Electronic document security management method and system based on big data
An electronic document and security management technology, applied in the direction of electronic digital data processing, digital data authentication, digital data protection, etc., can solve problems such as difficulty in controlling employees' personal behavior, large number of users, and unguaranteed operation of terminal PCs
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0034] Below in conjunction with embodiment the present invention is described in further detail.
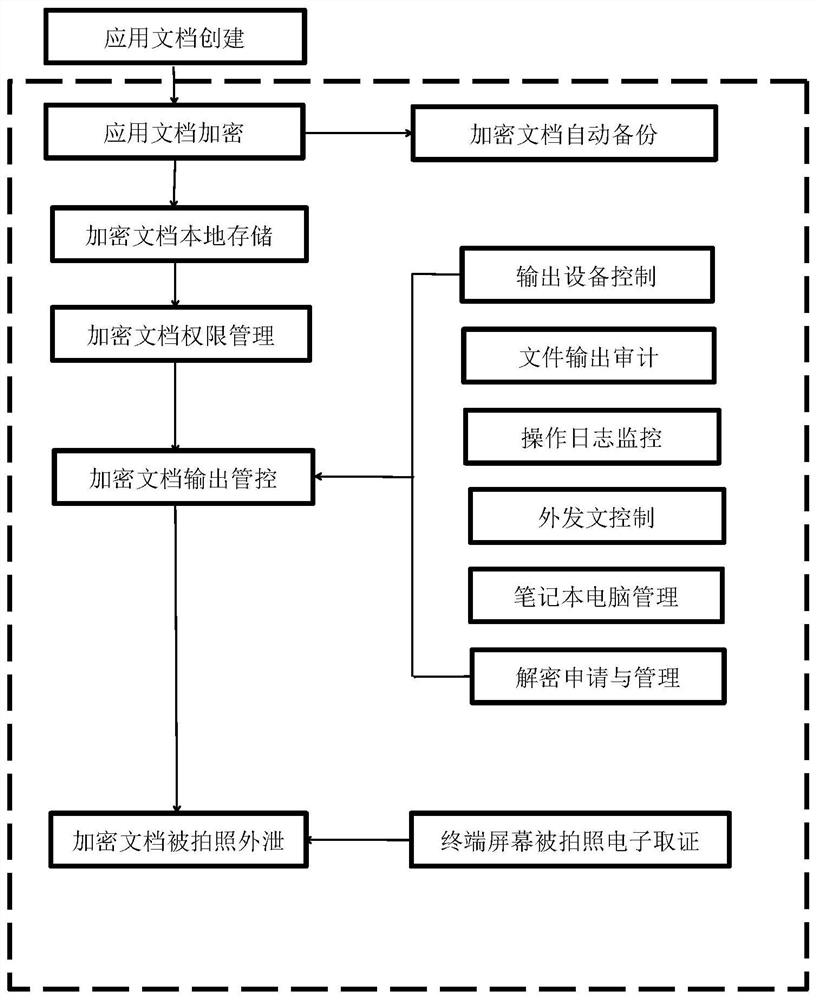
[0035] like figure 1 As shown, in order to carry out proactive defense in advance, the present invention discloses an embodiment of a method for electronic document security management based on big data, including the following steps: encrypted protection of documents, local storage of encrypted documents, and rights management of encrypted documents .
[0036] As a preferred solution, the document encryption protection is specifically: installing a client on the user's secret-related computer, using PKI technology, relying on digital certificates, transparently, compulsively, and automatically encrypting files that need to be protected; Protected files include existing or being generated electronic documents and design drawings.
[0037] The authority management of encrypted documents is as follows: based on the RSA asymmetric algorithm, different users are identified through...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com