Patents
Literature
33results about How to "Guaranteed non-reproducibility" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
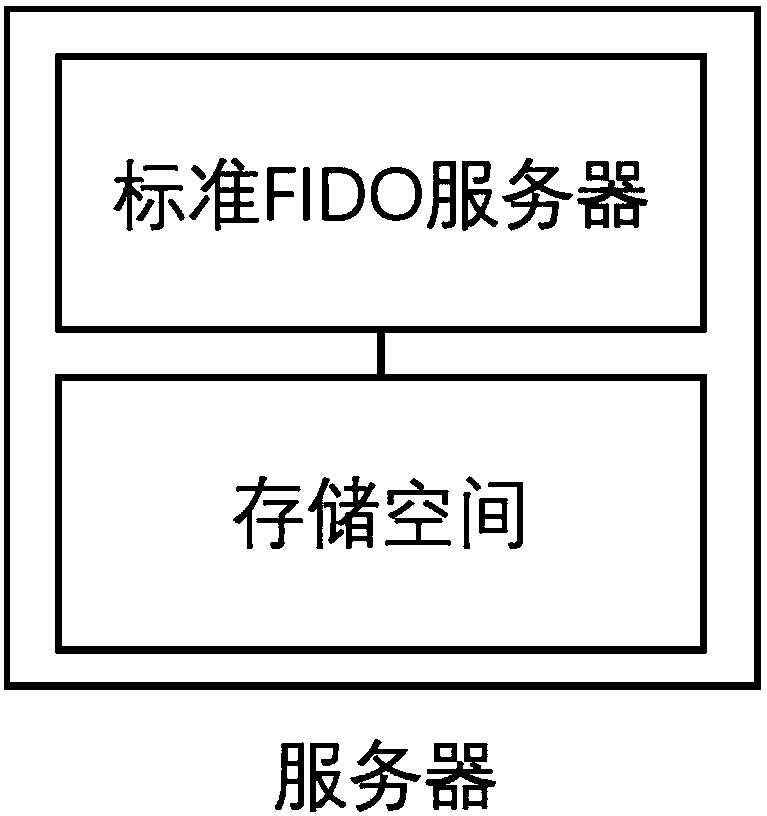
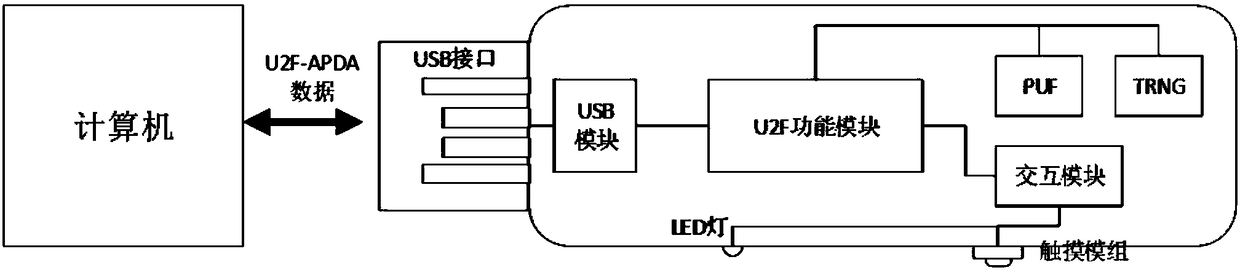
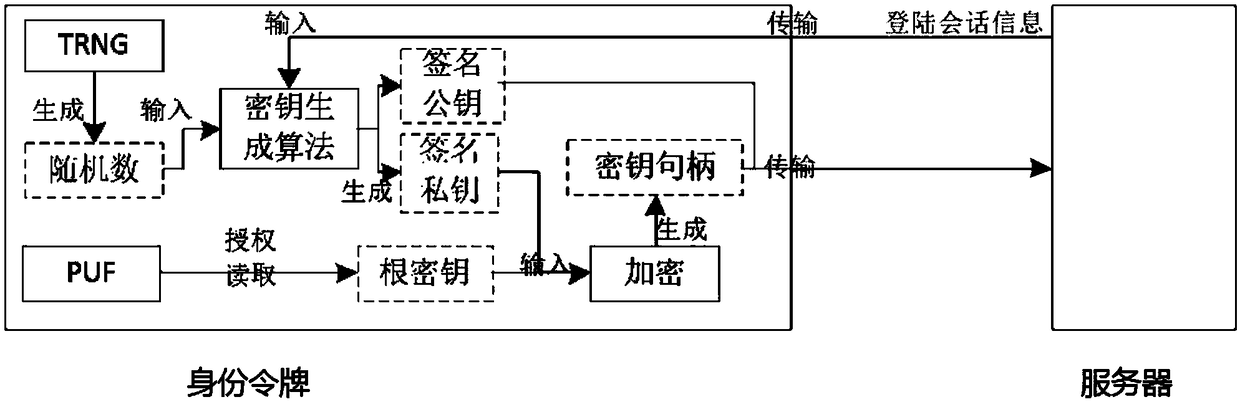
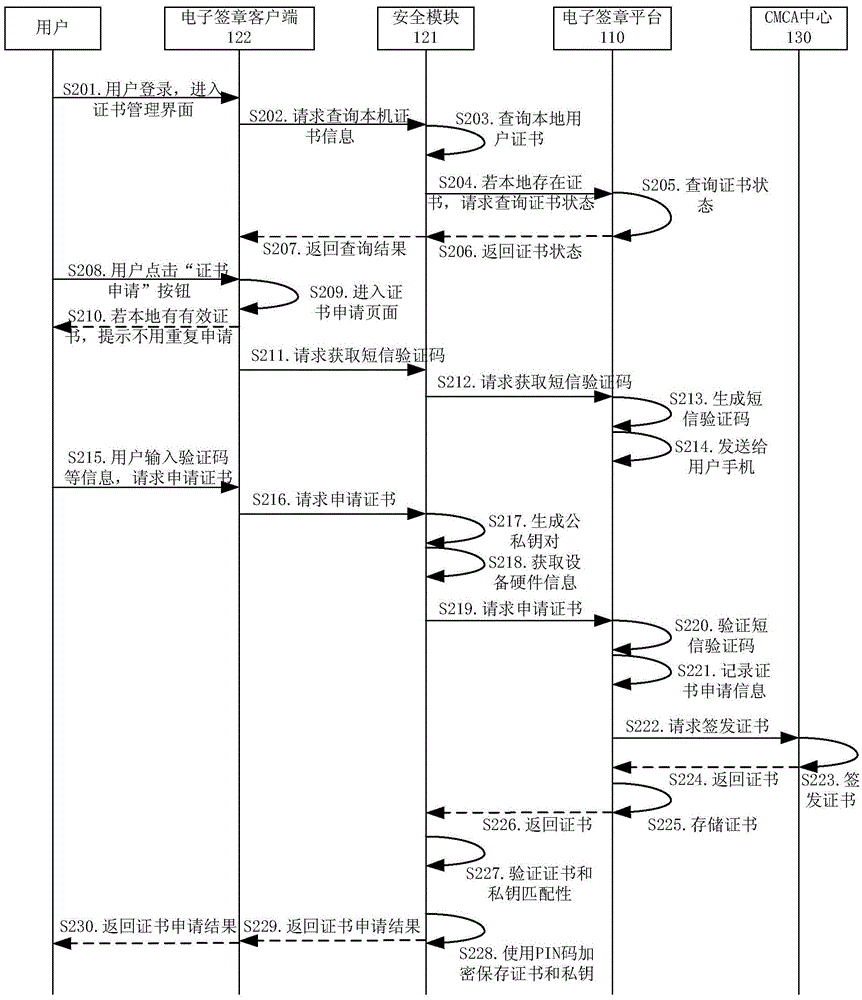
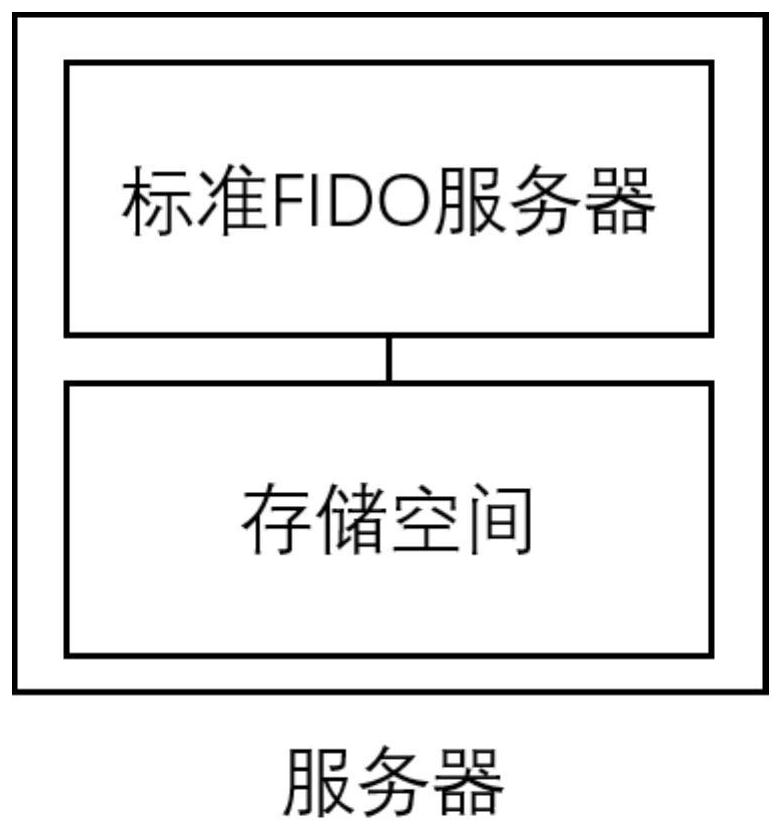
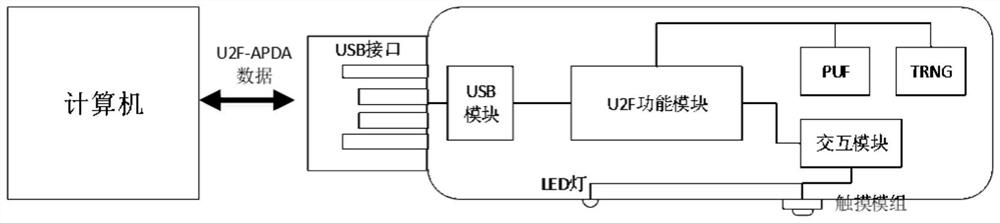
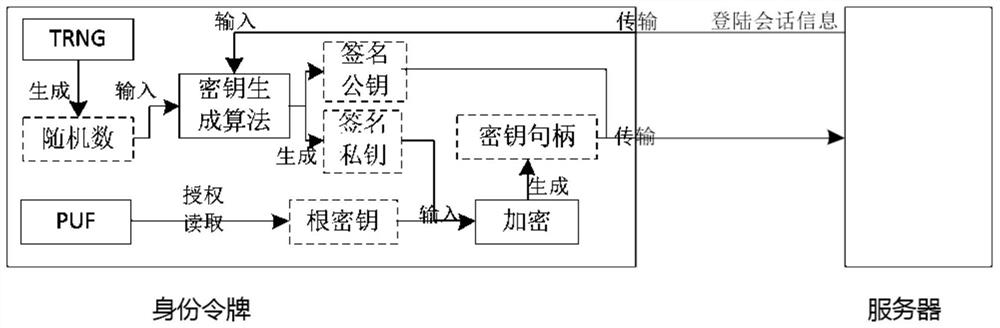
Identity authentication server and identity authentication token
ActiveCN108092776APrevent replay attacksAddressing leaked passwordsUser identity/authority verificationClient-sideNon-repudiation
The invention discloses an identity authentication server and an identity authentication token, wherein the identity authentication server comprises a standard FIDO server and a storage space for storing keys, namely, a database, which are connected with each other; the identity authentication token is based on physical unclonable and the FIDO U2F protocol and comprises a U2F module, and a PUF module,a TRNG module, a USB module and an interaction module, which are connected with the U2F module, and a touch module connected with the interaction module; and an identity token interacts with a client browser, and the client browser in turn interacts with an FIDO server in the authentication server. According to the identity authentication server disclosed by the invention, the physical unclonable function is combined with the FIDO, the uniqueness and non-replicability of the token are ensured by the physical unclonable function, and the accuracy of the user identity and the non-defective modification and non-repudiation of the operation are ensured by the FIDO.
Owner:NARI INFORMATION & COMM TECH
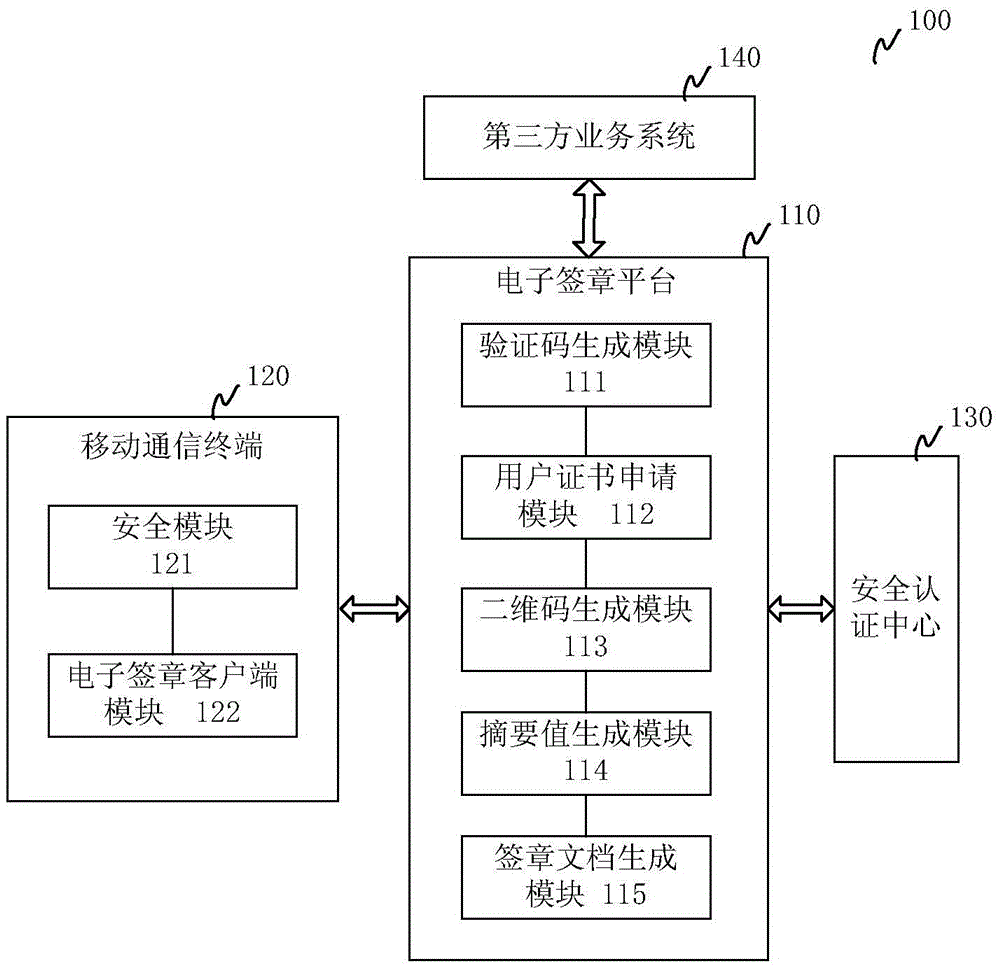
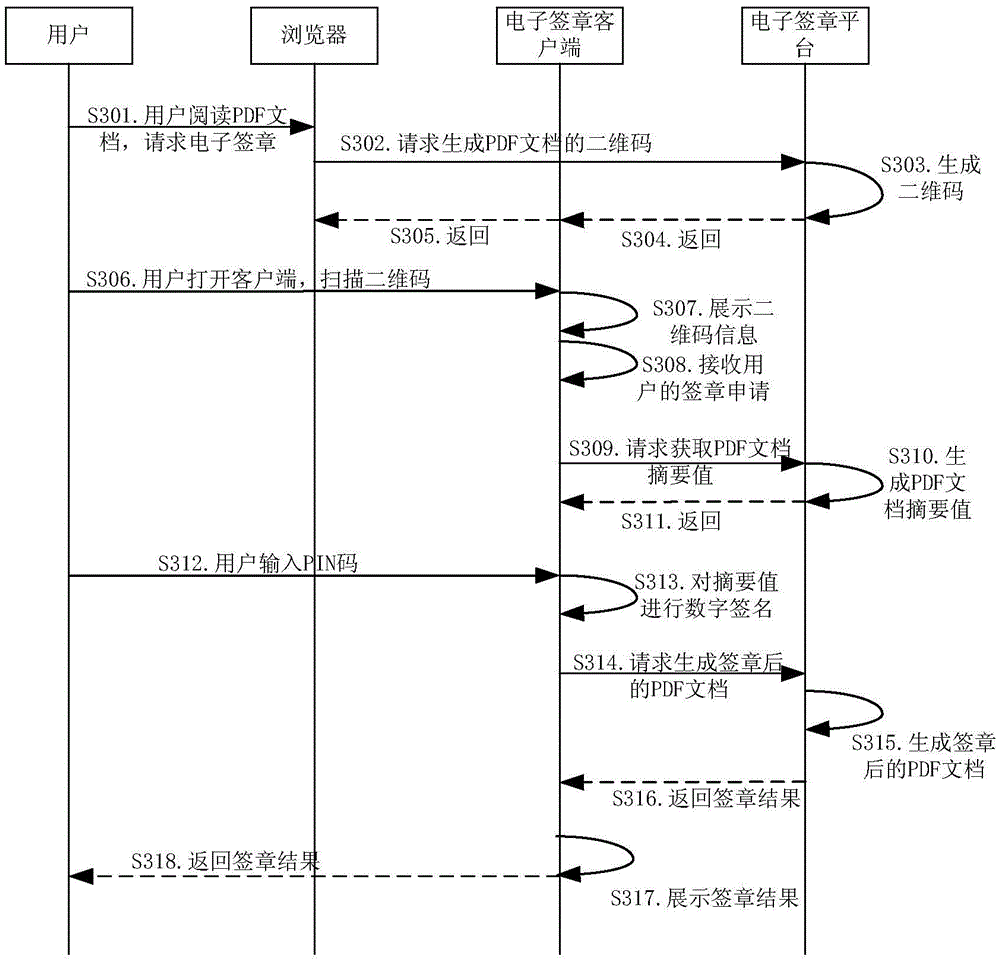
Method and system for electronic signature and mobile communication terminal used for electronic signature
ActiveCN106888089AProtection securityChen BenlowUser identity/authority verificationDigital signatureElectronic signature
The invention relates to a method and system for electronic signature and a mobile communication terminal used for electronic signature. The method includes the following steps: an electronic signature platform generates a two-dimensional code of a document to be signed based on a first electronic signature request sent by a user, and sends the two-dimensional code to a mobile communication terminal of the user; the mobile communication terminal scans the two-dimensional code and displays two-dimensional code information to the user, and requests the electronic signature platform for abstract values of the document to be signed based on a second electronic signature request of the user; the electronic signature platform generates abstract values and returns to the mobile communication terminal; the mobile communication terminal uses a user certificate stored therein to perform digital signature on the abstract values, and sends the digitally signed abstract values to the electronic signature platform to request for a document with a generated signature; and the electronic signature platform embedded the digitally signed abstract values into the document to be signed, and returns the document with the generated signature to the user. The electronic signature method provided by the invention is relatively safe, simple and rapid, and is low in cost.
Owner:卓望数码技术(深圳)有限公司
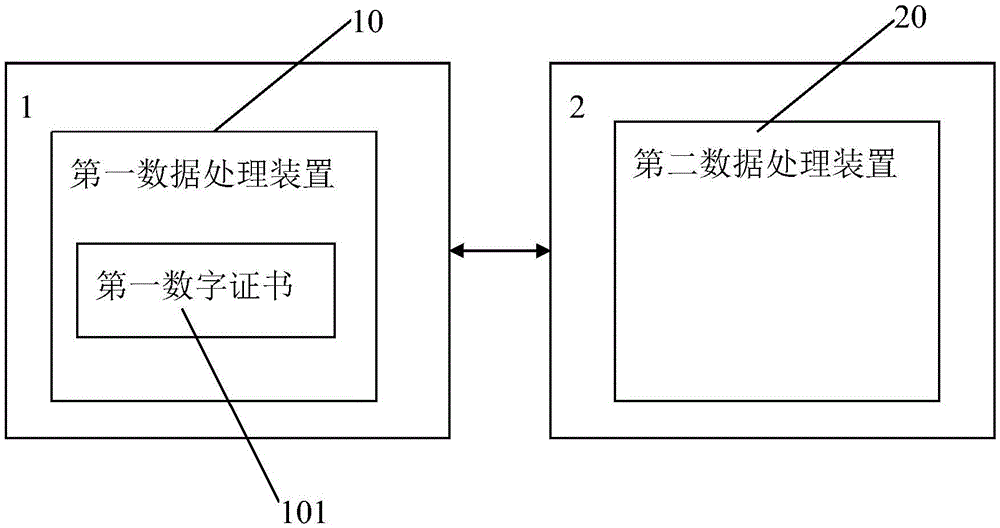
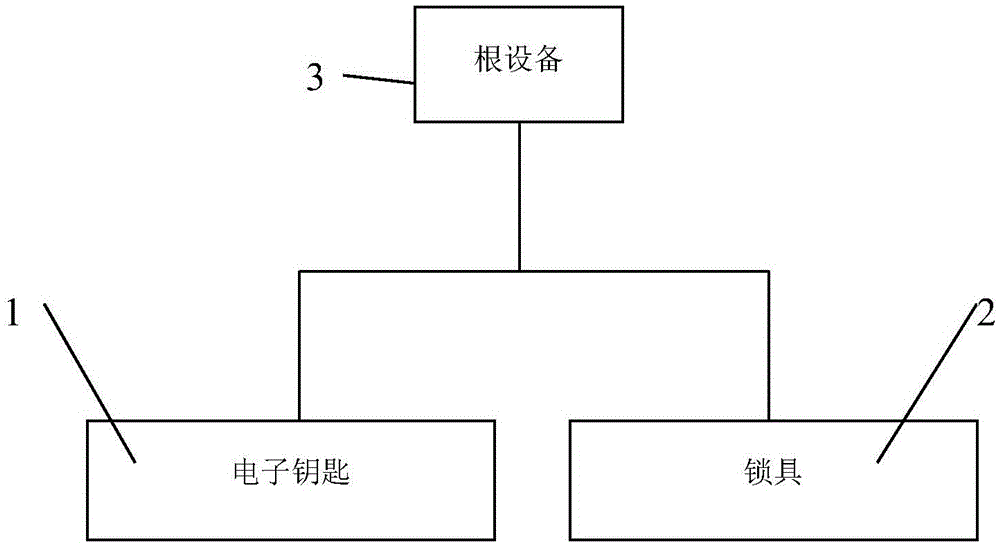
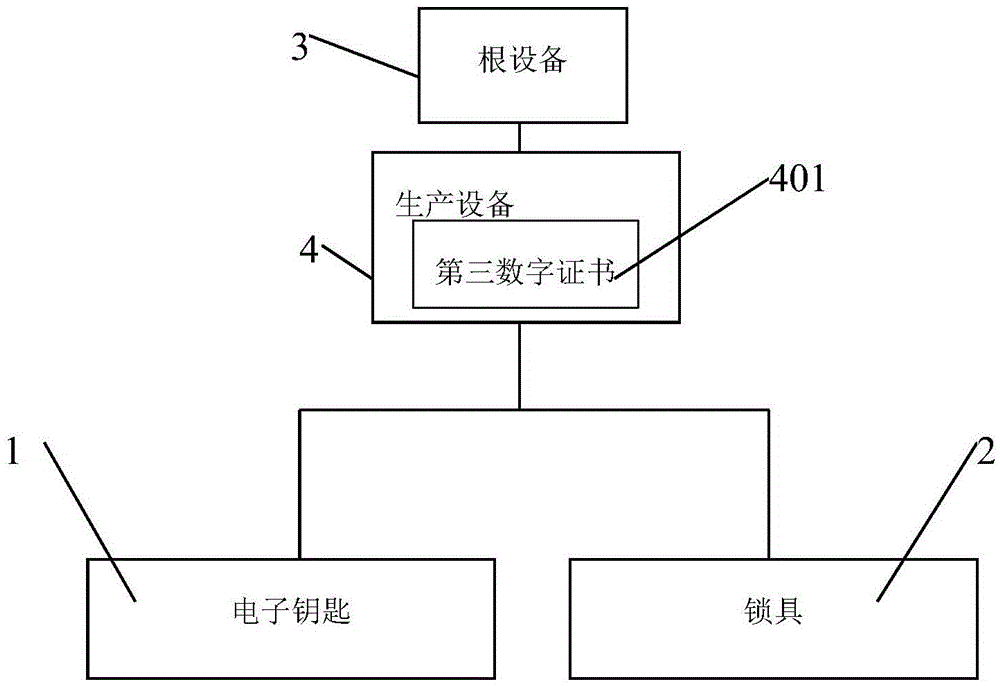
Electronic lock system and control method thereof
ActiveCN105554035AImprove securityEnsure safetyIndividual entry/exit registersTransmissionComputer hardwareAuthentication
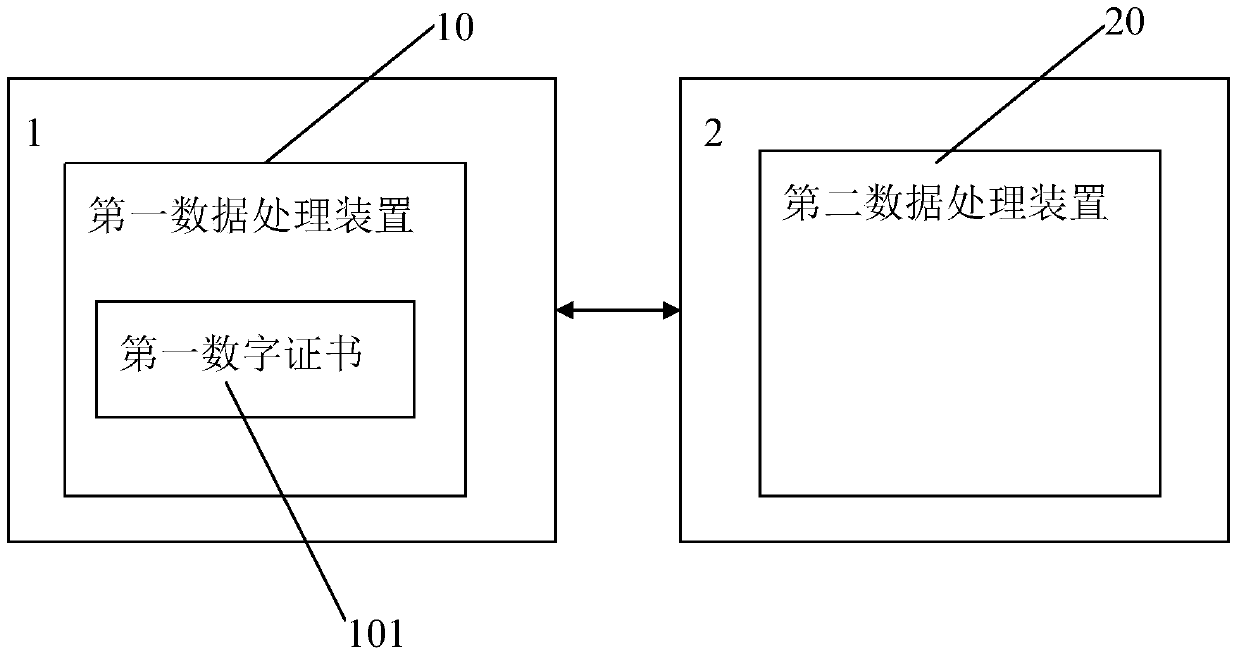
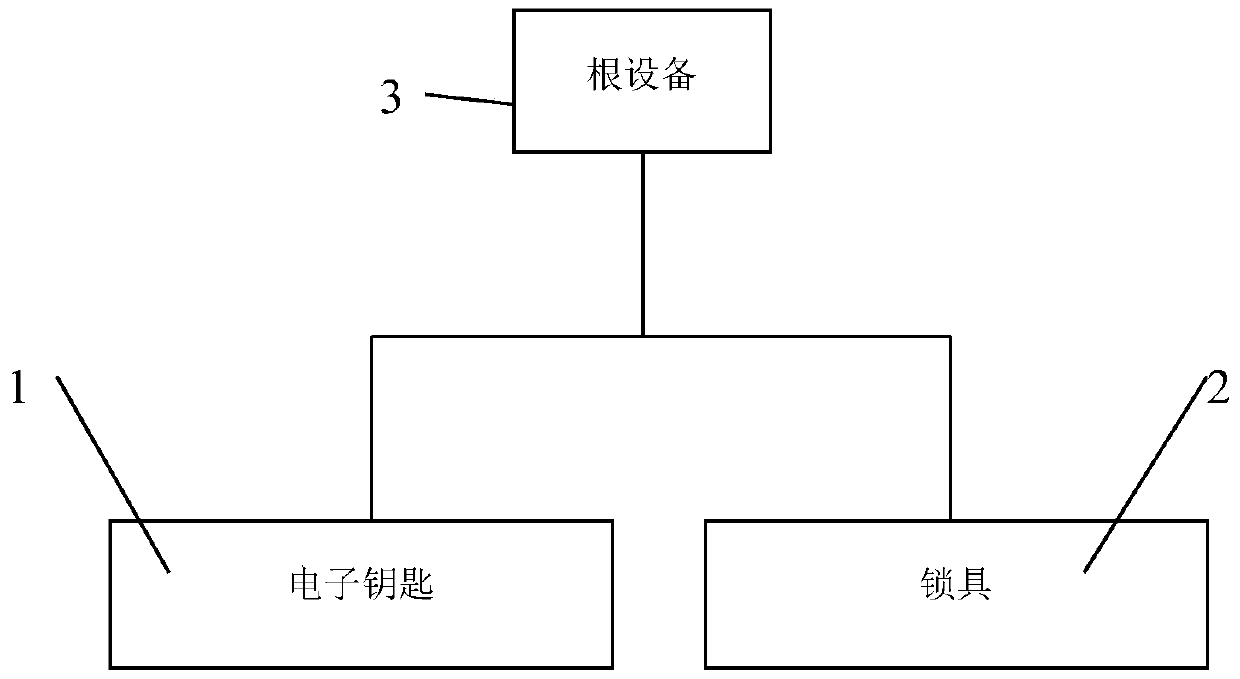
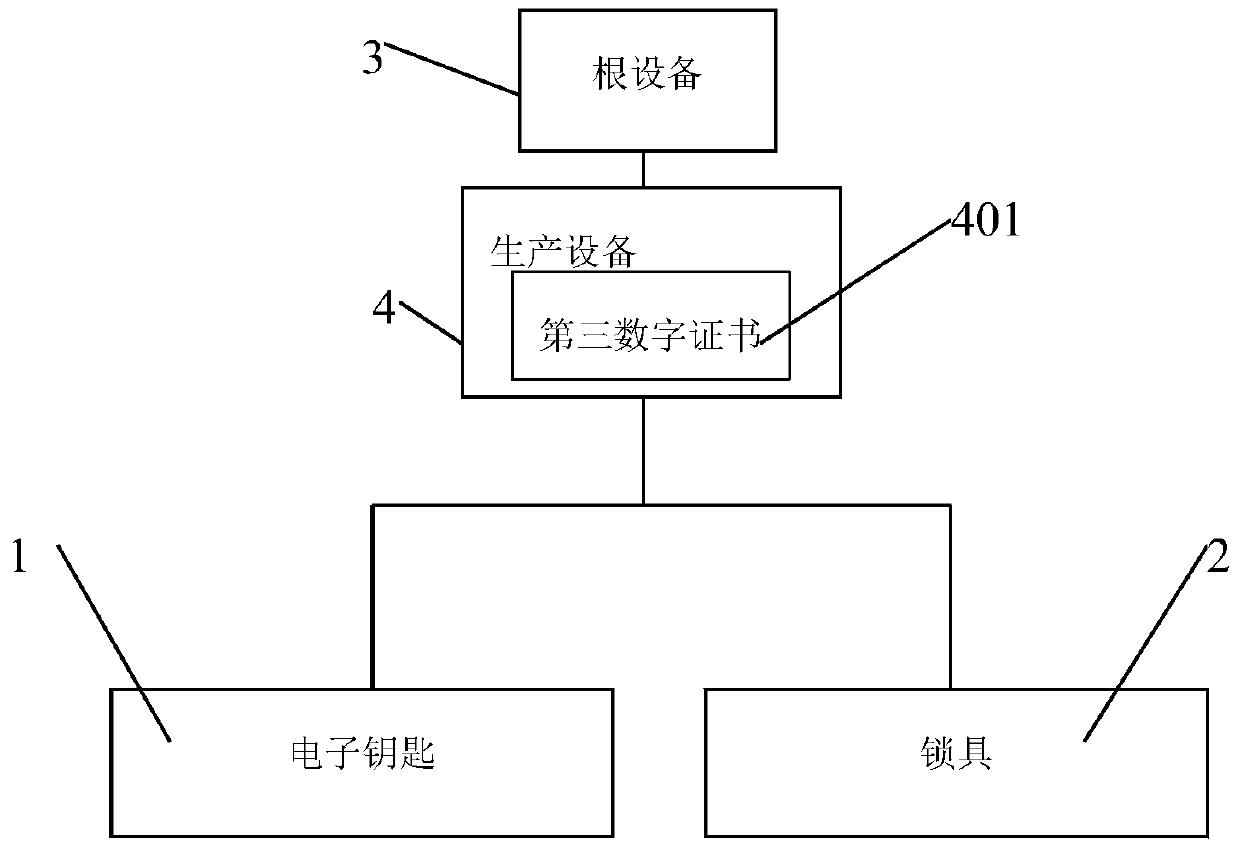
The invention provides an electronic lock system and a control method thereof. The electronic lock system comprises a lockset and an electronic key in communication connection with the lockset; the electronic lock system is characterized in that a first data processing device is installed in the electronic key; a first digital certificate is stored in the first data processing device; and a second data processing device is installed in the lockset, wherein the second data processing device is configured to be capable of communicating with the first data processing device so as to verify the first digital certificate and store the first digital certificate, send authentication data to the first data processing device when the lockset receives an unlocking request of the electronic key every time, authenticate response data returned by the first data processing device by utilizing the stored first digital certificate, and allow to open the lockset when authentication is passed. The electronic lock system disclosed by the invention has the characteristics of being high in security and more intelligent.
Owner:HIHALOCK BEIJING TECH CO LTD
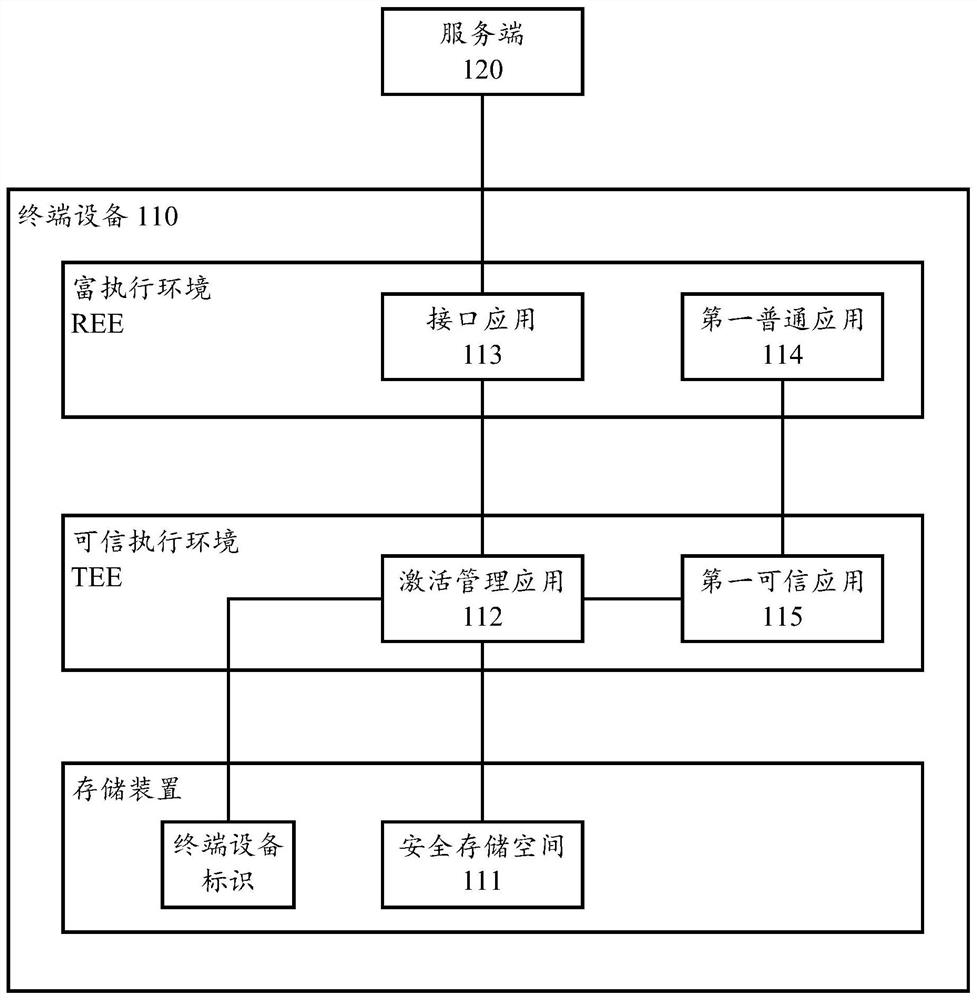
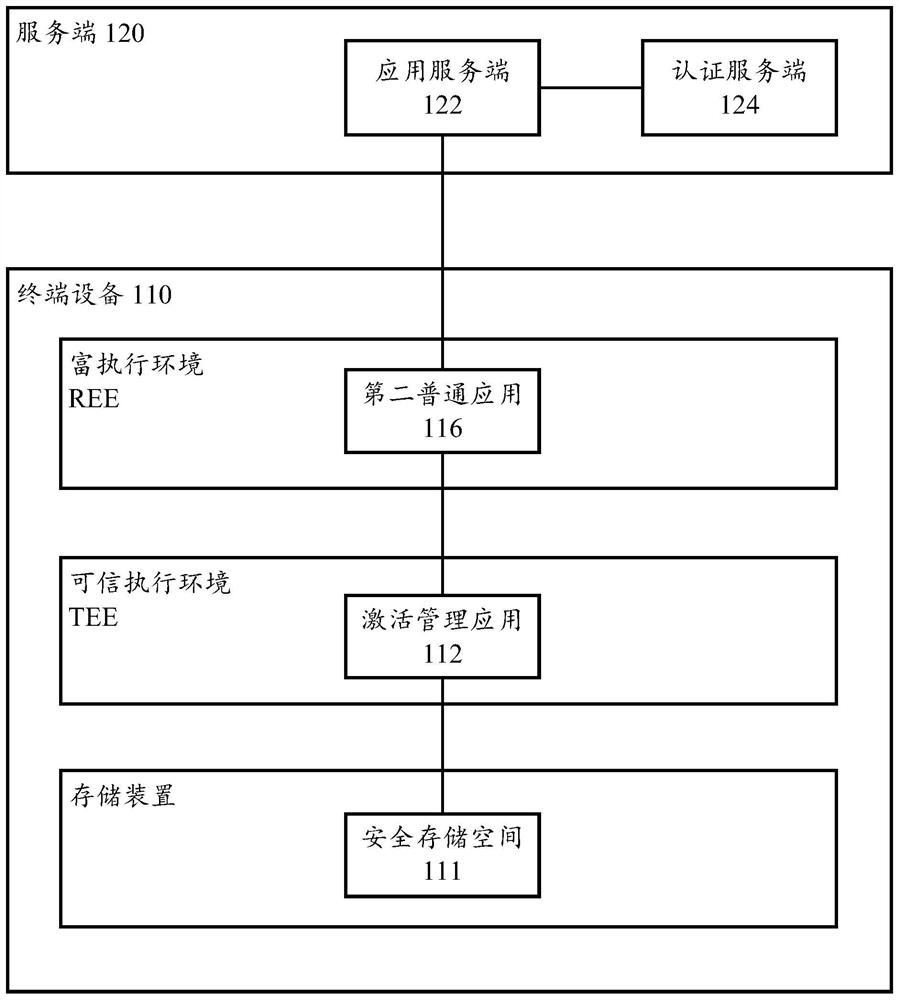
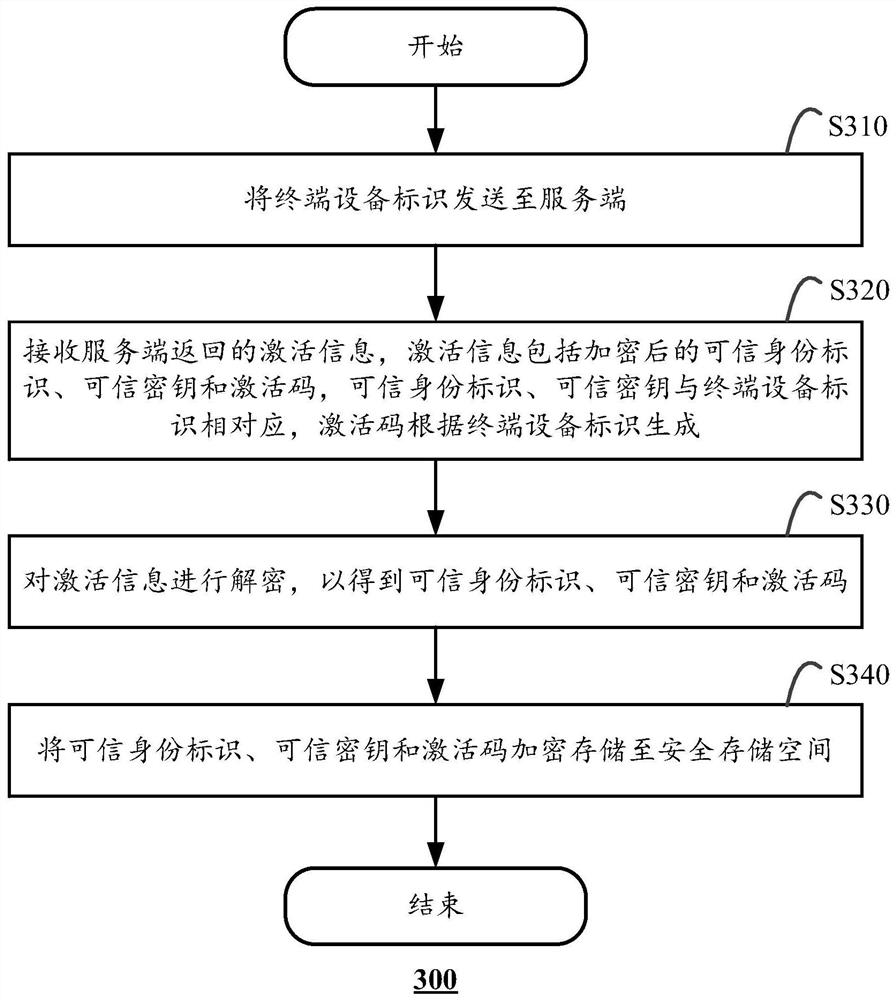
Application activation method and device based on trusted execution environment
PendingCN111625829AEnsure safetyImprove transmission securityDigital data protectionPlatform integrity maintainanceTerminal equipmentEngineering
The invention discloses an activation method of a trusted execution environment, the trusted execution environment is deployed in a terminal device, and the method comprises the following steps: sending a terminal device identifier to a server; receiving activation information returned by the server, the activation information comprising an encrypted trusted identity identifier, a trusted key andan activation code, the trusted identity identifier and the trusted key corresponding to the terminal device identifier, and the activation code being generated according to the terminal device identifier; decrypting the activation information to obtain a trusted identity, a trusted key and an activation code; and encrypting and storing the trusted identity, the trusted key and the activation codeinto a secure storage space. The invention also discloses an activation verification method of the trusted execution environment, an application activation and activation verification method based onthe trusted execution environment, and a corresponding device.
Owner:ALIBABA GRP HLDG LTD
Goods tracing anti-counterfeiting coding method
ActiveCN101980186AEnsure safetyUniqueness guaranteedRecord carriers used with machinesSpecial data processing applicationsComputer hardwareBarcode
The invention discloses a goods tracing anti-counterfeiting coding method and solves the technical problems of simple coding method of goods, and large amount of operation. The technical scheme adopted by the invention is that: the method is implemented in a database of a network server by using a computer and a matched software management procedure. The anti-counterfeiting coding method comprises the following steps of: classifying and numbering global goods and storing the numbers in the database of the network server; encrypting the classified numbers and generating check codes first by using a computer memory and the matched encrypt algorithm on the basis of the standard data encrypt algorithm; and encrypting the check codes and finally generating ASII code characters of 16 digits, writing in the radio frequency identification or preparing bar codes, pasting on products and storing in the database of the network server. The anti-counterfeiting coding method has the advantages that: the security, uniqueness and non-replicability of data are guaranteed by adopting the double-encryption manner of encrypting classified numbers and generating check codes and encrypting the check codes again and the deciphering difficulty is increased.
Owner:SHENZHEN JAVS TECH
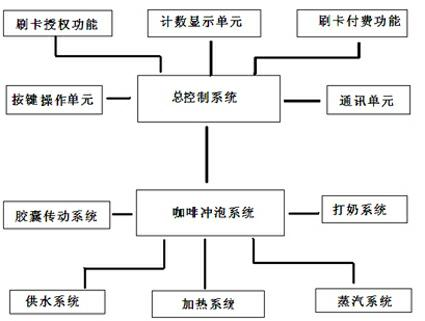
Anti-counterfeiting Internet of things coffee machine capable of counting and its anti-counterfeiting distribution method
ActiveCN102556531AGuaranteed non-reproducibilityPrevent fraudulent useBeverage vesselsPackagingDistribution methodAuthorization
The invention relates to the field of merchandise sales, in particular to a coffee machine for brewing a coffee capsule or equipment for brewing a coffee capsule-like beverage capsule bag or grain capsule bag, at the same time to a coffee capsule anti-counterfeiting identification and encryption method, further to a distribution method of the coffee capsule with anti-counterfeiting identification function, and still further to an identification method and counting method of the coffee machine for brewing the coffee capsule with anti-counterfeiting identification function. The inventive coffee capsule and coffee machine both adopt data encryption for uniqueness locking, and are enabled for use under specified authorization, so that the manufacturers and agents at each level can accurately monitor the product flow and sales, to ensure benefits of the manufacturers and agents, prevent shoddy products and guarantee rights and interests of consumers.
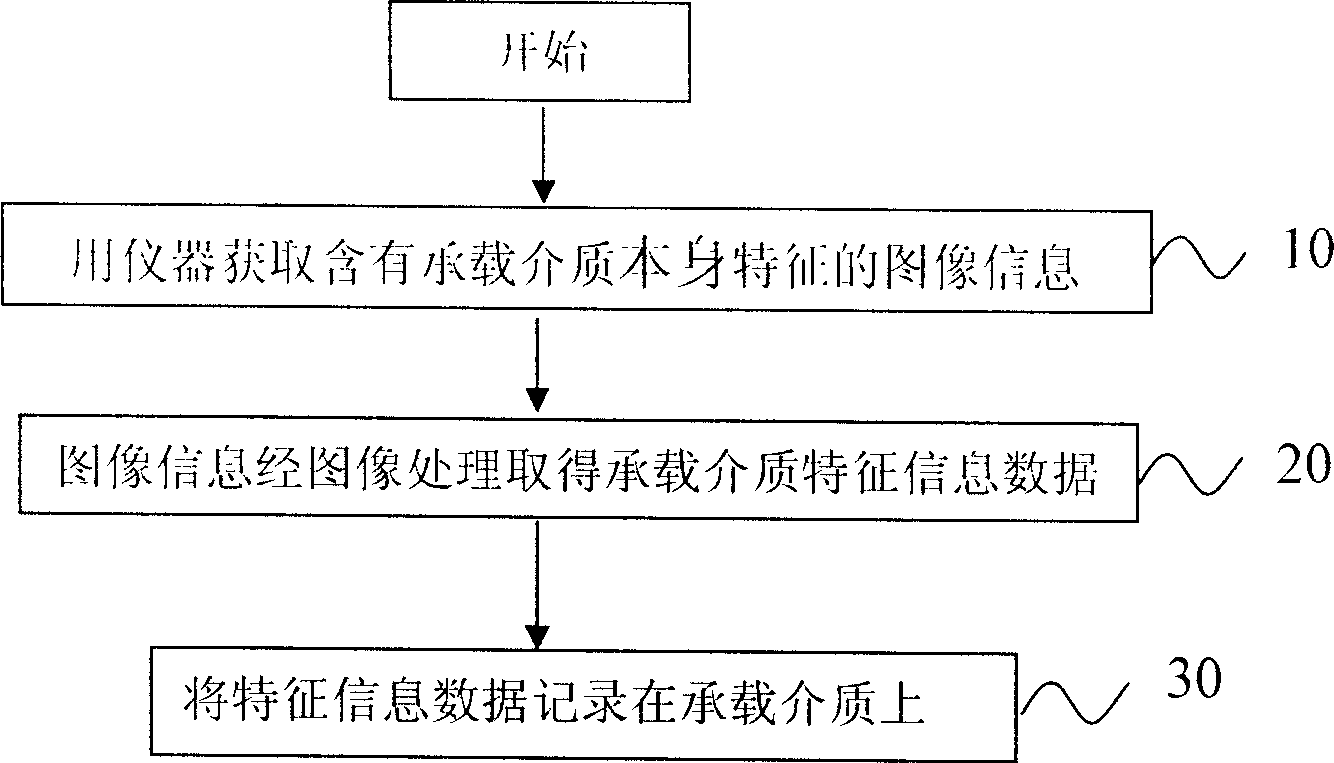
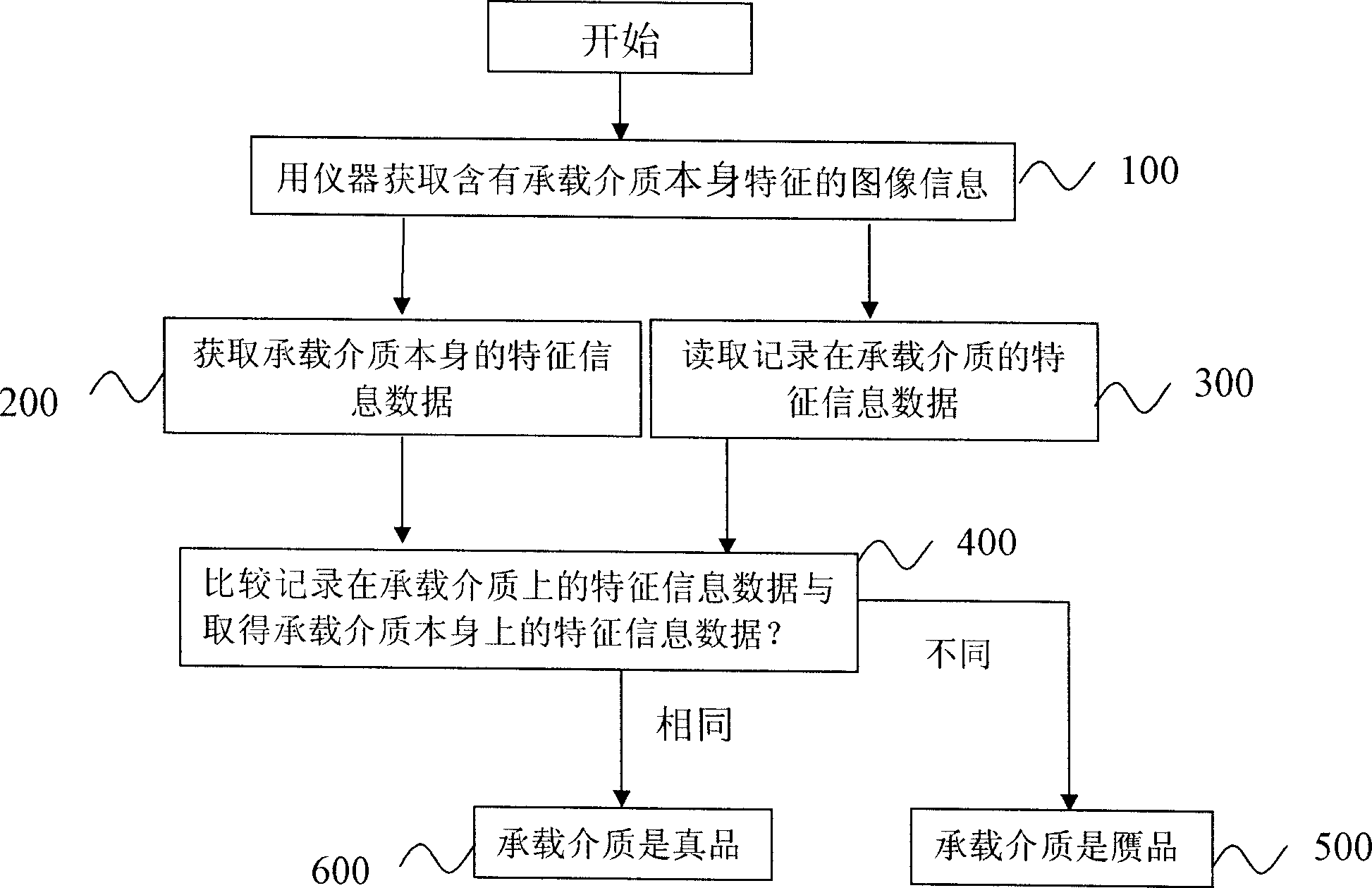
Anti-fake method of recording carrying medium self character
InactiveCN1904949AUniqueness guaranteedGuaranteed non-reproducibilityPaper-money testing devicesCo-operative working arrangementsComputer hardwareInstrumentation
The invention discloses a fake defend method that includes the following steps: gaining carrying medium self feather information data and recording on carrying medium itself; comparing the self feather information on carrying medium with gained information to take fake defend identification. The benefit of the invention is that: it could realize identification without altering the label, chip, or coating layer contained by bearing medium, and need not to be supported by database. It is a very effective fake defend method in different industry.
Owner:樊晓青
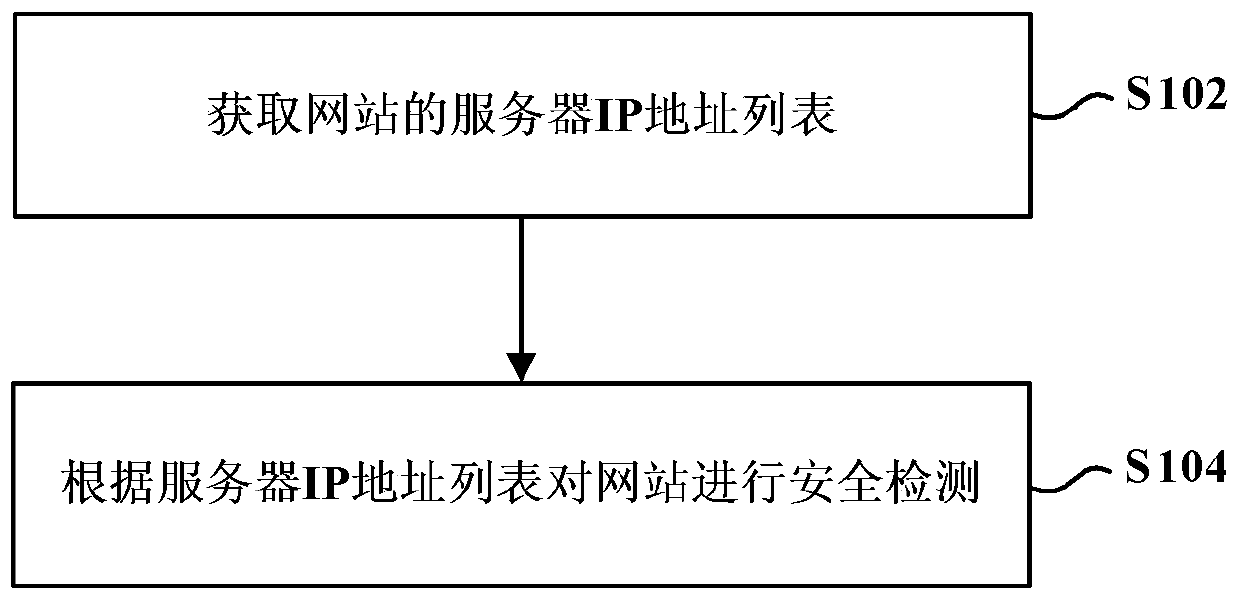
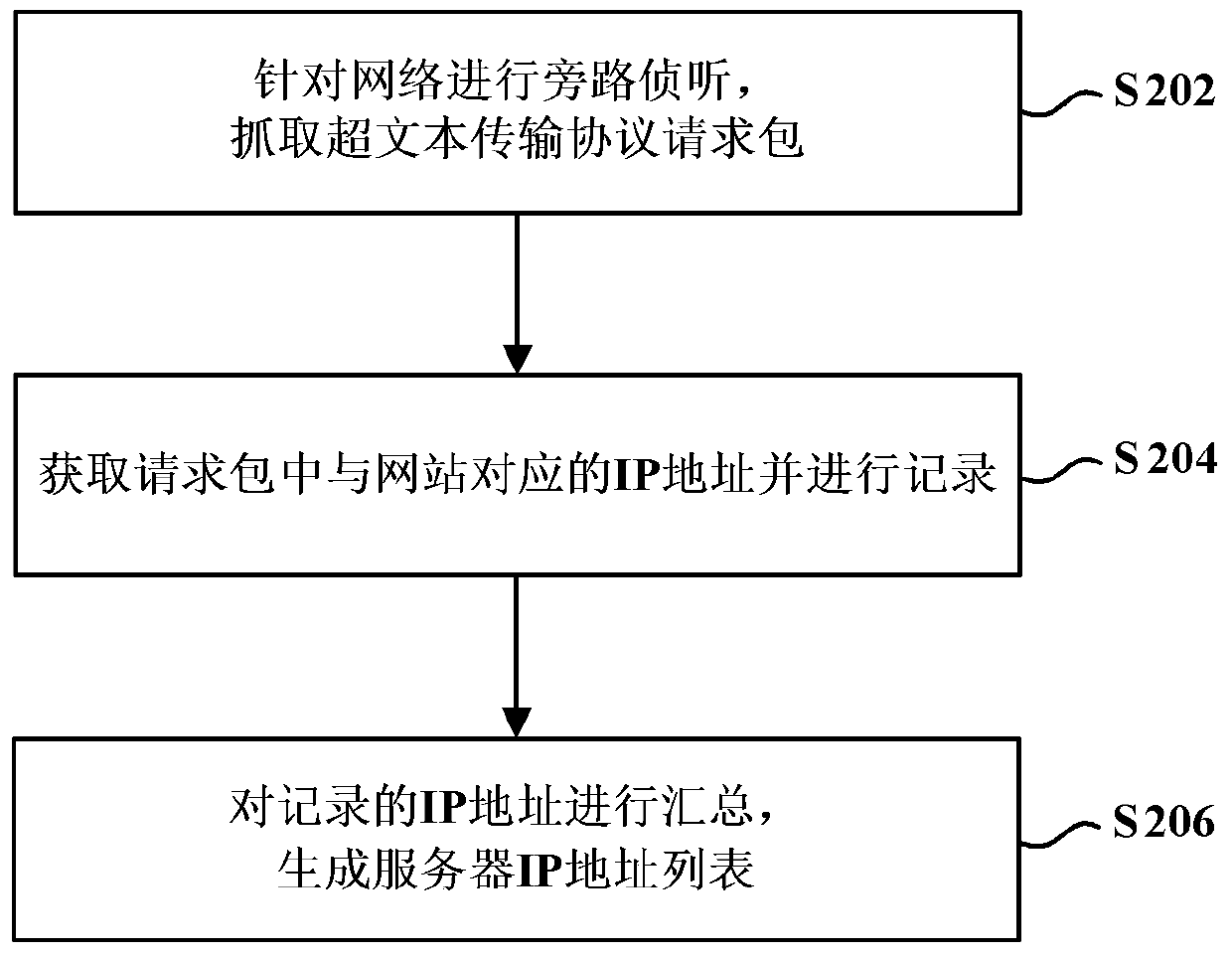
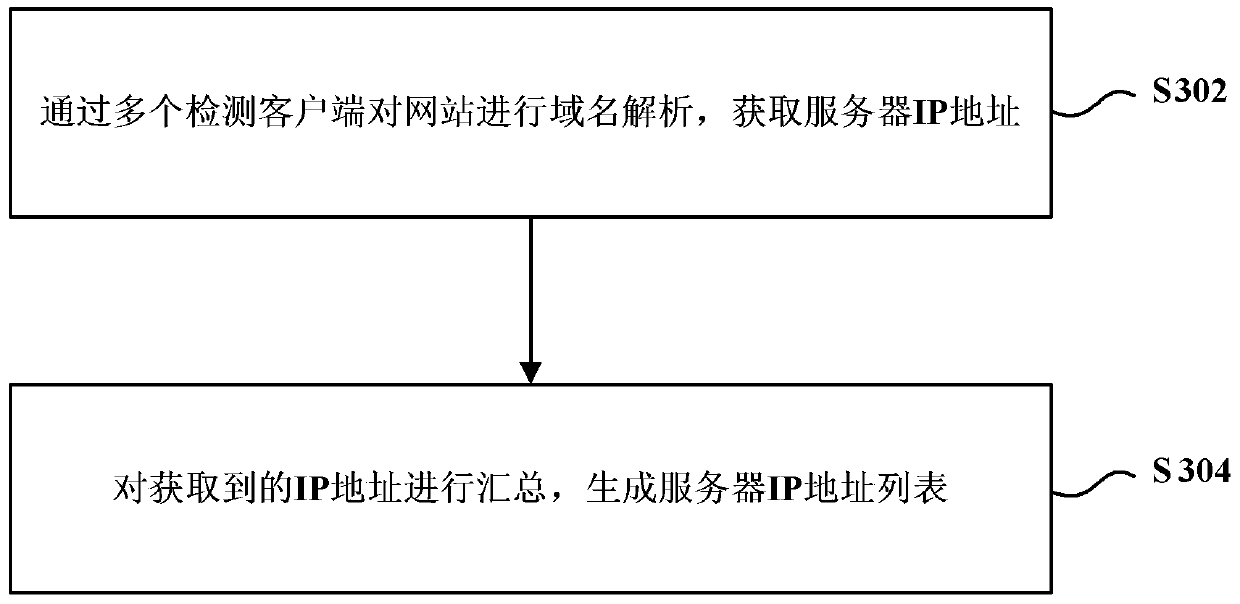
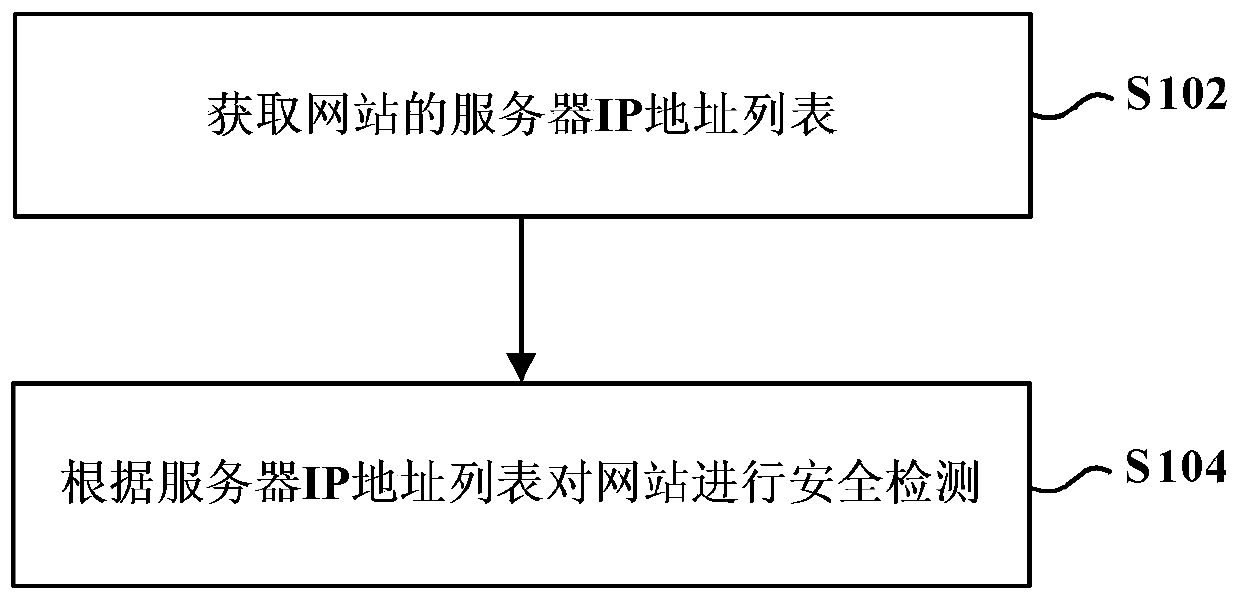
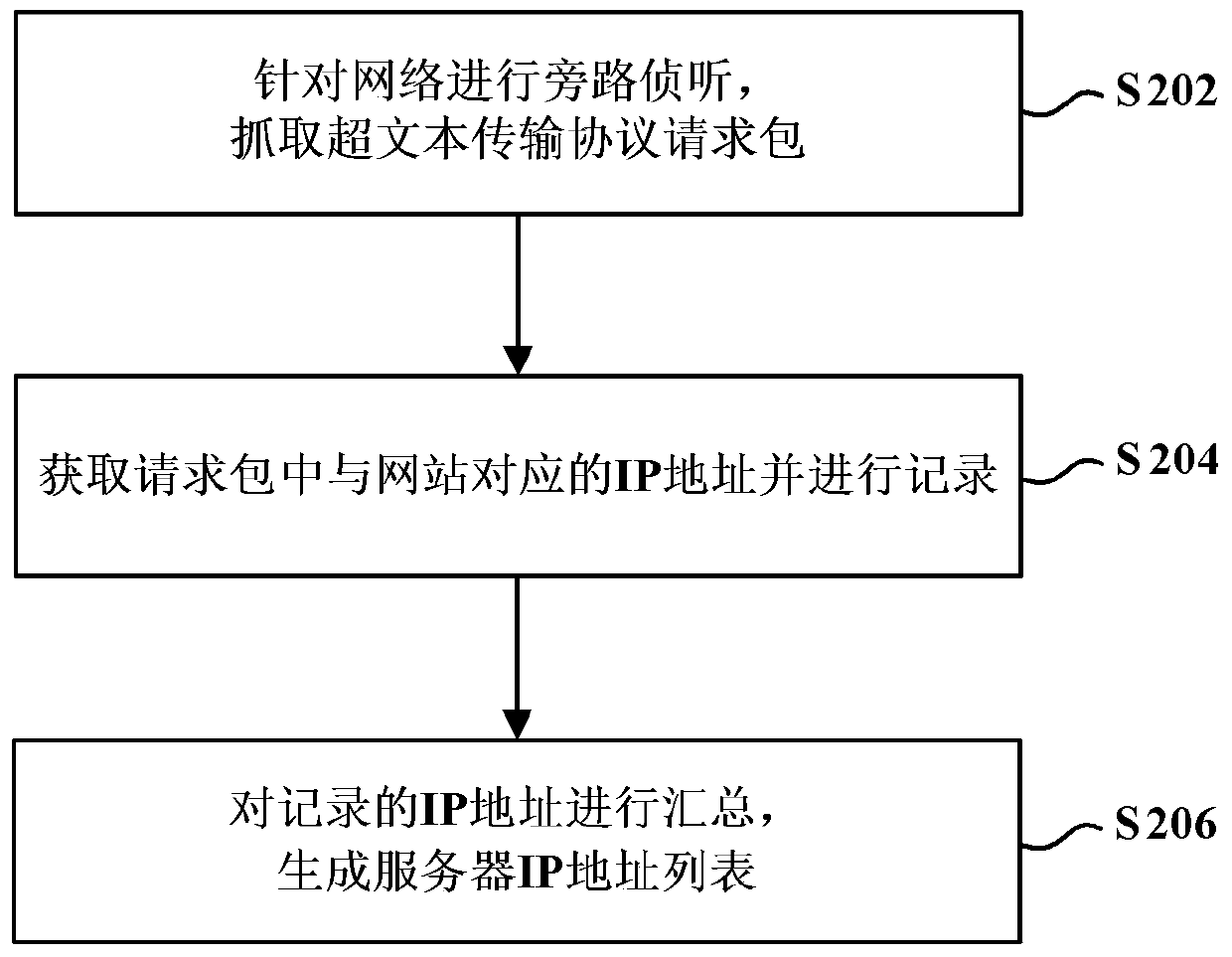
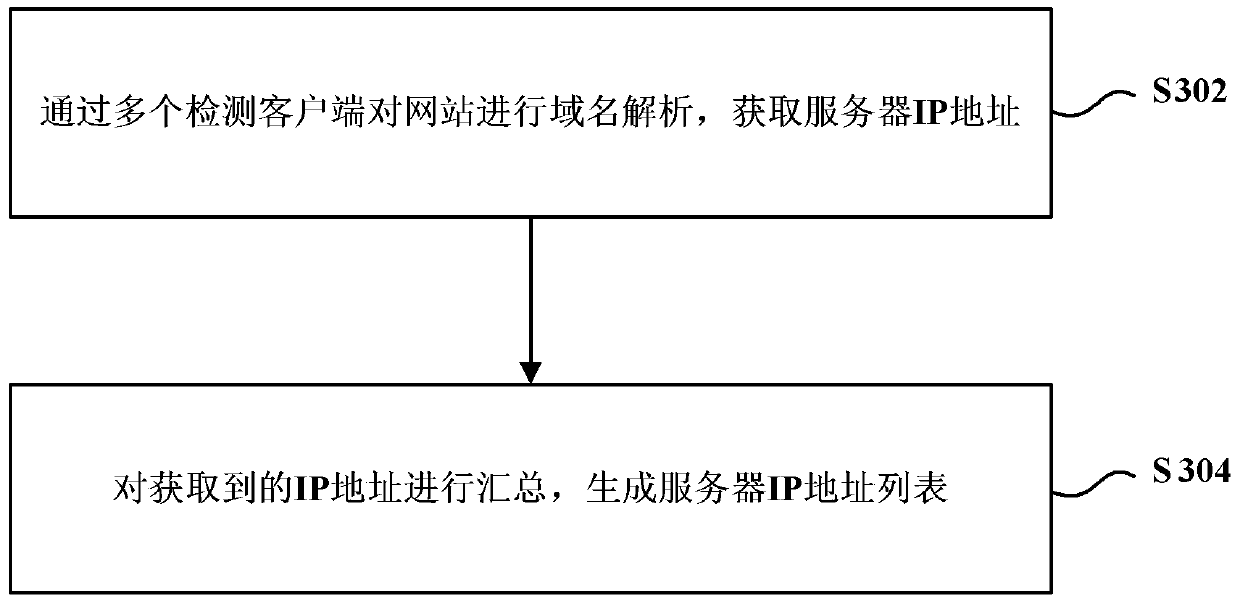
Website security detection method and website security detection device
ActiveCN105515882AUniqueness guaranteedGuaranteed non-reproducibilityData switching networksProtocol for Carrying Authentication for Network AccessSecurity function
The invention provides a website security detection method and a website security detection device. The method comprises the following steps: acquiring a server Internet Protocol IP address list of a website, wherein each server has an IP address, and the IP addresses of different servers are different; and performing security detection of the website based on the server IP address list. By using the website security detection method in the embodiment of the invention, security detection of websites can be performed more efficiently and reasonably, and the efficiency of website security detection can be improved.
Owner:BEIJING QIANXIN TECH
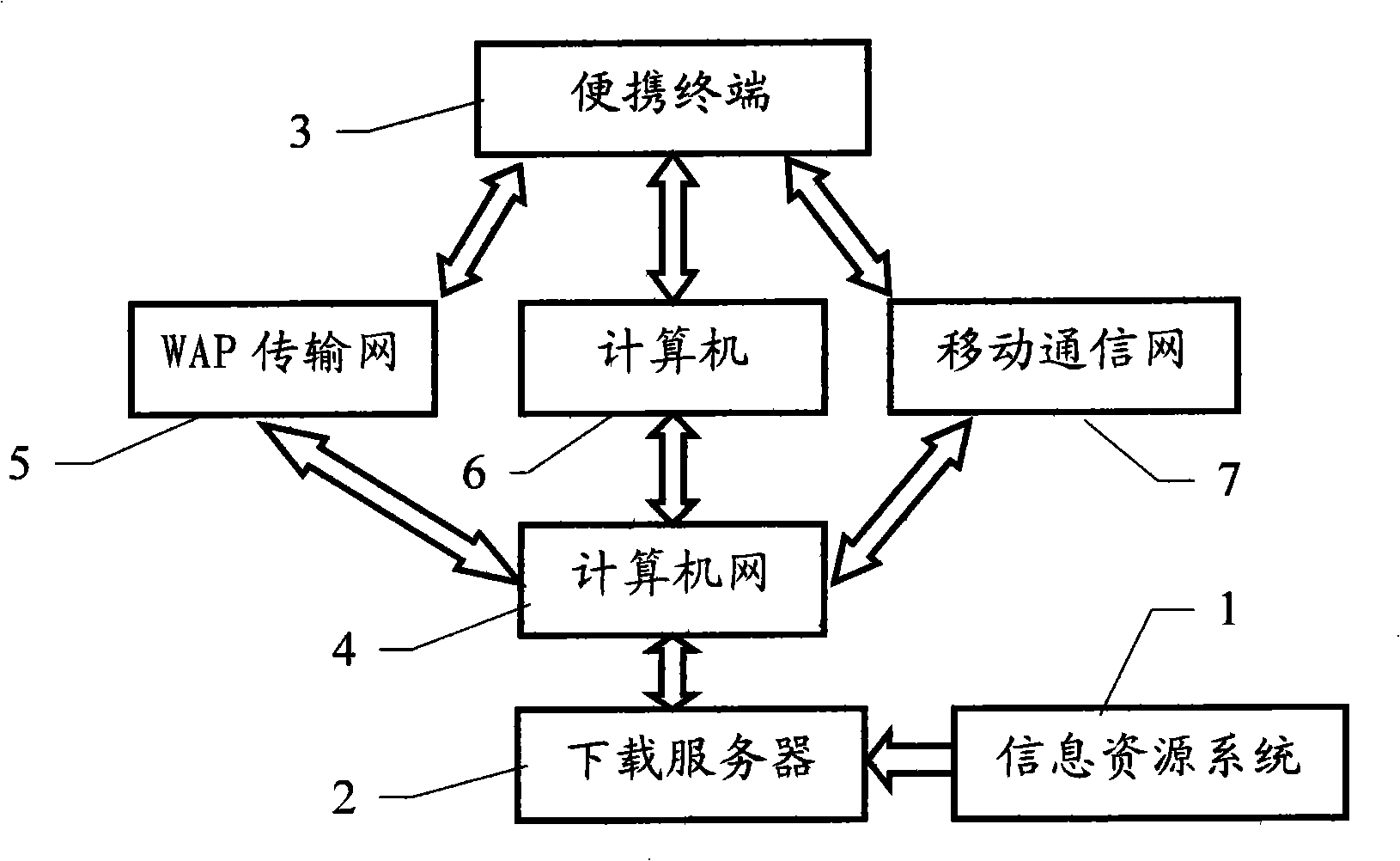
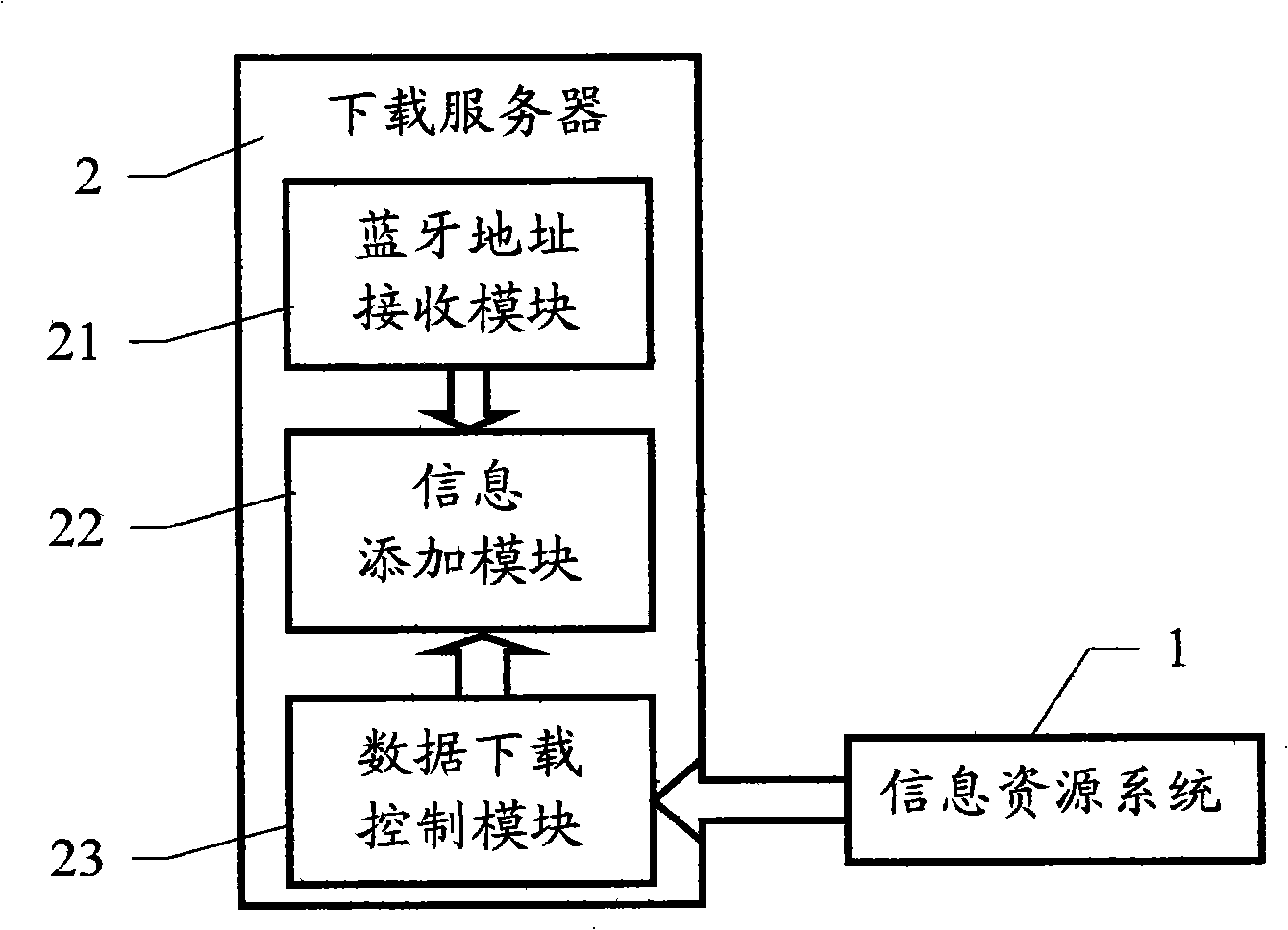
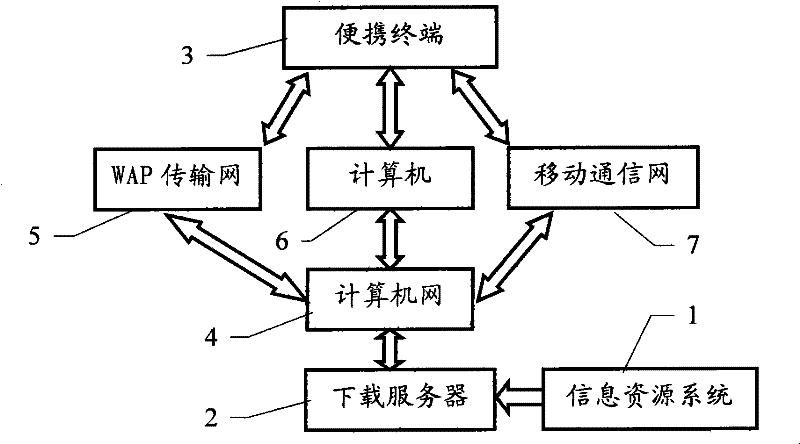
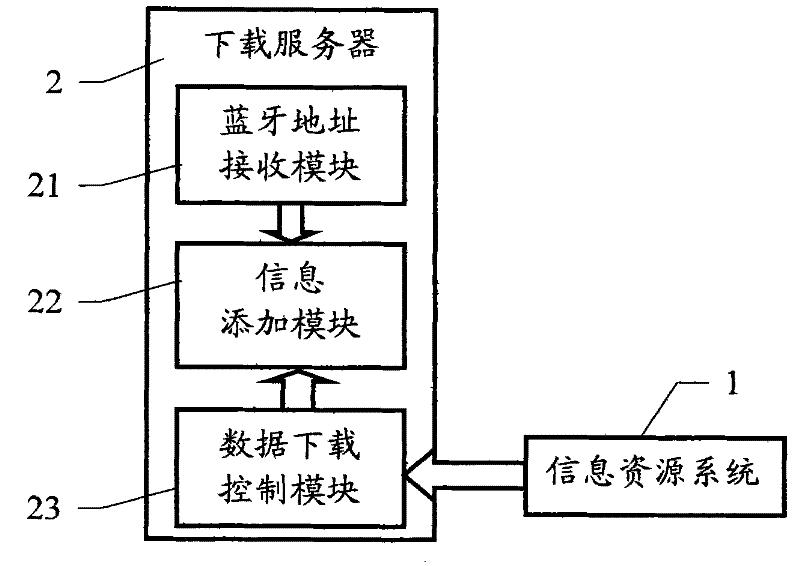
Copyright protection method and system for downloading data by portable terminal
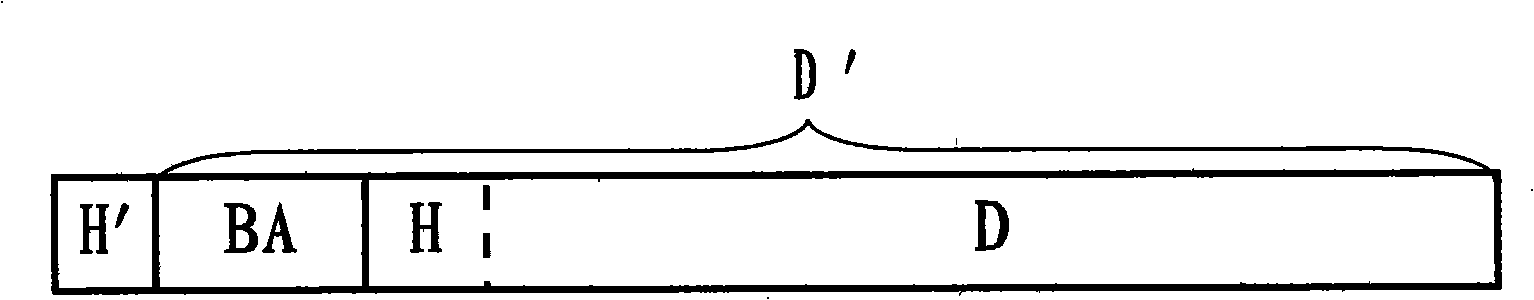
InactiveCN101340653AGuaranteed non-reproducibilityReduce data encryption burdenRadio/inductive link selection arrangementsProgram/content distribution protectionComputer hardwareOccupancy rate
The invention relates to a method and a system of copyright protection, which are used for a portable terminal to download data; the invention belongs to the technical field of digital copyright protection and relates to the method and the system of copyright protection in the process of data information transmitting. In the invention, a Bluetooth equipment address is taken as the encrypted information of downloaded data to encrypt the downloaded data, namely, before the data is transmitted or downloaded to the portable terminal which is provided with a built-in Bluetooth module, the Bluetooth equipment address of the portable terminal is added to the appropriate position of the downloaded data and then sent to the portable terminal; when the data is operated or played, the Bluetooth equipment address is extracted from the built-in Bluetooth module of the portable terminal and is used for comparison with the encrypted information added in the encryption of the data; if correct, the data document is operated or played, otherwise, operation is stopped. The method of the invention is characterized by simple encrypting and decrypting, low resource occupancy rate to the equipment, good confidentiality, convenient use, and the like, which is specially applicable to the potable terminal with limited hardware performance.
Owner:四川长城软件科技股份有限公司
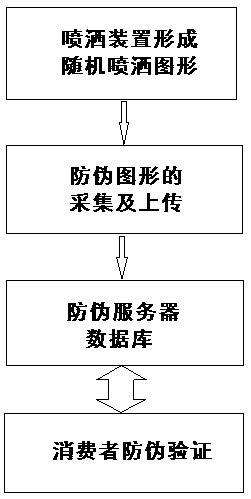
Anti-fake method and application using random spray coverage pattern and digital image contrast technology
InactiveCN108074110AAvoid Anti-Counterfeiting VulnerabilitiesUniqueness guaranteedDuplicating/marking methodsCommerceGraphicsDigital image
Disclosed is an anti-fake method and application using random spray coverage patterns and a digital image contrast technology. The method relates to an anti-fake technology. The method comprises the following steps of A, random spray coverage patterns are formed by a spraying device; B, anti-fake patterns are collected and uploaded; C, operation of a verification end is conducted; D, a verification process is conducted. According to the method, by the cooperation of randomly spraying and code information stickers of commodity identification information, all anti-fake information of the commodities are integrated into entitative random patterns, anti-fake patterns are transmitted and contrasted by using an information technology, the anti-fake information is read to prevent anti-fake vulnerabilities in the circulation of the commodities, uniqueness and unduplicated performance of the commodities are ensured, mechanical random spraying is adopted in mass production, equipment is the same, but an obtained random state set is completely uncontrollable. The random spraying method has a good anti-fake effect, despite the fact that the anti-fake method is simple to operate, but the anti-fake effect is good, risks of being cracked do not exist, the anti-fake cost is low, and the method is easy to query and verify, and has extremely high market popularization and application value.
Owner:王登顺
Anti-fake tracing method based on hyper-elliptic curve cryptosystem
ActiveCN105450399AEnsure safetyUniqueness guaranteedPublic key for secure communicationCryptosystemHand held devices
The invention discloses an anti-fake tracing method based on a hyper-elliptic curve cryptosystem. The anti-fake tracing method comprises the following steps: setting a production enterprise code, a date code and a specification code; performing encryption conversion on the production enterprise code, the date code and the specification code through a conversion method of system conversion and section partition; performing permutation and combination on section identification codes and authentication type codes in the production enterprise code, the date code and the specification code and generating a check code; taking an elliptic cure cryptosystem as a public key infrastructure platform, designing the tracing method and using a C / S architecture; a system distributes a public key and a private key to a handheld device, and during decoding, the handheld device inquires the public key and the private key to a server, compared with the existing anti-counterfeit technology, the anti-fake tracing method based on the hyper-elliptic curve cryptosystem provided by the invention has the advantages of being large in data volume and difficult to be imitated; besides, the security, the uniqueness and the unduplicatedness of data are guaranteed, the decoding difficulty is increased and the anti-falsification is strong.
Owner:SHANDONG ACADEMY OF AGRI MACHINERY SCI
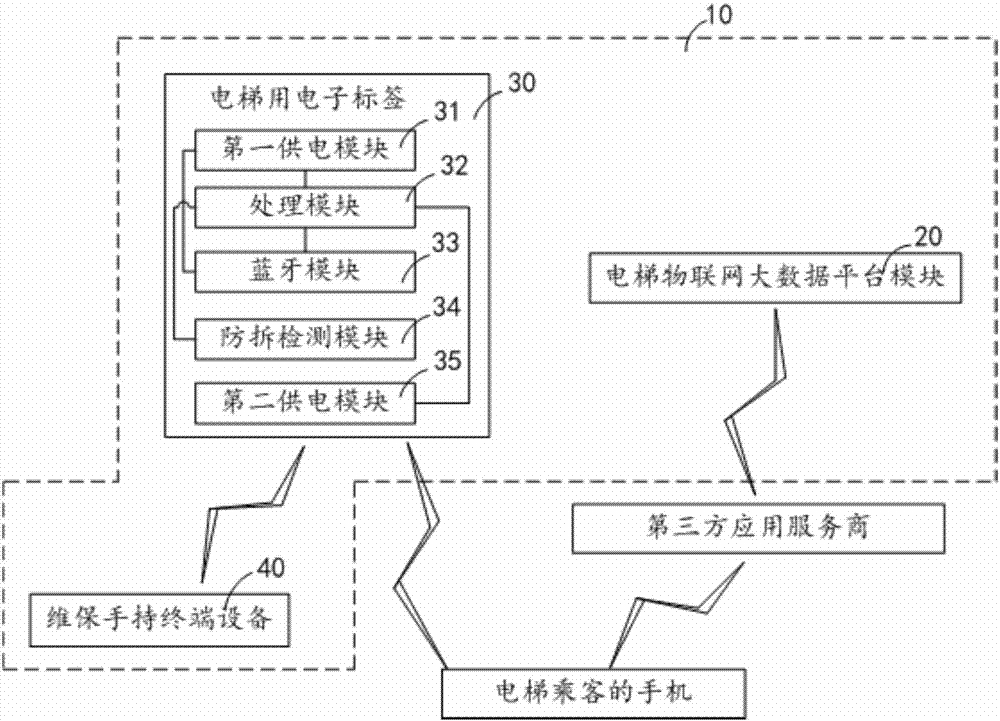
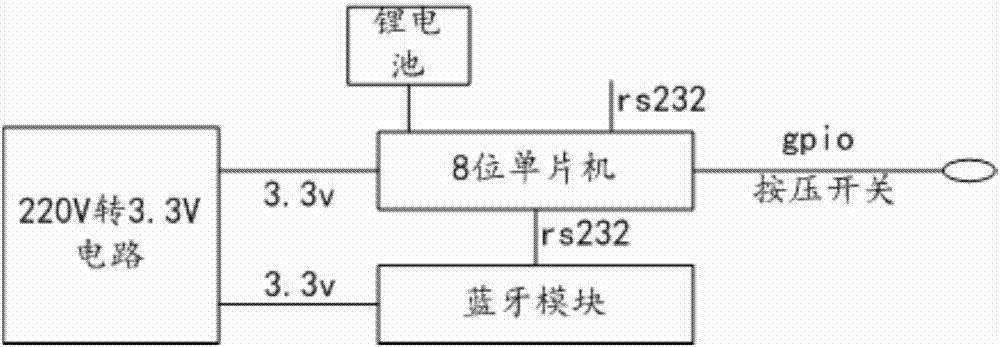
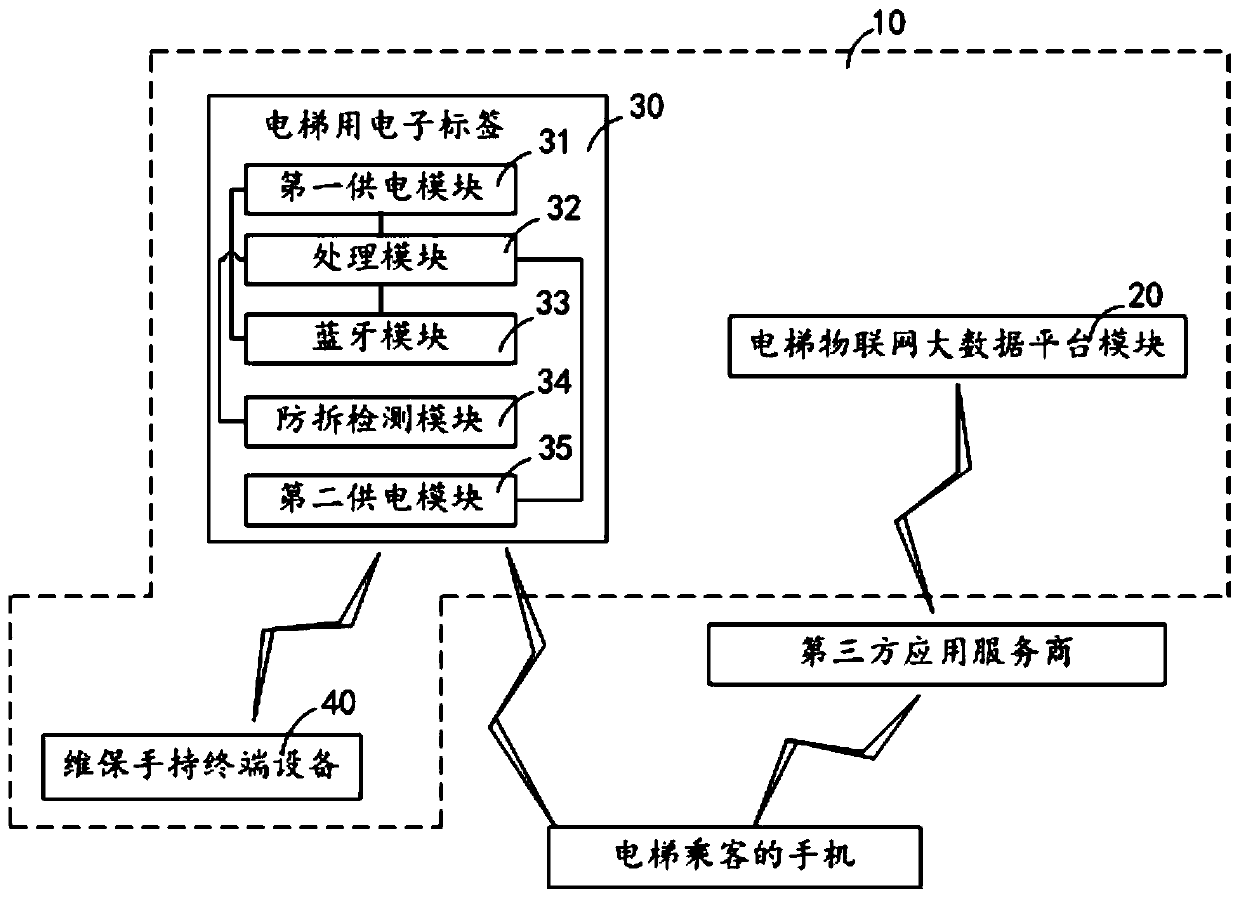
Elevator-used electronic label and elevator information query system
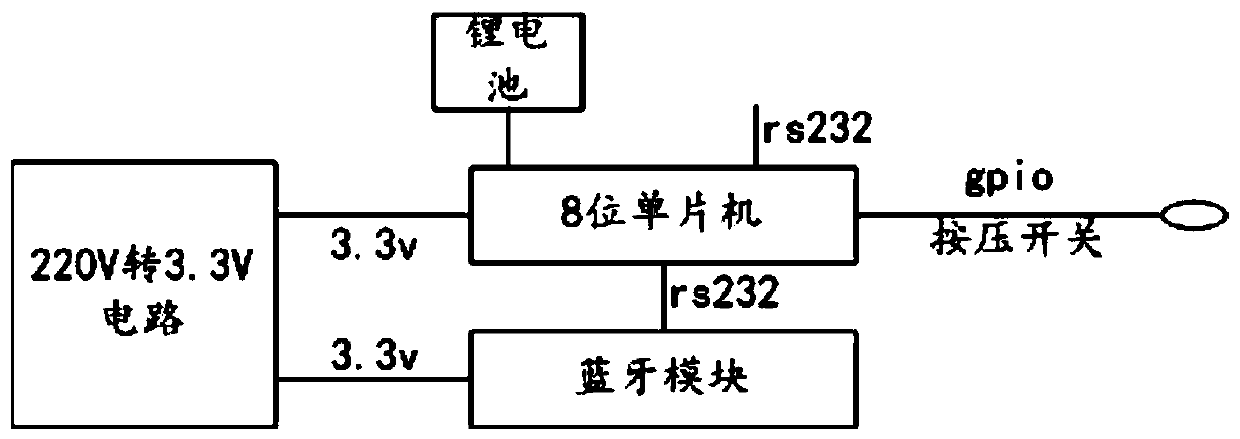
ActiveCN106934430AUniqueness guaranteedGuaranteed non-reproducibilityCo-operative working arrangementsDigital data protectionTerminal equipmentBluetooth
The invention discloses an elevator-used electronic label, which comprises a first power supply module, a processing module and a Bluetooth module, wherein the processing module is electrically connected with the first power supply module and the Bluetooth module; the first power supply module is also electrically connected with the Bluetooth module; the first power supply module provides working voltage for the processing module and the Bluetooth module; the processing module is used for regularly reading a pre-stored primitive elevator registration code and an encryption rule, corresponding elevator transmission information is generated according to the read primitive elevator registration code and the encryption rule, the generated elevator transmission information is provided for the Bluetooth module, and the elevator transmission information comprises readable information and encryption information; and the Bluetooth module is used for regularly transmitting the received elevator transmission information in a broadcast form according to an ibencon protocol, and thus, the information can be received by a mobile phone of an elevator passenger, and an elevator maintenance person can arrive at the elevator field and uses a maintenance handheld terminal device to receive the information to acquire the elevator registration code. The invention also provides an elevator information query system.
Owner:宁夏电通物联网科技股份有限公司
Interactive transaction service method for designating commodity generation identification code
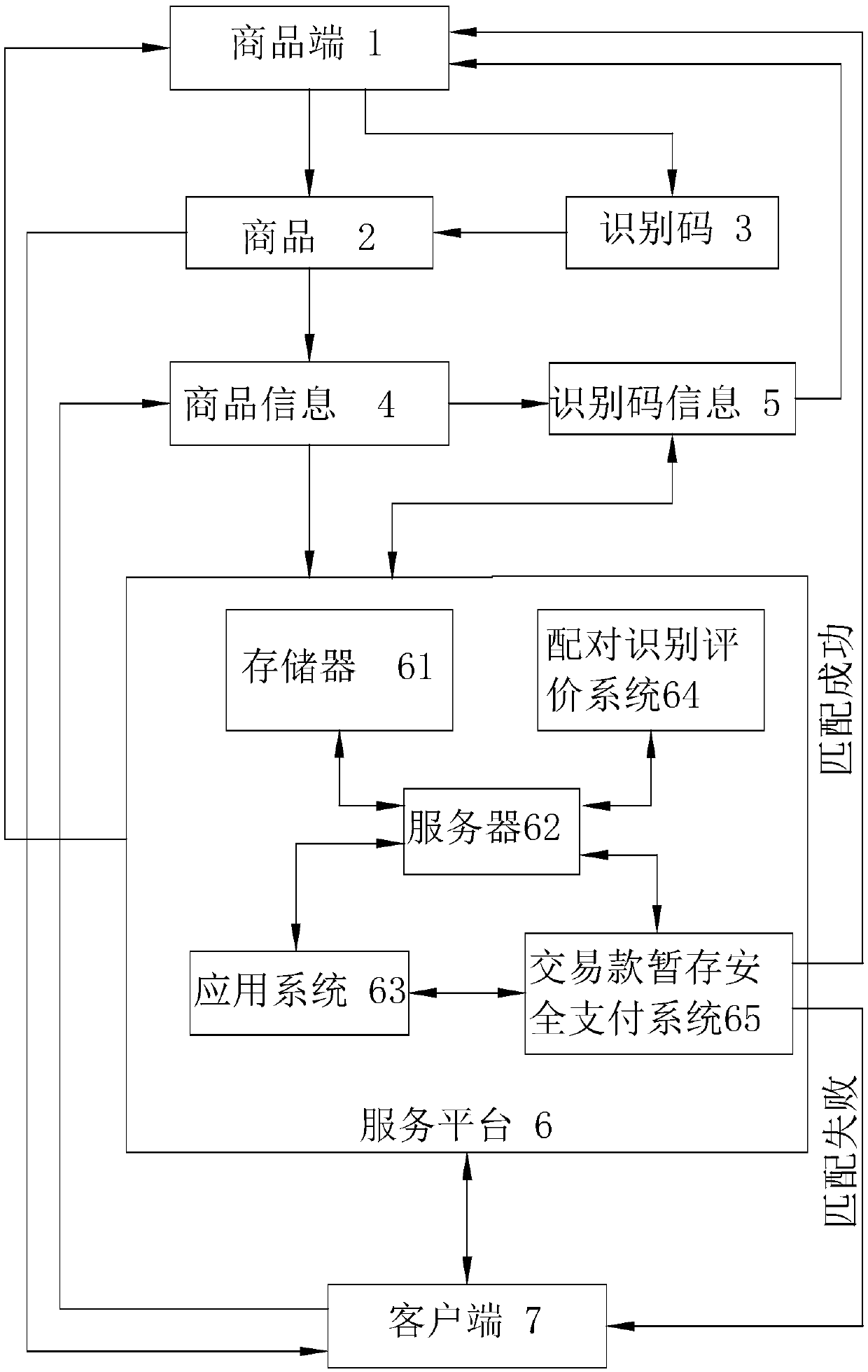
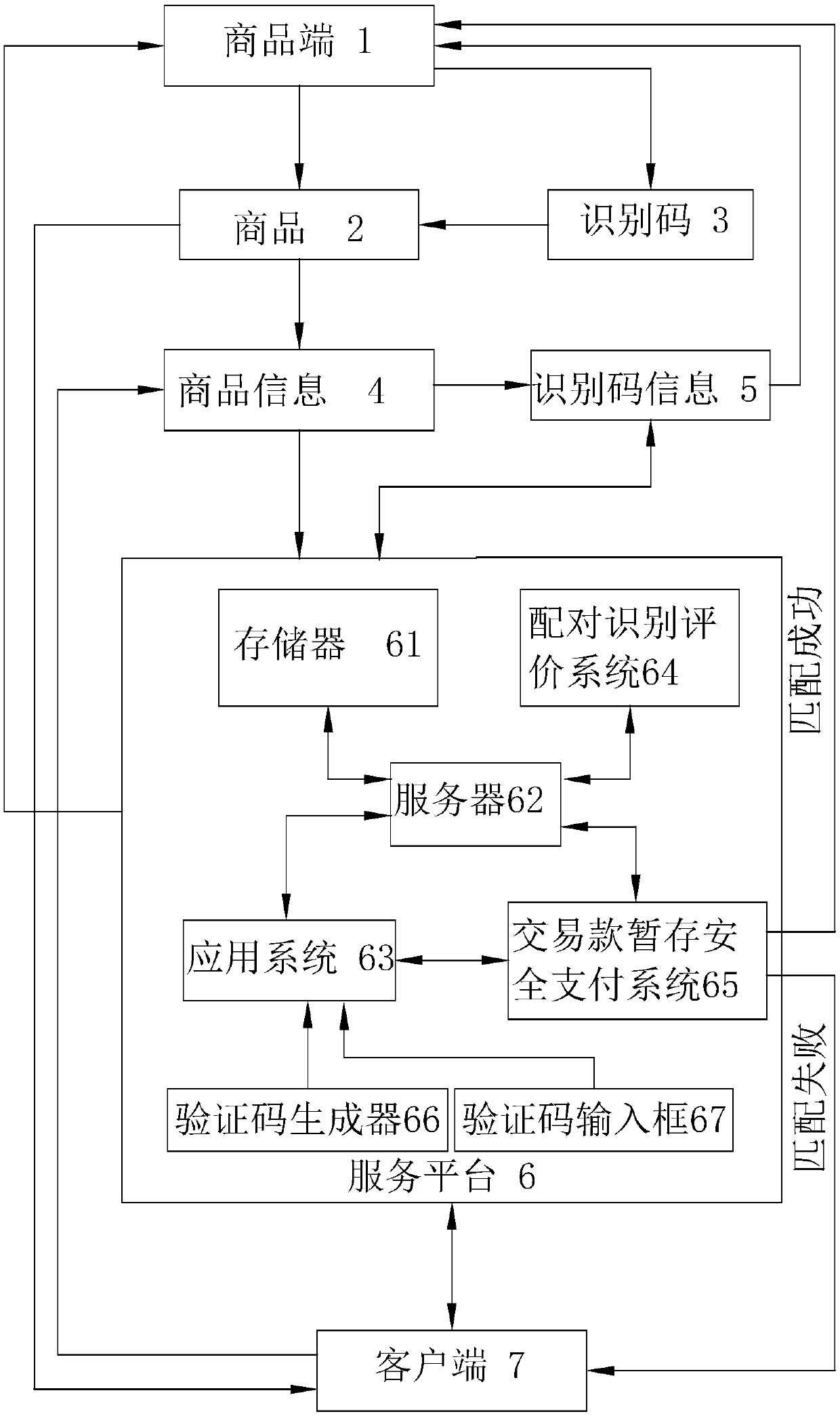
InactiveCN109523346APrevent counterfeitingAvoid package drop, etc.Buying/selling/leasing transactionsTransaction serviceCustomer information
The invention relates to an interactive transaction service method for designating commodity generation identification code, which comprises the following steps: when a client selects commodity information on a service platform and sends the commodity information to a merchant terminal through the service platform, the merchant terminal sets an identification code by itself or the service platformautomatically generates an identification code; when the merchant terminal sends the commodity information to the merchant terminal through the service platform, the merchant terminal automatically generates an identification code. The merchant end bundles and stores the commodity information of the selected commodity and the identification code information of the generated identification code and the customer information on the service platform. The service platform sends the commodity information and the customer information of the commodity selected by the client to the merchant or sends the identification code information to the client at the same time. At that merchant end, the merchandise corresponding to the selecte merchandise information of the client end is sent to the client end according to the customer information; The client end judges whether the identification code of the received commodity matches the commodity information or / and the identification code information atthe time of selection. The invention effectively improves the flexibility of the merchant end in producing and sending commodities, at the same time effectively prevents the counterfeiting of commodities, or avoids the phenomena of switching packages and the like in the transportation of commodities.
Owner:巫远程
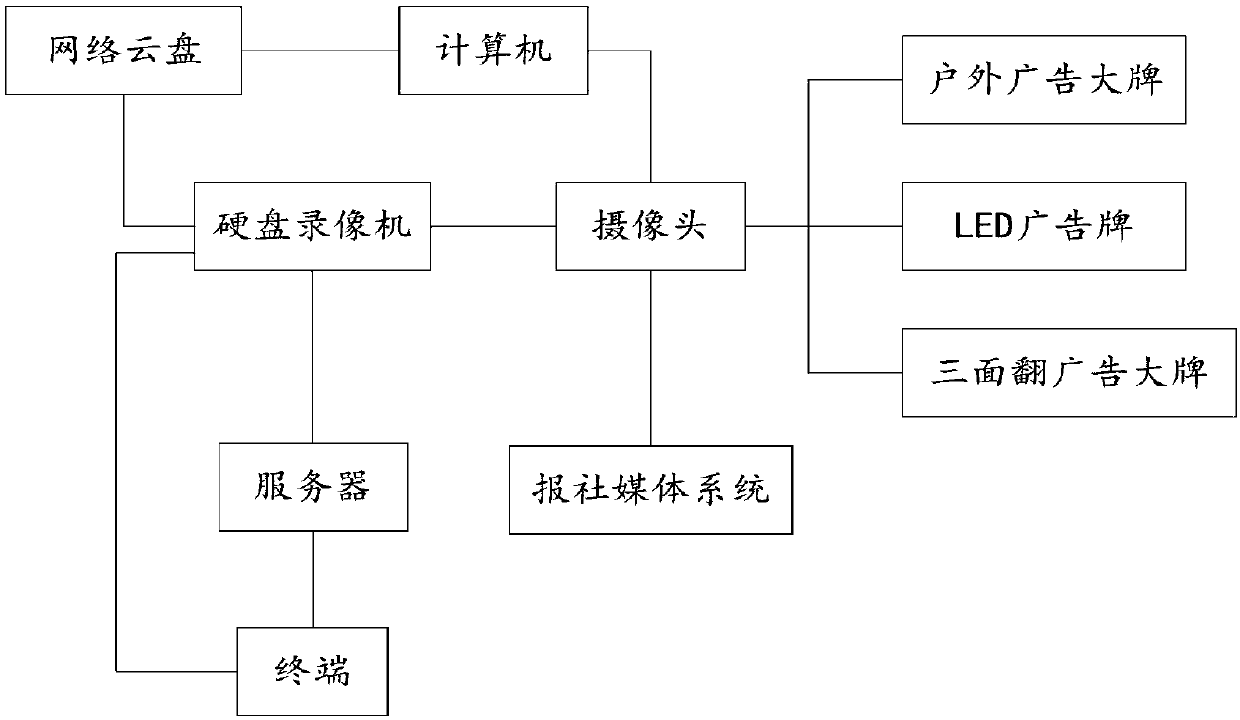
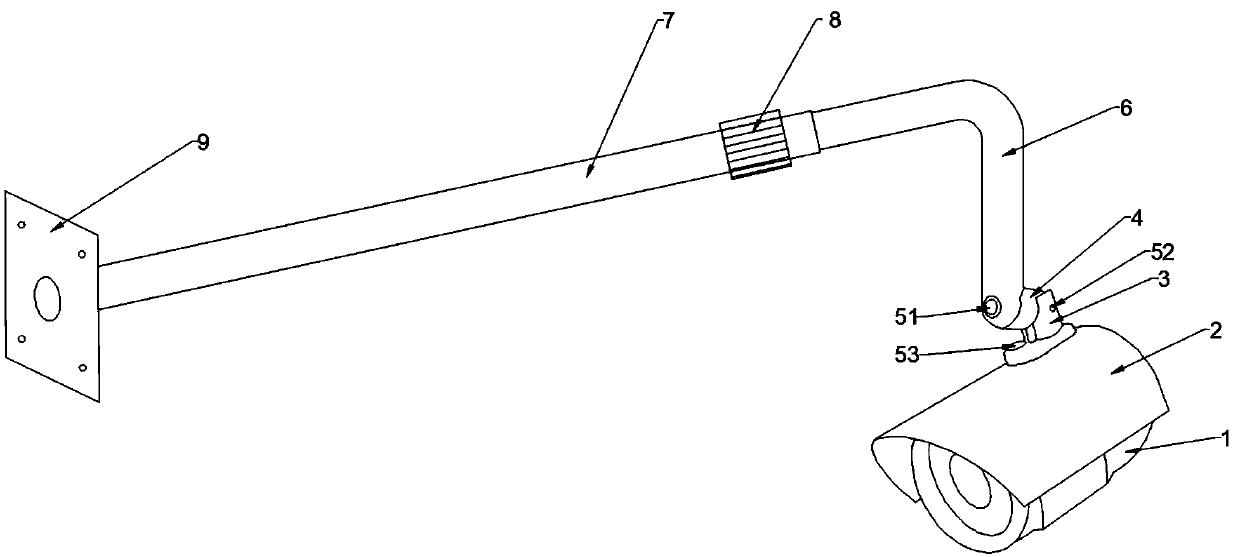
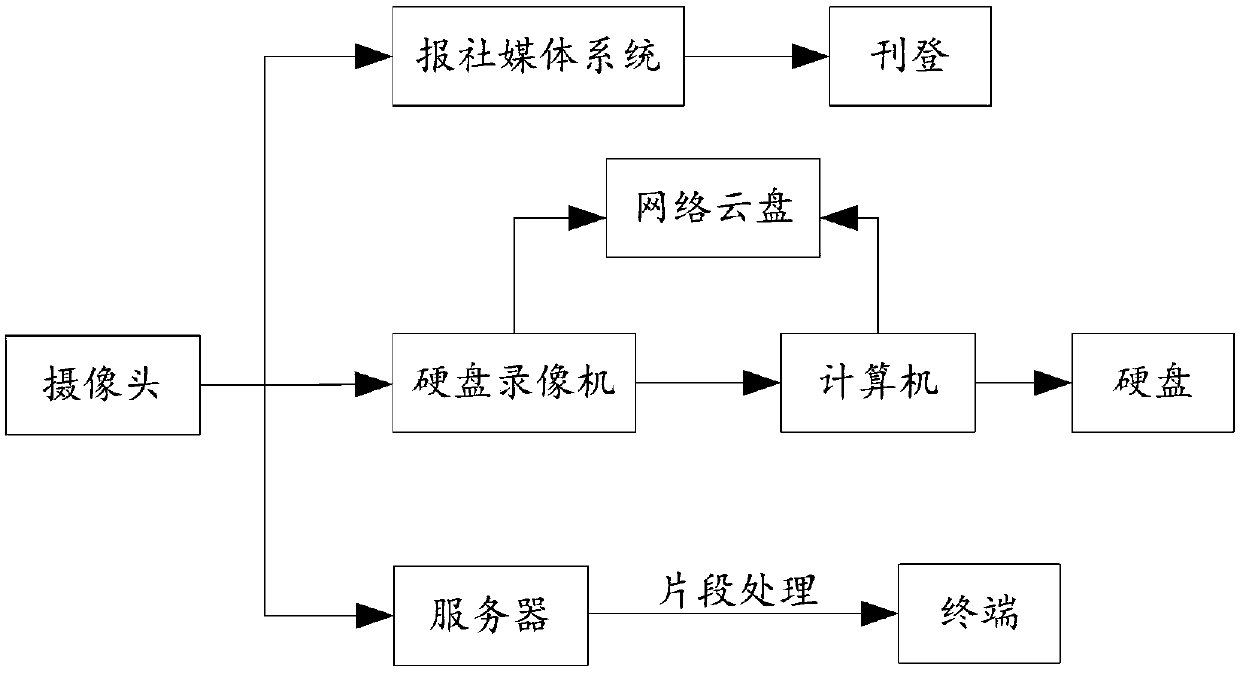
Billboard monitoring system and method
PendingCN109640058AGuaranteed accuracy and non-reproducibilityAvoid disputesTelevision system detailsColor television detailsFixed frameVideocassette recorder
The invention is applicable to the technical field of intelligent monitoring, and provides a billboard monitoring system and method. The system comprises an outdoor big billboard, an LED billboard, athree-sided big billboard, and camera components disposed on top corners of the outdoor big billboard, the LED billboard, and the three-sided big billboard, wherein the camera components comprise wide-angle cameras. The system also comprises: hard disk recorders, a newspaper media system, a server, and a computer equipped with a hard disk, wherein a hard disk recorder is embedded into each wide-angle camera, the camera components also comprise a bracket device that comprises a fixing rod, a lock nut, a telescopic rod and an angle adjusting device; and the angle adjusting device comprises a rotating knot, a screw and a fixing frame. The invention can effectively realize the information exchange and supervision between the customer, the advertiser and the media, effectively improve the monitoring of the billboard and improve the work efficiency.
Owner:湖南金力钢广告传播有限公司
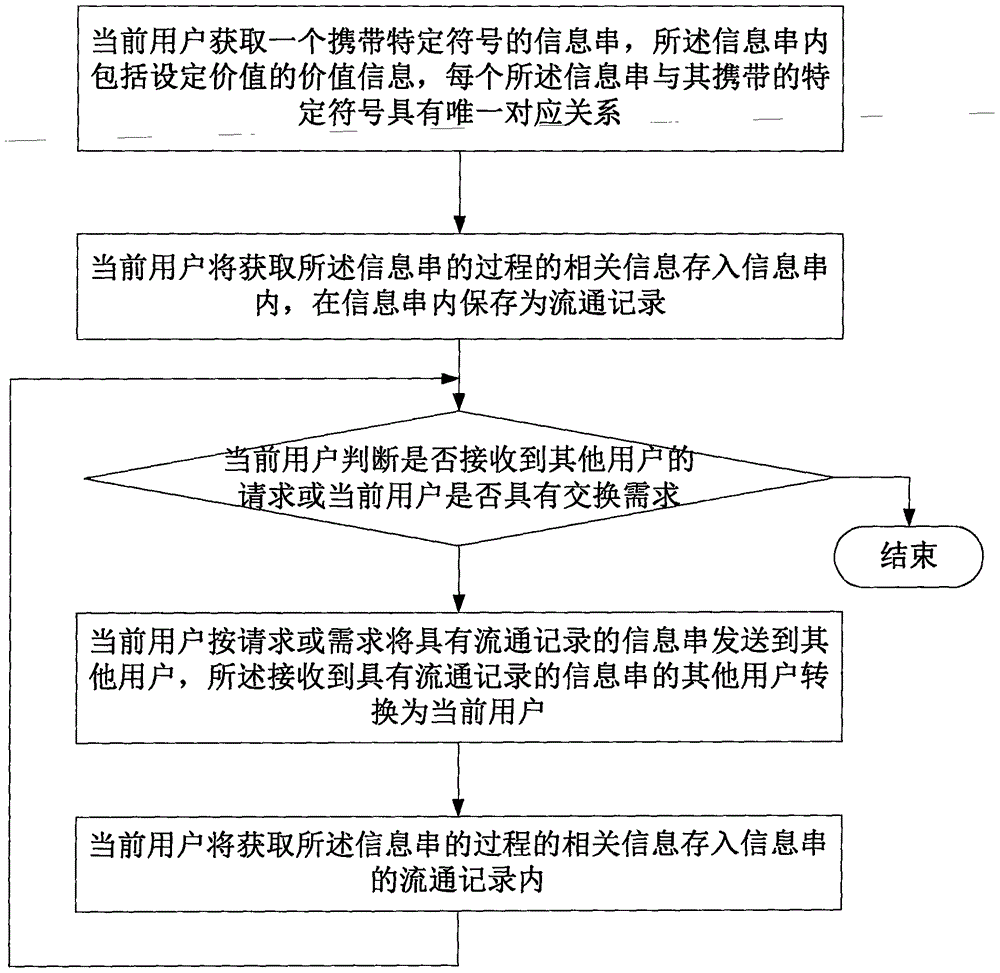
Circulating method and system for information in exchange
InactiveCN106469366AUniqueness guaranteedGuaranteed non-reproducibilityPayment circuitsRelevant informationLibrary science
The invention relates a circulating method and system for information in exchange, and the method comprises the steps: 1, enabling a current user to obtain one information string comprising a specific symbol, wherein the information string comprises the value information of a set value, and each information string has a unique corresponding relation with the carried specific symbol; 2, storing the related information of the process of obtaining the information string in the information string; 3, judging whether a request from another user is received or not or whether the current user has an exchange demand or not: executing step 4 if the request from another user is received or the current user has the exchange demand, or else, finishing the operation; 4, enabling the current user to transmit the information string with a circulating record to another user according to the request or demand of the current user, wherein the user who receives the information string with the circulating record is changed to the current user; 5, enabling the current user to related information of the process of obtaining the information string into the circulating record of the string information, and executing step 3. The method can achieve the exchange function, and also can achieve the information circulation.
Owner:太赞(北京)网络科技有限公司
TDAS-based wine bottle traceability anti-counterfeiting system and method
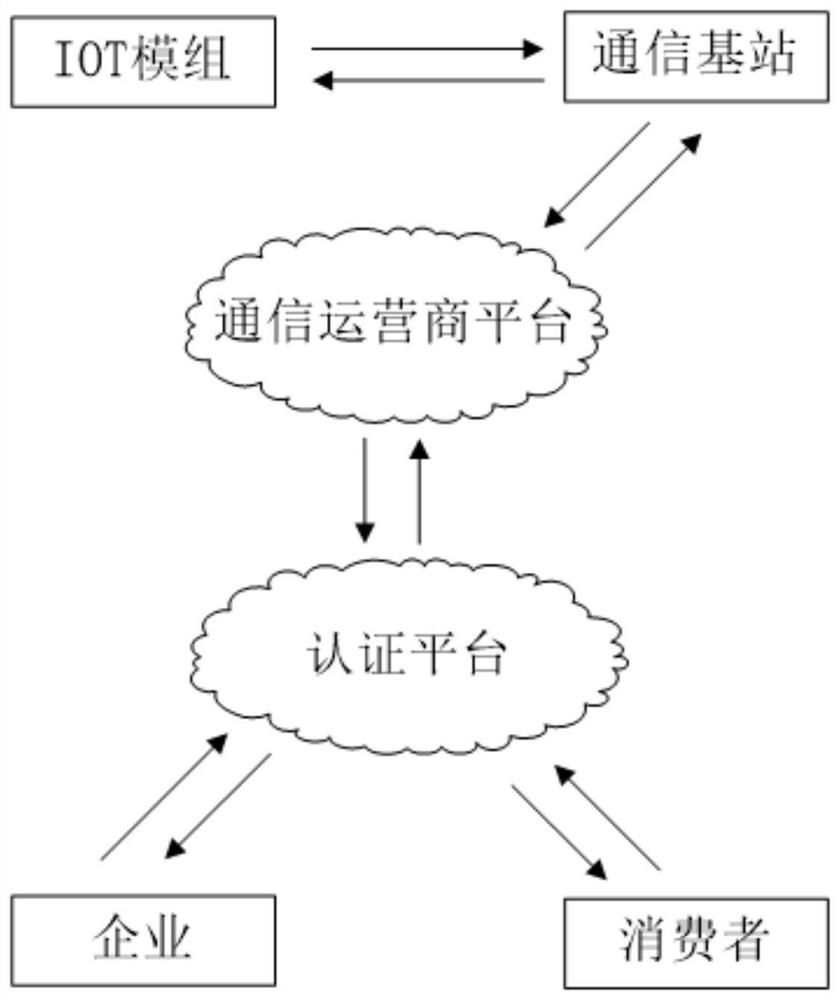
PendingCN111832677AGuaranteed non-reproducibilityGuaranteed unforgeableCo-operative working arrangementsCommerceBase stationSoftware engineering
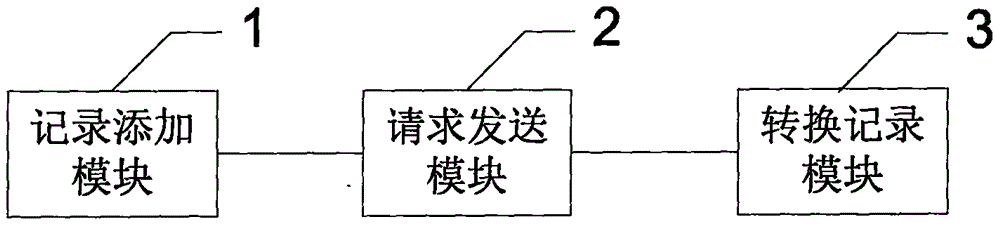
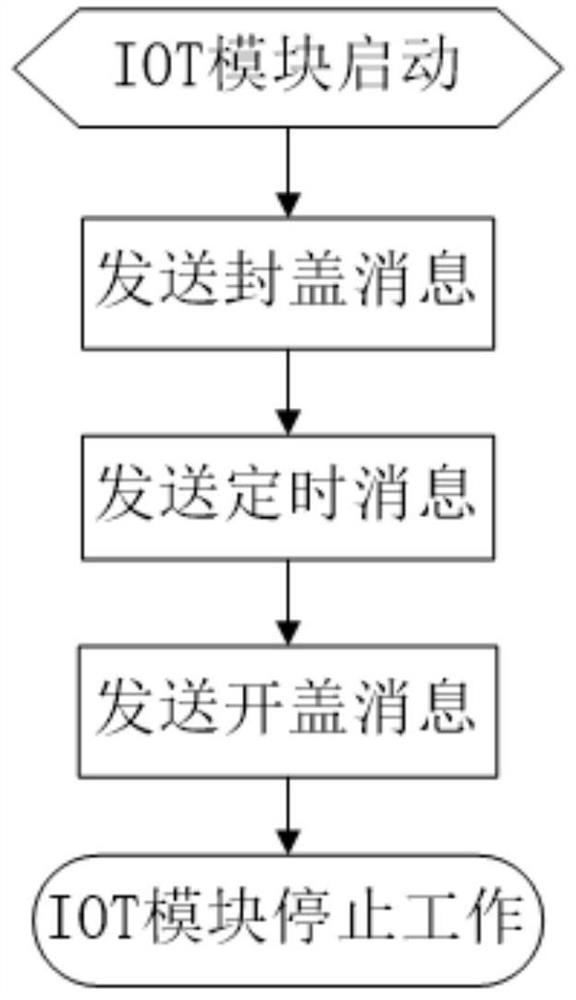
The invention discloses a TDAS-based wine bottle traceability anti-counterfeiting system, which comprises an IOT module, an RFID module and an authentication traceability platform, and the RFID moduleand the IOT module are integrated and packaged in a wine bottle cap; and the IOT module comprises a magnetic switch, the magnetic switch is matched with a magnetic sheet arranged on the wine bottle,and the magnetic switch triggers the IOT module to send a message to the authentication traceability platform. The invention also discloses a method, which comprises the following steps: the IOT module is started, and a message is sent to the authentication traceability platform by the IOT module; and the authentication traceability platform obtains the time and latitude and longitude positioningof the circulation node of the wine product through the base station code in the message. The capping message and the uncapping message of the IOT module are set to be triggered and sent only once, sothat the capping and uncapping operation of the wine is ensured not to be copied, and the wine is ensured not to be counterfeited; the authentication traceability platform acquires the logistics track of the wine through the data acquisition and analysis of the timing message, thereby ensuring the traceability of the circulation process of the wine and achieving the anti-counterfeiting effect.
Owner:SICHUAN JIUZHOU ELECTRONICS TECH
Urban intelligent electronic billboard monitoring system
InactiveCN110677620AGuaranteed accuracyGuaranteed non-reproducibilityClosed circuit television systemsTransmissionMonitoring systemEmbedded system
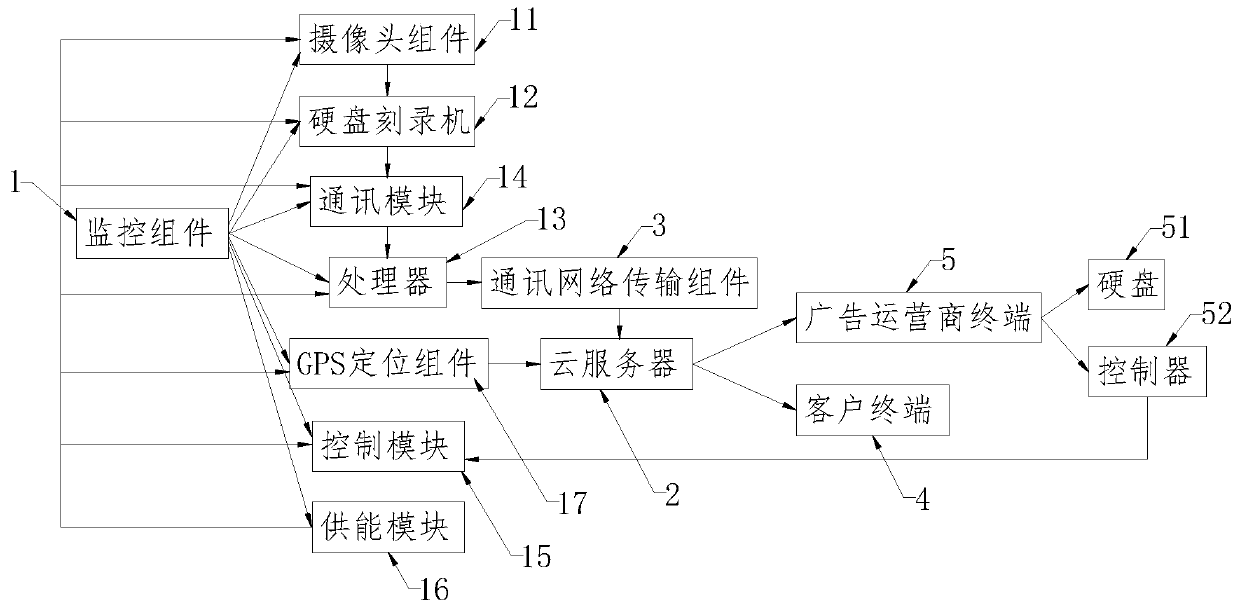
The invention discloses an urban intelligent electronic billboard monitoring system. The system comprises a monitoring assembly, a cloud server, a communication network transmission assembly, a clientterminal and an advertisement operator terminal. The monitoring assembly is installed on a supporting rod of the urban intelligent electronic billboard, is connected with an urban intelligent electronic billboard, is used for monitoring the advertisement state on an urban intelligent billboard, and transmitting advertisement state videos to the cloud server in real time through the communicationnetwork transmission assembly, and the cloud server processes each piece of advertisement state video information and sends the corresponding video information to the client terminal and the advertisement operator terminal for the client and the advertisement operator to check; according to the invention, an advertisement operator and a client can monitor the playing content of the billboard at the same time, so that the accuracy and non-replicability of information are ensured, disputes are avoided, the purpose of effectively improving the working efficiency is achieved, and the advantages ofreducing the labor pressure and reducing the enterprise operation cost are achieved.
Owner:安徽金誉堂文化产业发展有限公司
Elevator Electronic Label and Elevator Information Inquiry System
ActiveCN106934430BUniqueness guaranteedGuaranteed non-reproducibilityCo-operative working arrangementsDigital data protectionTerminal equipmentEmbedded system
The invention discloses an elevator-used electronic label, which comprises a first power supply module, a processing module and a Bluetooth module, wherein the processing module is electrically connected with the first power supply module and the Bluetooth module; the first power supply module is also electrically connected with the Bluetooth module; the first power supply module provides working voltage for the processing module and the Bluetooth module; the processing module is used for regularly reading a pre-stored primitive elevator registration code and an encryption rule, corresponding elevator transmission information is generated according to the read primitive elevator registration code and the encryption rule, the generated elevator transmission information is provided for the Bluetooth module, and the elevator transmission information comprises readable information and encryption information; and the Bluetooth module is used for regularly transmitting the received elevator transmission information in a broadcast form according to an ibencon protocol, and thus, the information can be received by a mobile phone of an elevator passenger, and an elevator maintenance person can arrive at the elevator field and uses a maintenance handheld terminal device to receive the information to acquire the elevator registration code. The invention also provides an elevator information query system.
Owner:宁夏电通物联网科技股份有限公司
Copyright protection method and system for downloading data by portable terminal
InactiveCN101340653BGuaranteed non-reproducibilityReduce data encryption burdenProgram/content distribution protectionSecuring communicationOccupancy rateData information
Owner:四川长城软件科技股份有限公司
An electronic lock system and its control method
ActiveCN105554035BImprove securityEnsure safetyIndividual entry/exit registersTransmissionComputer hardwareComputer science
The invention provides an electronic lock system and a control method thereof. The electronic lock system comprises a lockset and an electronic key in communication connection with the lockset; the electronic lock system is characterized in that a first data processing device is installed in the electronic key; a first digital certificate is stored in the first data processing device; and a second data processing device is installed in the lockset, wherein the second data processing device is configured to be capable of communicating with the first data processing device so as to verify the first digital certificate and store the first digital certificate, send authentication data to the first data processing device when the lockset receives an unlocking request of the electronic key every time, authenticate response data returned by the first data processing device by utilizing the stored first digital certificate, and allow to open the lockset when authentication is passed. The electronic lock system disclosed by the invention has the characteristics of being high in security and more intelligent.
Owner:HIHALOCK BEIJING TECH CO LTD
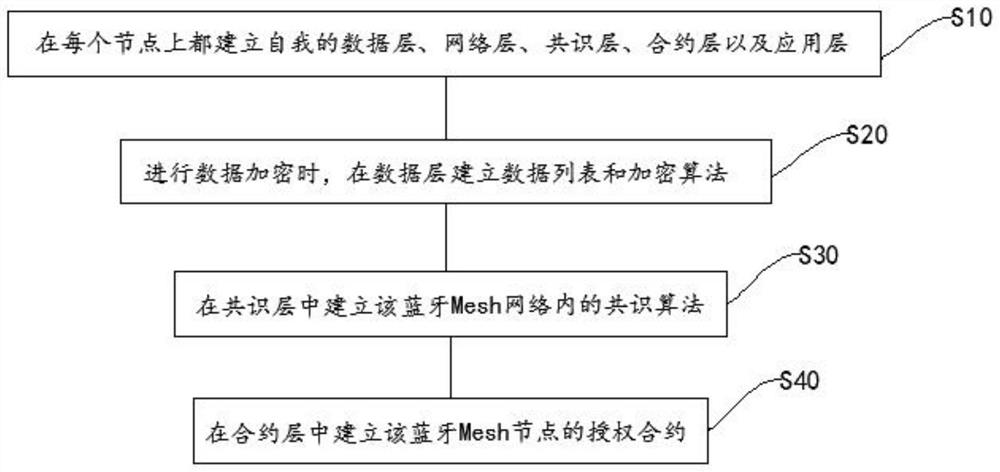
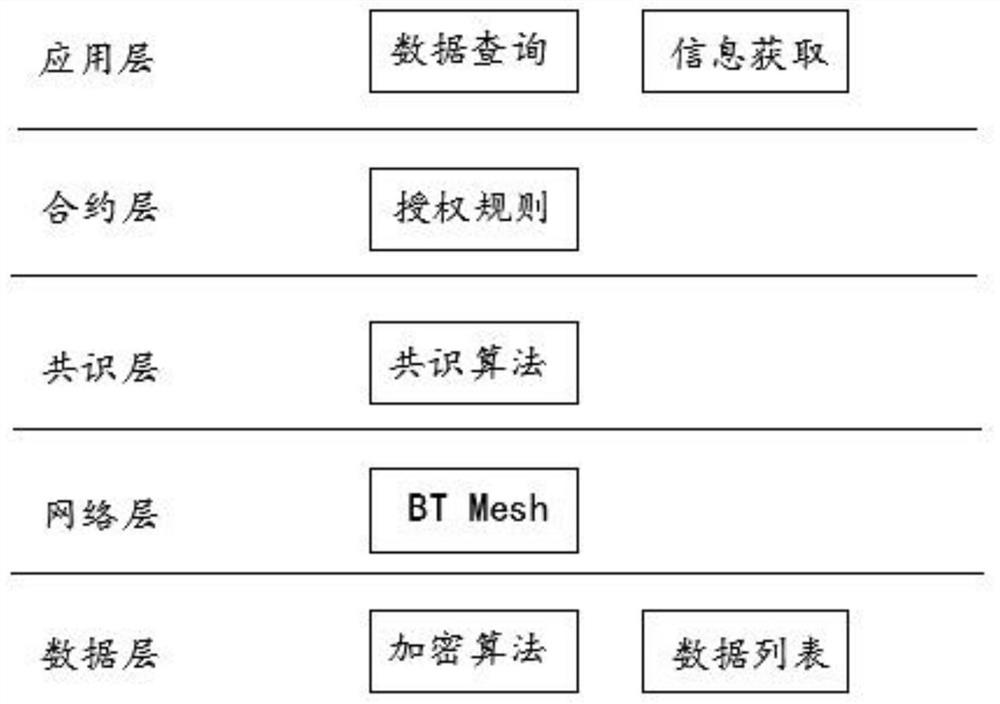
A Bluetooth mesh distributed blockchain data authorization encryption method
ActiveCN109413027BGuaranteed reliabilityGuaranteed non-reproducibilityUser identity/authority verificationShort range communication serviceEngineeringMesh node
The invention discloses a Bluetooth Mesh-based distributed block chain data authorization encryption method, which comprises the following steps: establishing its own data layer, network layer, consensus layer, contract layer and application layer on each node; performing data encryption At the same time, the data list and encryption algorithm are established in the data layer; the consensus algorithm in the Bluetooth Mesh network is established in the consensus layer; the authorization contract of the Bluetooth Mesh node is established in the contract layer to determine that each new node is newly added to the network. Or the information contract rules when exiting the network, the entire network of the present invention uses distributed encryption to complete the decentralization of the network, a block chain structure with high security and stability, and ensures the security of data in the entire network. Reliability and non-reproducibility. Bluetooth Mesh is currently mostly used in smart homes and smart cities. Using distributed authorization and encryption can ensure the non-reproducibility of each node and provide a unified platform for information traceability.
Owner:SHANGHAI MASHI INFORMATION TECH CO LTD
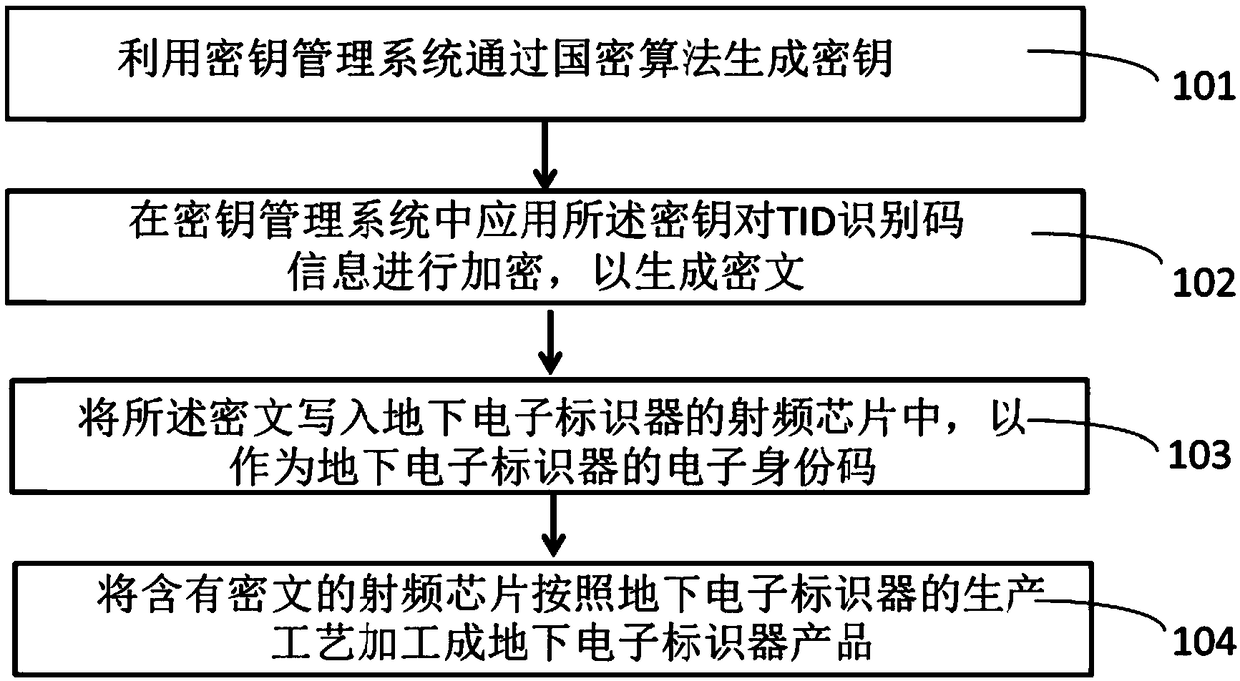
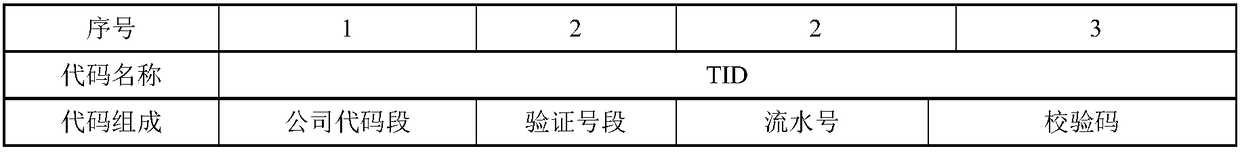
Method and product for using ciphertext as electronic identity code of electronic marker
InactiveCN108900297ALong-term existenceNot lostKey distribution for secure communicationRecord carriers used with machinesElectronic identificationCiphertext
The invention discloses a method and product for using ciphertext as electronic identity code of an electronic marker. The method comprises the following steps of generating a secret key through a state secret algorithm by using a key management system; using the key to encrypt the TID recognition code information in the key management system so as to generate ciphertext; writing the ciphertext into a radio frequency chip of the underground electronic marker to be used as the electronic identity code of the underground electronic marker; processing the underground electronic marker product byusing the radio frequency chip containing the ciphertext according to the production process of the underground electronic marker. The method and product by using the ciphertext as the electronic identity code of the underground electronic marker have the advantages that the safety of the underground electronic marker product can be obviously enhanced; the potential pipeline data file and pipelinepractical position leakage risk of the underground electronic marker product in the practical application can be eliminated to the great degree.
Owner:BEIJING SMARTCHIP MICROELECTRONICS TECH COMPANY +1
A System Based on Identity Authentication Server and Identity Authentication Token
ActiveCN108092776BUniqueness guaranteedGuaranteed non-reproducibilityUser identity/authority verificationEngineeringAuthentication server
The invention discloses an identity authentication server and an identity authentication token, wherein the identity authentication server comprises a standard FIDO server and a storage space for storing keys, namely, a database, which are connected with each other; the identity authentication token is based on physical unclonable and the FIDO U2F protocol and comprises a U2F module, and a PUF module,a TRNG module, a USB module and an interaction module, which are connected with the U2F module, and a touch module connected with the interaction module; and an identity token interacts with a client browser, and the client browser in turn interacts with an FIDO server in the authentication server. According to the identity authentication server disclosed by the invention, the physical unclonable function is combined with the FIDO, the uniqueness and non-replicability of the token are ensured by the physical unclonable function, and the accuracy of the user identity and the non-defective modification and non-repudiation of the operation are ensured by the FIDO.
Owner:NARI INFORMATION & COMM TECH
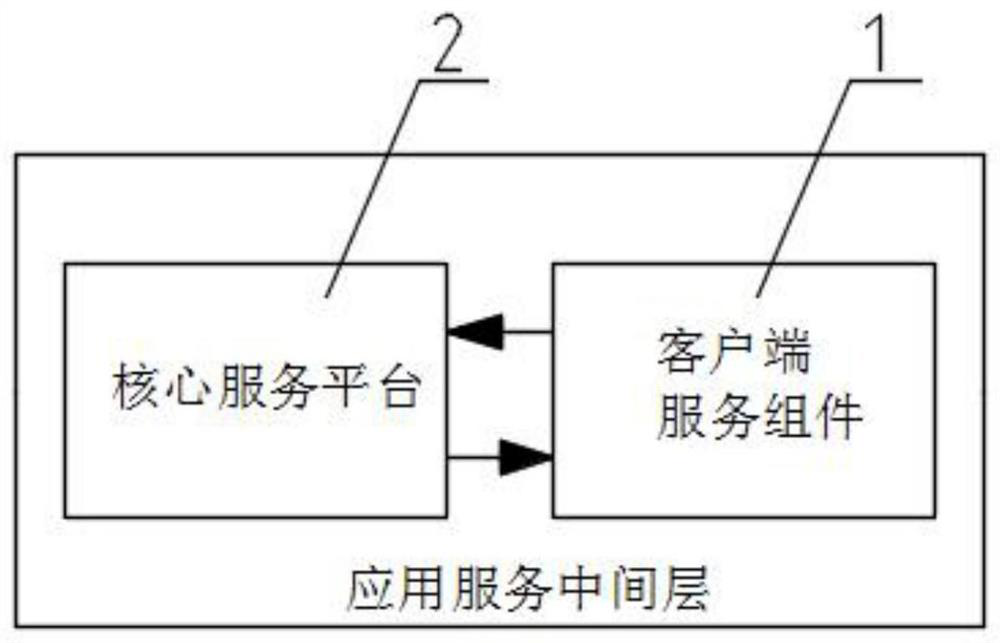
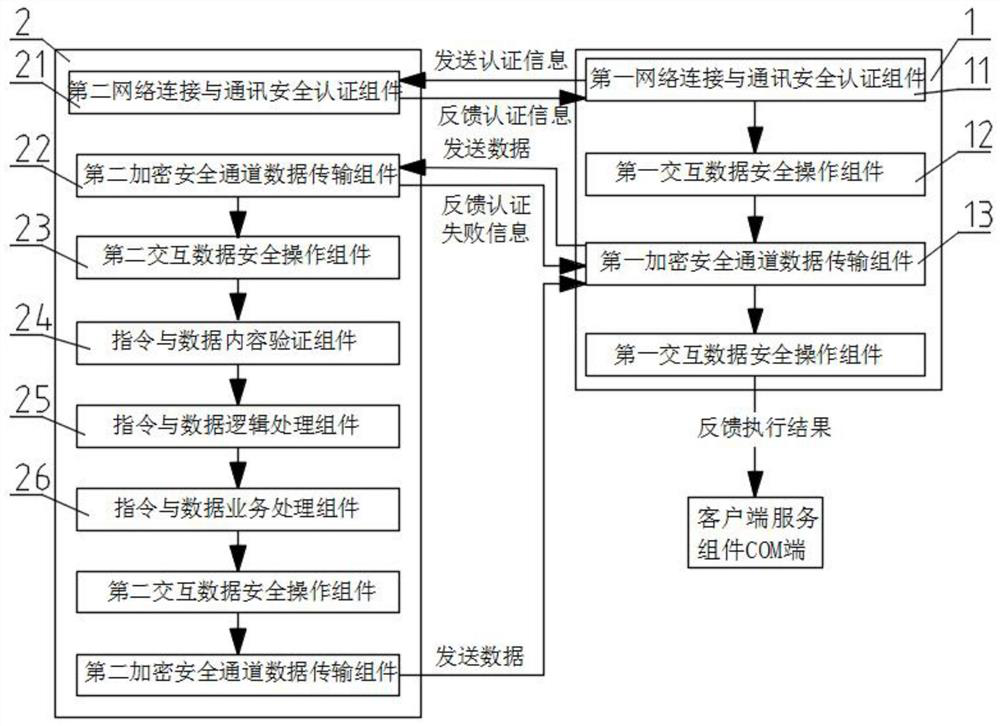
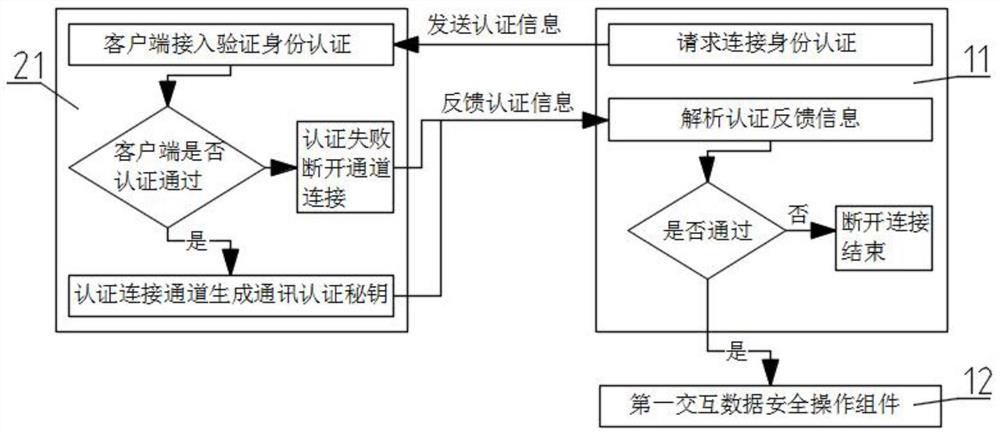
A method and system for security management and control of an application service-based core framework platform
The present invention relates to a method and system for security management and control of a core framework platform based on application services, including an application service middle layer, the application service middle layer includes a client service component and a core service platform, and the system uses the client service component and the core service The platform performs information interaction, and the core service platform obtains operation instructions according to the instructions received by the client service components and the corresponding relationship with the client service components, and parses the feedback data to the client service components, and the client service components transfer the core service platform The execution result of the feedback is sent to the COM terminal of the client service component; the beneficial effect of the present invention is to ensure the safe access of the platform, the security of data and instruction transmission, and the accuracy of the content, and the timeliness and single-point Use management to ensure data security performance; use the supporting multi-level secret key algorithm to generate a decryption key and decrypt the data content to ensure the security and non-reproducibility of the data content.
Owner:武汉蓝星软件技术有限公司
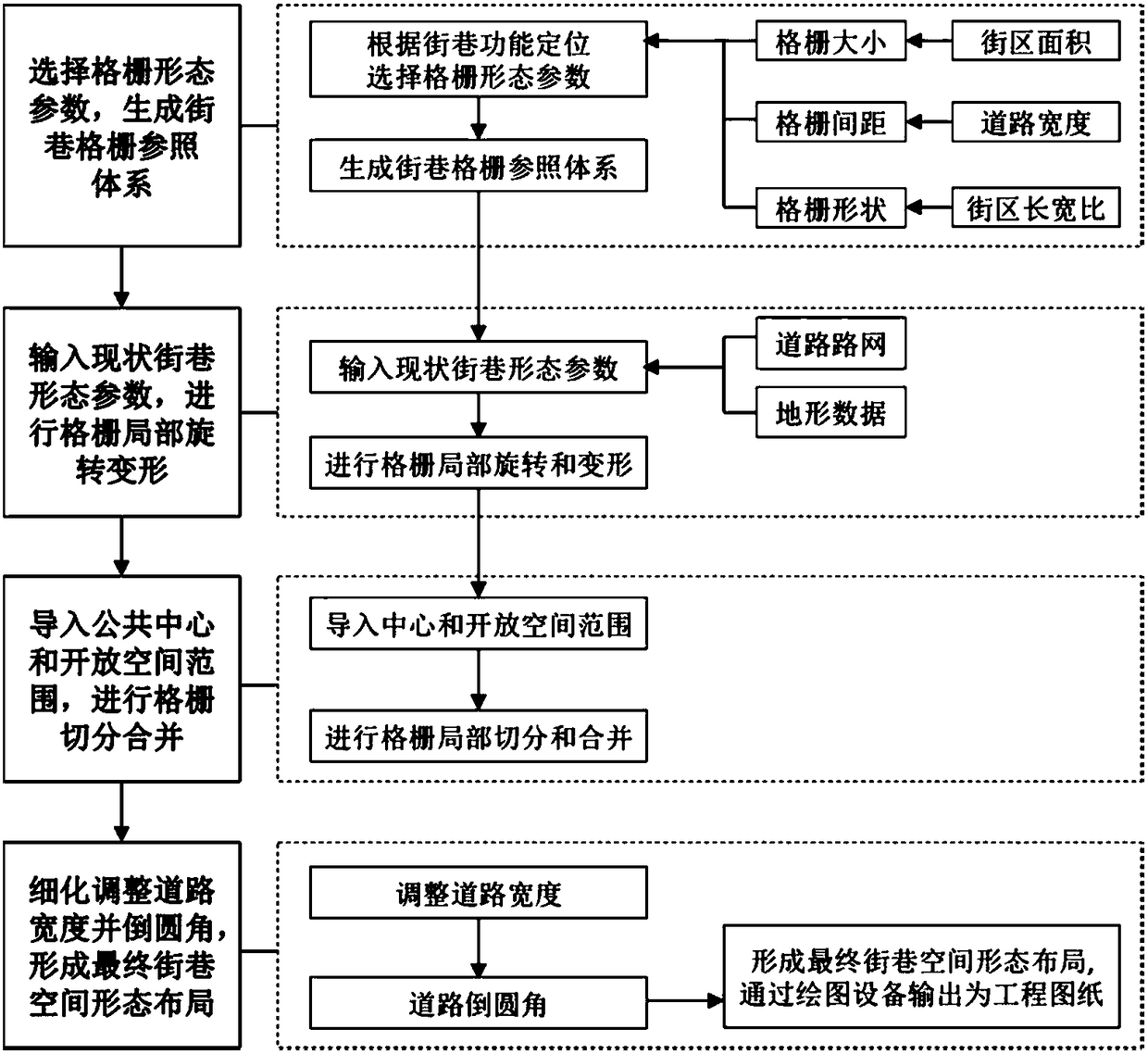
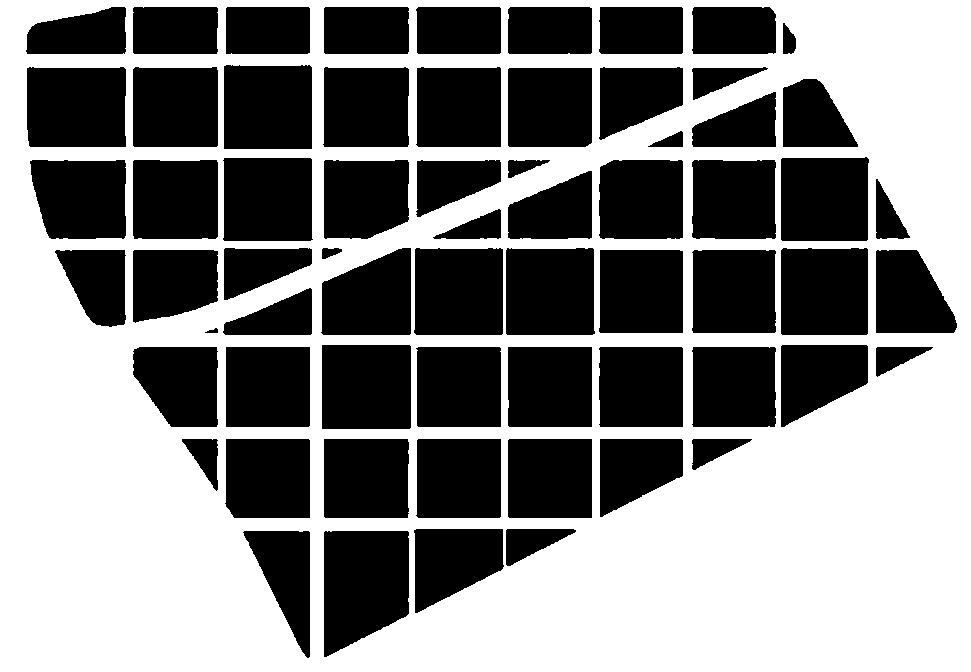
A method of spatial shape layout of streets and alleys based on grid selection
ActiveCN105894553BAchieve orderEasy to moveDrawing from basic elementsData processing applicationsGrid referenceSimulation
The invention discloses a street spatial form layout method based on grid selection. The street spatial form layout method includes the steps of generating a street grid reference system on basis of set grid form parameters; extracting present spatial form data from a vector diagram of a current street, superimposing the data onto the grid reference system, and conducting grid local rotation and deformation on the reference system according to the present form; setting a public center and an open space range, and conducting grid segmenting and merging; and conducting fine adjustment of the road width and form to form a final street spatial form layout. The invention achieves the overall logic and order of the spatial form layout through grid selection, and the operating method has the portability and is suitable for a variety of urban street layout design; and the invention has the advantages of flexible design, less time consumption, high efficiency, uniqueness and unduplicatedness of generated results, and so forth, and has a practical application value for planning engineering practice.
Owner:SOUTHEAST UNIV
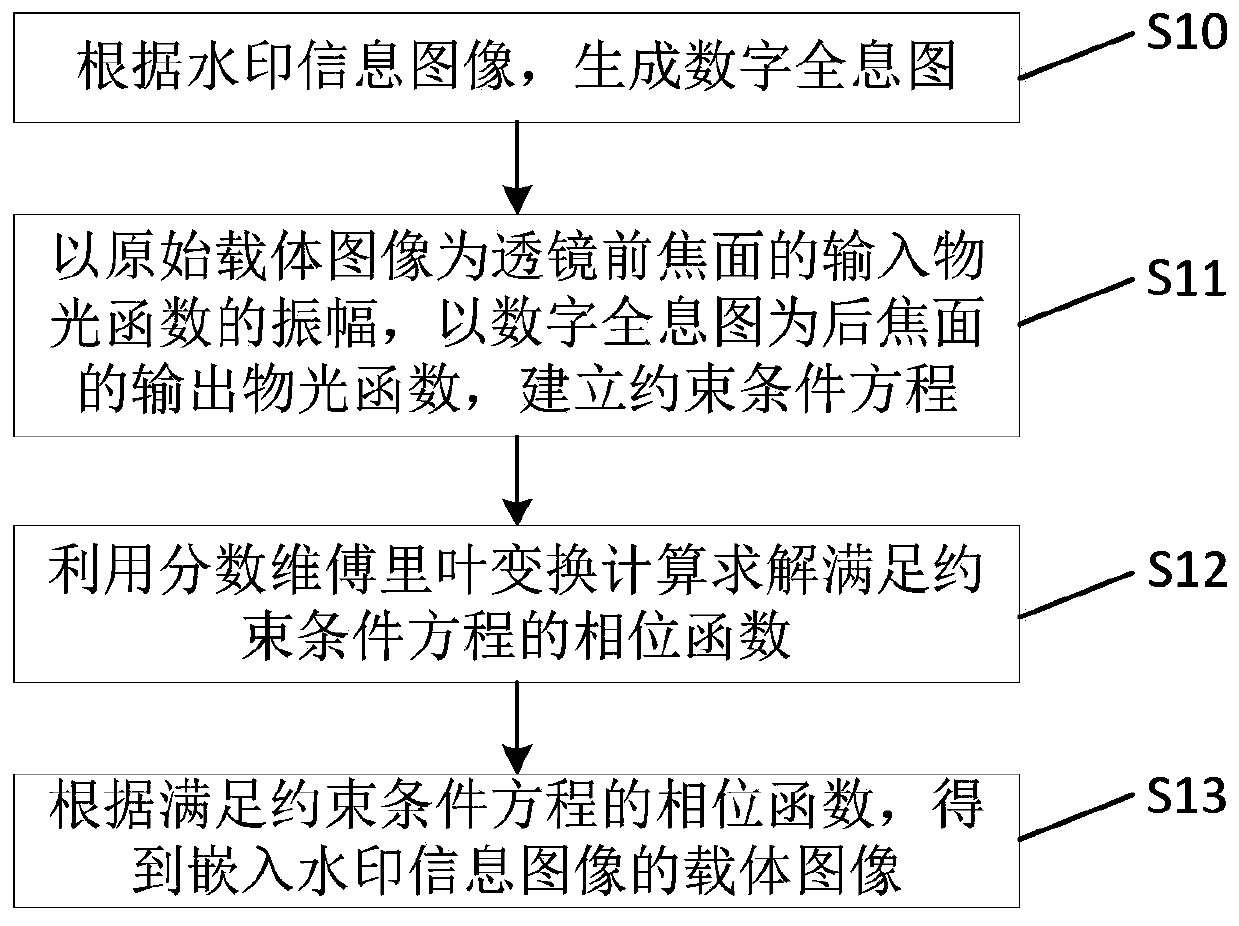
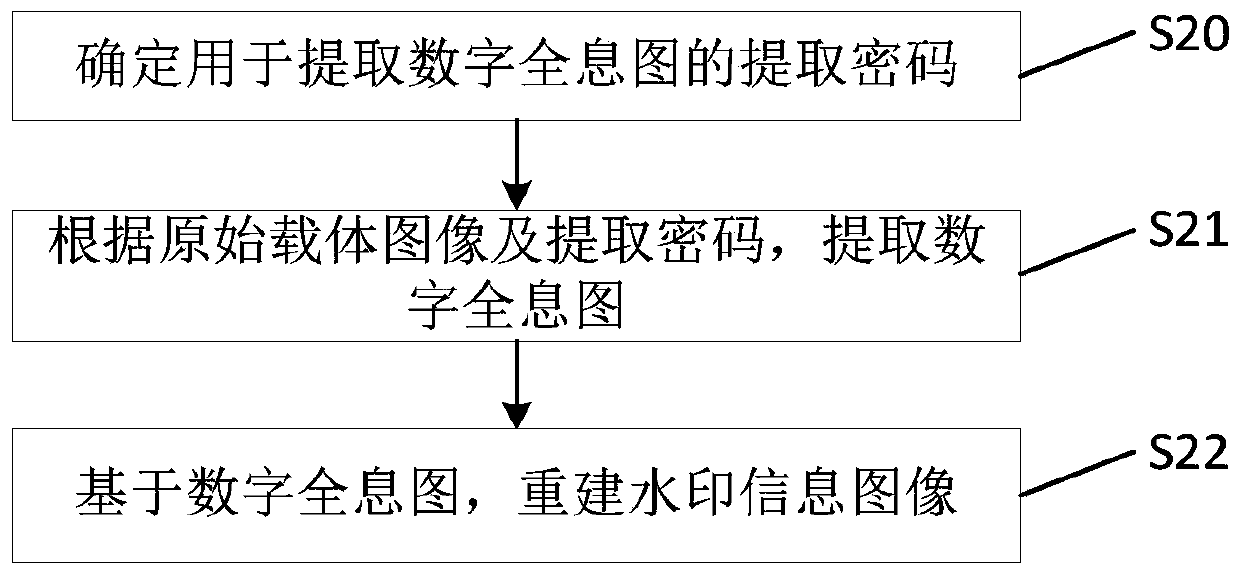
A digital watermark authentication method and device
ActiveCN109840874AStrong anti-printing characteristicsImplement multiple encryptionImage data processing detailsPictoral communicationPasswordPhase function
The invention discloses a digital watermark authentication method and device, and the method comprises the steps: generating a carrier image in which a watermark information image is embedded, and generating a digital hologram according to the watermark information image; Taking the original carrier image as the amplitude of an input object light function of the front focal plane of the lens; using a digital hologram as an output object light function of the rear focal plane; establishing a constraint condition equation comprising the original carrier image, the digital hologram and the phasefunction, calculating and solving the phase function satisfying the constraint condition equation by utilizing fractional Fourier transform, and obtaining the carrier image embedded with the watermarkinformation image according to the phase function satisfying the constraint condition equation; And determining an extraction password for extracting the digital hologram, extracting the digital hologram according to the original carrier image and the extraction password, and reconstructing a watermark information image based on the digital hologram. The invention provides a digital watermark authentication method and device with good anti-printing performance.
Owner:BEIJING INSTITUTE OF GRAPHIC COMMUNICATION
Method and system for preventing counterfeit by using differentiation of electromagnetic signals of RFID
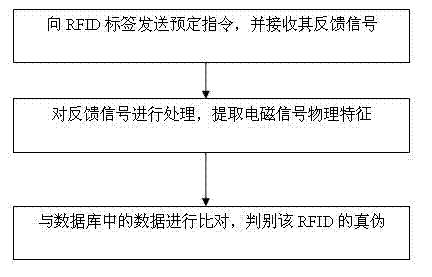
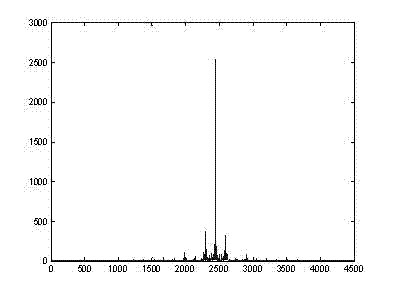
ActiveCN102073838BGuaranteed non-reproducibilityDigital computer detailsCharacter and pattern recognitionElectromagnetic shieldingRadio frequency
The invention discloses a method and a system for preventing counterfeit by using differentiation of electromagnetic signals of radio frequency identification (RFID). The method comprises the following steps of: sending an instruction to an RFID radio frequency tag to be identified, and receiving a signal fed back by the RFID radio frequency tag; performing electromagnetic signal physical property recognition on the received signal to obtain recognition characteristics; and performing matrix recognition on comparison parameters and records in a database to judge the truth and falsehood of theRFID. In the method and the system for preventing counterfeit by using the differentiation of the electromagnetic signals of the RFID, the characteristics of substances in the RFID radio frequency tag are used, namely different RFID antenna modules and integrated circuit (IC) chips have different physical properties, and differentiation of physical properties of electromagnetic signals exists between two RFID radio frequency tags with the same property, so that different RFID radio frequency tags are differentiated by measuring the differentiation, and unduplicatedness of the RFID radio frequency tags is guaranteed.
Owner:SHENZHEN SINOSUN TECH
Website security detection method and device
ActiveCN105515882BUniqueness guaranteedGuaranteed non-reproducibilityData switching networksWeb siteIp address
The invention provides a website security detection method and a website security detection device. The method comprises the following steps: acquiring a server Internet Protocol IP address list of a website, wherein each server has an IP address, and the IP addresses of different servers are different; and performing security detection of the website based on the server IP address list. By using the website security detection method in the embodiment of the invention, security detection of websites can be performed more efficiently and reasonably, and the efficiency of website security detection can be improved.
Owner:BEIJING QIANXIN TECH
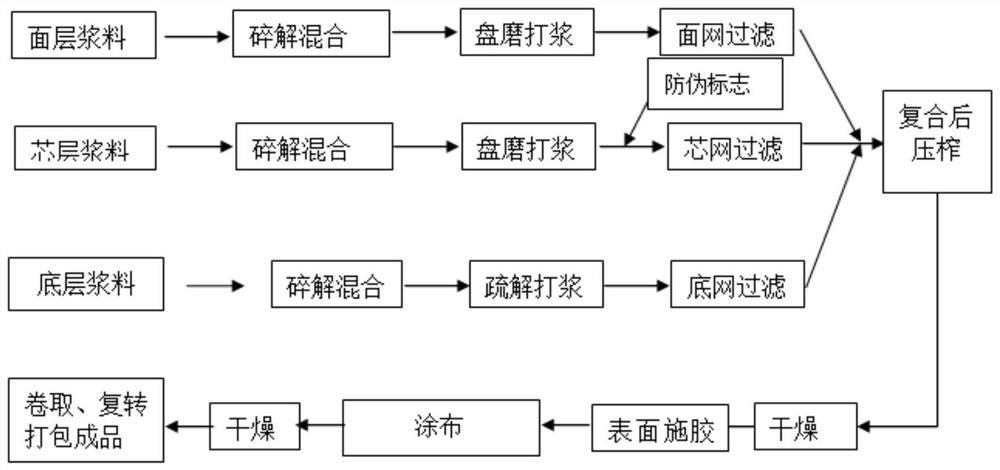
A preparation method of three-dimensional anti-counterfeiting white cardboard
ActiveCN109653021BGuaranteed non-reproducibilityReduce uncontrollabilityPaper/cardboardColorants/pigments additionCardboardIndustrial engineering
The invention provides a preparation method of three-dimensional anti-counterfeiting paper. Firstly, the surface paper layer slurry, the core paper layer slurry and the surface paper layer slurry are respectively prepared, the anti-counterfeiting mark is loaded on the carrier to obtain the anti-counterfeiting layer, and the anti-counterfeiting layer is Add it to the core paper layer slurry, and then compound the core paper layer slurry with the surface paper layer slurry and the surface paper layer slurry. After the paper sheet is formed, it will be pressed and dried for the first time. After drying for the second time, it is coiled and packaged to obtain three-dimensional anti-counterfeiting paper, and the carrier is glutinous rice paper. The invention adopts biomass-degradable glutinous rice paper as a carrier, and arranges the anti-counterfeiting marks in three-dimensional and irregular arrangement on the paper by adjusting the melting speed and temperature, so as to ensure the anti-counterfeiting technology without affecting each physical index of the paper. The non-reproducibility of anti-counterfeiting reduces the cost of anti-counterfeiting and the uncontrollability of anti-counterfeiting marks. It does not require modification of equipment or special treatment of slurry, and will not affect the physical properties and printing adaptability of the paper.
Owner:ZHUHAI HUAFENG PAPER
Goods tracing anti-counterfeiting coding method
ActiveCN101980186BEnsure safetyUniqueness guaranteedRecord carriers used with machinesSpecial data processing applicationsTheoretical computer scienceEngineering
The invention discloses a goods tracing anti-counterfeiting coding method and solves the technical problems of simple coding method of goods, and large amount of operation. The technical scheme adopted by the invention is that: the method is implemented in a database of a network server by using a computer and a matched software management procedure. The anti-counterfeiting coding method comprises the following steps of: classifying and numbering global goods and storing the numbers in the database of the network server; encrypting the classified numbers and generating check codes first by using a computer memory and the matched encrypt algorithm on the basis of the standard data encrypt algorithm; and encrypting the check codes and finally generating ASII code characters of 16 digits, writing in the radio frequency identification or preparing bar codes, pasting on products and storing in the database of the network server. The anti-counterfeiting coding method has the advantages that: the security, uniqueness and non-replicability of data are guaranteed by adopting the double-encryption manner of encrypting classified numbers and generating check codes and encrypting the check codes again and the deciphering difficulty is increased.
Owner:SHENZHEN JAVS TECH
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com