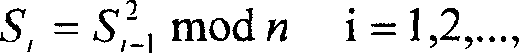Data encipher and decipher system based on dynamic variable-length code
A technology of variable length code and system state, applied in the field of information security in the field of information technology, can solve problems such as difficulties, and achieve the effect of good security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0030] The content of the present invention will be further described below in conjunction with specific embodiments.
[0031] 1. Encryption and decryption equipment, including:
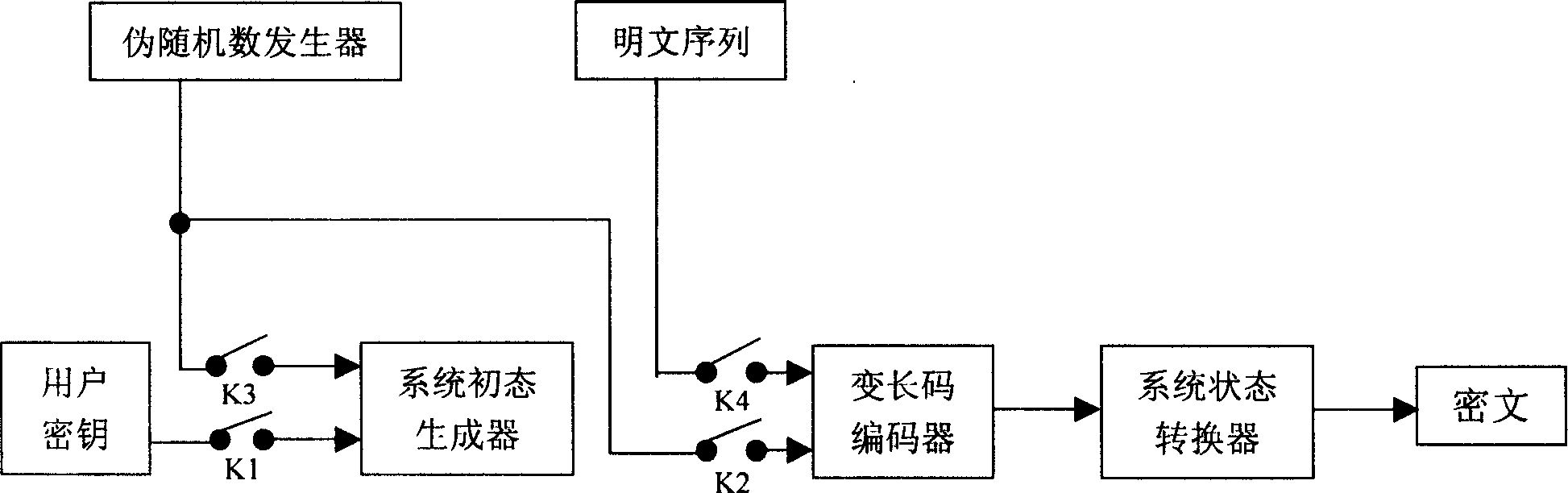
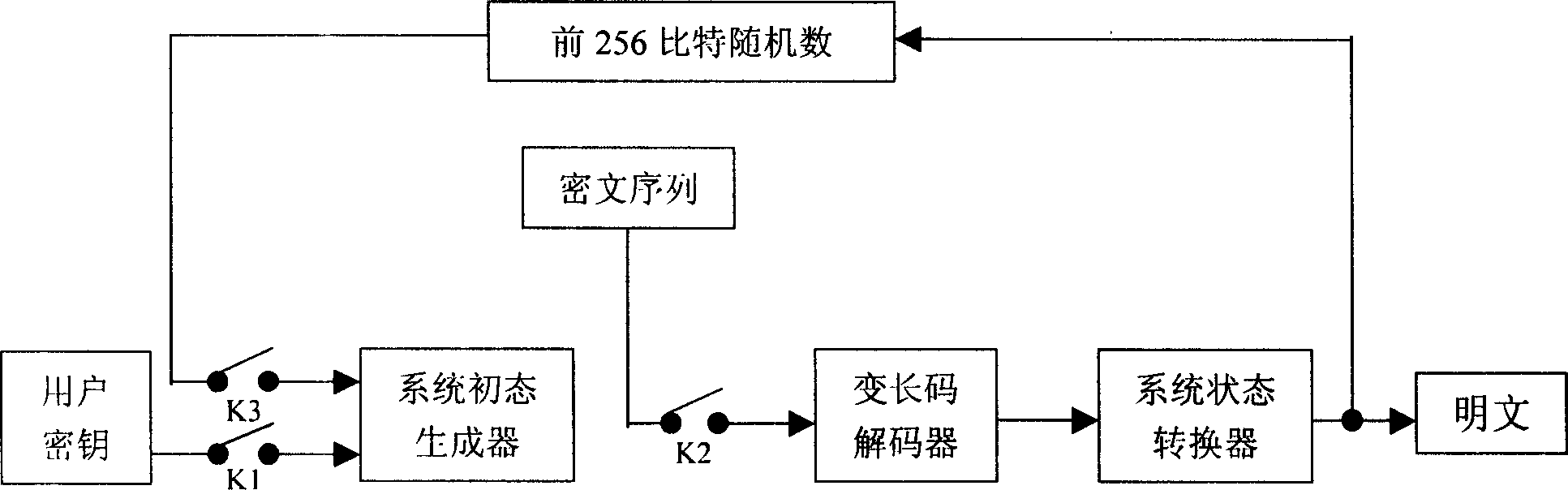
[0032] 1.1 System initial state generator: The automatic conversion of system state is the core of this system. The plaintext to be encrypted is a group of 8 bits, so there are 2 8 = 256 different characters, in order to illustrate the concept of "system state", first define the amount of "degree" of the character. The "degree" of a character (represented by the symbol D) is an amount related to the number of occurrences of the character in plaintext, and its initial value is determined by the user key. Every time a character appears, the D of the character increases by a certain value, and the increased value is determined by the D of the character at the previous moment. After the 256 characters are arranged according to their respective Ds from large to small, the sequence of the characters and...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com