Patents
Literature
49results about How to "Increase the difficulty of decryption" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Data encryption method and system
InactiveCN102567687AEncryption guaranteedGood encryptionDigital data protectionSecuring communicationComputer hardwareData transmission
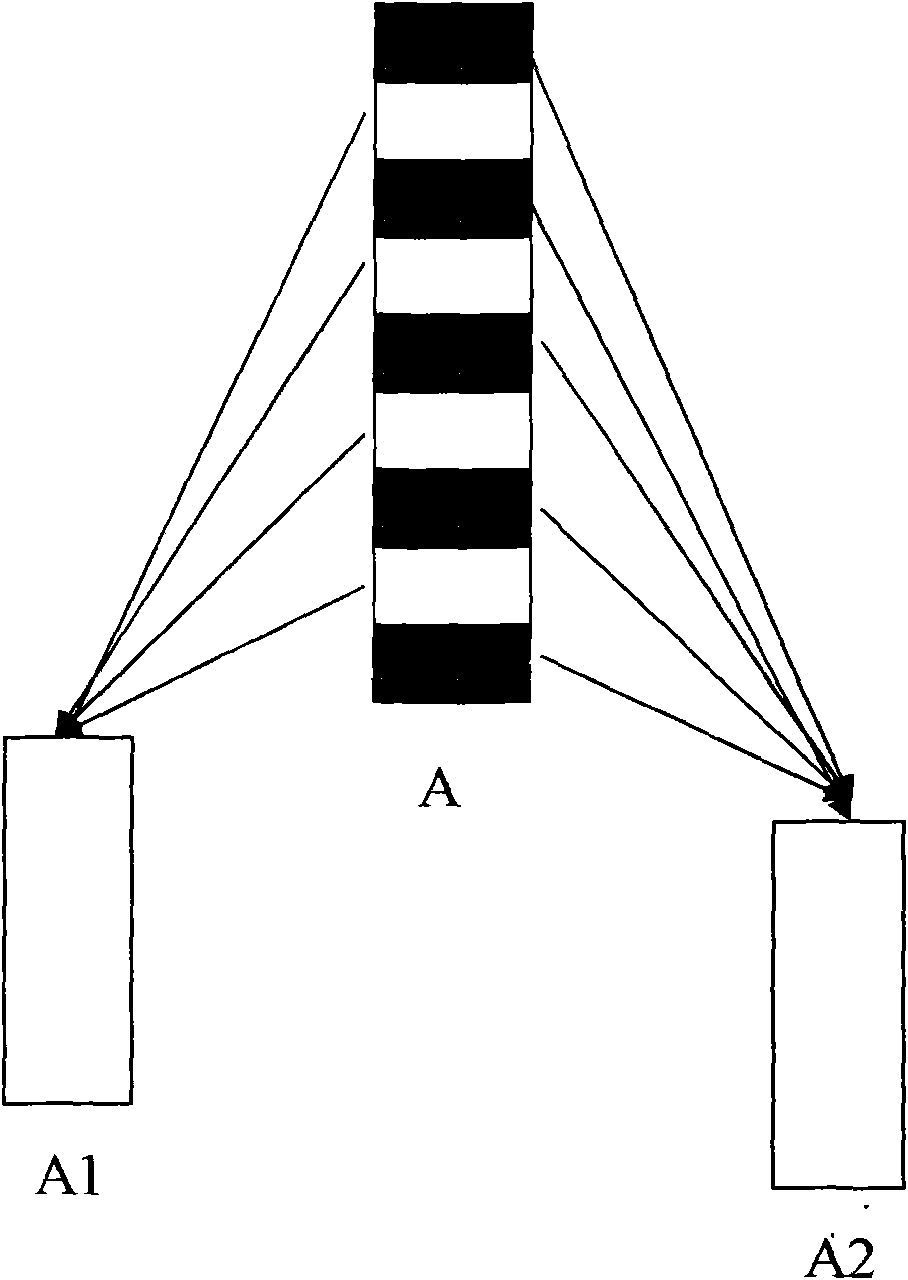
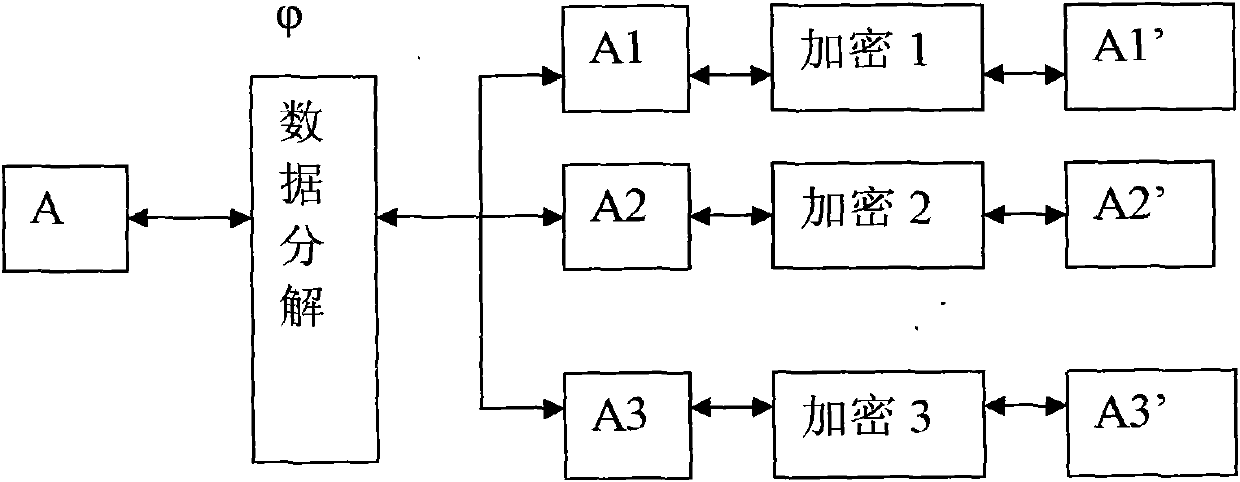
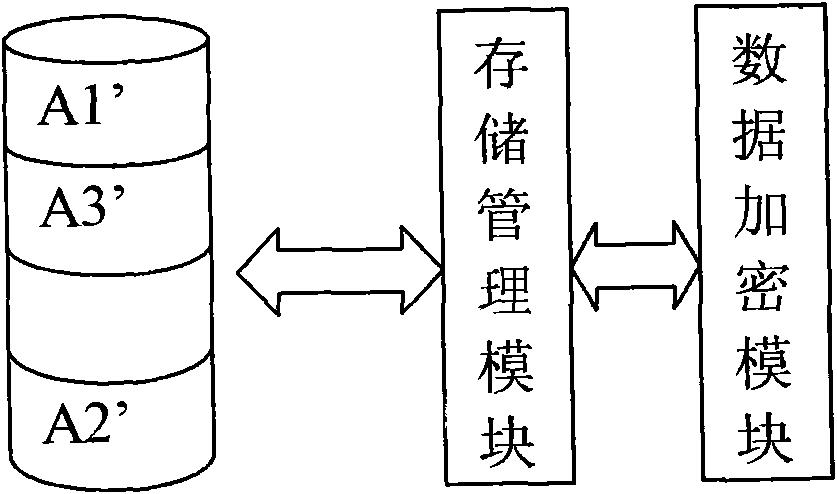
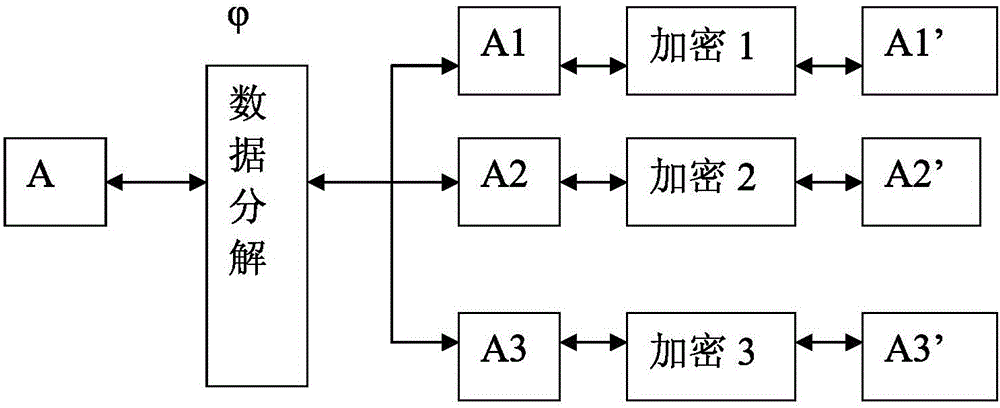
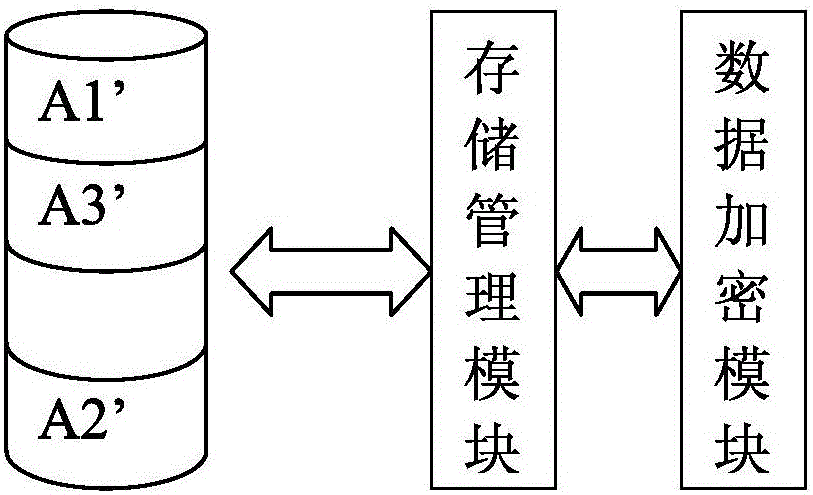
The invention relates to a data encryption method and a system. The data encryption method is characterized in that raw data is decomposed into at least two parts of data according to a preset function relationship. A data encryption storage method is characterized in that the preset function relationship is decomposed into at least parts of data, and the disassembled data is respectively stored in different memories. A data encryption transmission method is characterized in that a sending end decomposes raw data A into at least two parts according to the preset function relationship; the two parts are sent to a data receiving end via different data transmitting channels; and the data receiving end respectively receives the data, and combines and reduces the data into the raw data A according to the corresponding function relationship. As various combination modes are provided, the decryption difficulty is high after encryption, and the original encryption index is enhanced by times to guarantee the encryption effect of numbers. Only disassembly is required, and therefore, good encryption effect is achieved. In addition, the data encryption method has the advantages of low calculation amount and high encryption and decryption efficiency.
Owner:成都科创知识产权研究所
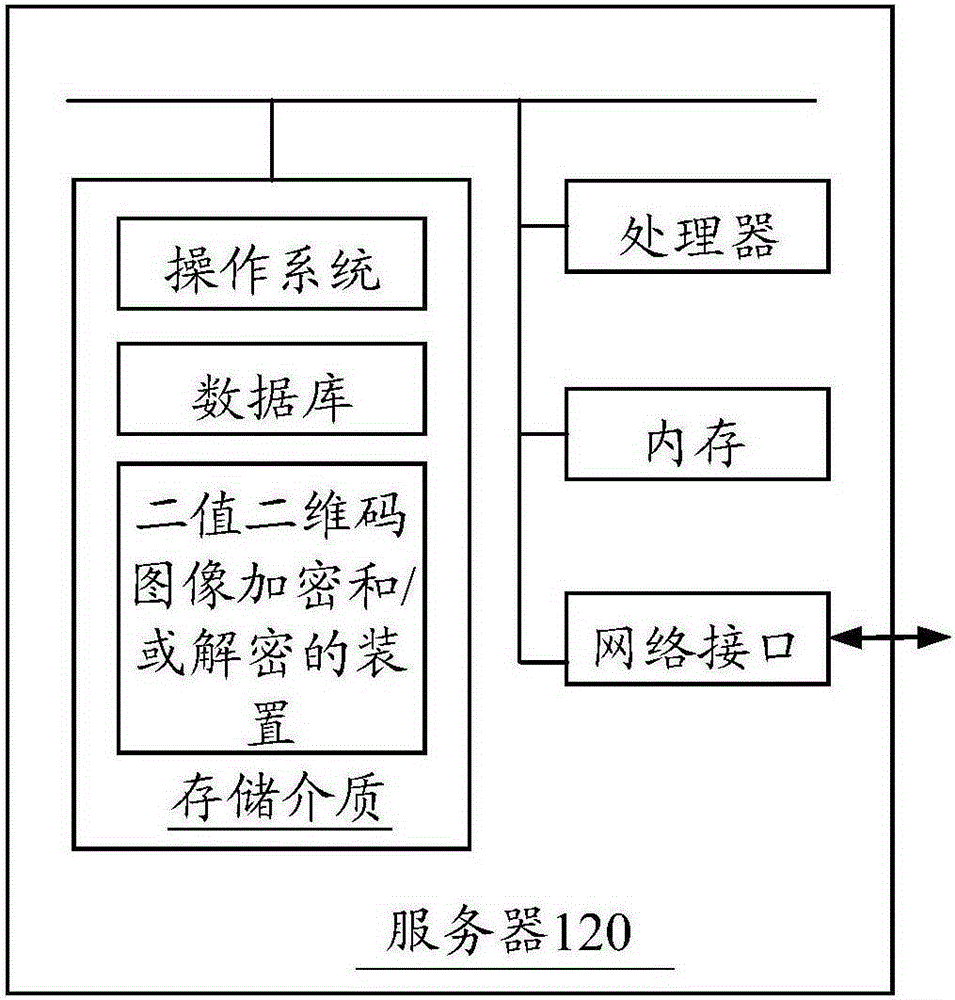
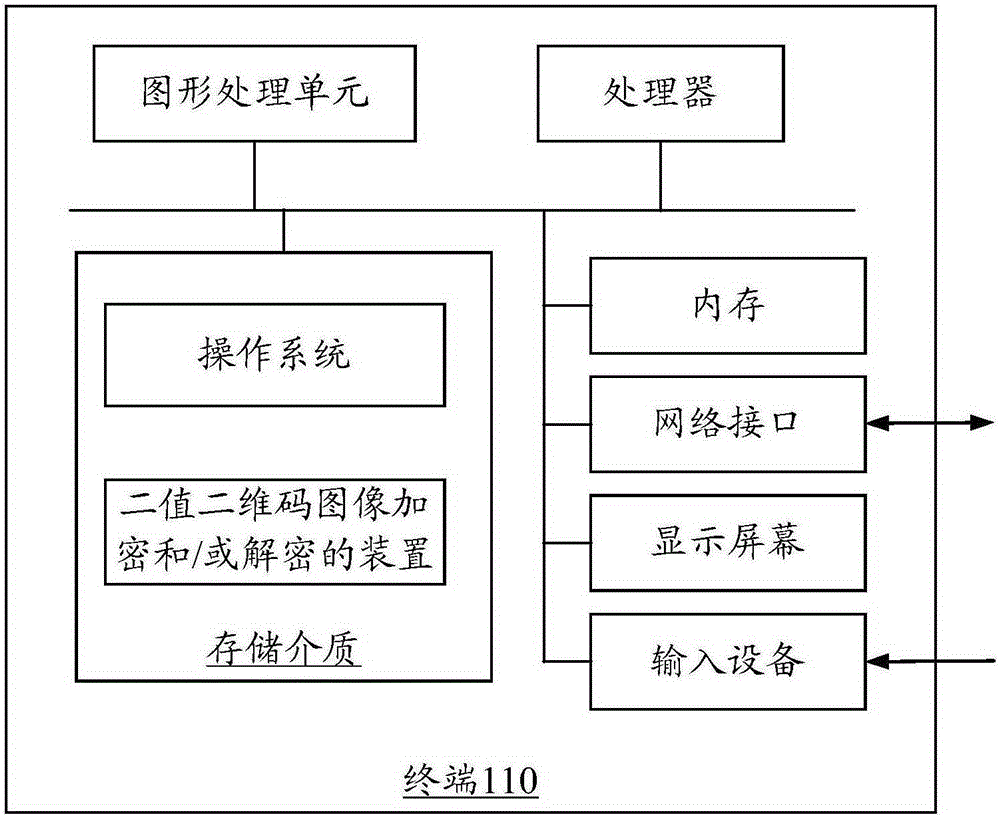
Binary two-dimensional code image encryption and decryption method and device
InactiveCN106651734AImprove securityIncrease the difficulty of decryptionImage data processing detailsRecord carriers used with machinesComputer hardwareMapping algorithm
The invention relates to a binary two-dimensional code image encryption method. The method includes obtaining a two-dimensional image, and generating a binary matrix according to the two-dimensional code image; obtaining a secret key which includes an initial value Z and a starting parameter, wherein the initial value Z is larger than 1, and the starting parameter is between 0 and 1; adopting a Z mapping algorithm to generate a two-dimensional secret key matrix according to the secret key; and performing XOR on elements of the binary matrix and elements of the two-dimensional secret key matrix in one-to-one correspondence to obtain an encrypted two-dimensional code image, decryption difficulty is increased, and security of two-dimensional code information is improved. In addition, a binary two-dimensional code image encryption device and binary two-dimensional code image decryption method and device are also provided.
Owner:CHONGQING UNIV OF POSTS & TELECOMM +1
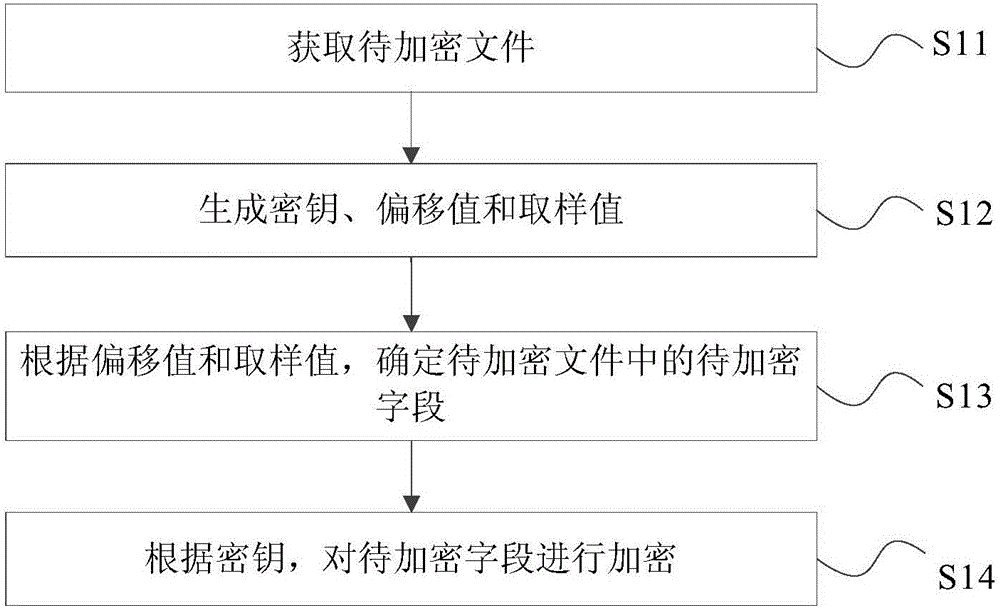
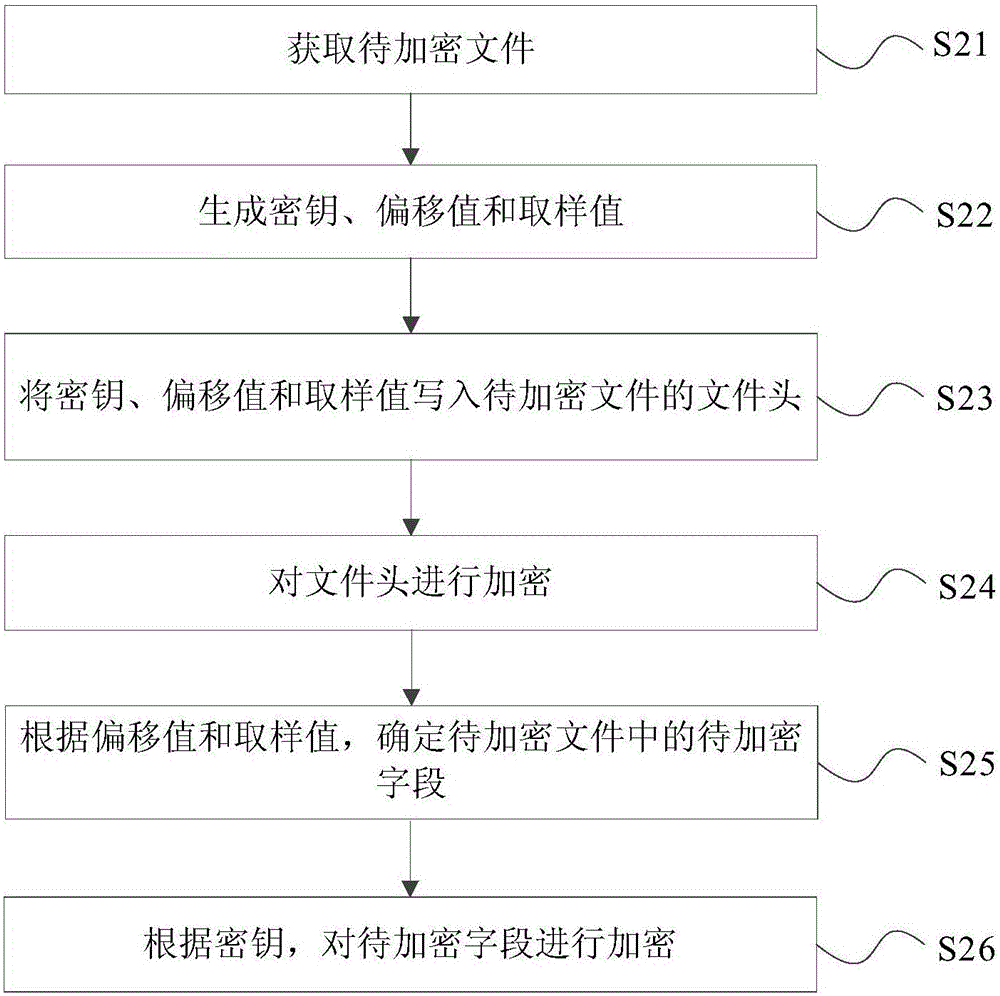
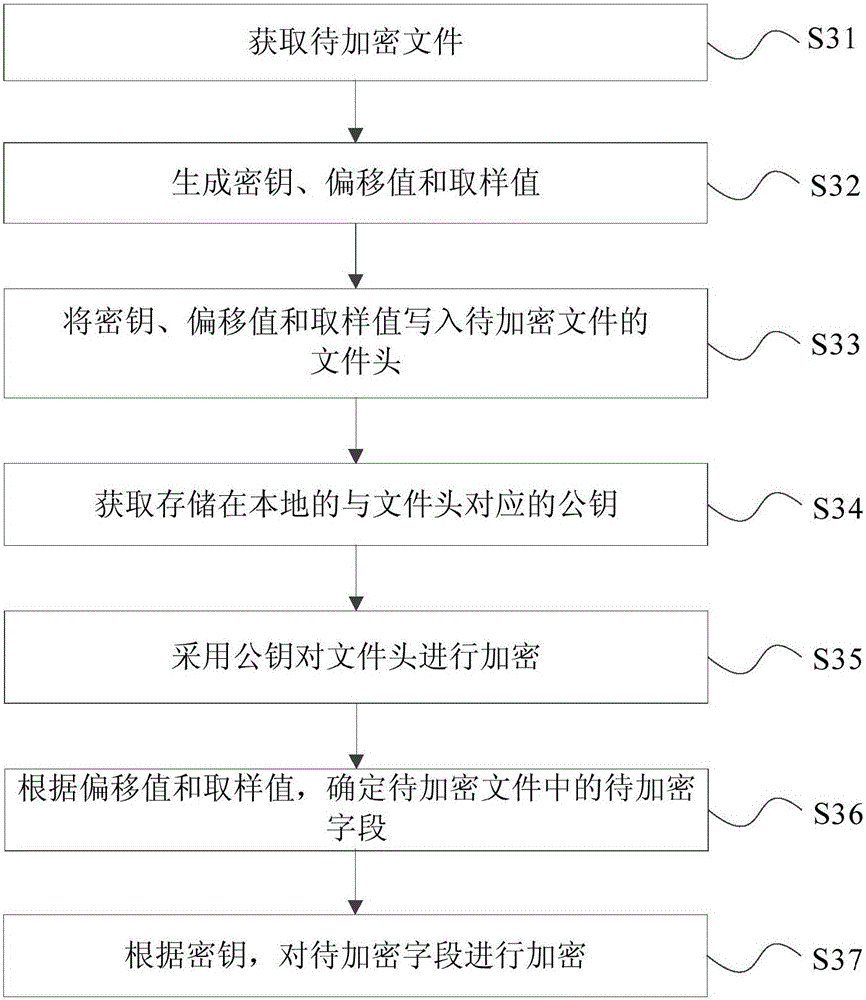
File encryption method, file decryption method, file encryption device and equipment
InactiveCN106372517AAvoid EncryptionImprove encryption efficiencyDigital data protectionComputer hardwareEncryption
The invention discloses a file encryption method, a file decryption method, a file encryption device and equipment. The method comprises the following steps: obtaining a to-be-encrypted file; generating a secrete key, an offset value and a sampling value; determining the to-be-encrypted field in the to-be-encrypted file according to the offset value and the sampling value; and encrypting the to-be-encrypted field according to the secrete key. According to the invention, the file encryption efficiency can be improved.
Owner:BEIJING XIAOMI MOBILE SOFTWARE CO LTD
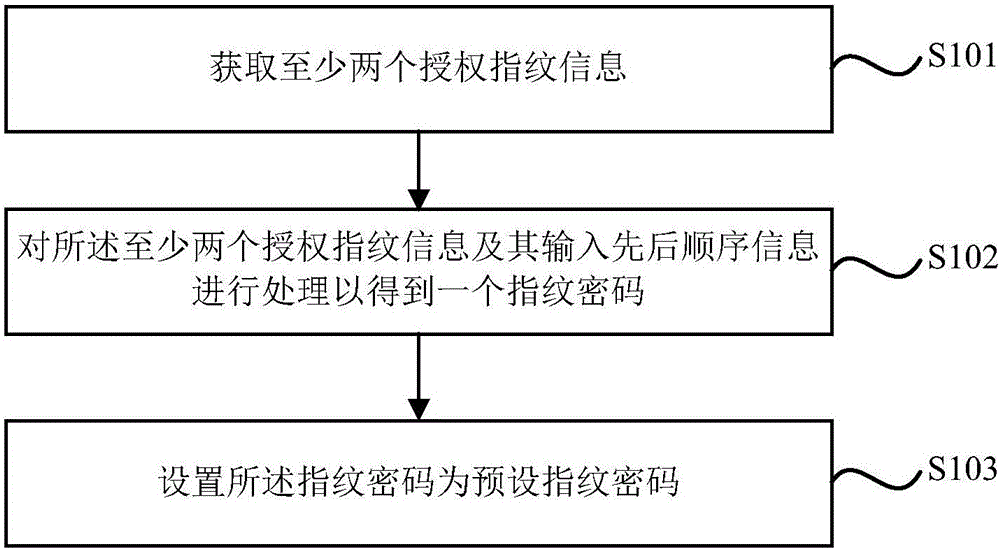
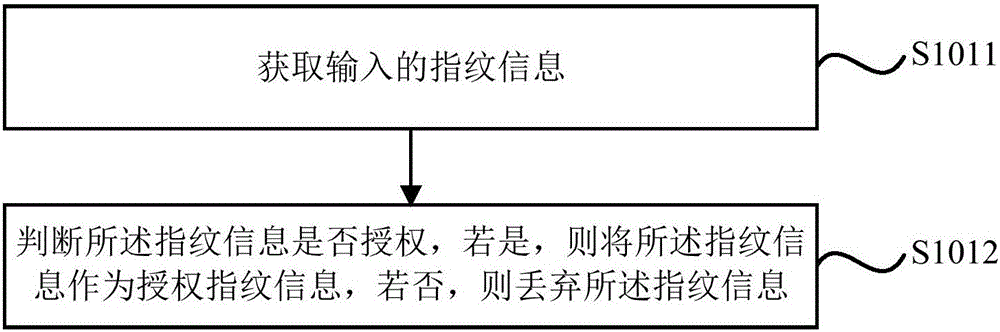
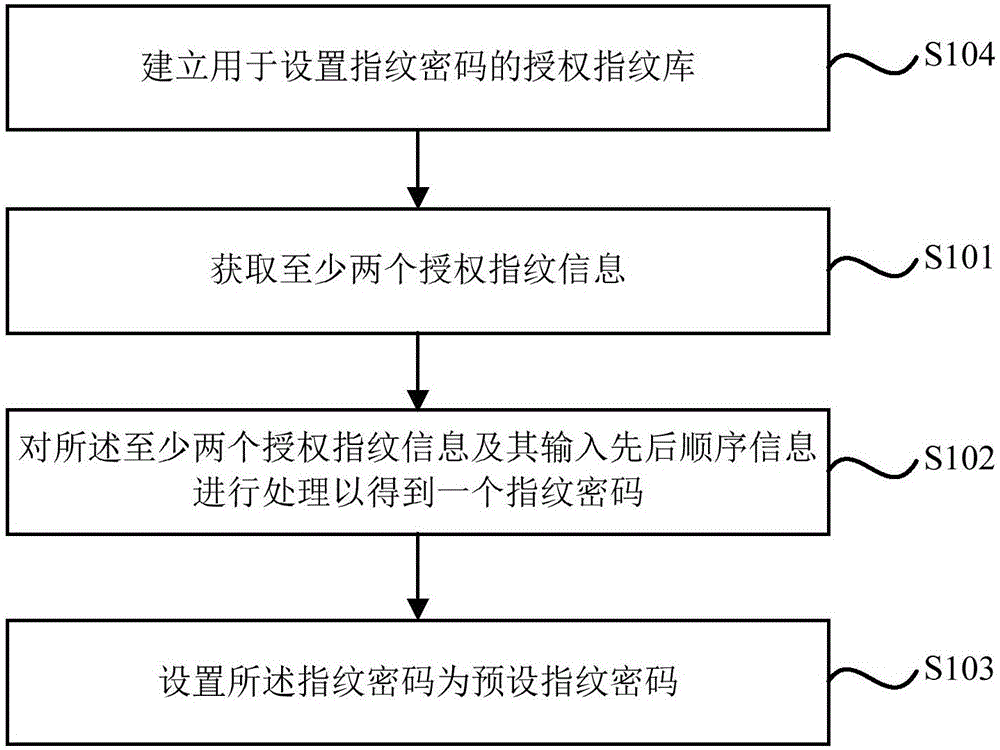
Fingerprint encryption and decryption method and fingerprint encryption and decryption system
InactiveCN106130729AIncrease the difficulty of decryptionImprove security levelKey distribution for secure communicationUser identity/authority verificationPasswordSecurity level
The invention discloses a fingerprint encryption and decryption method and a fingerprint encryption and decryption system. The fingerprint encryption method includes obtaining at least two authorized fingerprint information; processing the at least two authorized fingerprint information and input sequence information to obtain a fingerprint password; setting the fingerprint password as a preset fingerprint password. In the present invention, the fingerprint password is set through the authorized fingerprint information. The fingerprint password not only includes the authorized fingerprint information, but also includes the input sequence information of the authorized fingerprint information, which can increase the difficulty of decrypting the fingerprint password and improve the security level of the fingerprint password.
Owner:SHENZHEN TINNO WIRELESS TECH
Goods tracing anti-counterfeiting coding method
ActiveCN101980186AEnsure safetyUniqueness guaranteedRecord carriers used with machinesSpecial data processing applicationsComputer hardwareBarcode
The invention discloses a goods tracing anti-counterfeiting coding method and solves the technical problems of simple coding method of goods, and large amount of operation. The technical scheme adopted by the invention is that: the method is implemented in a database of a network server by using a computer and a matched software management procedure. The anti-counterfeiting coding method comprises the following steps of: classifying and numbering global goods and storing the numbers in the database of the network server; encrypting the classified numbers and generating check codes first by using a computer memory and the matched encrypt algorithm on the basis of the standard data encrypt algorithm; and encrypting the check codes and finally generating ASII code characters of 16 digits, writing in the radio frequency identification or preparing bar codes, pasting on products and storing in the database of the network server. The anti-counterfeiting coding method has the advantages that: the security, uniqueness and non-replicability of data are guaranteed by adopting the double-encryption manner of encrypting classified numbers and generating check codes and encrypting the check codes again and the deciphering difficulty is increased.
Owner:SHENZHEN JAVS TECH
Data encryption reporting method and device and data decryption method and device
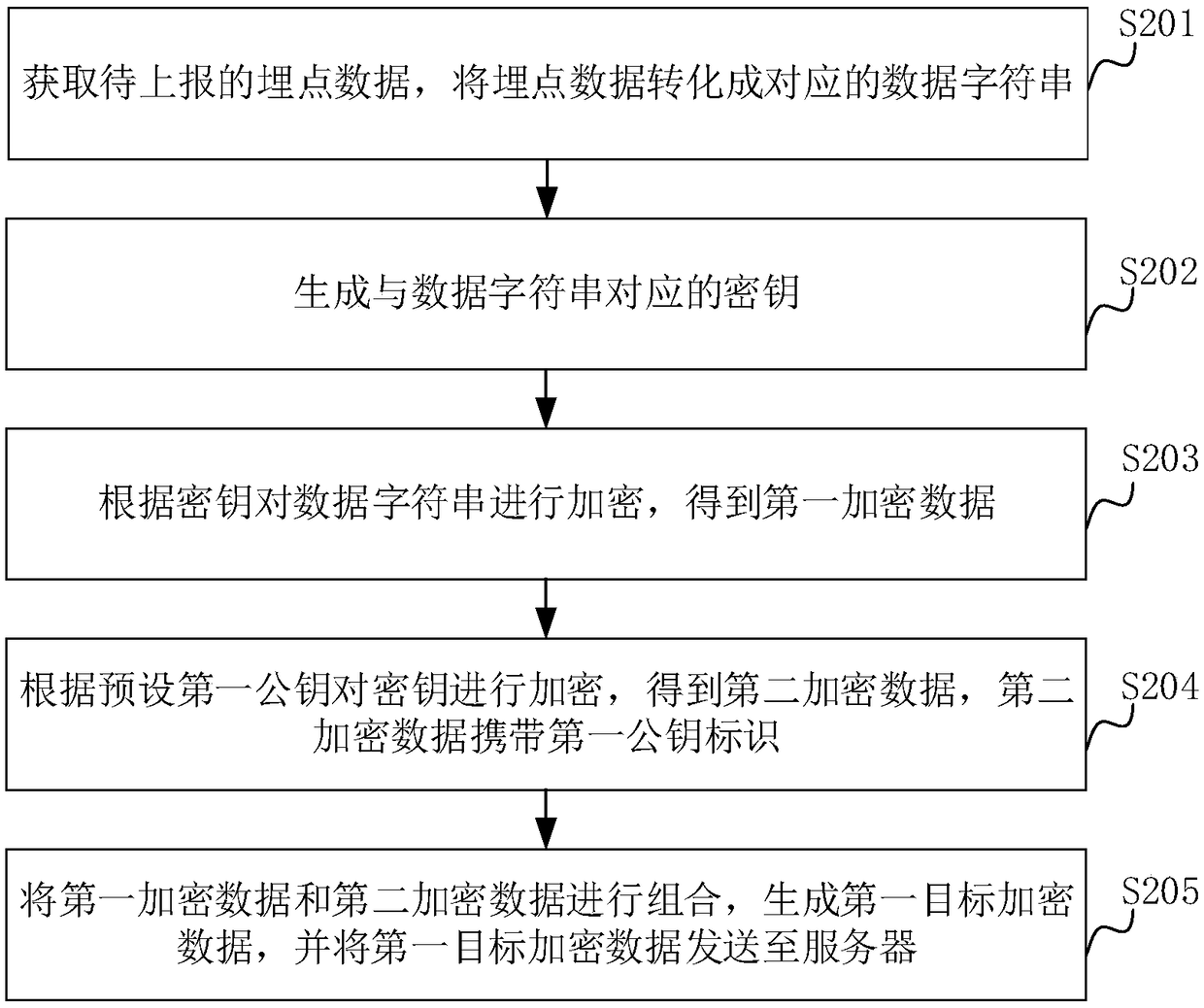
ActiveCN109474619AIncrease the difficulty of decryptionImprove securityTransmissionPublic key certificateData transmission
The invention relates to a data encryption reporting method and device and a data decryption method and device. The method comprises the following steps: obtaining buried point data to be reported, and converting the buried point data into a corresponding data string; generating a key corresponding to the data string; encrypting the data string according to the key to obtain first encrypted data;encrypting the key according to a preset first public key to obtain second encrypted data, wherein the second encrypted data carries a first public key identification; combining the first encrypted data and the second encrypted data to generate first target encrypted data, and sending the first target encrypted data to a server. Based on the cryptography technology, the method realizes the purposeof encrypting the buried point data to be reported, ensures the security of data transmission, avoids the data being stolen, and thus improves the security of the data; at the same time, the generated key is encrypted to further improve the security of the data.
Owner:CHINA PING AN PROPERTY INSURANCE CO LTD
Method for storing and transmitting video file
ActiveCN104836656AEnsure safetyIncrease the difficulty of decryptionSecuring communicationComputer hardwareRelevant information
The invention discloses a method for storing a video file, wherein the method is characterized by segmenting the video file, using a storage key to carry out data encryption to a segment in an xor manner, and randomly and uniformly storing in each resource hard disk of a cluster, generating a plurality of random file segment names, and introducing a combination complexity. The method of the invention can be used for re-encrypting a file segment to be transmitted and then respectively transmitting a segment ciphertext, a deciphering key, and relevant information of the video file via a double-transmission channel when the stored video file is transmitted, and the client end will decipher the downloaded file segment according to the obtained deciphering key. The method of the invention is convenient and efficient for realizing, and high in deciphering difficulty, and simultaneously ensures the safety of file resource in a server end and in a transmission process.
Owner:XIAMEN UNIV
Efficient encryption method and system of data
InactiveCN105809046AEncryption guaranteedGood encryptionDigital data protectionComputer hardwareOriginal data
The invention relates to an efficient encryption method and system of data. The encryption method of the data splits original data into at least two parts of data according to a preset rule, wherein the splitting is that the original data is split according to the preset rule according to a discontinuous way and is spliced again to obtain at least two parts of data. The invention also discloses a corresponding decryption method, an encryption and decryption storage system and the like. Since various combination ways are arranged, decryption difficulty is high after encryption is carried out, an original encryption index is enhanced manifold, and a data encryption effect is guaranteed. In addition, the data only needs to be split, and therefore, a good encryption effect can be performed. In addition, the encryption method is small in operation amount and high in encryption and decryption efficiency.
Owner:成都科创知识产权研究所
Metasurface structure design method realizing multi-dimensional optically manipulative image transformation
InactiveCN110133758AImplement image transformation operationsAvoid crosstalkPolarising elementsLength waveMulti dimensional
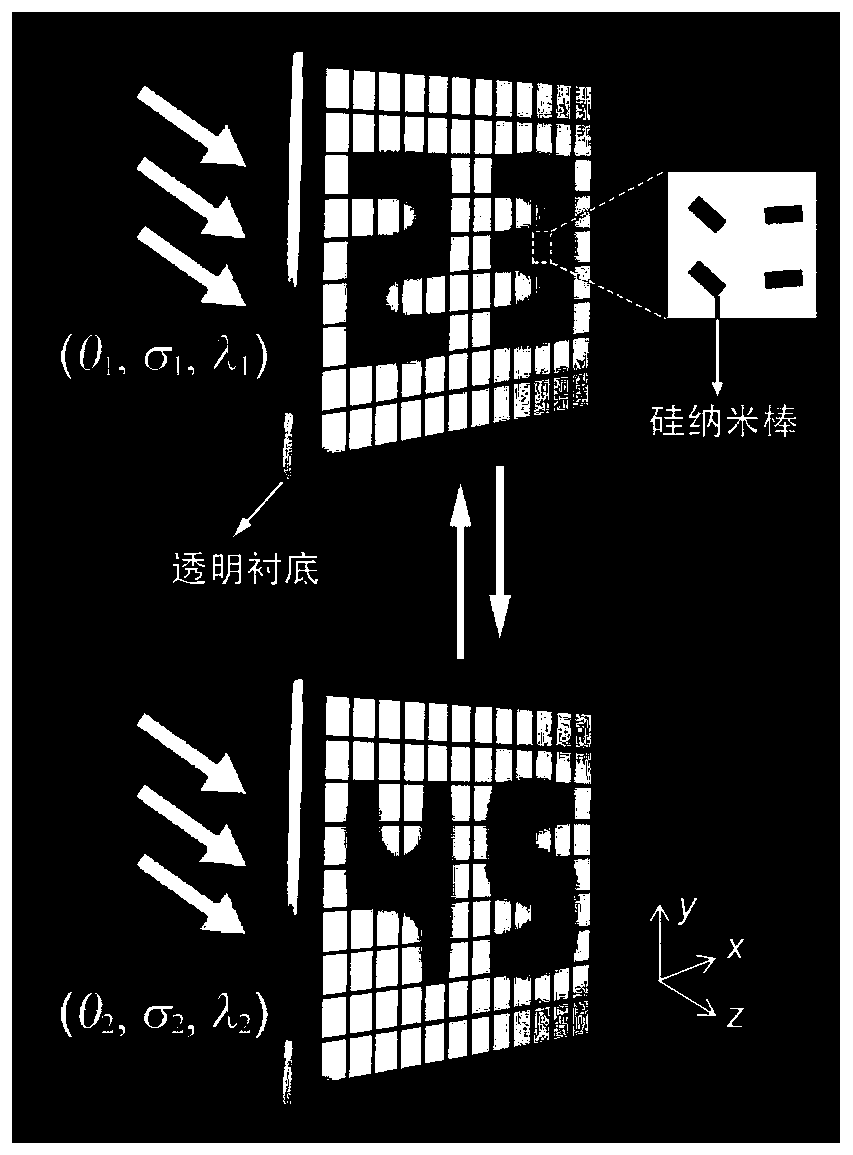
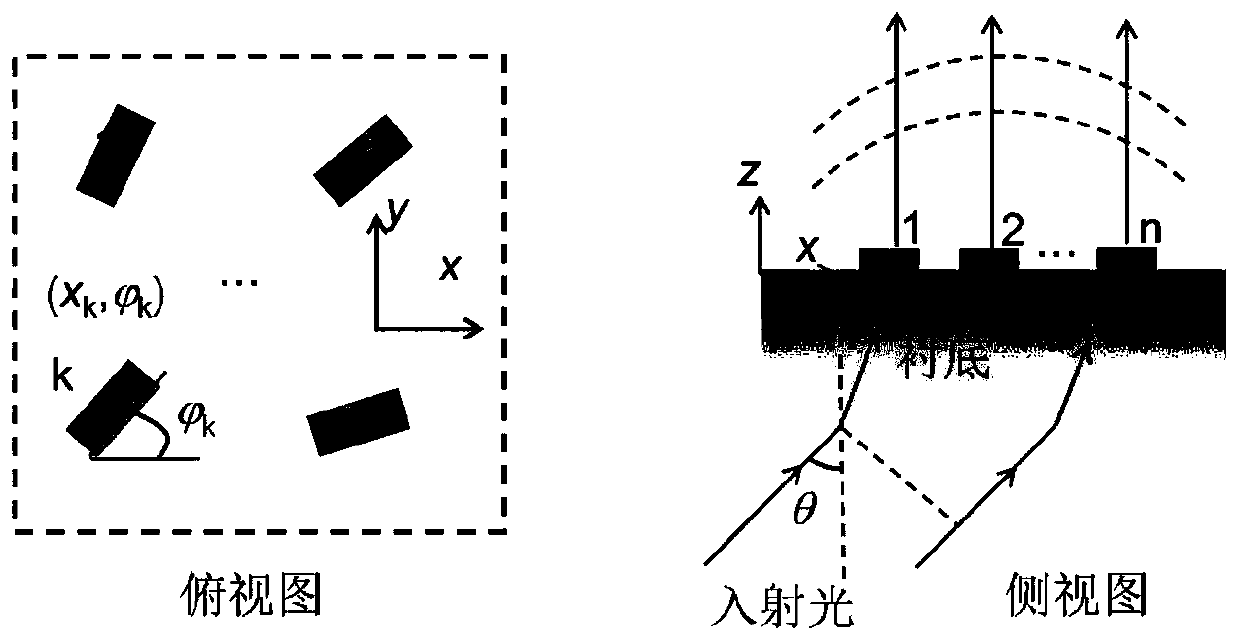
The present invention relates to the technical field of optical devices based on an artificial metasurface structure, more specifically, the invention relates to a metasurface structure design methodrealizing multi-dimensional optically manipulative image transformation. A metasurface structure composed of structural units is constructed on a transparent substrate; pixels of the metasurface structure are formed by the coherent interference among the structural units; a Jones matrix J is obtained for the structural unit with a rotation angle of phi; according to the incident light acting on the structural unit, a scattering factor of the incident light is obtained on the basis of the Jones matrix J of the structural unit; considering the pixels composed of the n structural units, when theincident light is incident on the transparent substrate at the incident angle theta, the wavelength lambda and the polarization state sigma, the intensity of the pixels of the metasurface is formed bythe coherent interference of all the structural units; and the multi-dimensional optically manipulative image transformation function of the metasurface structure is realized. The invention can realize the image transformation with any multi-dimensional optical parameters and solves the image crosstalk problem.
Owner:SUN YAT SEN UNIV
Information processing method and device based on characteristics of information, equipment and medium
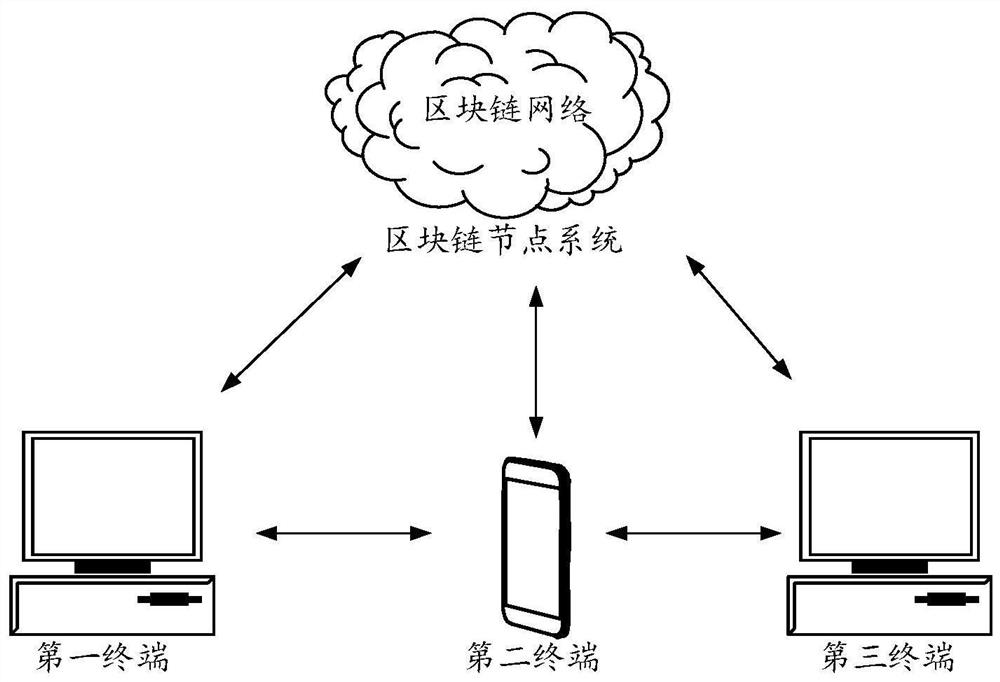
ActiveCN112184444AImprove securityAvoid crackingFinanceDatabase distribution/replicationInformation processingCiphertext
The embodiment of the invention discloses an information processing method and device based on information features, equipment and a medium, and mainly relates to a block chain technology and a hospital management technology, and the method comprises the steps: obtaining a target function for describing information and feature information of target information; dividing the target information according to the feature information of the target information to obtain at least two pieces of sub-information; obtaining a random number corresponding to each piece of sub-information, and adjusting each piece of sub-information according to the random number to obtain each piece of adjusted sub-information; according to the target function and each piece of adjusted sub-information, obtaining coordinate information corresponding to each piece of sub-information in the at least two pieces of sub-information; encrypting the coordinate information corresponding to each piece of sub-information inthe at least two pieces of sub-information to obtain a cipher text of the coordinate information corresponding to each piece of sub-information; and determining the cipher text as the cipher text of the target information, and storing the cipher text of the target information in the block chain network. By adopting the embodiment of the invention, the information security can be improved.
Owner:PING AN TECH (SHENZHEN) CO LTD
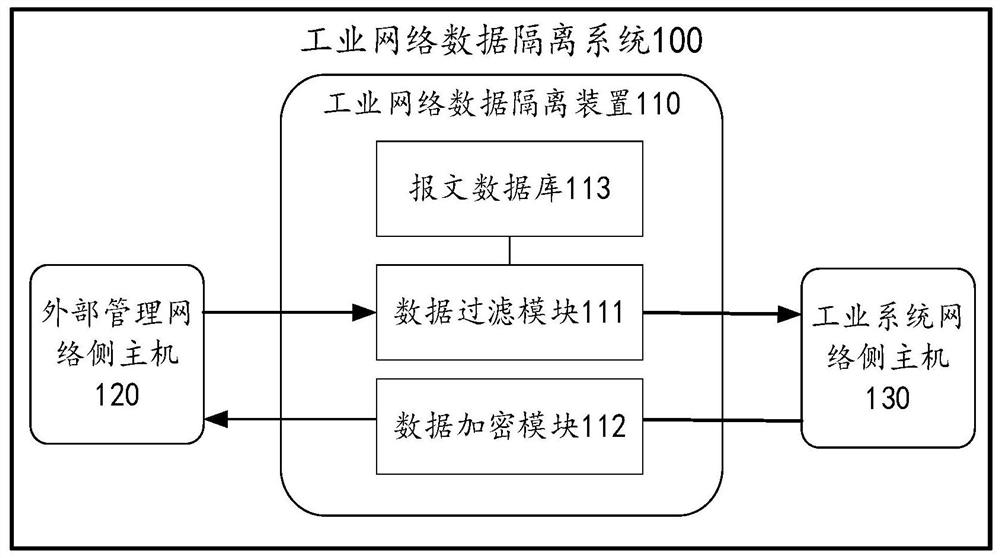
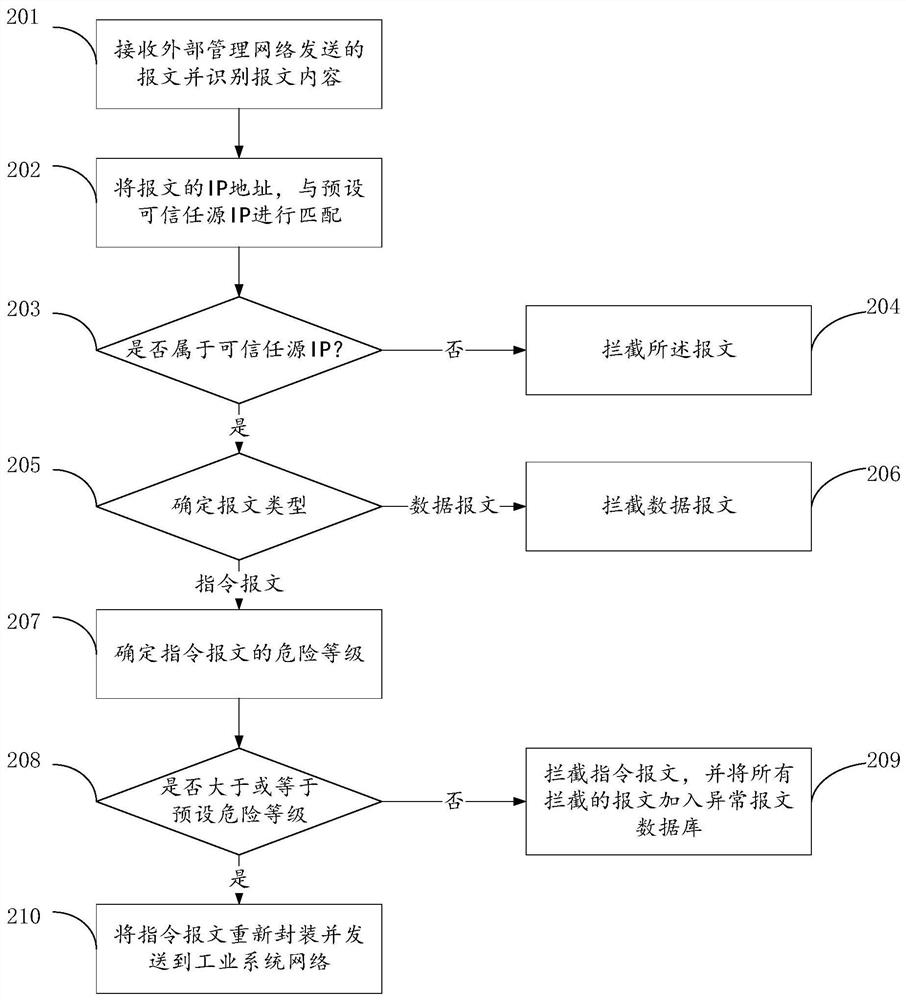
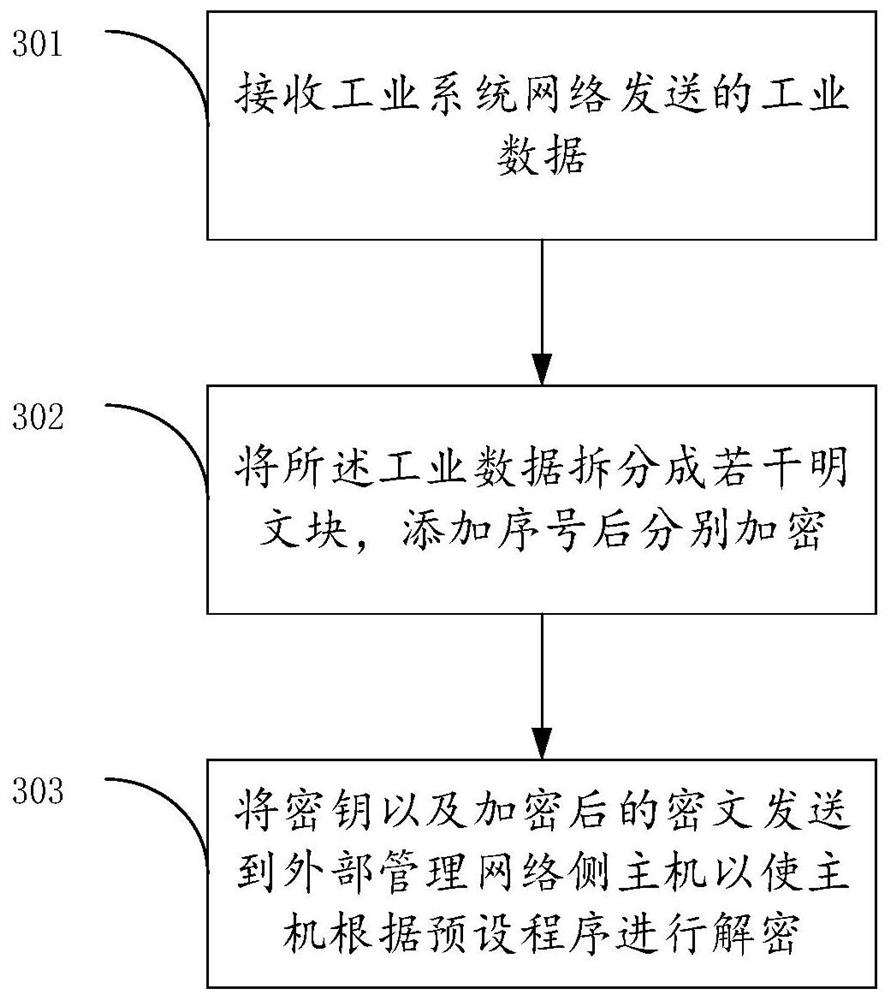
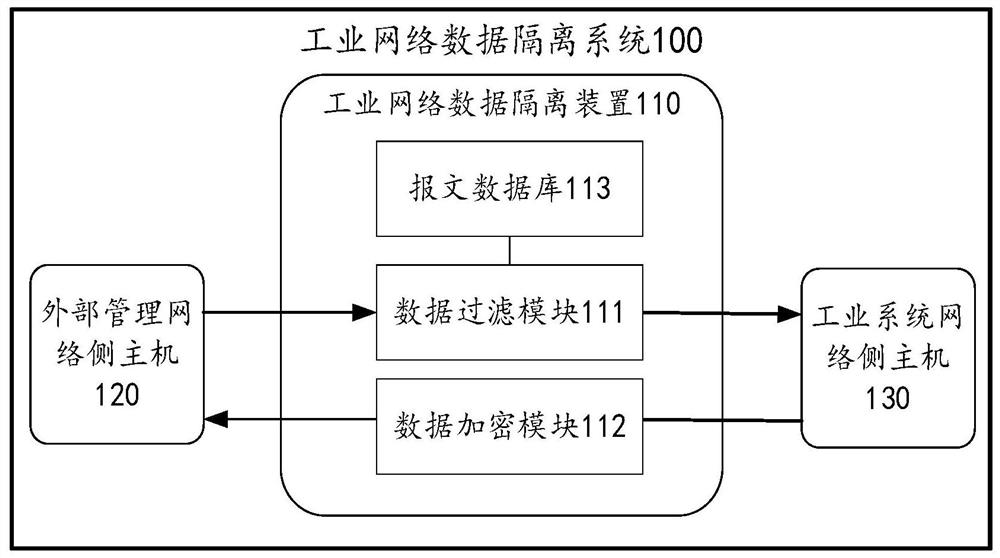
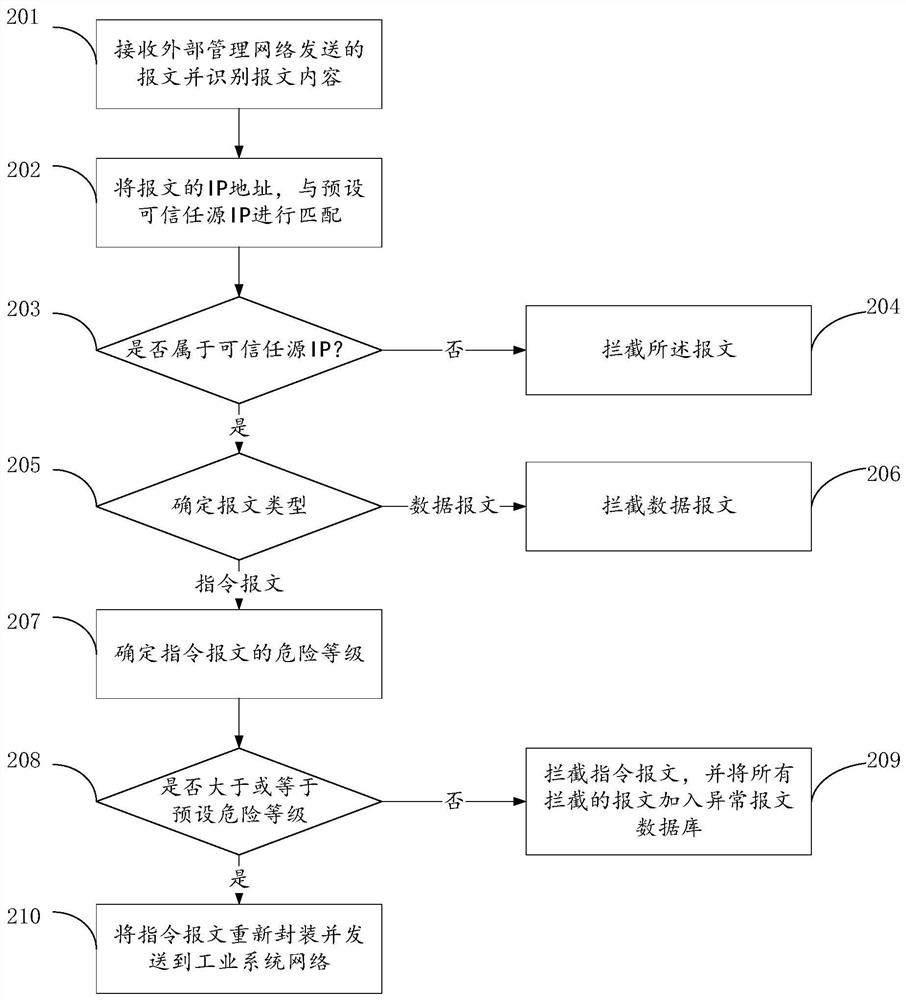
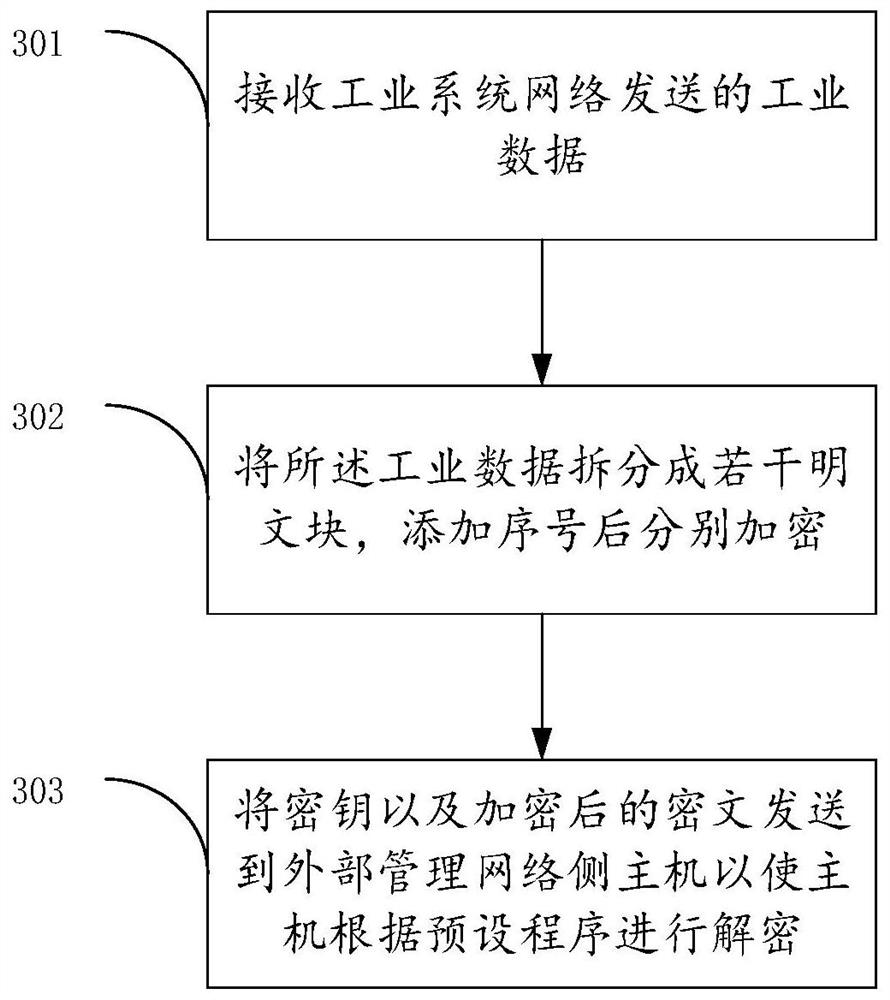
Industrial network data isolation method, device and storage medium
The invention provides an industrial network data isolation method, a device and a storage medium. The method comprises the following steps: receiving a message sent by an external management network side host, and determining the type of the message under the condition that the source IP address of the message belongs to the trusted source IP address range; under the condition that the type of the message is an instruction message, determining a danger level of the instruction message; under the condition that the danger level of the instruction message is lower than a preset danger level, sending the instruction message to an industrial system network side host; receiving industrial data sent by the industrial system network side host, performing data encryption on the industrial data, and sending the encrypted ciphertext and the key to the external management network side host to enable the external management network side host to decrypt the ciphertext; wherein the safety level of the external management network is lower than that of the industrial system network. The isolation effect of data isolation of an industrial system is improved.
Owner:山东云天安全技术有限公司
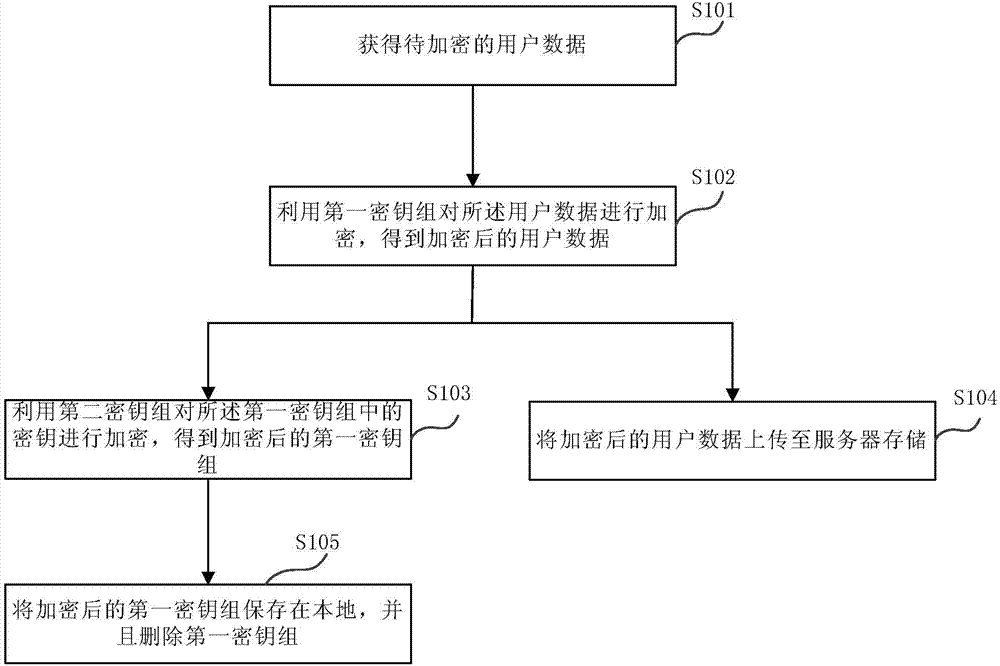
User data encryption method and device
InactiveCN103795547AIncrease the difficulty of decryptionImprove securityUser identity/authority verificationEncryption
The embodiment of the invention discloses a user data encryption method and device. The method comprises the steps of acquiring user data to be encrypted, using a first secret key set for encrypting the user data to obtain the encrypted user data, using a second secret key set for encrypting secret keys in the first secret key set to obtain the encrypted first secret key set, updating the encrypted user data to a server to be stored, storing the encrypted first secret key set locally, and deleting the first secret key set. The user data encryption method and device are used, even though a hacker obtains the encrypted user data and the encrypted first secrete key set, the encrypted user data can not be decrypted through the encrypted first secrete key set to obtain original user data, the decryption difficulty of the user data is improved, and therefore the safety of the user data is improved.
Owner:BEIJING KINGSOFT NETWORK TECH
Terminal encryption method and apparatus and terminal decryption method and apparatus
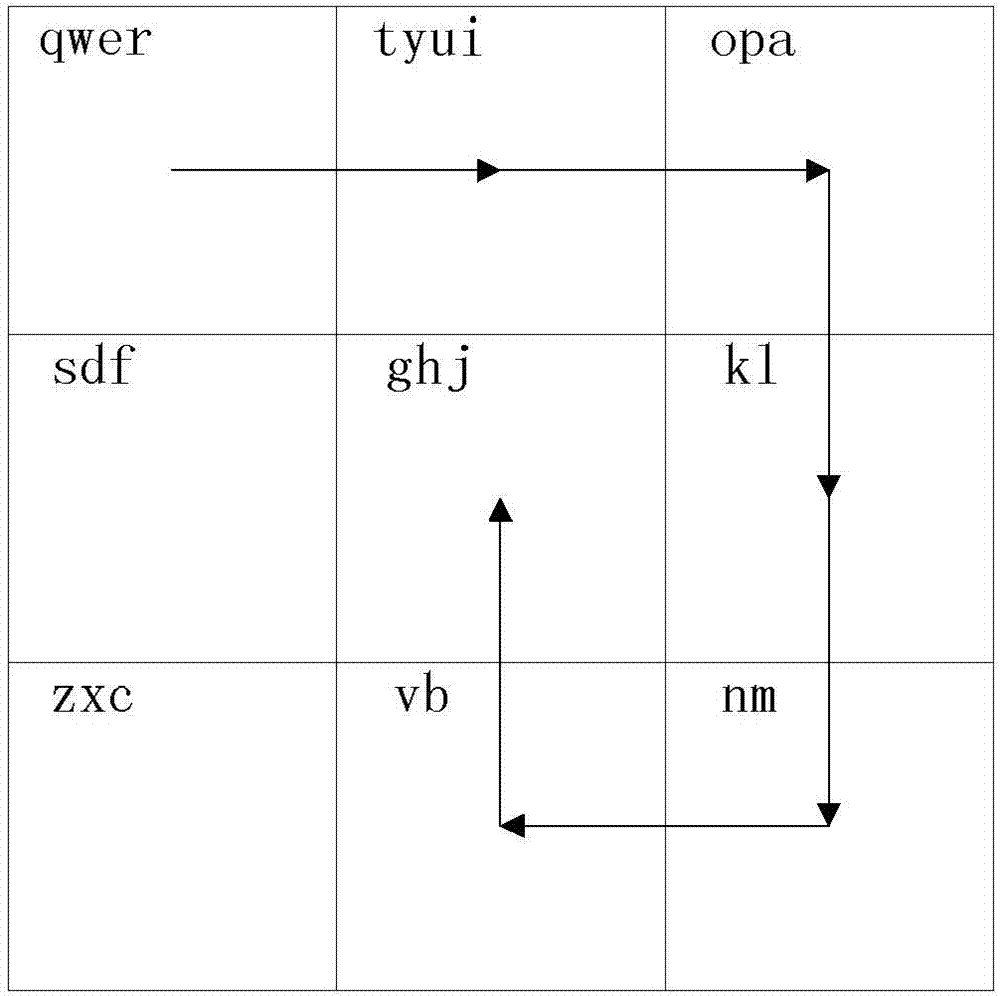
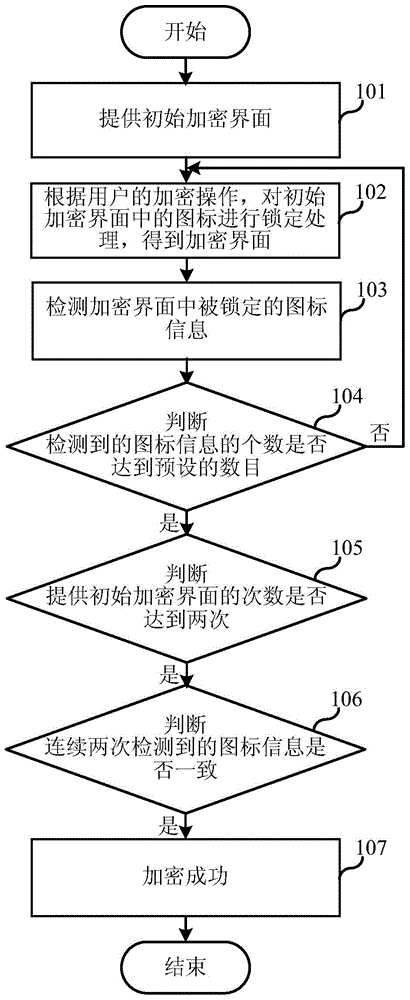
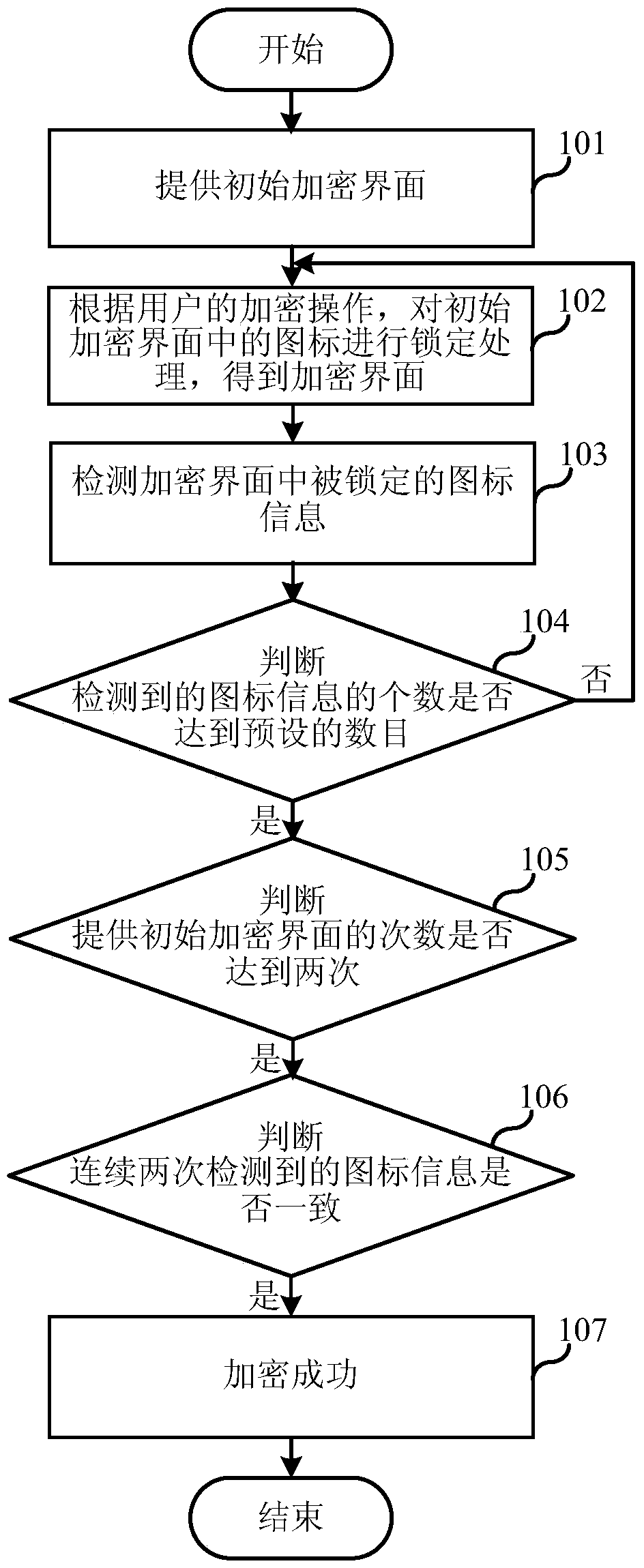
ActiveCN104966014AIncrease the difficulty of decryptionDigital data authenticationPasswordComputer terminal
The present invention relates to the technical field of electronic information and discloses a terminal encryption method and apparatus and a terminal decryption method and apparatus. According to the terminal encryption method and apparatus and the terminal decryption method and apparatus, the terminal decryption method comprises the following steps that: an initial decryption interface is provided, wherein the initial decryption interface comprises a plurality of different icons; according to decryption operation of a user, shift processing is carried out on the icons in the initial decryption interface to obtain a verification decryption interface; icon information of a password position in the verification decryption interface is acquired; and when the icon information is the same as password information, decryption succeeds. Compared to the prior art, the terminal authorization security can be improved and privacy information of the user is protected.
Owner:HUAQIN TECH CO LTD
Dynamic encrypting method realizing one secrete key for one file
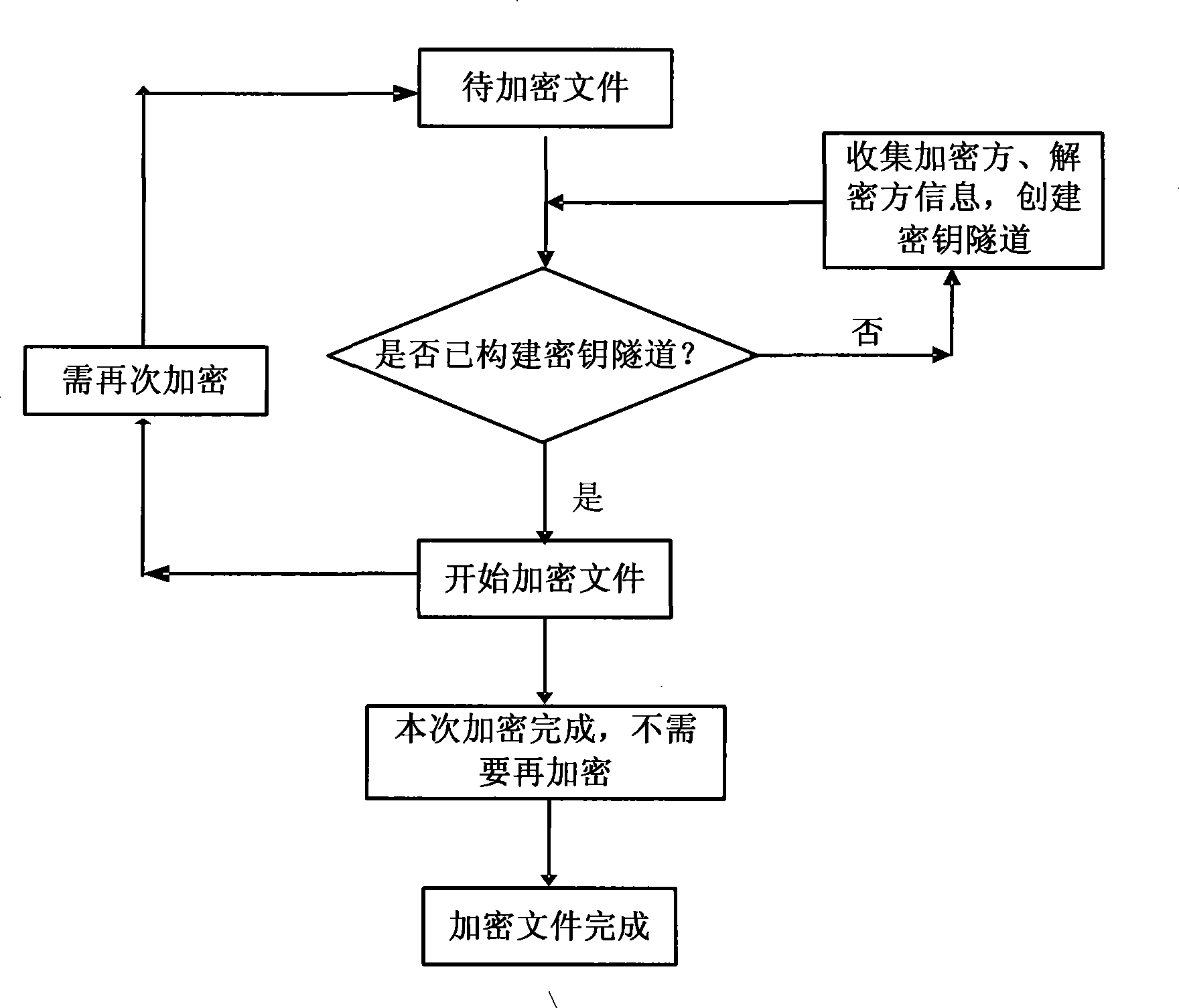
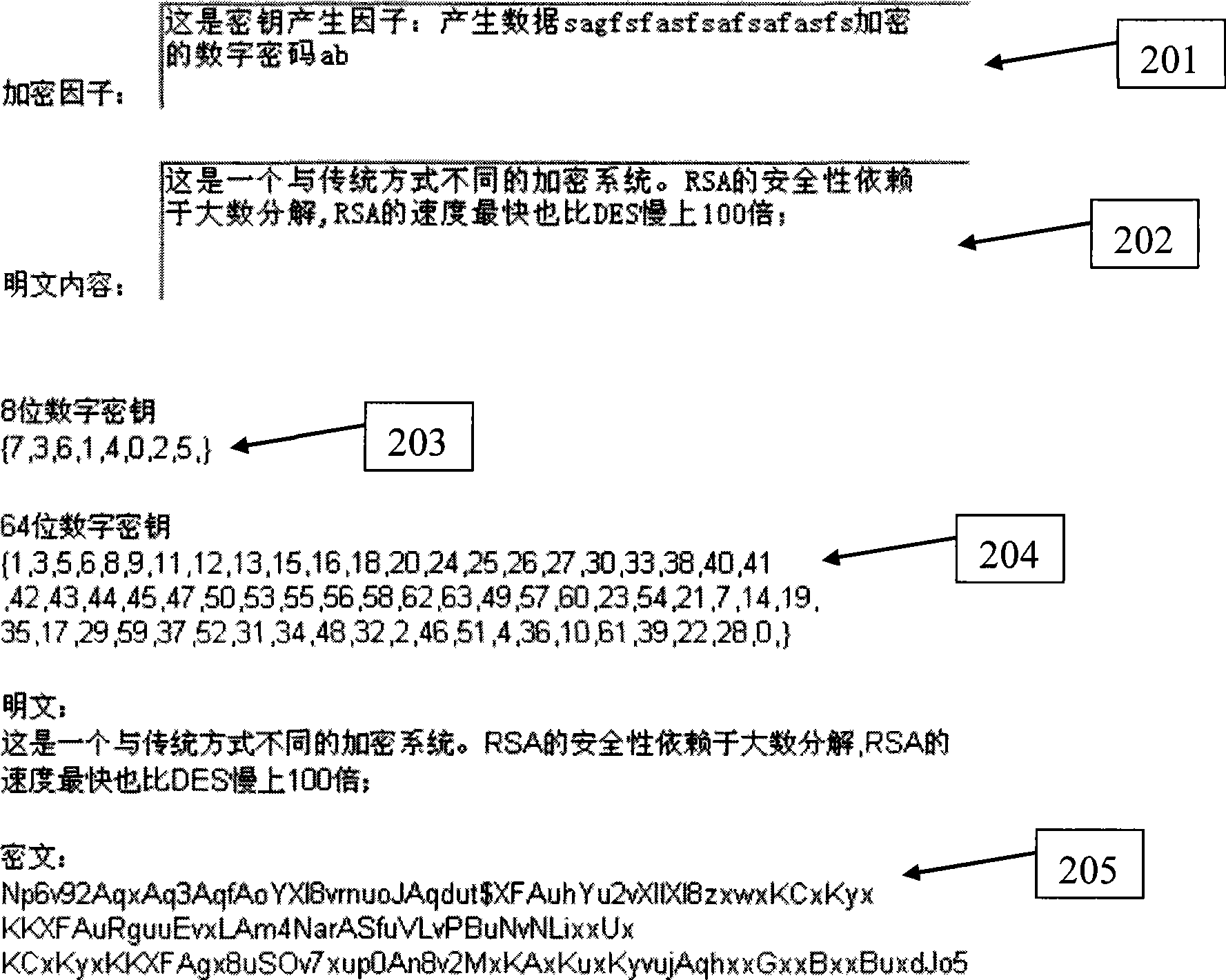
InactiveCN101534191AFast encryptionIncreased encryption complexityKey distribution for secure communicationComputer hardwareEncryption
The invention pertains to the technical field of computer encryption, more particularly relates to a dynamic encrypting method realizing one secret key for one file. The encrypting method comprises the following steps: (1) according to the agreement of the information encrypting party and the information decrypting party, an encryption factor program module establishes a secret key tunnel; an encryption factor is obtained by extracting the state information of the information encrypting party and the information decrypting party and the agreement between the two parties, and then the encryption factor is respectively mapped in 8D space and 64D space, thus obtaining two spatial positions; and the coordinate values corresponding to the two spatial positions are the extracted secret key; (2) in a system, a spatial switching program module maps a computer file to space specified by a first secret key group, thus obtaining a new mapping file; (3) in the system, a decimal conversion program module processes the mapping file according to the way specified by a second secret key group.
Owner:北京乾坤化物数字技术有限公司
Encryption method, device and equipment based on features of information and storage medium
PendingCN112131593AIncrease the difficulty of decryptionImprove securityFinanceSemantic analysisCiphertextEngineering
The embodiment of the invention discloses an encryption method, device and equipment based on features of information and a storage medium, and the method comprises the steps: obtaining a target function for describing information, and the feature information of to-be-processed target information; dividing the target information according to the feature information of the target information to obtain at least two pieces of sub-information; obtaining coordinate information corresponding to each piece of sub-information in the at least two pieces of sub-information according to the target function; encrypting the coordinate information of each piece of sub-information in the at least two pieces of sub-information to obtain a ciphertext of the coordinate information corresponding to each piece of sub-information; and determining the ciphertext of the coordinate information corresponding to each piece of sub-information as the ciphertext of the target information, and storing the ciphertext of the target information in a blockchain network. By adopting the method, the security of the target information can be improved, the method is suitable for the field of smart medical treatment, and the construction of smart cities can be further promoted.
Owner:ONE CONNECT SMART TECH CO LTD SHENZHEN
Multiparameter three-dimensional digital encryption method
InactiveCN103401684AIncrease the difficulty of decryptionOvercoming complexitySecuring communicationOriginal dataXML Encryption
The invention relates to the field of computer scrambling coding theory and communication, and provides a multiparameter three-dimensional digital encryption method, which includes the following steps: based on original data in a computer storage and according to the arbitrary carry number and integer computational formula, a plurality of encryption keys of original data can be obtained through the FPGA, then the original data can be stored in a three-dimensional coordinate enciphered data represented by encryption keys, and besides an encryption key and original data storage sequence linear list is formed and communicated with enciphered data through a network, so that the data encryption is realized. The encryption method adopts a simple computational formula, has many encryption parameters and great difficulty in decryption, and overcomes the deficiencies that the former asymmetric encryption computational formula is complex, is limited to word length and causes high possibility of forming decimals as no decimal is formed in the calculating parameters.
Owner:DALIAN UNIV OF TECH
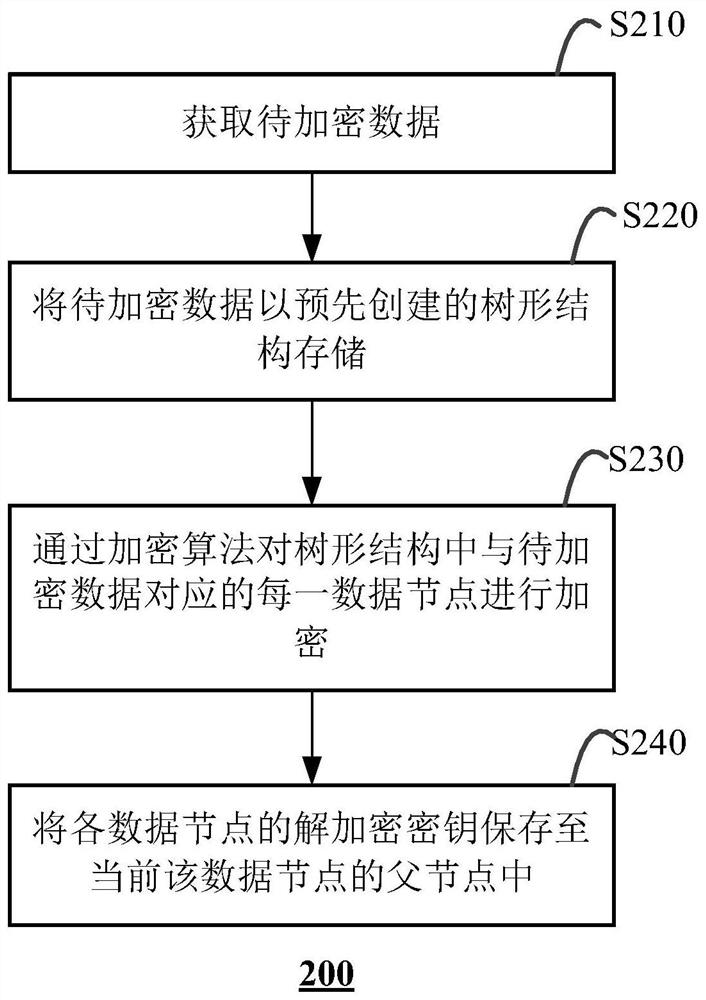
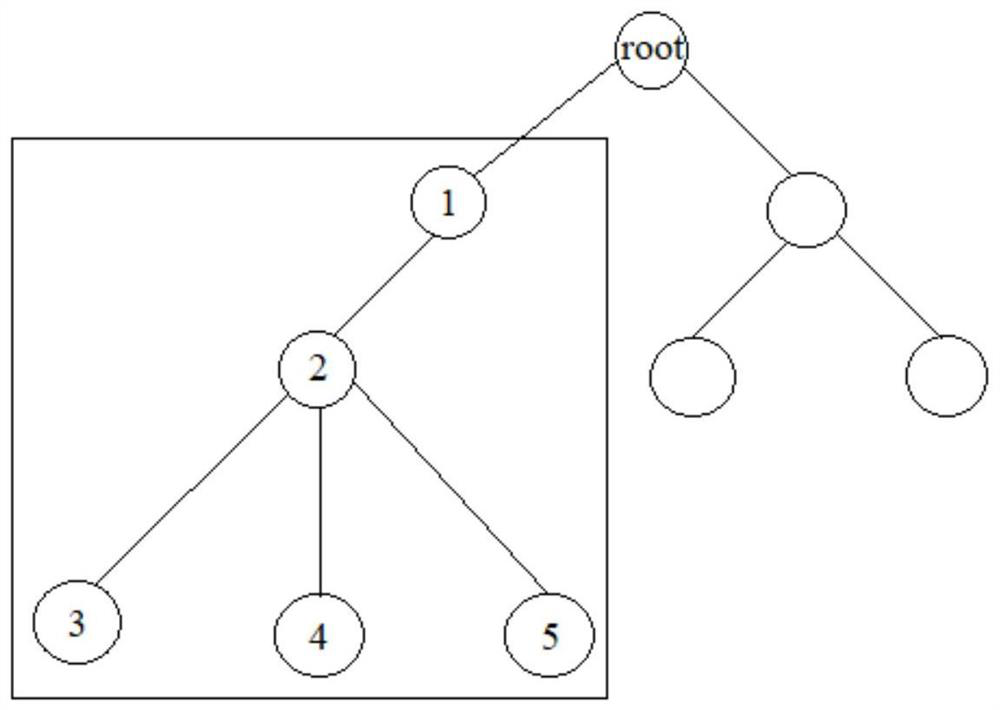
Data encryption method and computing equipment
ActiveCN113139195AImprove securityAchieve protectionDigital data protectionTheoretical computer scienceEngineering
The invention discloses a data encryption method and computing equipment. The method comprises the following steps: acquiring to-be-encrypted data; storing the to-be-encrypted data in a tree structure, wherein the maximum storage capacity of each node in the tree structure is the same, and all leaf nodes except the rightmost leaf node in the tree structure store the data with the maximum capacity; encrypting each node corresponding to the to-be-encrypted data in the tree structure through an encryption algorithm; and storing the encryption key of each node in a father node of the node. According to the method, the to-be-encrypted data is divided into the plurality of data blocks, the data blocks are stored in the tree structure, each node in the tree structure stores the data block or the data block pointer, and each node in the tree structure is encrypted, so that metadata and real data are protected, and the security of data encryption is improved. Moreover, the encryption key of each node is stored in the father node of the node, so that the decryption difficulty is high, and the security of data encryption is further improved.
Owner:UNIONTECH SOFTWARE TECH CO LTD
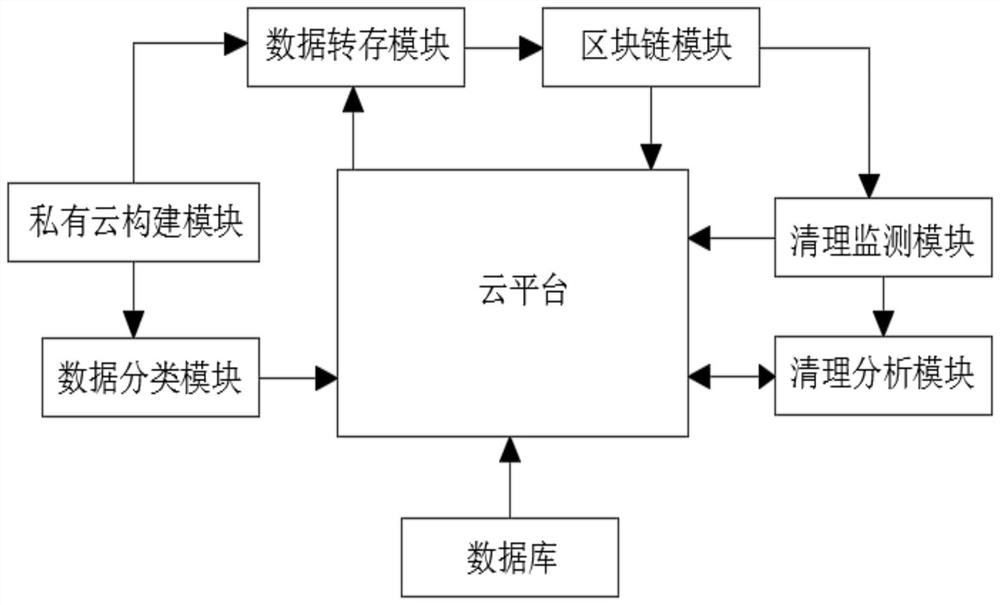
Industrial internet data encryption storage system
PendingCN114817962AImprove securityPrevent leakageInput/output to record carriersDatabase distribution/replicationThe InternetIndustrial Internet
The invention discloses an industrial internet data encryption storage system, which relates to the technical field of data storage and comprises a data classification module, a data transfer module and a storage distribution module. The data classification module is connected with the private cloud and is used for carrying out storage grade analysis on the industrial internet data stored in the private cloud, if a storage grade value is greater than or equal to a storage threshold value, marking the corresponding industrial internet data as core data, and initiating encryption transfer of the corresponding core data; the data transfer module is used for randomly splitting the corresponding core data into a corresponding number of data blocks according to the storage level value, encrypting the corresponding data blocks and then storing the encrypted data blocks in the block chain module in a distributed manner; the block chain module comprises a plurality of storage blocks and is used for screening out a corresponding number of storage blocks as selected blocks according to the size of the storage and allocation values and carrying out distributed storage on the data blocks; the possibility that the data blocks are cleaned is effectively reduced, other users can conveniently inquire, and the data storage efficiency is improved.
Owner:万申科技股份有限公司
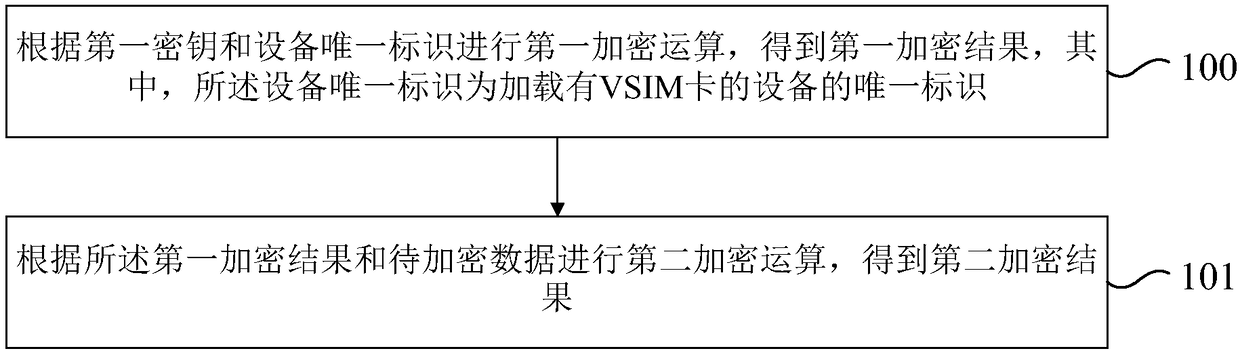
Data encryption method and device of VSIM card
ActiveCN108155993AStop cloningAvoid crackingKey distribution for secure communicationMultiple keys/algorithms usageComputer hardwareCiphertext
The invention relates to a data encryption method and device of a VSIM card, which are characterized by conducting a first encoding operation according to a first key and an only mark loaded with theVSIM card of the device, and obtaining a first encoding result; then conducting a second encoding operation according to the first encoding result and data to be encoded, and obtaining a second encoding result. The data to be encoded which is loaded with the VSIM card device is associated with the only mark of the device so that the second encoding result cannot be declassified when other hardwaredevices cannot obtain the only mark of the device, and therefore the data to be encoded is effectively prevented from being cloned by other devices. Meanwhile, the encryption algorithm forms multipleencryption, which increases decryption difficulties and effectively prevents cipher text from being declassified. In addition, no extra chip is needed so that cost is low, safety is high, and generality is sound.
Owner:广东树米科技有限公司 +2
Anti-fake tracing method based on hyper-elliptic curve cryptosystem
ActiveCN105450399AEnsure safetyUniqueness guaranteedPublic key for secure communicationCryptosystemHand held devices
The invention discloses an anti-fake tracing method based on a hyper-elliptic curve cryptosystem. The anti-fake tracing method comprises the following steps: setting a production enterprise code, a date code and a specification code; performing encryption conversion on the production enterprise code, the date code and the specification code through a conversion method of system conversion and section partition; performing permutation and combination on section identification codes and authentication type codes in the production enterprise code, the date code and the specification code and generating a check code; taking an elliptic cure cryptosystem as a public key infrastructure platform, designing the tracing method and using a C / S architecture; a system distributes a public key and a private key to a handheld device, and during decoding, the handheld device inquires the public key and the private key to a server, compared with the existing anti-counterfeit technology, the anti-fake tracing method based on the hyper-elliptic curve cryptosystem provided by the invention has the advantages of being large in data volume and difficult to be imitated; besides, the security, the uniqueness and the unduplicatedness of data are guaranteed, the decoding difficulty is increased and the anti-falsification is strong.
Owner:SHANDONG ACADEMY OF AGRI MACHINERY SCI
Control method and system for engine control unit to manage loan vehicle
PendingCN111815431AControl operating conditionsControl regulationFinanceTransmissionControl cellEmbedded system
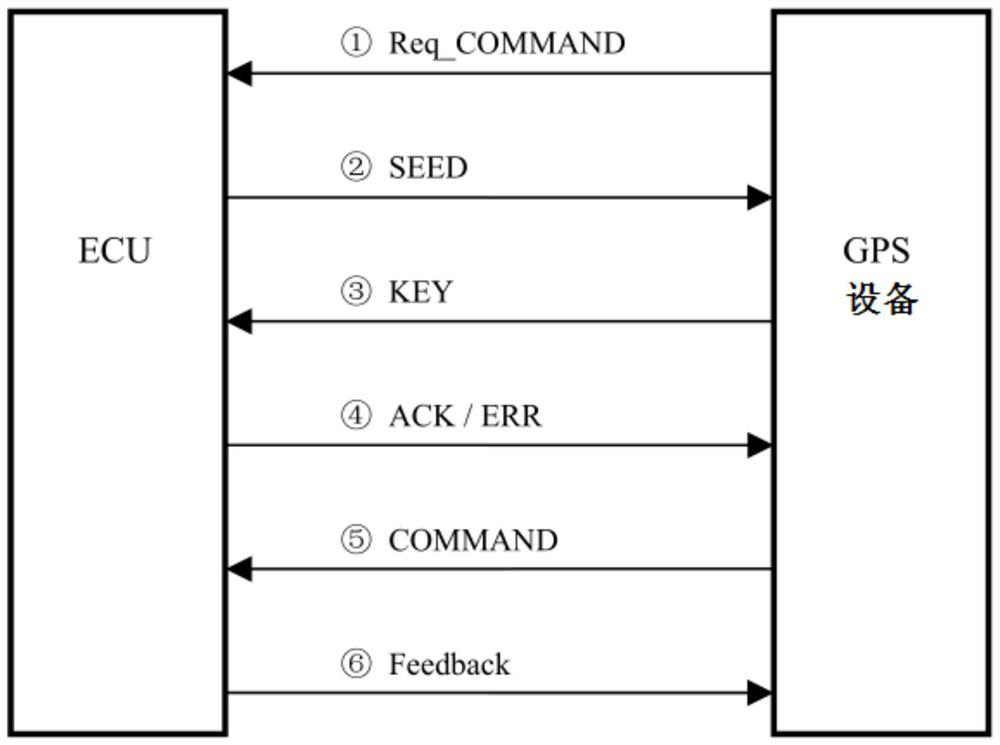
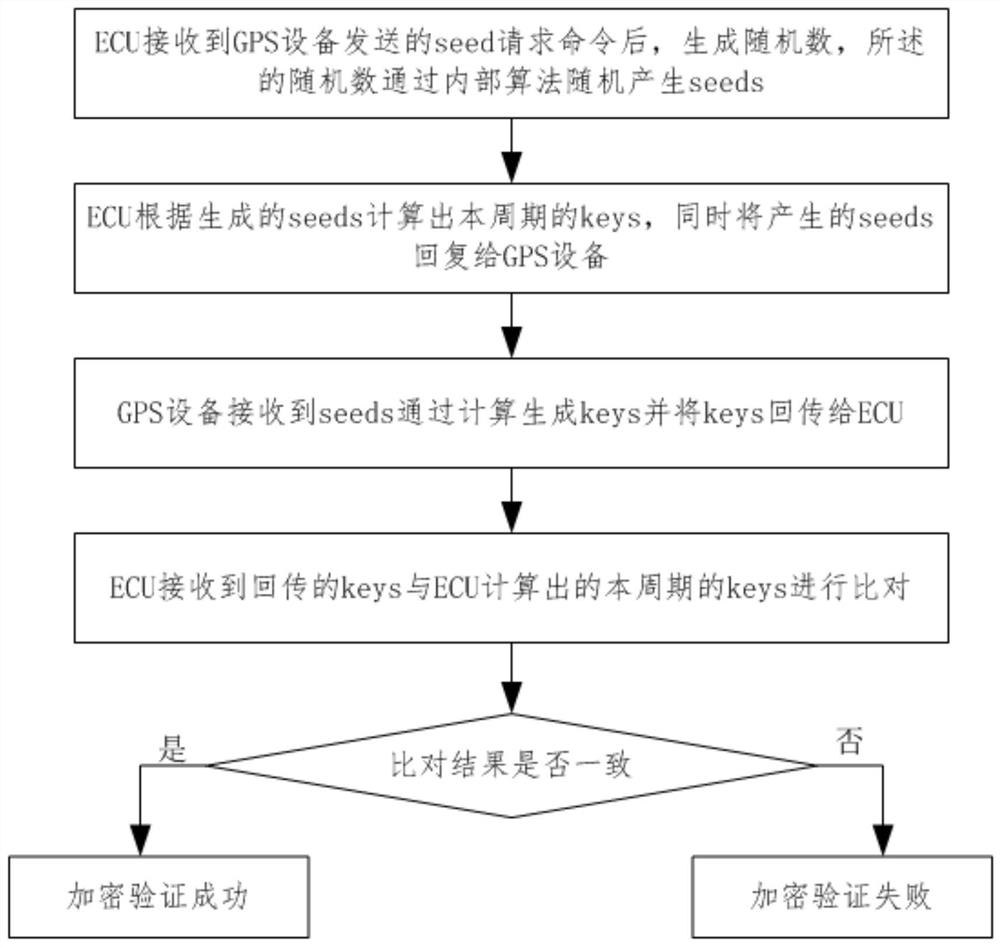
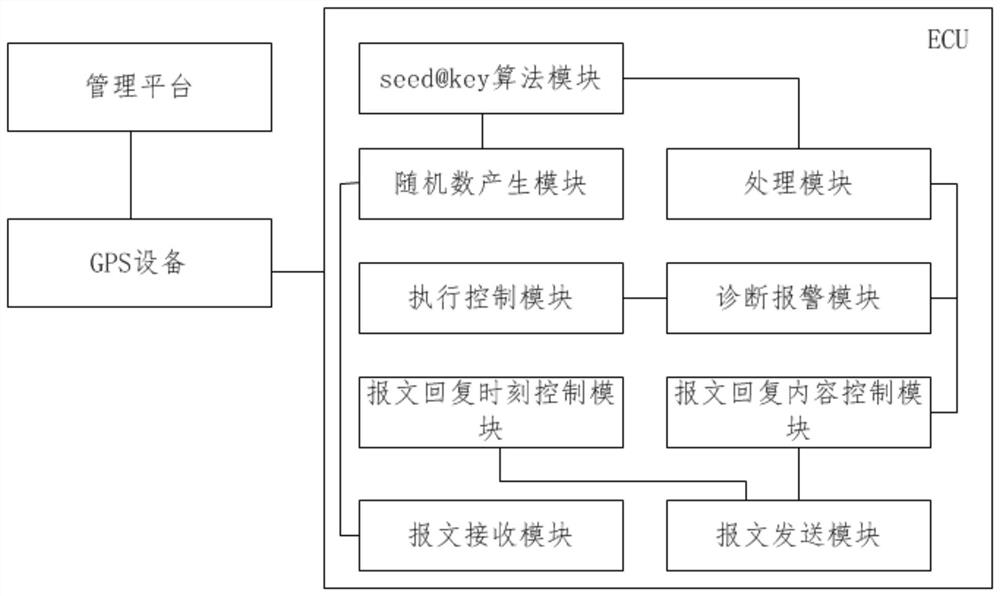
The invention provides a control method and system for an engine control unit to manage a loan vehicle. The control method comprises the following steps: GPS equipment receives a command sent by a management platform; a search request command is sent to ECU; the ECU generates a random number for encryption verification and returns an encryption verification result after receiving a search requestcommand sent by the GPS equipment; the GPS equipment sends heartbeat or a command to the ECU according to an encryption verification result returned by the ECU; and after receiving the heartbeat or command, the ECU responds to and executes the successfully encrypted related command of the GPS equipment, and sends the execution condition to the GPS equipment. Due to a random number generation function and an algorithm function for generating random sequence, the difficulty of artificial decryption is increased, and encryption interaction is strict, and cracking is not easy; and command receiving and engine operation condition controlling can be effectively achieved, and effective supervision on loan purchasing vehicles is achieved, and the control method is suitable for large-scale application.
Owner:SINO TRUK JINAN POWER
Safety authentication method and system based on HTTP protocol
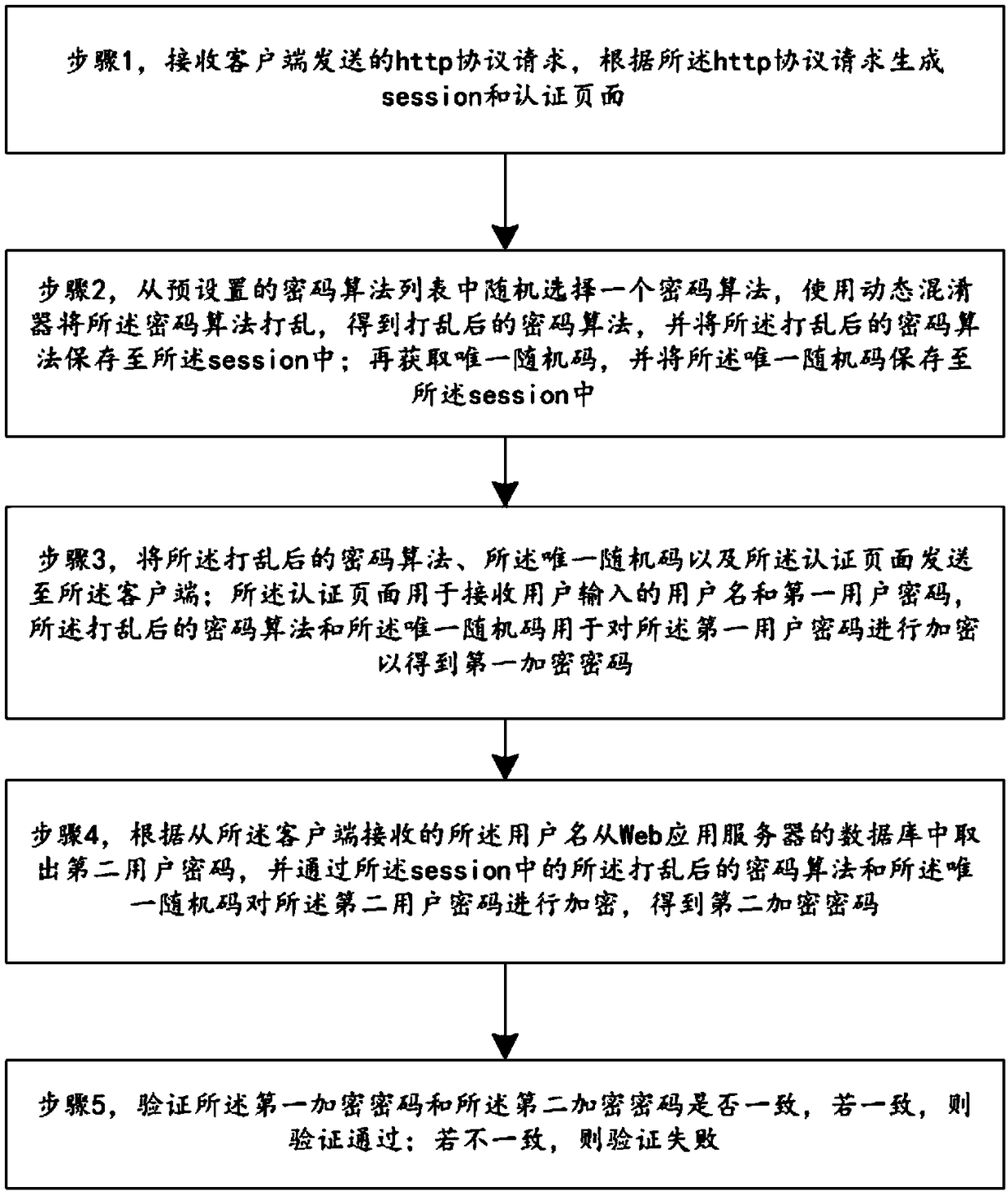
InactiveCN109347867AIncrease the difficulty of decipheringAvoid crackingKey distribution for secure communicationEncryption apparatus with shift registers/memoriesPasswordSecret code
The invention relates to a safety authentication method and system based on an HTTP protocol. The method is characterized in that an encryption algorithm is randomly selected from a password algorithmlibrary with a highly-customized non-standard irreversible password algorithm library in a table authentication manner based on the Http protocol in order to perform irreversible decryption on a userpassword in conjunction with a unique random code generated once a client accesses a server. The encryption method is a non-standard and highly-customized method, so that a safe authentication mechanism is realized; various attacks occurring in basic authentication and digest authentication are avoided; and password cracking and playback authentication can be effectively prevented.
Owner:GUILIN CHANGHAI DEV
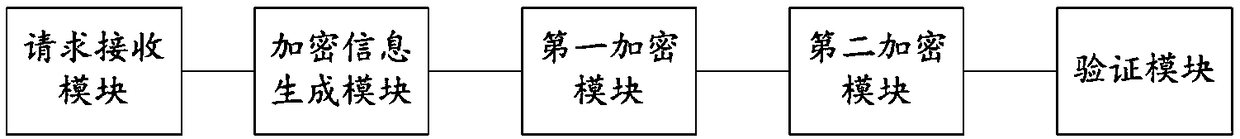
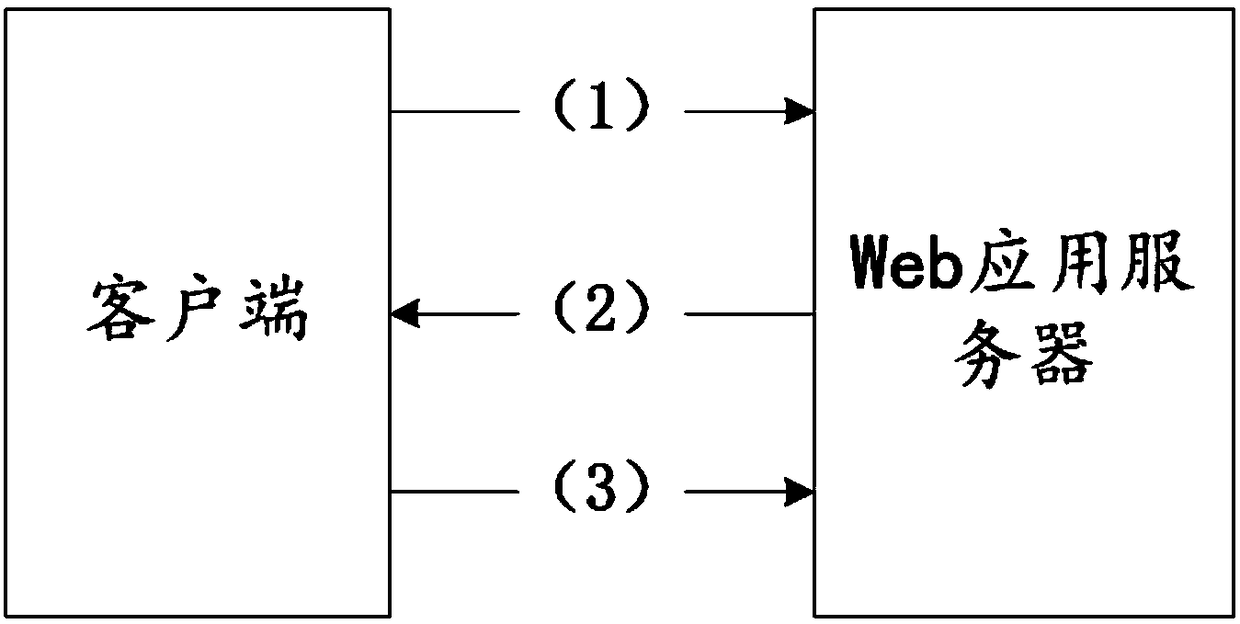
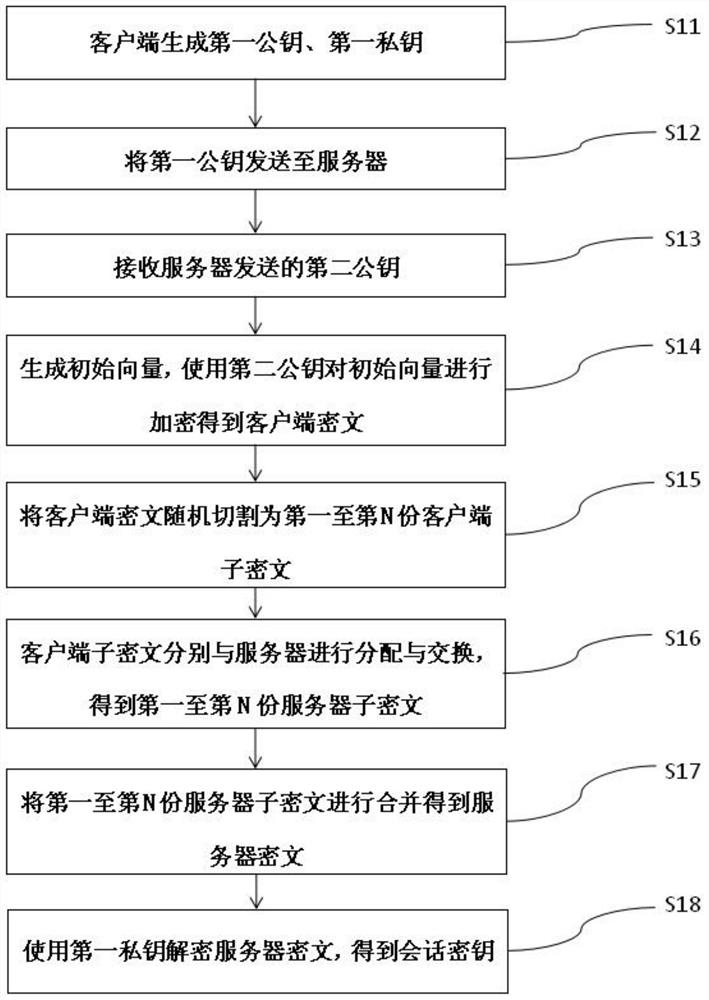
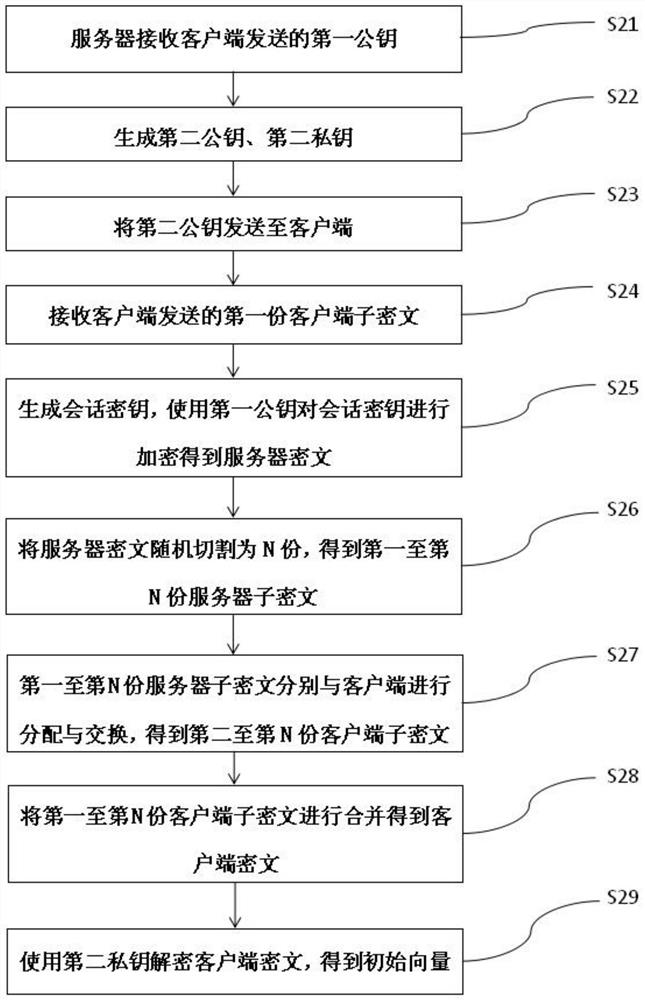
Chain key exchange method, client, server and system
ActiveCN112702332AIncrease the difficulty of decryptionIncrease the difficultyKey distribution for secure communicationKey exchangeMan-in-the-middle attack
The invention relates to the technical field of data security, in particular to a chain key exchange method, a client, a server and a system. The method comprises the following steps: enabling a client to generate a first public key and a first private key; sending the first public key to a server, and receiving a second public key sent by the server; generating an initial vector, and encrypting the initial vector by using a second public key to obtain a client ciphertext; randomly cutting the client ciphertext into N parts, and carrying out distribution and exchange with a server to obtain server sub-ciphertext; and combining the server sub-ciphertext into a server ciphertext, and decrypting the server ciphertext by using the first private key to obtain a session key. On the basis of an original chain key exchange protocol, corresponding improvement is made for possible man-in-the-middle attacks, traditional halving transmission is abandoned, an N-time chain key exchange algorithm is adopted, the encryption strength of data is greatly improved, attackers cannot crack the data within the effective time of information. And the possibility that the secret-related information is cracked is reduced, and the data security is ensured.
Owner:张华
Encryption and decryption methods for file transfers
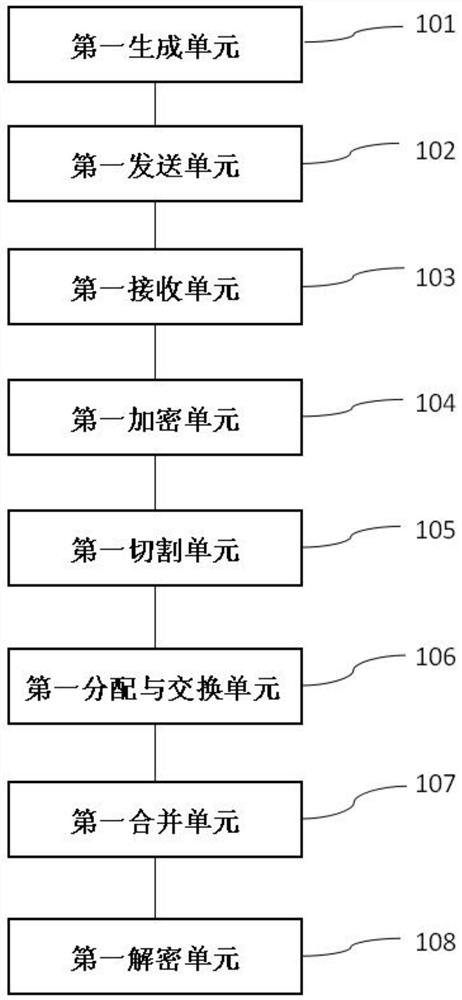
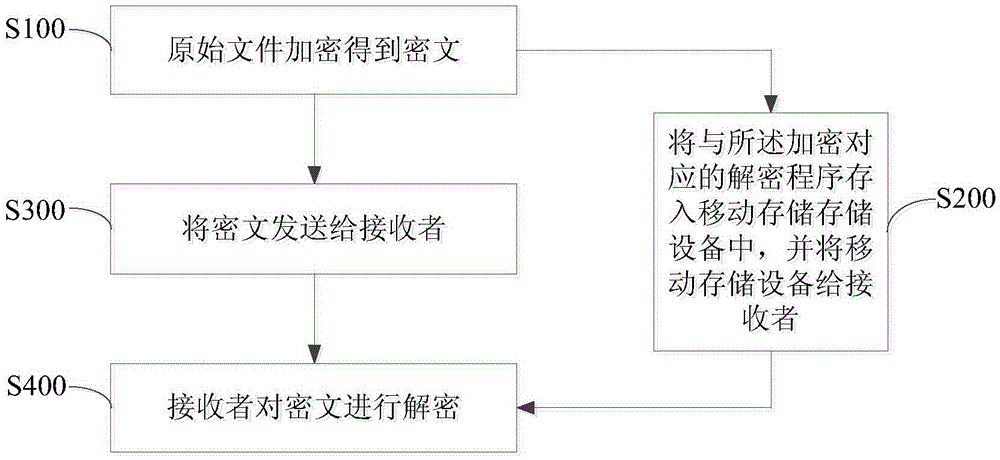
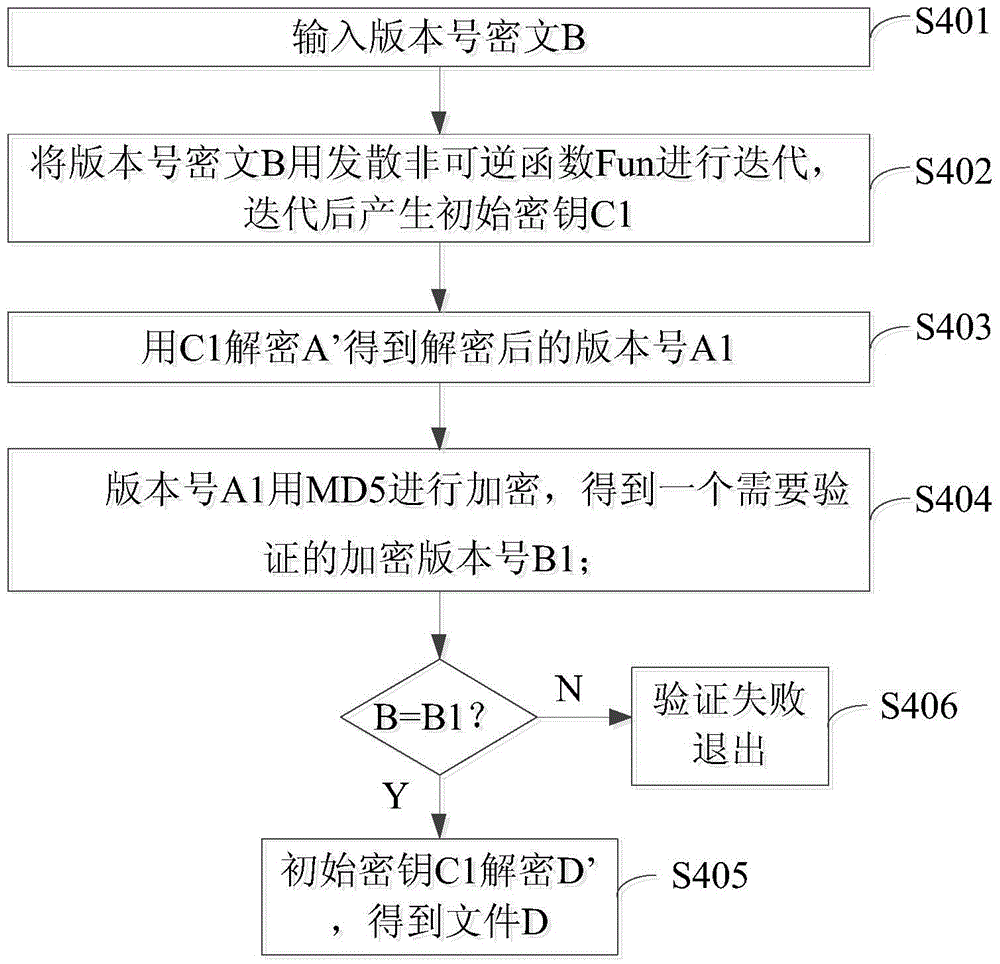
ActiveCN103684750BImprove encryption securityIncrease the difficulty of decryptionEncryption apparatus with shift registers/memoriesComputer hardwareHash function
The invention discloses an encryption and decryption method for file transmission. The method comprises the following steps: generating a file version number; encrypting the file version number with a hash function to generate a version number ciphertext; using an iterative function to iteratively generate the version number ciphertext The initial key for file encryption; put the version number into the file, and encrypt the file with Advanced Encryption Standard; send the file ciphertext and version number ciphertext to the receiver; the receiver decrypts by inputting the version number ciphertext. And implant the program corresponding to encryption and decryption in the encryption and decryption program into the mobile storage device, so that even if the decryption software is stolen and the ciphertext is stolen, the decryption operation cannot be performed. The invention is applied to the protection of file transmission and copying in the local area network , can put an end to the illegal operation of the file.
Owner:武汉千里路智能交通科技有限公司
A method, device and storage medium for industrial network data isolation
ActiveCN112637176BIncrease the difficulty of decryptionImprove accuracyTransmissionCiphertextIndustrial systems
The application proposes an industrial network data isolation method, device and storage medium. The method includes: receiving a message sent by a host on the external management network side, and determining the type of the message when the source IP address of the message belongs to the trusted source IP address range; In the case where the type is a command message, determine the danger level of the command message; when the danger level of the command message is lower than the preset danger level, send the command message to the industrial system network side Host; receive the industrial data sent by the industrial system network side host, encrypt the industrial data, and send the encrypted ciphertext and key to the external management network side host so that the external The host on the management network side decrypts the ciphertext; the security level of the external management network is lower than that of the industrial system network. The present application improves the isolation effect of the data isolation of the industrial system.
Owner:山东云天安全技术有限公司
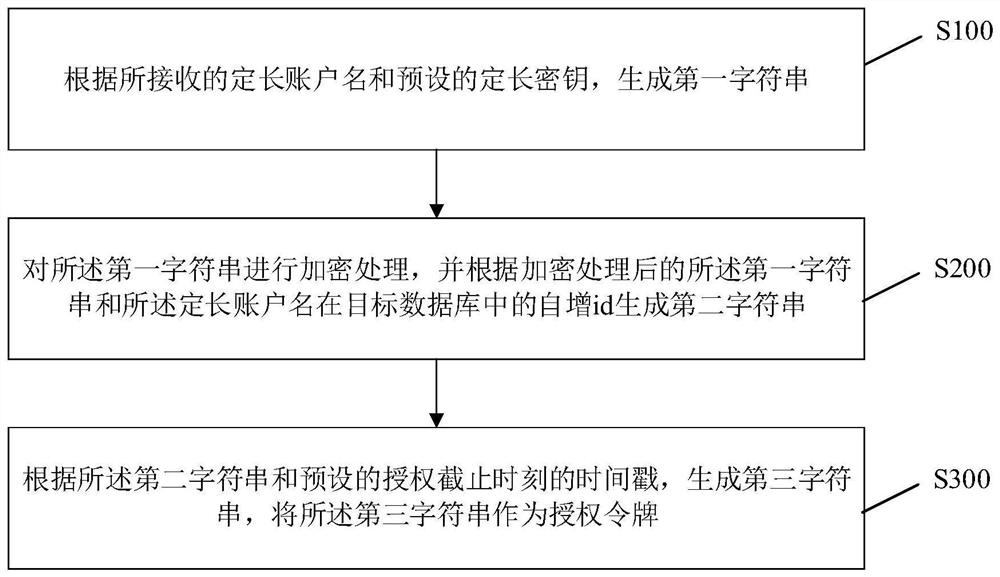
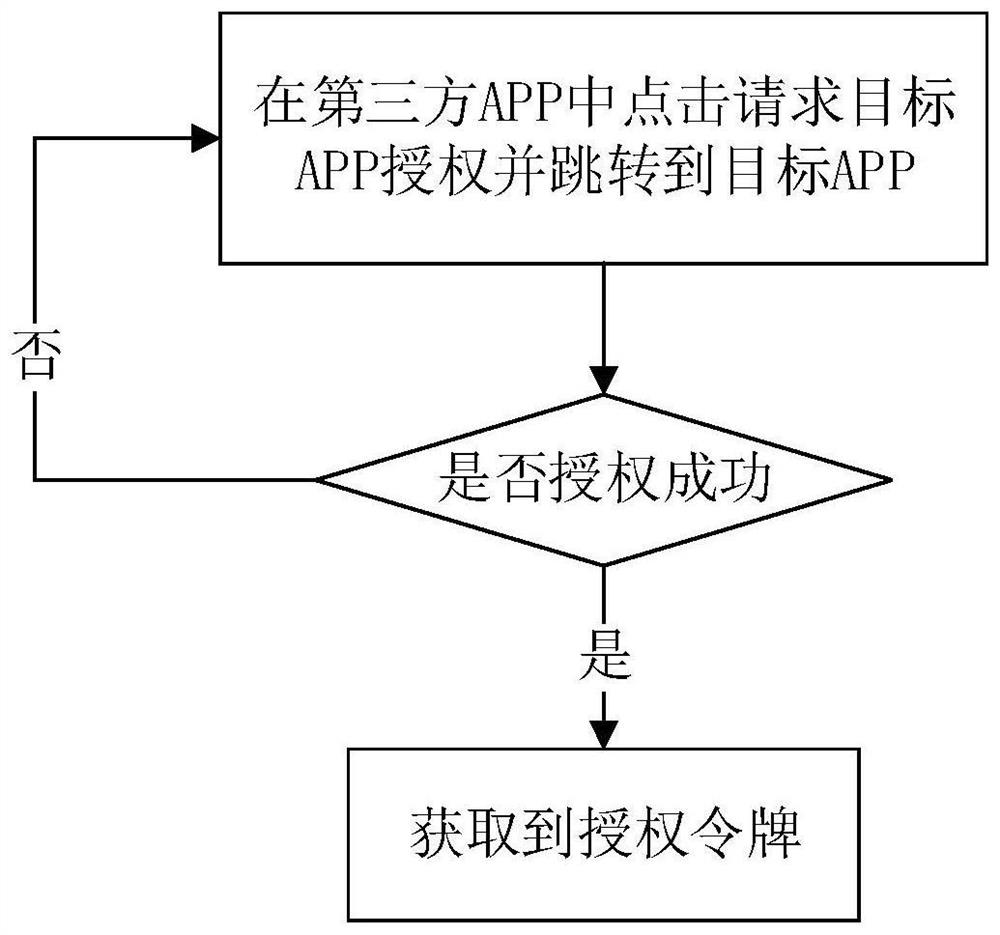
Authorization token generation method and third-party application association method
PendingCN114462010AImprove securityPrevent leakageDigital data protectionDigital data authenticationThird partyTimestamp
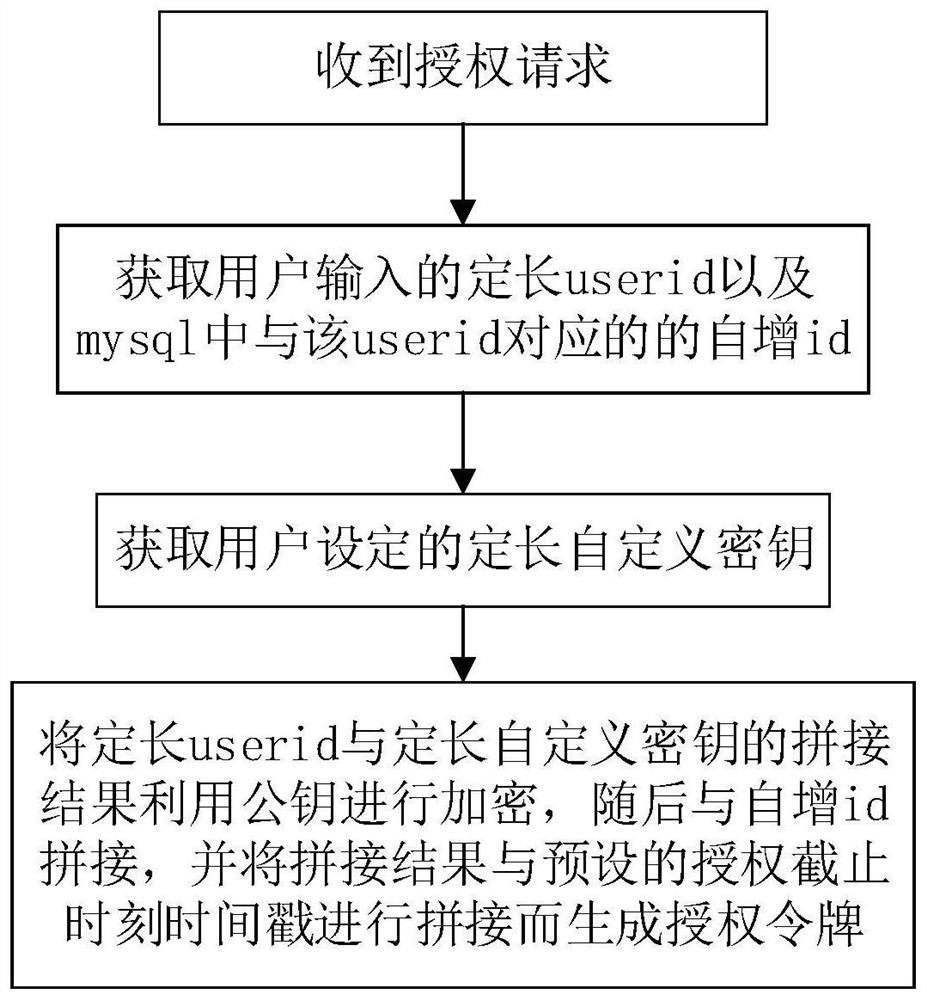
The invention provides a method for generating an authorization token and a method for associating a third-party application. The authorization token generation method is applied to a target application, and comprises the following steps: generating a first character string according to a received fixed-length account name and a preset fixed-length key; performing encryption processing on the first character string, and generating a second character string according to the encrypted first character string and a self-increasing id of the fixed-length account name in a target database; and generating a third character string according to the second character string and a timestamp of a preset authorization cut-off moment, and taking the third character string as an authorization token. In the process of generating the authorization token, the fixed-length account name of the user is encrypted, so that the security of the account name of the user is improved, and the leakage of account information of the user is prevented.
Owner:GREE ELECTRIC APPLIANCES INC +1
Three-state magnetic control matrix module and coded lock applying same
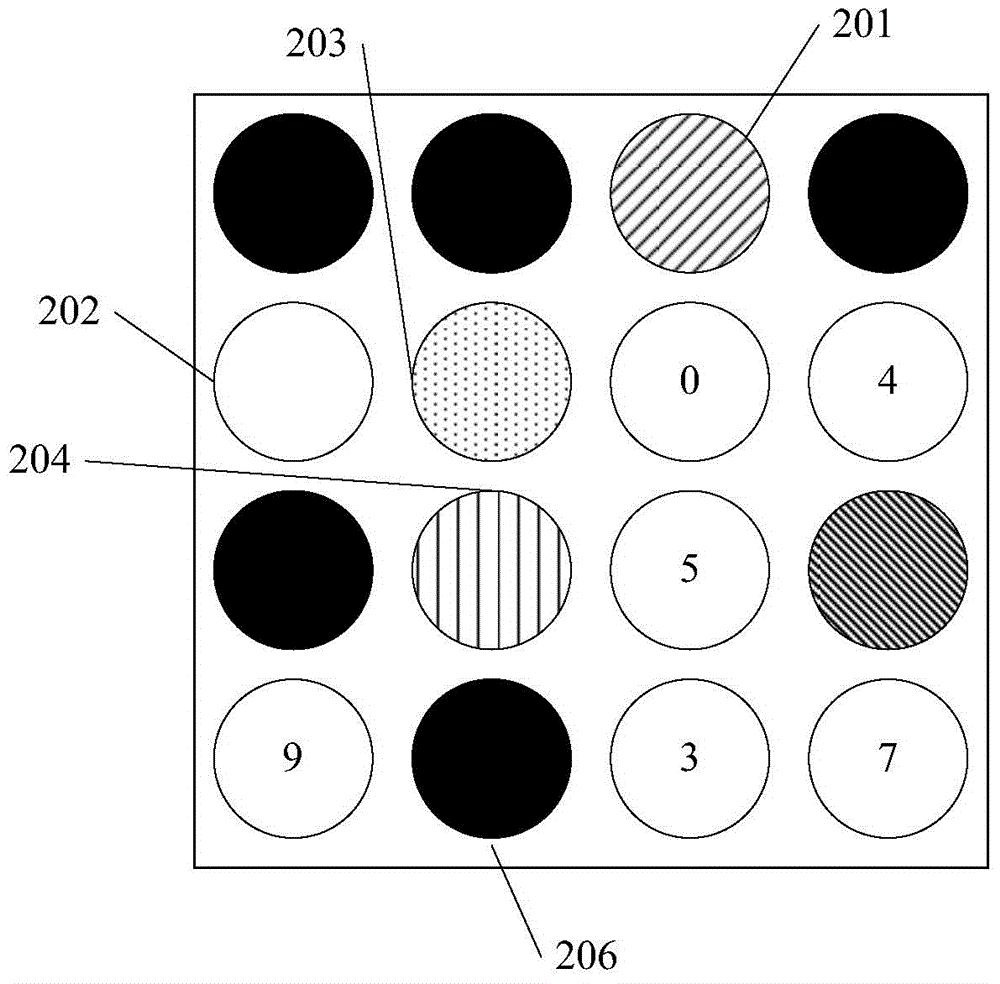
PendingCN110374416ADeepening Diversity and ComplexityIncrease the difficulty of decryptionNon-mechanical controlsElectric permutation locksPhysicsMagnet
The invention discloses a three-state magnetic control matrix module and a coded lock applying the same and belongs to the technical field of magnetic effects. The three-state magnetic control matrixmodule comprises a magnetic matrix and a trigger part matched with the magnetic matrix, the magnetic matrix is formed by arranging and combining N magnetic control logical units, wherein N is larger than or equal to 1, and the magnetic matrix is formed by the multiple magnetic control logical units. The magnetic control logical units are connected with different voltage inputs correspondingly in virtue of rotation of a permanent magnet, and different voltage three-state signals are output correspondingly. The unlocking difficulty of the coded lock is further improved by achieving a three-stateinput function through the three-state magnetic control matrix module, decoding difficulty is improved directly due to input complexity and diversity, and property and personal safety is ensured.
Owner:河北晶冰蕊电子元件有限公司
Terminal encryption method and encryption device, terminal decryption method and decryption device
ActiveCN104966014BIncrease the difficulty of decryptionDigital data authenticationPasswordComputer terminal
Owner:HUAQIN TECH CO LTD
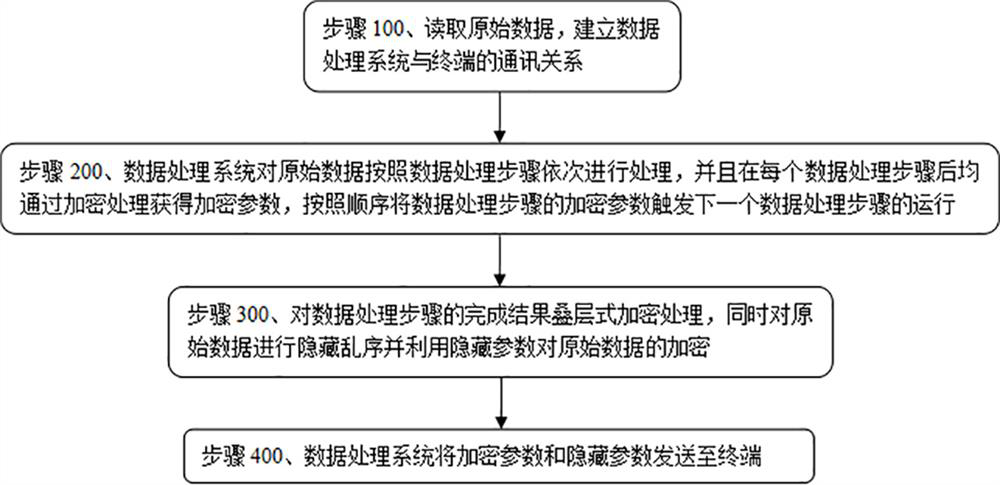
A data processing method for improving data security
Owner:成都中轨轨道设备有限公司
An information processing method and device
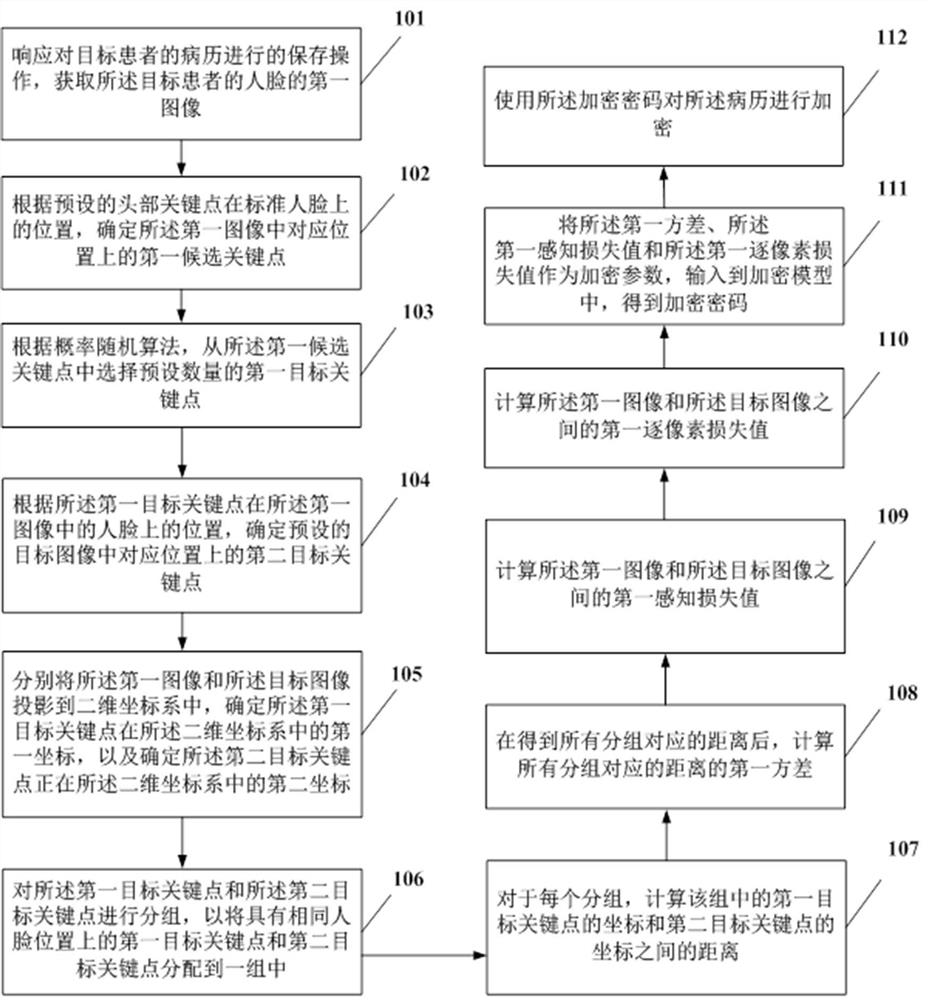
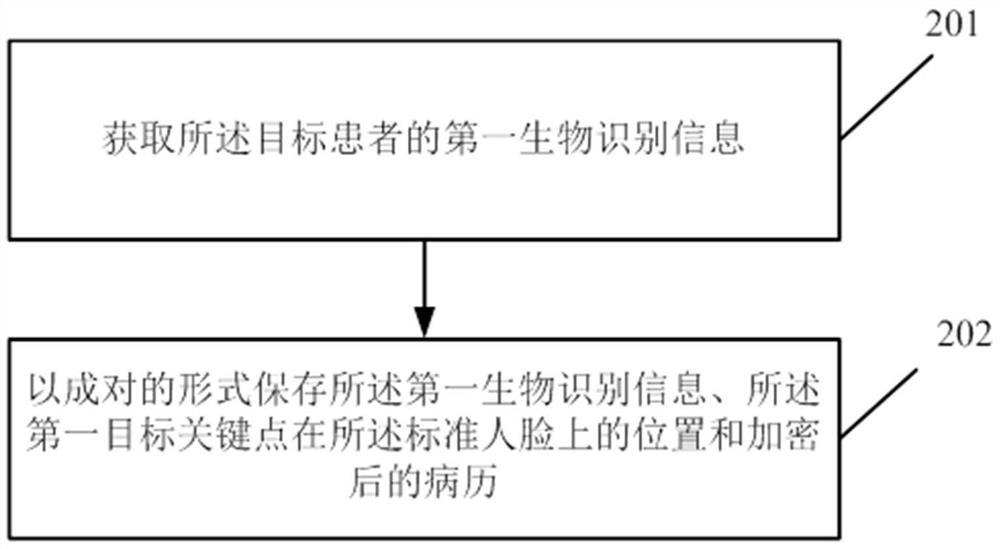
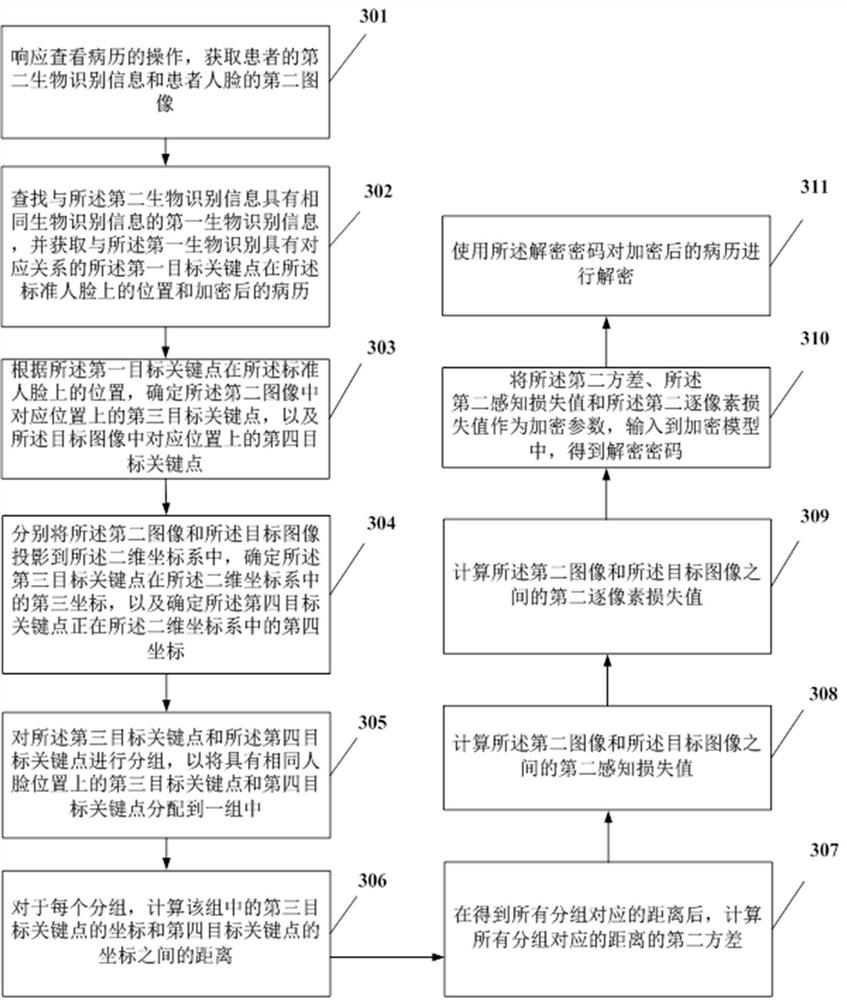
ActiveCN112466425BIncrease the difficulty of decryptionEncrypted password securityCharacter and pattern recognitionDigital data protectionMedical recordInformation processing
The present application provides an information processing method and device, wherein the method includes: when saving the medical records, selecting key points at the same position from the first image and the target image, and then calculating the key points at the same position The distance between the coordinates in the two-dimensional coordinate system, and then calculate the first variance of each distance, and calculate the first perceptual loss value and the first pixel-by-pixel loss value between the first image and the target image, and then the first The variance, the first perceptual loss value and the first pixel-by-pixel loss value are used as encryption parameters and input into the encryption model to obtain the encryption password; use the generated encryption password to encrypt the medical records, and the information security of the patient's medical records can be improved by the above method .
Owner:BEIJING MORE HEALTH TECH GRP CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com