Patents
Literature
219results about How to "Protect intellectual property" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Method for generating configuration for middleware protocol conversion of Internet of vehicles
ActiveCN104331292AAvoid interventionImprove stabilitySpecific program execution arrangementsError checkDBc
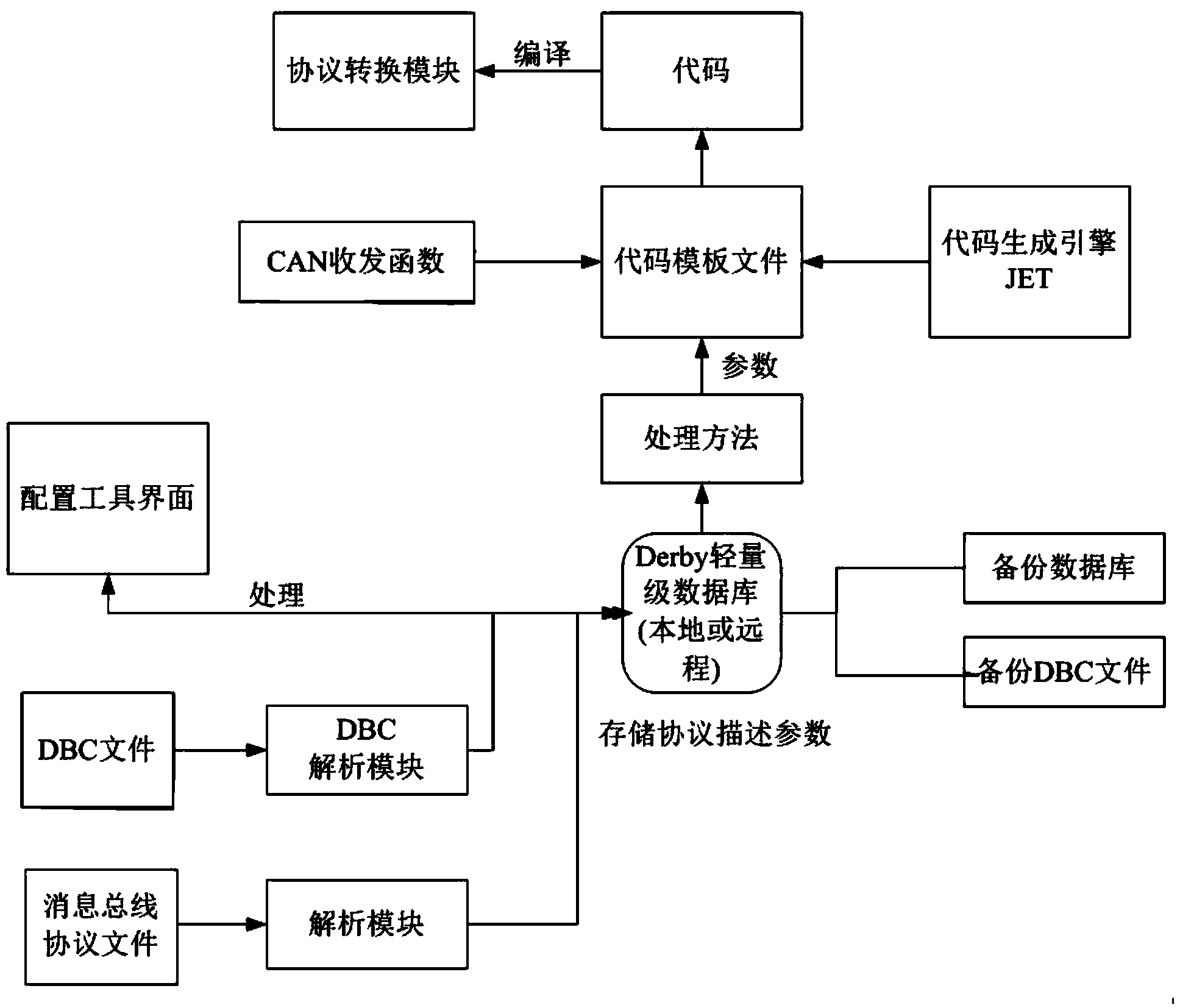
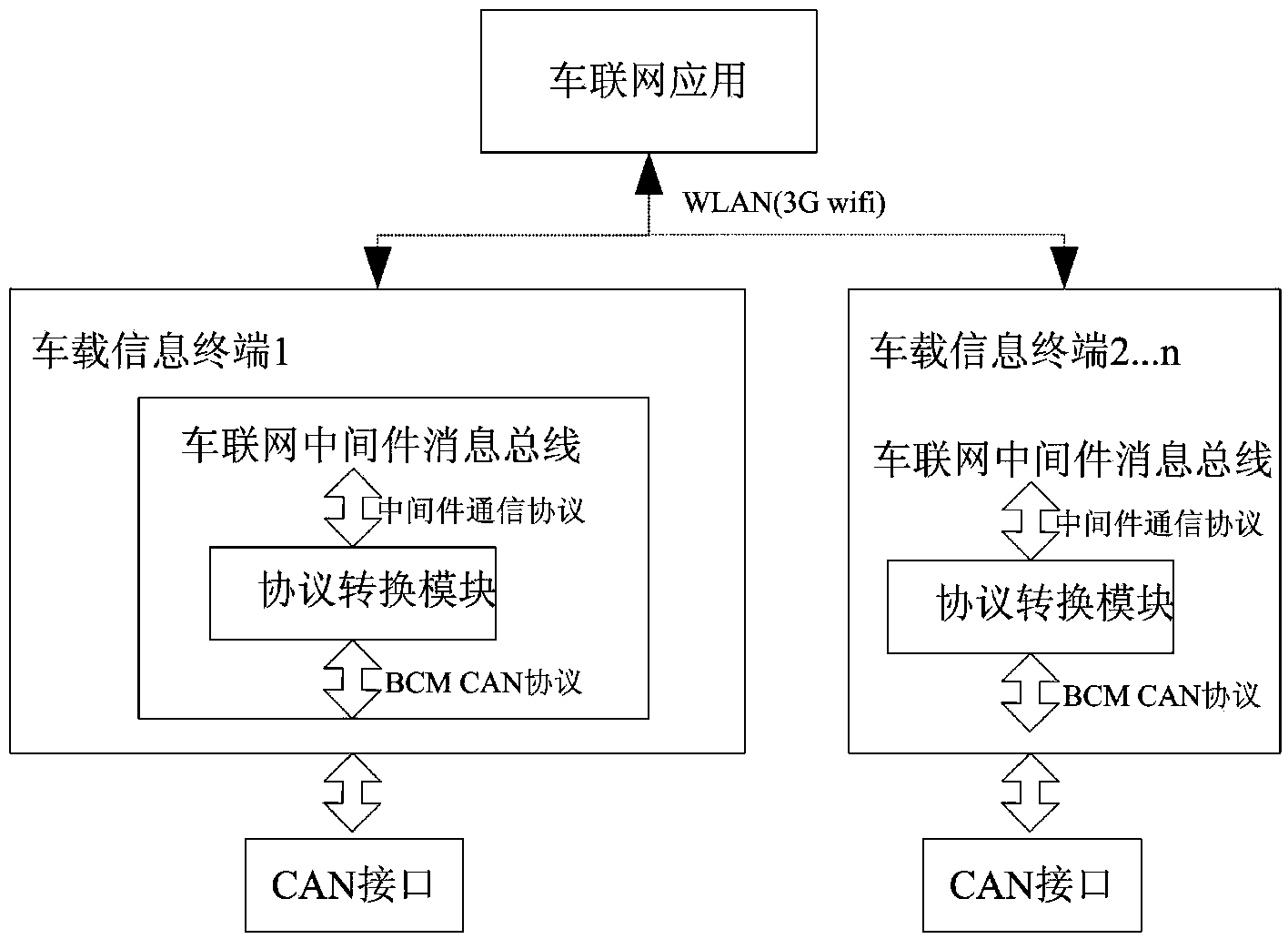
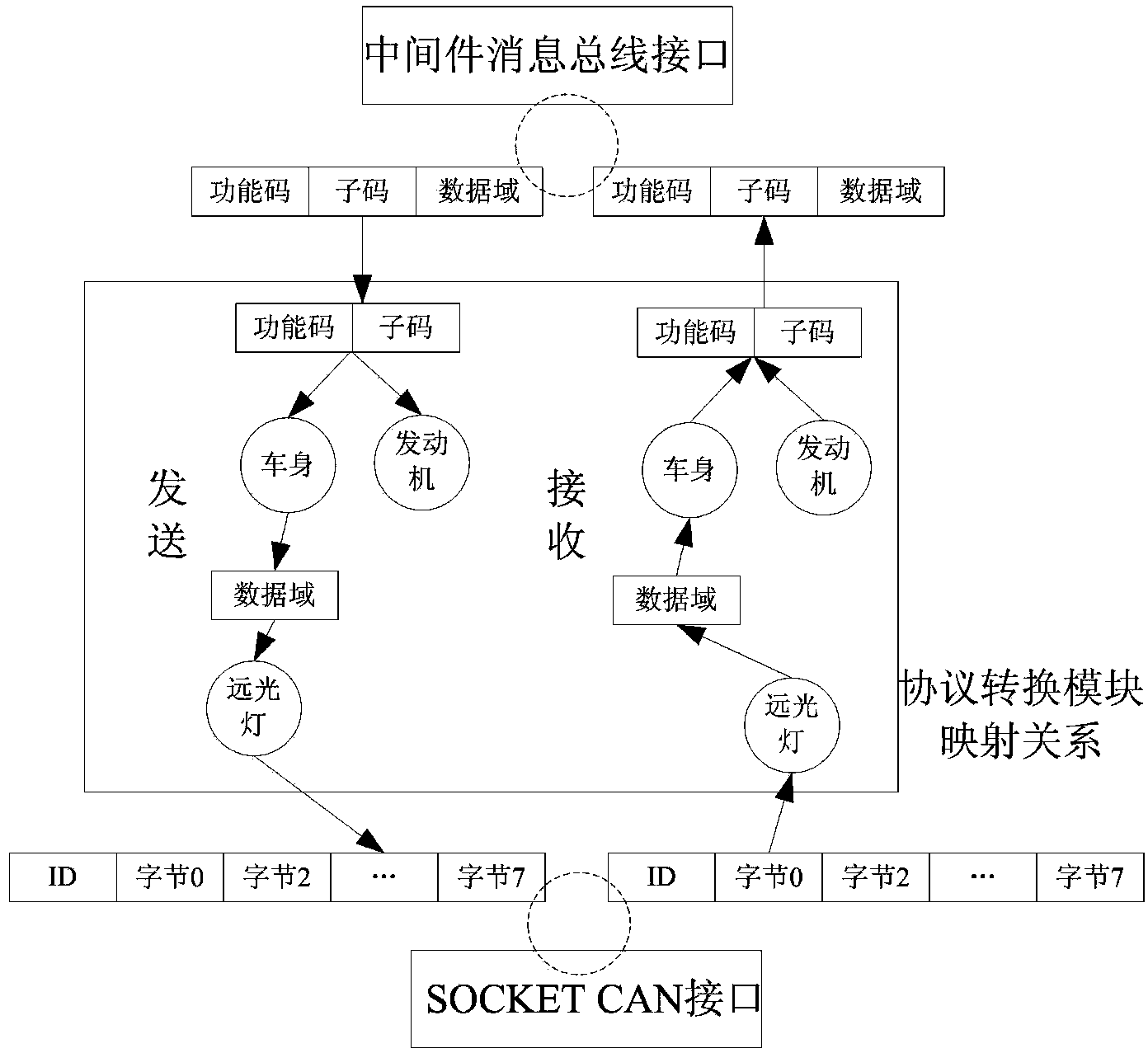
The invention discloses a method for generating configuration for middleware protocol conversion of the Internet of vehicles. According to the method, the rapid development of a protocol conversion module is realized through configuration, vehicle enterprise communication protocol conversion parameters are added into a configuration tool through reading DBC (DataBase Commander) file description information which is compiled according to the communication protocol of the Internet of vehicles, configuration information is stored in a database, and middleware protocol conversion module codes of the Internet of vehicles are automatically generated by using protocol conversion template files; a vehicle body network is rapidly integrated with other networks, so as to realize the communication of the Internet of vehicles; the configuration tool can automatically generate configuration files and an application framework and carries out error check on the configuration of a user, worker involvement is avoided as much as possible, and the error rate is lowered, so that the stability of the protocol conversion module can be actively improved.
Owner:CHONGQING UNIV OF POSTS & TELECOMM
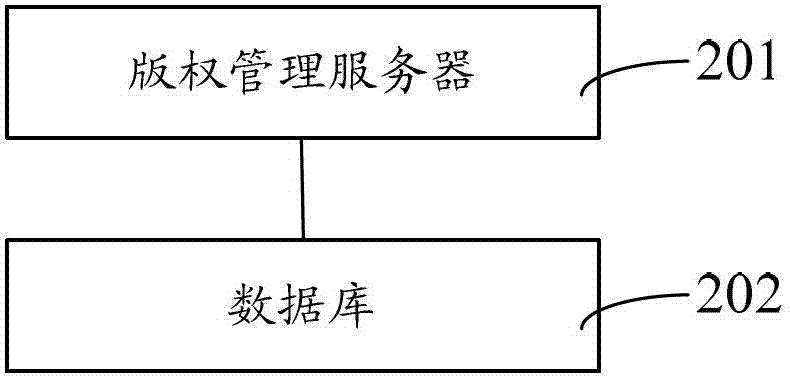
Protecting method and protecting system for authentication server software copyright
ActiveCN102780699AProtect intellectual propertyEasy to installUser identity/authority verificationComputer security arrangementsIntellectual propertyDigital signature
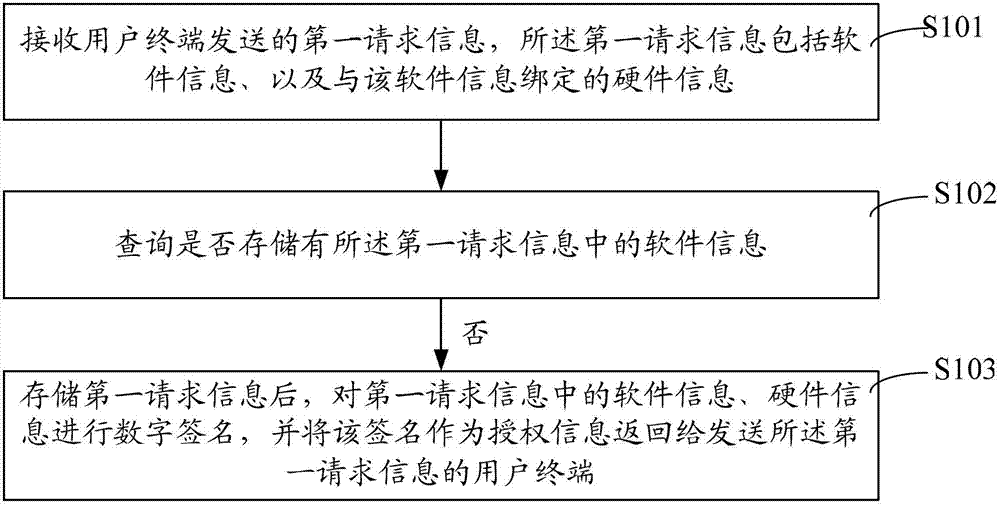
The invention discloses a protecting method and a protecting system for authentication server software copyright. The protecting method includes authorization request. The authorization request includes the steps that first request information sent by a user terminal is received, and the first request information comprises software information and hardware information bound with the software information; whether the software information in the first request information is stored is queried; and if the software information in the first request information is not stored, after the first request information is stored, a digital signature is conducted on the software information and the hardware information in the first request information, and the signature is used as authorization information and sent to the user terminal of the first request information. By combining the software information and the hardware information, authentication server software can only be installed and operated on legal hardware and can not be operated on other hardware, and therefore intellectual property of vast authorization server software developers is completely protected. Numerous modules are not required to be installed on a client terminal due to an online software protecting method, and therefore installing, deployment and maintaining are easy.
Owner:GCI SCI & TECH
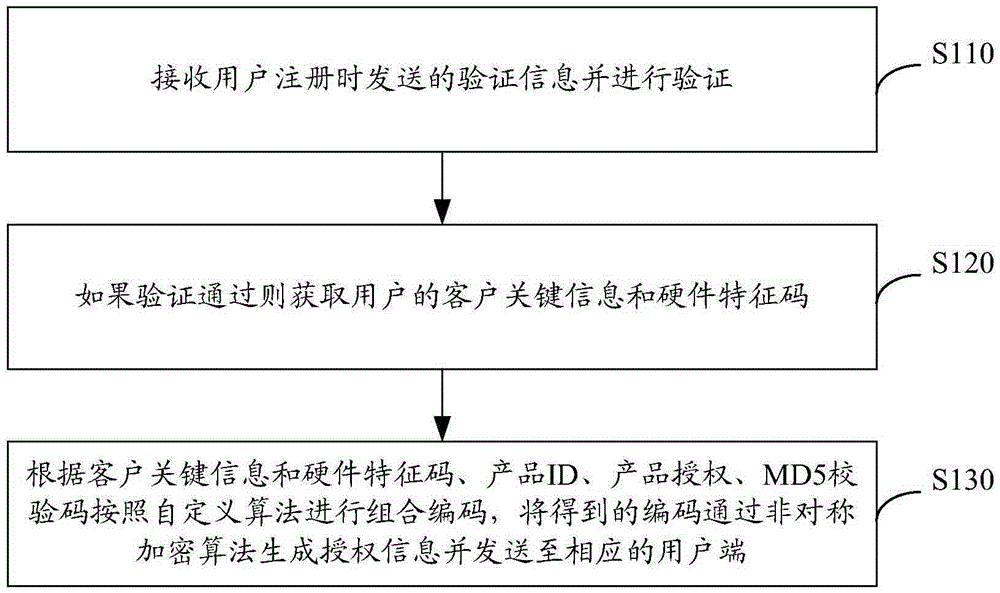
Software protecting, authorizing and registering method
ActiveCN104700002APrevent piracyAvoid business lossProgram/content distribution protectionFeature codeAuthorization
The invention discloses a software protecting, authorizing and registering method. The software protecting, authorizing and registering method comprises the following steps: receiving verification information sent out during user registration and verifying; if the verification is successful, obtaining client key information and hardware feature codes of a user; carrying out integrated coding in accordance with custom arithmetic and according to the client key information and the hardware feature codes, product ID, product authorization and MD5 check codes, generating authorization information by obtained codes through asymmetric cryptographic algorithm and sending the authorization information to a corresponding user side. The method provided by the invention can protect product intellectual property, limit unauthorized use of software products, can effectively prevent piracy and avoid business loss, further can support rich and flexible authorized packaging and pricing mechanisms, can achieve high efficiency and low cost software distributing and delivering, and further can be used for comprehensive analysis to software product selling, marketing and customer conditions.
Owner:航天信息软件技术有限公司
Software Development and Sales Life-Cycle Services
InactiveUS20080092107A1Protect intellectual propertyComputer security arrangementsSoftware designPaymentSoftware engineering
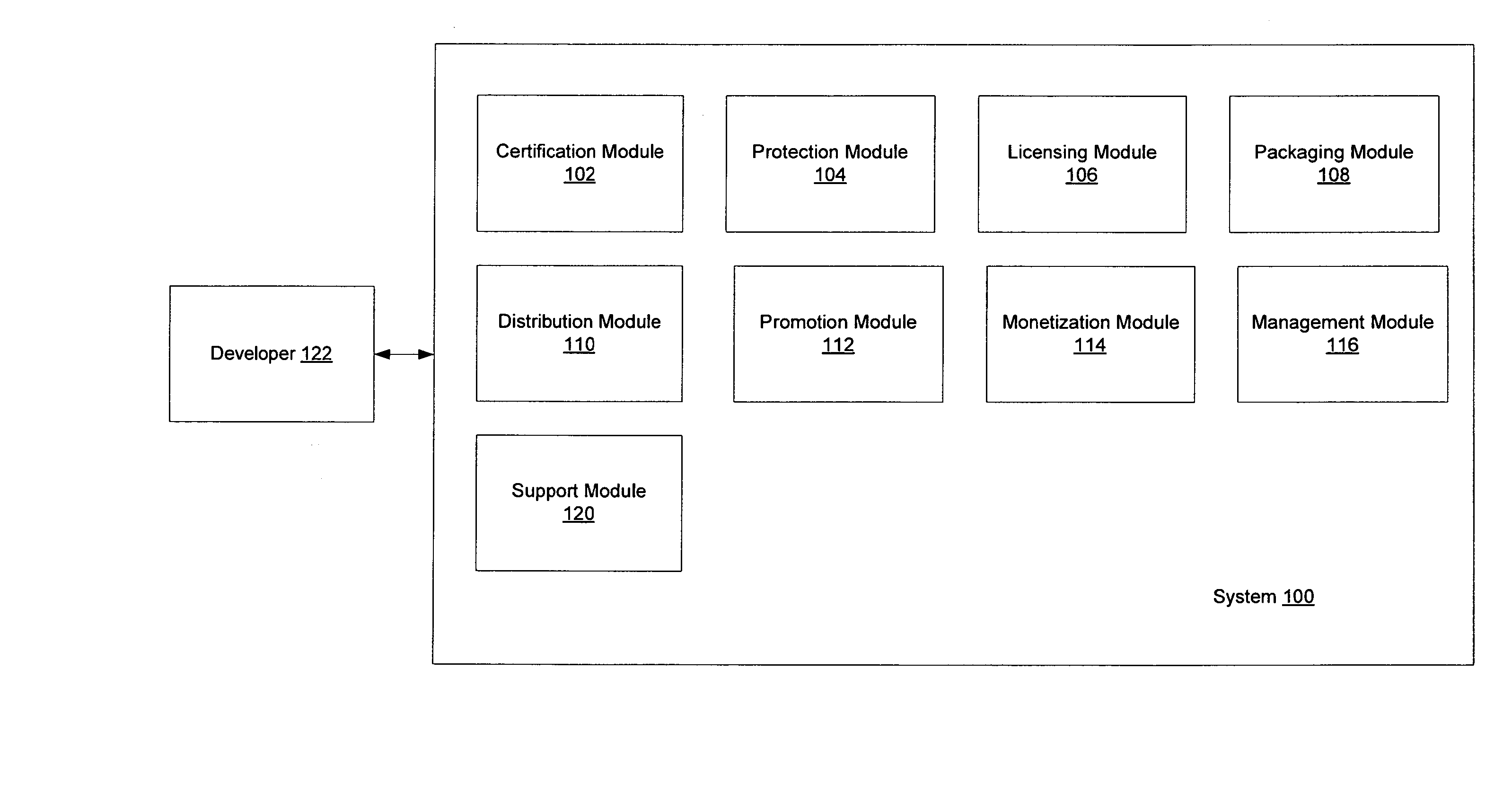
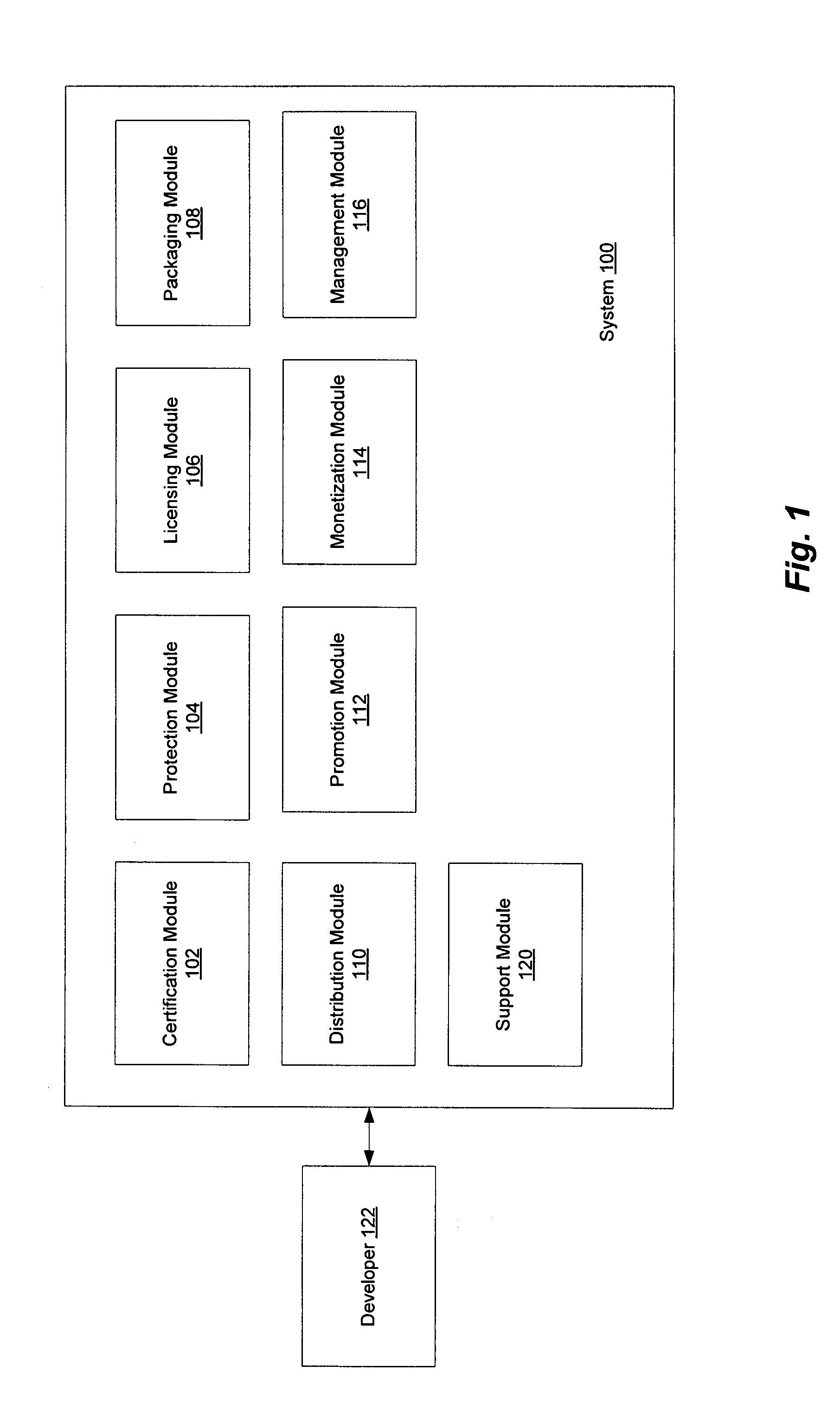
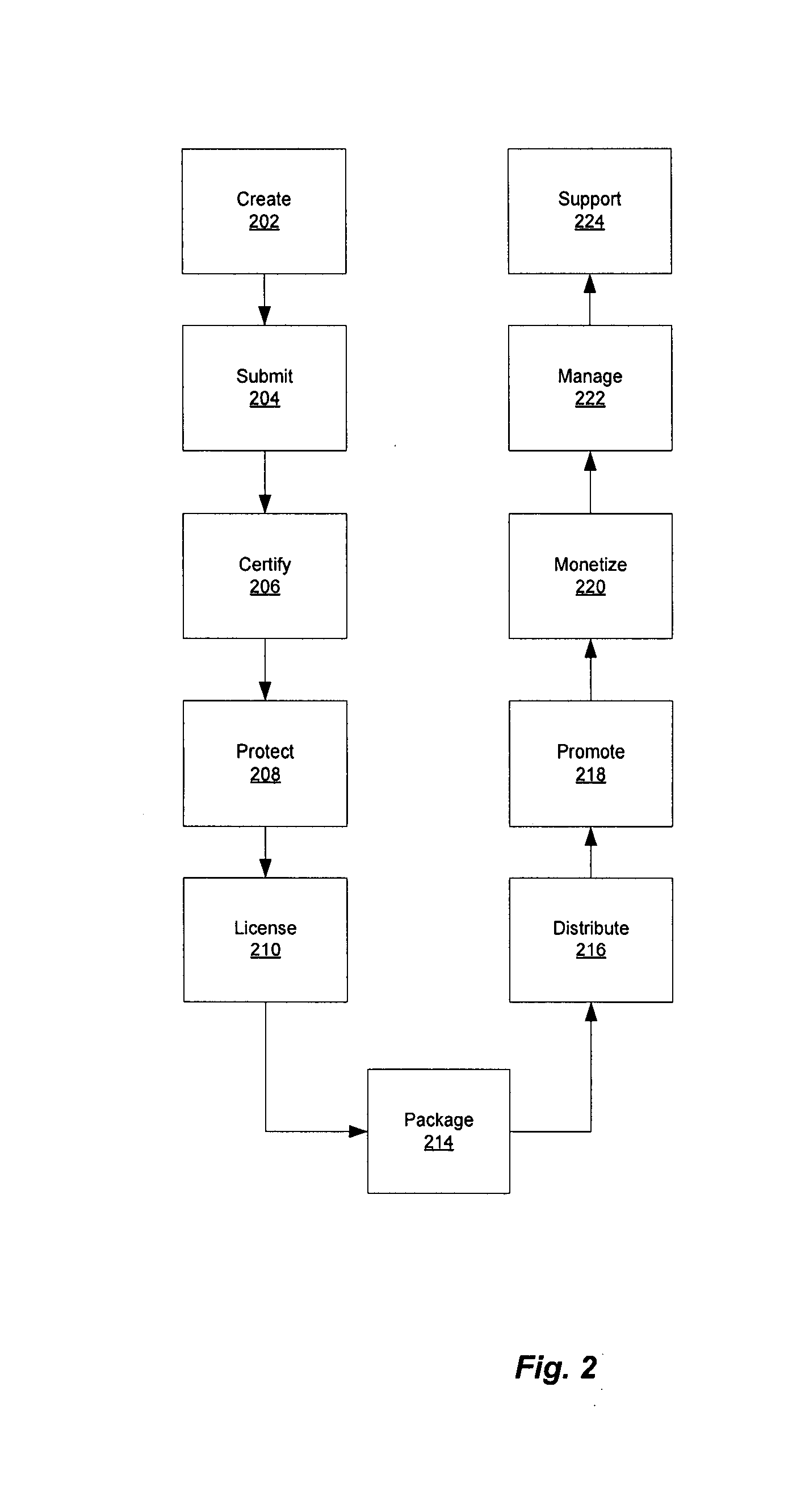
Software developers compete with larger software publishers using a system and method for certifying, protecting, licensing, packaging, distributing, promoting, monetizing, and supporting software applications. A certification module determines compliance with mandatory criteria. A protection module enables the developer to specify portions of the application subject to protection against malfeasance. A licensing module includes a selection of licenses from which the developer can choose. A packaging module is used by the developer to make flexible combinations of different licenses into a saleable unit. Using a distribution module, the developer can then distribute the software application, updates and patches to end users. A promotion module makes products available in online catalogues for end users. A monetization module allows end users to purchase the applications, issuing activation keys and enabling payment. A management module enables end users to manage purchases and licenses. A support module lets end uses submit feedback and support requests.
Owner:BRIGHT HUB
Modularized reconfigurable networked digital control system in open type
ActiveCN1873570AEasy to implement refactoringEasy to upgradeTotal factory controlNumerical controlMicrocontrollerOperational system
The invention relates to a reconstructable network open digital control system that includes bus connecting main controlling module, memory extending module, motion control module, network module, human-computer interface module, PLC module, and state monitoring module. Each module includes a function circuit, bus interface and module identification chip and a hardware driving and process reflection chip. The main control module contains open type embedded real time operation system that is running virtual module. The module identification chip stores the identification code of the seven modules to describe the function type. The invention is suitable for MCU, and DSP core digital system.
Owner:天津市泰森数控科技有限公司
3D printing system supporting cloud service
ActiveCN105291440AReduce difficulty of useFast design iterationAdditive manufacturing apparatusOriginal equipment manufacturerComputer terminal
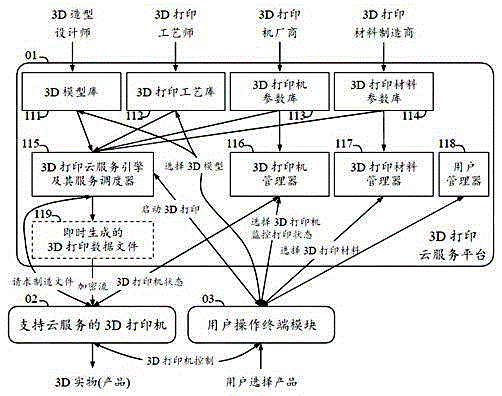
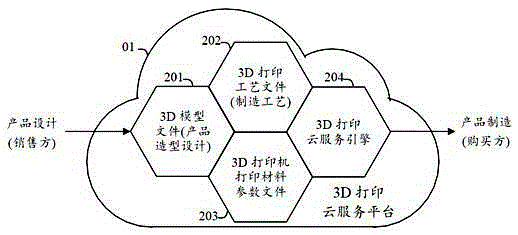
The invention discloses a 3D printing system supporting cloud service. The 3D printing system comprises a cloud service platform, a 3D printer supporting cloud service and a user operation terminal module, wherein the cloud service platform comprises a model library, a printing process library, a printer parameter library, a printing material parameter library, a 3D printing cloud service engine and a service scheduler thereof; the 3D printing cloud service engine and the service scheduler thereof comprise a printing model hierarchical processing algorithm engine. When a user chooses to print certain model in a 3D model library, the 3D printing cloud service engine and the service scheduler thereof locate a corresponding printing resource file and generate a 3D printing file according to a printer and a printing material used by the user. Through the 3D printing system supporting cloud service, the using difficulty of the 3D printer can be reduced; the user is more likely to obtain professional-class-quality works; the product trading manner is characterized by selling design, buying design and self producing or producing by original equipment manufacturer; the investment risk of the product designer can be reduced; the waste of social resources can be reduced.
Owner:ZHEJIANG UNIV OF TECH
Method for generating electronic channel chart based on Changjiang River standards
InactiveCN102095425AEnsure safetyEnsure integrityInstruments for road network navigationInformation processingSource Data Verification
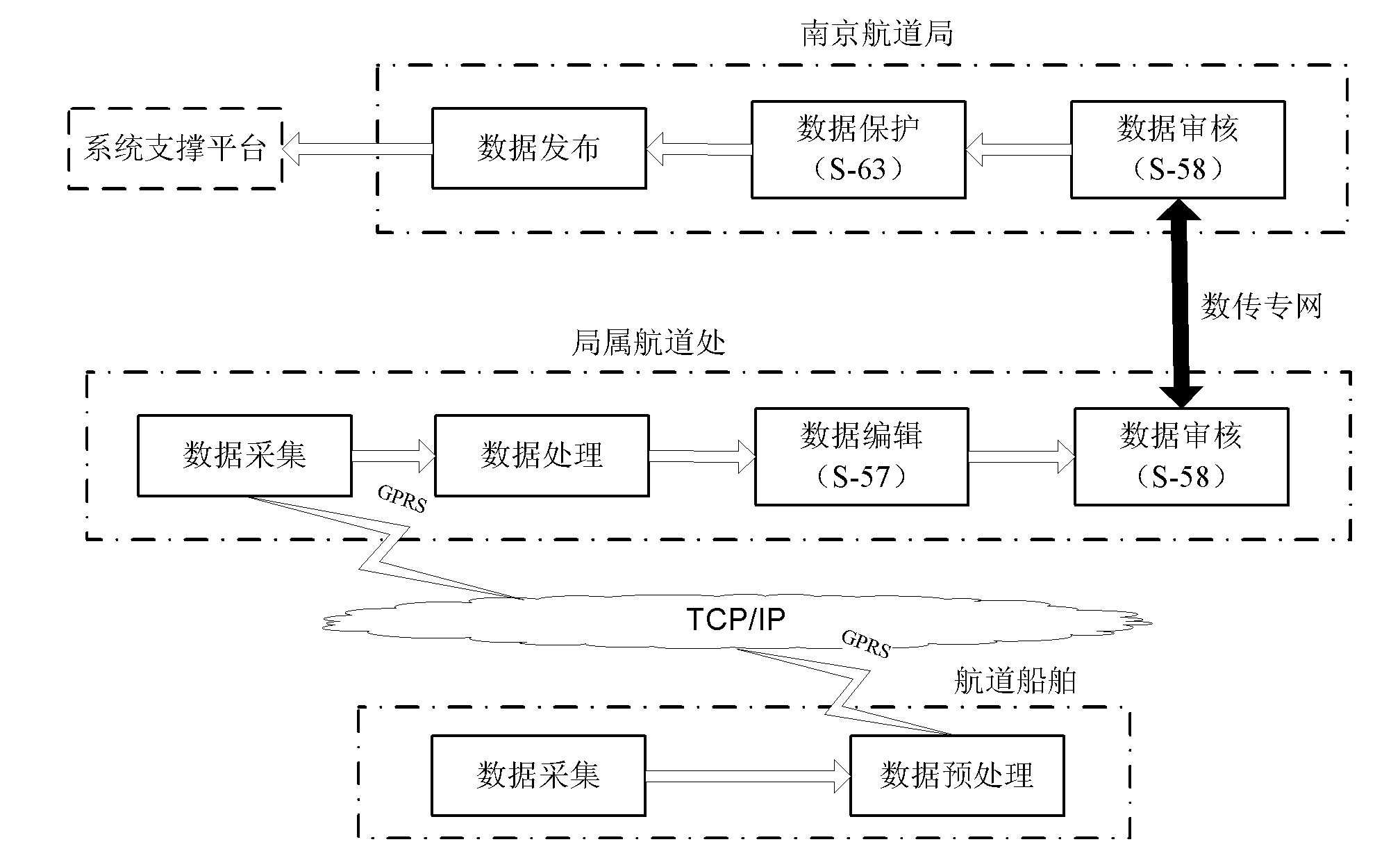
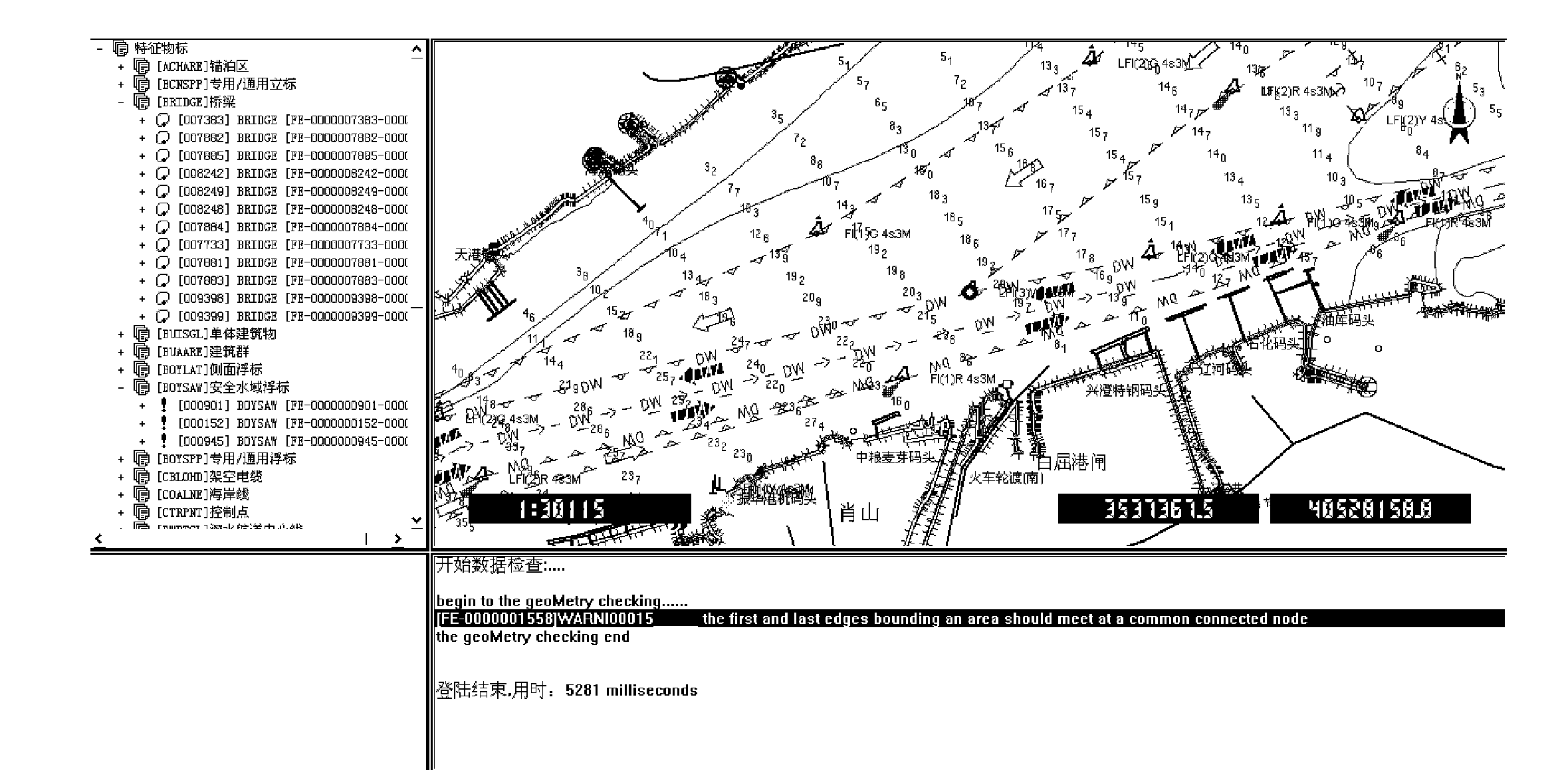
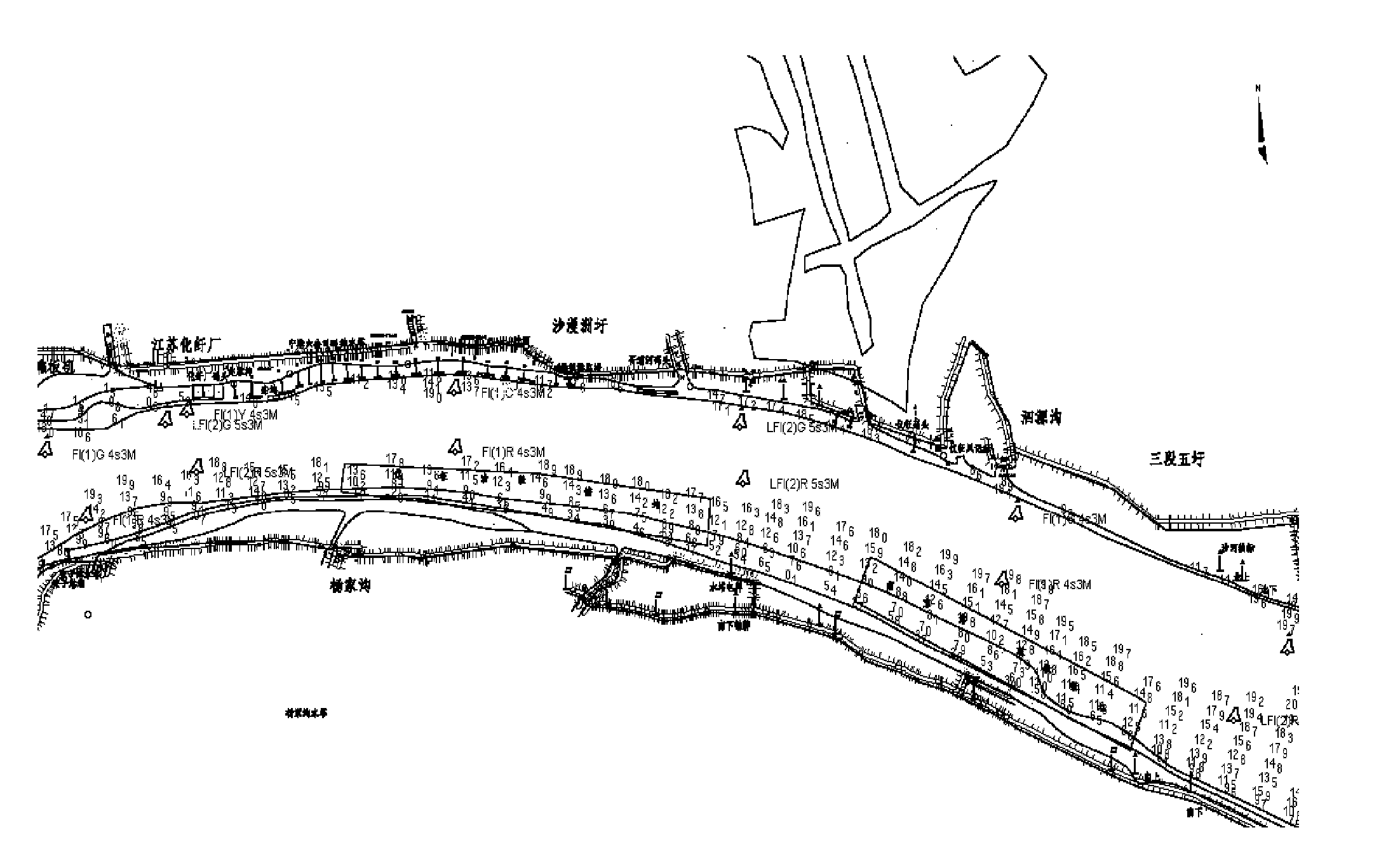
The invention discloses a method for generating an electronic channel chart based on the Changjiang River standards, which is mainly based on the digital channel measurement data transmission standard of the Changjiang River, the digital channel measurement data verification standard of the Changjiang River and the electronic sea chart data protection scheme recommended by IHO (International Hydrography Organization), sets up a standardized electronic channel chart database of the Changjiang River by utilizing advanced computer network technology, data communication technology and geographic information processing technology, realizes the measurement and the management for channels over the Changjiang River, the generation of the electronic channel chart and the automation, integration and networking of the entire release process by means of the generation flow including data acquisition, data processing, editing of the channel chart, checking of the channel chart, release of the channel chart and application of the channel chart, and provide, in the form of browser, the latest electronic channel chart service for ships sailing on the Changjiang River, shipping related departmentsand enterprises and public institutions in time. The method has the obvious advantages of normative data format, complete data updating mechanism, mature business system, safe information protection mechanism, great advantage in popularization and the like.
Owner:长江南京航道局 +2
Protein for regulating and controlling chloroplast growth and gene and application thereof
InactiveCN103290027AEffective Protection of Intellectual PropertyProtect intellectual propertyFungiBacteriaMutationBiotechnology
The invention provides a protein for regulating and controlling chloroplast growth and gene and application thereof, and belongs to the field of gene engineering technology. The invention discloses a gene nucleotide sequence for coding chloroplast growth protein and amino acid sequence of the protein. The invention provides a transgenic cell line containing the gene and transgenic recombinant bacteria containing the gene, and provides the application of the gene. The mutation of gene for coding the chloroplast growth protein can lead to low temperature albinism of young leaf and young ear albinism, and if the gene is knocked out, chloroplast development is stopped and the plant is dead at the seedling stage because of albinism. The product can be applied to the genetic improvement of plant and other works, and the gene provided is an important indication gene, and can be used as a target gene and applied to hybrid rice seed production, and is convenient for detecting purity of hybrid progeny. The product is applied in routine seed production, and because of the homozygous lethal characteristic, the product can prevent invalid seed preservation and seed product of progeny, thereby effectively protecting intellectual property of variety owner.
Owner:CHINA NAT RICE RES INST
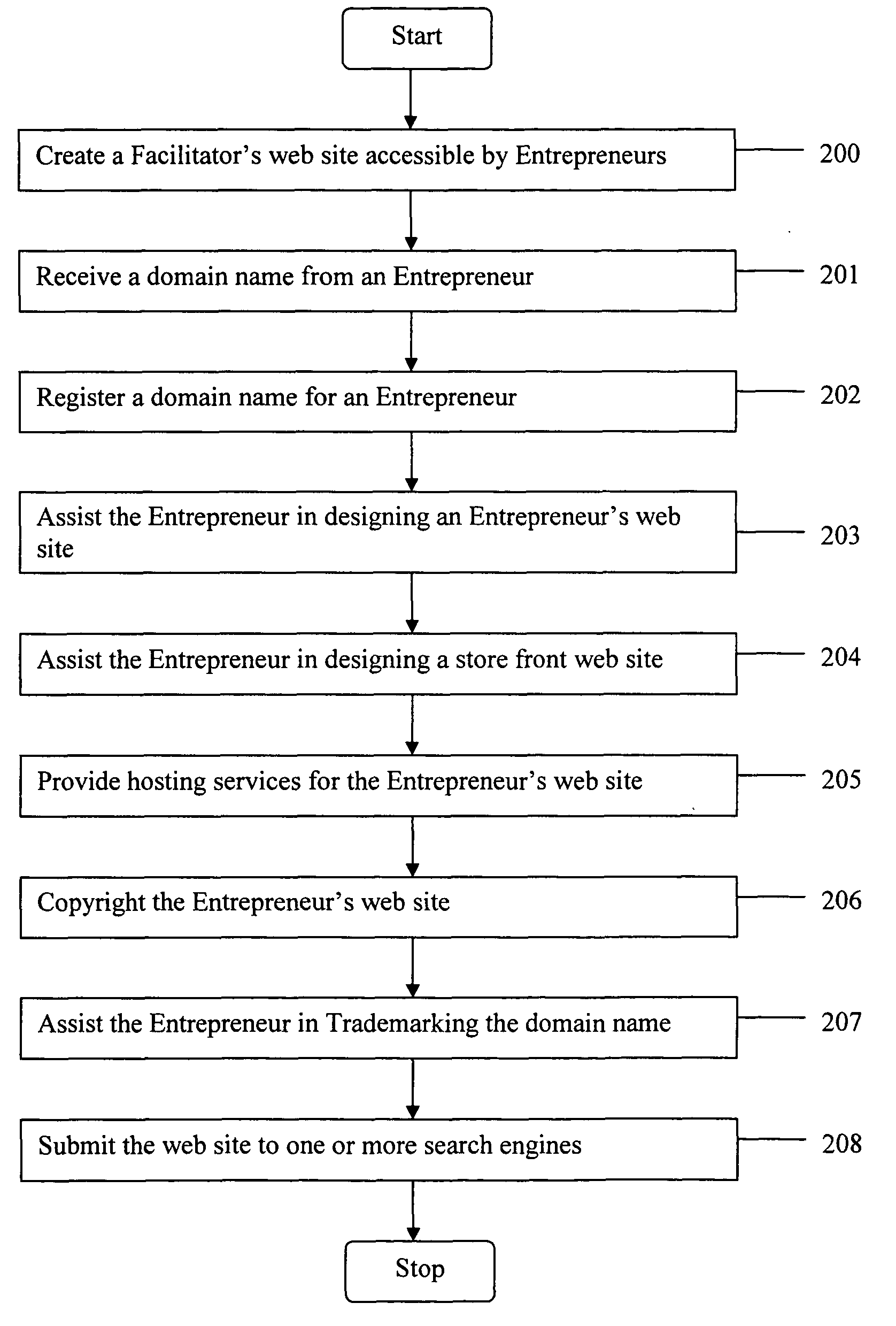
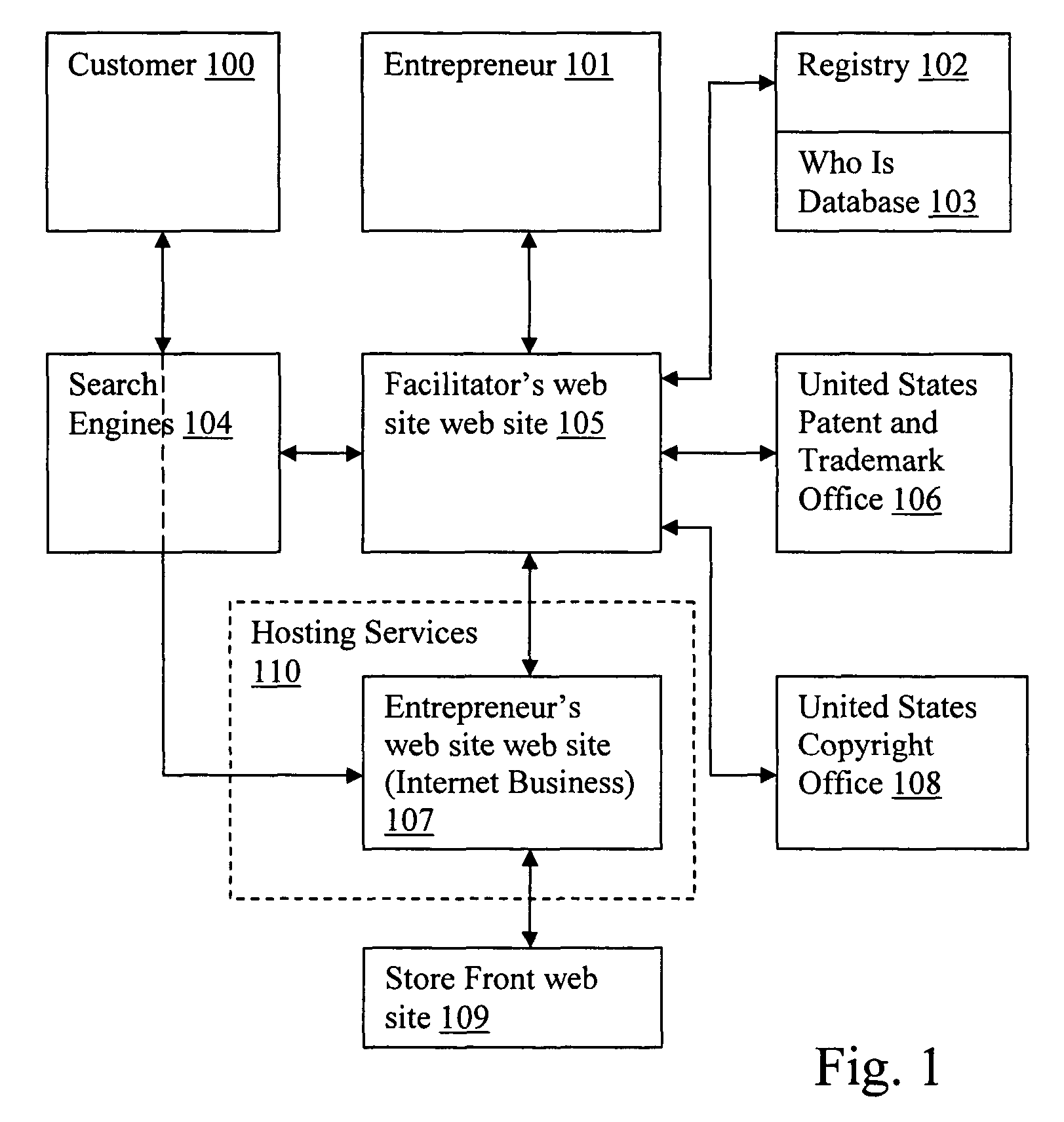
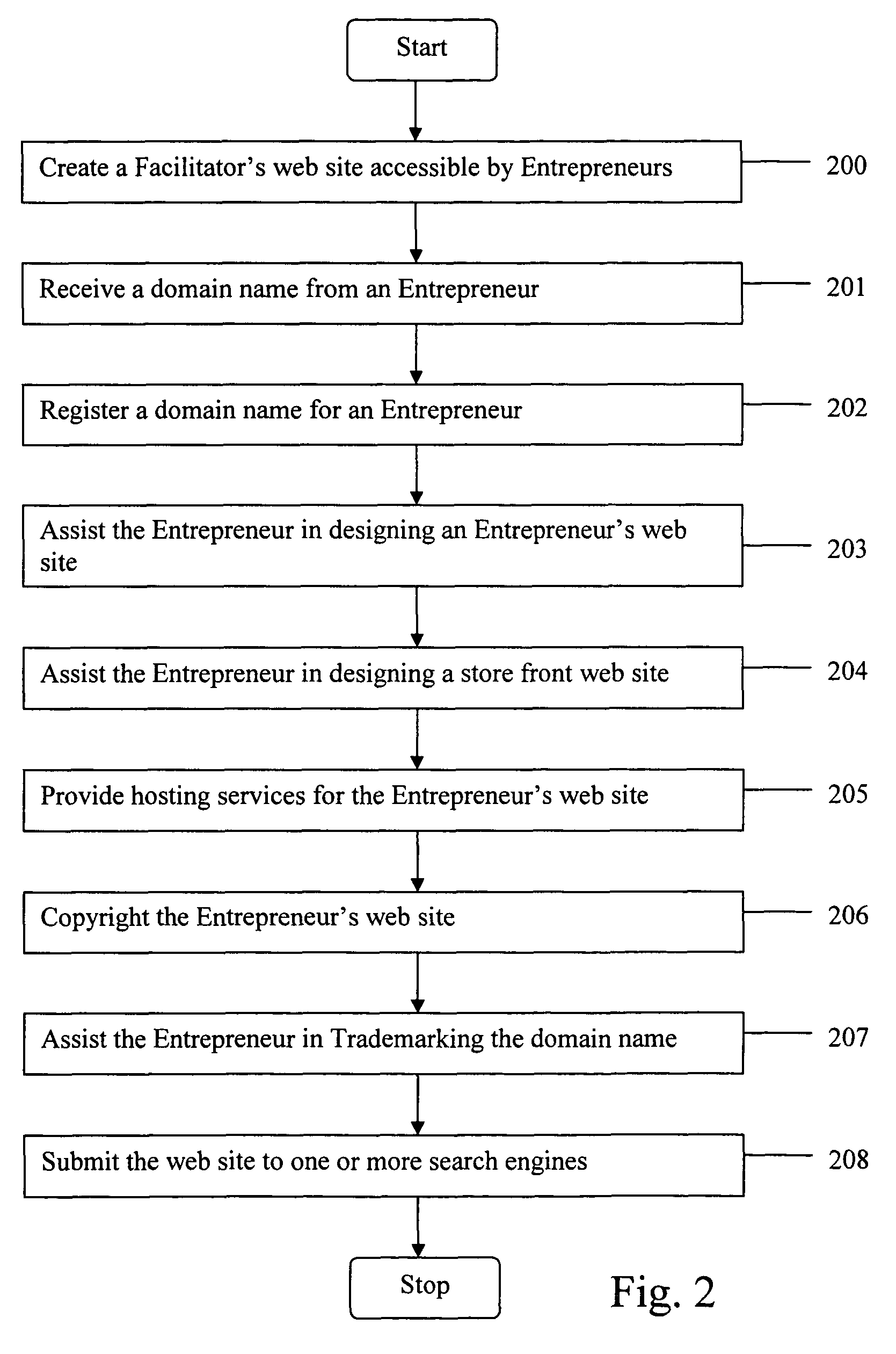
Method for a facilitator to assist an entrepreneur in creating an internet business
ActiveUS8356090B2Reduce frustrationReduce chanceDigital computer detailsOffice automationDomain nameWeb site
The present invention provides a method for an Entrepreneur to start an Internet business by creating an Entrepreneur's web site using tools provided at a Facilitator's web site. The method allows the Entrepreneur to access the Facilitator's web site, register a desired available domain name, trademark the domain name, design an Entrepreneur's web site accessible via the domain name, design a similar appearing store front web site to handle commercial transactions, copyright the Entrepreneur's web site, offer hosting services for the Entrepreneur's web site and submit the Entrepreneur's web site to one or more search engines. Tremendous synergies may be achieved and serious pitfalls avoided in creating the Internet business by receiving overall guidance and assistance from one web site, i.e. a Facilitator's web site, in performing these processes.
Owner:GO DADDY OPERATING
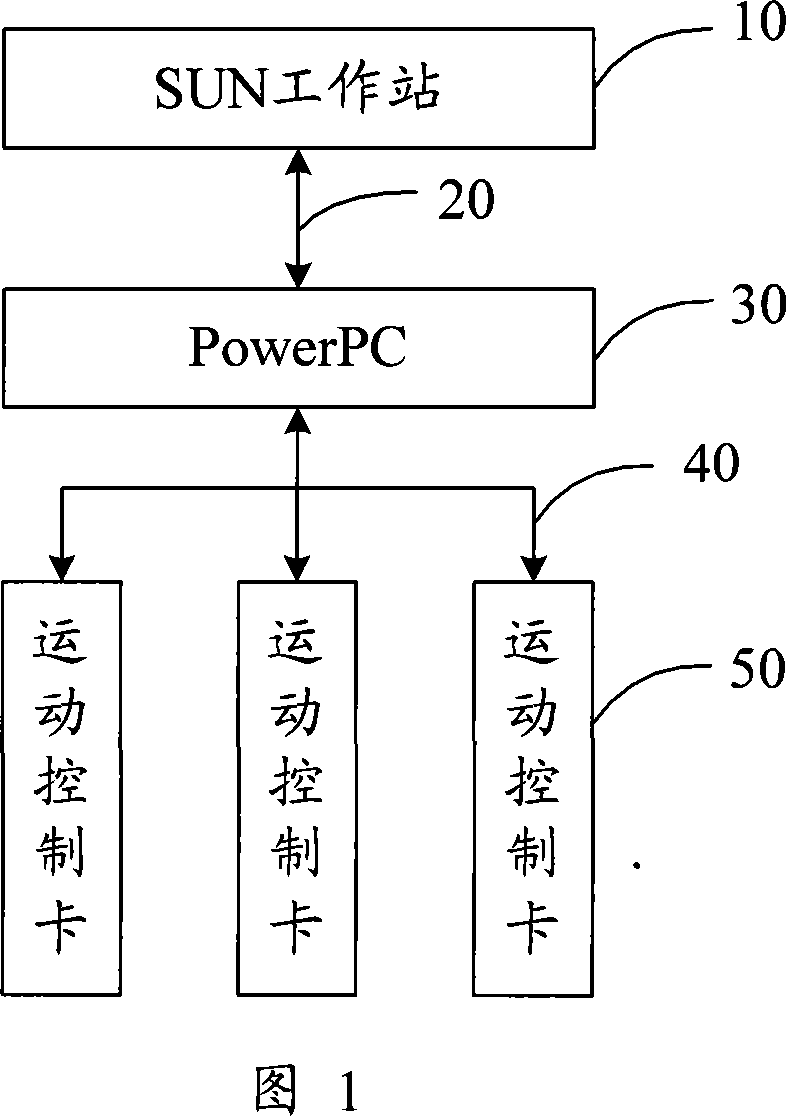
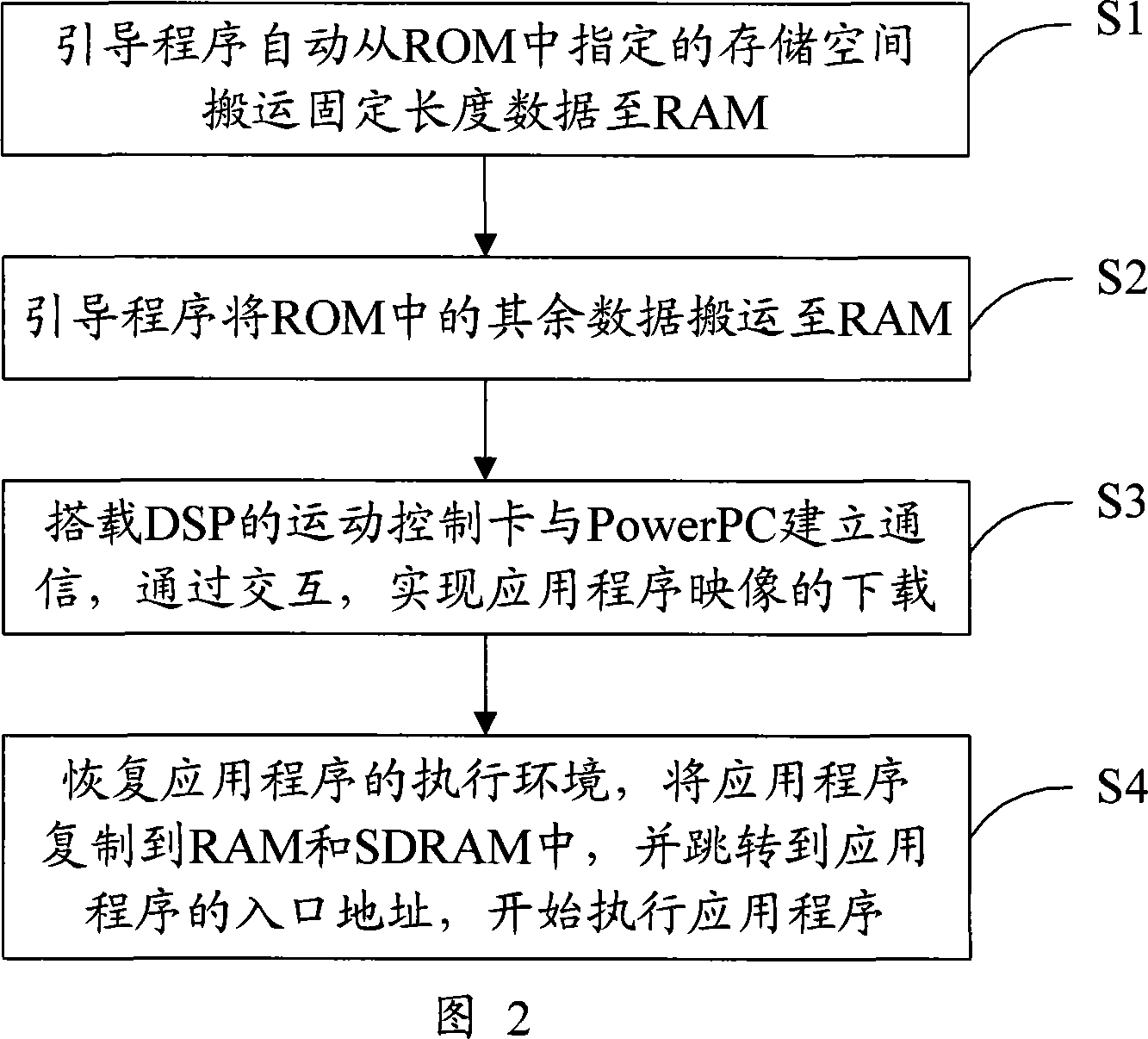
Program dynamic loading method
ActiveCN101067789AImplement dynamic loadingProtect intellectual propertyProgram loading/initiatingGoal systemApplication software
This invention provides a dynamic loading method for programs used in dynamically loading applied programs to a target system of DSP, which includes an exterior non-volatile ROM, an exterior SDRAM and a slice RAM, and the method includes: processing images of an applied program according to an applied program to be executed and resuming information corresponding to the generated applied program image, then solidifying the resuming information and a lead program to the ROM, connecting the DSP to a PC to execute the lead program in the ROM after the system is turned on to communicate with the PC and loading the image on the SDRAM, then copying the image of the applied program to related positions of the RAM and the SDRAM and resetting the DSP to an operation environment of the applied program to carry out the applied program.
Owner:SHANGHAI MICRO ELECTRONICS EQUIP (GRP) CO LTD
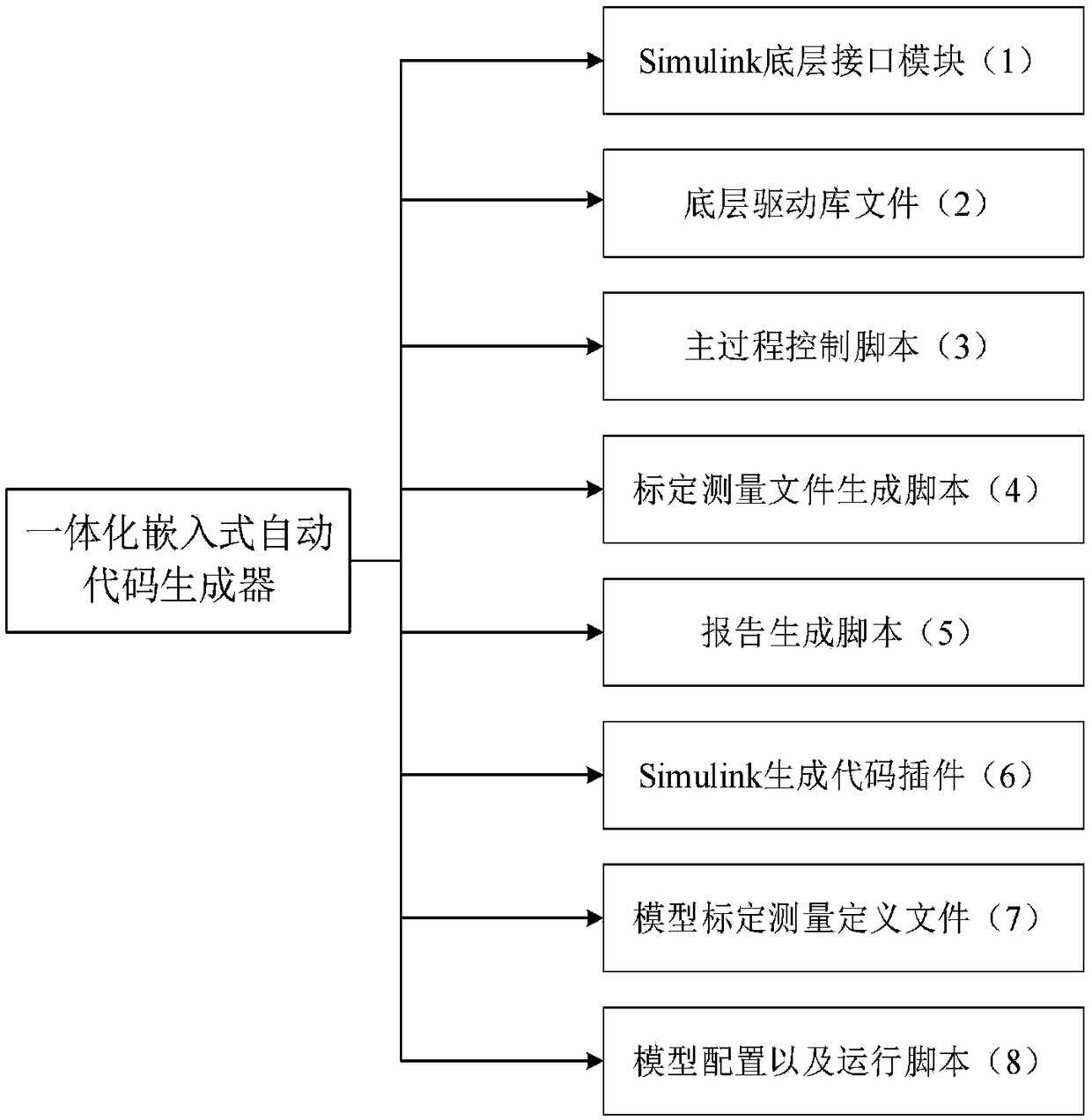
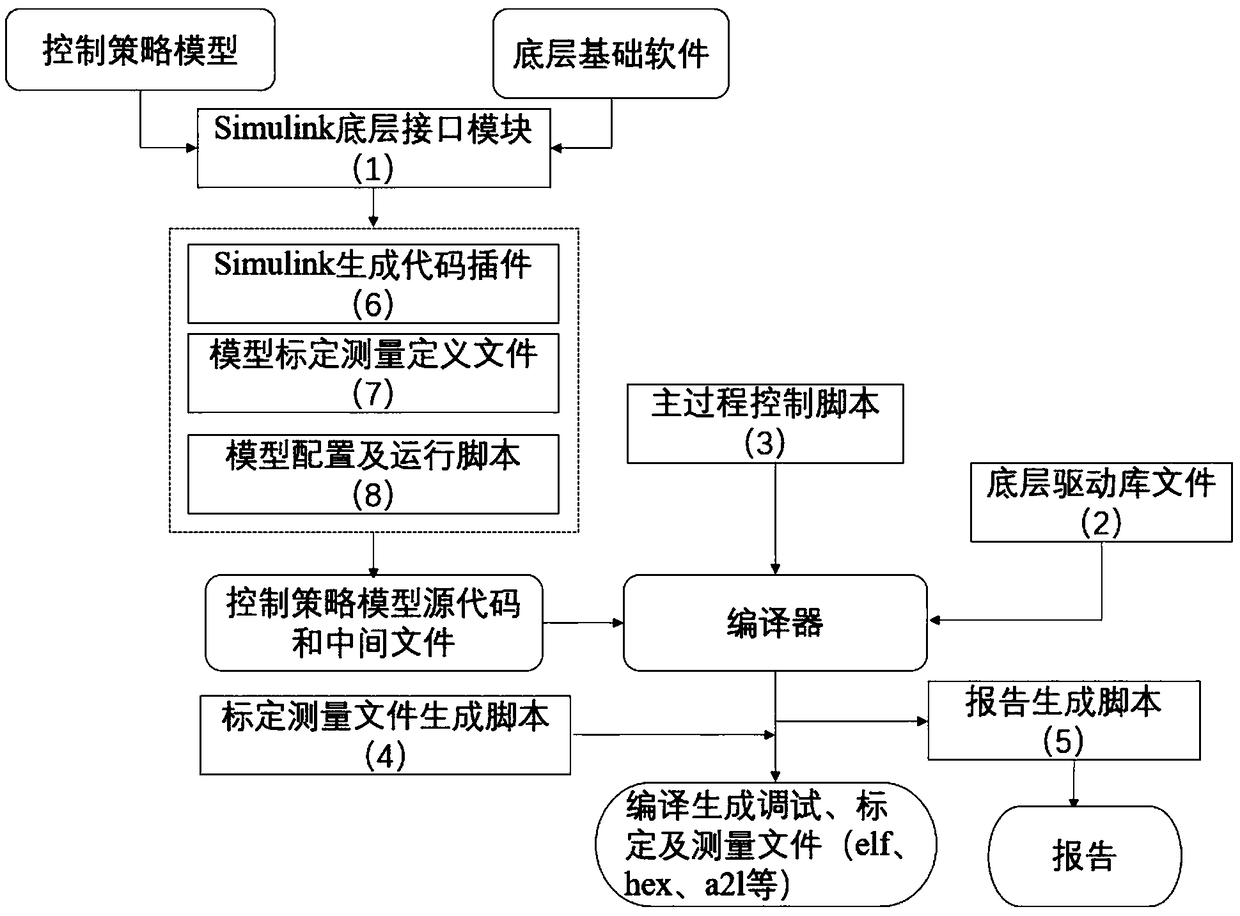
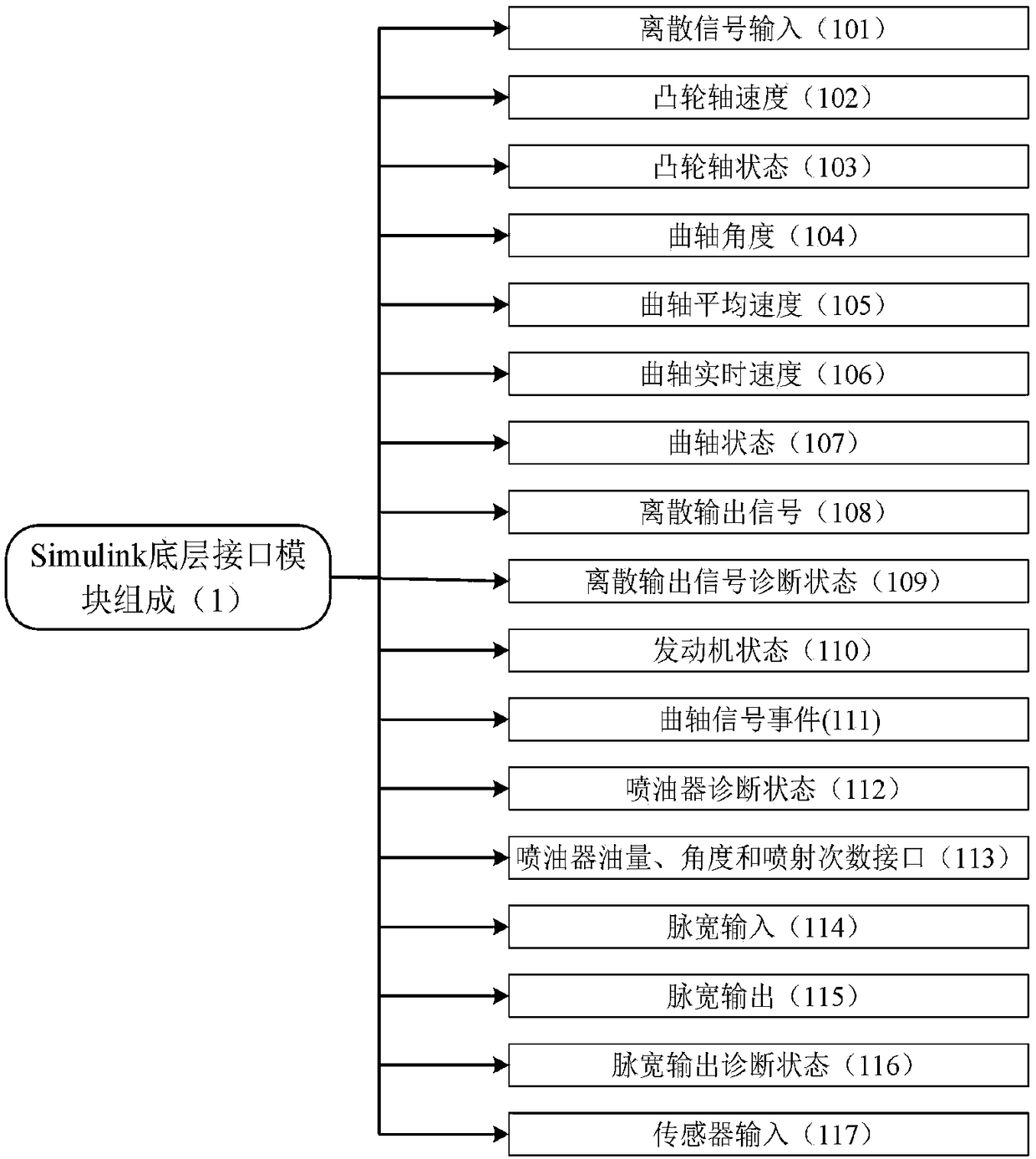
Integrated ECU embedded object code automatic generator and automatic generation method
ActiveCN109002290ACompact structureProtect intellectual propertyElectric testing/monitoringModel driven codeGeneration processObject code
The invention discloses an integrated ECU embedded object code automatic generator and an automatic generation method, belonging to the diesel engine ECU software special development platform field. The object code generator consists of a Simulink bottom interface module, a bottom driver library file, a main process control script, a calibration measurement file generation script, a report generation script, a Simulink code generation plug-in, a model calibration measurement definition file, and a model configuration and running script. The invention can realize one-key integration of a control strategy model and basic software of bottom layer and automatic generation and compilation of embedded product code in the development process of ECU software of engine electronic control unit; theinvention simplifies the generation process of ECU execution software, saves the time of human participation in the process of software integration and product code generation, and shortens the development cycle of ECU software products and improves the development efficiency by parallel development of control strategy model and basic software, division of labor and cooperation.
Owner:昆明理工鼎擎科技股份有限公司
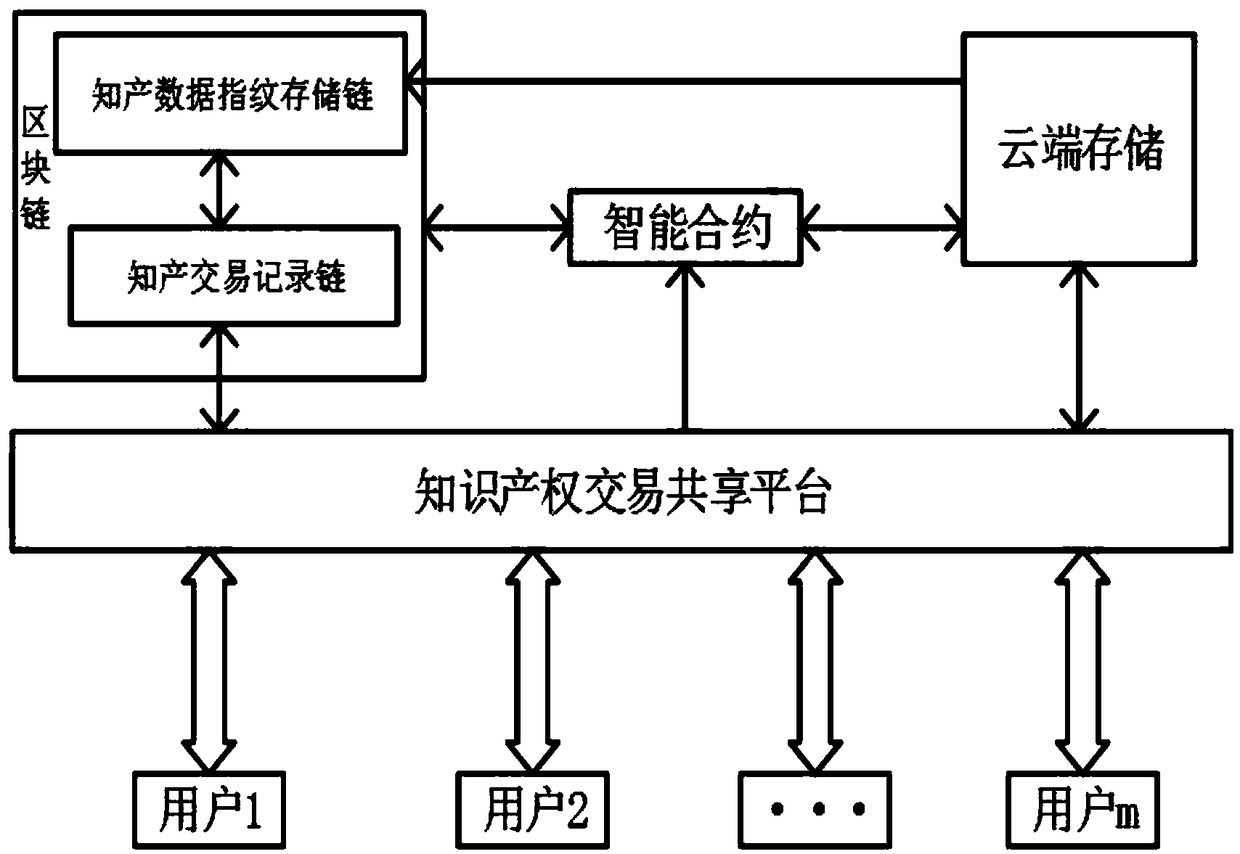
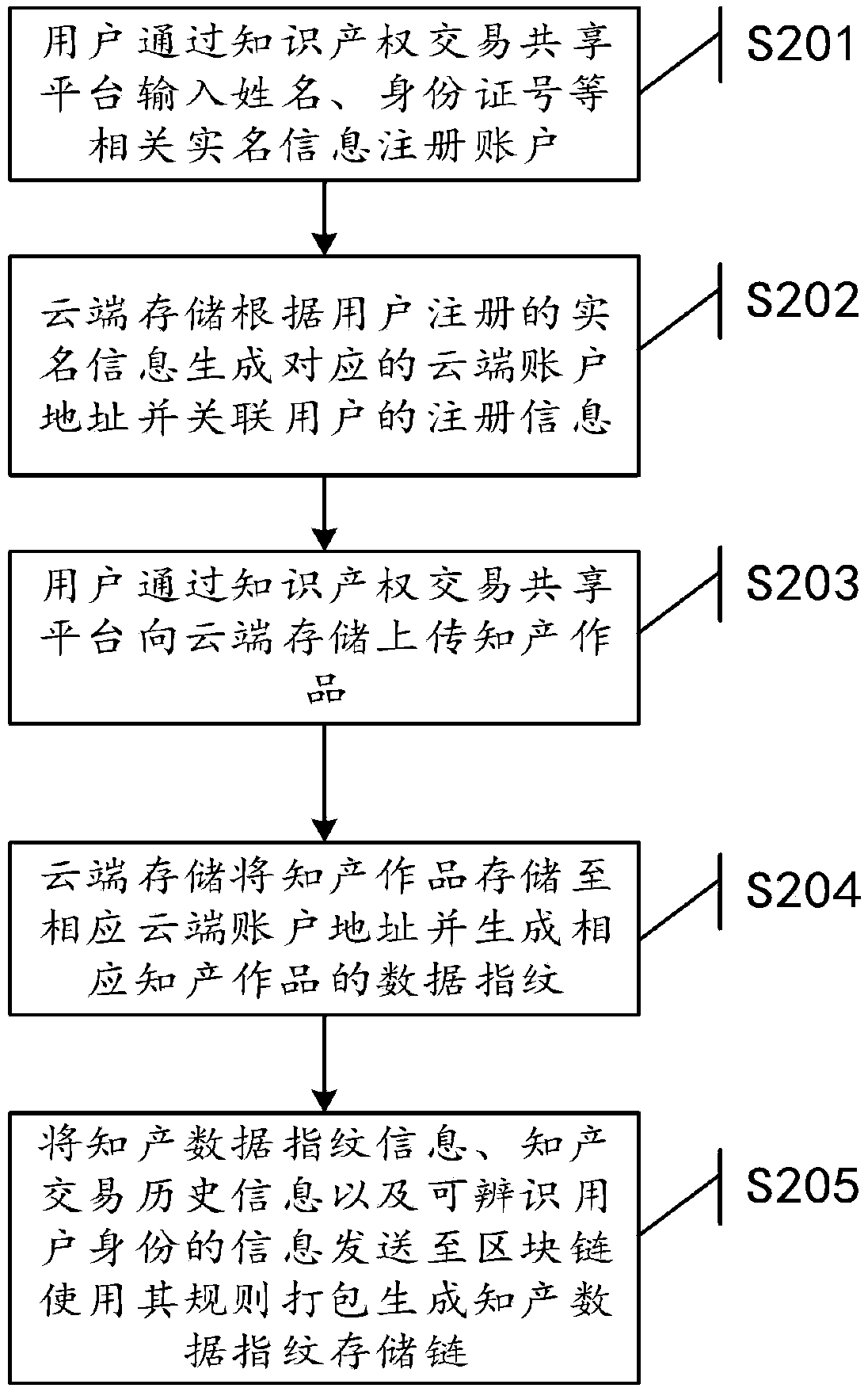
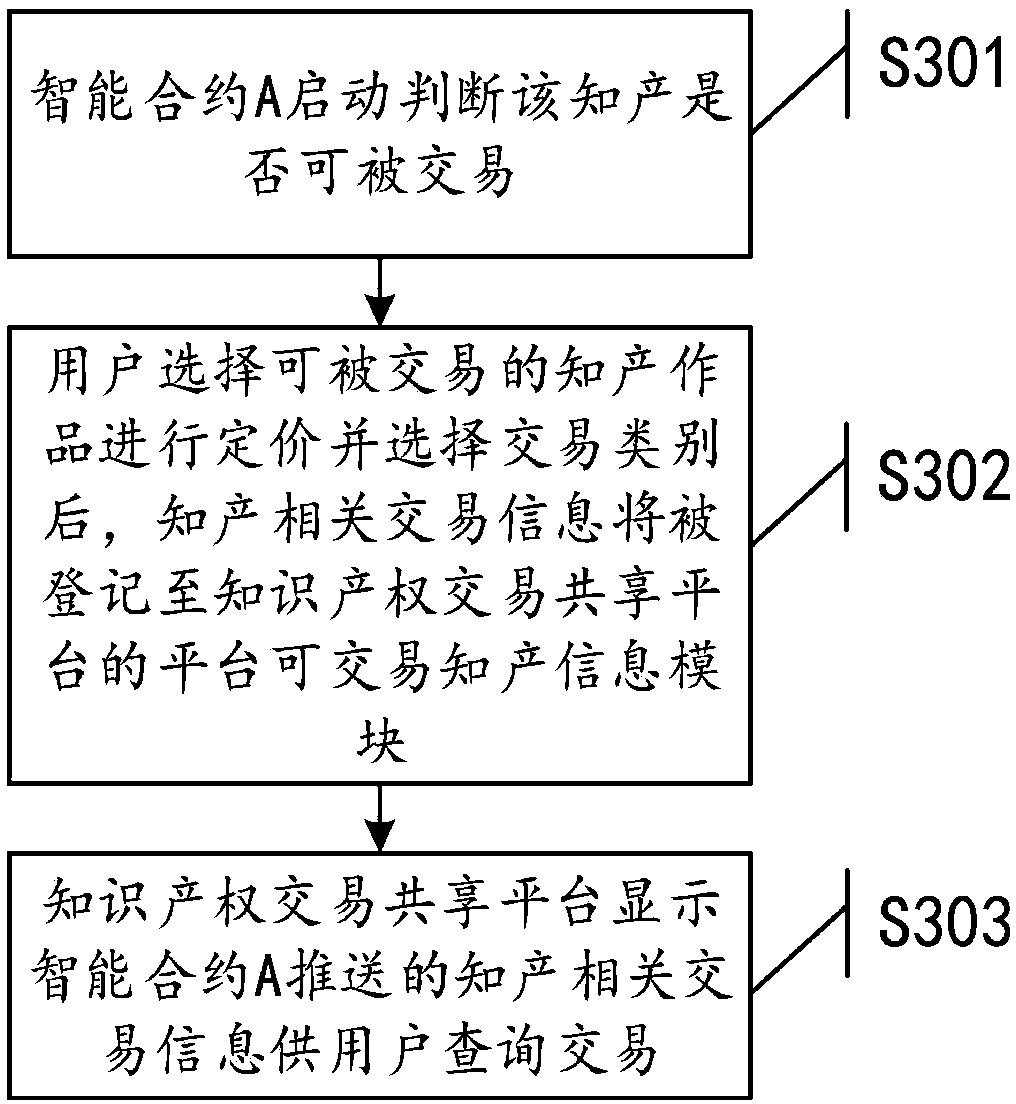
Intellectual property transaction sharing platform and method based on block chain
ActiveCN108711051AProtect intellectual propertyEasy to shareFinanceDigital data protectionIntellectual propertyDependability
The invention discloses an intellectual property transaction sharing platform and method based on a block chain. The intellectual property transaction sharing platform based on the block chain comprises an intellectual property transaction sharing platform, cloud storage, an intelligent contract and the block chain; wherein the intellectual property transaction sharing platform is used for users of visualization operation and realizing personal related information management, intellectual property information query and transaction functions; the cloud storage uses the cloud computing technology to store the intellectual property works of the user and generates corresponding data fingerprints; the intelligent contract is used for monitoring the status of intellectual property transactions and setting corresponding follow-up actions for different states; and the block chain uses a consensus mechanism and an encryption algorithm to store the intellectual property data fingerprint information and the intellectual property transaction information in a distributed way. The intellectual property transaction sharing platform based on the block chain can make online intellectual property transactions have high security and reliability; and in case of legal disputes, relevant electronic evidence can be extracted from the platform to safeguard the legitimate rights and interests of the users.
Owner:法信公证云(厦门)科技有限公司
3D printer control system for supporting user side
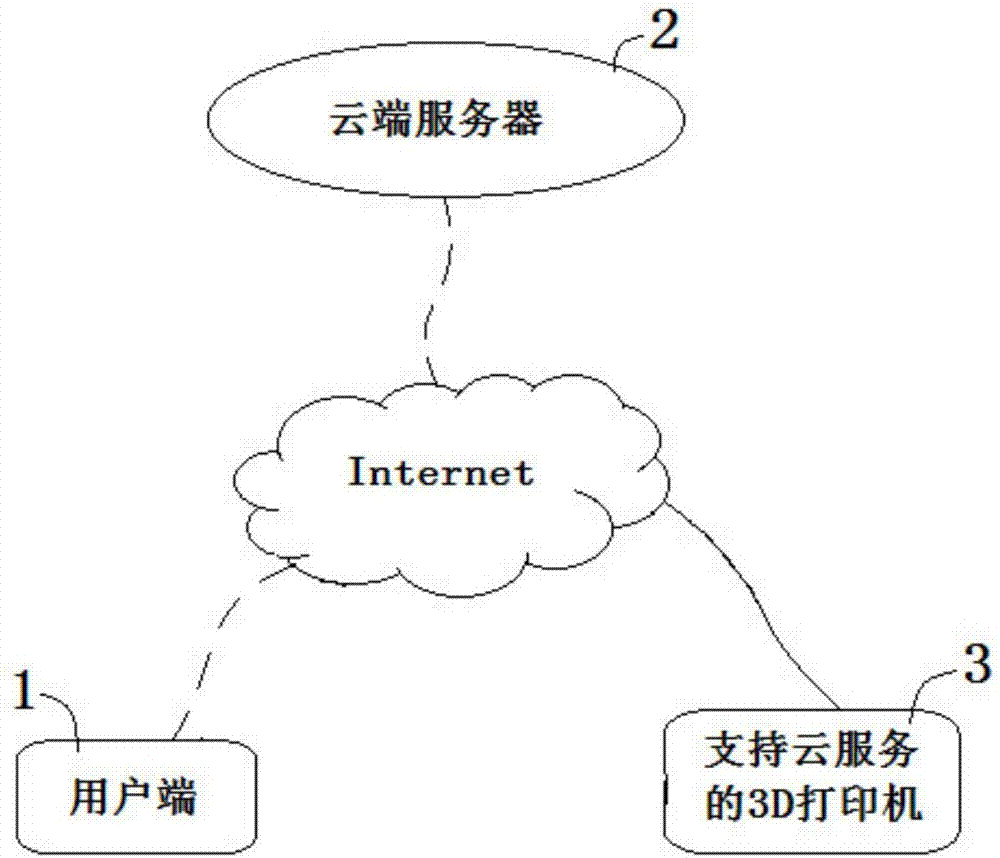
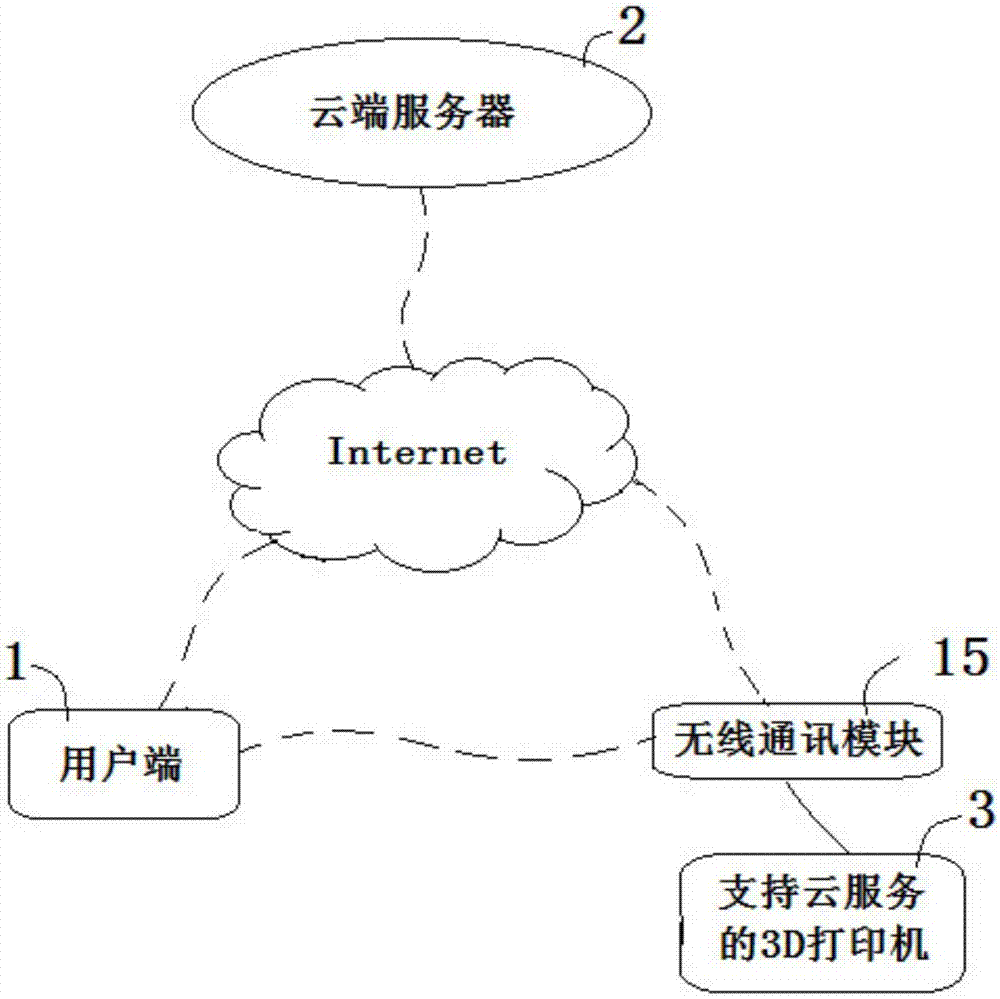
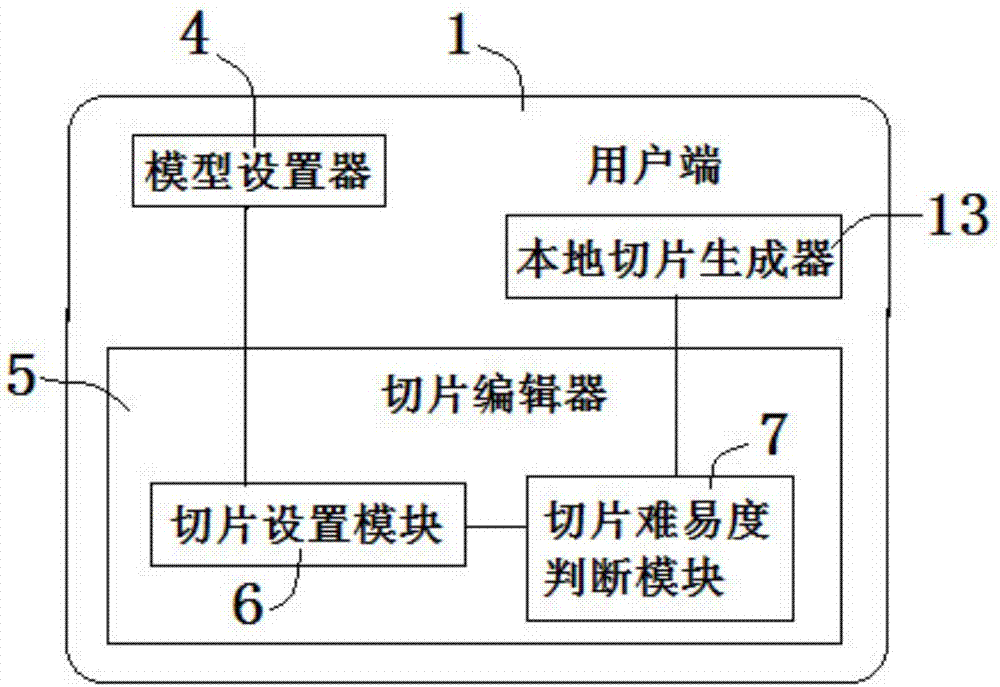
ActiveCN107368268ASolve the problem that cannot be controlled remotelySolve adaptation problemsAdditive manufacturing apparatusManufacturing data aquisition/processingControl systemThe Internet
The invention relates to a 3D printer control system for supporting a user side. The system comprises the user side, a cloud side server and a 3D printer for supporting cloud service, the user side, the cloud side server and the 3D printer interact with one another through the Internet, the user side comprises a model setter, a slice editor and a local slice generator, the model setter selects a to-be-printed 3D model, and the slice editor sets a slice strategy, and calculates the number of nodes and sections, and if the number of the nodes or the sections is lower than a set numerical value, the local slice generator generates a local 3D print text and a slice preview; the cloud side server comprises a 3D model library and a cloud side slice generator, if the number of the nodes or the sections is higher than the set numerical value, the user side uploads the slice strategy, the cloud side slice generator generates a cloud side 3D print text according to the slice strategy, and the user side downloads the cloud side 3D print text and afterwards generates a slice preview; the 3D printer receives the 3D print texts and afterwards conducts 3D printing work. According to the 3D printer control system for supporting the user side, remote manipulation of the 3D printer is achieved, and the system is adaptive to 3D printers of various types.
Owner:BEIJING JUZHENKONGJIAN TECH CO LTD
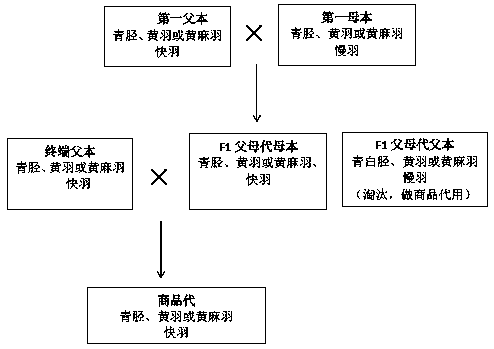
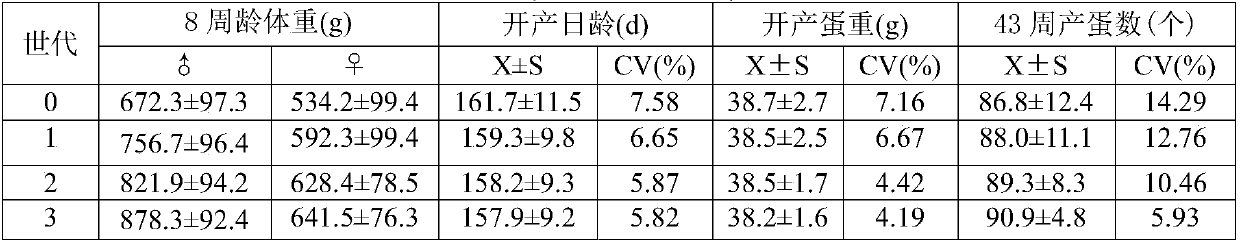
Hybrid seed production method of high uniformity yellow chicken complete set line suitable for chilled marketing
ActiveCN108029634AProtect intellectual propertyImprove survival rateAnimal husbandryHybrid seedAnimal science
The invention belongs to the technical field of poultry genetic breeding, and particularly relates to a hybrid seed production method of high uniformity yellow chicken three-line combination suitablefor chilled marketing. According to the method, a slow-feathering, yellow-feathering and green-shank chicken line is adopted as a first male parent, a fast-feathering, yellow-feathering, yellow-shank,high-yield and high-quality chicken line is adopted as a first female parent, and hybridization is conducted to obtain an F1 female parent; a local chicken line which is fast-feathering, and yellow-feathering, jute-feathering, sexual precocity and big cockscomb in appearance with the weight within + / -10% of the average weight is selected as a terminal sire, and hybridization is conducted betweenthe terminal sire and the F1 female parent to obtain commercial generation with high uniformity. According to the method, by means of regular and molecular breeding, selections of physical conformation, sexual precocity, weight uniformity and slaughter traits and comprehensive selection of meat quality traits are focused on and carried out, the bred yellow chicken commercial generation is high inuniformity and survival rate, and significant in heterosis; and the chicken has big cockscomb, green shank, fine pores and firm skin.
Owner:JIANGSU INST OF POULTRY SCI +1
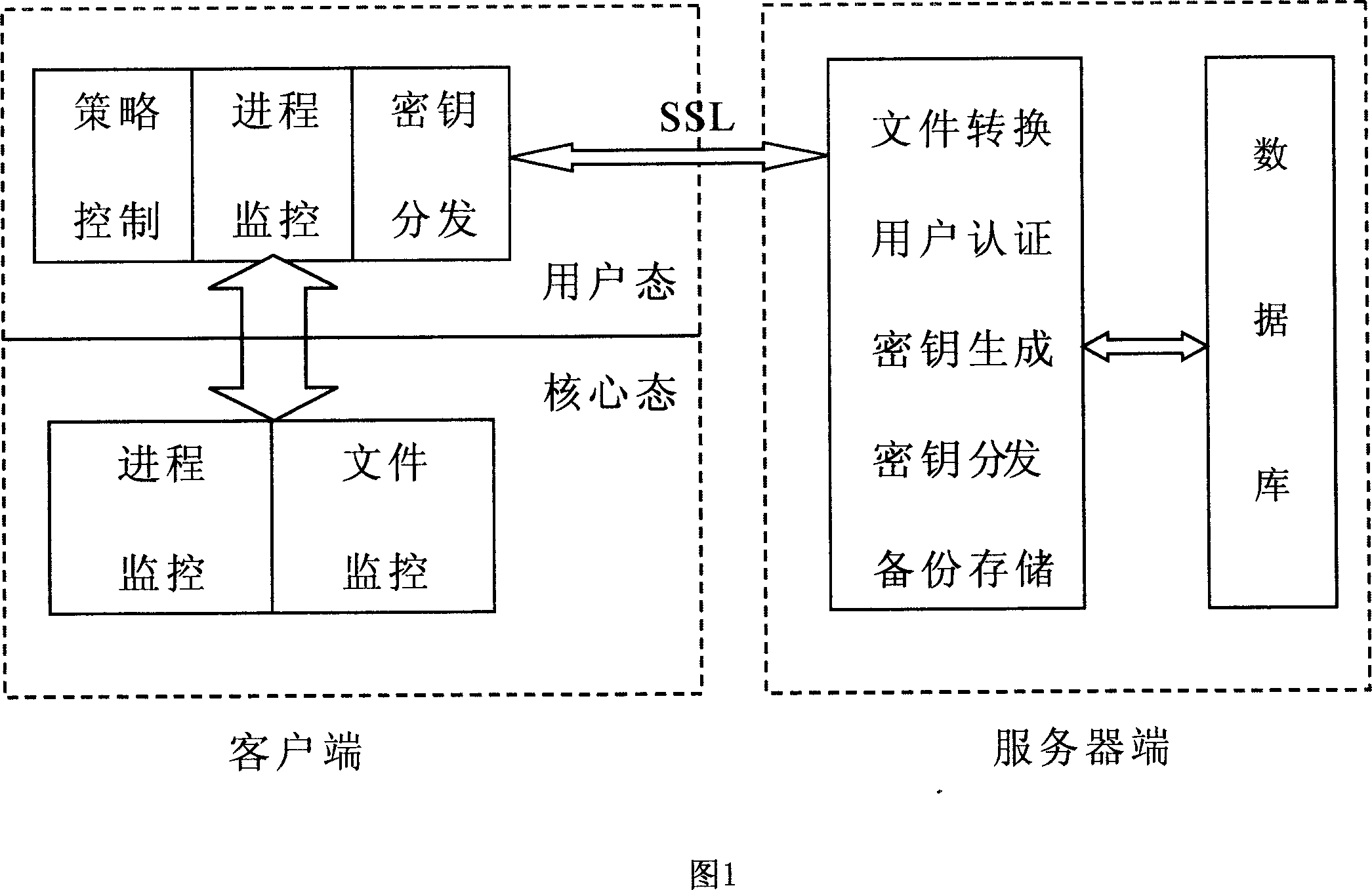
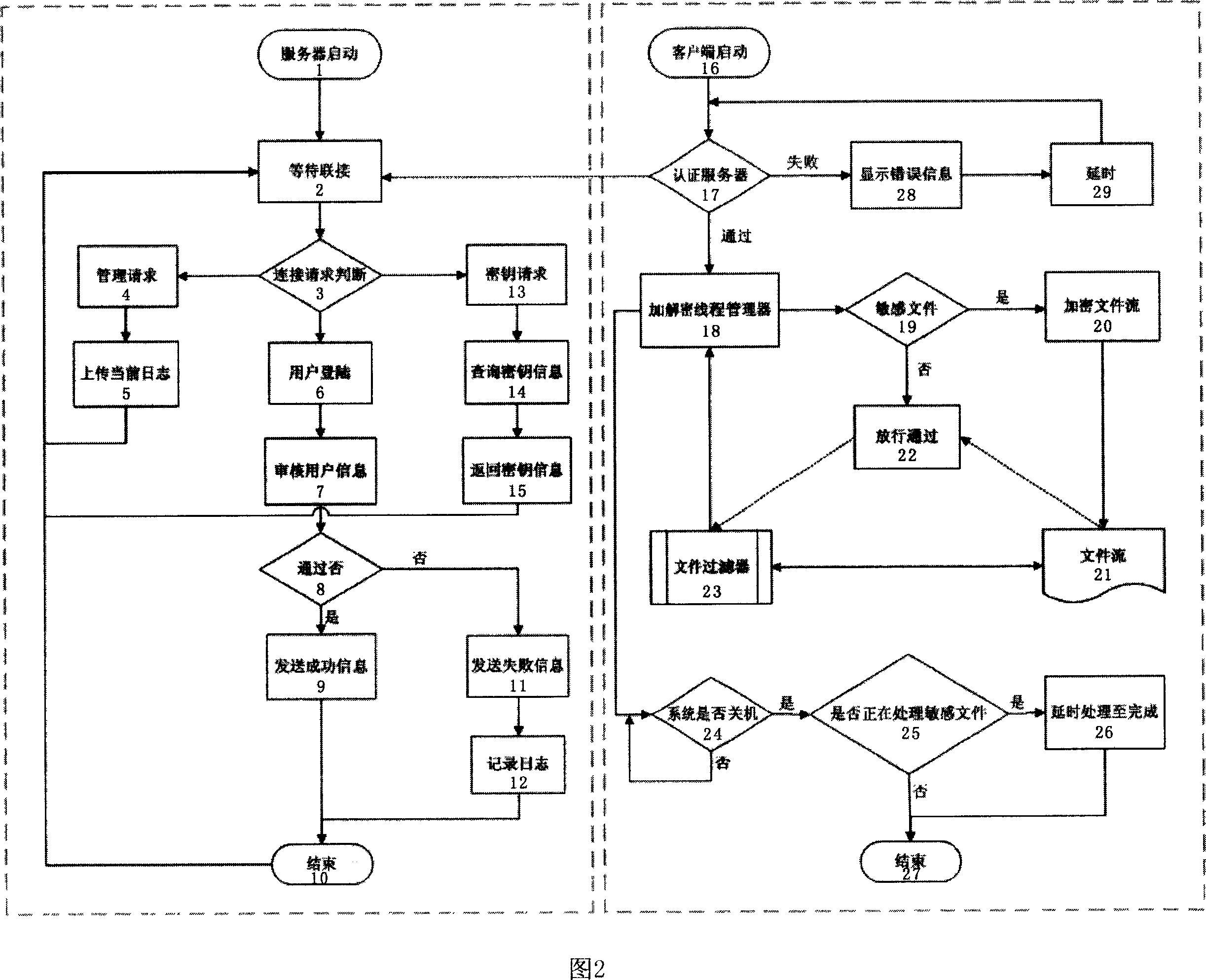
Method for encrypting/deciphering dynamically data file
InactiveCN101098224ASolve confidentiality issuesGuaranteed uptimePublic key for secure communicationUnauthorized memory use protectionPlaintextOperational system
The invention discloses a method for dynamically encrypting and decrypting data document, which comprises that in network condition, via C / S mode, manager centralized controls important documents of user computer, the system dynamically decrypts and encrypts clear text, the important documents can only be read or changed under the control of server in special network condition, which content is shown as cryptogram when off the network condition, when user copies clear text document from other places, the documents can not be changed when the system is sensitive, or else, in storage, the documents are converted into cryptogram type. The invention is based on software platform, correlated only with operation system, but not application programs, to dynamically encrypt and decrypt the data documents, therefore, the data documents can only work in private network condition, while the leaked document is in cryptogram type, to protect intellectual property.
Owner:CHINA NON-FERROUS METALS PROCESSING TECH CO LTD
Integrated circuit program burning method and burning system
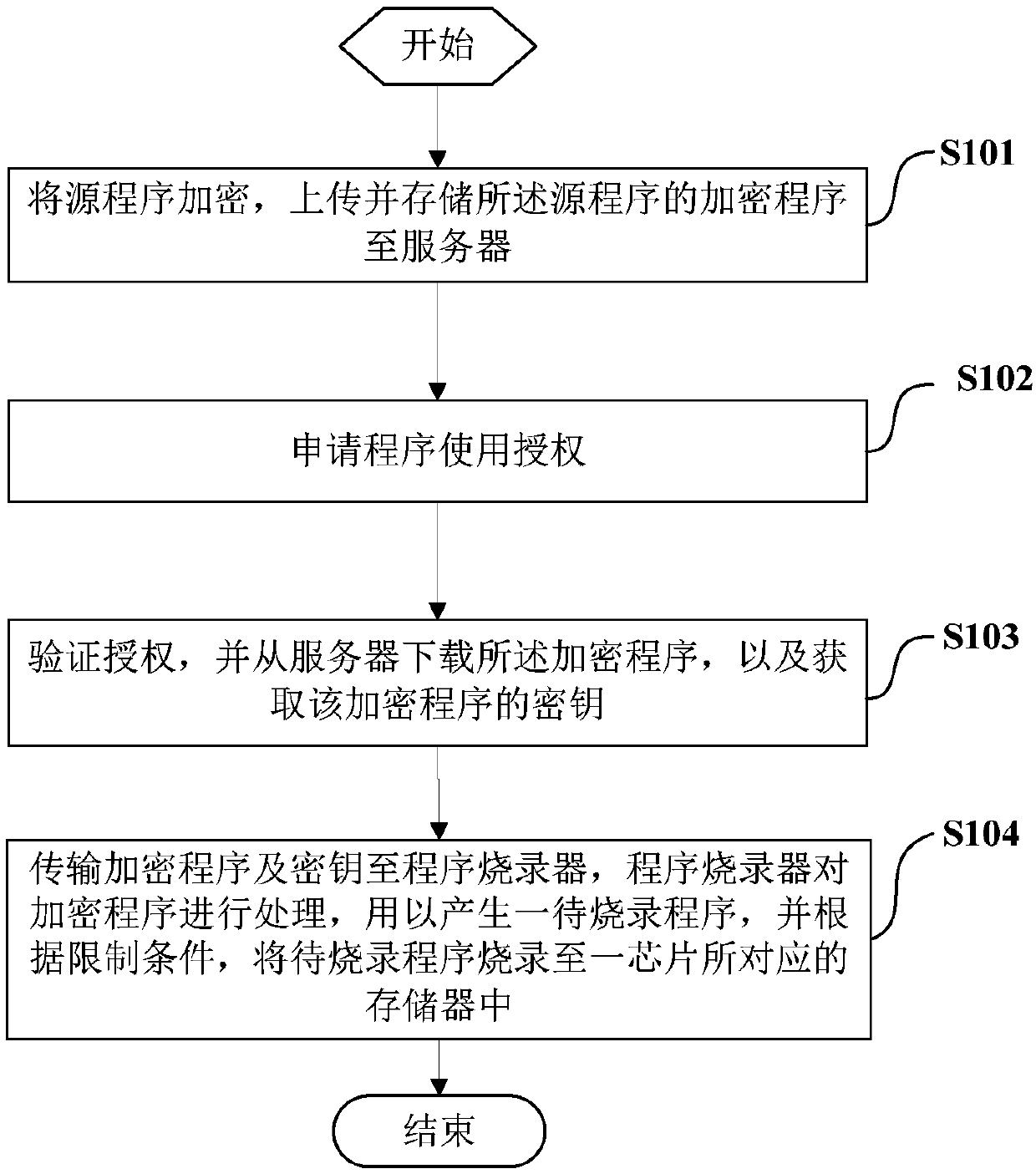
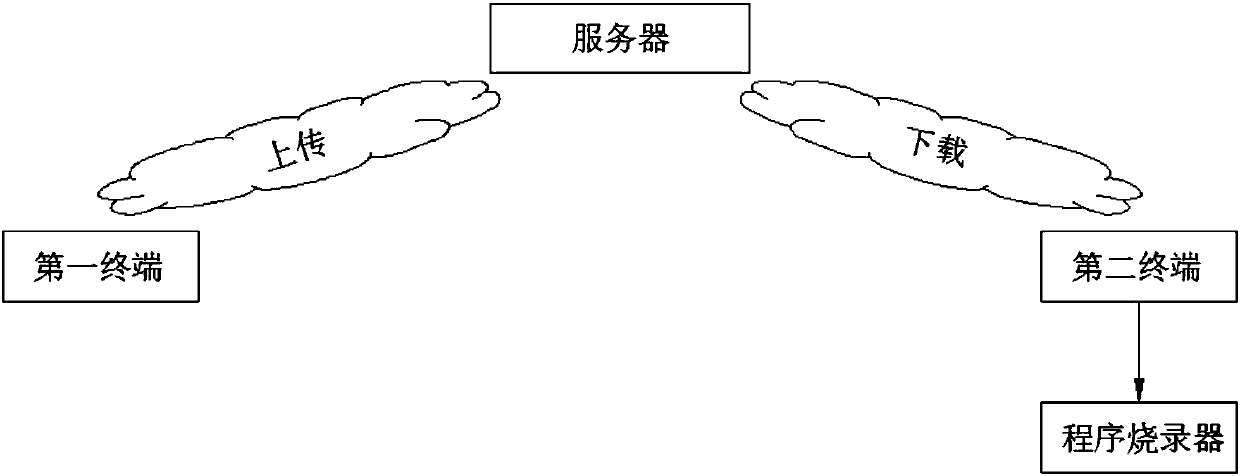
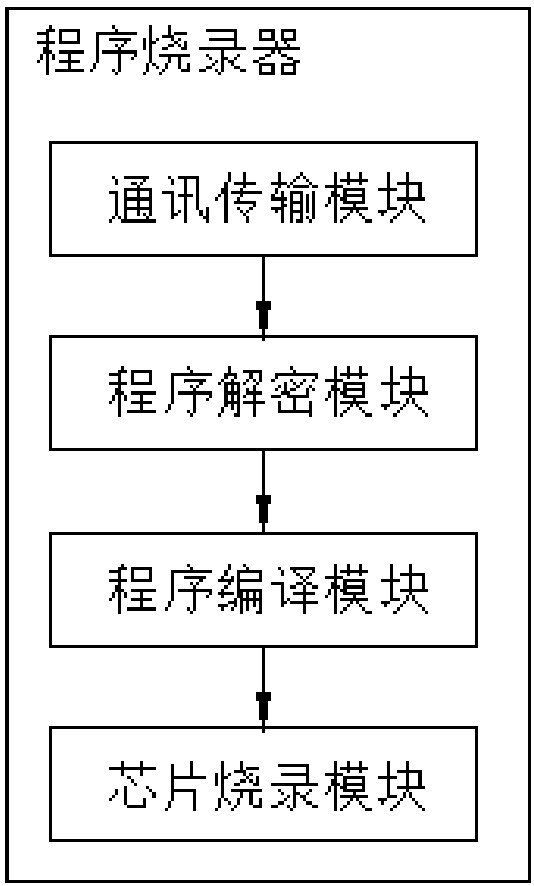
ActiveCN107729723AProtection of rights and interestsProtect intellectual propertyTransmissionProgram/content distribution protectionSoftware engineeringAuthorization
The invention relates to an integrated circuit program burning method and burning system, wherein the integrated circuit program burning method comprises the following steps of encrypting source program, and uploading and storing encryption program of the source program to a server; applying for program use authorization; verifying the authorization; downloading the encryption program from the server, and obtaining a secret key of the encryption program; transmitting the encryption program and the secret key to a program burner; processing the encryption program by the program burner so as togenerate program to be burnt; burning the program to be burnt to a memory corresponding to a chip according to limiting conditions. The integrated circuit program burning method and burning system have the advantages that a program user can obtain the encryption program and the secret key by only obtaining the authorization of a program developer; the encryption program can be burnt to the memoryof the chip only after the encryption program is sent to the burner; in the whole process, the program user does not obtain the source program and cannot perform decompilation on the encryption program, so that the rights and interests and the intellectual property of the developer are protected.
Owner:SHENZHEN XIDUN TECH CO LTD
Method for realizing associative simulation of machine and control system based on service
InactiveCN101533262AProtect intellectual propertyImprove reuseSimulator controlTransmission protocolLoose coupling
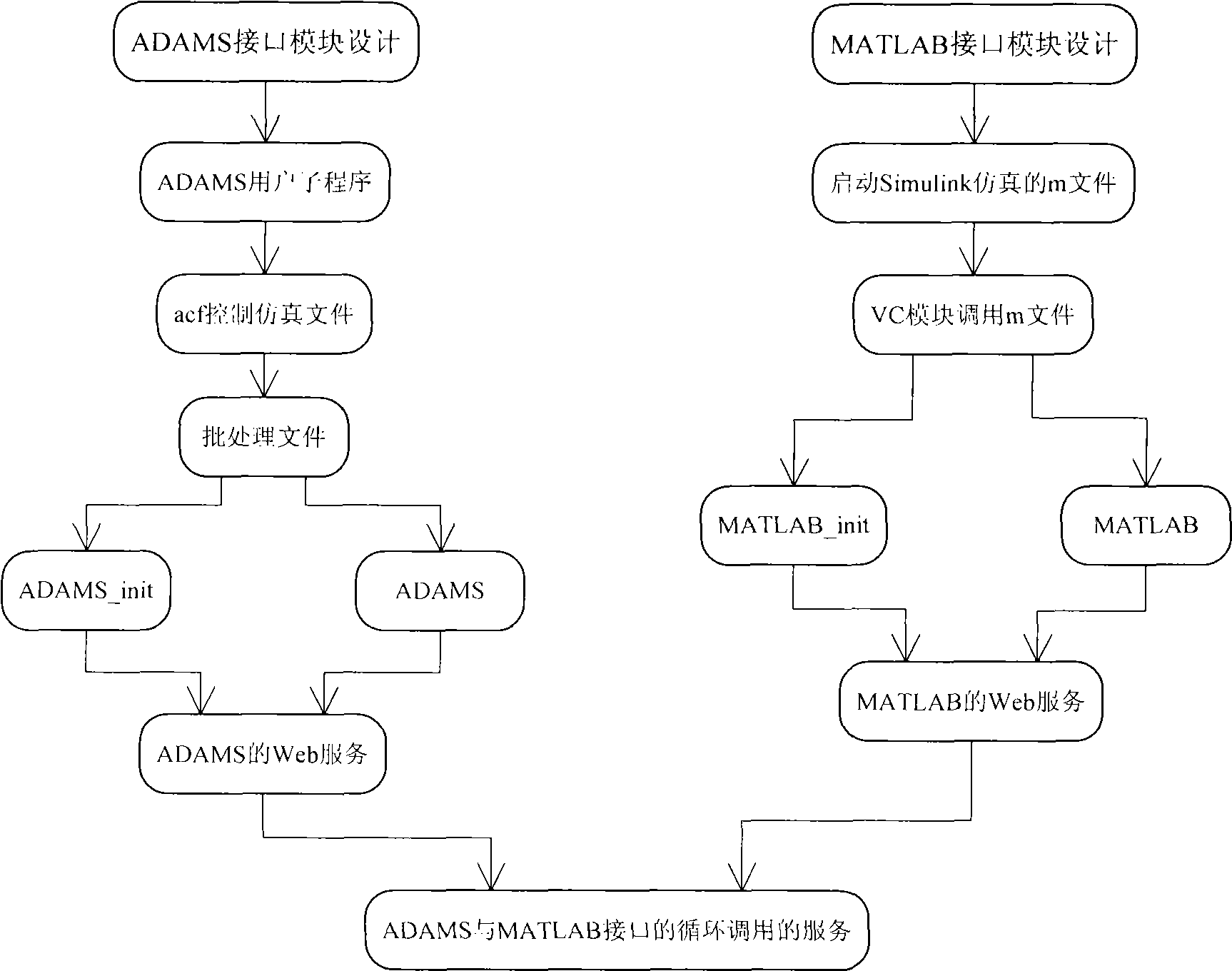
The invention provides a method for realizing associative simulation of machine and control system based on service. The method comprises three main steps of a first step of compiling an ADAMS universal interface module and encapsulating to be Web service; a second step of compiling an MATLAB universal interface module and performing Web service encapsulation; and a third step of registering and issuing Web service, and realizing application program associative calling of wide area network. The invention comprises application program encapsulation based on service and realizes loose coupling between ADAMS and MATLAB under a service-oriented architecture (SOA), and transparent position and transport protocol by means of an ADAMS user subprogram and an MATLAB engine technique, so as to meet the optimisation requirements of complex product on distributed collaborative simulation in multiple fields. The invention solves the integration and module reusability of the existing ADAMS mechanical system and MATLAB control system in distributed collaborative simulation, supports the Web service encapsulation of ADAMS and MATLAB and supports distributed collaborative simulation in multiple fields in the wide area network environment. The collaborative simulation system has simple construction, strong expansibility and wide application prospect.
Owner:BEIHANG UNIV
Device and method for controlling a fluid actuator
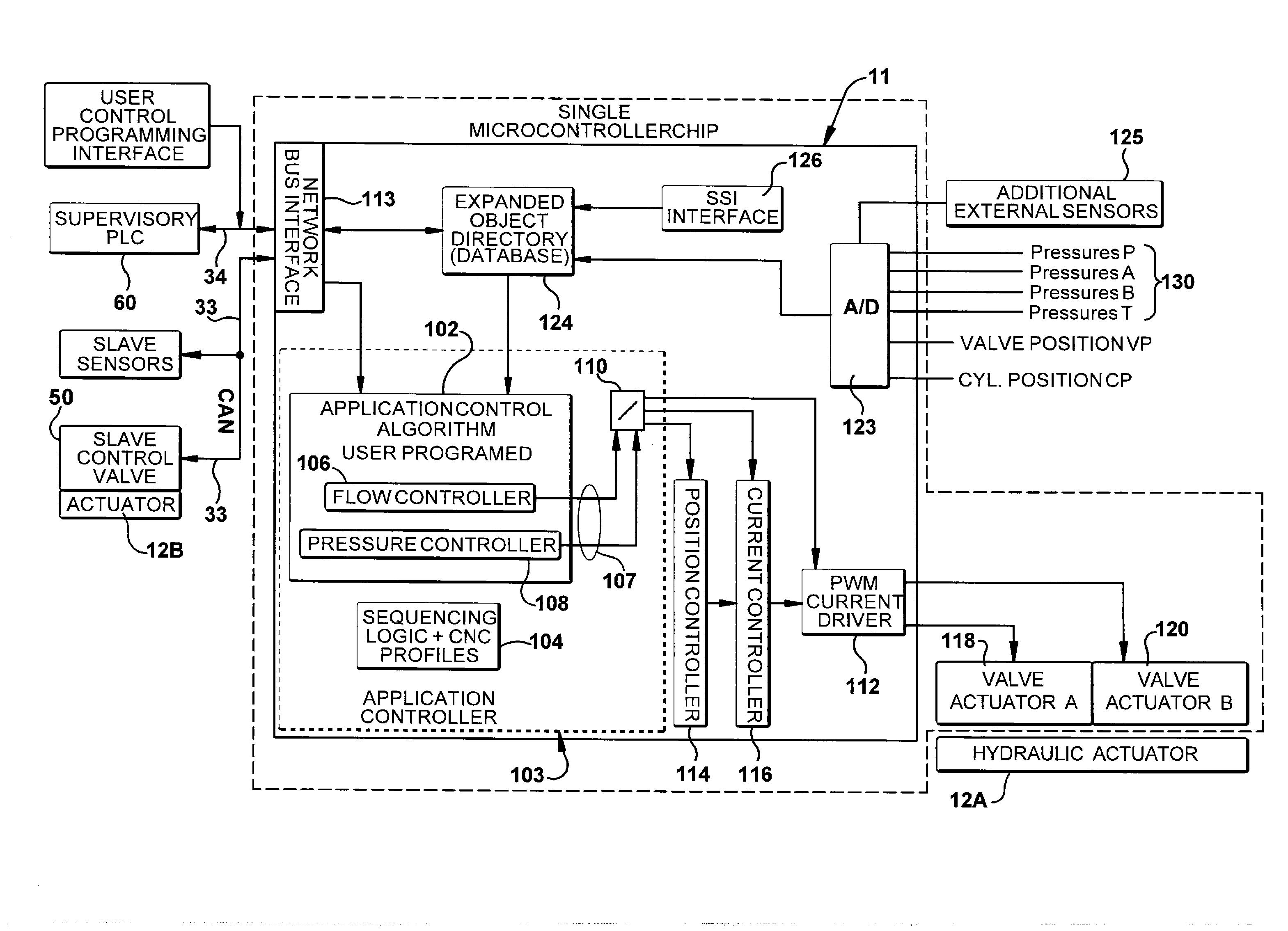
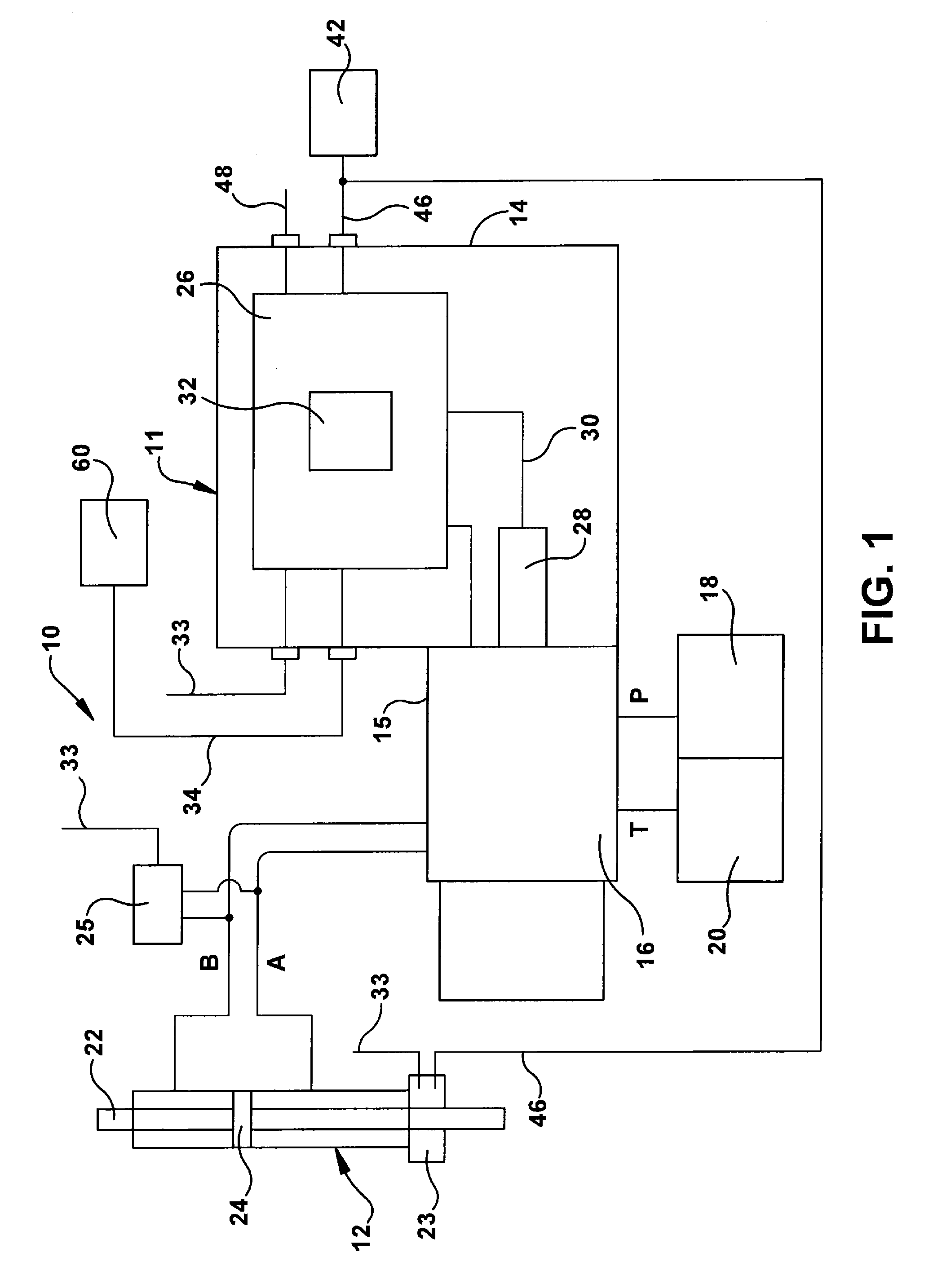
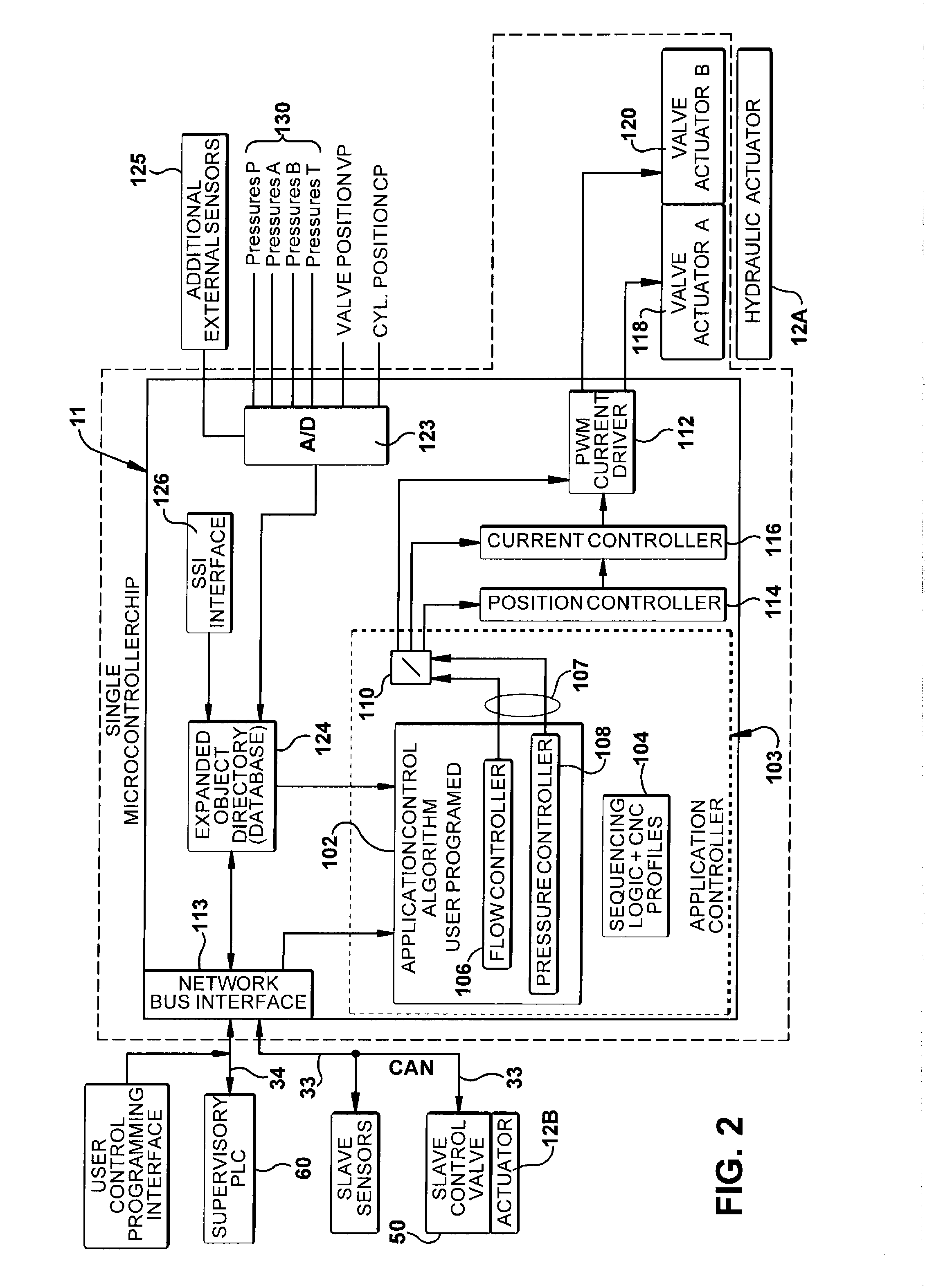
ActiveUS20110208362A1Improve dynamic performanceIncrease chanceComputer controlSimulator controlElectricityOn board
A device for controlling the motion of a fluid actuator which includes an electrically operated control valve that controls the flow of a pressurized fluid to and from the fluid actuator in response to signals generated by an actuator controller which uses an on-board, user programmable microprocessor where the user can download various control algorithms into the microprocessor for controlling the motion of the actuator based on such parameters as fluid pressure and flow rates and actuator displacement. Various external sensors can be connected to the controller for monitoring and control purposes using various signal interfaces such as an analog to digital converter or an SSI interface. A local communication bus is used to communicate with one or more slave actuators each having their own electrically operated control valve that controls the flow of a pressurized fluid to and from the slave actuator in response to control signals generated by the controller and sent to the slave control valve over the local bus. Sensors are used to measure various operating parameters of the slave actuator and generate signals that are sent to the controller over the local bus. A supervisory computer is used to send a high level command signal to the controller where the controller generates a closed loop control signal to one or more fluid actuators.
Owner:DANFOSS AS
Identification method for stacked two-dimensional code with a plurality of characters and numbers in complicated background
InactiveCN108009460AProtect intellectual propertyAvoid enteringSensing by electromagnetic radiationGraphicsCrucial point
The invention provides an anti-counterfeit identification method based on hybrid stacking of a plurality of characters and numbers of a two-dimensional code. The method comprises the steps of calculating a communicating threshold, extracting a position detecting pattern area according to gravity center detection and area ratio, obtaining four corner points of the two-dimensional code through a line segment with longest distance among three position detecting patterns, eliminating influence of two-dimensional deformation and photographing angle to corner point detection of the two-dimensional code, respectively calculating an innermost square area, a middle square area and an outer square area of the position detecting pattern according to the center of the position detecting pattern by means of three times of area increase, calculating the corner points of the outer square area of the position detecting pattern by means of approximation of two sets of lines, calculating the edge key points of four boundaries of the two-dimensional code by means of a bridging method, calculating the length of the curve between the key points of the deformed two-dimensional code by means of integration, and calculating the corresponding coordinates of the key points on the deformed two-dimensional code on the corrected image through a telescoping ratio. The anti-counterfeit identification methodis a new anti-counterfeit identification method and effectively protects related knowledge property and economic benefit of legal manufacturers.
Owner:姚佑霖
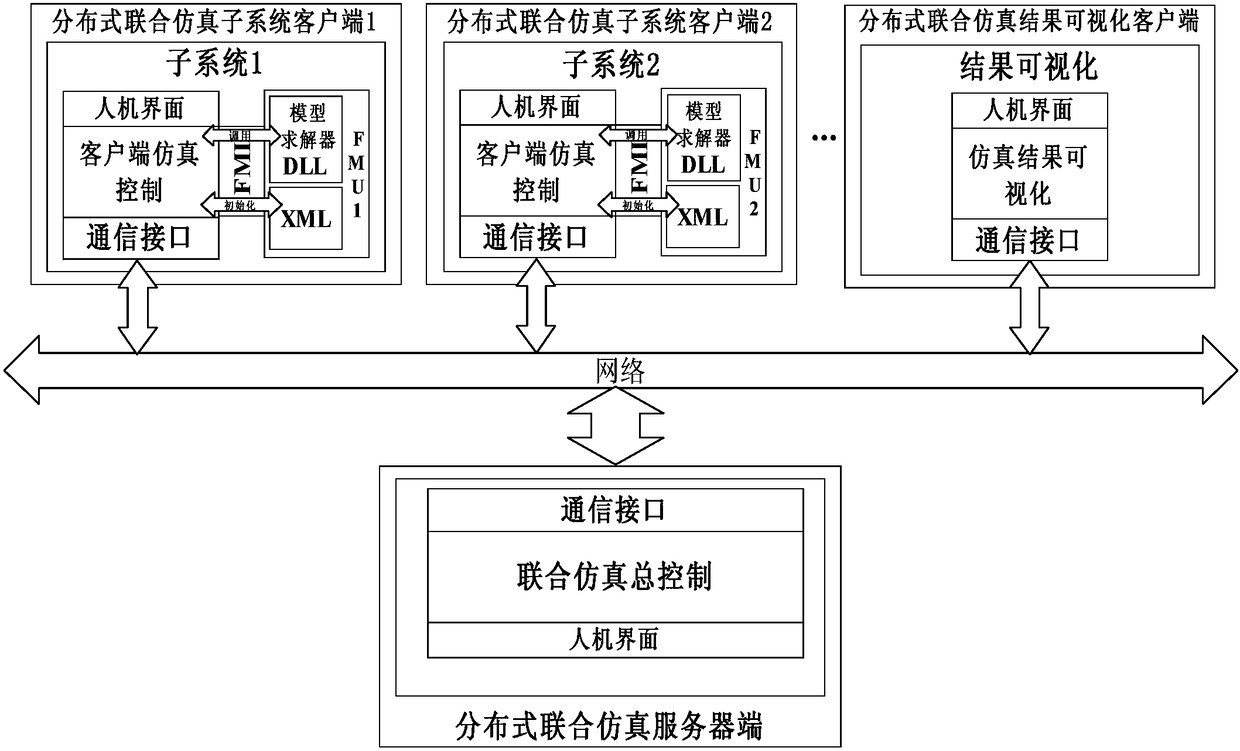
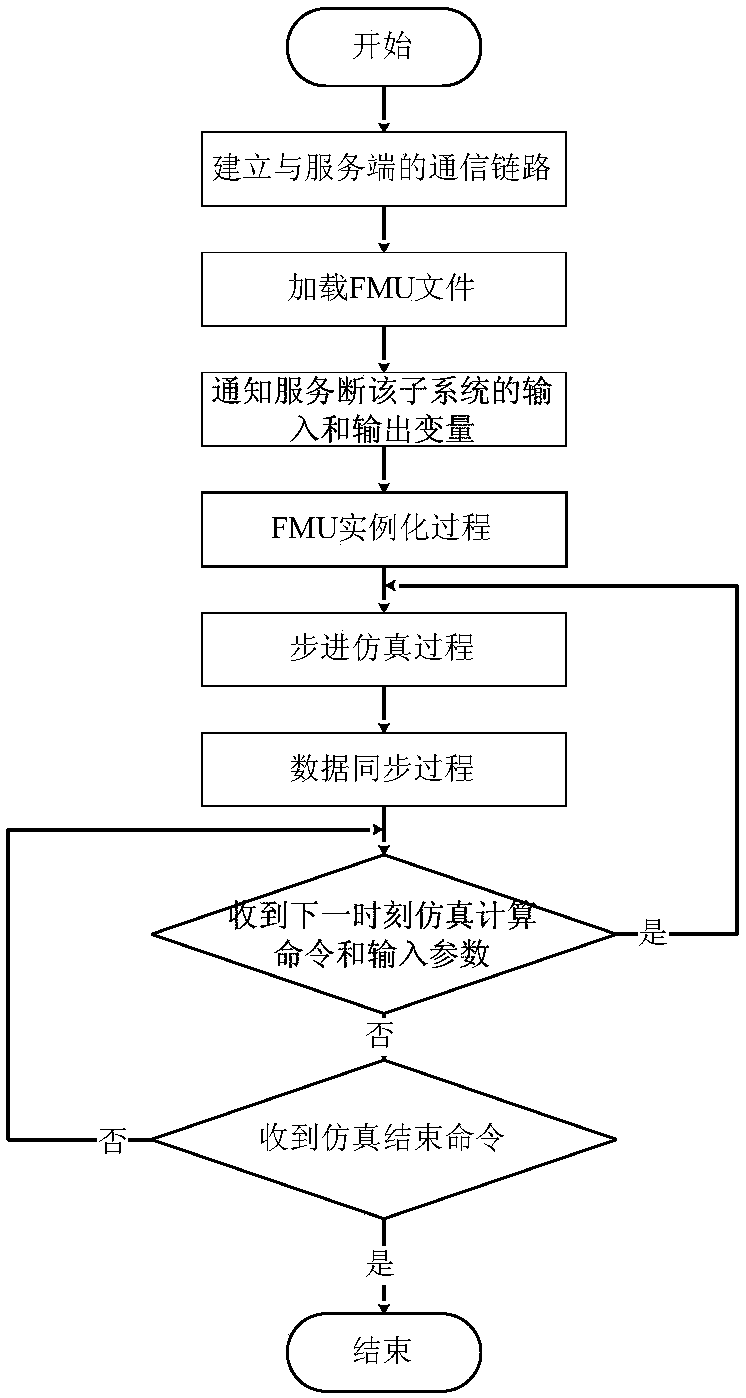
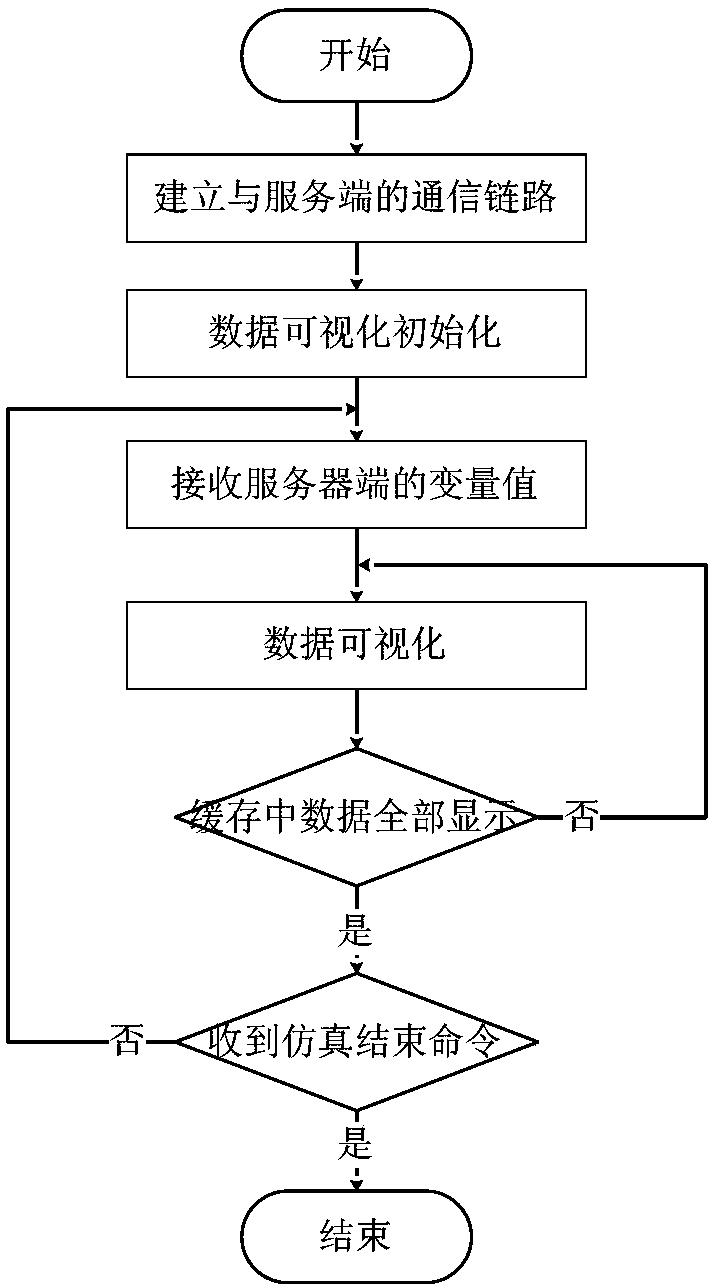
Distributed full-digital joint simulation system and method
InactiveCN108427776ARealize simulationEnable co-simulationDesign optimisation/simulationSpecial data processing applicationsSynchronous controlIntellectual property
The invention relates to a distributed full-digital joint simulation system and method, and particularly aims at realizing full-digital joint simulation according with an FMI standard by using distributed and client / server structures in coupling system design and iterative verification stages. The system consists of three parts: a distributed joint simulation subsystem client, a distribution jointsimulation result visualization client and a distributed joint simulation server, wherein the distributed joint simulation subsystem client is mainly used for realizing digital simulation calculationof each subsystem; the distributed joint simulation result visualization client is mainly used for realizing visualization of simulation results; and the distributed joint simulation server is mainlyused for realizing synchronous control of joint simulation. According to the system and method, joint simulation of heterogeneous system models is realized, joint simulation of cross-geographic areasis realized, and black box-mode simulation is adopted so that the intellectual properties are protected.
Owner:中国科学院沈阳计算技术研究所有限公司
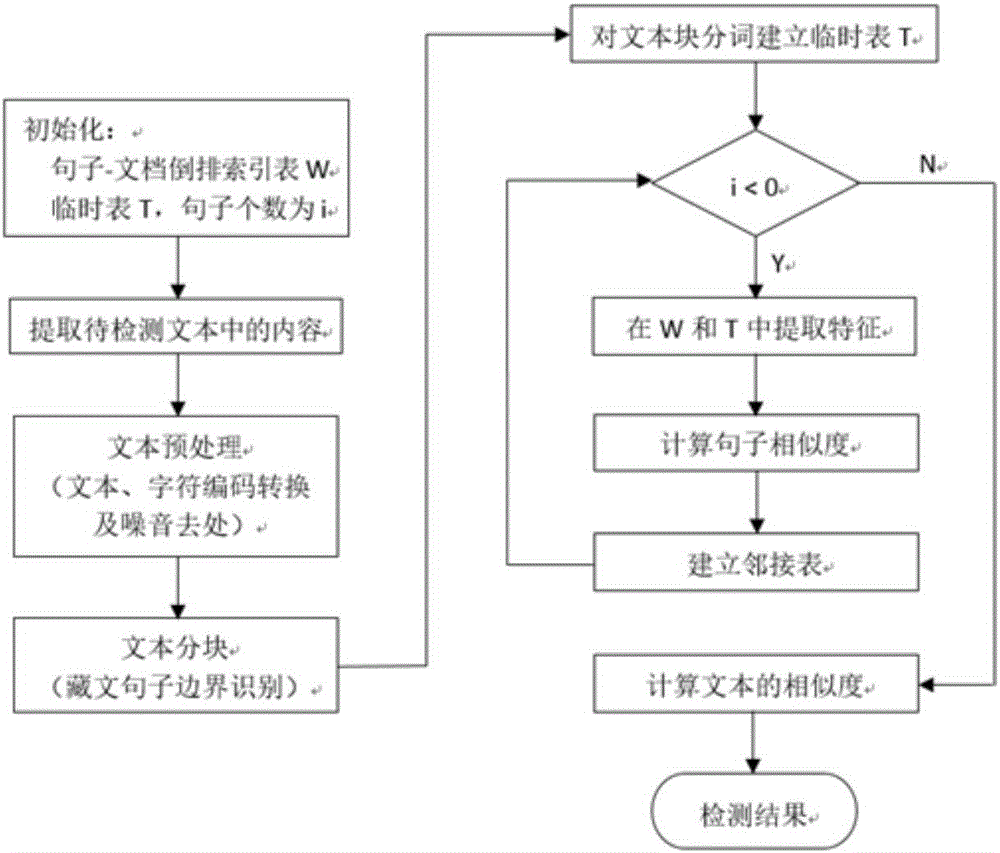
Tibetan language thesis copying detection method and Tibetan language thesis copying detection system based on Tibetan language sentence levels
PendingCN106227897AComputableSimplify complex relationshipsWeb data indexingNatural language data processingTerminal serverThe Internet
The invention discloses a Tibetan language thesis copying detection method and a Tibetan language thesis copying detection system based on Tibetan language sentence levels. The Tibetan language thesis copying detection method includes: subjecting Tibetan language text characters to code conversion and noise removal preprocessing; segmenting a text into text blocks according to sentences through boundary identification of Tibetan language sentences and establishing a temporary table of segmented text blocks; extracting and computing text features from a sentence-document inverted index table and the temporary table according to the number of the sentences to obtain sentence similarity; establishing an adjacency list in accordance with the sentence similarity, computing text block similarity and detecting copying of two Tibetan language theses according to a text block similarity value. The Tibetan language thesis copying detection system comprises a Tibetan language thesis copying detection device and a database, wherein the Tibetan language thesis copying detection device is connected to a client terminal server through the Internet, and the database is connected to the server and used for storing Tibetan language theses. The Tibetan language thesis copying detection device comprises a preprocessing module for code conversion and noise removal of the text characters, a temporary table module for constructing the segmented text blocks, an extracting module for constructing sentence text features and a copying detection module for detecting whether the theses have similar copied data or not.
Owner:QINGHAI UNIV FOR NATITIES
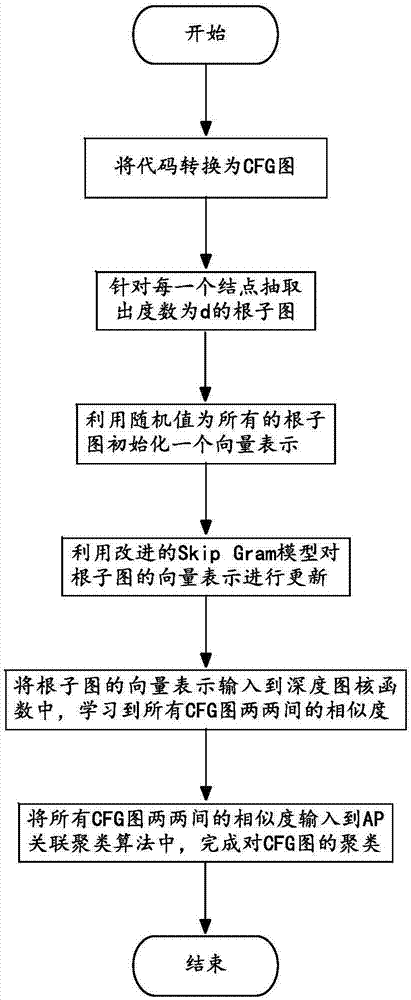
Duplicated code detecting method based on neural network language model
ActiveCN107273294AAvoid the curse of dimensionalityGet similarityBiological neural network modelsSoftware testing/debuggingCluster algorithmPattern recognition
The invention discloses a duplicated code detecting method based on a neural network language model and belongs to the technical field of duplicated code detecting methods. The problem that duplicated codes unchanged essential cannot be detected by adopting a duplicated code detecting method in the prior art, accordingly the detection accuracy rate is low, and economic losses of code originators are likely caused is solved. The duplicated code detecting method comprises the steps that 1, each of codes is converted into a corresponding CFG image; 2, a root diagram of each node in each CFG image is extracted; 3, all the root diagrams are represented by adopting vectors; 4, the vector representations of the root diagrams are input into a depth diagram-kernel function for learning, and the similarity of all the CFG images is obtained; 5, the similarity of all the CFG images is input into an AP associating and clustering algorithm, CFG image clustering is performed to obtain multiple clustering clusters, and the codes corresponding to the CFG images in the same clustering cluster are duplicated codes. The duplicated code detecting method is used for finding duplicated codes.
Owner:UNIV OF ELECTRONICS SCI & TECH OF CHINA
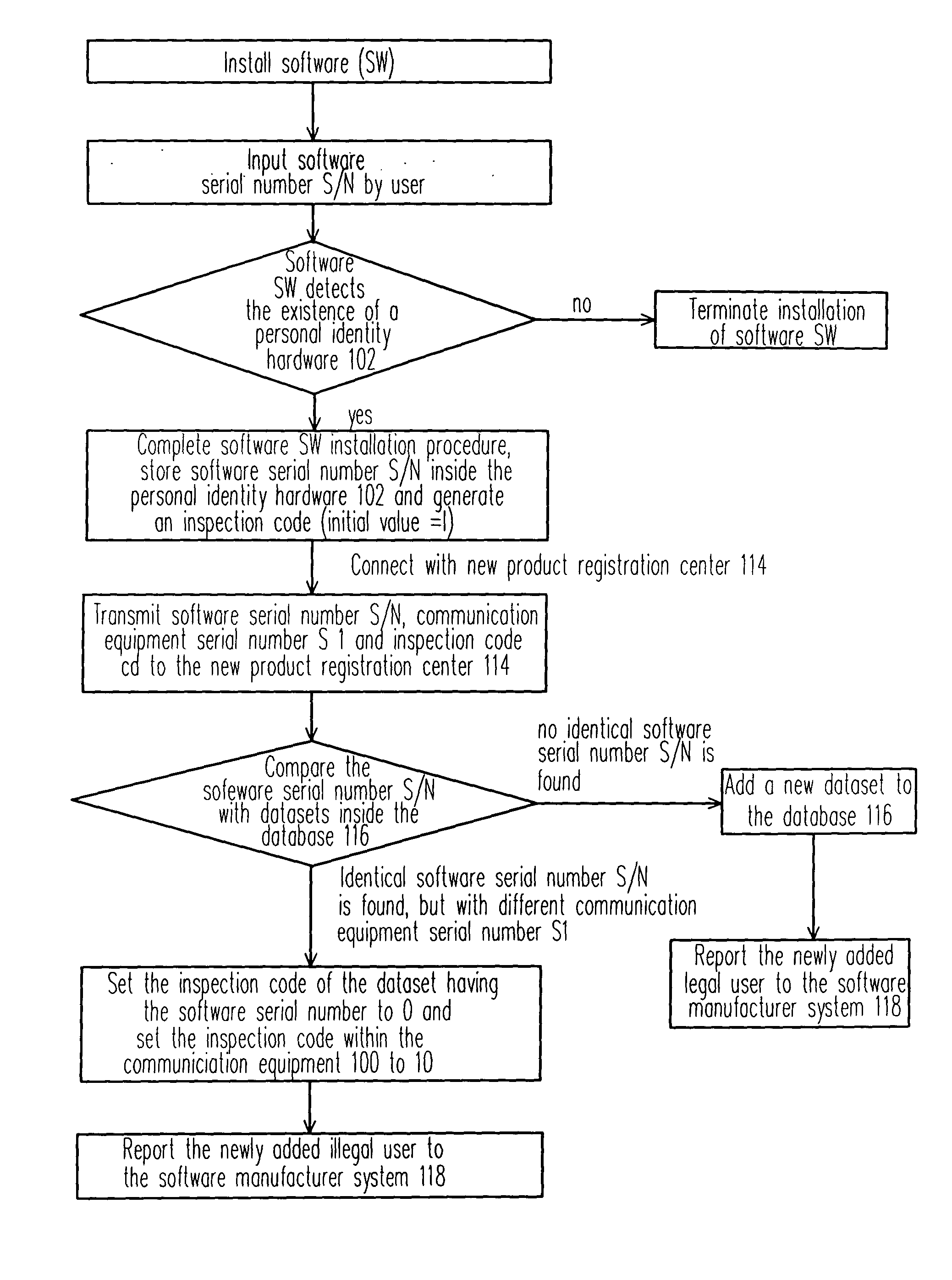
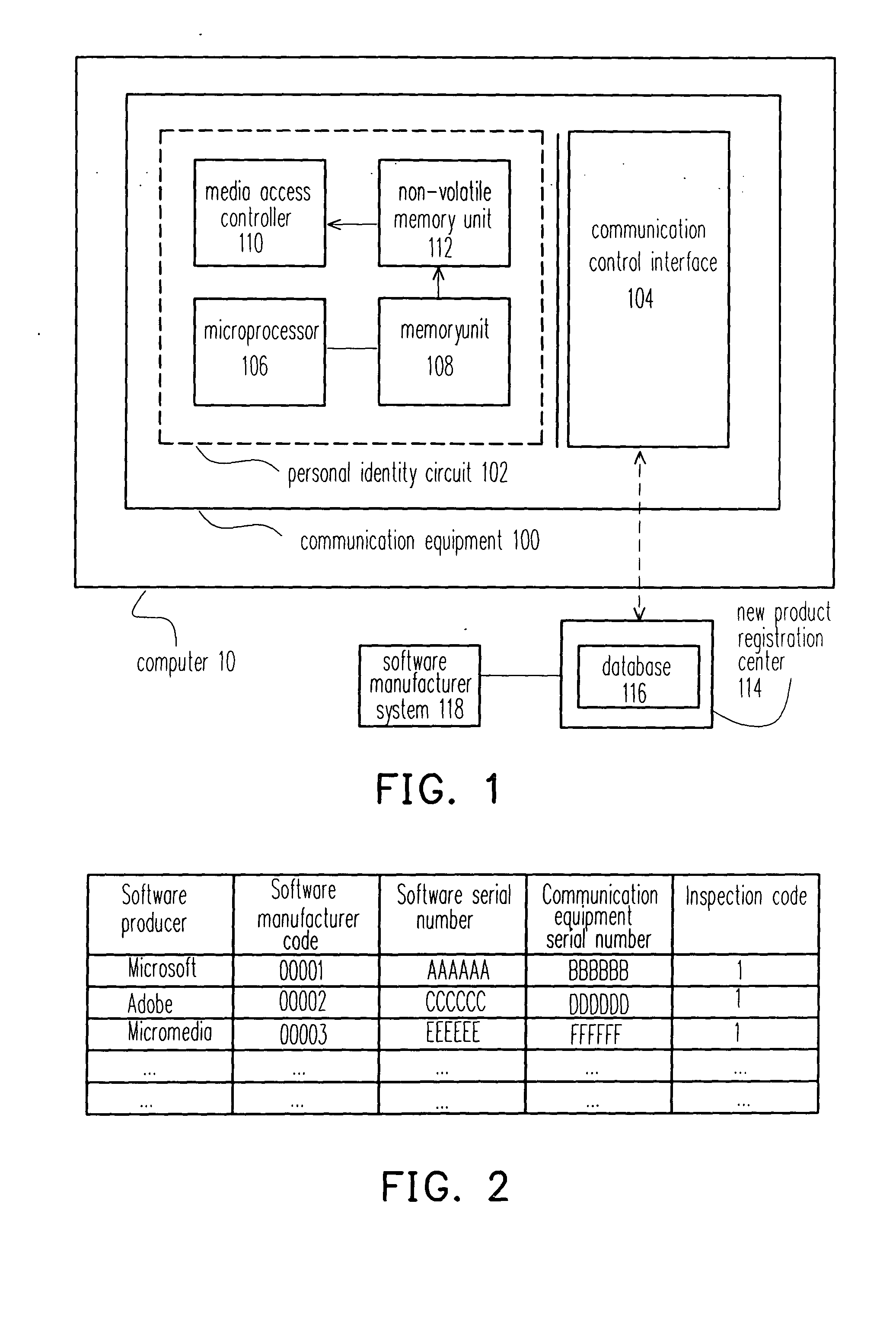
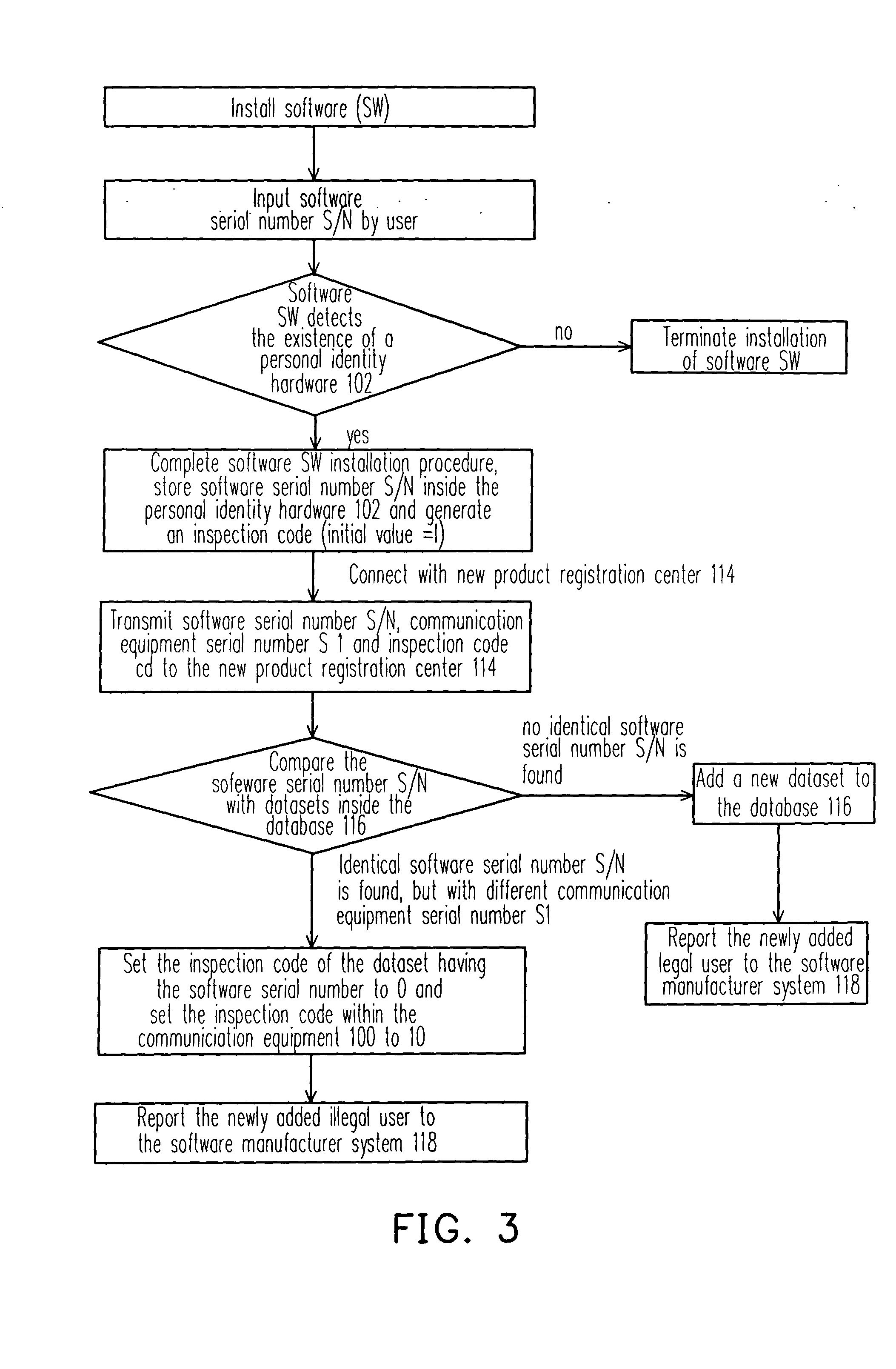
System and method for detecting illegal software loading by using hardware and used chips thereof
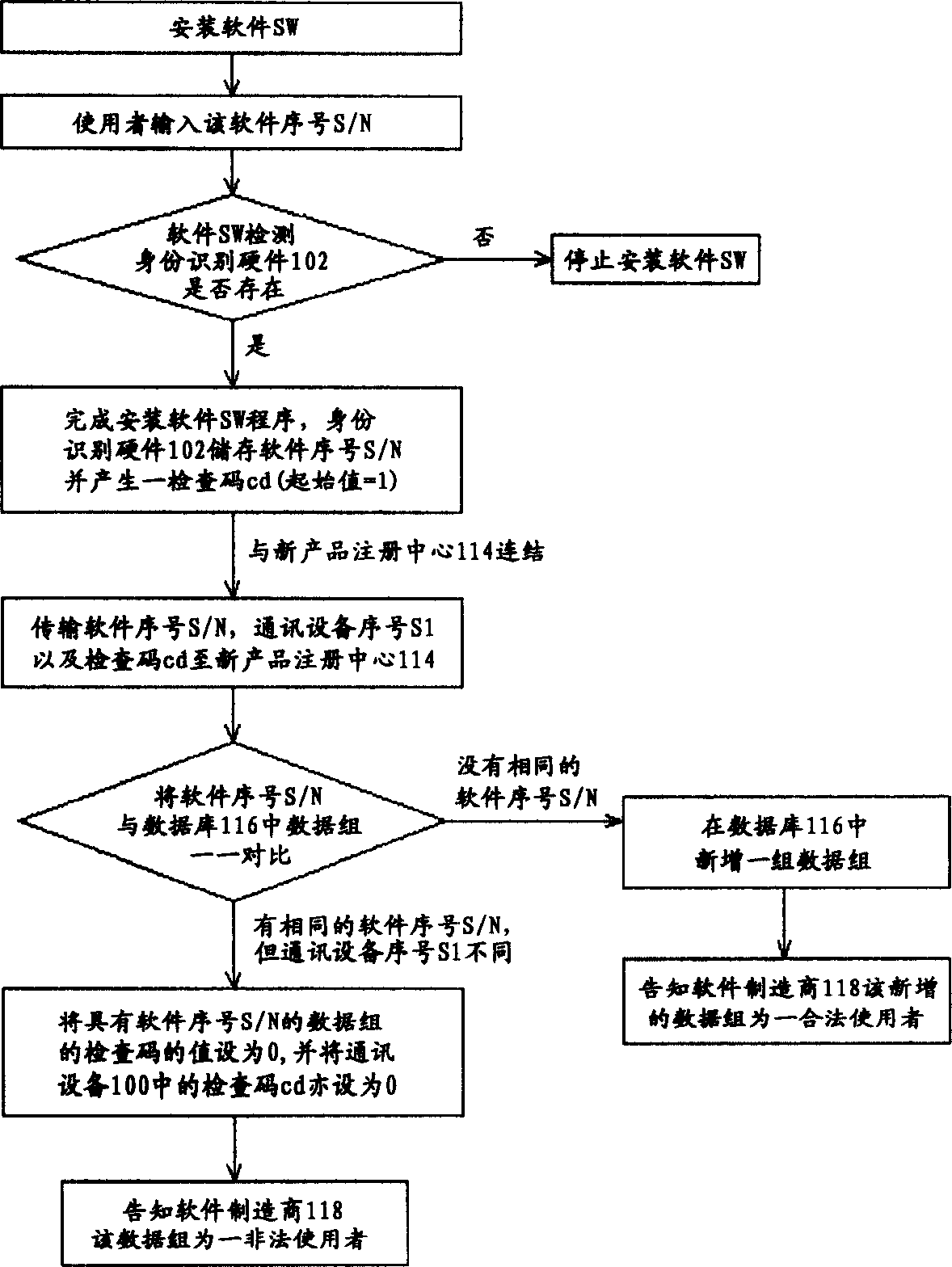
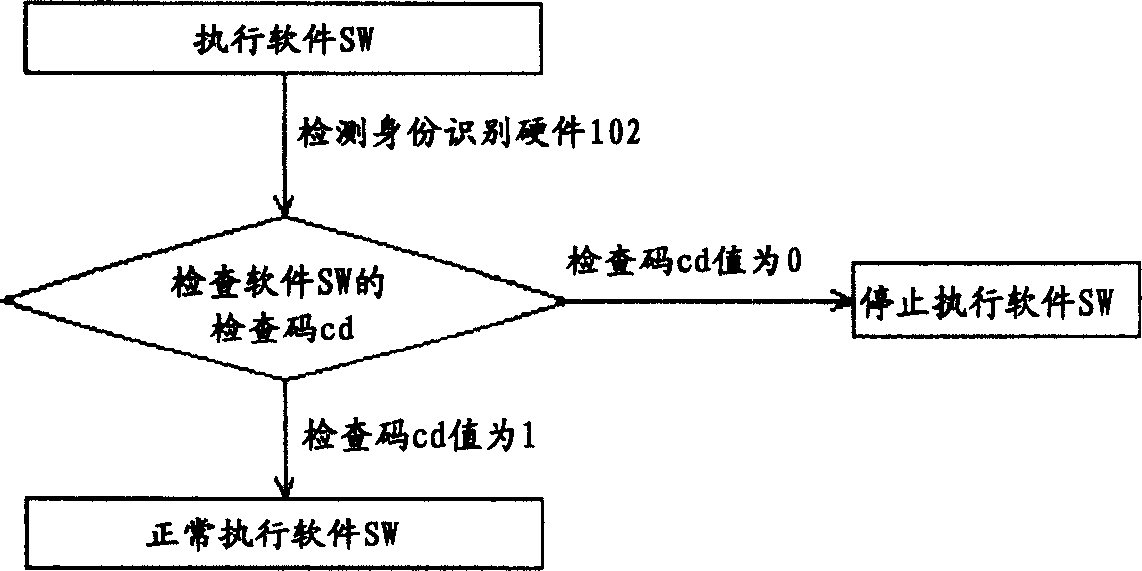
InactiveCN1595364AProtect intellectual propertyProtection of rights and interestsProgram loading/initiatingRedundant data error correctionComputer hardwareComputer science
The invention relates to a software copyright protecting system and the method together with its chips and peripheral system, which is a smart security-ID integrated circuit. In order to acquire the legal using right, the user has to register the software order number and the communication equipment order number of the user's computer to the smart security-ID integrated circuit. The smart security-ID integrated circuit can be used as a built-in module. At the same time, the built-in module can inform the manufacturer of the software, when the illegal user registers illegally.
Owner:UNITED MICROELECTRONICS CORP
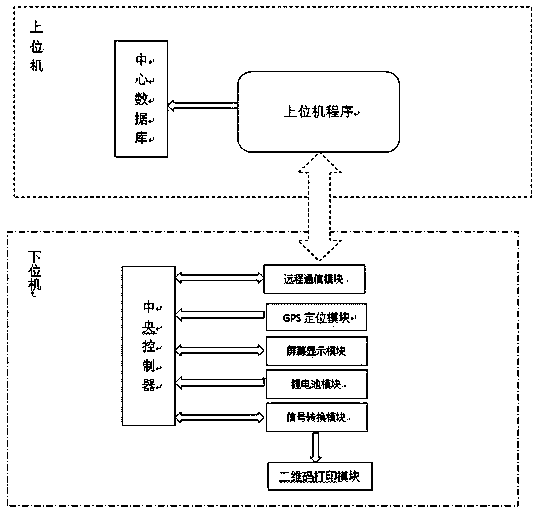
Two-dimensional code vegetable security traceability marking and inquiring system based on space-time information
InactiveCN105512902AUniqueness guaranteedProtect intellectual propertyCommerceRecord carriers used with machinesTime informationLong-haul communications
The invention discloses a two-dimensional code vegetable security traceability marking and inquiring system based on space-time information. The two-dimensional code vegetable security traceability marking and inquiring system comprises a central controller module, a positioning module, a screen display module, a remote communication module, a signal conversion module, a two-dimensional code printing module, a lithium battery module and a central database, wherein the positioning module, the screen display module, the remote communication module and the signal conversion module are all connected with the central controller module; the two-dimensional code printing module is connected with the signal conversion module; the remote communication module is in communication with the central database through a wireless signal; the lithium battery module is used for supplying power to the whole system. According to the two-dimensional code vegetable security traceability marking and inquiring system based on the space-time information, disclosed by the invention, the uniqueness and the authenticity of a two-dimensional code are ensured according to time information and space information of the generated two-dimensional code, accurate tracking on a complete process of production, processing, storage and selling of vegetables can be realized, and the vegetable quality safety supervision ability can be increased; the right of consumers to know the quality information of vegetable products is guaranteed through vegetable quality security traceability.
Owner:SHANDONG AGRICULTURAL UNIVERSITY
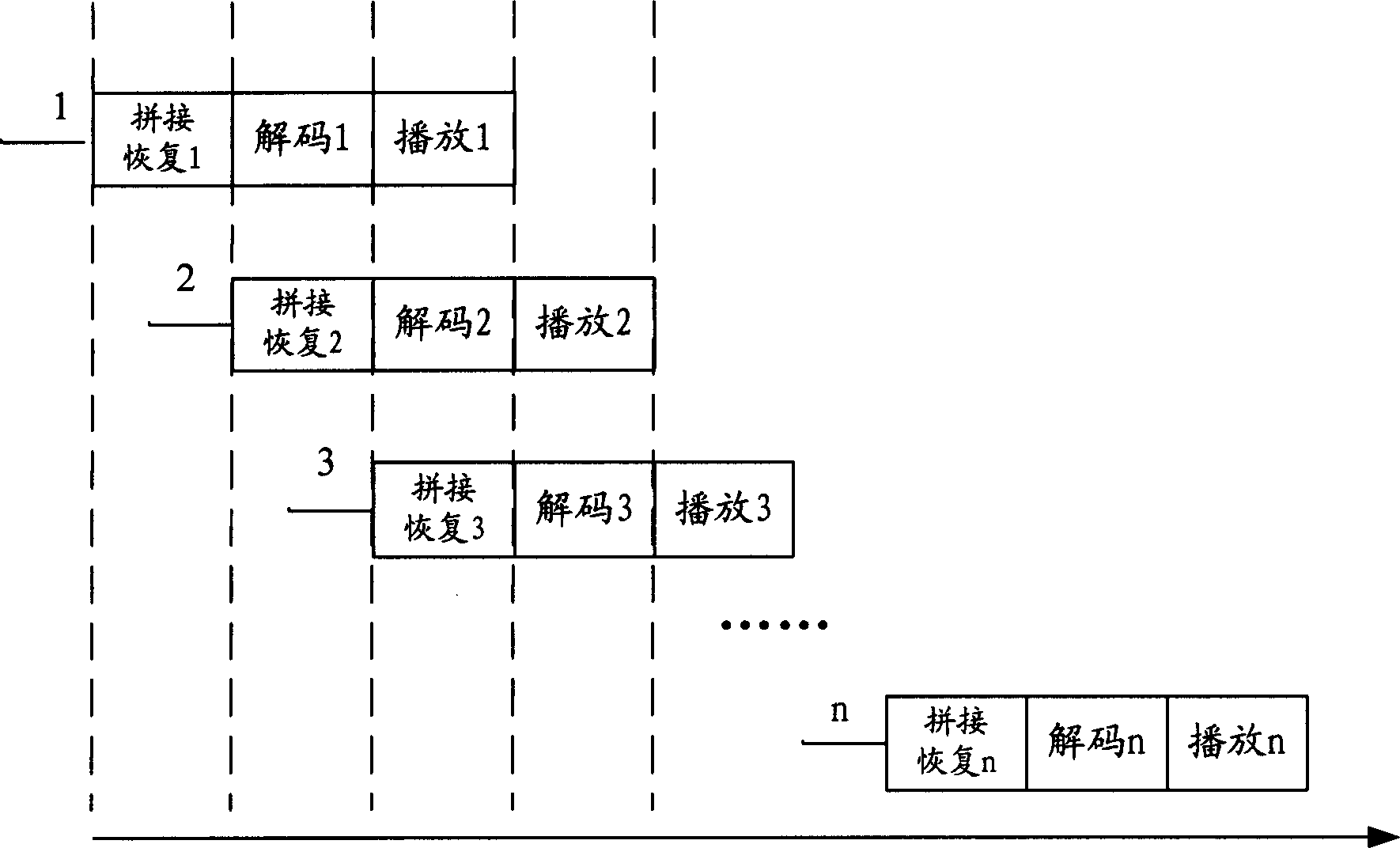
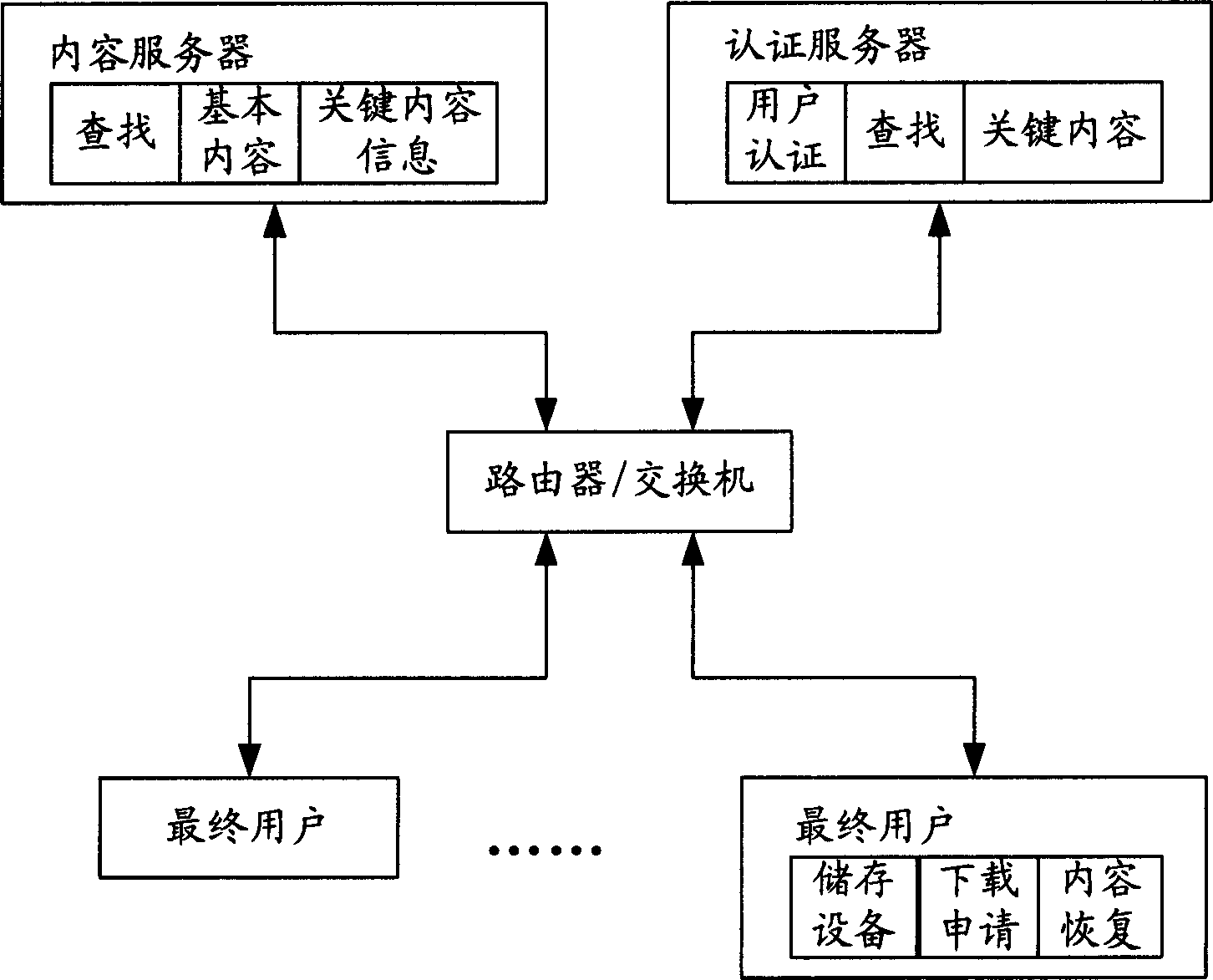
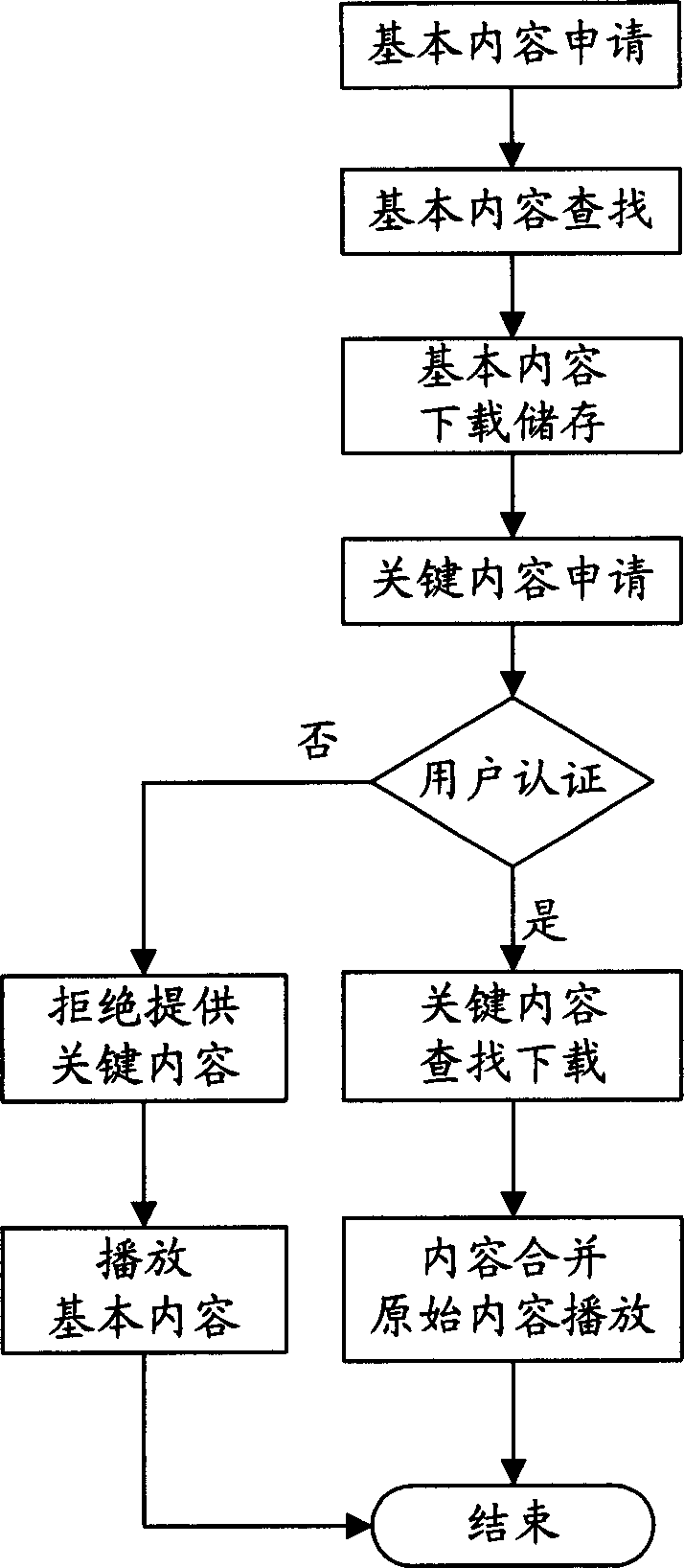
Multimedia web site spliting and reconstructing method
InactiveCN1337808AHigh speedSave bandwidthStore-and-forward switching systemsSpecial data processing applicationsClient-sideServer-side
The present invention discloses a multimedia web station separation and reproduction method, the separation includes the steps: making all the files of web station undergo the process of relative treatment, dividing result into two portions, one portion of them is the files placed in customer side, they are enciphered compressed multimedia raw material which can not be directly browsed, and the other portion is the pseudo-web pages which are remained in the server end and obtain after the orginal HTML web page document being in web station is modified. The reproduction in cludes the followingsteps: wehn a user uses computer with above-mentioned first portion contents to access the web station contaiing the above-mentioned second portion contents, the related pseudo web page can be automatically treated to produce formed web page document, then the deciphering decompression program is used to read out multimedia raw material stored in the customer side and make deciphering decompression so as to produce complete web page which can be correctly browsed by browsing device of customer side and its behavior is identical to that of original web page.
Owner:北大资产经营有限公司
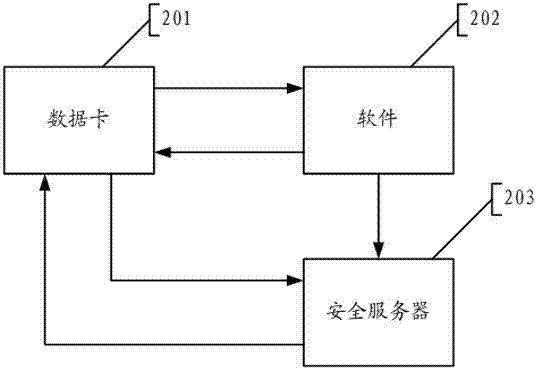
Software authentication data card, software authentication system and software authentication method
InactiveCN102480724AImprove protectionProtection of legal rightsTransmissionSecurity arrangementThe InternetSoftware protection
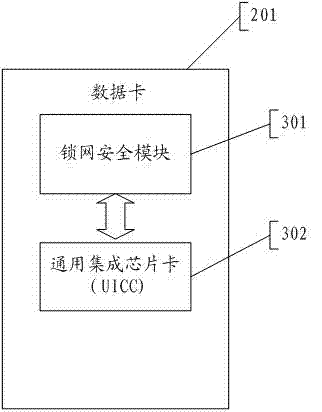
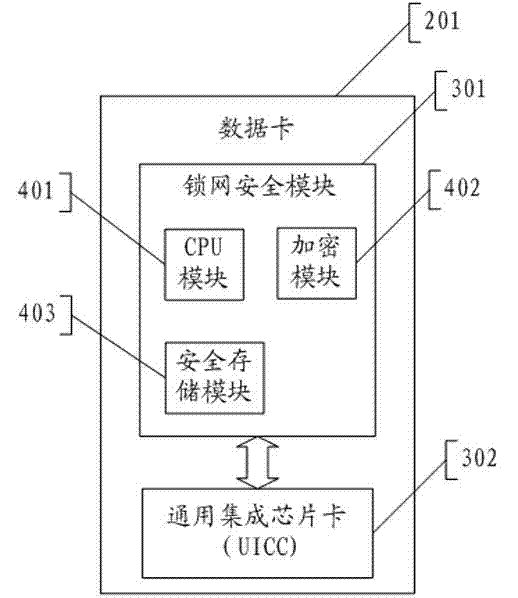
The invention relates to a data card with software authentication function, a software authentication system and a software authentication method. The data card includes a lock net security module that is arranged between a global system for mobile communications (GSM) module and a data card interface; and the lock net security module is used for receiving and storing key information of at least one piece of protected software and a software authentication parameter that is needed for execution of the key information as well as simultaneously carrying out authentication on the authentication parameter and international mobile subscriber identification number (IMSI) information provided by a universal integrated chip card (UICC). The software authentication system comprises the above-mentioned software authentication data card and a security server that is used for carrying out software registration according to the software authentication parameter and the key information of the protected software and the IMSI information of the UICC. And a host equipped with the protected software utilizes the software authentication data card to carry out communication with the security server by an internet. According to the invention, software protection can be effectively carried out and random software propagation and utilization can be prevented; moreover, the data card function can be expanded and external interfaces of equipment including a computer and the like can be saved.
Owner:NATIONZ TECH INC
DSP (Digital Signal Processing) and FPGA (Field Programmable Gate Array)-based universal controller of power electronic system
ActiveCN106774030AFacilitation of reliability researchImprove reliabilityProgramme controlComputer controlDigital signal processingControl signal
Owner:ZHEJIANG JUZI INTELLIGENT TECH
System, method and chip for hardware detection of illegal software user, computer system having hardware detection chip thereof and a software registration center
InactiveUS20050050347A1Prevent illegal useProtect intellectual propertyDigital data processing detailsAnalogue secracy/subscription systemsProtection systemComputer science
A software copyright protection system, method, chip and peripheral subsystem is provided. In one aspect of this invention, a smart security identity (SID) integrated circuit (IC) is used for registering a legal user. To become an authorized users of a particular software program, a software serial number and a communication equipment serial number must be submitted to the smart SID IC in a registration process to obtain a legal inspection code. The smart SID IC not only serves as a hardware serial number built-in module, but also reports to the software producer any illegal software registration attempts.
Owner:UNITED MICROELECTRONICS CORP
Creation method of sweet pepper SSR finger-print and application thereof
InactiveCN101748195AProtect intellectual propertyBreeder rights violationsMicrobiological testing/measurementSweet PeppersAgricultural science
The invention discloses a creation method of sweet pepper SSR finger-print and an application thereof. The method is as follows: screening SSR primer for different sweet pepper varieties and inbred line total DNA to obtain 12 pairs of SSR polymorphism molecular markers, and performing electrophoretic separation to obtain corresponding SSR molecular marker polymorphism gram through the 12 pairs of SSR polymorphism molecular markers. The technology can make definite conclusion on the sweet pepper genetype, performs genetic classification to sweet pepper breeding material which is not recorded on an exact pedigree, makes up the deficiency of the pedigree record, also can be used for identifing the hereditary feature of the inbred line of sweet pepper, and protects the variety of the inbred line against invasion.
Owner:SHANGHAI ACAD OF AGRI SCI
Separating and replaying method for video frequency image
InactiveCN1649412ARealize the operationProtect intellectual propertyPulse modulation television signal transmissionSelective content distributionDECIPHERComputer graphics (images)
This invention provides a method for the splitting and reproduction of video images including: the video image forms several reference frames and non-reference frames by encoding, among which, the splitting refers to extract a part or total compressed video image data in the above total or part reference frames, the extracted video compressed data are key contents, others are basic contents, which are stored or transmitted separately, a user decoder can split-join the key and basic contents to a complete original video image to play it if getting them the same time, if it cannot get the key content, then the decoded recovered image is wrong, which can protect the copyright of video images effectively not needing extra cipher / decipher algorithms.
Owner:BEIDA QINGNIAO INTEGRATED CIRCUIT BEIJING
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com