Method and device for constructing sequential cipher
A technology of sequence cipher and structure, applied in the field of cipher, it can solve problems such as incomprehension and incomprehension, and achieve the effect of high security strength
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
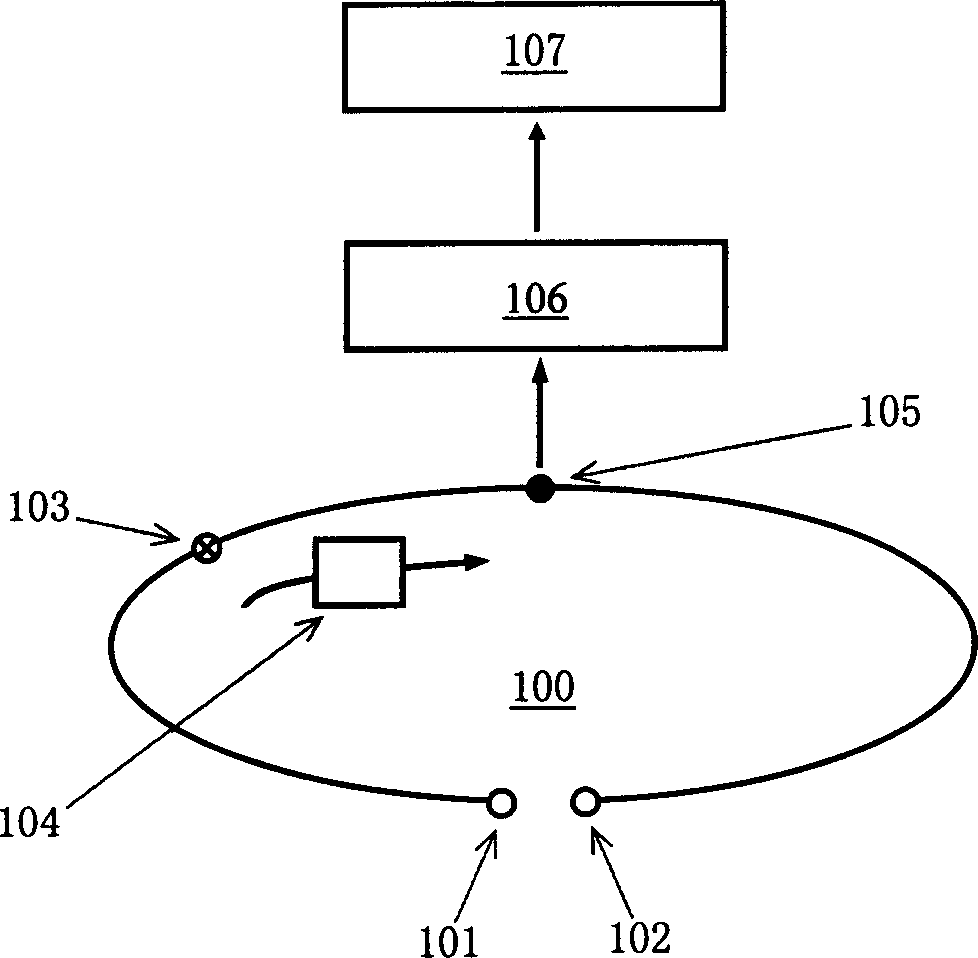
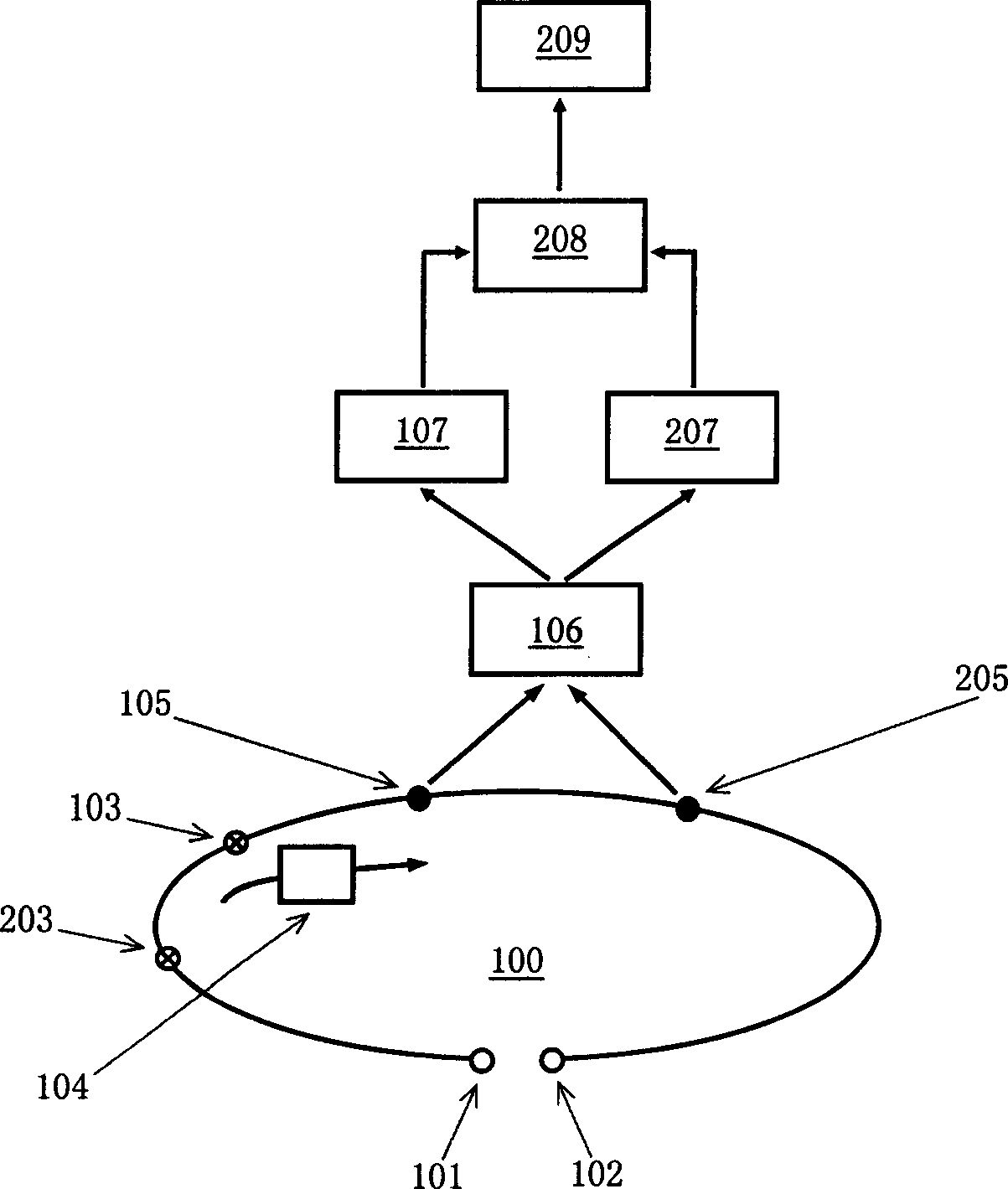
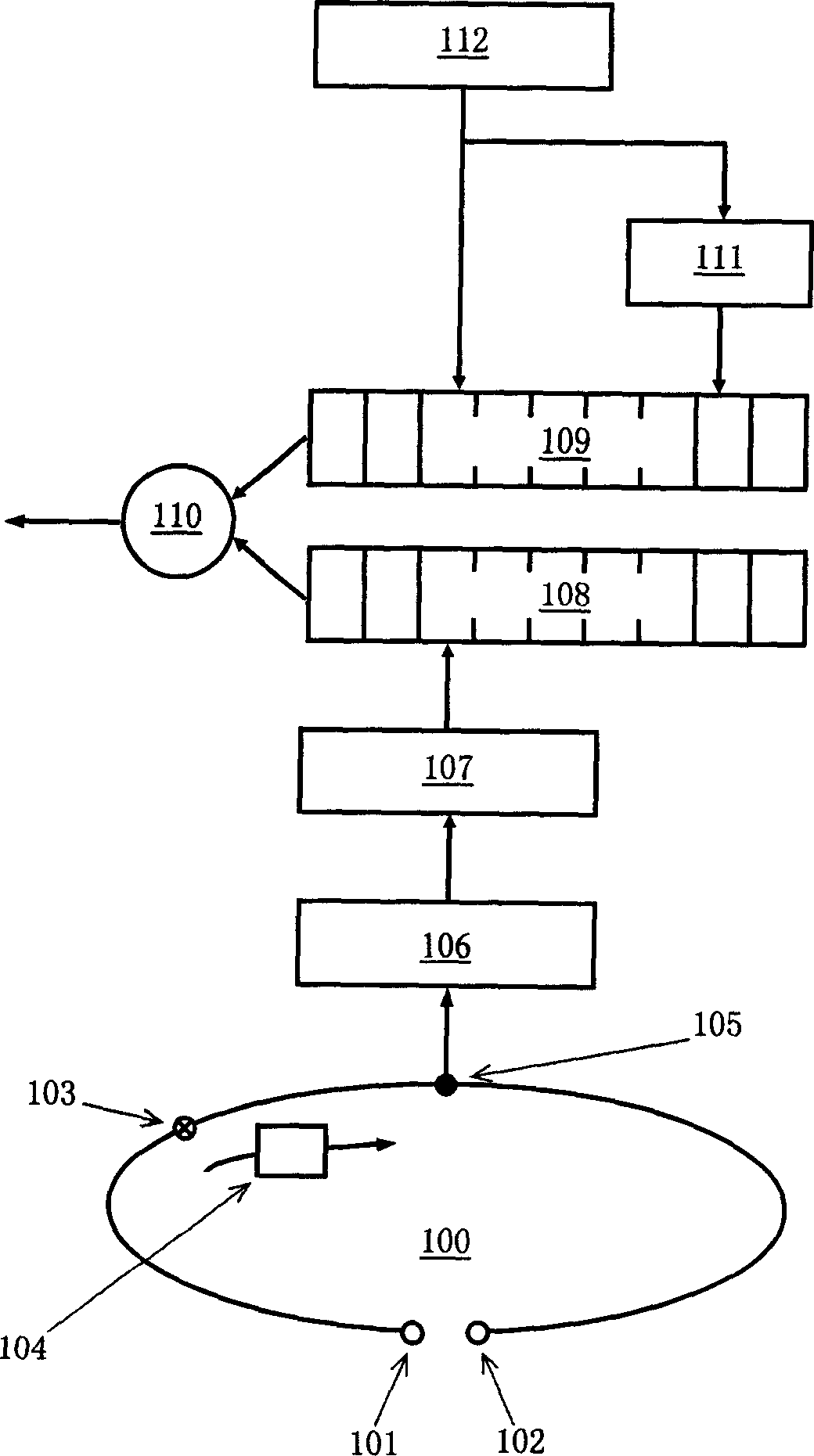
[0018] What the present invention considers is a method and device for constructing sequence ciphers; its main content is a method and device for key sequence generation, or more broadly understood as a method and device for generating pseudo-random numbers. In view of well-known reasons, the present invention does not explicitly define or explain certain terms, nouns and expressions used, such as: sender, receiver, encryption, decryption, password, XOR, one-way hash function (One-way hash function), hash function (Hashfunction), bit, bit, number expression, etc. For some specific nouns, follow the meanings described or defined in the present invention, such as: root key space, current root key, current frame key, root key, frame key, seed, step, step size, "Double" or "Multiple" key synthesis methods, etc.
[0019] In the present invention, the basic steps required by the method and device for generating the key sequence are:
[0020] 1) The sender and receiver secretly or ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com