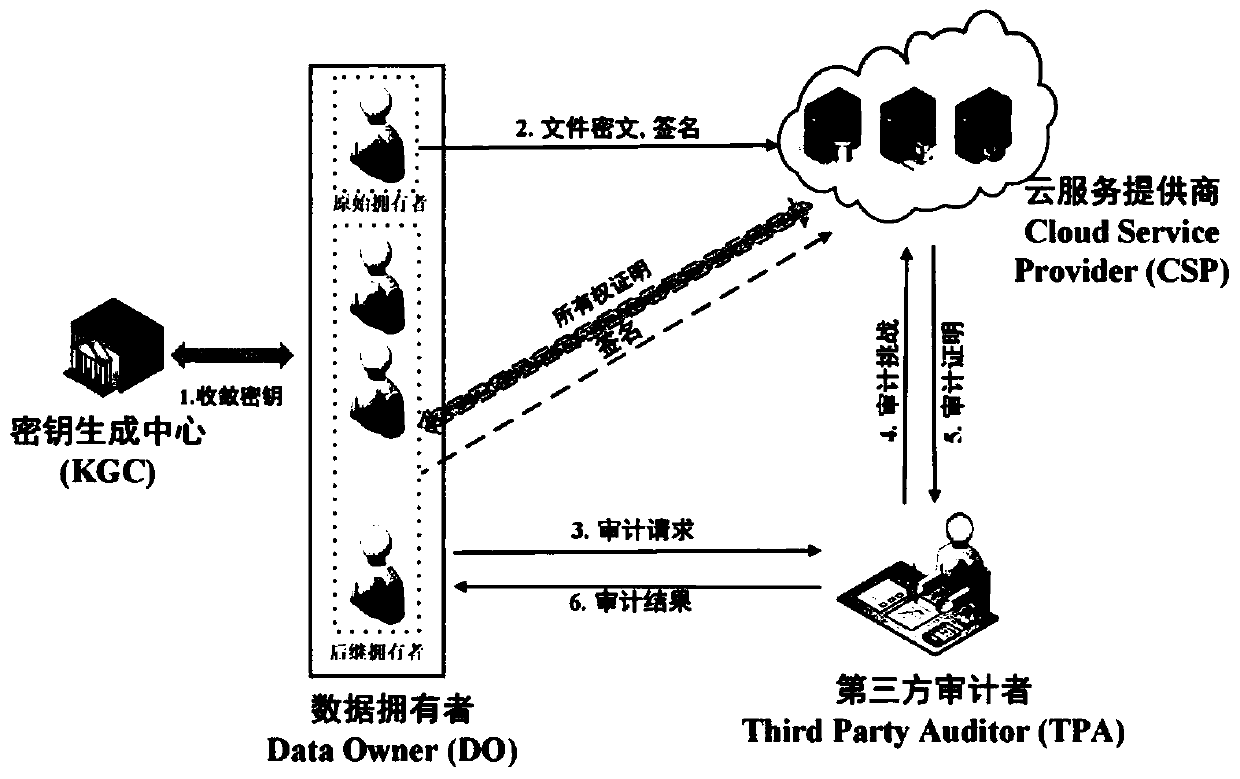
Outsourcing data deduplication cloud storage method supporting privacy and integrity protection
ActiveCN110677487AResolve duplicationSolve protection problemsKey distribution for secure communicationUser identity/authority verificationCiphertextData file
The invention discloses an outsourcing data deduplication cloud storage method supporting privacy and integrity protection. Firstly, client deduplication and security authentication label deduplication of a data file are realized, so that the communication overhead and the storage burden of a cloud server are greatly reduced; and secondly, by adopting the extractor technology, the ciphertext of the outsourcing storage data does not depend on an encipher and an encryption algorithm, but depends on the data, so that ciphertext data deduplication is realized, and the privacy of the data is ensured in the deduplication process and the integrity auditing process. And finally, the RS erasure code technology is adopted to improve the fault-tolerant capability of deduplication cloud storage; a cloud service provider is also supported to spontaneously and regularly delegate a third-party auditor to carry out batch public cloud auditing on the data stored in the cloud server so as to ensure theintegrity of the data; meanwhile, a data owner is also supported to initiate public cloud auditing on the integrity of the file anytime and anywhere, so that the privacy of the data can be always protected in auditing and deduplication processes. The method provided by the invention is effective in the aspect of deduplication and efficient in the aspect of integrity cloud auditing.
Owner:中科柏诚科技(北京)股份有限公司
Electric power multi-objective decision support method based on intelligent data mining model
InactiveCN103295079AResolve duplicationAddresses failure to cover all aspects of reviewsForecastingDecision modelRegression analysis
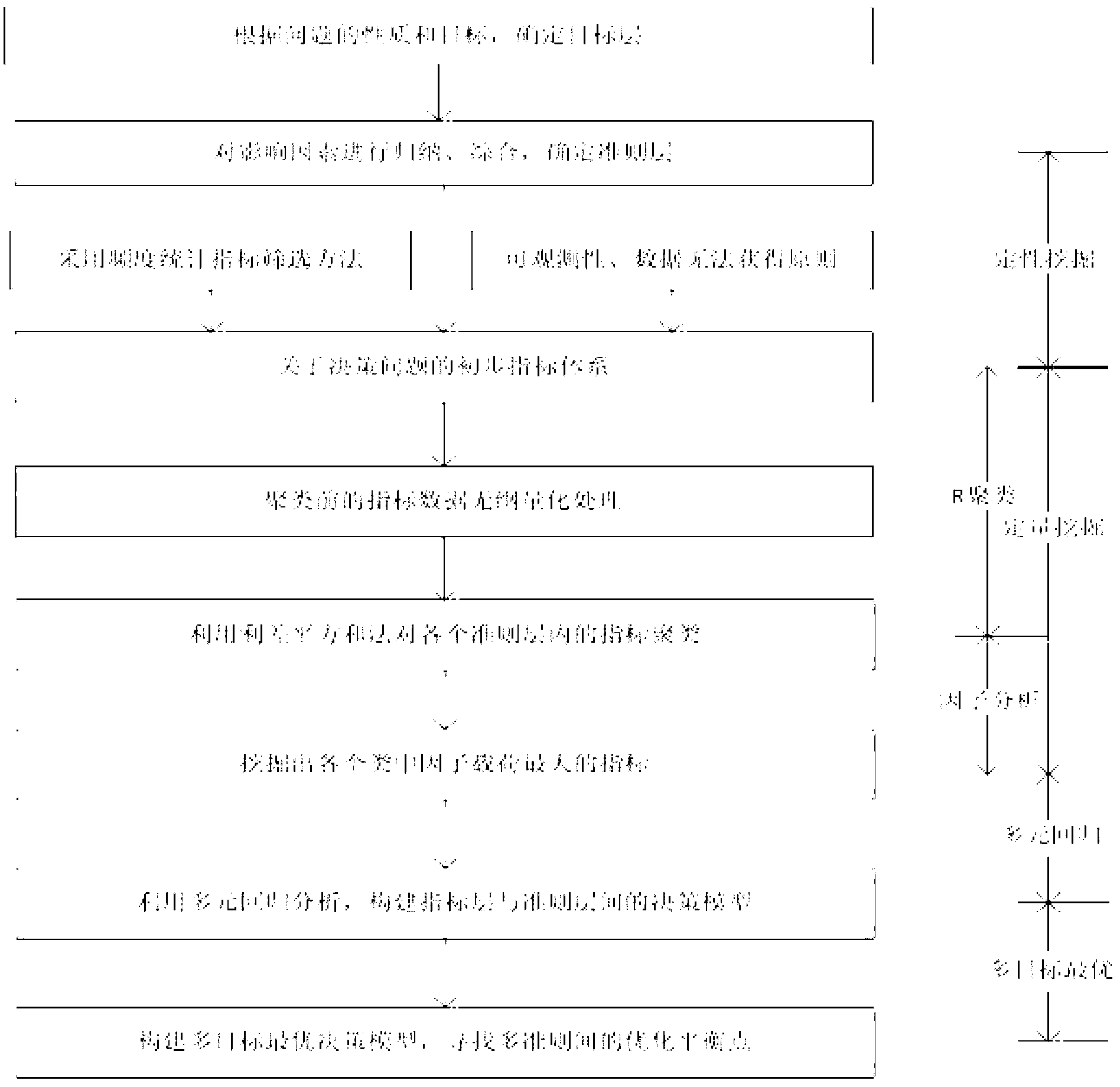
The invention relates to an electric power multi-objective decision support method based on an intelligent data mining model. The method comprises the steps of enabling a decision maker to be clear on decision objectives and determine objective layers according to properties of practical problems; calculating all influence factors needing to be considered to achieve the objectives, performing induction and synthesis on the influence factors, and determining criterion layers; adopting a frequency statistical index screening method to perform mass election on all indexes under every criterion layer, and deleting indexes from which observed data cannot be obtained according to an observability principle; adopting the sum of deviation squares to cluster the indexes in every criterion layer; adopting a factor analysis method to analyze factor loads of every statistical index, reserving indexes with maximum factor loads in every kind of indexes, and screening out co-factor indexes between the multiple criterion layers; establishing decision models between indexes layers and the criterion layers on the basis of a multivariate regression analysis method; searching optimal balancing points between multiple criterions according to decision models of every criterion so as to achieve optimum of a final objective layer.
Owner:STATE GRID CORP OF CHINA +1
Data processing method and apparatus, and data interaction method and apparatus
InactiveCN106709013AReduce consumptionResolve duplicationSpecial data processing applicationsData needsData storing
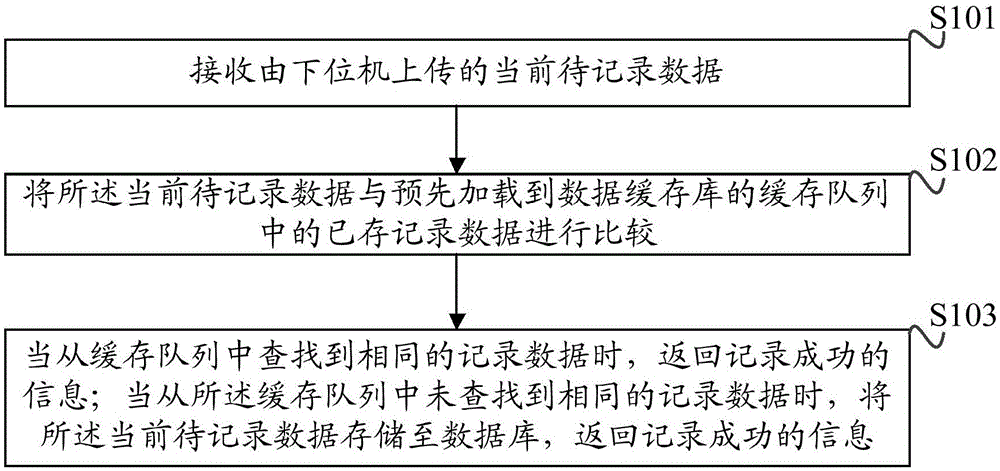
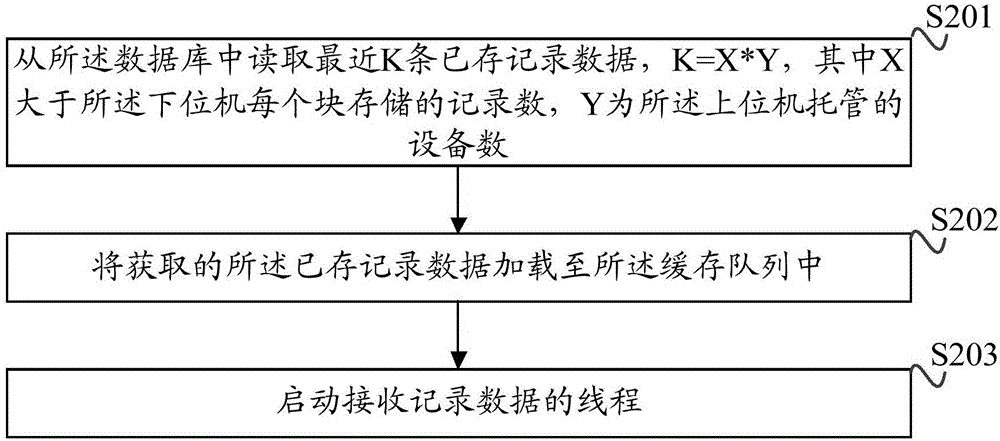
The invention discloses a data processing method. The method comprises the steps of receiving current to-be-recorded data uploaded by a lower computer through an upper computer; comparing the current to-be-recorded data with stored record data preloaded in a caching queue of a data caching library; when the same record data is found in the caching queue, returning recording success information; when the same record data is not found in the caching queue, storing the current to-be-recorded data in a database, and returning the recording success information; obtaining the current to-be-recorded data needed to be uploaded to the upper computer by the lower computer; receiving the recording success information returned by the upper computer; and when the current to-be-recorded data is all uploaded, deleting the current to-be-recorded data stored in the lower computer. According to the method, the consumption of database performance of the upper computer is reduced, and the problem of repeated recorded data of the upper computer is solved. In addition, the invention provides a data processing apparatus, a data interaction method and a data interaction apparatus with the abovementioned technical advantages.
Owner:SHENZHEN JIESHUN SCI & TECH IND
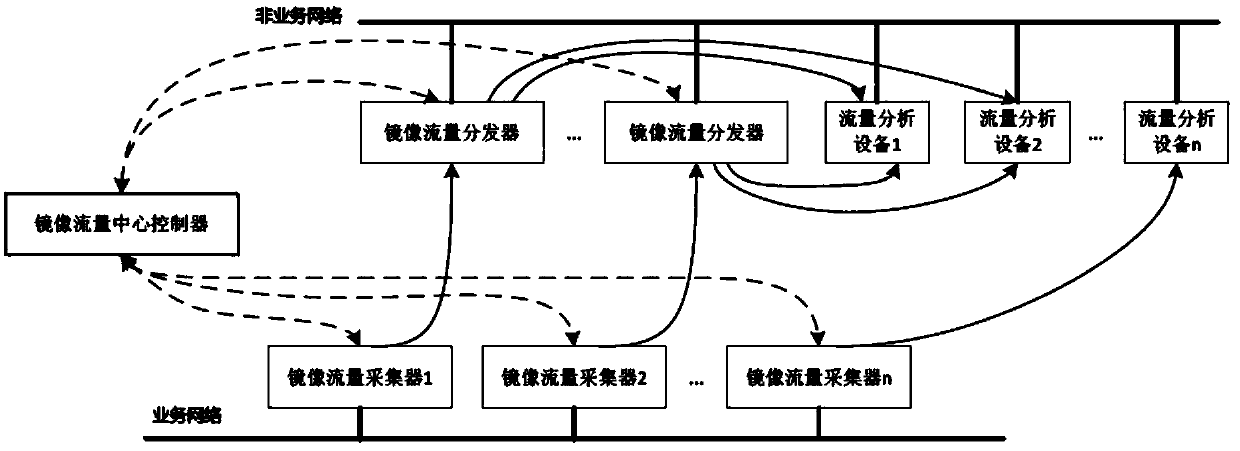
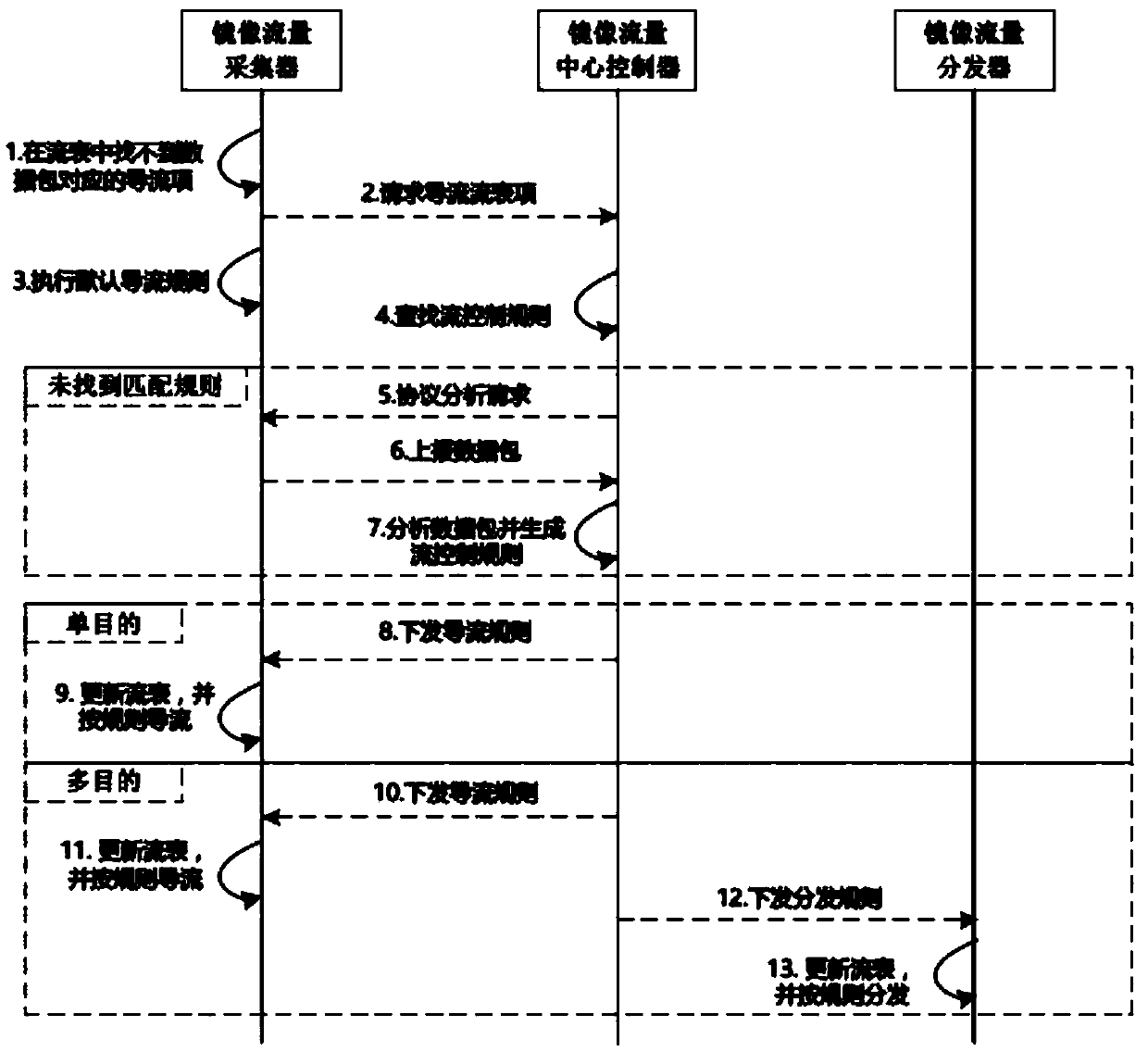
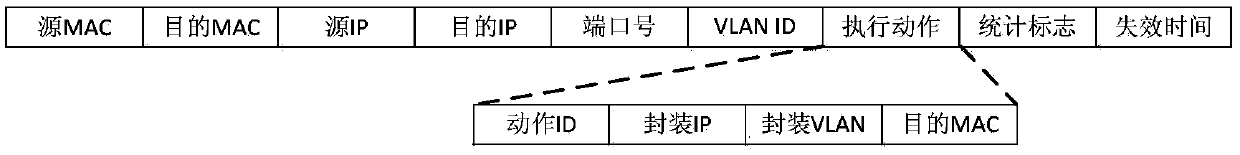
Mirror network traffic control protocol in virtual network environment
InactiveCN108234315AEasy accessResolve duplicationNetworks interconnectionNetwork communicationSoftware
The invention discloses a mirror network traffic control protocol based on software definition in a virtual network environment. The protocol is applicable to a functionally decoupled and distributedly deployed mirror traffic collection, mirror traffic distribution and mirror traffic control system structure. A mirror traffic collector node / virtual machine is deployed in a business network environment of a user and has a main function of capturing mirror traffic in a virtual environment and carrying out forwarding according to purposes appointed by the protocol. A mirror traffic distributor isdeployed in a non-business network environment, so influences of network loads on normal network communication of the business network environment of the user do not need to be taken into consideration. The mirror traffic distributor has the main function of copying and distributing traffic according to a multi-purpose traffic analysis device appointed by the protocol. A mirror traffic central controller uniformly controls forwarding logic of the whole mirror network traffic and provides a software defined interface.
Owner:QINGDAO XIANGZHI ELECTRONICS TECH CO LTD
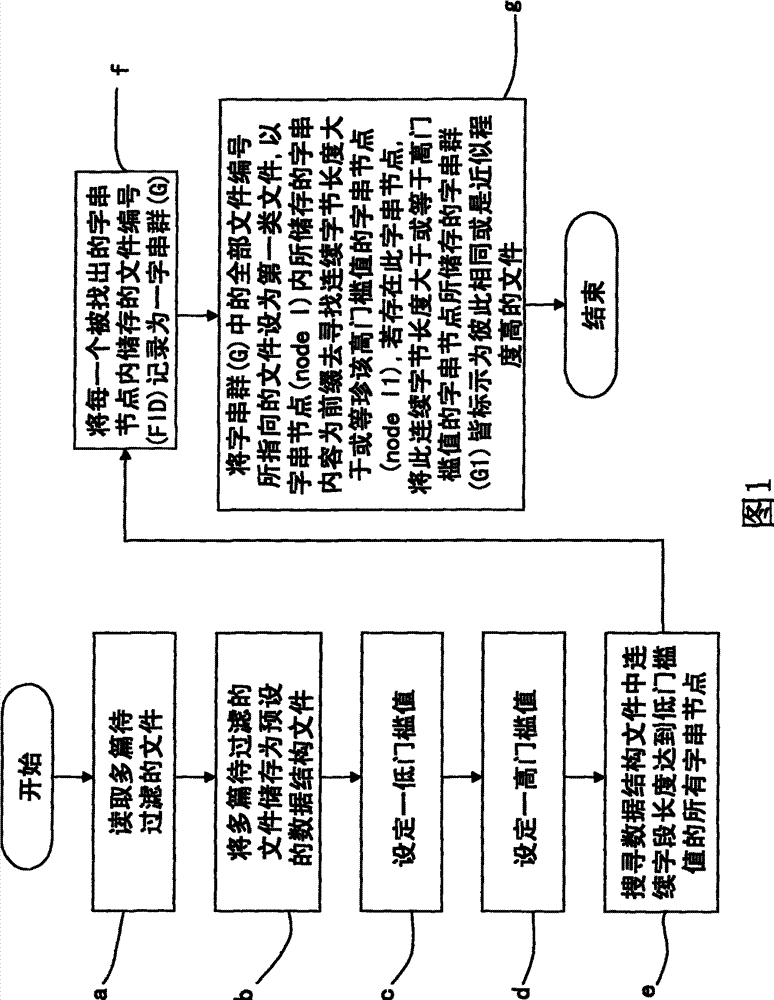
Method for filtering same or similar files
InactiveCN101714147AResolve duplicationReduce duplicationSpecial data processing applicationsTree (data structure)Database
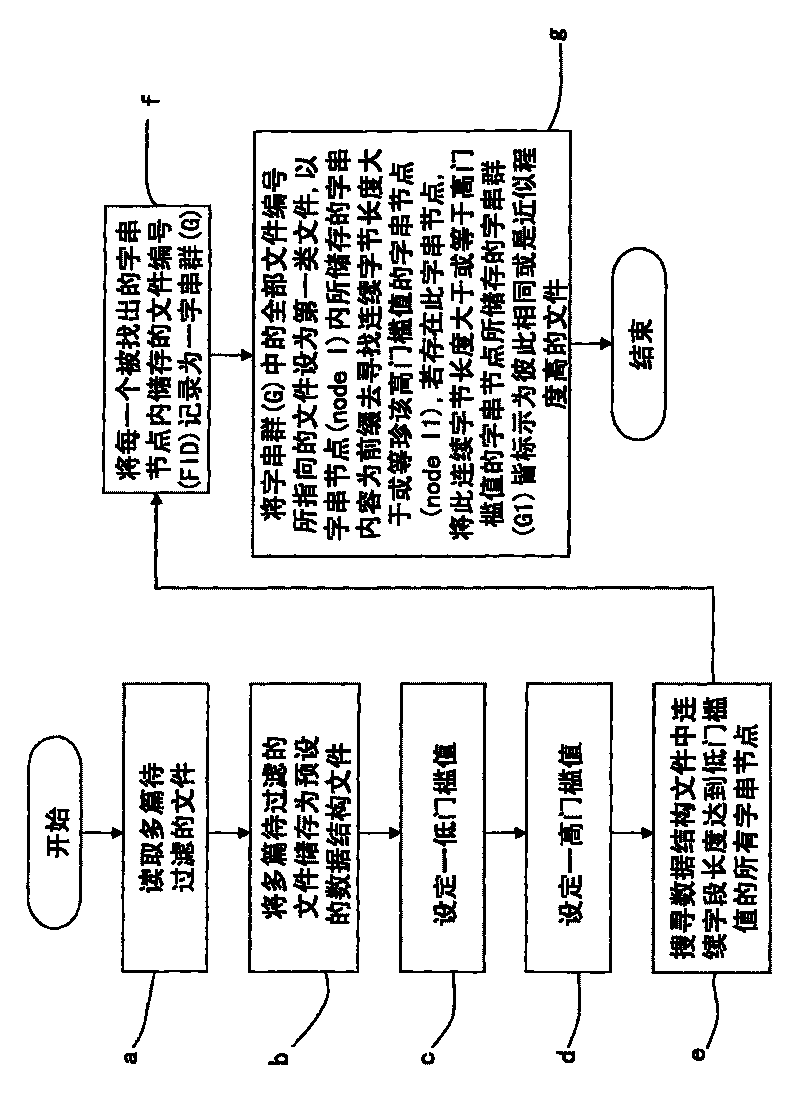
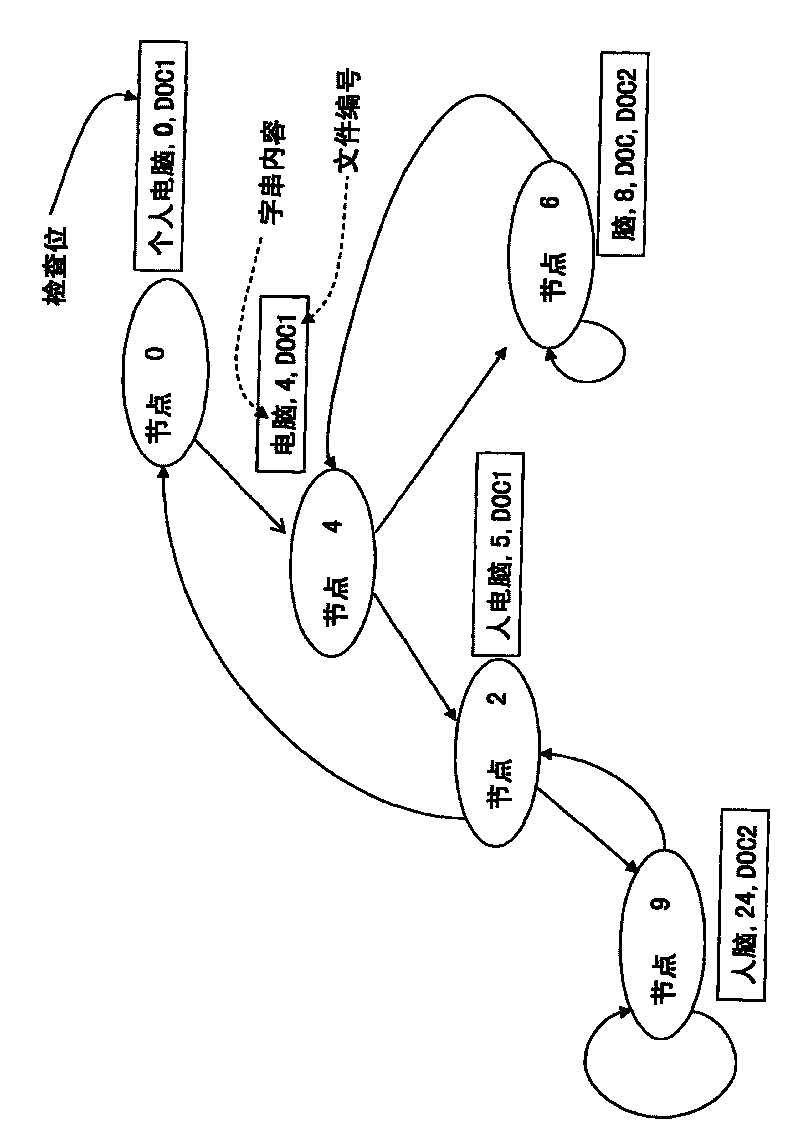
The invention discloses a method for filtering the same or similar files. The method comprises the following steps of: storing a plurality of files to be filtered into a pat tree data structure file (PT file) in a pat tree data structure; searching all the character string nodes of which continuous character length reaches a low threshold and all the files to which the character string nodes belong in the PT file; searching files in which continuous character contents are same, and the same continuous character length reaches a high threshold in the files; searching all the character string nodes of which continuous character length reaches a low threshold and all the files to which the character string nodes belong in the PT file; searching files in which continuous character contents are same, and the ratio of the same continuous character length to the total length of the prior file content reaches a ratio threshold; and marking the files as files having the same content or high degree of approximation. The method can filter the files having the same content or high degree of approximation and solves the problem repeating a great number of same or similar files.
Owner:ESOBI
Automatic irrational number speed ratio grinding and polishing machine
ActiveCN106737127AAchieve ultra-smooth and low-damageAchieve damageGrinding carriagesGrinding drivesDrive shaftEngineering
The invention discloses an automatic irrational number speed ratio grinding and polishing machine. The automatic irrational number speed ratio grinding and polishing machine comprises a traditional grinding machine, a connecting seat, an X-axis movable sliding table, a Y-axis movable sliding table, a Z-axis movable sliding table, a driving rotation motor, a driving synchronous pulley, a driven synchronous pulley, a motor driving shaft, a driving shaft, an upper grinding and polishing disc, a lower grinding and polishing disc and a movable plate. According to the automatic irrational number speed ratio grinding and polishing machine, irrational number rotation is conducted through the driving rotation motor, the driving shaft is controlled to conduct irrational number rotation, the requirement of the upper grinding and polishing disc and the lower grinding and polishing disc for the irrational number speed ratio can be met, thus, the problem that grinding paths of grinding particles on a workpiece are repeated under the condition of the rational number speed ratio is solved, the surface quality of planar grinding machining is improved, and ultra-smooth and low-damage machining of the surface of the workpiece is achieved; and through a strip-shaped hole in the motor driving shaft, the situation that an upper grinding disc spindle and a lower grinding disc spindle are locked when the feeding amount is too large can be effectively prevented, and the safety of grinding and polishing is improved.
Owner:ZHEJIANG UNIV OF TECH
Integrated data-handling method and device based on multi-system user
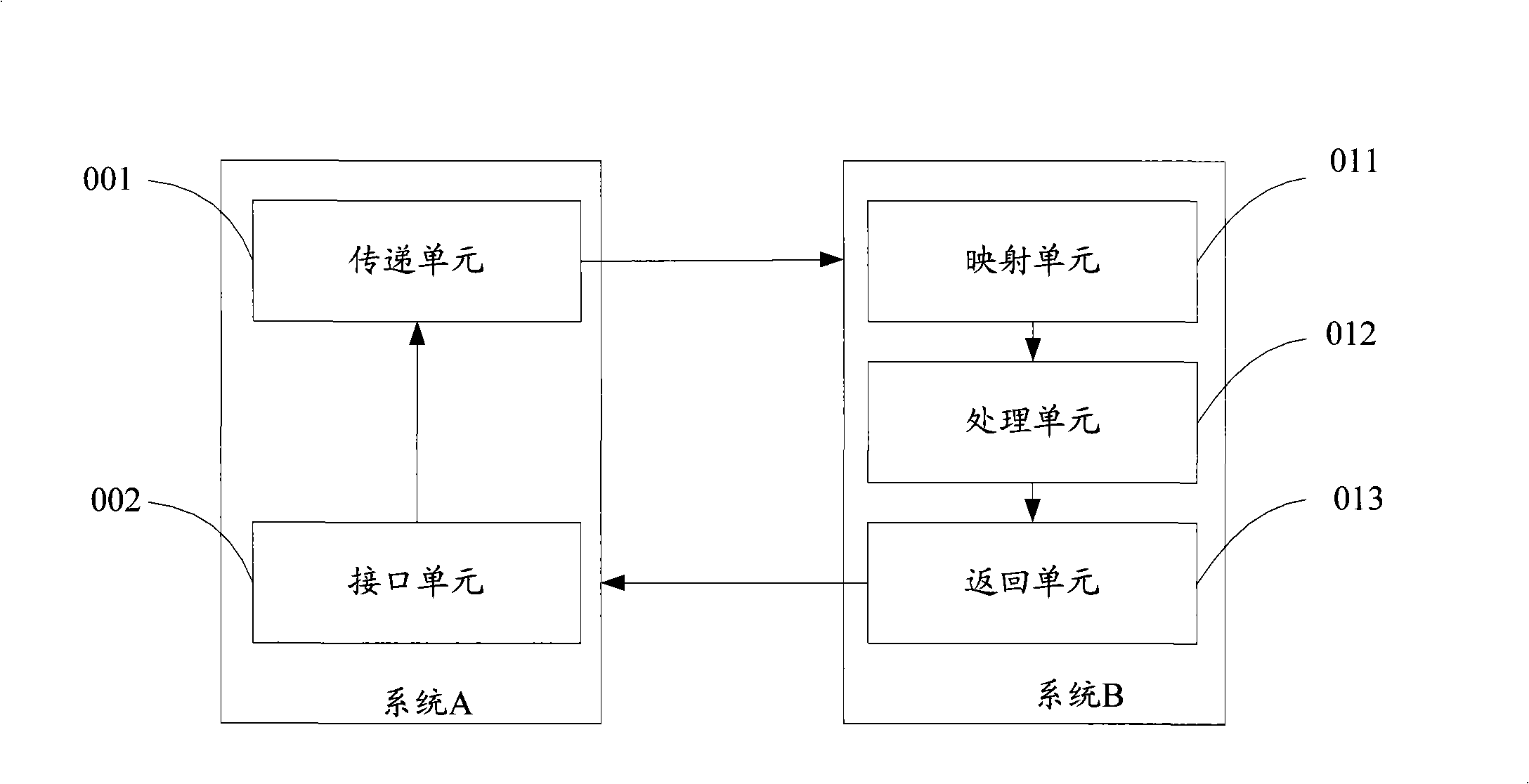
InactiveCN101287018AAvoid the build processAchieve integrationUser identity/authority verificationResourcesComputer scienceData processing
The invention discloses a data processing method and a device based on multisystem user integration. In the method provide by the invention, an access request for a system B is submitted by the user in a system A; the system A sends a sole identity mark and the access request to the system B; the system B maps out corresponding information of the user according to the sole identity mark and carries out data processing according to the access request and the information of the user; the system B sends the result of the data processing and the sole identity mark back to the system A. The device provided by the invention comprises the system A consisting of an interface unit and a transmission unit and the system B consisting of a mapping unit, a processing unit and a returning unit. The method and device provided by the invention can avoid verbose work brought by the establishment and maintenance of user association table in the user integration and lead the realization of the user integration to be simple and easy.
Owner:KINGDEE SOFTWARE(CHINA) CO LTD
Payment authentication system based on combination of hand veins and multiple fingerprints
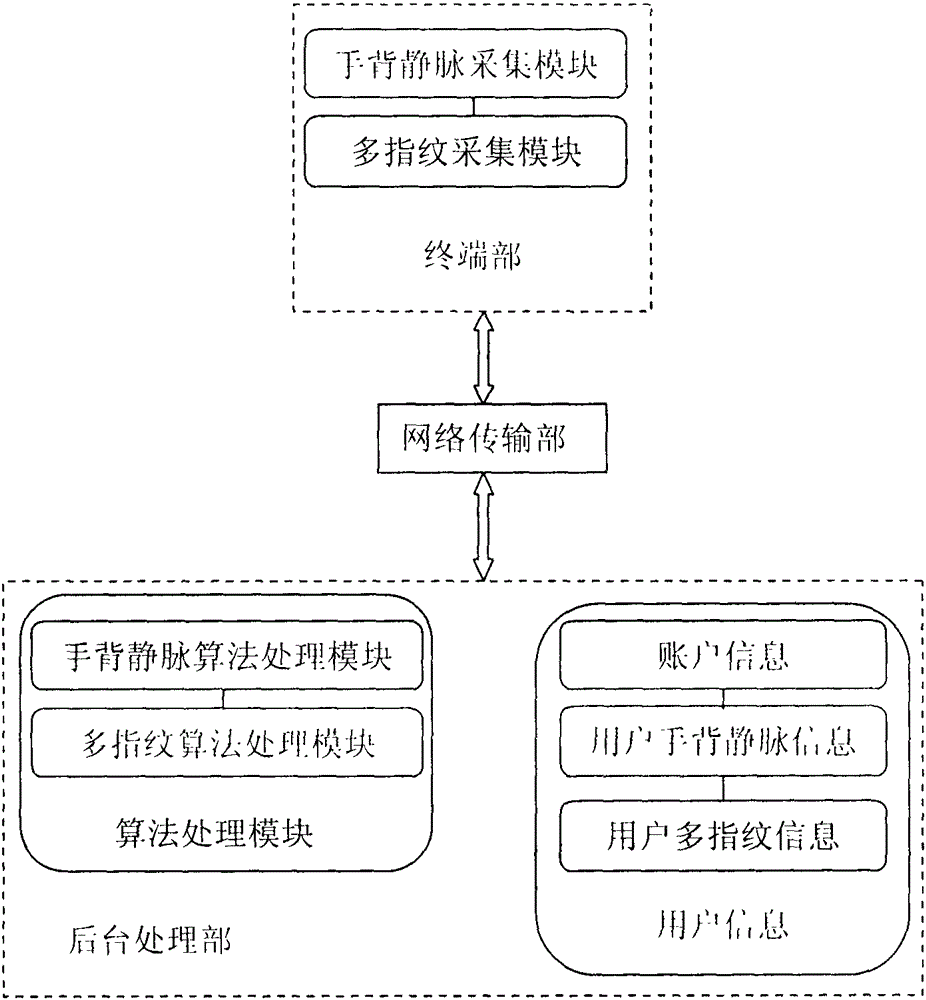
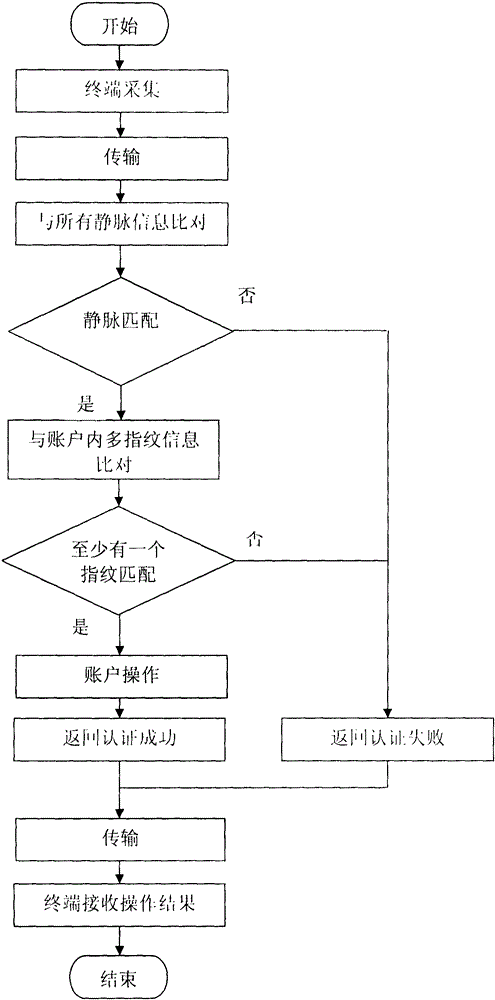
Provided is a payment authentication system based on the combination of hand veins and multiple fingerprints, comprising a terminal portion, a network transmission portion and a background processing portion, and employing a mode of first registering an account and then performing transaction authentication. In operation of the system, the terminal portion collects user hand veins and multiple fingerprints, and transmits collected data to the background processing portion through the network transmission portion; the background processing portion respectively matches the user hand veins and multiple fingerprints with the user information recorded in the system, and returns information; the network transmission portion transmits the returned information to the terminal portion. The system employs a double authentication mode based on the combination of hand veins and multiple fingerprints to perform account authentication, and can effectively improve the security and correctness of account authentication in a payment process.
Owner:TIANJIN POLYTECHNIC UNIV
Method and apparatus for paged loading of client contents
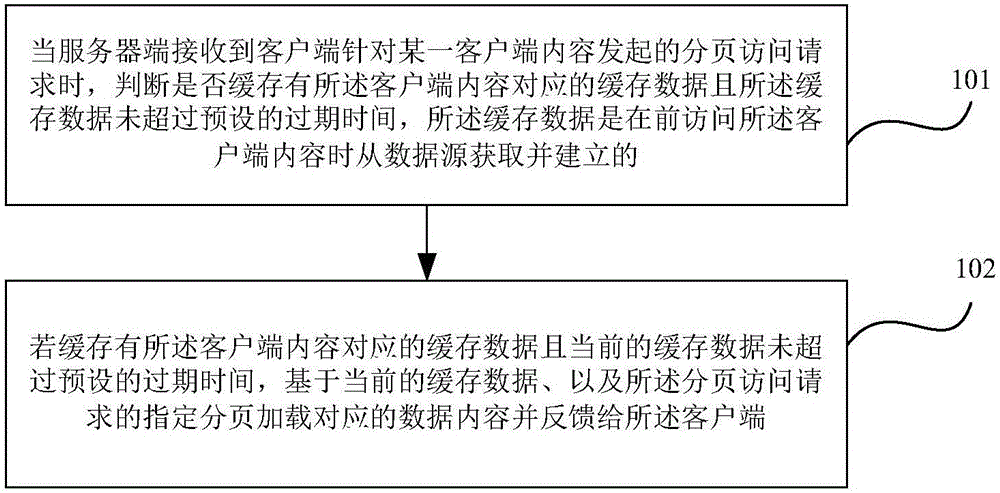
ActiveCN106708568ATimely updateResolve duplicationProgram loading/initiatingExecution for user interfacesClient-sideData content
Embodiments of the invention provide a method and an apparatus for paged loading of client contents. The method comprises the steps of judging whether cached data corresponding to the client contents is cached or not and that the cached data does not exceed preset expiration time when a server receives a paged access request initiated for the client contents by a client, wherein the cached data is obtained from a data source and established when the client contents are accessed; and if the cached data corresponding to the client contents is cached and the current cached data does not exceed the preset expiration time, loading corresponding data contents based on the current cached data and a specified page of the paged access request, and feeding back the corresponding data contents to the client. The technical scheme has the following beneficial effects: the problem that data seen by a user during page turning operation is repeated while the data is updated in a scene that an update frequency is relatively high and data sorting is re-updated each time can be solved.
Owner:MICRO DREAM TECHTRONIC NETWORK TECH CHINACO
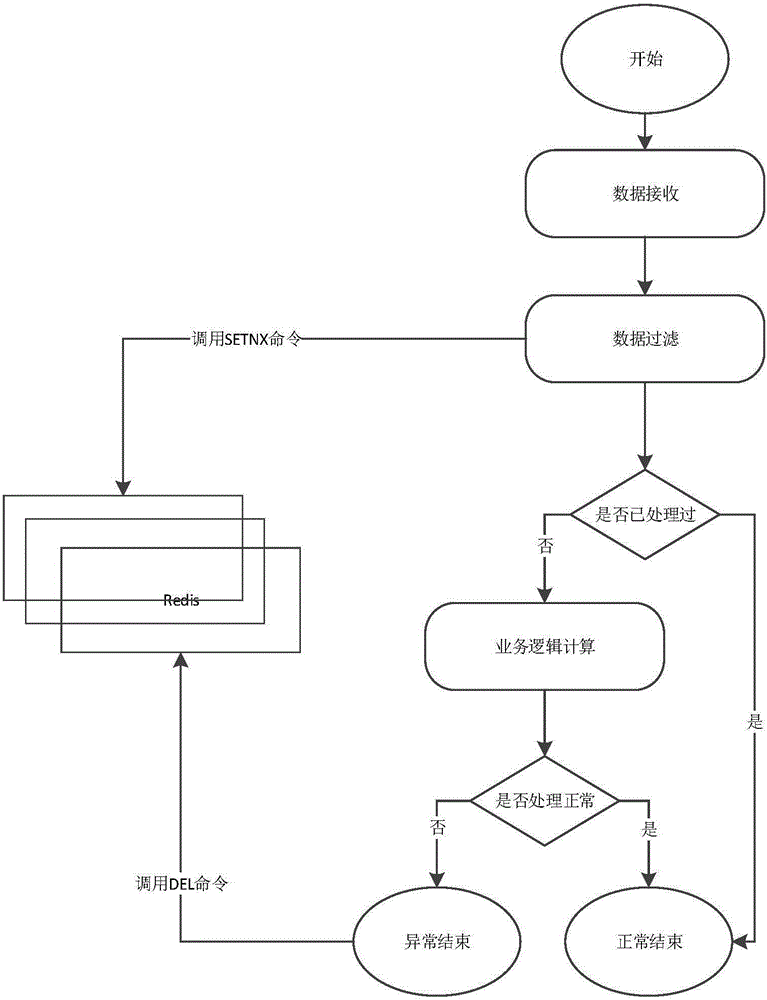
Kafka message uniqueness method based on Redis
The invention relates to a Kafka message uniqueness method based on Redis. Redis is utilized to solve the problem of message repeated consumption in Kafka. The method comprises the steps that: Kafka receives message data; a distributed vote algorithm is adopted to filter the received message data; business logic processing is carried out on the message data after the filtering; and whether the business logic processing is wrong is judged, if yes, the message data wrong in business logic processing is deleted, and if not, the process is ended normally. Compared with the prior art, the Kafka message uniqueness method has the advantages that the message repeated consumption is avoided, the handling capacity is high, and the reliability is high.
Owner:上海浦东发展银行股份有限公司信用卡中心
Server supporting cascade connection of multiple backboards
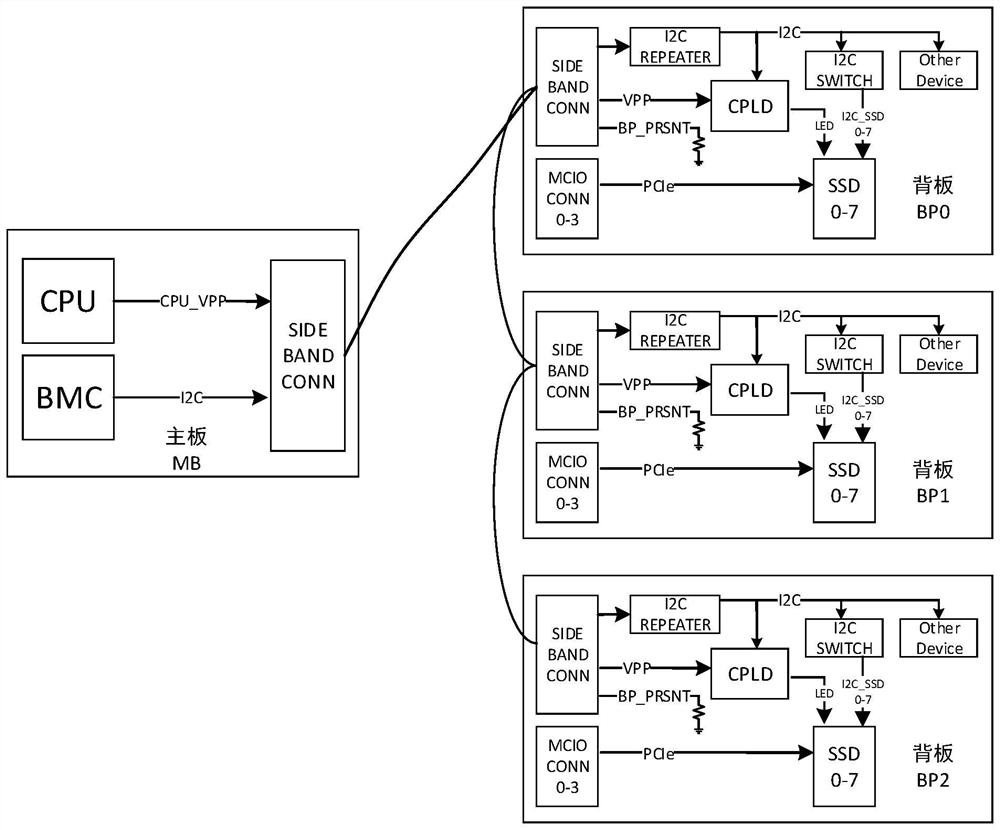
ActiveCN113448402AResolve duplicationUnified designDigital processing power distributionEmbedded systemBus
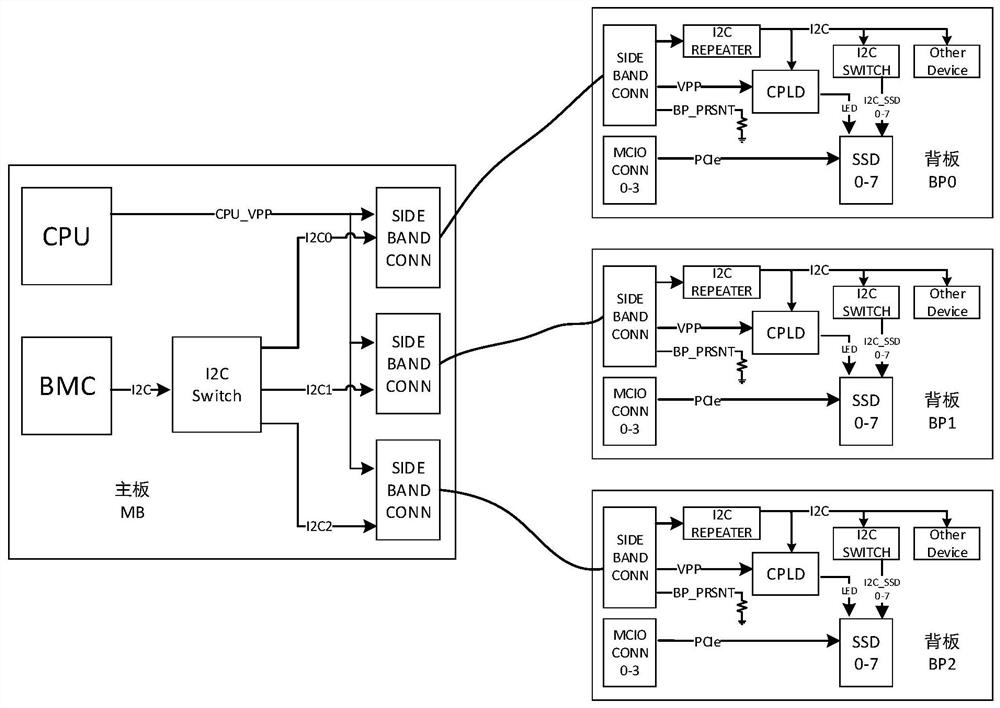
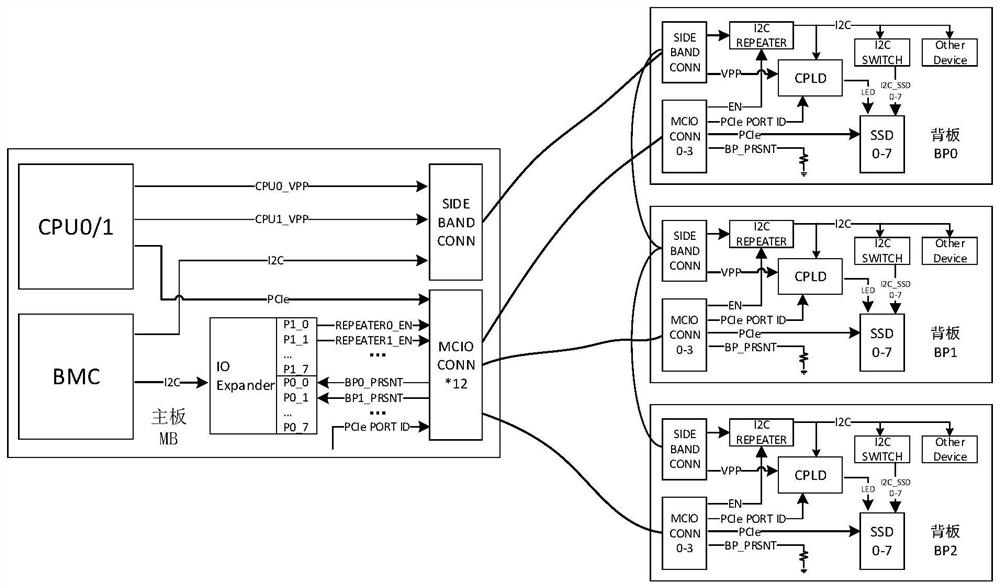
The invention discloses a server supporting cascade connection of multiple backboards. The server comprises a mainboard, the mainboard is provided with a BMC, a mainboard low-speed connector, an Expander chip and a plurality of mainboard high-speed connectors, the BMC is connected to the mainboard low-speed connector through an I2C bus, and the BMC is connected to the Expander chip through the I2C bus; a plurality of backboards, each backboard is provided with an I2C repeater, a backboard low-speed connector and a backboard high-speed connector, the backboard low-speed connector and the backboard high-speed connector are connected with the I2C repeater, the multiple backboard low-speed connectors are sequentially connected in series and then connected with the mainboard low-speed connectors, and each backboard corresponds to one mainboard high-speed connector, each backboard high-speed connector is connected with the corresponding mainboard high-speed connector and then is connected to the Expander chip; the BMC is configured to detect the in-place backboards and enable the I2C repeater of any in-place backboard, and the backboards where the enabled I2C repeaters are located serve as gated backboards. The server provided by the invention solves the problem of duplicate I2C addresses of cascaded backboards, improves the polling efficiency of the BMC accessing the backboard equipment, and reduces the load of the I2C bus.
Owner:SHANDONG YINGXIN COMP TECH CO LTD
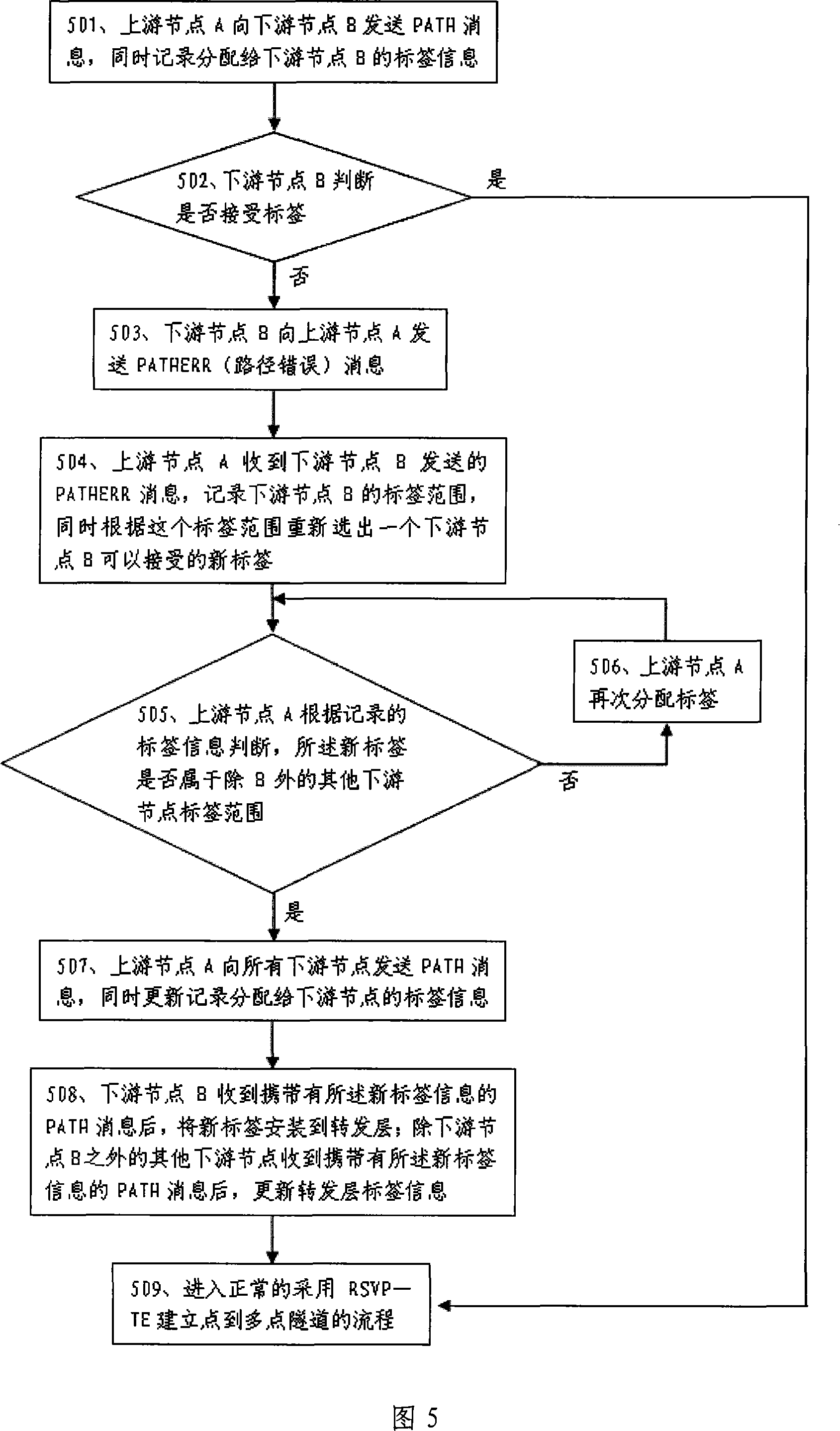
Upstream node label allocation method and system for point-to-point tunnel
InactiveCN101150503ANo repetitionResolve duplicationSpecial service provision for substationDistribution systemComputer science
The invention relates to the communications field, which discloses a method for upstream label distribution used in peer-to-multipeer tunnel to ensure that the label remains the same when a plurality of upstream nodes distribute an identical label to the same downstream node. The method introduces a negotiation mechanism between upstream nodes and downstream nodes; after distributing a label to a downstream node, if an upstream node receives feedback label information from the downstream node, the upstream node then redistributes a label to the downstream node based on the feedback information from the downstream nodes. At the same time, the invention also discloses an upstream label distribution system applied in peer-to-multipeer tunnel.
Owner:GLOBAL INNOVATION AGGREGATORS LLC
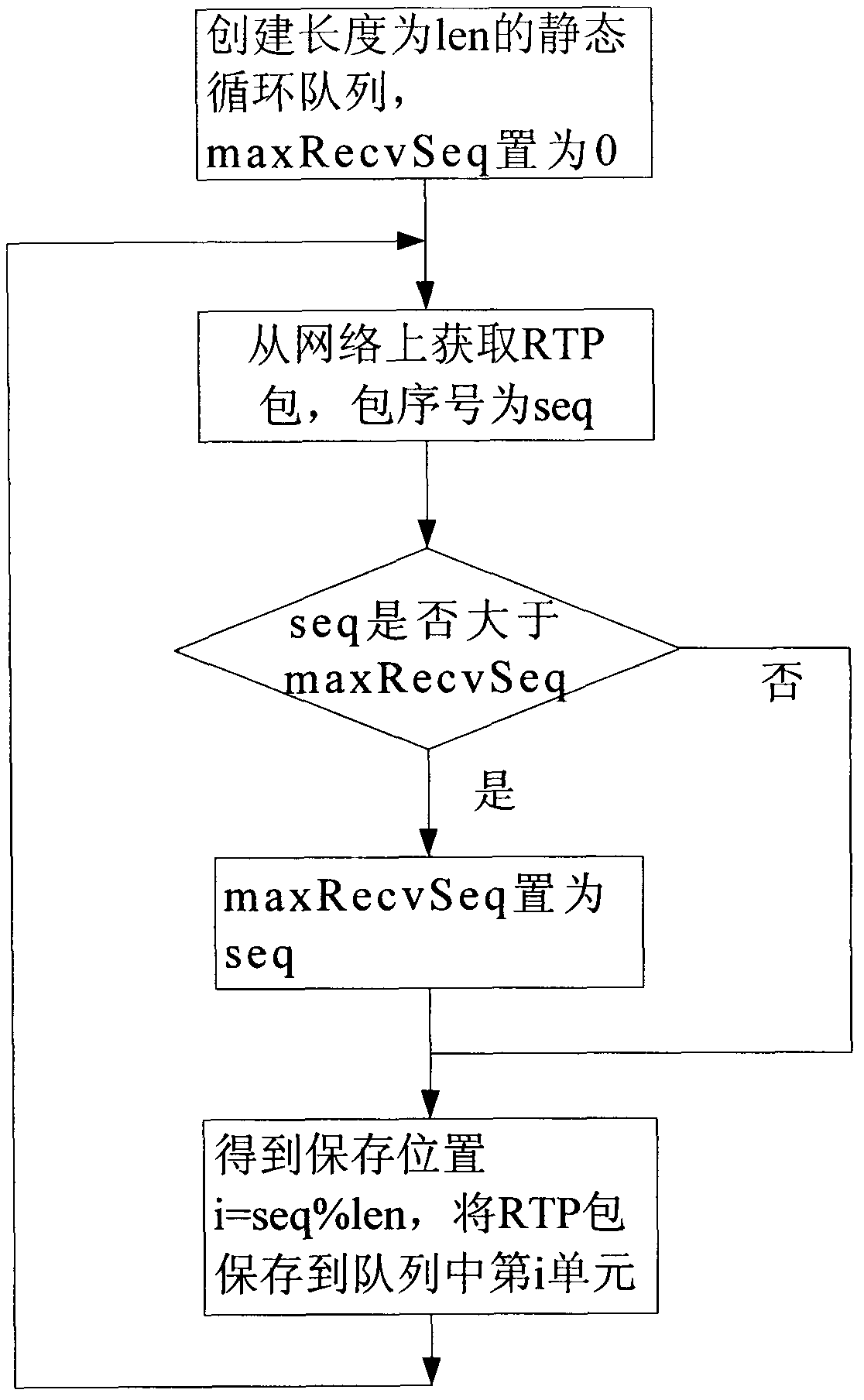
Method for removing jitter, disorder and repeated packets when receiving RTP packets
InactiveCN103108256AEliminate jitterEliminate packet duplicationSelective content distributionReal-time Transport ProtocolReal-time computing
The invention discloses a method for removing jitter, disorder and repeated packets when receiving RTP (Real-time Transport Protocol) packets. The method comprises the steps as follows: before receiving the RTP packets by a system, creating a static circular queue with the length of len, wherein each unit in the queue is used for storing one RTP packet; when normally receiving the RTP packets, carrying out modulus operation on len by a packet sequence number seq of RTP to obtain a storage position i=seq%len; storing the packets into the ith unit in the queue; and when the number of the packets in the queue reaches a certain value, uniformly taking out the RTP packets from the queue for processing so as to achieve the purpose of removing jitter. According to the method, the process of receiving the RTP packets is simplified by utilizing the characteristic that the RTP packet reading and writing positions can be quickly obtained by the static circular queue, so that the system overhead is greatly reduced.
Owner:SUZHOU INDAL PARK YUNSHI INFORMATION TECH
Policy online test method, device and equipment
ActiveCN110290024AImprove iteration efficiencySolve redundancyData switching networksTest flowCode redundancy
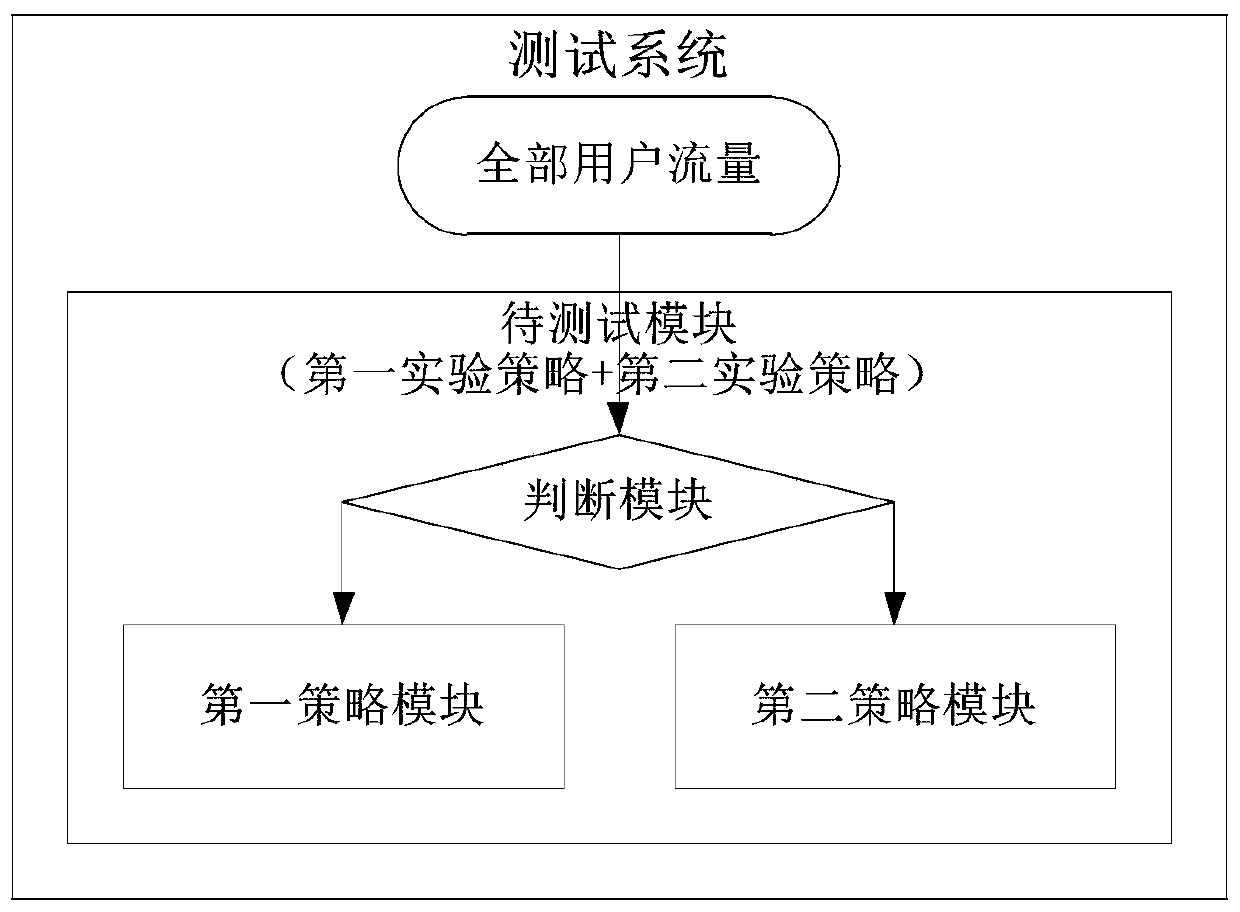
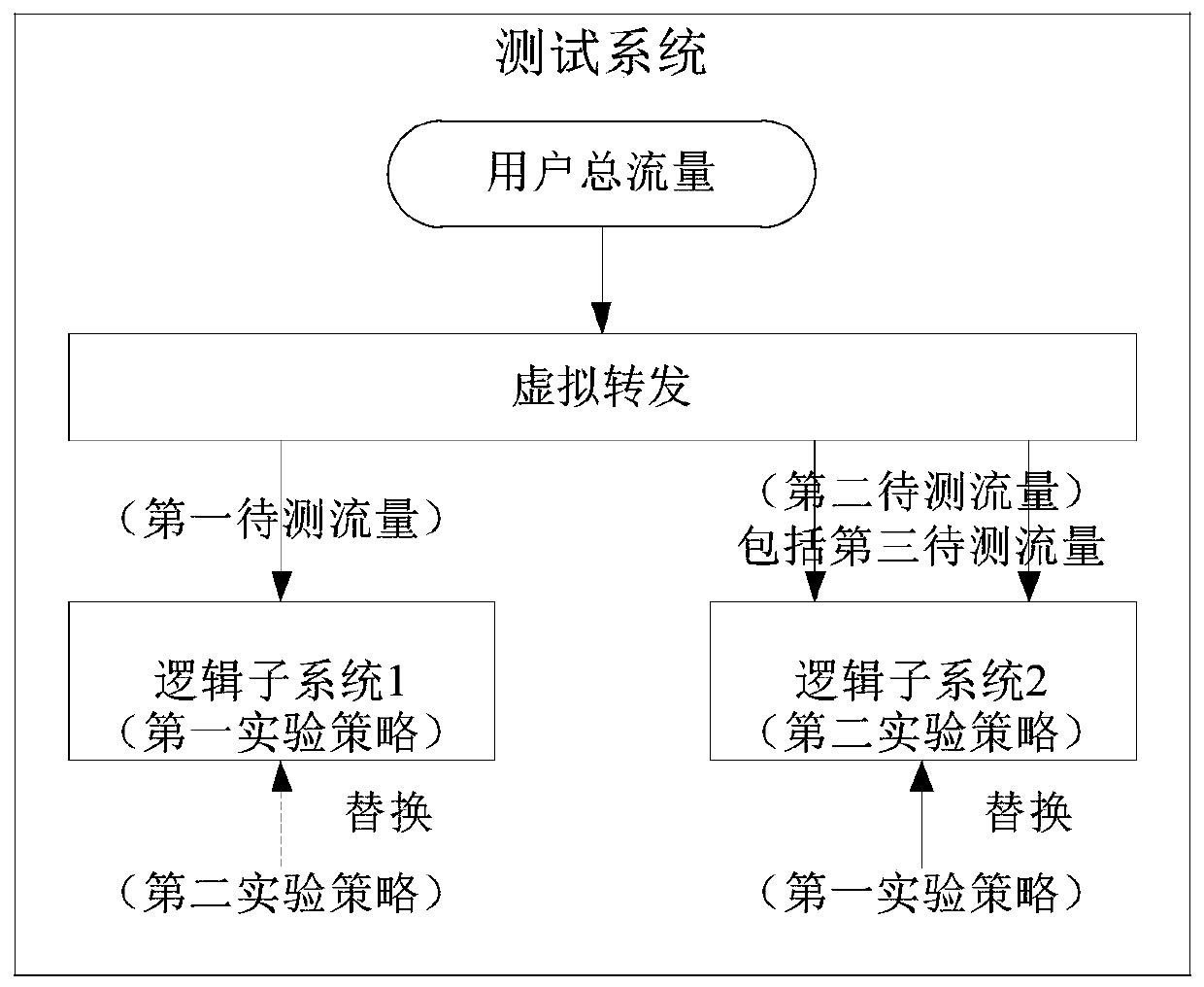
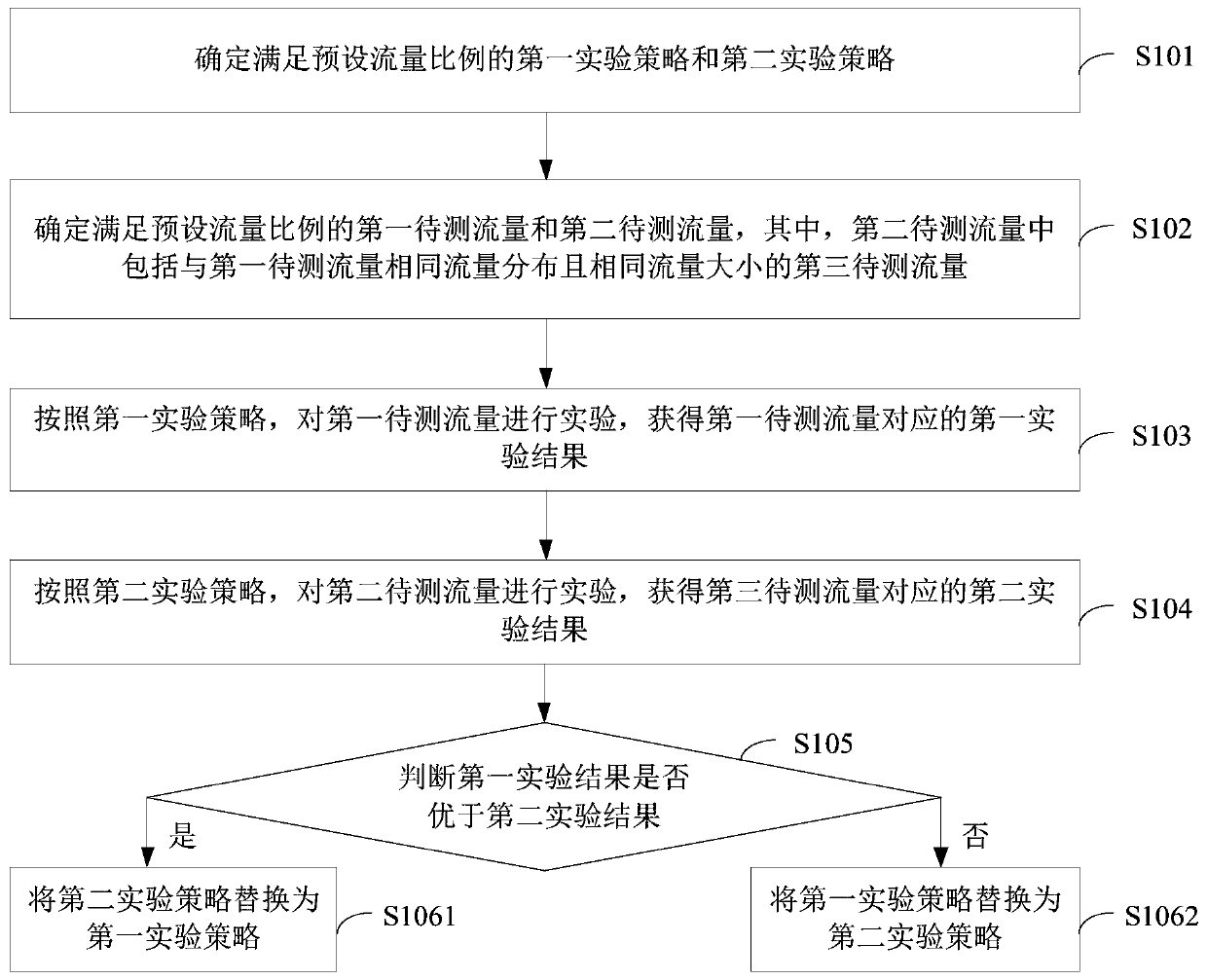
The invention provides a policy online test method, device and equipment. The method comprises the following steps: determining a first experiment strategy and a second experiment strategy meeting a preset flow ratio; and determining a first to-be-measured flow and a second to-be-measured flow meeting a preset flow ratio, the second to-be-measured flow comprising a third to-be-measured flow having the same flow distribution and the same flow size as the first to-be-measured flow; according to the first experiment strategy, carrying out an experiment on the first to-be-tested flow to obtain a first experiment result corresponding to the first to-be-tested flow; according to the second experiment strategy, carrying out an experiment on the second to-be-tested flow to obtain a second experiment result corresponding to the third to-be-tested flow; if the first experiment result is superior to the second experiment result, replacing the second experiment strategy with the first experiment strategy; and if the second experiment result is superior to the first experiment result, replacing the first experiment strategy with the second experiment strategy. Therefore, the problems of code redundancy and repetition in the traditional technology are solved, and the development and maintenance cost is reduced.
Owner:BEIJING BAIDU NETCOM SCI & TECH CO LTD
Database primary key acquisition method and device
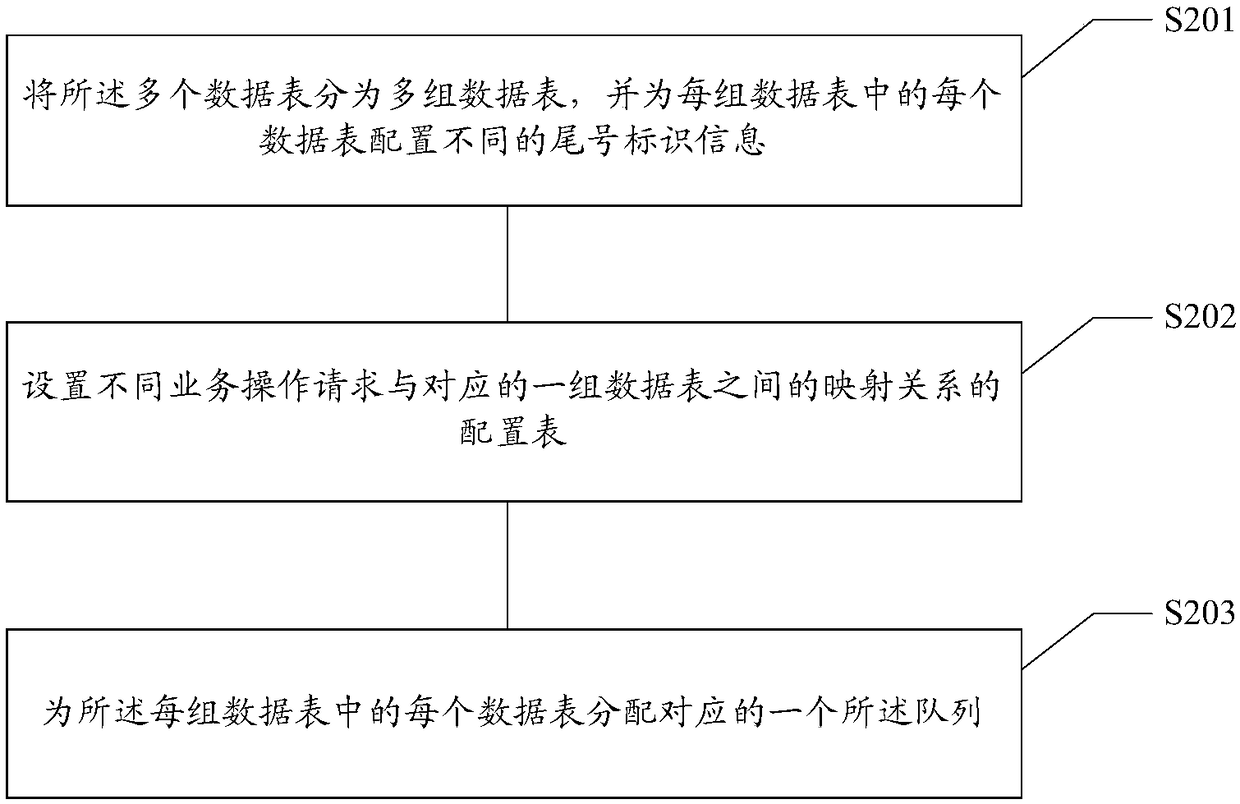
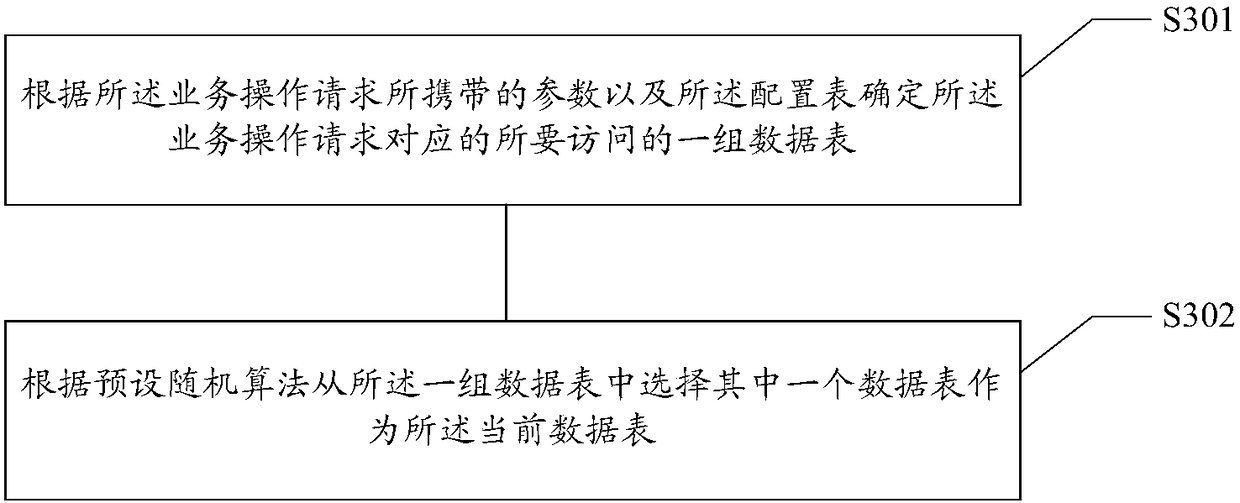
ActiveCN108959285AResolve duplicationImprove service capabilitiesSpecial data processing applicationsData libraryElectronic equipment
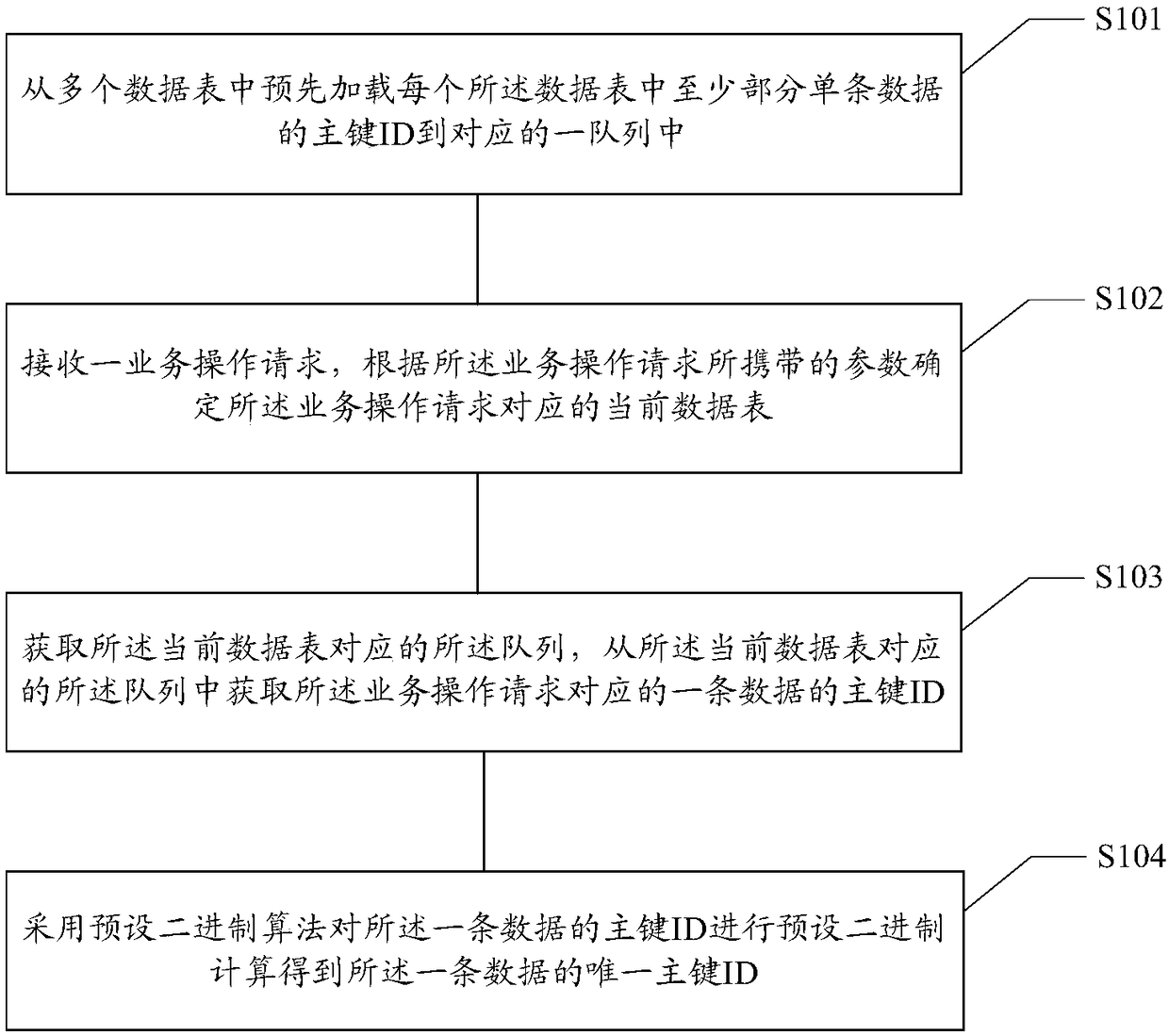
The invention relates to a database primary key acquisition method and device, a storage medium and electronic equipment. The method comprises the following steps: the primary key ID of at least a part of single data in each data table is preloaded into a corresponding queue from a plurality of data tables; receiving a service operation request and determining the current data table correspondingto the service operation request according to parameters carried by the service operation request; obtaining the queue corresponding to the current data table and obtaining the primary key ID of a piece of data corresponding to the service operation request from the queue corresponding to the current data table; and the preset binary algorithm is applied to perform preset binary calculation on theprimary key ID of one piece of data so as to obtain the unique primary key ID of one piece of data. The ID can be directly obtained from the queue without accessing the database so that the service performance can be greatly enhanced, the higher-performance unique ID service can be provided and the performance of the obtained unique primary key ID in the case of a large number of high concurrencycalls can be enhanced.
Owner:BEIJING JINGDONG SHANGKE INFORMATION TECH CO LTD +1
Hotel label automatic configuration method and device, electronic equipment and storage medium
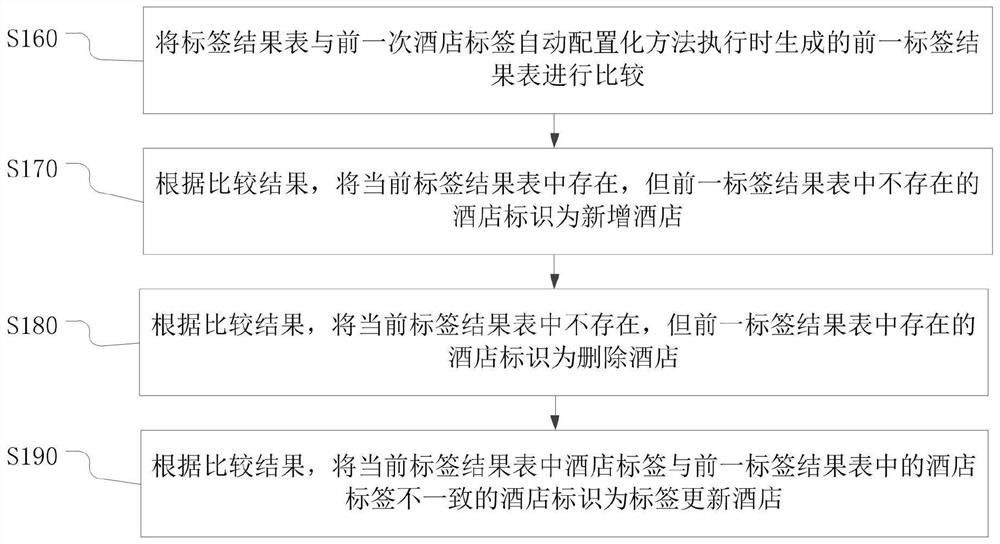
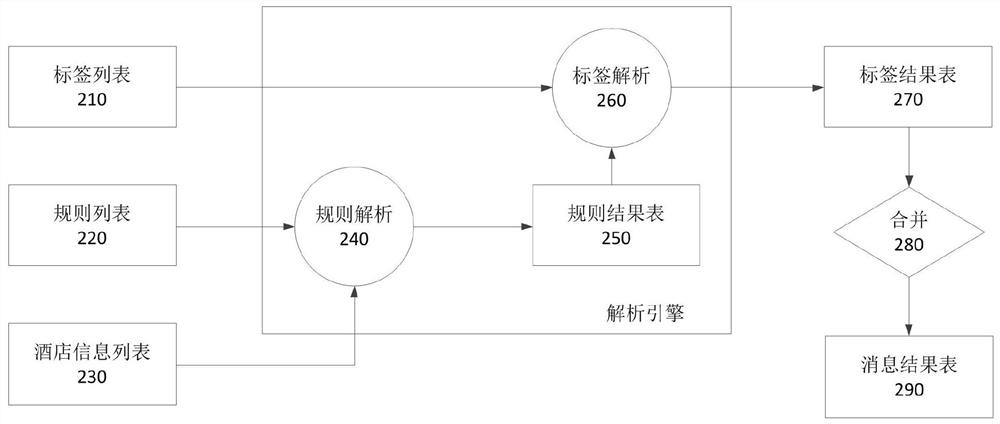
PendingCN112231568AReduce workload and complexitySolve the problem of code duplicationDatabase updatingData processing applicationsEngineeringInformation acquisition
The invention provides a hotel tag automatic configuration method and device, electronic equipment and a storage medium, and the method comprises the steps: obtaining a hotel information list, whereinthe hotel information list stores a plurality of pieces of attribute information of a hotel; obtaining a rule list, wherein each rule item in the rule list comprises a rule identifier, rule content and a tag number associated with the rule content; making rule analysis on the hotel information list and the rule list to generate a rule result table, with the rule result table storing a rule resultof each hotel for each rule item in the hotel information list and a tag number associated with the rule item; obtaining a tag list, wherein each tag item in the tag list comprises a tag number and alogic relationship of a rule associated with the tag number; making tag analysis on the rule result table and the tag list, generating a tag result table, wherein the tag result table stores hotels with rule results meeting the logic relationship and associated tag numbers. The method and the device provided by the invention automatically configure hotel tags.
Owner:CTRIP COMP TECH SHANGHAI
Knowledge graph data mining and recommending method based on dynamic suboptimal minimum spanning tree
PendingCN113626678ALower latencyResolve duplicationWeb data indexingCharacter and pattern recognitionGraph spectraGraph match
The invention discloses a knowledge graph data mining and recommending method based on a dynamic suboptimal minimum spanning tree, which comprises the following steps of: 1) performing isomorphic sub-graph matching in a knowledge graph according to a sub-graph corresponding to a query condition to obtain a plurality of query results; abstracting each query result into a node; 2) constructing a minimum spanning tree of the query results by taking the importance degree of each query result as the sum of the importance degrees of the entities in the query result as the weight of a corresponding node and taking the dissimilarity degree between the query results as an edge weight; and (3) cutting edges in the minimum spanning tree to form a plurality of different connected branches, and respectively returning a node with the highest importance degree in each connected branch to serve as a query result to be output. According to the method, the importance and diversity of the promotion content can be considered at the same time, and the waiting time of the user can be shortened.
Owner:PEKING UNIV
Method and equipment for networking social monitoring resources and monitoring platform
ActiveCN103491346AAchieve accessResolve duplicationClosed circuit television systemsSelective content distributionThird partyDevice type
The invention provides a method for networking social monitoring resources and a monitoring platform. The method comprises the steps that A. a trigger is connected with a server; B. a local area network IP address and the equipment type of the social monitoring resources are reported to the server by the trigger; C. local area network IP address and equipment type information of the social monitoring resources are recorded by the server; D. instruction messages are constructed by the server to instruct the trigger to send triggering messages to the social monitoring resources; E. the triggering messages are constructed by the trigger according to the instruction messages and are sent to the social monitoring resources so as to ensure that response messages are fed back to the server by the social monitoring resources according to the triggering messages; F. the response massages sent by the social monitoring resources are received and processed by the server, reply messages are fed back to the social monitoring resources by the server and the server is connected with the social monitoring resources. The method and equipment for networking the social monitoring resources and the monitoring platform achieve the access of social resources (third-party equipment) under the conditions that original networking is not changed and equipment is not increased.
Owner:ZHEJIANG UNIVIEW TECH CO LTD
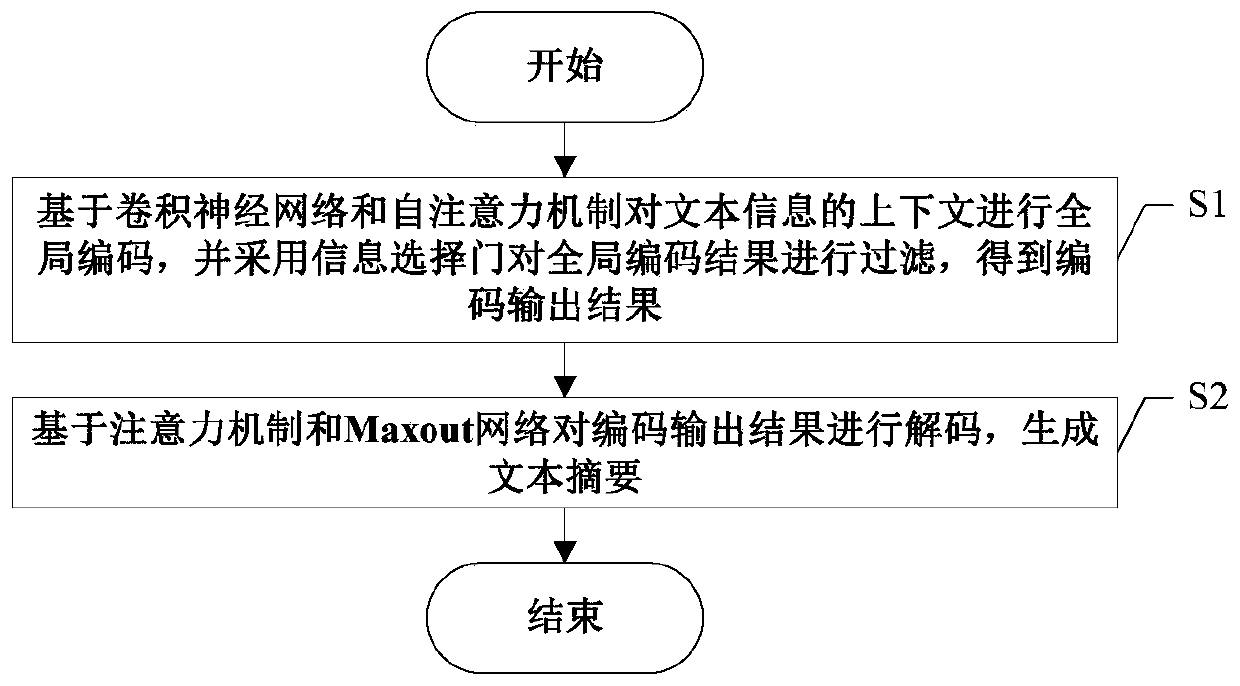
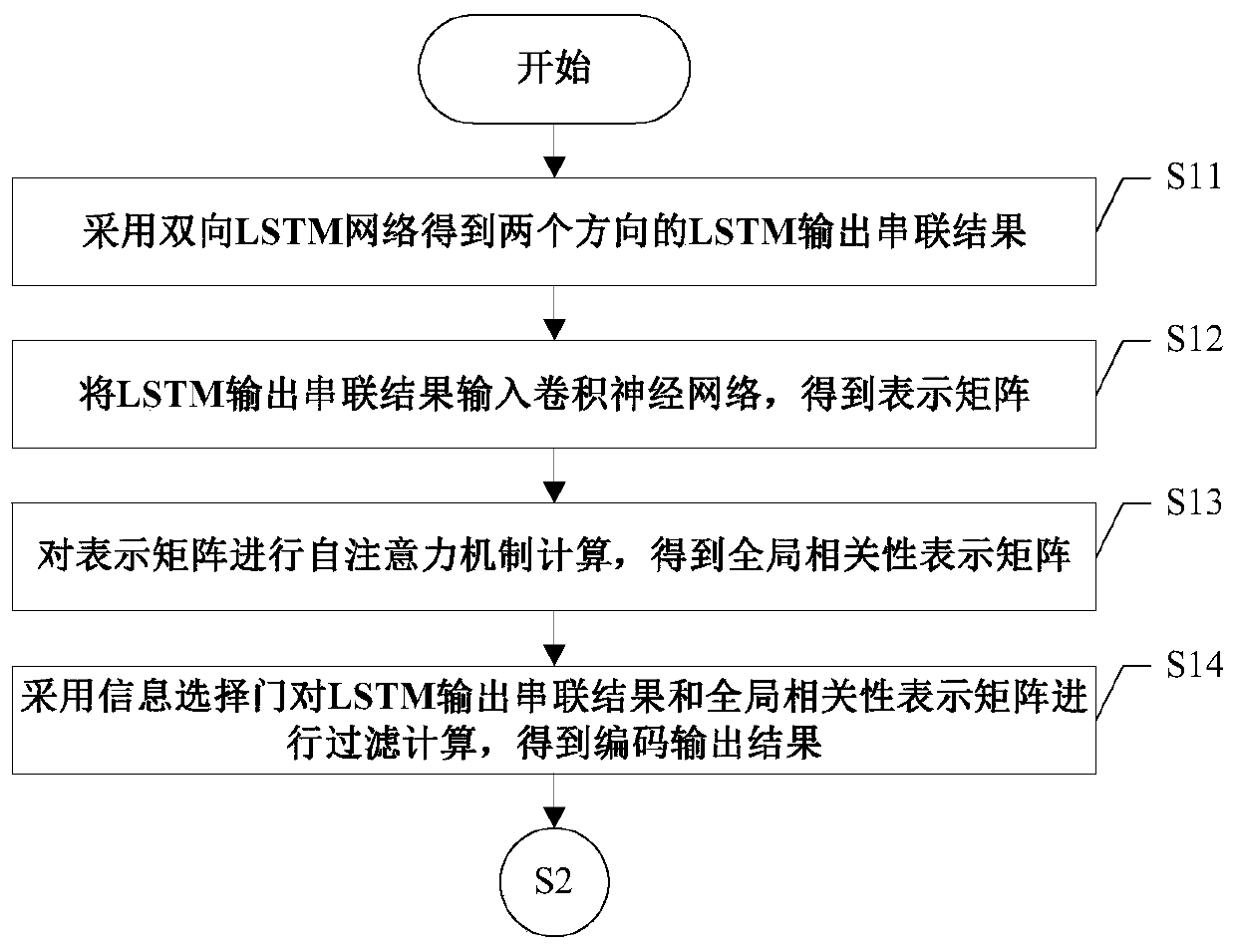
Automatic text abstraction method
ActiveCN110390010AResolve duplicationStrengthen the summary effectText processingNeural architecturesAlgorithmTheoretical computer science
The invention discloses an automatic text abstraction method, and the method comprises the steps: enabling a CNN (Convolutional Neural Network) and a self-attention mechanism self-to carry out the self-attention of the CNN; combining an action, an information selection gate and a Maxout network for use, and controlling inflow of original text information in the information coding stage so as to select important information; and meanwhile, further selecting the most important decoding information as output by using the Maxout network in the decoding stage. According to the method, the problem of repeated abstract word generation is effectively solved, and useless information can be filtered out as much as possible on the basis that important information of an original text is reserved.
Owner:UNIV OF ELECTRONICS SCI & TECH OF CHINA
A mirrored network traffic control method in a virtualized network environment
ActiveCN106100999BEasy accessResolve duplicationData switching networksNetwork communicationSoftware
A software-defined mirroring network traffic control protocol in a virtualized network environment, characterized in that the protocol can adapt to the system structure of mirroring traffic collection, mirroring traffic distribution and mirroring traffic control in a functionally decoupled and distributed deployment, mirroring The traffic collector node / virtual machine is deployed in the user's business network environment, and its main function is to capture the mirrored traffic in the virtualized environment and forward it according to the purpose specified in the protocol; the mirrored traffic distributor is deployed in the non-business network environment In the middle, there is no need to consider the impact of network load on the normal network communication of the user business network environment. Its function is to replicate and distribute traffic according to the multi-purpose traffic analysis device specified in the protocol; the mirror traffic center controller forwards the traffic of the entire mirror network Logic for unified control, providing a software-defined interface.
Owner:BEIJING RUIHE YUNTU TECH CO LTD
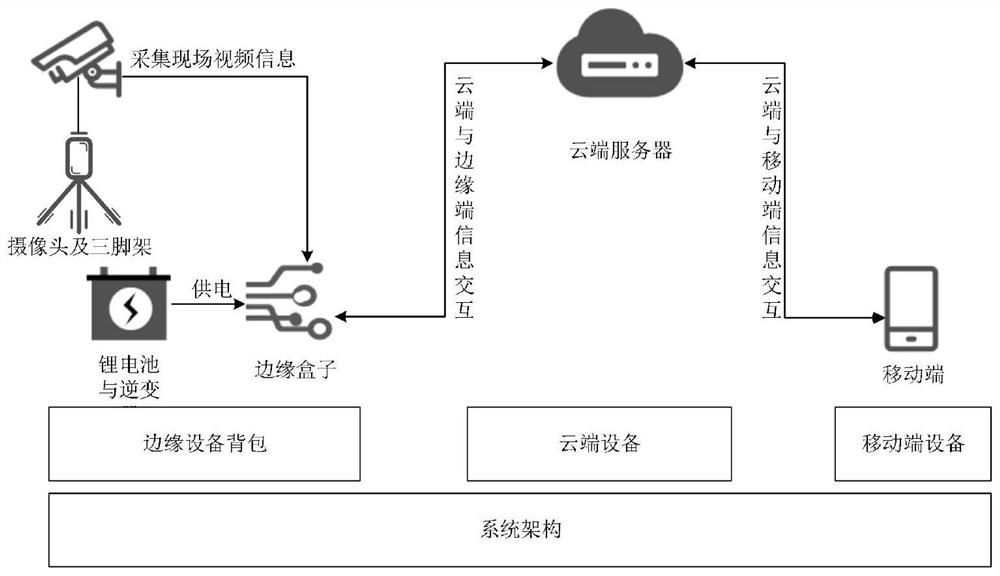
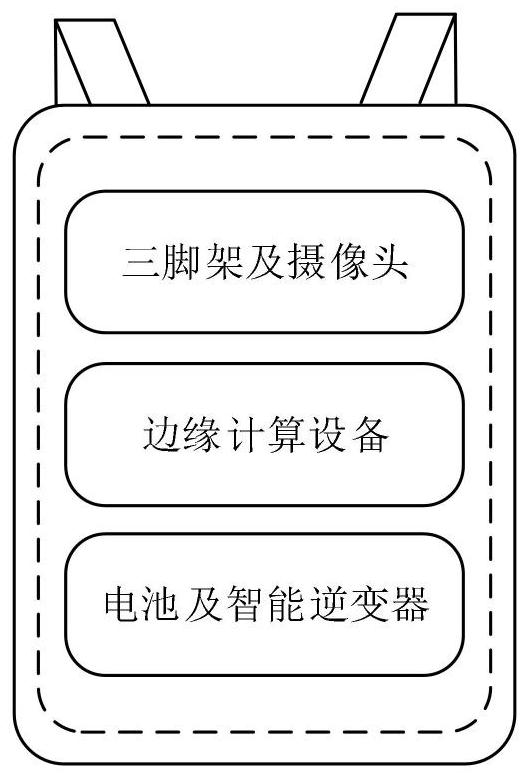
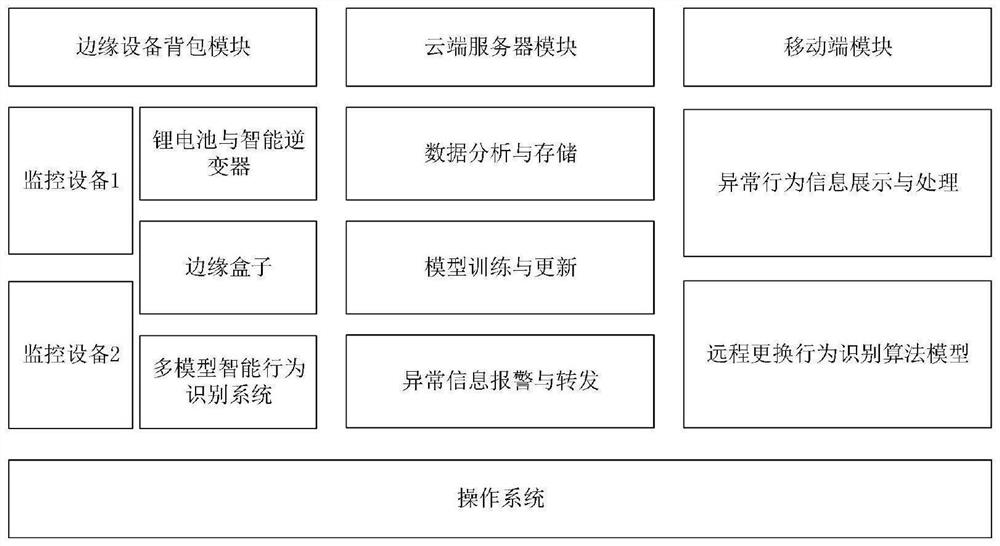
Portable abnormal behavior intelligent analysis system
PendingCN113989931AImplement resizingAdd direction vectorCharacter and pattern recognitionNeural architecturesVideo monitoringEdge computing
The invention provides a portable abnormal behavior intelligent analysis system. The system mainly comprises an edge equipment backpack, a cloud server and a mobile terminal platform. The edge equipment backpack comprises a lithium battery, an intelligent inverter, a monitoring camera, a tripod, an intelligent behavior recognition system and an edge computing device. The intelligent abnormal behavior identification takes edge end equipment as a carrier, and is used for realizing real-time alarm of abnormal behaviors, displaying a result on a mobile terminal and providing an alarm processing function; and the cloud server is used for training the intelligent behavior recognition model and updating parameters. The system aims to build a portable video monitoring alarm platform, deploy cameras, add edge calculation rules, realize an abnormal behavior alarm function, process alarm information in real time and reduce alarm time delay.
Owner:CHONGQING UNIVERSITY OF SCIENCE AND TECHNOLOGY
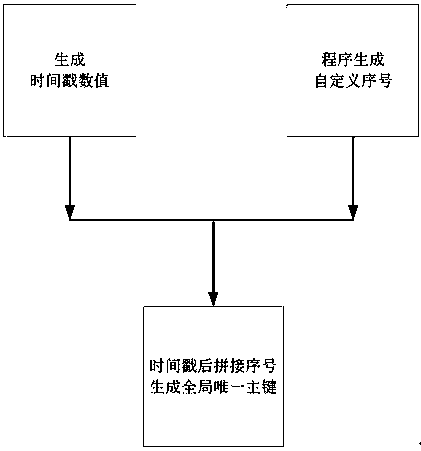
A database primary key generation method suitable for distributed system
InactiveCN109241177ASolve the duplicate database primary keyImprove query efficiencyDatabase distribution/replicationSpecial data processing applicationsTimestampPrimary Key
The invention provides a database primary key generation method suitable for a distributed system, which belongs to the technical field of computer application and solves the problem of primary key conflict of a traditional distributed system. Because the traditional distributed system has multiple terminals, each independent terminal transaction may operate the database at the same time, which iseasy to cause database primary key conflict. To solve this problem, the sequence number and timestamp mechanism are used to avoid primary key collision. Specifically: when the terminal of the distributed system needs to insert data into the database, the current timestamp is generated first, then the timestamp is stitched with the sequence number generated by the program, and finally the primarykey of the database is formed. Because the sequence number is unique, it ensures that the primary key inserted into the database is also unique. The invention can effectively solve the primary key conflict problem caused by the transaction operation of the distributed system, and ensures the uniqueness of the primary key in the database. Compared with the existing method, it is simple and efficient.
Owner:SICHUAN UNIV
Method for filtering same or similar files
InactiveCN101714147BResolve duplicationReduce duplicationSpecial data processing applicationsTheoretical computer scienceTree (data structure)
The invention discloses a method for filtering the same or similar files. The method comprises the following steps of: storing a plurality of files to be filtered into a pat tree data structure file (PT file) in a pat tree data structure; searching all the character string nodes of which continuous character length reaches a low threshold and all the files to which the character string nodes belong in the PT file; searching files in which continuous character contents are same, and the same continuous character length reaches a high threshold in the files; searching all the character string nodes of which continuous character length reaches a low threshold and all the files to which the character string nodes belong in the PT file; searching files in which continuous character contents are same, and the ratio of the same continuous character length to the total length of the prior file content reaches a ratio threshold; and marking the files as files having the same content or high degree of approximation. The method can filter the files having the same content or high degree of approximation and solves the problem repeating a great number of same or similar files.
Owner:ESOBI
A Hardware-Based Reflective Memory Network System
ActiveCN113300893BResolve duplicationFlexible solutionInterprogram communicationNetwork connectionsComputer hardwareComputer network
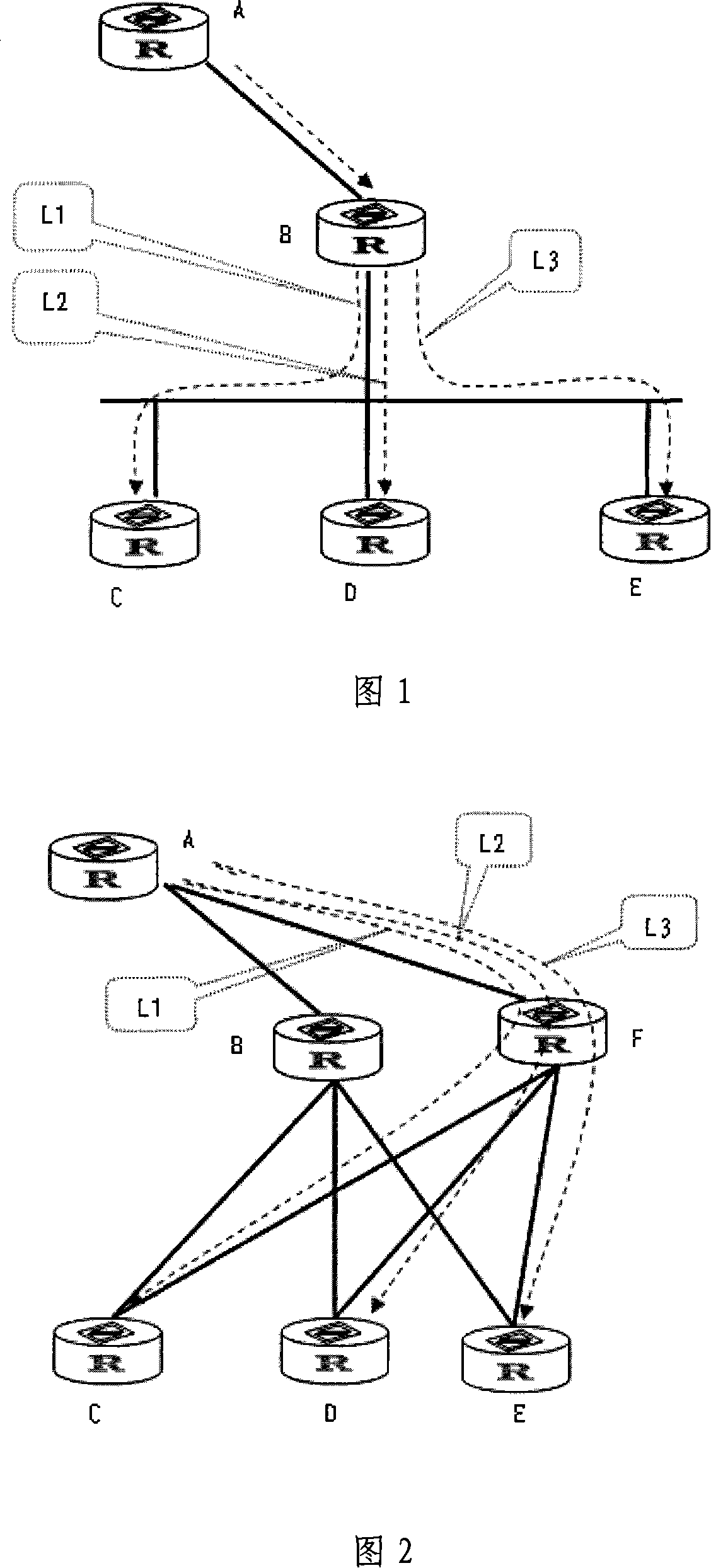
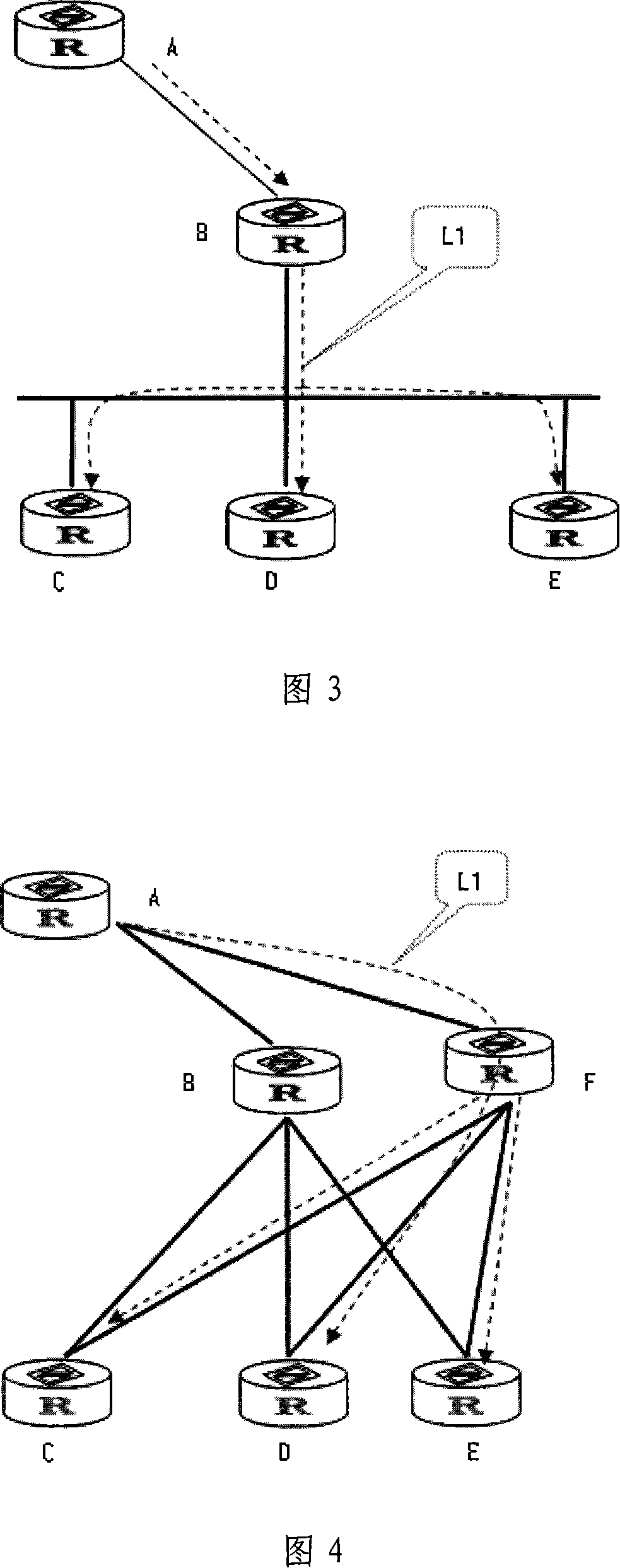
The present invention provides a hardware-based reflective memory network system, including a gateway and multiple reflective memory networks; each reflective memory network includes multiple network nodes, and each network node is provided with a corresponding node number; each Each of the reflective memory networks is respectively connected to a gateway optical port of the gateway, and the node number of the gateway in each of the reflective memory networks is set, and is connected to other network nodes in the reflective memory network. Node numbers are not repeated. The system introduces gateway technology, through which each network is numbered and isolated, but at the same time it can complete data sharing.
Owner:NORTHWESTERN POLYTECHNICAL UNIV
Global unique distributed ID generation method
PendingCN114116060AResolve duplicationMeet the needs of faster growthProgram loading/initiatingComplex mathematical operationsDistributed computingSerial code
The invention discloses a globally unique distributed ID (Identity) generation method, which comprises the following steps of: pre-configuring an embedded publishing mode, and acquiring a local IP (Internet Protocol) when a service instance is started; an instance list file is generated in a local machine, and a machine serial number is returned after service instances are registered; performing bit operation on the IP and the machine serial number to obtain a globally unique machine bit; the method comprises the following steps: defining displacement digit information of each item and a maximum limit sequence of the digit when an ID is generated through idMeta, performing rightward digit operation on the generated ID, and performing AND operation on the generated ID and the maximum limit sequence of the digit to obtain a numerical value of the ID when the ID is generated; and performing leftward operation on the machine bit and the version number, the time type, the current time and the current machine serial number defined by the IdMeta to obtain a unique distributed ID. According to the method disclosed by the invention, the global uniqueness ID can be generated without relying on a central service during embedded use, the problem of ID repetition is solved, the storage space is saved, the performance is improved, and the requirement when the business growth speed is relatively high is met.
Owner:中企云链(北京)金融信息服务有限公司
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com