Process and device for preventing fraudulent use of terminal software
A terminal software and software technology, applied in the direction of computer security devices, instruments, program/content distribution protection, etc., can solve the problems affecting the profit margin of terminal solution providers and the lack of protection mechanism of terminal solution providers, so as to improve sales profits, The effect of preventing theft
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
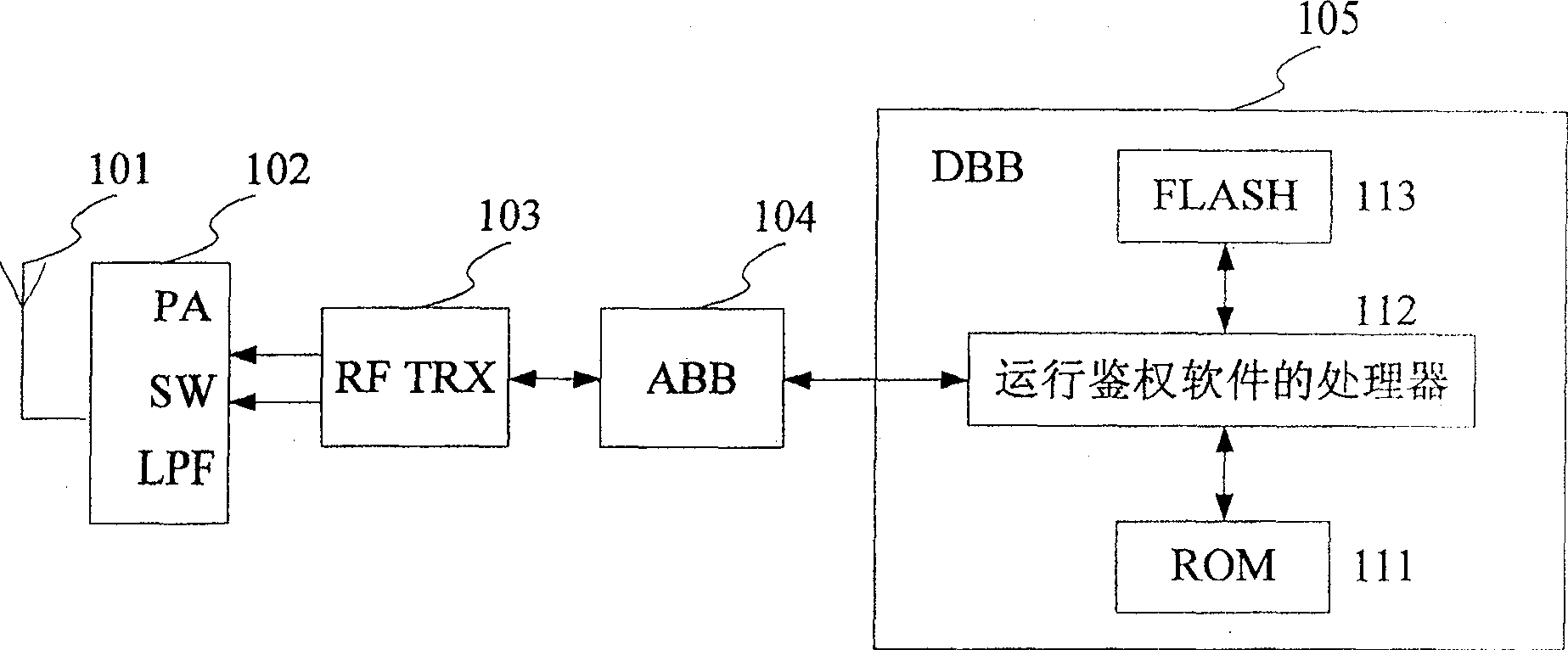
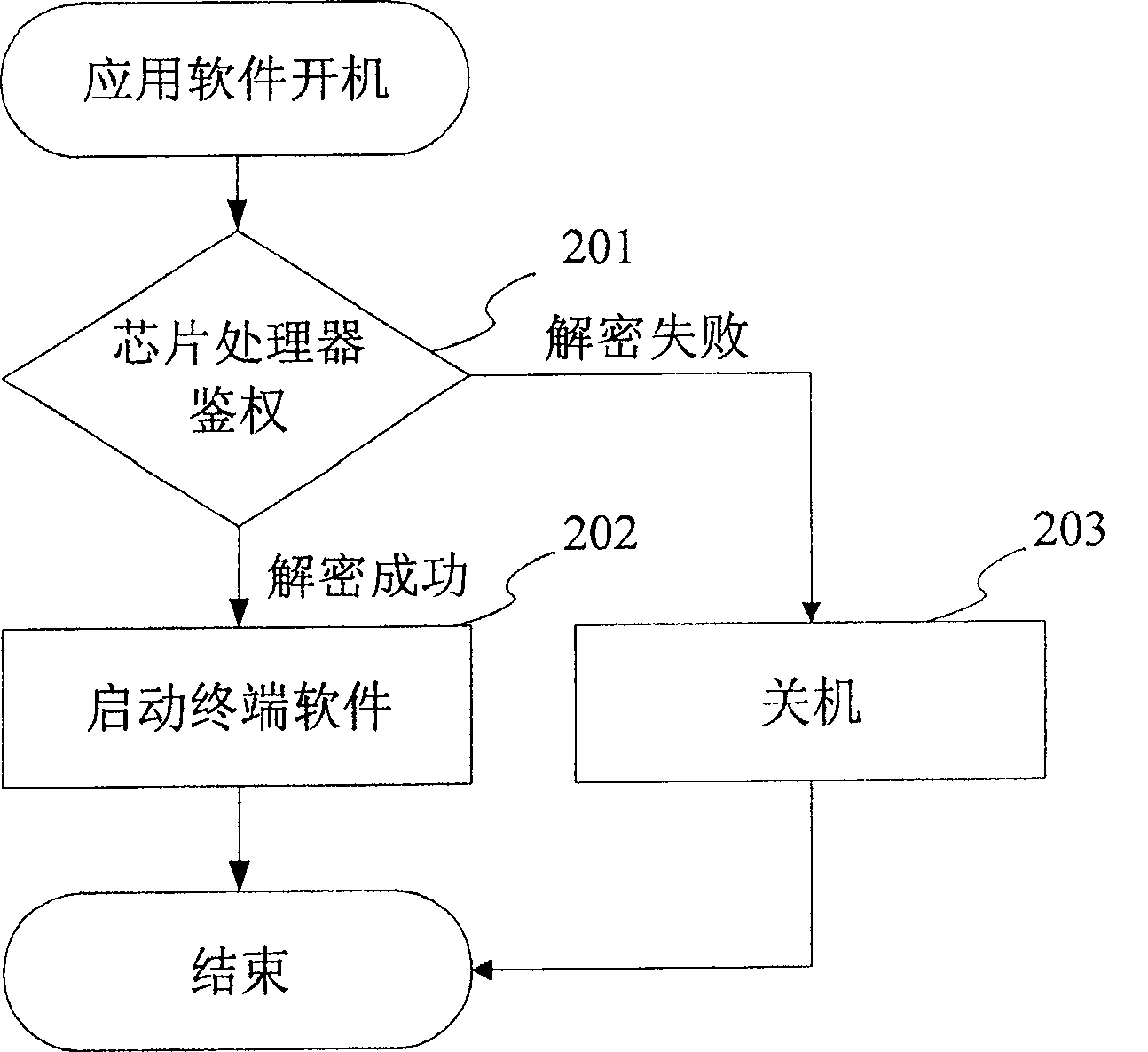
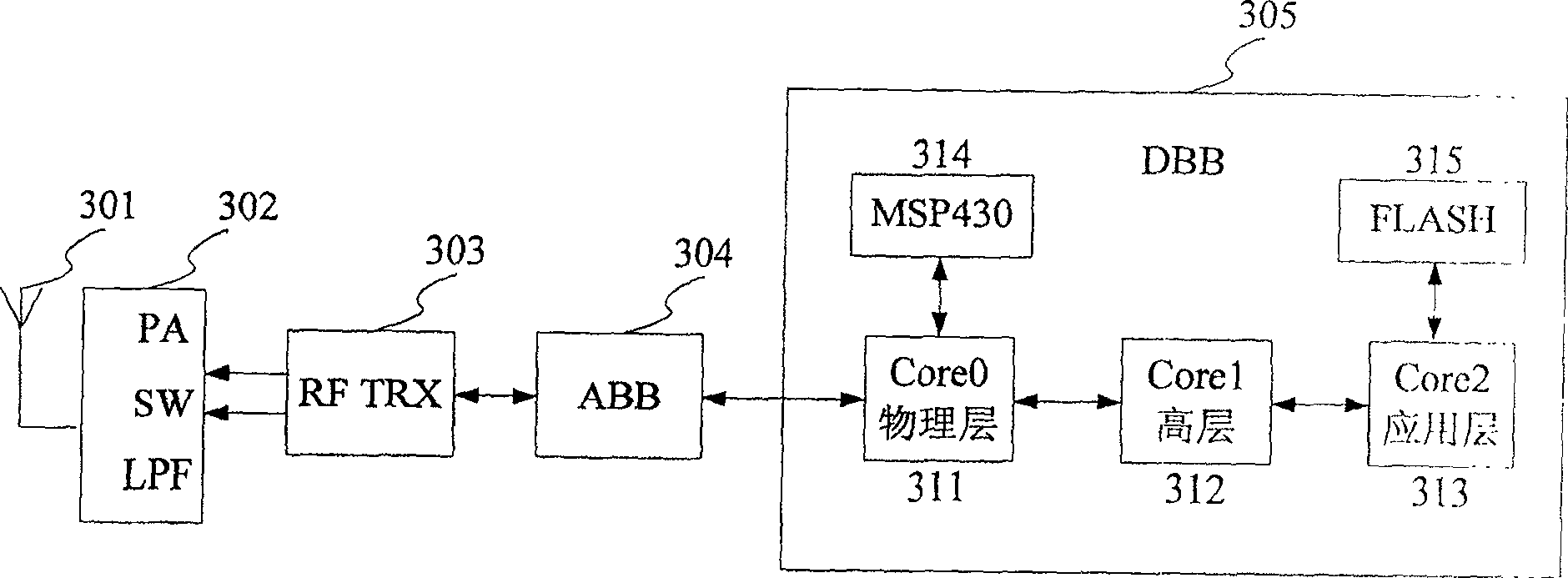
[0035] The present invention will be further described in detail below in conjunction with the accompanying drawings and specific embodiments. The preferred implementation scheme of the present invention is divided into two parts, the encryption process and the decryption process, which are specifically expressed as follows:
[0036] Encryption process: set a plain code, key 1 and key 2, use key 1 to encrypt the plain code to obtain a password, use key 2 to encrypt key 1 to obtain key 3, and store the password and key 3 in the micro In the processor, the key 2 is stored in a memory;
[0037] Decryption process: read the password and key 3 from the microprocessor, read the key 2 from the memory, use the reverse process of the encryption process to decrypt to obtain the plain code, and compare the obtained plain code with the preset plain code Compare the authentication to determine whether they are the same, if they are the same, the decryption is successful, otherwise the dec...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com