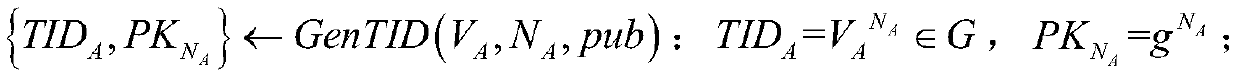A secure underwater transmission method supporting obfuscation and zero-knowledge
A transmission method and zero-knowledge technology, applied in transmission systems, digital transmission systems, secure communication devices, etc., can solve problems such as lack of encryption primitives, uncertainty of aircraft information and number, etc., and achieve integrity and encryption Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0022] The present invention will be further described below in conjunction with the accompanying drawings.
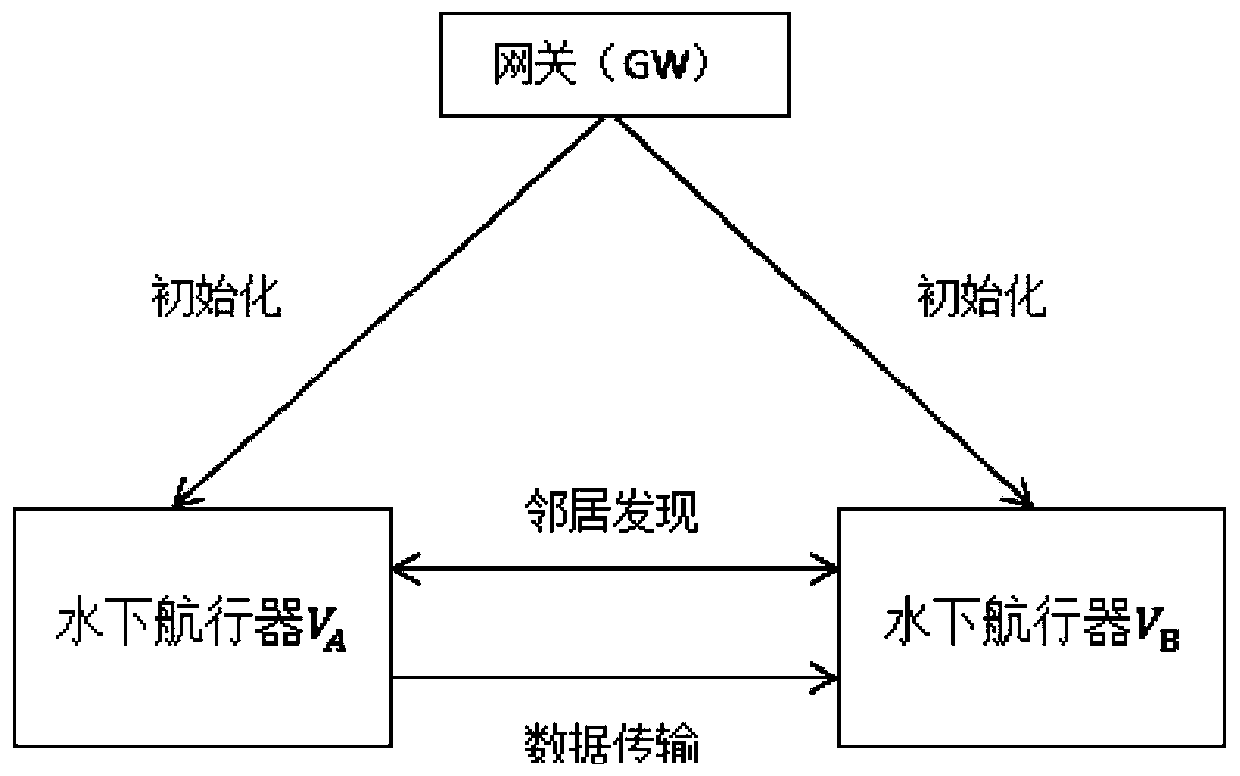
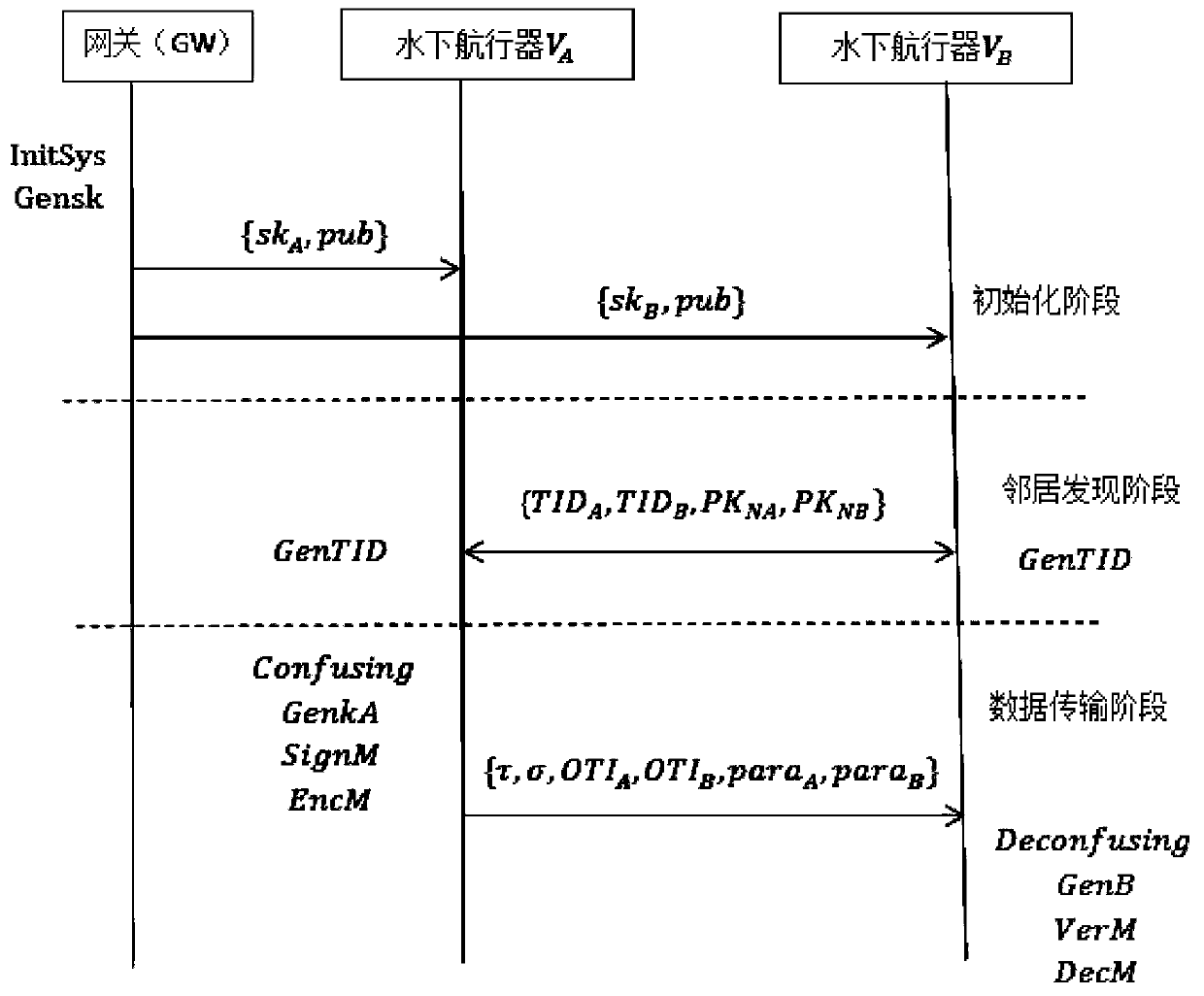
[0023] Such as figure 1 , figure 2 Shown is a secure underwater transmission method that supports confusion and zero-knowledge, including three entities, namely gateway GW, underwater vehicle A and underwater vehicle B; the method includes three main stages, namely initialization phase, neighbor discovery phase, and data transfer phase. The implementation process of the three entities in the three stages will be described in detail below.
[0024] (1) Initialization stage: the gateway GW generates its own private key sk GW , public password parameter pub, underwater vehicle A private key sk A and underwater vehicle B private key sk B , and distribute to underwater vehicle A and underwater vehicle B through a pre-established secure channel, so that underwater vehicle A and underwater vehicle B have their own key materials.
[0025] Step (101): The gateway GW uses...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com