Virtual private network applying hardware encipher/decipher
A virtual private network, encryption and decryption technology, applied in the direction of preventing unauthorized use of memory, etc., can solve problems such as difficult implementation and heavy workload
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
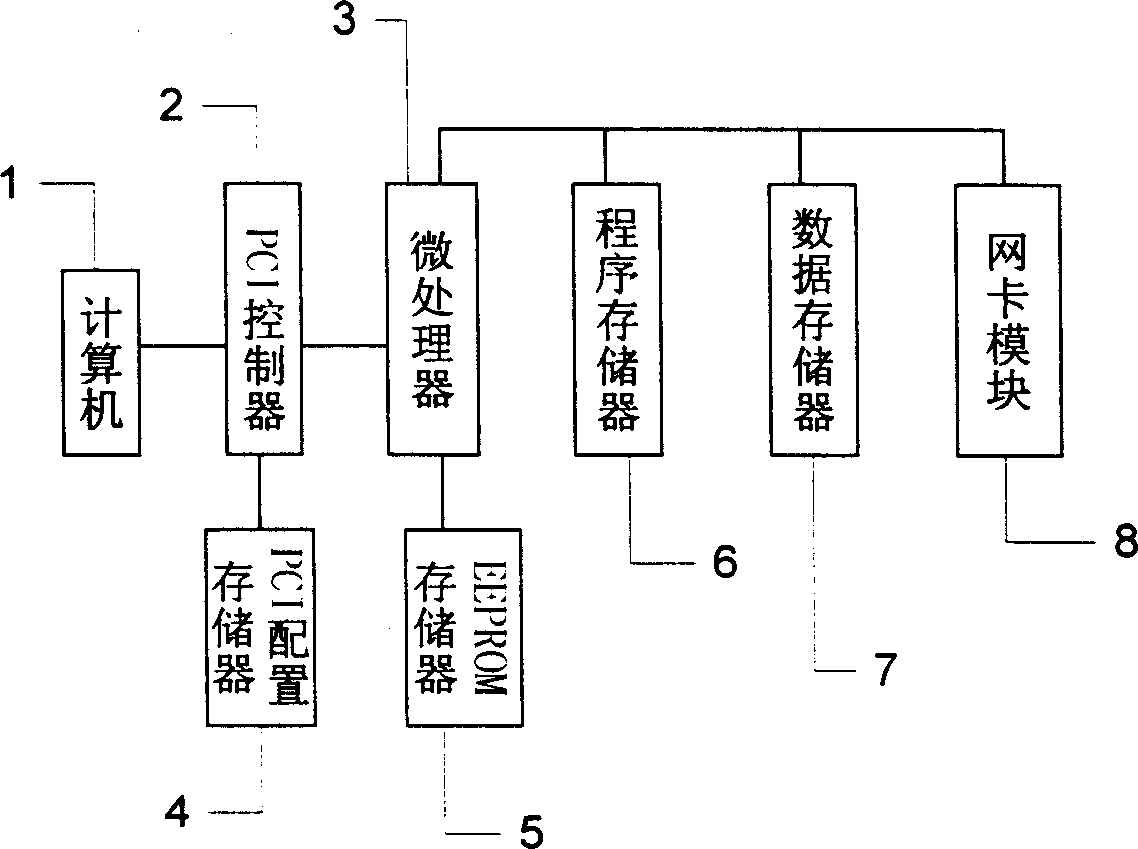
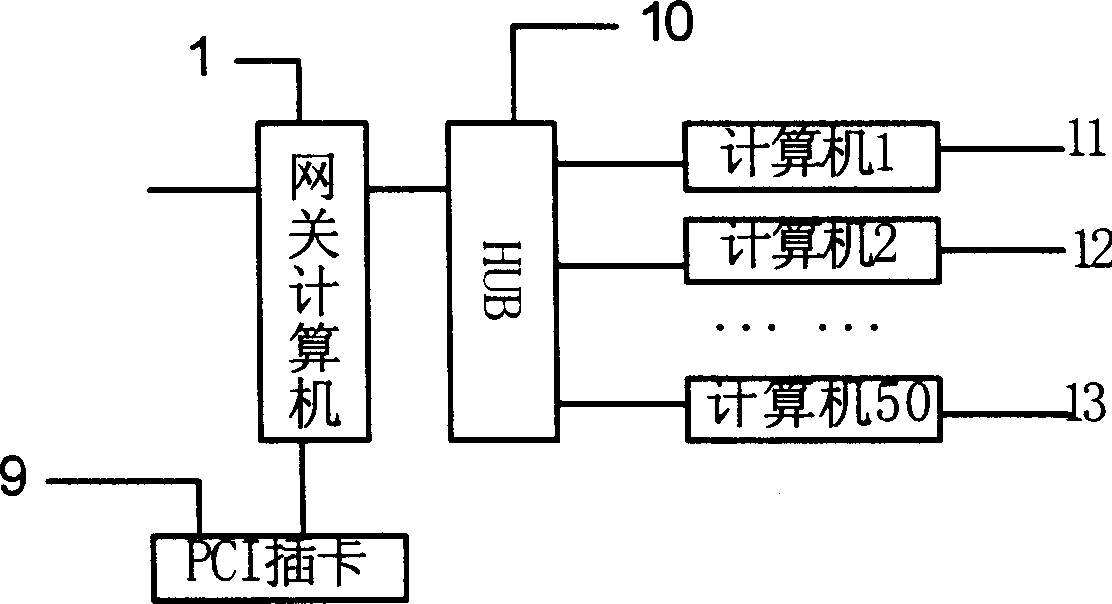
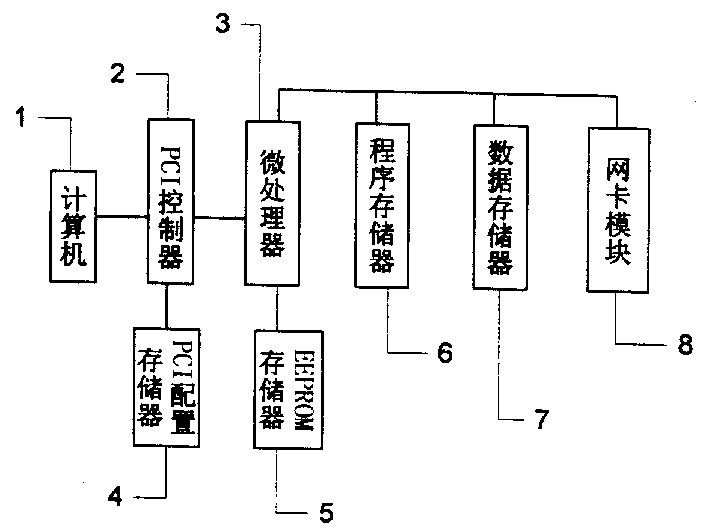
[0009] Such as figure 1 and figure 2 As shown, the present invention has a built-in PCI card 9 in the computer 1 used as a gateway, and uses the PCI card 9 to realize the encryption algorithm, decryption algorithm, digital signature, identity authentication, etc. in the virtual private network technology. When the users between the subnets access each other, the PCI plug-in card 9 adopts any mature data stream encryption and decryption algorithm solidified in the policy library memory 5 and the program memory 6, and passes the data through the PCI controller 2 and the PCI configuration memory 4 by the microprocessor. Received by the device 3 and temporarily stored in the data memory 7, the data stream is encrypted by the microprocessor 3 and then output through the network card module 8, so as to achieve safe and efficient communication between computers in the virtual private network environment.
[0010] PCI plug-in card 9 is a circuit board, and this plug-in card is made ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com