Binary two-dimensional code image encryption and decryption method and device
A two-dimensional code and image technology, applied in the computer field, can solve the problems of low encryption algorithm complexity, low security, and high publicity, and achieve the effects of improving security, high sensitivity, and high computational complexity
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
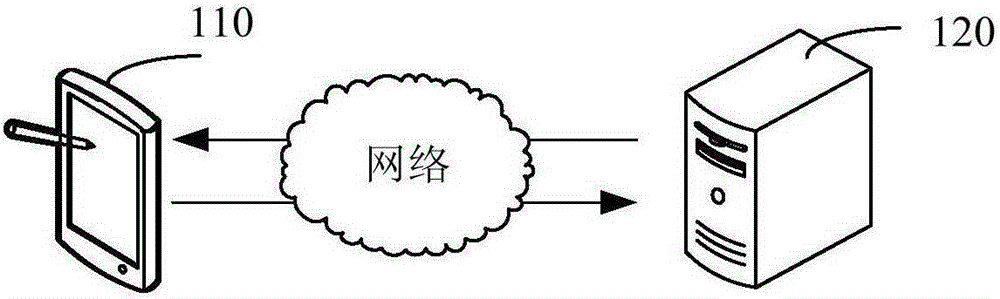
[0042] figure 1 It is an application environment diagram for the operation of the method for encrypting and decrypting binary two-dimensional code images in one embodiment. Such as figure 1 As shown, the application environment includes a terminal 110 and a server 120, wherein the terminal 110 and the server 120 communicate through a network.
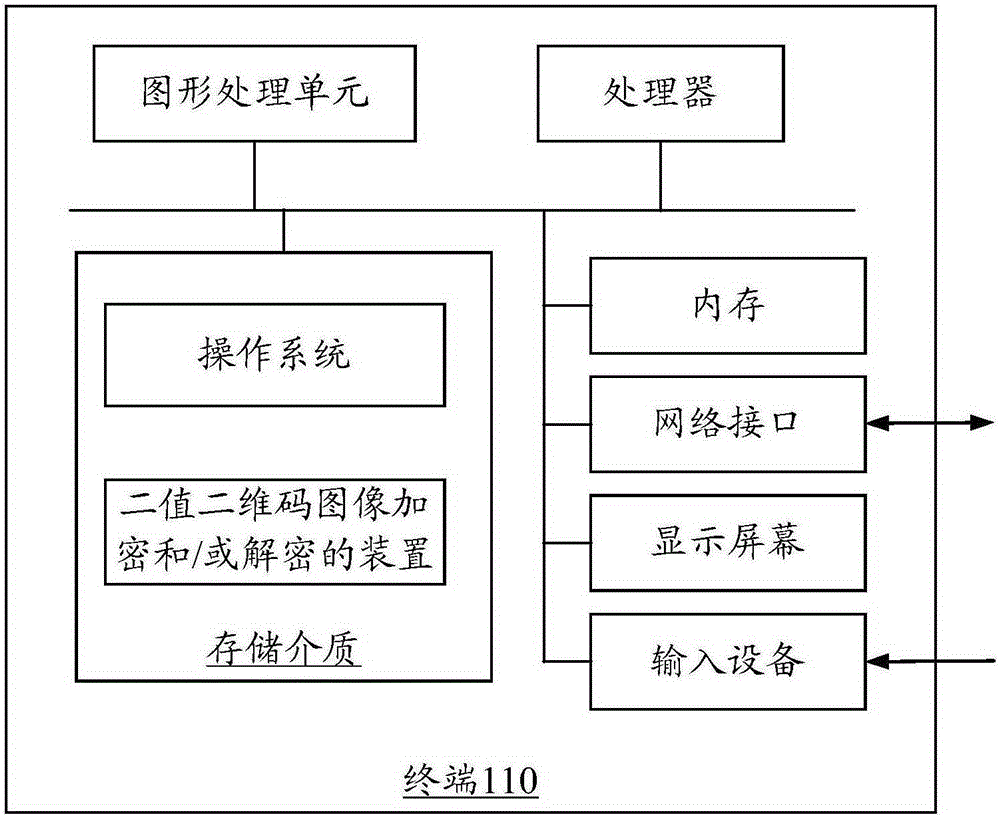
[0043] The terminal 110 may be a smart phone, a tablet computer, a notebook computer, a desktop computer, etc., but is not limited thereto. The encrypted two-dimensional code can be sent between the terminal 110 and the server 120 through the network. The device for encrypting and decrypting binary two-dimensional code images can be in the terminal or in the server.
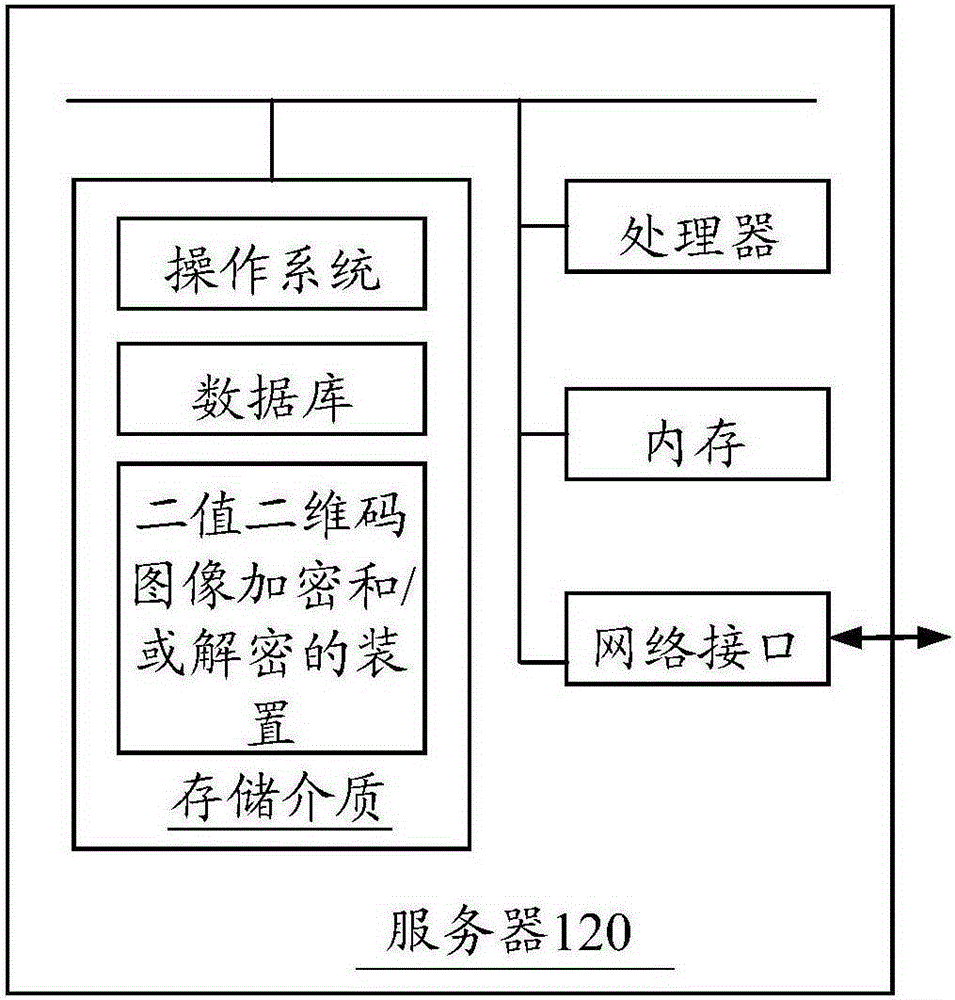
[0044] In one embodiment, figure 1 The internal structure of the server 120 in figure 2 As shown, the server 120 includes a processor, a storage medium, a memory, and a network interface connected through a system bus. Wherein, the storage medium of the server 120 s...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com