Grouping encryption and decryption algorithm
A block encryption and algorithm technology, applied in digital transmission systems, electrical components, transmission systems, etc., can solve the problems of long ciphertext, increase ciphertext input time and operation amount, and achieve the effect of reducing time and operation amount
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
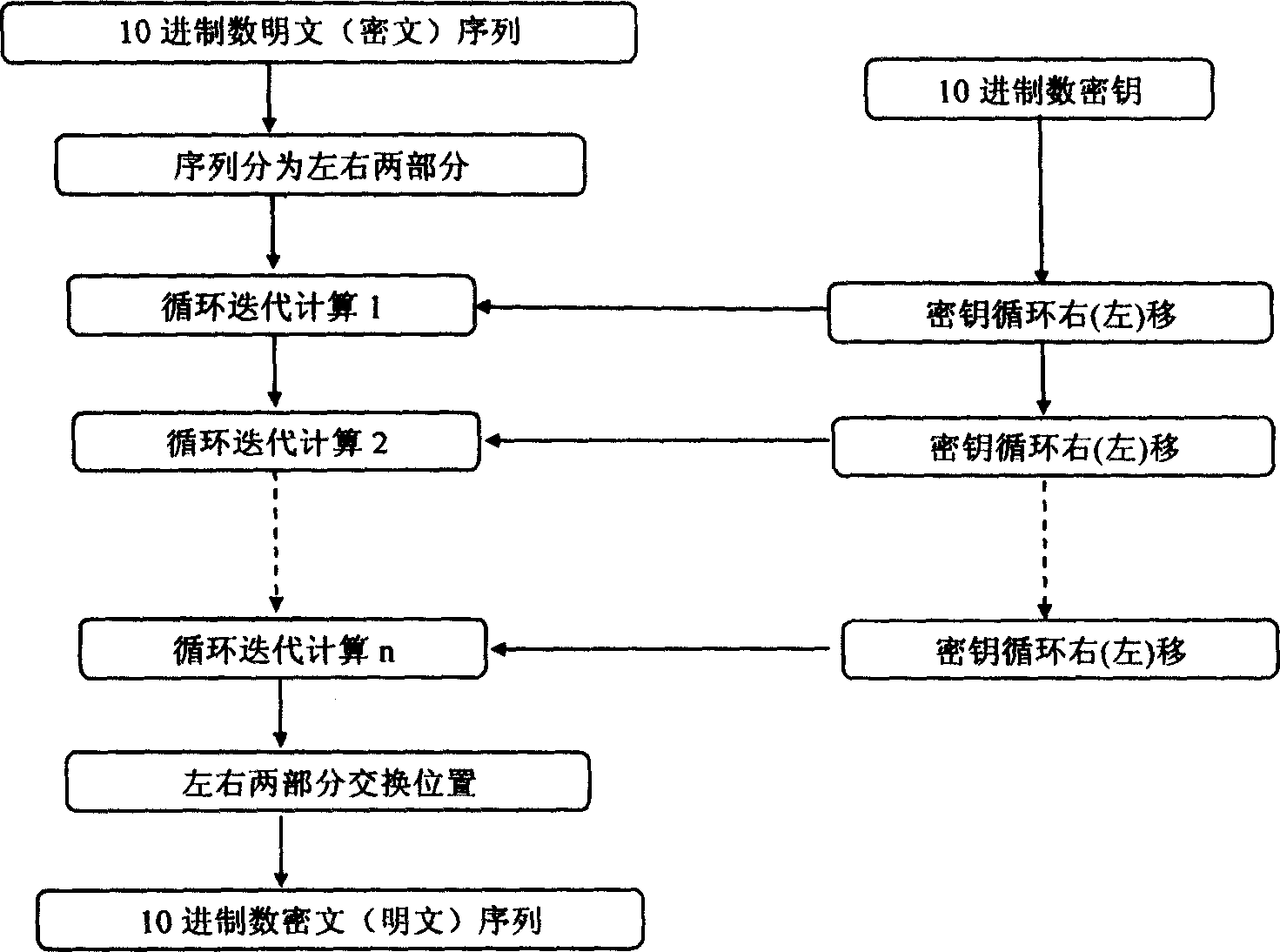
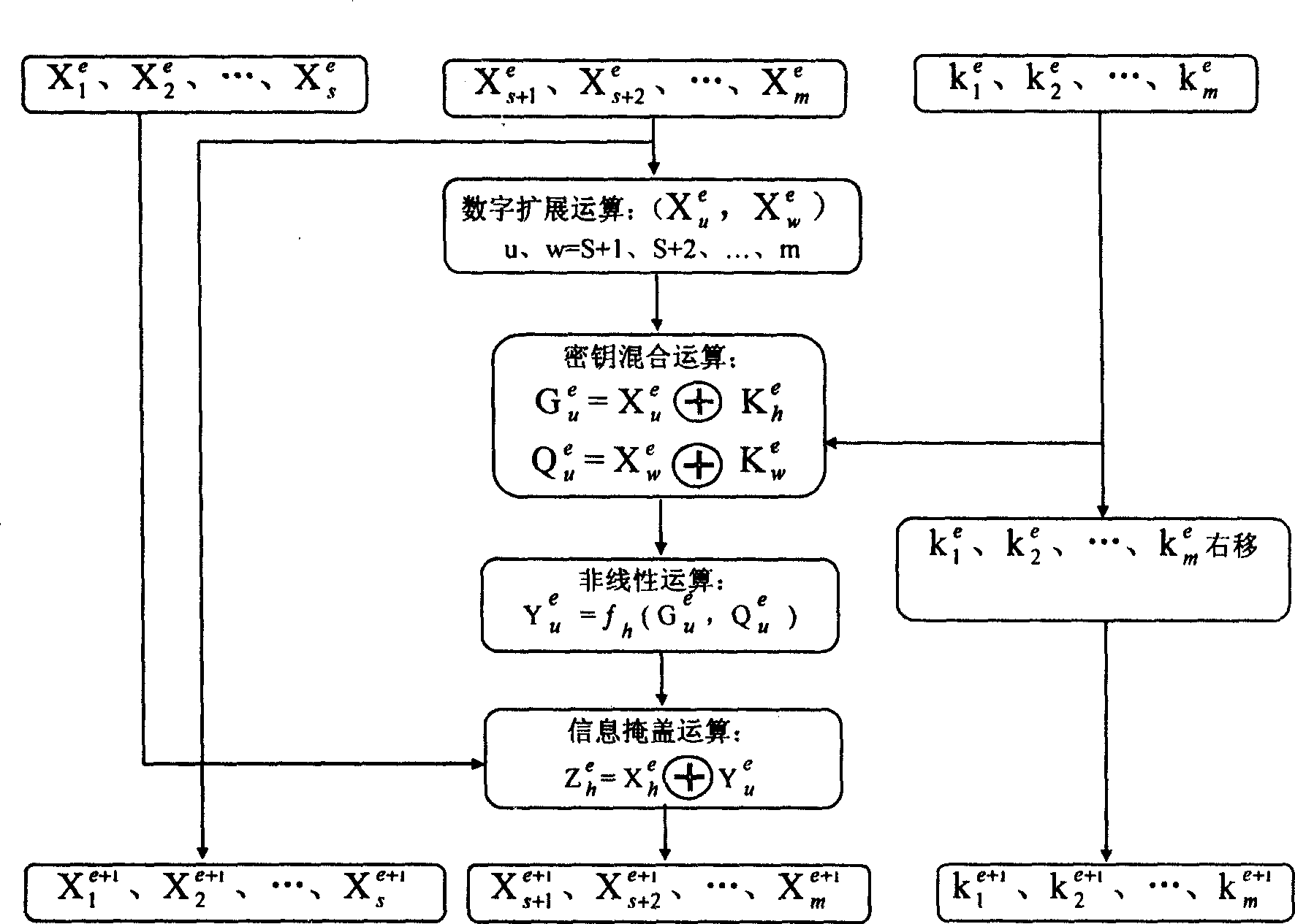
[0047] In the field of information security technology, the bill number sequence (plaintext) displayed by the decimal number is set as P here, and the specific operation process of the block encryption algorithm for the plaintext is as follows figure 2 As shown, it includes grouping operations on plaintext P, encryption loop iterative calculation, position transformation and output ciphertext, etc. The encryption loop iterative calculation includes six sub-operation processes, which are digital expansion operation, mixed operation of key and variable, nonlinear Transformation operation, information concealment operation, reassignment operation, and one-time key cycle right shift operation, the above operation processes are all existing technologies, the difference is that in this embodiment, the plaintext P is a set of decimal numbers P 1 ,P 2 ,...,P i ,...,P m , 0≤i≤m, and the number Pi takes one of the following a and b value ranges,
[0048] a. 0≤Pi ≤9
[0049] b. 0≤P ...
Embodiment 2
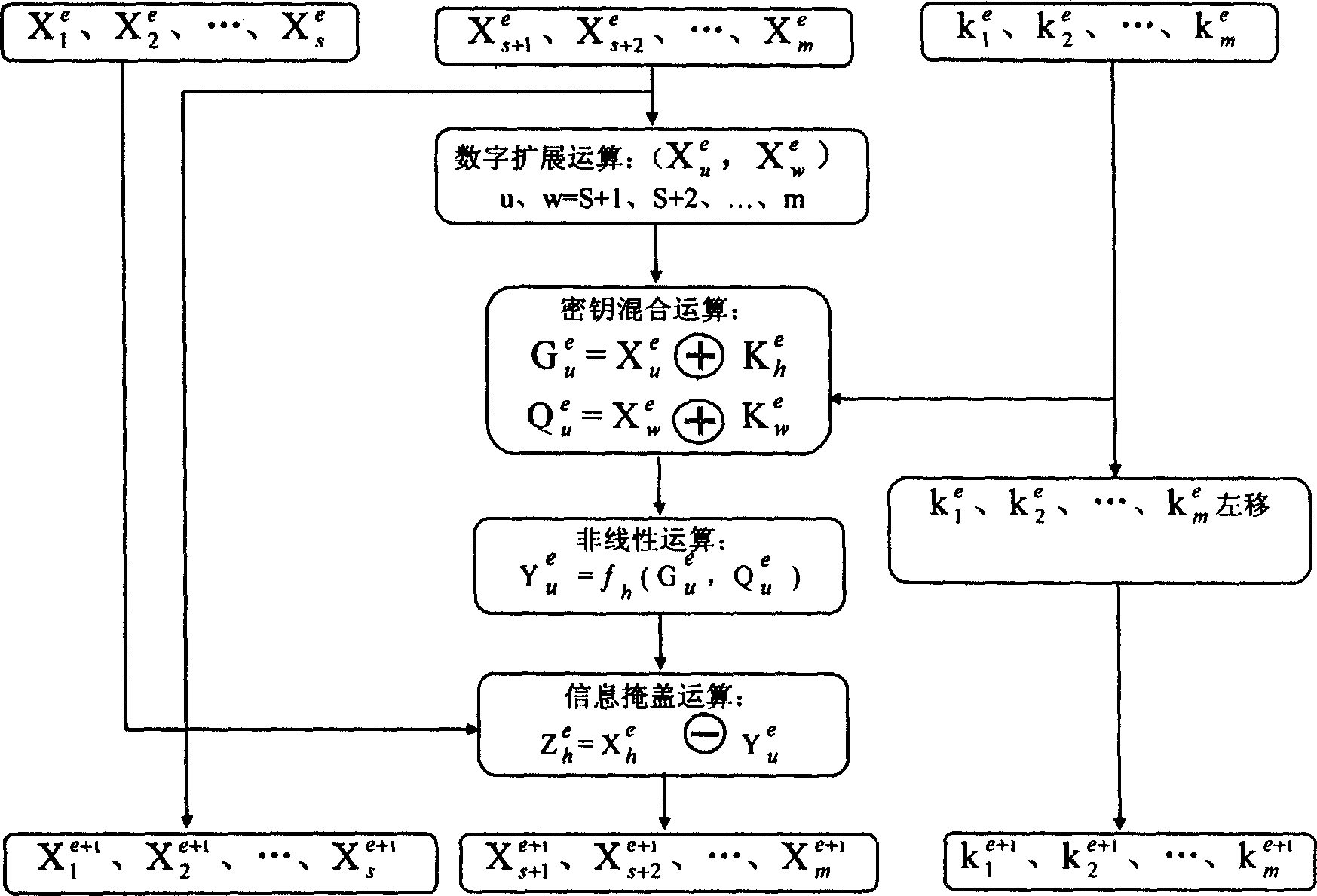
[0078] In this embodiment, the ciphertext output in the corresponding embodiment 1 is decrypted, and the specific operation process of the decryption algorithm is as follows: image 3 As shown, it includes grouping operation on ciphertext C, decryption loop iterative calculation, position transformation and output plaintext, etc. The decryption loop iterative calculation includes six sub-operation processes, which are digital expansion operation, mixed operation of key and variable, non-linear Transformation operation, information masking operation, reassignment and key one cycle left shift operation, the above operation process is
[0079] current technology.
[0080] Corresponding to the encryption algorithm in Embodiment 1, the input ciphertext C of the decryption algorithm is a set of decimal numbers C 1 、C 2 ,...,C i ,...,C m , 0≤i≤m, and the number C i Only one of the following a and b value ranges can be taken.
[0081] a. 0≤C i ≤9
[0082] b. 0≤C i ≤99
[008...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com