Encryption and decryption methods for file transfers
A file transfer and file technology, applied in the field of file transfer encryption and decryption, can solve the hidden dangers of file security, not applicable to ordinary enterprises, cracking encrypted files, etc., to increase encryption security, strengthen unbreakability, and increase decryption. effect of difficulty
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0029] The method of the present invention will be further described in detail below in conjunction with the accompanying drawings and specific embodiments.
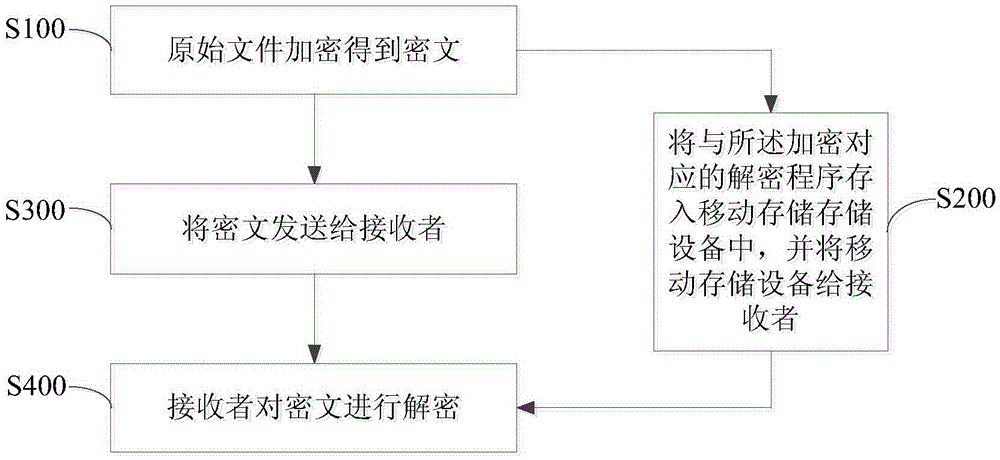
[0030] Such as figure 1 As shown, the encryption and decryption method for file transfer includes the following steps:
[0031] Step S100, encrypt the original file D to obtain ciphertext.
[0032] The encryption method of this embodiment is as follows: figure 2 As shown, it specifically includes the following steps:
[0033] S101. Use a random function to generate a sequence as the version number A of the original file D, and establish a corresponding relationship between the version number A and the original file D and store it in a local encryption computer.
[0034] S102. Encrypt the version number A with MD5 to obtain the version number ciphertext B. In this embodiment, the hash function is used to perform MD5 encryption for illustration.
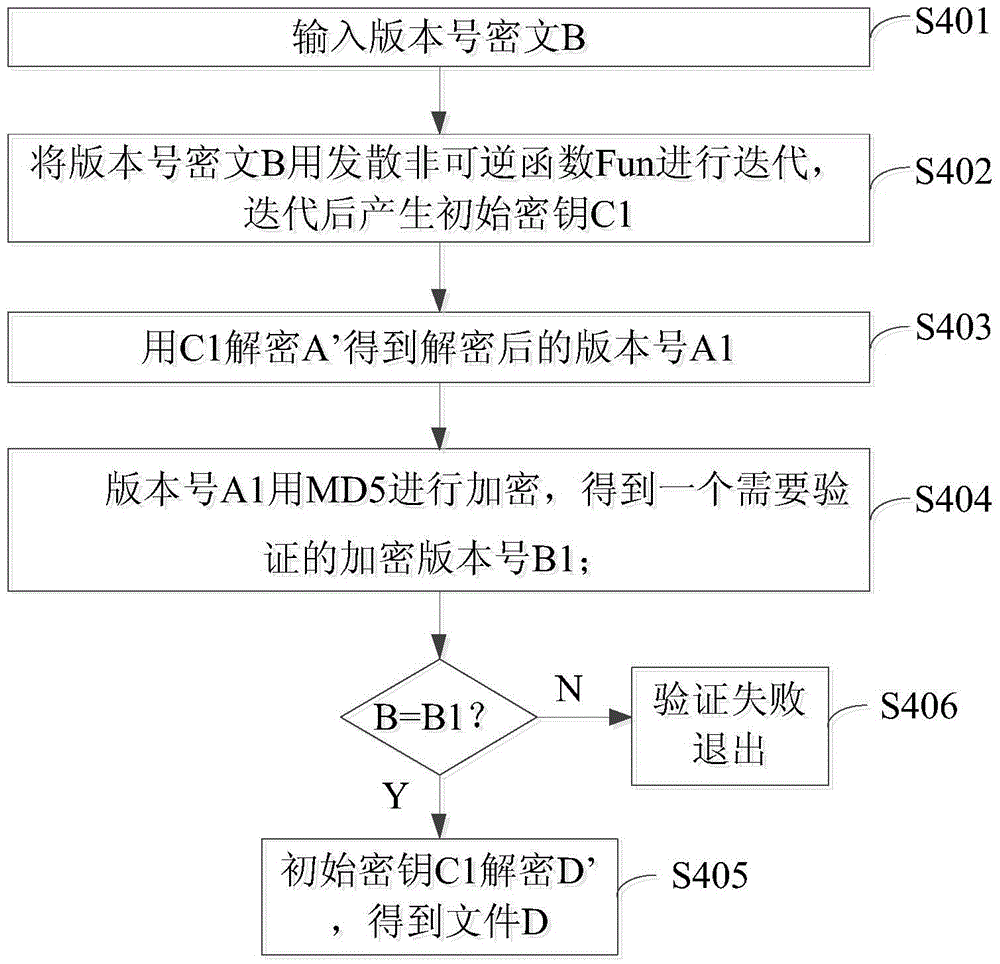
[0035] S103. Iterate the version number ciphertext B by using the diver...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com