File cloud storage security solution method and system
A solution and cloud storage technology, applied in the field of file encryption storage, to achieve the effect of improving security and solving confidentiality problems
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
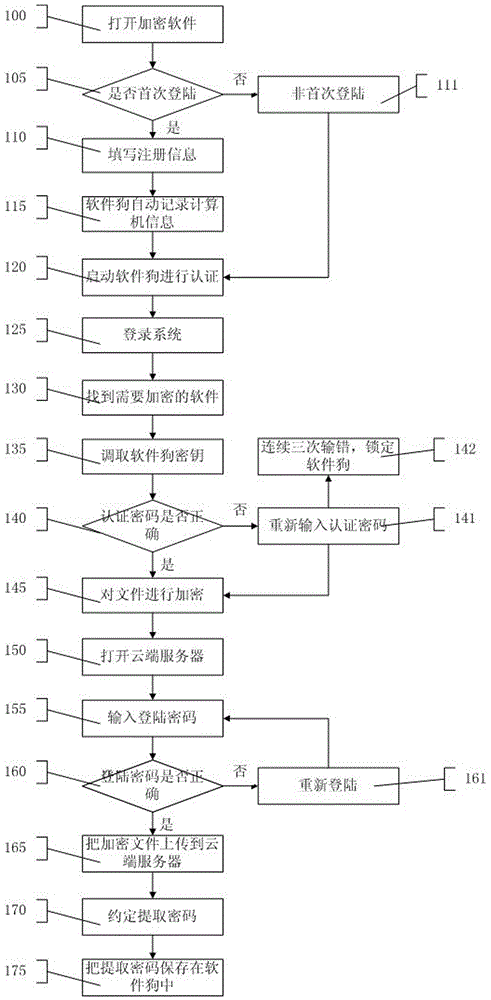
[0054] The cloud storage method of the file includes reading the file to be encrypted, then encrypting the file, and finally uploading the encrypted file to the cloud server. When you log in to the system for the first time, you need to fill in your personal registration information and verify it with the information in the dongle. After the verification is passed, you can log in to the system. Open the encrypted file, use the authentication password to retrieve the key information in the dongle, and the authentication password includes at least one of a digital password, a dynamic password, and a fingerprint password. The file is encrypted with the key information, and the key version and file content are recorded in the key encoding. Log in to the cloud server, enter the login password and authenticate, upload the file to the cloud server, agree to extract the password and save it in the dongle.
[0055] figure 1 It is a file encryption flow chart of the cloud storage secu...
Embodiment 2
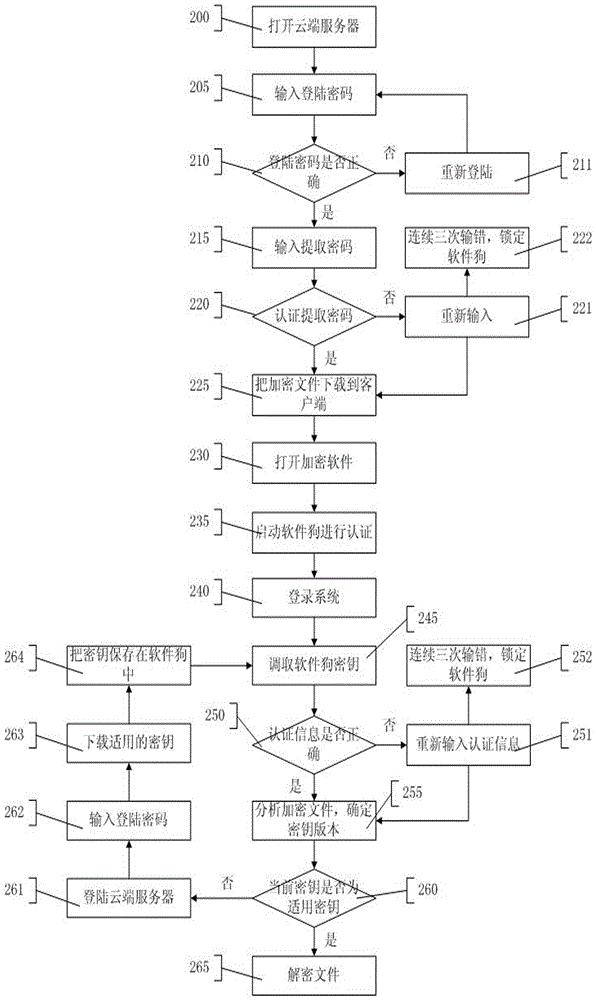
[0060] The cloud storage method of the file comprises downloading the encrypted file in the cloud server, and decompressing the file to obtain the original file. Open the cloud server, enter the login password and verify the login password, enter and verify the extraction password, and download the encrypted file. Log in to the encryption system and start the dongle for identity authentication, use the authentication password to retrieve the key information in the dongle, and the authentication password includes at least one of a digital password, a dynamic password, and a fingerprint password. Determine whether the current key information is applicable to the file, and if applicable, decrypt the file; if not, log in to the cloud server to download the used key information, and decrypt the file.
[0061] figure 2 It is a file decryption flow chart of the cloud storage security solution for files and the system of the present invention. Such as figure 2 As shown, step 200,...
Embodiment 3
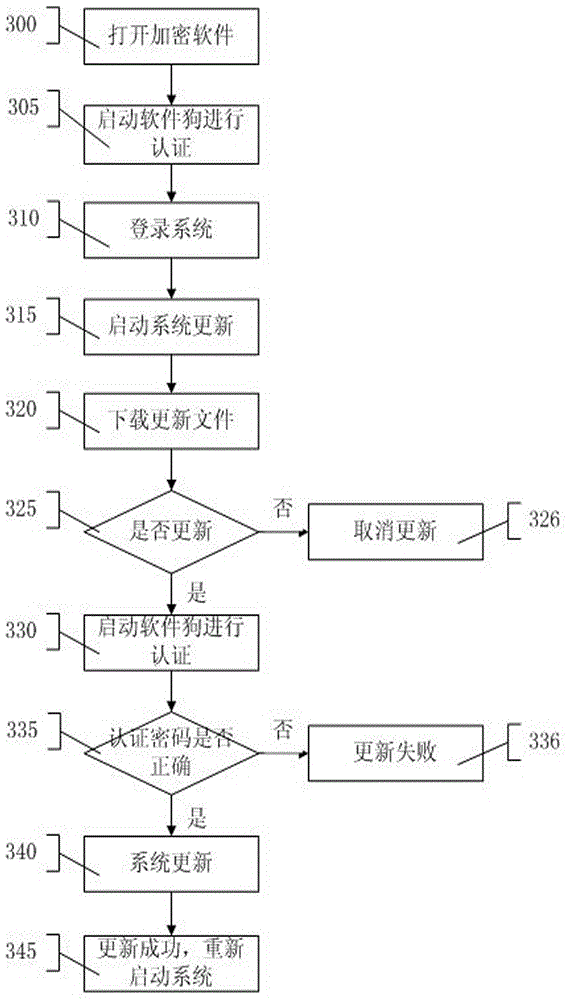
[0067] image 3 It is a flow chart of the cloud storage security solution for files and the system update of the system of the present invention. Such as image 3 As shown, step 300, step 305 and step 310 are executed in sequence, the encryption software is opened and the dongle is activated for information authentication, and the authentication information includes user information and computer information. After the information authentication is passed, log in to the encryption system. Step 315, step 320 and step 325 are executed in sequence to start the system update program, download the update file from the software company website, and determine whether to update. If not, execute step 326 to cancel the update.
[0068] If it is determined to update, then execute steps 330 and 335 to start the dongle for authentication, input the 8-digit authentication password on the dongle, the dynamic authentication password and the user fingerprint authentication password sent to t...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com