Patents
Literature
88 results about "Traffic profile" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
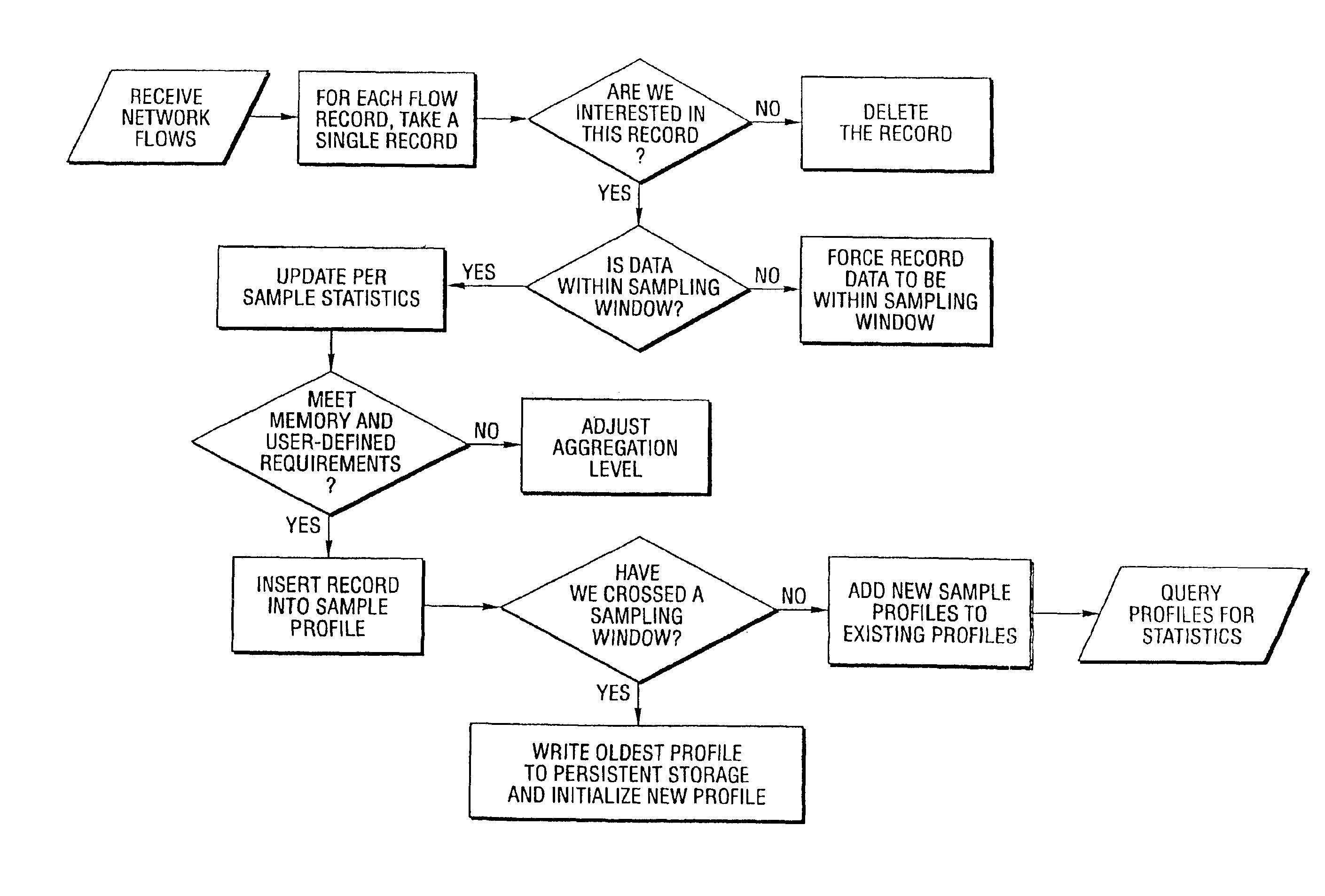
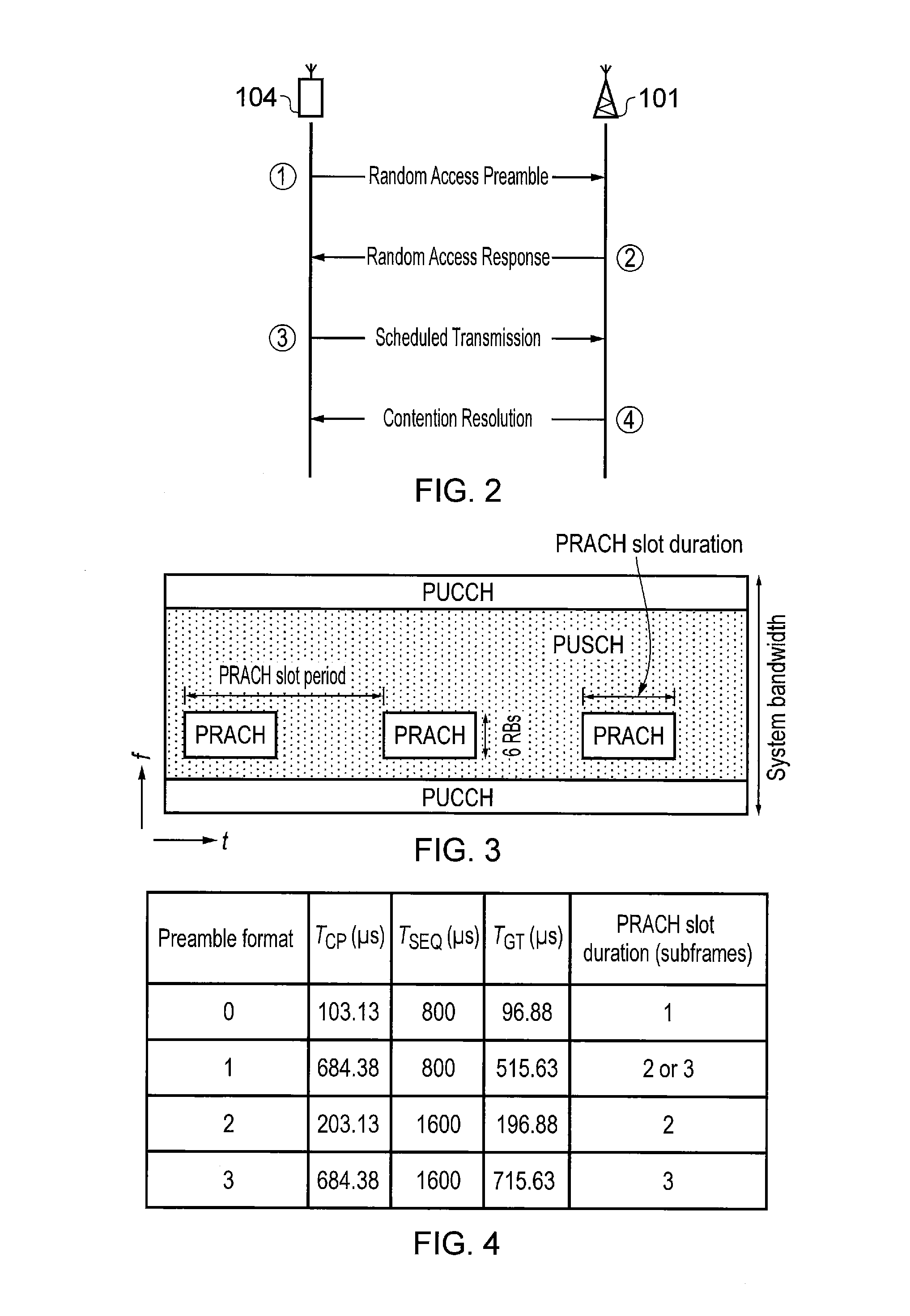
Method and system for profiling network flows at a measurement point within a computer network
InactiveUS6944673B2Multiple digital computer combinationsData switching networksTraffic characteristicMeasurement point
A method and system for profiling network flows at a measurement point within a computer network is provided. The method includes measuring network flows having invariant features at a measurement point located within routing infrastructure of the computer network to obtain flow statistics. The method also includes aggregating the flow statistics to obtain a traffic profile of the network flows at the measurement point. The method and system utilize the natural hierarchy in the Internet addressing scheme to provide a means for making tractable measurements of network traffic in high-speed networks. Moreover, the method and system adapt dynamically to the changing underlying traffic characteristics to maintain a maximum memory footprint for the profiles. The method and system adapt by adjusting the level of aggregation of the traffic endpoints along a scale from Interface to fully specified network address.
Owner:RGT UNIV OF MICHIGAN
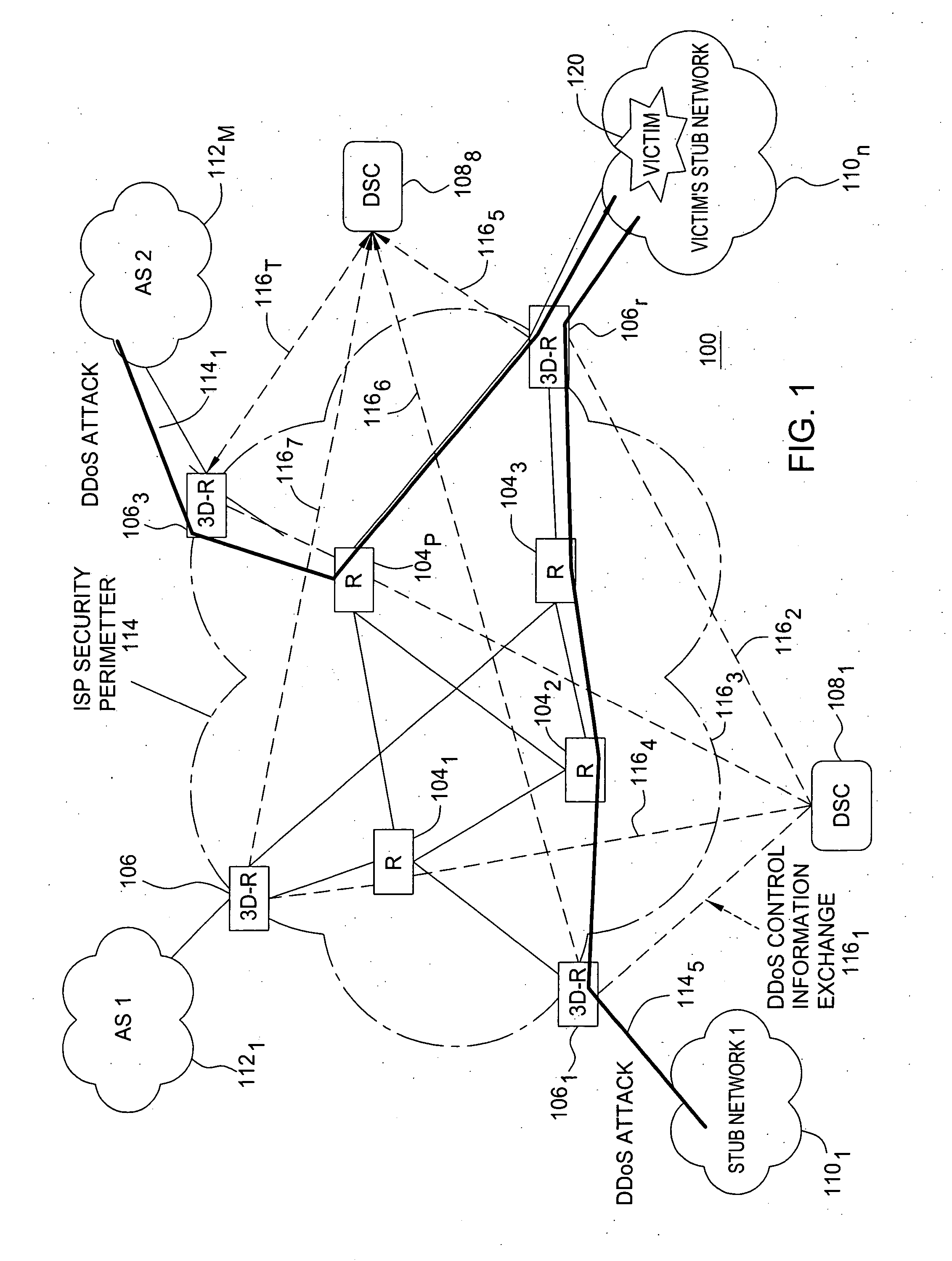
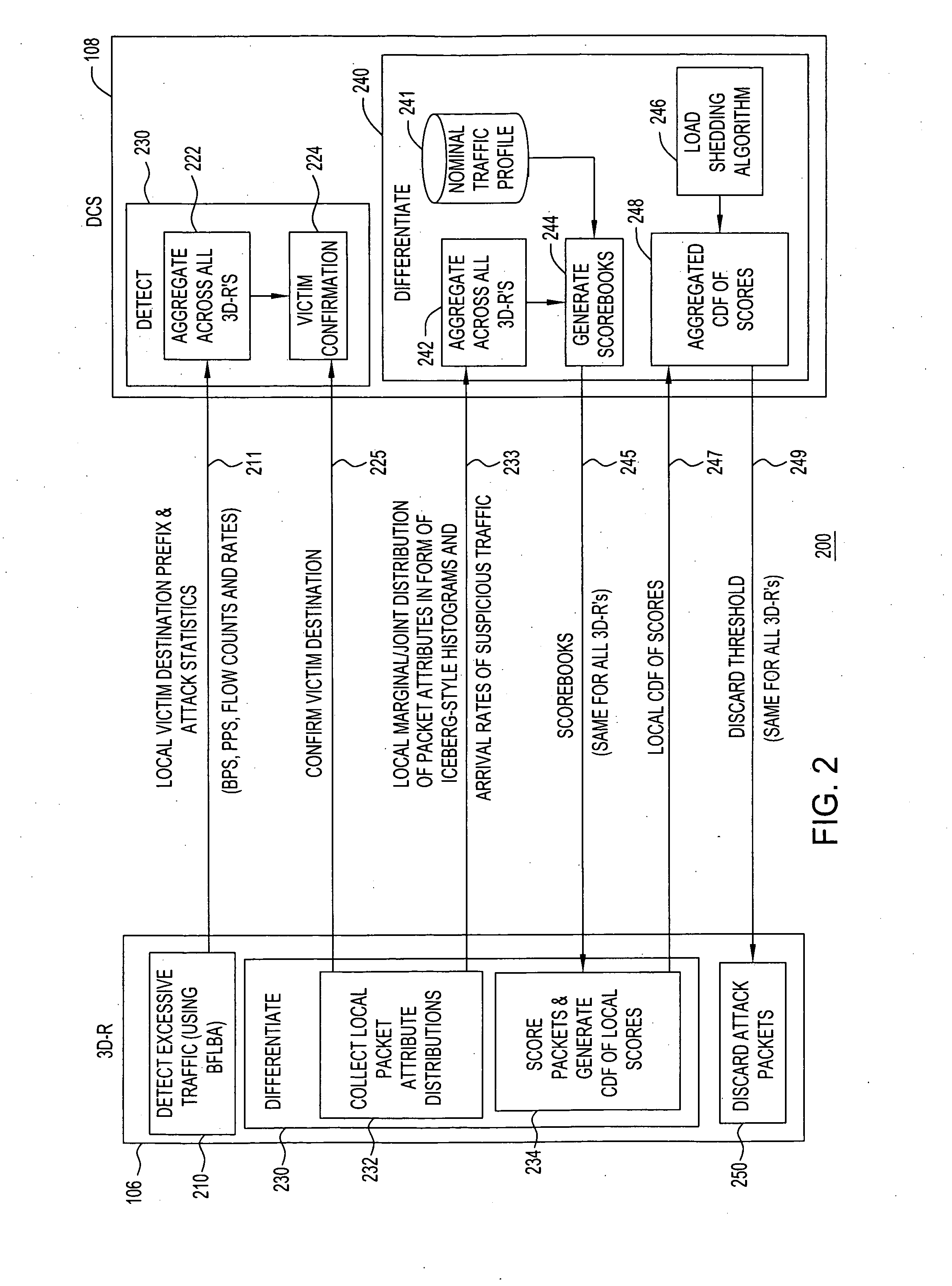
Distributed architecture for statistical overload control against distributed denial of service attacks
ActiveUS20050111367A1Overcome disadvantagesError preventionTransmission systemsOverload controlDistribution function
In a network including a centralized controller and a plurality of routers forming a security perimeter, a method for selectively discarding packets during a distributed denial-of-service (DDoS) attack over the network. The method includes aggregating victim destination prefix lists and attack statistics associated with incoming packets received from the plurality of routers to confirm a DDoS attack victim, and aggregating packet attribute distribution frequencies for incoming victim related packets received from the plurality of security perimeter routers. Common scorebooks are generated from the aggregated packet attribute distribution frequencies and nominal traffic profiles, and local cumulative distribution function (CDF) of the local scores derived from the plurality of security perimeter routers are aggregated. A common discarding threshold is derived from the CDF and sent to each of the plurality of security perimeter routers, where the discarding threshold defines a condition in which an incoming packet may be discarded at the security perimeter.
Owner:WSOU INVESTMENTS LLC
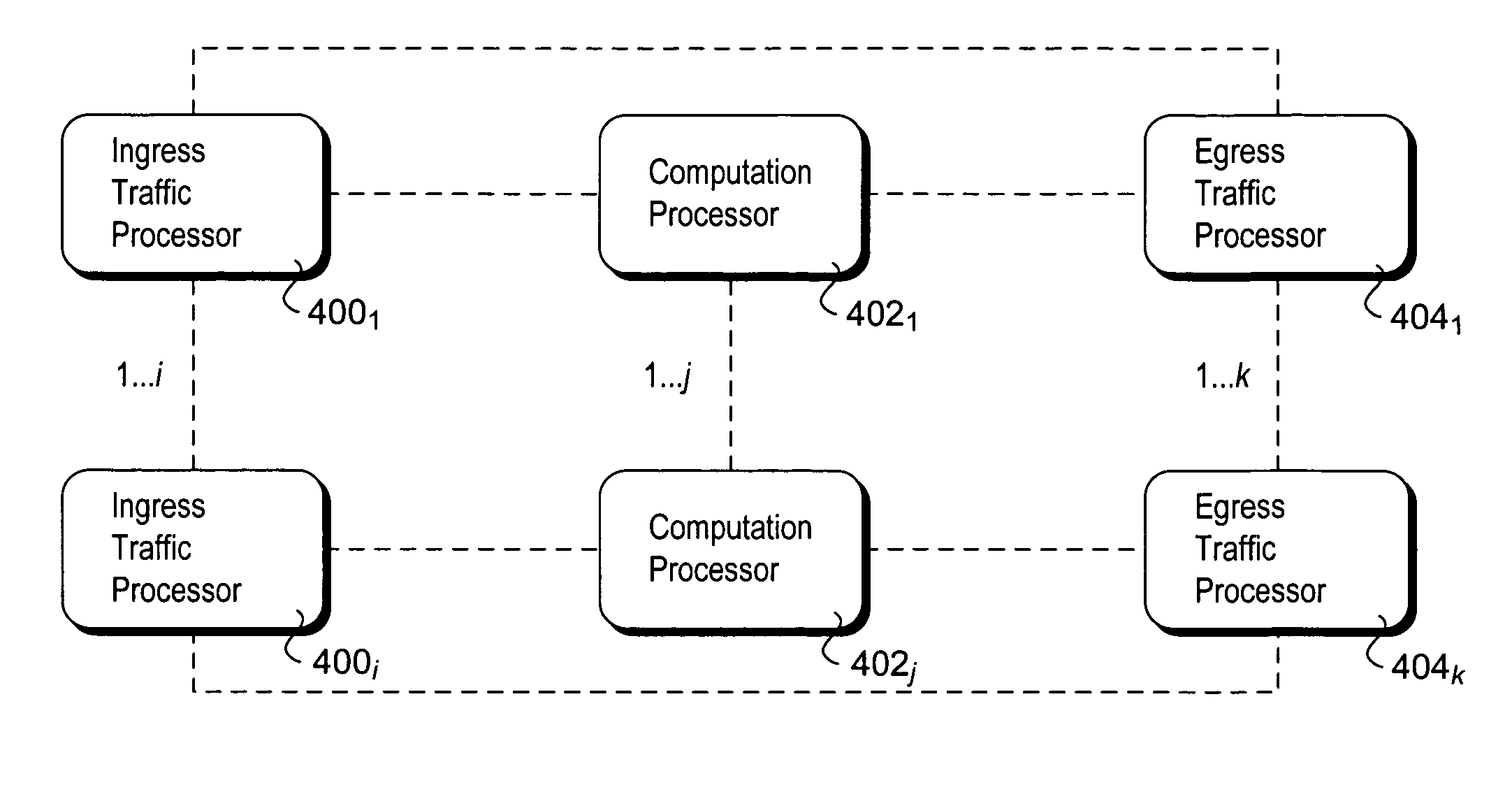
Packet flow bifurcation and analysis
ActiveUS20070058632A1Improve matchData switching by path configurationTraffic capacityProcessing element
Methods and apparatus for optimum matching of a traffic profile with an individual traffic flow using flow bifurcation and analysis. Bifurcation and duplication of packets that make up a flow received at an ingress element are forwarded to each of egress traffic and computation processor resources, such that egress traffic operations and traffic analysis operations may be performed concurrently without introducing jitter or delay in either bifurcated processing path. The traffic analysis includes maintaining flow statistics, flow stateful information and classifying the flow as a particular application traffic type. The optimum traffic profile for this application traffic type is then selected and applied to the individual flow. The traffic analysis data is forwarded to ingress and egress processing elements in real time, and ingress and egress traffic processing operations are dynamically adjusted in view of the traffic analysis data.
Owner:TELLABS COMM CANADA
Reconfigurable noc for customizing traffic and optimizing performance after noc synthesis
Systems and methods described herein are directed to solutions for Network on Chip (NoC) interconnects that supports reconfigurability to support a variety of different traffic profiles each having different sets of traffic flows after the NoC is designed and deployed in a SoC. Reconfiguration of the NoC to map and load a new traffic profile or change the currently mapped traffic profile is performed by an external optimization module which maps various transactions of a given traffic profile to the NoC and reconfigure the NoC hardware by loading the computed mapping information. As part of the mapping process, load balancing between NoC layers may be performed by automatically assigning the transactions in the traffic profile to be routed over certain NoC layers and channels, automatically determining the routes based on the bandwidth requirements of the transaction. The deadlock avoidance and isolation properties of various transactions are maintained during the mapping.
Owner:INTEL CORP
Intrusion detection in communication networks
ActiveUS20120278890A1Increase the number ofSolve the high false alarm rateMemory loss protectionError detection/correctionNetwork activityInternet traffic
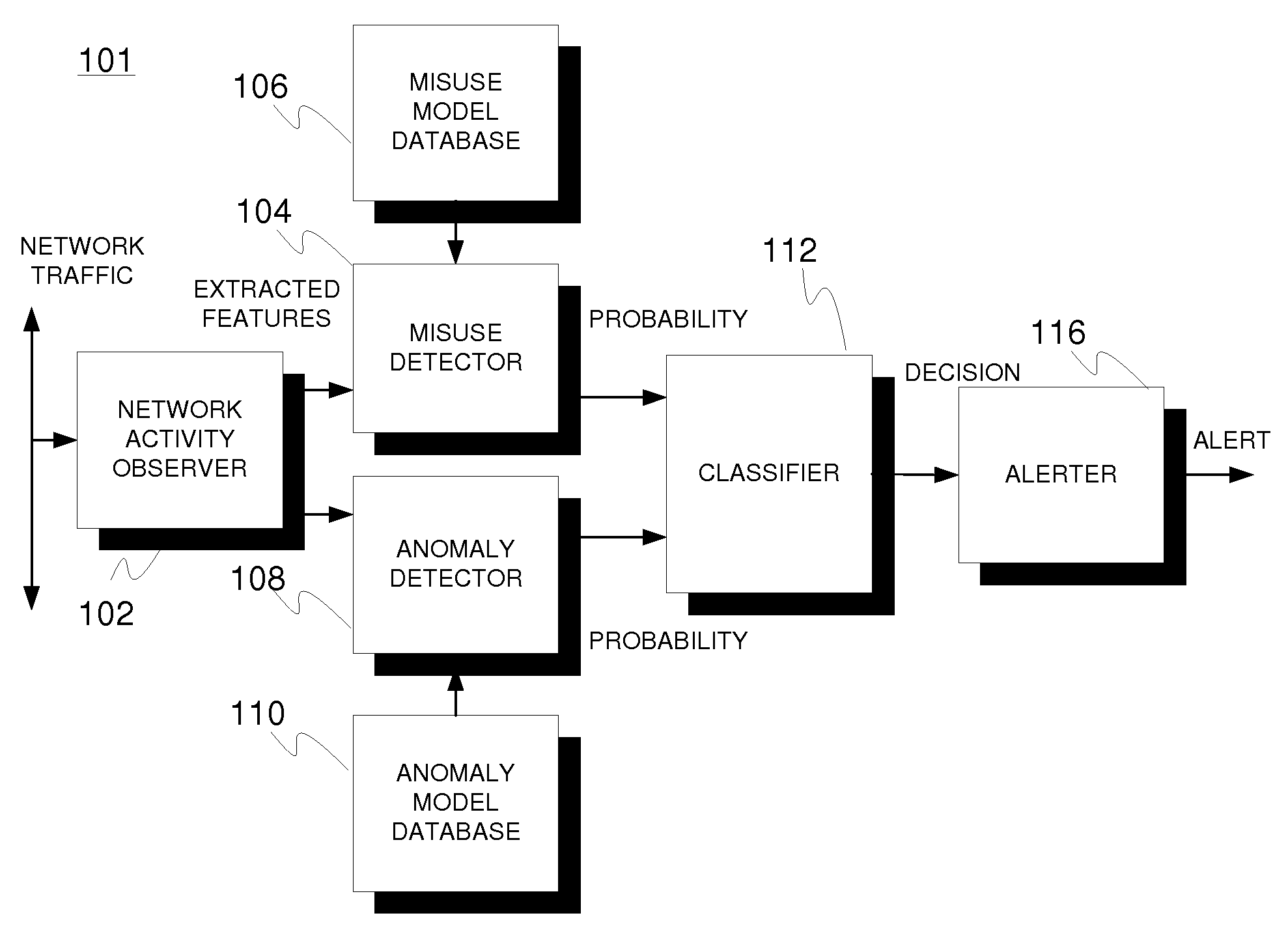
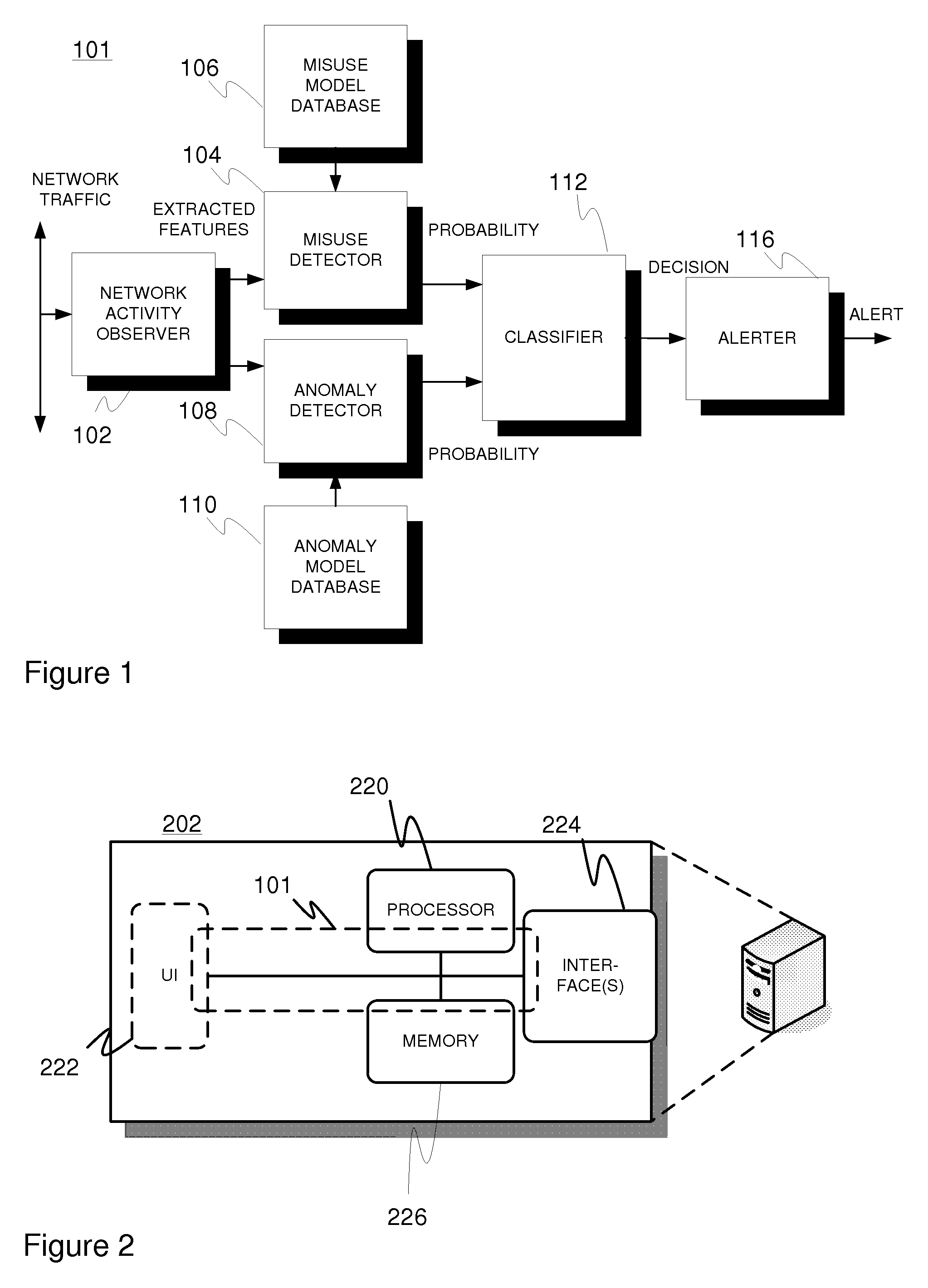
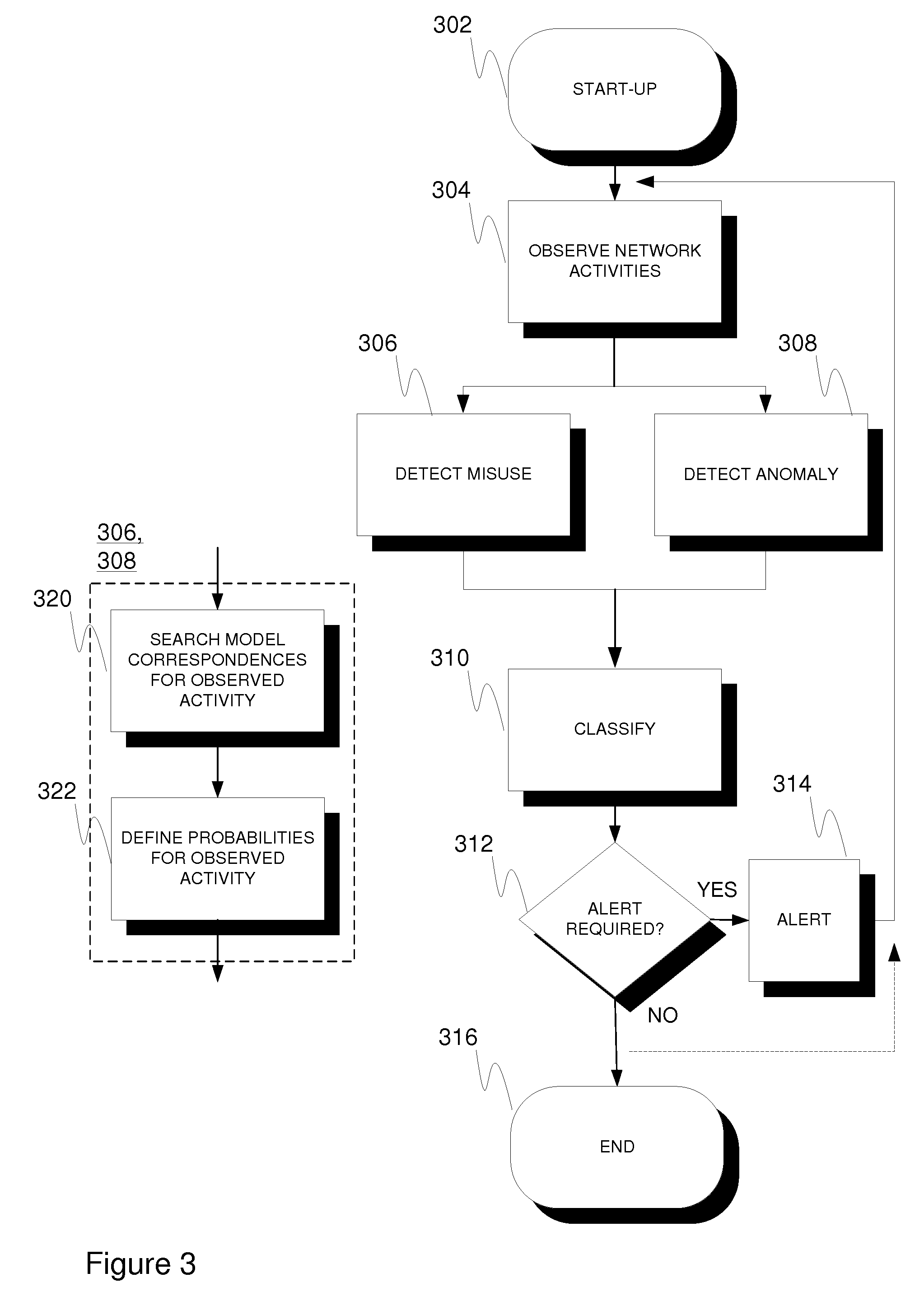
An intrusion detection arrangement (101) for communication networks comprising a network activity observer (102) configured to monitor network traffic by the related traffic elements, such as data packets, thereof and to establish traffic profiles relative to the monitored traffic elements, such as one profile per each monitored traffic element, a misuse detector (104) configured to determine a first indication of a probability of the profiled traffic representing malicious activity through co-operation with a model repository (106) comprising at least one model characterizing a known intrusion attack, an anomaly detector (108) configured to determine, at least logically in parallel with the misuse detector, a second indication of a probability of the profiled traffic representing anomalous activity through cooperation with a model repository (110) comprising at least one model characterizing legitimate network activity, and a classifier (112) configured to operate on said first and second indications to generate a classification decision on the nature of the profiled traffic, wherein the applied classification space includes at least one class for legitimate traffic and at least one other class for other traffic such as malicious and / or anomalous traffic. A corresponding method is presented.
Owner:BIN 2022 SERIES 822 OF ALLIED SECURITY TRUST I
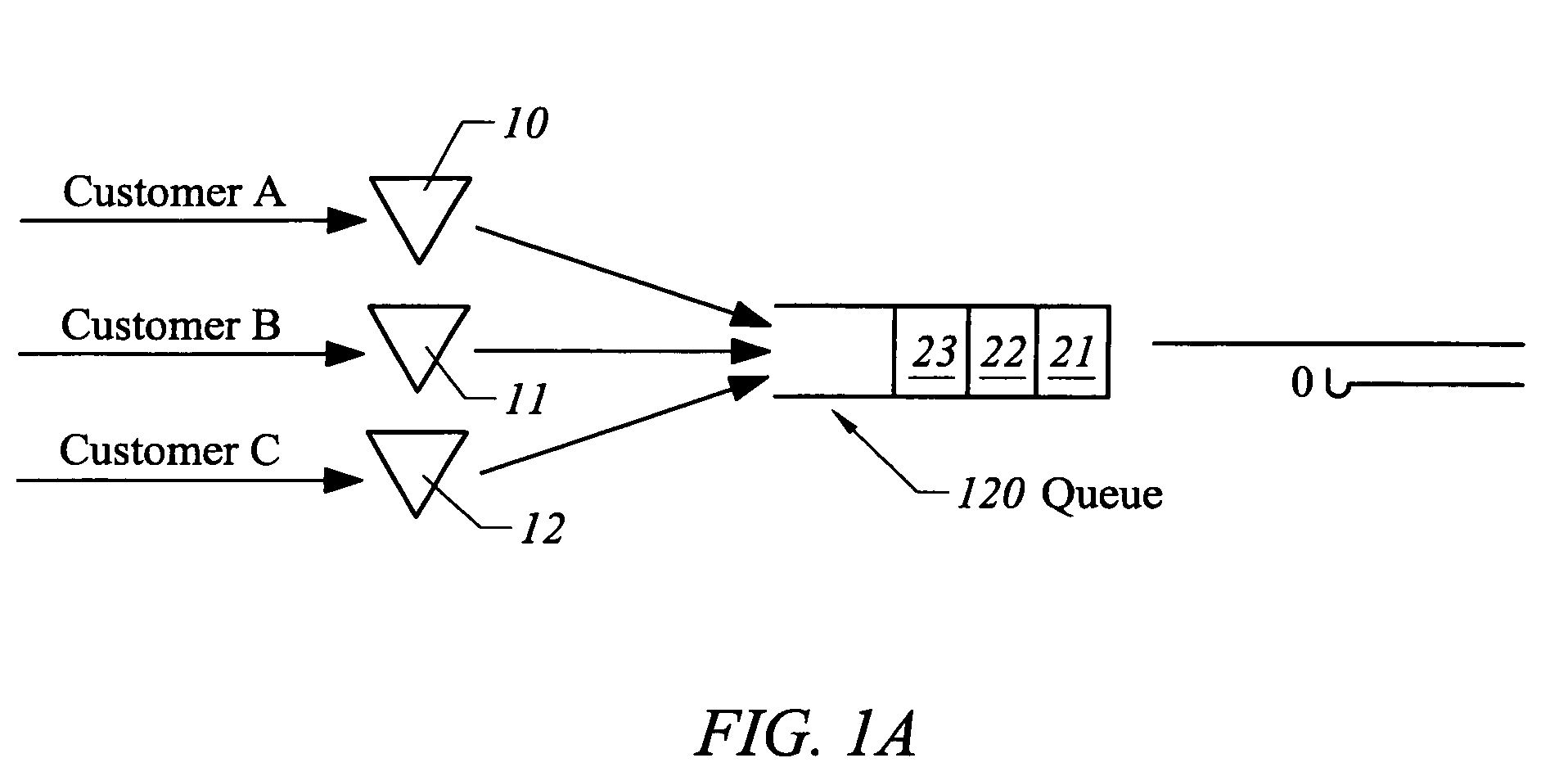
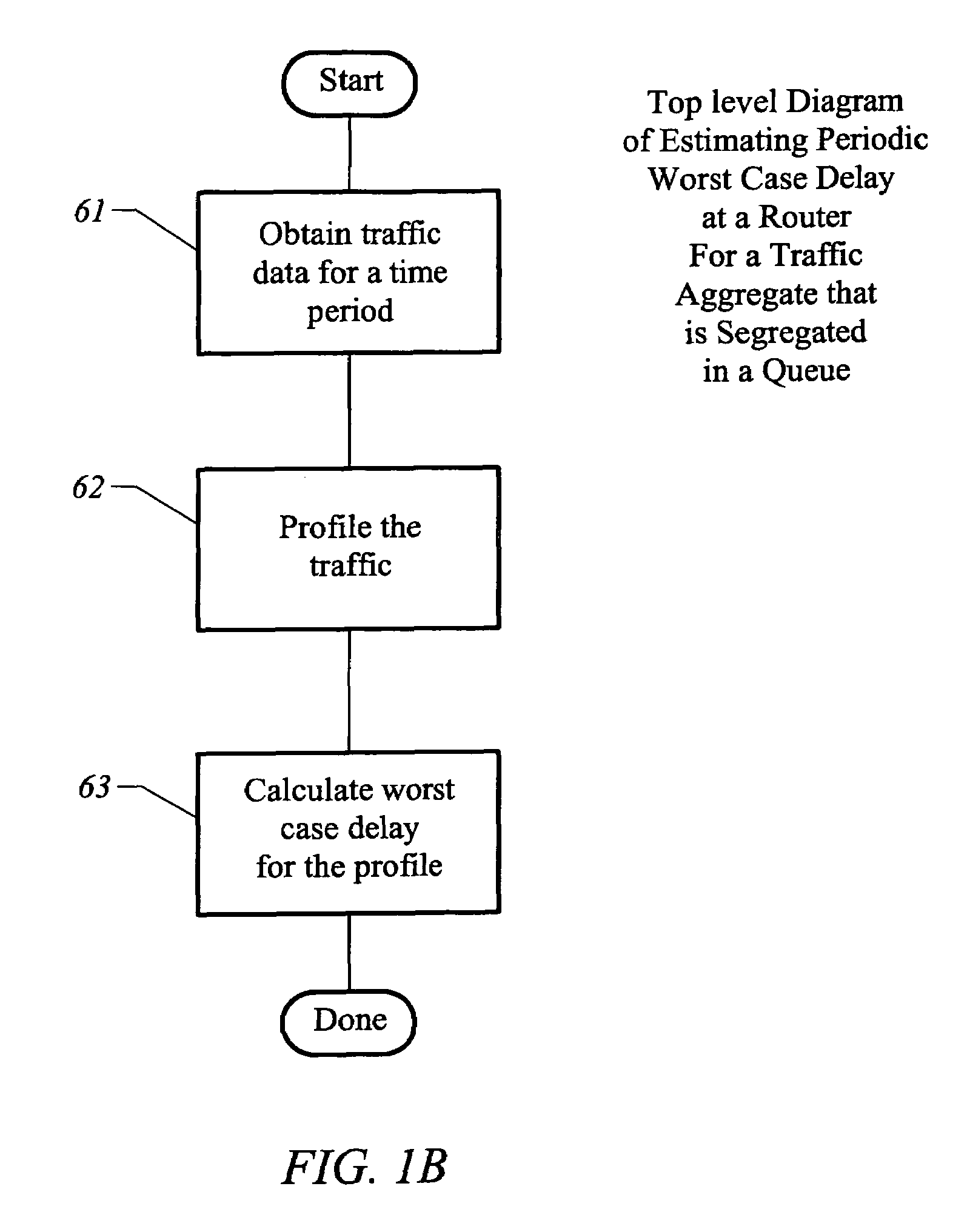
Method and apparatus for estimating periodic worst-case delay under actual and hypothetical conditions using a measurement based traffic profile
Methods and apparatuses for estimating periodic worst-case delay for a class of traffic. An aggregate (i.e., a class or label on which traffic is classified and queued) has an associated bandwidth (“negotiated rate”), which typically is a maximum average bandwidth that has been agreed upon by the traffic generator (“customer”) and service provider. Delay for an aggregate is obtained by summing all the delays of class queues of each router in the path. Traffic data for the aggregate is collected. A burst-rate profile is calculated for the traffic data, with the rate parameter set to the value of the negotiated rate. A periodic worst-case delay estimate associated with the burst-rate profile is calculated, using the output link capacity allotted to the aggregate (“allocated bandwidth”) as input.
Owner:CISCO TECH INC
Packet flow bifurcation and analysis
ActiveUS7508764B2Improve matchError preventionTransmission systemsTraffic capacityProcessing element
Methods and apparatus for optimum matching of a traffic profile with an individual traffic flow using flow bifurcation and analysis. Bifurcation and duplication of packets that make up a flow received at an ingress element are forwarded to each of egress traffic and computation processor resources, such that egress traffic operations and traffic analysis operations may be performed concurrently without introducing jitter or delay in either bifurcated processing path. The traffic analysis includes maintaining flow statistics, flow stateful information and classifying the flow as a particular application traffic type. The optimum traffic profile for this application traffic type is then selected and applied to the individual flow. The traffic analysis data is forwarded to ingress and egress processing elements in real time, and ingress and egress traffic processing operations are dynamically adjusted in view of the traffic analysis data.
Owner:TELLABS COMM CANADA
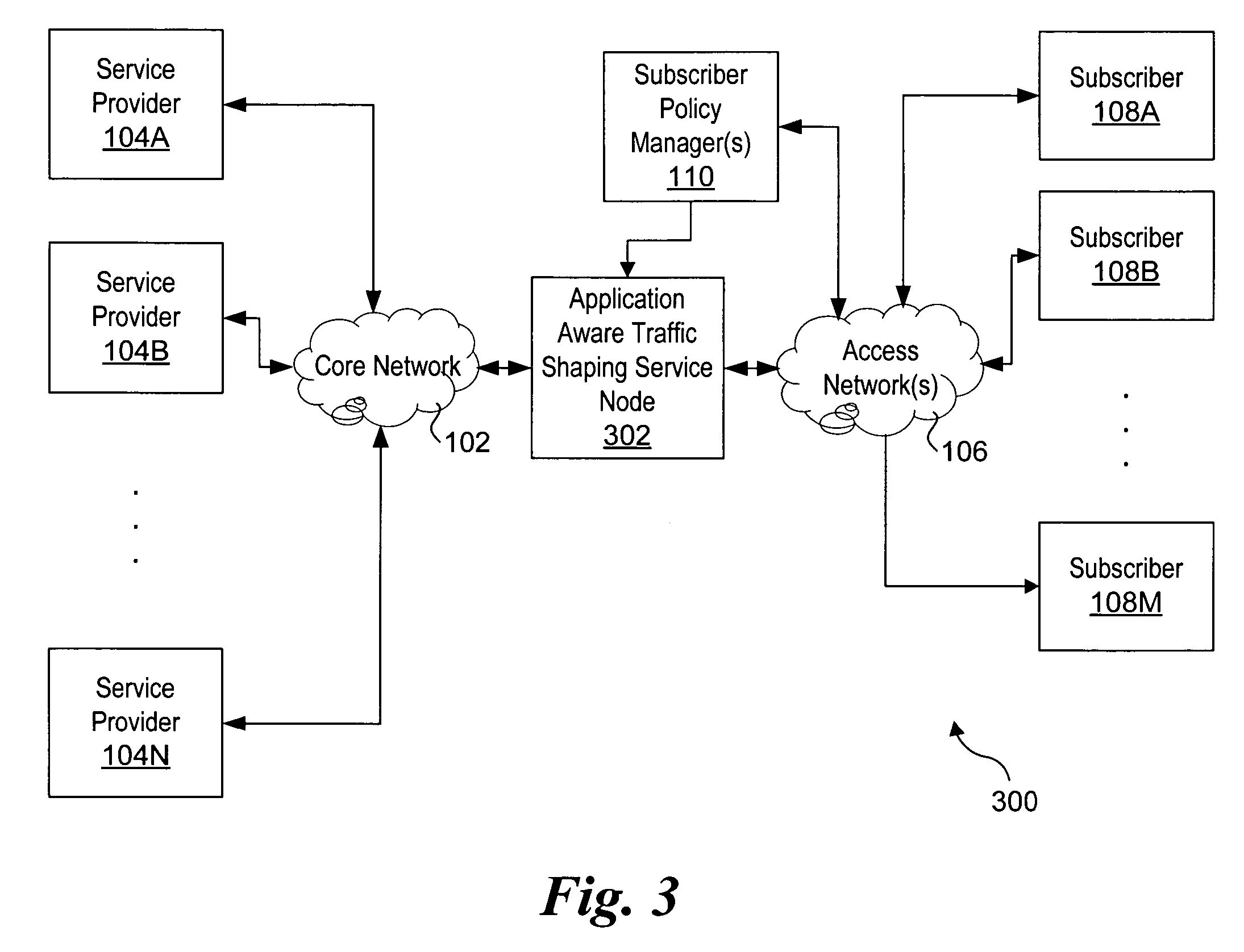
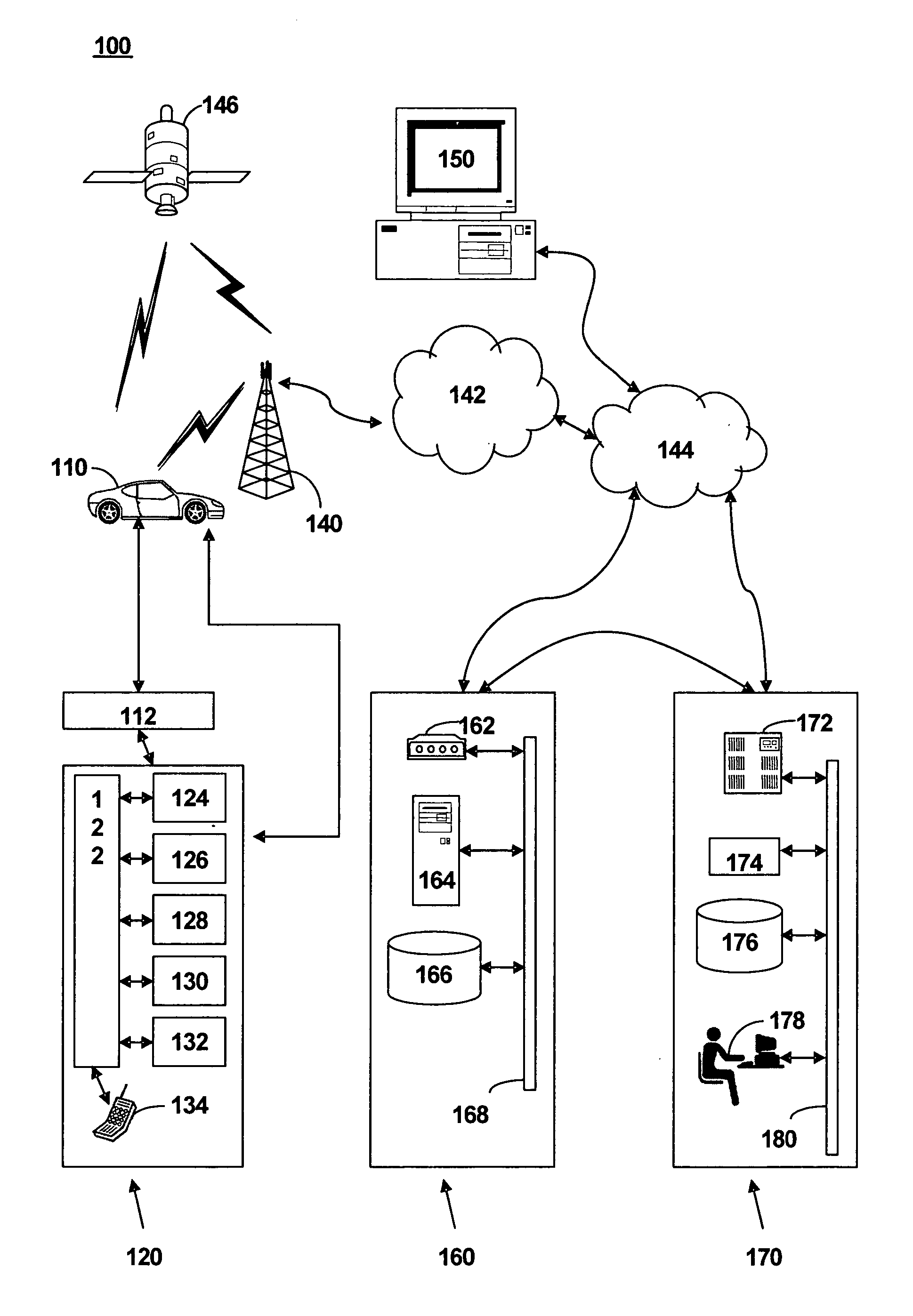
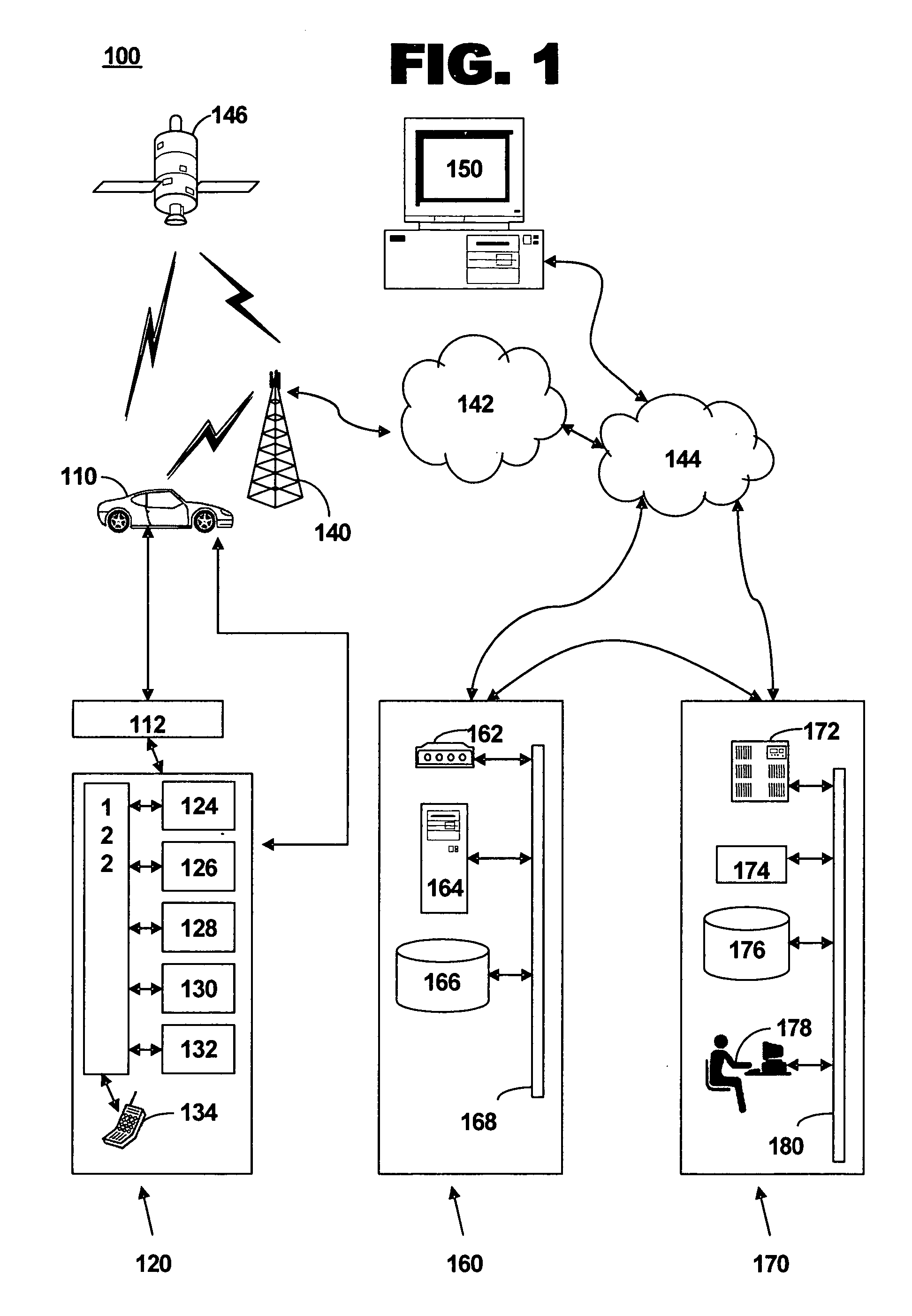
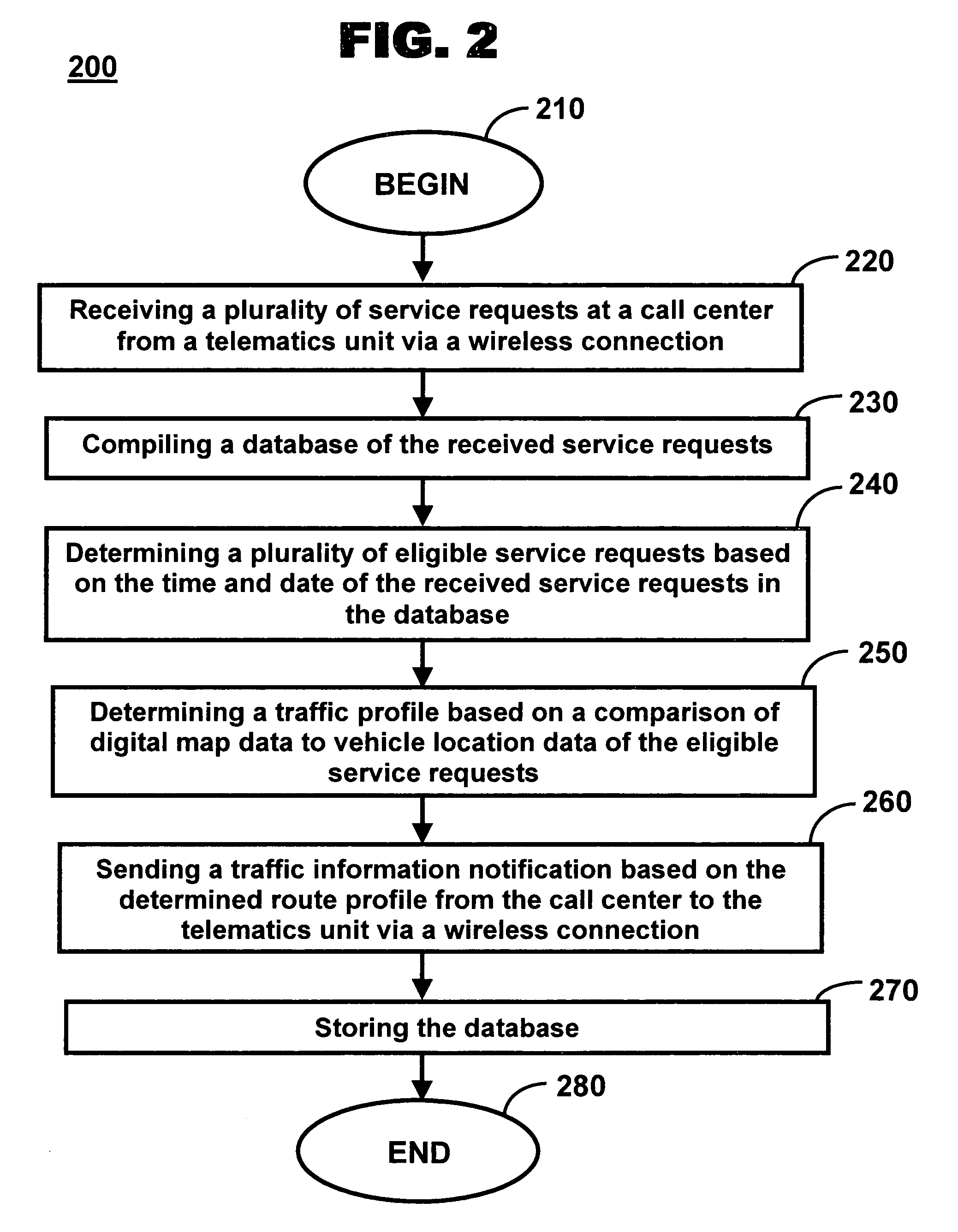
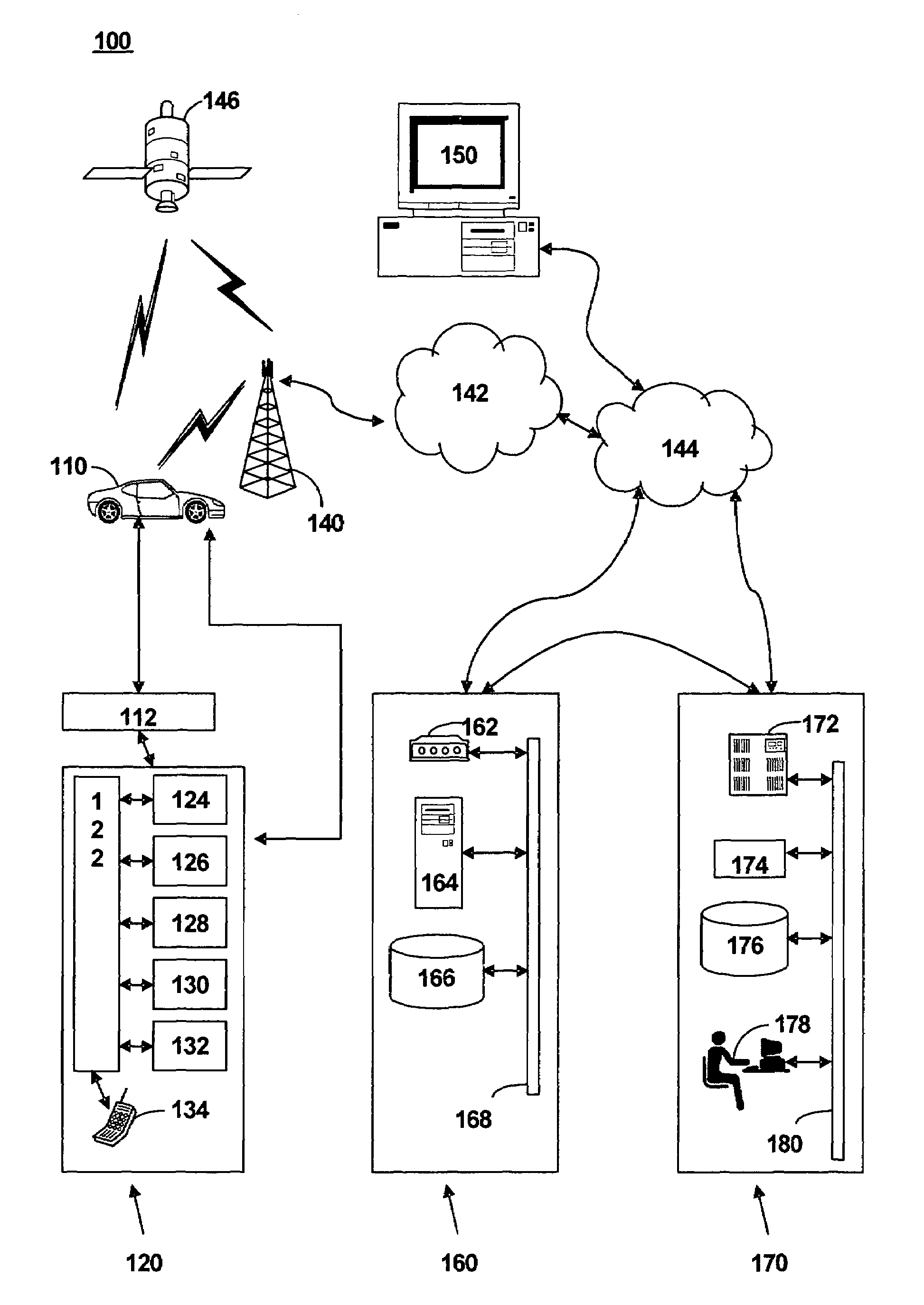
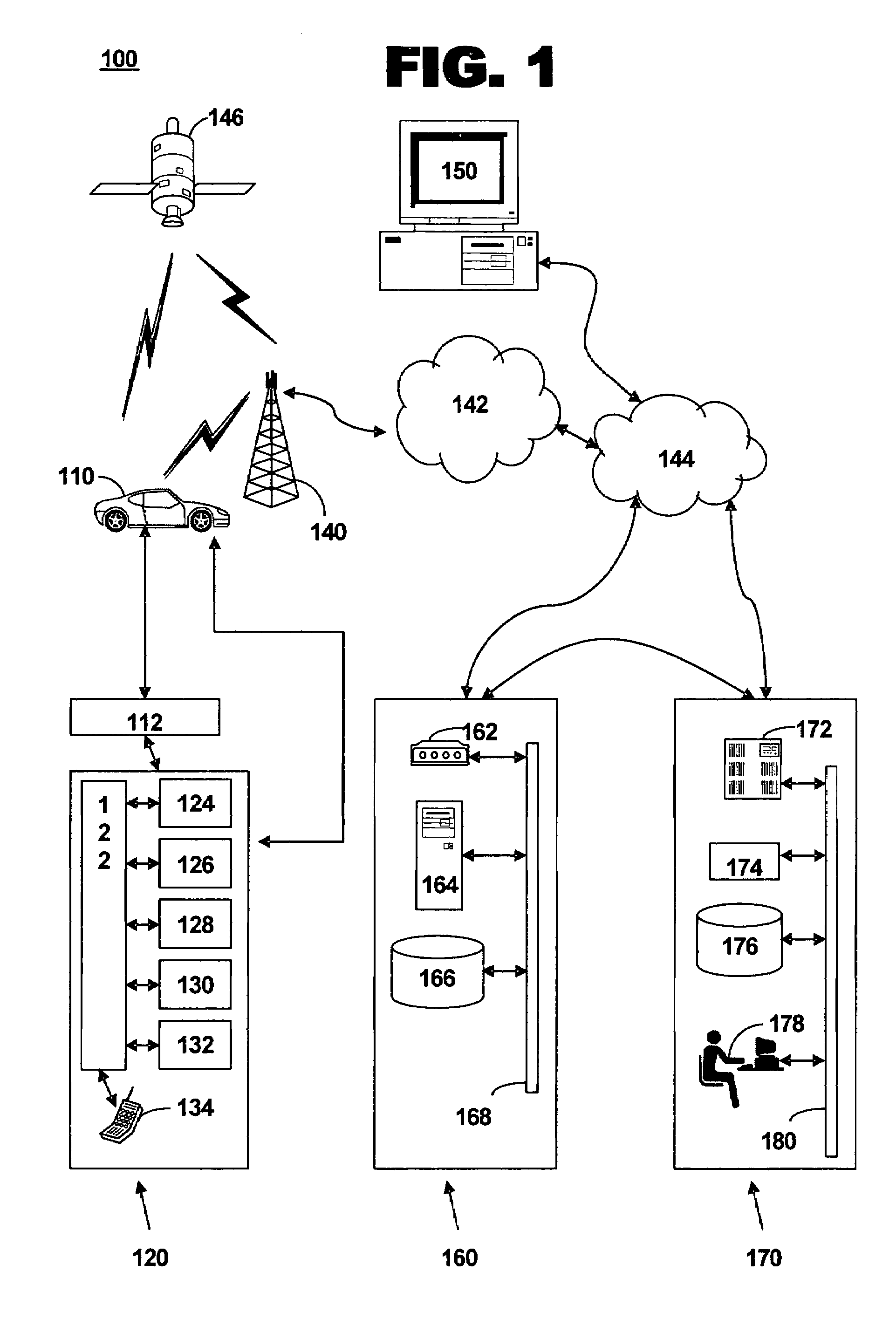
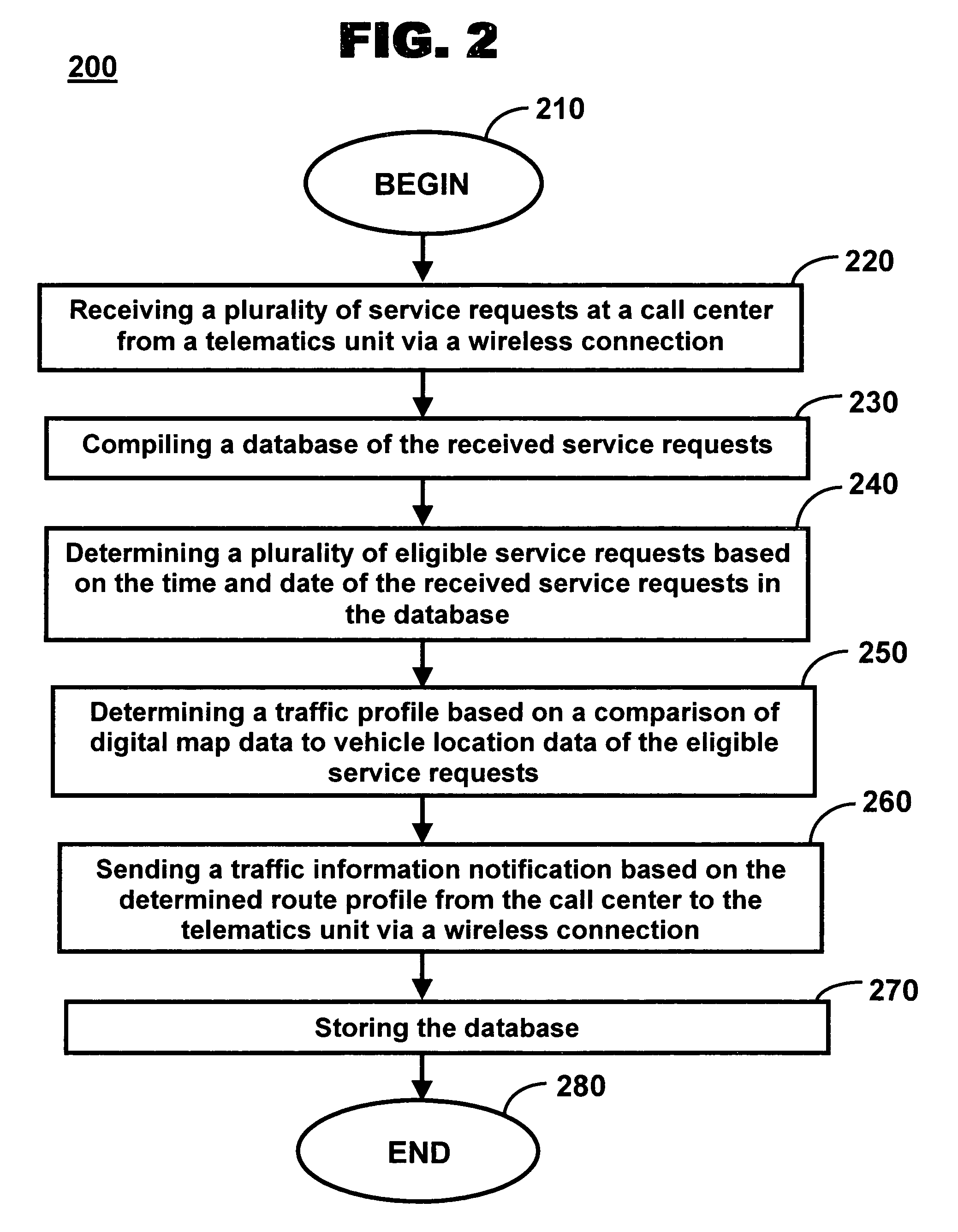
Method and system for determining traffic information traffic profiles
ActiveUS20060291633A1Controlling traffic signalsAnalogue computers for vehiclesMobile vehicleInformation processing
A method of determining traffic information for a mobile vehicle includes receiving a plurality of service requests at a call center from a telematics unit via a wireless connection. The service request includes time, date, and vehicle location data. A database of the received service requests is compiled. A plurality of eligible service requests is determined based on the time and date of the received service requests in the database. A traffic profile is determined based on a comparison of digital map data to vehicle location data of the eligible service requests.
Owner:GENERA MOTORS LLC
System and method for determining traffic conditions
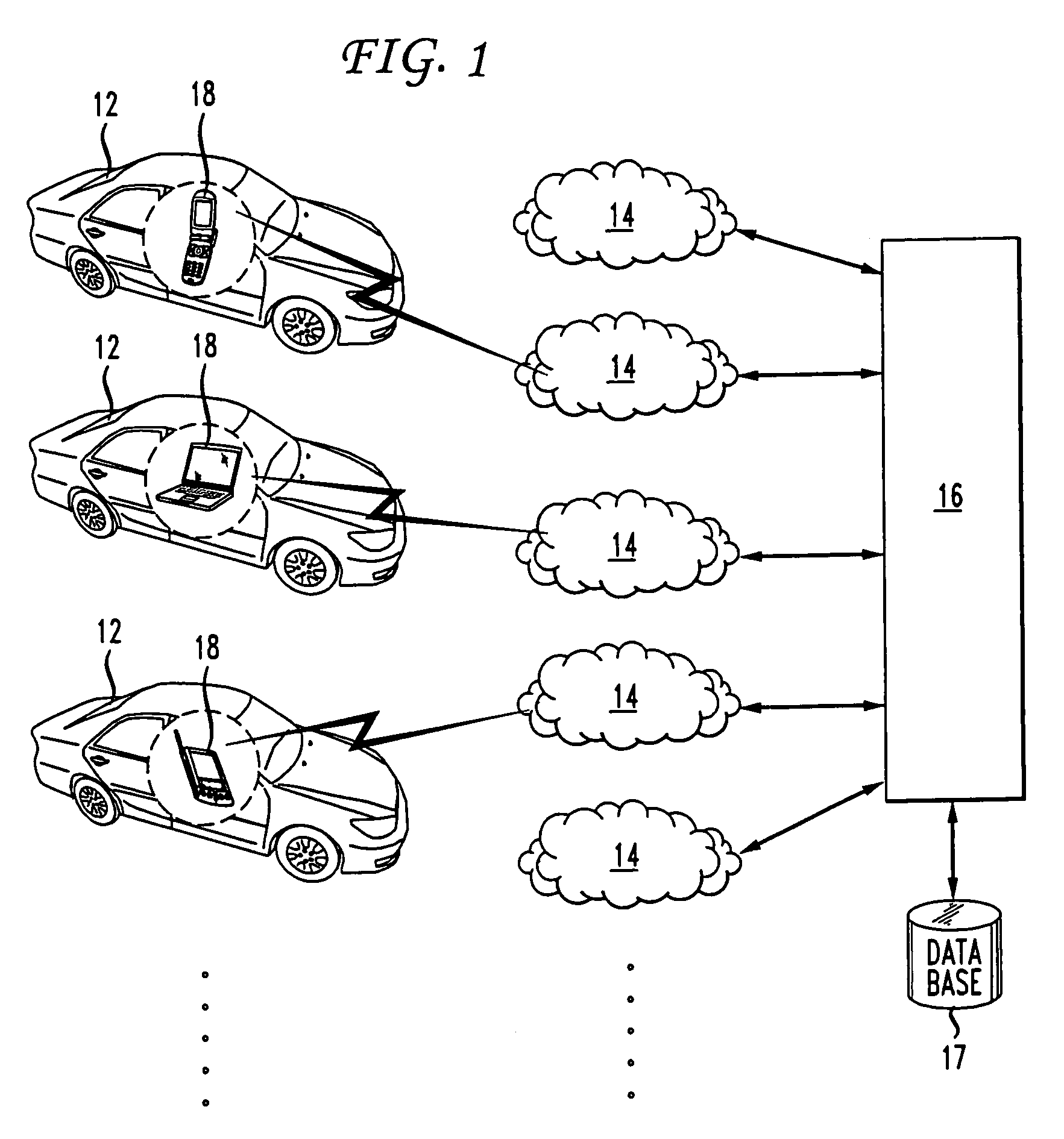
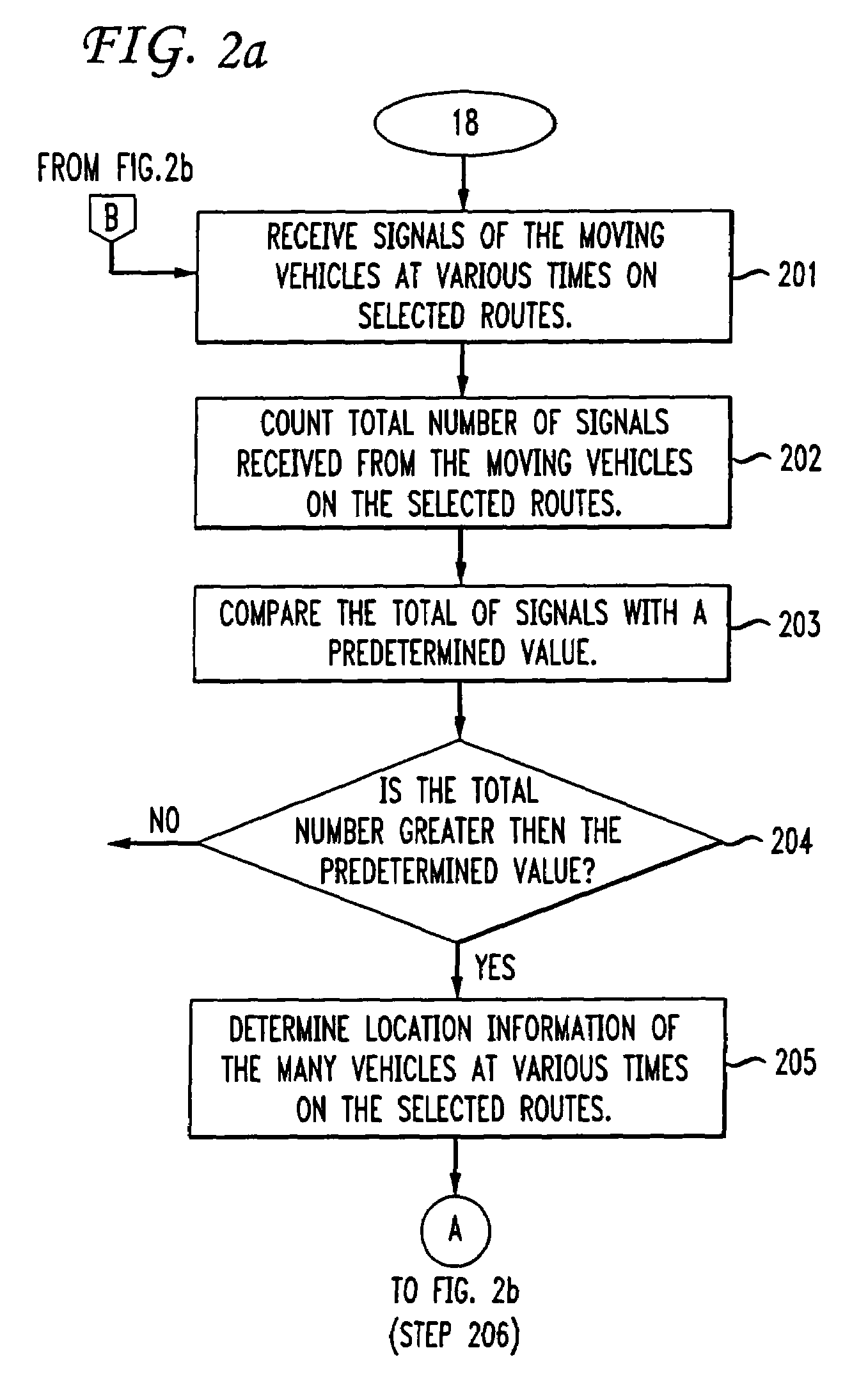
ActiveUS7228224B1Analogue computers for vehiclesInstruments for road network navigationMobile vehicleEngineering
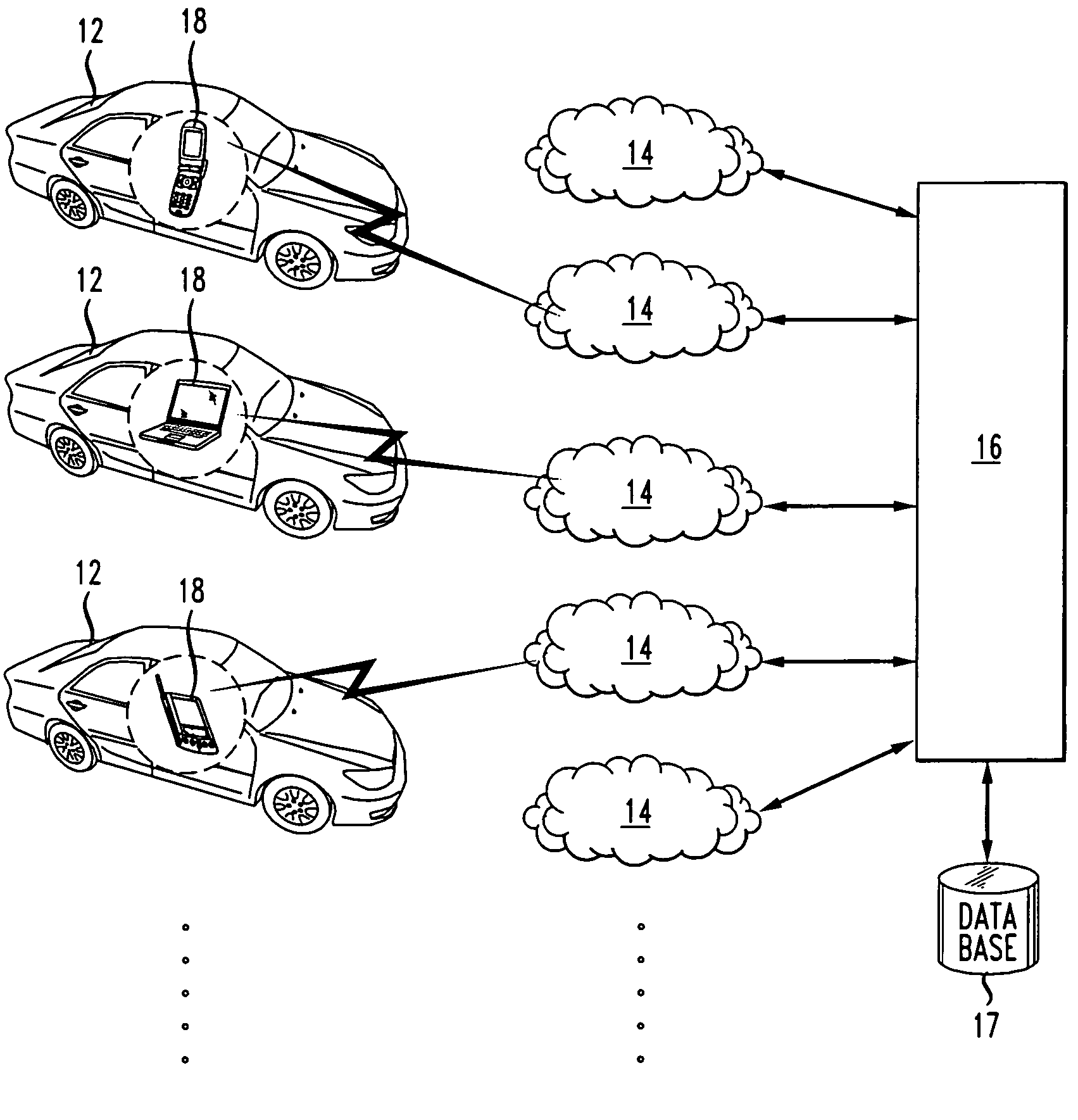
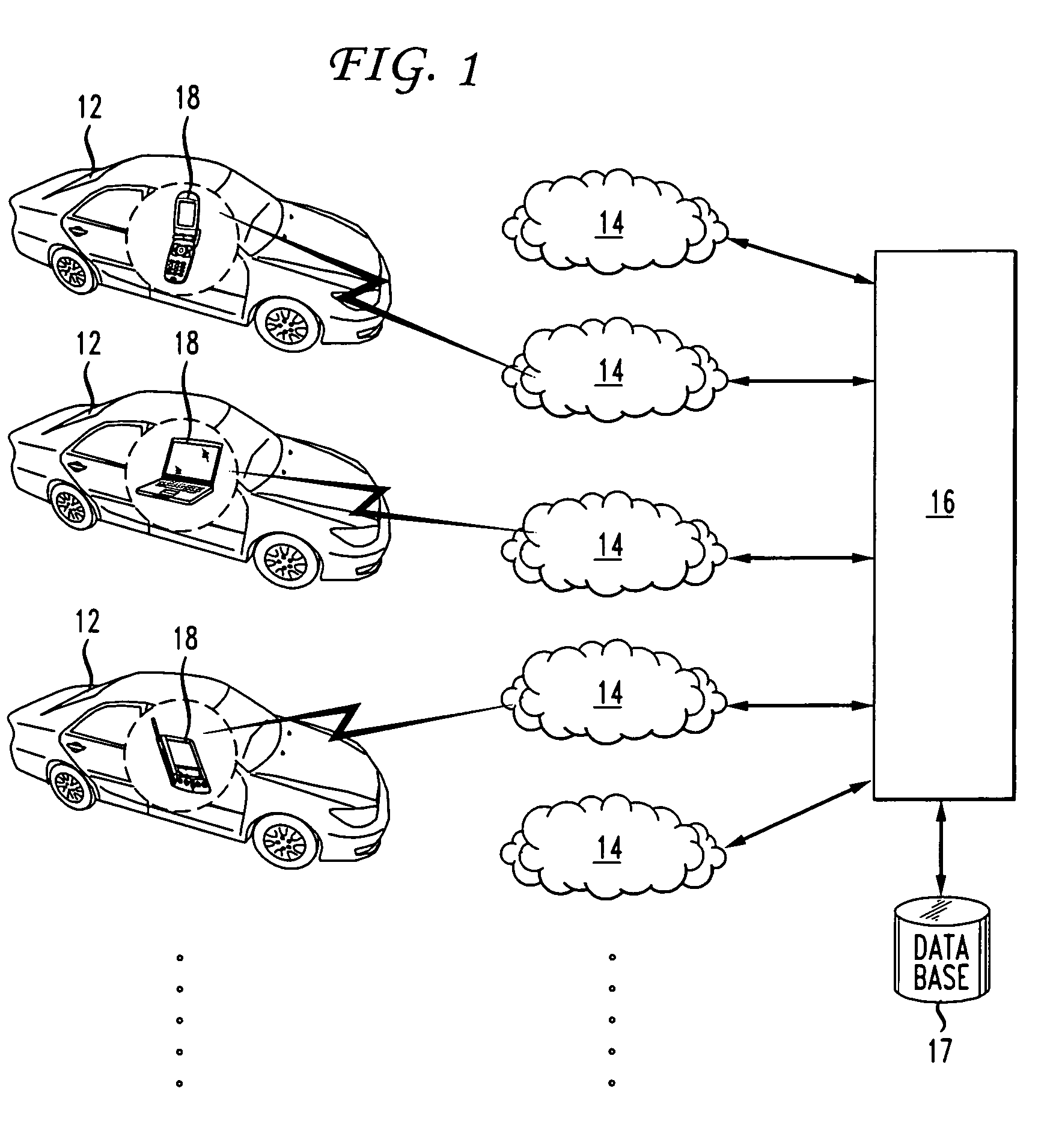
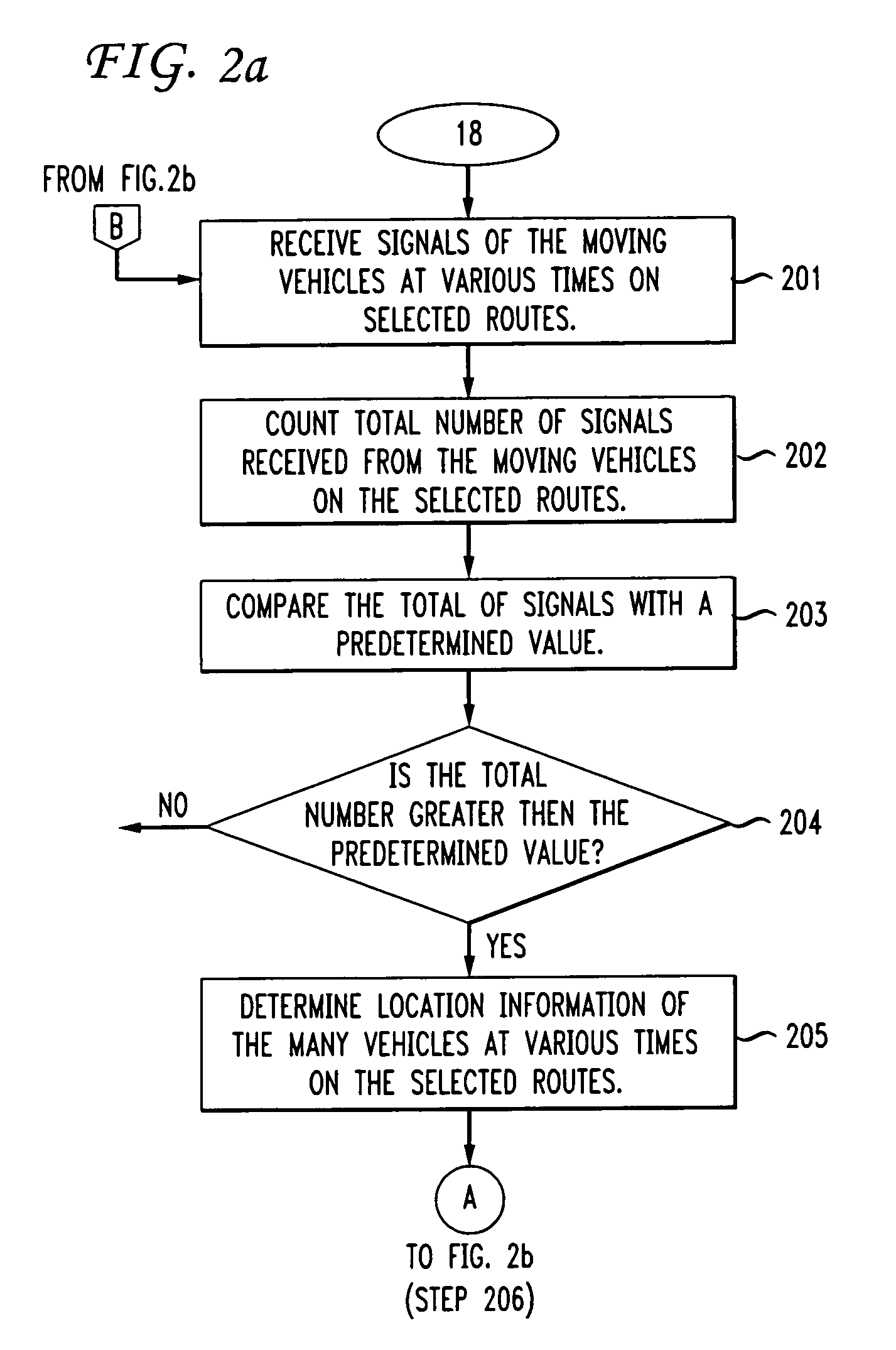
The present invention provides a method and apparatus for determining traffic conditions using wireless devices. A number of signals from the vehicles traveling in selected routes are received by several wireless communication networks via the wireless devices. The total number of signals received are used to compare if there are sufficient number of vehicles traveling on the selected routes. If so, then the location information of the moving vehicles at various times is determined by the wireless communication network and forwarded to a central computer. The central computer coordinates with the wireless communications network for information needed to compute traffic data. The central computer computes the velocity of the moving vehicles and a traffic profile is created based on the velocity and location information of the moving vehicles. Furthermore, the traffic profile is sent to the moving vehicles.
Owner:AMERICAN TELEPHONE & TELEGRAPH CO
Measurement-Based Validation of a Simple Model for Panoramic Profiling of Subnet-Level Network Data Traffic
A system and method for profiling subnet-level aggregate network data traffic is disclosed. The system allows a user to define a collection of features that combined characterize the subnet-level aggregate traffic behavior. Preferably, the features include daily traffic volume, time-of-day behavior, spatial traffic distribution, traffic balance in flow direction, and traffic distribution in type of application. The system then applies machine learning techniques to classify the subnets into a number of clusters on each of the features, by assigning a membership probability vector to each network thus allowing panoramic traffic profiles to be created for each network on all features combined. These membership probability vectors may optionally be used to detect network anomalies, or to predict future network traffic.
Owner:AT&T INTPROP I L P
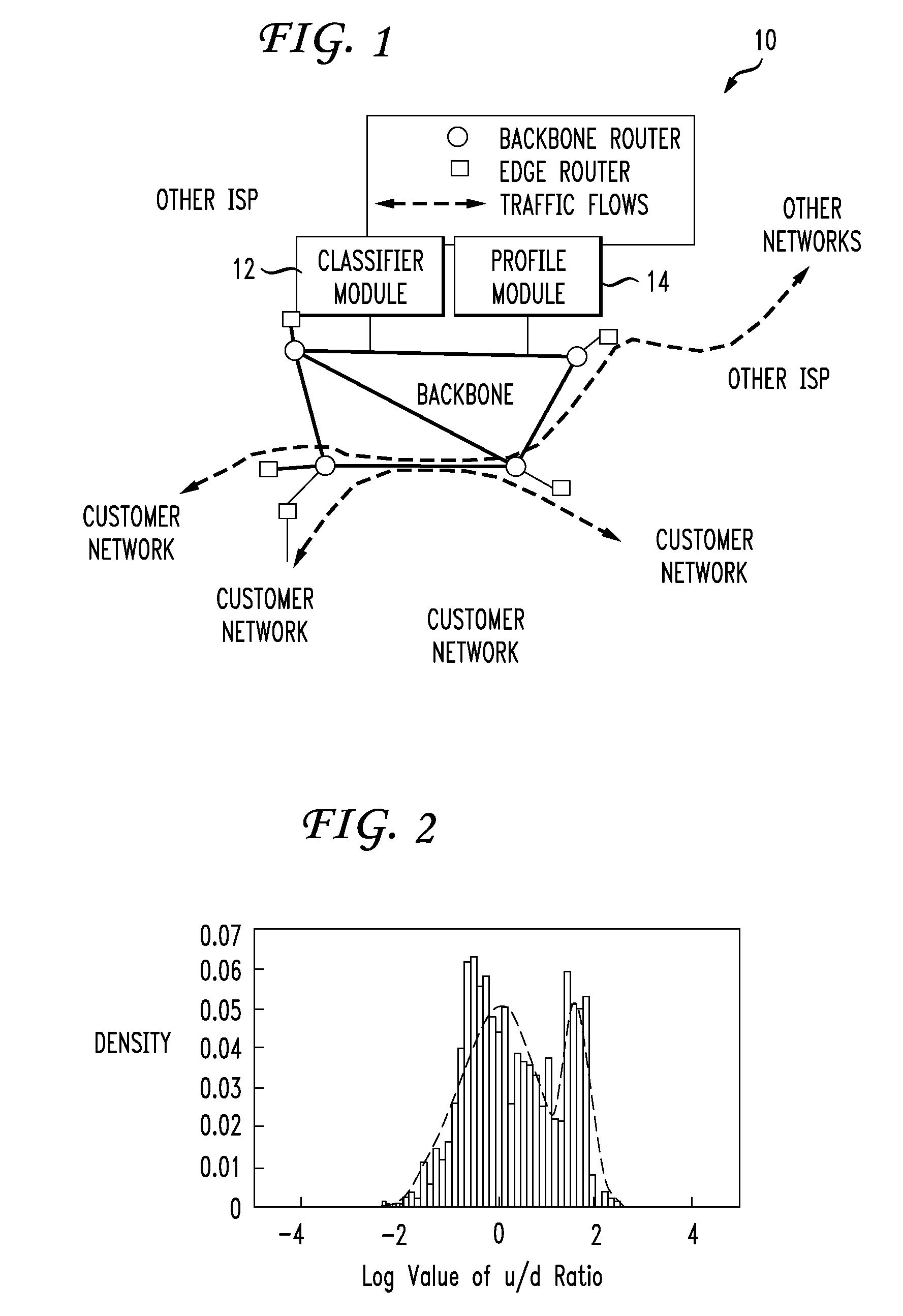
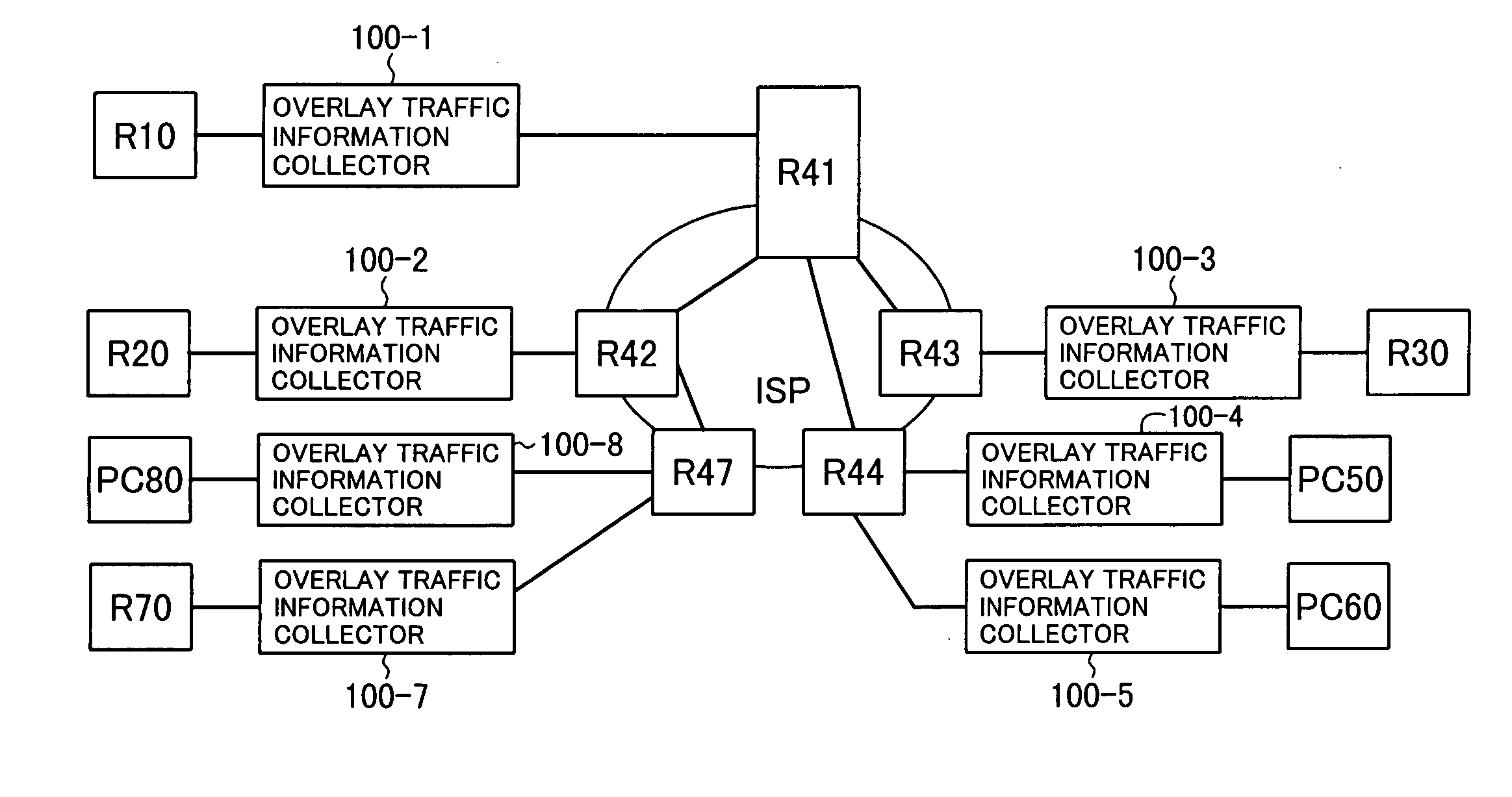
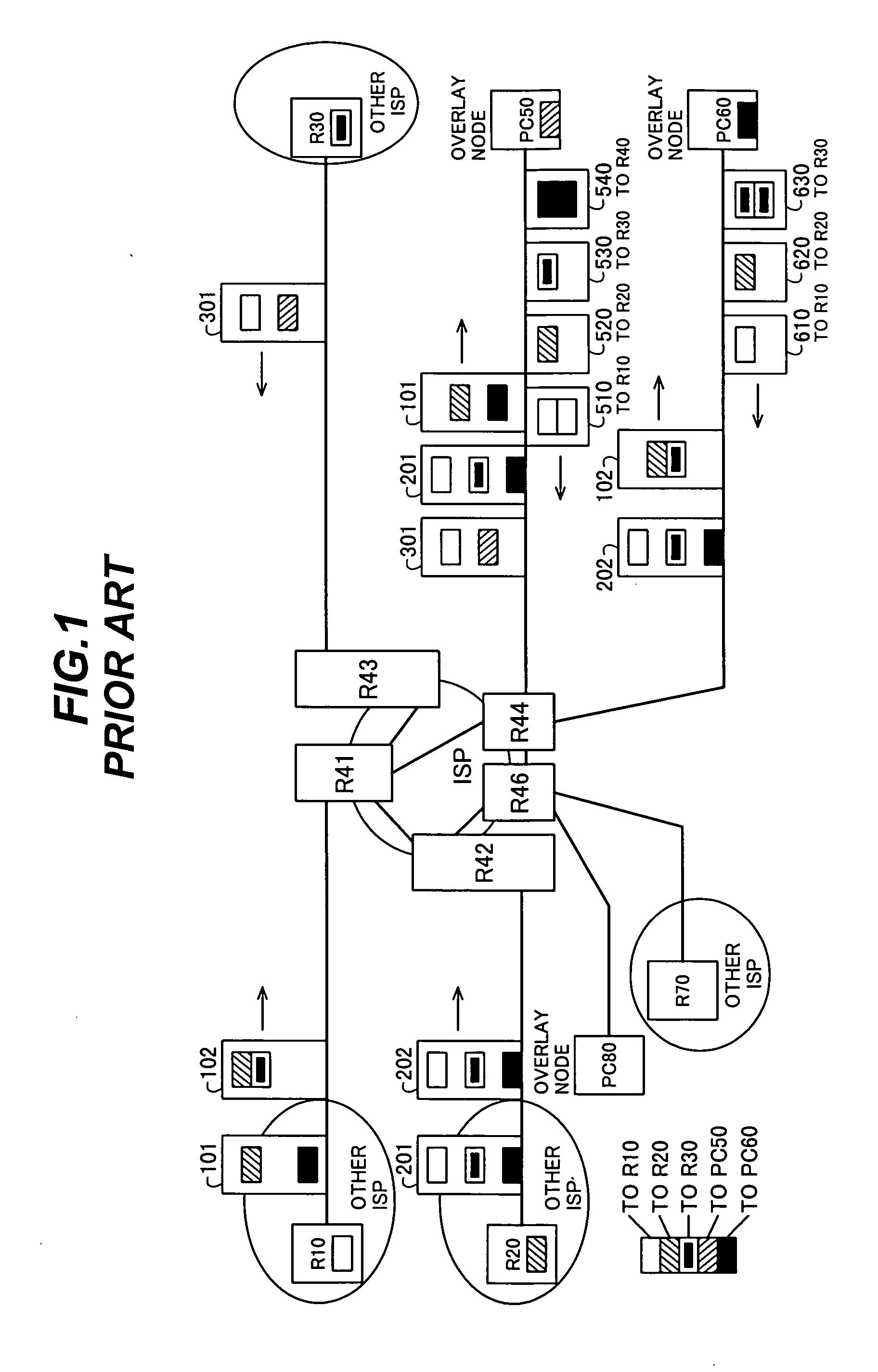
Overlay network traffic detection, monitoring, and control
InactiveUS20100185760A1Observed effectMultiple digital computer combinationsData switching networksTraffic capacityMultiple point
An overlay network traffic detection system deploys traffic measurement units at multiple points on a network, creates profiles of the network traffic measured at each point, and then compiles the traffic profiles obtained at different points. The compiled profile of outbound traffic originating at a node is compared with the compiled profile of inbound traffic addressed to the same node. A strong correlation between the two profiles indicates that the node is relaying overlay network traffic. Further information can be gained by profile screening, by active interference in the traffic flow, by launching known information into the network at known times and observing its effect on the traffic profiles, and by observing keyword distributions in non-encrypted traffic.
Owner:OKI ELECTRIC IND CO LTD
Method and system for determining traffic information traffic profiles
Owner:GENERA MOTORS LLC
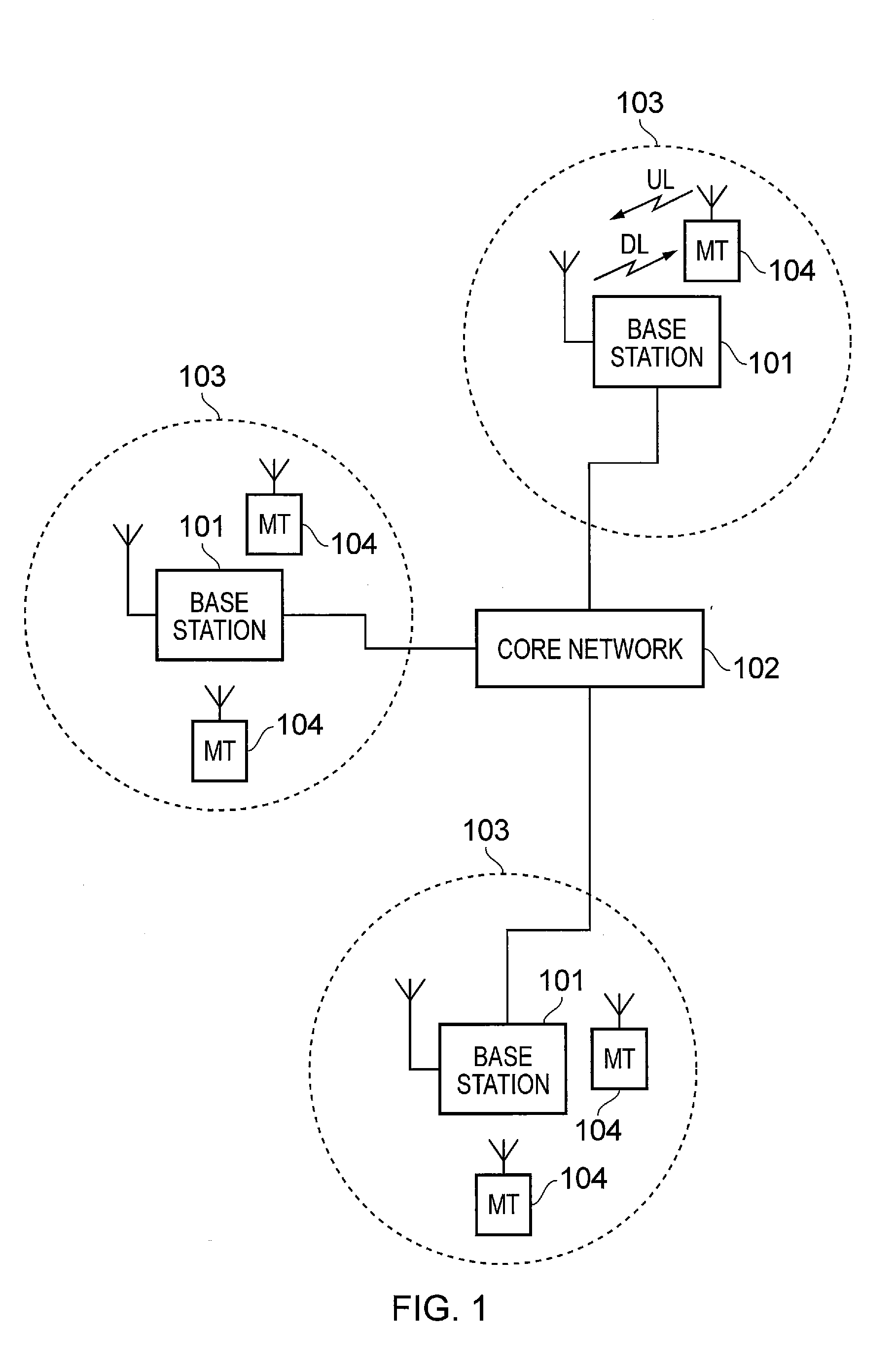
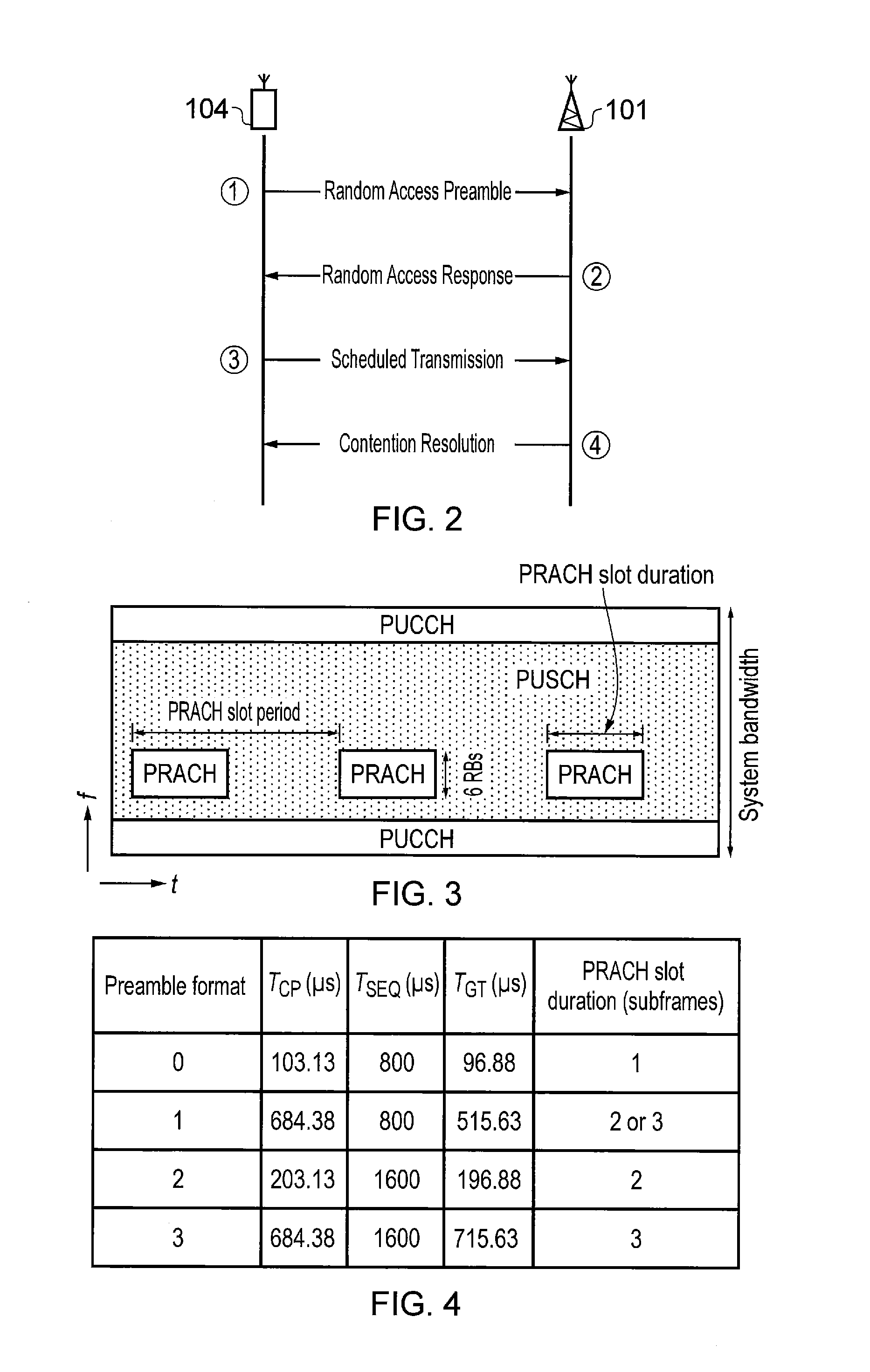
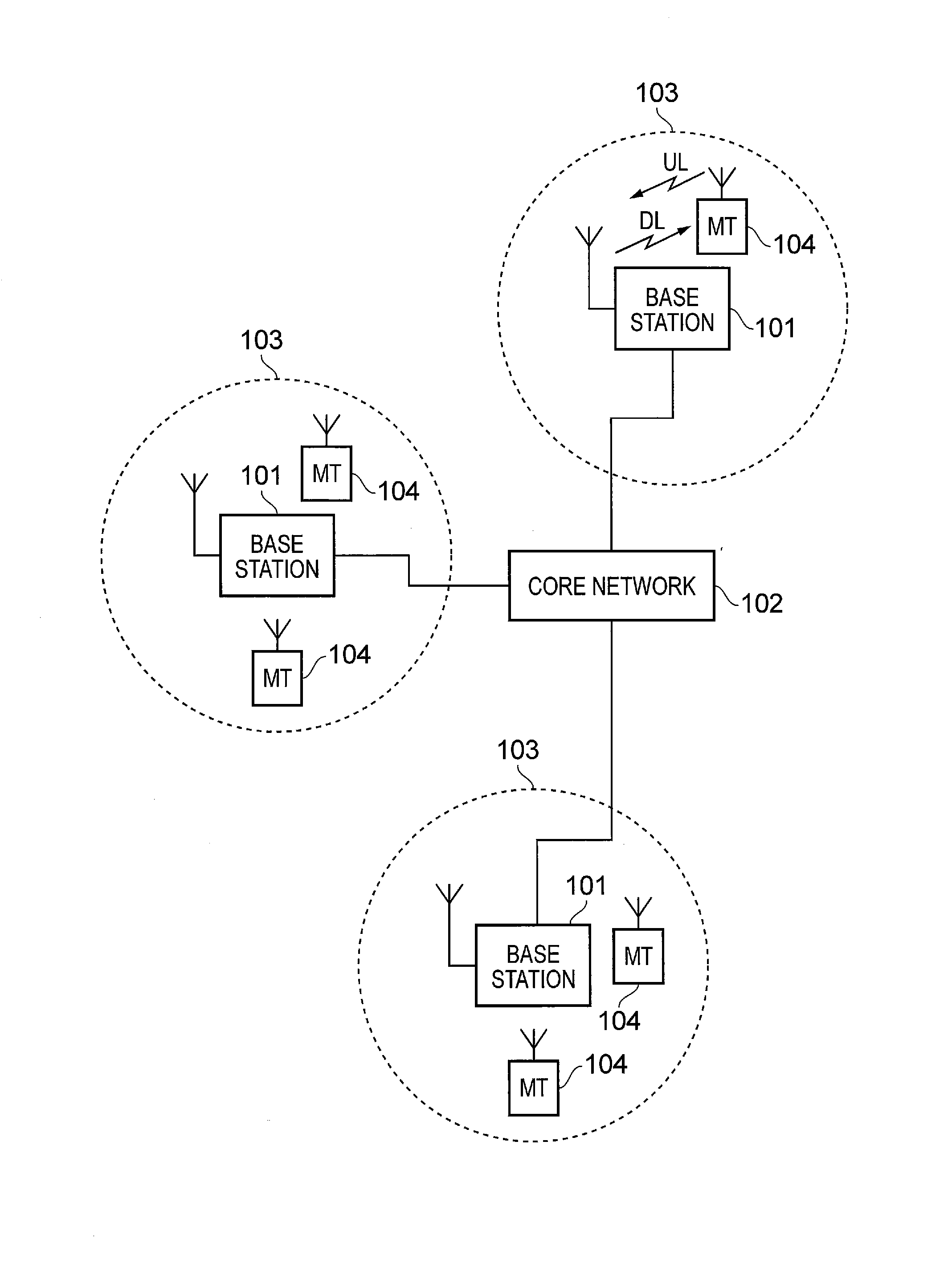
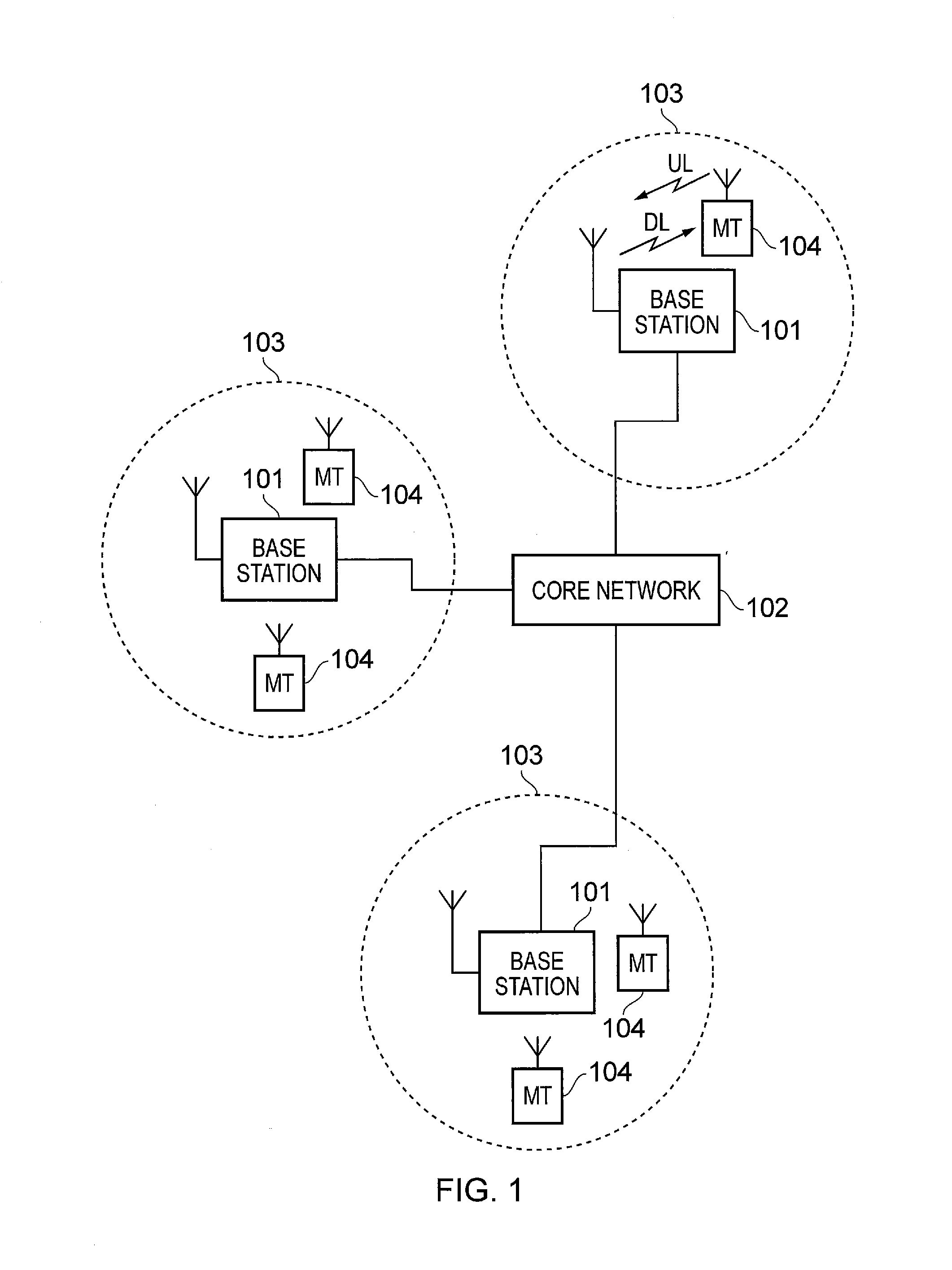
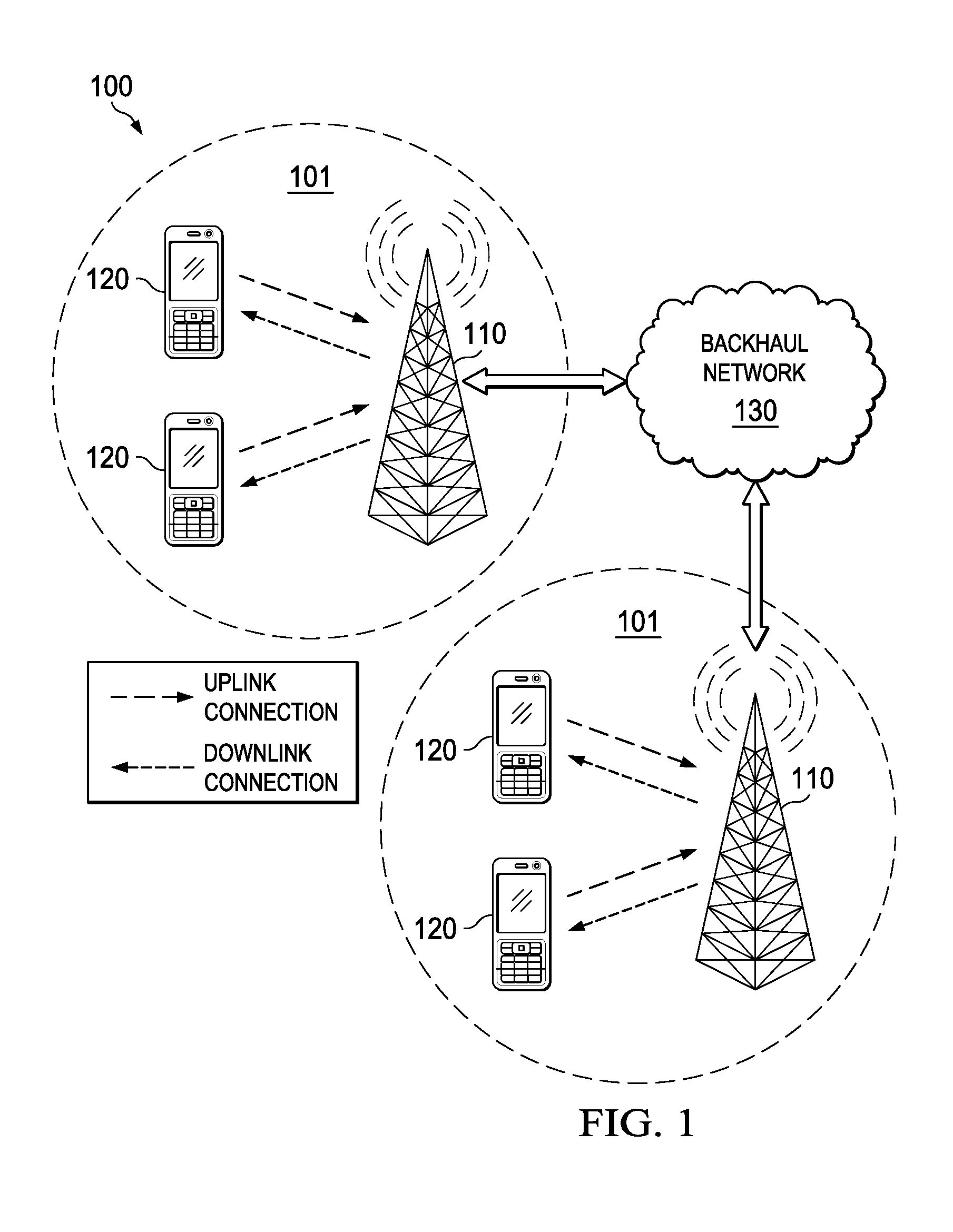
Mobile terminal device and associated method for obtaining uplink resources
ActiveUS20150271791A1Error preventionFrequency-division multiplex detailsTraffic capacityUplink transmission
A method of allocating radio resources for uplink transmissions in a wireless telecommunications system, the method including: a first terminal device communicating a request for an allocation of radio resources to a base station; the base station determining there is an association between the first terminal device and a second terminal device based on their having similar predicted traffic profiles for uplink data; and the base station establishing a radio resource allocation for the second terminal device based on the resources requested by the first terminal device, and consequently transmitting radio resource allocation messages to allocate radio resources to the first and the second terminal devices for respective uplink transmissions based on the request for an allocation of radio resources received from the first terminal device.
Owner:CONVIDA WIRELESS LLC
Base station and associated method for assigning uplink resources to terminal devices with a similar traffic profile
ActiveUS20150282155A1Assess restrictionWireless commuication servicesTraffic capacityUplink transmission
A method of allocating radio resources for uplink transmissions in a wireless telecommunications system, including: a first terminal device communicating a request for an allocation of radio resources to a base station; the base station determining whether there is an association between the first terminal device and a second terminal device based on their having similar predicted traffic profiles for uplink data; and the base station establishing a radio resource allocation for the second terminal device based on the resources requested by the first terminal device, and consequently transmitting radio resource allocation messages to allocate radio resources to the first and the second terminal devices for respective uplink transmissions based on the request for an allocation of radio resources received from the first terminal device.
Owner:CONVIDA WIRELESS LLC
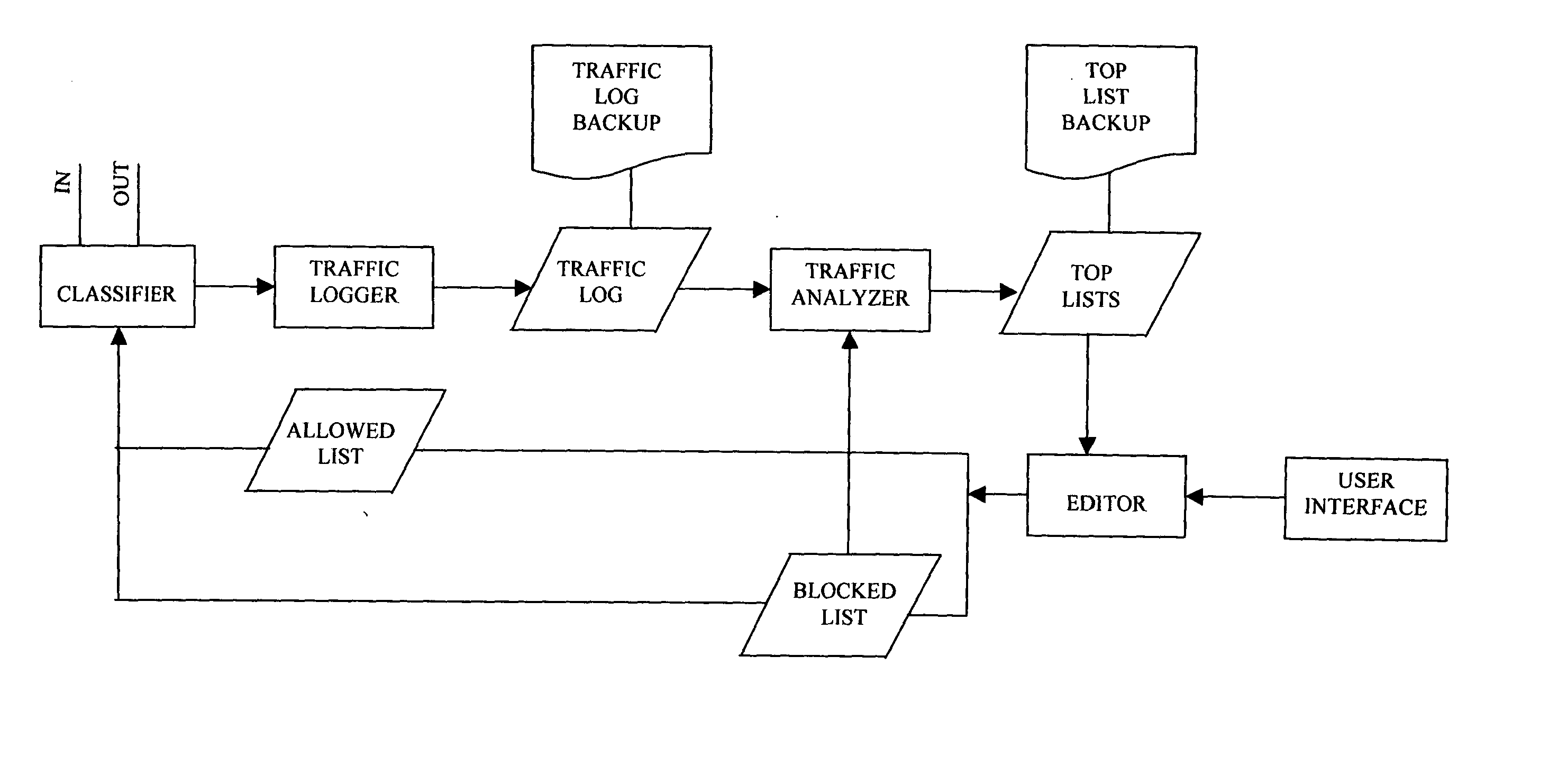
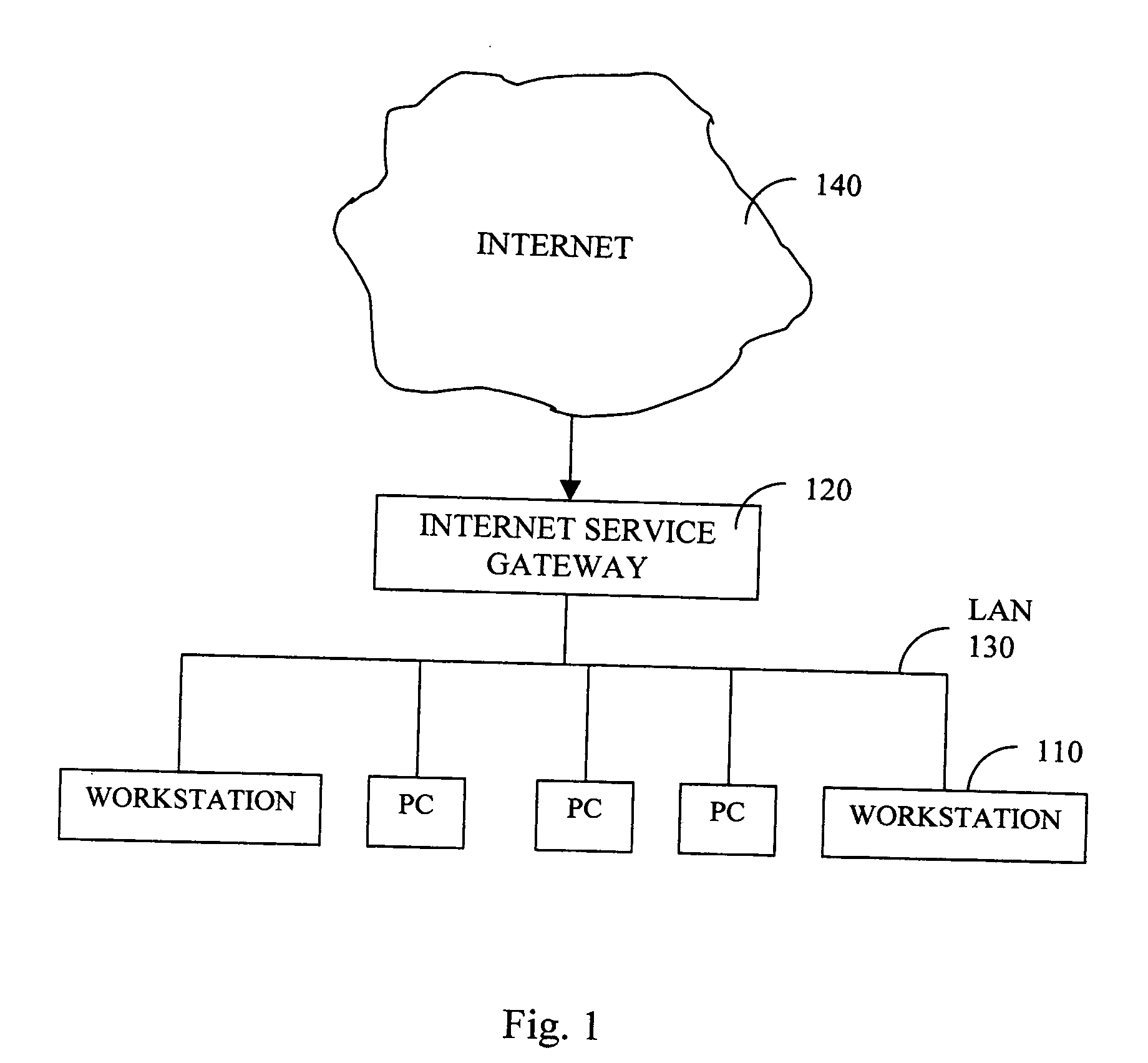
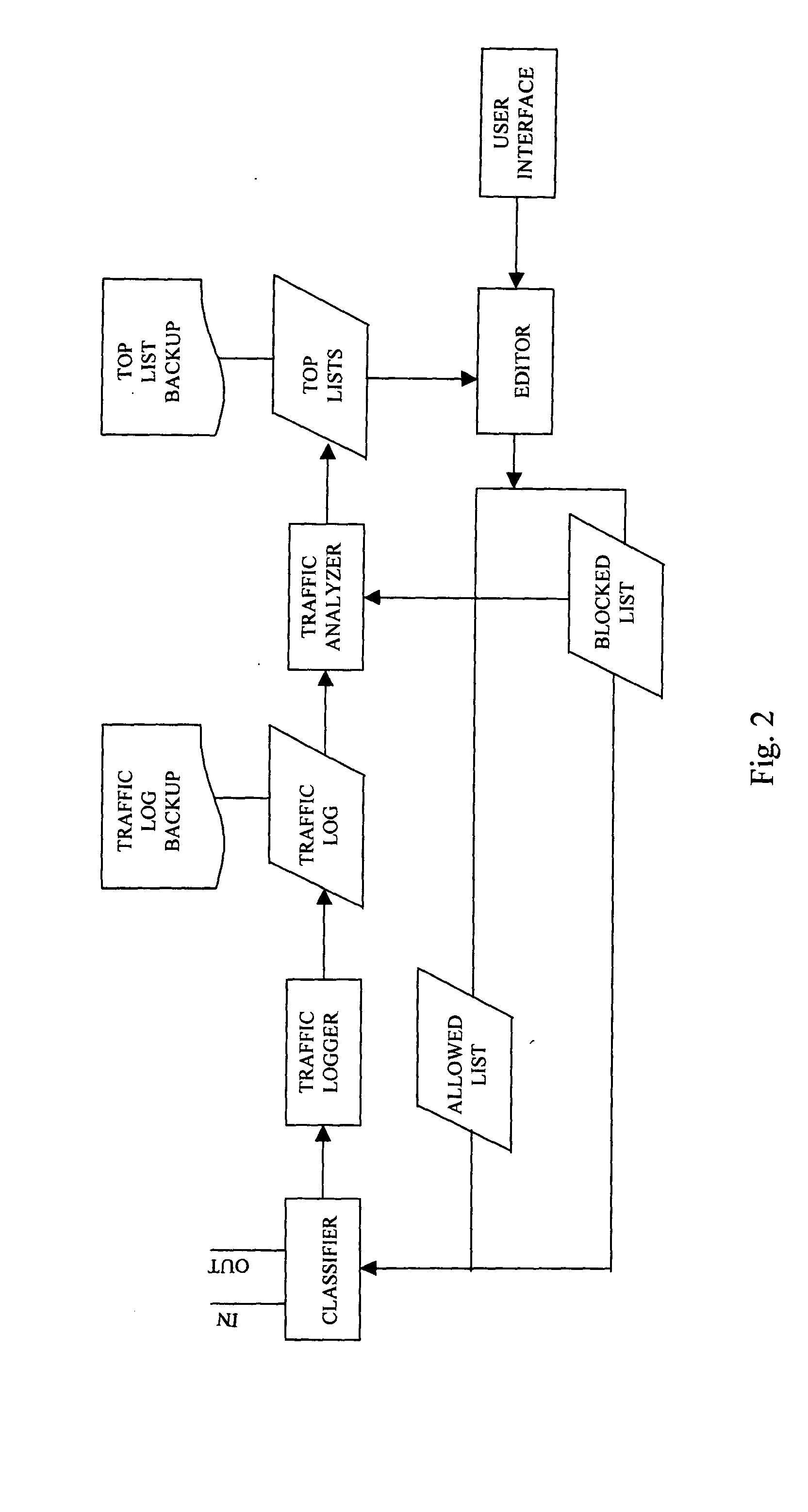
Method, system and computer program products for adaptive web-site access blocking
InactiveUS20040267929A1Effectively and adaptively controlEfficient and effective managementDigital computer detailsSecuring communicationInternet trafficUser interface
This invention discloses an Internet service gateway for controlling an access to an Internet web-site from a group of users. The service gateway includes a traffic logger for continuously monitoring a number of Internet accesses to each of a plurality of Internet web-sites from the group of users through the Internet service gateway for generating an Internet traffic log. The service gateway further includes a traffic analyzer for continuously counting and ranking the Internet accesses to each of the Internet web-sites and for generating a list of traffic-profile suspect Internet web-sites. The service gateway further includes an editor for allowing the access controller to edit a selection input for selecting the list of blocking web-sites among the list of traffic-profile suspect web-sites. The service gateway further includes a user interface to allow the access controller to provide entries directly to a list of blocking web-sites among the list of traffic-profile suspect web-sites.
Owner:SERVGATE TECH
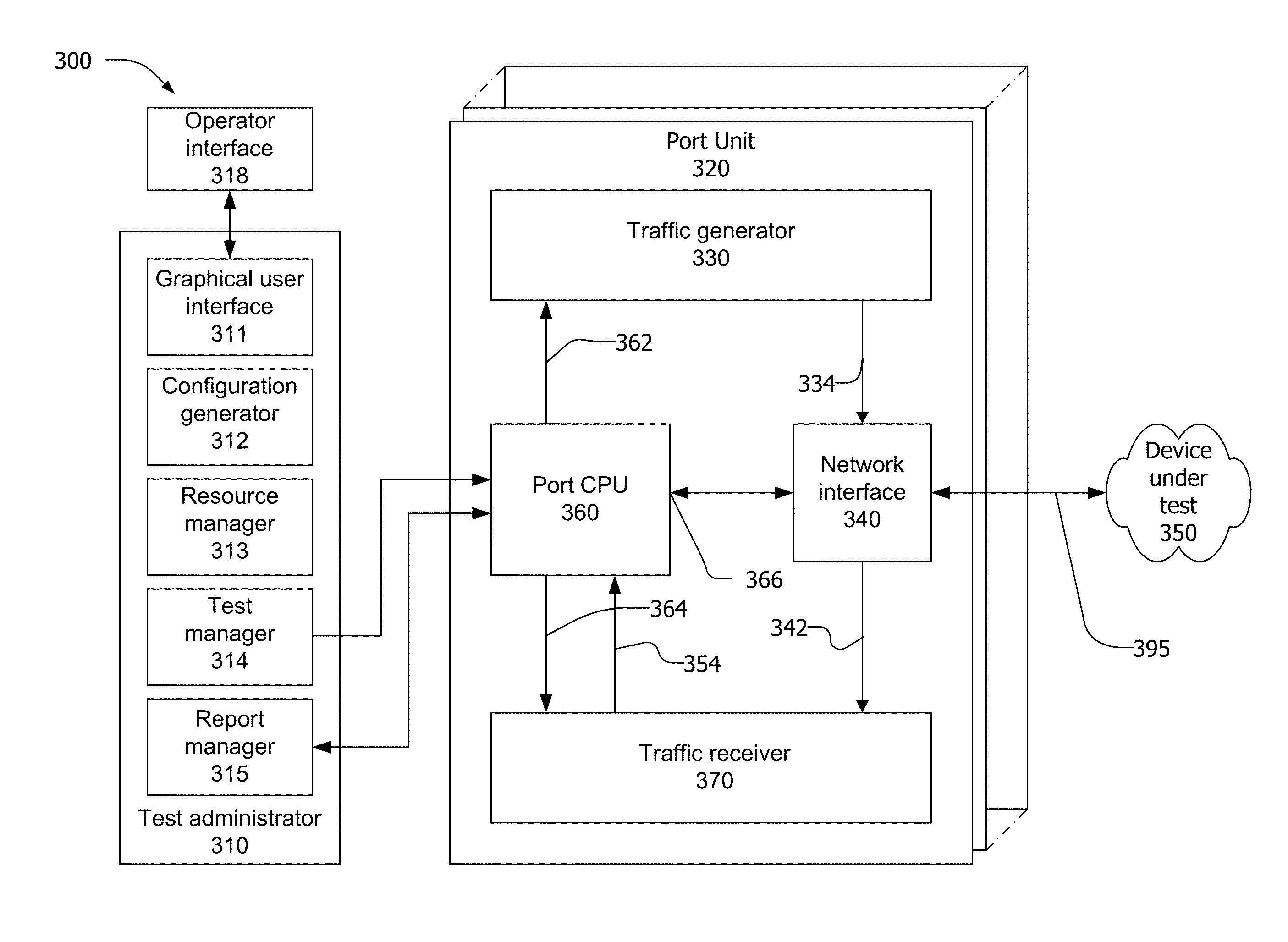
Dynamic balancing of a traffic mix for data center device testing
There is disclosed a method for testing a network device comprising defining a traffic profile wherein the traffic profile defines a type of network traffic comprising a sequence of packets and wherein the traffic profile associates the network traffic with a communication axis. The method also comprises defining a traffic template wherein the traffic template comprises one or more traffic profiles, a relative weight to identify a weight of the profile within an overall traffic configuration, and a load rate that defines the maximum amount of packets that can be transmitted at a certain time. The method further comprises generating network traffic based on the traffic template, and transmitting the network traffic to a device under test wherein the relative weight of the traffic profile may be changed dynamically in real-time.
Owner:KEYSIGHT TECH SINGAPORE (SALES) PTE LTD
Streaming bridge design with host interfaces and network on chip (NoC) layers
ActiveUS9699079B2Simplified managementHigh degreeData switching networksQuality of serviceTraffic capacity
Systems and methods described herein are directed to streaming bridge design implementations that help interconnect and transfer transaction packets between multiple source and destination host interfaces through a Network on Chip (NoC) interconnect, which includes a plurality of NoC router layers and virtual channels (VCs) connecting the router layers. Implementations are configured to support a variety of different traffic profiles, each having a different set of traffic flows. Streaming bridge design implementation can divide streaming bridge into a streaming TX bridge and a streaming RX bridge, wherein TX bridge is operatively coupled with host TX interfaces and RX bridge is operatively coupled with host RX interfaces, and where TX bridge forwards transaction packets from host TX interfaces to different router layers / VCs of NoC, and RX bridge, on the other hand, receives packets from NoC router layers / VCs and transmits the packets to host RX interfaces based on Quality of Service.
Owner:INTEL CORP
Gathering traffic profiles for endpoint devices that are operably coupled to a network
ActiveUS20090046720A1Facilitate methodError preventionTransmission systemsTraffic capacityPacket loss
Methods and computer program products for gathering a traffic profile for an endpoint device operably coupled to a network. Methods include simultaneously sending a set of numerically sequenced packets to a plurality of endpoint devices on the network including the endpoint device, wherein the plurality of endpoint devices are time synchronized with the numerically sequenced packets; receiving the numerically sequenced packets at the endpoint device; electronically storing packet data for the numerically sequenced packets at the endpoint device, wherein the packet data is stored for a user configurable time period; collecting the packet data within the user configurable time period; and using the collected packet data to determine packet loss information or packet sequence information for the endpoint device.
Owner:AT&T INTPROP I L P
Managing network traffic for improved availability of network services
ActiveUS8095635B2Method can be usedPrecise functionError preventionFrequency-division multiplex detailsTraffic capacityNetwork service
Managing network traffic to improve availability of network services by classifying network traffic flows using flow-level statistical information and machine learning estimation, based on a measurement of at least one of relevance and goodness of network features. Also, determining a network traffic profile representing applications associated with the classified network traffic flows, and managing network traffic using the network traffic profile. The flow-level statistical information includes packet-trace information and is available from at least one of Cisco NetFlow, NetStream or cflowd records. The classification of network flows includes tagging packet-trace flow record data based on defined packet content information. The classifying of network flows can result in the identification of a plurality of clusters based on the measurement of the relevance of the network features. Also, the classification of network traffic can use a correlation-based measure to determine the goodness of the network features.
Owner:AT&T INTPROP I L P
Lightweight Application Classification for Network Management
ActiveUS20100014420A1Method can be usedEasy to useError preventionTransmission systemsTraffic capacityNetwork management
Managing network traffic to improve availability of network services by classifying network traffic flows using flow-level statistical information and machine learning estimation, based on a measurement of at least one of relevance and goodness of network features. Also, determining a network traffic profile representing applications associated with the classified network traffic flows, and managing network traffic using the network traffic profile. The flow-level statistical information includes packet-trace information and is available from at least one of Cisco NetFlow, NetStream or cflowd records. The classification of network flows includes tagging packet-trace flow record data based on defined packet content information. The classifying of network flows can result in the identification of a plurality of clusters based on the measurement of the relevance of the network features. Also, the classification of network traffic can use a correlation-based measure to determine the goodness of the network features.
Owner:AT&T INTPROP I L P
System and method for determining traffic conditions
InactiveUS7392130B1Analogue computers for vehiclesInstruments for road network navigationMobile vehicleEngineering
The present invention provides a method and apparatus for determining traffic conditions using wireless devices. A number of signals from the vehicles traveling in selected routes are received by several wireless communication networks via the wireless devices. The total number of signals received are used to compare if there are sufficient number of vehicles traveling on the selected routes. If so, then the location information of the moving vehicles at various times is determined by the wireless communication network and forwarded to a central computer. The central computer coordinates with the wireless communications network for information needed to compute traffic data. The central computer computes the velocity of the moving vehicles and a traffic profile is created based on the velocity and location information of the moving vehicles. Furthermore, the traffic profile is sent to the moving vehicles.
Owner:AMERICAN TELEPHONE & TELEGRAPH CO
Using multiple traffic profiles to design a network on chip
Owner:INTEL CORP
Method and system for transmission control protocol (TCP) traffic smoothing
Various aspects of a method and system for transmission control protocol (TCP) traffic smoothing are presented. Traffic smoothing may comprise a method for controlling data transmission in a communications system that further comprises scheduling the timing of transmission of information from a TCP offload engine (TOE) based on a traffic profile. Traffic smoothing may comprise transmitting information from a TOE at a rate that is either greater than, approximately equal to, or less than, the rate at which the information was generated. Some conventional network interface cards (NIC) that utilize TOEs may not provide a mechanism that enables traffic shaping. By not providing a mechanism for traffic shaping, there may be a greater probability of lost packets in the network.
Owner:AVAGO TECH WIRELESS IP SINGAPORE PTE
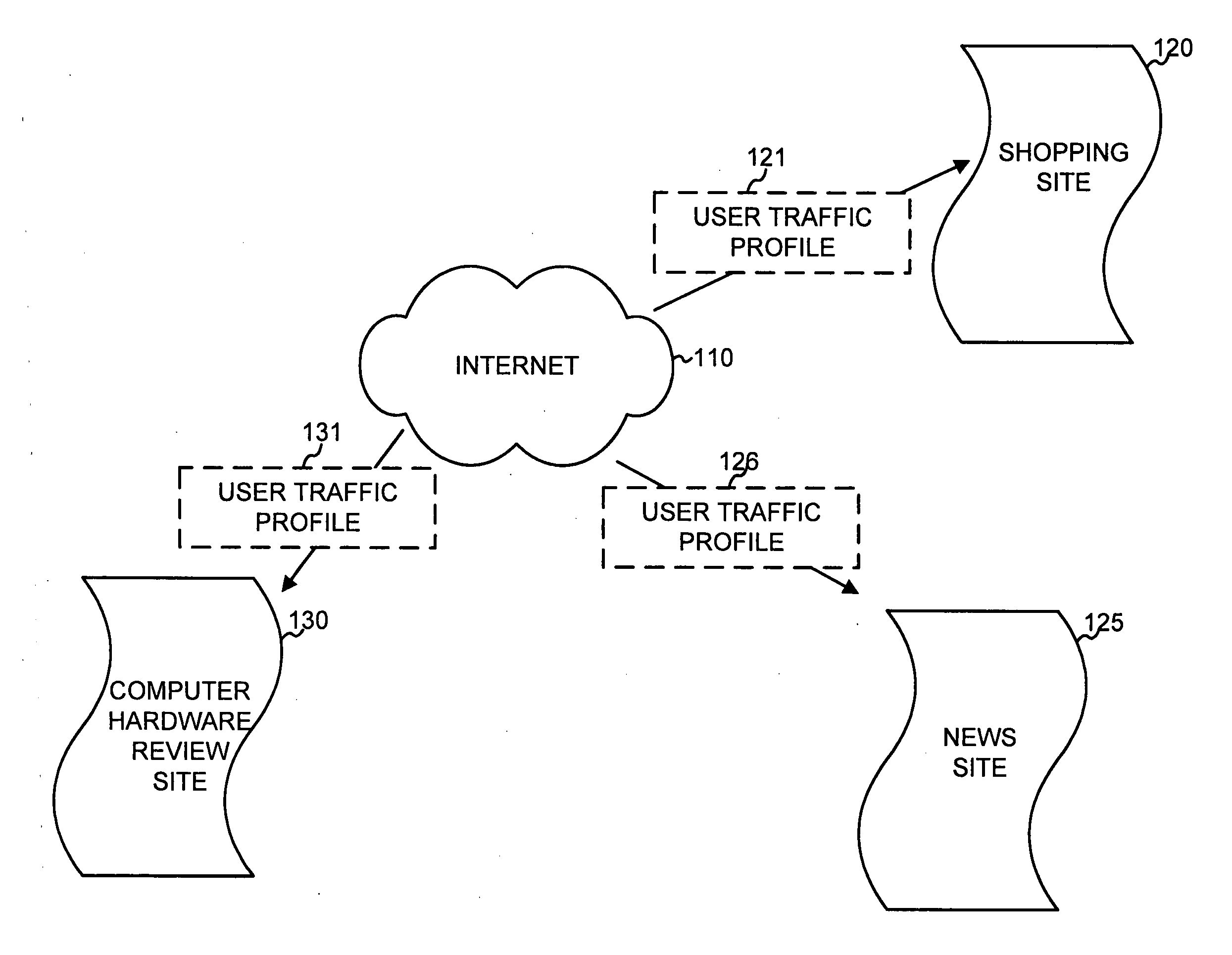
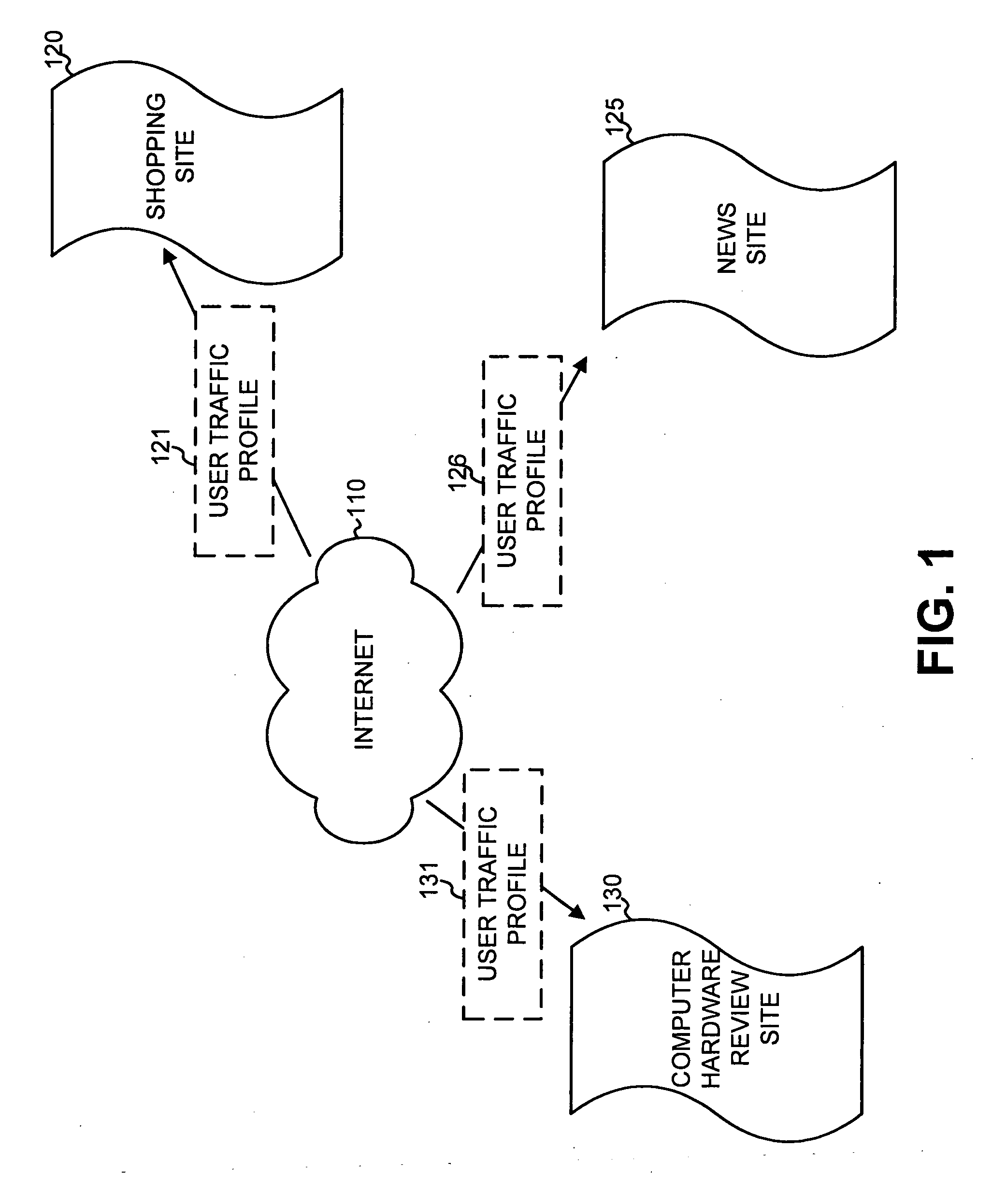
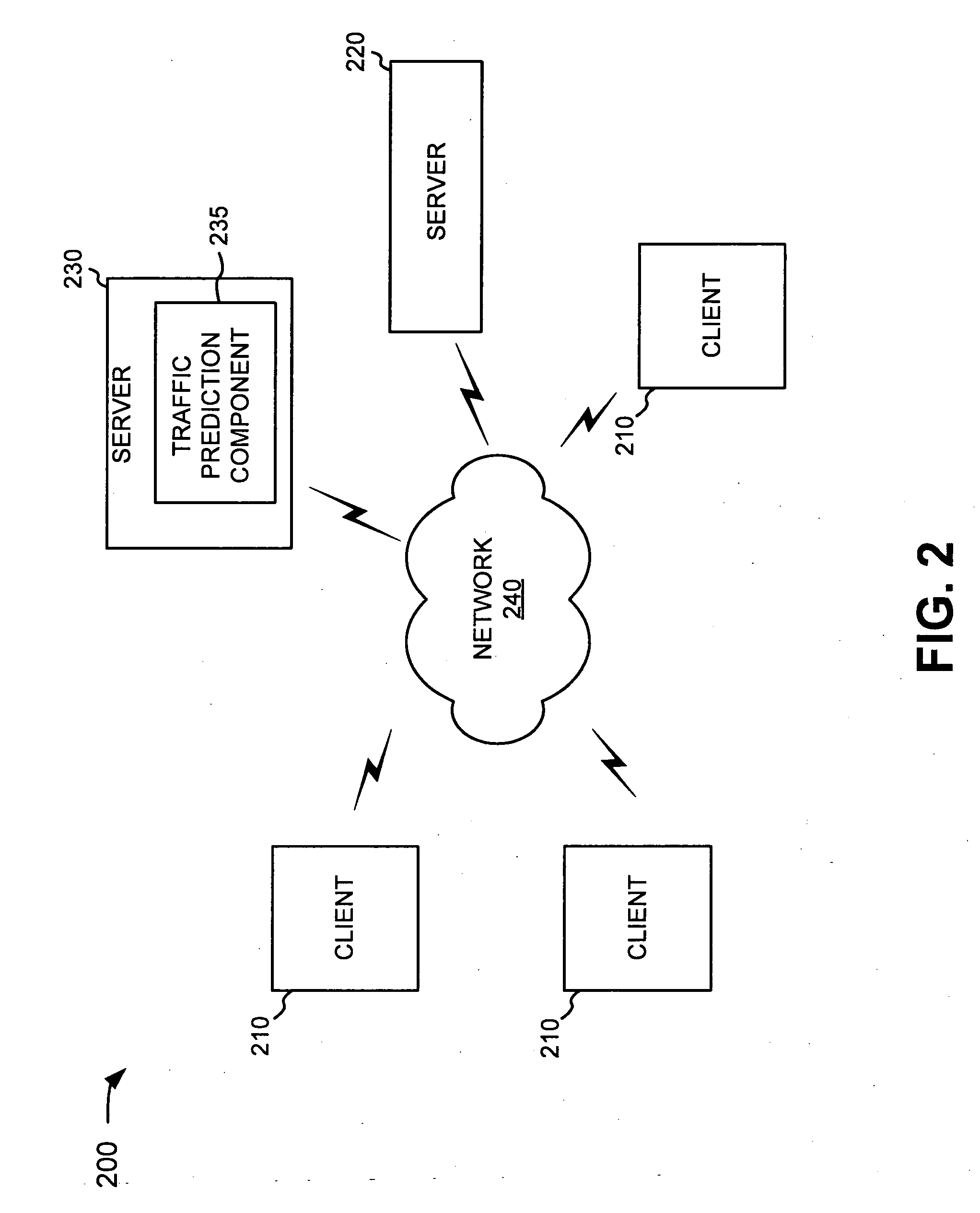
Traffic prediction for web sites
A traffic prediction component may automatically generate predicted traffic profiles for web sites based on tags that characterize the sites. An initial set of tags can be selected for a web site based on a set of predefined rules. An initial traffic profile may be selected based on the initial set of tags. The predicted profile of user traffic is then generated based on the initial set of tags and on the initial traffic profile.
Owner:GOOGLE LLC
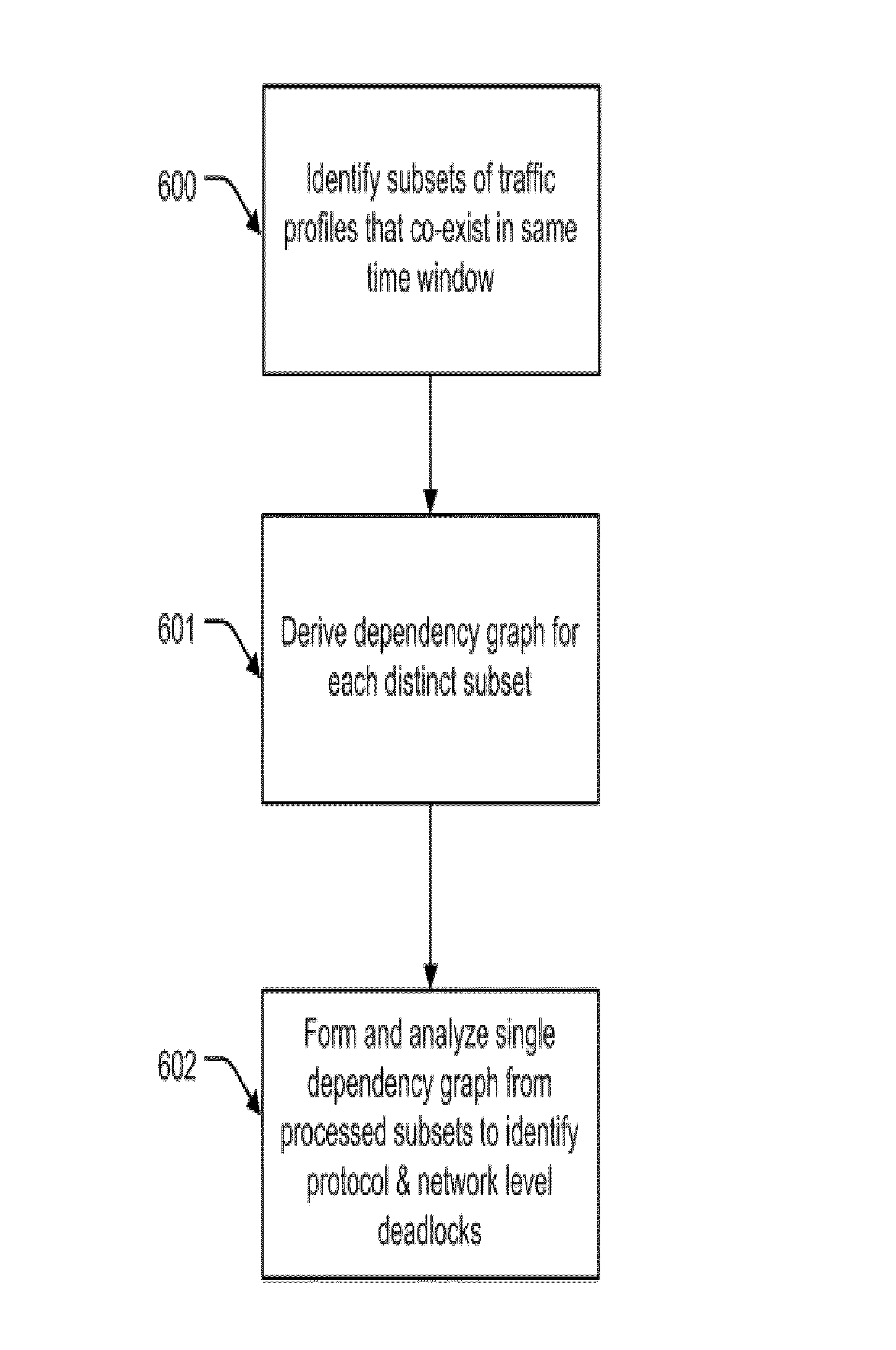
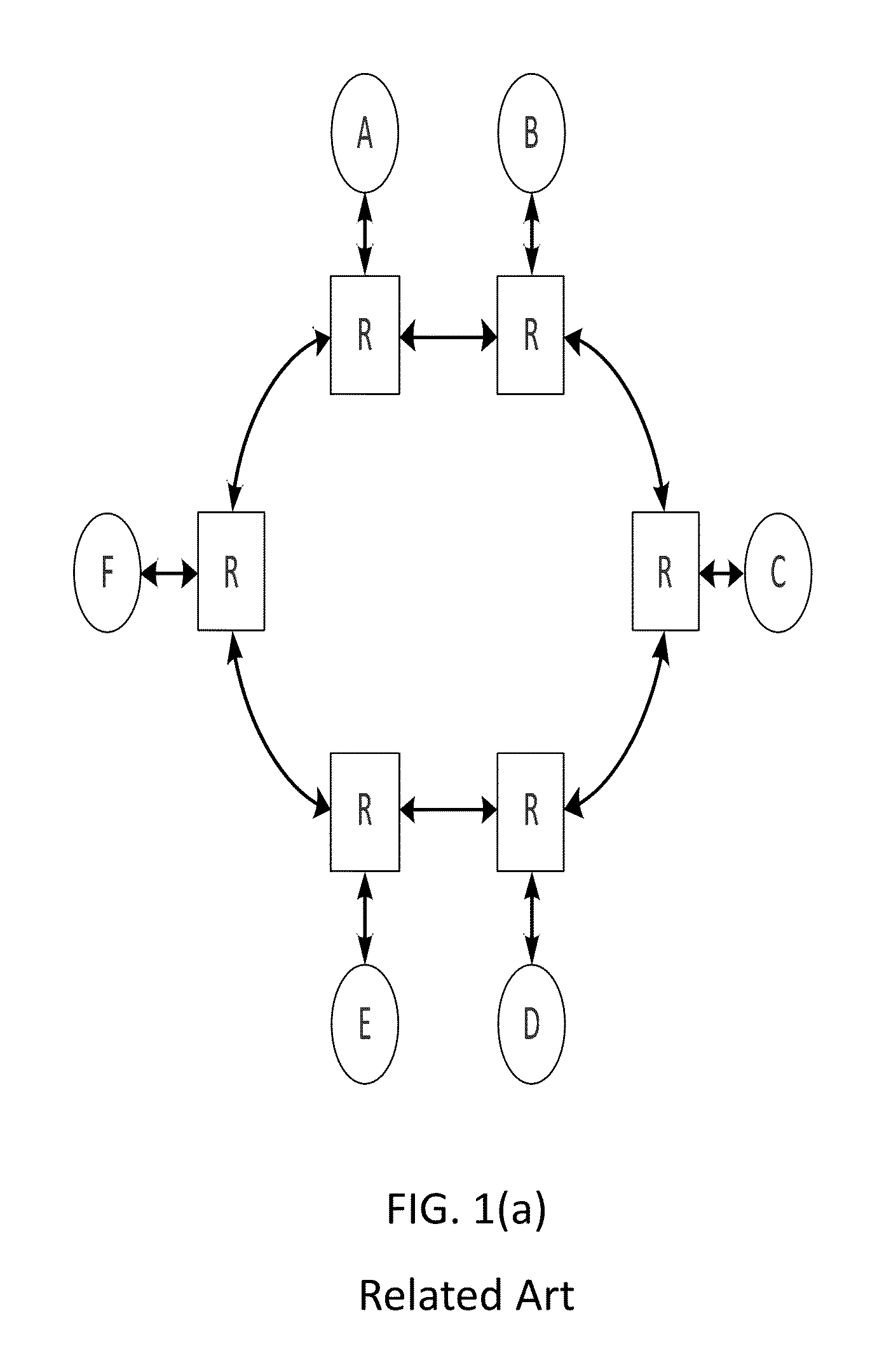
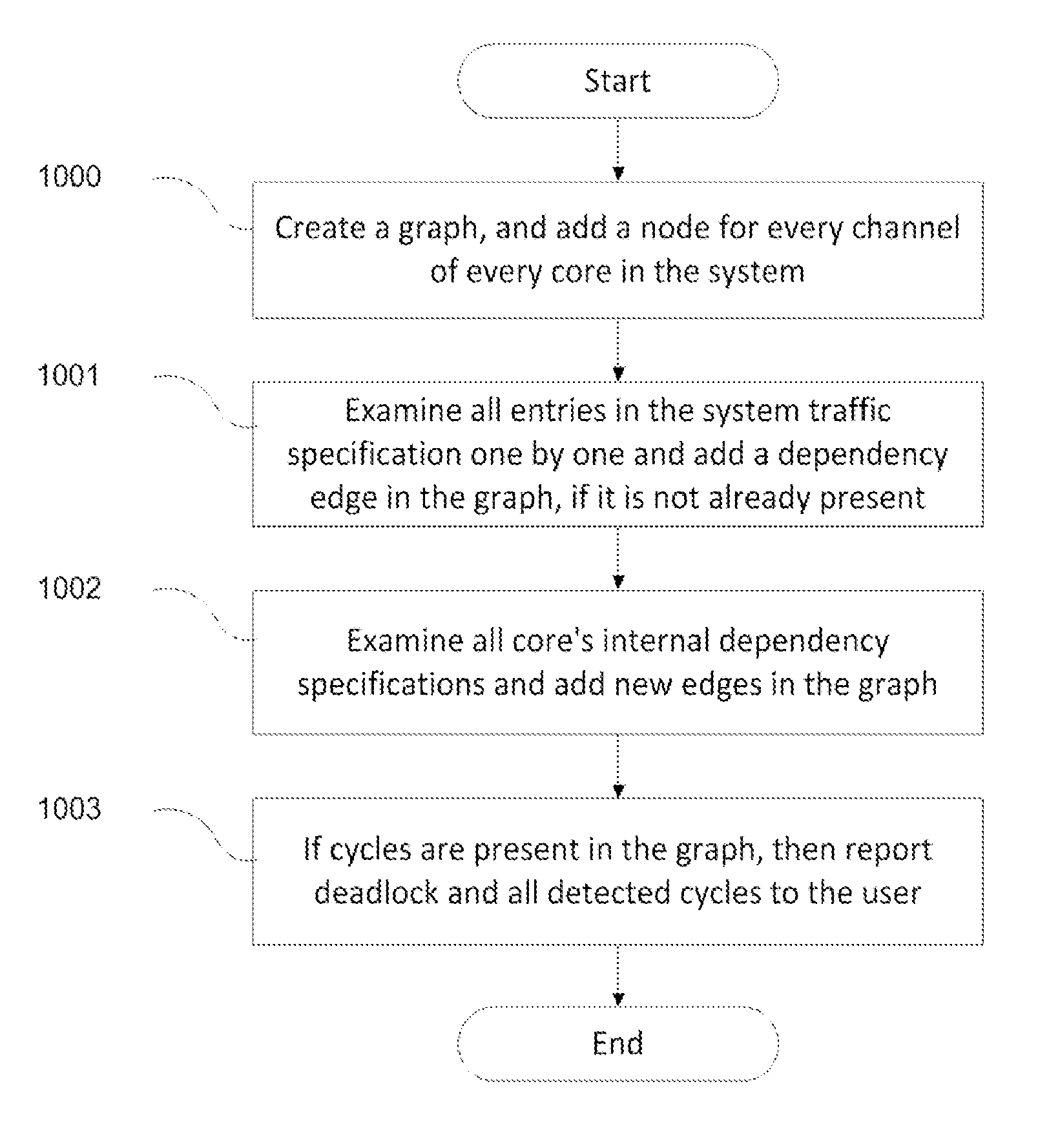
Automatic deadlock detection and avoidance in a system interconnect by capturing internal dependencies of IP cores using high level specification
InactiveUS9009648B2Save resource costData switching networksSpecial data processing applicationsDeadlock freeNetworks on chip
Owner:INTEL CORP
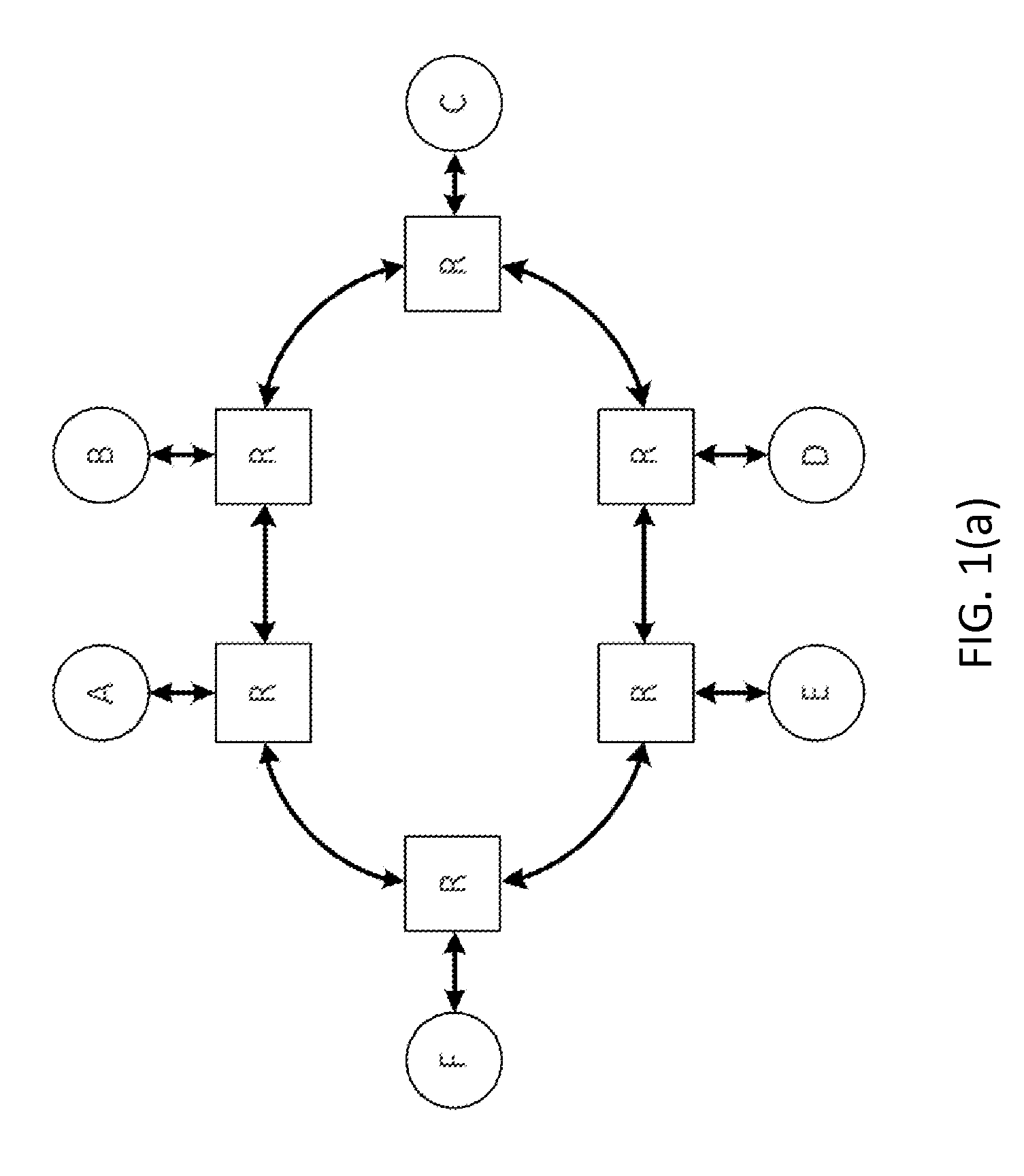
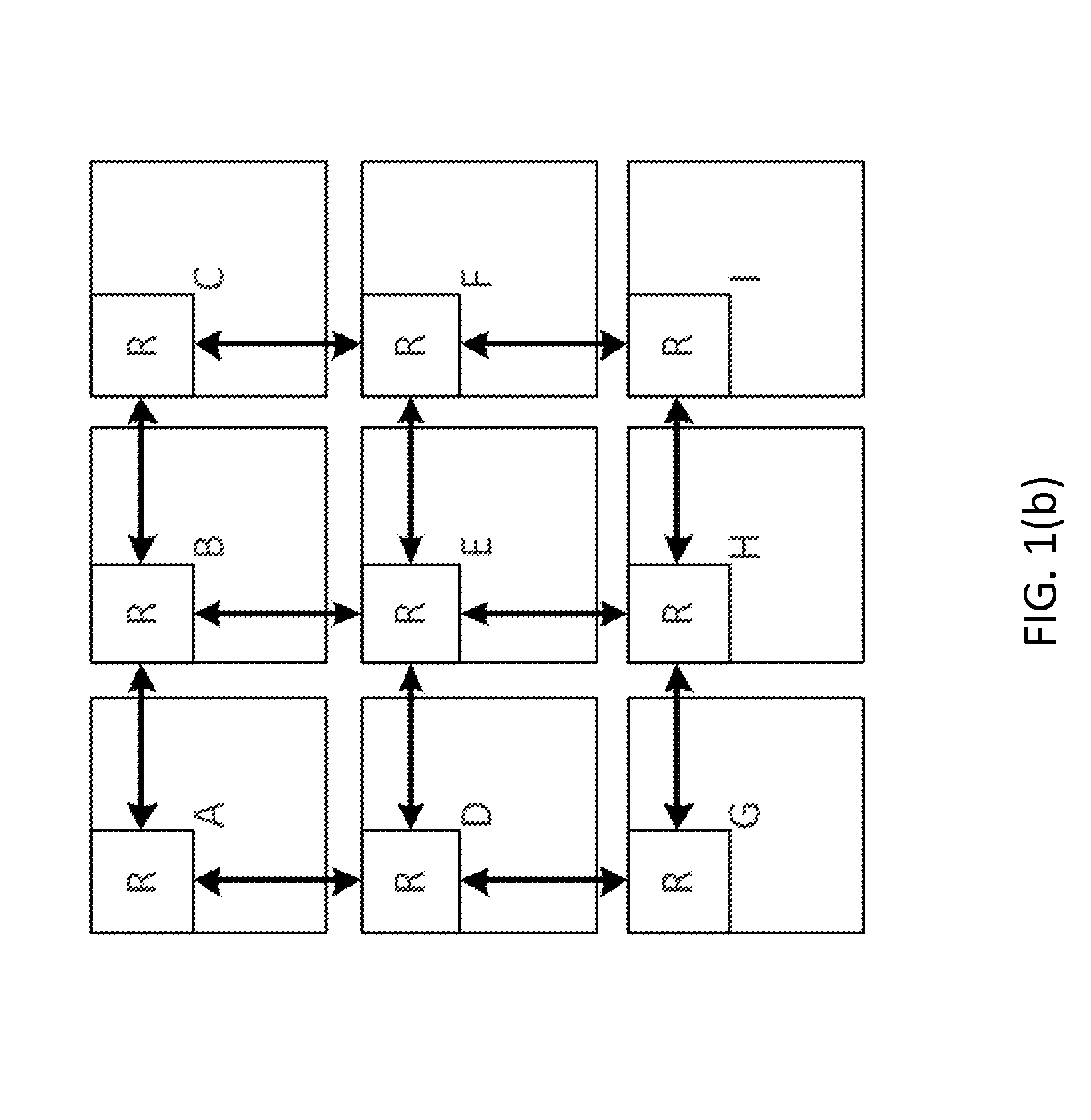
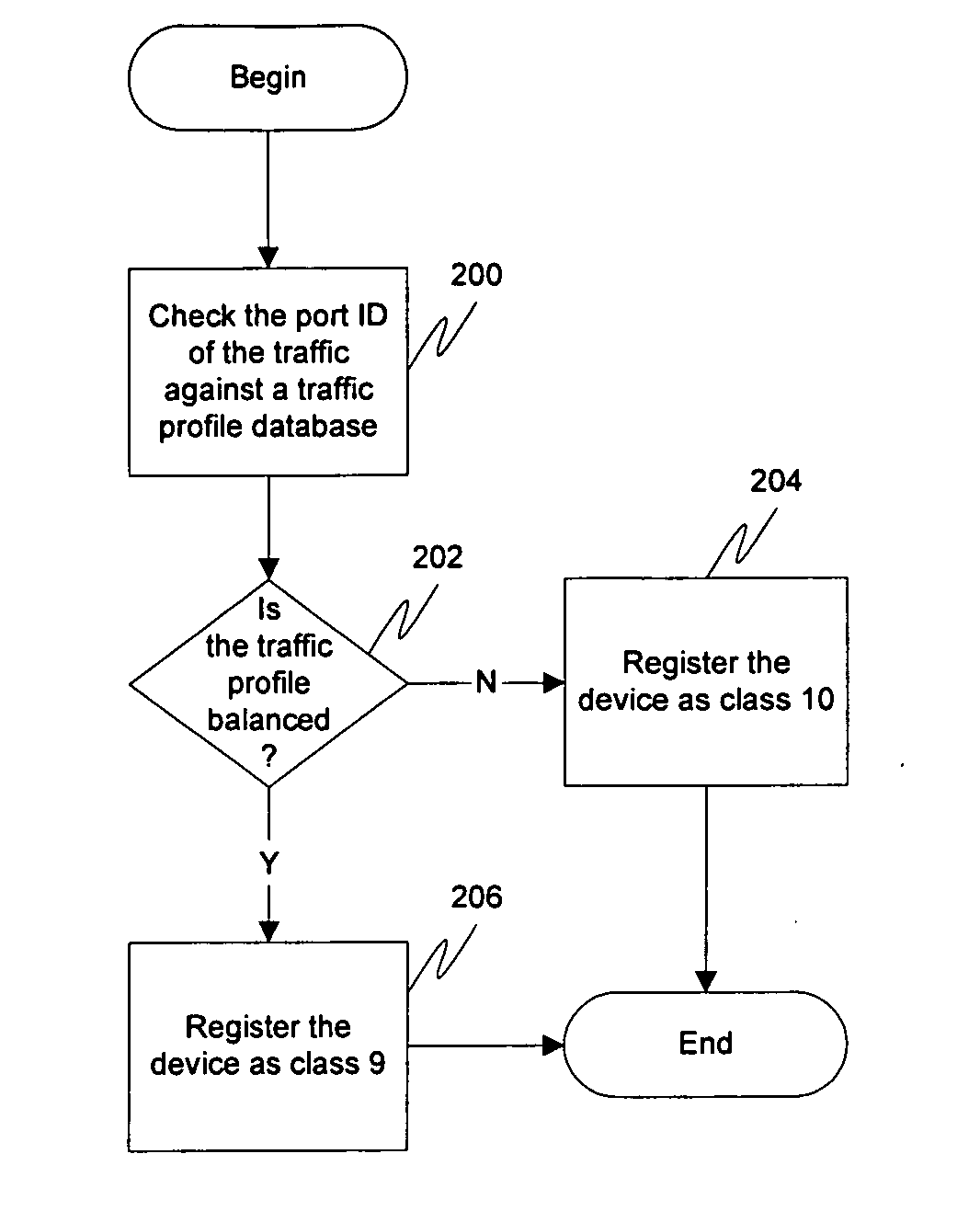
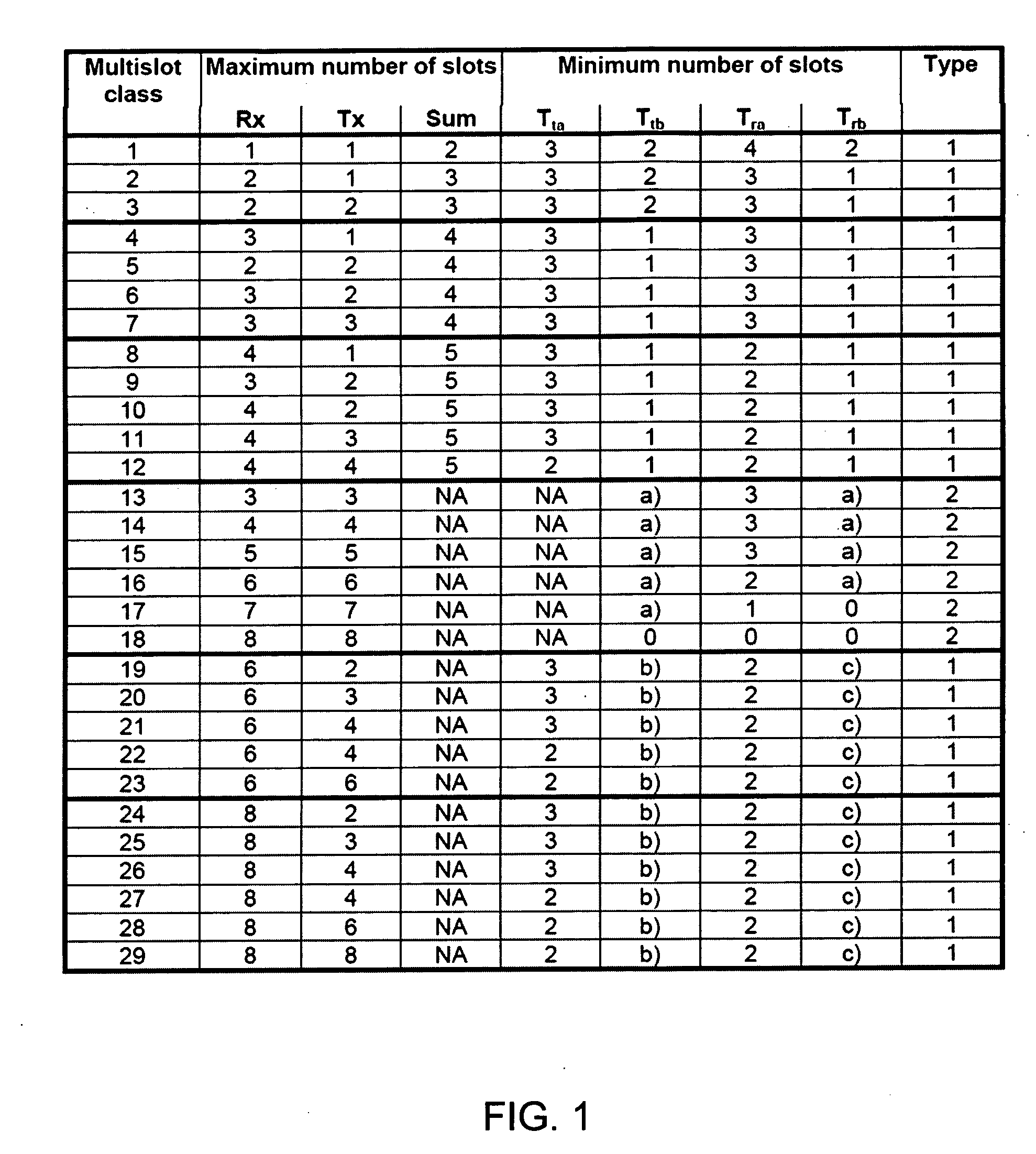
Configurable multislot class for wireless devices
InactiveUS20060250957A1Effective distributionError preventionTransmission systemsTransport control protocolMobile device
A solution is provided wherein the mobile device selects a multislot class based on the profile of the traffic to be utilized by the mobile device. This may be performed manually by a user, or may be performed automatically where an application or driver software automatically and dynamically determines the best multislot class for the applications being used. This can be accomplished, for example, by looking at the classification of the transport control protocol (TCP) port numbers used, by examining the data sent and received by the network, and / or looking up a profile for the user or device. If the user changes applications or some other event occurs on the mobile device that might cause a change in the profile of the traffic, the mobile device may terminate its current multislot class assignment and re-announce itself, allowing the system to transfer the mobile device to a new multislot class.
Owner:NETGEAR INC
Network Traffic Profile Aggregation for Efficient Discrete Event Smart Grid Network Simulations
Systems and methods are provided for modeling and simulating a communication network operating under at least one communication protocol, which supports a Smart Grid electricity network. Communication performance data of the communication network are generated by a processor based on operating behavior of the Smart Grid with a plurality of assets under a first condition. Devices in the Smart grid are grouped in bins for rapid modeling. One or more different configurations of the communication network are entered into the processor and related performance data is also generated. Network configurations are compared based on the generated performance data which may include end-to-end delay and reception rate. Processor based systems to perform modeling methods are also provided.
Owner:SIEMENS IND INC +1
Session Admission Control Method and Apparatus
InactiveUS20080232360A1Easy to useLow bandwidth efficiencyData switching by path configurationStore-and-forward switching systemsTraffic capacityData stream
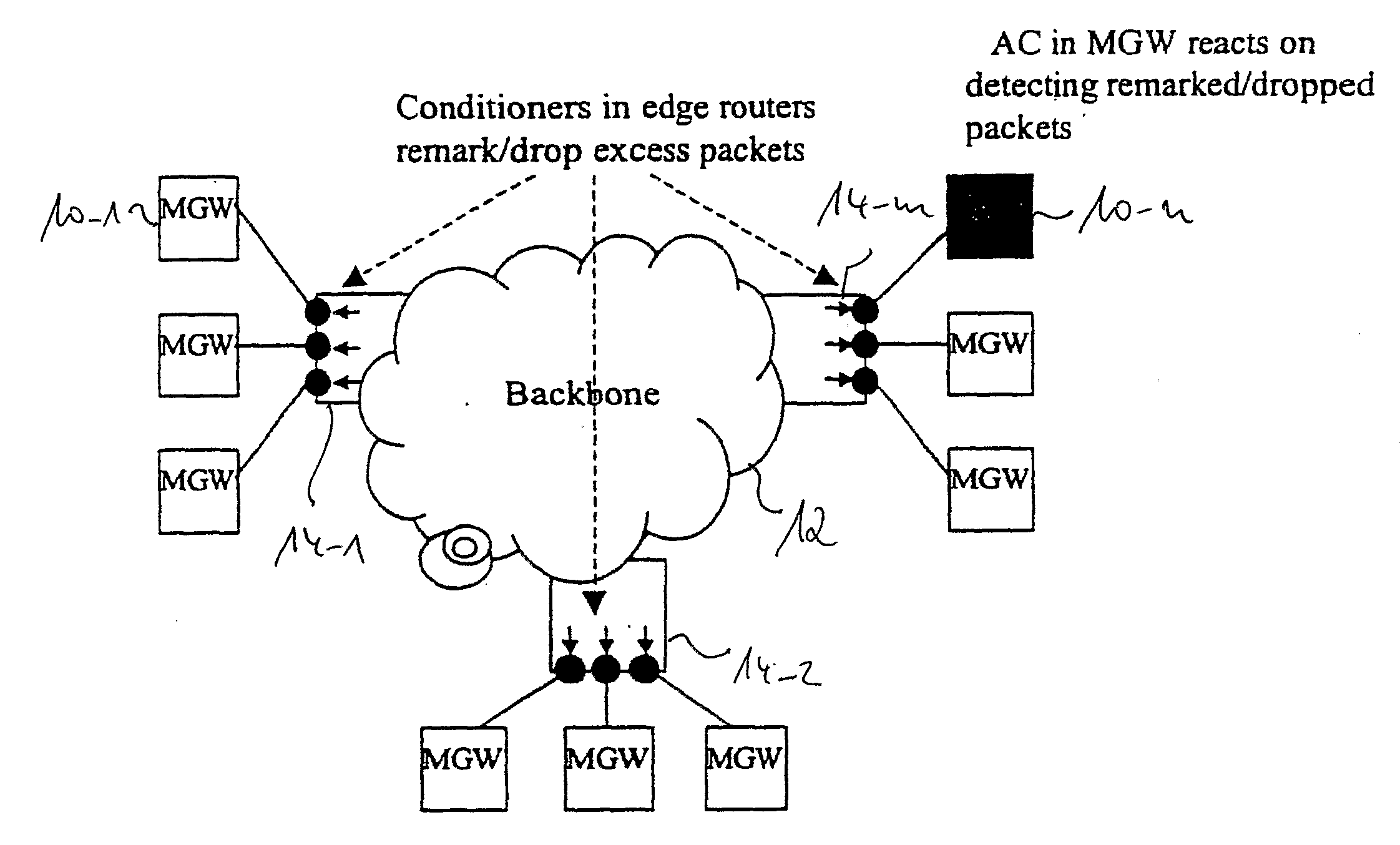
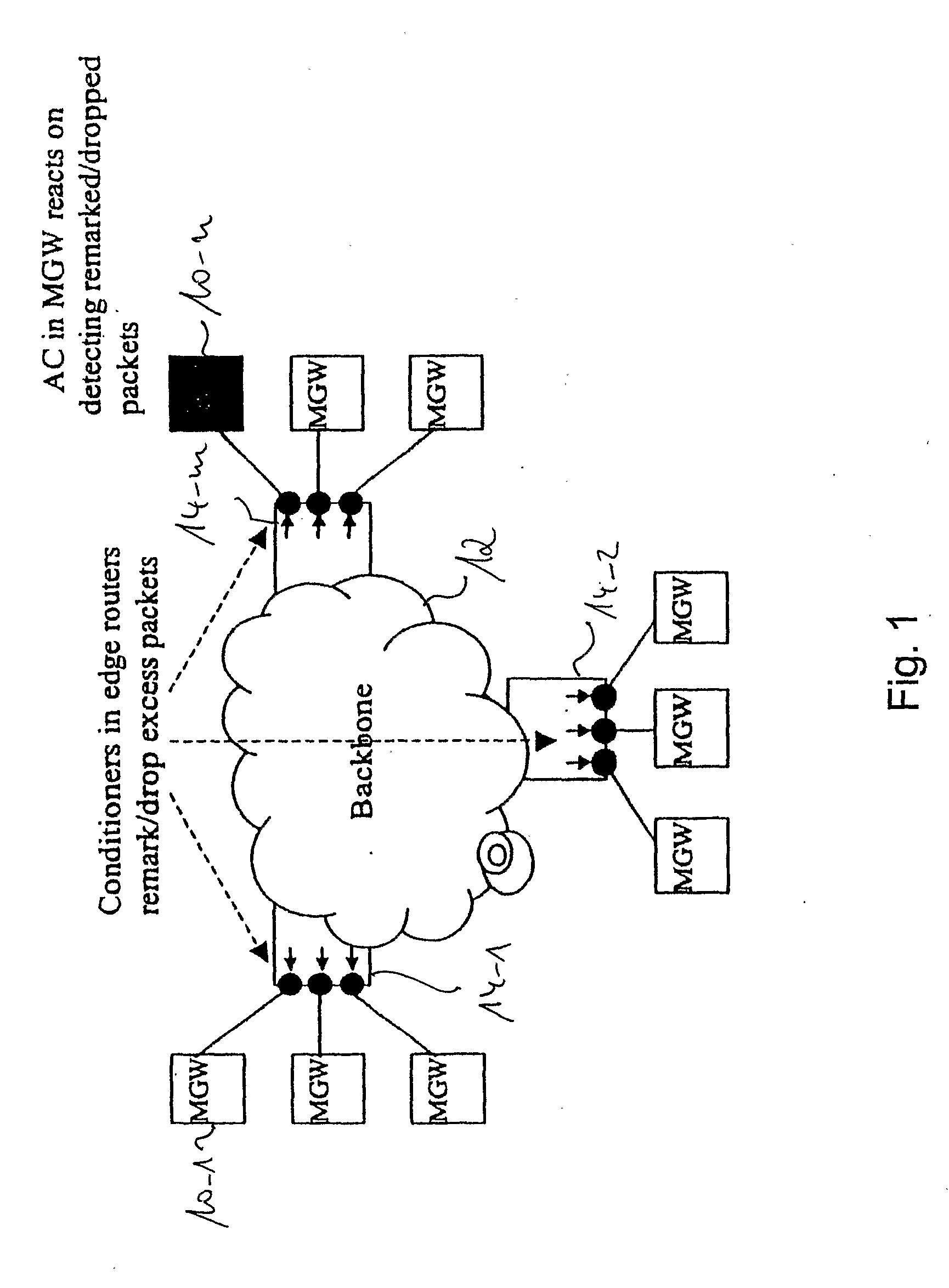
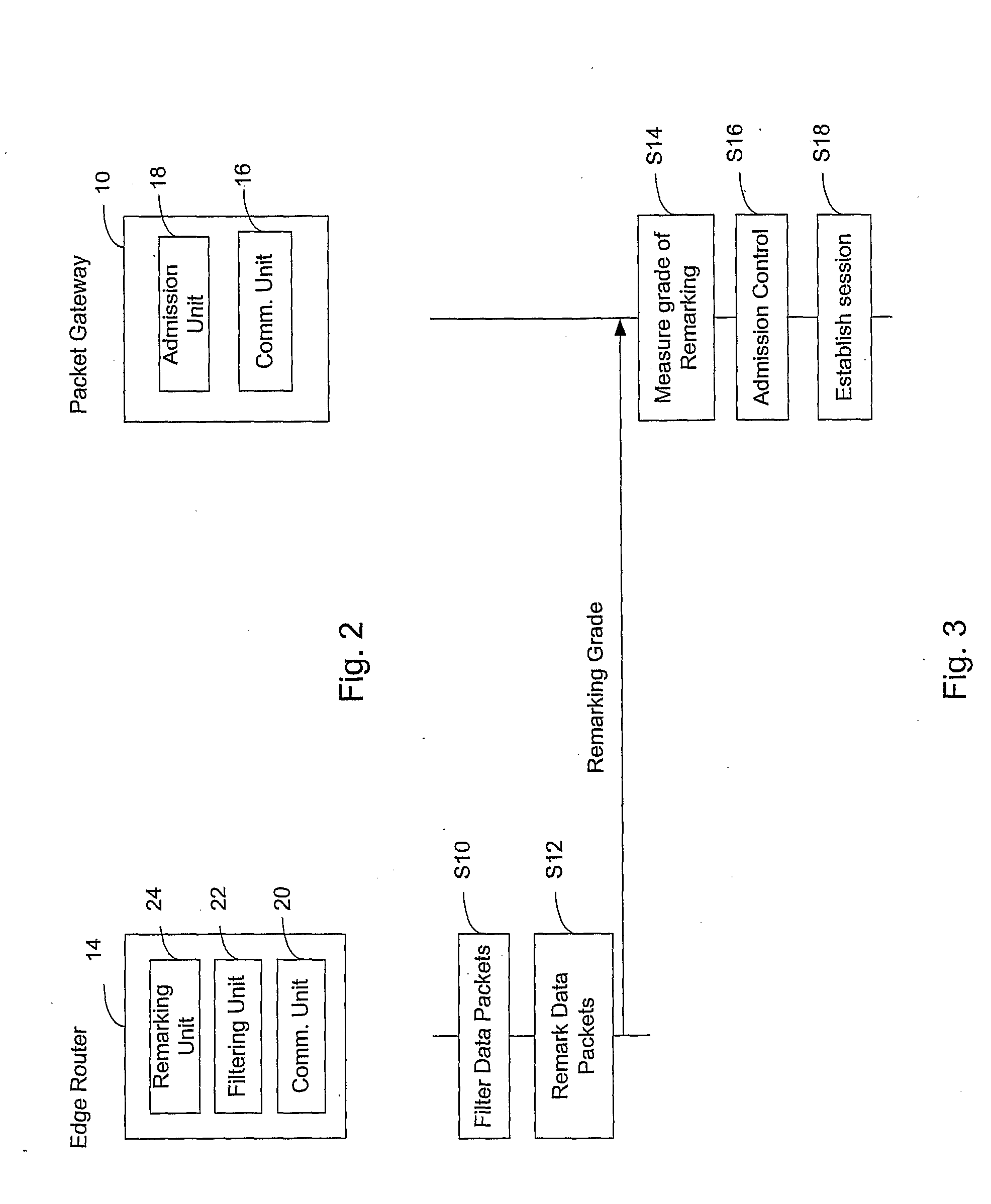
For efficient and fast admission control with respect to a new session and for exchange of data stream packets between an edge router (14) and a packet gateway (10) it is proposed to execute, at the edge router (14), selection of traffic streams of certain types from specific source nodes and target nodes and to also execute related traffic conditioning. Then, having selected specific data packet streams, the edge router (16) remarks data packets when the data packet streams are not in conformance with a predetermined traffic profile. This remarking serves as a performance indication for the packet gateway session admission control mechanism. In other words, the packet gateway (10) considers the number of remarked packets and determines on admission control for a new data packet stream session as a function of the number of remarked packets.
Owner:TELEFON AB LM ERICSSON (PUBL)
Self-adaptive scheduling method and network element
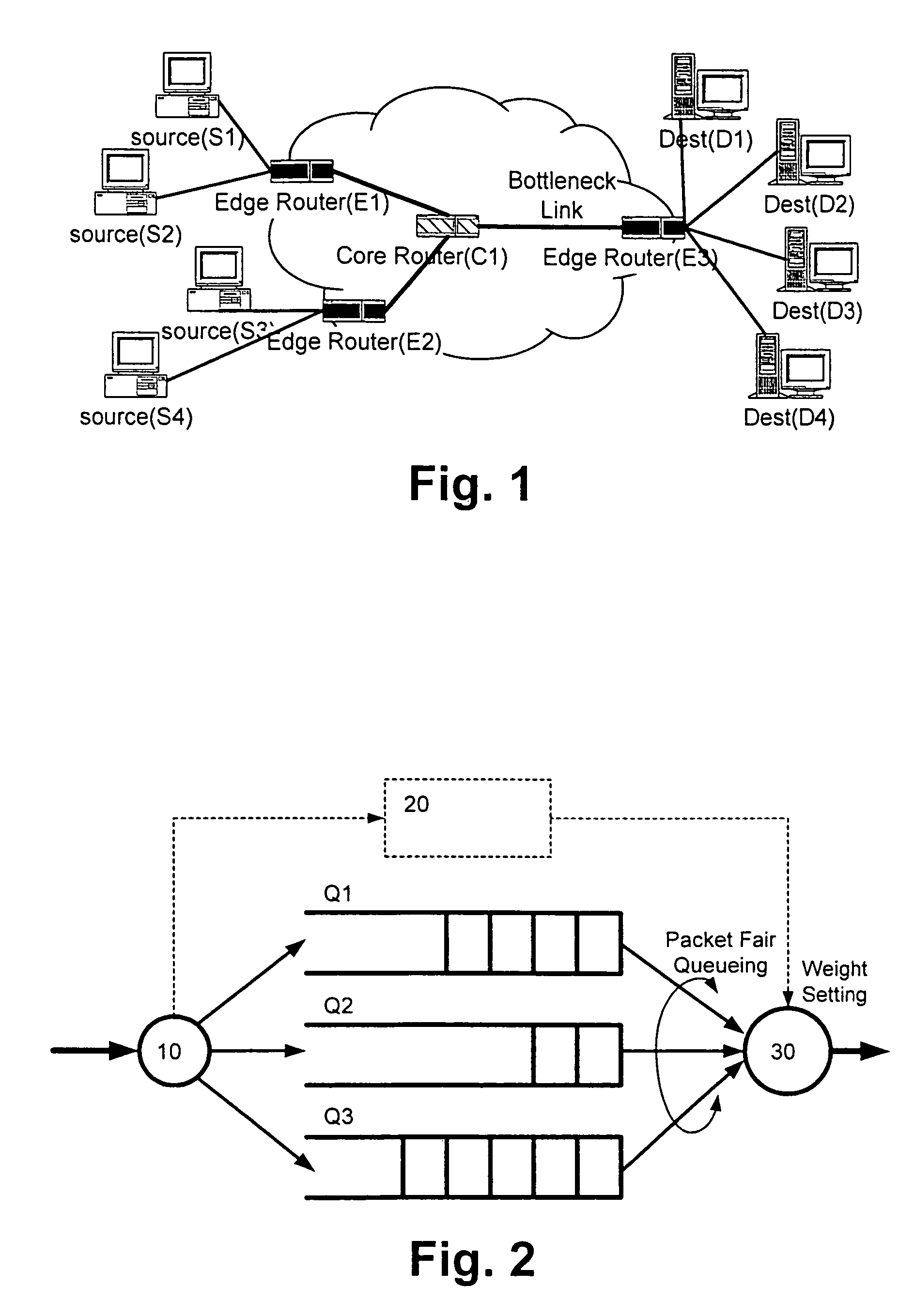
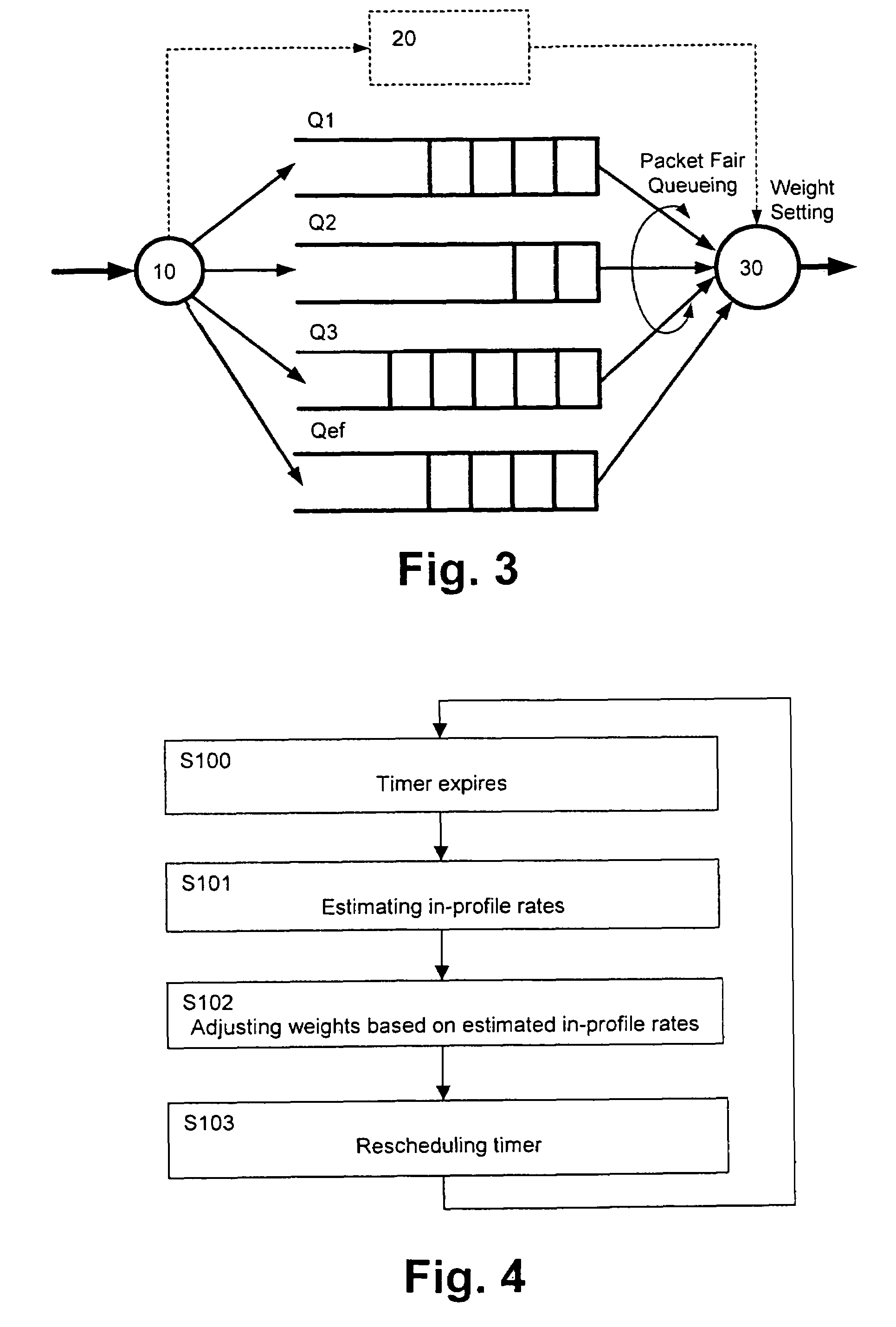
InactiveUS7917648B2FairnessEnsure fairnessSpecial service provision for substationError preventionTraffic capacityDifferentiated services
The present invention relates to a method and network element for scheduling data transmission in a packet data network, e.g. a differentiated services network. Data traffic of a predetermined traffic class is classified based on a predetermined traffic profile, e.g. responsive or non-responsive traffic, and an in-profile rate of the data traffic is estimated. Then, a weight determining a transmit order of queued data packets of said predetermined traffic class is adjusted according to the estimated in-profile rate. Thus, the data traffic is marked into different classes based on the traffic profile and a queue scheduler improves fairness between the classified flows in the packet data network. Thereby, enhanced fairness between traffic profiles can be achieved easily and effectively.
Owner:NOKIA CORP
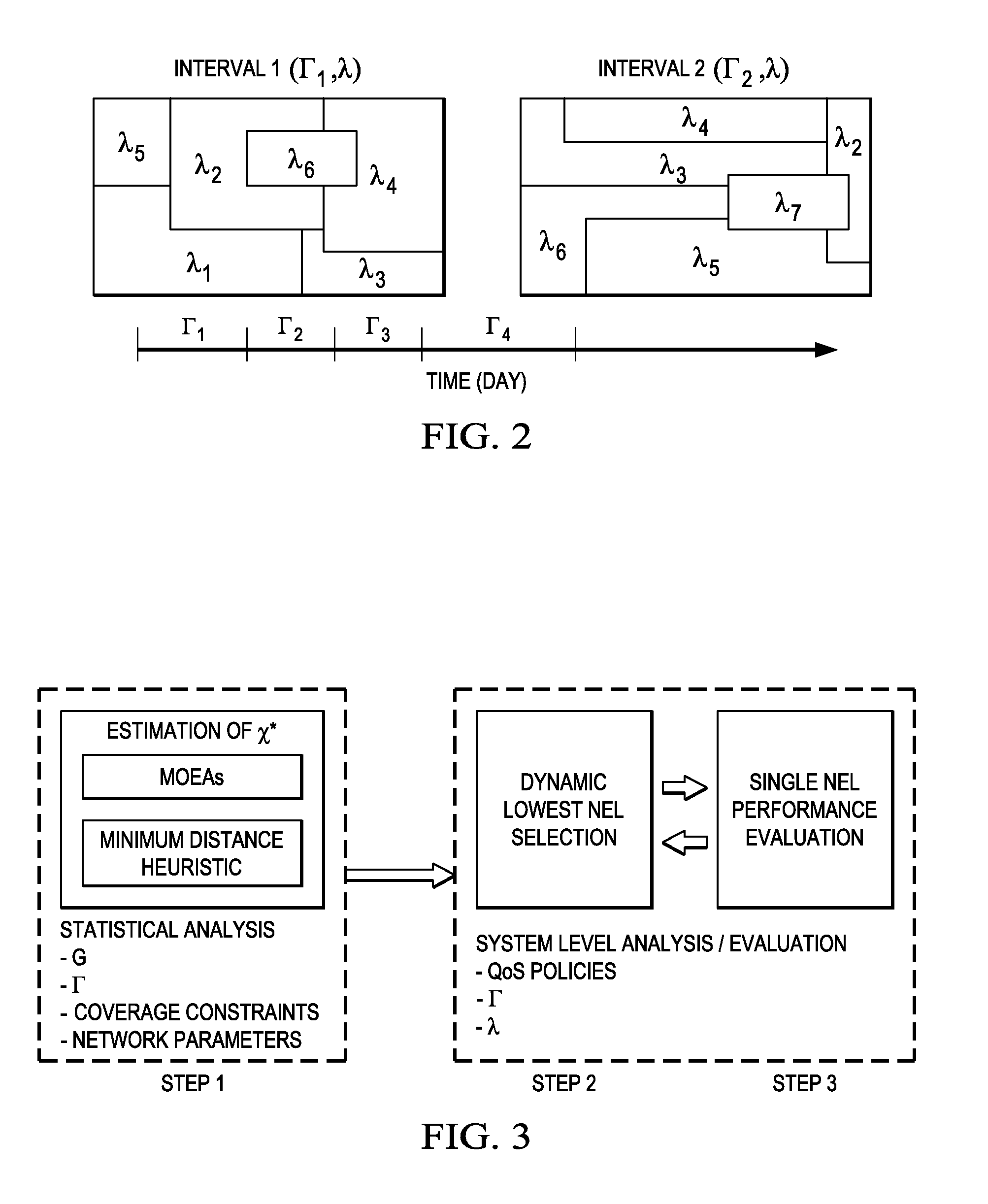
System and Methods for Multi-Objective Cell Switch-Off in Wireless Networks
ActiveUS20150023163A1Reduce network energy levelEasy to usePower managementError preventionQuality of serviceWireless mesh network
Embodiments are provided for a multi-objective scheme for solving a cell switch-off problem. The multi-objective solution seeks to minimize or reduce network energy consumption by switching off some of the cells in the network while allowing enough capacity according to traffic needs and quality of service requirement. An embodiment method includes determining, for each one of a plurality of established traffic profiles, a set of solutions with respect to a number of active cells from a plurality of cells in the network and an aggregate network capacity. The method further includes matching a given traffic profile to one of the established traffic profiles, and evaluating performances of the solutions corresponding to that traffic profile. A solution from the solutions is then selected in accordance with the evaluation. The selected solution indicates which of the cells in the wireless network to be switched off.
Owner:HUAWEI TECH CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com