Mirror network flow control protocol in virtualization network environment
A flow control and mirroring network technology, applied in the field of information security, can solve the problems of resource waste, serious occupation of business physical computer computing resources and network resources, analysis of data packet occupation, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0039] The present invention will be described in further detail below in conjunction with the accompanying drawings.
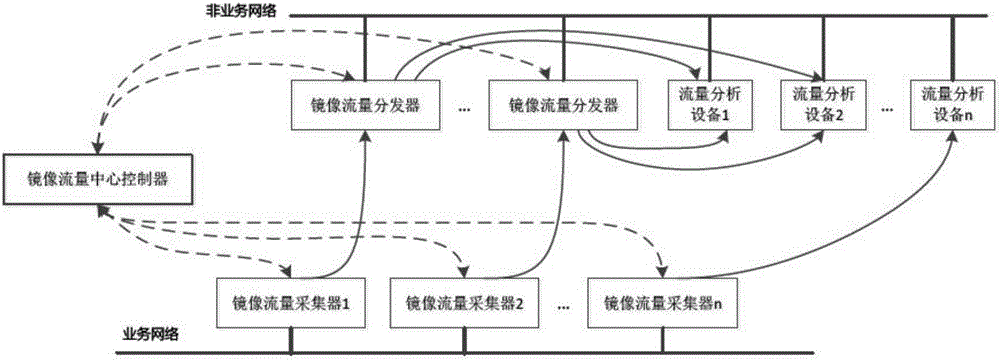
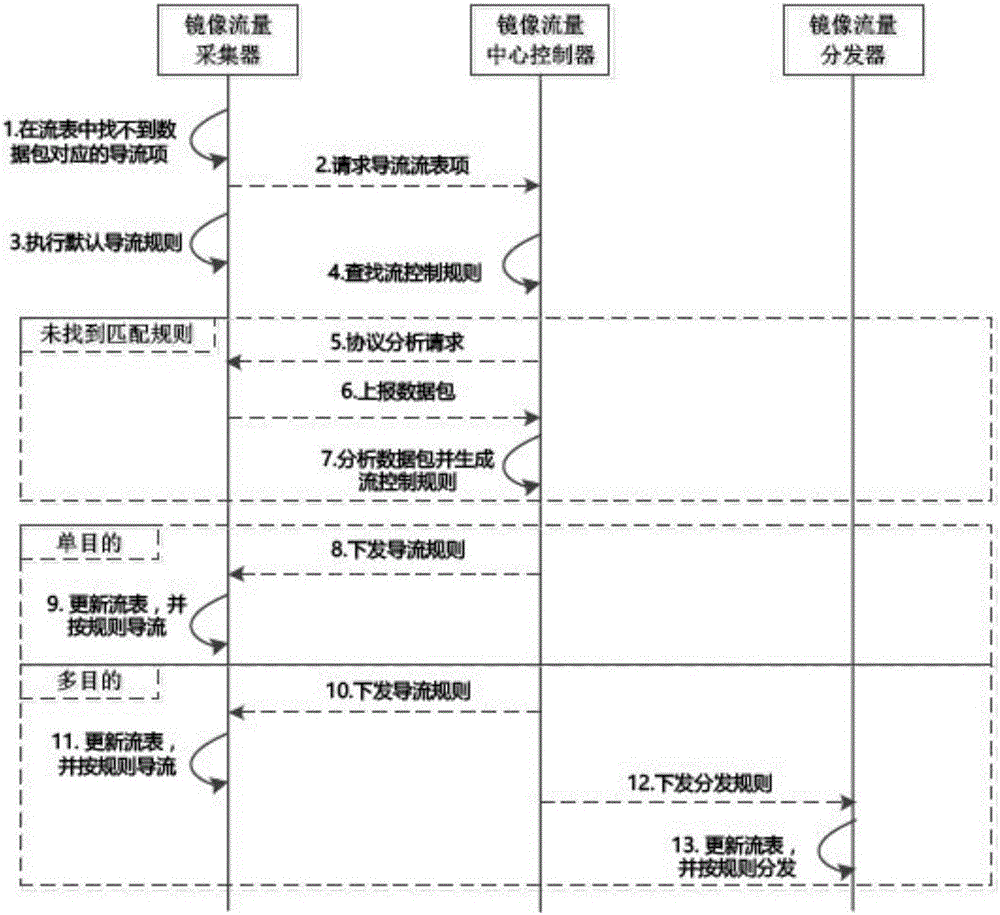
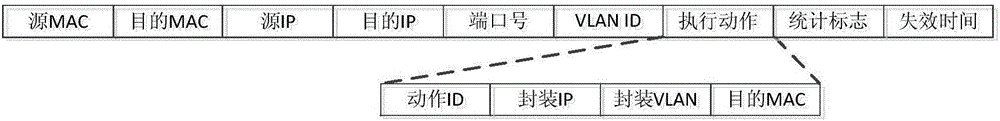
[0040] like Figure 10 As shown, assuming that the network load of physical host A is high, the communication traffic between virtual machine A and virtual machine B is not in the diversion flow tables of mirrored traffic collector 1 and mirrored traffic collector 2 . The communication traffic between virtual machine A and virtual machine B includes video service flow and internal calls of general business systems. The internal call traffic of the business system needs to be monitored and audited by the intrusion detection system and application performance management system, but the The flow entry also does not exist in the mirror traffic center controller. The reason is that the mirrored traffic center controller only stores policies issued by users through software definition instead of specific flow entries. Policy such as protocol X of virtual machine ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com