Patents
Literature
31results about How to "To achieve the purpose of encryption" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Chirp signal-based signal transmitting and receiving method for ultra wide band secret communication
InactiveCN101741414ATo achieve the purpose of confidentialityTo achieve the purpose of encryptionSecuring communicationFourier transform on finite groupsWide band
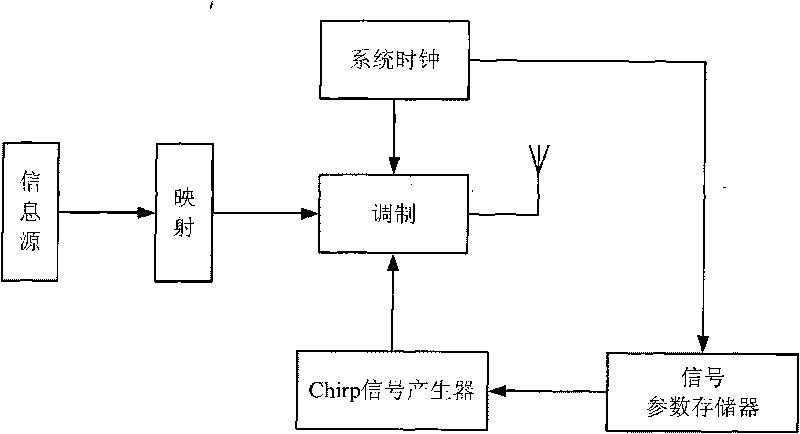
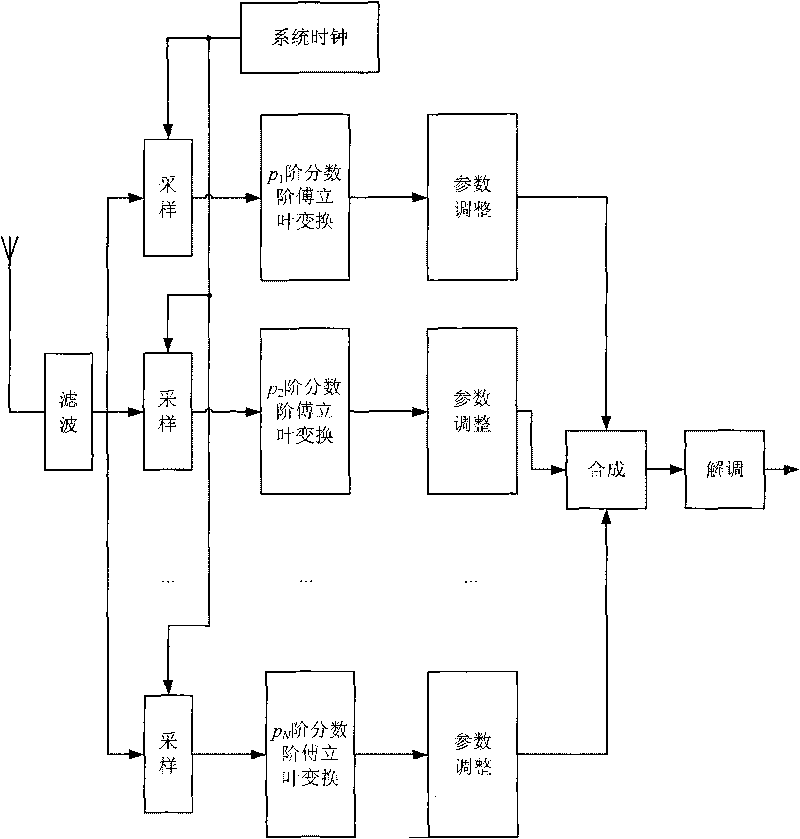
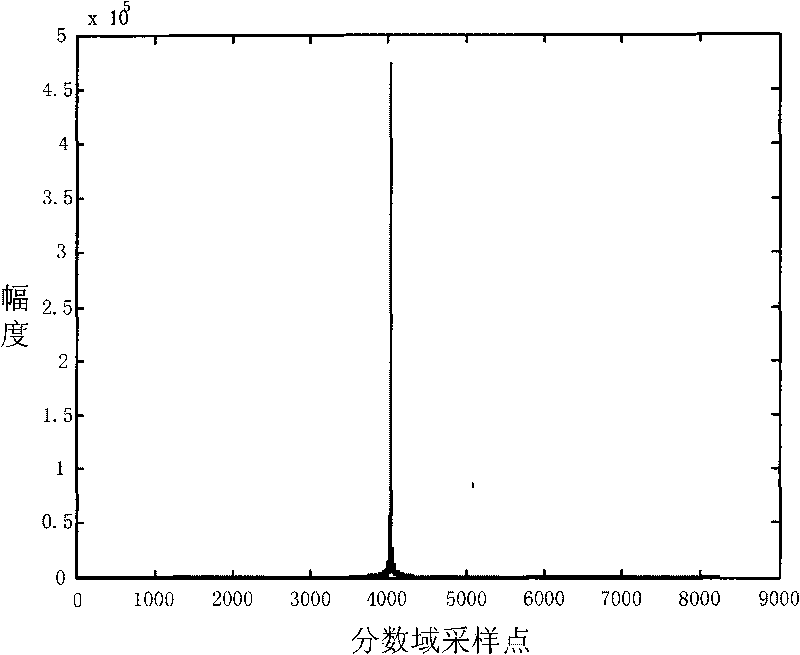
The invention discloses a Chirp signal-based signal transmitting and receiving method for ultra wide band secret communication, which relates to a signal transmitting and receiving method for the ultra wide band secret communication and solves the problem that a conventional communication method cannot ensure the security of communication in the communication. The Chirp signal-based signal transmitting and receiving method for the ultra wide band secret communication comprises a transmitting process and a receiving process, wherein the transmitting process comprises the following steps: mapping digital information output by an information source to obtain binary modulation information, and sending and emitting a pulse signal of a current time according to a set parameter by a modulation Chirp signal generator; and the receiving process comprises the step that: in a system set time, a receiving end samples the ith modulation signal, performs fractional Fourier transform and parameter adjustment on the ith modulation signal, adds and synthesizes the signals to obtain a synthesized signal and demodulates and outputs the synthesized signal. The method is suitable for the process of the ultra wide band secret communication.
Owner:HARBIN INST OF TECH
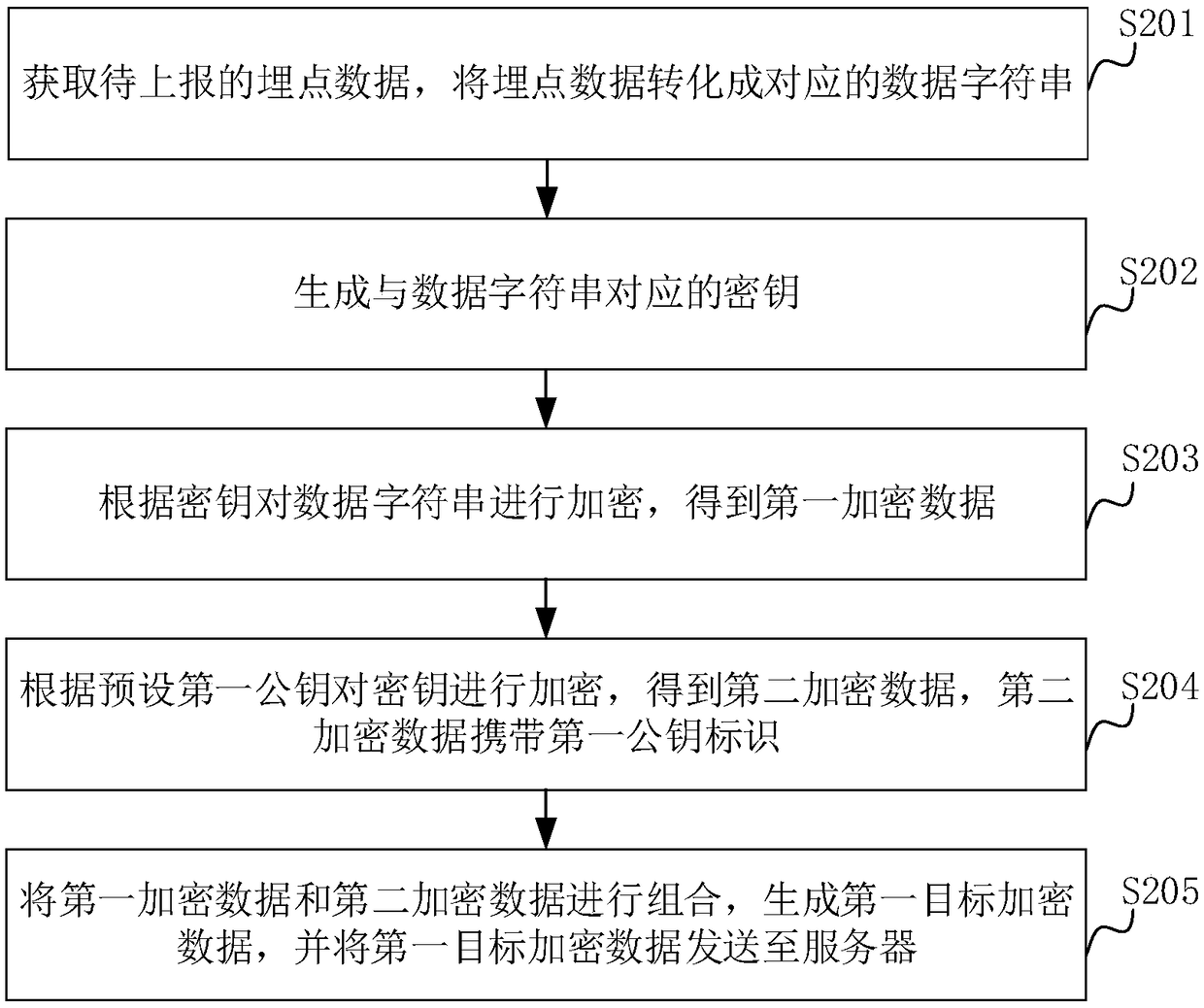
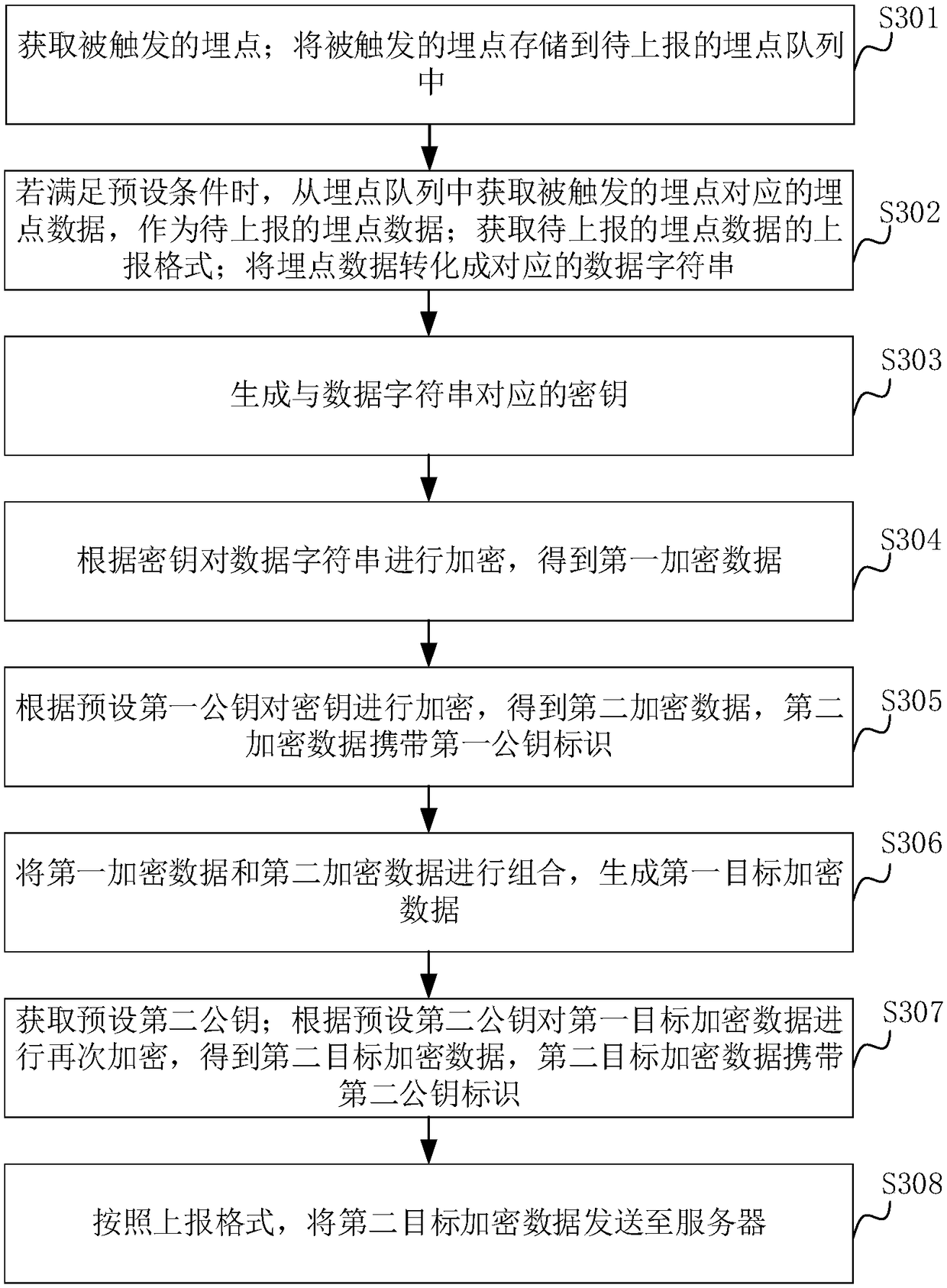
Data encryption reporting method and device and data decryption method and device
ActiveCN109474619AIncrease the difficulty of decryptionImprove securityTransmissionPublic key certificateData transmission
The invention relates to a data encryption reporting method and device and a data decryption method and device. The method comprises the following steps: obtaining buried point data to be reported, and converting the buried point data into a corresponding data string; generating a key corresponding to the data string; encrypting the data string according to the key to obtain first encrypted data;encrypting the key according to a preset first public key to obtain second encrypted data, wherein the second encrypted data carries a first public key identification; combining the first encrypted data and the second encrypted data to generate first target encrypted data, and sending the first target encrypted data to a server. Based on the cryptography technology, the method realizes the purposeof encrypting the buried point data to be reported, ensures the security of data transmission, avoids the data being stolen, and thus improves the security of the data; at the same time, the generated key is encrypted to further improve the security of the data.
Owner:CHINA PING AN PROPERTY INSURANCE CO LTD
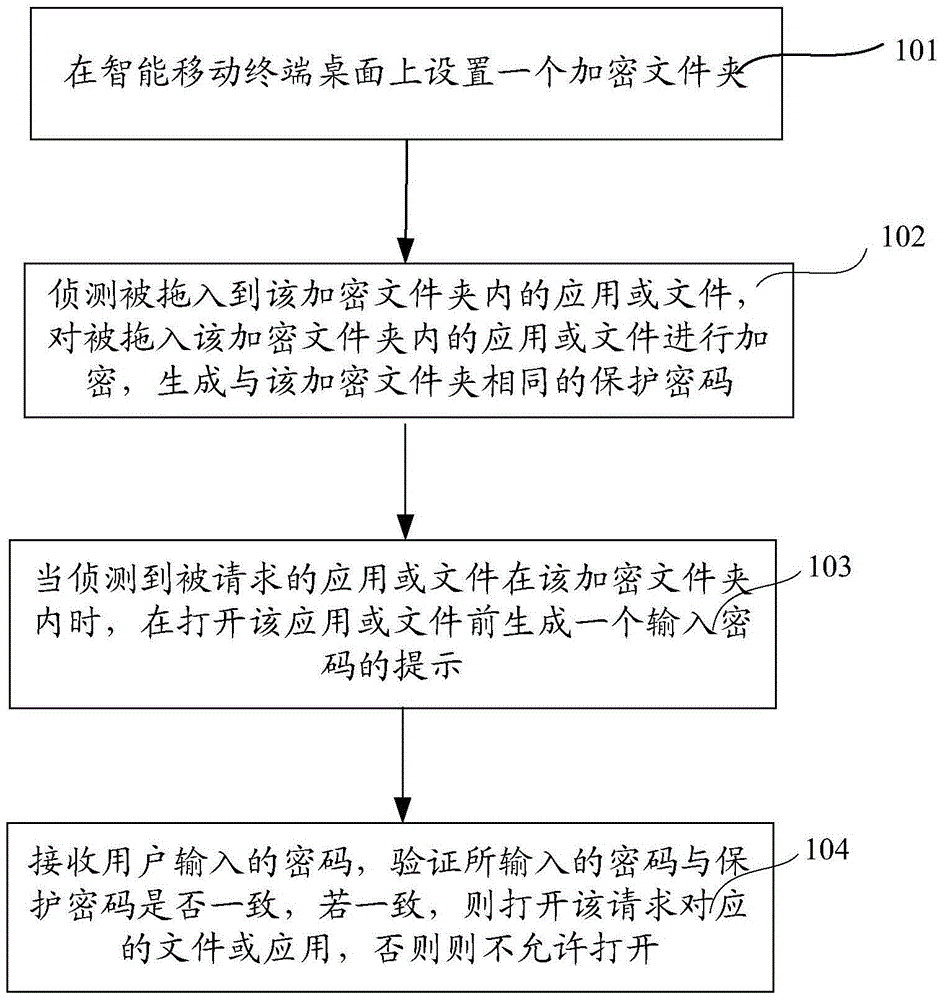
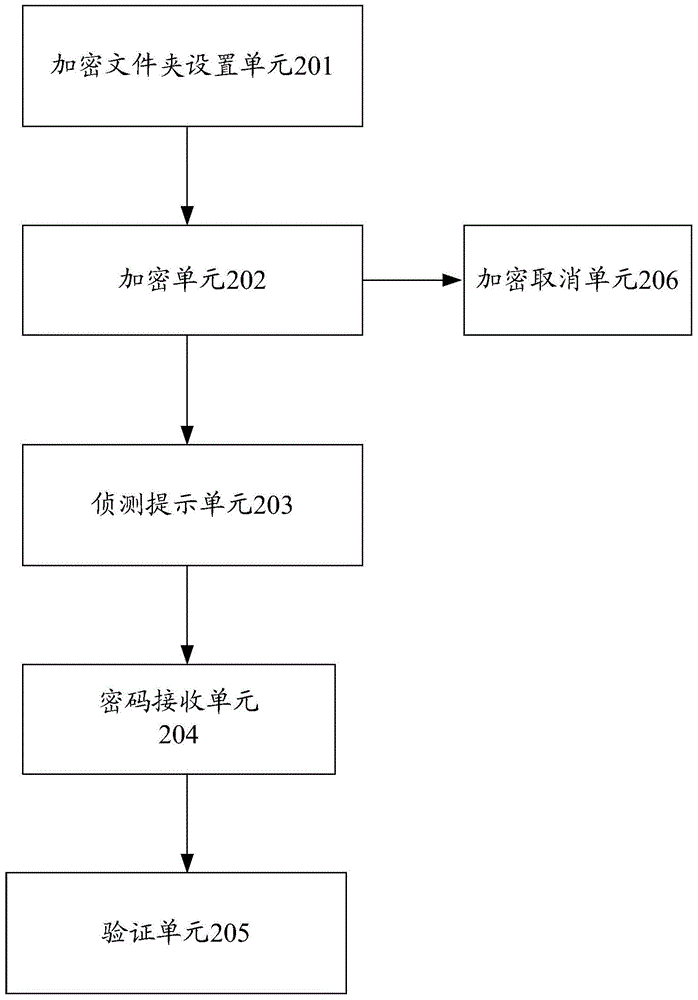
Information encryption method and device
InactiveCN105678186ATo achieve the purpose of encryptionEasy to useDigital data protectionPasswordUser input
The invention discloses an information encryption method and device. The method includes the following steps: step 1, setting an encrypted folder on the desktop of an intelligent mobile terminal; step 2, detecting the application or file, encrypt the application or file dragged into the encrypted folder, and generate the same protection password as the encrypted folder; Step 3, when it is detected that the requested application or file is in the encrypted folder, Generate a password input prompt before opening the application or file; step 4, receive the password entered by the user, verify whether the input password is consistent with the protection password, if they are consistent, open the file or application corresponding to the request, otherwise not It is allowed to be opened, and through the present invention, convenient and effective encryption processing can be performed on the applications or files of the intelligent mobile terminal.
Owner:SHANGHAI DROI TECH CO LTD
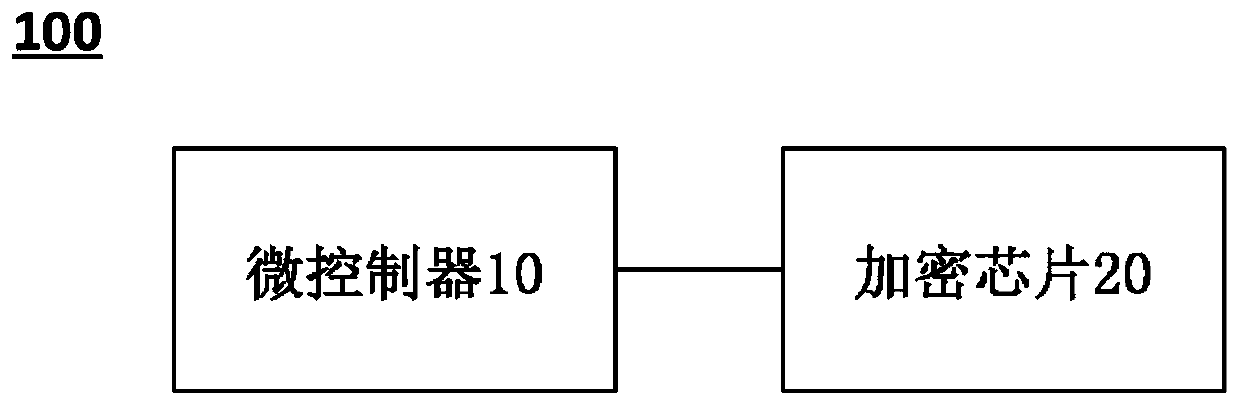
Secure gateway device of vehicle and secure communication method
InactiveCN110427784AImprove securityTo achieve the purpose of encryptionDigital data protectionInternal/peripheral component protectionSecure communicationComputer module
The invention provides a secure gateway device of a vehicle and a secure communication method, and belongs to the field of secure communication. The secure gateway device includes: a microcontroller storing a partial code of a complete program of the secure gateway device, and an encryption chip which stores residual codes which form the complete program together with the partial codes, so that anexternal module needs to be authorized by the encryption chip to read the complete program when accessing the secure gateway device. The invention also provides a secure communication method appliedto the secure gateway device. According to the secure gateway device and the secure communication method, the communication security of the gateway of the vehicle can be improved.
Owner:ZHEJIANG GEELY NEW ENERGY COMML VEHICLES CO LTD +2
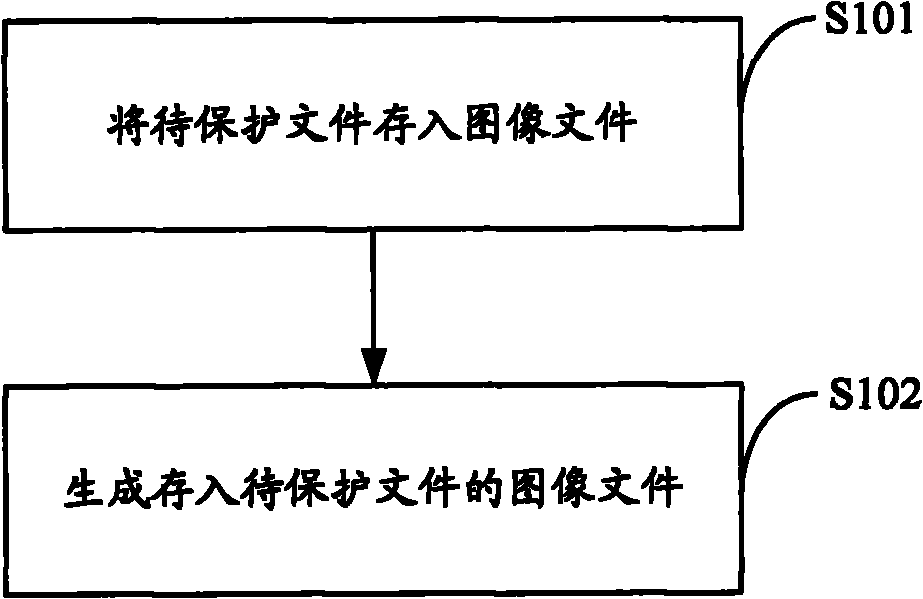
File encryption protection method and device
InactiveCN102156842ANot easy to compileNot easy to stealDigital data protectionComputer softwareEncryption
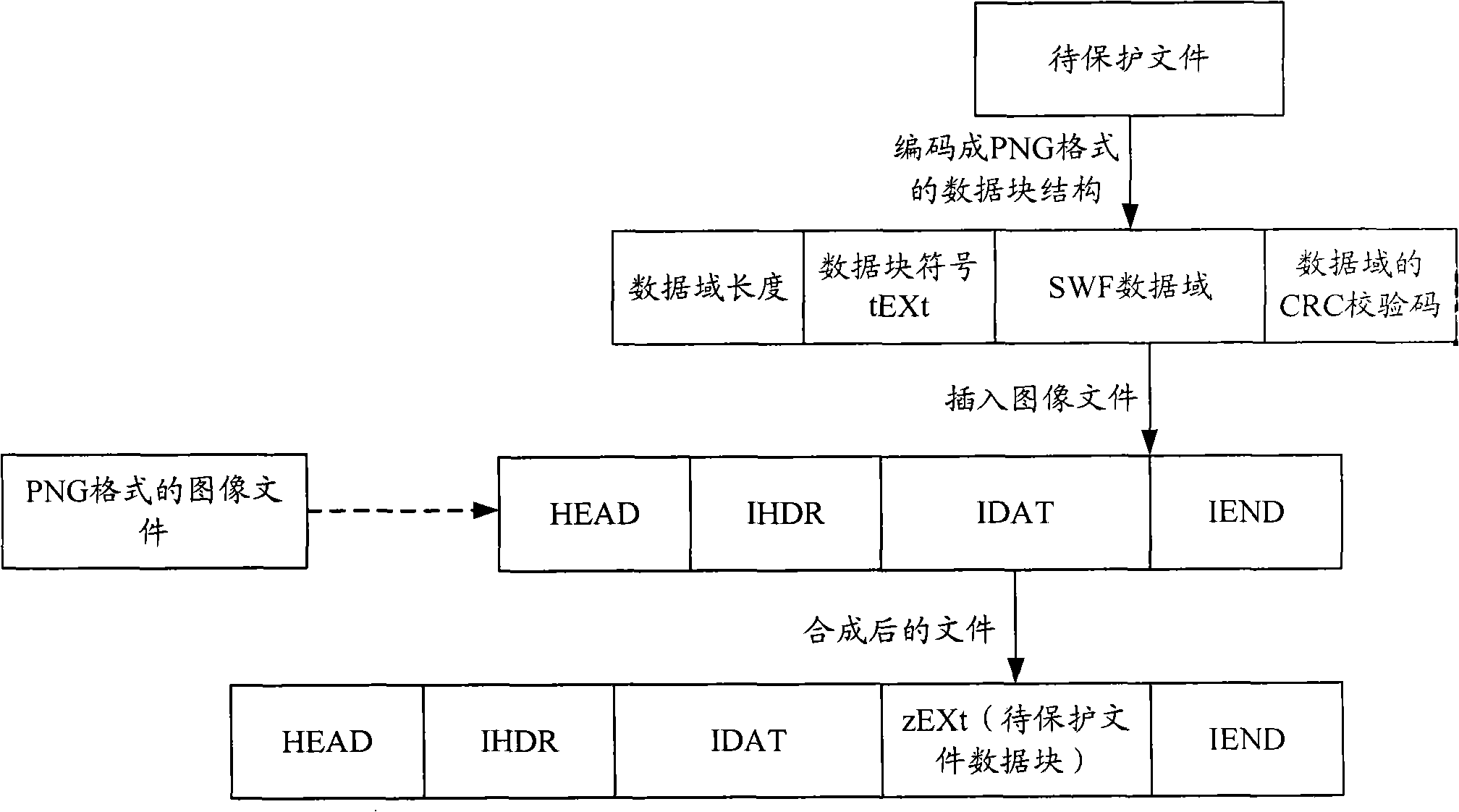
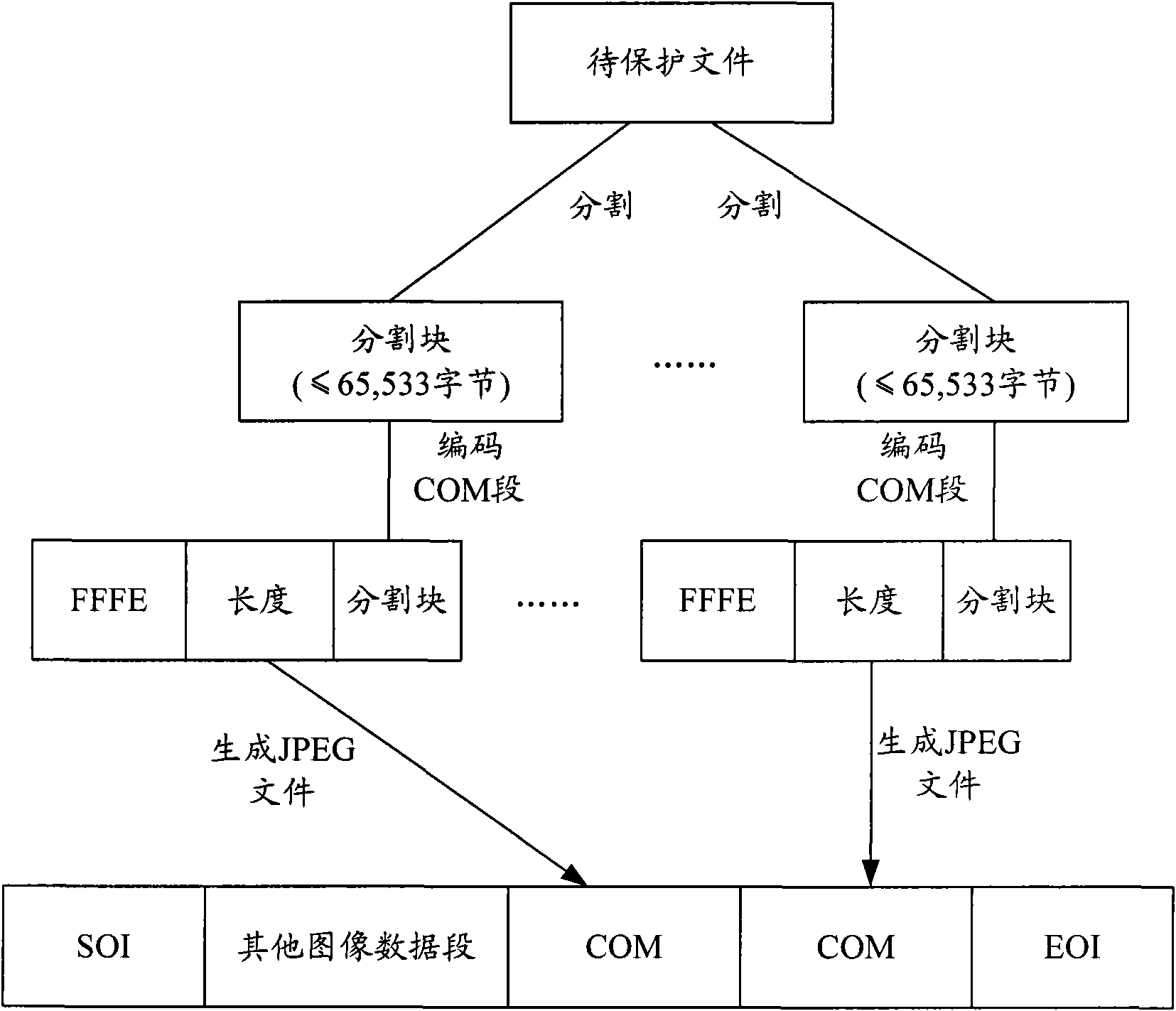
The invention is applied in the field of computer software, and provides a file encryption protection method and a file encryption protection device. The method comprises the following steps of: storing a file to be protected into an image file; and generating the image file stored with the file to be protected. According to the embodiment, by storing the file to be protected such as a resource file or the like into the image file, the file to be protected is not easily compiled or embezzled; and if the image file is not decoded, only a picture is seen, so the purpose of encrypting the file to be protected can be well fulfilled.
Owner:TENCENT TECH (SHENZHEN) CO LTD
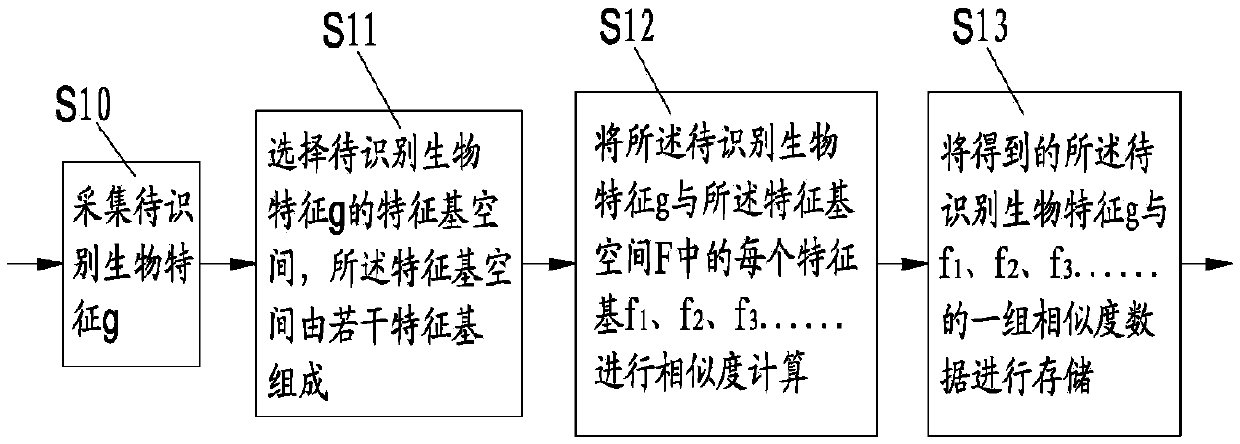
Encryption method of biological feature, encryption matching method and encryption system, and encryption matching system
ActiveCN105847003ATo achieve the purpose of encryptionAvoid demandUser identity/authority verificationData setCiphertext
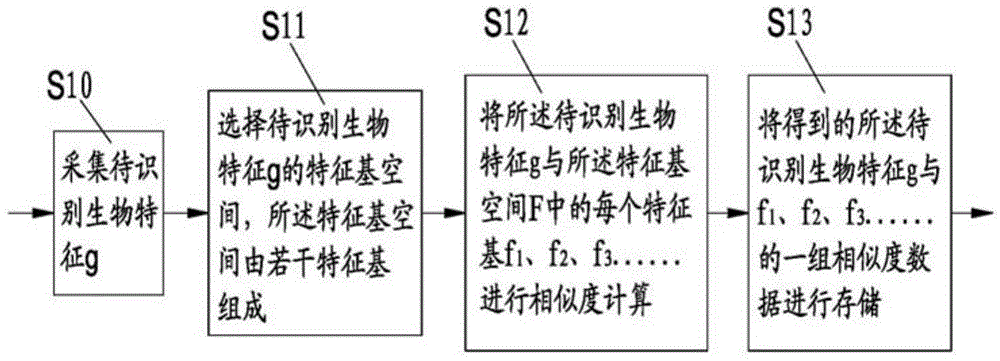
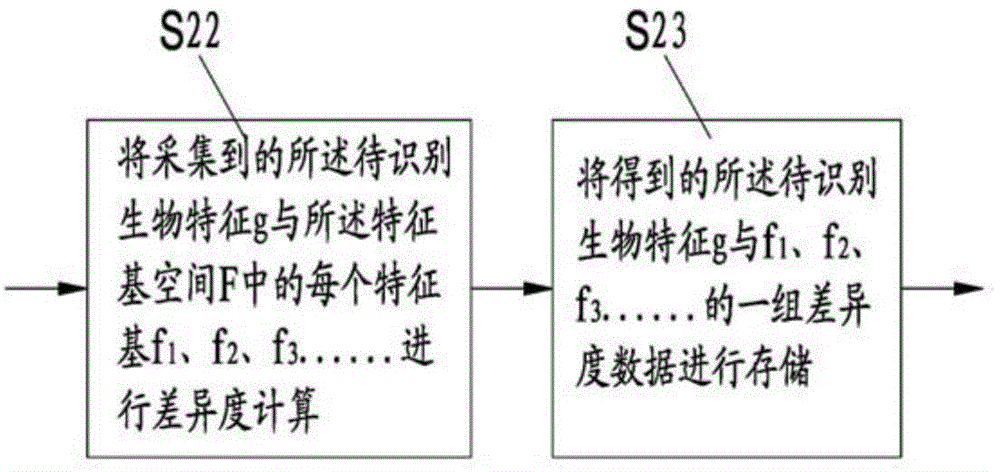
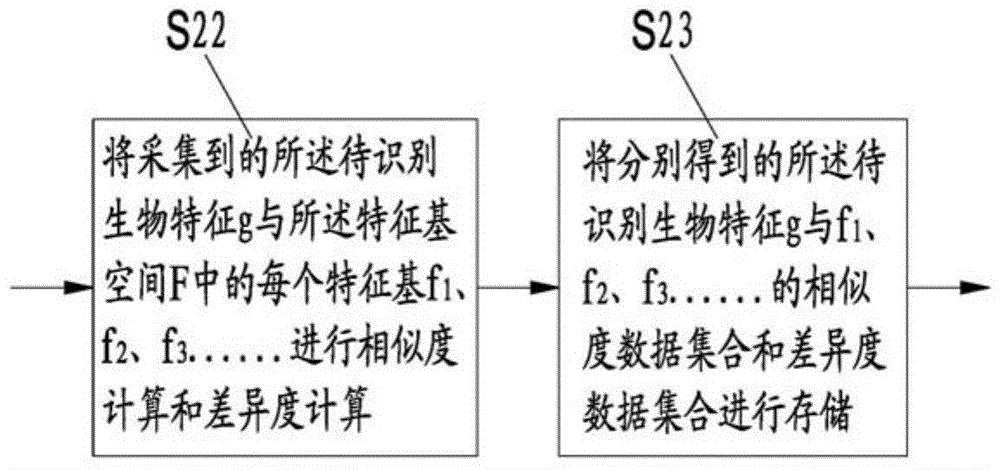
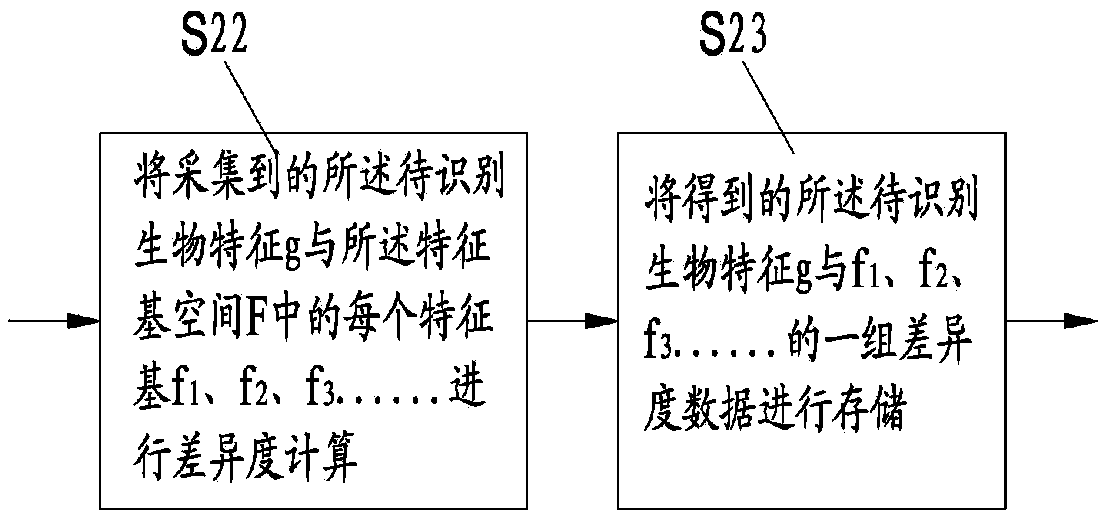
The invention discloses an encryption method of biological features, an encryption matching method and an encryption system, and an encryption matching system. The encryption method comprises the following steps: respectively computing similarity and / or difference of a to be identified biological feature with each feature base in N feature base spaces to obtain a corresponding data set, thereby realizing the encryption on the biological feature; respectively computing the similarity and / or the difference of two to be identified biological features with each feature base in the feature base space, comparing the computing result in the one-to-one correspondence, thereby realizing the matching of two to be identified biological features. The to be identified biological feature is converted into a group of abstract code data, the group of code data supports the one-way encrypted storage, the matching of the biological feature based on the code data or the cipher text is realized, the requirement of the clear text of the biological feature is avoided, and the security of the biological feature on the identification is guaranteed.
Owner:渭南印象认知技术有限公司
Database authority management and data protection method and device, equipment and storage medium
ActiveCN114840521ARealize the dataAchieve protectionRelational databasesDigital data protectionData contentData storage system
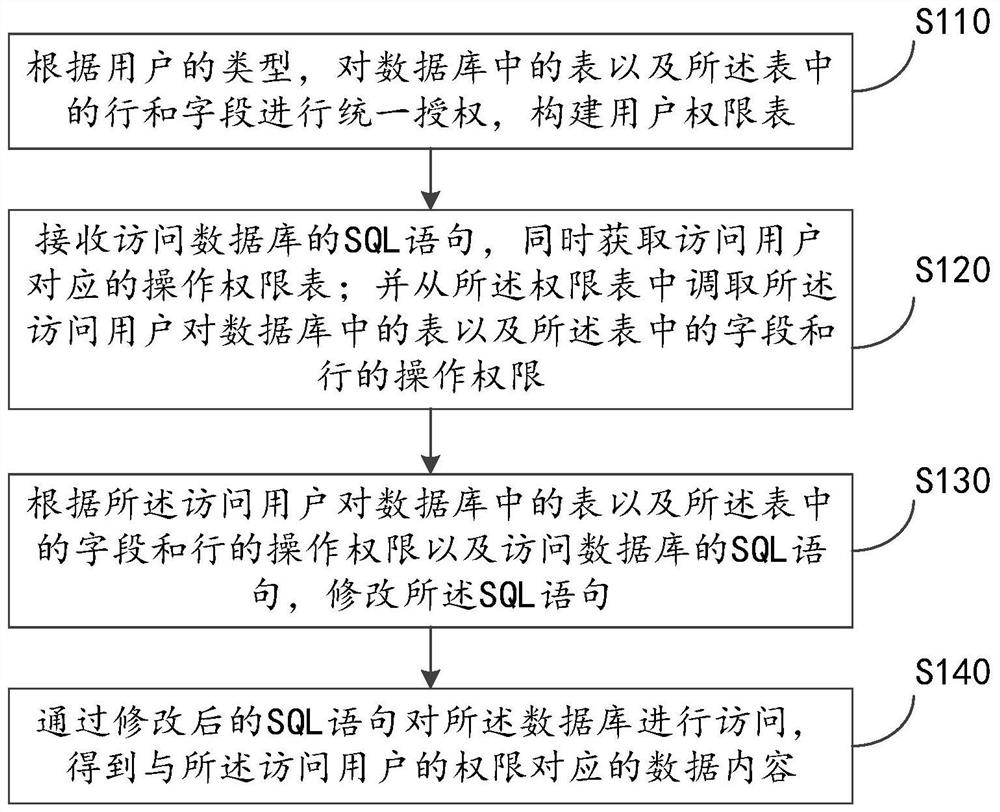
The embodiment of the invention provides an authority management and data protection method and device applied to a database, equipment and a computer readable storage medium. The method comprises the following steps: according to the type of a user, performing unified authorization on a table in a database and rows and fields in the table, and constructing a user permission table; receiving an SQL statement of an access database, and obtaining an operation authority table corresponding to an access user at the same time; calling an operation authority of the access user on a table in a database and a field and a row in the table from the authority table; modifying an SQL (Structured Query Language) statement according to the operation authority of the access user on a table in a database, a field and a row in the table and the SQL statement accessing the database; and accessing the database through the modified SQL statement to obtain data content corresponding to the authority of the access user. In this way, the authority of the physical data storage system is improved, and data protection can be achieved without modifying the data content of the physical data storage system.
Owner:BEIJING YOYO TIANYU SYST TECH
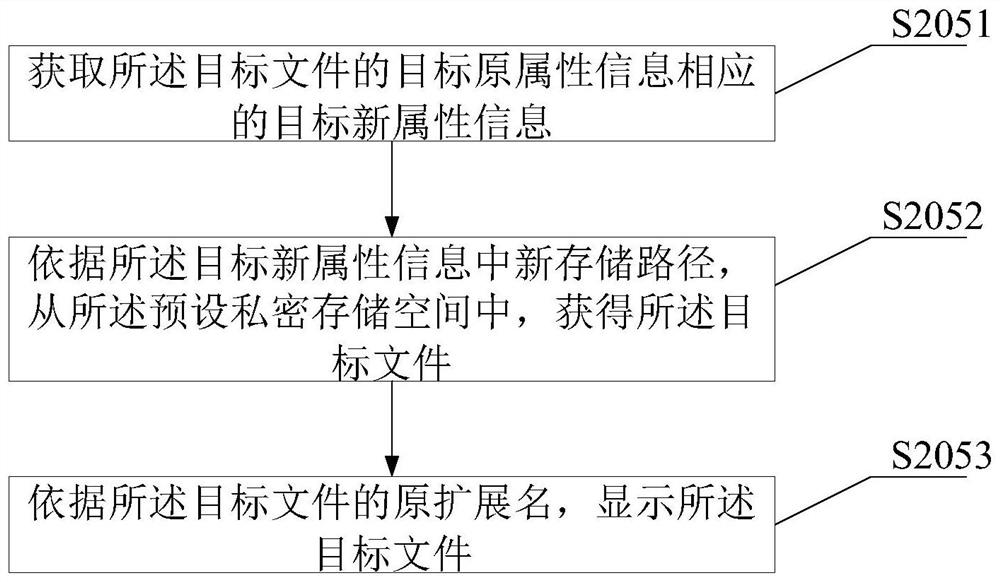
Encryption method, application lock and electronic equipment
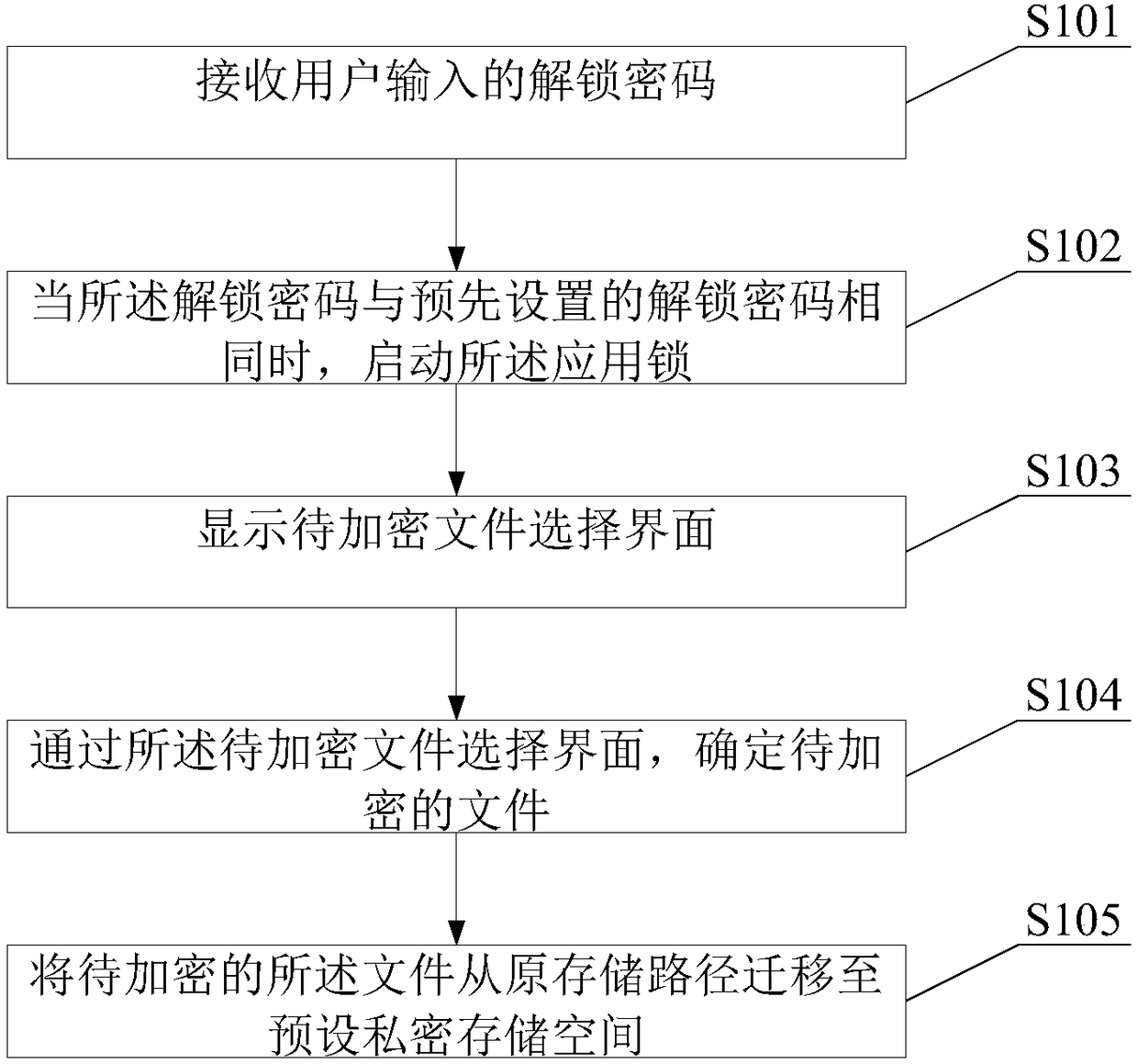
ActiveCN108573161ATo achieve the purpose of encryptionDigital data protectionDigital data authenticationApplication softwareComputer hardware
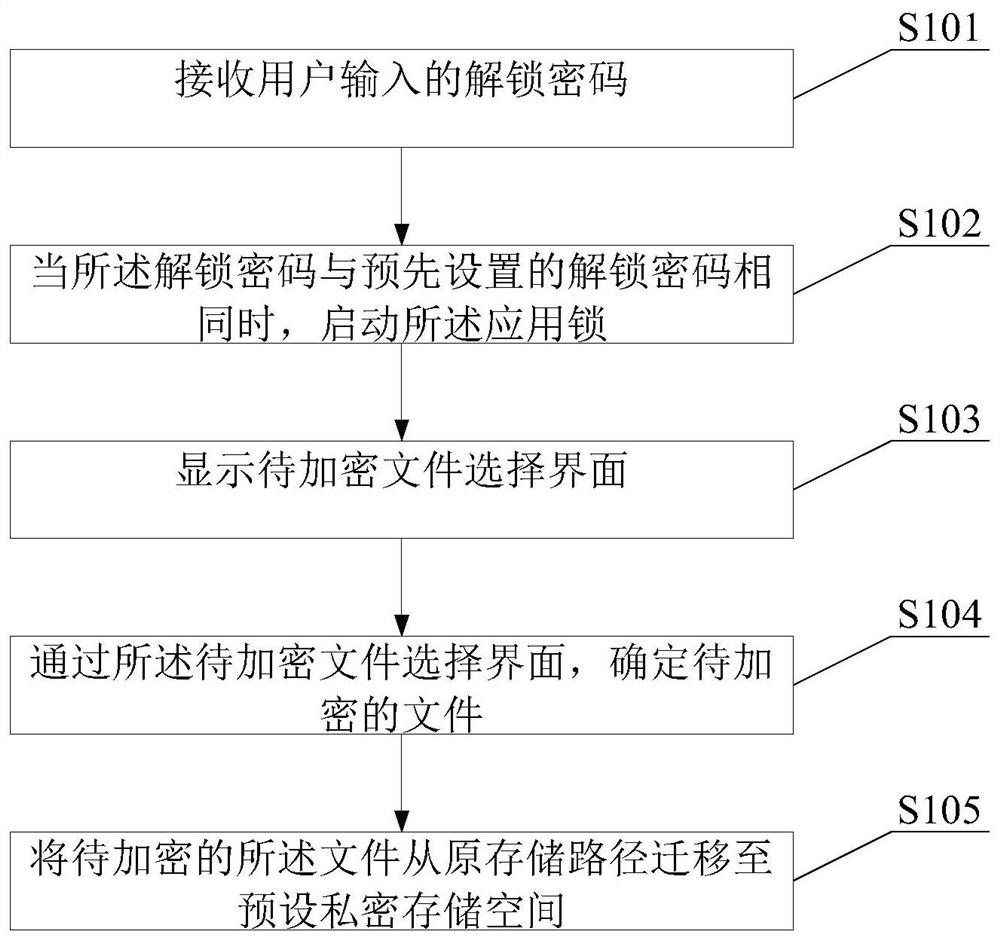
The invention provides an encryption method, an application lock and electronic equipment. The encryption method comprises the steps of receiving an unlock password input by a user, unlocking the application lock when the unlock password input by the user is identical to a preset unlock password, and displaying a to-be-encrypted file selection interface; determining a to-be-encrypted file throughthe to-be-encrypted file selection interface; migrating the to-be-encrypted file to a preset private storage space from an original storage path. In this way, the to-be-encrypted file is migrated to the preset private storage space from the original storage path without encrypting a whole application program storing the to-be-encrypted file, and therefore the purpose of encrypting one or more files separately is achieved.
Owner:北京贝塔科技有限公司
Data encryption transmission method
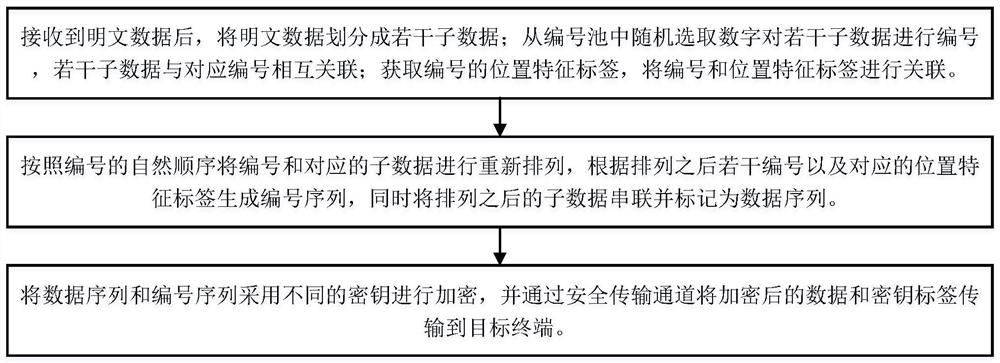
PendingCN114338217ATo achieve the purpose of encryptionImprove securityMultiple keys/algorithms usagePlaintextTheoretical computer science
The invention discloses a data encryption transmission method, relates to the technical field of data encryption, and solves the technical problem of low data encryption and transmission security caused by adopting a fixed key to encrypt and decrypt data in the prior art. The plaintext data is divided into a plurality of sub-data according to the set unit quantity, the plurality of sub-data are numbered, the number and the corresponding sub-data are reordered according to the natural sequence, the number sequence and the data sequence are obtained, the number sequence and the data sequence are encrypted through different secret keys, and the purpose of data encryption is achieved. The safety of the data is improved through double encryption; according to the method, before the numbers and the corresponding sub-data are reordered, the position feature tags corresponding to the numbers are obtained, the reference nodes are randomly selected, and the reference nodes can be quickly determined according to the number sequence; according to the invention, the data cracking difficulty is improved, and the data security is further ensured.
Owner:NANYANG INST OF TECH
Moire fringe anti-counterfeiting method for improving anti-counterfeiting information concealment
InactiveCN108521536ATo achieve the purpose of encryptionEasy extractionPictoral communicationPattern recognitionEncryption
The invention discloses a Morie fringe anti-counterfeiting method for improving anti-counterfeiting information concealment. The method comprises the following steps: (1) preparing an original drawingand anti-counterfeiting information; (2) performing half-tone processing; (3) encrypting the anti-counterfeiting information; and (4) synthesizing an image. Through the method disclosed by the invention, the selection range of each of the original drawing and the anti-counterfeiting information is greater, the encryption and decoding are realized in the image, and the concealment and the extraction recognition performance are strong.
Owner:合肥博之泰电子科技有限公司
Biological feature recognition method, device and system for privacy protection and electronic equipment
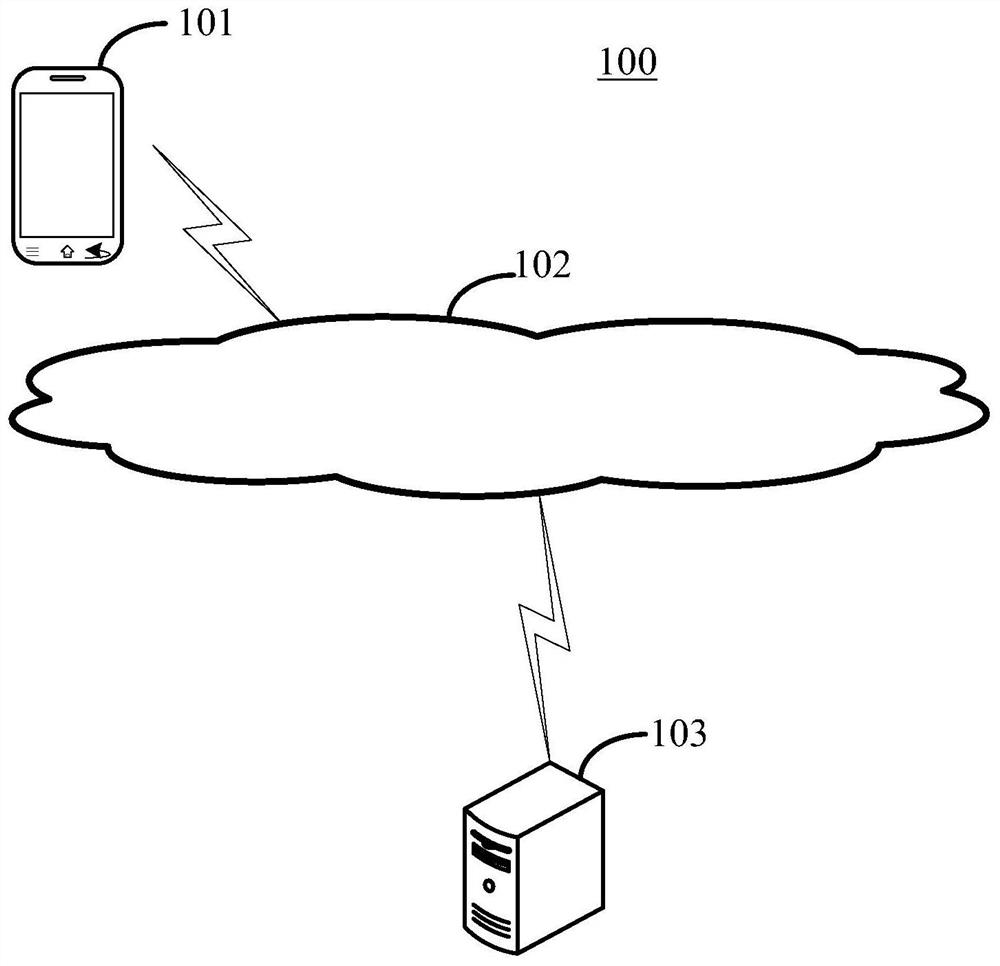
PendingCN111783965ATo achieve the purpose of encryptionImprove securityDigital data protectionNeural architecturesPrivacy protectionEngineering
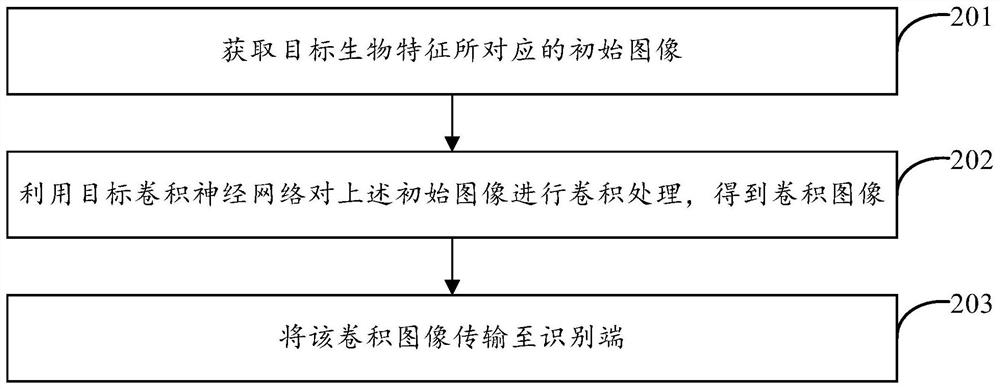
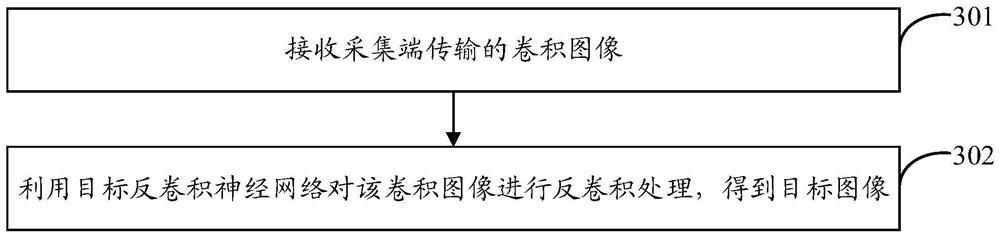
The embodiment of the invention provides a biological feature recognition method, device and system for privacy protection and electronic equipment. According to one specific implementation mode, themethod comprises the steps: acquiring an initial image corresponding to a target biological feature; performing convolution processing on the initial image by using a target convolution neural networkto obtain a convolution image; transmitting the convolution image to an identification end to enable the identification end to perform deconvolution processing on the convolution image by using a target deconvolution neural network to obtain a target image used for biological feature identification. A distance value between the convolution image and the initial image is greater than a first threshold; and the distance value between the target image and the initial image is smaller than a second threshold value.
Owner:ALIPAY (HANGZHOU) INFORMATION TECH CO LTD
Method and device for encrypting and decrypting picture
InactiveCN109033863AFast encryptionTo achieve the purpose of encryptionDigital data protectionProgram/content distribution protectionComputer hardwareComputer science
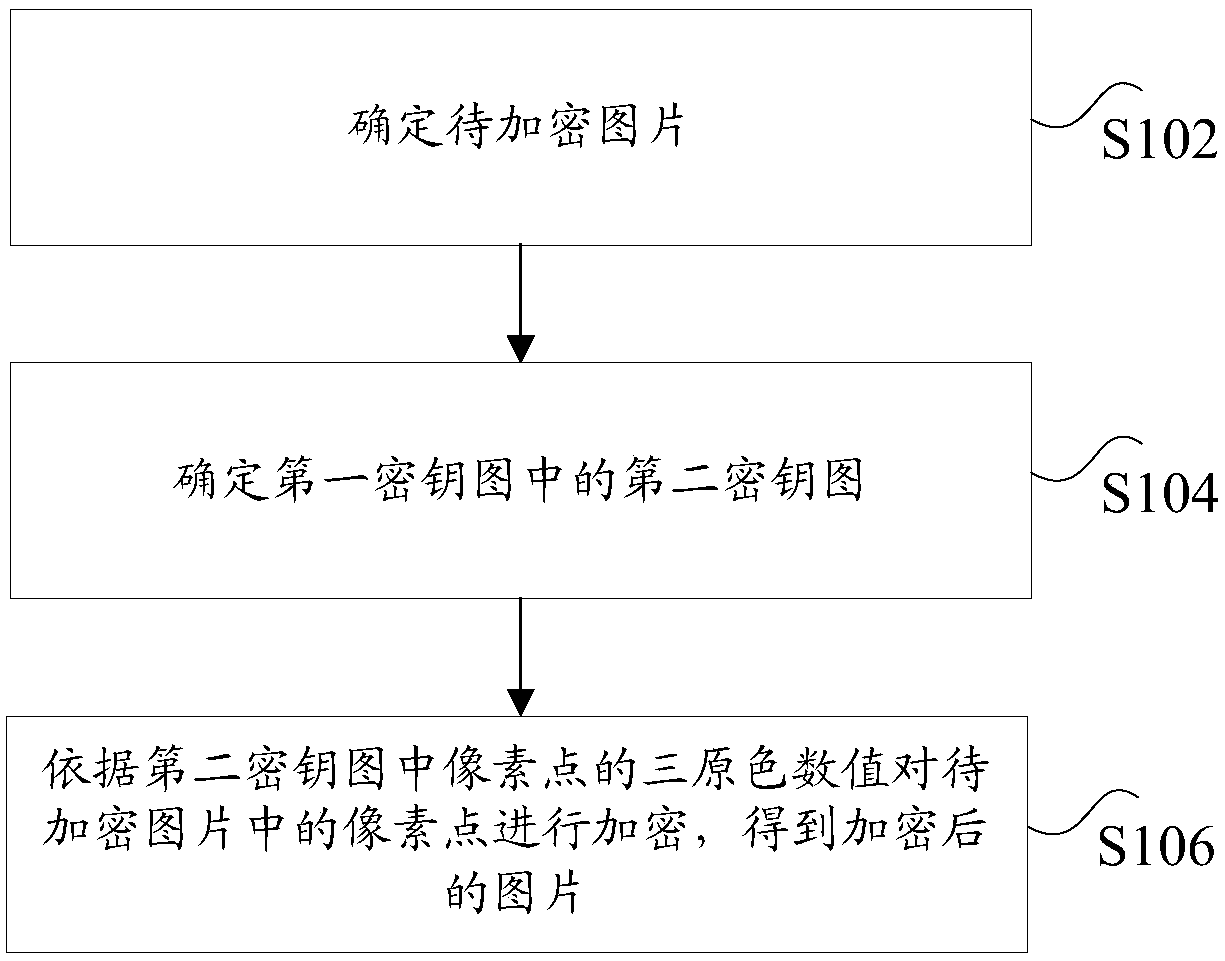
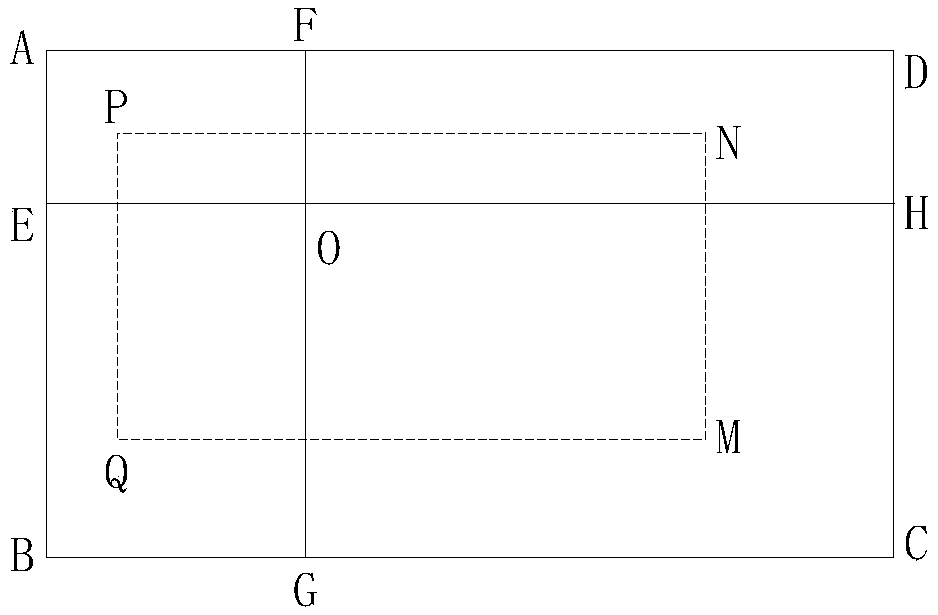
The present application discloses a picture encryption and decryption method and apparatus. The method comprises the following steps: determining a picture to be encrypted; determining a second key map in the first key map, wherein the first secret key map is used for encrypting a picture to be encrypted by the three primary color values of pixel points in the first secret key map, the second secret key map is a first rectangular area formed by taking a designated point in the first secret key map as a vertex of the first rectangular area and taking a length and a width of the picture to be encrypted as a length and a width of the first rectangular area; the pixel points in the picture to be encrypted are encrypted according to the three primary color values of the pixel points in the second secret key map to obtain the encrypted picture. The present application solves a technical problem of picture information disclosure due to a lack of effective picture encryption means.
Owner:GUANGZHOU SHIYUAN ELECTRONICS CO LTD
Login encryption method
InactiveCN103312709AImplement encryptionEasy to crackDigital data authenticationTransmissionPasswordCryptogram
The invention belongs to the field of information technology and particularly relates to a login encryption method. The method includes the steps of selecting an original information file, placing the file, setting a password, and allowing a user to log in. The login encryption method has the advantages that the problems that login is cracked easily and input information is difficult to memorize in the prior art are solved; less content needs to be memorized by users, and login is simpler and safer.
Owner:ZHENGZHOU UNIVERSITY OF AERONAUTICS
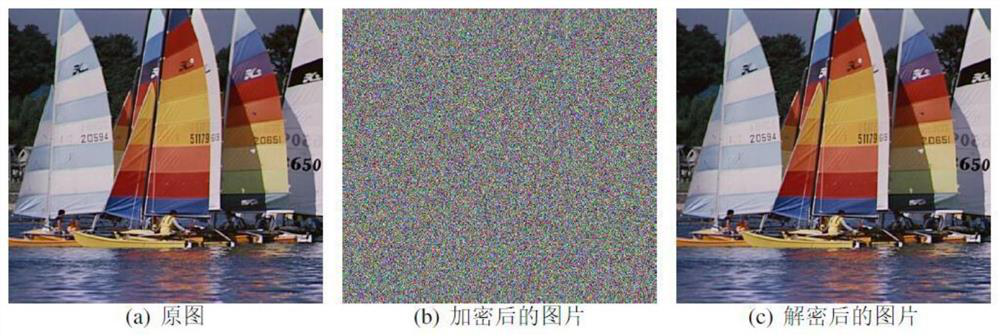
Image encryption and decryption method based on novel two-dimensional fractional order chaotic mapping
ActiveCN114401351AComplex structureIncreased complexitySecuring communication by chaotic signalsHigh level techniquesKey spaceAlgorithm
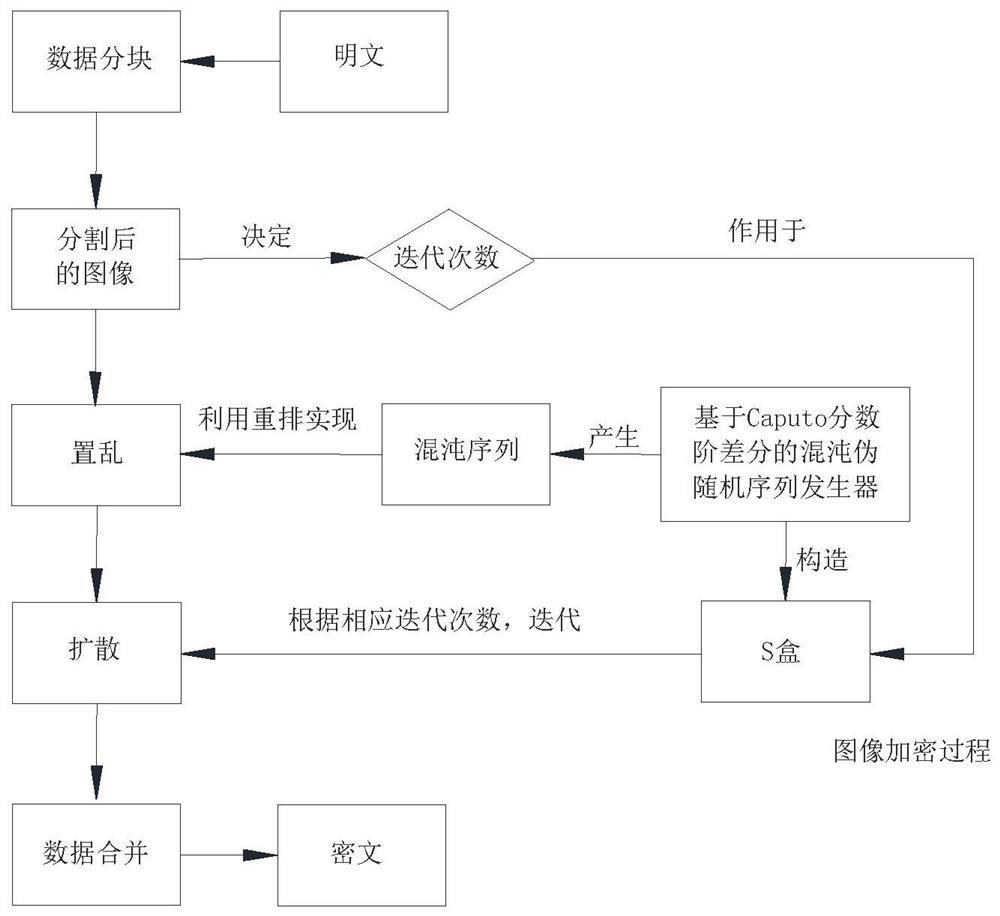
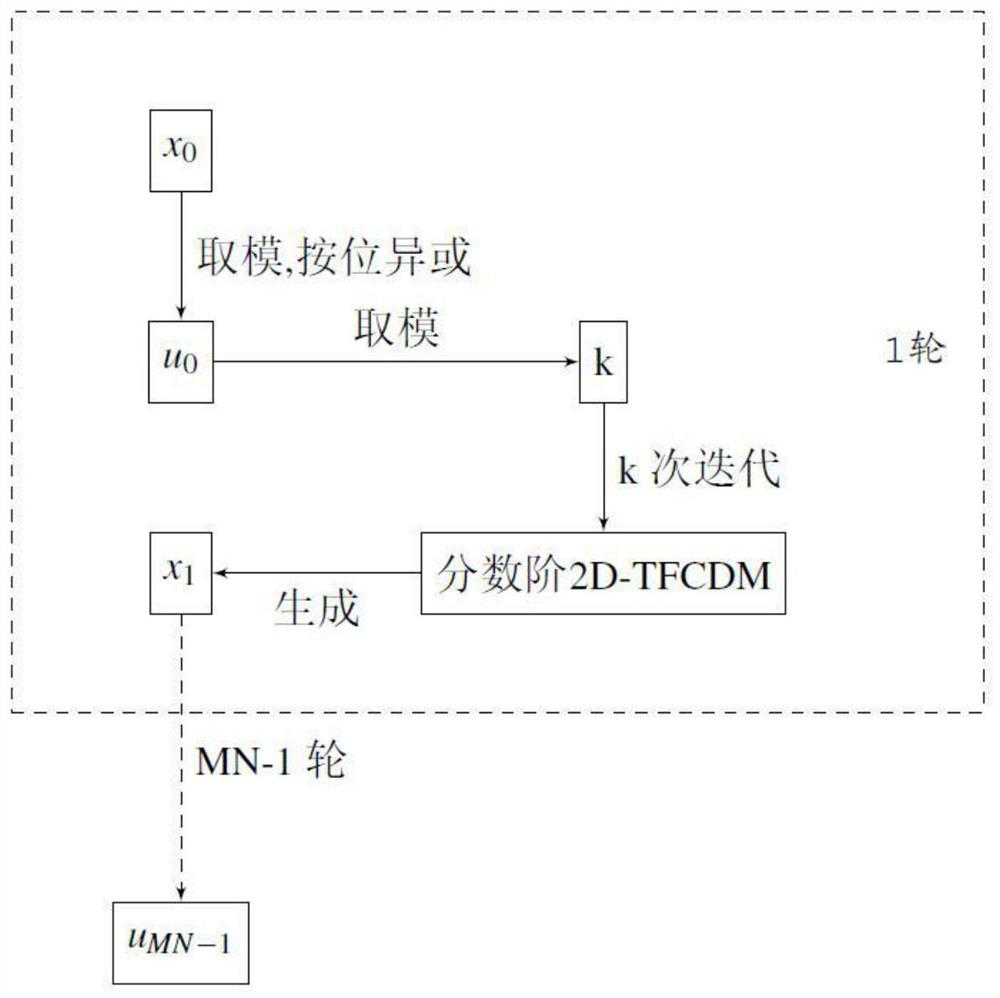
The invention discloses an image encryption and decryption method based on novel two-dimensional fractional order chaotic mapping, and the method is characterized in that during encryption, S1, a fractional order chaotic signal is generated; s2, scrambling the original image by using the fractional order chaotic signal; s3, selecting a secret key image, and encrypting the scrambled image pixel value by using the fractional order chaotic signal and the secret key image; during decryption, I, the pixel value of the encrypted image is decrypted by using the chaotic signal sequence and the secret key image; and II, recovering the pixel position of the encrypted image by using the chaotic signal sequence. Fractional order two-dimensional TFCDM chaotic mapping is used for generating a chaotic sequence, then discrete chaotic signals are used for scrambling image pixels and diffusing pixel values for encryption, the discrete chaotic signals generated by a new mapping formula are more complex in structure and higher in randomness, the complexity of an encryption algorithm is higher, the fractional order is added as a secret key, and the encryption efficiency is improved. The algorithm has the advantages of larger key space, higher attack resistance and higher security.
Owner:NORTHWEST A & F UNIV
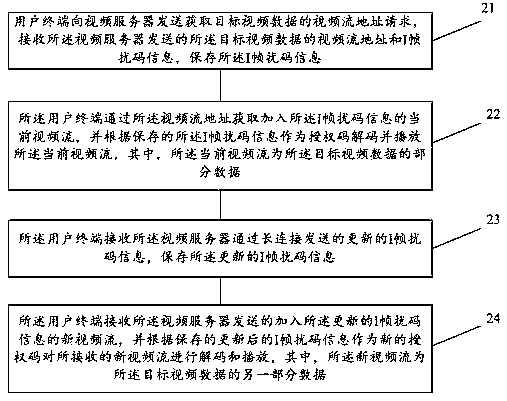
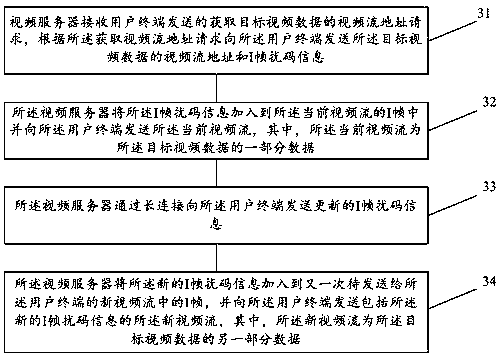
Method and device for protecting security of video data and computer storage medium
PendingCN110730365ATo achieve the purpose of encryptionTo achieve the purpose of anti-theftSelective content distributionTelecommunicationsAuthorization
The embodiment of the invention provides a method and device for protecting security of video data and a computer storage medium. A user terminal sends a video stream address request for obtaining target video data to a video server, receives a video stream address and I-frame scrambling code information of the target video data sent by the video server, and stores the I-frame scrambling code information, wherein the I-frame scrambling code information is used for scrambling an I frame in a video stream; and the user terminal acquires a current video stream added with the I-frame scrambling code information through the video stream address, and decodes and plays the current video stream by taking the stored I-frame scrambling code information as an authorization code, and the current videostream is a part of data of the target video data. According to the method and device for protecting the security of the video data and the computer storage medium, the scrambling code information isadded based on the video key frame I-Frame to achieve the purpose of video encryption, and effective theft prevention can be achieved.
Owner:SHANGHAI SUMI TECH CO LTD
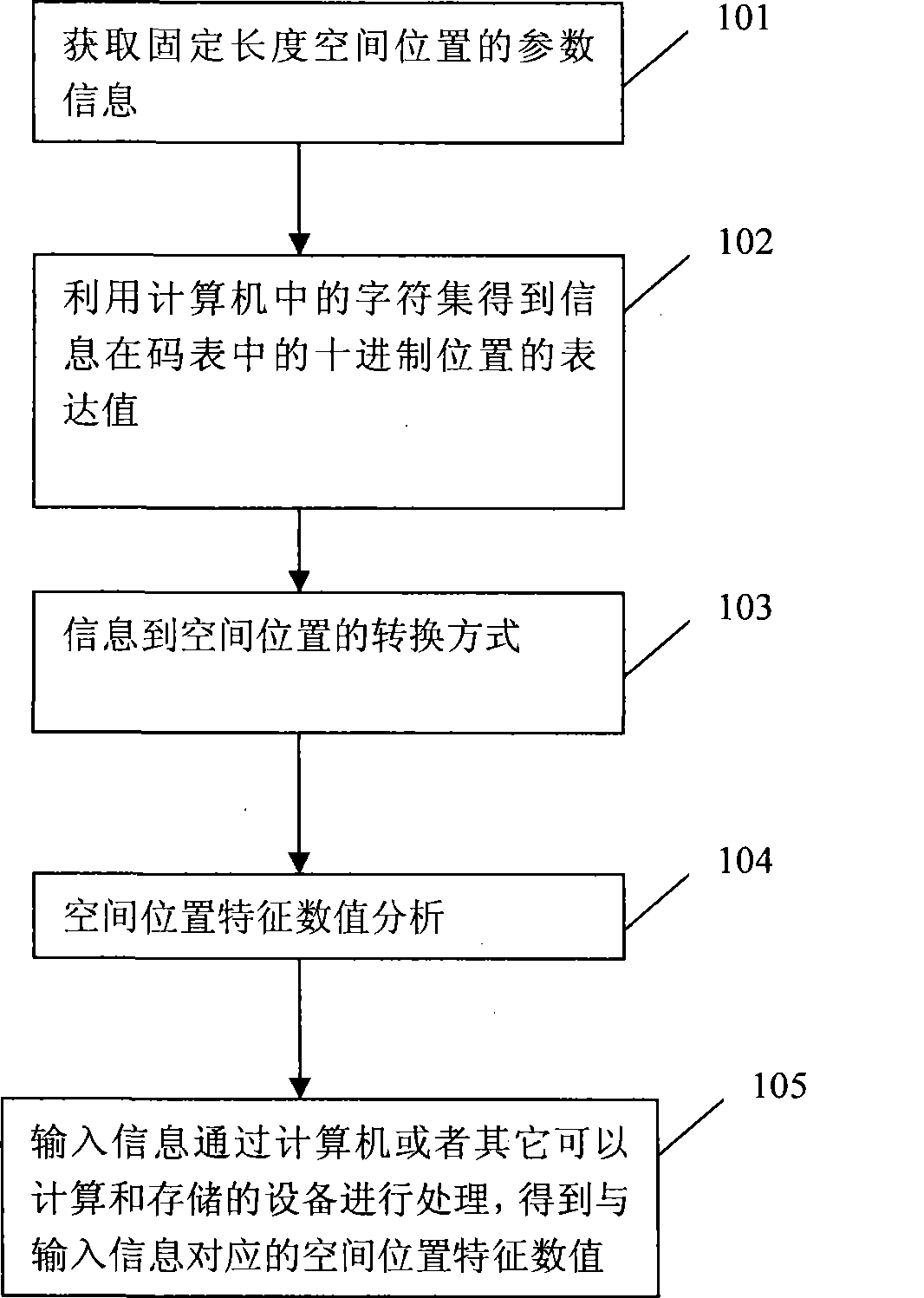
Method for extracting spacial position feature value of fixed length from information
InactiveCN101499900AAchieve restorationTo achieve the purpose of encryptionEncryption apparatus with shift registers/memoriesAlgorithmTransfer procedure
The invention relates to a method used for extracting fixed-length spatial location characteristic numerals from information in the information security techniques, which comprises the following steps: parameter information of a fixed-length spatial location is obtained; decimal expression values of the information in a code table are obtained by a symbol set in a computer; a converting method from the information to the spatial location is obtained; the fixed-length spatial location characteristic numerals are analyzed; and the input information is processed by the computer or other equipments with computing and storing functions, thus obtaining the spatial location characteristic numerals which are corresponding to the input information. The method can simply, intuitively and efficiently extract the unique fixed-length spatial location characteristic numeral which are corresponding to the information from the information; by the method, the same effect can be achieved by judging the spatial location characteristic numerals when the user judges whether the information is modified in a transmission process; and as the spatial location characteristic numerals have fixed length and certain regularity, the efficiency is greatly improved, when the processing of the information including encryption, identification and judgement is carried out, and the method has strong practicability.
Owner:北京乾坤化物数字技术有限公司
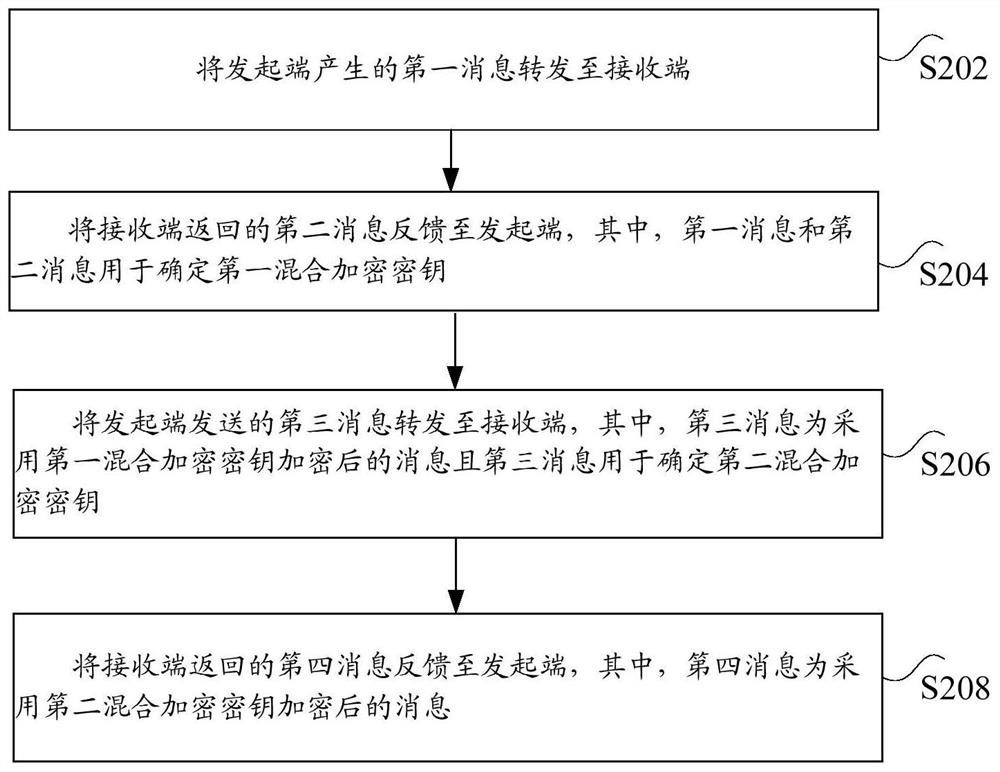
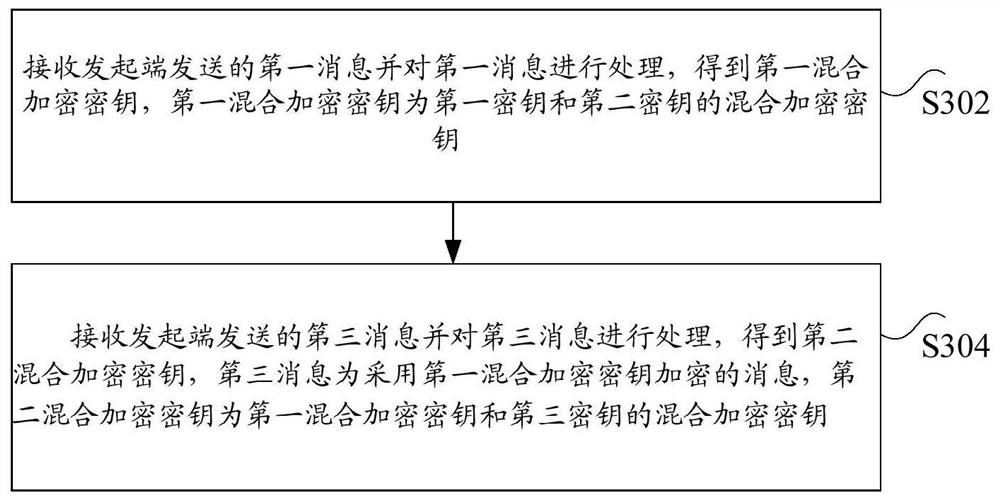
Communication link establishment method and device, storage medium, processor and system
ActiveCN113300832AImplement multiple encryptionTo achieve the purpose of encryptionKey distribution for secure communicationEngineeringCommunication link
The invention discloses a communication link establishment method and device, a storage medium, a processor and a system. The method comprises a secret key negotiation process, the negotiation process is used for determining an encryption secret key, and the negotiation process comprises the following steps: forwarding a first message generated by an initiating end to a receiving end; feeding back a second message returned by the receiving end to the initiating end, wherein the first message and the second message are used for determining the first hybrid encryption key; forwarding a third message sent by the initiating end to the receiving end, wherein the third message is a message encrypted by adopting the first hybrid encryption key and is used for determining a second hybrid encryption key; and feeding back a fourth message returned by the receiving end to the initiating end, the fourth message being a message encrypted by using the second hybrid encryption key. The technical problem that in the prior art, an anti-VPN technology is prone to being cracked is solved.
Owner:ALIBABA GRP HLDG LTD
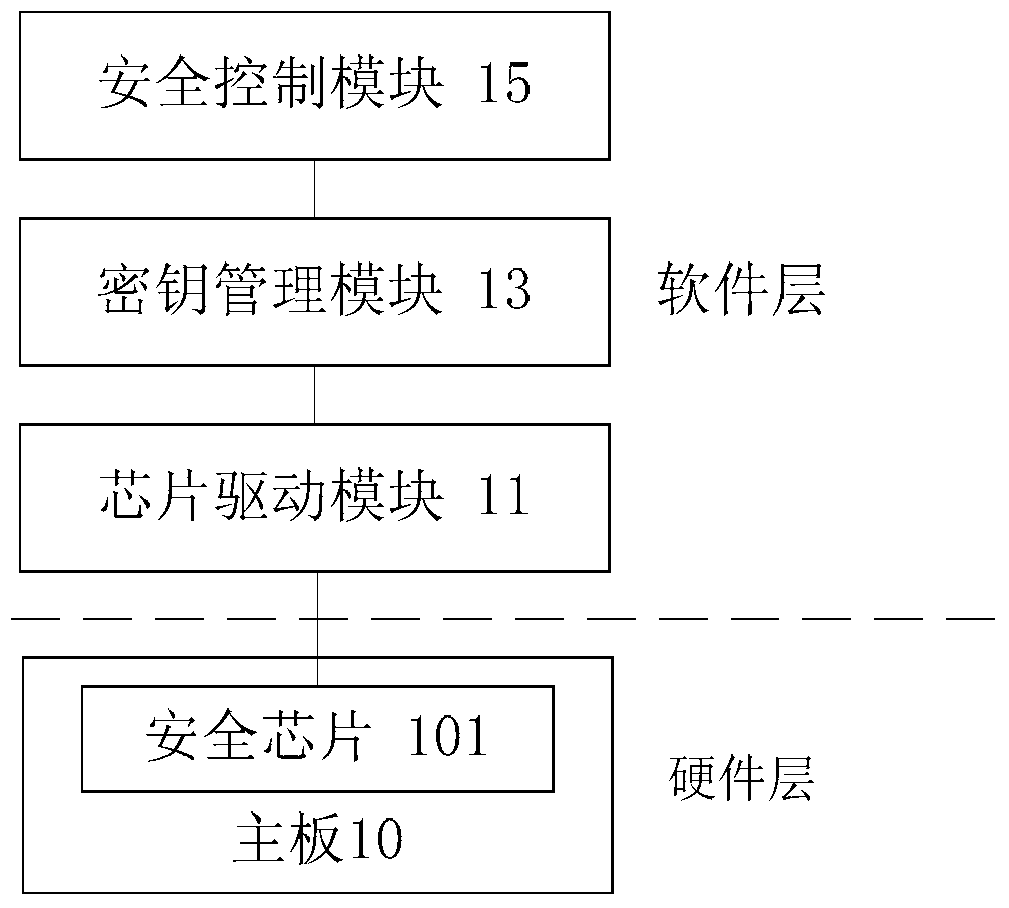
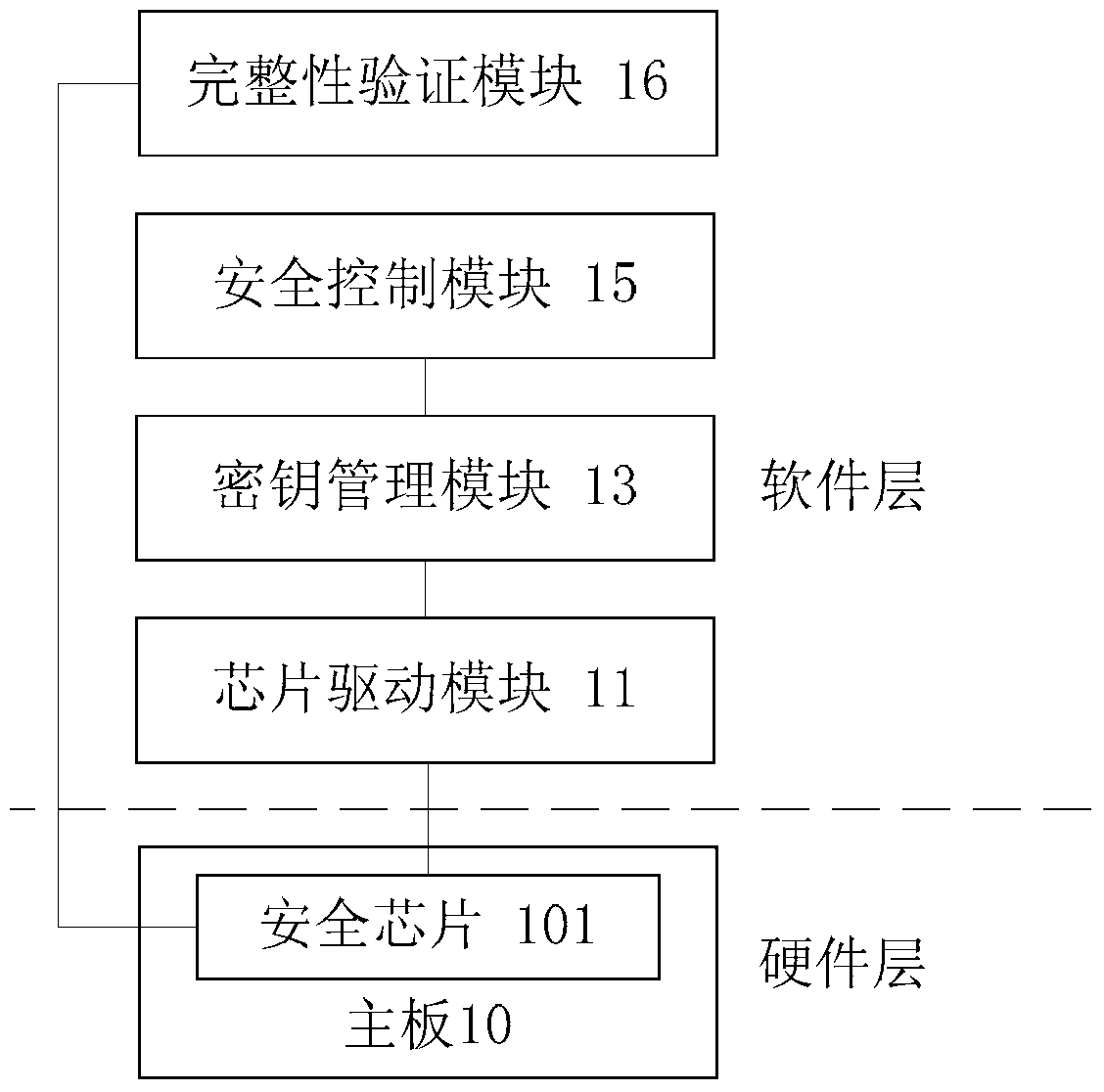
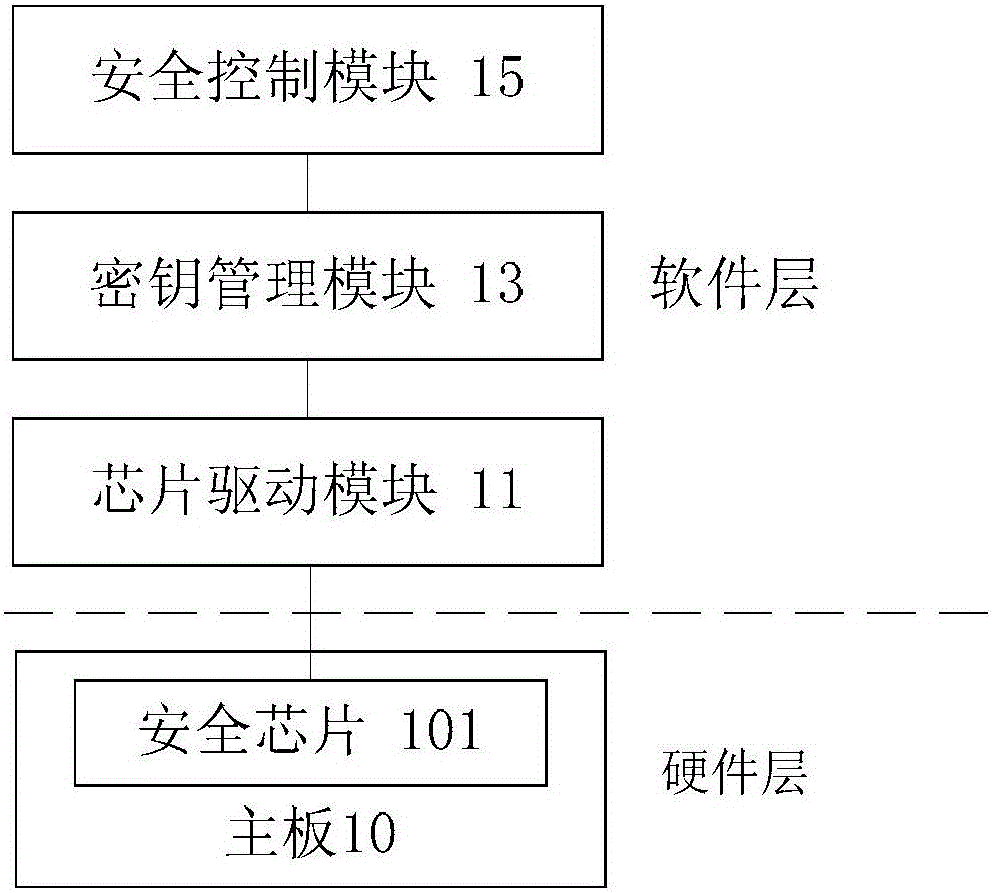
Security Control System Applied to Mobile Terminals
ActiveCN105827659BImprove data securityTo achieve the purpose of encryptionTransmissionSecurity arrangementControl systemData information
Owner:POSBANK
Process and device for preventing fraudulent use of terminal software
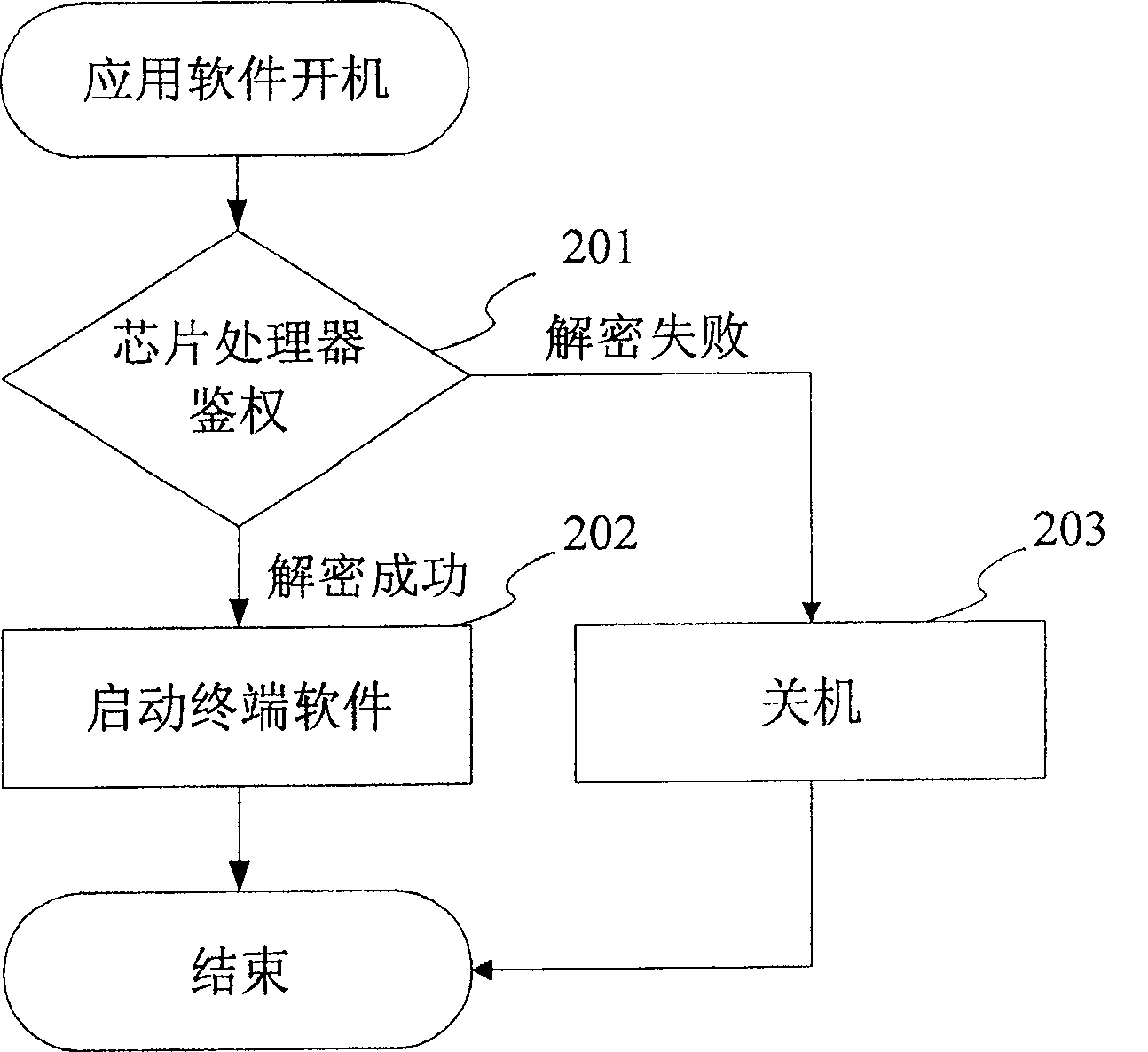
ActiveCN100489877CTo achieve the purpose of encryptionMaster the power of encryptionProgram/content distribution protectionPasswordProtection mechanism
The present invention discloses a method which can prevent the terminal software from being embezzled, the encryption flow is as follows: a plain code, a key1 and a key 2 are set, the key 1 is used to encrypt the plain code to get a password, the key 2 is used to encrypt the key 1 to get a key 3, at last, the password and the key3 are stored in a microprocessor, the key 2 is stored into a memory; the decryption flow is as follows: authentication software reads the password and the key 3 from the microprocessor, and the key2 is read from the memory, the decryption is performed to get the plain code, the plain code is used to judge whether the plain code is as same as the pre-set plain code, if the plain code is as same as the pre-set plain code, then the decryption is successful, otherwise, the decryption is failure. At the same time, a device which prevents the terminal software from being embezzled is disclosed, the device includes a microprocessor used to store the password and the key3; a memory used to store the key2, and a processor unit used to implement the authentication of terminal software. Through the present invention, the terminal scheme provider is enabled to possess a set of completely independent terminal software protection mechanisms.
Owner:LEADCORE TECH
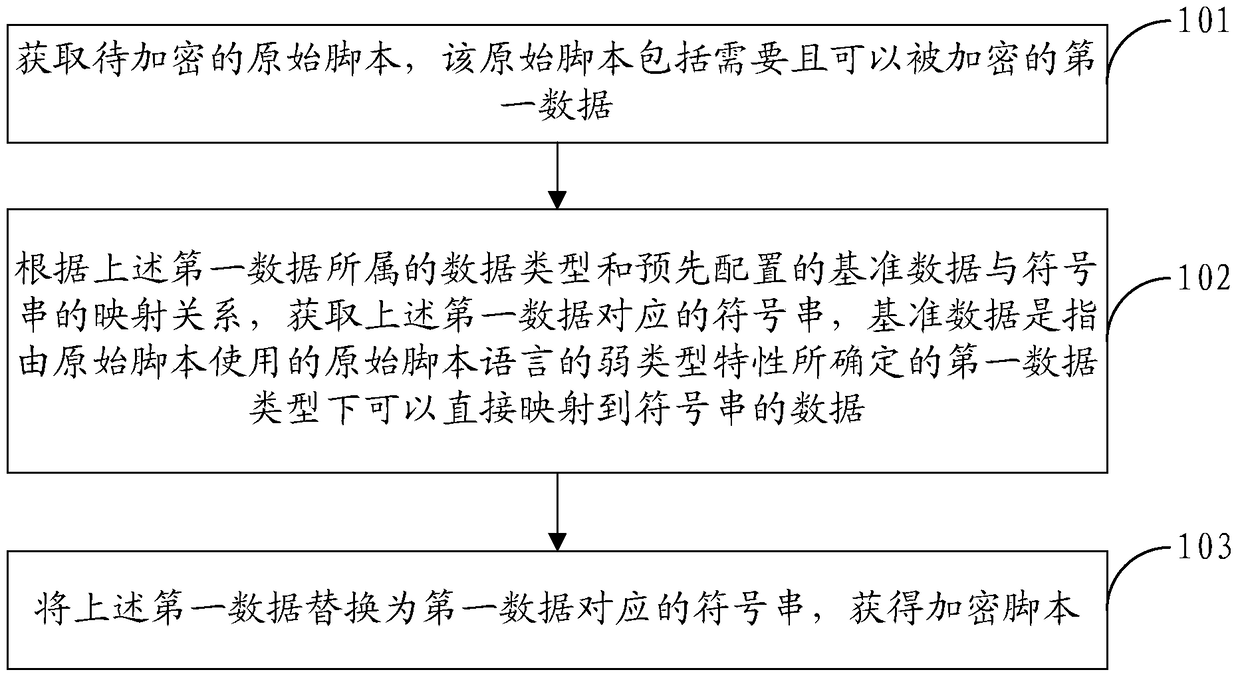
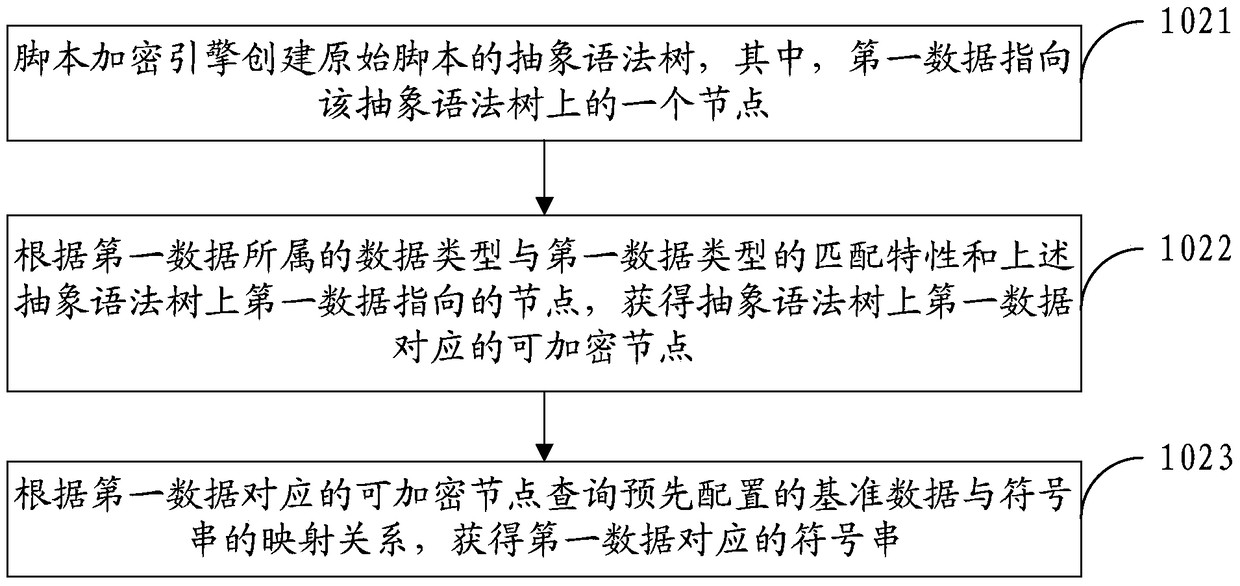
Script encryption method, decryption method and engine
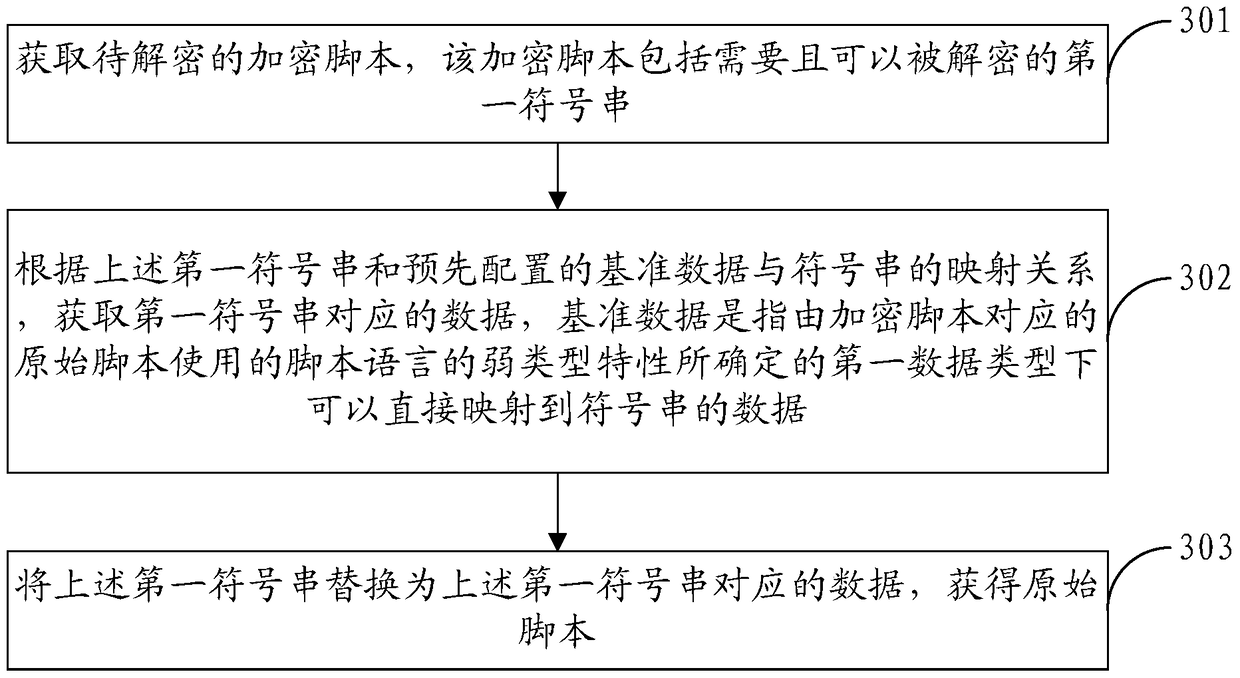
ActiveCN105447342BTo achieve the purpose of encryptionImprove securityProgram/content distribution protectionScripting languageBaseline data
The invention provides a script encryption method, a script decryption method and an engine. The script encryption method comprises the following steps: acquiring an original script to be encrypted, wherein the original script comprises first data required to be encrypted; acquiring a symbol string corresponding to the first data according to the data type of the first data and the mapping relation between pre-configured reference data and the symbol string, wherein the reference data are data which belong to the first data type determined according to the weak type characteristic of a scripting language used by the original script and can be directly mapped to the symbol string; and replacing the first data with the symbol string corresponding to the first data, so as to obtain an encrypted script. According to the technical scheme of the invention, the original script is encrypted with the symbol string, so that the encrypted script looks like a messy code and is difficult to decrypt. Therefore, the security of scripts can be improved.
Owner:ADVANCED NEW TECH CO LTD
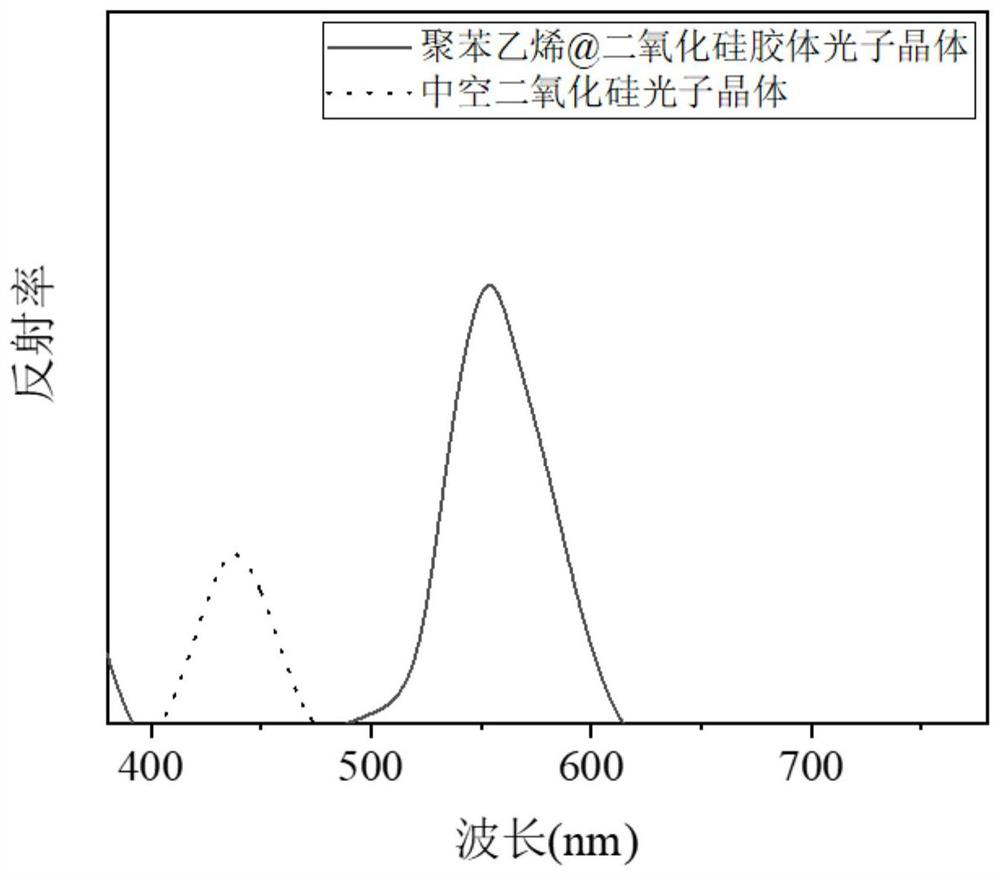
Preparation and Application of Photonic Crystal Materials with Responsive Stealth Patterns
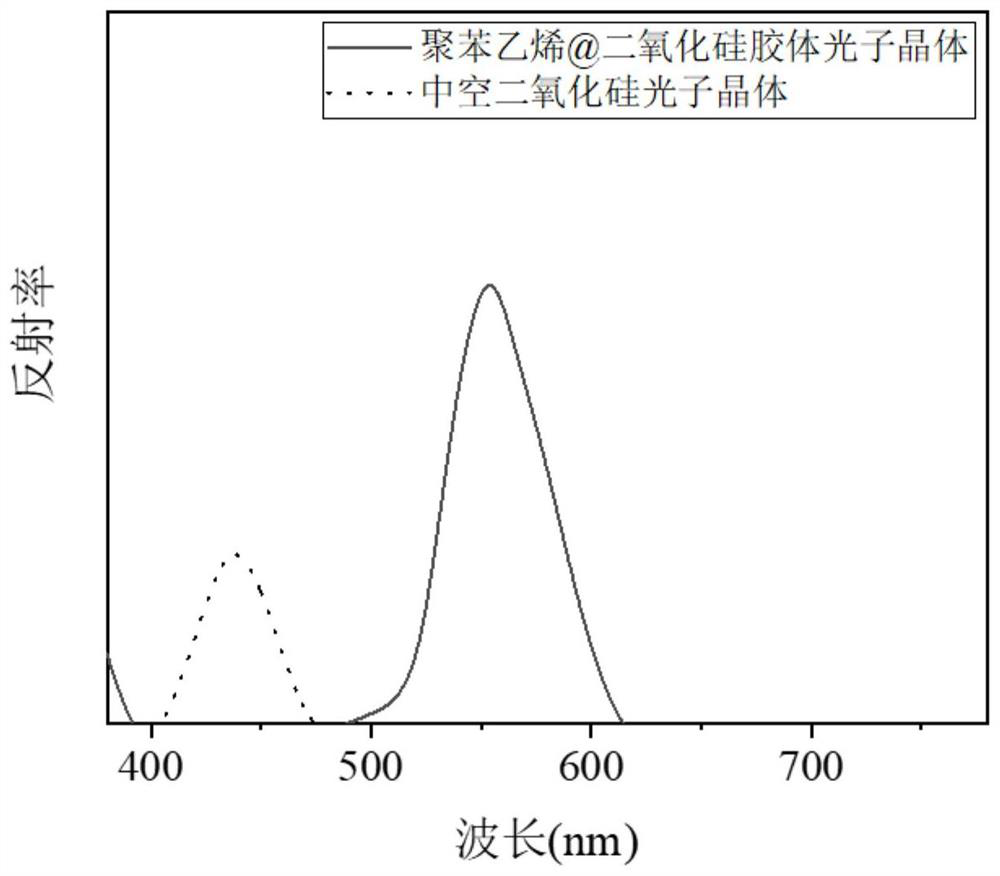
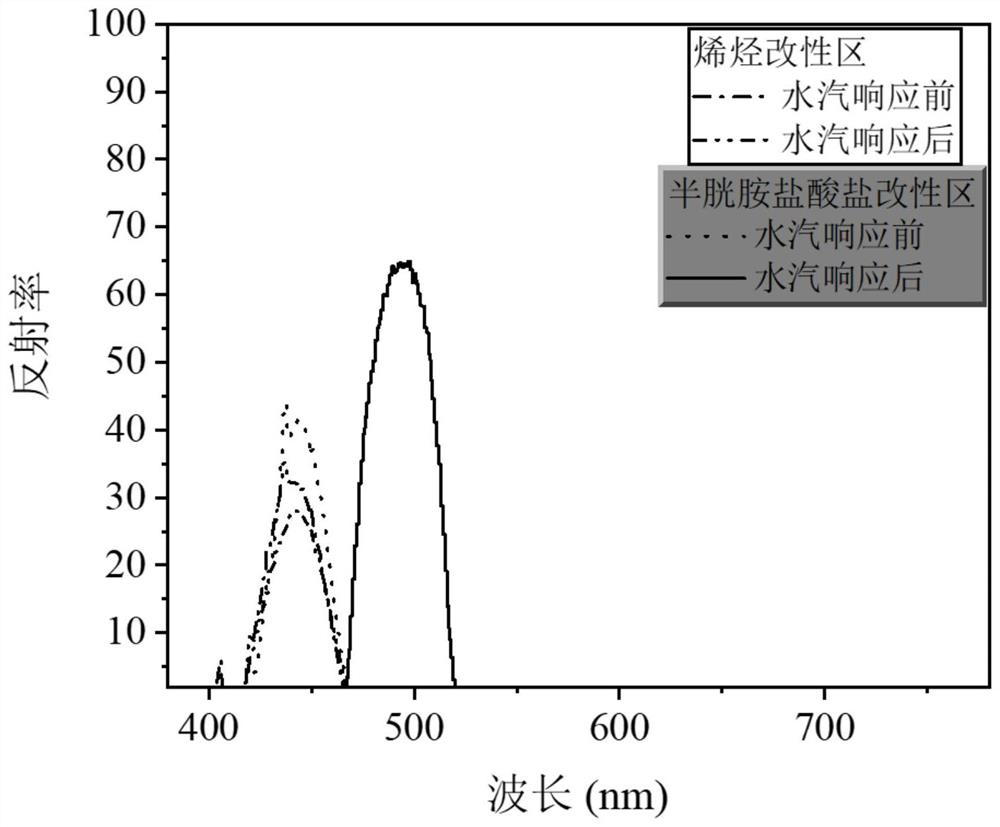
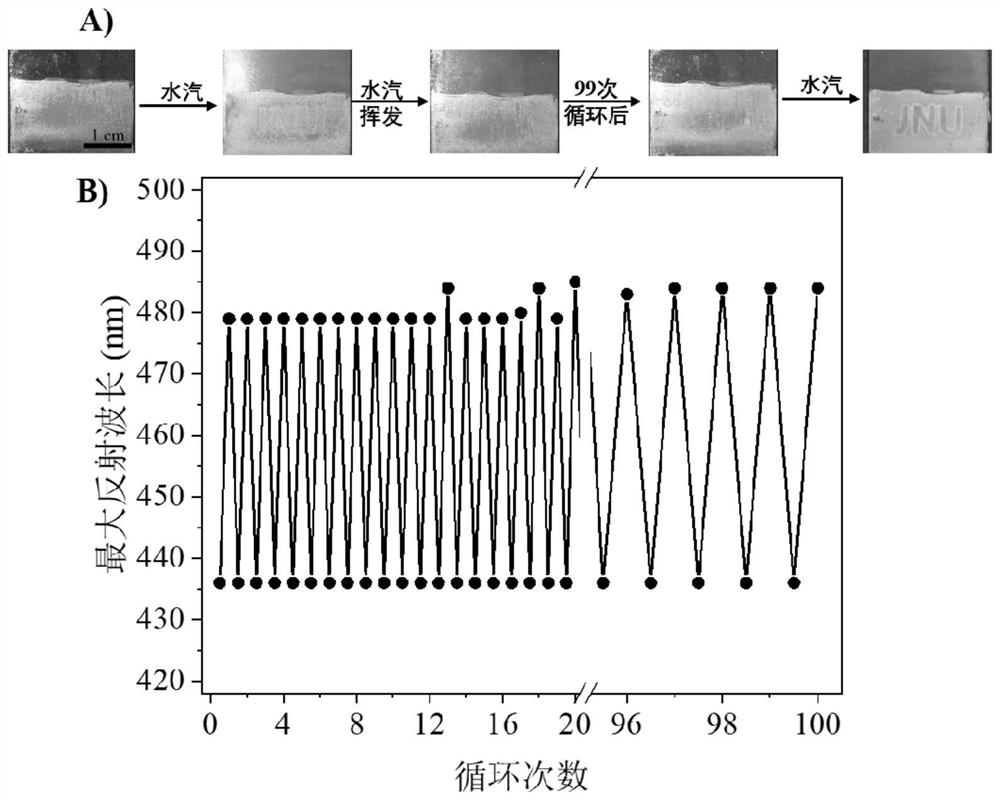
ActiveCN113073378BQuick responseImprove stabilityPolycrystalline material growthFrom normal temperature solutionsPhotonic crystalMicrosphere
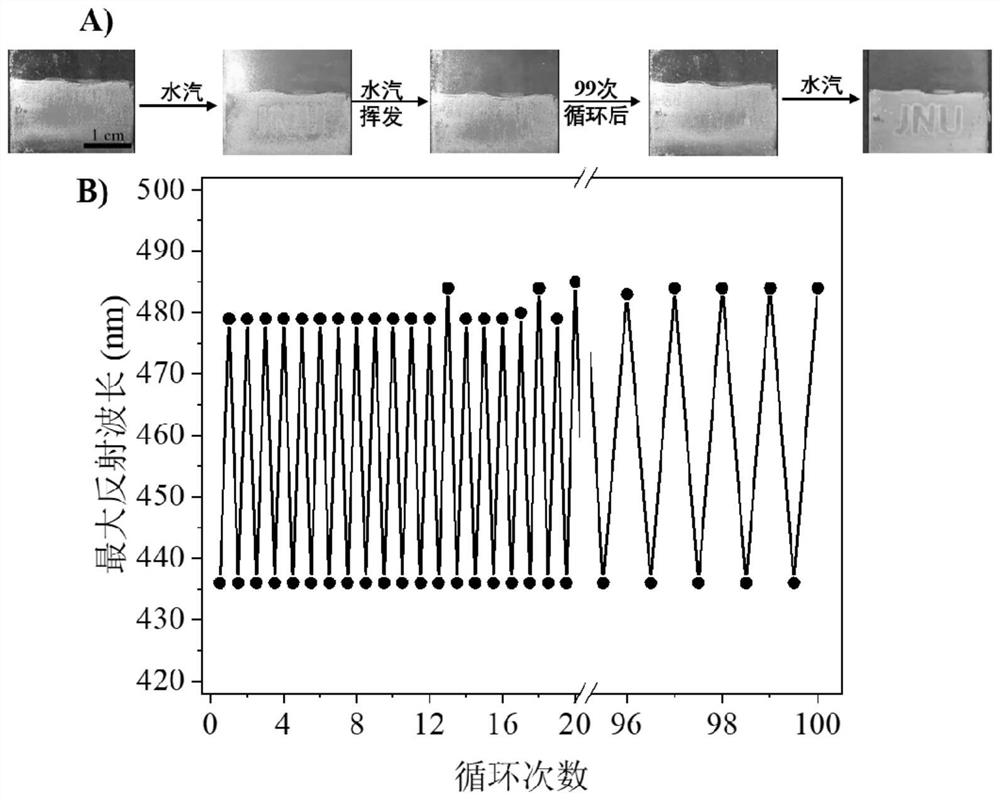
The invention discloses the preparation and application of photonic crystal materials with responsive invisible patterns, and belongs to the technical field of nanometer materials and functional polymer materials. The invention uses polystyrene microspheres as templates to prepare hollow silica photonic crystals, and then selectively constructs regions with different hydrophilicity and hydrophobicity on the hollow silica photonic crystals through Michael addition reaction to form regions that can selectively respond to water vapor. invisible pattern. The modified hollow silica photonic crystal material with invisible patterns prepared by the invention can be used for moisture detection and other solvent detection. Under the action of dynamic moisture, obvious patterns of different colors can be displayed within 1 second, and its It has long-term stability and high responsiveness, and there is no obvious error after 100 repetitions. The method provided by the invention has good application prospects in the fields of preparation of polystyrene microspheres, hollow silica microspheres and photonic crystals thereof, patterned preparation, detection of various solvents and their vapors, and the like.
Owner:JIANGNAN UNIV
Data processing method and device, electronic equipment and computer readable storage medium
PendingCN114254361AEncrypted securitySolve technical problems that are vulnerable to crackingDigital data protectionComputer hardwareEncryption
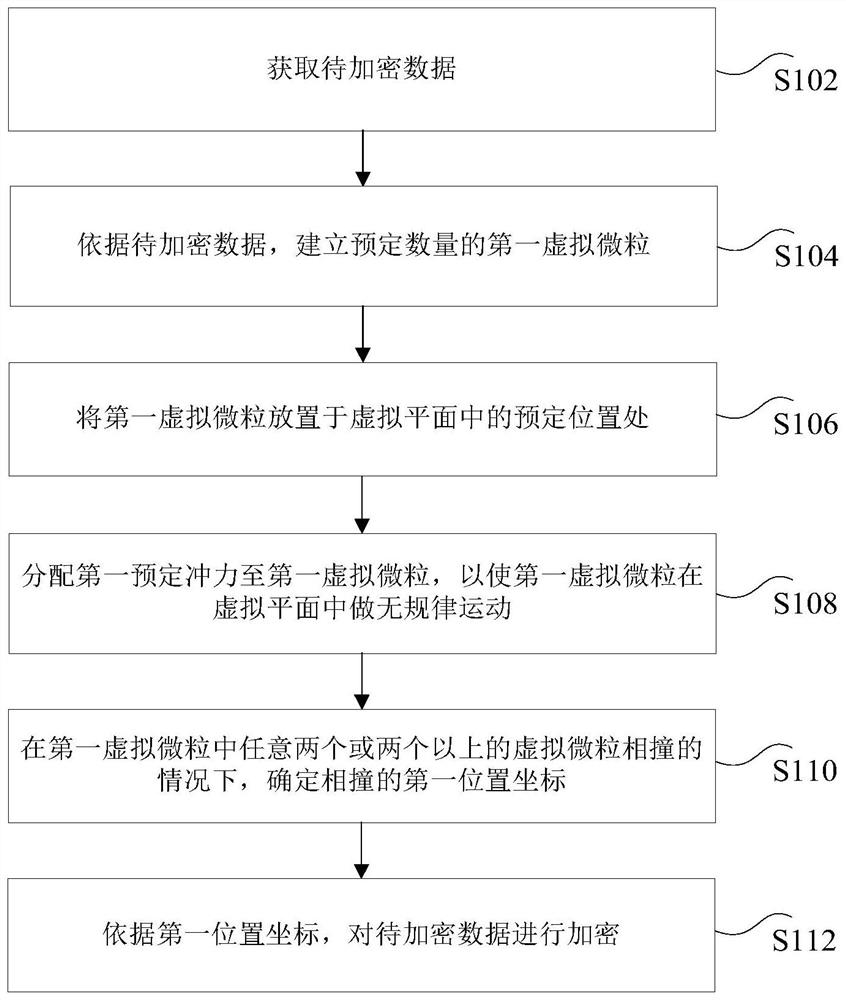
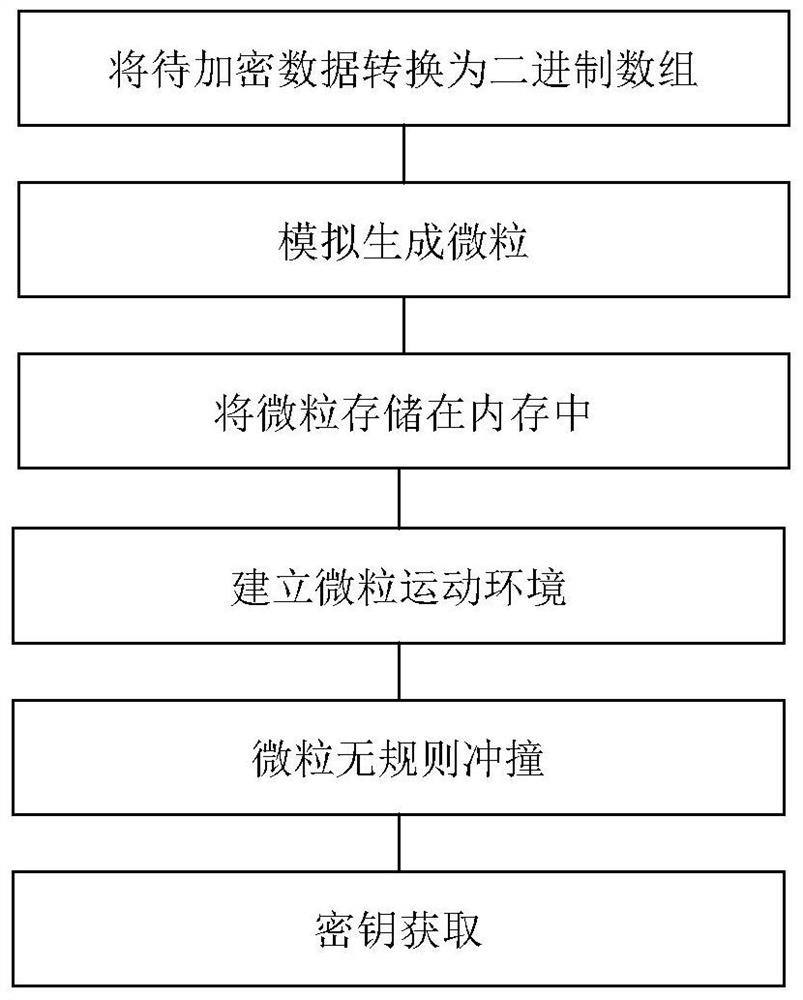
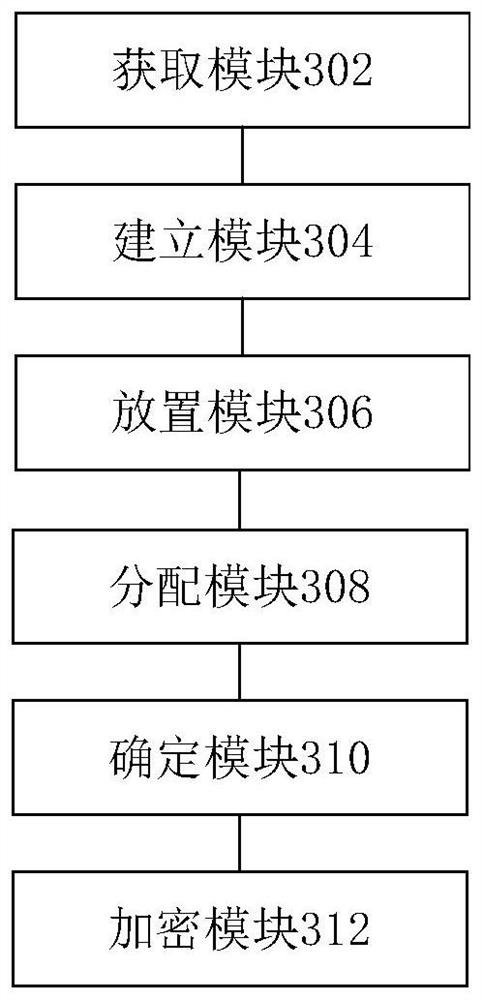
The invention discloses a data processing method and device, electronic equipment and a computer readable storage medium. The method comprises the following steps: acquiring to-be-encrypted data; establishing a preset number of first virtual particles according to the to-be-encrypted data; placing the first virtual particle at a predetermined position in the virtual plane; distributing a first preset impulsive force to the first virtual particle, so that the first virtual particle does irregular motion in the virtual plane; under the condition that any two or more than two virtual particles in the first virtual particles collide with each other, first position coordinates of collision are determined; and encrypting the to-be-encrypted data according to the first position coordinate. According to the method and the device, the technical problems that the encryption mode is simple and the encrypted data is easy to crack when encryption protection is carried out on the to-be-encrypted data in the prior art are solved.
Owner:CHINA TELECOM CORP LTD
Method for achieving Moire pattern anti-counterfeiting in halftone areas of images
InactiveCN108621622ABroaden your optionsImplement encryptionPattern printingImage data processing detailsPattern recognitionImage synthesis
Owner:合肥博之泰电子科技有限公司
Security control system applied to mobile terminal
ActiveCN105827659AImprove data securityTo achieve the purpose of encryptionTransmissionSecurity arrangementData informationControl system
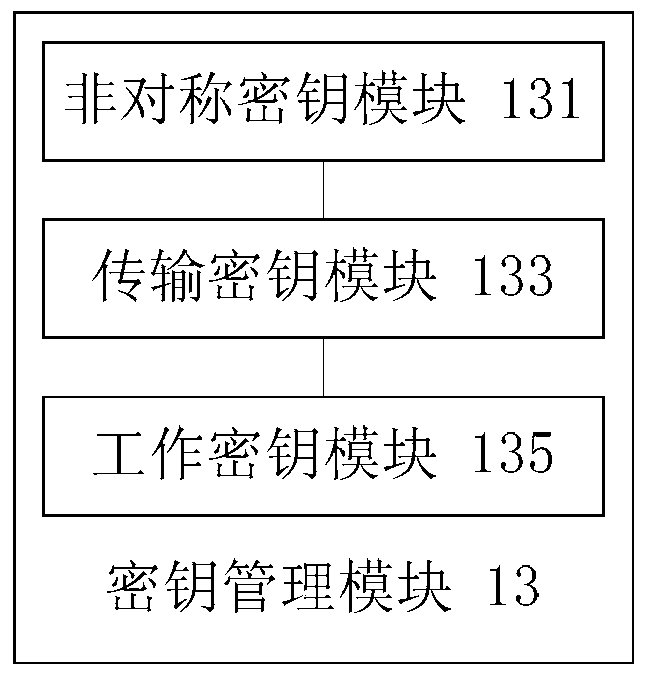
The invention discloses a security control system applied to a mobile terminal. A main board of the mobile terminal is provided with a security chip. The system comprises a chip driving module which is connected with the security chip and is used for driving the security chip to generate security keys, and types of the security keys at least comprise an asymmetric key, a transmission key and a work key; a key management module which is connected with the chip driving module and is used for driving the chip driving module to employ the key type corresponding to the data information according to the content of the data information for encryption and decryption processing on the data information; and a security control module which is connected with the key management module and is used for sending a control instruction to the key management module for encryption processing on the data information, and the control instruction is used for controlling the key management module. The system solves technical problems of poor data security and easy tampering caused by only soft encryption processing on the data existing in a mobile terminal in the prior art.
Owner:POSBANK
Preparation and application of photonic crystal material with responsive invisible pattern
ActiveCN113073378AQuick responseImprove stabilityPolycrystalline material growthFrom normal temperature solutionsPhotonic crystalMicrosphere
The invention discloses preparation and application of a photonic crystal material with a responsive invisible pattern, and belongs to the technical field of nano materials and functional polymer materials. A hollow silicon dioxide photonic crystal is prepared by taking polystyrene microspheres as a template, and then areas with different hydrophilicity and hydrophobicity are selectively constructed on the hollow silicon dioxide photonic crystal through a Michael addition reaction, so that an invisible pattern capable of selectively responding to water vapor is formed. The prepared modified hollow silicon dioxide photonic crystal material with an invisible pattern can be used for moisture detection and other solvent detection, can display obvious patterns with different colors within 1 second under the action of dynamic moisture, has long-term stable high responsiveness, and has no obvious error after being repeatedly used for 100 times. The method provided by the invention has a better application prospect in the fields of preparation of polystyrene microspheres, hollow silicon dioxide microspheres and photonic crystals thereof, preparation of patterns, detection of various solvents and steam thereof and the like.
Owner:JIANGNAN UNIV
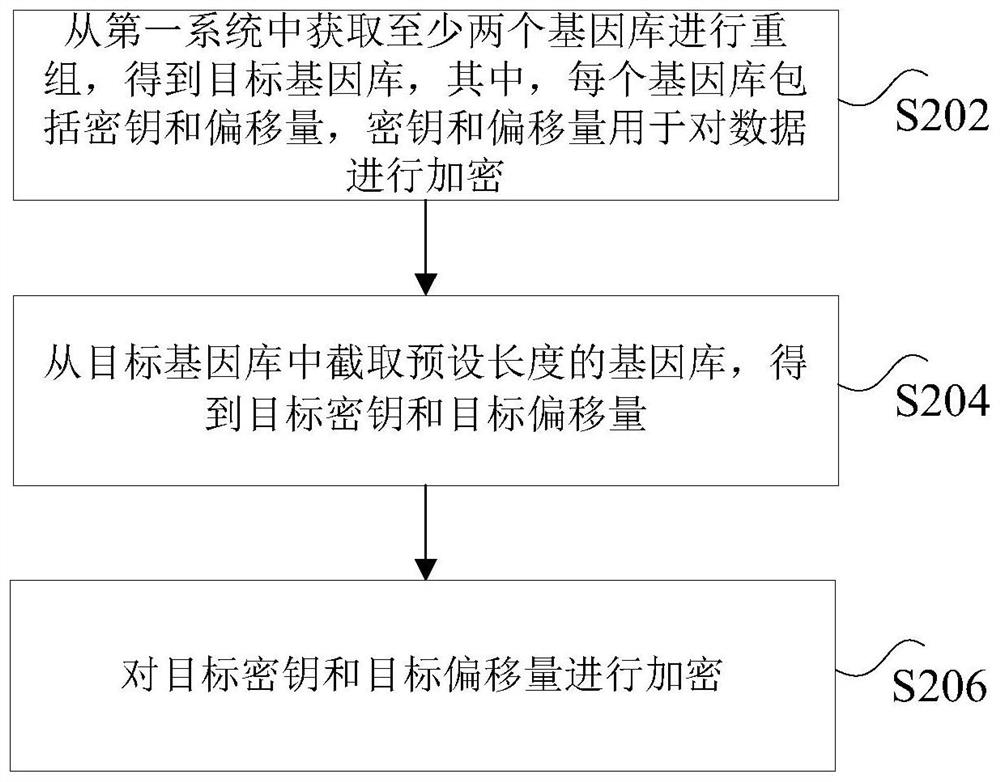
Secret key generation method and device
PendingCN114285563ATo achieve the purpose of encryptionImprove securityKey distribution for secure communicationDigital data protectionComputer hardwareEngineering
The invention discloses a key generation method and device. The method comprises the steps that at least two gene banks are obtained from a first system to be recombined, a target gene bank is obtained, each gene bank comprises a secret key and offset, and the secret keys and the offset are used for encrypting data; intercepting a gene pool with a preset length from the target gene pool to obtain a target key and a target offset; and encrypting the target key and the target offset. According to the method and the device, the technical problem that the security of data protection is not high enough due to a traditional data desensitization mode is solved.
Owner:CHINA TELECOM CORP LTD
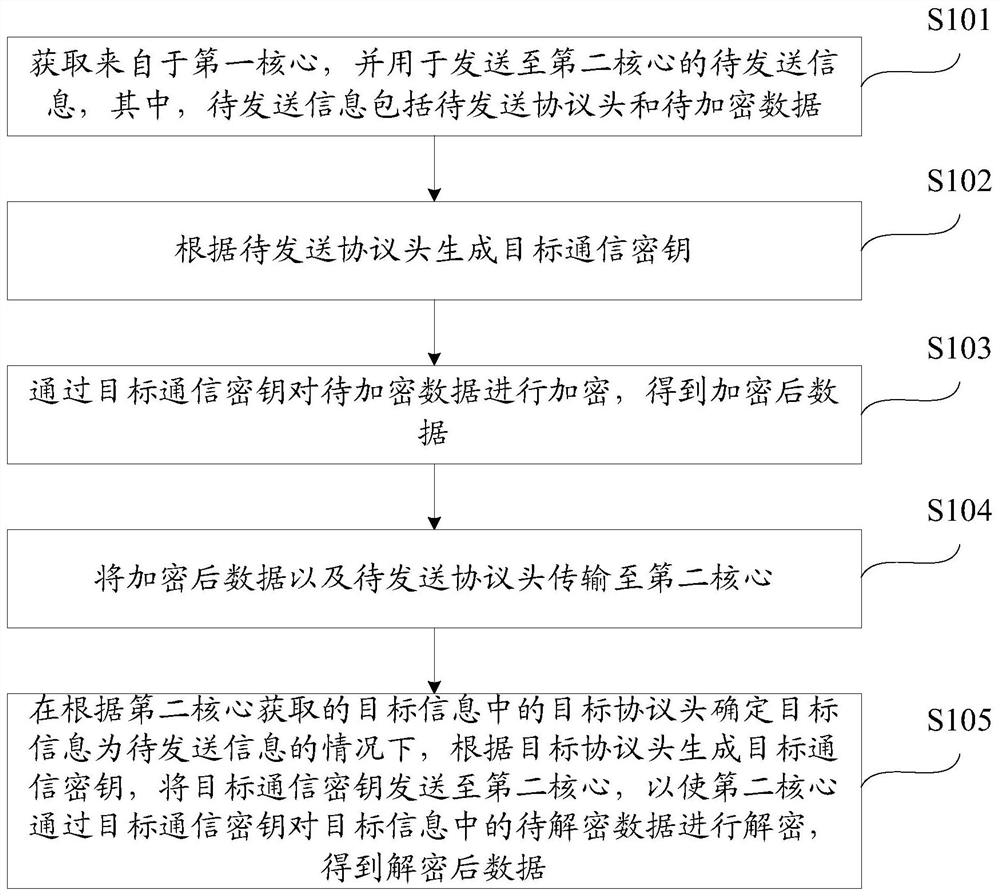
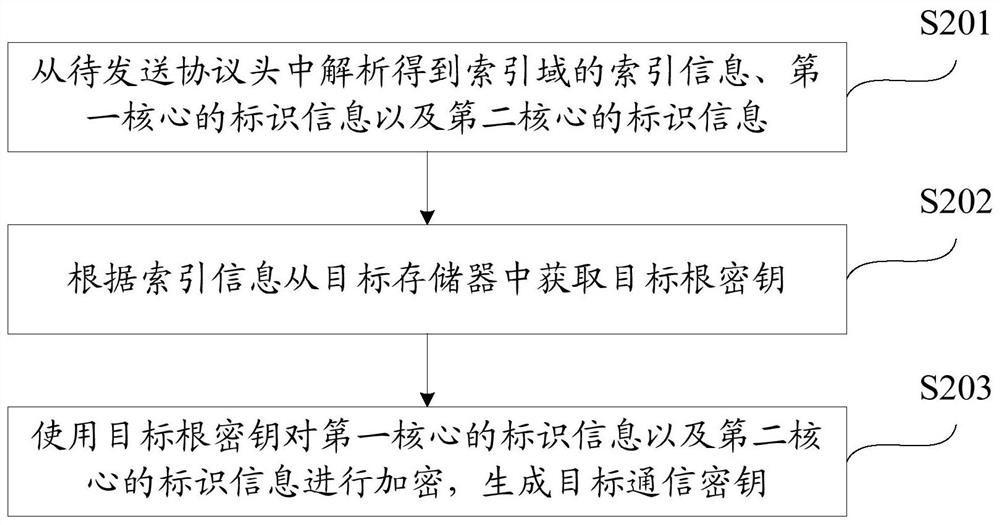
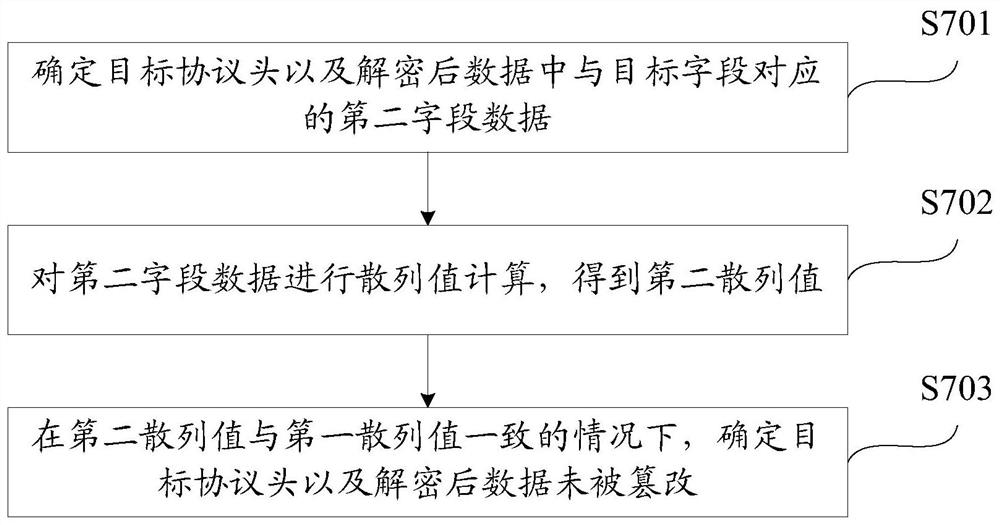
Inter-core communication method and device in multi-core microprocessor
PendingCN113742790ATo achieve the purpose of encryptionEnsure safetyInterprogram communicationInternal/peripheral component protectionComputer networkDual core
The invention relates to an inter-core communication method and device in a multi-core microprocessor, and the method comprises the steps: obtaining to-be-sent information which comes from a first core and is used for being sent to a second core; generating a target communication key according to a to-be-sent protocol header; encrypting the to-be-encrypted data through the target communication key to obtain encrypted data; transmitting the encrypted data and the protocol header to be sent to a second core; under the condition that the target information is determined to be information to be sent according to the target protocol header in the target information acquired by the second core, generating a target communication key according to the target protocol header, and sending the target communication key to the second core, so that the second core decrypts data to be decrypted in the target information through the target communication key to obtain decrypted data. According to the application, the purpose of encrypting the communication information between the dual cores can be achieved, and the problem that the confidential information of a user is leaked due to the fact that a hacker obtains the communication content between the cores through monitoring is prevented.
Owner:GREE ELECTRIC APPLIANCES INC +1
Biometric Encryption Method, Encryption Matching Method and Encryption System, Encryption Matching System
ActiveCN105847003BTo achieve the purpose of encryptionAvoid demandUser identity/authority verificationPlaintextData set
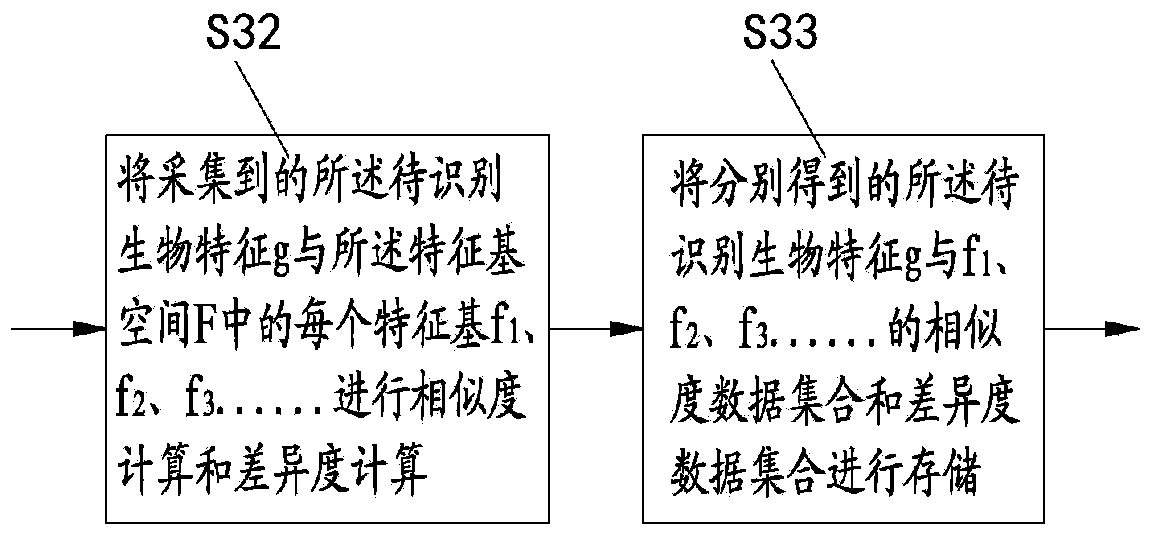
The invention discloses an encryption method of biological features, an encryption matching method and an encryption system, and an encryption matching system. The encryption method comprises the following steps: respectively computing similarity and / or difference of a to be identified biological feature with each feature base in N feature base spaces to obtain a corresponding data set, thereby realizing the encryption on the biological feature; respectively computing the similarity and / or the difference of two to be identified biological features with each feature base in the feature base space, comparing the computing result in the one-to-one correspondence, thereby realizing the matching of two to be identified biological features. The to be identified biological feature is converted into a group of abstract code data, the group of code data supports the one-way encrypted storage, the matching of the biological feature based on the code data or the cipher text is realized, the requirement of the clear text of the biological feature is avoided, and the security of the biological feature on the identification is guaranteed.
Owner:渭南印象认知技术有限公司
Encryption methods, app locks, and electronic devices
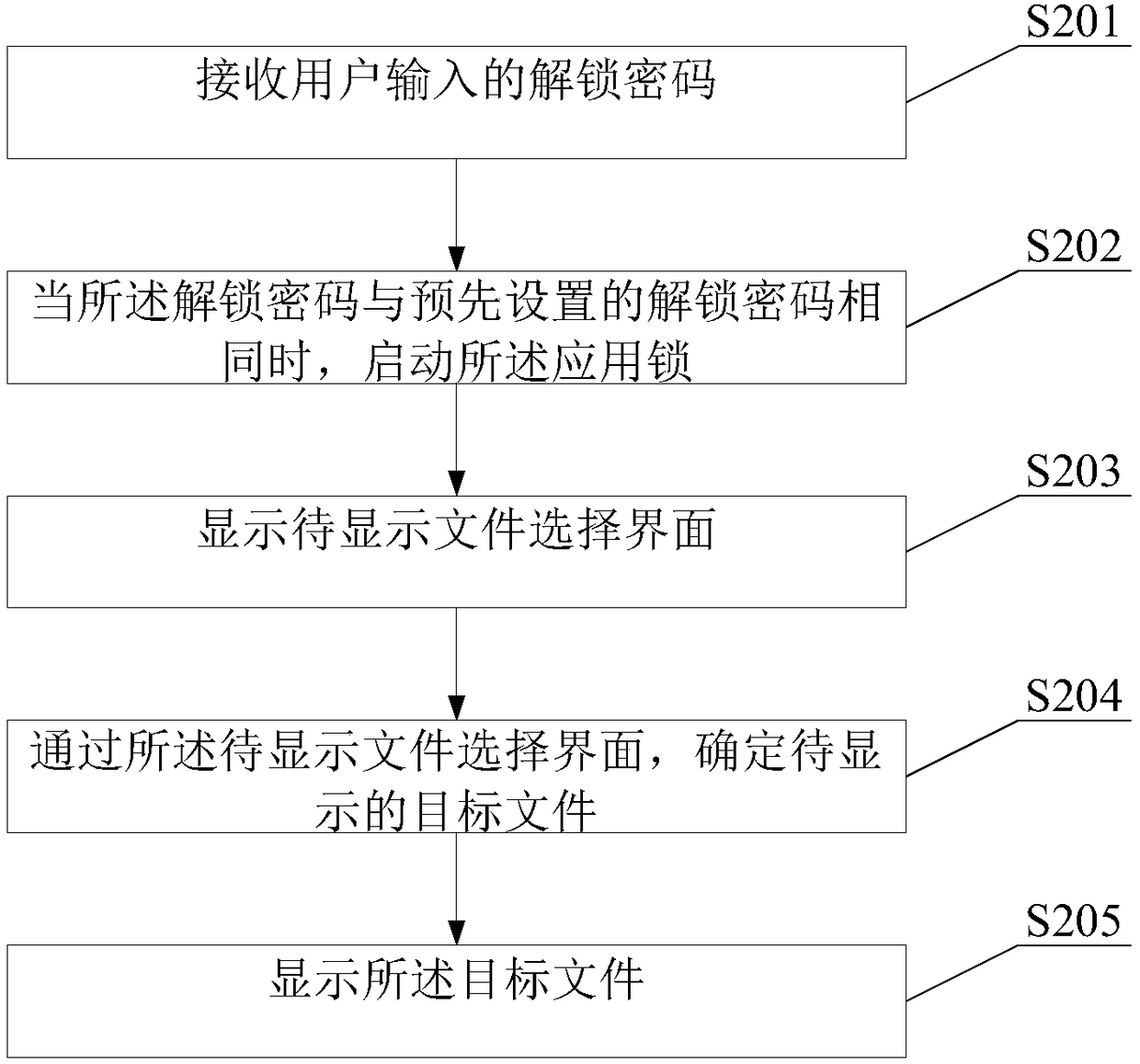
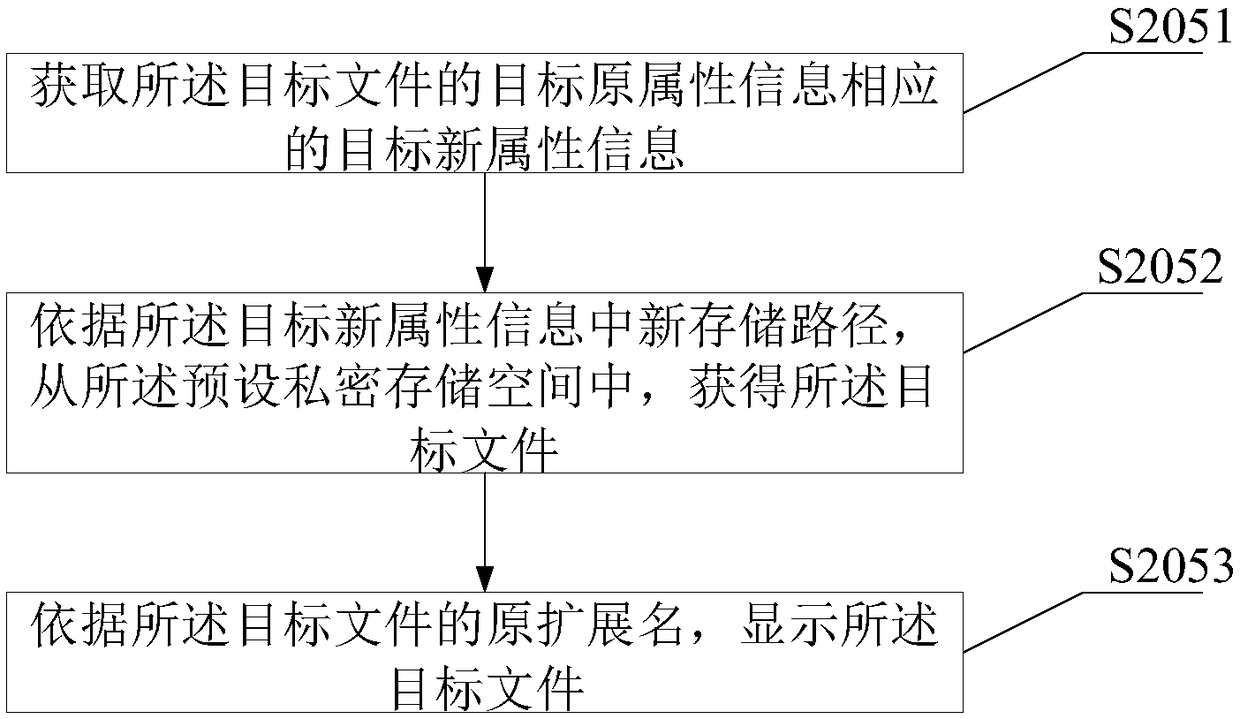
ActiveCN108573161BTo achieve the purpose of encryptionDigital data protectionDigital data authenticationPasswordCryptogram
The invention provides an encryption method, an application lock and an electronic device, which receive an unlocking password input by a user, and when the unlocking password input by the user is the same as the preset unlocking password, start the application lock and display a file selection interface to be encrypted; Through the file selection interface to be encrypted, determine the file to be encrypted; migrate the file to be encrypted from the original storage path to the preset private storage space, so that the application that stores the file to be encrypted does not need to be encrypted as a whole, but will need to be encrypted The files are migrated from the original storage path to the preset private storage space, thus achieving the purpose of encrypting one or more files individually.
Owner:北京贝塔科技有限公司
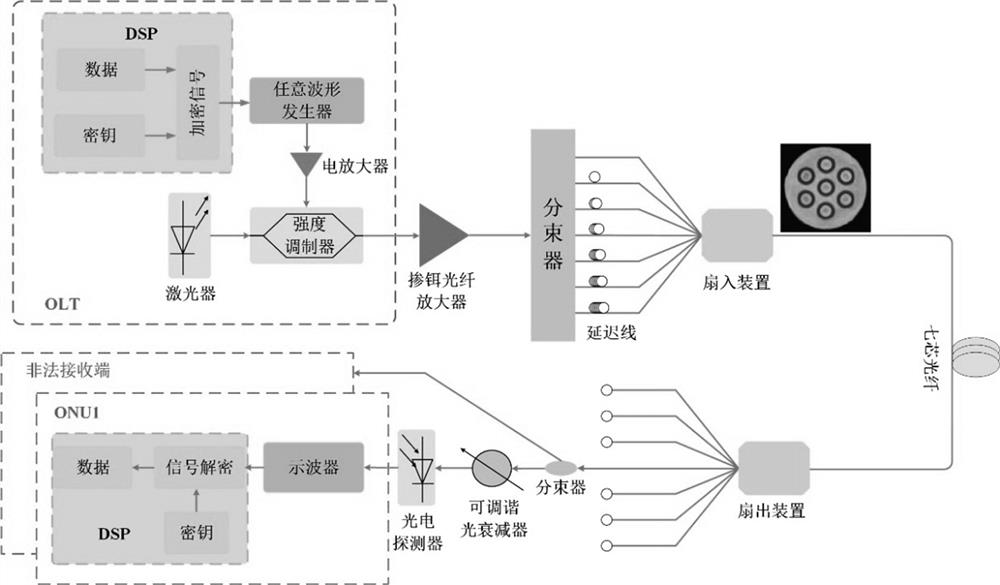
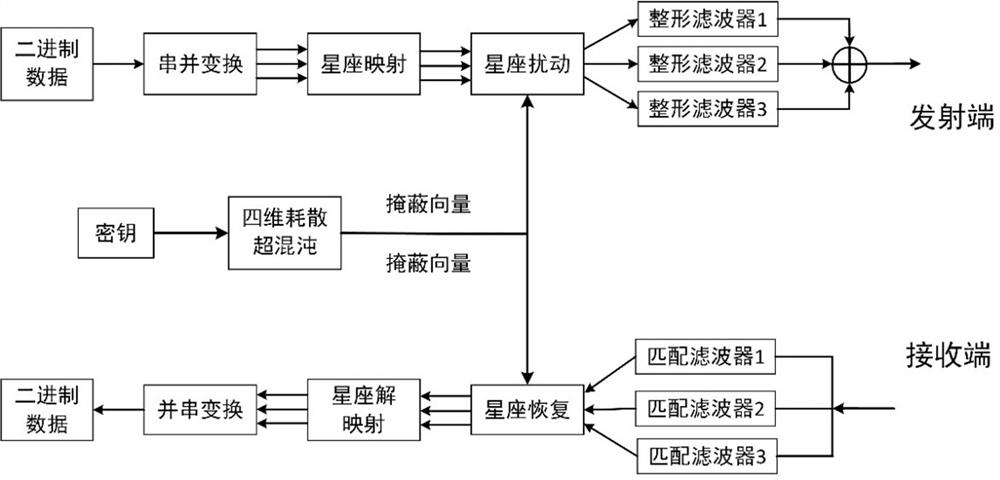
Multi-core optical fiber transmission method based on high-dimensional constellation multistage encryption
PendingCN114513260ATo achieve the purpose of encryptionIncrease the difficultyFibre transmissionElectromagnetic transmission optical aspectsSignal onDigital signal processing
The invention relates to the technical field of optical transmission, and discloses a multi-core optical fiber transmission method based on high-dimensional constellation multi-level encryption, which comprises the following steps of: 1) performing off-line digital signal processing on original data to generate an encrypted signal, and importing the encrypted signal into an arbitrary waveform generator to perform digital-to-analog conversion at 25GSa / s; and 2) amplifying the radio frequency signal through an electric amplifier before the radio frequency signal is injected into the Mach-Zehnder modulator for intensity modulation. According to the multi-core optical fiber transmission method based on high-dimensional constellation multistage encryption, a spherical encryption high-security optical transmission method is designed, so that signals on a transmission channel have a property similar to random noise, the purpose of information encryption is achieved, the difficulty of stealing information by an illegal ONU is greatly improved, and the security of the ONU is improved. Therefore, the overall safety of optical network transmission is improved, and meanwhile, the seven-core optical fiber is adopted for transmission, so that the transmission capacity is greatly improved.
Owner:NANJING UNIV OF INFORMATION SCI & TECH
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com