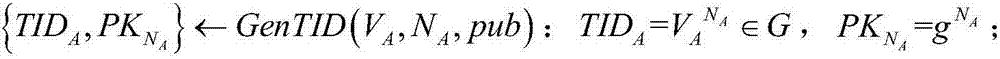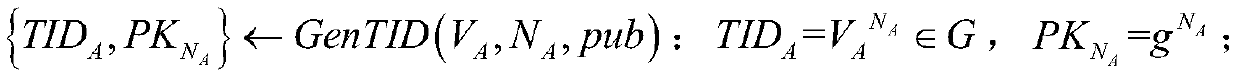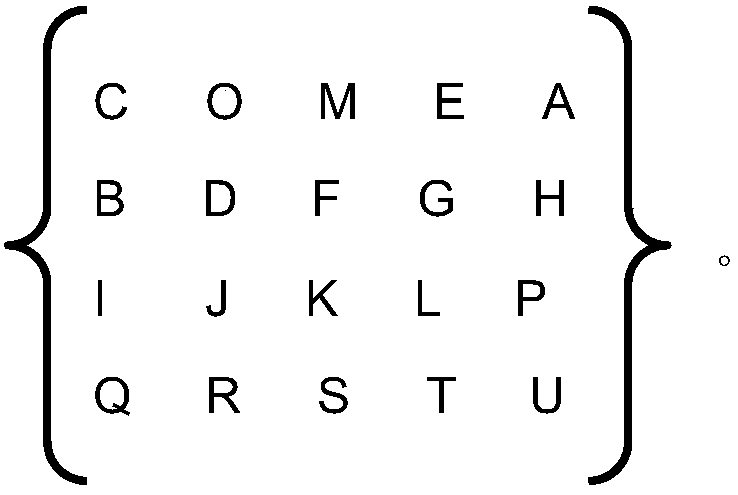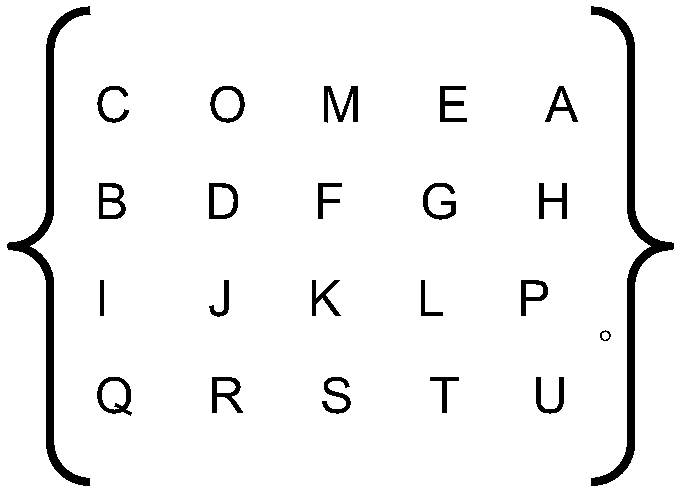Patents
Literature
33results about How to "Encryption guaranteed" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Algorithm for encrypting image on basis of chaotic mapping and series changing
InactiveCN102915519AEncryption guaranteedImage data processing detailsSelective content distributionStatistical analysisComputer science
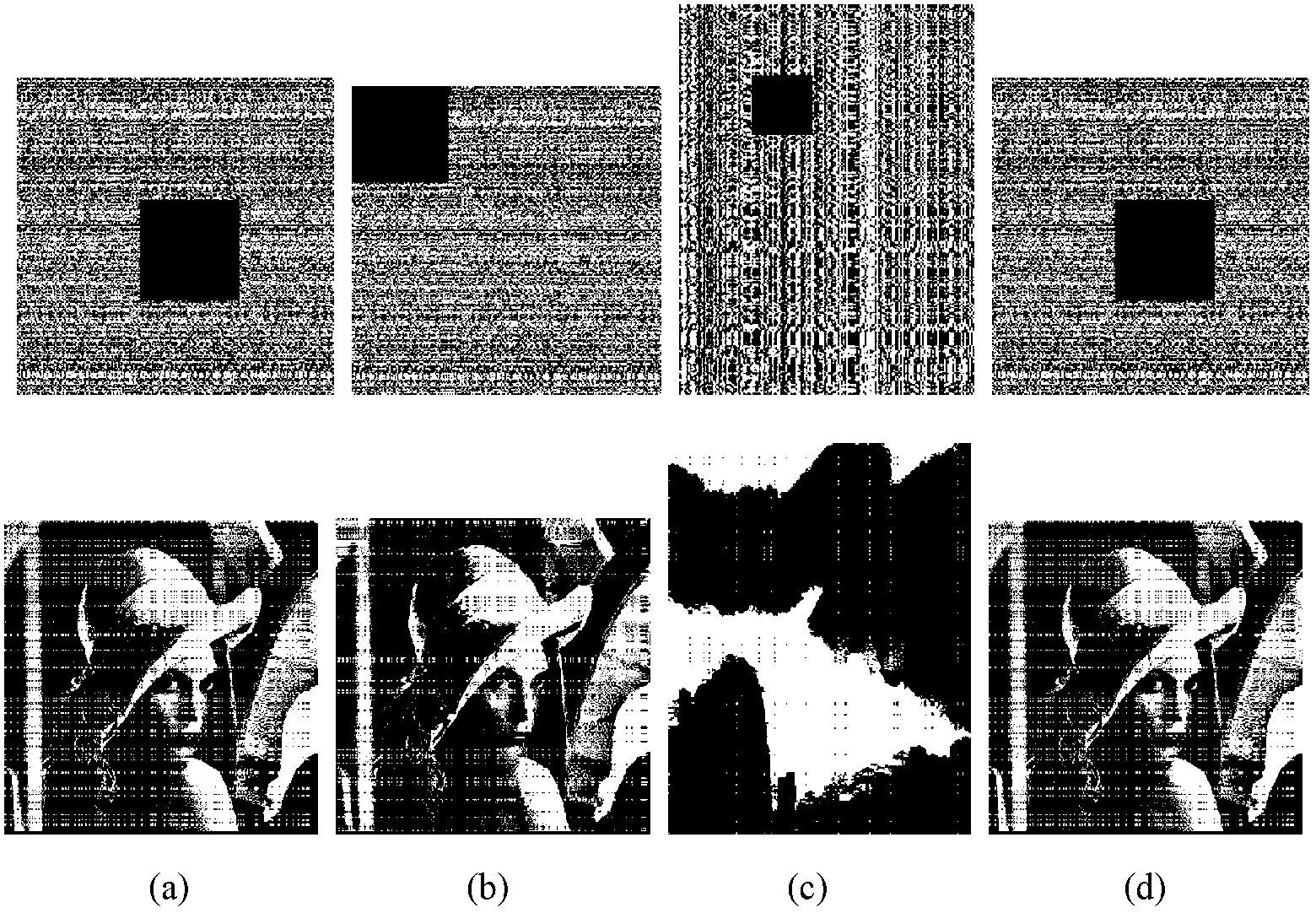
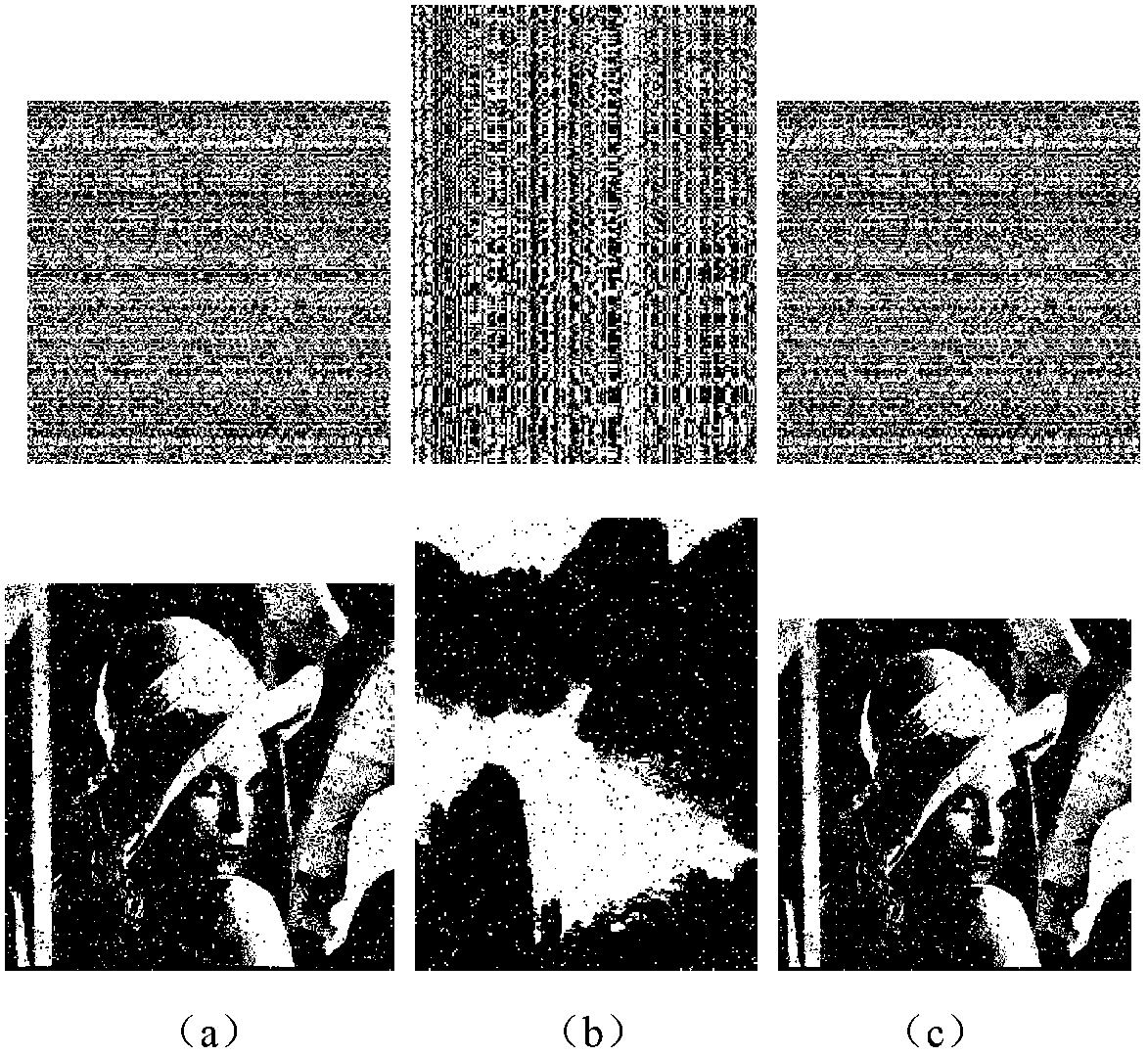
An algorithm for encrypting an image on the basis of chaotic mapping and series changing comprises the following steps that: the pixel value of an image and a two-dimensional matrix which has the same size with the image and is formed by a Logistic chaotic sequence are subjected to binary bitwise XOR processing; the Logistic chaotic sequence is subjected to the mapping transformation so that two two-dimensional matrixes are formed; a row matrix is multiplied by an image matrix and a line matrix in sequence, so that location chaotic operation is finished; and the original image information cannot be visually sensed from the obtained encrypted image and can be completely hidden. By the method, the encrypted imaged can resist the attack from gray value statistic analysis and general interference attack from shear, noise and gauss lowpass filtering.
Owner:NORTHEAST FORESTRY UNIVERSITY
Data encryption method and system
InactiveCN102567687AEncryption guaranteedGood encryptionDigital data protectionSecuring communicationComputer hardwareData transmission
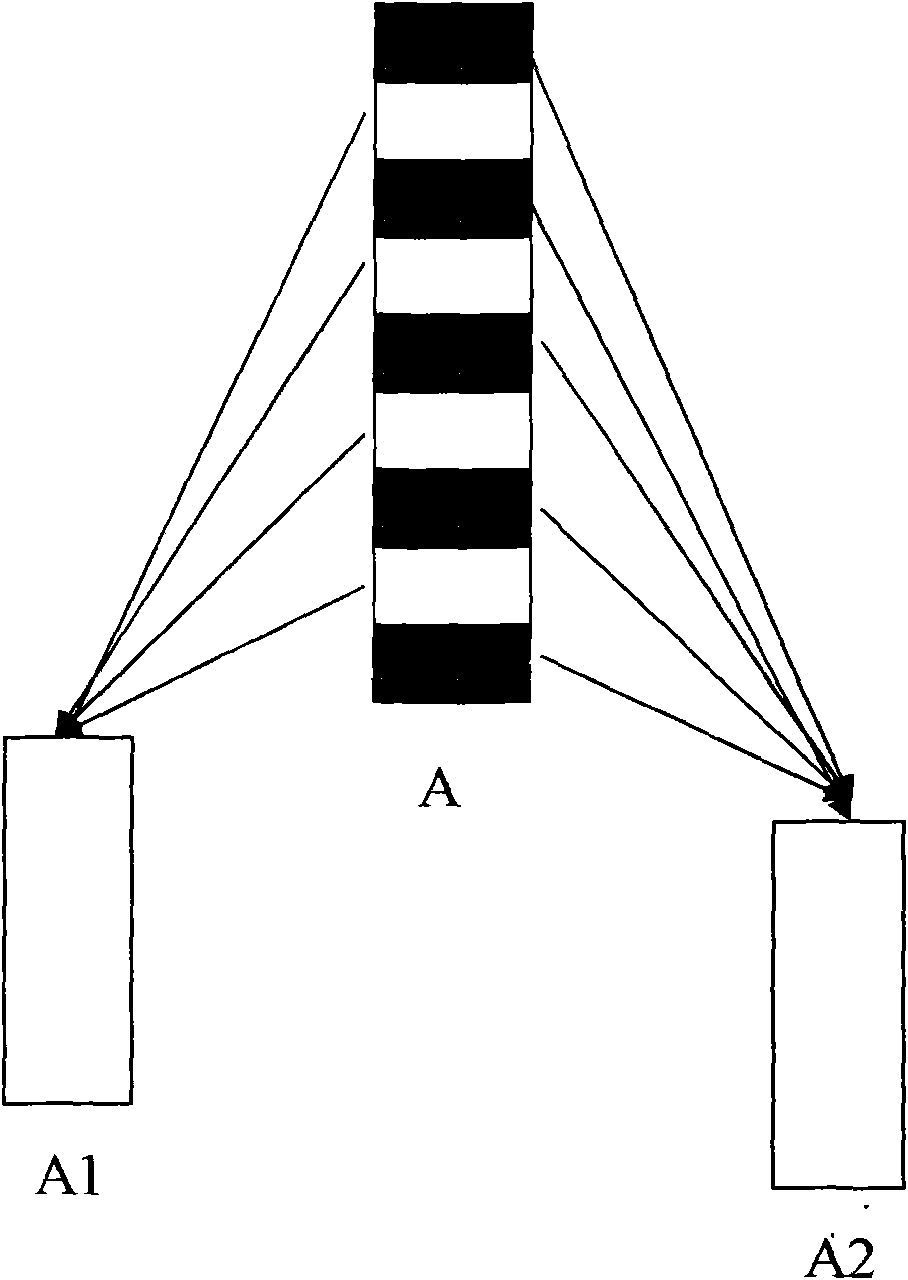
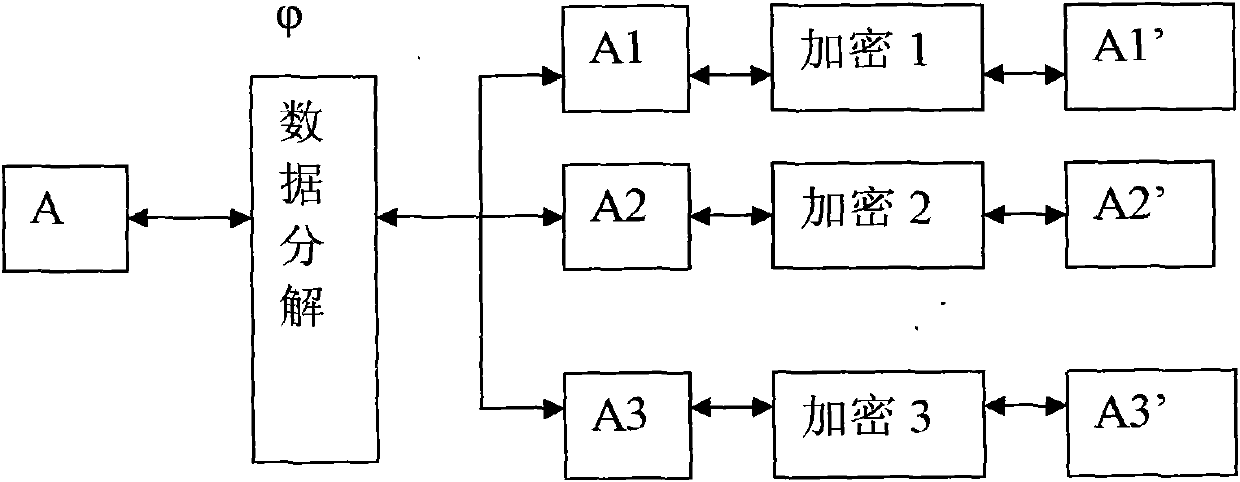
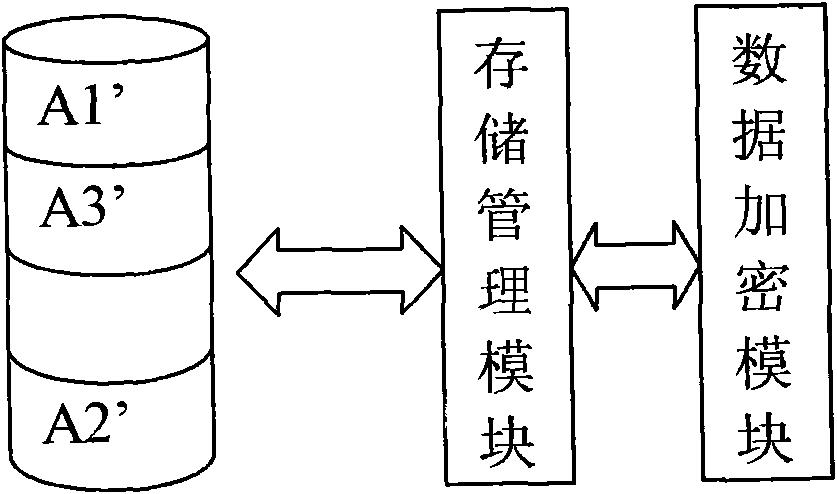
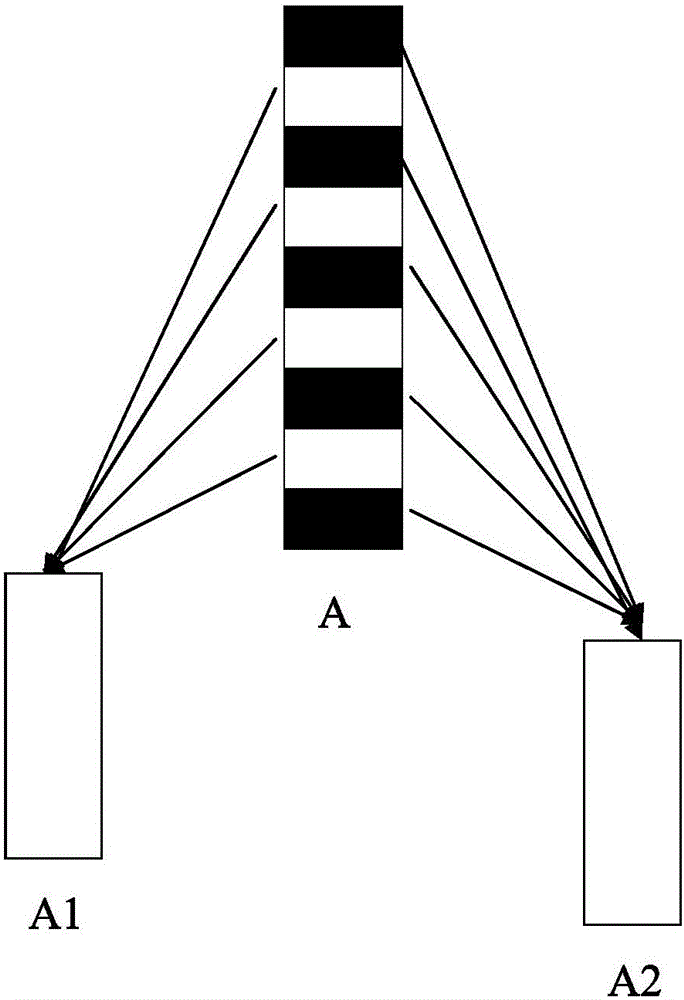
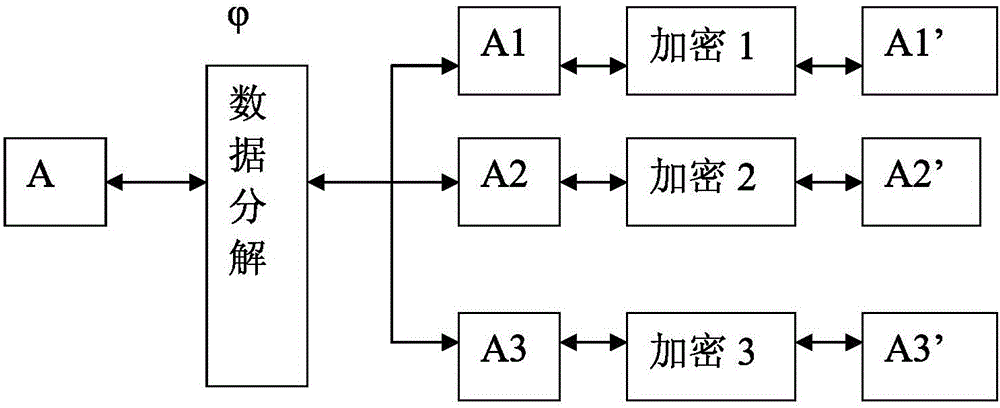
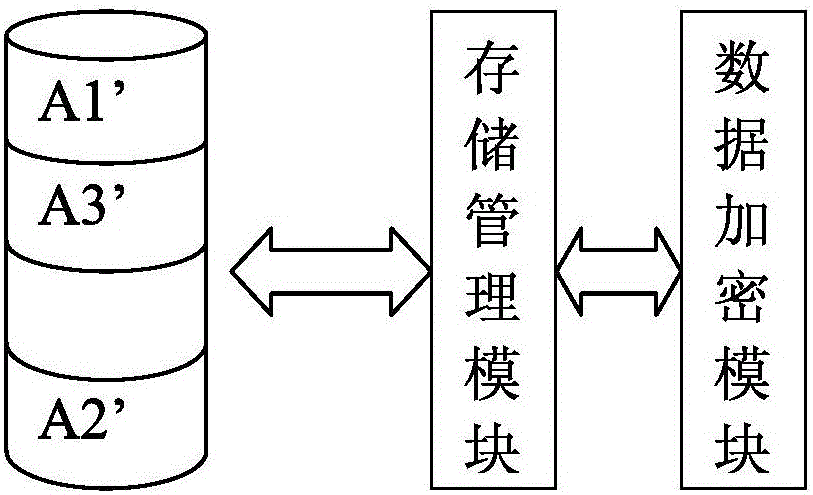
The invention relates to a data encryption method and a system. The data encryption method is characterized in that raw data is decomposed into at least two parts of data according to a preset function relationship. A data encryption storage method is characterized in that the preset function relationship is decomposed into at least parts of data, and the disassembled data is respectively stored in different memories. A data encryption transmission method is characterized in that a sending end decomposes raw data A into at least two parts according to the preset function relationship; the two parts are sent to a data receiving end via different data transmitting channels; and the data receiving end respectively receives the data, and combines and reduces the data into the raw data A according to the corresponding function relationship. As various combination modes are provided, the decryption difficulty is high after encryption, and the original encryption index is enhanced by times to guarantee the encryption effect of numbers. Only disassembly is required, and therefore, good encryption effect is achieved. In addition, the data encryption method has the advantages of low calculation amount and high encryption and decryption efficiency.
Owner:成都科创知识产权研究所
Efficient encryption method and system of data
InactiveCN105809046AEncryption guaranteedGood encryptionDigital data protectionComputer hardwareOriginal data
The invention relates to an efficient encryption method and system of data. The encryption method of the data splits original data into at least two parts of data according to a preset rule, wherein the splitting is that the original data is split according to the preset rule according to a discontinuous way and is spliced again to obtain at least two parts of data. The invention also discloses a corresponding decryption method, an encryption and decryption storage system and the like. Since various combination ways are arranged, decryption difficulty is high after encryption is carried out, an original encryption index is enhanced manifold, and a data encryption effect is guaranteed. In addition, the data only needs to be split, and therefore, a good encryption effect can be performed. In addition, the encryption method is small in operation amount and high in encryption and decryption efficiency.
Owner:成都科创知识产权研究所
Data encrypting method and encrypted data transmitting device
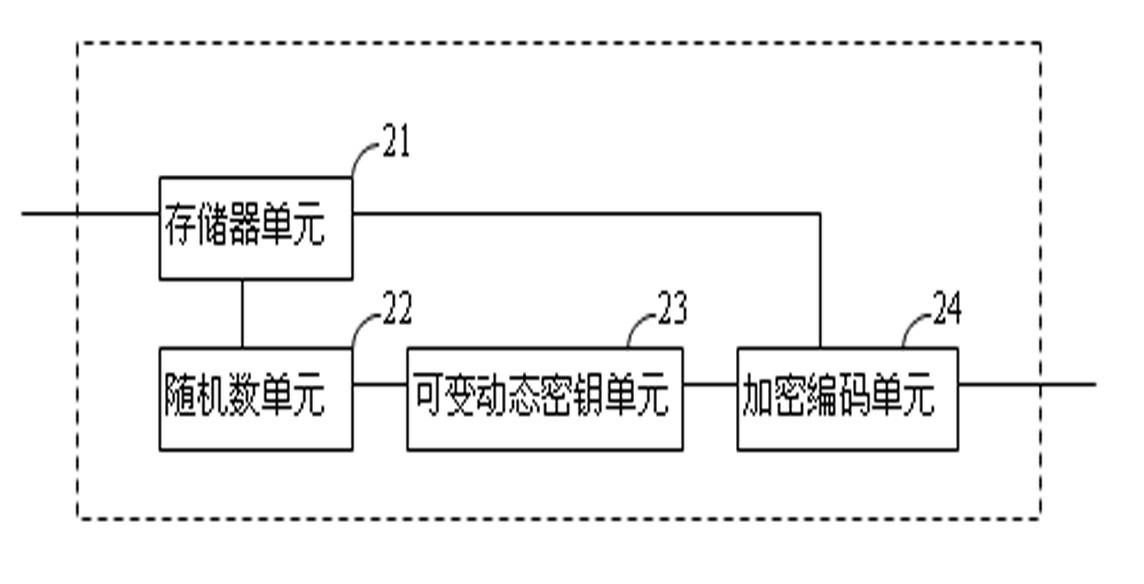
InactiveCN102546185AImprove confidentialityEncryption guaranteedKey distribution for secure communicationUser identity/authority verificationData domainEncryption
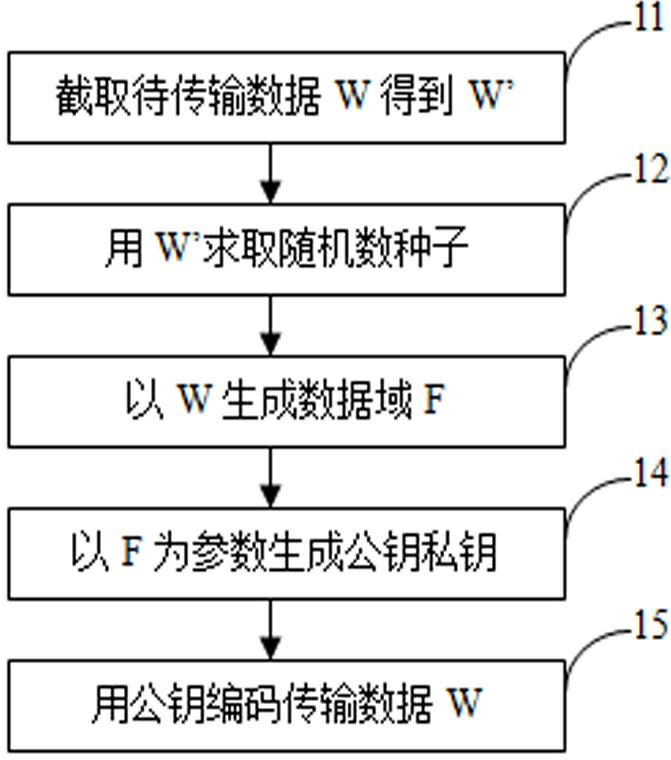
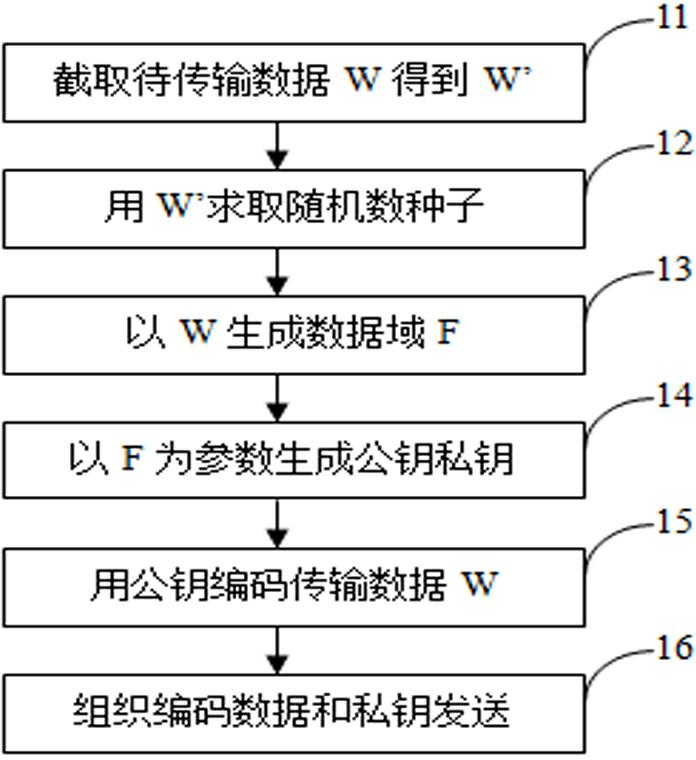
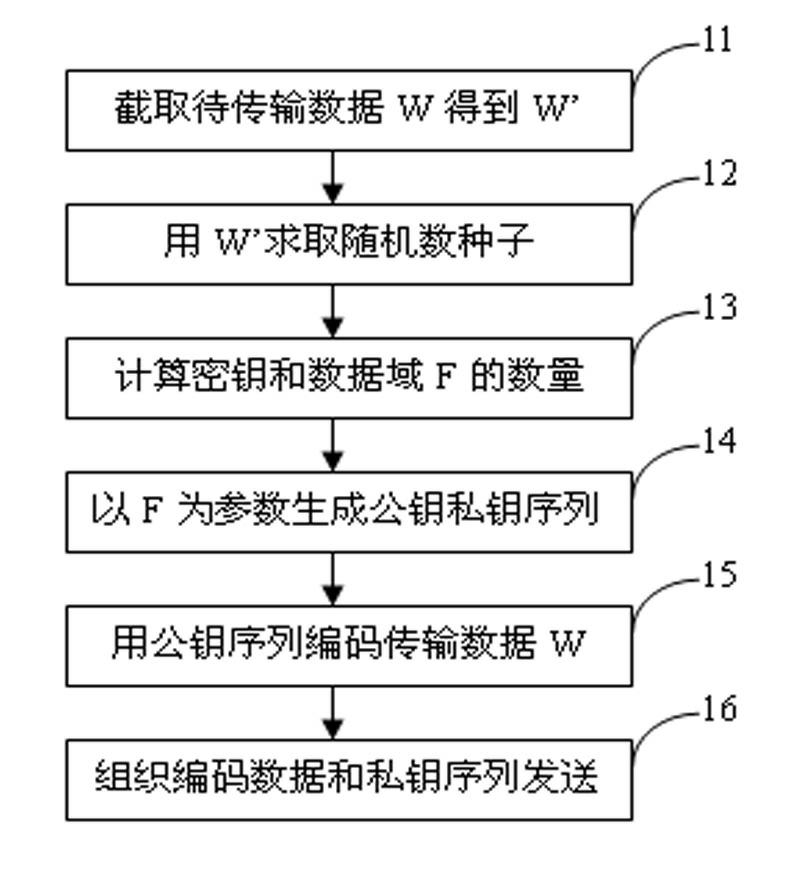
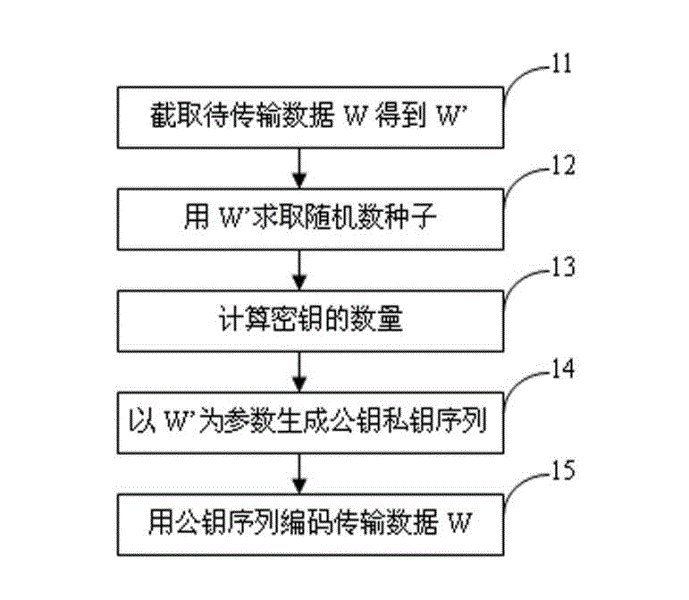
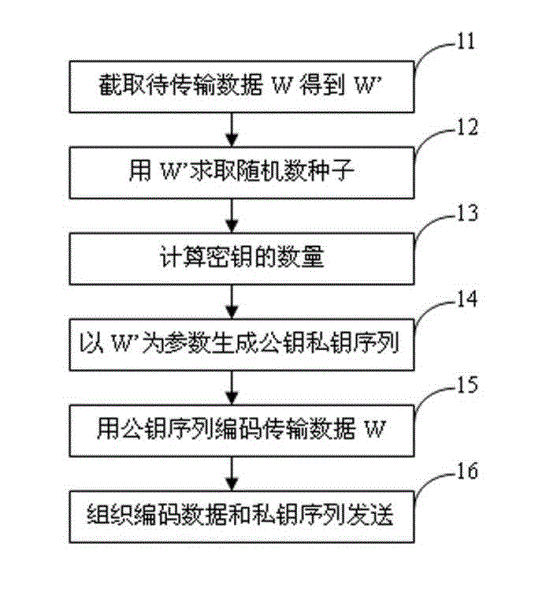
The invention provides a data encrypting method and an encrypted data transmitting device. The data encrypting method comprises the following steps: firstly, randomly capturing data W' with a reserved length k from transmission data W; generating a random number r by using the data W' as a seed, randomly calculating the length q and an initial point a of a data domain by using the r as the seed, and capturing the data from the transmission data W by using the q and the a as parameters so as to generate a data domain F; generating a public key E and a private key R by using the data domain F as a parameter; and finally, encoding the W by using the publish key E so as to obtain an encryption result Z. The invention further provides a data encrypting device, an encrypted data transmitting method, and the encrypted data transmitting device.
Owner:光束科技(北京)有限公司
Method for encrypting data and method for transmitting encrypted data
InactiveCN102611550AImprove confidentialityEncryption guaranteedPublic key for secure communicationData domainComputer security
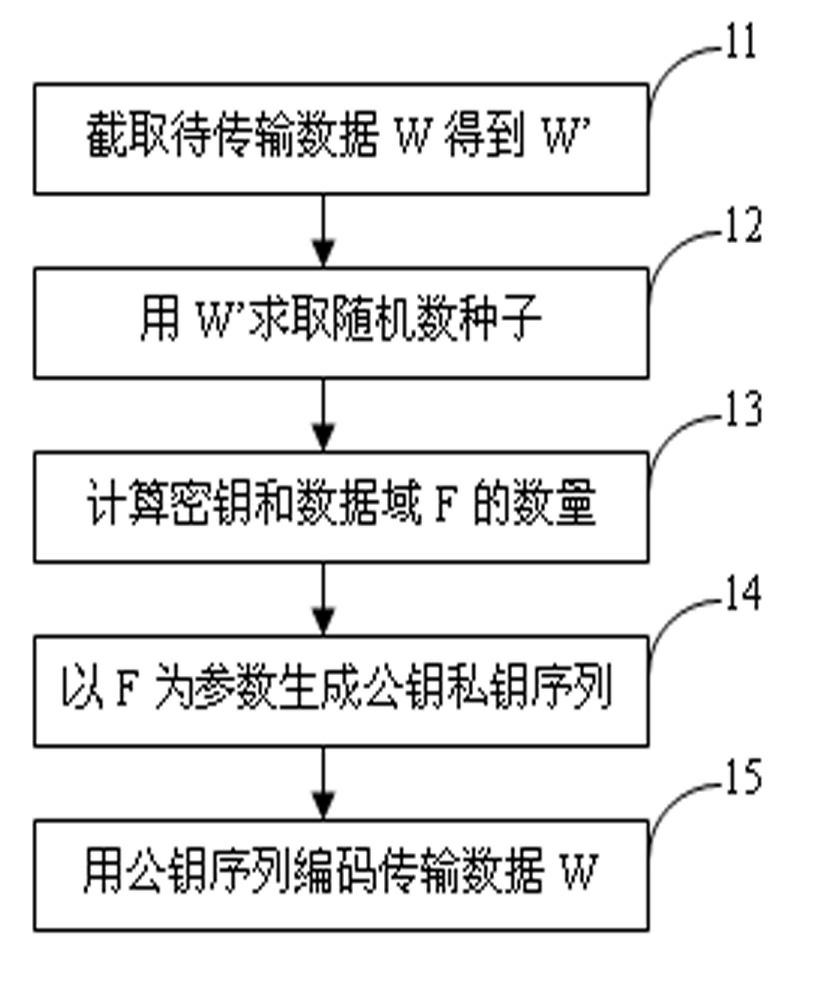
The invention provides a method for encrypting data and a method for transmitting encrypted data. The method for encrypting data comprises the following steps of: firstly, randomly intercepting data w' with a preset length k from transmission data w; generating a random number gamma by taking the data w' as a seed, and calculating a secret key and the number p of data domains by taking r as a seed, wherein p is more than or equal to 1 and less than C, and C is a constant; and randomly calculating the length qi and starting point ai of p data domains Fi, intercepting data from the transmission data w by taking qi and ai as parameters to generate a data domain Fi, wherein i is no less than 1 and no more than p; generating a public key Ei sequence and a private key Ri sequence by taking the data domain Fi as the parameter; and finally, circularly encoding w by the public key Ei to obtain an encrypted result Z. The invention further provides a device for encrypting data, a method for transmitting the encrypted data and a transmission device of the encrypted data.
Owner:光束科技(北京)有限公司
Selective satellite image compression encryption method based on Chacha20 and CCSDS
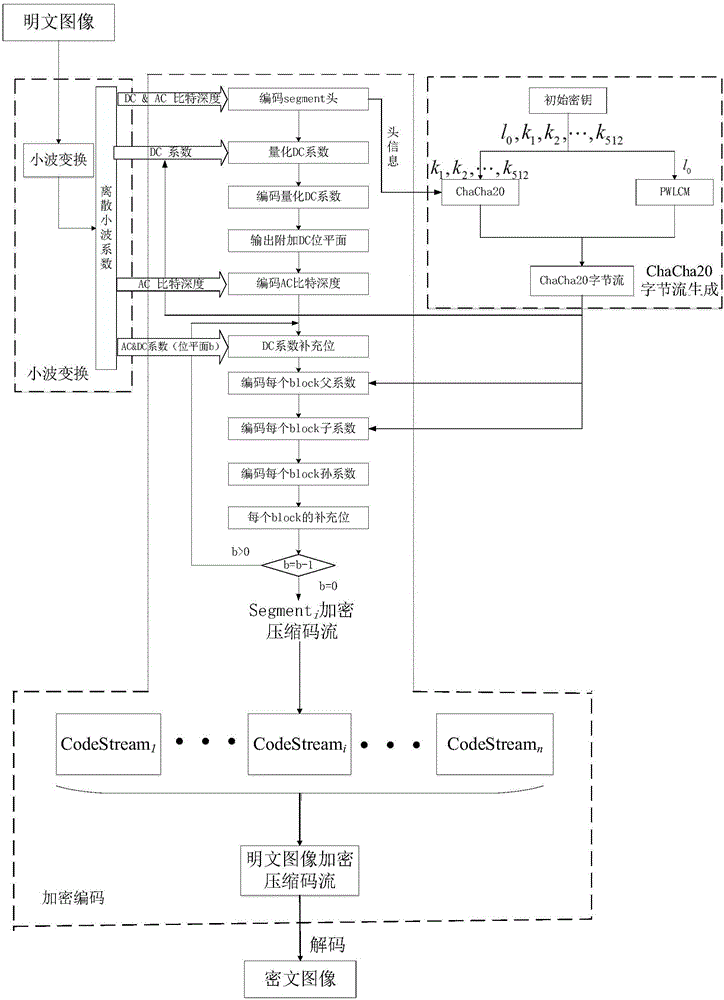
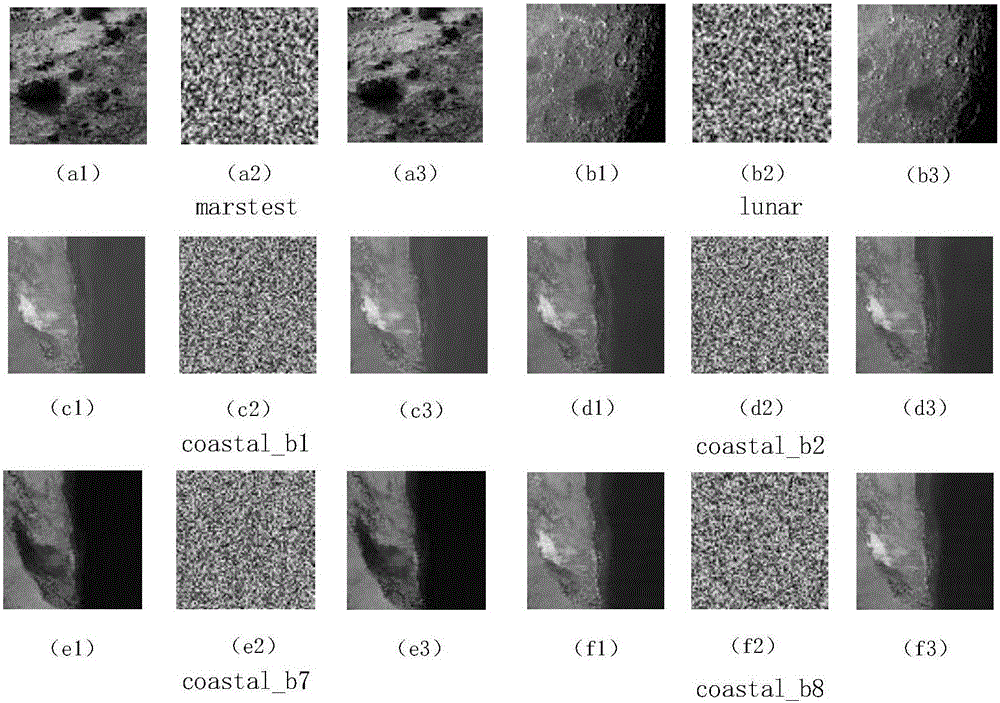
InactiveCN105704499AIncreased sensitivityHigh encryption strengthDigital video signal modificationPlaintextAc coefficient
The invention provides a selective satellite image compression encryption method based on Chacha20 and CCSDS. Aiming the characteristics of a satellite image, the method comprises the steps: firstly carrying out the three-stage two-dimensional discrete wavelet transformation through employing a 9 / 7 integral wavelet in a CCSDS image compression algorithm, and obtaining a DC coefficient and an AC coefficient after transformation; secondly generating a ChaCha20 initial byte stream through the head information in a coding item and a 512-bit initial secret key and ChaCha20 Hash; thirdly carrying out the summation and modular operation of a chaos initial secret key and a plaintext image normalization value through the byte stream generated by PWLCM (Piecewise Linear Chaotic Map) and the ChaCha20 initial byte stream, and generating a ChaCha20 byte stream; fourthly carrying out the XOR encryption of the ChaCha20 byte stream and the DC coefficient and AC coefficient (the father and son coefficients in each block) and all AC coefficient symbol bites; finally enabling the encrypted DC and AC coefficients to be coded and compressed, and completing the compression and encryption of the satellite image. The generation of the ChaCha20 byte stream is related with the to-be-encrypted satellite image and a compression coding parameter, thereby improving the encryption adaptability.
Owner:NORTHWESTERN POLYTECHNICAL UNIV
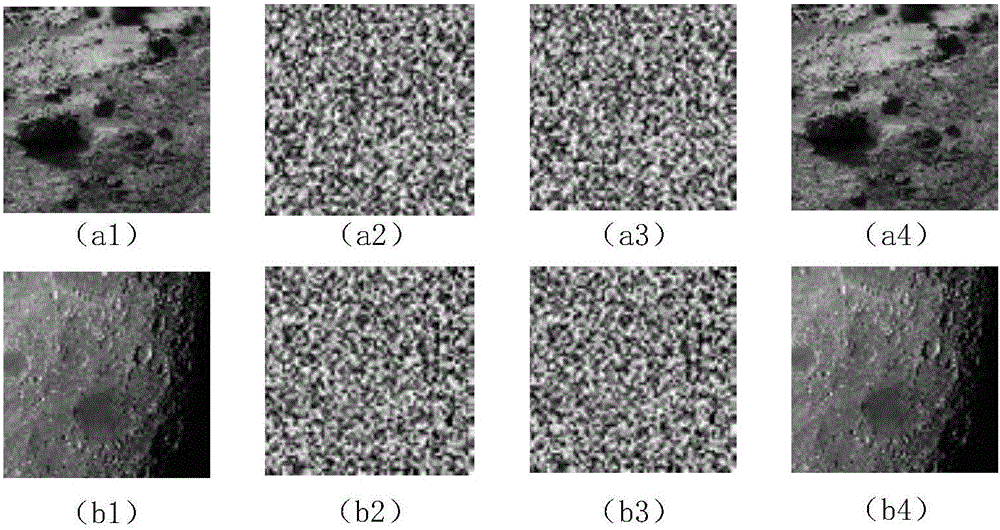
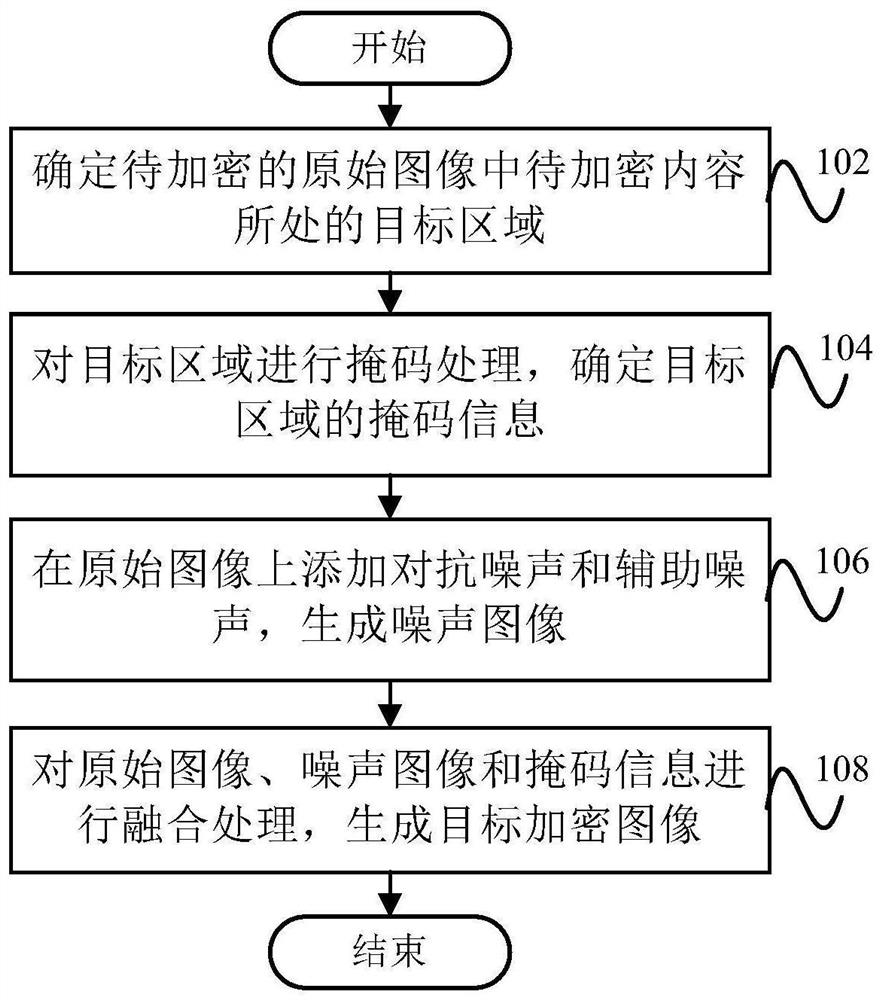
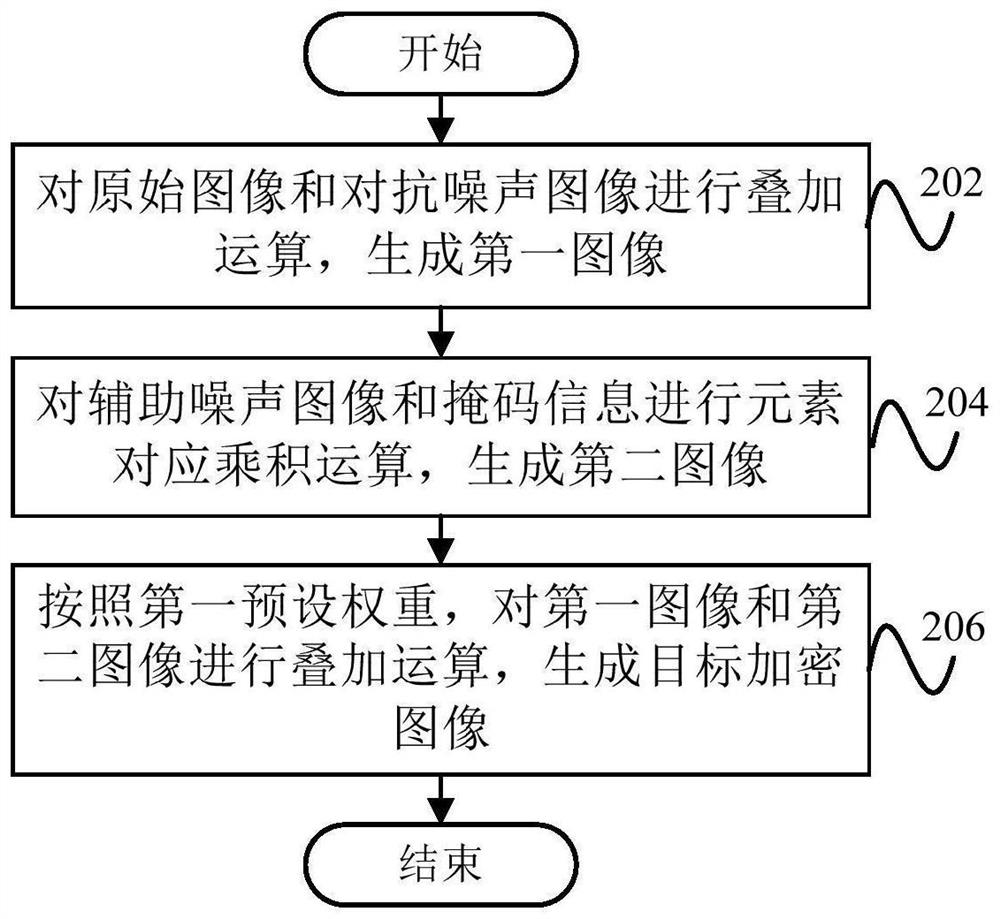
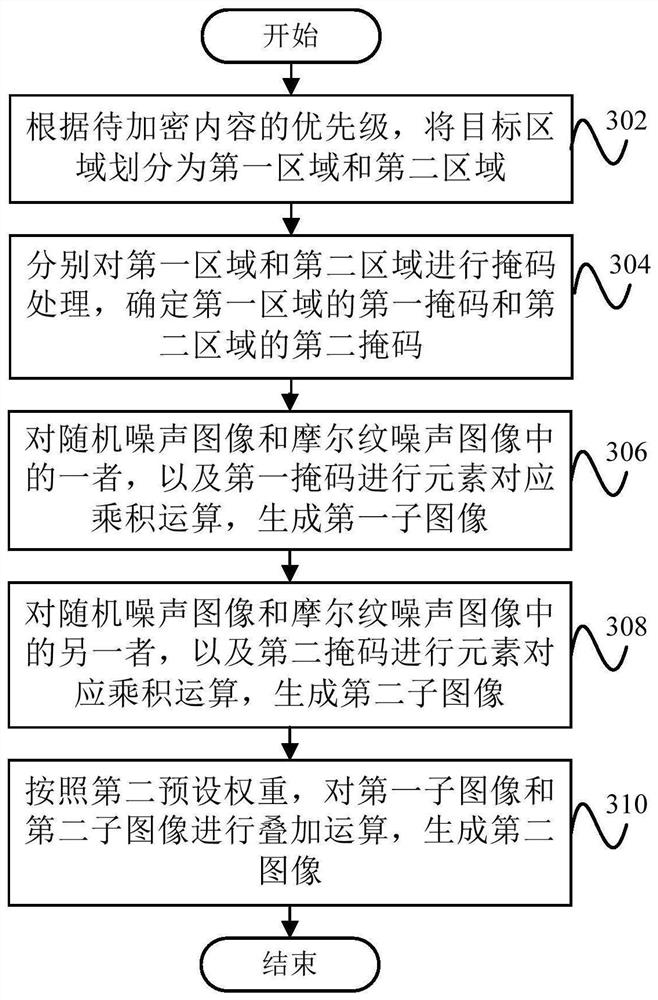
Image encryption method and device, electronic equipment and readable storage medium
PendingCN113486377AImplement encryptionImprove securityDigital data protectionImaging processingComputer graphics (images)
The embodiment of the invention provides an image encryption method and device, electronic equipment and a readable storage medium, and belongs to the technical field of image processing. The image encryption method comprises the following steps: determining a target area where to-be-encrypted content in a to-be-encrypted original image is located; performing mask processing on the target area, and determining mask information of the target area; adding adversarial noise and auxiliary noise to the original image, and generating a noise image; and performing fusion processing on the original image, the noise image and the mask information to generate a target encrypted image.
Owner:VIVO MOBILE COMM HANGZHOU CO LTD
Security underwater transmission method capable of supporting confusion and zero knowledge
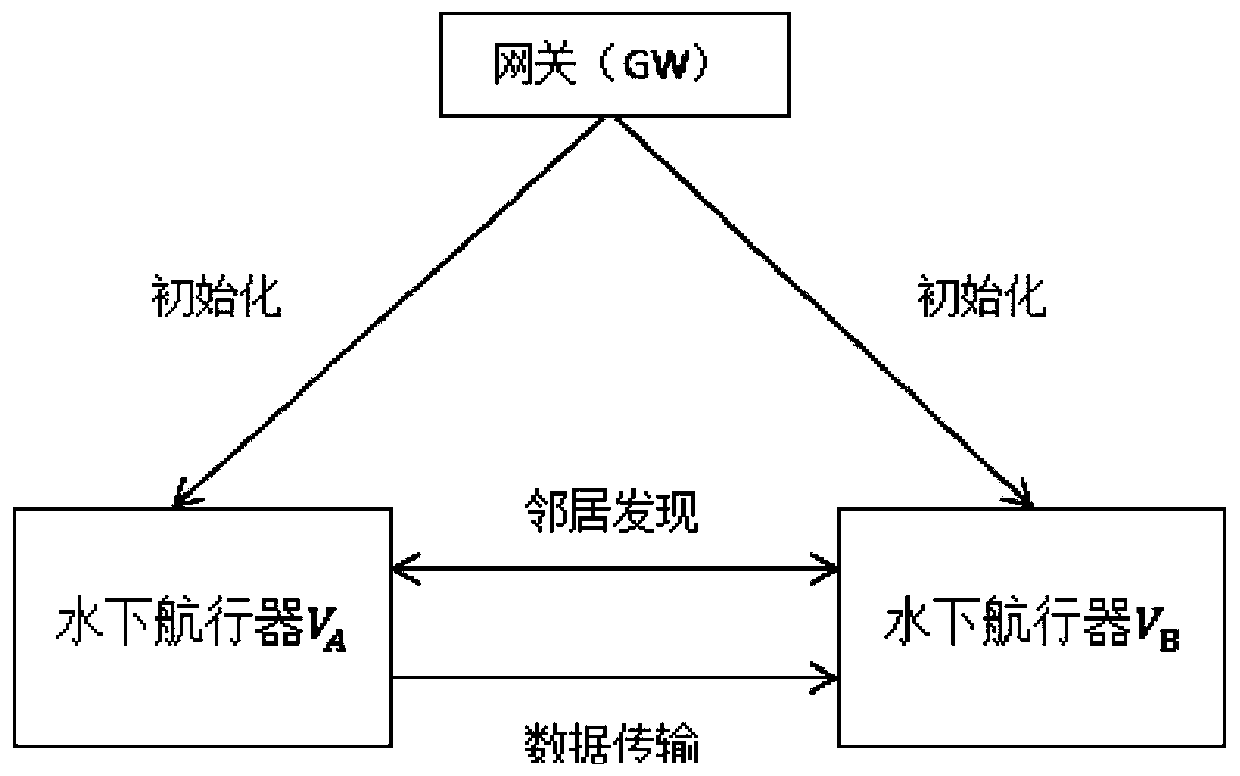
ActiveCN107426176AIntegrity guaranteedEncryption guaranteedUser identity/authority verificationMarine engineeringConfusion
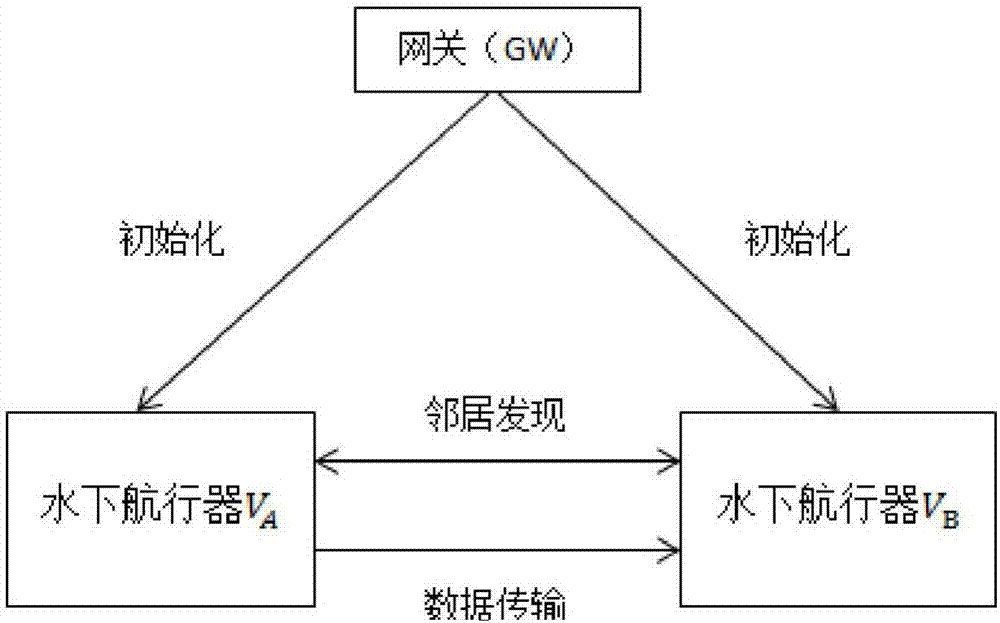
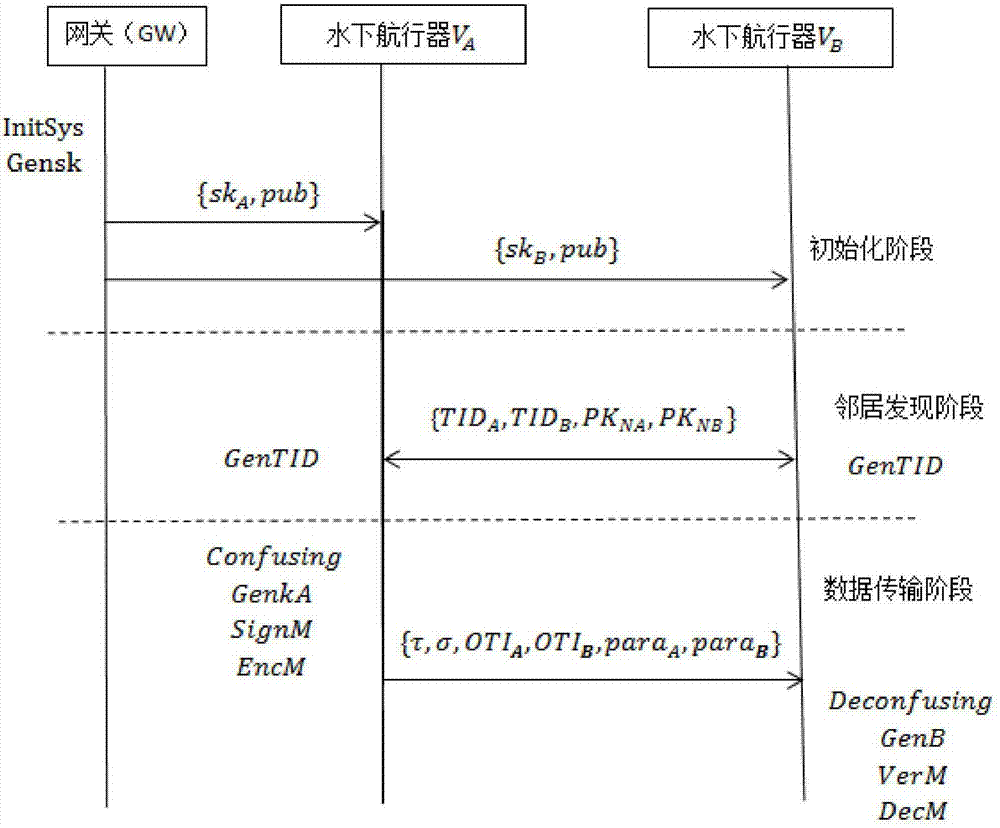
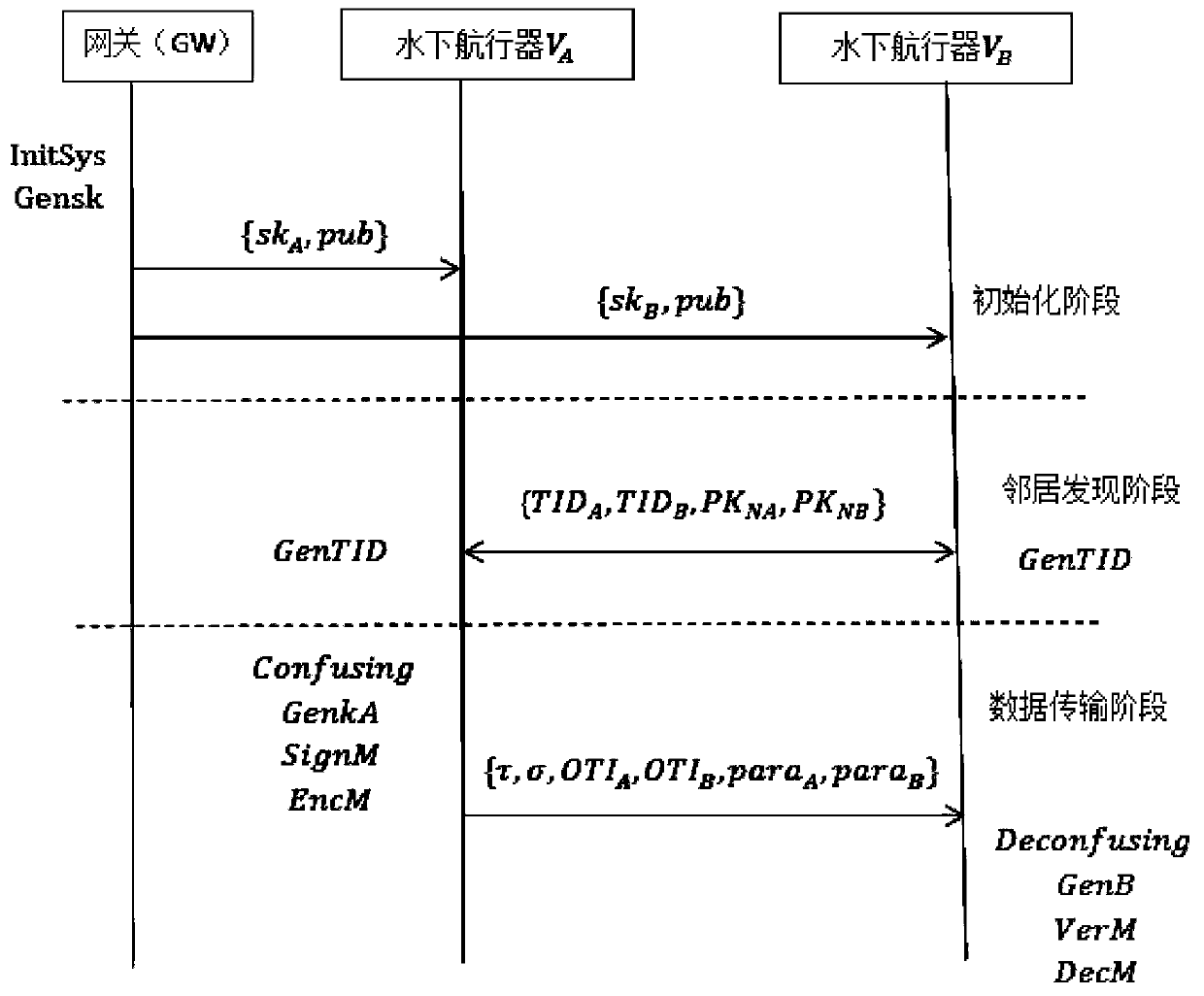
The invention discloses a security underwater transmission method capable of supporting confusion and zero knowledge. The method includes following steps: (1) an initialization stage: a gateway GW generates key materials and distributes the key materials to an underwater vehicle A and an underwater vehicle B; (2) a neighbor discovery stage: the underwater vehicle A and the underwater vehicle B generate and broadcast temporary identities when the two underwater vehicles meet underwater; and (3) a data transmission stage: a sending party firstly generates primary identity information of both parties, performs data encryption and signature, and sending related information to a receiving party; and the receiving party receives the information, verifies whether the receiving party is a correct receiving party, then calculates the temporary identity of the sending party, and decrypts and verifies the received data. According to the method, opponents can be prevented from detecting the related information of the underwater vehicle or counting, and the problem of the conventional underwater wireless communication is solved.
Owner:SOUTHEAST UNIV
Retrieval method and system for encrypted information evidence based on block chain and electronic equipment
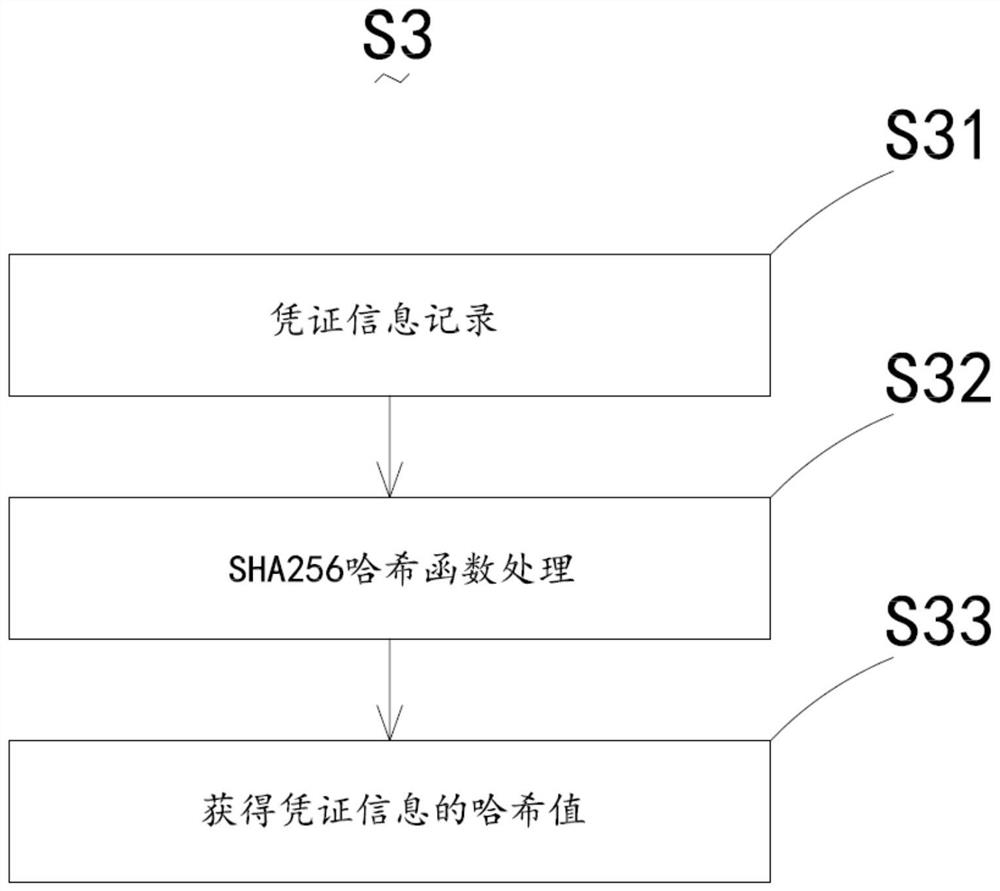
PendingCN113468549AGuaranteed on-chainEncryption guaranteedEncryption apparatus with shift registers/memoriesDigital data protectionHash functionData retrieval
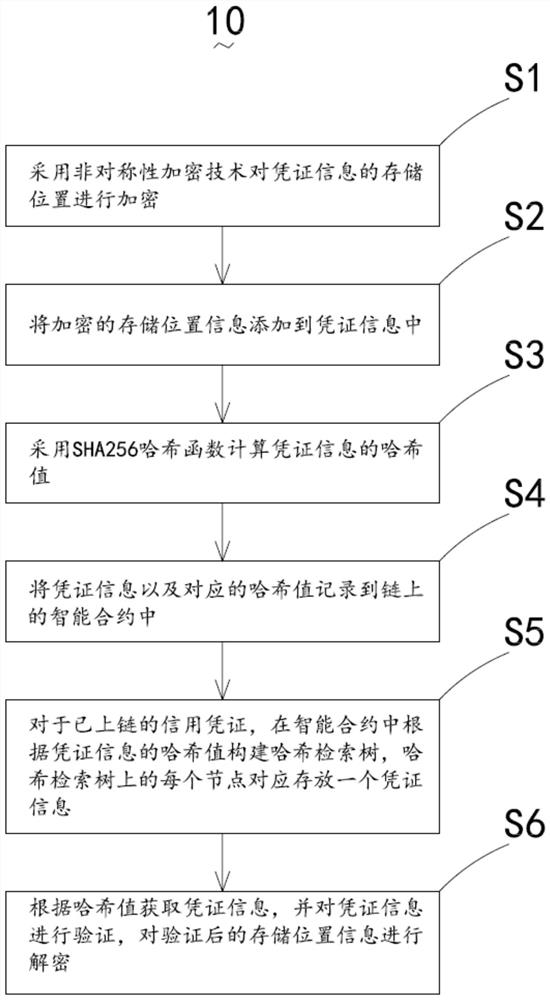
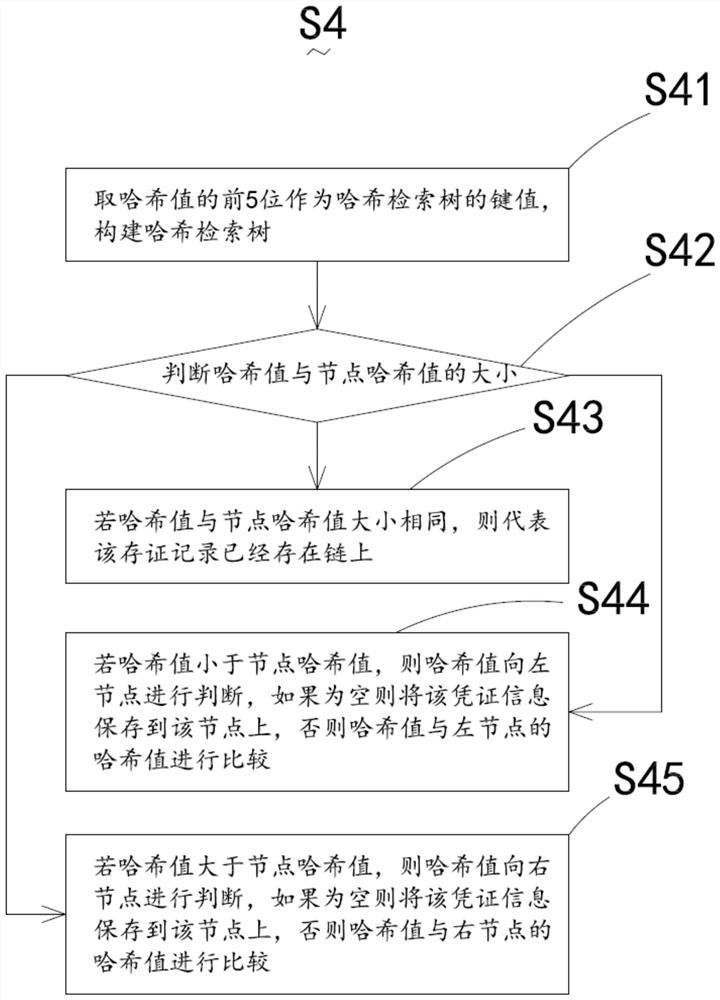
The invention discloses a retrieval method for encrypted information evidence storage based on a block chain. The retrieval method comprises the following steps: encrypting a storage position of certificate information by adopting an asymmetric encryption technology; adding the encrypted storage location information to the voucher information; calculating a hash value of the voucher information by adopting an SHA256 hash function; recording the voucher information and the corresponding hash value into the smart contract on the chain; for the chained credit voucher, creating a hash retrieval tree in the smart contract according to the hash value of the voucher information, wherein each node on the hash retrieval tree correspondingly stores one piece of voucher information; and according to the Hash value, obtaining the voucher information, verifying the voucher information, and decrypting the verified storage position information. The retrieval method and system for encrypted information evidence based on the block chain and the electronic equipment have the advantages of high confidentiality, quick data retrieval and the like.
Owner:深圳前海移联科技有限公司
Method and device for encrypting data and transmission method and transmission device of encrypted data
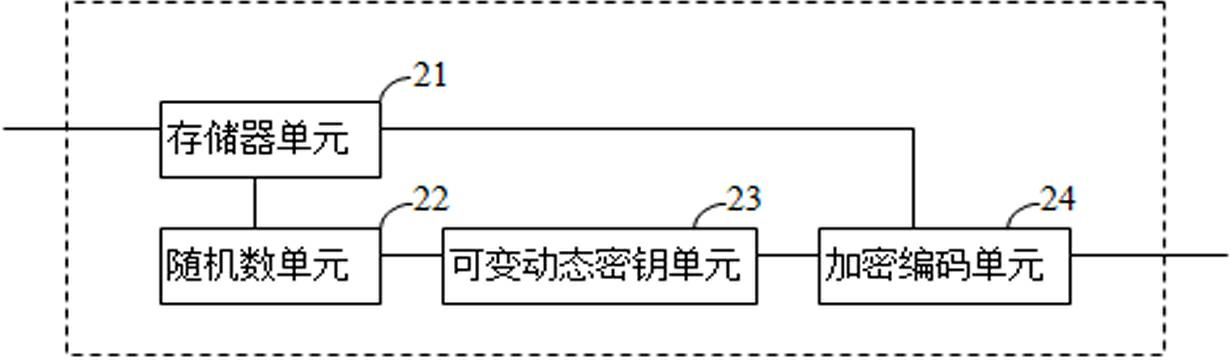
InactiveCN102624527AImprove confidentialityEncryption guaranteedKey distribution for secure communicationPublic key for secure communicationEncryptionTransmission delay
The invention provides a method for encrypting data and a transmission device of encrypted data. The method for encrypting data includes that first, data W' with preset length k is intercepted randomly from transmitting data W; the data W' is used as a seed, a random number r is generated, the r is used as a seed to calculate the quantity p of secret keys at random, and p belongs to [1,C), wherein C is a constant; then the data W' is used as a parameter to generate a public key Ei and a private key Ri, and 1<=i<=p; and finally the public key Ei encodes W in cycling mode to obtain an encryption result Z. The invention further provides a device for encrypting the data, a transmission method of the encrypted data and the transmission device of the encrypted data.
Owner:光束科技(北京)有限公司
Digital image encryption method, decryption method and system based on chaotic system
PendingCN114157408ALarge dynamic propertiesStrong dynamic propertiesSecuring communication by chaotic signalsChaotic systemsDigital image
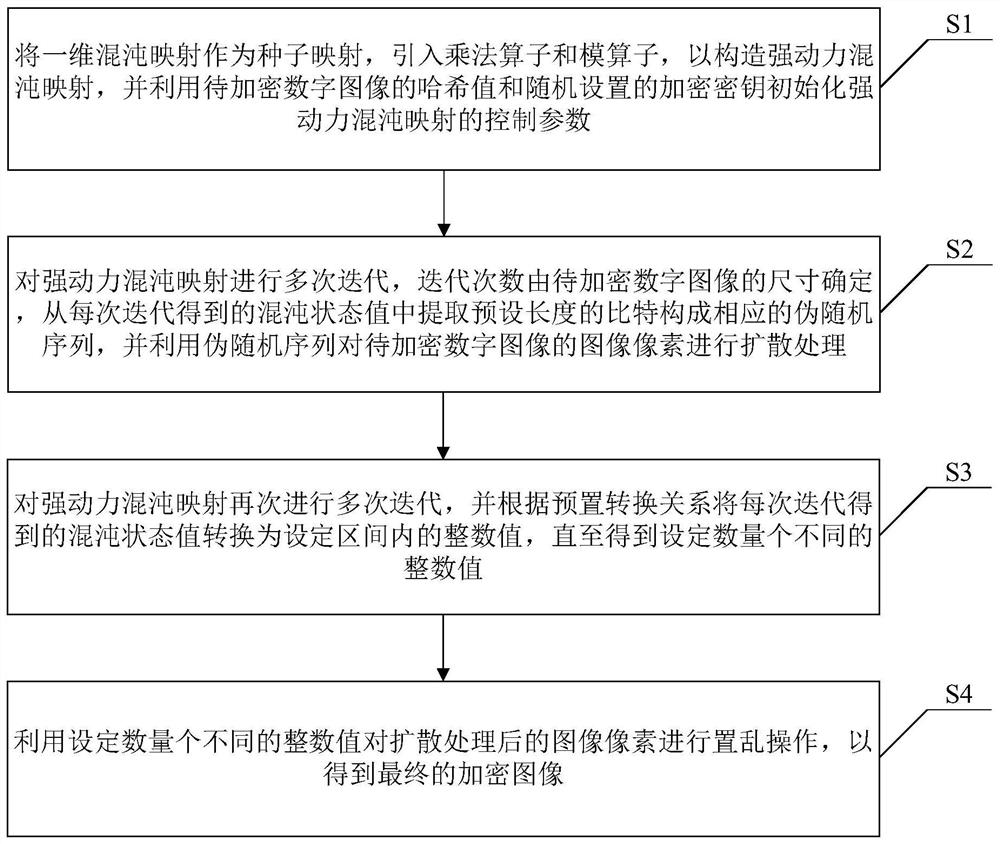
The invention discloses a digital image encryption method, decryption method and system based on a chaotic system, and belongs to the field of chaotic image encryption, and the encryption method comprises the steps: taking a one-dimensional chaotic mapping as a seed mapping, introducing a multiplication operator and a modular operator, constructing a strong dynamic chaotic mapping, initializing a control parameter of strong dynamic chaotic mapping by using the hash value of the digital image to be encrypted and the encryption key; iterating the strong dynamic chaotic mapping for multiple times, extracting bits with a preset length from a chaotic state value obtained by each iteration to form a corresponding pseudo-random sequence, and diffusing image pixels of the digital image to be encrypted by using the pseudo-random sequence; and performing multiple iterations on the strong dynamic chaotic mapping again, converting a chaotic state value obtained by each iteration into an integer value in a set interval until a set number of different integer values are obtained, and performing scrambling operation on image pixels after diffusion processing to obtain a final encrypted image. And the digital image is encrypted safely and effectively.
Owner:HUAZHONG UNIV OF SCI & TECH
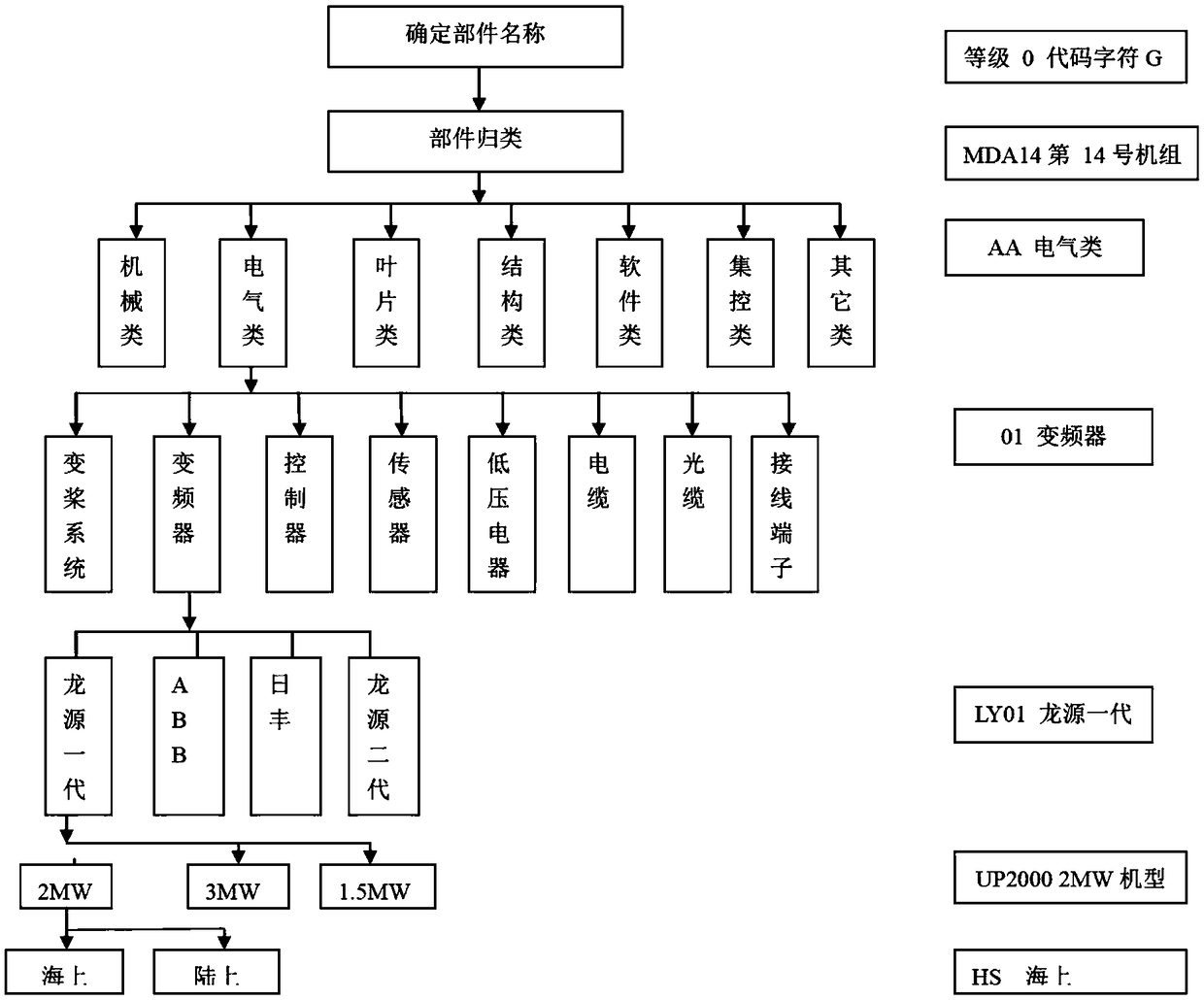
Method for automatic coding component names of fan system, its system and application
InactiveCN109343480AEnsure safetyEncryption guaranteedTotal factory controlProgramme total factory controlSCADASoftware engineering
The invention discloses a method for automatically generating codes for the name of components of a fan system and its system and application; it belongs to the field of fan control. The fan system comprises several wind turbines. The auto-coding method includes: collecting the identification information of the said part; comparing the identification information of the part against the coding database and calling the code in the database corresponding to each piece of information in the said identification information; connecting each called code to form a unique coding sequence for the part name; the unique coding sequence is used to replace the part name in the drawings, in the master programming and / or in the SCADA display to the outside. The special coding management is used for all components of the wind power plant that has proposed the invention, which ensures that any error in the process can be traced back to its source; because of the uniqueness of the code, the program, theelectrical drawings and the like, in which the code is used replacing the part name, are all unique, thus ensuring the safety of the whole system.
Owner:GUODIAN UNITED POWER TECH
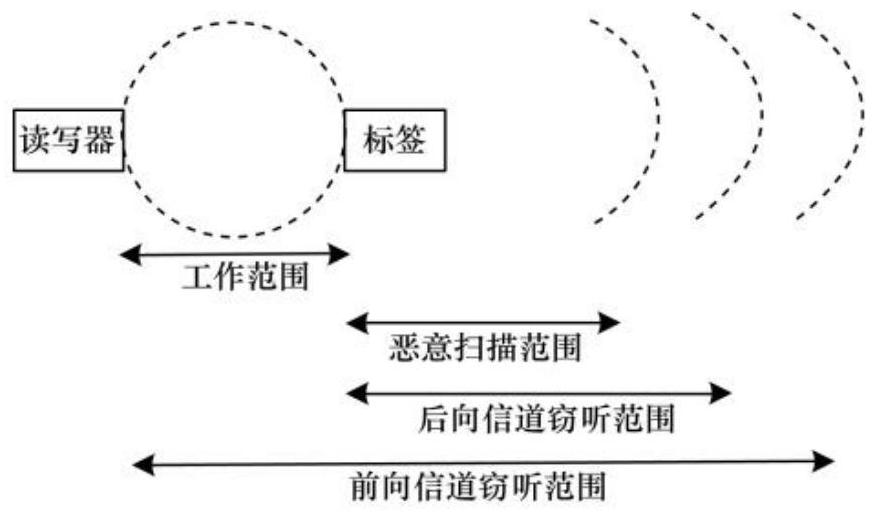
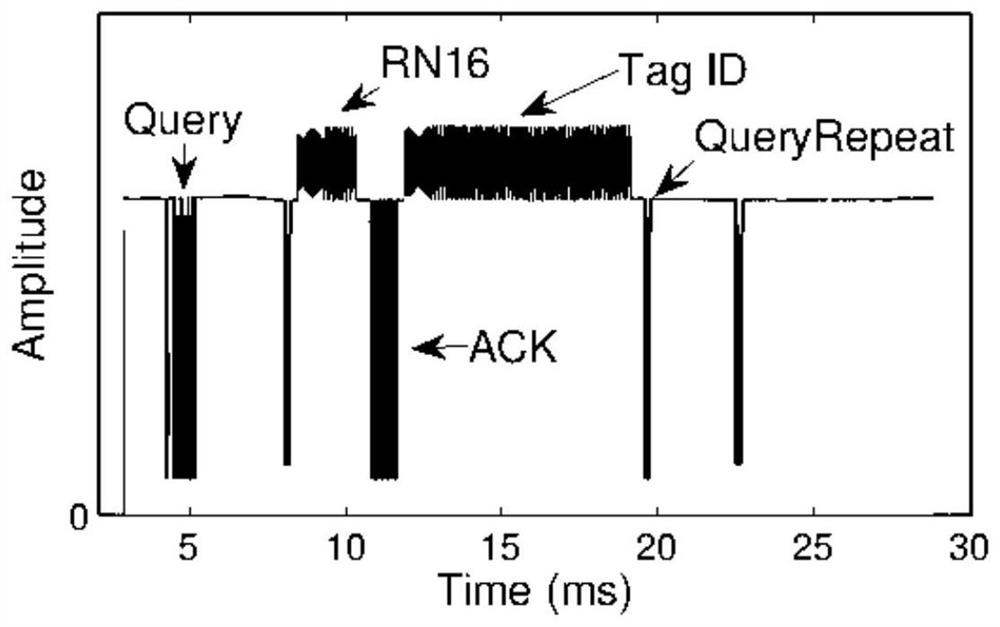
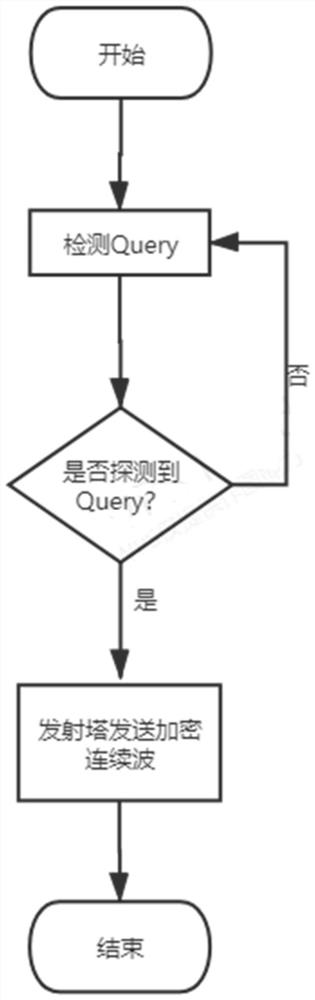
Base-station-like energy supply encryption method based on RFID passive transmission
PendingCN113225734AGuaranteed supplyEncryption guaranteedCircuit arrangementsSecurity arrangementStationReflected waves
The invention relates to the technical field of data transmission, in particular to a base-station-like energy supply encryption method based on RFID passive transmission, which comprises the following steps: a launching tower silently and continuously receives commands of a reader / receiving end in a local area; when a Query command sent by the reader / receiving end is received, the launching tower starts to send a continuous wave with encrypted information to the tag for encryption and reflection communication of the tag; the reader receives the encrypted information of the reflected wave with the continuous wave sent by the launching tower from the label, and performs corresponding decoding at a receiving end; by additionally arranging the launching tower, energy supply is guaranteed, and meanwhile the encryption effect is guaranteed; and the transmission stability and encryption requirements are improved.
Owner:TAIYUAN UNIV OF TECH
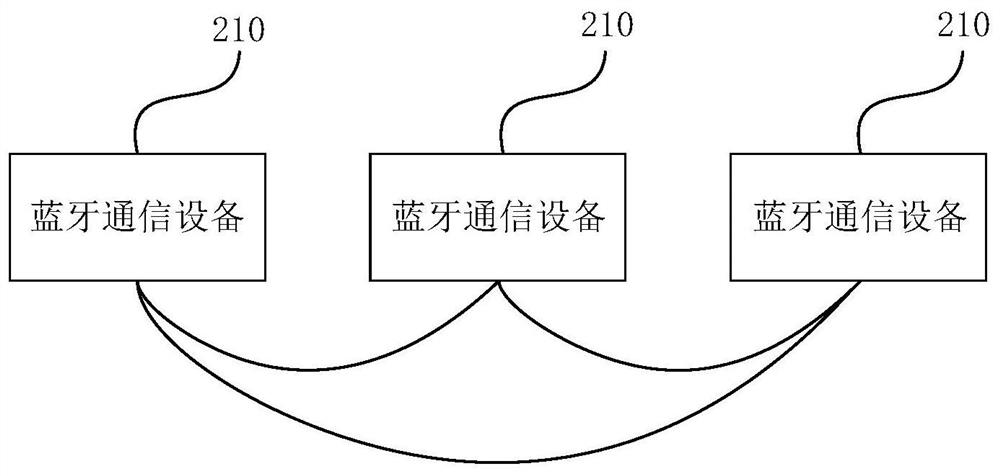
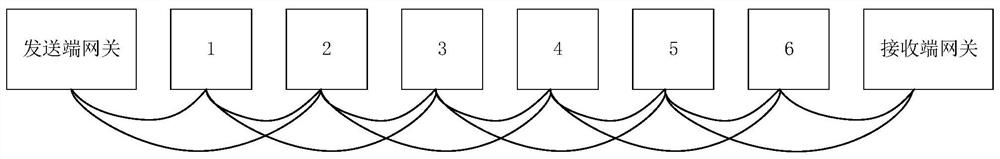
Bluetooth communication system and method
PendingCN113766474AEncryption guaranteedGuaranteed compactnessNear-field transmissionShort range communication serviceCommunications systemEmbedded system
The embodiment of the invention discloses a Bluetooth communication system, and the system comprises at least two Bluetooth communication devices, and at least two Bluetooth communication devices are arranged according to a preset sorting rule. Each Bluetooth communication device is used for forming a new information acquisition message after adding the device information corresponding to the Bluetooth communication device to the received information acquisition message, and transmitting the information acquisition message to a target device as a source device; wherein the received information acquisition message is sent by a sending end gateway or is sent by the Bluetooth communication device serving as the source device corresponding to the information acquisition message; the target device is a receiving end gateway or a Bluetooth communication device satisfying a set transmission strategy. According to the Bluetooth communication system provided by the embodiment of the invention, a transmission path can be ensured not to be interrupted when a link link is lost in a transmission process, and a network storm cannot be generated in a local area network due to the fact that a plurality of Bluetooth communication modules report messages at the same time.
Owner:SHANGHAI SIIC LONGCHUANG SMARTER ENERGY TECH CO LTD
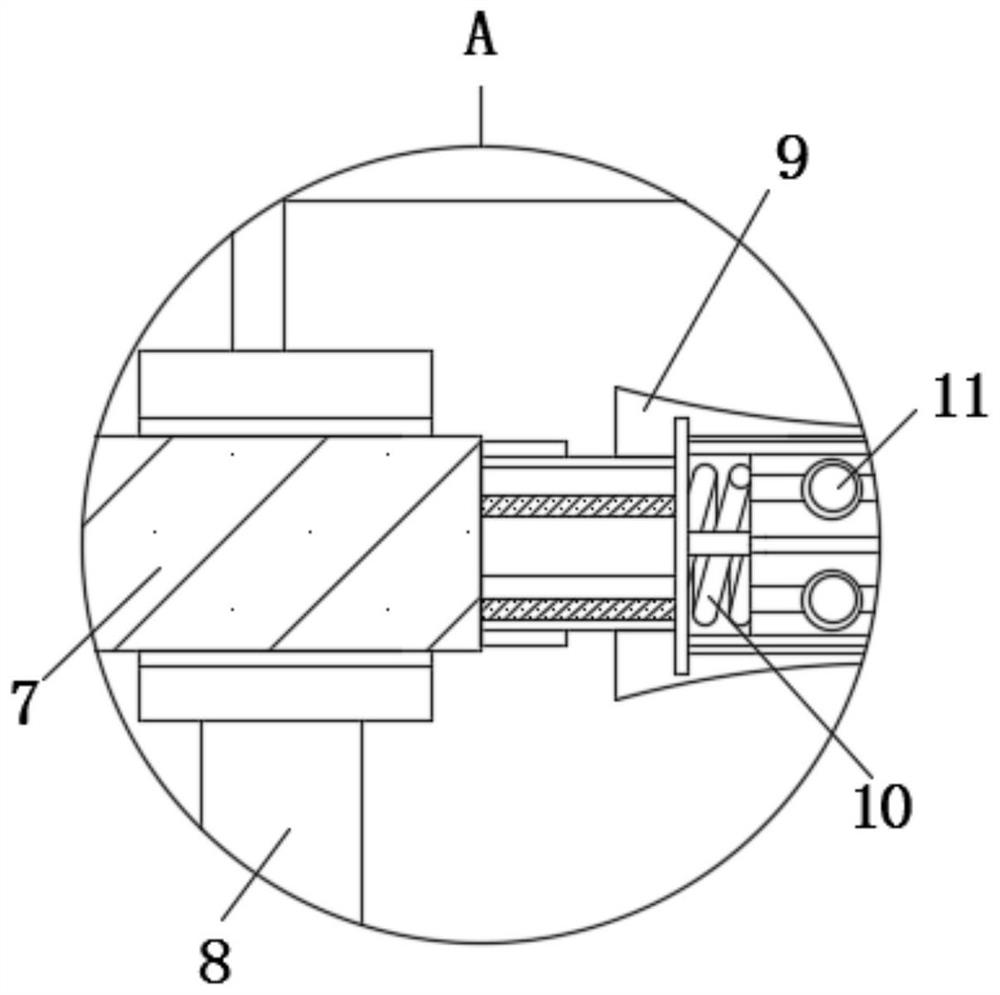
High-security computer encryption auxiliary device with data protection function
InactiveCN112543930AAvoid enteringAvoid destructionDigital data protectionInternal/peripheral component protectionEngineeringStructural engineering
The invention relates to the technical field of computer equipment, in particular to a high-security computer encryption auxiliary device with a data protection function. The auxiliary device comprises an equipment main body, positioning slide rails are fixedly connected to the left side wall and the right side wall in the equipment main body, and reset frames are fixedly connected to the lower surfaces of the positioning slide rails; a movable plate is fixedly connected to the right side face of the reset frame, an extrusion plate is fixedly connected to the lower surface of the movable plate, an electromagnet is fixedly connected to the position, located below the movable plate, of the bottom face in the equipment main body, and insect expelling powder in an air cushion is extruded and discharged, so that insects in a machine room are prevented from entering the equipment, thus the data lines and internal parts will not be damaged, the working failure of encryption software is avoided, the equipment is well protected, the limiting clamping plates and the clamping plates interact to limit the middle data lines, the data lines are prevented from being separated and loosened, and the working efficiency of the equipment is ensured.
Owner:HANGZHOU ZHOUJIN TECH CO LTD
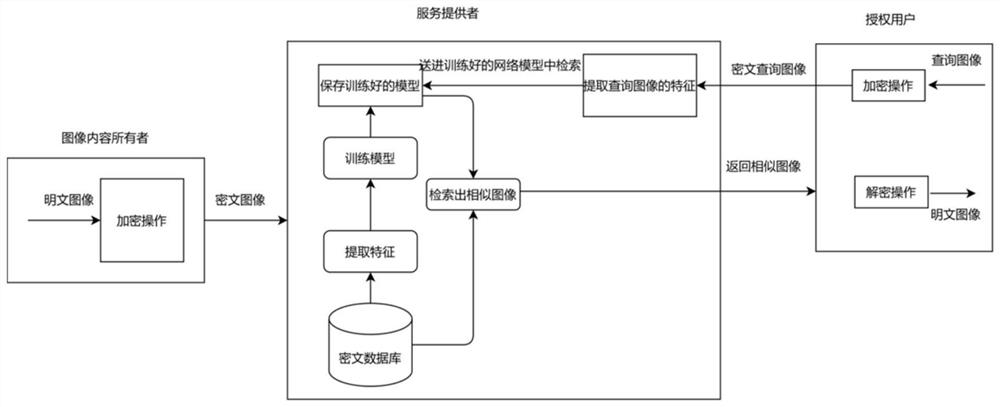
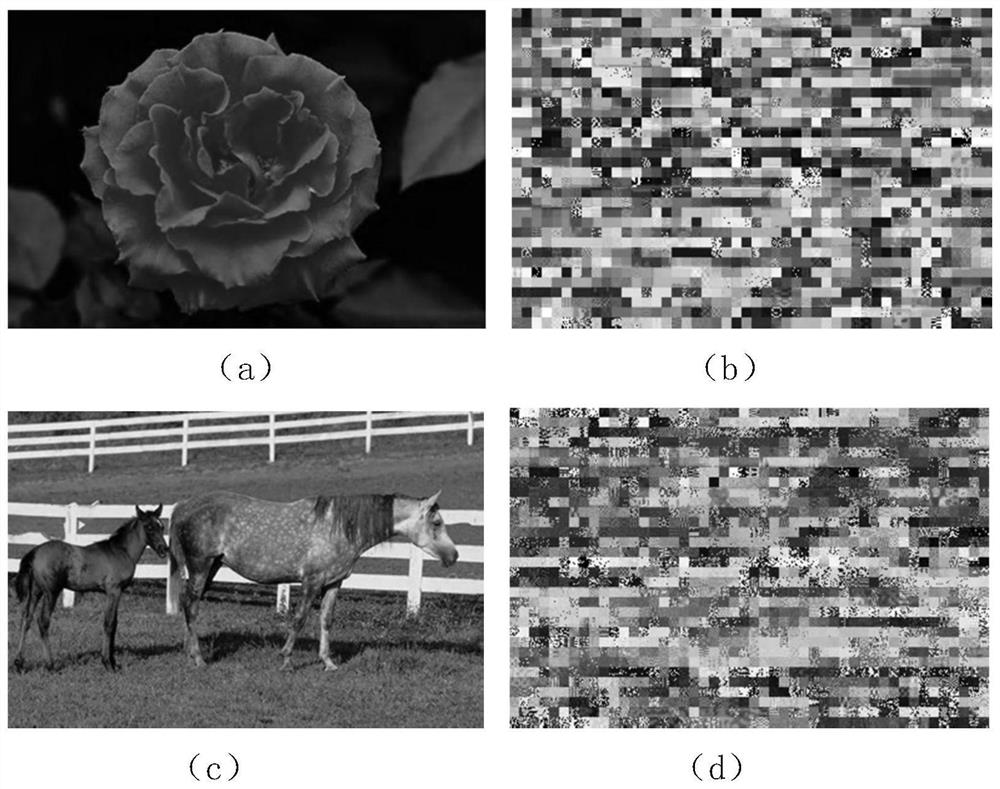
Ciphertext JPEG image retrieval method and application
PendingCN112417190AFix the leakAchieve safe storageDigital data protectionMetadata still image retrievalFeature extractionCiphertext
The invention discloses a ciphertext JPEG image retrieval method and application, and the method comprises the steps: obtaining a plaintext image and a corresponding DC coefficient and AC coefficient,carrying out the image encryption of the plaintext image, carrying out the encryption of a bit stream generated through entropy coding, obtaining an encrypted JPEG bit stream, and extracting featuresfrom the encrypted JPEG bit stream; analyzing the ciphertext JPEG bit stream to extract features, and extracting Huffman code histograms of the DC coefficient and the AC coefficient as features; constructing a neural network model, inputting the Huffman code histogram features of the ciphertext image into the neural network model, and training the neural network model; and inputting the encryptedciphertext graph of the to-be-retrieved image, inputting the Huffman code histogram features of the ciphertext graph into the trained neural network model, and outputting a ciphertext image similar to the to-be-retrieved image. According to the method, the image retrieval precision is improved, and the JPEG image format compatibility and encryption performance are ensured.
Owner:JINAN UNIVERSITY
Data communication method, device and vehicle of in-vehicle bus
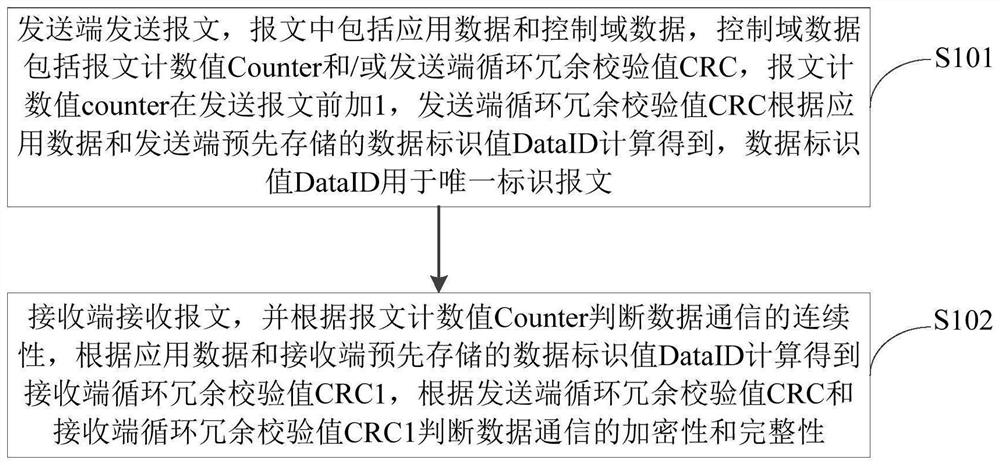
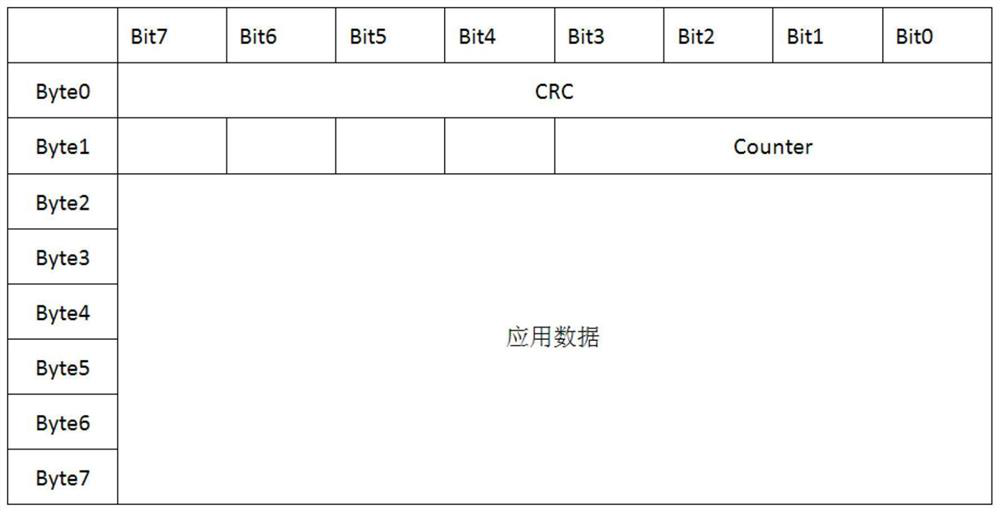
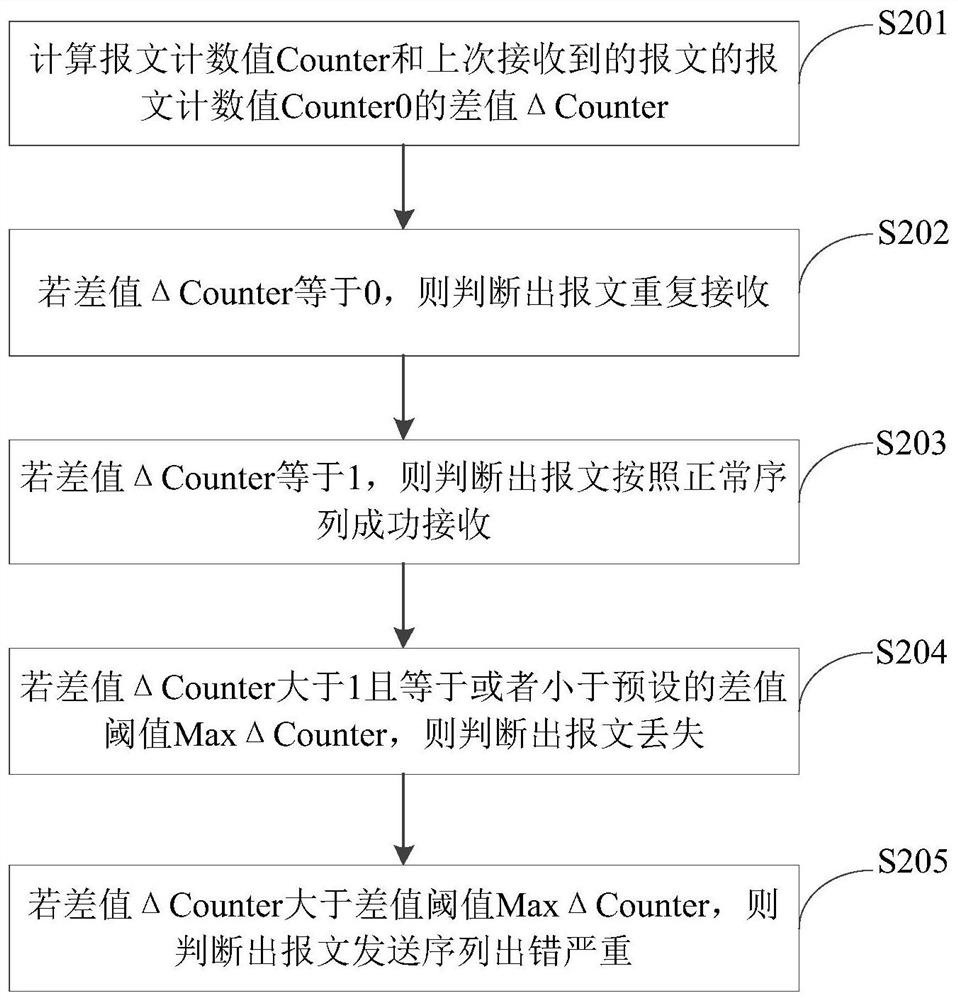
ActiveCN110213018BGuaranteed continuityEncryption guaranteedTransmission link error control systemSecuring communicationData controlData pack
The present invention provides a data communication method, device and vehicle for a vehicle-mounted bus. The data communication method includes: a sender sends a message, the message includes application data and control domain data, and the control domain data includes a message count value and / or Or the CRC value of the sender, the message count value is added 1 before the message is sent, and the CRC value of the sender is calculated based on the application data and the data identifier value pre-stored by the sender, and the data identifier value is used for Uniquely identifies the message; the receiving end receives the message and judges the continuity of data communication according to the message count value, and calculates the CRC value of the receiving end according to the application data and the data identification value pre-stored by the receiving end. The cyclic redundancy check value and the cyclic redundancy check value of the receiving end judge the encryption and integrity of the data communication. The data communication method, device and vehicle of the in-vehicle bus of the present invention can ensure the continuity, integrity and encryption of end-to-end data communication.
Owner:BAIC MOTOR CORP LTD
Gateway system based on safe communication
InactiveCN113890733AGuaranteed not to be leakedEncryption guaranteedKey distribution for secure communicationMessaging/mailboxes/announcementsSecure communicationKey server
The invention belongs to the field of communication, and discloses a gateway system based on safe communication, which comprises a plurality of gateways and a server, at least one first gateway is provided with a short message communication interface, the plurality of gateways are in safe communication with the server, the first gateway requests a secret key from the server through a short message, the server sends the secret key to the first gateway, and the server sends the secret key to the first gateway. The first gateway splits a secret key into a plurality of sub-secret keys according to a Shamir secret sharing threshold method and sends the sub-secret keys to other gateways, after data to be sent by other gateways are partitioned, the sub-secret keys are randomly used as symmetric secret keys to encrypt the partitioned data and send the partitioned data to the server, and the server decrypts the received data by using the sub-secret keys. The encrypted secret key is sent through the short message, it is effectively guaranteed that the secret key is not leaked, the secret key is further decomposed into the sub-secret keys, the sub-secret keys are used for encrypting data, and the encryption effect is guaranteed.
Owner:上海赋华网络科技有限公司
Implementation method for memory data encryption protection
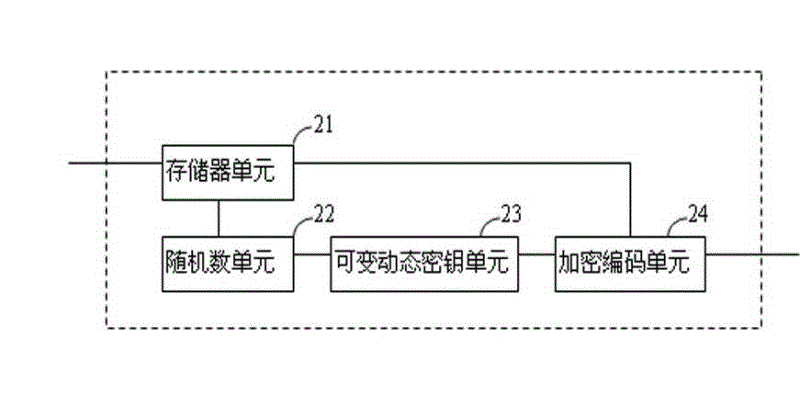
ActiveCN107908980AImprove securityEncryption guaranteedDigital data protectionInternal/peripheral component protectionComputer hardwareOriginal data
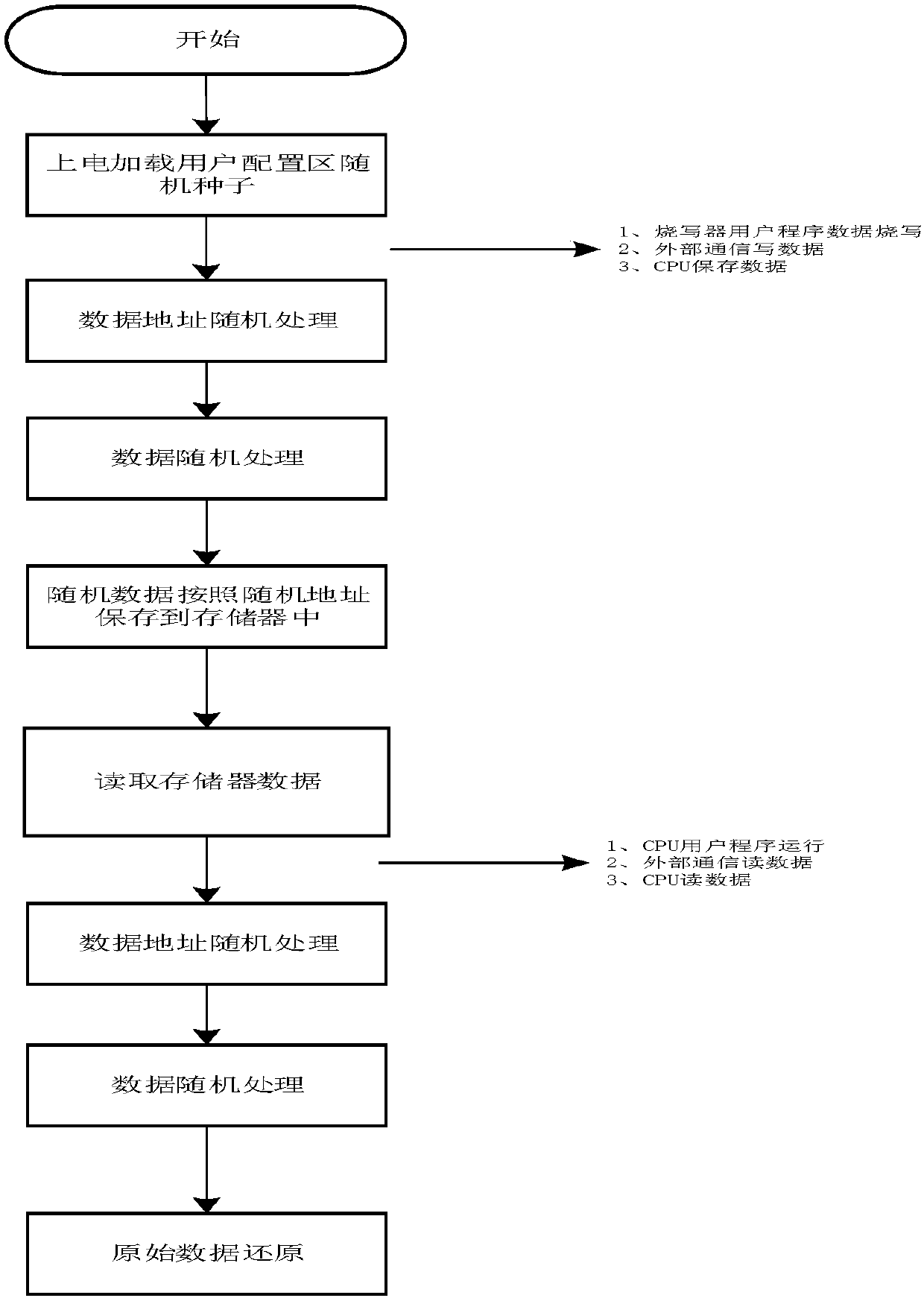
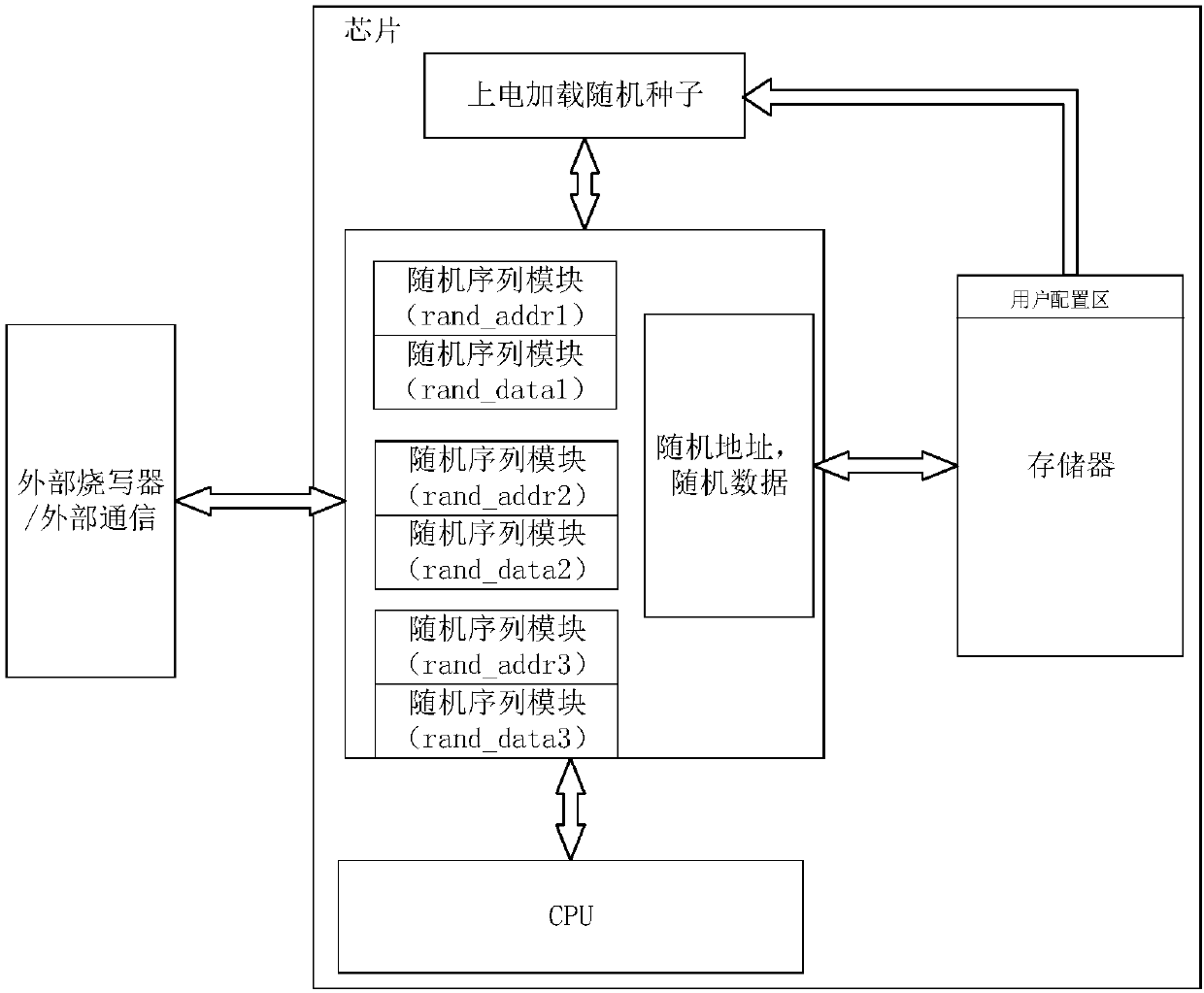
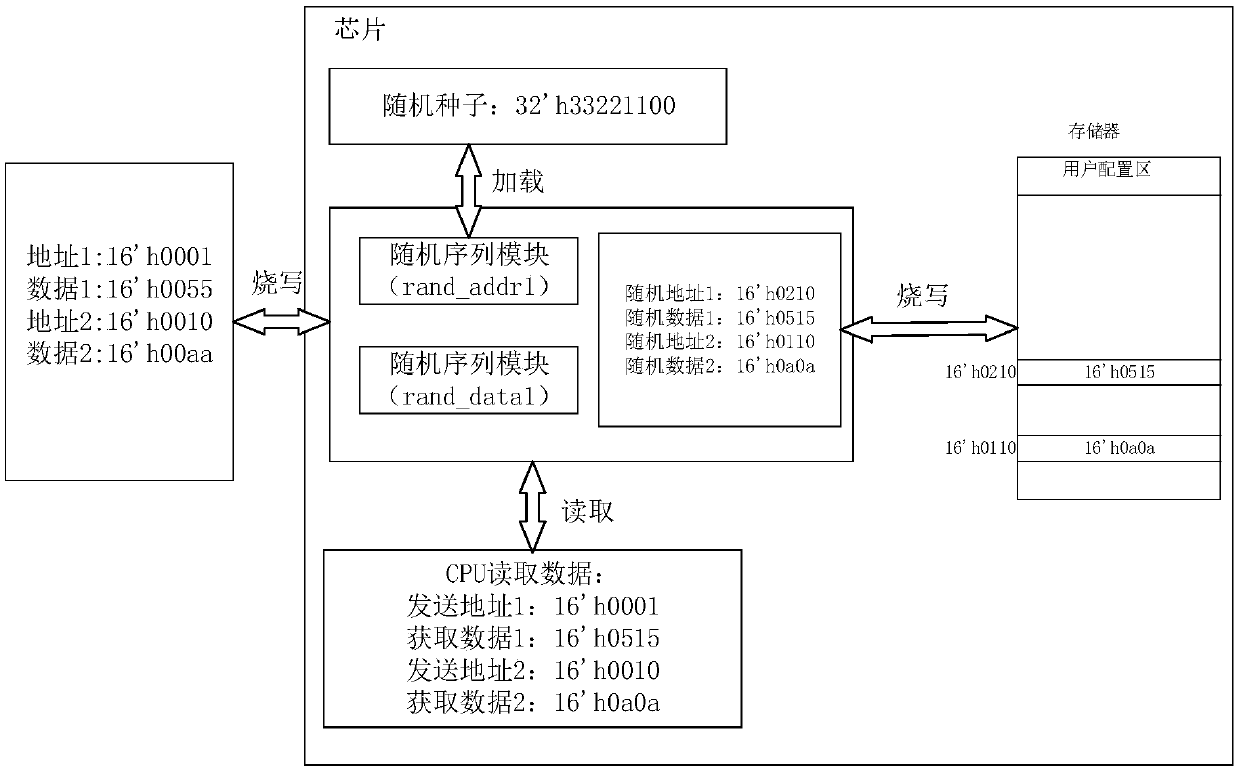
The invention discloses an implementation method for memory data encryption protection. According to the method, a memory needs to open up a user configuration region, configure random seeds and set arandom sequence module first; then original data is processed through the random sequence module, so that the saving address of the original data in the memory is changed into a random address; and the original data is processed through the random sequence module, so that the original data is changed into random data. Through the method, the purpose of high encryption protection of the memory data is achieved, the security of user data is improved, the reliability of a chip is improved, and meanwhile the scheme is easy and convenient to implement and small in area power consumption.
Owner:CHIPSEA TECH SHENZHEN CO LTD
Anti-collision interruptible recovery voice secret transmission method, device and system
InactiveCN112235790AAvoid session failurePromote recoveryKey distribution for secure communicationConnection managementCommunications securityTerminal server
The invention relates to the technical field of communication security, and discloses an anti-collision interruptible recovery voice secret transmission method, device and system, and the method comprises the steps: carrying out grading of a user terminal, employing an identity secret key to read an identifier, obtaining a transmission secret key through the identifier, carrying out transmission of a session secret key through the transmission secret key, and establishing an encrypted session through the session key. The device comprises a user terminal, a server and a background database, thesystem comprises one or more processors, a storage device and an anti-collision interruptible recovery voice secret transmission device. Conflict processing of multiple voice communication requests can be achieved, voice communication can be conveniently and reliably kept secret, and meanwhile, when the session is accidentally interrupted, effective unification of confidentiality recovery, data two-party identification and data confidential transmission can be realized, so that the confidential data is prevented from being maliciously eavesdropped or counterfeited, and the method has a relatively good practical value.
Owner:合肥诺卡物联网科技有限公司
A data tamper-proof blockchain on-chain method
ActiveCN113326504BIntegrity guaranteedEncryption guaranteedDigital data protectionDigital data authenticationProtection mechanismData acquisition
Owner:厦门致联科技有限公司
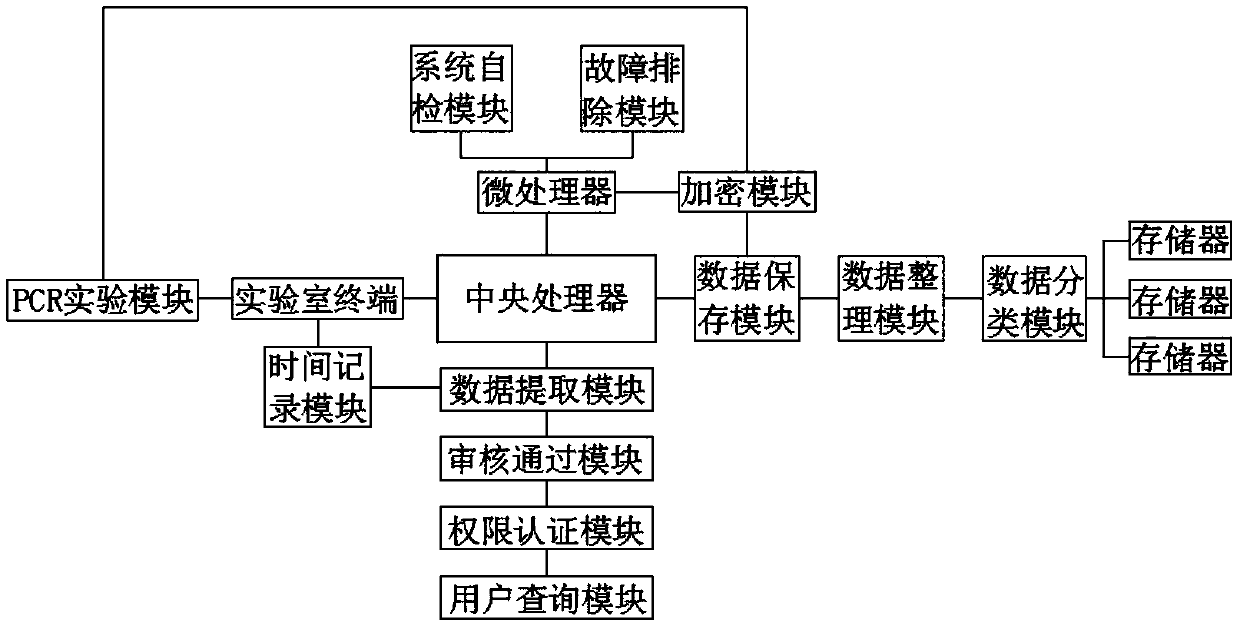
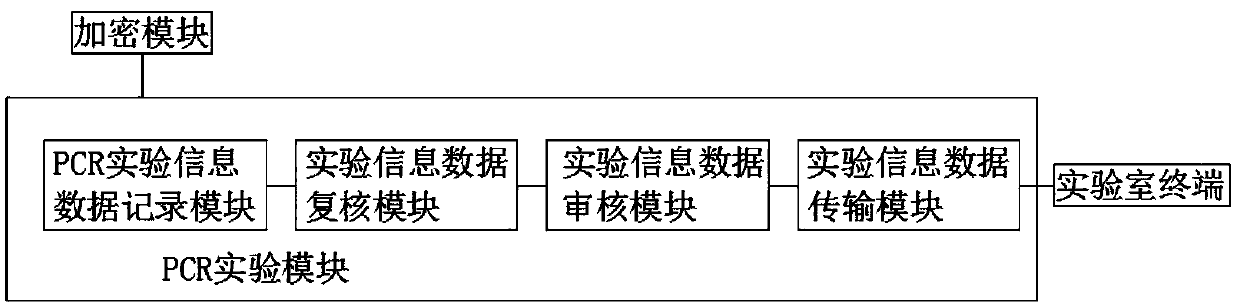
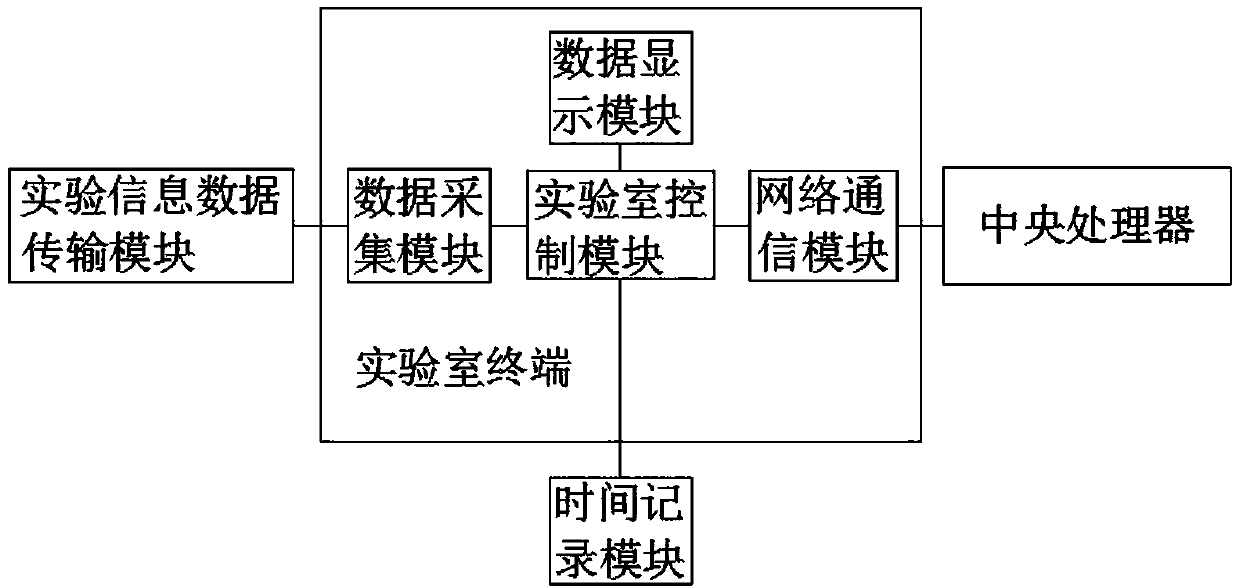
An intelligent system for laboratory management of PCR inspection records
PendingCN109558430AEasy to operateEncryption guaranteedDatabase management systemsDigital data protectionReal time displayEncryption
The invention relates to the technical field of laboratory management, in particular to an intelligent system for laboratory management of PCR inspection records. The system includes a central processing unit, the central processing unit is arranged in a laboratory management center; the central processing unit is electrically connected with a laboratory terminal; the laboratory terminal is electrically connected with a PCR experiment module; wherein the central processing unit is electrically connected with a data extraction module, the data extraction module is electrically connected with anaudit passing module, the audit passing module is electrically connected with an authority authentication module, the authority authentication module is electrically connected with a user query module, the laboratory terminal is electrically connected with a time recording module, and the time recording module is electrically connected with the data extraction module. The intelligent system for laboratory management of PCR inspection records is convenient to use and operate, orderly proceeding of experiments and real-time display of experiment data can be guaranteed due to the existence of the PCR experiment module, and meanwhile, the system can guarantee the encryption of the experiment data and orderly classified storage of the data.
Owner:GUANGDONG SOURCE OF WISDOM INFORMATION TECH CO LTD
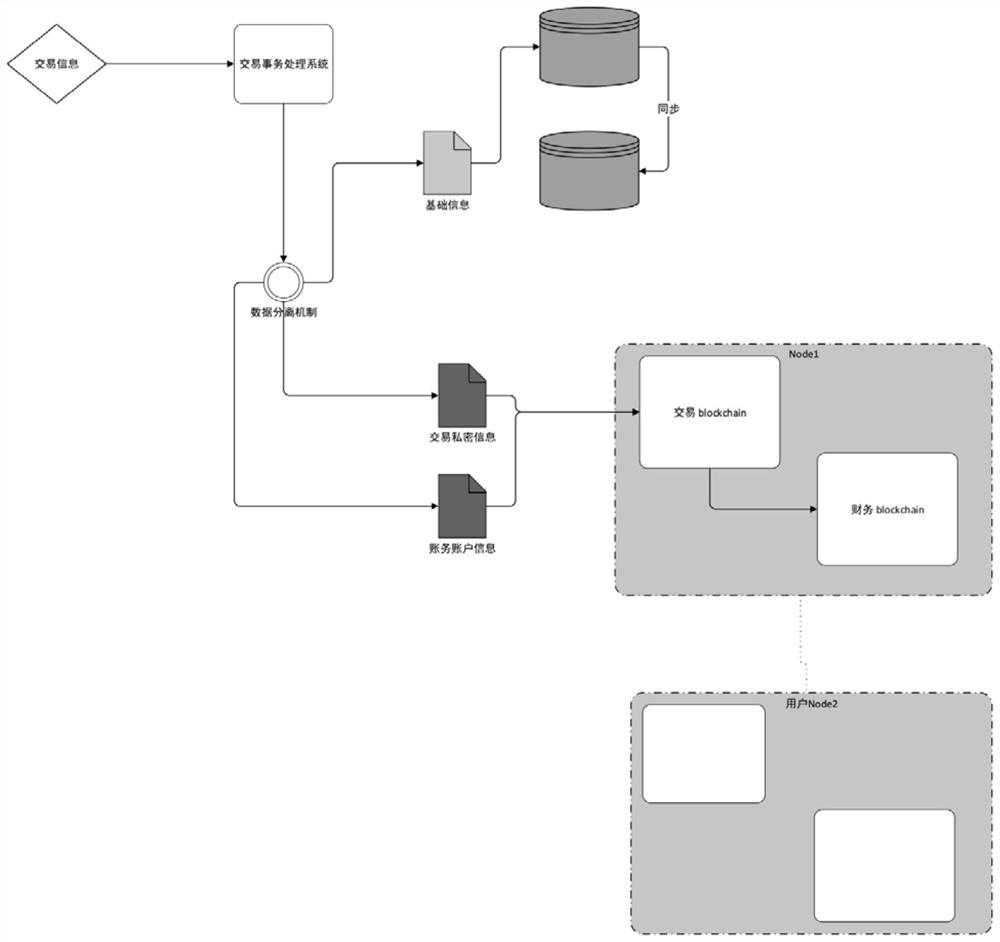
Transaction information storage and financial storage method based on traditional data and block chain
PendingCN112633881AEnsure safetyEncryption guaranteedDatabase distribution/replicationDigital data protectionFinancial transactionData store
The invention discloses a transaction information storage and financial storage method based on traditional data and a block chain, which separates data in a transaction system and separately stores the data according to related software security and a data level protection system. According to the invention, data in a transaction system is separated, and the data is separately stored according to related software security and a data level protection system. The high concurrency performance during transaction is ensured, and the encryption during data storage and the security of a financial system are also ensured.
Owner:中付(深圳)技术服务有限公司
A hydrogen energy vehicle vehicle network system
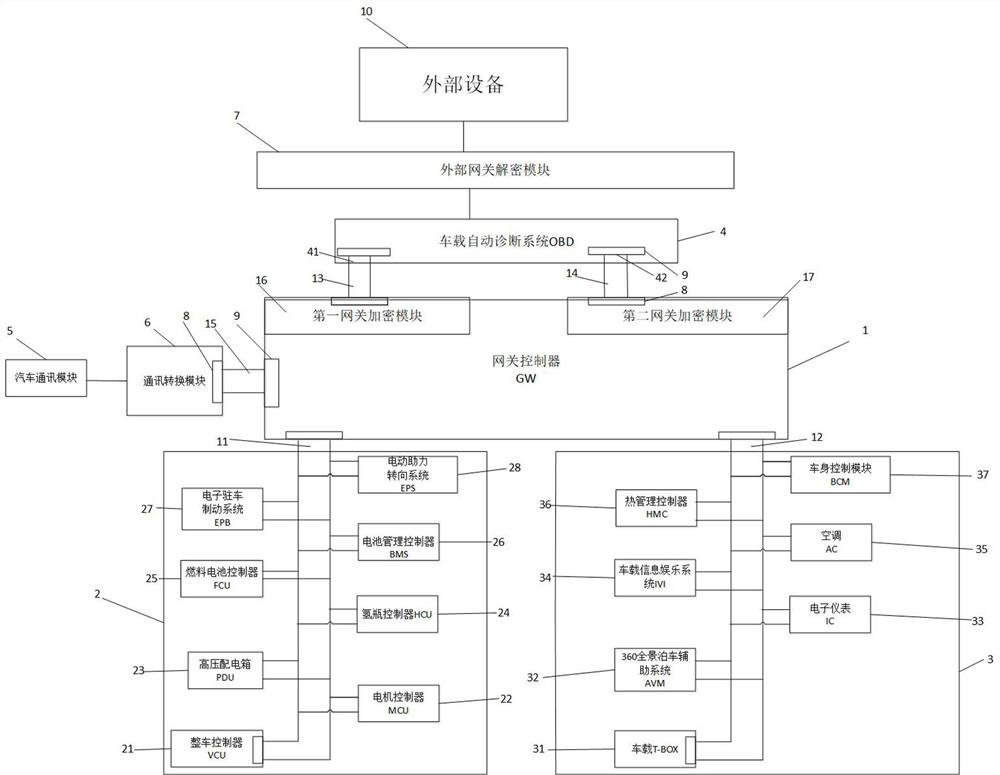
ActiveCN112422392BRealize functionReliable and secure network architectureNetwork connectionsBus networksIn vehicleNetworked system
The invention provides a whole vehicle network system for hydrogen energy vehicles, including a gateway controller, a vehicle brake module, a vehicle management module and an on-board automatic diagnosis system, wherein the gateway controller includes a first CAN network, a second CAN network, a third CAN network, and a third CAN network. The CAN network, the fourth CAN network, the first gateway encryption module and the second gateway encryption module, the input end of the first gateway encryption module is electrically connected to the first CAN network, and the output end of the first gateway encryption module is connected to the first gateway encryption module. The three CAN networks are electrically connected, the input terminal of the second gateway encryption module is electrically connected to the second CAN network, the output terminal of the second gateway encryption module is electrically connected to the fourth CAN network, and the vehicle brake module is electrically connected to the third CAN network. A CAN network is electrically connected, the vehicle management module is electrically connected to the second CAN network, the vehicle-mounted automatic diagnosis system includes a sixth CAN network and a seventh CAN network, the sixth CAN network is electrically connected to the third CAN network, The seventh CAN network is electrically connected to the fourth CAN network.
Owner:WUHAN GROVE HYDROGEN AUTOMOBILE CO LTD
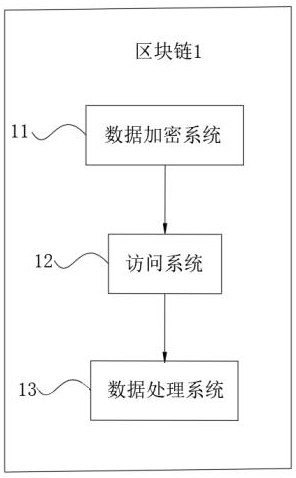
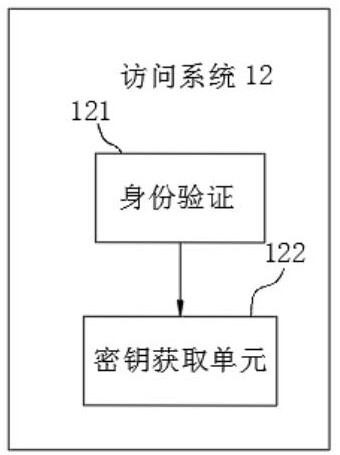
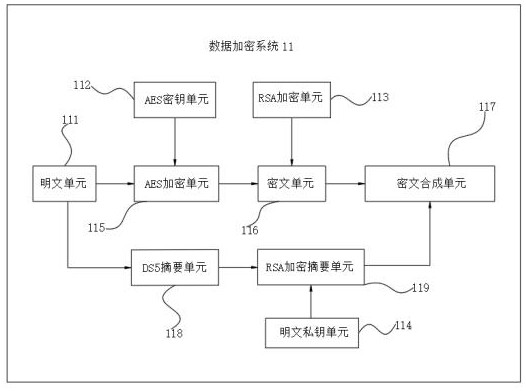
Data encryption system for block chain
InactiveCN112380558AEncryption guaranteedRealize two-way protection functionDigital data protectionComputer hardwareCiphertext
The invention discloses a data encryption system for a block chain, and the system is characterized in that the output end of a first plaintext unit is electrically connected with the input end of anAES encryption unit, the output end of a first AES key unit is electrically connected with the input end of the AES encryption unit, the output end of the AES encryption unit is electrically connectedwith the input end of a first ciphertext unit, the output end of the RSA encryption unit is electrically connected with the input end of the first ciphertext unit, the output end of the first plaintext unit is electrically connected with the input end of the first DS5 abstract unit, and the output end of the first DS5 abstract unit is electrically connected with the input end of the RSA encryption abstract unit. The invention relates to the technical field of data encryption. According to the data encryption system for the block chain, the problem that when traditional data is uploaded, single encryption protection is conducted on the data, but in the method, when the identity of a data sending party or a data receiving party is pretended or forged by others to destroy encryption of the data, the data can be tampered or deleted or lost in the transmission process is solved.
Owner:东莞市莞云信息科技有限公司
Underwater communication equipment with encryption and decryption capabilities, transmitter and receiver
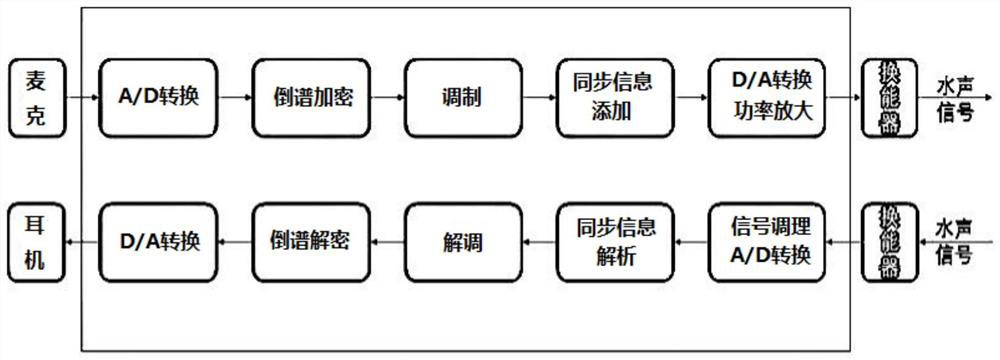
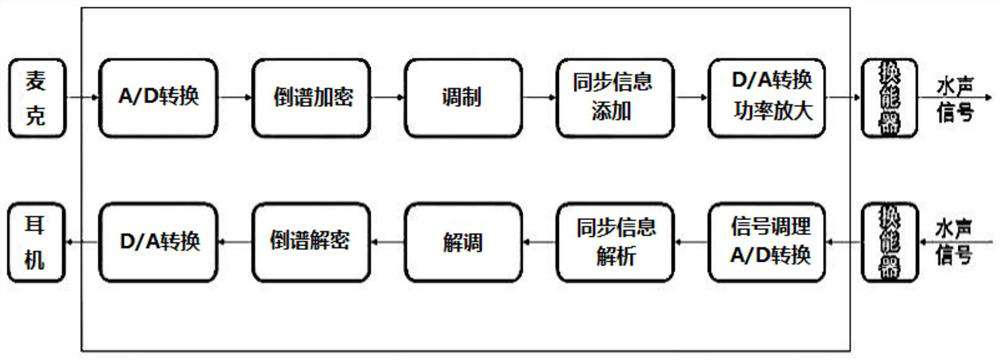
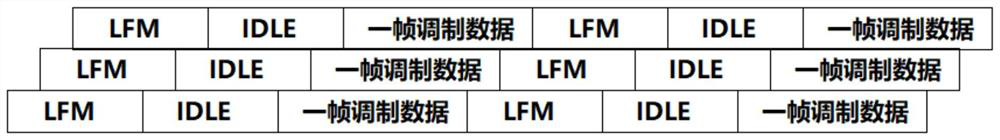
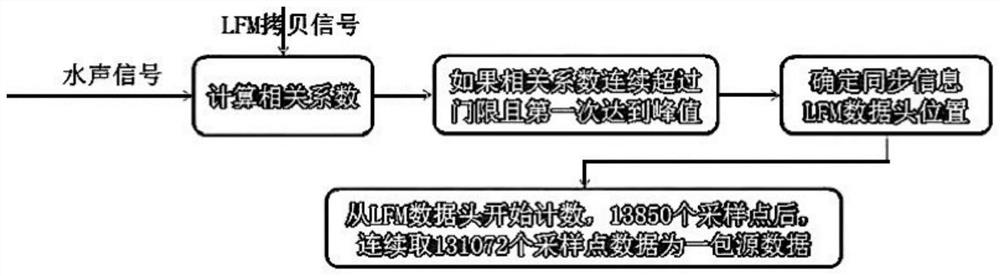
ActiveCN111711493AImplement encryptionEncryption guaranteedSonic/ultrasonic/infrasonic transmissionSynchronisation receiversComputer hardwareSignal conditioning circuits
The invention relates to underwater communication equipment with encryption and decryption capabilities, a transmitter and a receiver. The underwater communication equipment comprises a transmitting unit and a receiving unit, and the transmitting unit comprises a first A / D conversion module, a cepstrum encryption module, a modulation module, a first D / A conversion module and a transmitting transducer which are connected in sequence; and the receiving unit comprises a receiving transducer, a signal conditioning circuit, a second A / D conversion module, a demodulation circuit, a cepstrum decryption module and a second D / A conversion module which are connected in sequence. According to the invention, underwater analog communication encryption can be effectively realized.
Owner:THE THIRD RES INST OF CHINA ELECTRONICS TECH GRP CORP
A secure underwater transmission method supporting obfuscation and zero-knowledge
ActiveCN107426176BIntegrity guaranteedEncryption guaranteedUser identity/authority verificationNeighbour discoveryRelevant information
The invention discloses a security underwater transmission method capable of supporting confusion and zero knowledge. The method includes following steps: (1) an initialization stage: a gateway GW generates key materials and distributes the key materials to an underwater vehicle A and an underwater vehicle B; (2) a neighbor discovery stage: the underwater vehicle A and the underwater vehicle B generate and broadcast temporary identities when the two underwater vehicles meet underwater; and (3) a data transmission stage: a sending party firstly generates primary identity information of both parties, performs data encryption and signature, and sending related information to a receiving party; and the receiving party receives the information, verifies whether the receiving party is a correct receiving party, then calculates the temporary identity of the sending party, and decrypts and verifies the received data. According to the method, opponents can be prevented from detecting the related information of the underwater vehicle or counting, and the problem of the conventional underwater wireless communication is solved.
Owner:SOUTHEAST UNIV
Blockchain uploading method for preventing data tampering
ActiveCN113326504AIntegrity guaranteedEncryption guaranteedDigital data protectionDigital data authenticationComplete dataProtection mechanism
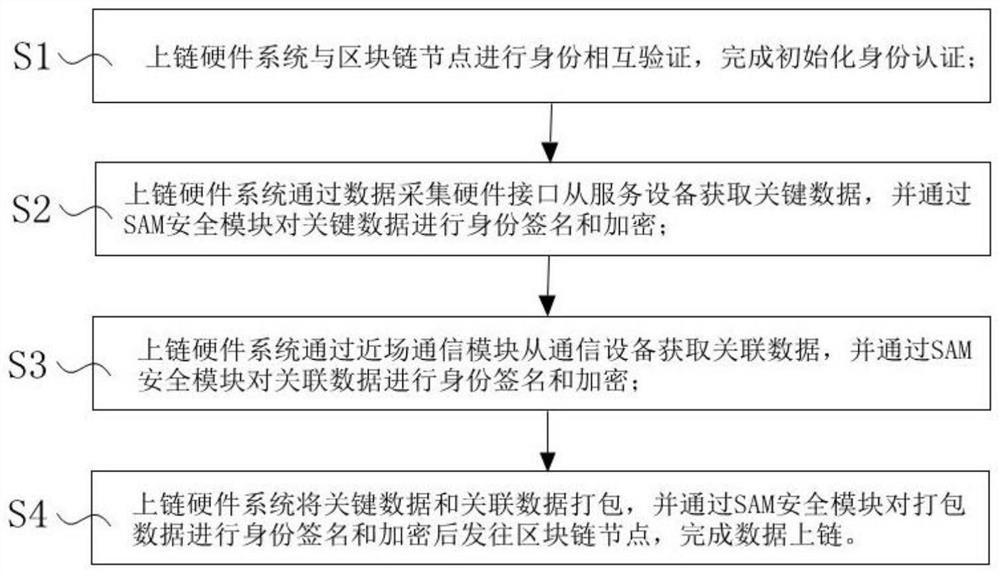
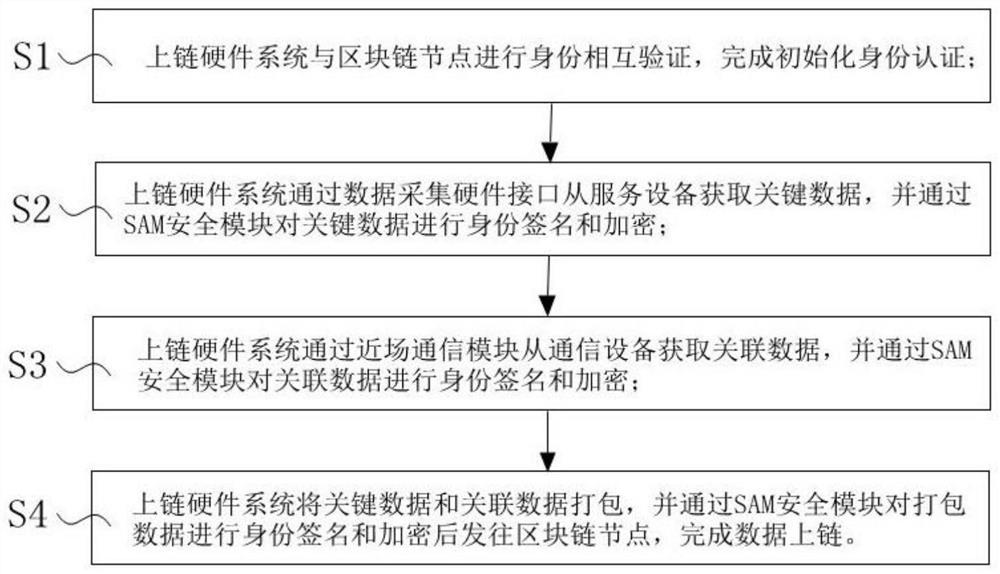
The invention discloses a data tampering prevention blockchain uplink method, and the method comprises the following steps that S1, an uplink hardware system and a blockchain node carry out identity mutual verification, and initialized identity authentication is completed; S2, the uplink hardware system obtains the key data from the service equipment through the data acquisition hardware interface, and performs identity signature and encryption on the key data; S3, the uplink hardware system obtains the associated data from the communication device through the near field communication module, and performs identity signature and encryption on the associated data; S4, the uplink hardware system packages the key data and the associated data, performs identity signature and encryption on the packaged data, and sends the packaged data to the block chain node to complete data uplink. According to the method disclosed by the invention, the key data is ensured to pass through the verification and protection mechanism of the uplink hardware system before being uplink, and is directly uplink on the block chain node, so that the risk that the data is maliciously modified before being uplink through other service platforms is avoided, and the integrity and encryption of the uplink data are ensured.
Owner:厦门致联科技有限公司
Underwater communication equipment, transmitter and receiver with encryption and decryption capabilities
ActiveCN111711493BImplement encryptionEncryption guaranteedSonic/ultrasonic/infrasonic transmissionSynchronisation receiversComputer hardwareSignal conditioning circuits
The invention relates to an underwater communication device with encryption and decryption capabilities, a transmitter and a receiver, including a transmitting unit and a receiving unit, and the transmitting unit includes a sequentially connected first A / D conversion module, a cepstrum encryption module, a modulation module, a first D / A conversion module and a transmitting transducer; the receiving unit includes a receiving transducer connected in sequence, a signal conditioning circuit, a second A / D conversion module, a demodulation circuit, a cepstrum decryption module and a first Two D / A conversion modules. The invention can effectively realize underwater analog communication encryption.
Owner:THE THIRD RES INST OF CHINA ELECTRONICS TECH GRP CORP
Information security management method and system for internet of things based on combinatorial encryption algorithm
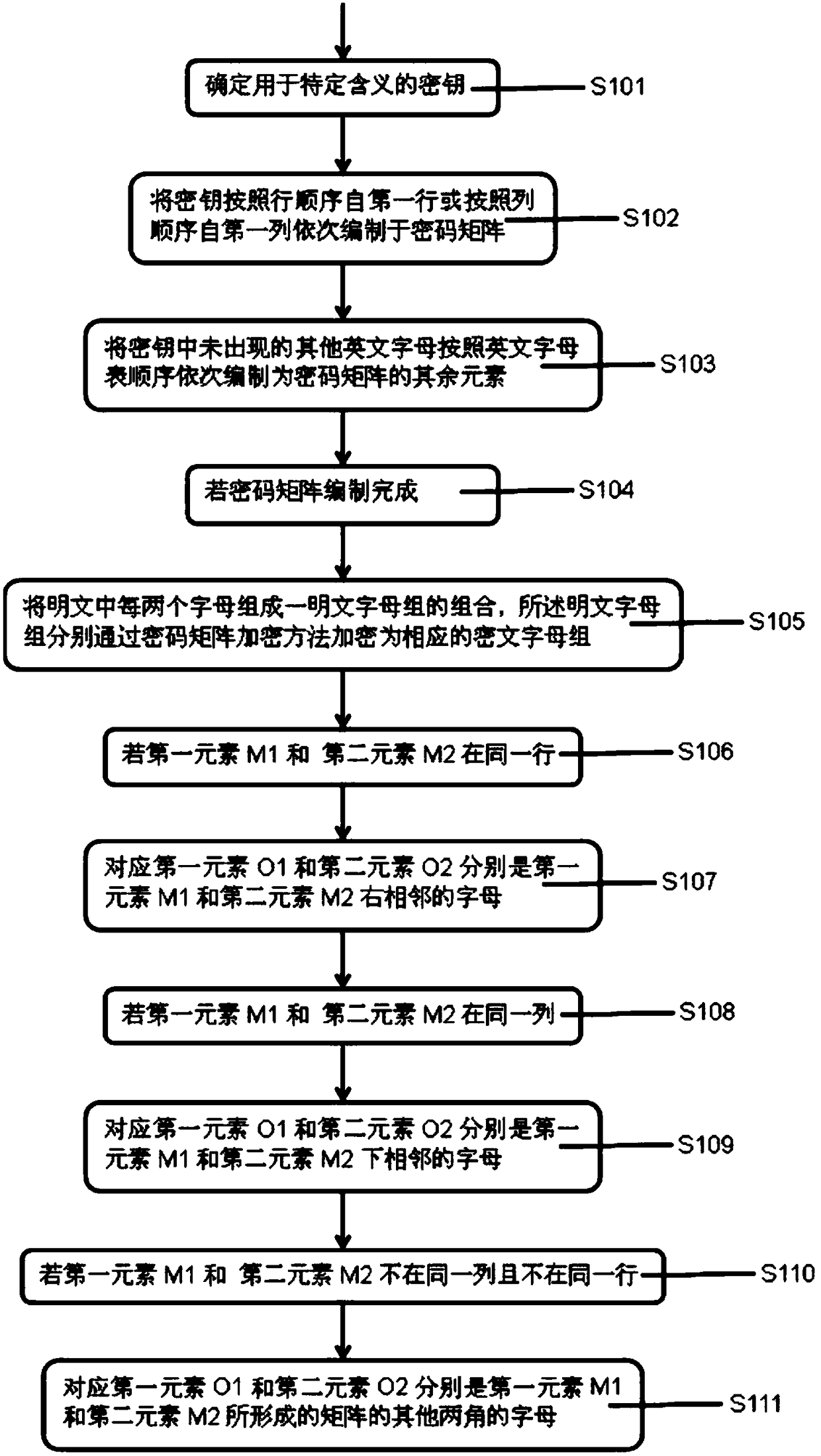
InactiveCN109257175AImprove security strengthImprove confidentialityMultiple keys/algorithms usageEncryption apparatus with shift registers/memoriesInternet of ThingsSafety management systems
The invention belongs to the technical field of information security, in particular to an information security management method for the Internet of Things based on a combined encryption algorithm, the invention also provides an information security management system of the internet of things based on a combined encryption algorithm; the cryptographic matrix encryption method comprises the following steps: if the first element M1 and the second element M2 are in the same row, the corresponding first element O1 and the second element O2 are letters adjacent to the right of the first element M1and the second element M2, respectively.As that exist encryption method is relatively simple, when the password is attacked by force, the encryption key can be decrypted quickly by exhausting the limited number of times directly, which leads to the problem of poor information security. The invention has the advantages of enhancing the information security intensity, facilitating the memory and easy storage, ensuring the integrity of ciphertext, and ensuring the flexibility of encryption.
Owner:CHANGSHU INSTITUTE OF TECHNOLOGY +1
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com