Data encrypting method and encrypted data transmitting device
A technology for encrypting data and data, applied in the field of data transmission, can solve problems such as difficult mathematical algorithms, difficult security, difficult data transmission, etc., and achieve the effects of high encryption security, excellent data compression ability and random encryption ability
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
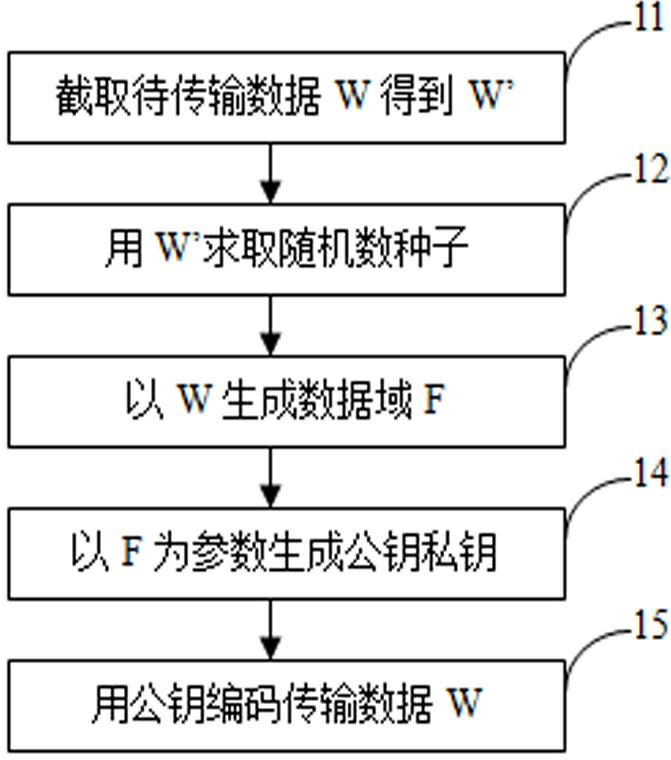
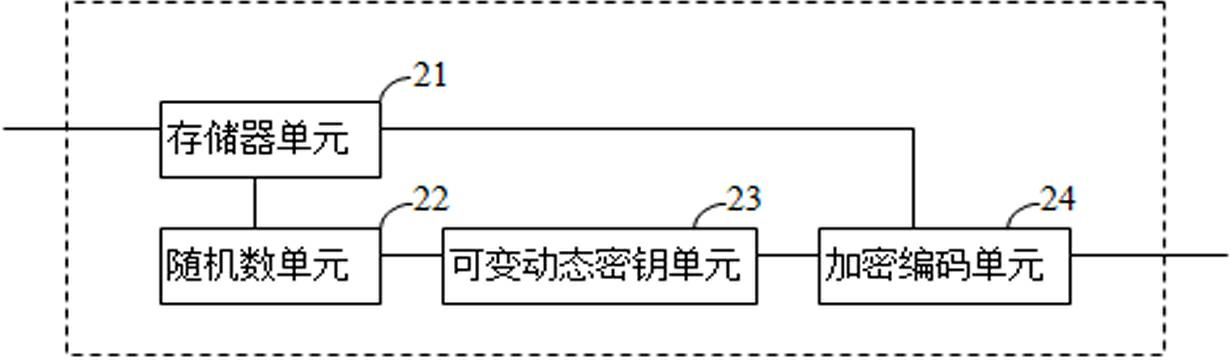
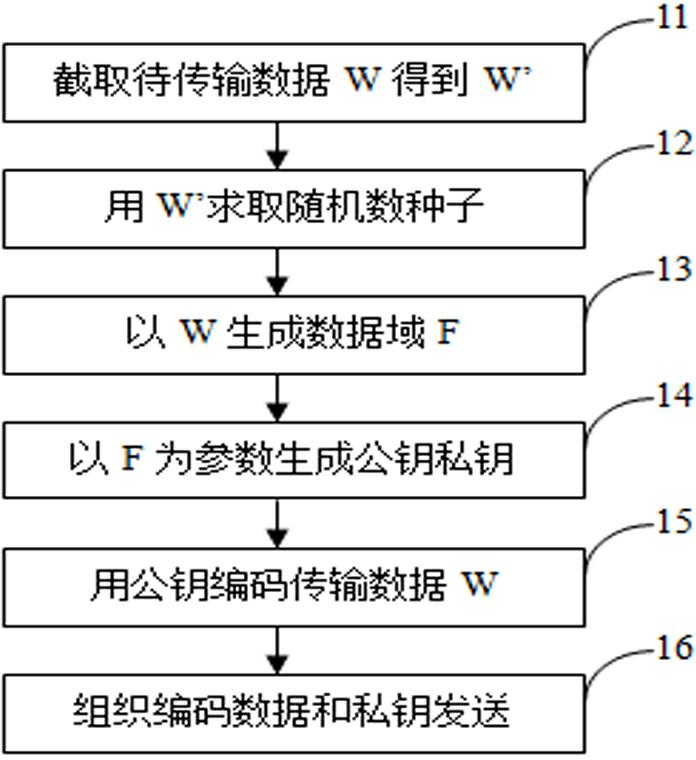
[0039] first reference figure 1 the examples. According to this embodiment, we know that data encryption adopts variable and random dynamic encryption means. First, in step 11, the transmission data W to be encrypted is read into the memory or cache of the computer system at one time or in the form of data flow, and W is used as the basis for generating the encryption key. However, the length of W is uncertain, and simply using W as the basis for key generation will make the consumption of computing resources uncertain, thus making the performance of products applying this method unstable. Therefore, this example adopts a relatively Optimizing practices. The method is to set a constant k in advance, randomly intercept the data W' of predetermined length k from the transmission data W, and use W' as the basis of the encryption key. In general applications, the length of W is usually greater than k. At this time, the acquisition of W' is an interception operation, and the sta...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com