Dynamic encrypting method realizing one secrete key for one file
A dynamic encryption and key technology, applied in key distribution, can solve the problems of increasing encryption complexity, increasing key length, and taking less time to achieve the effect of increasing encryption complexity, fast encryption and fast speed.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
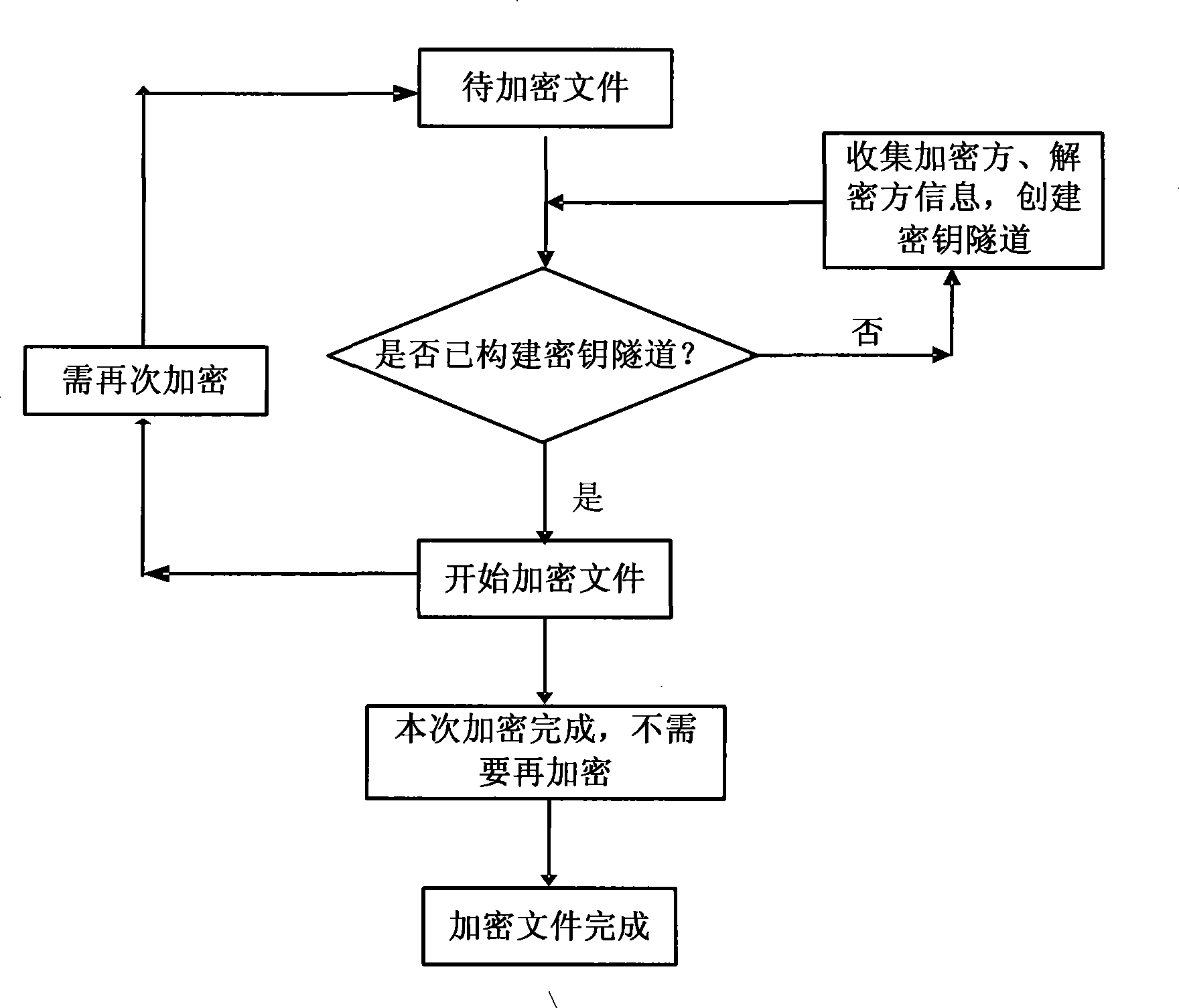
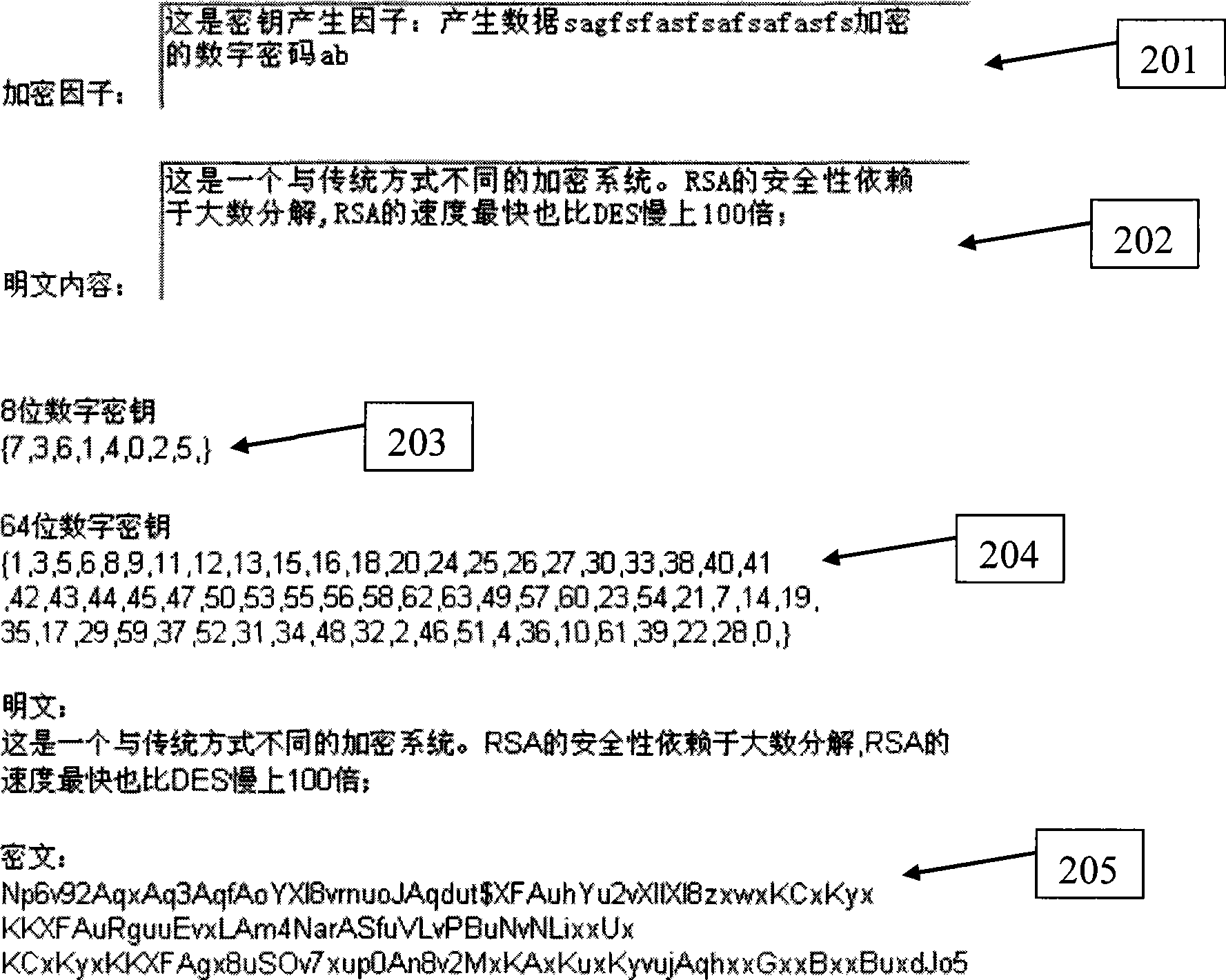
[0026] This one-text-one-cipher dynamic encryption method can be realized by computer software, computer hardware, or a combination of computer software and hardware. combined process box figure 1 and concrete examples figure 2 , explained below.
[0027] This invention cites a Chinese patent titled "Method for Extracting Characteristic Values of Fixed-Length Spatial Positions from Information", which was applied for by the inventor Zhao Wenyin on February 1, 2008, and the patent application number is 200810057400.0. This method describes Concrete steps for extracting spatial location from textual information.
[0028] On the encryption side, the flowchart is as follows figure 1 shown. At the beginning of the process, the files to be encrypted are specified by the user. figure 1 Other steps in are carried out automatically by the computer system according to the present invention.
[0029] 1) Select any file that needs to be encrypted.
[0030] 2) Connect the encrypt...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com