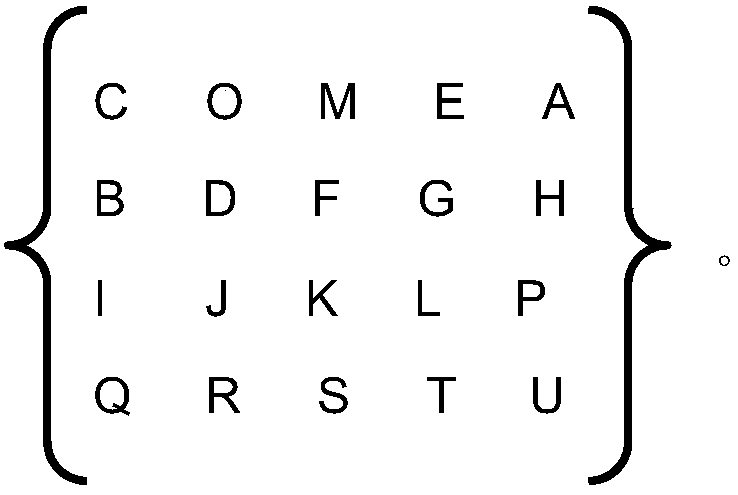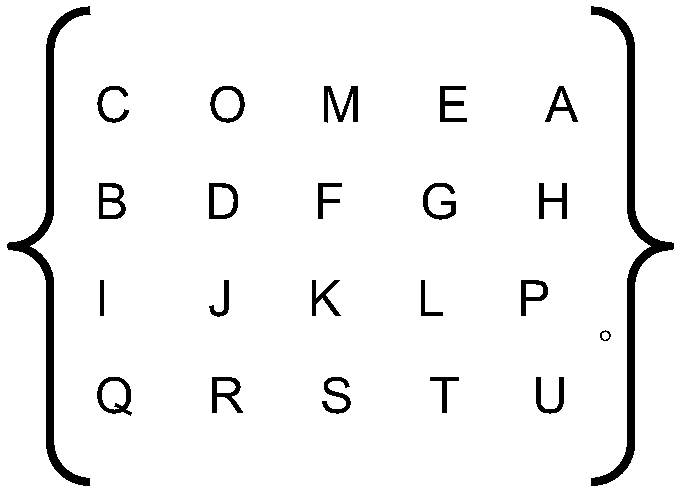Information security management method and system for internet of things based on combinatorial encryption algorithm
An encryption algorithm and information security technology, which is applied in the field of information security management of the Internet of Things based on the combined encryption algorithm and the information security management system of the Internet of Things based on the combined encryption algorithm, can solve problems such as poor information security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
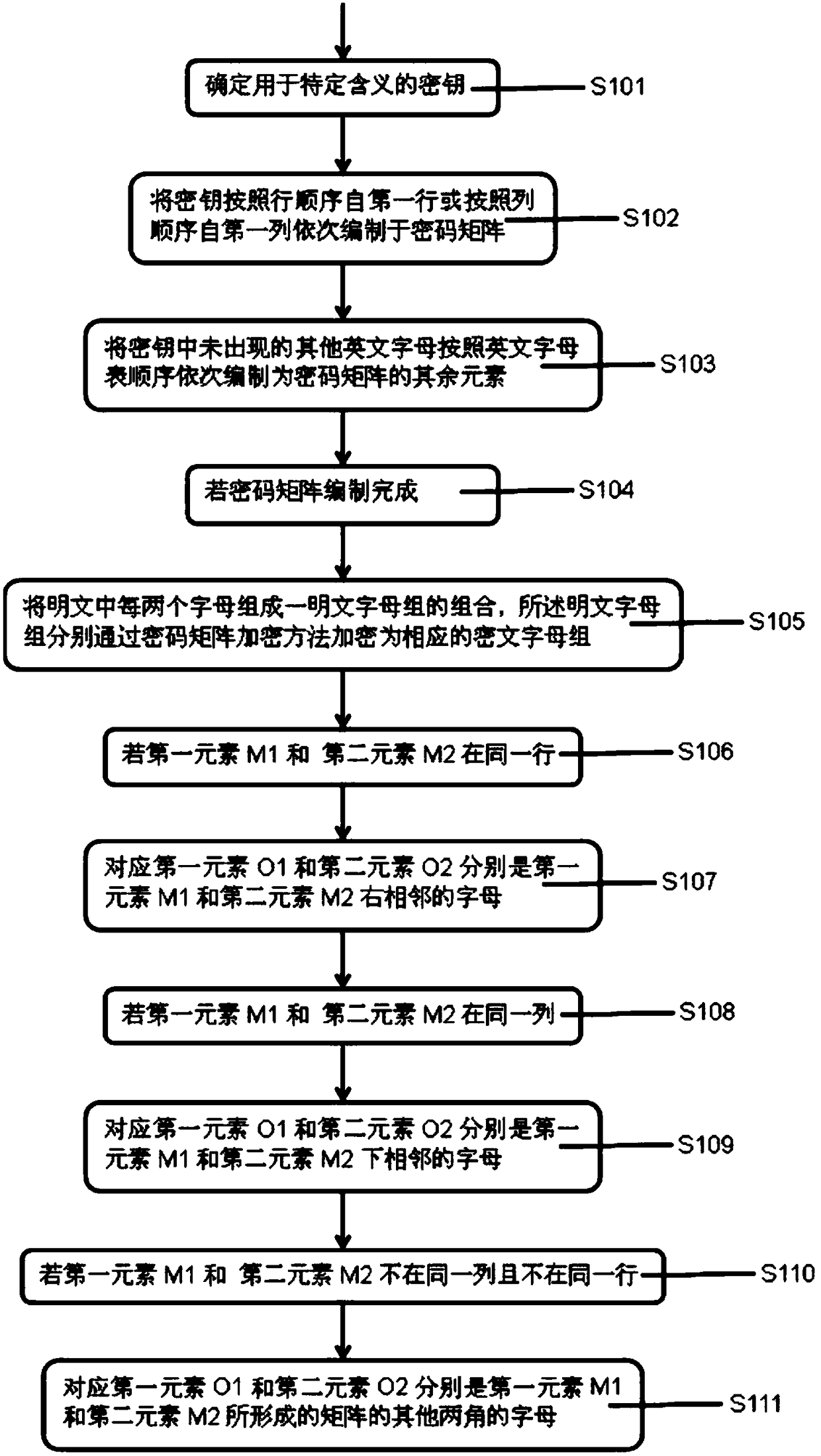
[0066] This embodiment: as figure 1 As shown, a method for information security management of the Internet of Things based on a combined encryption algorithm includes:
[0067] Determine the key S101 for a specific meaning;
[0068] Compile the key into the password matrix S102 sequentially from the first row according to the row order or from the first column according to the column sequence, and compile other English letters that do not appear in the key into the remaining elements of the password matrix according to the English alphabet order S103;
[0069] If the password matrix is prepared S104, then every two letters in the plaintext form a combination of a plaintext alphabet, and the plaintext alphabet is encrypted into a corresponding ciphertext alphabet S105 by the password matrix encryption method;
[0070] The plaintext letter group includes a first element M1 and a second element M2;
[0071] The ciphertext alphabet includes a first element O1 and a second elem...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com