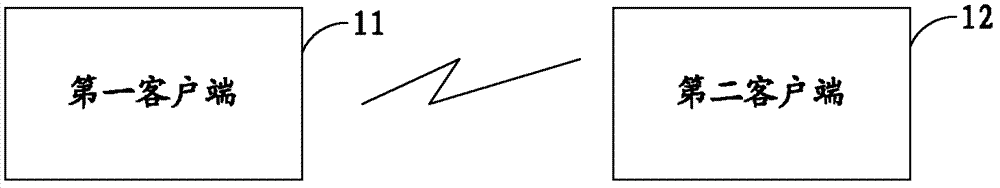Patents
Literature
304 results about "Network traffic control" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
In computer networking, network traffic control is the process of managing, controlling or reducing the network traffic, particularly Internet bandwidth, e.g. by the network scheduler. It is used by network administrators, to reduce congestion, latency and packet loss. This is part of bandwidth management. In order to use these tools effectively, it is necessary to measure the network traffic to determine the causes of network congestion and attack those problems specifically.
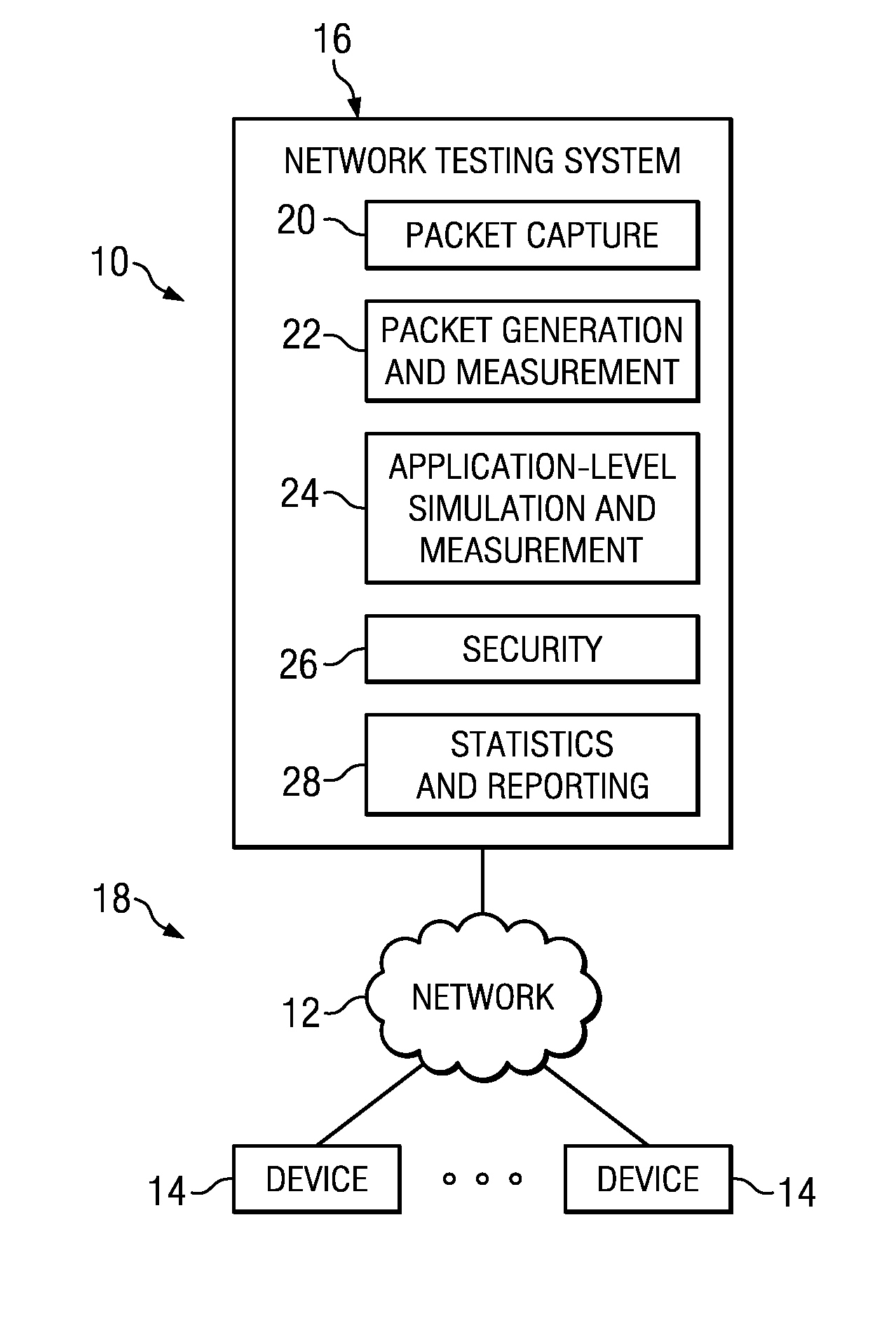
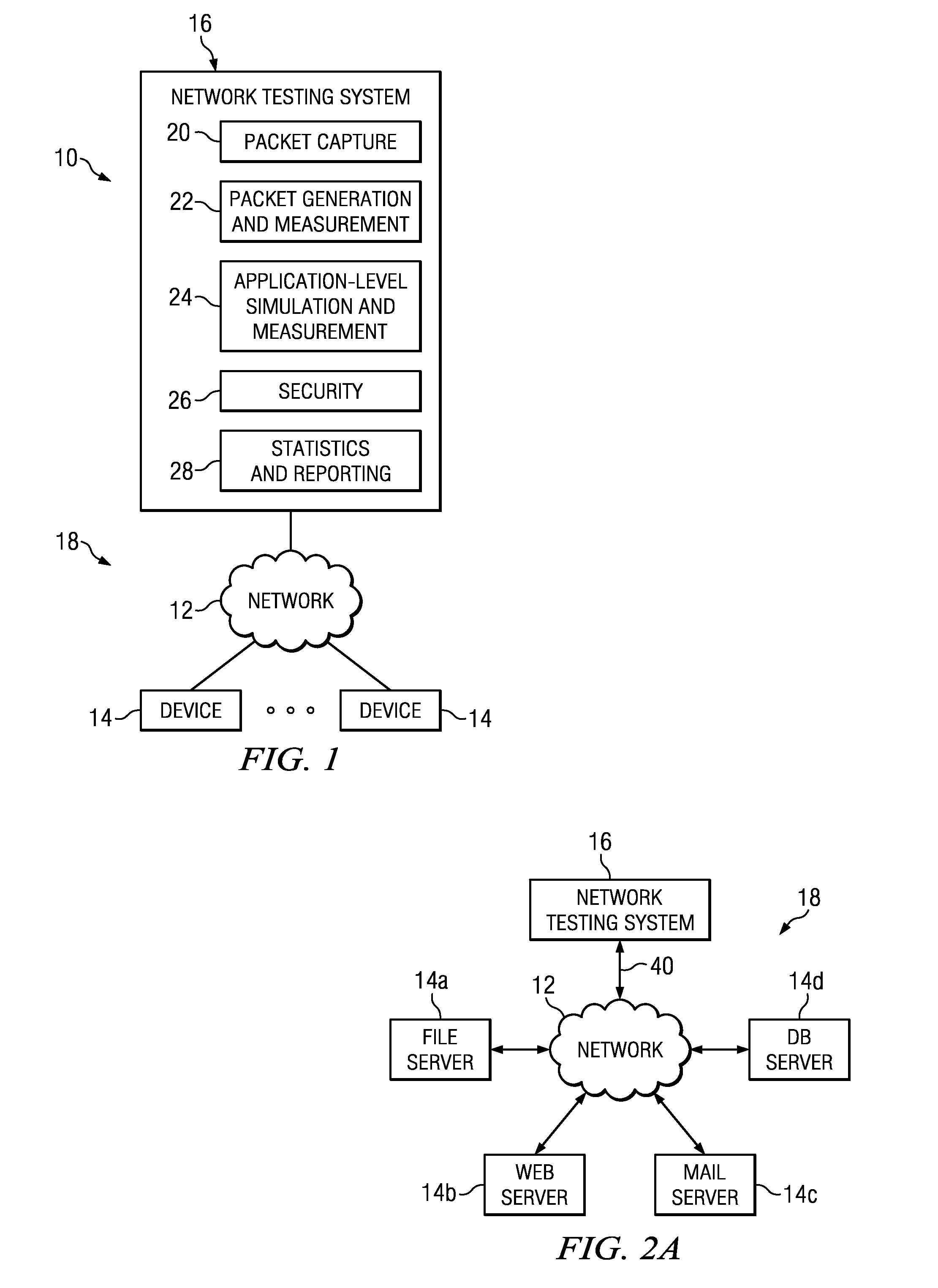
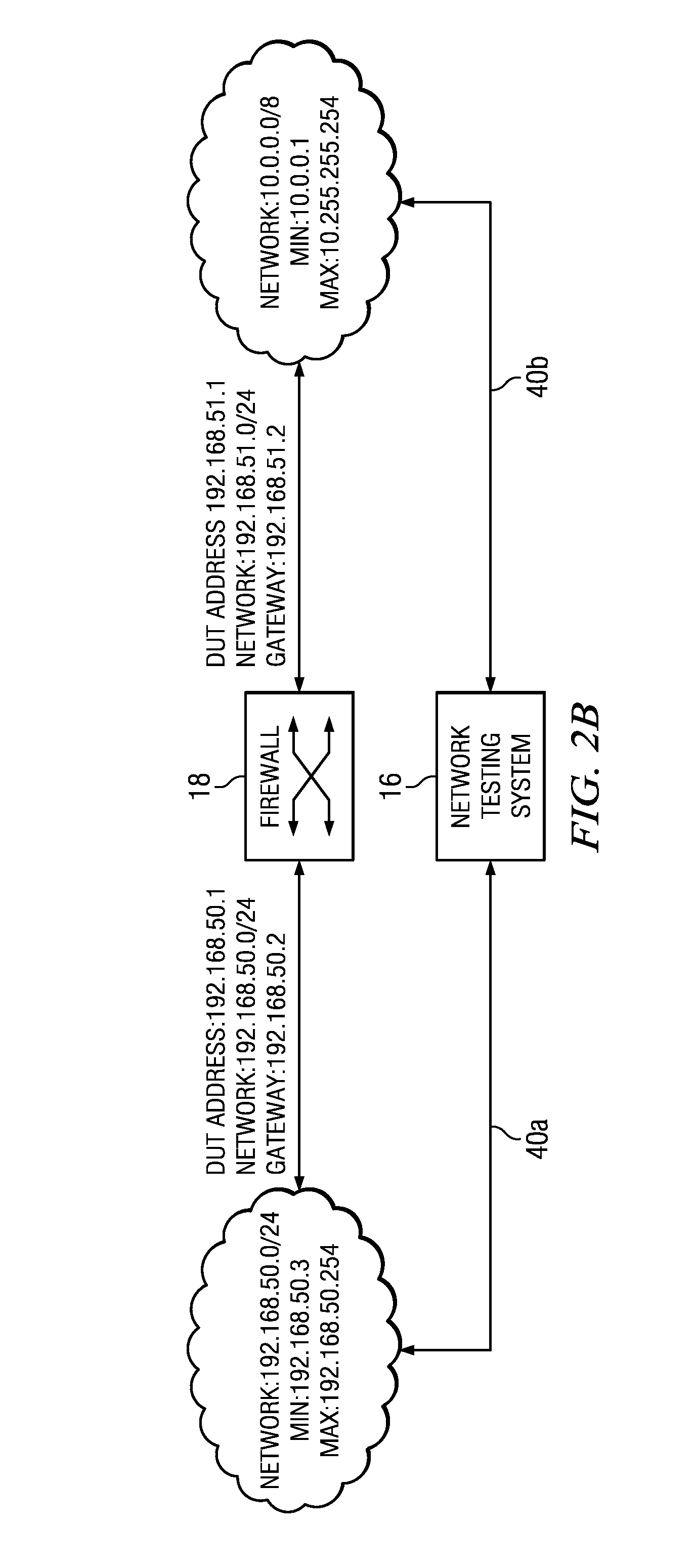
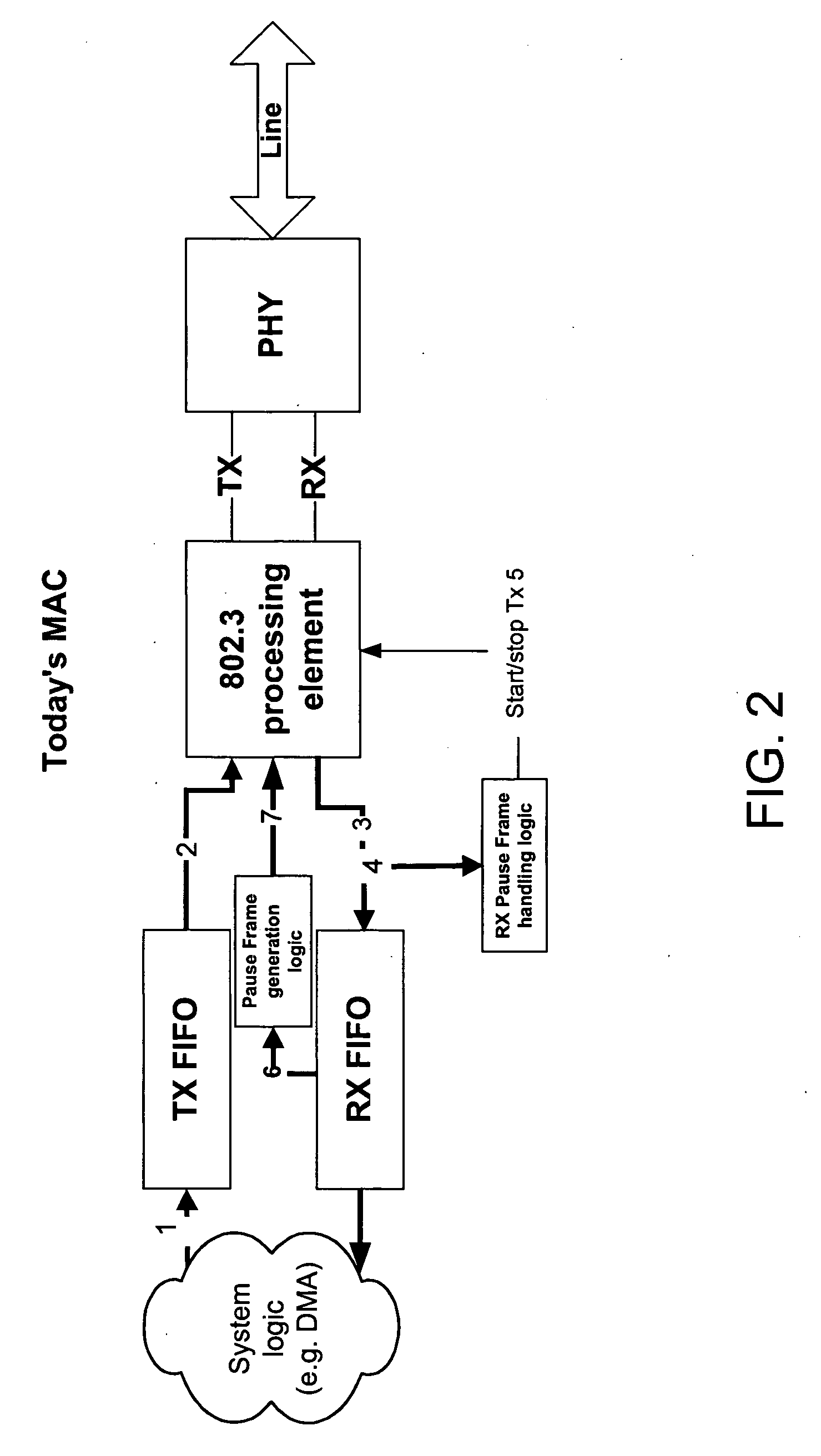
Packet capture for error tracking
A method of tracking network traffic anomalies in a computing system, comprises receiving an ingress network packet at a configurable logic device (CLD), associating a timestamp with the packet, identifying at least one anomaly based on the contents of the packet, and storing the anomalous packet and the timestamp in a persistent memory.
Owner:BREAKINGPOINT SYST
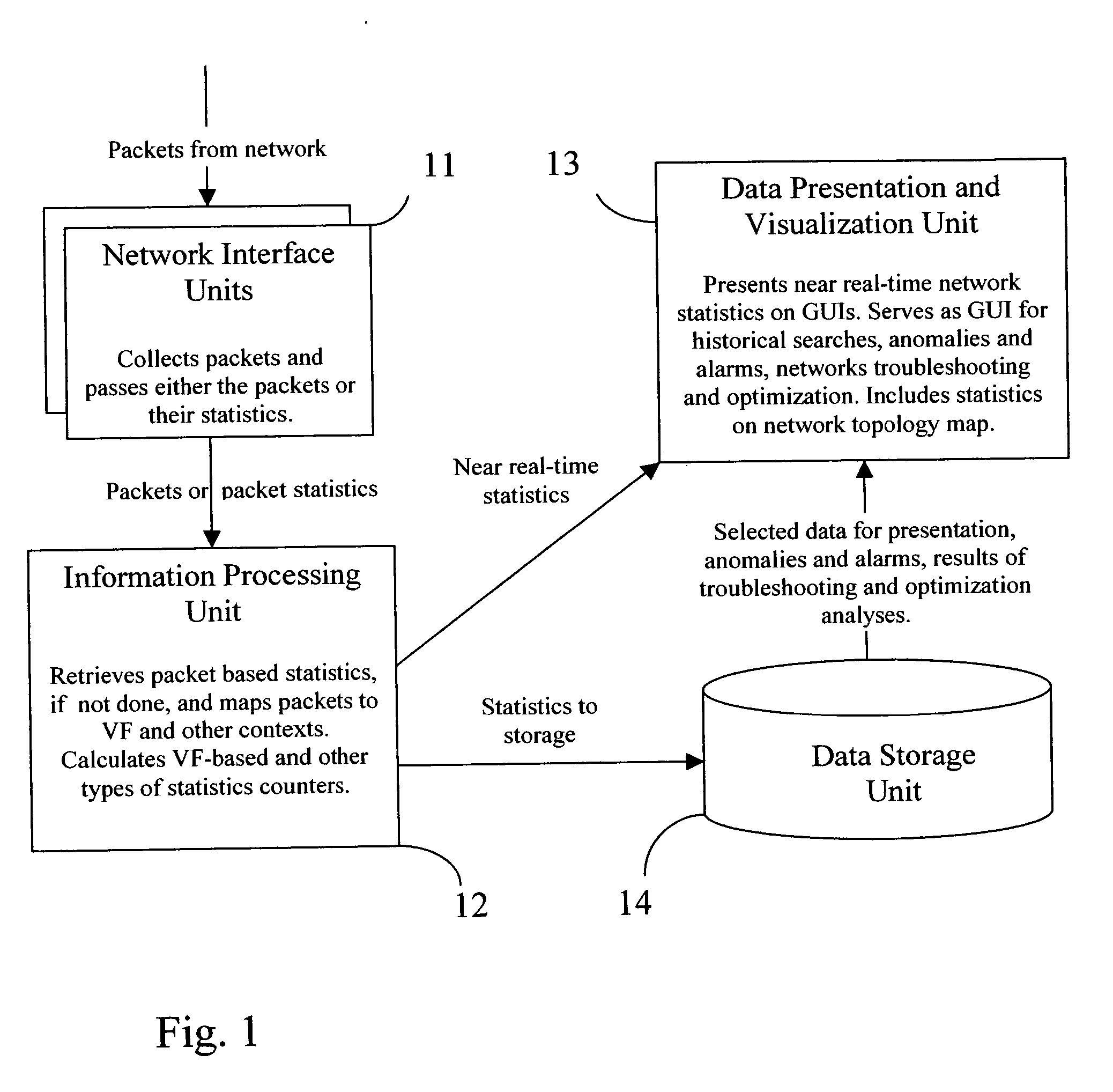
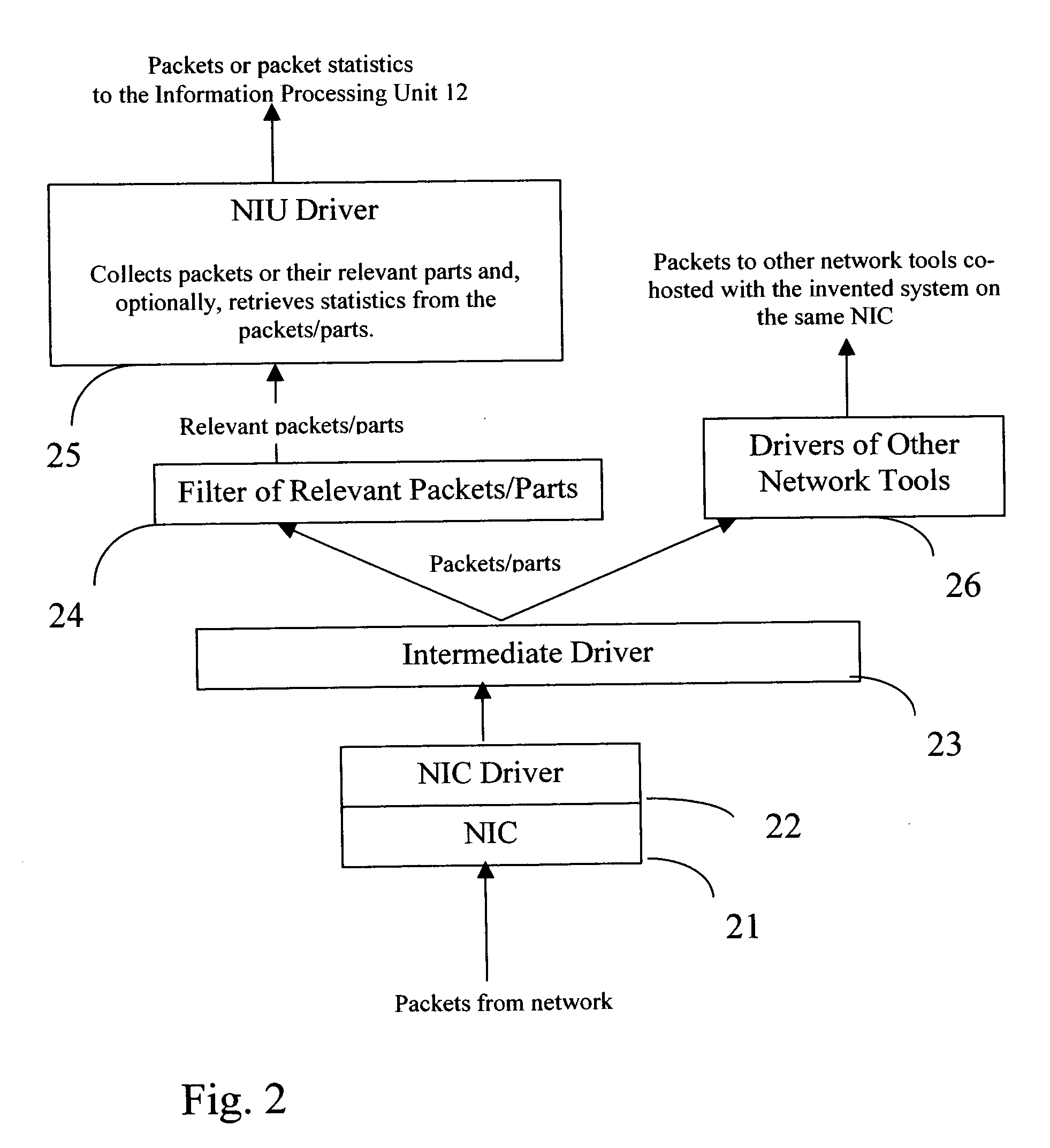
Flows based visualization of packet networks with network performance analysis, troubleshooting, optimization and network history backlog
InactiveUS20060028999A1Improve network securityEasy to highlightError preventionTransmission systemsProcess informationStreamflow
The present invention is a computer system and a method for gathering, processing and analysis of network information resulting in presentation and visualization of packet networks in the form of individual virtual flows, sometimes also called connections or sessions, containing their statistical characteristics in a time-sampled dynamics. The system, deployed as a separate device or co-hosted with other network devices, collects and processes information from all valid packets in network, classifies and maps gathered statistics to the statistics of relevant virtual flows. The statistical information is further processed by the system to provide near-real presentation, as well as stored in a searchable database for future analyses. The invention to be used by network engineers and administrators as a tool for a near real-time control of network traffic, as an analytical tool for solving network bottlenecks, network performance optimization and troubleshooting analyses, cutting costs by optimizing network layout, appropriate organization of traffic and intelligent configuration of QoS, routers and other network devices.
Owner:IAKOBASHVILI ROBERT +1
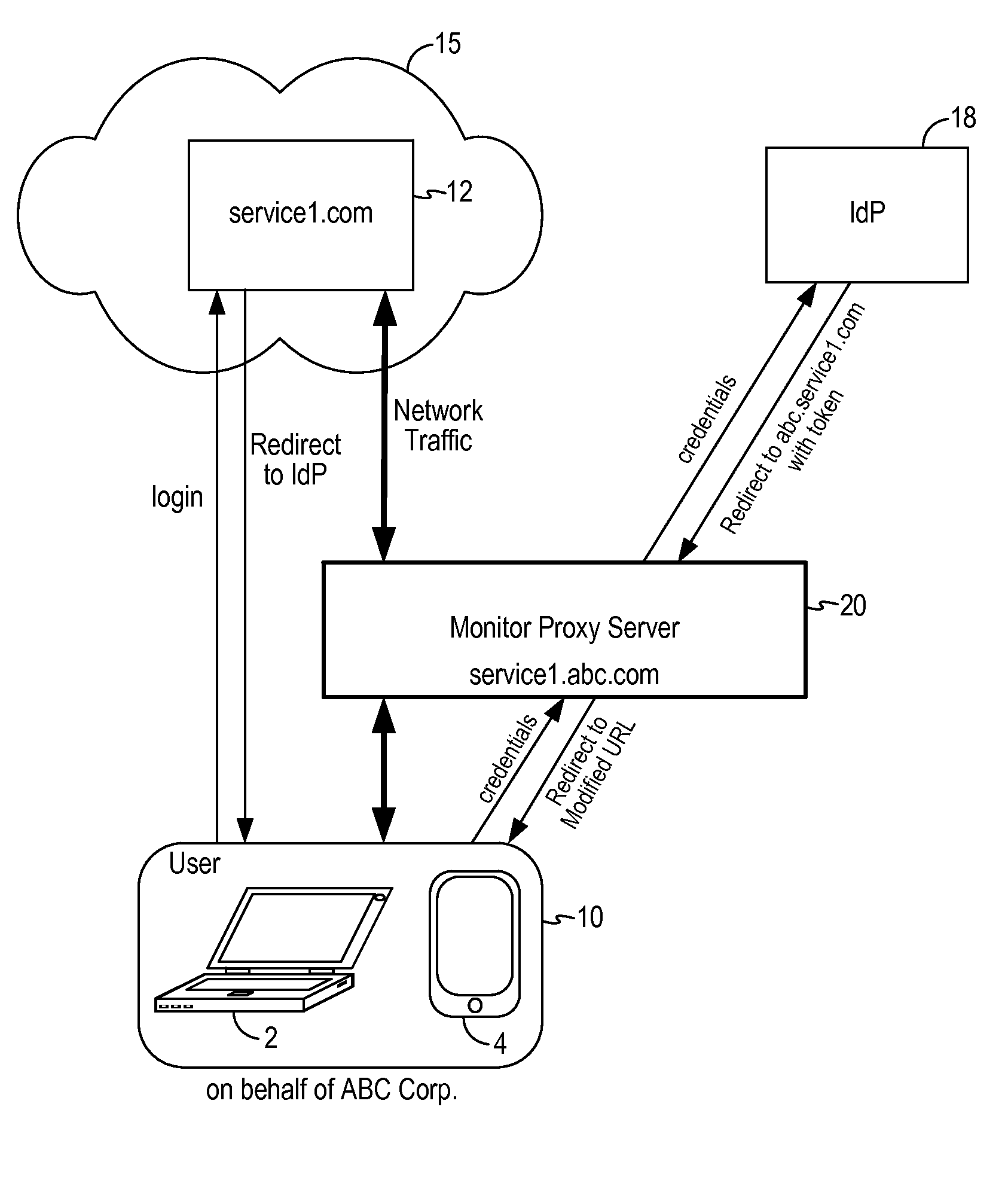
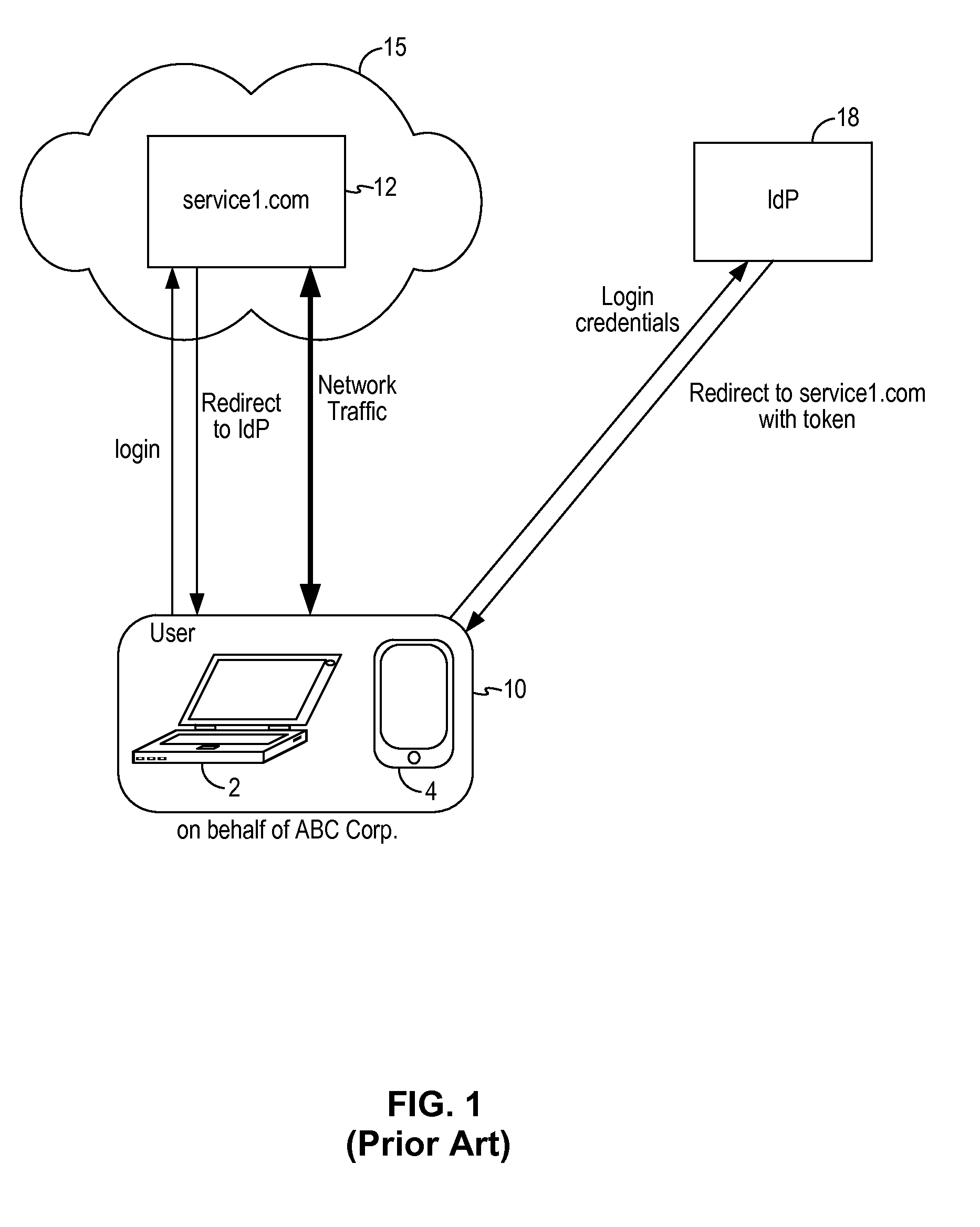
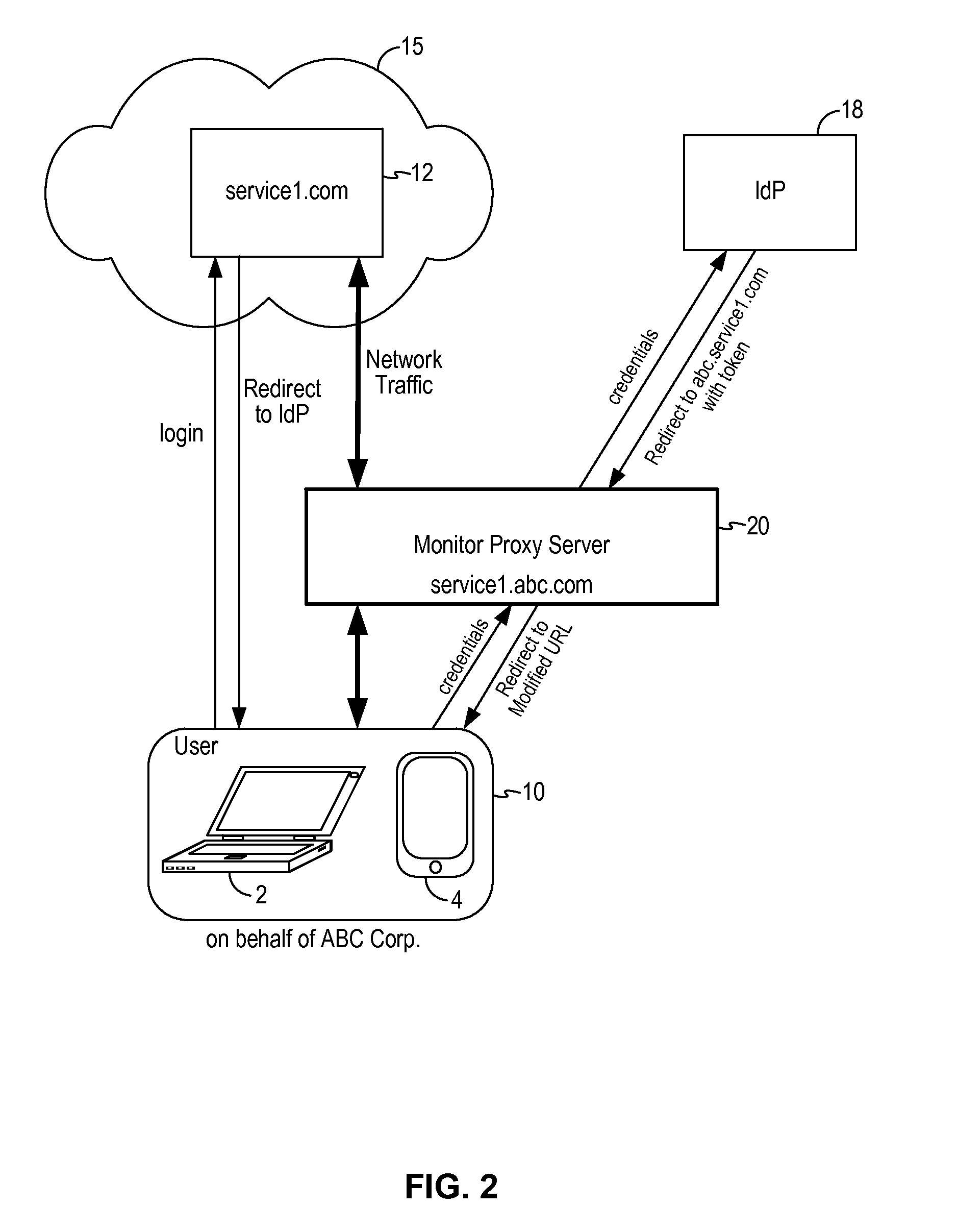
Network traffic monitoring system and method to redirect network traffic through a network intermediary
ActiveUS9137131B1Digital computer detailsData switching networksMonitoring systemNetwork communication
A network traffic monitoring system for redirecting network traffic between a client device and a cloud service includes a monitor proxy server configured as a network intermediary between the client device and a federated identity provider and between the client device and the cloud service. The monitor proxy server is configured to receive a redirect response generated by the federated identity provider upon user authentication. The monitor proxy server is configured to rewrite the redirect web address to the web address of the monitor proxy server. The monitor proxy server is further configured to rewrite a response web address in network communications between the cloud service and the client device to the web address of the monitor proxy server. As a result, network traffic between the cloud service and the client device is routed through the monitor proxy server after user authentication by the federated identity provider.
Owner:SKYHIGH SECURITY LLC
Security monitoring of network connections using metrics data
ActiveUS20180219879A1Avoid disadvantagesImprove Security Monitoring EfficiencyData switching networksTraffic capacityNetwork connection
Various embodiments of the present invention set forth techniques for security monitoring of a network connection, including analyzing network traffic data for a network connection associated with a computing device, identifying one or more network traffic metrics for the network connection based on the network traffic data, determining that the network connection corresponds to at least one network connection profile based on the one or more network traffic metrics, detecting a potential security threat for the network connection based on the one or more network traffic metrics and the at least one network connection profile, and initiating a mitigation action with respect to the network connection in response to detecting the potential security threat. Advantageously, the techniques allow detecting potential security threats based on network traffic metrics and categorizations, without requiring monitoring of the content or the total volume of all traffic exchanged via the connection.
Owner:SPLUNK INC
Network traffic monitoring for search popularity analysis
The popularity of web pages is monitored and used to rank the web pages retrieved in response to an Internet search. The popularity of a web page is proportionate to the number of visits to that web page. Web pages with greater popularity are ranked higher in priority. Furthermore, the score of a first web page is propagated to a plurality of second web pages to which the first web page is linked substantially in relative proportion to the popularity of the links from the first web page to each of the second web pages. Monitoring devices monitor TCP packets traversing the Internet and extract information from the TCP packets, such as the requested URI or URL, the client IP address, a server IP address and a server host name, and a referrer URI, if any. The extracted information is forwarded to a processing module that keeps track of the popularity of the web pages.
Owner:THE BOEING CO
Method and means for network control of traffic
InactiveUS6496773B1Large capacityReduce blockingAnalogue computers for vehiclesAnalogue computers for trafficInternet trafficSimulation
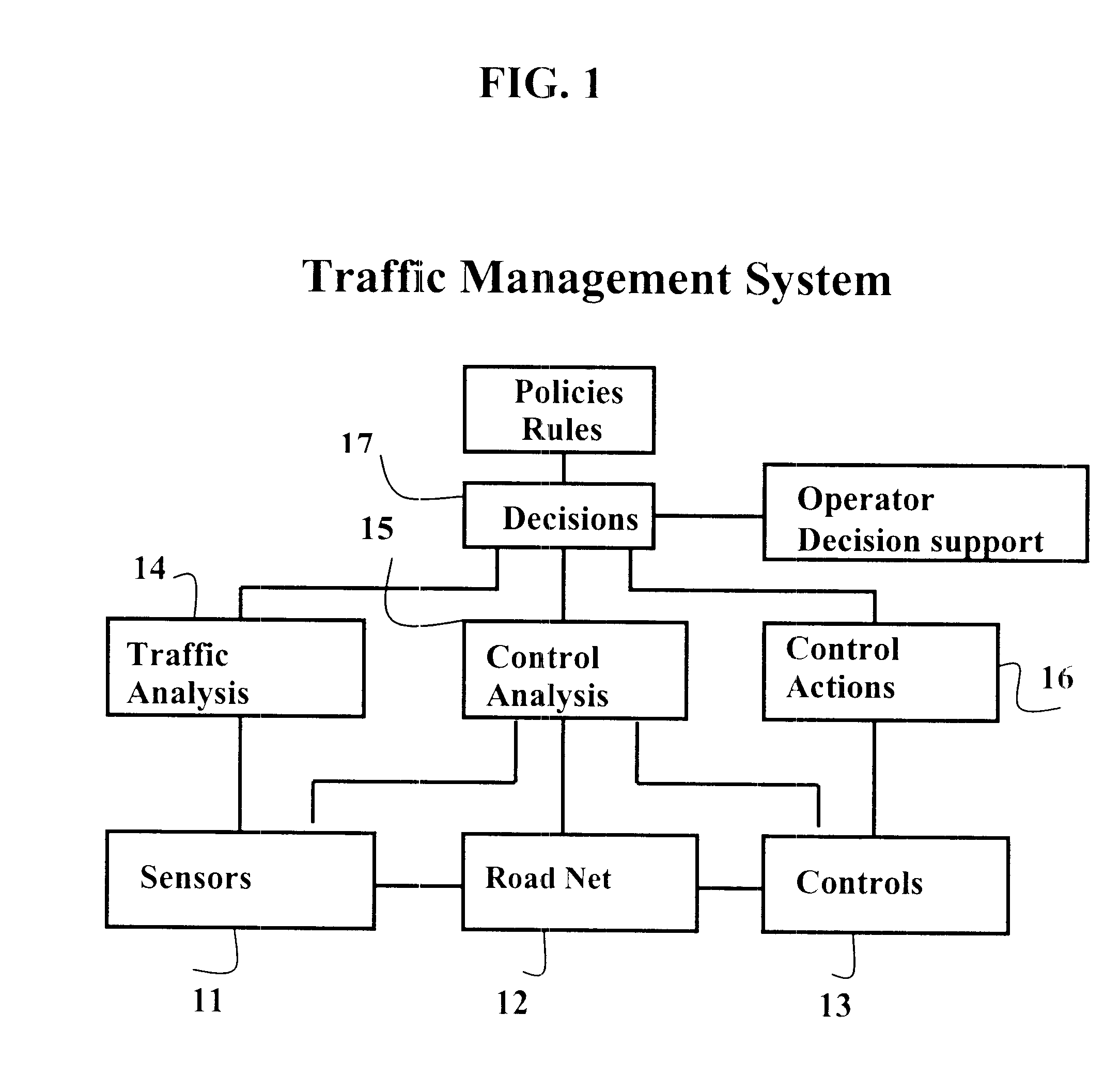
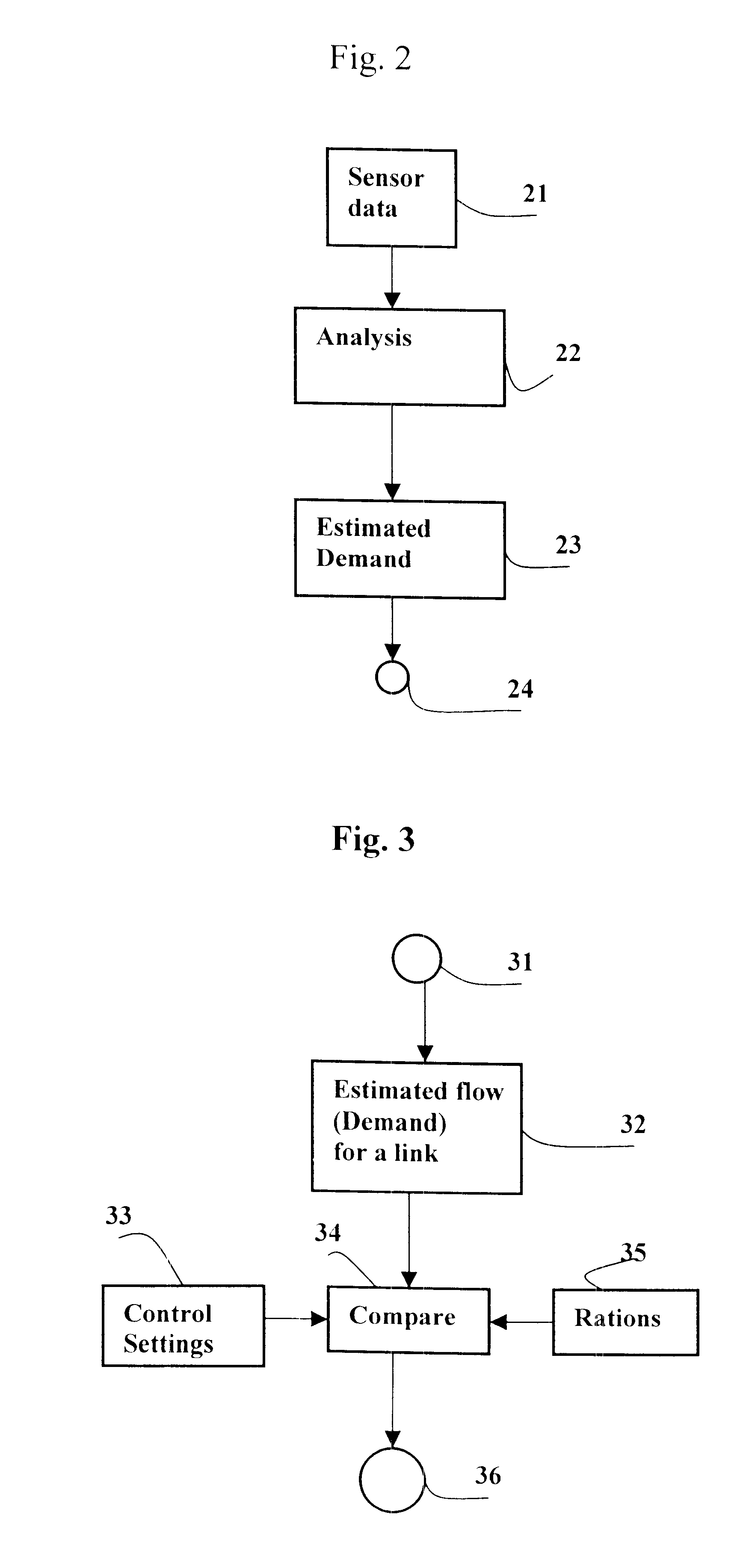
The invention relates to a method for detection and prediction of incidents and traffic queues formed by overloading. This is done in real time with use of sensors in a road network. Predictions are used also to reach a faster and more reliable detection. Sensor measurements are also used in the process, where the comparison with expected values are used for successively updating stored parameter values for the involved algorithms. By this, the system can succeedingly adapt itself for changed situations. The strong traffic variations, that are naturally occurring at short time intervals are treated with the use of noise-based methods. By this, there are formed distribution related measures as e.g. the standard deviation, which can be estimated from measurements, and submit a base for estimating probabilities for deviations of a certain size, e.g. related to the standard deviation. Automatic incident detection (AID) is based on determination of the desired false-alarm rate, and the related threshold level. The method includes accumulated measurements. Faster and more reliable incident detections are received with the use of the invented prediction process method.
Owner:OLSSON KJELL
OpenFlow network flow control method for QoS assurance of application
InactiveCN105357068AEasy to implementEasy to deployData switching networksTraffic capacityNetwork link
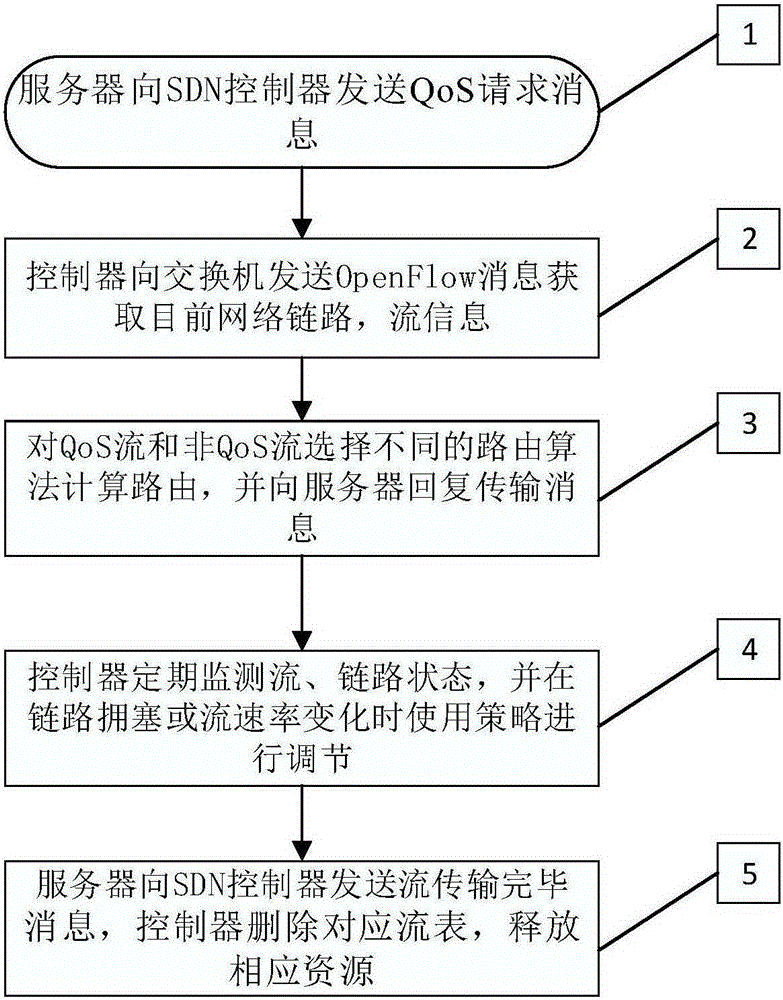
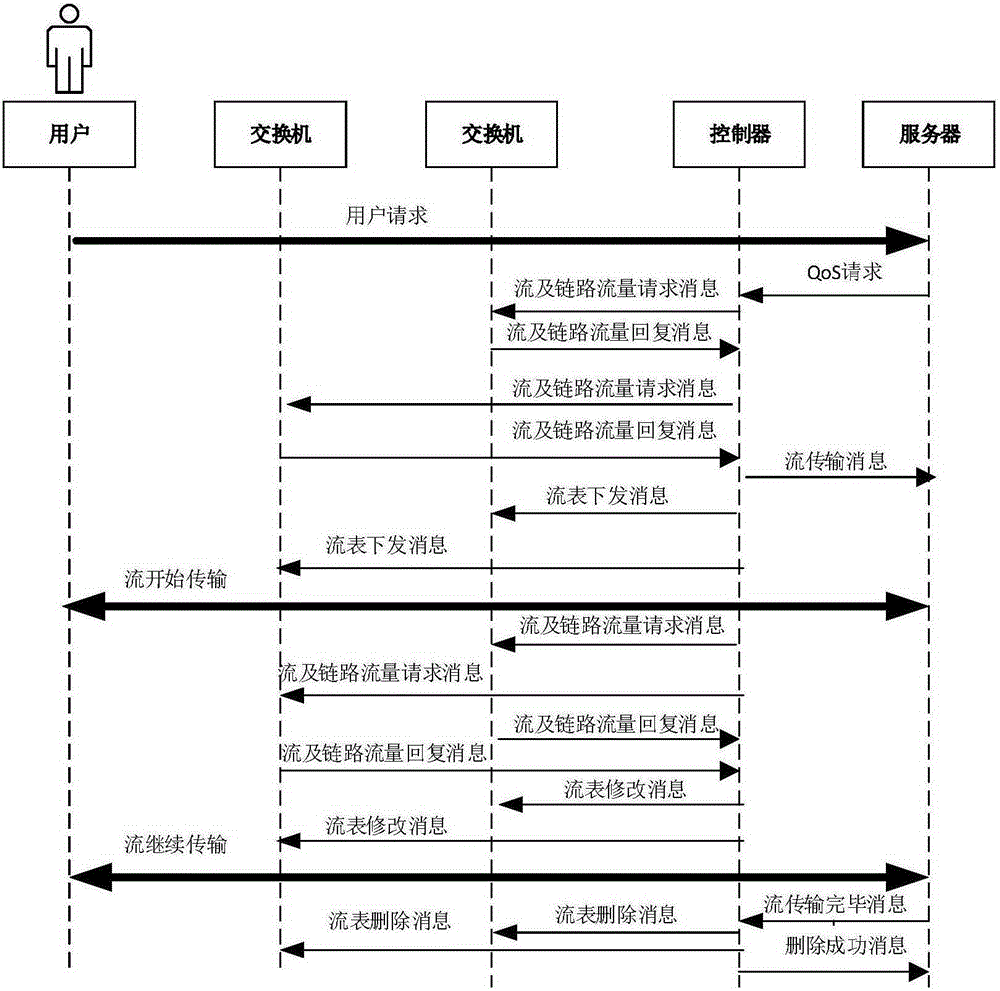
The invention provides an OpenFlow network flow control method for the QoS assurance of an application. The OpenFlow network flow control method comprises the following steps that: a user requests a service from a server; the server sends a QoS request message to an SDN controller; after receiving the message, the controller calculates an optimal transmission path for the server according to a network resource use condition and reserves a resource; and simultaneously, the transmission state and the network link condition of the server are monitored when the server transmits a QoS data flow, such that a QoS flow is transmitted reliably and stably. A required network resource is provided for an application service by strictly assuring the QoS transmission of the application service and utilizing the service difference to network resource requirements; therefore, the QoS of the application is effectively ensured; and simultaneously, the network resource is utilized effectively.
Owner:HUAZHONG UNIV OF SCI & TECH
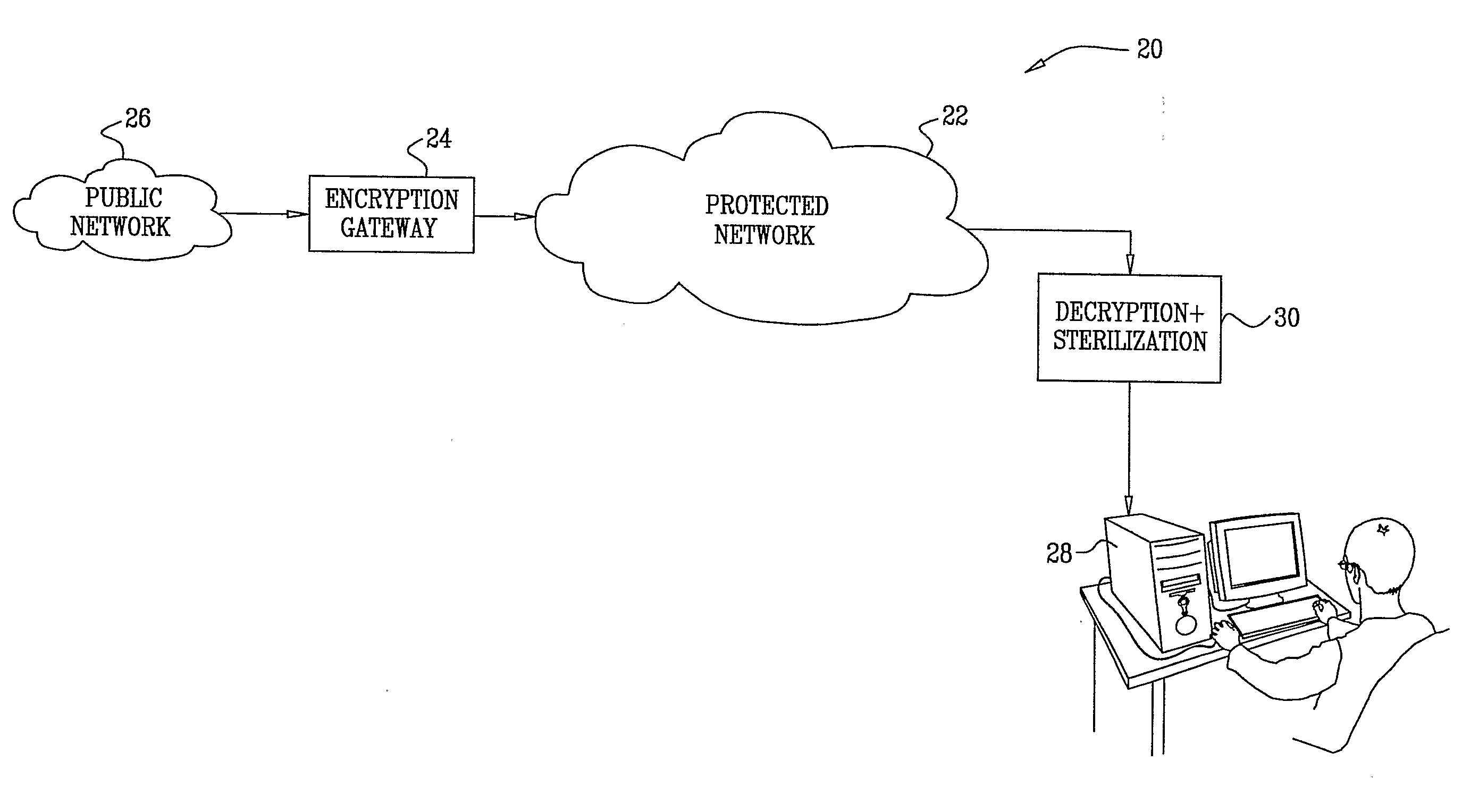
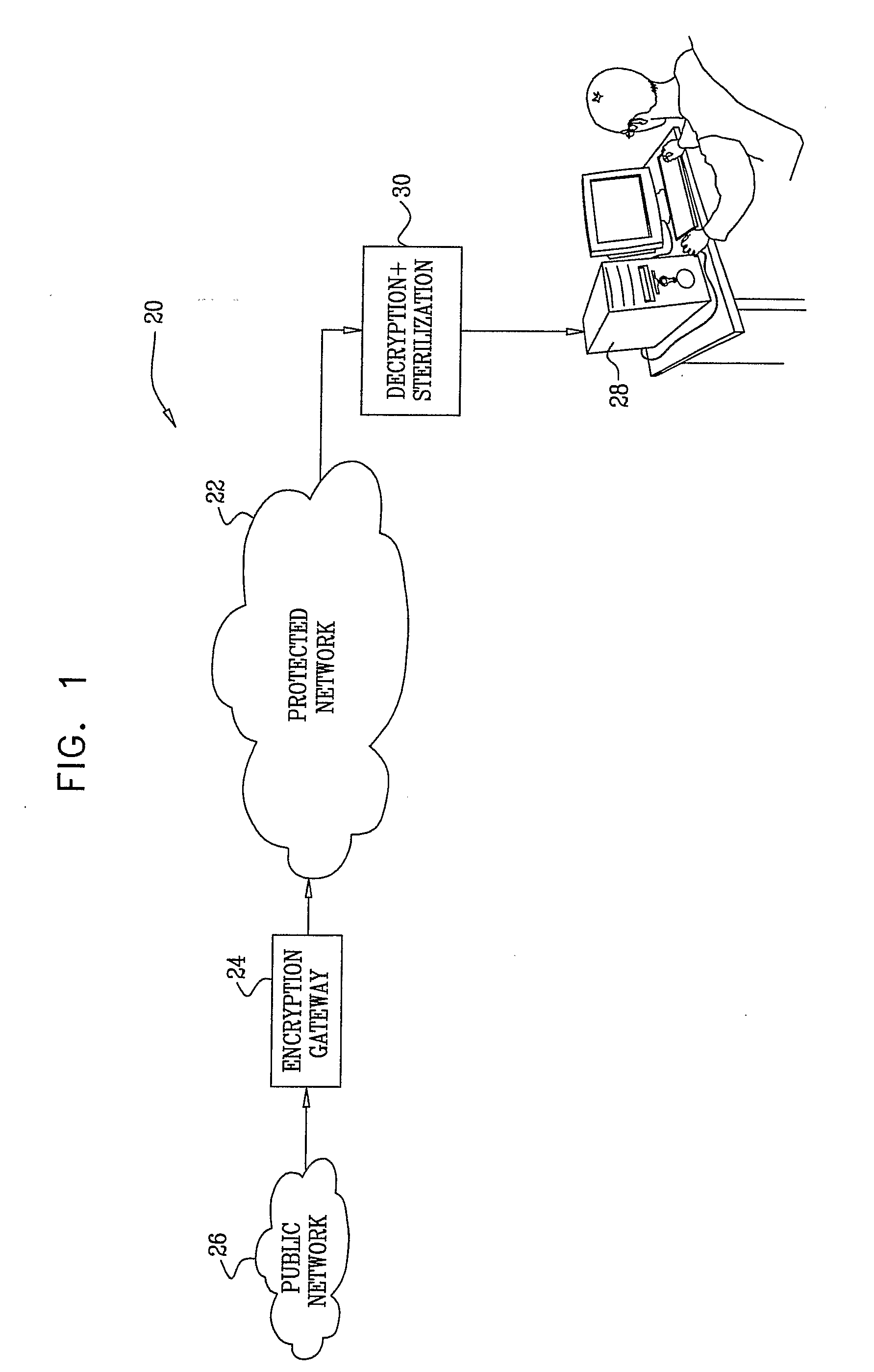
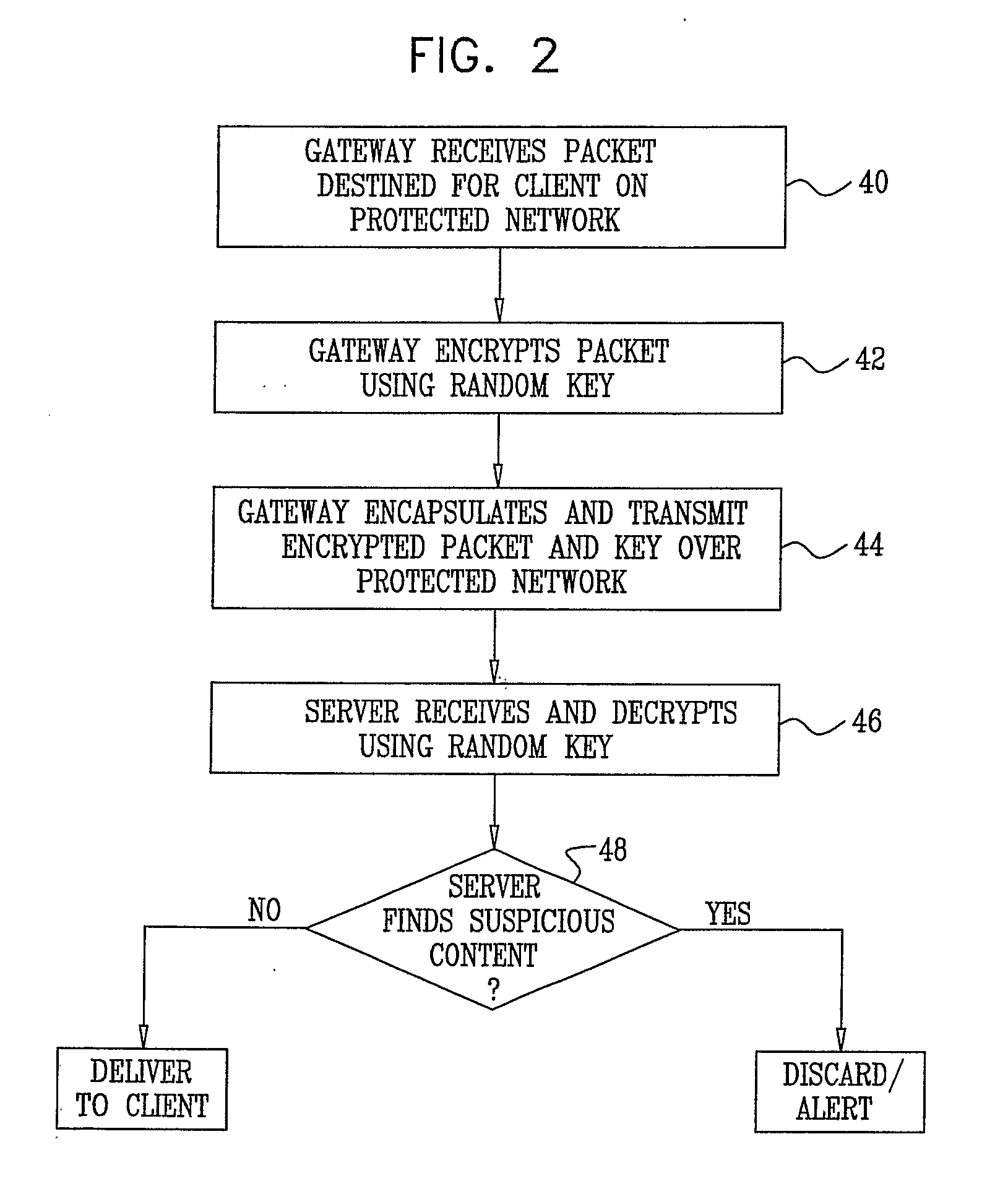
Encryption-based control of network traffic
ActiveUS20090319773A1Neutralize malicious effect of transmissionKey distribution for secure communicationMemory loss protectionTraffic capacityEncryption
A computer-implemented method for protecting a computer network (22) includes receiving at a gateway (24) data transmitted from a source address for delivery to a destination on the computer network. The data are encrypted at the gateway using an encryption key selected from a set of one or more keys that are not available to the source address. The encrypted data are transmitted over the computer network toward the destination. The transmitted encrypted data are received and decrypted for use at the destination by means of one of the keys in the set.
Owner:WATERFALL SECURITY SOLUTIONS LTD
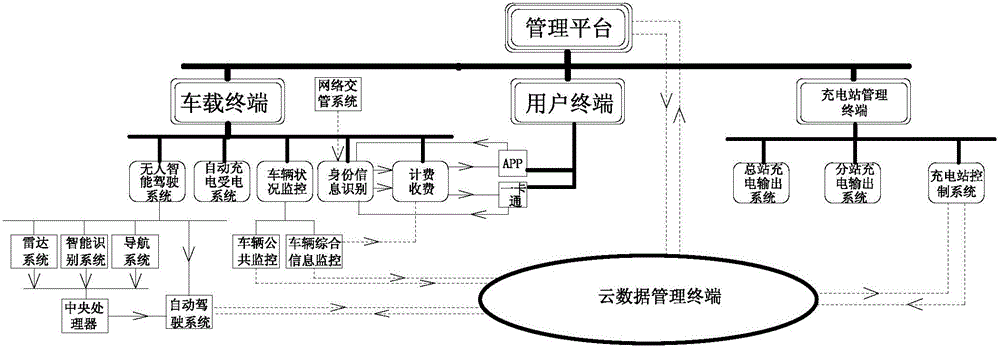
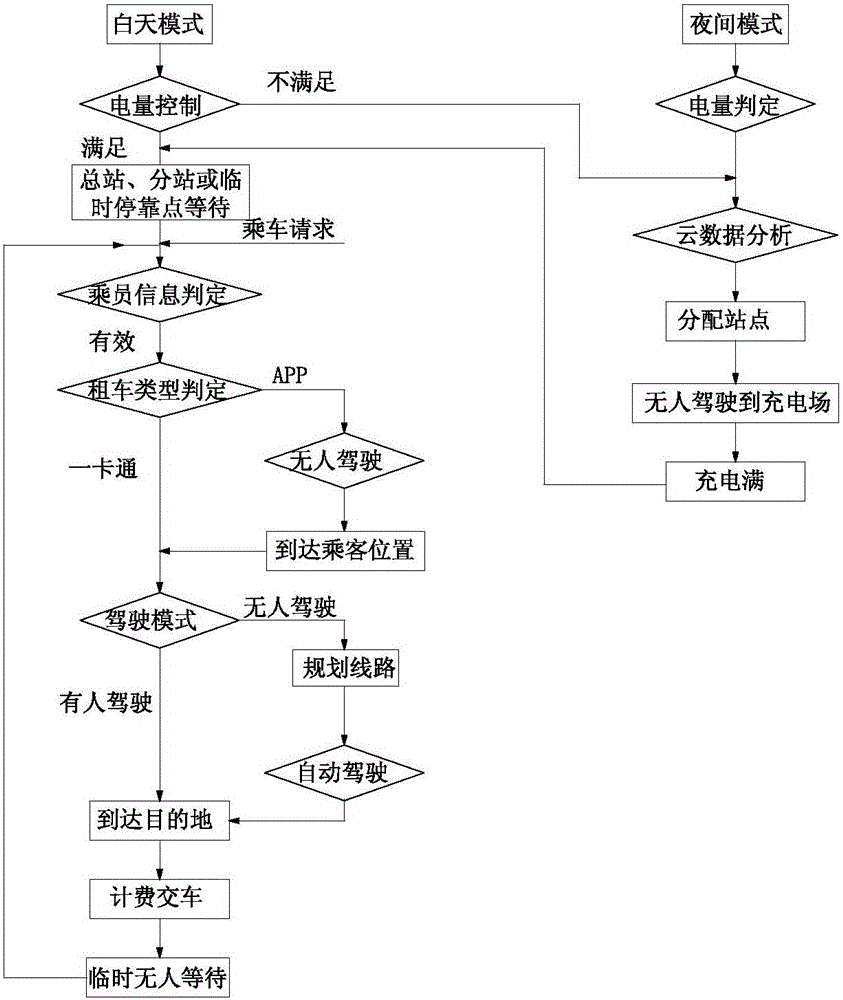
Intelligent transportation system with unmanned driving and field return charging functions and implementation method
ActiveCN105788333AConvenient travelEasy to useCharging stationsRoad vehicles traffic controlElectricityCloud data management
The invention discloses an intelligent public transportation system with unmanned driving and field return charging functions.The intelligent public transportation system comprises a management platform, a vehicle-mounted terminal, a network traffic control system, a user terminal, a charging station management terminal and a cloud data management terminal.The vehicle-mounted terminal comprises an unmanned intelligent driving system, an automatic charging electricity receiving system, a vehicle status monitoring system, an identity information recognition system and a charging system, all of which are connected with the management platform.The unmanned intelligent driving system and the vehicle status monitoring system are both connected with the cloud data management terminal.The identity information recognition system and the charging system are both connected with the user terminal, and the identity information recognition system is connected with the charging system.The charging station management terminal is connected with the cloud data management terminal.The electric vehicle technology and the unmanned driving technology are combined, a cloud data analysis and intelligent management system achieves a special vehicle use operating mode, and on the premise that safe vehicle use is guaranteed, an individual, intelligent and green public transportation means is provided for a user.
Owner:SICHUAN VOCATIONAL COLLEGE OF CHEM TECH
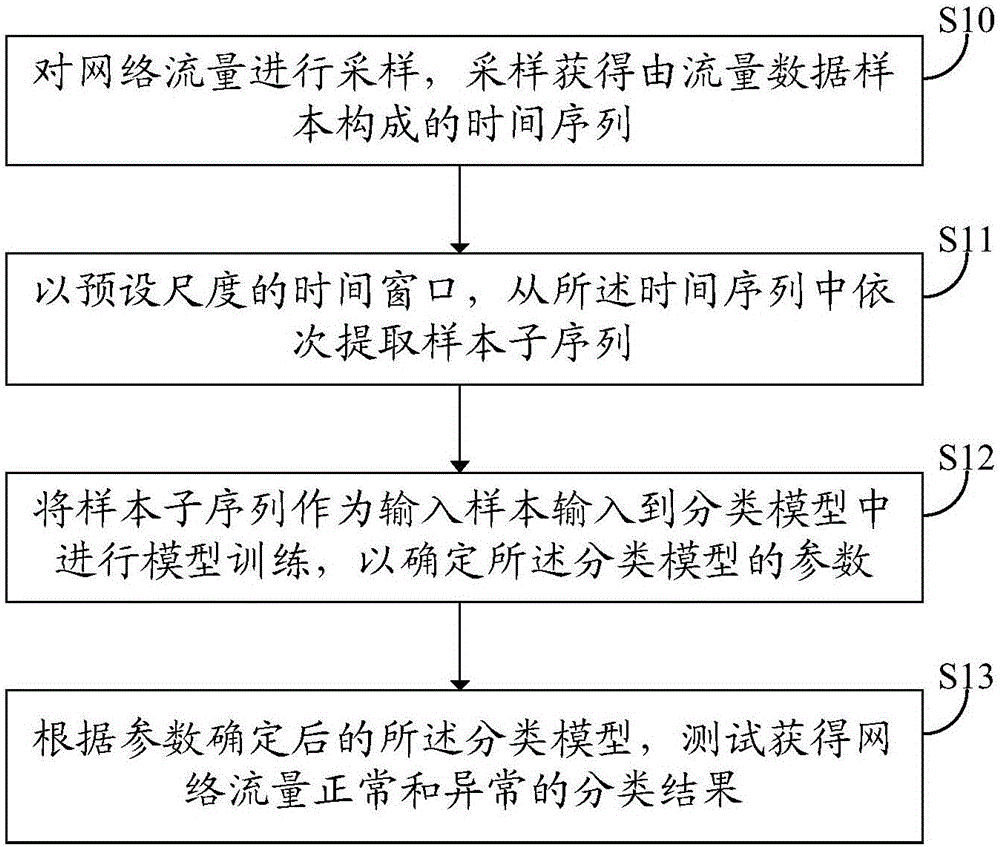
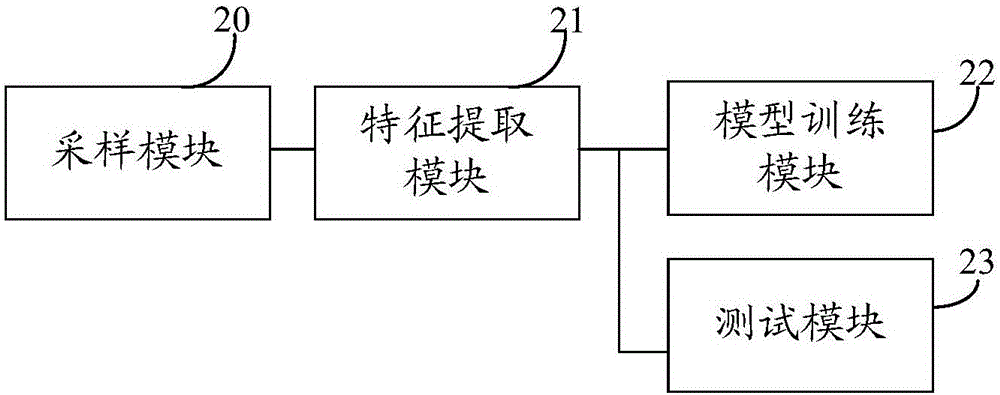
Network traffic abnormality detection method and system
InactiveCN106411597ANormal and Abnormal Classification ResultsImprove accuracyData switching networksTemporal informationAnomaly detection
The invention discloses a network traffic abnormality detection method and system. The method comprises the steps of sampling network traffic, thereby obtaining time sequences composed of traffic data samples through sampling; extracting sample subsequences from the time sequences according to time windows of preset sizes; inputting the sample subsequences into a classification model for model training by taking the sample subsequences as input samples, thereby determining parameters of the classification model; and testing to obtain normal and abnormal classification results of the network traffic according to the classification model of which parameters are determined. According to the network traffic abnormality detection method and system provided by the invention, the extracted time sequence composed of the traffic data samples are taken as the samples for model training and classification detection, the fact that network traffic changes have continuity and correlation in time is taken into consideration, and time information is introduced into abnormal traffic detection and classification. Compared with the prior art, the method and the system have the advantage that the accuracy of carrying out abnormal behavior detection on the network traffic can be improved.
Owner:GUANGDONG UNIV OF TECH
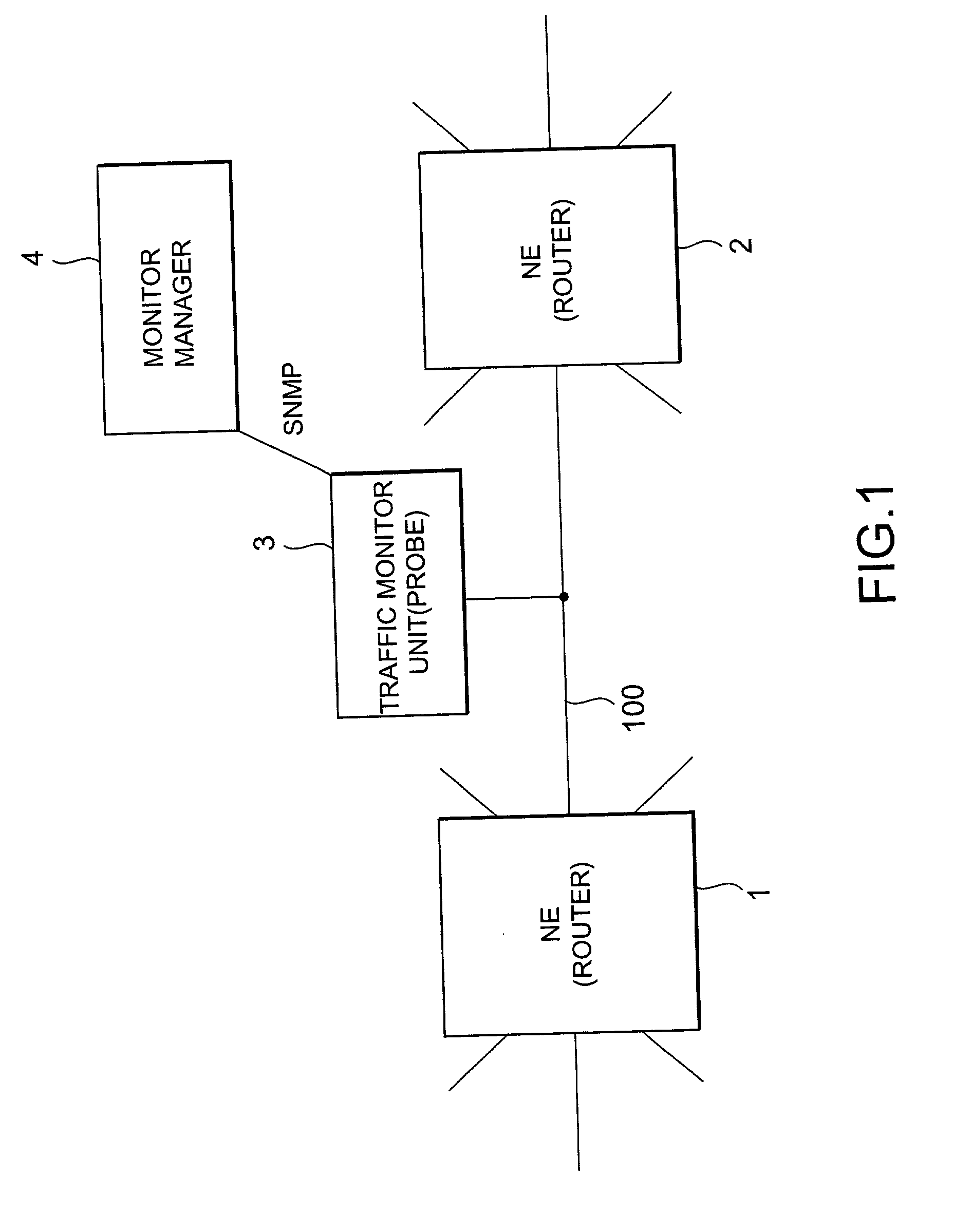
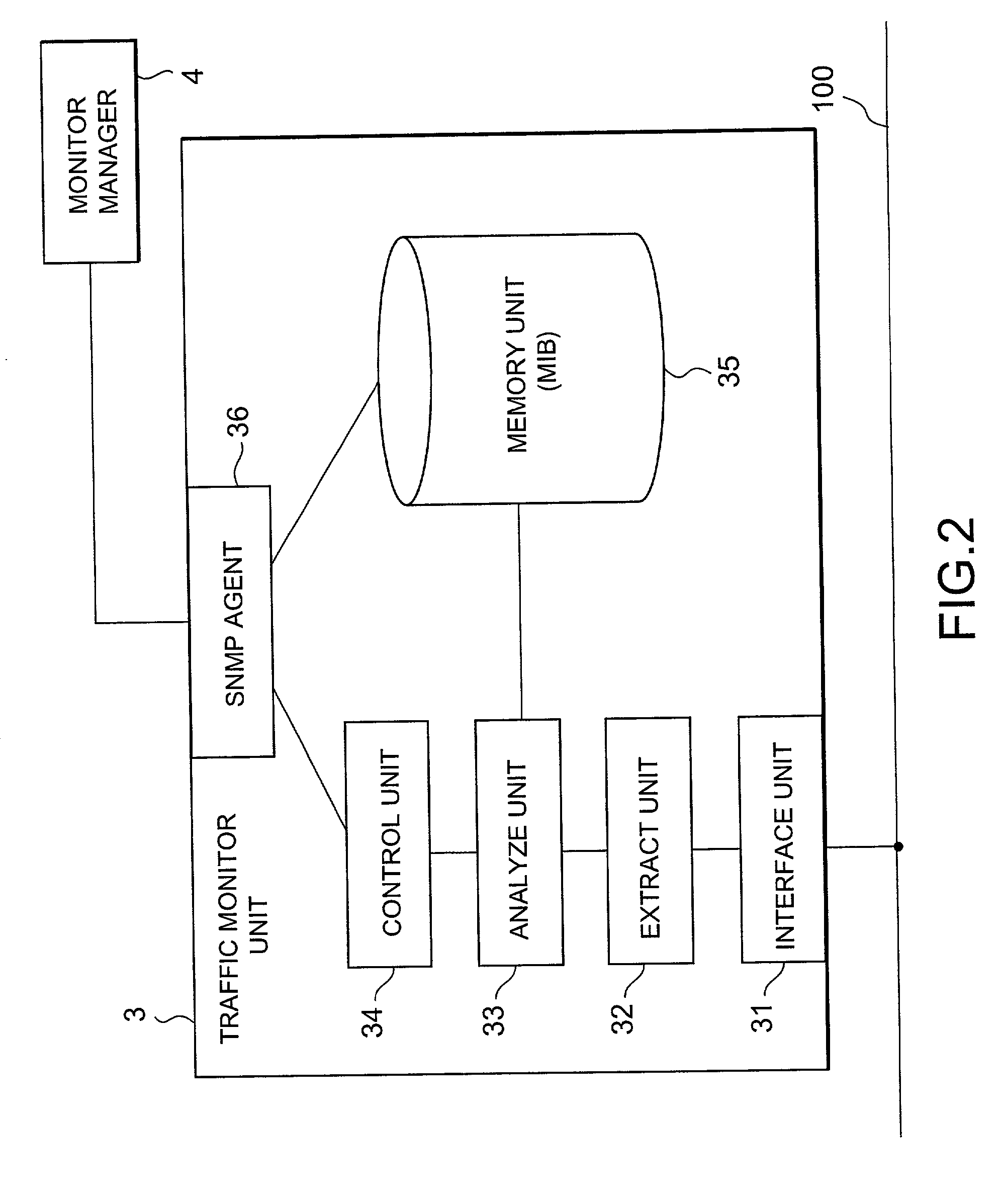
Network traffic monitoring system and monitoring method
InactiveUS20010052011A1Reducing can be gatheredLarge networkDigital computer detailsData switching by path configurationTraffic capacityIp address
In a network traffic monitoring system and method for capturing a service distribution to monitor an IP network using Diffserv protocol, each IP packet on the network is monitored by extracting DSCP and IP addresses from a header of the packet. Then, traffic information is accumulated for each service class and for each sub network address, using the extracted information.
Owner:NEC CORP
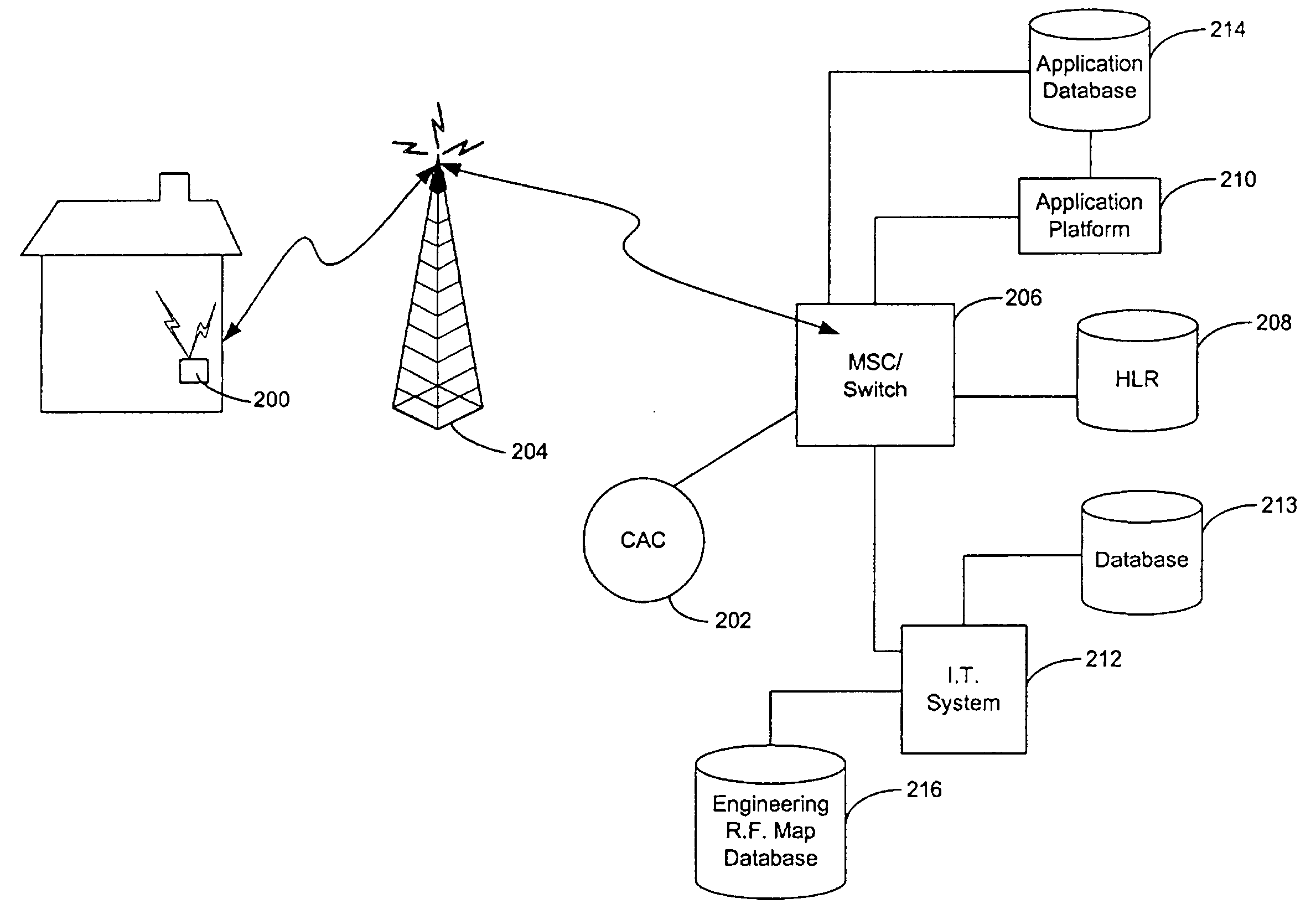
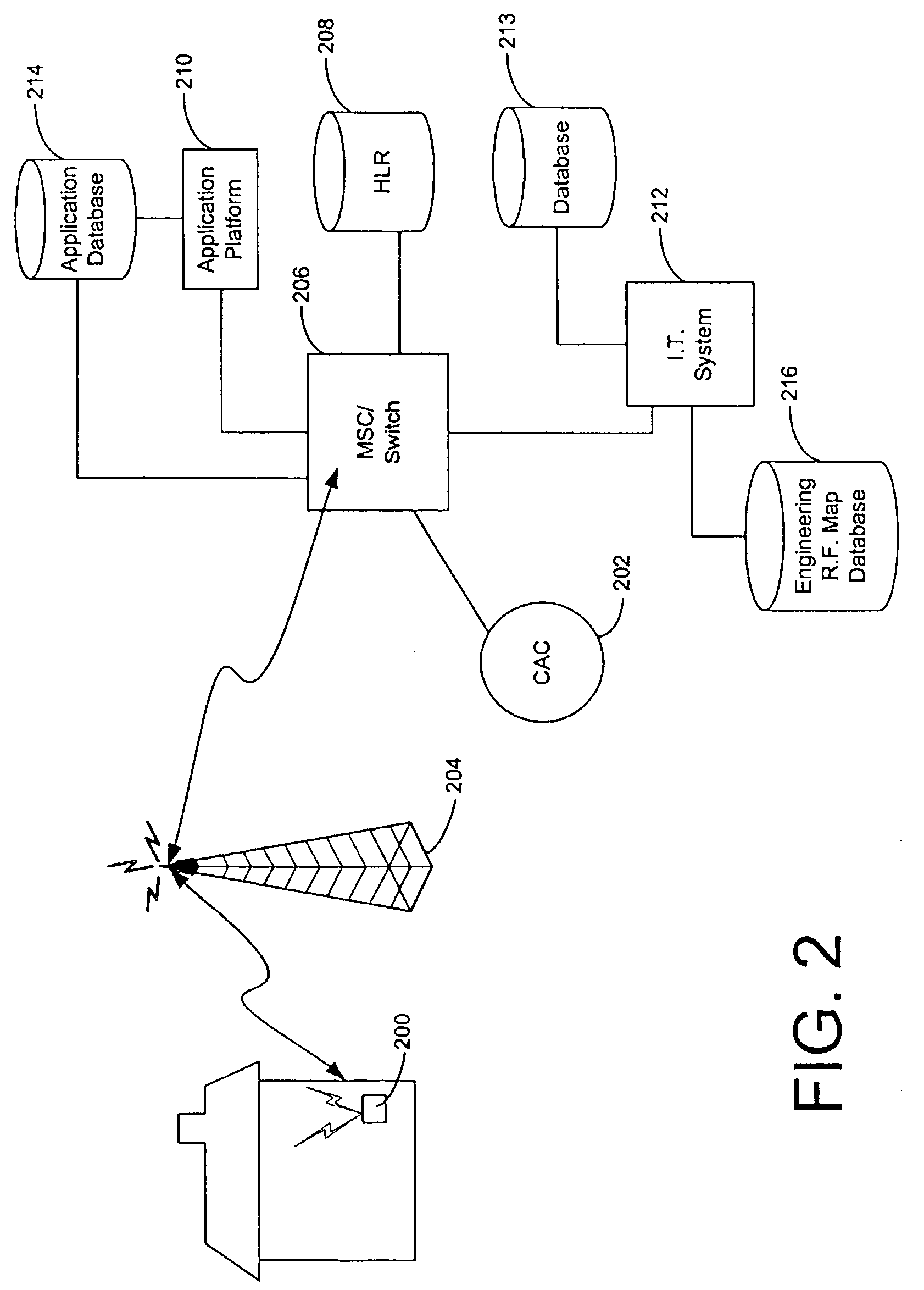
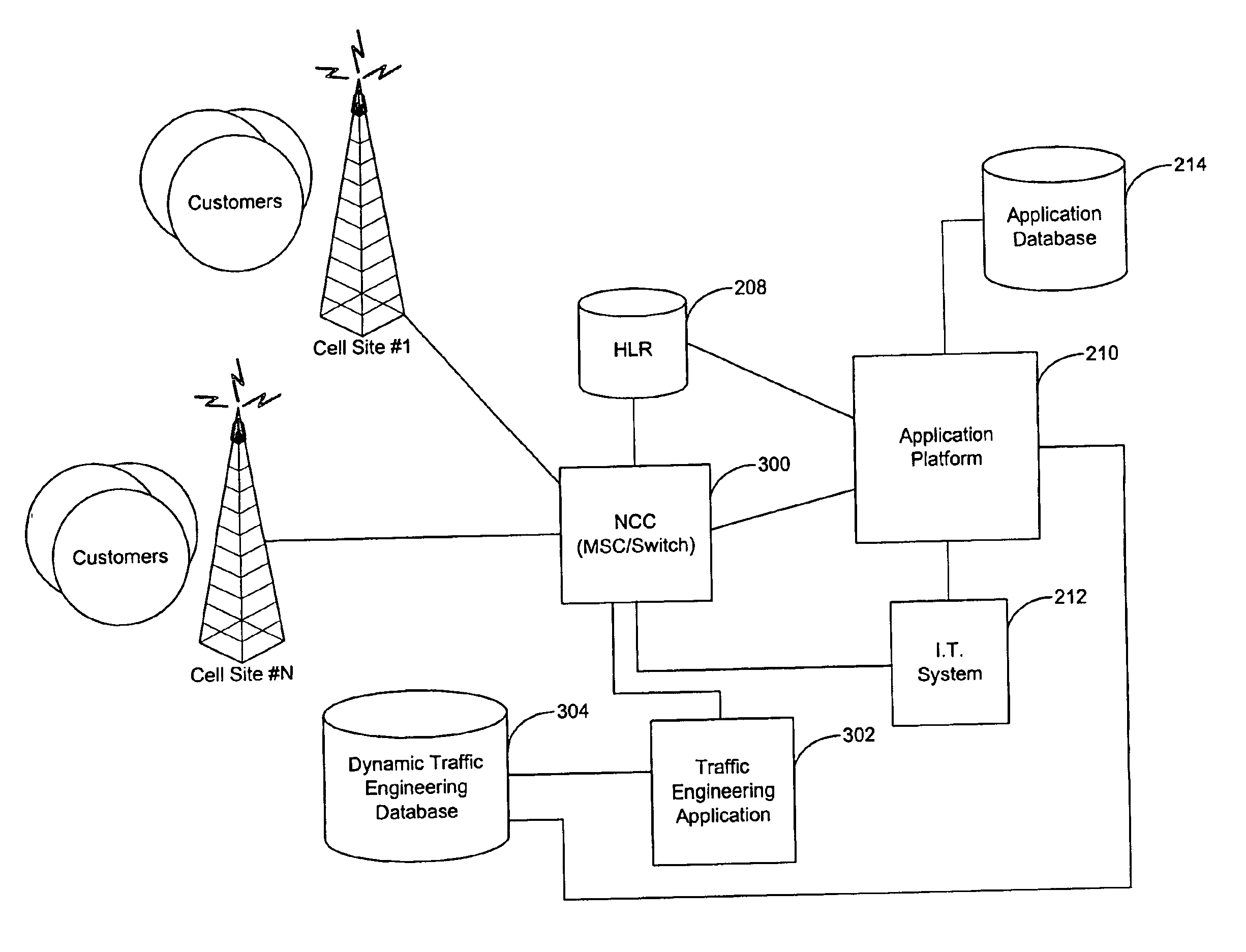
Apparatus and method for providing dynamic communications network traffic control
InactiveUS20060142018A1Less-expensive to providePromote activationAccounting/billing servicesNetwork traffic/resource managementControl communicationsCritical time
Systems and methods for controlling traffic on a communications network include dynamic and flexible control plans that enable service providers to control or influence customer access to communications facilities. Communications facilities are monitored to identify network elements, such as cell sites, that are overloaded. When the traffic intensity on a particular facility exceeds a predetermined level, either active or passive control is imposed on subscribers that are in the geographic area of the facility. Active control involves blocking, delaying or disrupting subscriber calls during the critical time period. Passive control involves providing cost incentives or disincentives during low or peak periods of traffic intensity. Customers are notified of the commencement and / or termination of active or passive control preferably via SMS. When implemented with stationary cellular service, the systems and methods aid in traffic engineering and provide opportunities for customers to reduce the cost and increase the accessibility of telephone service.
Owner:AT&T INTPROP I LP
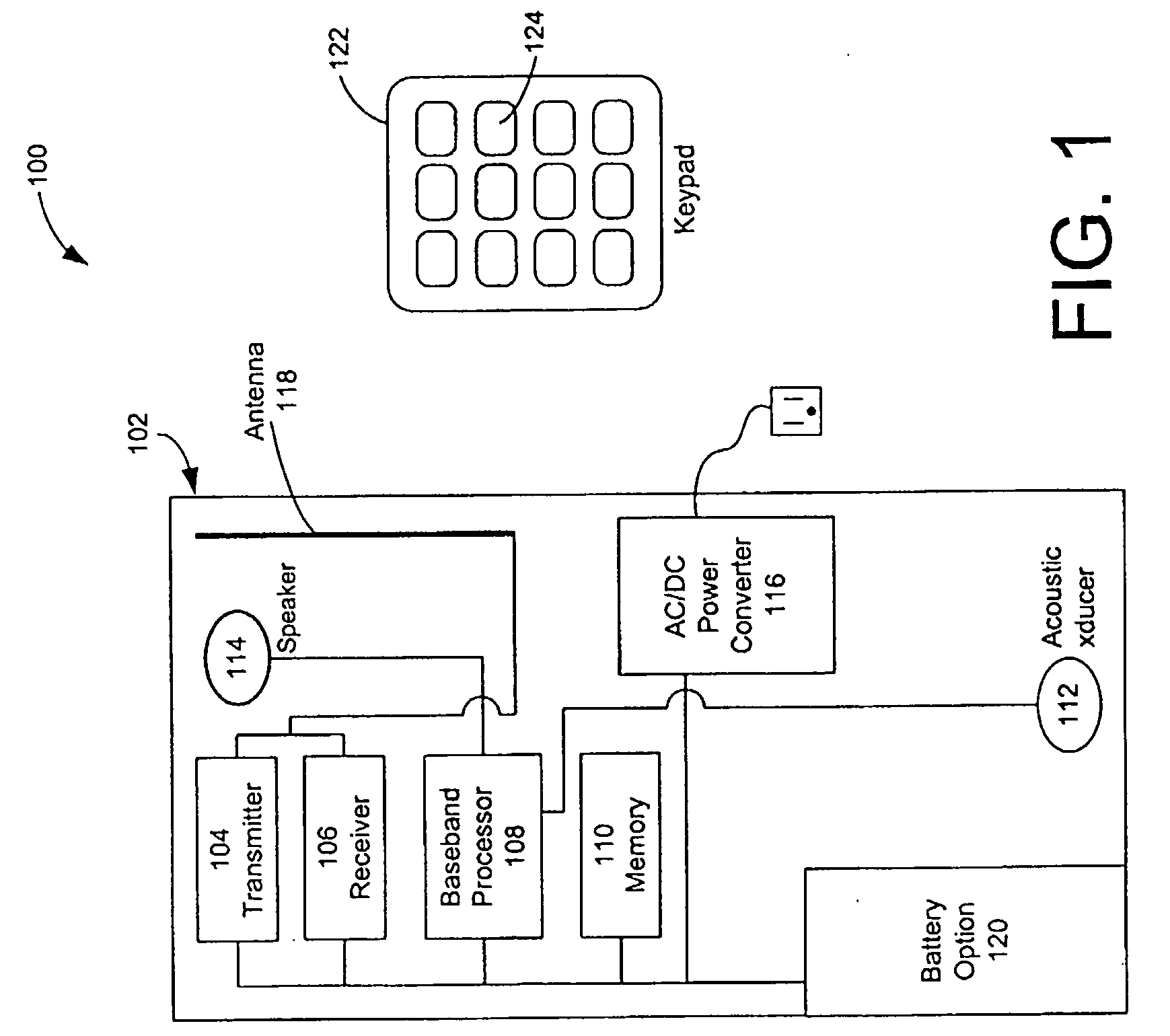
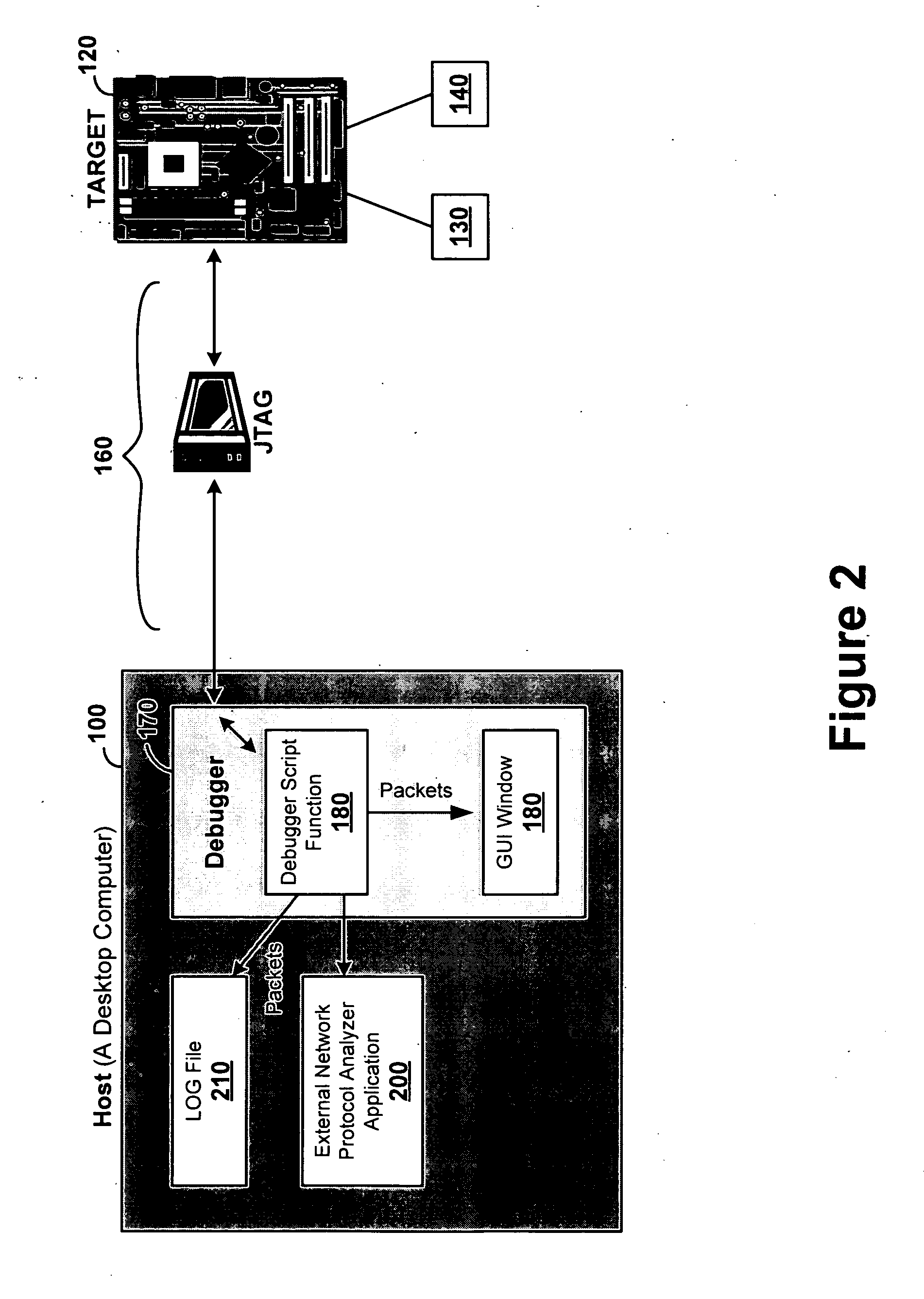
Network traffic monitoring using embedded target-side analyzer during embedded software development
InactiveUS20080056139A1Error preventionFrequency-division multiplex detailsSoftware development processAnalysis data
A debugging system running on a host device uses an embedded target-side network analyzer to acquire communications information such as packets. The target-side network analyzer logs and analyzes packets by obtaining data from the target's Internet Protocol (IP) stack when diagnostic functions are invoked at breakpoints. This allows display, logging, analysis and other uses of decoded network traffic. This approach can be used in applications (e.g., wireless or those using protocols such as RADIUS and PPP, etc.) where identifying and intercepting traffic to or from a specific target device may be difficult or impossible. With this approach developers can analyze network traffic in real time without any special hardware.
Owner:MENTOR GRAPHICS CORP
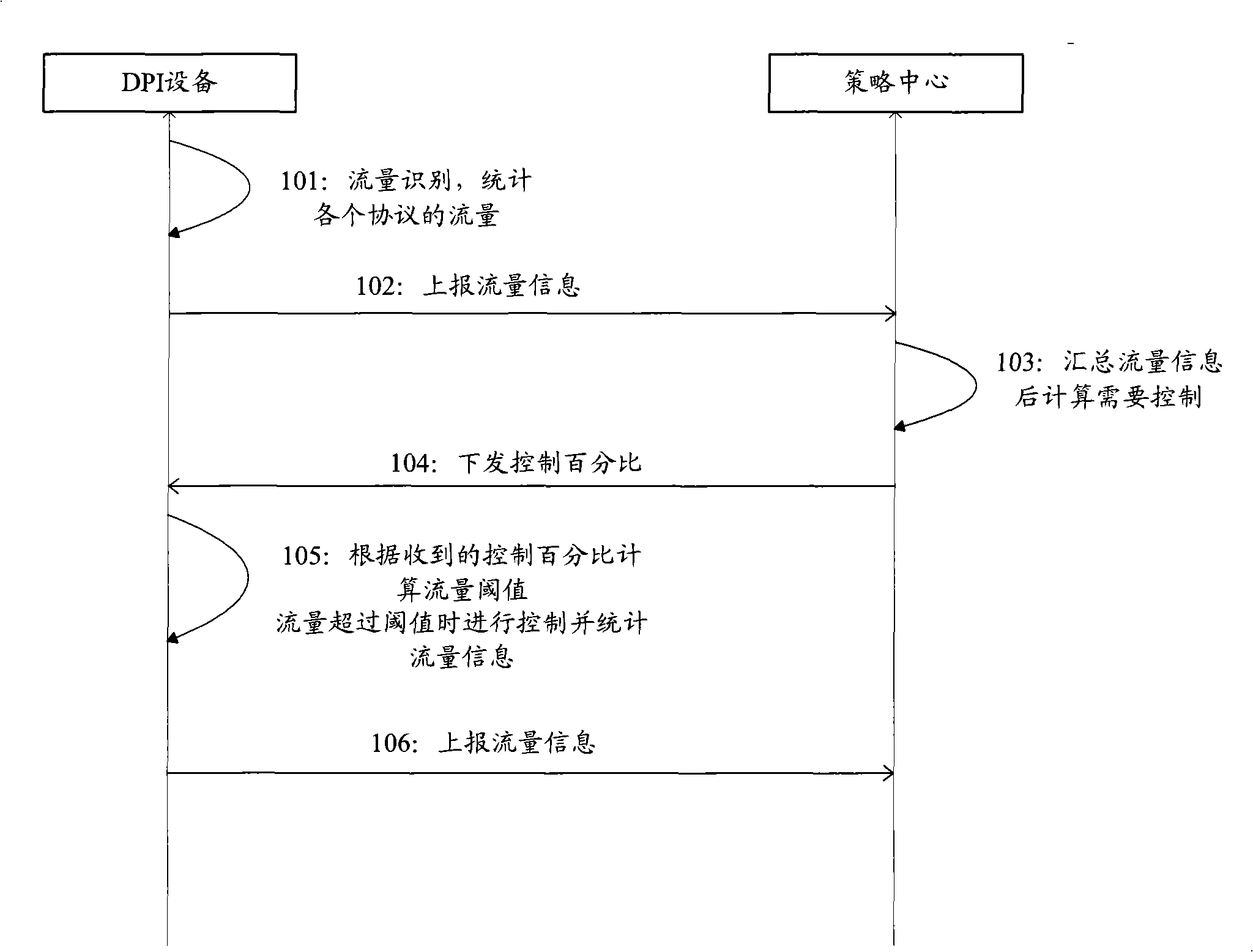
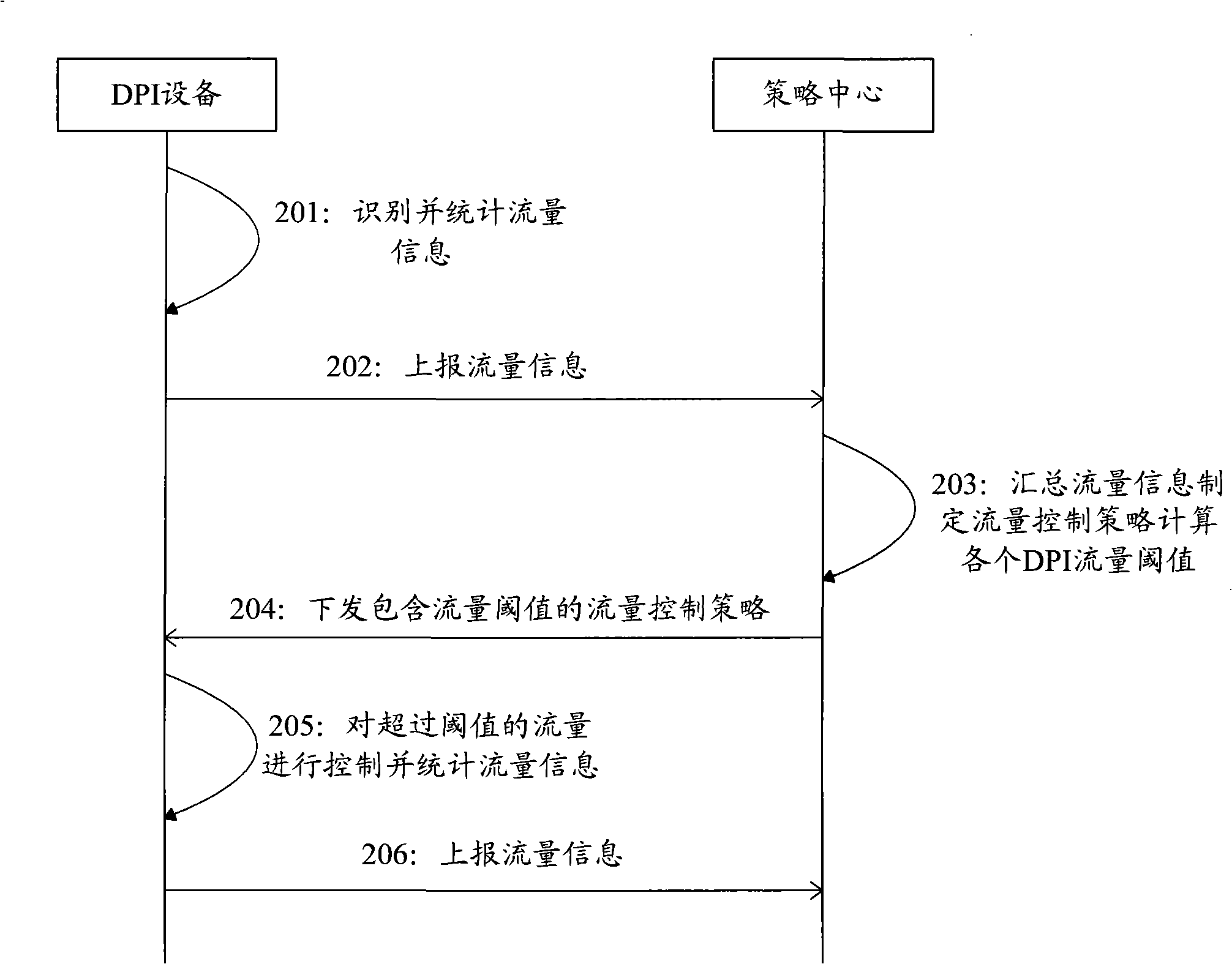
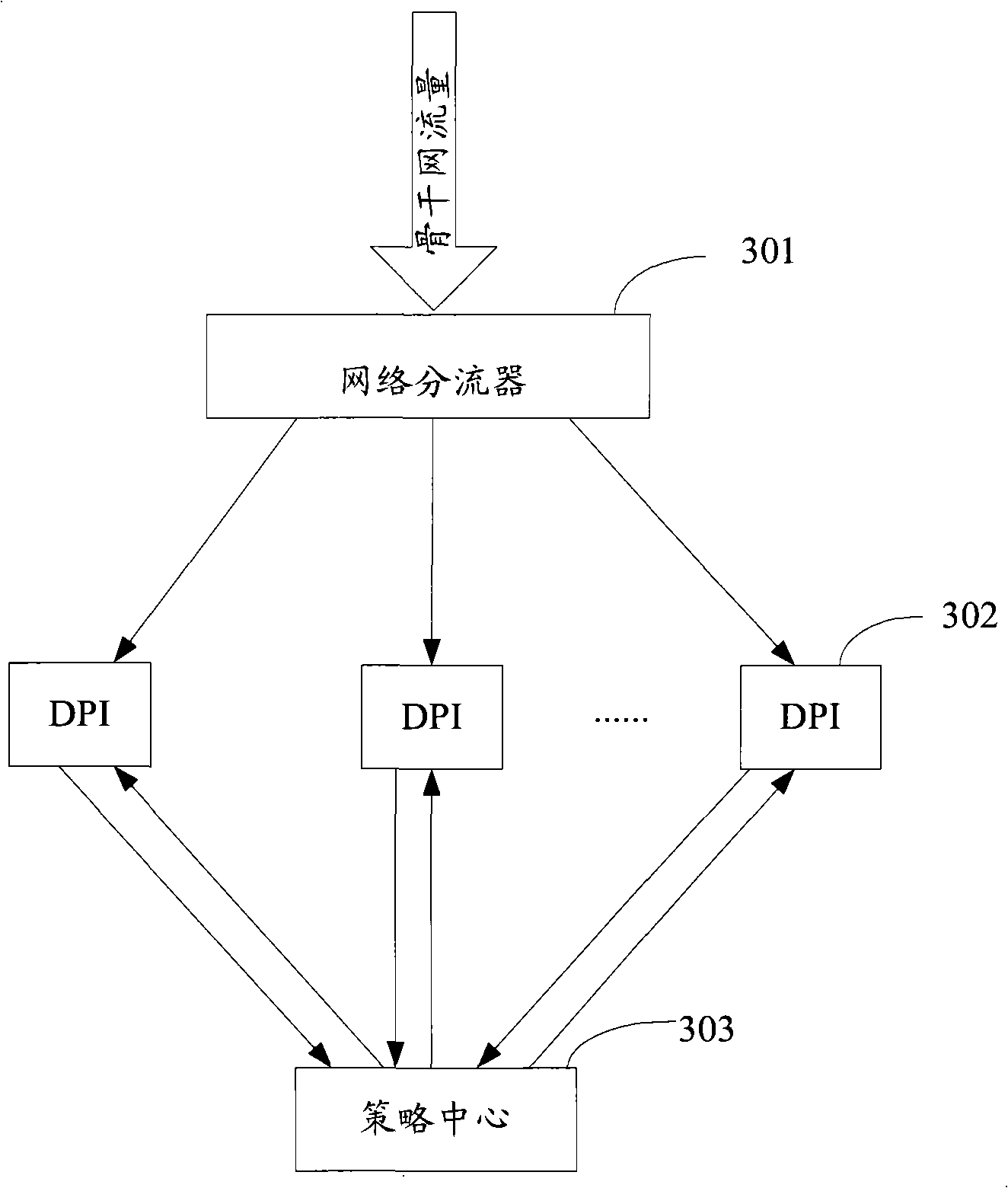
Network flow control method, device and system
The embodiment of the invention discloses a network flow control method and a corresponding system and a device. The network flow control method comprises the steps that: a strategy center resolves flow information calculated by a DPI device according to the content of a received deep packet to calculate the total network flow, and formulates a corresponding flow control strategy according to the total network flow and sends the corresponding flow control strategy to the DPI device; the DPI device obtains a corresponding flow threshold value of the next predetermined period of time according to the flow control strategy; the DPI device controls the flow when the flow passing through the DPI device exceeds the flow threshold value. By the technical proposal provided by the embodiment of the invention, the strategy control center can formulate different flow control strategies according to the specific flow information calculated by the DPI device, and therefore selective control over service flow can be carried out, which has no effect on the normal service of users.
Owner:HUAWEI DIGITAL TECH (CHENGDU) CO LTD
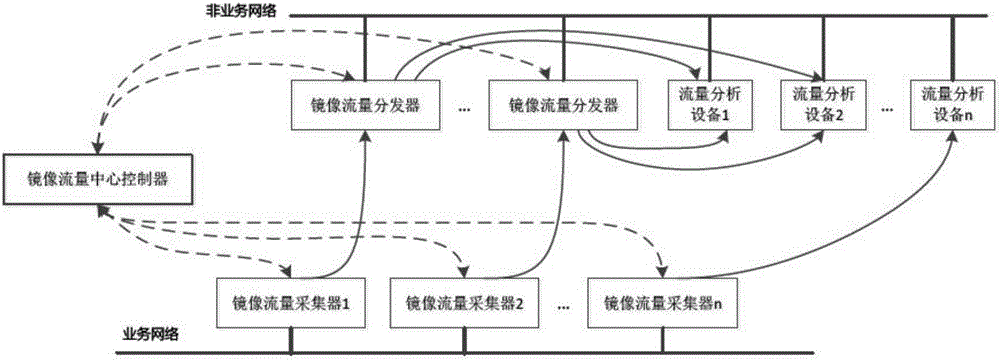
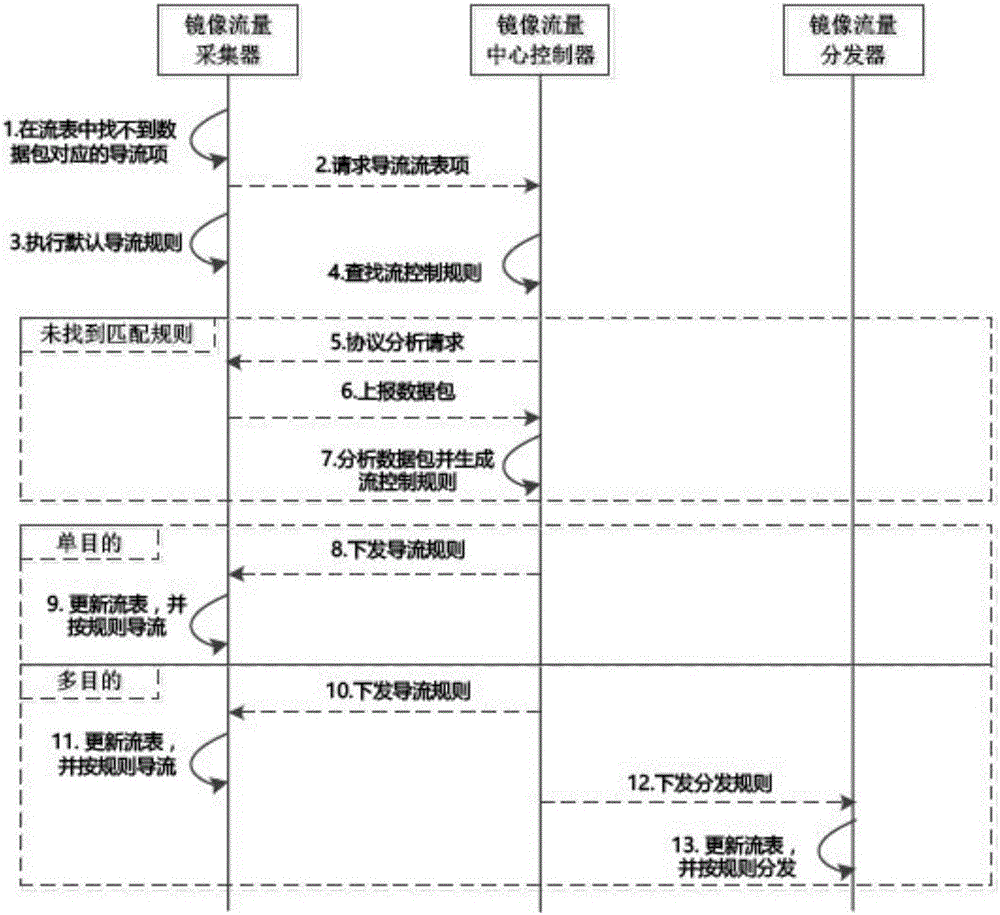
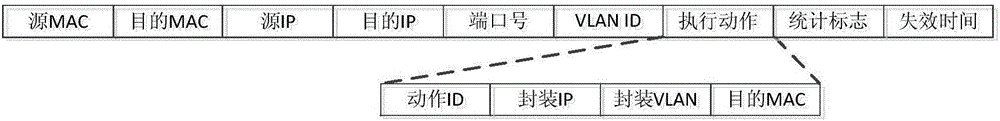
Mirror network flow control protocol in virtualization network environment
ActiveCN106100999AEasy accessResolve duplicationData switching networksNetwork communicationRTP Control Protocol
A mirror network flow control protocol based on a software definition in a virtual network environment is characterized in that the protocol can adapt a system structure of mirror flow collection, mirror flow distribution and mirror flow control, which is decoupling in functions and has distributed disposition. A mirror flow collector node / virtual machine is deployed in a business network environment of a user, and has a main function to capture the mirror flow in the virtual network environment and to carry out forwarding according to a target assigned by the protocol. A mirror flow dispatcher is deployed in a non-business network environment, that is the influence of a network load on the normal network communication of the user business network environment does not need to be considered, and the function of the mirror flow dispatcher is to carry out flow copy and distribution according to a multi-purpose flow analysis device assigned by the protocol. A mirror flow center controller uniformly controls forwarding logic of the whole mirror network flow, and provides soft defined interfaces.
Owner:BEIJING RUIHE YUNTU TECH CO LTD
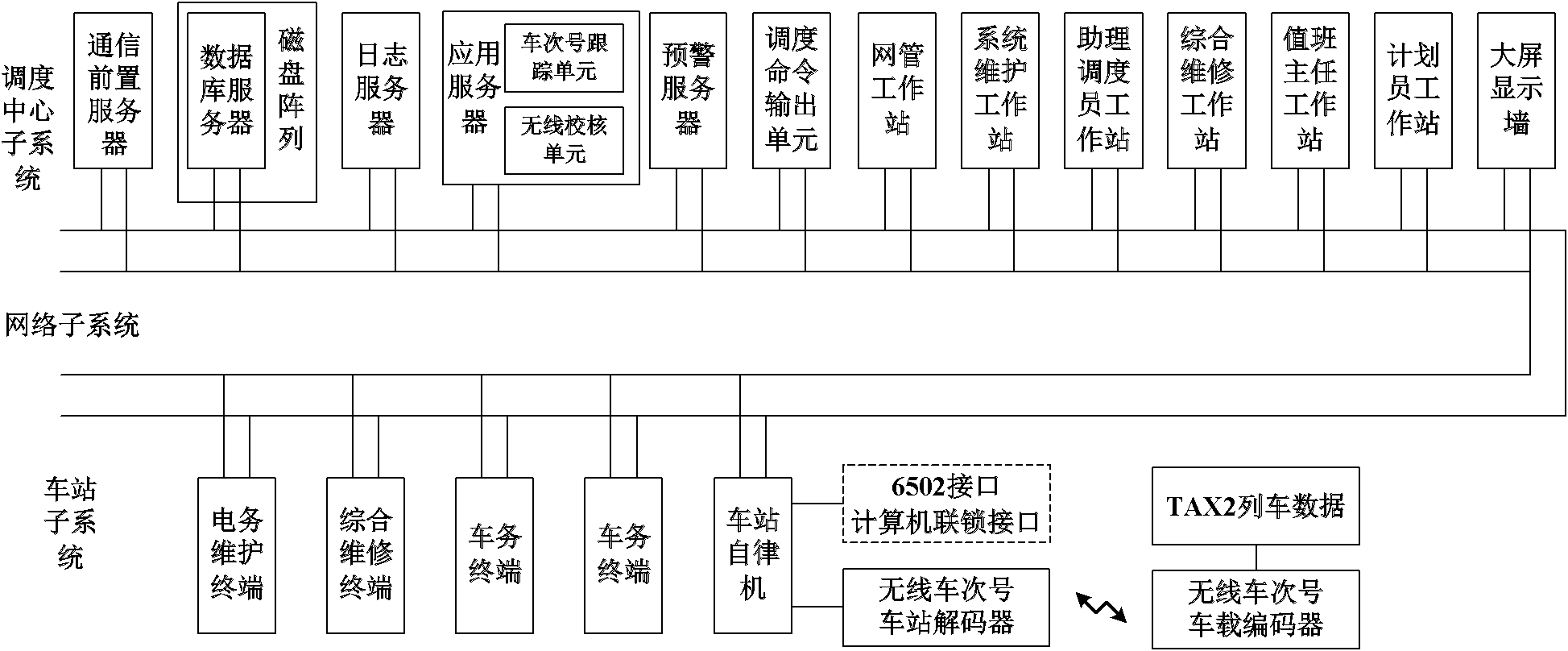
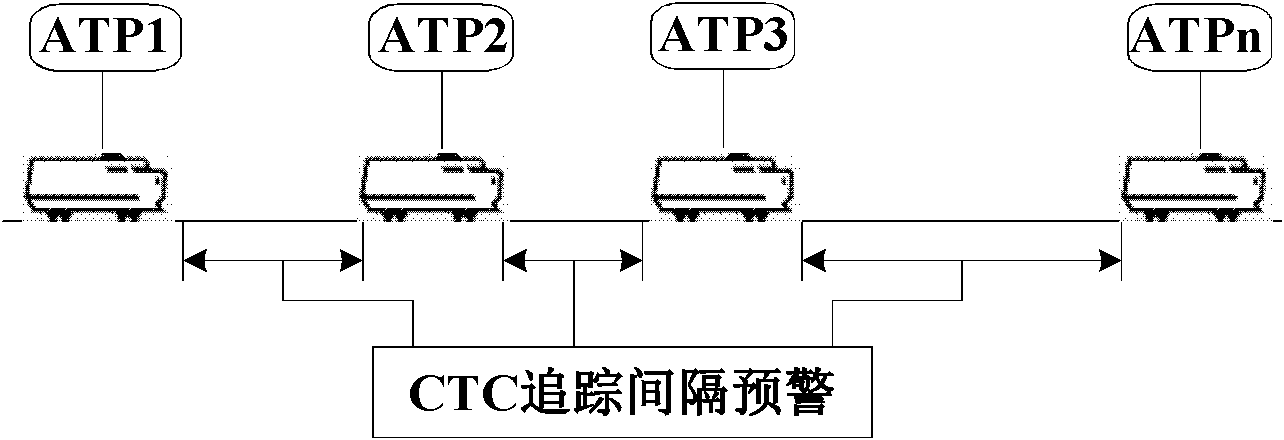
Train tracking interval real-time early warning system based on CTC (central traffic control) and early warning method
ActiveCN102514601APlay a supervisory roleImprove securityAutomatic systemsEarly warning systemApplication server
The invention discloses a train tracking interval real-time early warning system based on CTC (central traffic control) and an early warning method, which belong to the field of high-speed train safety control technology. A dispatching center subsystem early warning server of the system consists of an early warning server and a dispatching command output unit, an application server of the dispatching center subsystem consists of a train number tracking unit and a wireless checking unit, vehicular equipment comprises a wireless train number vehicular encoder, and the system comprises a wireless train number decoder. The method includes acquiring a train number from decoded train comprehensive information by the aid of the wireless checking unit, comparing the acquired train number with a train number obtained by the train number tracking unit, and acquiring an accurate and reliable train number; and computing tracking intervals of a train by the aid of the early warning server, and controlling the dispatching command output unit to output control instruction according to a computation result. The train tracking interval real-time early warning system based on CTC and the early warning method form double channels with an ATP (automatic train protection) computation tracking interval method, a monitoring effect for a train tracking interval ATP control effect is realized, and integral safety of a train control system is improved.
Owner:BEIJING JIAOTONG UNIV
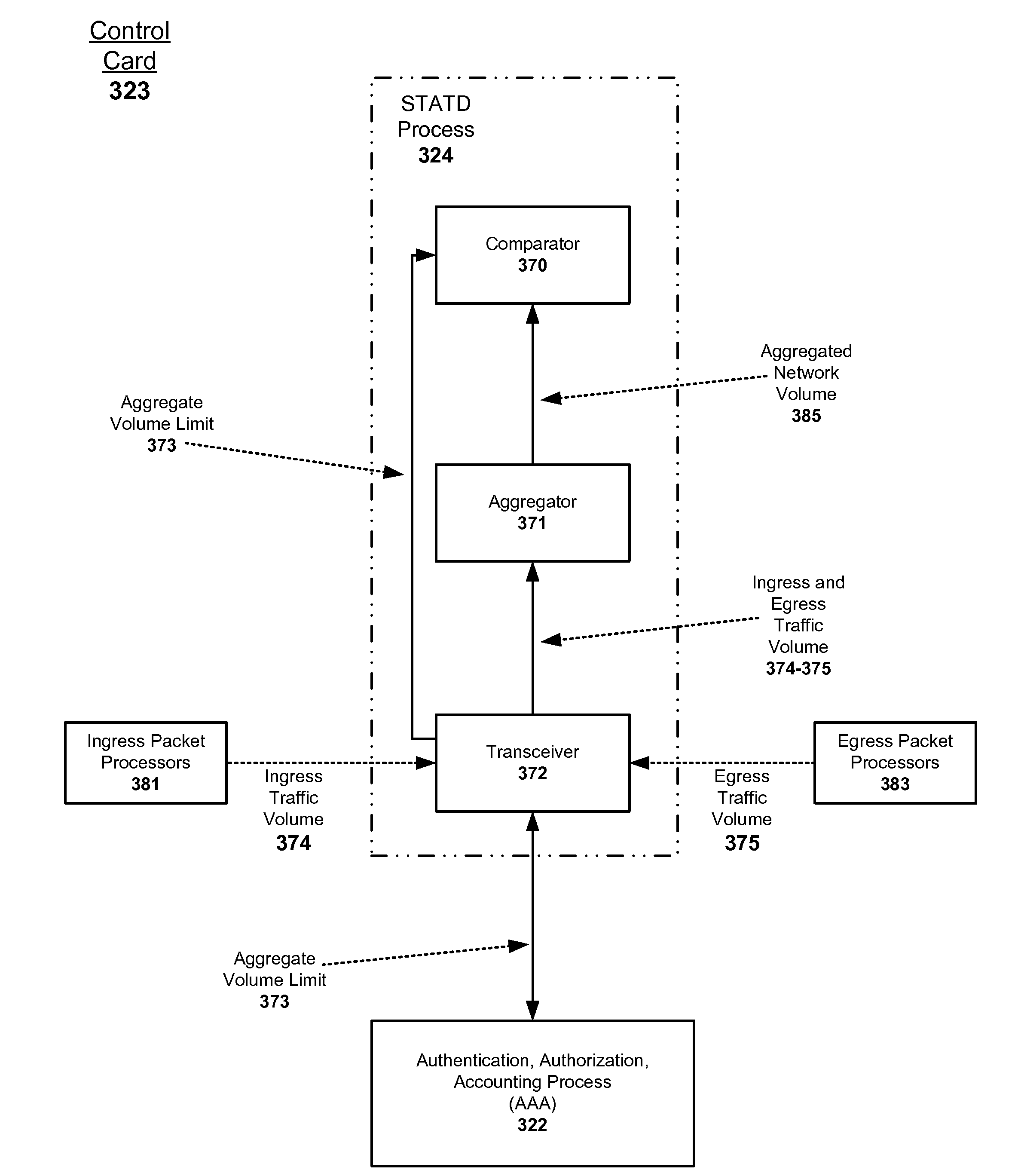
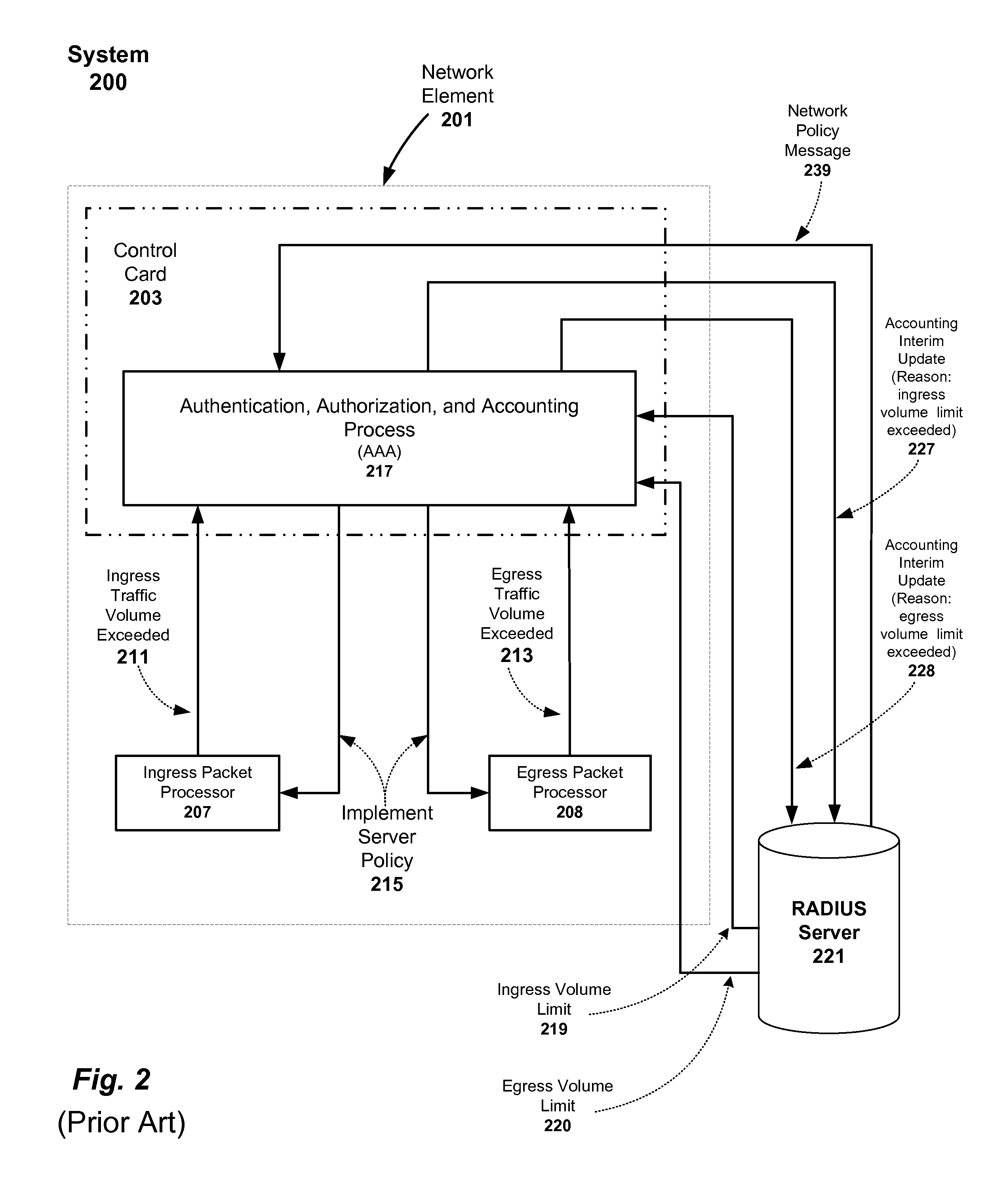
Adaptive method and apparatus for adjusting network traffic volume reporting
ActiveUS20090059812A1Traffic volume is limitedError preventionTransmission systemsTraffic capacityComputer network
An adaptive method and apparatus for accurate network traffic volume limit reporting including receiving a network traffic volume limit for each subscriber based on the subscriber's level of service and reporting the network traffic volume on a more frequent basis for subscribers who are approaching their network volume limit.
Owner:TELEFON AB LM ERICSSON (PUBL)
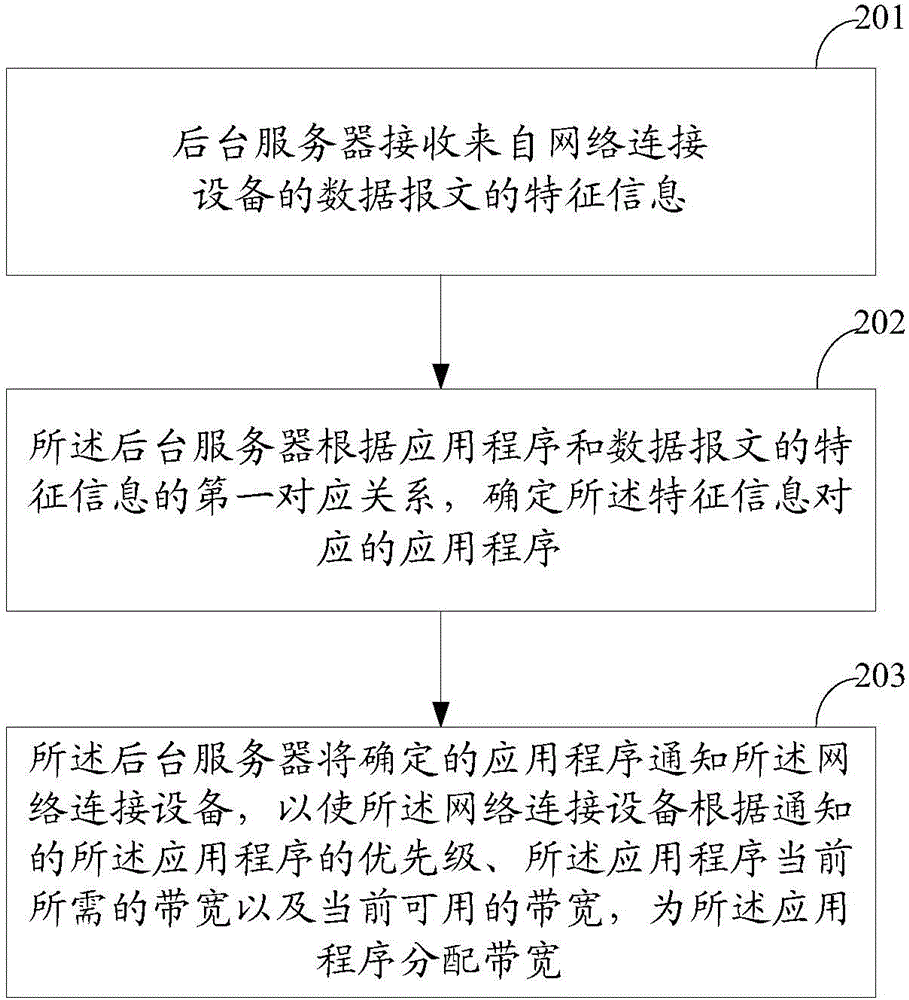
Network traffic control method and device
ActiveCN103986715ATimely processingEasy to controlData switching networksTraffic capacityNetwork communication
The embodiment of the invention relates to the technical field of network communication and provides a network traffic control method and device. The network traffic control method and device are used for solving the problem that bandwidth needed by a certain specific application program cannot be guaranteed during traffic control in a local area network in the prior art. The method comprises the steps of determining the application program corresponding to feature information of received data messages according to the first corresponding relation of the feature information of the data messages and the application program, determining the current bandwidth needed by the application program according to the bandwidth occupied by the received data messages of the application program, and distributing bandwidth for the application program according to the priority of the application program, the current needed bandwidth of the application program and the current available bandwidth. The network traffic control method and device enable the data messages of the application program of high priority to be processed in time.
Owner:HISENSE
Apparatus and method for providing dynamic communications network traffic control
InactiveUS7006831B2Less-expensive to providePromote activationAccounting/billing servicesNetwork traffic/resource managementControl communicationsCritical time
Systems and methods for controlling traffic on a communications network include dynamic and flexible control plans that enable service providers to control or influence customer access to communications facilities. Communications facilities are monitored to identify network elements, such as cell sites, that are overloaded. When the traffic intensity on a particular facility exceeds a predetermined level, either active or passive control is imposed on subscribers that are in the geographic area of the facility. Active control involves blocking, delaying or disrupting subscriber calls during the critical time period. Passive control involves providing cost incentives or disincentives during low or peak periods of traffic intensity. Customers are notified of the commencement and / or termination of active or passive control preferably via SMS. When implemented with stationary cellular service, the systems and methods aid in traffic engineering and provide opportunities for customers to reduce the cost and increase the accessibility of telephone service.
Owner:BELLSOUTH INTPROP COR
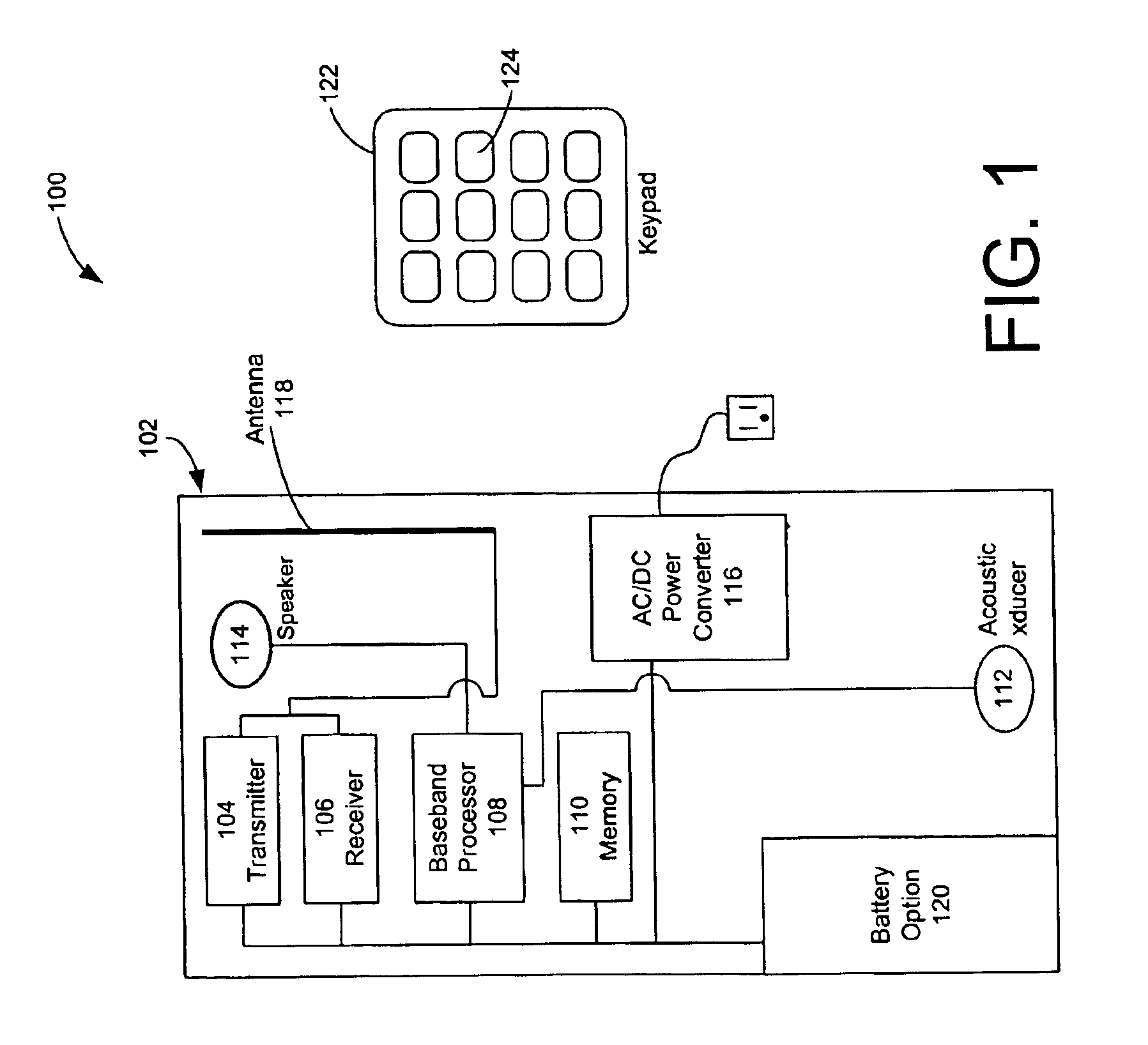
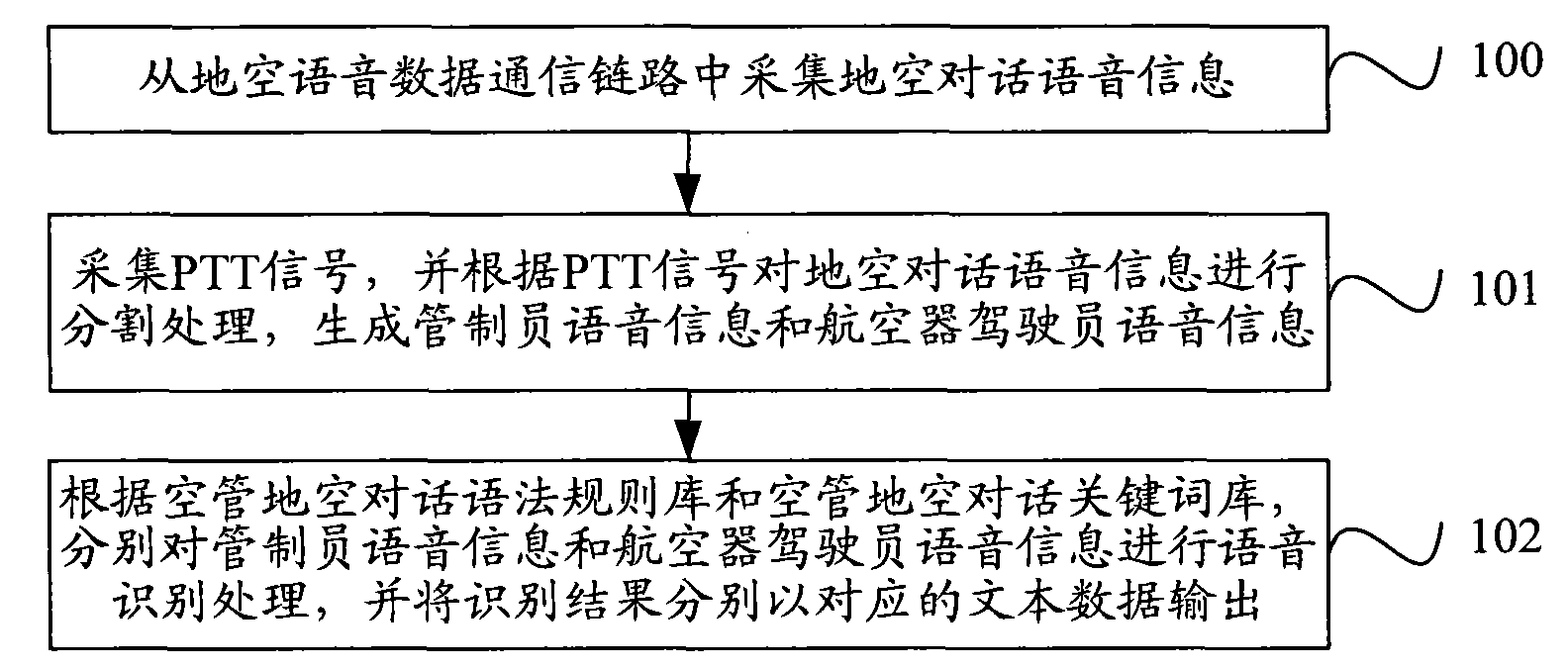
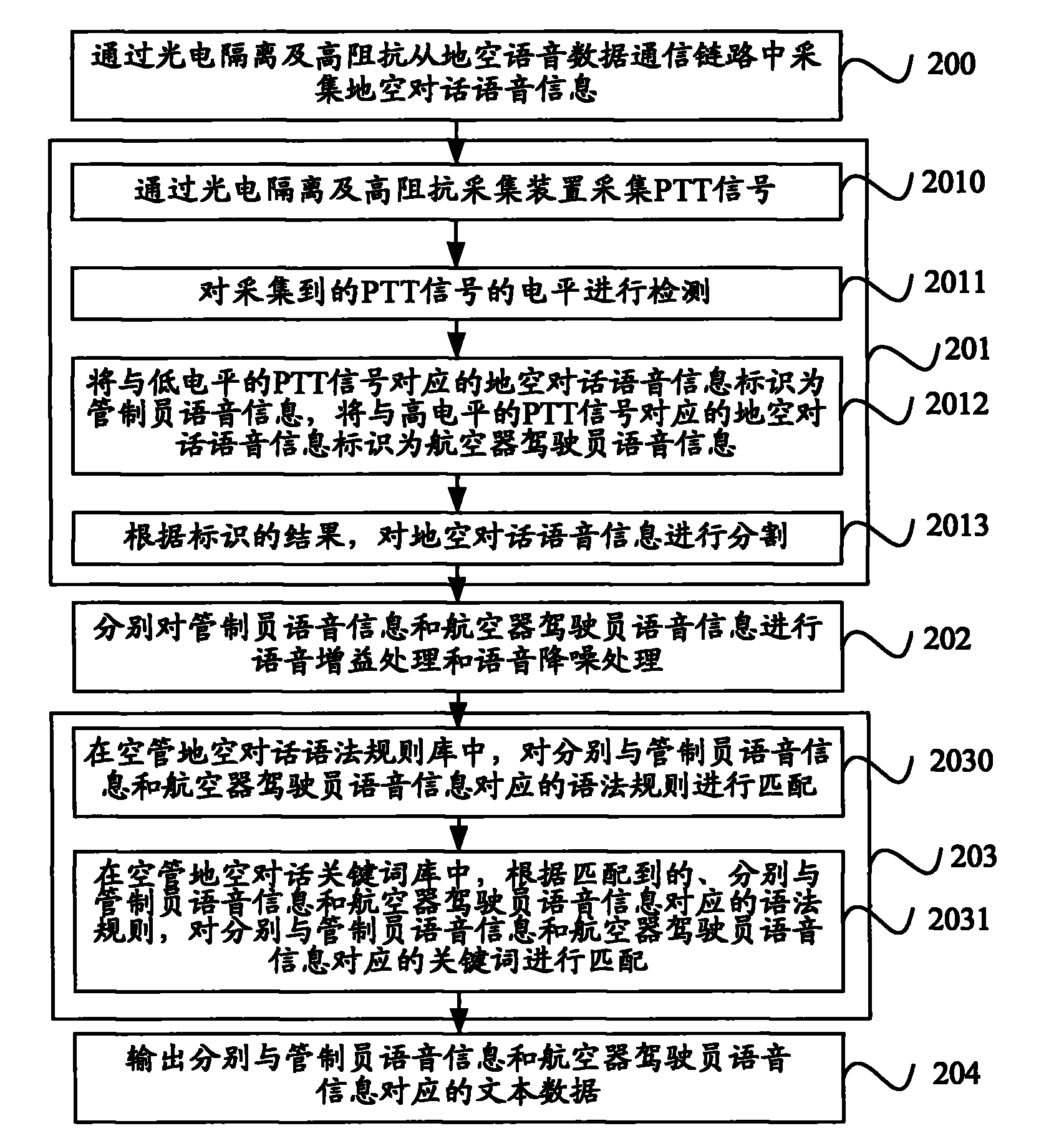
Voice recognition method and voice recognition device in air traffic control system
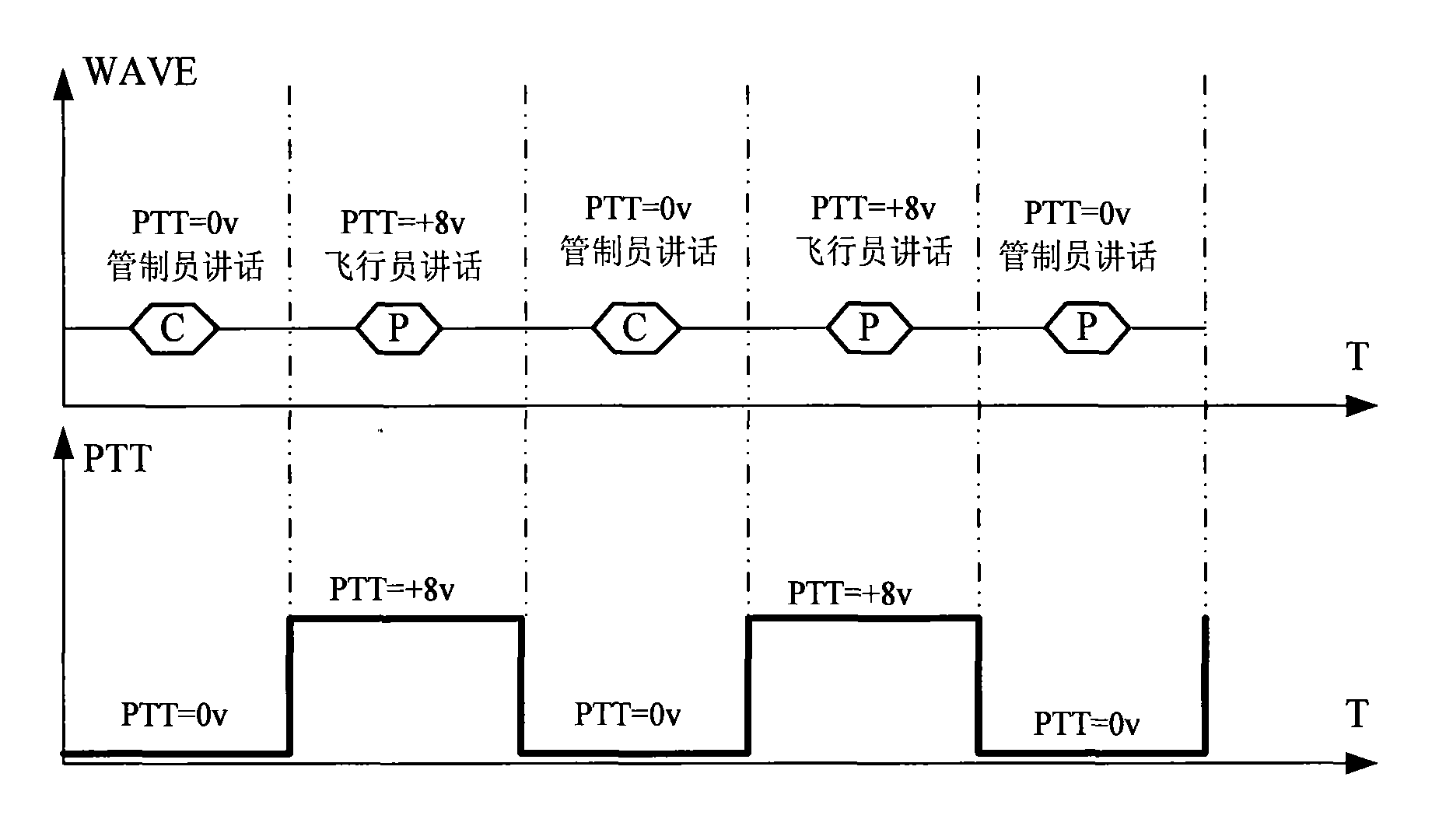
InactiveCN101916565AReduce error rateAccurate identificationSpeech recognitionStations for two-party-line systemsAviationDriver/operator
The invention provides a voice recognition method and a voice recognition device in an air traffic control system. The method comprises the following steps: collecting ground-to-air dialogue voice information from a ground-to-air voice communication link; collecting a PTT signal, segmenting the ground-to-air dialogue voice information according to the PTT signal to generate air traffic controller voice information and driver voice information in an aircraft; and carrying out voice recognition on the air traffic controller voice information and the driver voice information in the aircraft according to a preset air traffic control ground-to-air dialogue grammatical rule bank and a preset air traffic control ground-to-air dialogue keyword bank respectively, and outputting recognition results in corresponding texts. Through using a voice rule and keyword recognition method, the invention still provides accurate voice recognition service in the air traffic control system with high application complexity so as to further improve automation level of air traffic control and navigation safety and reliability in China, and the voice recognition device also can be applied to various complex application scenes in the aviation field.
Owner:北京华安天诚科技有限公司
Network flow control of Internet Of Things (IoT) devices
A method, apparatus and computer program product for use in monitoring and controlling network behavior of Internet of Things (IoT) devices connected to a network. According to this approach, a set of network characteristics of an IoT device (e.g., as published by the device manufacturer) are assigned various risk values and then monitored over an initial time period to generate a “fingerprint” of the device's network flow. This flow is then transformed into one or more flow control rules representing “normal” or abnormal behavior of the IoT device. Preferably, the rules are instantiated into a network boundary control system (NBCS), such as an enterprise router, gateway, or the like, and then enforced, e.g., to generate alerts or others actions when the rules are triggered. The approach enables dynamic and automated threat detection and prevention based on anomalous and / or known-bad behavior.
Owner:IBM CORP
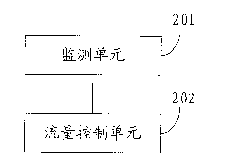
Method and device for controlling network traffic and local area network system
ActiveCN101827033AAvoid preemptionReduce deliveryError preventionData switching networksNetwork applicationControl network
The invention discloses a method and a device for controlling network traffic and a local area network system, wherein the method comprises the steps: monitoring a new uplink packet to be sent; controlling the traffic of the uplink packet to be sent in the following modes when triggering condition for traffic control is met: when the uplink packet to be sent comes from a first uplink packet applied in a preset high-priority network, the first uplink packet is added into an uplink sending caching queue; when the uplink packet to be sent comes from a second uplink packet applied in a preset non-high-priority network, whether the second uplink packet is allowed to be sent is determined according to current bandwidth occupation; if yes, the second uplink packet is added into the uplink sending caching queue, or else, the second uplink packet is discarded. The method is capable of lowering influence of some network application to other network applications.
Owner:BEIJING SOGOU TECHNOLOGY DEVELOPMENT CO LTD
Video chatting method and system
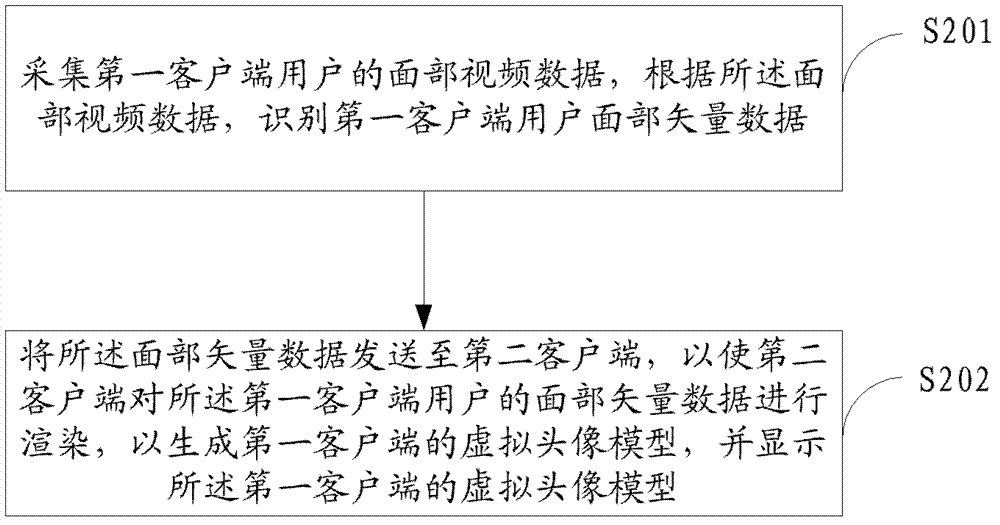
ActiveCN103368929APrivacy protectionLow costTwo-way working systemsData switching networksPattern recognitionNetwork reduction
The invention is applied to the technical field of computers, and provides a video chatting method and a video chatting system. The method comprises the following steps of acquiring the facial video data of a first client user, and identifying the facial vector data of the first client user according to the facial video data; and transmitting the facial vector data to a second client, so that the second client renders the facial vector data of the first client user to generate a virtual image model of the first client user, and displays the virtual image model of the first client user. According to the method and the system, the facial vector data is transmitted through a network in a video chatting process, so that network traffic is greatly reduced, the method and the system can be smoothly used in an ordinary mobile network, the data transmission speed is high, and the network traffic cost is greatly reduced.
Owner:TENCENT TECH (SHENZHEN) CO LTD
Network equipment type identification method and system based on decision tree
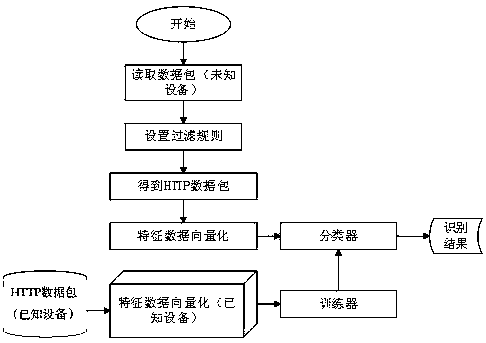
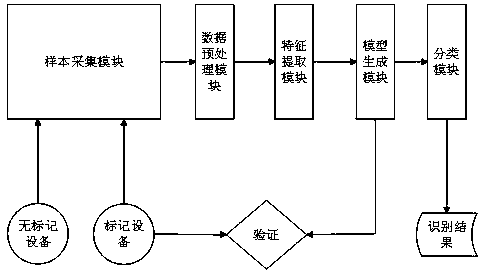
ActiveCN109063745AWon't catchIncrease varietyCharacter and pattern recognitionTransmissionTraffic capacityFeature vector
The invention relates to a network equipment type identification method and a system based on a decision tree, belonging to the technical field of network security. The method comprises the steps of collecting data flow of network equipment, preprocessing the network flow, extracting HTTP data packets from the flow, vectorizing the characteristic data of text type, and utilizing the characteristicvector to carry out decision tree. C45 classification, the final identification of the type of equipment; The invention can adopt a decision tree based on network traffic tree. C45 algorithm identifythat type of network device. The method is based on the passive method to detect the type of unknown device, which will not be captured by the intrusion detection system. At the same time, the type of unknown device can be recognized, and the type of unknown device can be added to the system to improve the generalization ability.
Owner:NANJING UNIV OF POSTS & TELECOMM
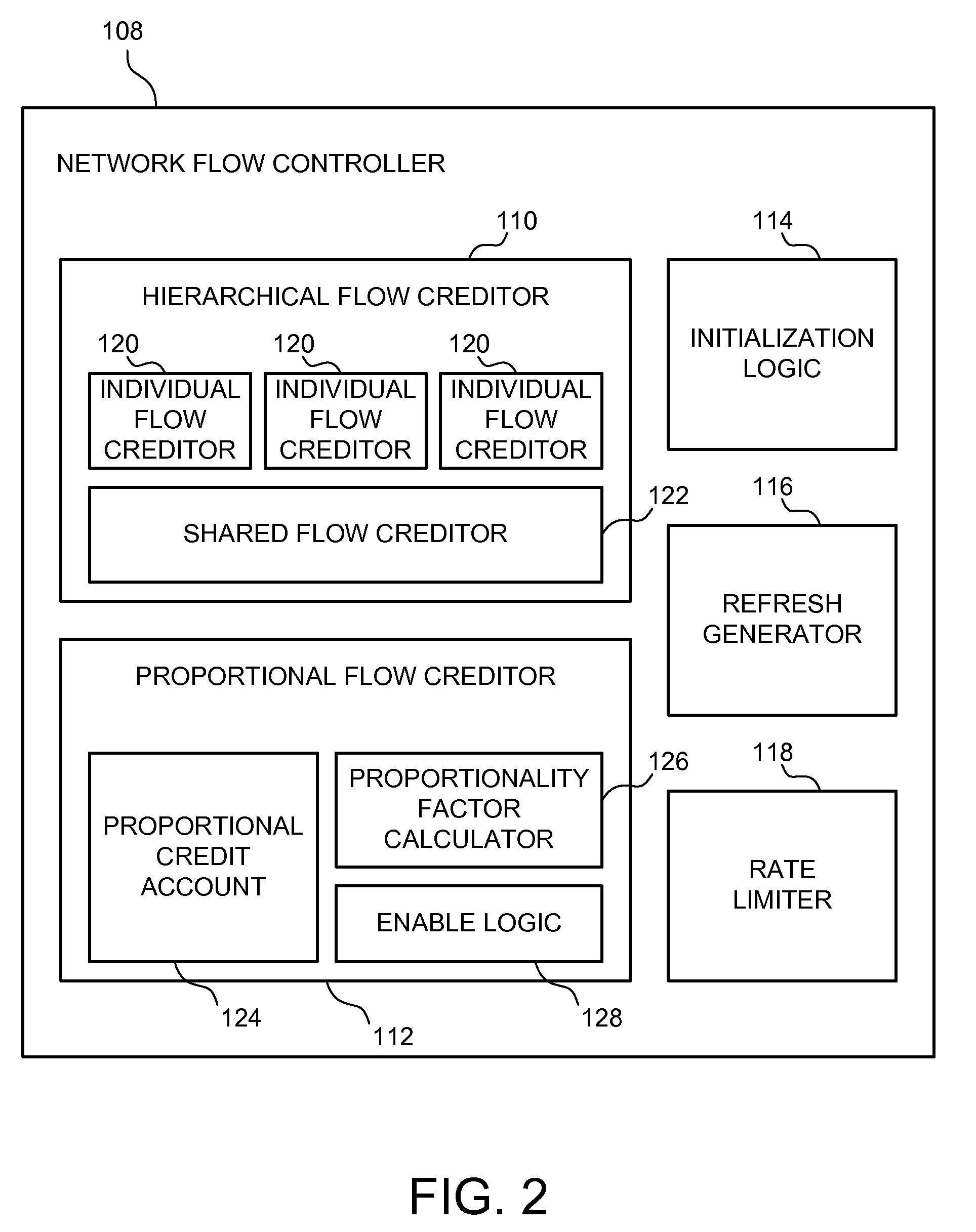
Hierarchical rate limiting with proportional limiting
InactiveUS20080316921A1Error preventionFrequency-division multiplex detailsRate limitingTraffic flow
A network flow controller to manage network traffic bandwidth is described. Embodiments of the network flow controller include a hierarchical flow creditor, a proportional flow creditor, and a rate limiter. The hierarchical flow creditor is configured to manage a plurality of hierarchical credit accounts. The hierarchical credit accounts include a shared credit account associated with a plurality of distinct network traffic flows for a shared bandwidth resource. The proportional flow creditor is configured to track an oversubscription of the shared bandwidth resource by the plurality of distinct network traffic flows. The rate limiter is coupled to the hierarchical flow creditor and the proportional flow creditor. The rate limiter is configured to limit at least one of the distinct network traffic flows based on the oversubscription tracked by the proportional flow creditor.
Owner:WSOU INVESTMENTS LLC
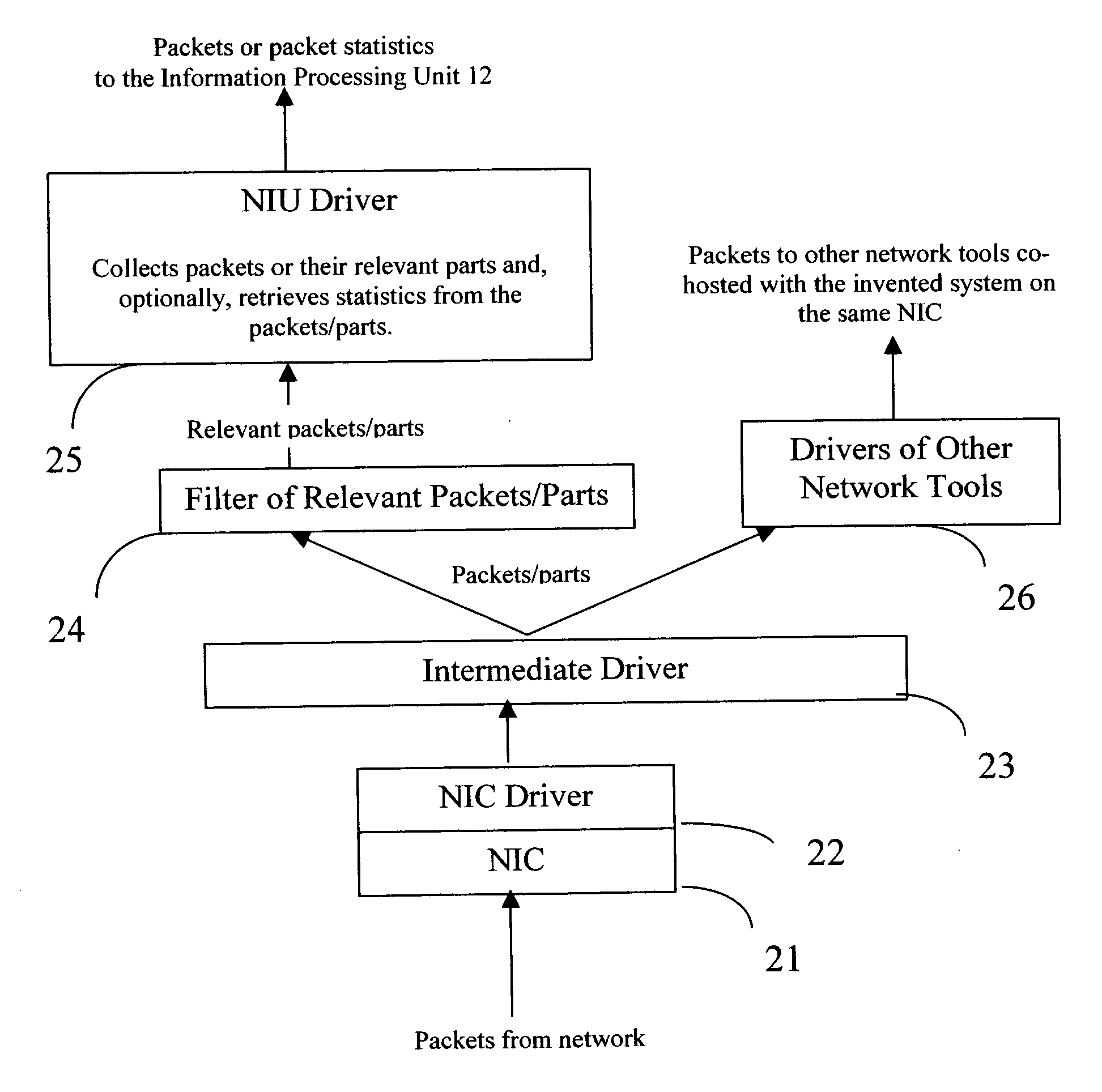
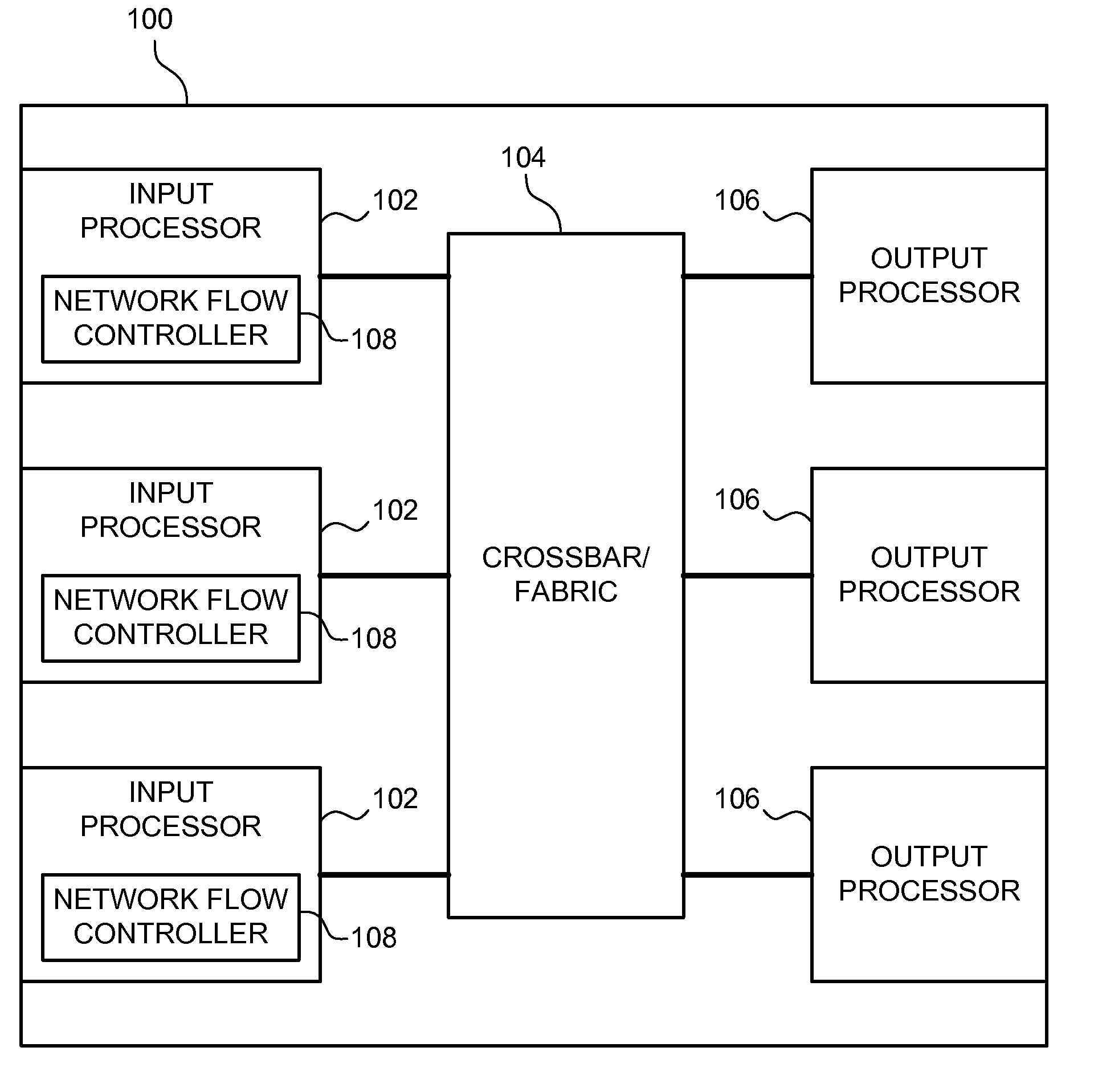
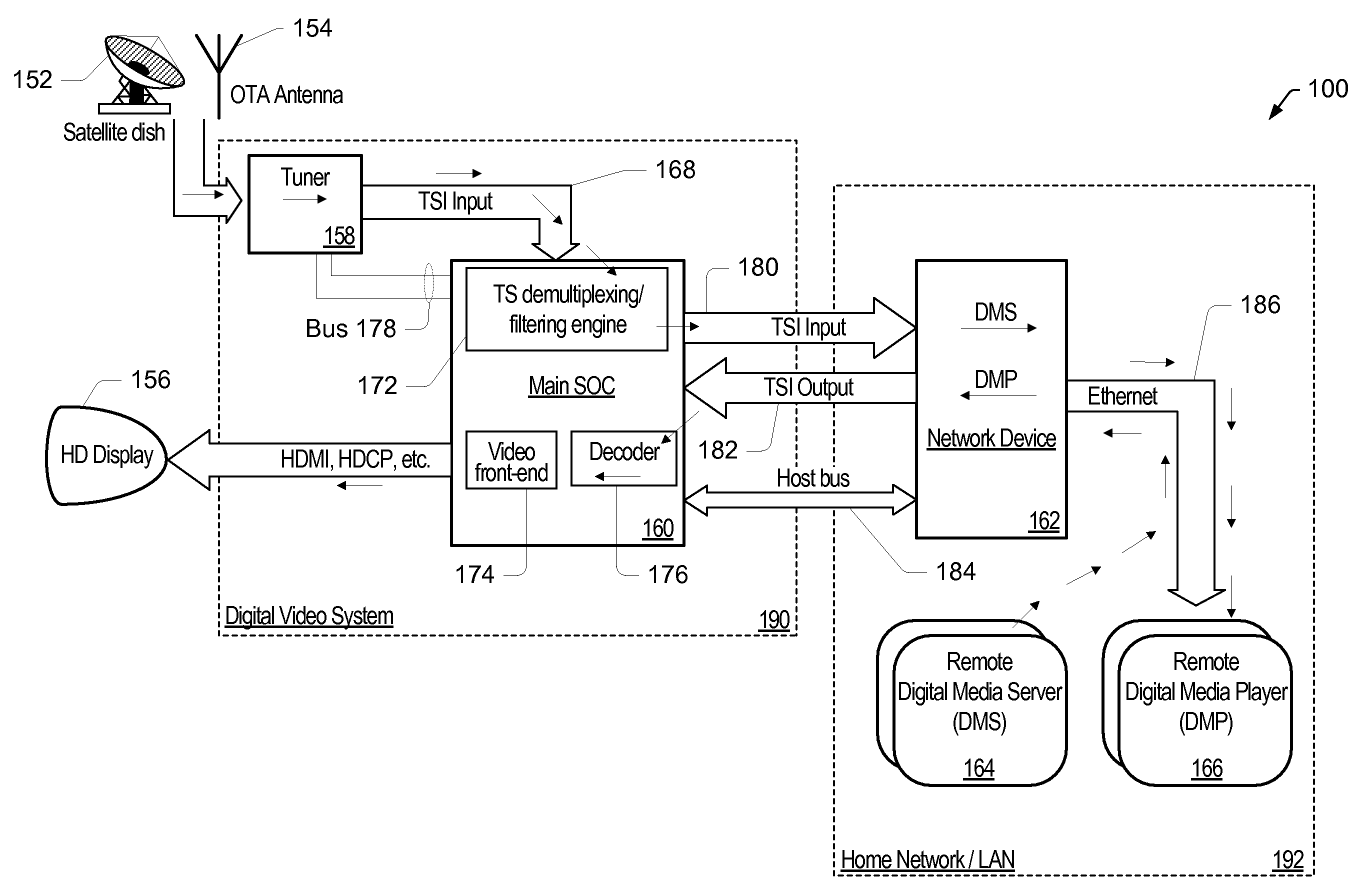
Network Traffic Controller (NTC)
ActiveUS20080109562A1Reduce CPU involvementMultiple digital computer combinationsSelective content distributionDigital videoNetwork address
A Network Device (ND) may be configured to enable secure digital video streaming for HD (high definition) digital video systems over a standard network. The ND may operate in at least one of two modes, a co-processor mode and a stand-alone mode, and may provide at least three high level functions: network interface control (NIC), video streaming offload (VSO), and stand-alone video streaming (SVS). To seamlessly execute the VSO functionality, the ND may be configured to have two network stacks running synchronously on a single network interface having a single network address. The two network stacks may share the data traffic, while the Host network stack may act as a master, and configure the ND network stack to accept only specifically designated traffic, thus offloading some of the data processing to the processor configured in the ND. The ND network system may appear as an ordinary network controller to the Host, from which the user may configure the ND network driver to obtain / set the network address, configure the physical layer link speed and duplex mode, configure the multicast filter settings, and obtain and clear the network level statistics.
Owner:MICROCHIP TECH INC
Lightweight Application Classification for Network Management
ActiveUS20100014420A1Method can be usedEasy to useError preventionTransmission systemsTraffic capacityNetwork management
Managing network traffic to improve availability of network services by classifying network traffic flows using flow-level statistical information and machine learning estimation, based on a measurement of at least one of relevance and goodness of network features. Also, determining a network traffic profile representing applications associated with the classified network traffic flows, and managing network traffic using the network traffic profile. The flow-level statistical information includes packet-trace information and is available from at least one of Cisco NetFlow, NetStream or cflowd records. The classification of network flows includes tagging packet-trace flow record data based on defined packet content information. The classifying of network flows can result in the identification of a plurality of clusters based on the measurement of the relevance of the network features. Also, the classification of network traffic can use a correlation-based measure to determine the goodness of the network features.
Owner:AT&T INTPROP I L P
Network flow control method and device
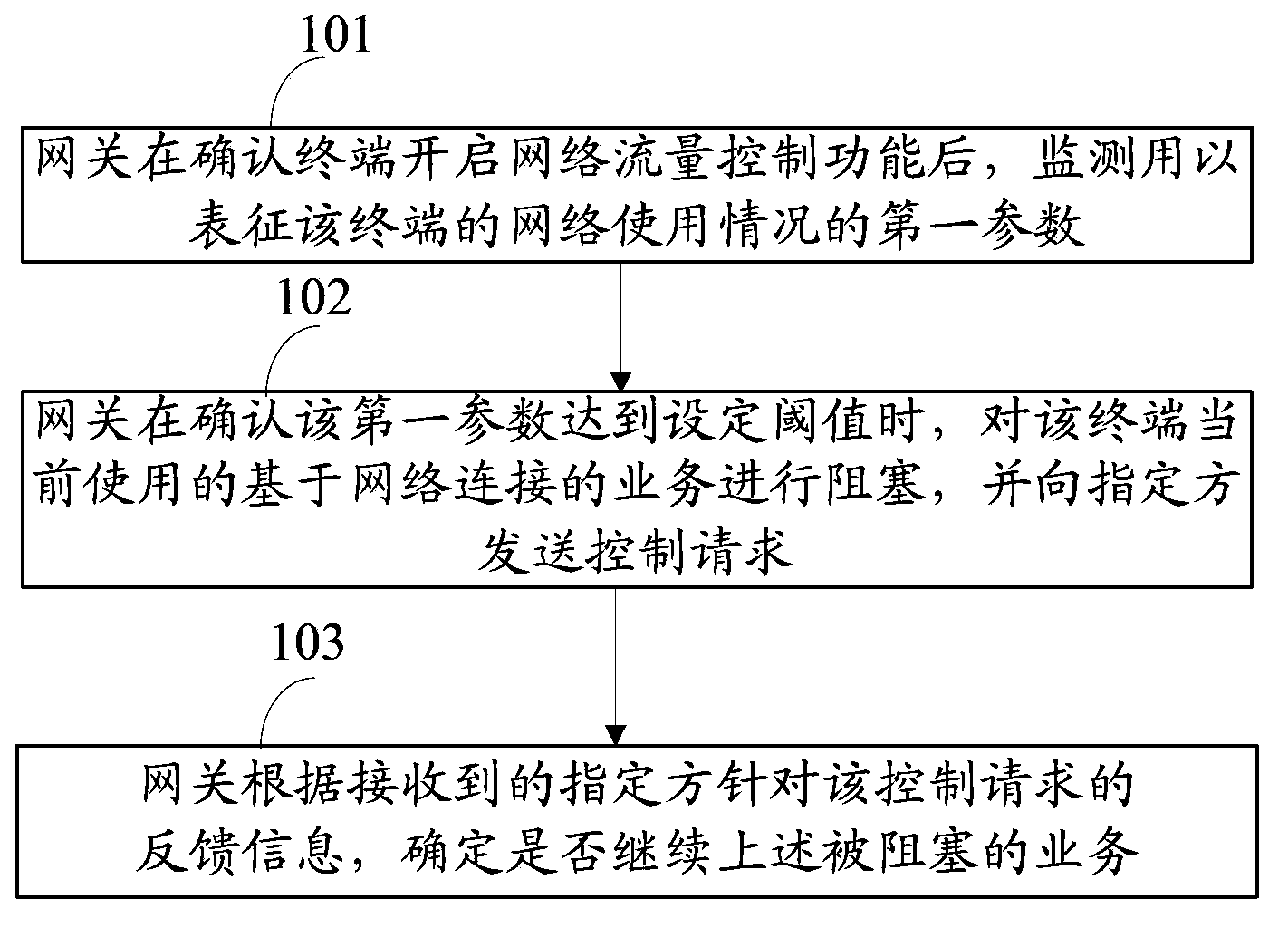
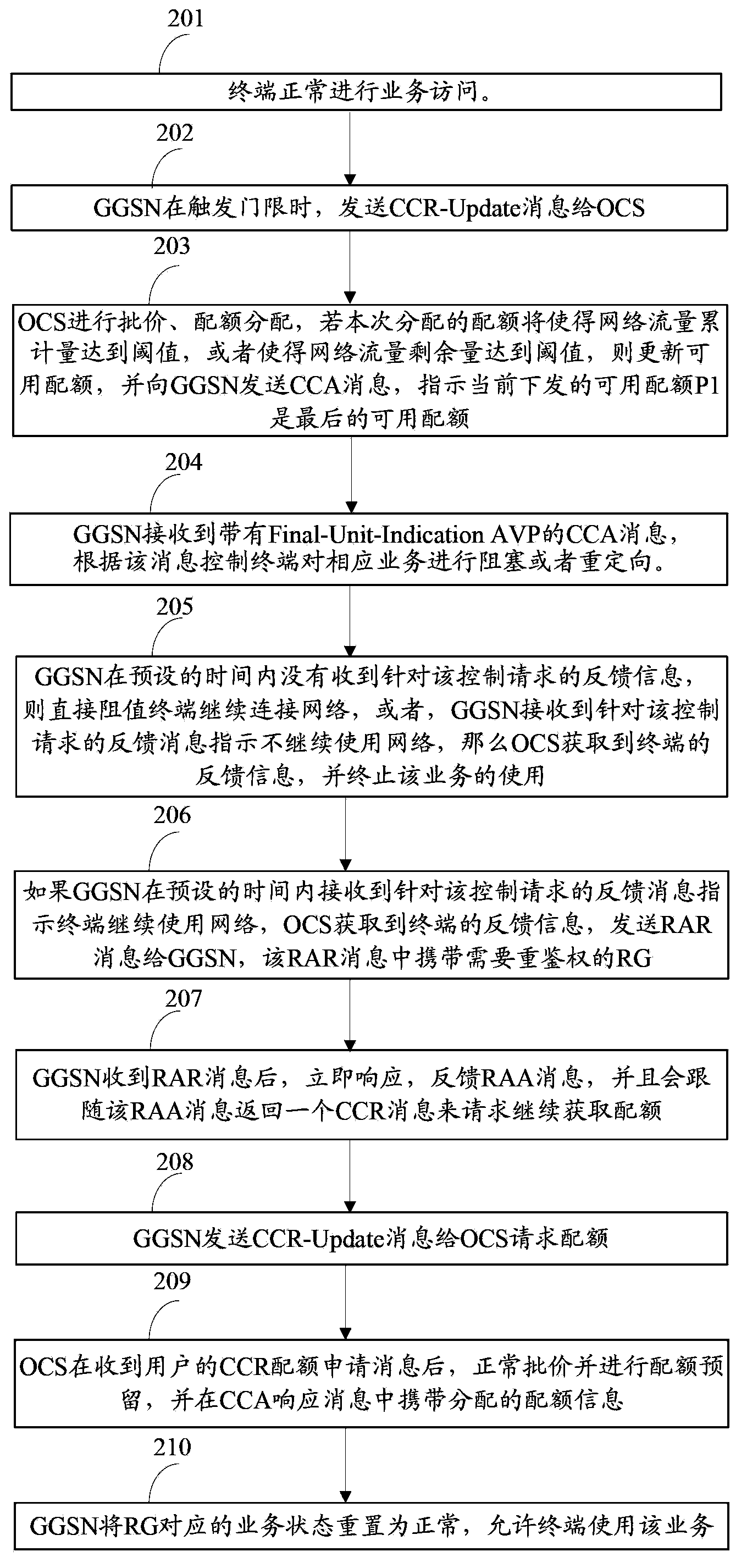
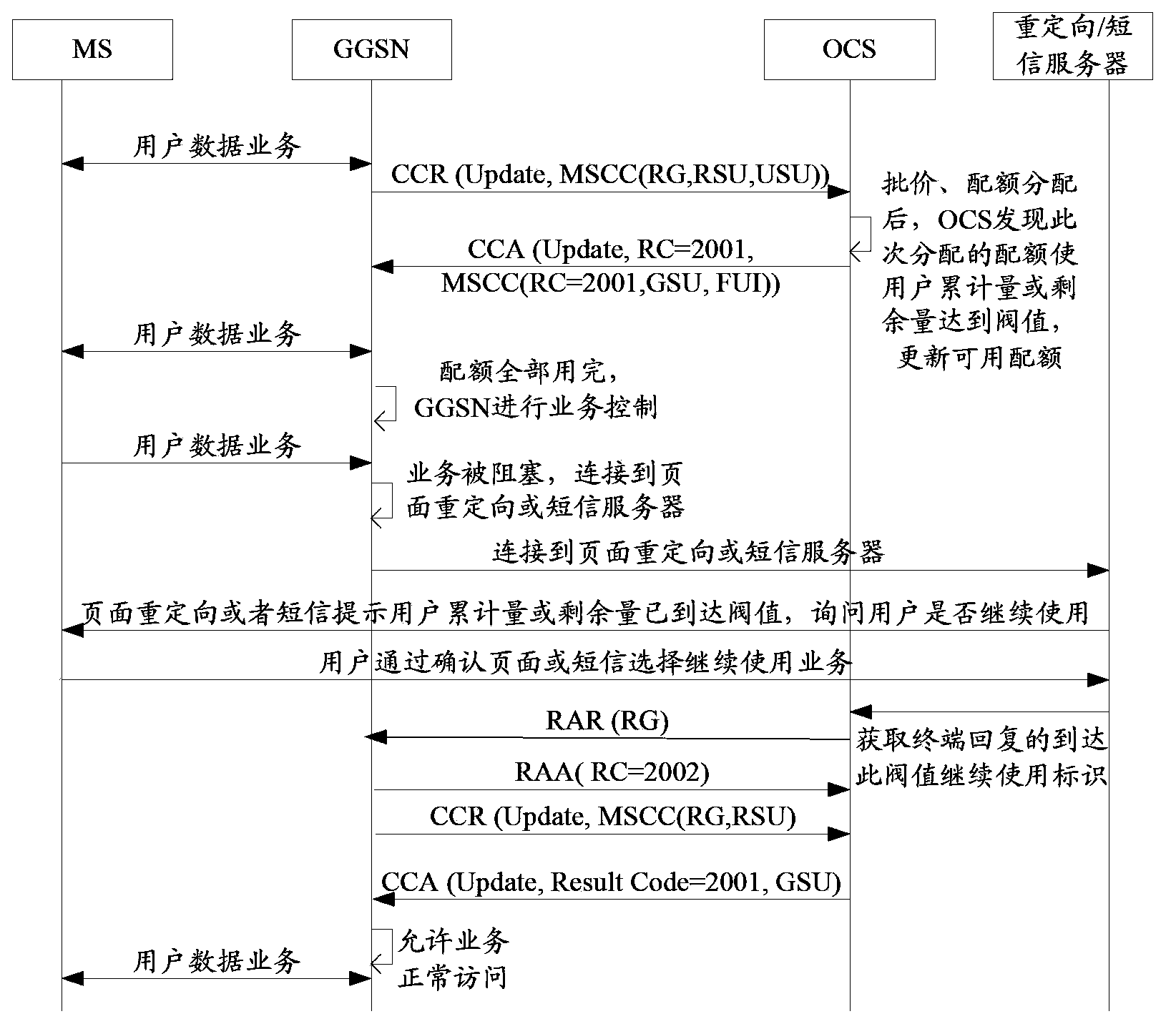
An embodiment of the invention discloses a network flow control method and device. The method includes monitoring a first parameter used for representing the network use condition of a terminal after determining that the terminal starts a network flow control function; blocking business currently used by the terminal and based on network connection when determining that the first parameter reaches a set threshold and transmitting a control request to an assigned party; determining whether to continue the business aiming at feedback information of the control request according to the received assigned policy. The method and device is used for solving the problem in the prior art that the network using behavior of the terminal cannot be controlled accurately due to the fact that the business cannot be suspended before network flow generation or in the network flow generation process.
Owner:CHINA MOBILE GROUP SHANDONG
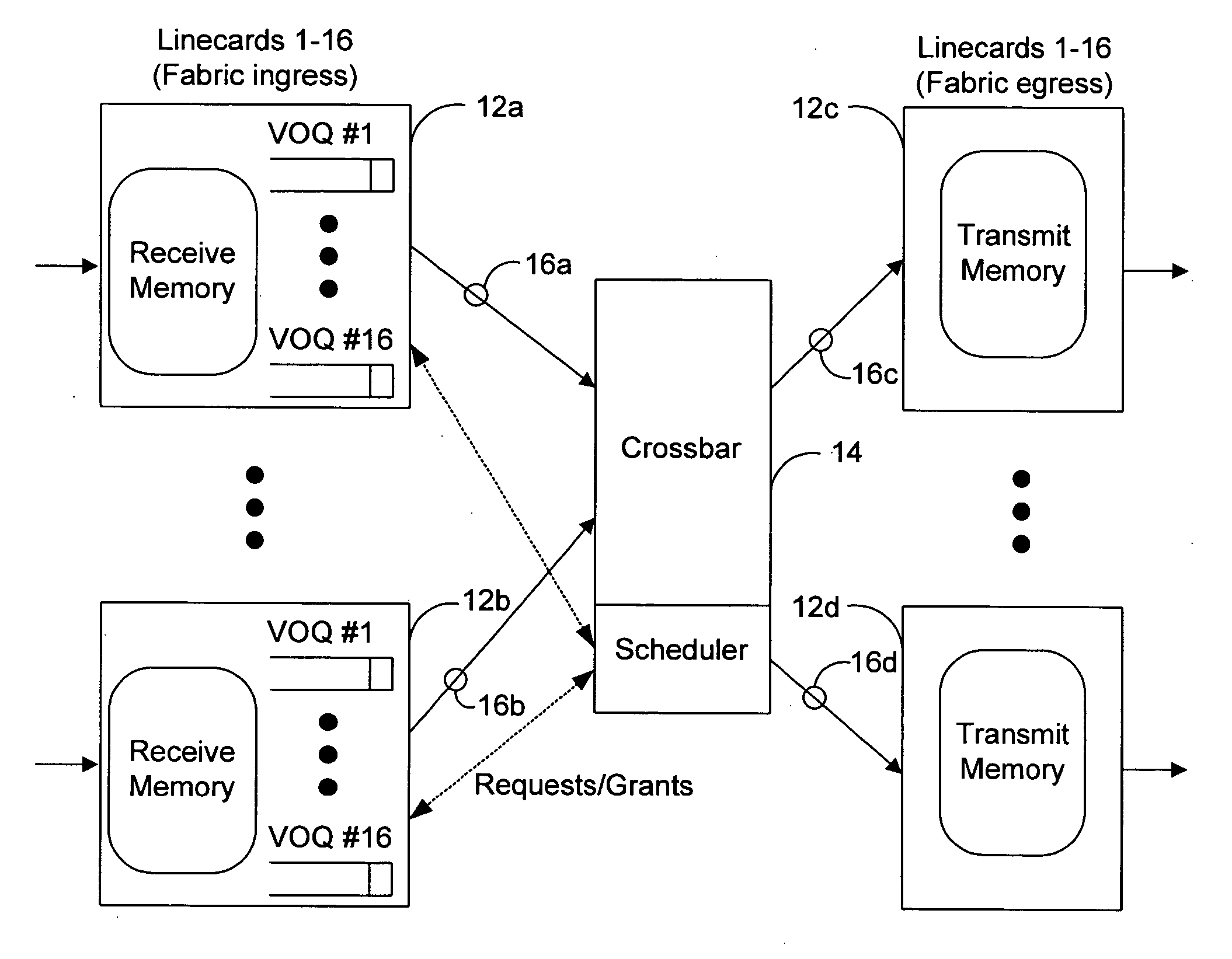
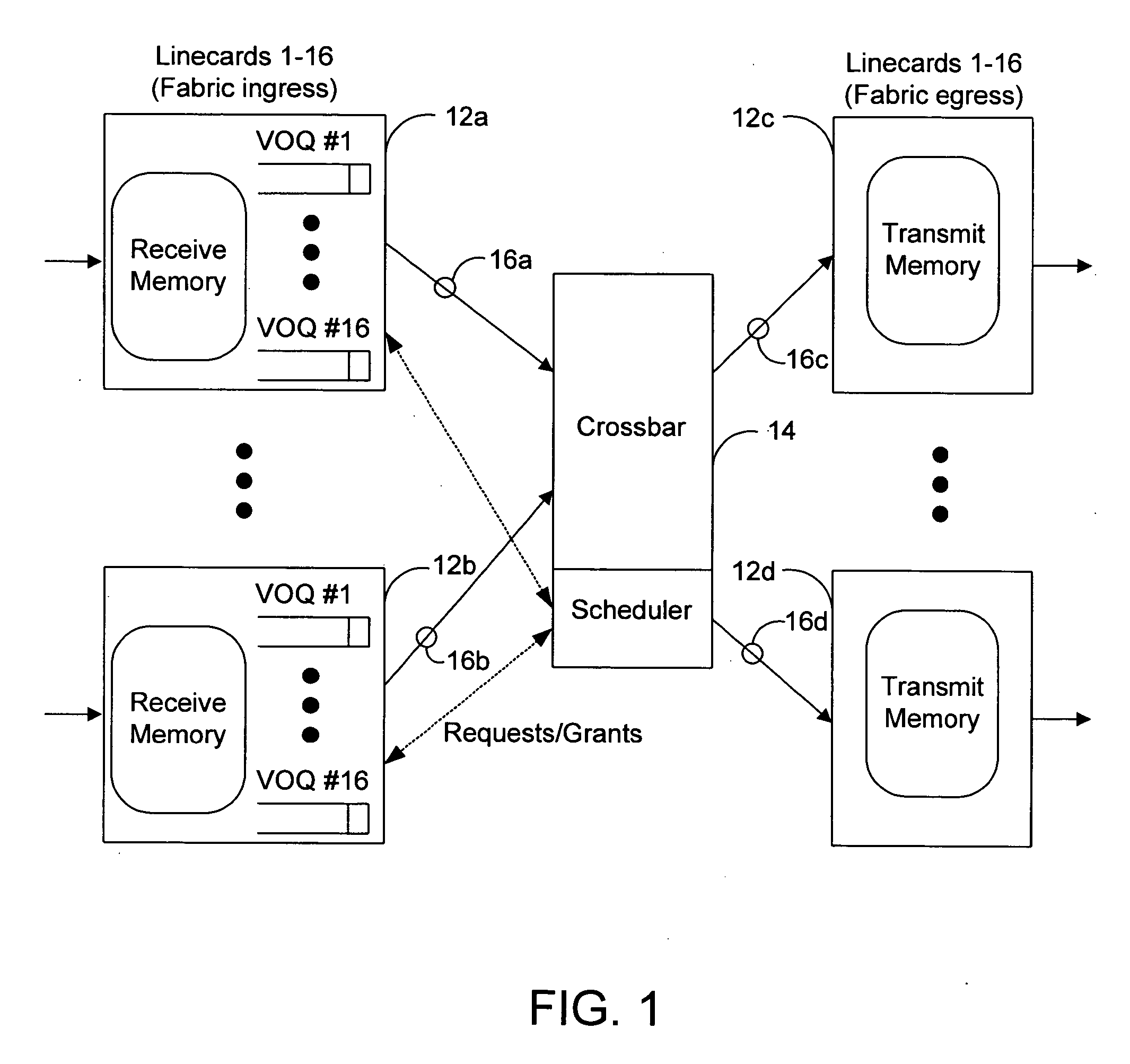
Queue aware flow control
A network flow control system utilizes flow-aware pause frames that identify a specific virtual stream to pause. Special codes may be utilized to interrupt a frame being transmitted to insert a pause frame without waiting for frame boundaries.
Owner:CISCO TECH INC
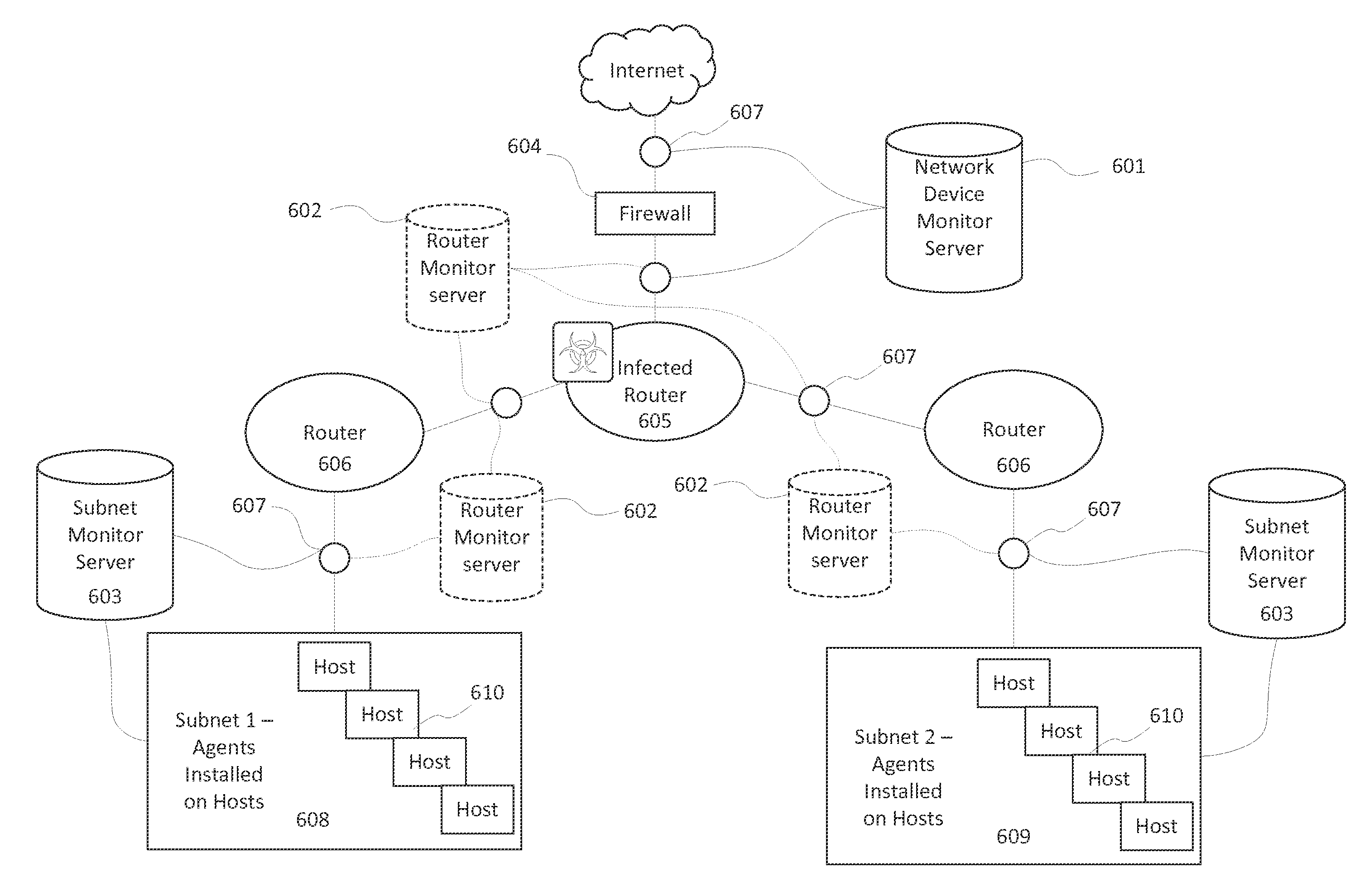
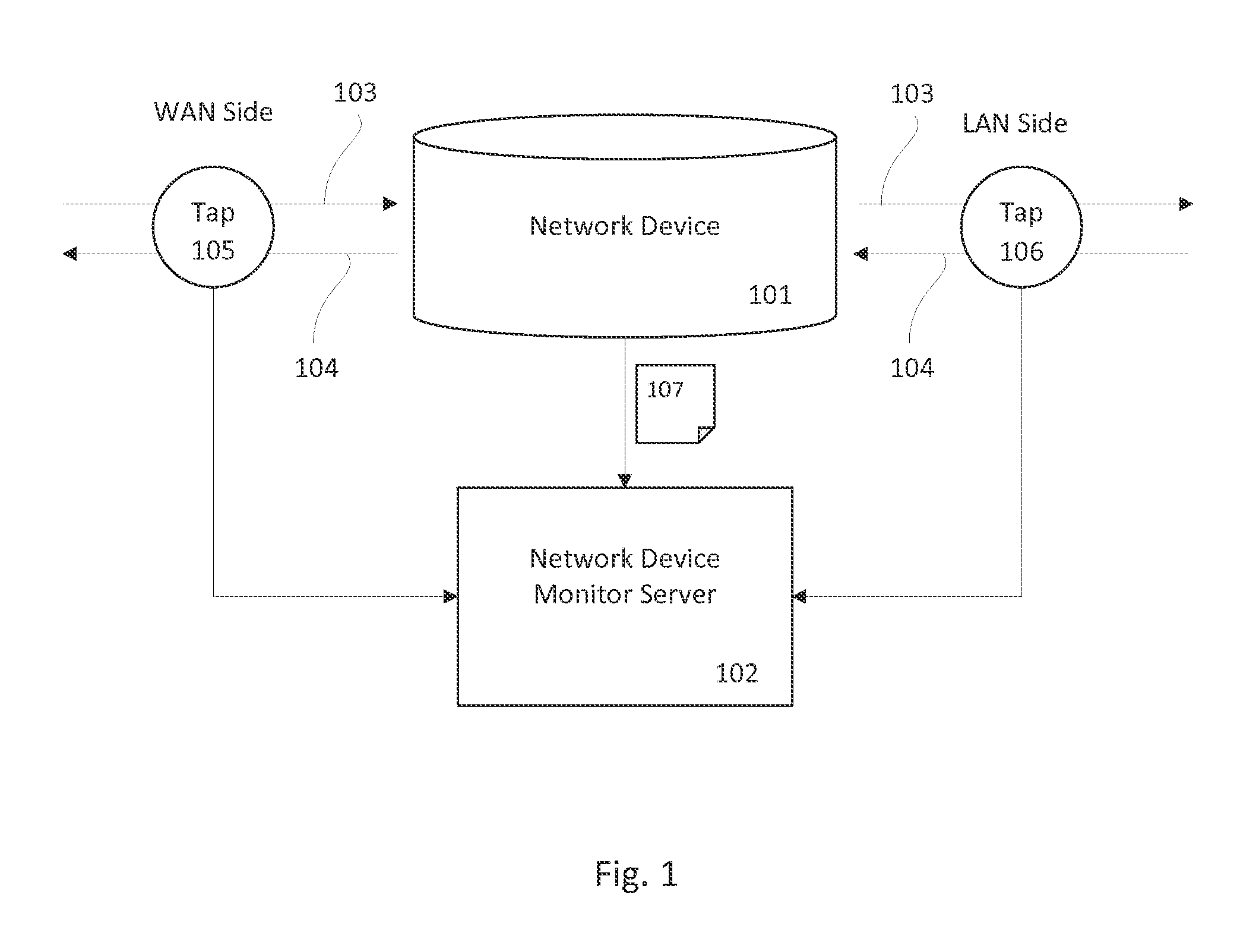
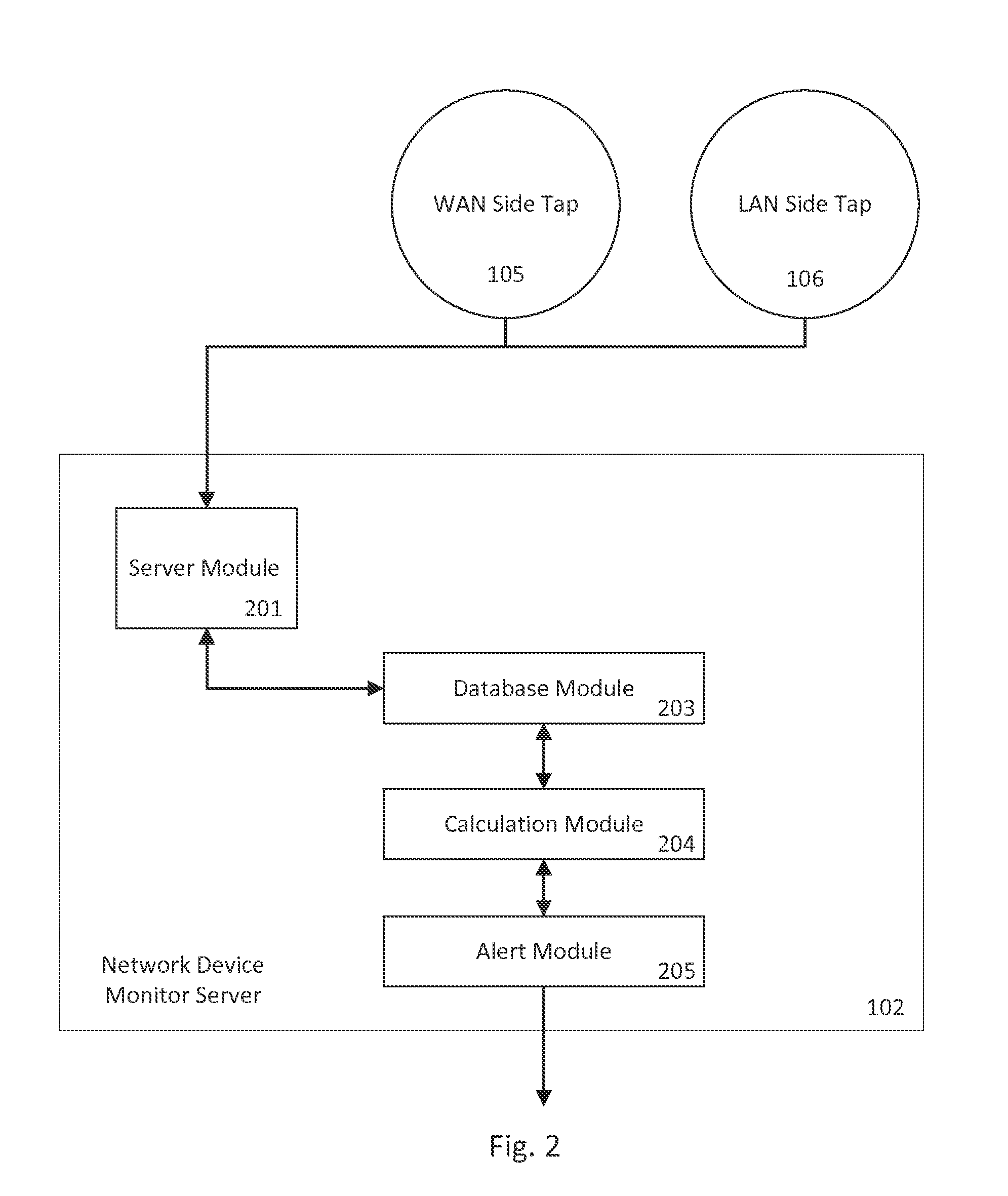
Identifying malware-infected network devices through traffic monitoring
The present invention generally relates to detecting malicious network activity coming from network devices such as routers and firewalls. Specifically, embodiments of the present invention provide for detecting stealth malware on a network device by comparing inbound and outbound network traffic to discover packets originating from the network device and packets that violate configuration rules. When combined with a network traffic monitor server configured to monitor actual network traffic reports and to receive known network traffic reports from host computers, the system can detect stealth network traffic originating from both network devices and host computer systems.
Owner:HEILIG DAVID PAUL
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com