Blockchain uploading method for preventing data tampering
A data tampering and blockchain technology, applied in the blockchain field, can solve problems such as malicious modification of data, and achieve the effect of meeting business needs, ensuring integrity and encryption
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
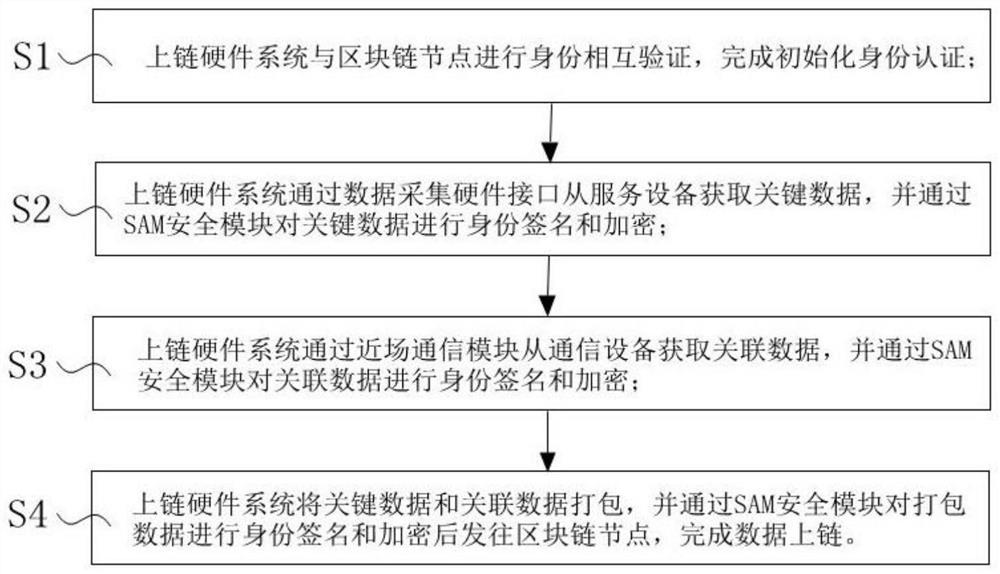
[0023] like figure 1 , The block chain winding method of preventing data tampering, the method implemented by the hardware chain, said chain comprising a housing system hardware, CPU, Internet access module, data acquisition hardware interfaces, a near field communication module, the SAM the security module, the special data area A DT And hardware tamper module housing, the method includes the following steps:
[0024] Sl, chain systems and the hardware block chain mutual authentication node identification, authentication initialization is completed; the upper strand is connected by a hardware system with block chain 4G node. The near field communication module NFC, Bluetooth, Zigbee, one kind of 433M or 2.5G.
[0025] The process is as follows: on each of the chain block is assigned a unique hardware serial number block chain link ID is the serial number from the ID block chains 8-byte random number ID RQ +16 bytes directly fixed ID value CQ Composition prior to complete the init...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com