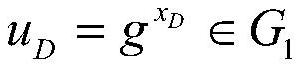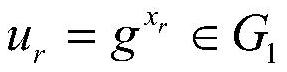Patents
Literature
38results about How to "Solve confidentiality issues" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
RFID (Radio Frequency Identification Device) based seafood supply chain traceability system under exclusive shop direct sales model
InactiveCN101819656AAvoid defectsImprove work efficiencyCo-operative working arrangementsCommerceRelevant informationNetwork connection
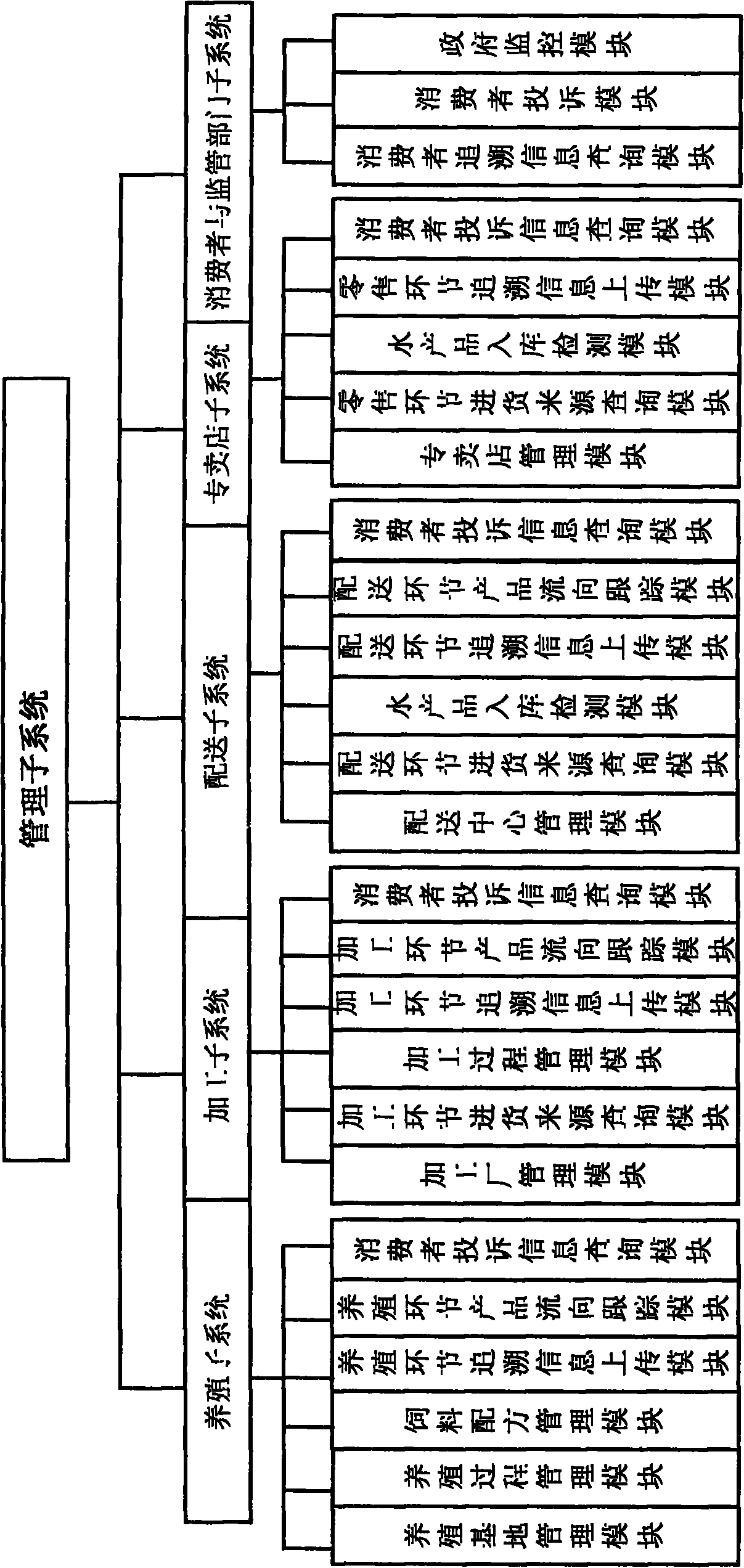
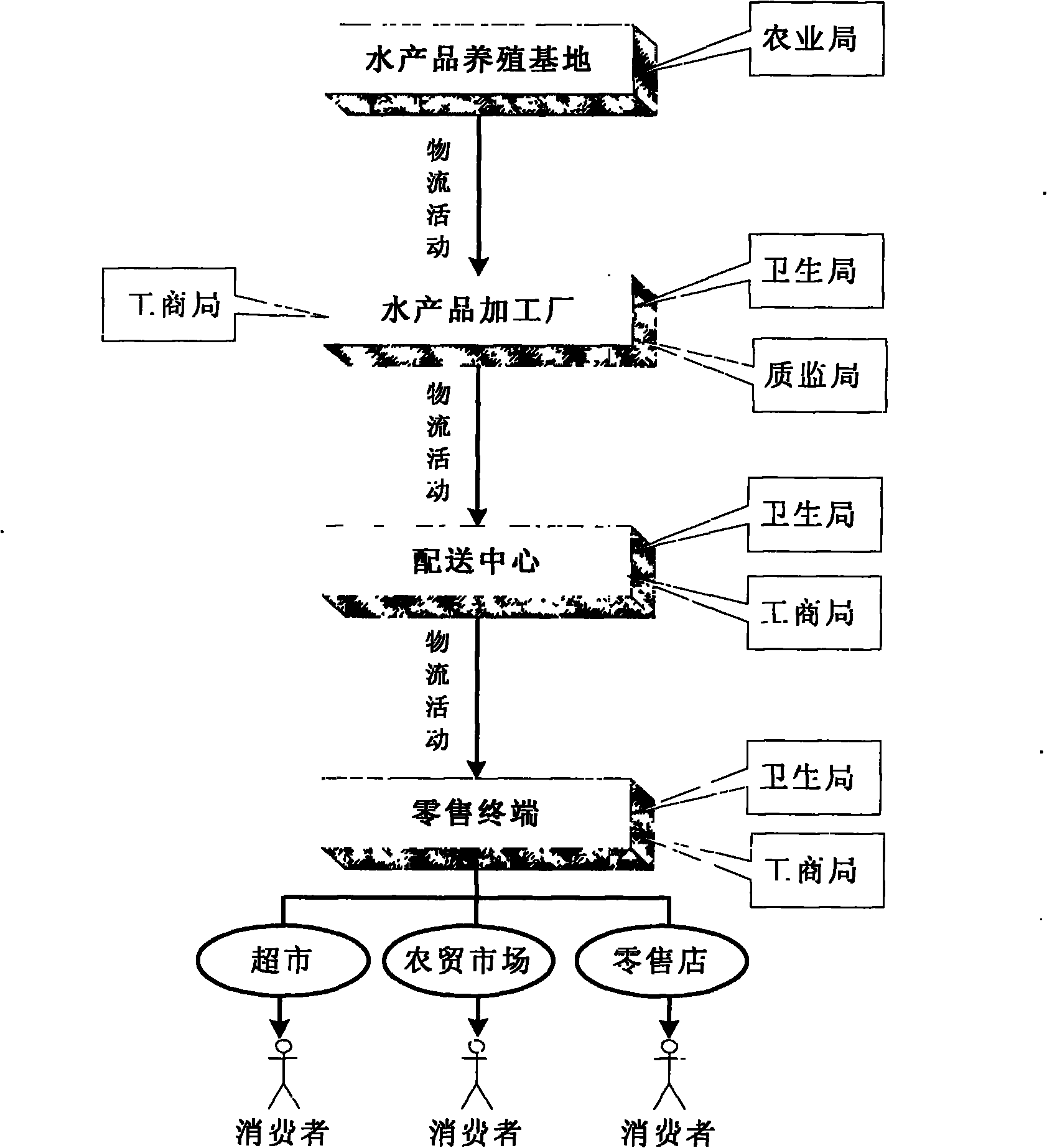
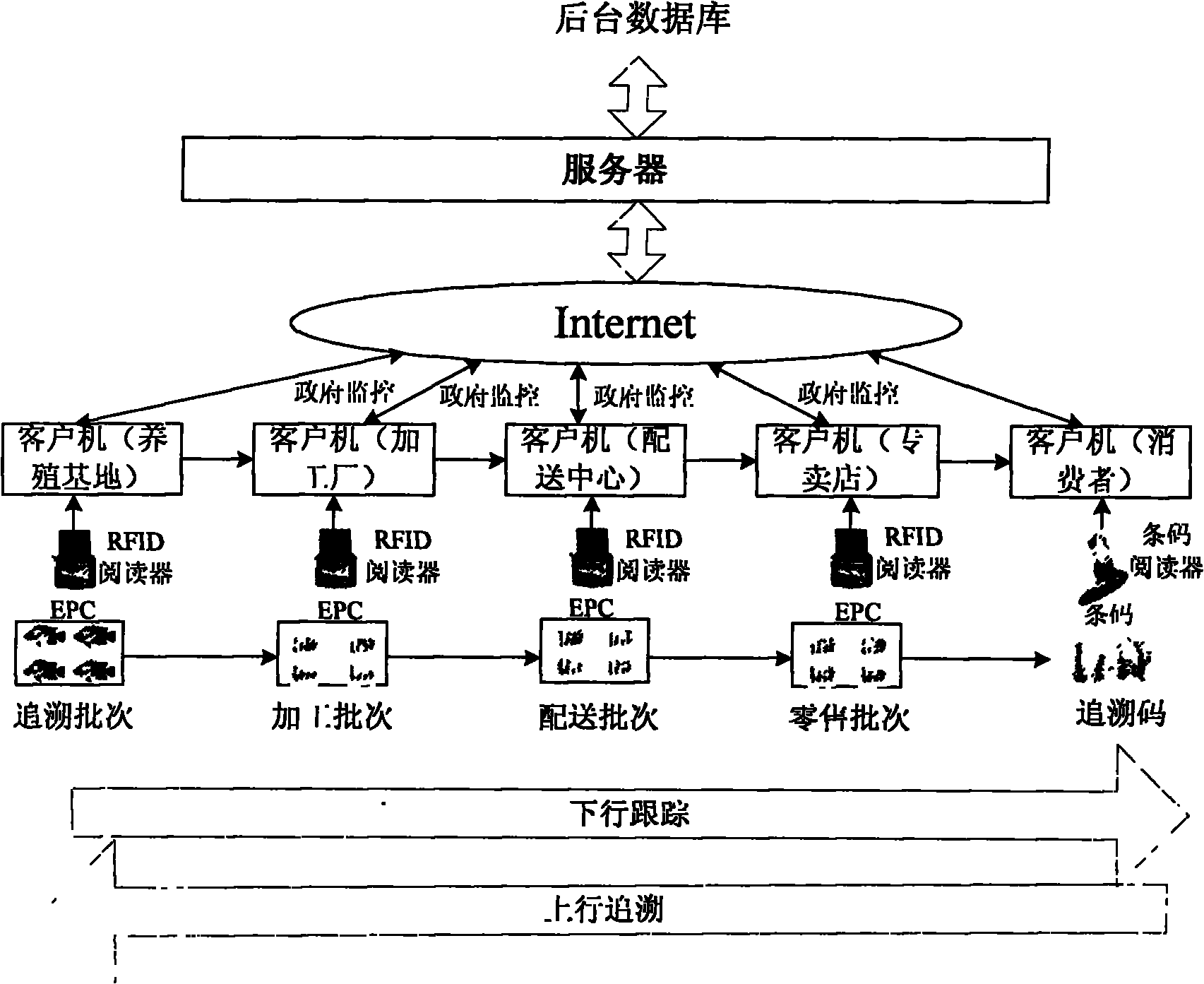
The invention discloses an RFID (Radio Frequency Identification Device) based seafood supply chain traceability system under an exclusive shop direct sales model, comprising a client, a server and a backend database which are all in network connection; the client comprises RFID reader-writers, an RFID electronic label and a client computer, wherein the RFID reader-writer is in network connection with a plurality of RFID electronic label networks, and a plurality of RFID read-writers are in network connection with the client computer; the server comprises a culture subsystem, a processing subsystem, a delivery subsystem, an exclusive shop subsystem, a consumer and controlling authority subsystem and a management subsystem, wherein the management subsystem is respectively connected with the culture subsystem, the processing subsystem, the delivery subsystem, the exclusive shop subsystem and the consumer and controlling authority subsystem, and the culture subsystem, the processing subsystem, the delivery subsystem, the exclusive shop subsystem and the consumer and controlling authority subsystem are in network connection. The invention has the advantages of high speed, high efficiency, convenient management, capability of tracking relevant information of each link of a supply chain, and the like.
Owner:SOUTH CHINA UNIV OF TECH
A confrontation simulation and efficiency evaluation system based on equipment parameterization
PendingCN109948228AImprove portabilityImprove reusabilitySpecial data processing applicationsFull life cycleService Component Architecture
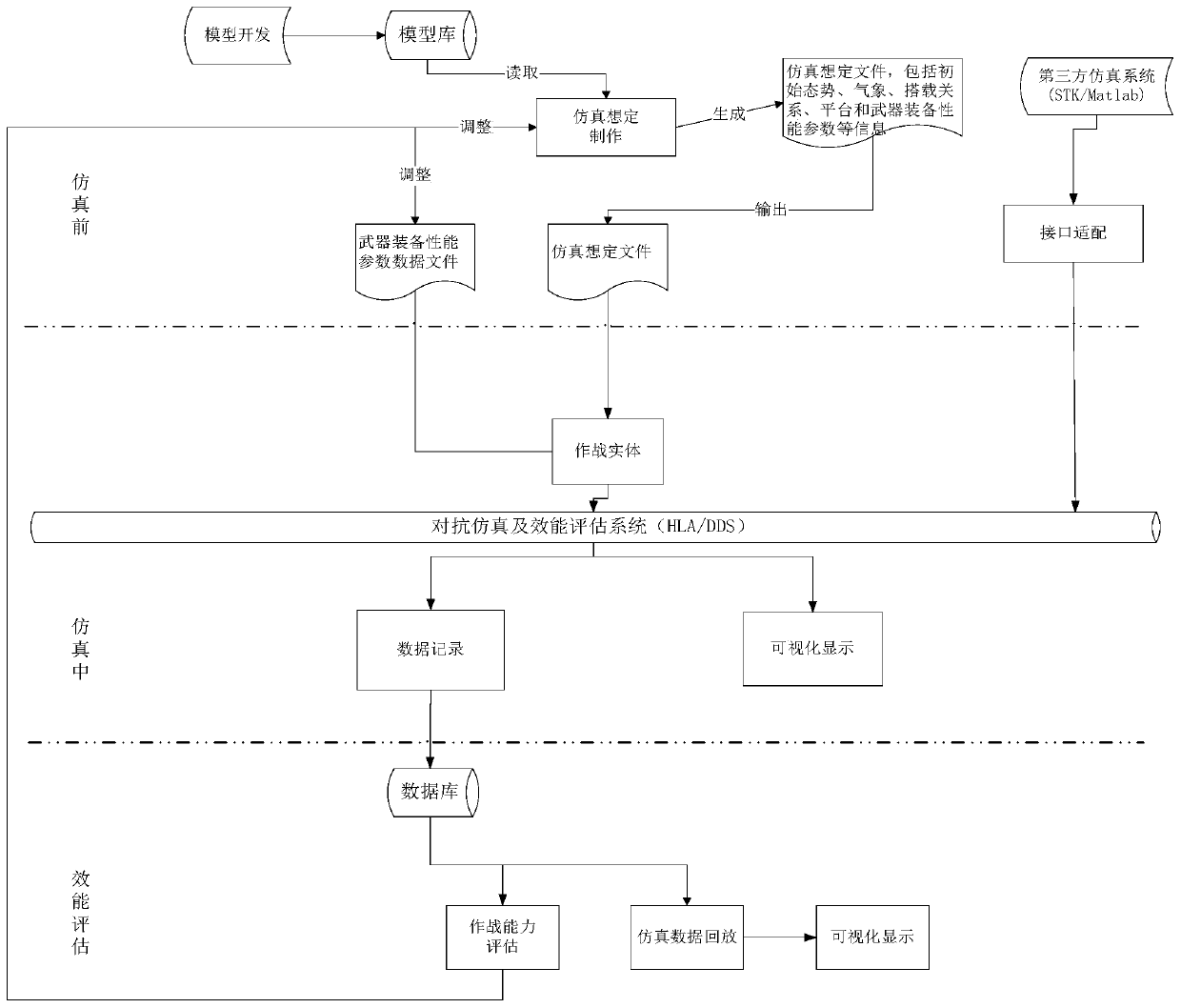
The invention designs a confrontation simulation and efficiency evaluation system based on equipment parameterization. According to the system, a simulation model development module supports a simulation service component architecture, an engineering management and operation guide control module adopts a distributed simulation guide control technology, a simulation resource management tool is adopted to uniformly manage and deploy models, scenarios and parameter resources in a simulation resource library, and the models, scenarios and parameter resources are deployed on a target node in a distributed simulation network; the simulation platform loads and operates various simulation resources through the simulation execution engine, and the efficiency assessment module adopts custom data management and efficiency assessment technologies. The system is used for an equipment confrontation simulation and efficiency evaluation software system in a large-scale combined action scene, solves the problems of universalization, platformization and expandability of a confrontation simulation system, supports full-life-cycle whole-process development, and can process simulation and evaluation tasks related to multiple types of simulation objects and multiple action scenarios.
Owner:CHINA SHIP DEV & DESIGN CENT
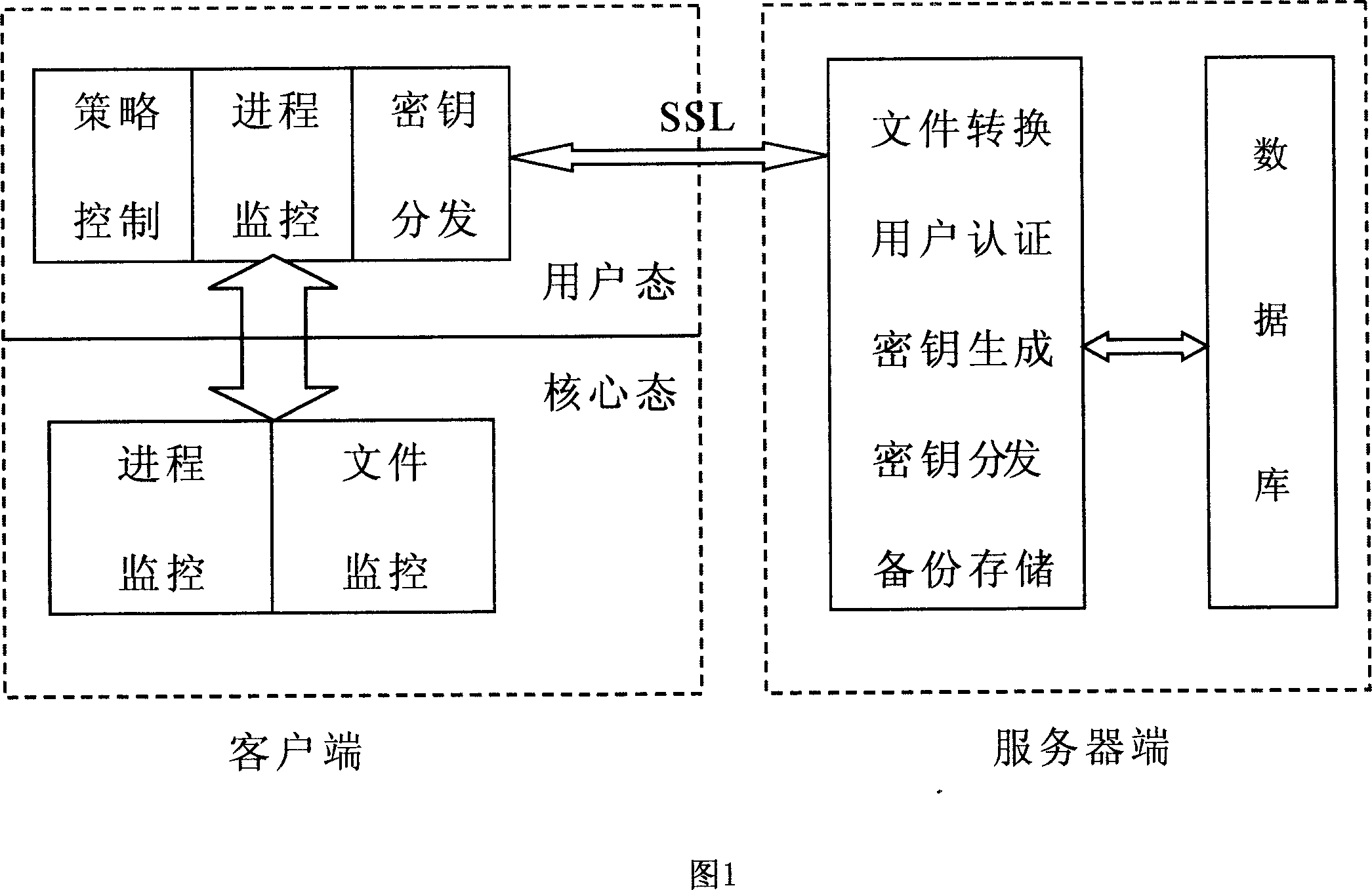
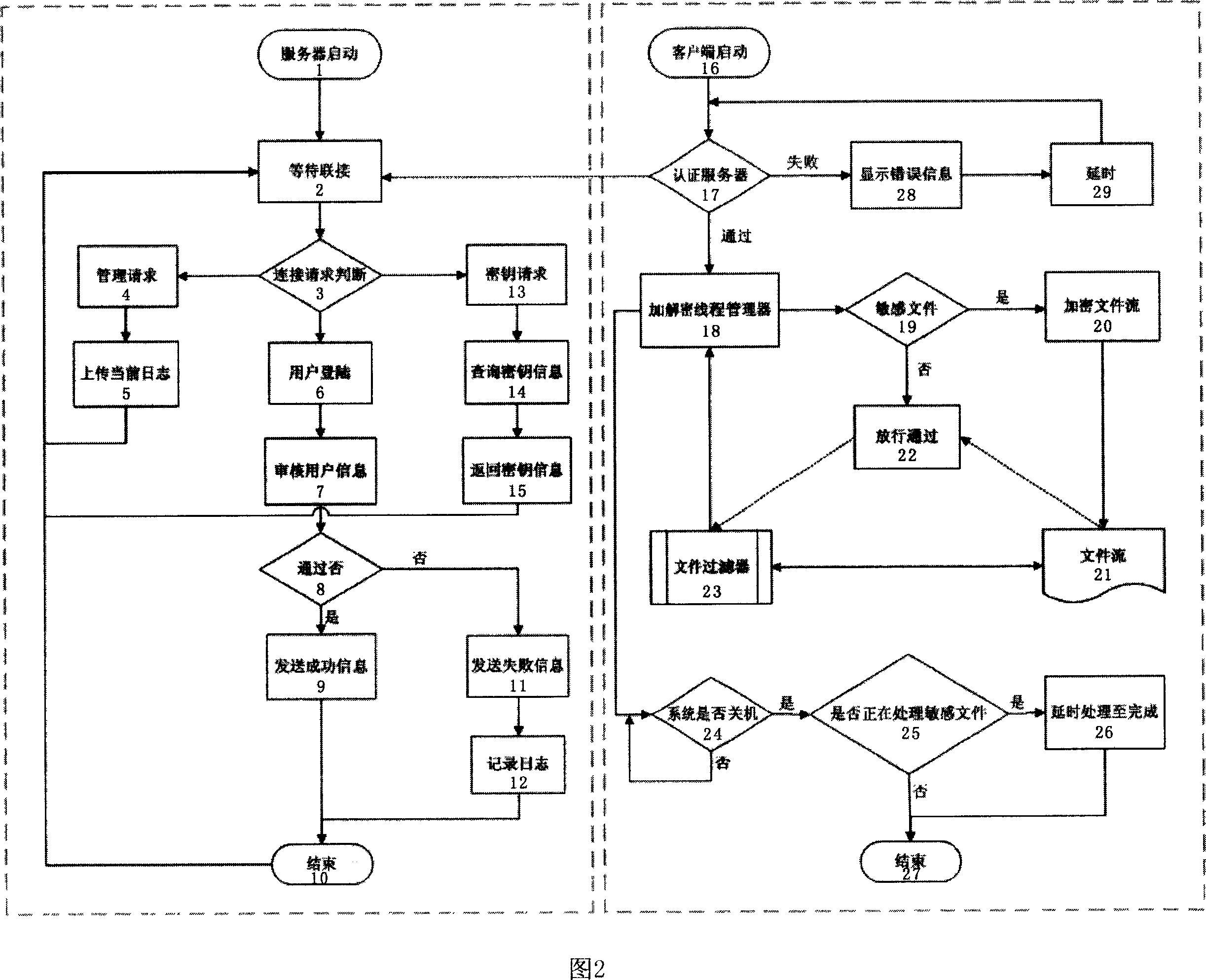
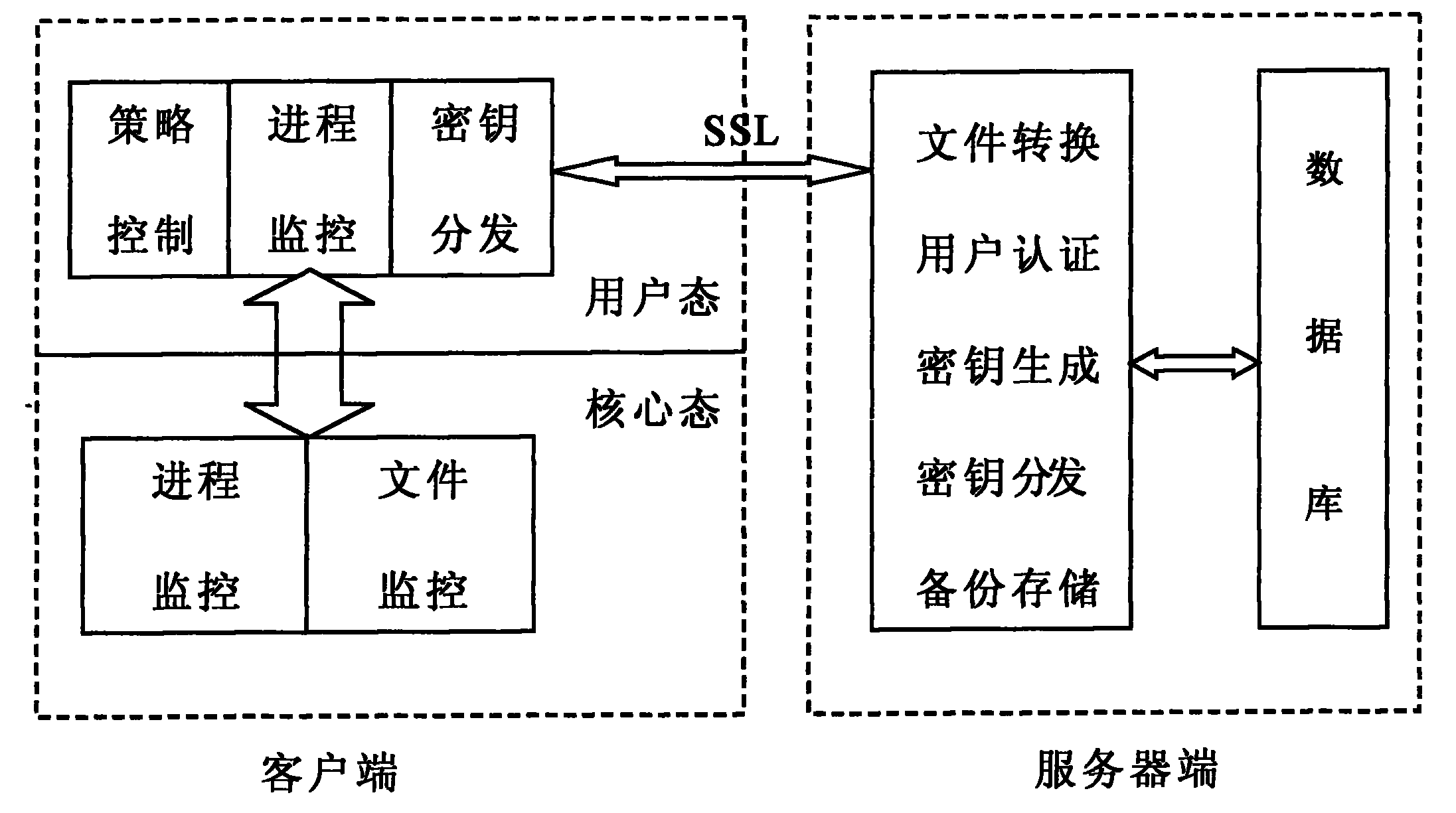
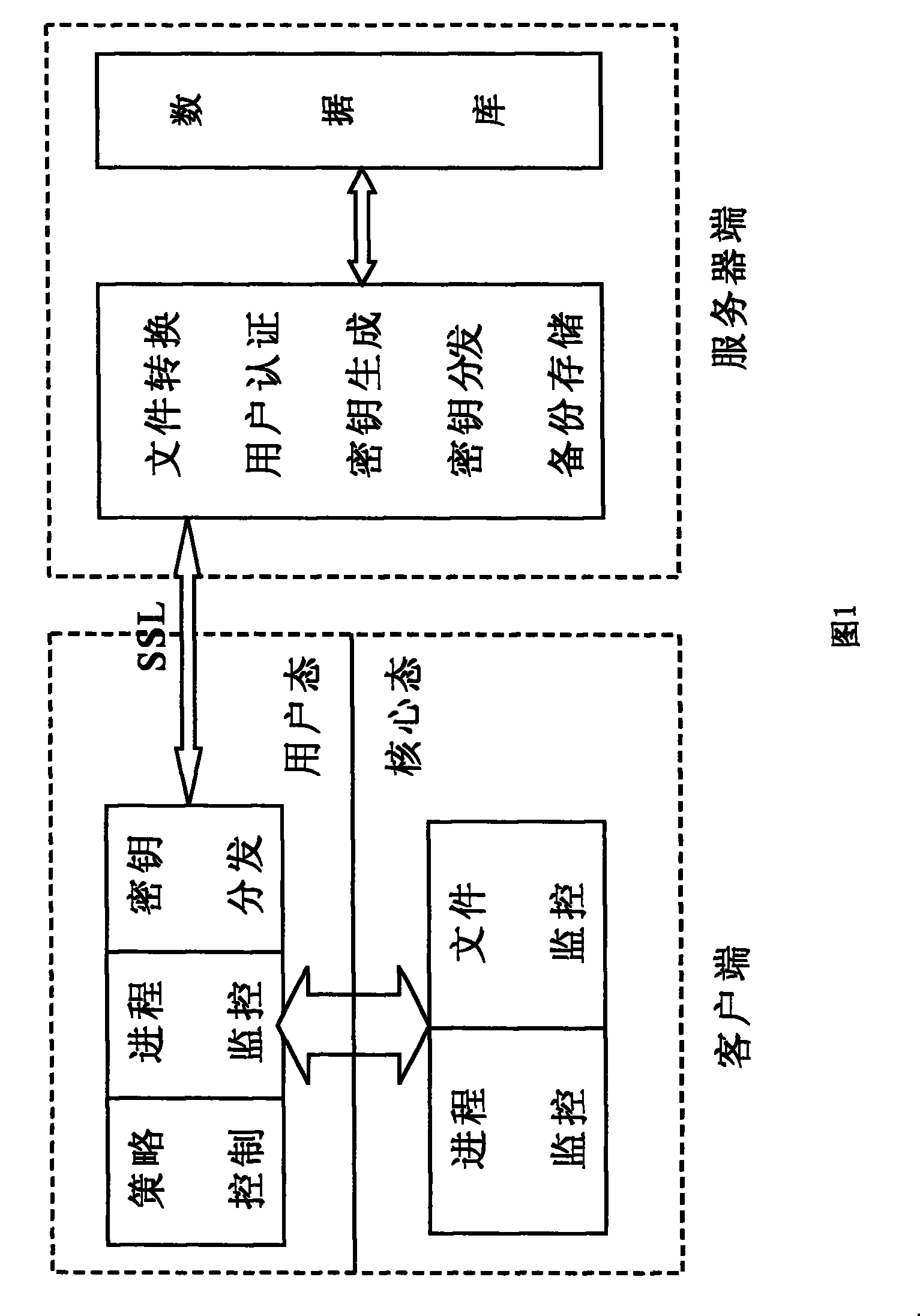
Method for encrypting/deciphering dynamically data file
InactiveCN101098224ASolve confidentiality issuesGuaranteed uptimePublic key for secure communicationUnauthorized memory use protectionPlaintextOperational system
The invention discloses a method for dynamically encrypting and decrypting data document, which comprises that in network condition, via C / S mode, manager centralized controls important documents of user computer, the system dynamically decrypts and encrypts clear text, the important documents can only be read or changed under the control of server in special network condition, which content is shown as cryptogram when off the network condition, when user copies clear text document from other places, the documents can not be changed when the system is sensitive, or else, in storage, the documents are converted into cryptogram type. The invention is based on software platform, correlated only with operation system, but not application programs, to dynamically encrypt and decrypt the data documents, therefore, the data documents can only work in private network condition, while the leaked document is in cryptogram type, to protect intellectual property.
Owner:CHINA NON-FERROUS METALS PROCESSING TECH CO LTD
X-band satellite-borne phased-array antenna
InactiveCN108172976AEnsure safetyLow powerAntenna supports/mountingsRadiating elements structural formsIsoetes triquetraDielectric plate
The invention relates to an X-band satellite-borne phased-array antenna. The X-band satellite-borne phased-array antenna comprises an antenna cover, an installation plate and a plurality of same antenna units, wherein centers of the plurality of antenna units are arranged on the installation plate in an equilateral triangle lattice mode, the antenna cover covers the plurality of same antenna unitsand is fixed with the installation plate, each antenna unit is a multi-layer microstrip antenna and comprises a radiation patch, an antenna unit shell, an SMA coaxial connector, a grounding plate, abottom-layer dielectric plate, an upper-layer dielectric plate and a parasitic patch, an inner core of the SMA coaxial connector sequentially penetrates through the installation plate, the grounding plate and the bottom-layer dielectric layer and is connected with the radiation patch, an outer skin of the SMA coaxial connector is fixedly connected with the installation plate, the installation plate is connected with the grounding plate, the radiation patch is arranged on the center of the bottom-layer dielectric plate, the parasitic patch is arranged in the center of an upper surface of the upper-layer dielectric plate, an air medium is arranged between the bottom-layer dielectric plate and the upper-layer dielectric plate, and the peripheries of the bottom-layer dielectric plate, the grounding plate and the upper-layer dielectric plate are fixed with the antenna unit shell.
Owner:TIANJIN JINHANG COMP TECH RES INST
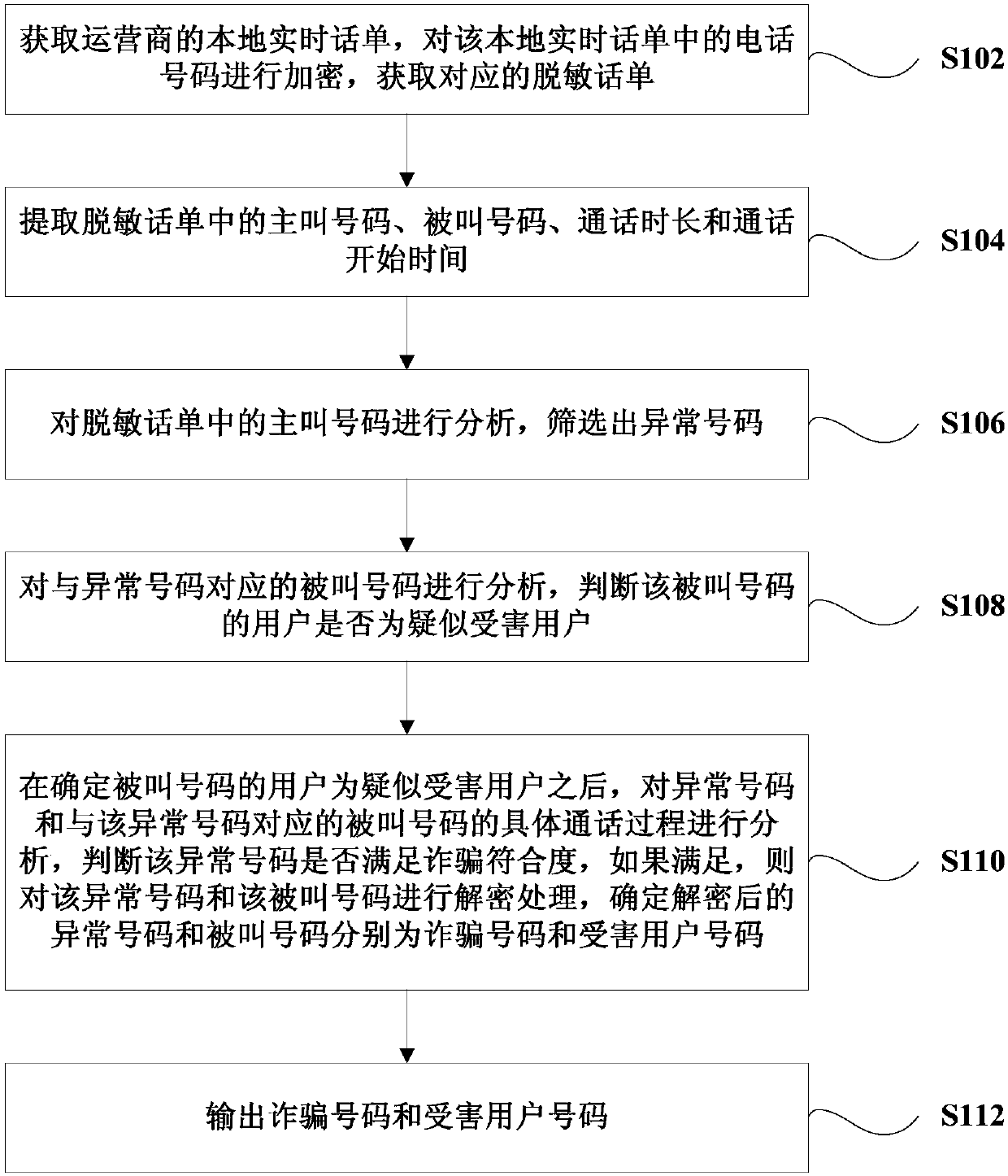
A fraud phone identification method and system
ActiveCN109698884APrecise positioningRealize identificationSupervisory/monitoring/testing arrangementsStart timeInternet privacy
The invention provides a fraud phone identification method and system. The method comprises the following steps: obtaining a local real-time call ticket of an operator, encrypting a telephone number in the local real-time call ticket, and obtaining a corresponding desensitization call ticket; Extracting a calling number, a called number, call duration and call starting time in the desensitizationcall ticket; Analyzing the calling number, and screening out an abnormal number; Analyzing the called number corresponding to the abnormal number, and judging whether the user of the called number isa suspected victim user or not; Analyzing the specific conversation process of the abnormal number and the called number corresponding to the abnormal number, judging whether the abnormal number meetsthe fraud conformity or not, if yes, decrypting the abnormal number and the called number, and determining that the decrypted abnormal number and called number are the fraud number and the number ofthe victim user respectively; And outputting the fraud number and the victim user number. According to the invention, the identification of the fraud phone is realized.
Owner:CHINA TELECOM CORP LTD
Context aware systems and methods utilizing hierarchical tree structures
InactiveCN1585942ASolve confidentiality issuesInformation formatContent conversionData miningComputing systems
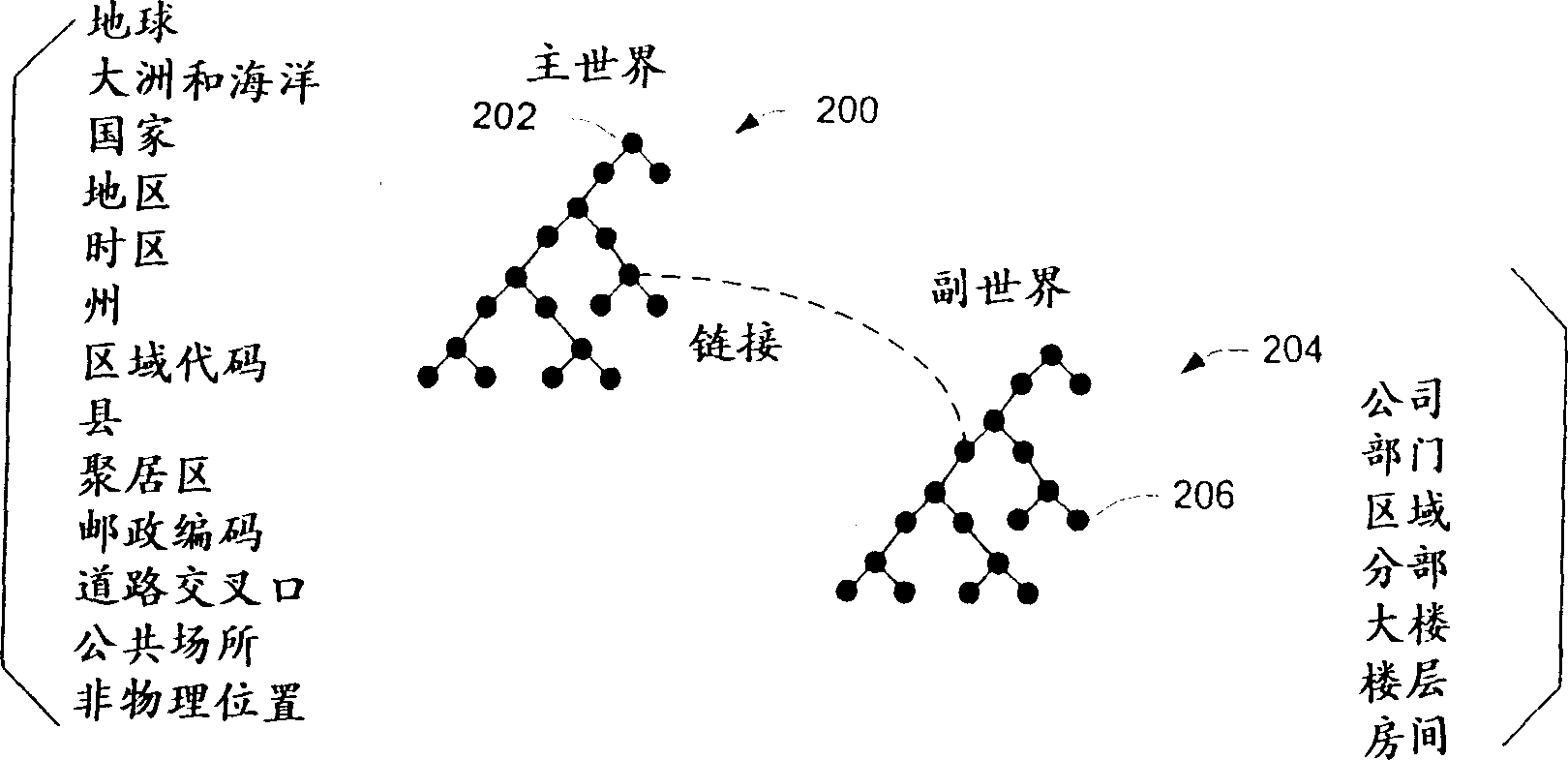
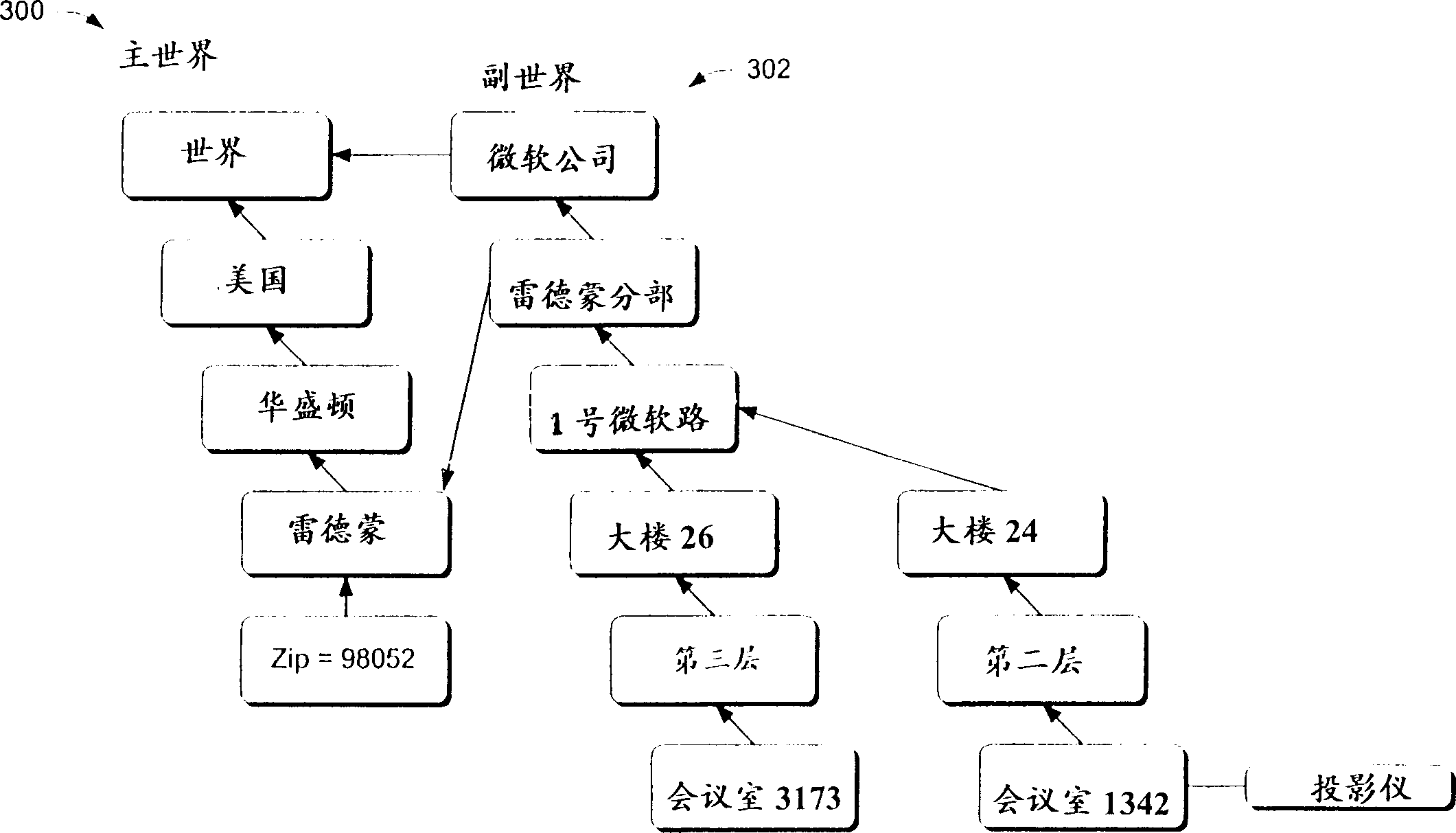
Context-aware computing systems and methods are described. In particular embodiments, location aware systems and methods are described. In the described embodiments, hierarchical tree structures are utilized to ascertain a device context or location. The tree structures can be stored on or accessible to mobile or stationary computing devices so that the devices can determine their own particular context or location. In one embodiment, one of the tree structures comprises a Master World tree structure that contains nodes that represent geographical divisions of the Earth. Another of the tree structures can comprise a so-called Secondary World that contains nodes that represent physical or logical entities that are organization or company specific views of the world. A computing device can automatically determine its context or location by ascertaining a node on one or more of the tree structures and then traversing the tree structure to ascertain the complete context. Once a context or location is ascertained, goods or services associated with the context or location can be accessed.
Owner:MICROSOFT CORP
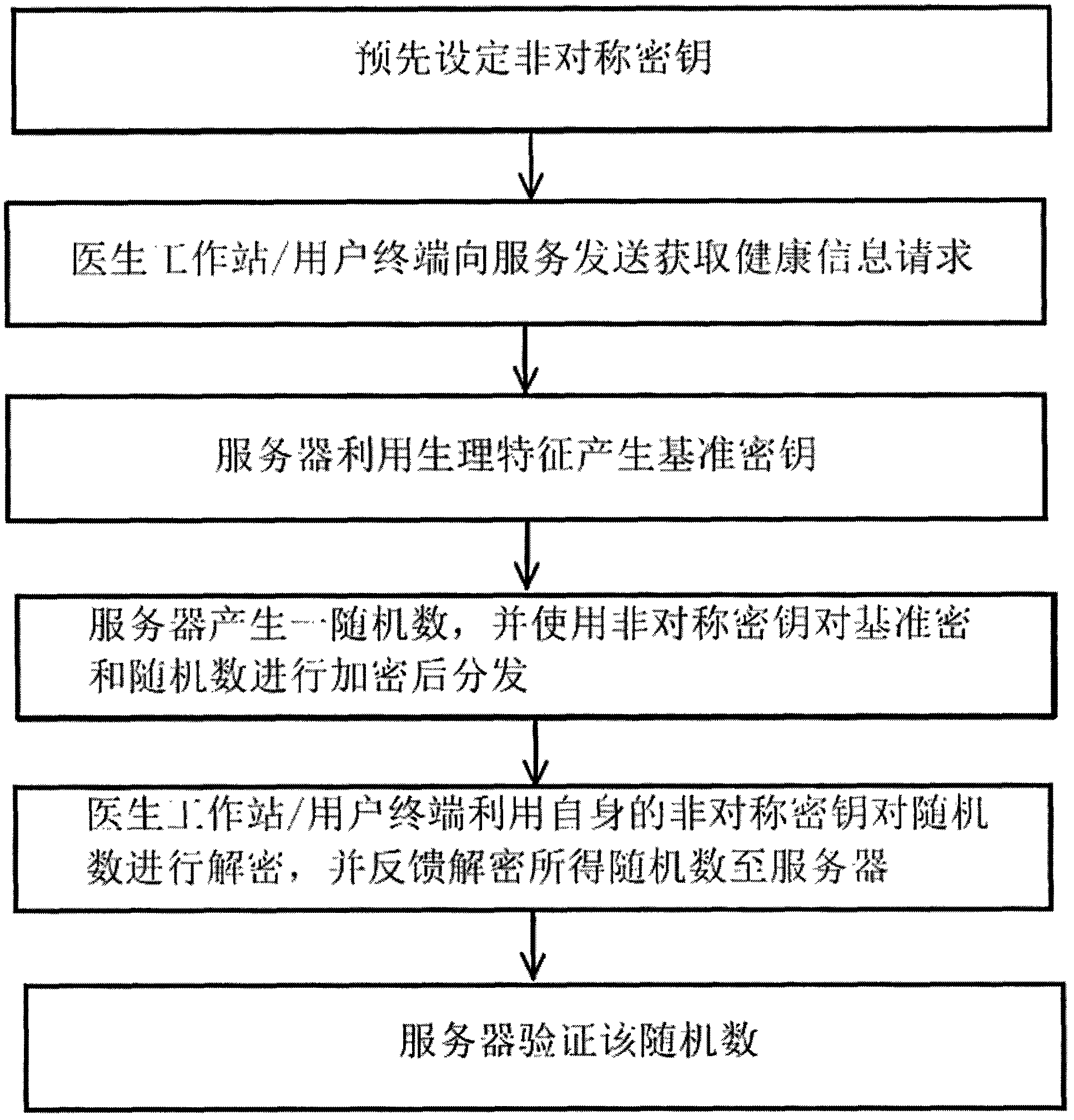
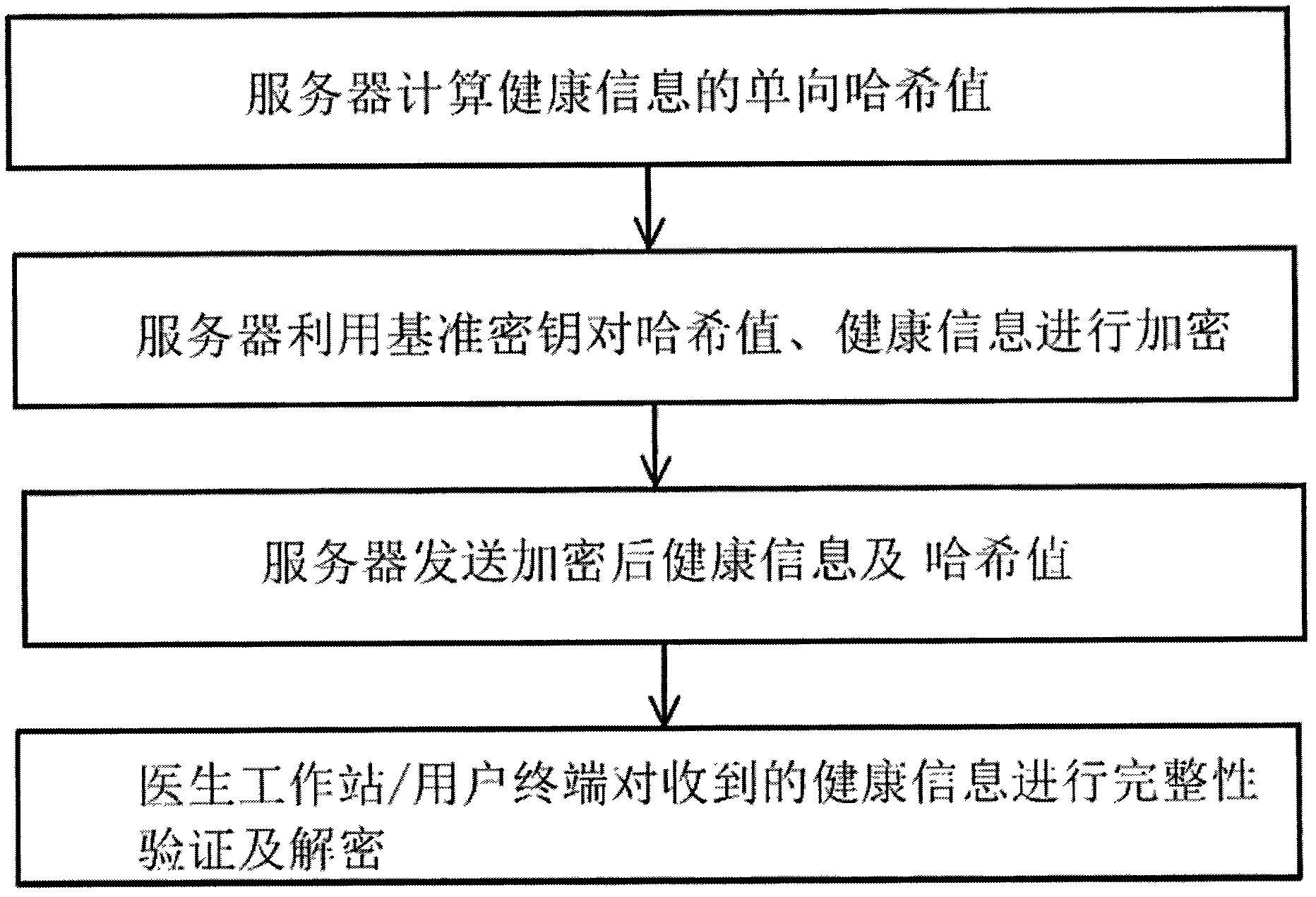
Secure transmission method for health information
InactiveCN102546655AEnsure safetyReduce loadKey distribution for secure communicationDiagnostic recording/measuringDatabase serverSecure transmission
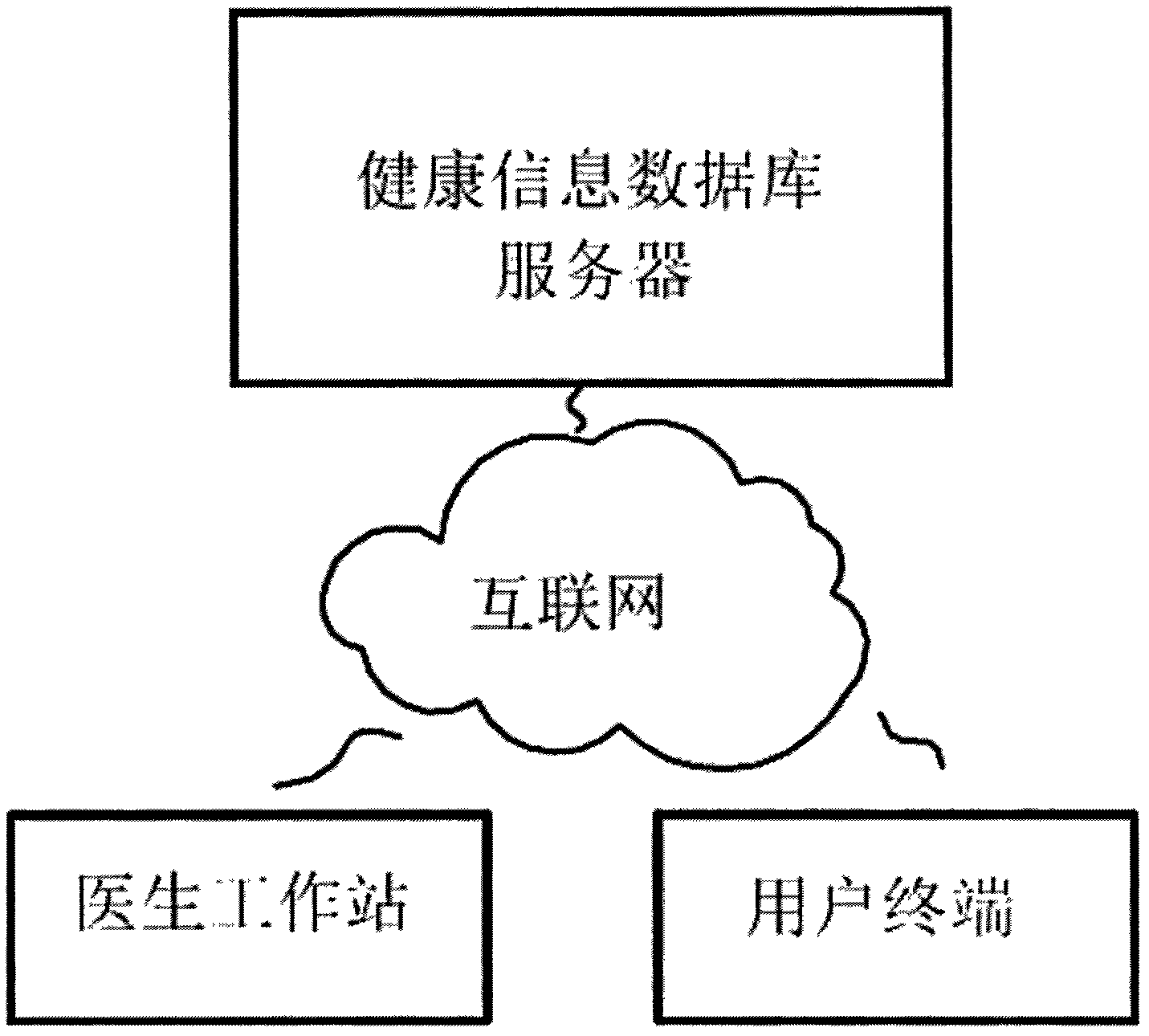
The invention discloses a secure transmission method for health information, and aims to realize the secure transmission of the health information between a health information database server and a doctor workstation / user terminal. The method is characterized by comprising the following steps that: 1, an asymmetric key is set in advance between the health information database server and the doctor workstation / user terminal; 2, the health information database server generates a reference key by utilizing physiological characteristics; 3, the health information database server encrypts the reference key through the asymmetric key, and distributes the reference key; 4, a random number is verified; 5, after the random number passes the verification, the health information database server calculates a one-way hash value, encrypts the hash value and the health information by utilizing the reference key, and transmits the encrypted hash value and the encrypted health information; and 6, the doctor workstation / user terminal performs integrity verification and decryption on the received health information.
Owner:ZHONGSHAN IKER DIGITAL TECH
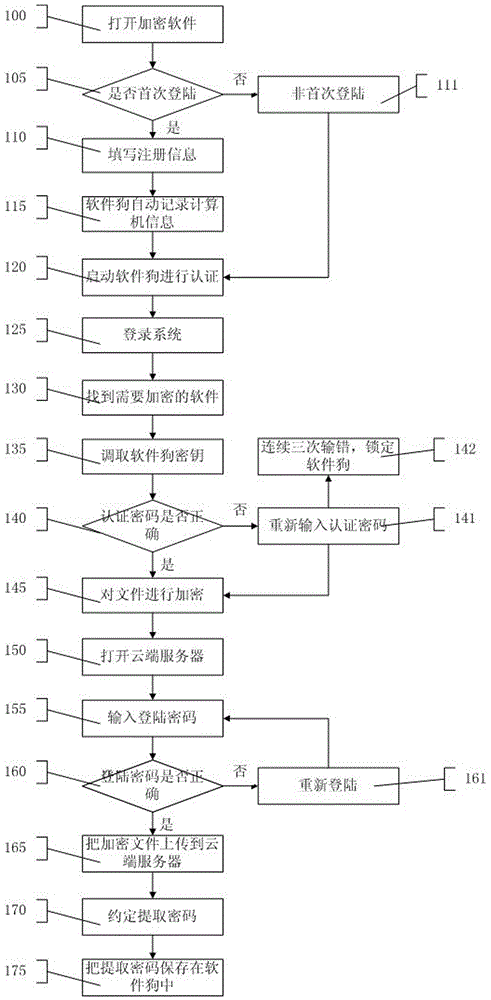
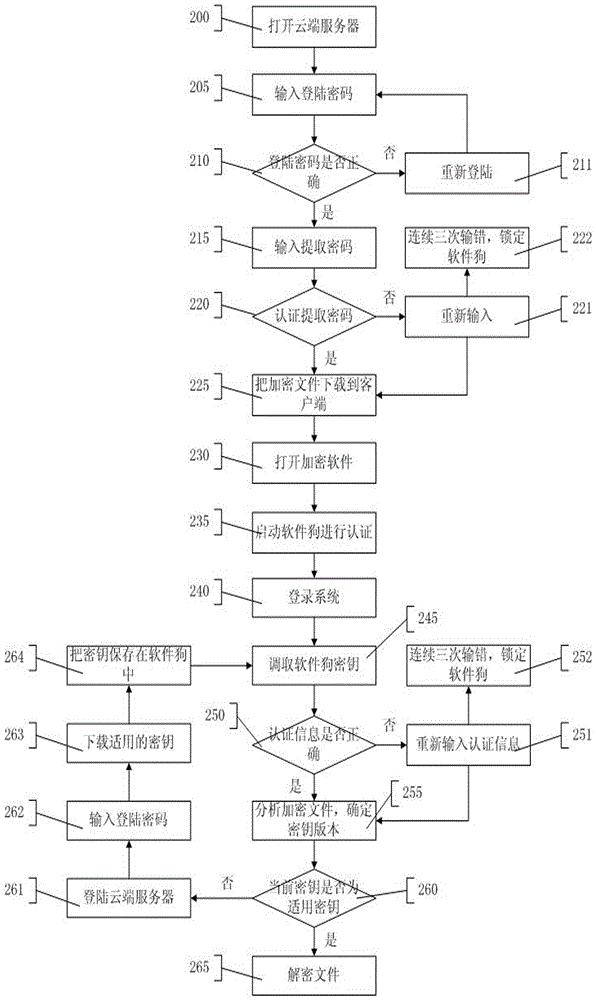
File cloud storage security solution method and system
InactiveCN105871892ASolve confidentiality issuesImprove securityTransmissionSoftware engineeringCloud storage security
The invention provides a file cloud storage security solution method and system. The method is divided into two parts, namely encryption and decryption. The encryption method includes the steps that a computer is loaded with a softdog, a file encryption secret key in the softdog is obtained in an authentication mode, the secret key is utilized to conduct encryption on a file required to be encrypted, and the encrypted file is unloaded to a cloud server. The decryption method includes the steps that the cloud server is started, the encrypted file is downloaded, a local computer is loaded with the softdog, the file encryption secret key in the softdog is obtained in an authentication mode, the encrypted file is decrypted through the secret key, and the original file is obtained. By means of the file cloud storage security solution method and system, the file can be encrypted to the maximum degree and protected against losses.
Owner:BEIJING UNION UNIVERSITY
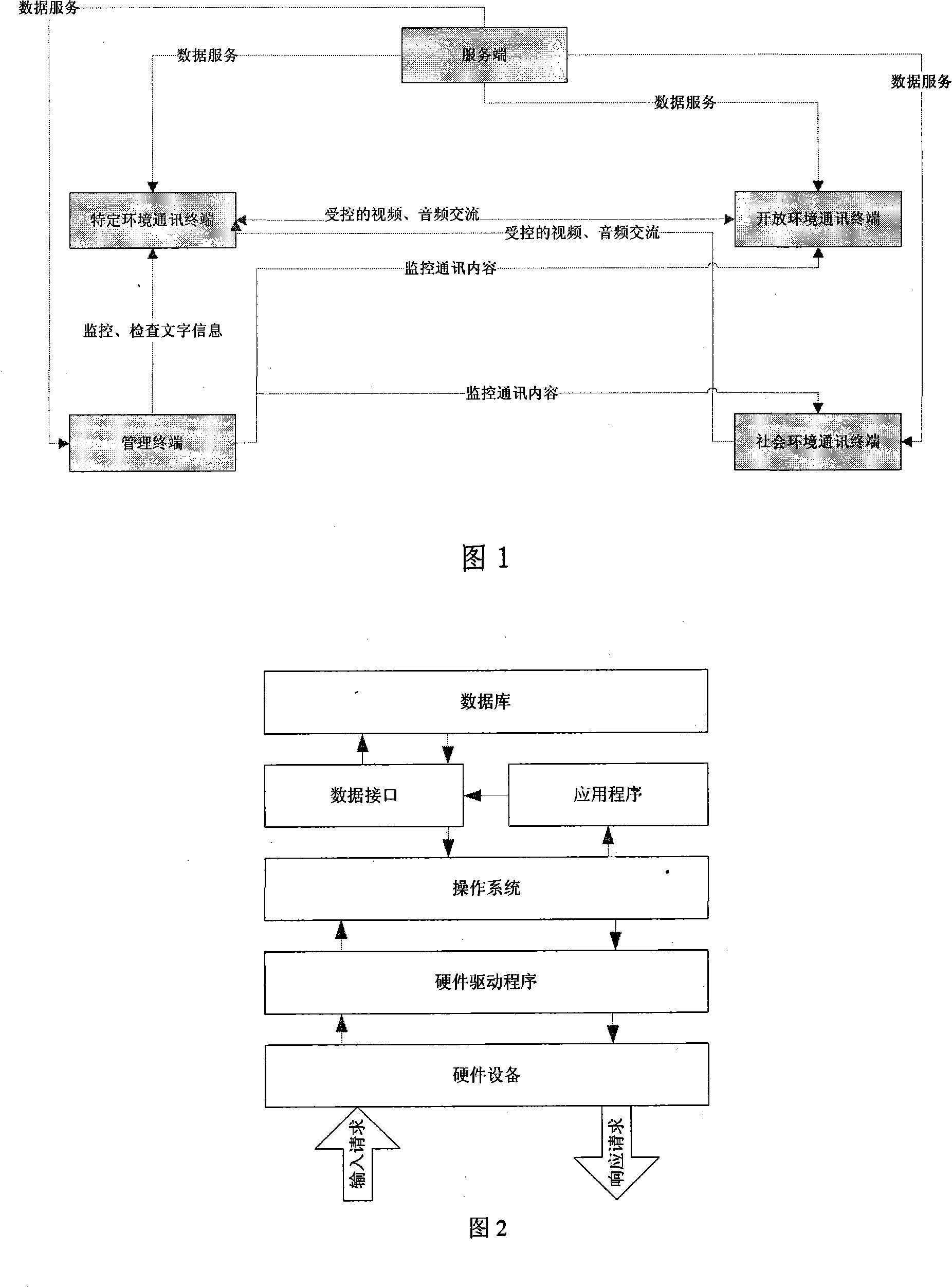
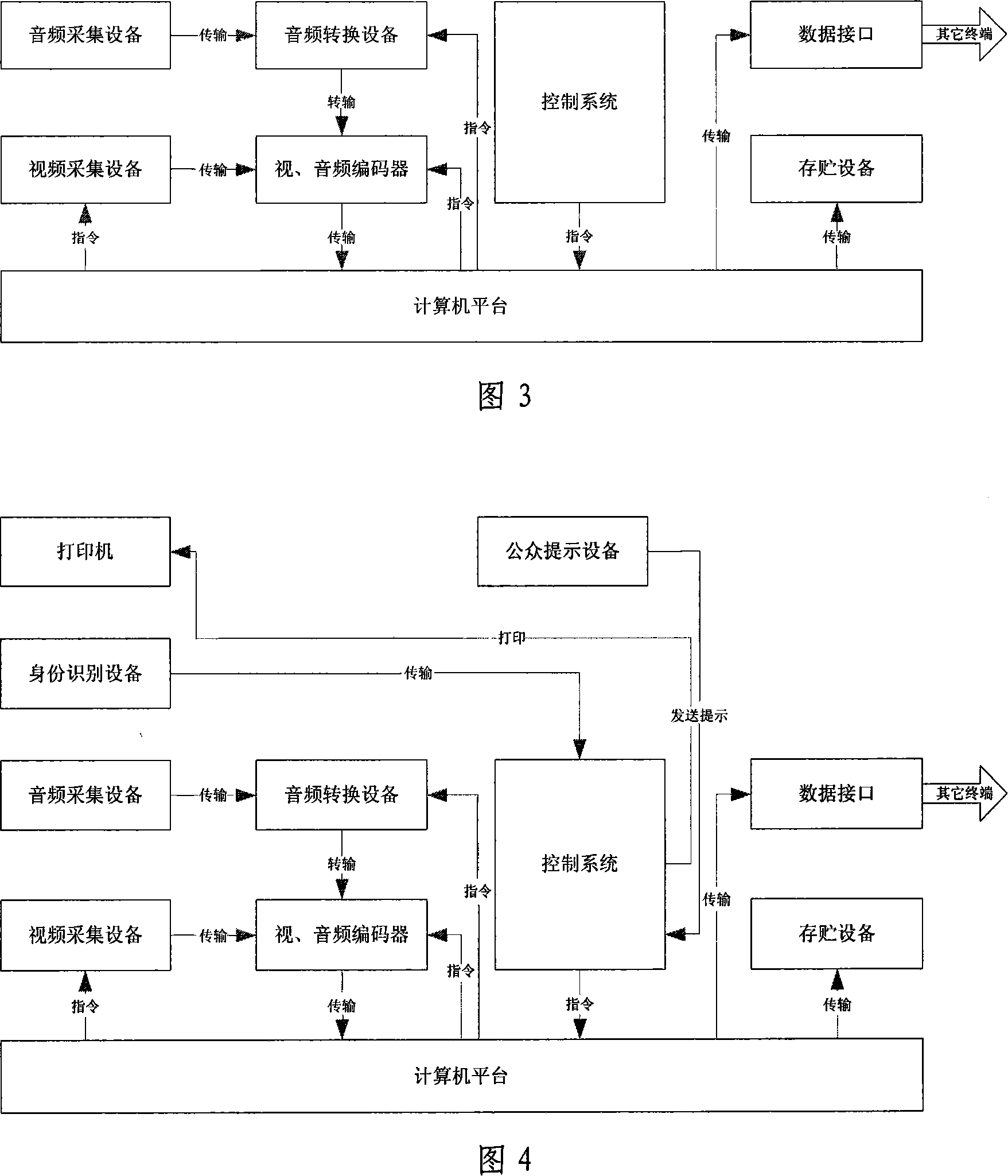
Specific crowd multimedia communication system and method
InactiveCN101119514ASolve remoteFix security issuesTelephonic communicationRadio/inductive link selection arrangementsInformatizationCommunications system
A multimedia communication system method for the specific group of people belongs to the multimedia informatization system, which respectively arranges a specific environment communication terminal, an opening environment communication terminal, a social environment terminal, a service terminal and a managing terminal in the four areas of the specific environment, the social environment, the opening environment and the managing mechanism, so as to realize that the specific environment communication terminal makes calls to the opening environment communication terminal or sends the SMS to the social mobile phone; the cosial environment terminal makes calls to soecific environment communication terminal or seads the SMS to the specific group of people; the opening environment terminal makes calls to the specific environment communication terminal. The invention solves the specific group of people consulate and communicat in a safe, controllable and pursuable enviromant, and safety and secrecy. The present invention can be used for the prison, the school, the army, the public security organs system, and the hospital etc., to develop a plurality of the works from the psychology induction, the legal aid, the medical diagnalse and the occupation induction etc.
Owner:济南中磁电子科技有限公司
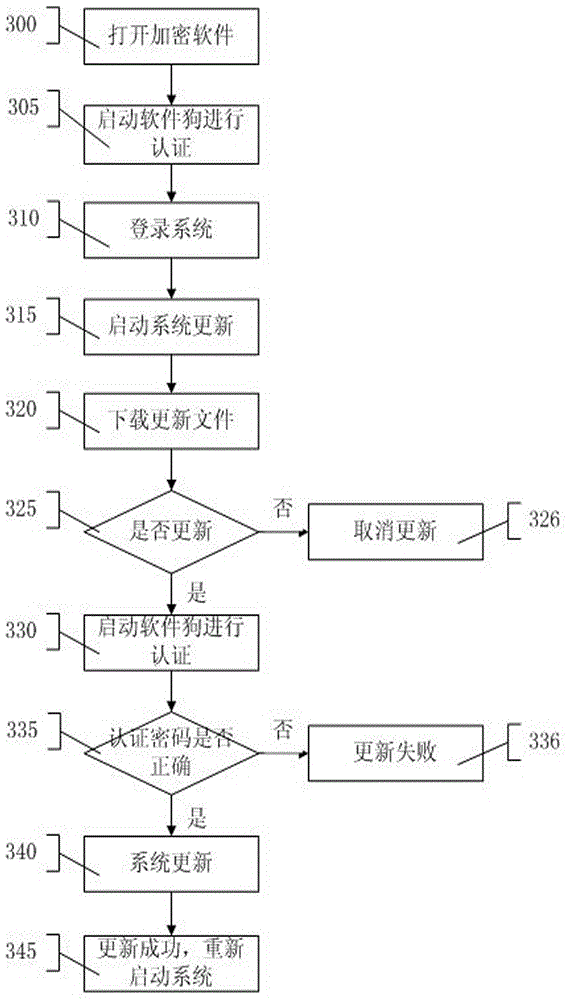
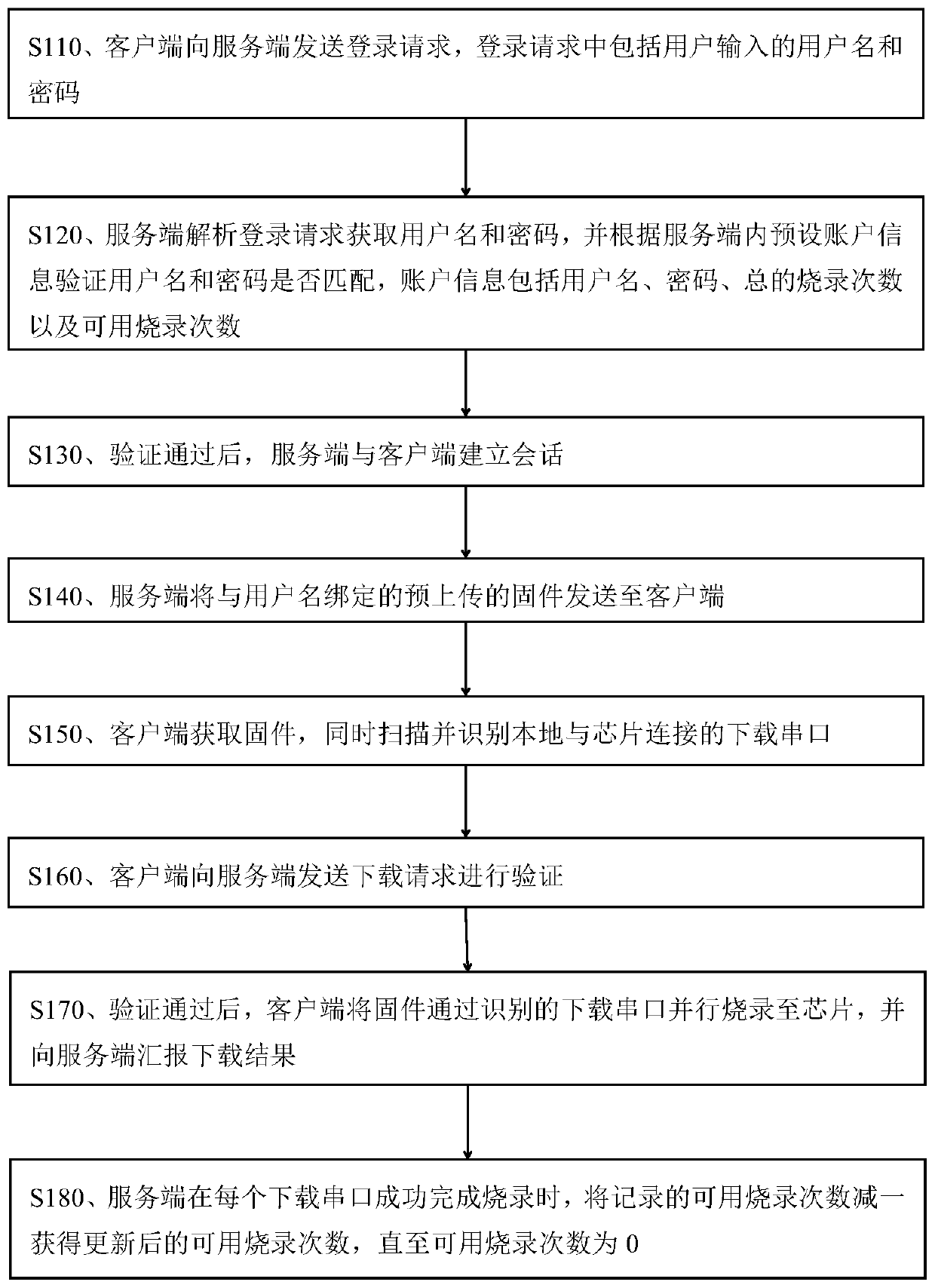
Distributed chip online burning method and system
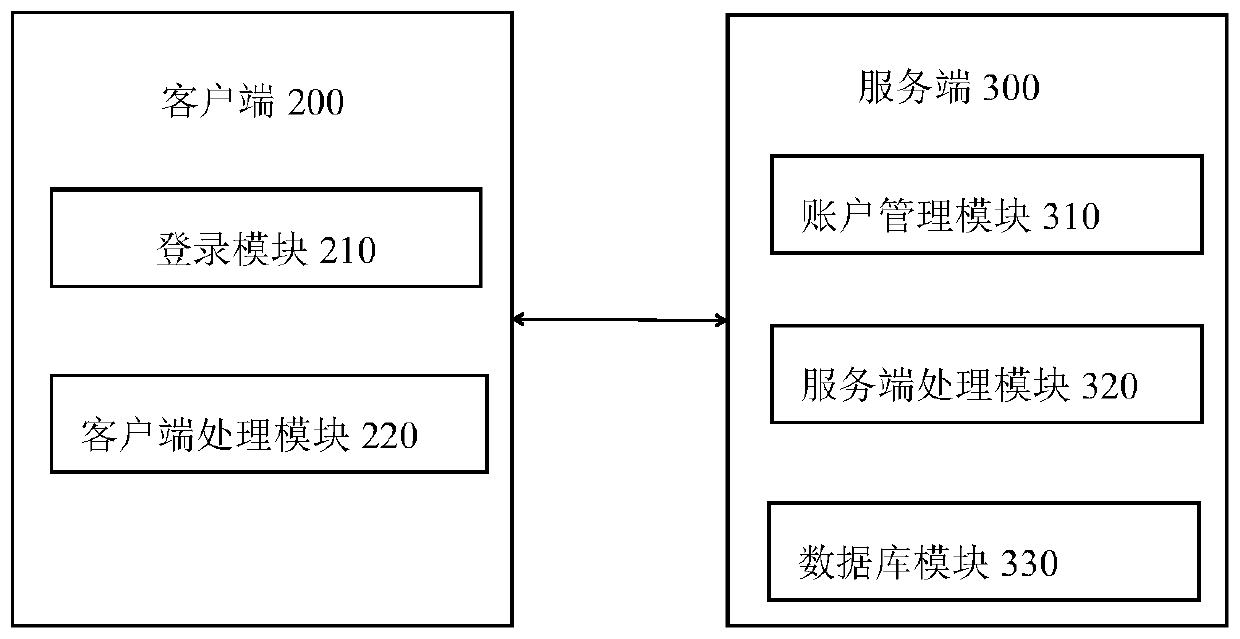
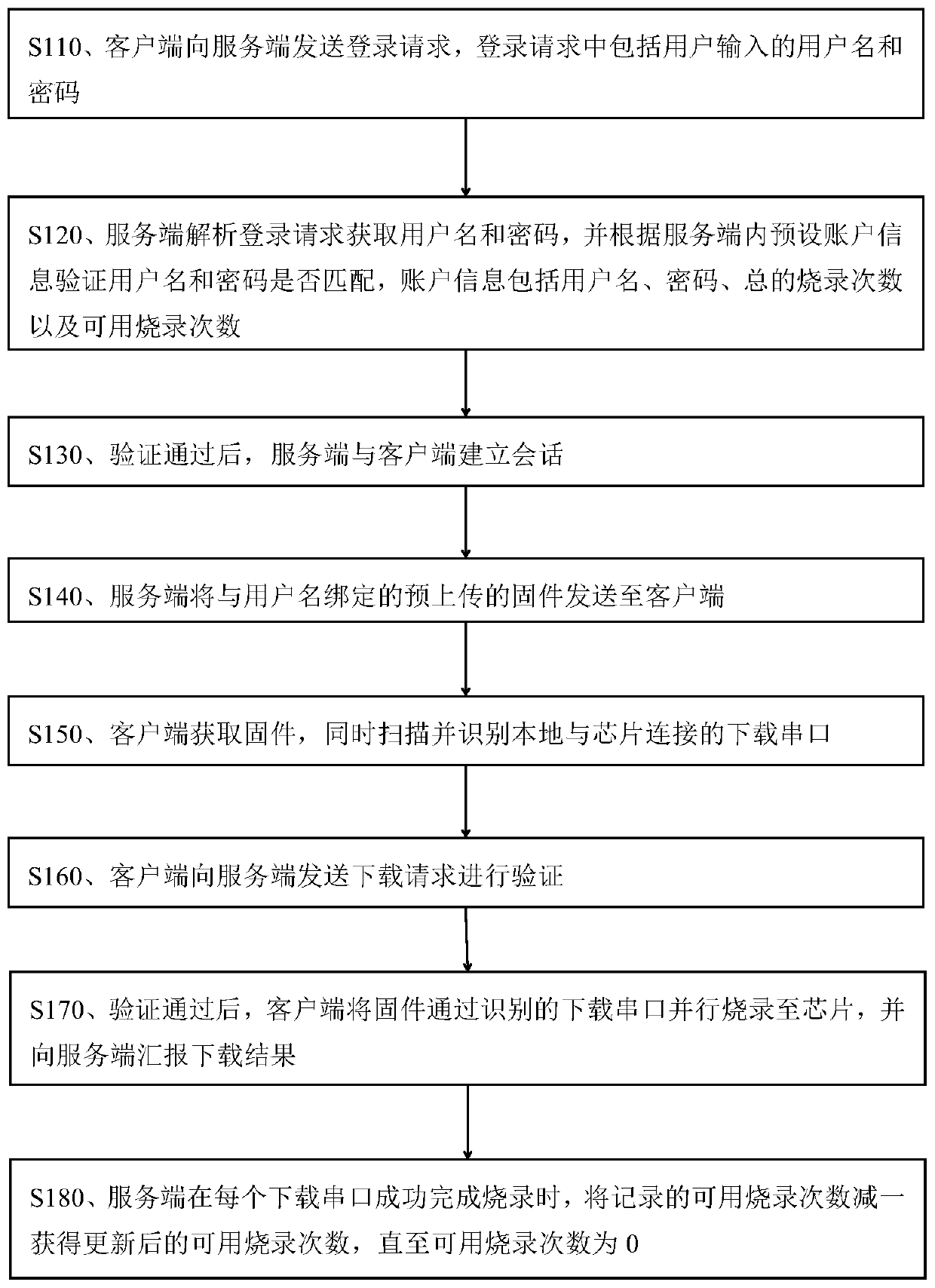
InactiveCN110045970ASolve confidentiality issuesSolve the problem of frequently mailing chips back and forthProgram/content distribution protectionSoftware deploymentConfidentialityPassword
The embodiment of the invention discloses a distributed chip online burning method and system. The method comprises: a client sending a login request to a server; the server parsing the login requestto obtain a user name and a password for verification; after the verification is passed, the server establishing a session with the client; the server sending the pre-uploaded firmware bound with theuser name to the client side; the client acquiring the firmware and scanning and identifying a local downloading serial port connected with the chip; the client sending a download request to the server for verification; and after the firmware passes the verification, the client burning the firmware to the chip in parallel through the identified downloading serial port. According to the distributedburning system, multi-port parallel burning can be achieved, the number of burned chips can be remotely controlled, the confidentiality problem in the chip burning process can be solved, the number of burned chips using firmware can be clearly known, and the problem that the chips need to be frequently mailed back and forth due to frequent software version replacement and the like is solved.
Owner:邝建红
Synthetic environment simulation platform
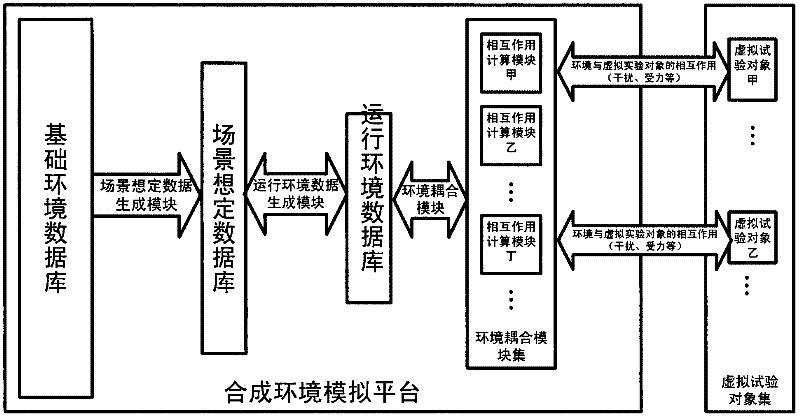
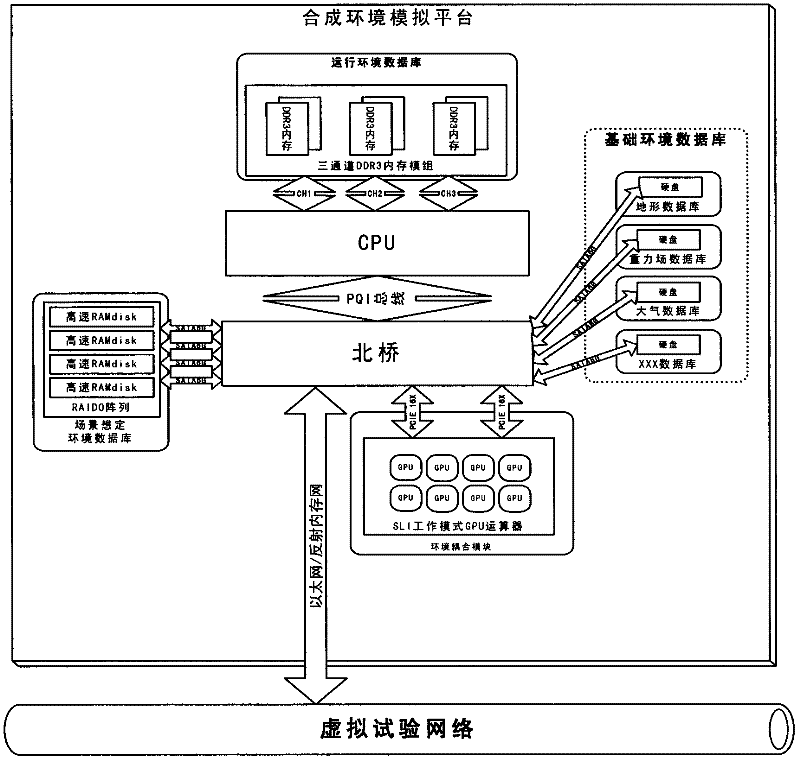
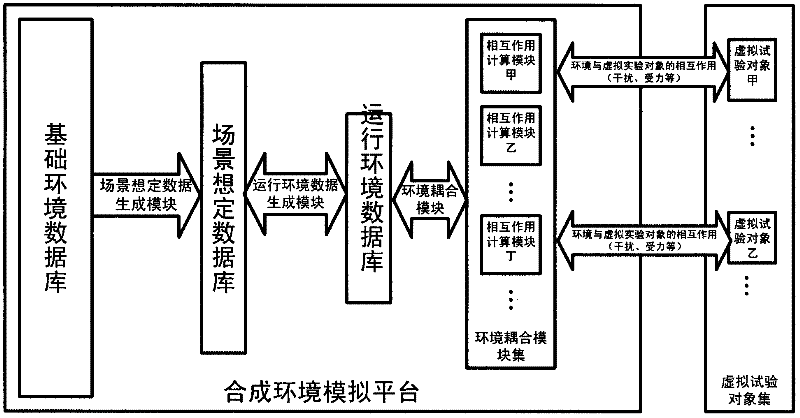
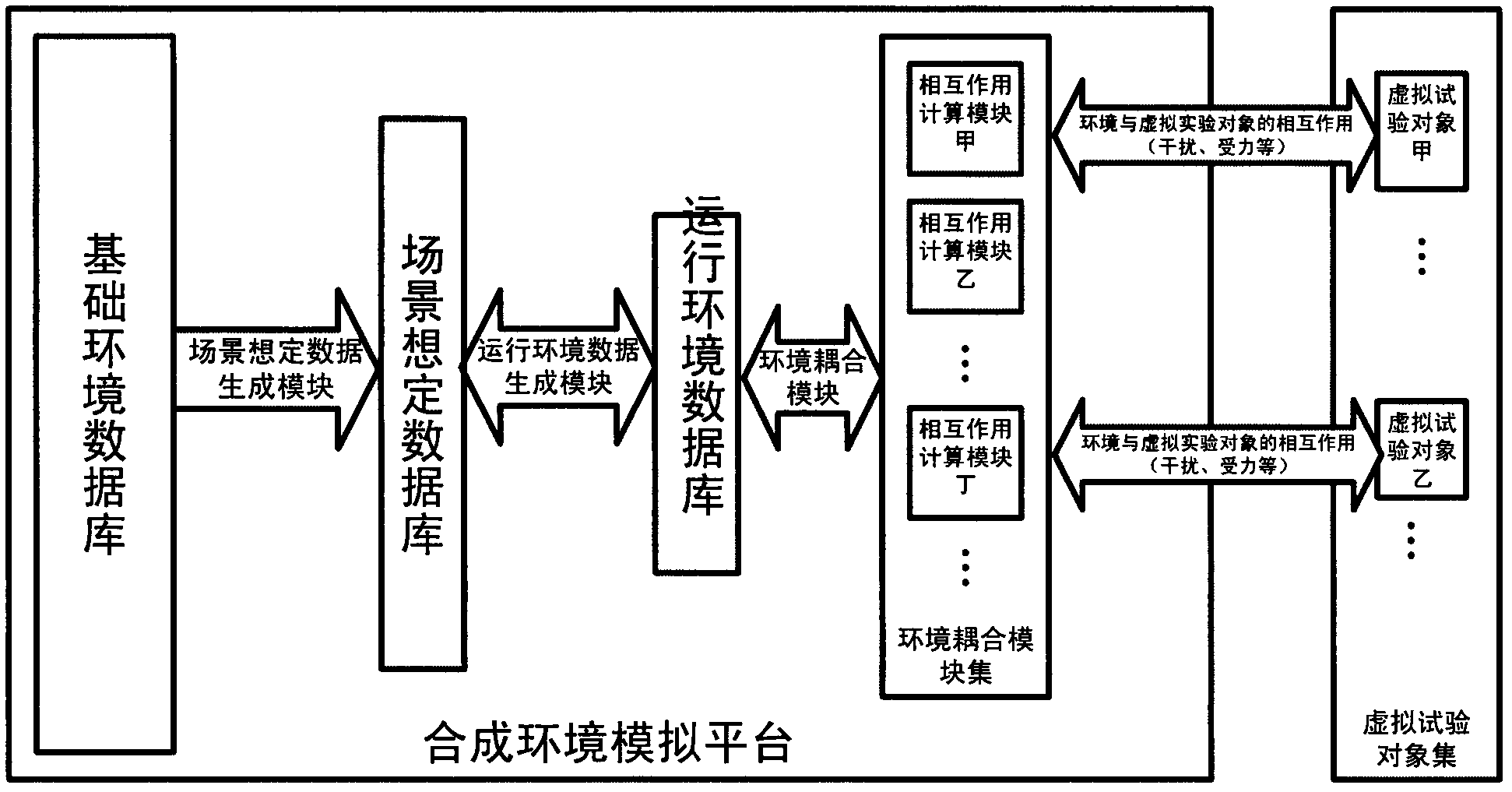
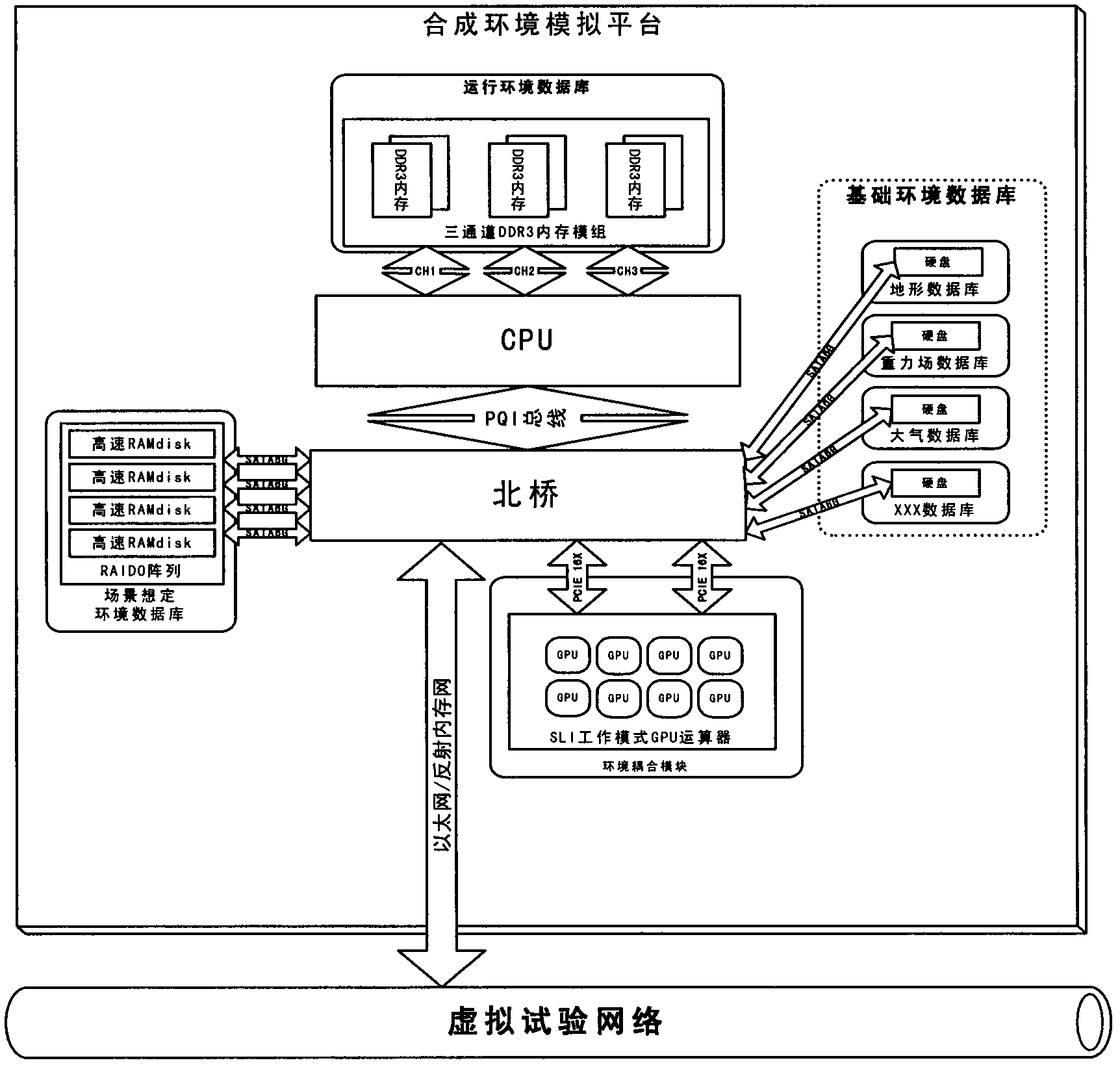
ActiveCN102364488ASolve confidentiality issuesRelieve stressSpecial data processing applicationsEnvironmental dataVirtual test
The invention discloses a synthetic environment simulation platform which is used for supplying environmental data to a virtual test object in a virtual test process. The synthetic environment simulation platform comprises a basic environment database, a scene scenario environment database, a running environment database, a scene scenario data generation module, a running environment data generation module and an environment coupling module. By adopting the synthetic environment simulation platform, calculation of interaction between the virtual test object and a synthetic environment model is realized.
Owner:CHINA ACAD OF LAUNCH VEHICLE TECH
Apparatus and method for automatic network storage of short messages received by mobile telephone
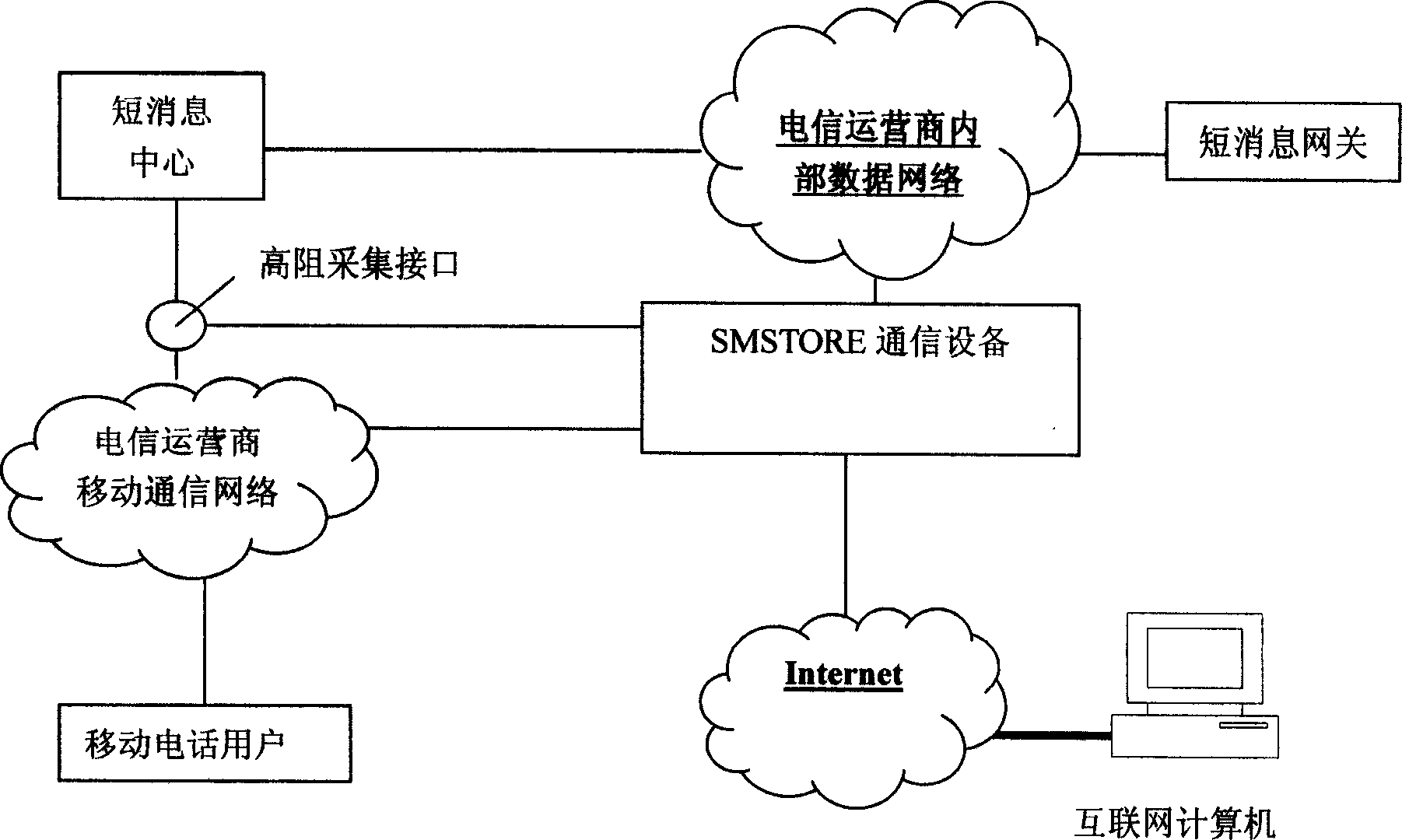
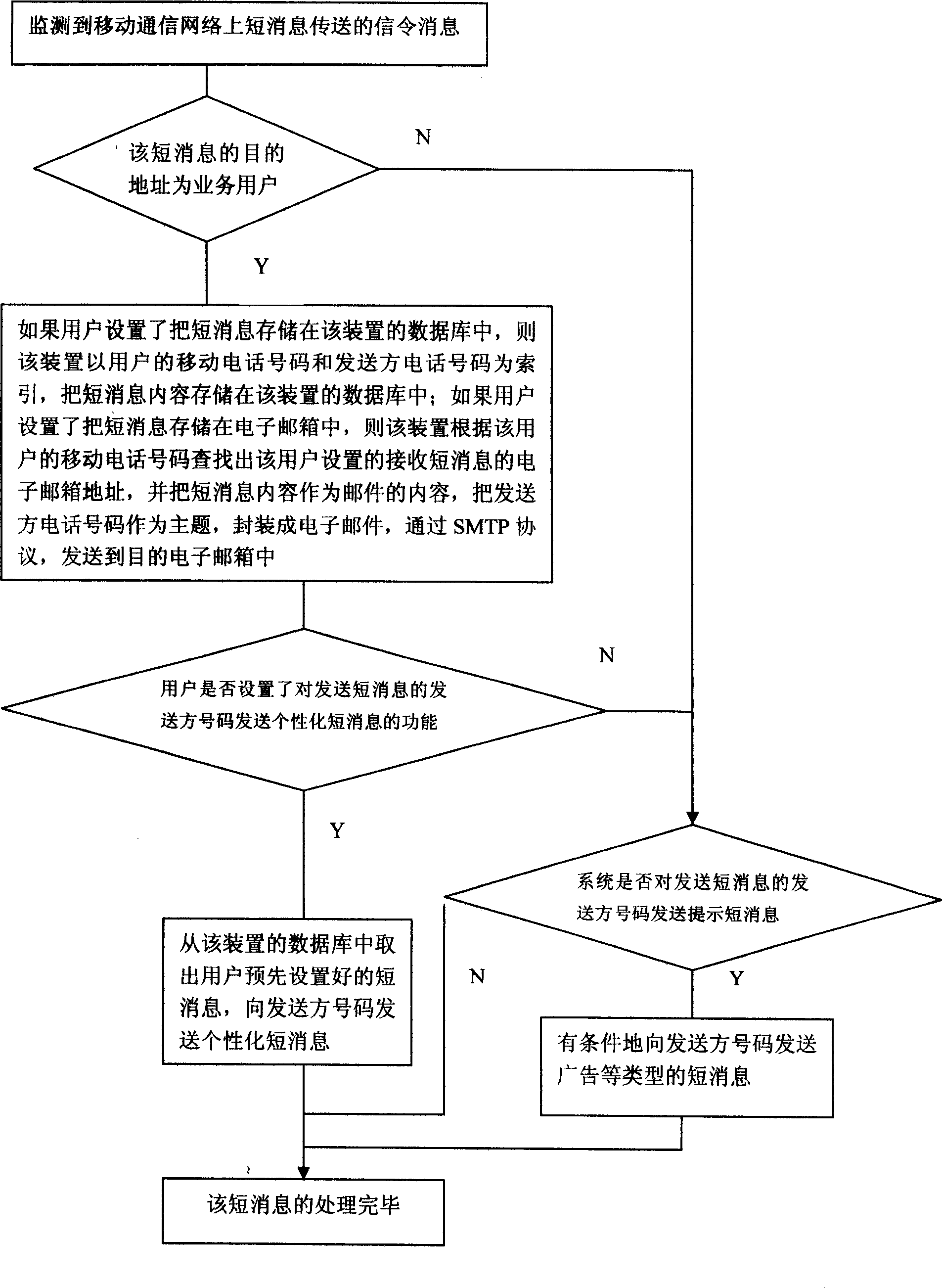
InactiveCN1812603ASolve long-term storageSolve confidentiality issuesRadio/inductive link selection arrangementsMessaging/mailboxes/announcementsPersonalizationThe Internet
A method for automatically carrying ort network storage for short message of mobile phone includes obtaining short message sent to SMSTORE user by SMSTORE communication device from mobile communication network of telecommunication company and carrying out network storage on said short message i.e. storing content of short message automatically into databank of SMSTORE communication device according to setting of user or packaging content of short message to be electronic mail being sent to electronic mailbox of user .
Owner:候万春
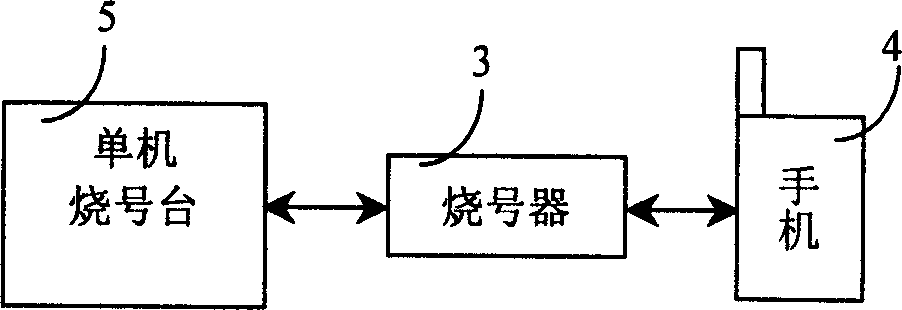
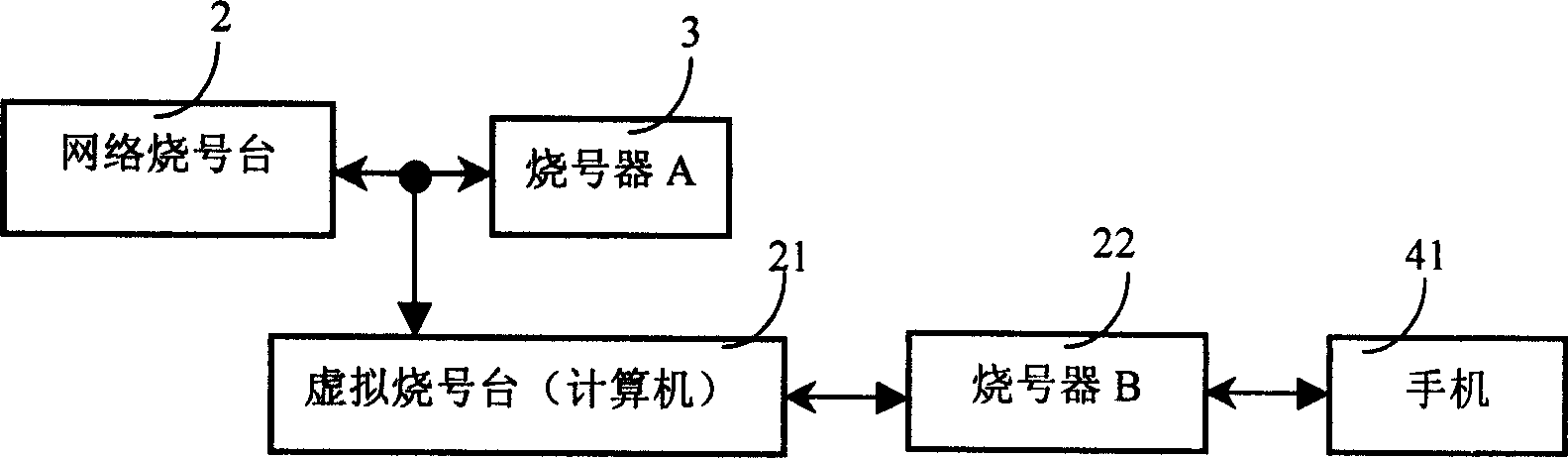
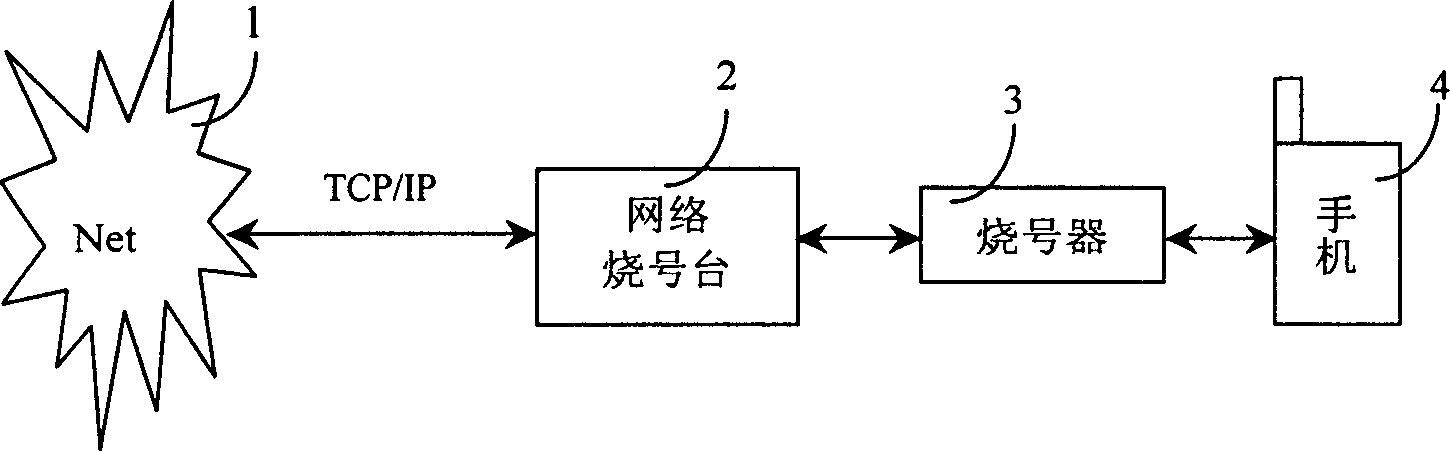
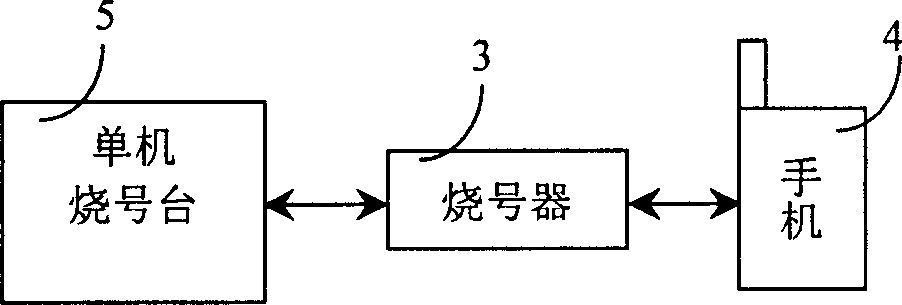
A method and system for expanding compatibility of PHS network number writing station
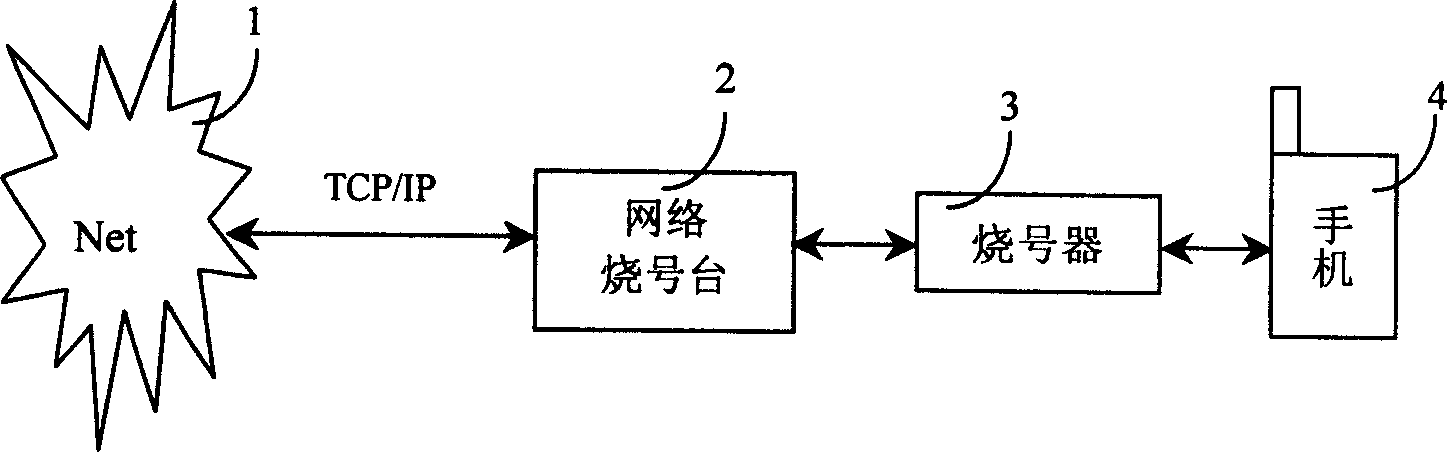
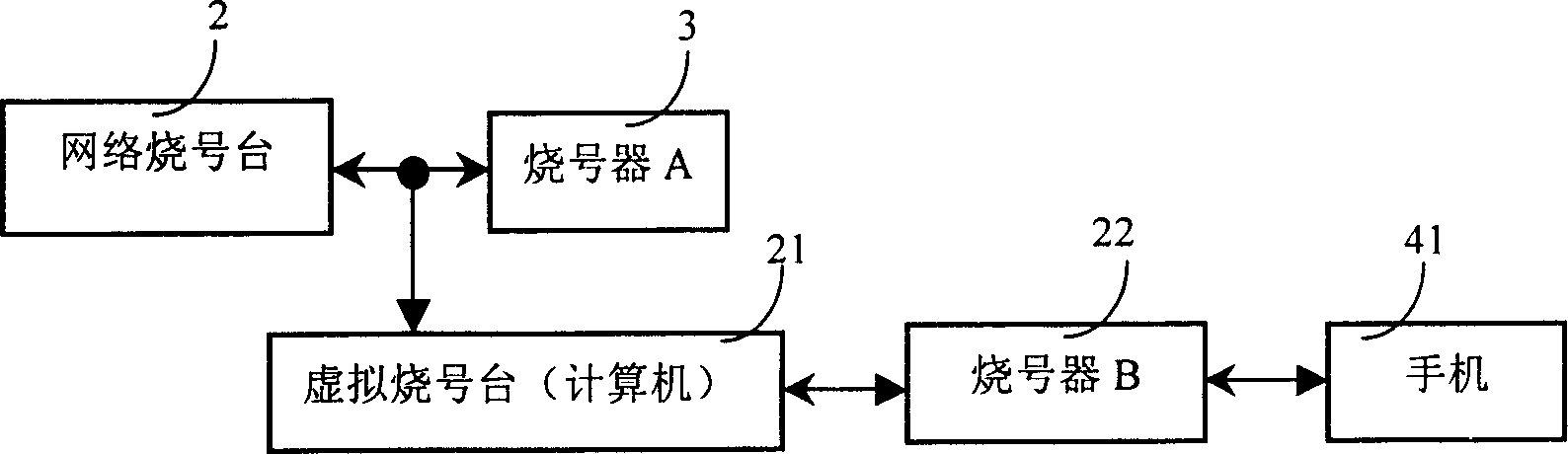
InactiveCN1568036AAddressing Confidentiality and CompatibilityEnsure safetyRadio/inductive link selection arrangementsData switching networksUser informationMobile phone
The invention discloses a method and system to extend the compatibility of PHS network number burning platform used to write network information and user information to mobile terminal by PHS network number burning platform through the number burning machine. A virtual number burning platform which can simulate the process of normal number burning of the virtual object connects between the PHS network number burning platform and the number burning machine. The virtual number burning platform can intercept the data sent to the number burning machine from the network number burning platform and burning the intercepted information that the mobile terminal needs to a new type mobile terminal. The invention and the system can improve the support and compatibility of the network number burning platform to a great deal new type mobile phone.
Owner:南通国邦科技发展有限公司
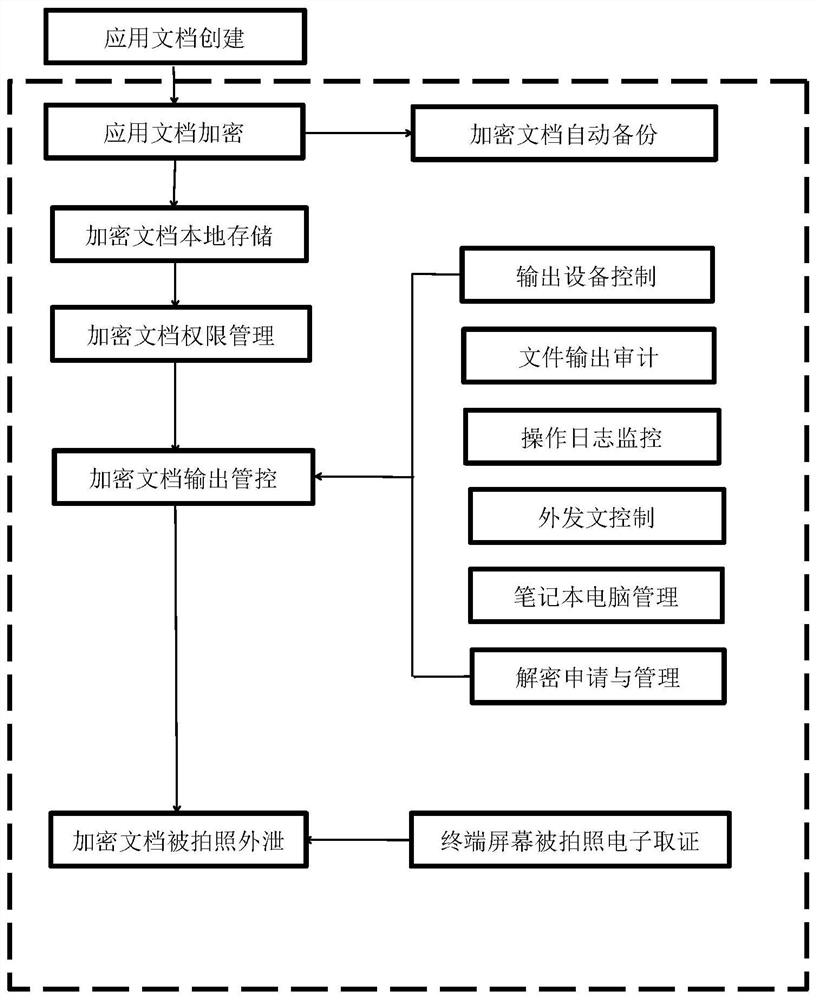
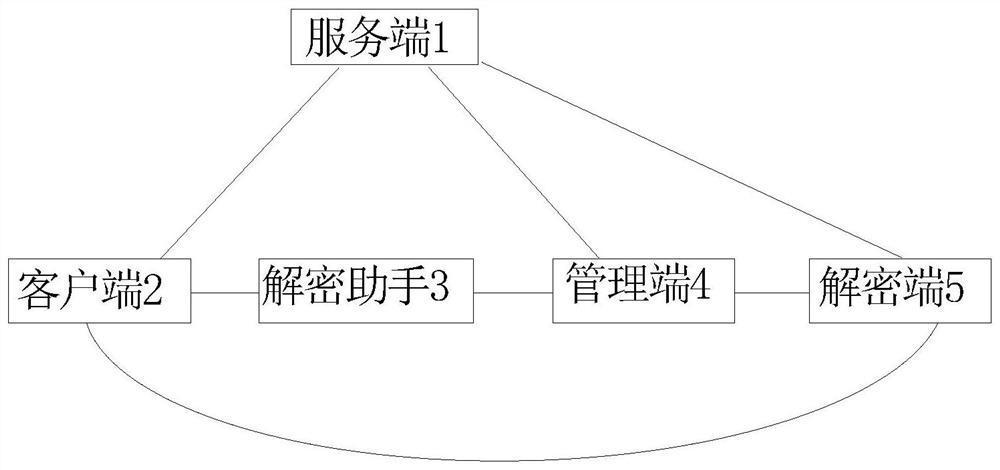
Electronic document security management method and system based on big data
PendingCN112948870ASolve confidentiality issuesSolve needsDigital data protectionDigital data authenticationConfidentialityEngineering
The invention relates to an electronic document security management method based on big data. The method comprises the following steps of encryption protection of a document, local storage of the encrypted document, authority management of the encrypted document, output management and control of the encrypted document, automatic backup of the encrypted document and electronic evidence collection after a terminal screen is photographed. The encrypted document output control comprises output equipment control, file output auditing, operation log monitoring, outgoing document control, notebook computer management and decryption application and management. Besides, the invention further discloses a management system of the system. The system comprises a server side, a client side, a decryption side, a management side and a decryption assistant, the server side is installed on a server, and the client side, the decryption side, the management side and the decryption assistant are all installed on terminal computers of corresponding users. The confidentiality and safety management requirements of internal data assets of a company can be perfectly met, and various secret divulging channels are blocked.
Owner:北京国联易安信息技术有限公司
Distributed type vulnerability scanning and evaluating method
ActiveCN104954379ASolve the problem of stepping in every scanEfficient decompositionPlatform integrity maintainanceTransmissionVulnerability scanningReal-time computing
The invention discloses a distributed type vulnerability scanning and evaluating method. According to the method, a control terminal sends scanning strategies and scanning objective data to at least one detection node, each detection node performs scanning actions according to received scanning strategies and scanning objective data and sends back scanning data to the control terminal, state information of each detection node at each period of state is sent to the control terminal, and the control terminal determines the state of each detection node according to the state information receiving time. According to the distributed type vulnerability scanning and evaluating method, the problem that a user is required to get involved in scanning each time is solved, meanwhile, the distributed type scanning is effectively realized, a task is effectively decomposed, the performance is improved, and the problem about secret-associated issues can be solved.
Owner:西安交大捷普网络科技有限公司
Secret writing fax machine
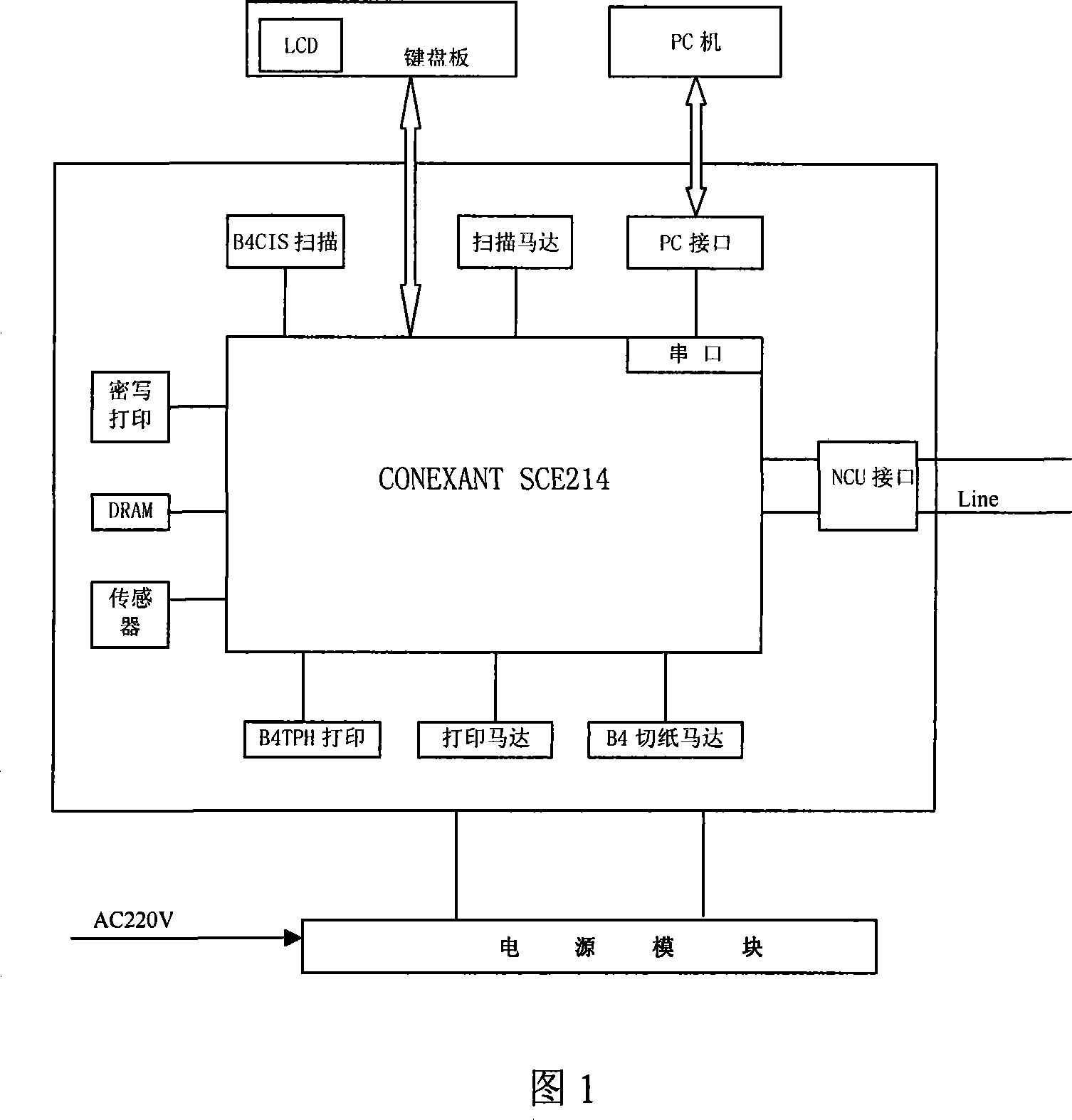
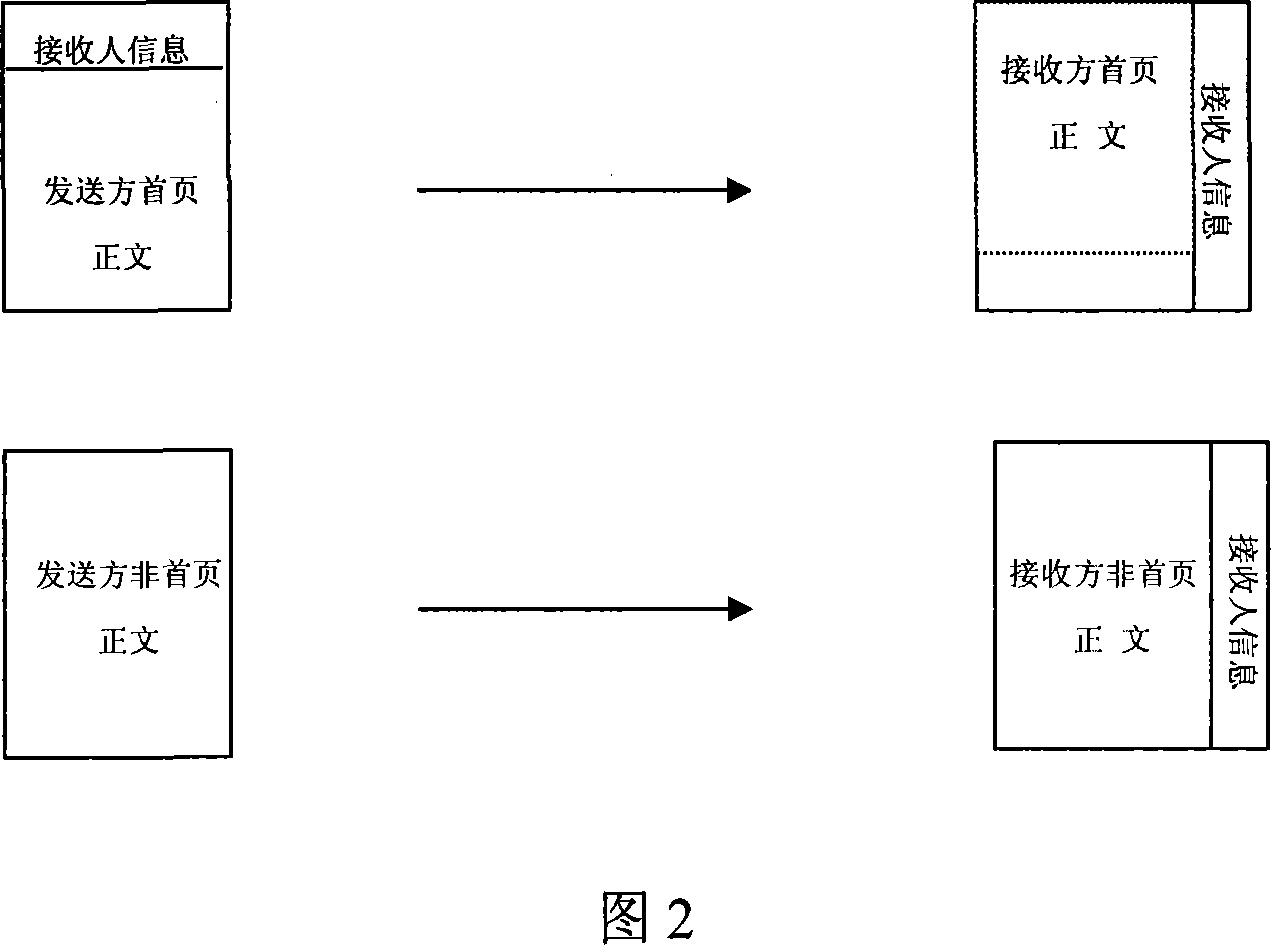
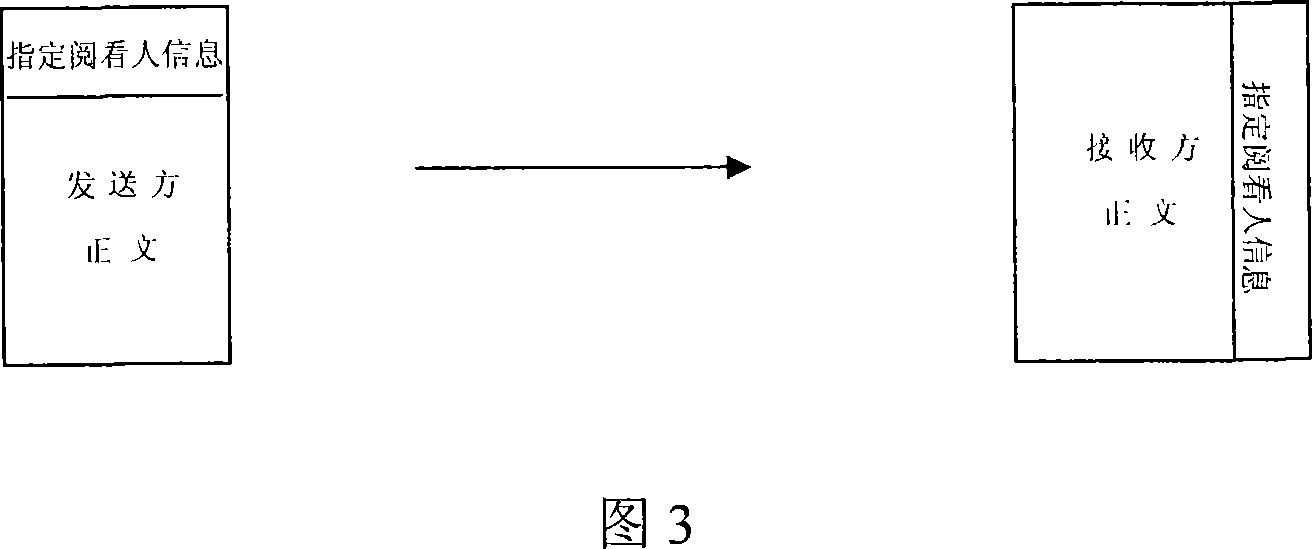
The invention uses a dedicated steganography paper, a B4 thermofax printer with software and hardware functionalities base on a CONEXANT fax main control chip to print the received message on the dedicated steganography paper through a special data processing approach. The visible area of the steganography paper prints the information about the recipients, and the steganography area of the paper prints the text message; the invention also designs a control circuit for controlling the paper-cutting position.
Owner:TOEC TECH
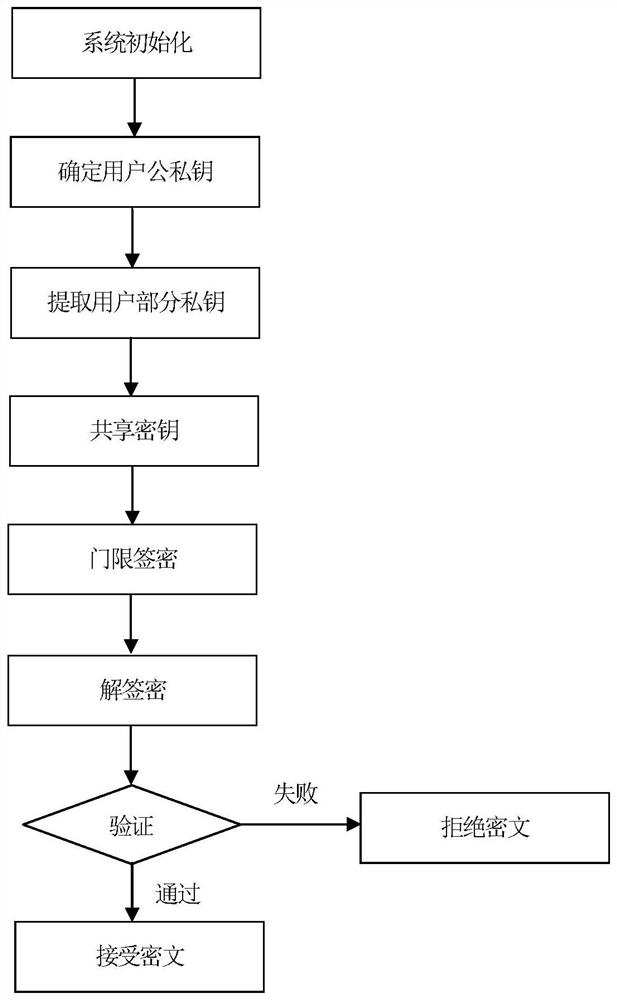
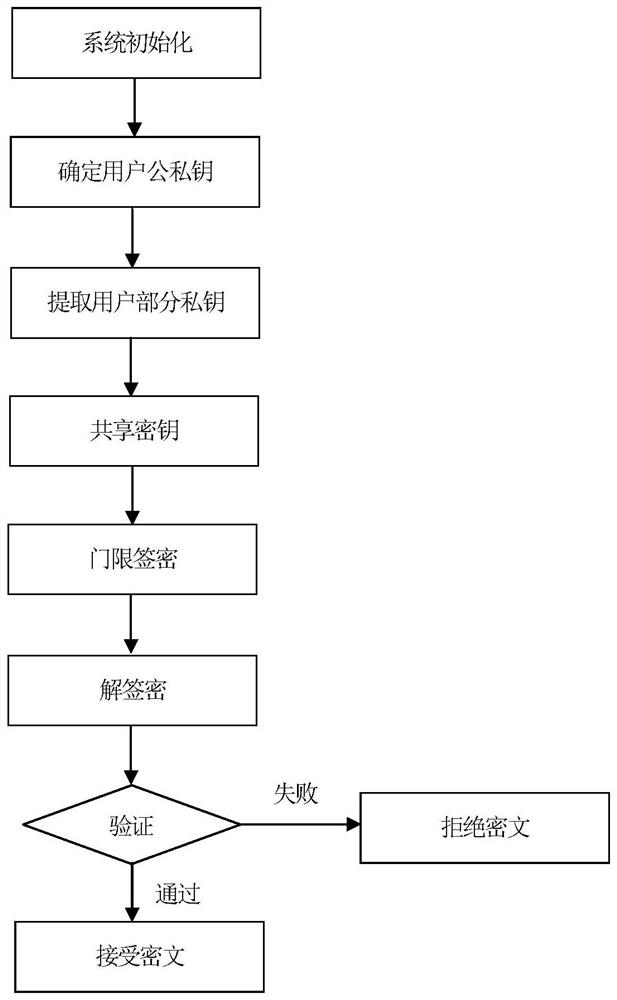
Certificateless threshold signcryption method under secret sharing mechanism
ActiveCN112260830ASolve management problemsAvoid single point of failure problemsKey distribution for secure communicationEncryption apparatus with shift registers/memoriesInternet privacySigncryption
The invention discloses a certificateless threshold signcryption method under a secret sharing mechanism. The method comprises the steps of initializing a system, determining public and private keys of a user, extracting part of private keys of the user, threshold signcryption and unsigncryption. A certificateless threshold encryption and authentication method is adopted in the threshold signcryption step, so the problems of certificate management and key escrow and the problem of single-point failure caused by the uniqueness of a private key are solved; on the theoretical basis of certificateless public key cryptography, a secret sharing mechanism and threshold signcryption, the security is improved, the problems of dependence on a secure channel, certificate management and key escrow areavoided, the problem that a private key owner has absolute permission is solved, and adaptive selection ciphertext attacks and adaptive selection message attacks can be defended, so the method is suitable for a network information security application environment. The method has the advantages of good security, low computation complexity and the like, and has a good application prospect in the field of network information security.
Owner:青海交通职业技术学院
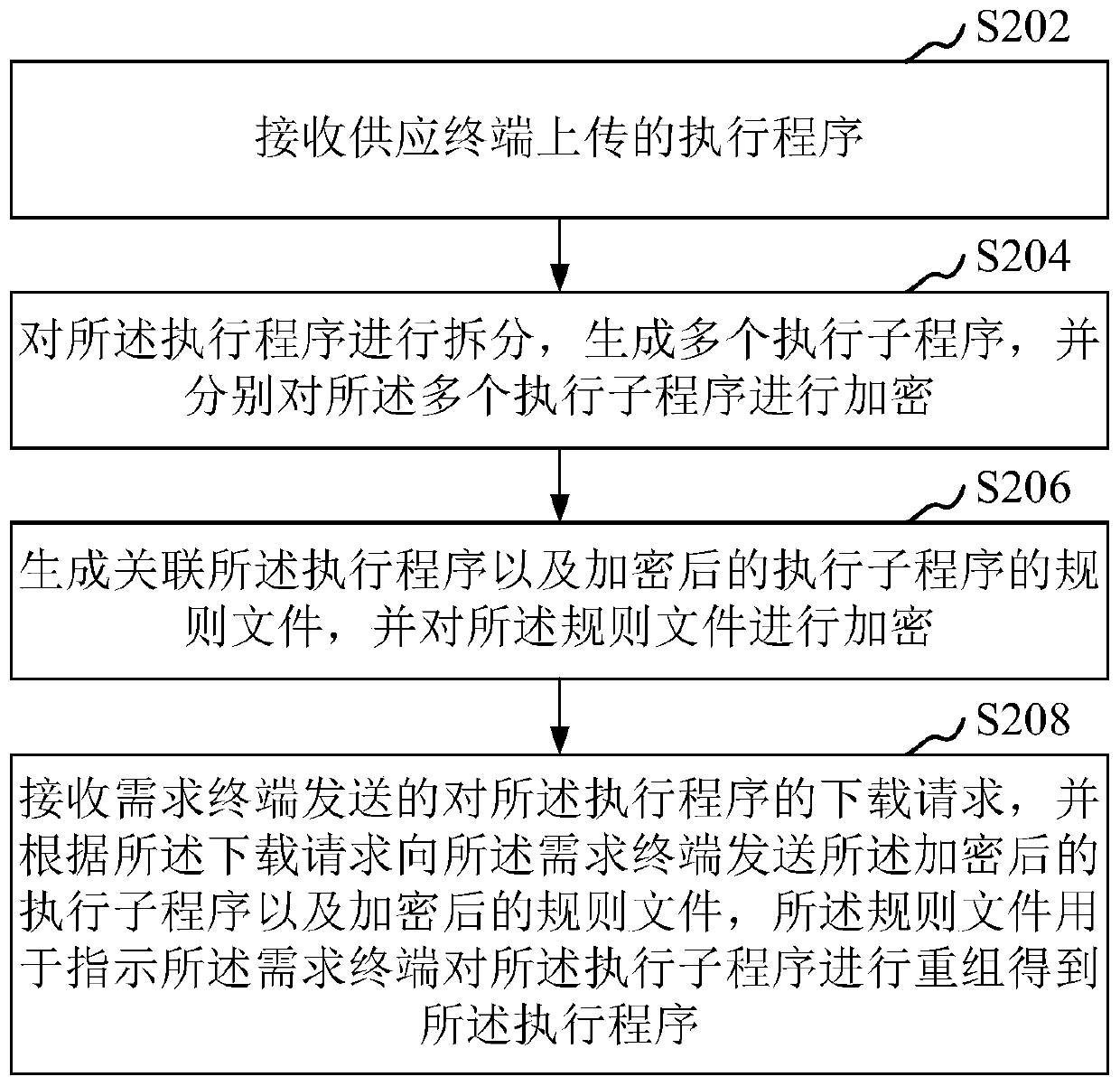
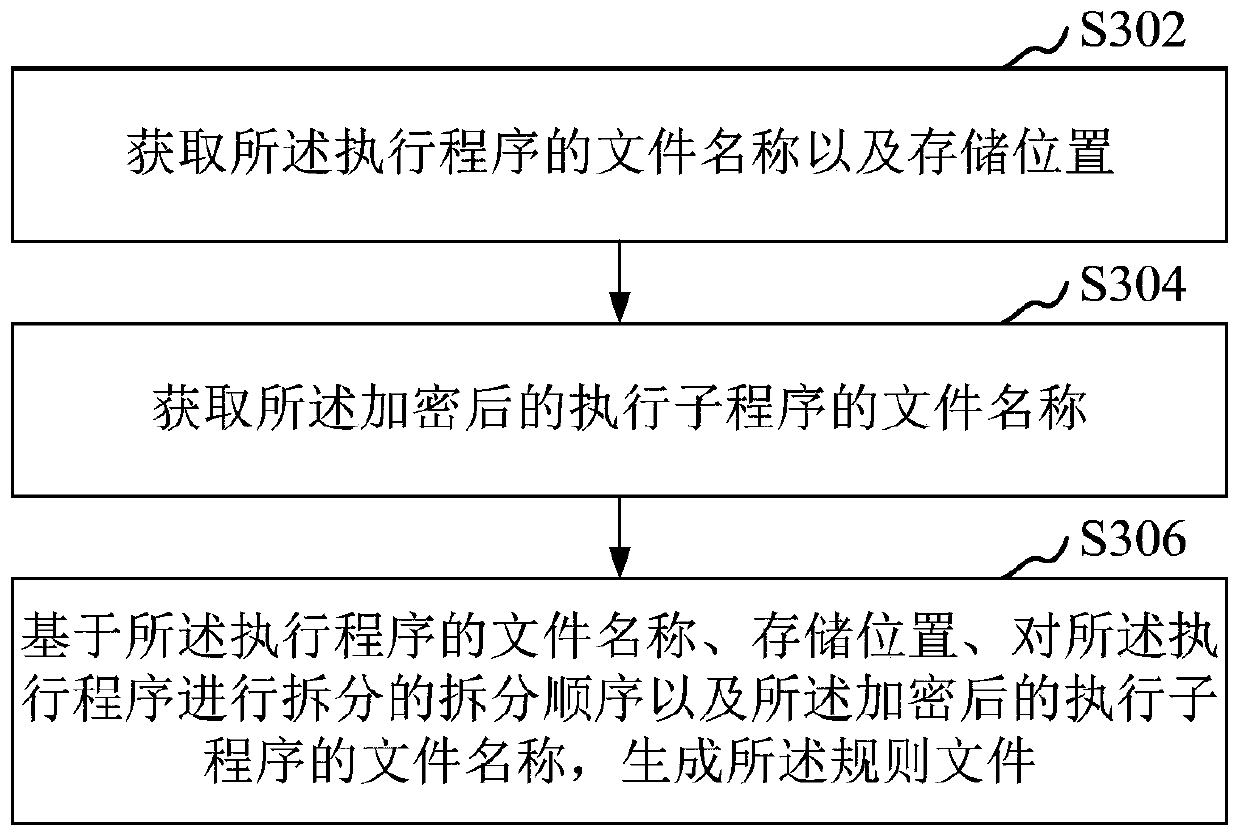
Execution program processing method, system, device, computer equipment and medium
ActiveCN111125645ASolve confidentiality issuesDigital data protectionEnergy efficient computingConfidentialitySoftware engineering
The invention relates to the field of data security, in particular to an executive program processing method, a system, a device, computer equipment and a storage medium. The method comprises the following steps: receiving an executive program uploaded by a supply terminal; splitting the executive program to generate a plurality of executive subprograms, and respectively encrypting the plurality of executive subprograms; generating a rule file associated with the execution program and the encrypted execution subprogram, and encrypting the rule file; and receiving a download request for the execution program sent by a demand terminal, and sending the encrypted execution subprogram and an encrypted rule file to the demand terminal according to the download request, the rule file being used for indicating the demand terminal to recombine the execution subprogram to obtain the execution program. By adopting the method, the confidentiality problem of the executive program can be solved.
Owner:SHANGHAI ORIGIMED CO LTD
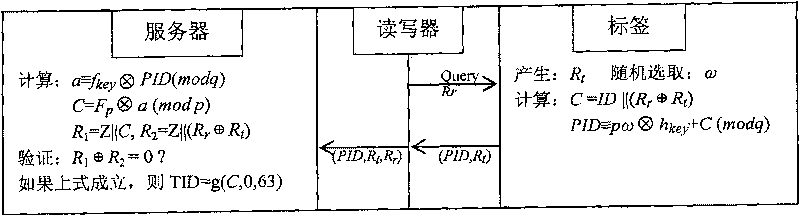
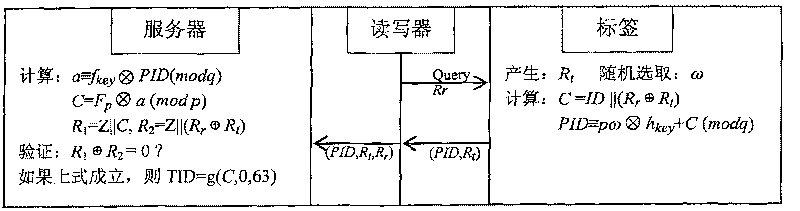
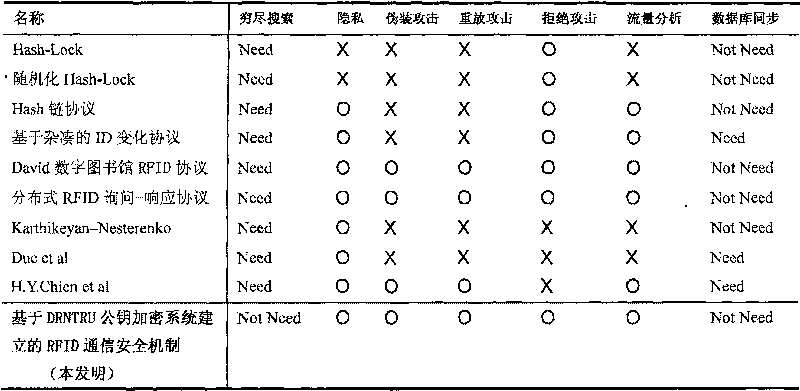
RFID communication security mechanism established based on dynamic randomization DRNTRU public key encryption system
InactiveCN101217362BImprove confidentialityResistance to denial of service attacksKey distribution for secure communicationCo-operative working arrangementsLimited resourcesCommunications security
The invention discloses an RFID communication safety mechanism which is established by a public key encrypting system on the base of dynamic randomization DRNTRU (Dynamic, Randomized Number Theory Research Unit). The RFID communication safety mechanism which is established by a public key encrypting system based on the dynamic randomization DRNTRU can not only effectively solve the safety problemof the RFID system. The method is novel, simple and easy to realize, does not need to fully search secret keys and TID (tag identifier) of, does not need secret key synchronization, only needs single-direction authentication and is suitable for the RFID system having limited resource and requiring high-speed responding.
Owner:SUN YAT SEN UNIV
Emergency monitoring and processing device for power primary equipment defects
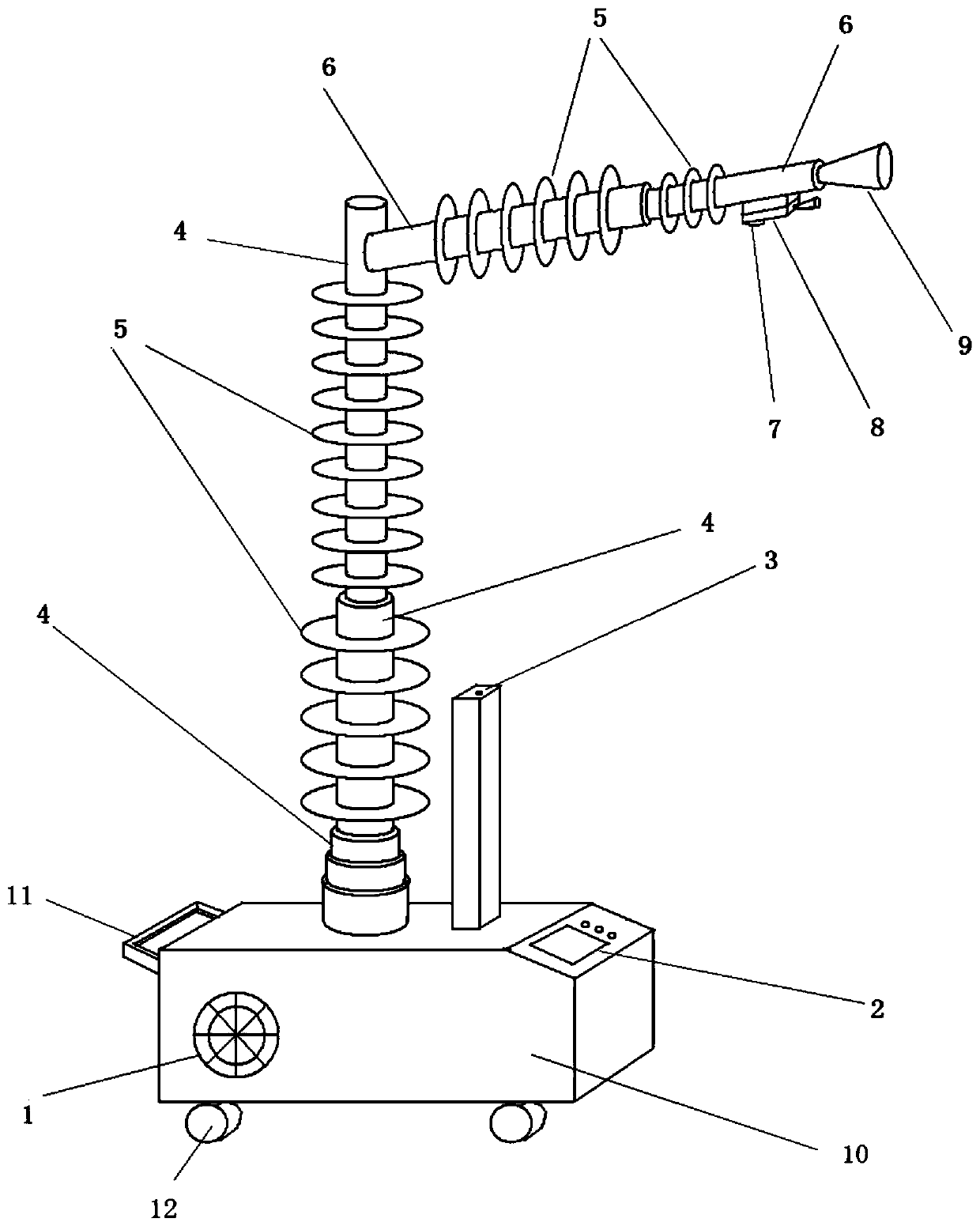
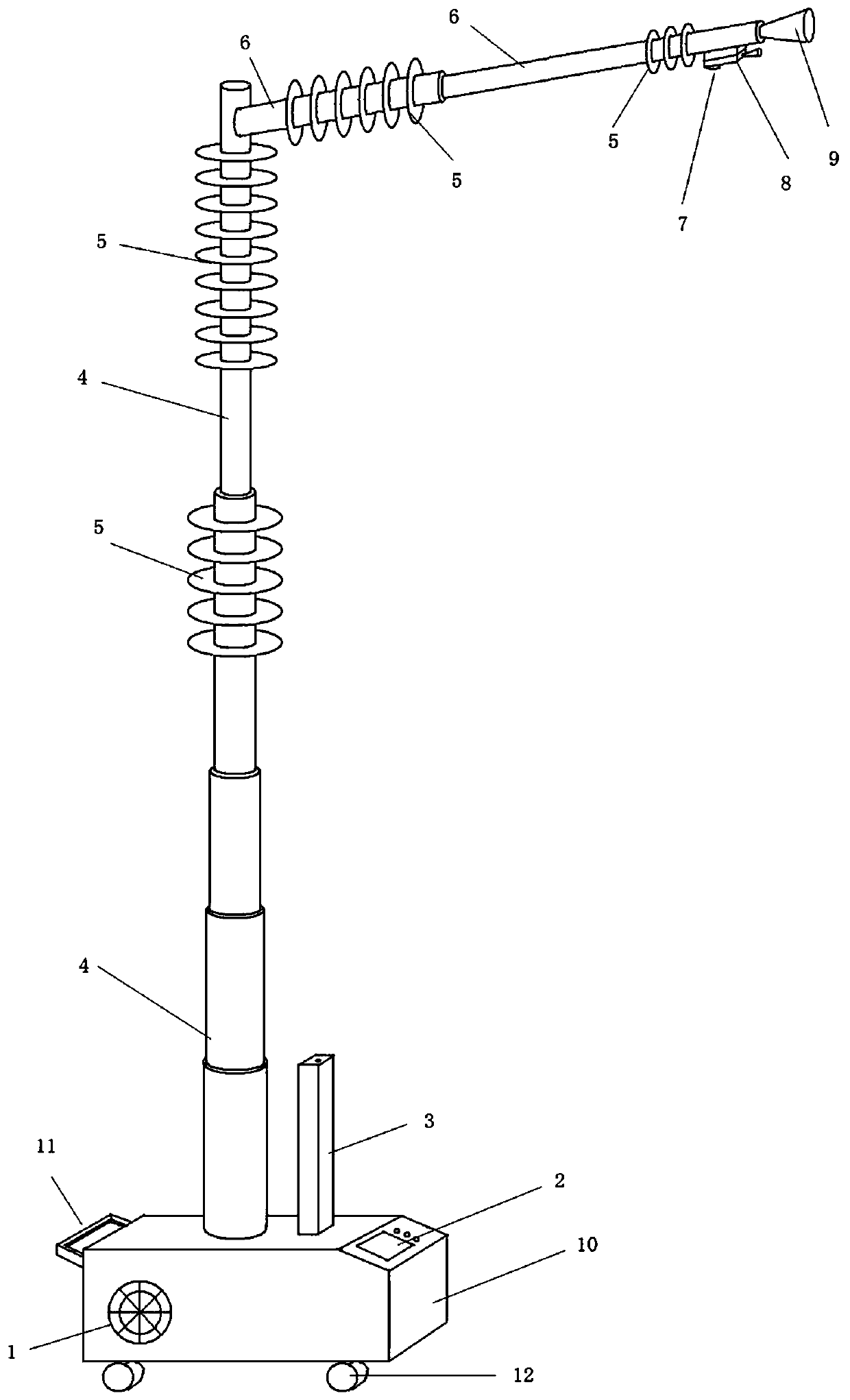
ActiveCN110868571AReduce oxidation rateClearly monitor visible light imagesTelevision system detailsColor television detailsStructural engineeringCentrifugal fan
The invention relates to an emergency monitoring and processing device for defects of power primary equipment. The trolley comprises a trolley base, a longitudinal insulating telescopic rod and a transverse insulating telescopic rod, a centrifugal fan is arranged in the cart base; the end part of the transverse insulating telescopic rod is provided with an air nozzle; the longitudinal insulating telescopic rod is of a hollow rod structure with one closed end. The transverse insulating telescopic rod is of a hollow rod structure; an air outlet of the centrifugal fan is communicated with the interior of the longitudinal insulating telescopic rod; the longitudinal insulating telescopic rod is communicated with the interior of the transverse insulating telescopic rod; the longitudinal insulating telescopic rod and the transverse insulating telescopic rod are of a multi-section rod-shaped structure; a double-image shooting module is arranged at the bottom of the rod wall of the outermost section of the transverse insulating telescopic rod, a laser power receiving and communication module is arranged on the double-image shooting module, and a laser power supply and communication module matched with the laser power receiving and communication module for work is arranged on the upper surface of the cart base. Compared with the prior art, the system has the advantages of emergency cooling, comprehensive monitoring, low cost and the like.
Owner:SHANGHAI MUNICIPAL ELECTRIC POWER CO +1
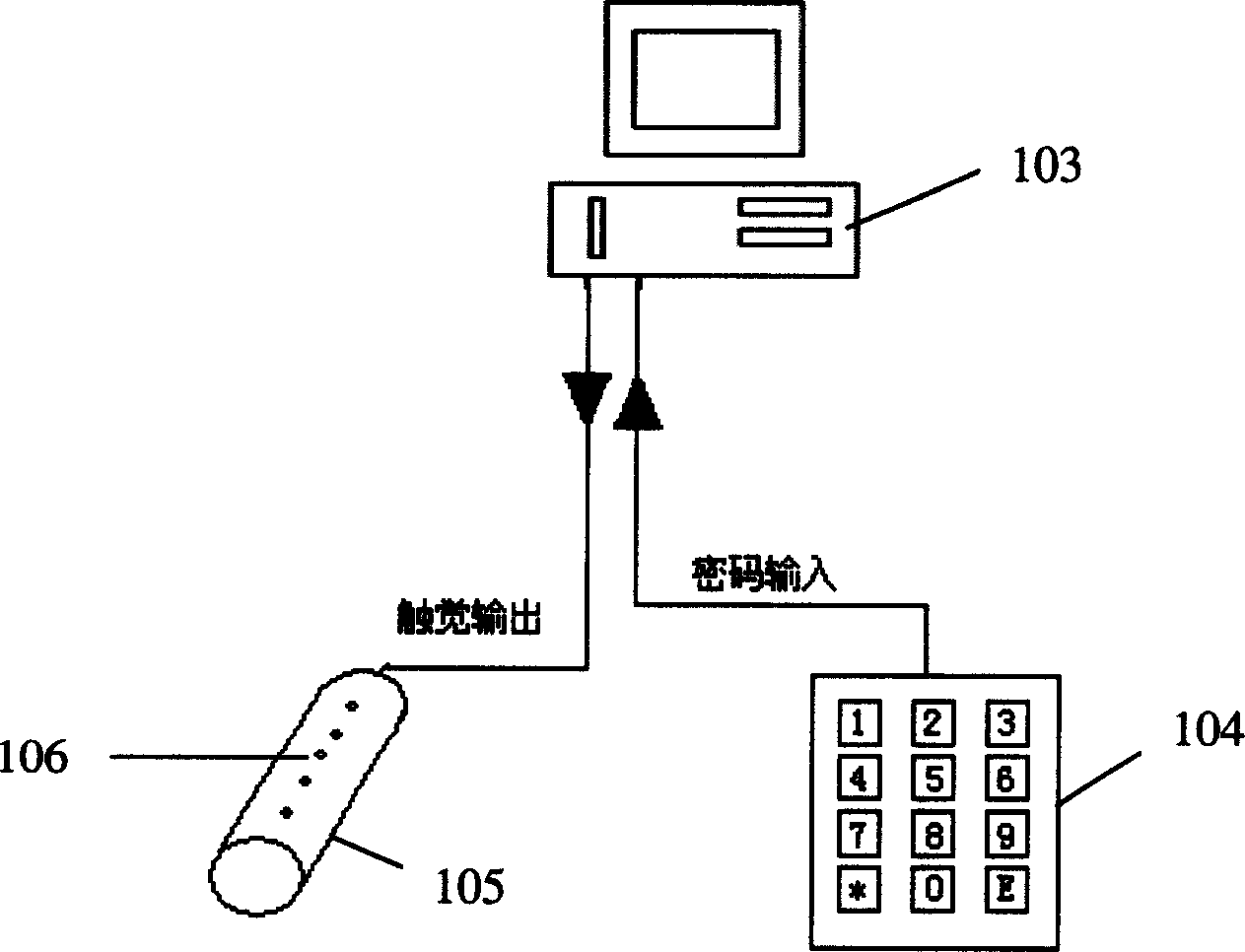
Toutch-feeling out-put type cipher inputting system and inputting method
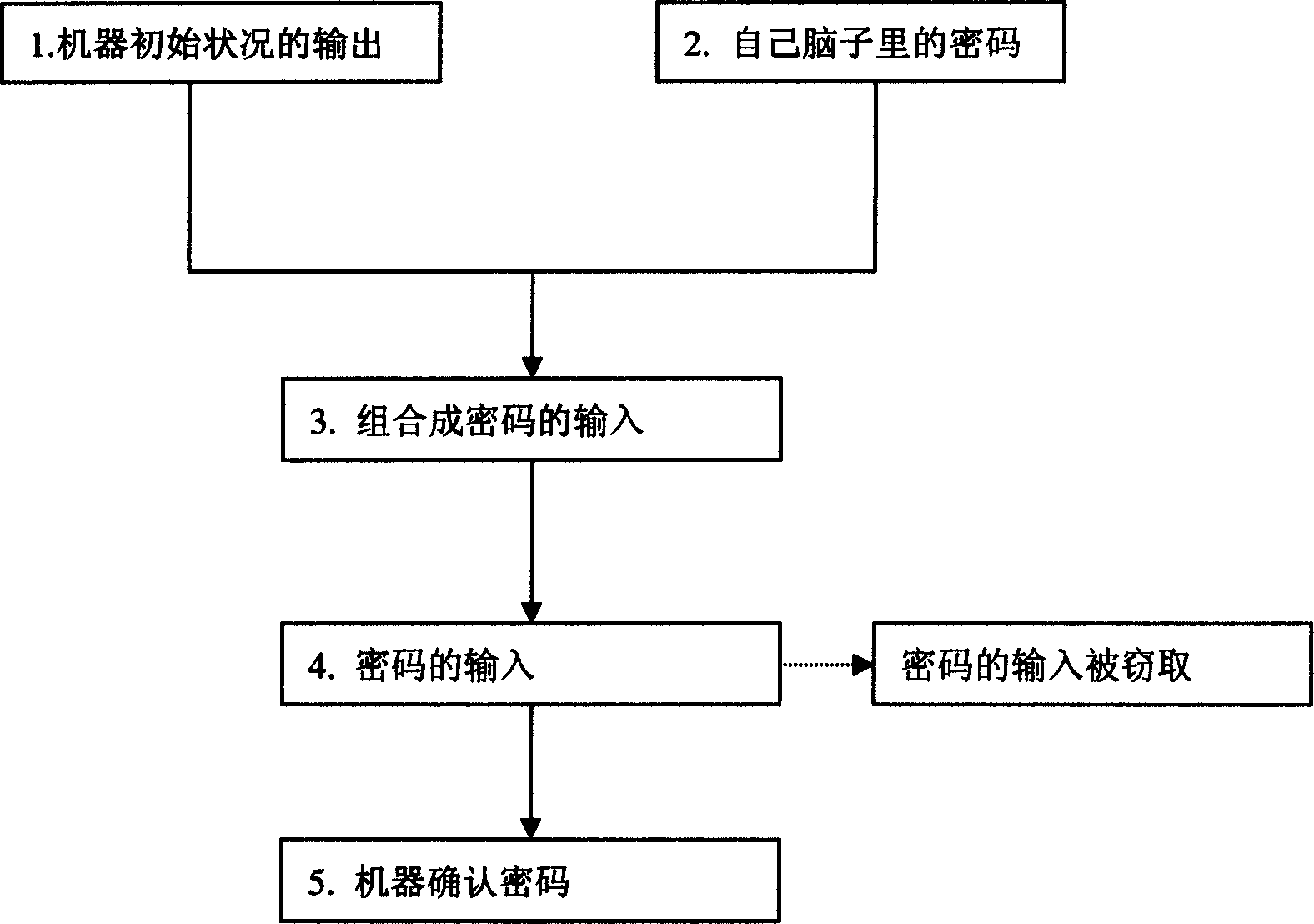
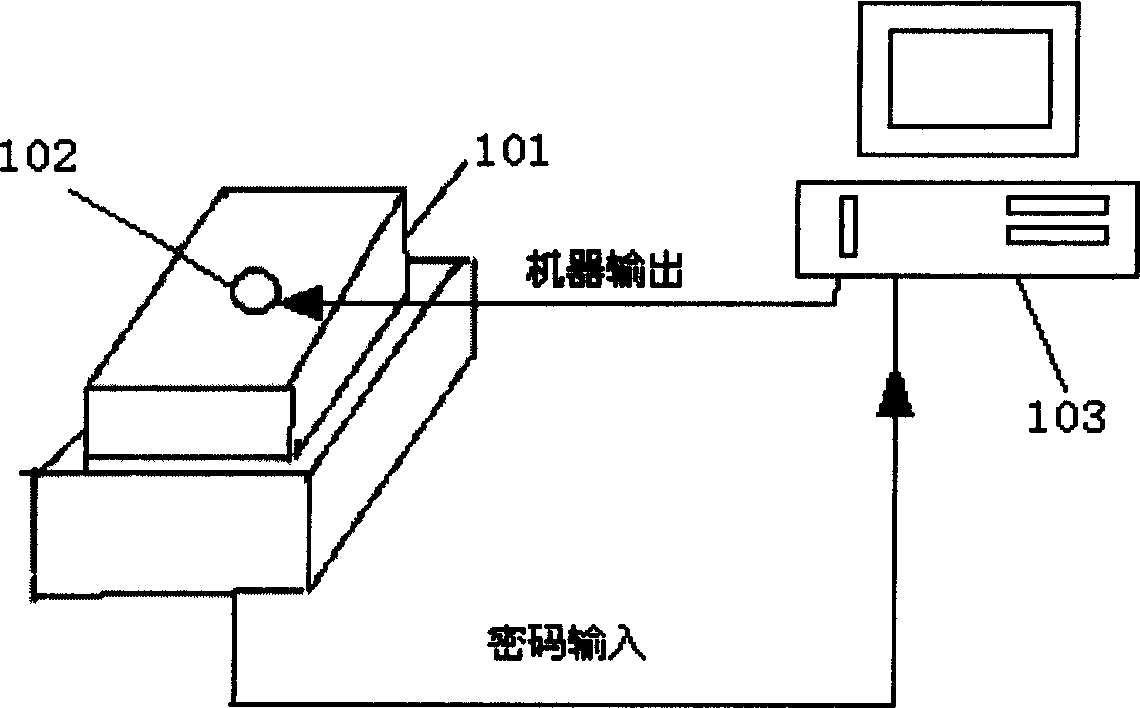
InactiveCN1581216ASolve confidentiality issuesInput/output for user-computer interactionGraph readingComputer scienceEmbedded system
The present invention relates to a tactile sense outputted cipher input system and its input method. Said system includes several basic keys on every key a contact is respectively set, said several basic key are parallelly arranged and formed ito a key sequence, and said key sequence is connected with computer, and said contacts are connected with said computer. Said invention also provides its method for inputting cipher code and concrete steps, and can effectively solve the privacy problem for inputting cipher code.
Owner:杨涛
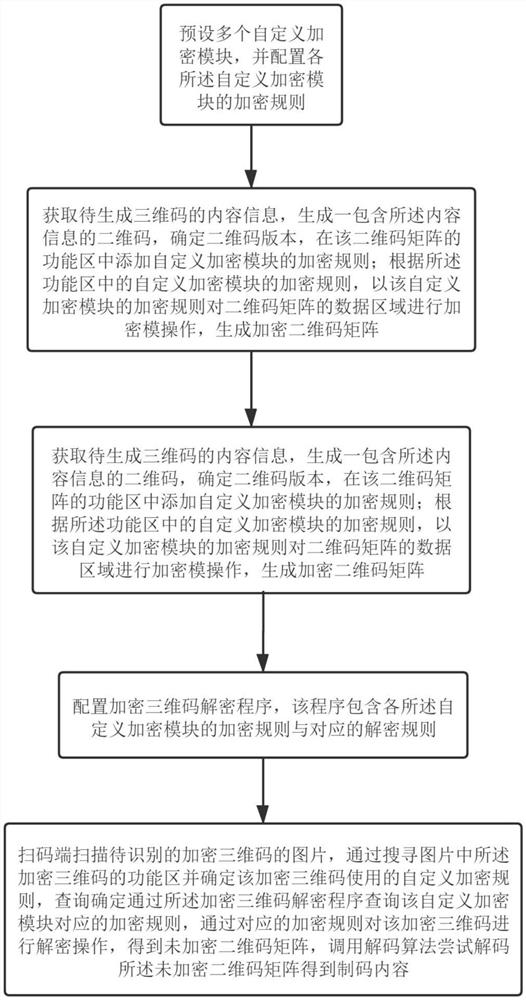
Encrypted three-dimensional code generation and identification method and system
ActiveCN114154605ASolve confidentiality issuesSolve needsDigital data protectionRecord carriers used with machinesCode generationAlgorithm
The invention relates to a method for generating and identifying an encrypted three-dimensional code. The method comprises a code generating step and an identifying step, the code generation step specifically comprises the following steps: presetting a plurality of user-defined encryption modules and encryption rules; the method comprises the steps of obtaining to-be-coded content, determining a user-defined encryption rule, compiling the to-be-coded content into an unencrypted two-dimensional code matrix, and performing encryption operation according to the selected user-defined encryption rule to generate an encrypted two-dimensional code matrix; drawing a two-dimensional code graph through the encrypted two-dimensional code matrix, and obtaining a background picture to be fused with the two-dimensional code graph to generate an encrypted three-dimensional code; the decoding step specifically comprises the following steps: configuring an encrypted three-dimensional code decryption program containing respective defined encryption rules at a code scanning end; and the code scanning end scans the encrypted three-dimensional code picture to be identified, determines the self-defined encryption rule used by the encrypted three-dimensional code, decrypts the encrypted three-dimensional code through the corresponding decryption rule to obtain an unencrypted two-dimensional code matrix, and decodes the unencrypted two-dimensional code matrix to obtain the code making content.
Owner:CN3WM XIAMEN NETWORK TECH CO LTD
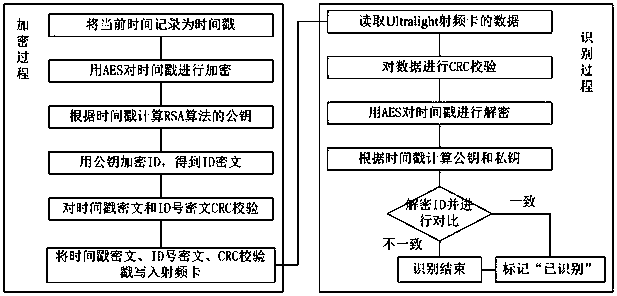
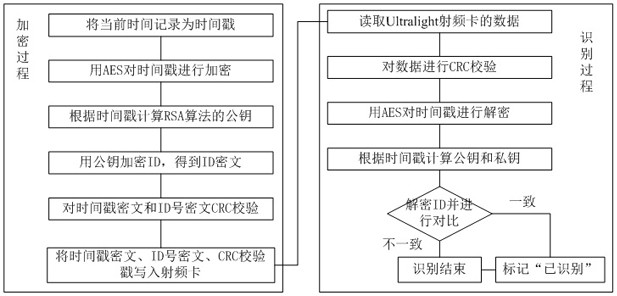
Dynamic RSA encryption method for Ultralight radio frequency (RF) card through time stamp, and dynamic RSA identification method for Ultralight RF card through time stamp
ActiveCN108540288ASolve confidentiality issuesLow costKey distribution for secure communicationError preventionComputer hardwareCiphertext
The invention discloses a dynamic RSA encryption method for an Ultralight radio frequency (RF) card through a time stamp. The method comprises the following steps: recording current time as the time stamp; encrypting the time stamp through AES to obtain time stamp ciphertext; carrying out specific operation on the time stamp to obtain a public key satisfying the RSA algorithm; reading an ID numberof the Ultralight RF card; encrypting the read ID number through the public key to obtain ID number ciphertext; carrying out accumulation and operation on the time stamp ciphertext and the ID numberciphertext to obtain CRC data; and writing the time stamp ciphertext, the ID number ciphertext and the CRC data into a data area of the Ultralight RF card. The invention further discloses a corresponding dynamic RSA identification method for the Ultralight RF card through the time stamp. The encryption method and the identification method provided by the invention have the advantage that the cracking difficulty and the safety of the Ultralight RF card are improved.
Owner:CHENGDU TME SOFTWARE
Synthetic environment simulation platform
ActiveCN102364488BSolve confidentiality issuesRelieve stressSpecial data processing applicationsComputer scienceEnvironmental data
The invention discloses a synthetic environment simulation platform which is used for supplying environmental data to a virtual test object in a virtual test process. The synthetic environment simulation platform comprises a basic environment database, a scene scenario environment database, a running environment database, a scene scenario data generation module, a running environment data generation module and an environment coupling module. By adopting the synthetic environment simulation platform, calculation of interaction between the virtual test object and a synthetic environment model is realized.
Owner:CHINA ACAD OF LAUNCH VEHICLE TECH
Method for encrypting/deciphering dynamically data file
InactiveCN101098224BProtect intellectual propertySolve confidentiality issuesPublic key for secure communicationUnauthorized memory use protectionPlaintextOperational system
The invention discloses a method for dynamically encrypting and decrypting data document, which comprises that in network condition, via C / S mode, manager centralized controls important documents of user computer, the system dynamically decrypts and encrypts clear text, the important documents can only be read or changed under the control of server in special network condition, which content is shown as cryptogram when off the network condition, when user copies clear text document from other places, the documents can not be changed when the system is sensitive, or else, in storage, the documents are converted into cryptogram type. The invention is based on software platform, correlated only with operation system, but not application programs, to dynamically encrypt and decrypt the data documents, therefore, the data documents can only work in private network condition, while the leaked document is in cryptogram type, to protect intellectual property.
Owner:CHINA NON-FERROUS METALS PROCESSING TECH CO LTD
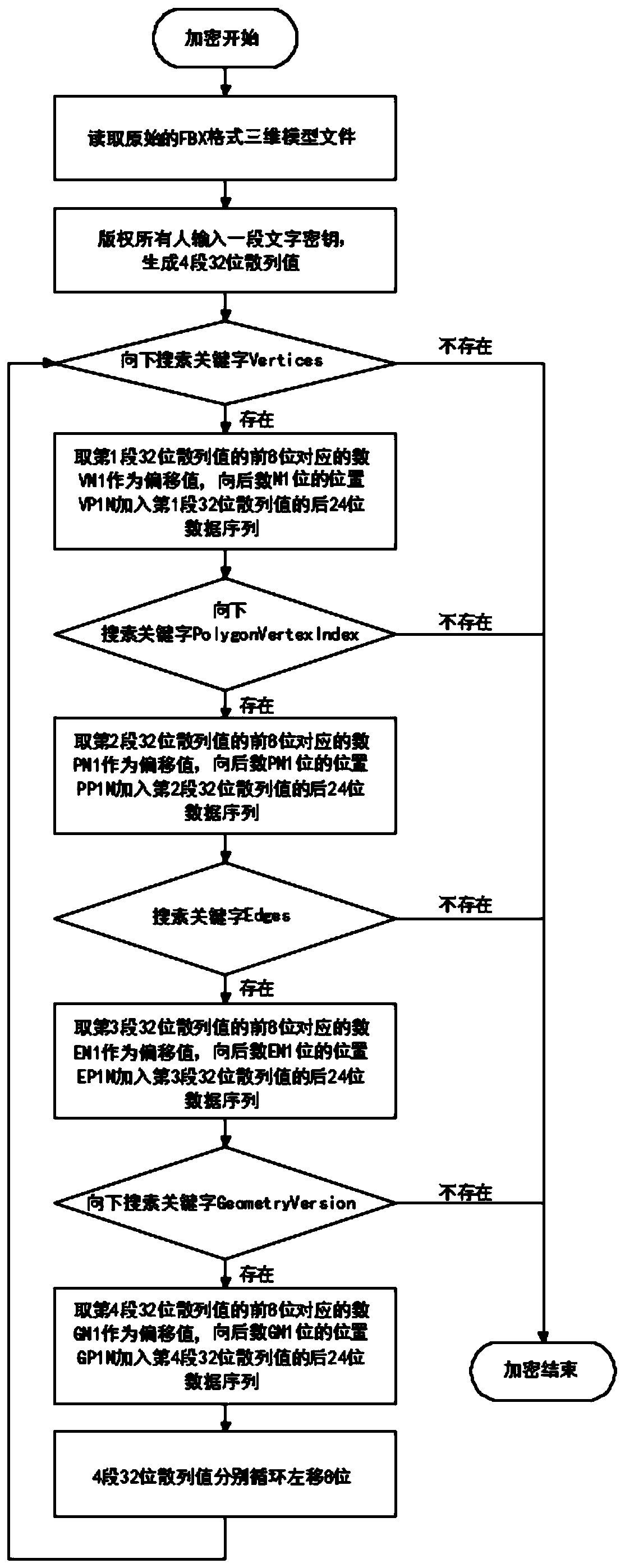
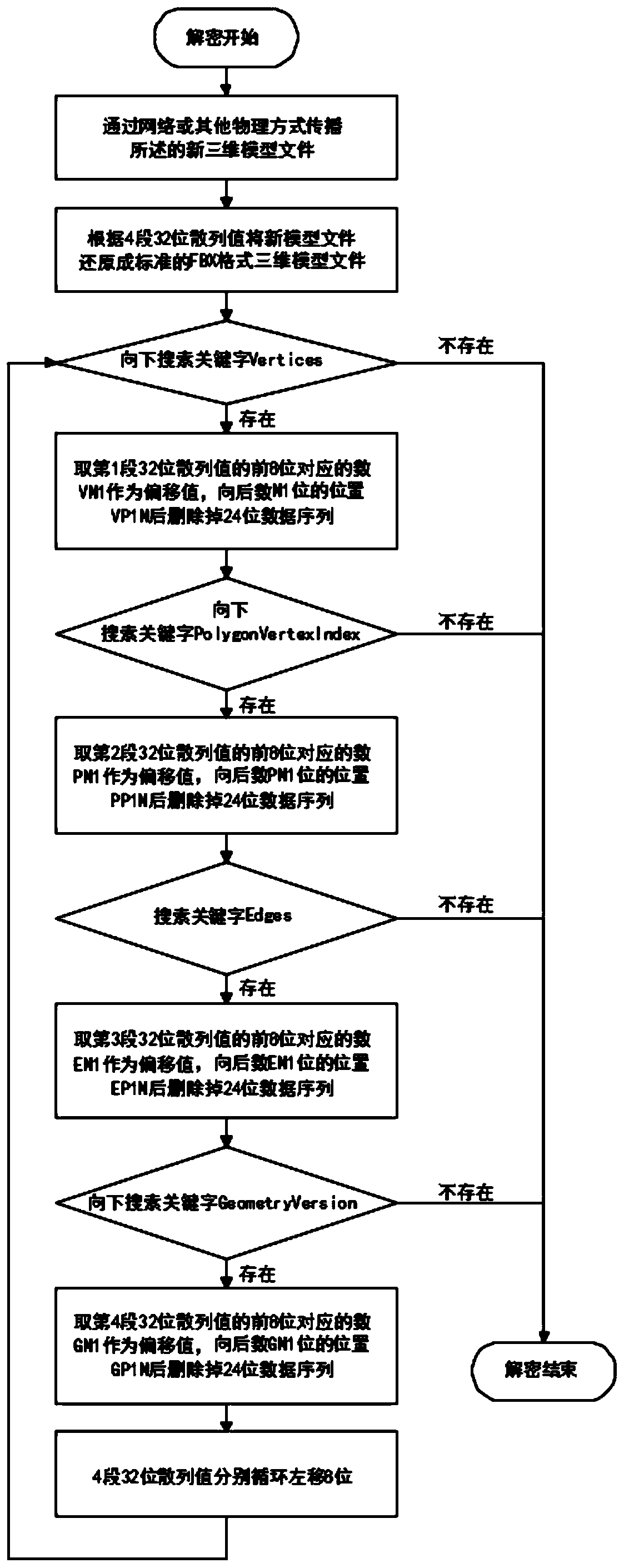
Encryption and decryption method of FBX format three-dimensional model
ActiveCN110138555AImprove efficiencyImprove securityKey distribution for secure communicationEncryption apparatus with shift registers/memoriesThree dimensional modelComputer hardware
The invention discloses an encryption and decryption method of an FBX format three-dimensional model, particularly relates to the field of three-dimensional models, and comprises an encryption moduleand a decryption module, 1) the encryption method of the encryption module comprises the following steps: S101, reading an original FBX format three-dimensional model file; and S102, inputting a section of text key by a copyright owner, and generating four sections of 32-bit hash values through MD5 encryption. The invention provides a simple, easy-to-use and high-efficiency encryption and decryption method for an FBX format three-dimensional model. Encryption and decryption method are adopted, the adding position of the random data of the model file is calculated through the preset secret key,the adding position of the random data of the model file can be adjusted by changing the secret key, and therefore the advantage that the decryption method is high in efficiency is kept, meanwhile, the safety of the algorithm is improved, the algorithm is not prone to being cracked, and the complexity of the three-dimensional model decryption algorithm is low.
Owner:长沙能川信息科技有限公司
Certificateless threshold signcryption method under secret sharing mechanism
ActiveCN112260830BSolve management problemsAvoid single point of failure problemsKey distribution for secure communicationEncryption apparatus with shift registers/memoriesComputation complexityCertificate
A certificateless threshold signcryption method under a secret sharing mechanism, which consists of steps of system initialization, determining a user's public and private keys, extracting a part of the user's private key, threshold signcryption, and decrypting the signcryption. In the threshold signcryption step, the method of certificate-free threshold encryption and authentication is adopted, which solves the problem of certificate management and key escrow and the problem of single point of failure caused by the unique private key; with certificate-free public key cryptography and secret sharing mechanism And threshold signcryption is the theoretical basis, which improves security, avoids the dependence on secure channels, certificate management and key escrow issues, and the private key owner has absolute authority issues, which can defend against adaptively chosen ciphertext attacks and adaptively chosen Message attack, suitable for network information security application environment. The invention has the advantages of good security, low calculation complexity, etc., and has a good application prospect in the field of network information security.
Owner:青海交通职业技术学院
A dynamic rsa encryption and identification method for ultralight radio frequency cards using time stamps
ActiveCN108540288BSolve confidentiality issuesLow costKey distribution for secure communicationError preventionCiphertextRadio frequency
The invention discloses a dynamic RSA encryption method for an Ultralight radio frequency (RF) card through a time stamp. The method comprises the following steps: recording current time as the time stamp; encrypting the time stamp through AES to obtain time stamp ciphertext; carrying out specific operation on the time stamp to obtain a public key satisfying the RSA algorithm; reading an ID numberof the Ultralight RF card; encrypting the read ID number through the public key to obtain ID number ciphertext; carrying out accumulation and operation on the time stamp ciphertext and the ID numberciphertext to obtain CRC data; and writing the time stamp ciphertext, the ID number ciphertext and the CRC data into a data area of the Ultralight RF card. The invention further discloses a corresponding dynamic RSA identification method for the Ultralight RF card through the time stamp. The encryption method and the identification method provided by the invention have the advantage that the cracking difficulty and the safety of the Ultralight RF card are improved.
Owner:CHENGDU TME SOFTWARE
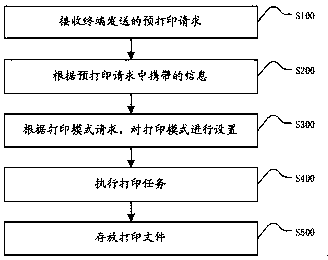
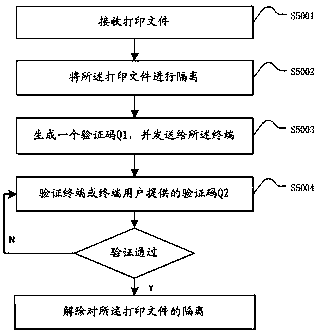
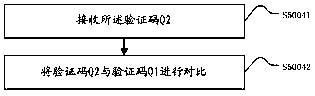
Method and apparatus for multi-mode shared printing
InactiveCN107656608ASolve the problem of effective confidentialitySolve confidentiality issuesDigital data protectionPower supply for data processingConfidentialityPaper based
The invention discloses a method and apparatus for multi-mode shared printing are disclosed. The method includes: receiving a pre-print request sent by a terminal; acquiring a print mode request according to the information carried in the pre-print request; setting a print mode according to the print mode request; executing a print job: printing the preprint file carried in the pre-print request and outputting the print file; and storing the print file. The apparatus includes a request receiving unit, an information acquisition unit, a mode setting unit, a printing unit, and a storage unit. The method and apparatus canautomatically select the corresponding printing ink / printing paper based on the user's requirement for the service life of the print file to achieve the effect of automatic text erasure on the expiration date and further to ensure the confidentiality of the file content without destroying the file, is in line with the concept of environmental protection, and has practicality and high flexibility.
Owner:成都创慧科达科技有限公司
A method and system for expanding compatibility of PHS network number writing station
InactiveCN1281078CEnsure safetyImplementation supportRadio/inductive link selection arrangementsData switching networksComputer compatibilityInformation acquisition
The invention discloses a method and a system for expanding the compatibility of PHS network number burning stations, which are used to write network information and user information to mobile terminals through the PHS network number burning station through the number burning device, and the PHS network number burning stations A virtual number-burning station that can simulate the normal number-burning process of a virtual object is connected to the number-burning device, and the virtual number-burning station can intercept the data sent by the network number-burning station to the number-burning device, and The acquired information required by the mobile terminal is then passed through another marking device to burn the new type of mobile terminal. The method and the system can improve the support and compatibility of the network number burning station for a large number of emerging mobile phones.
Owner:南通国邦科技发展有限公司
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com