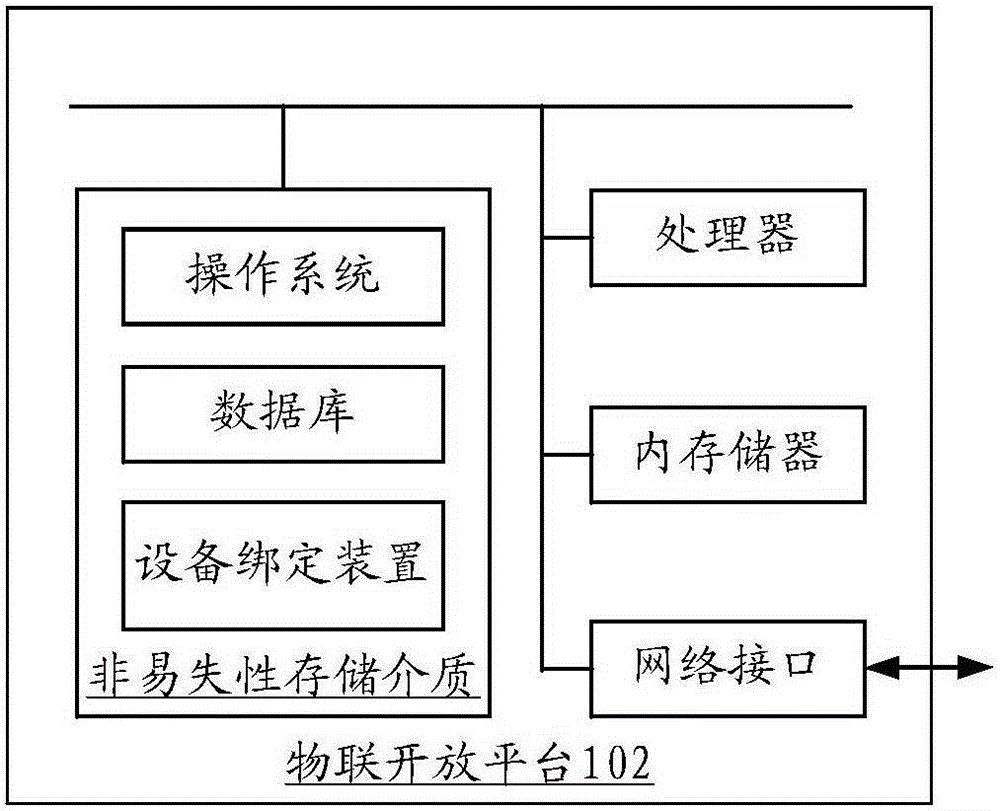
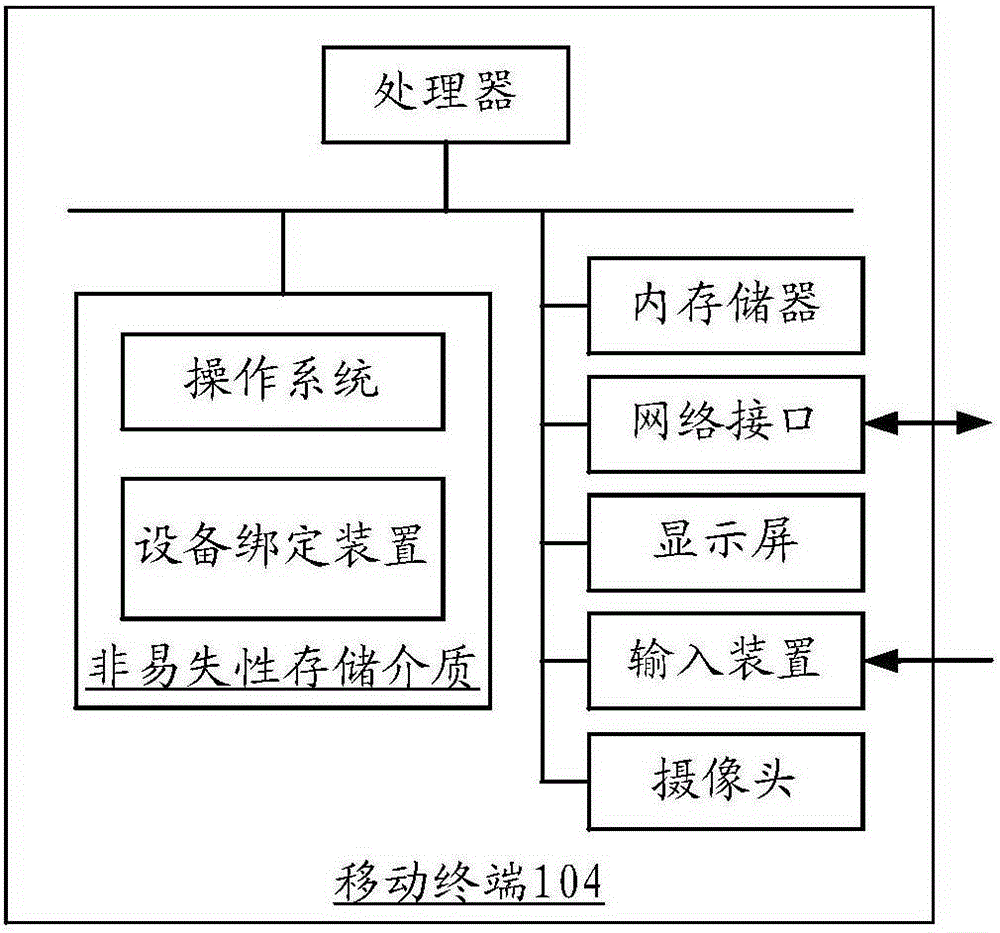
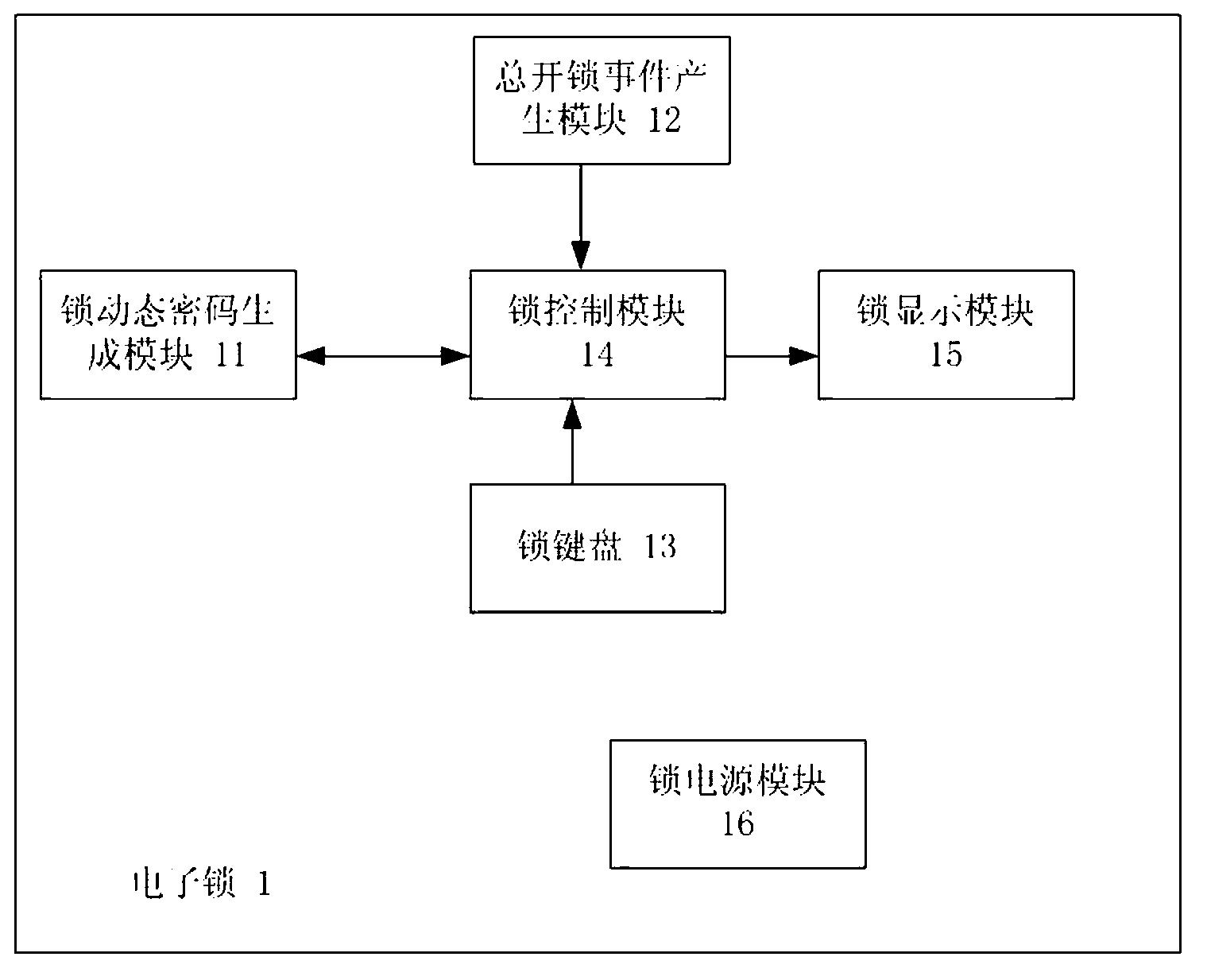
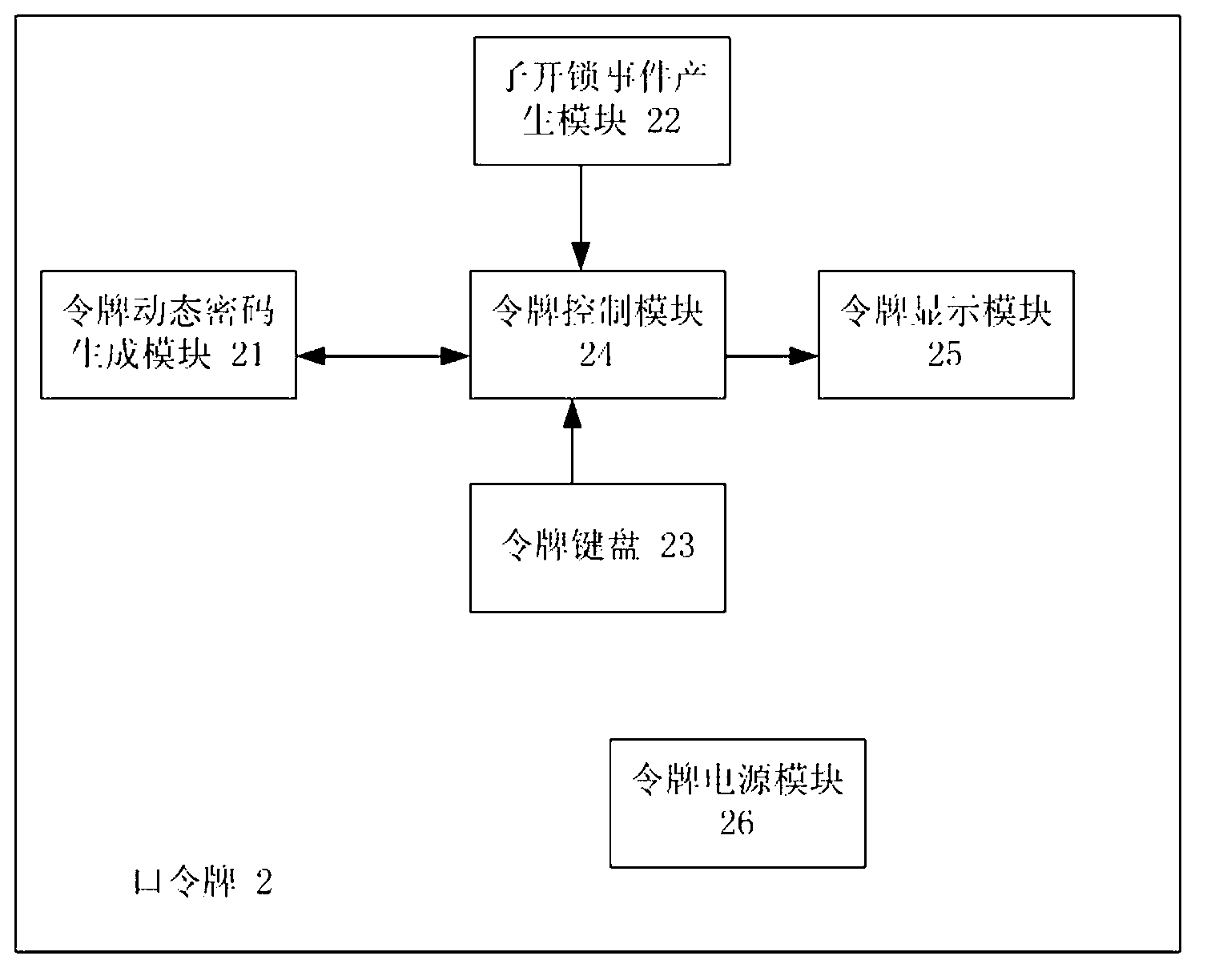
Patents
Literature
232 results about "Equipment serial number" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
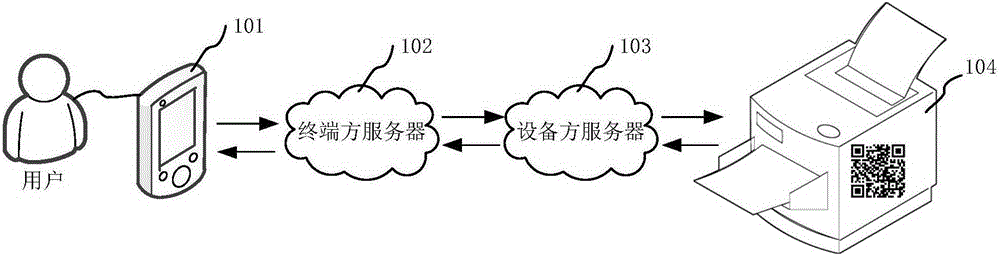
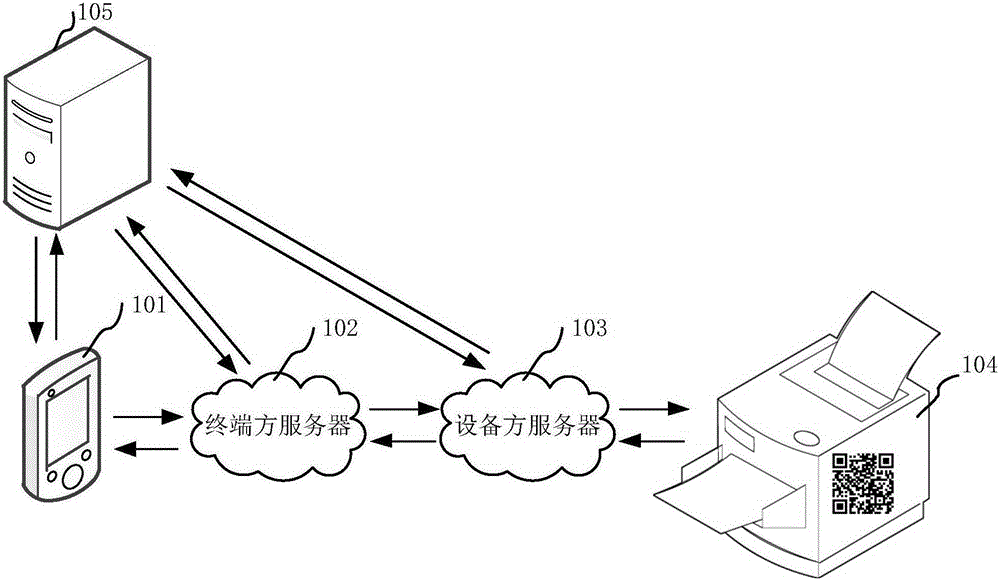
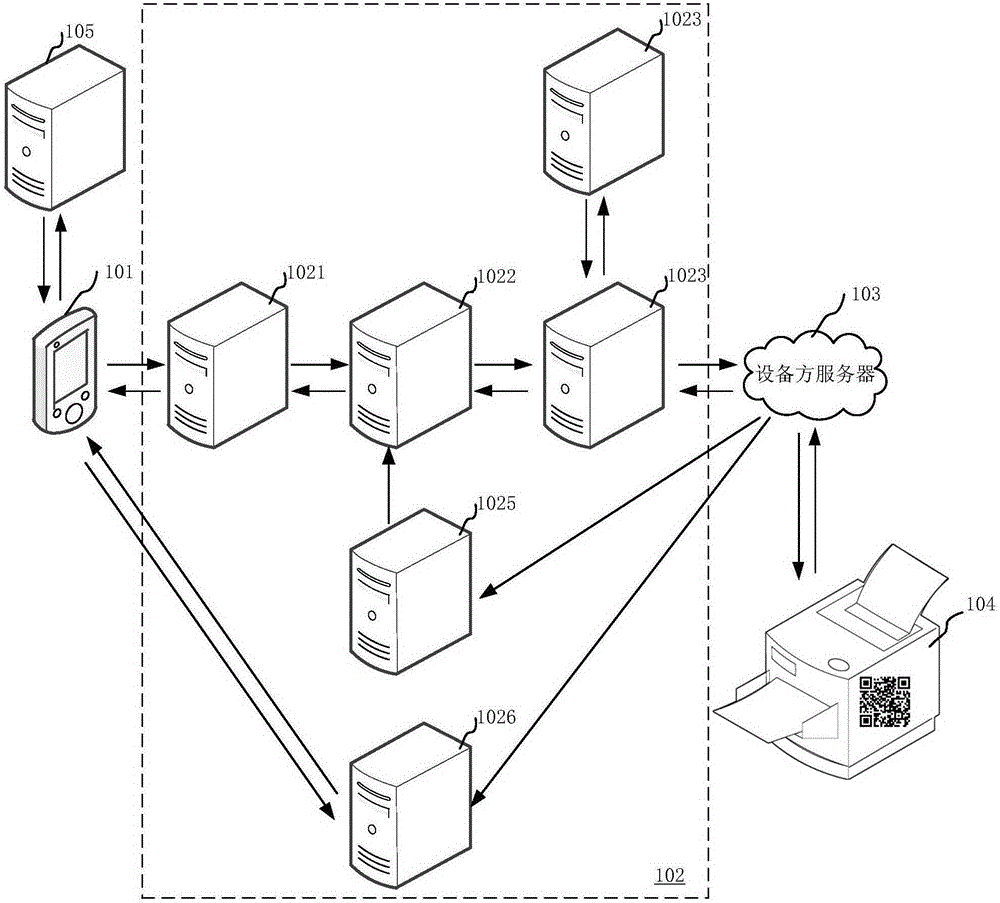
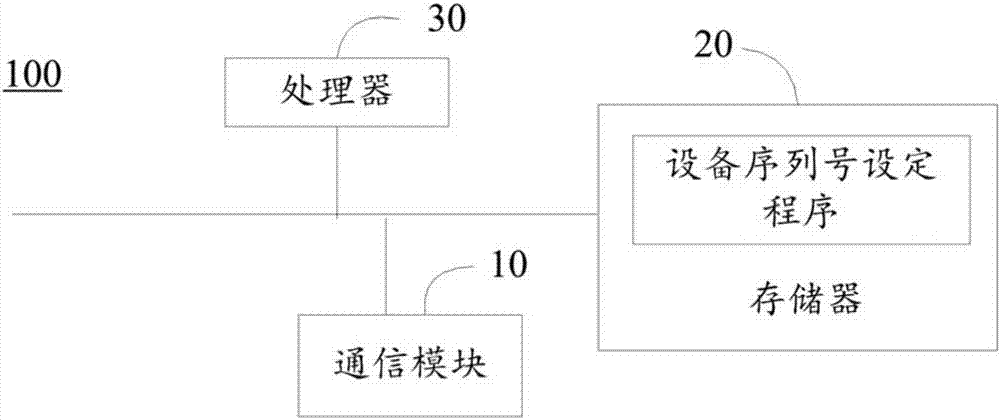
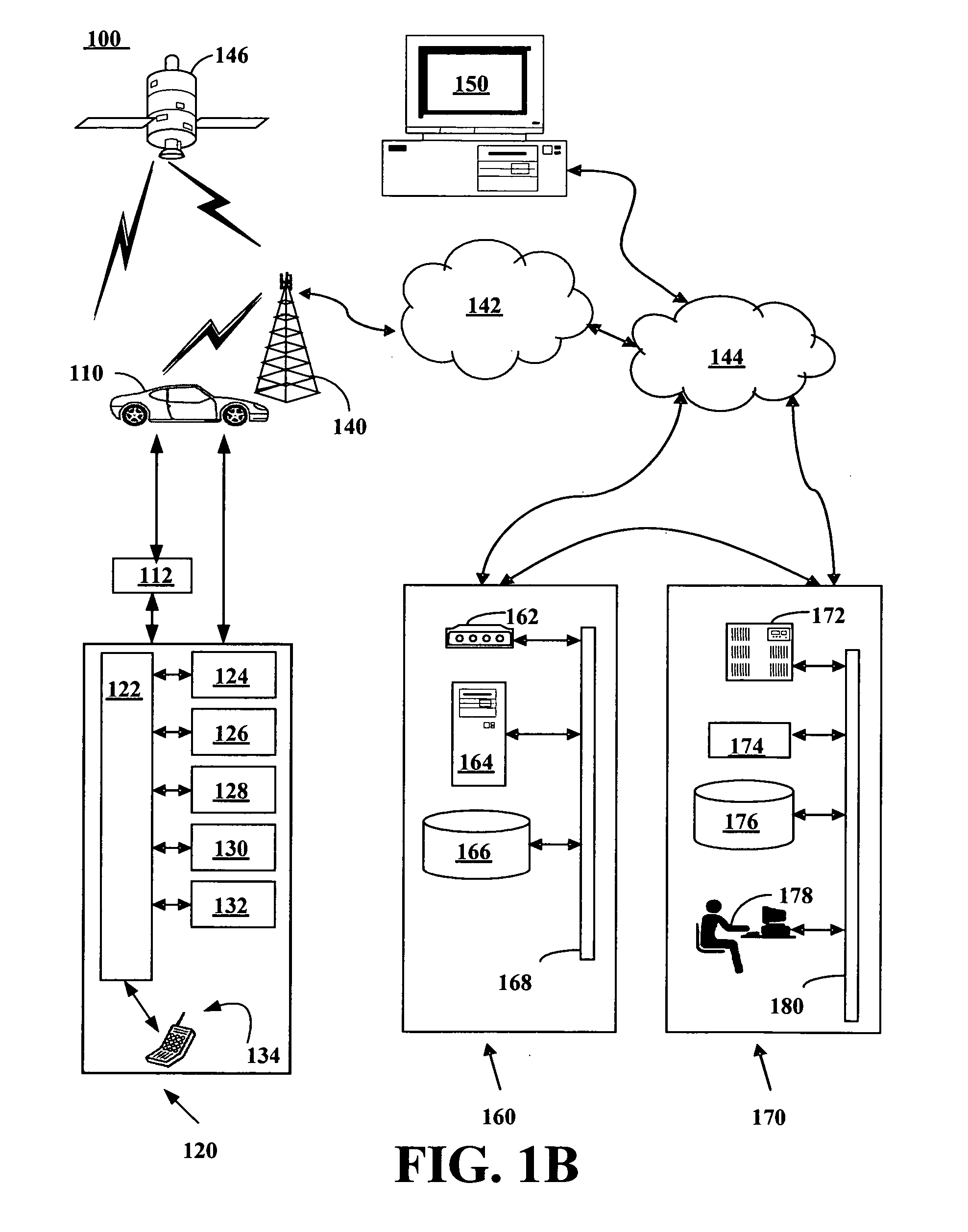
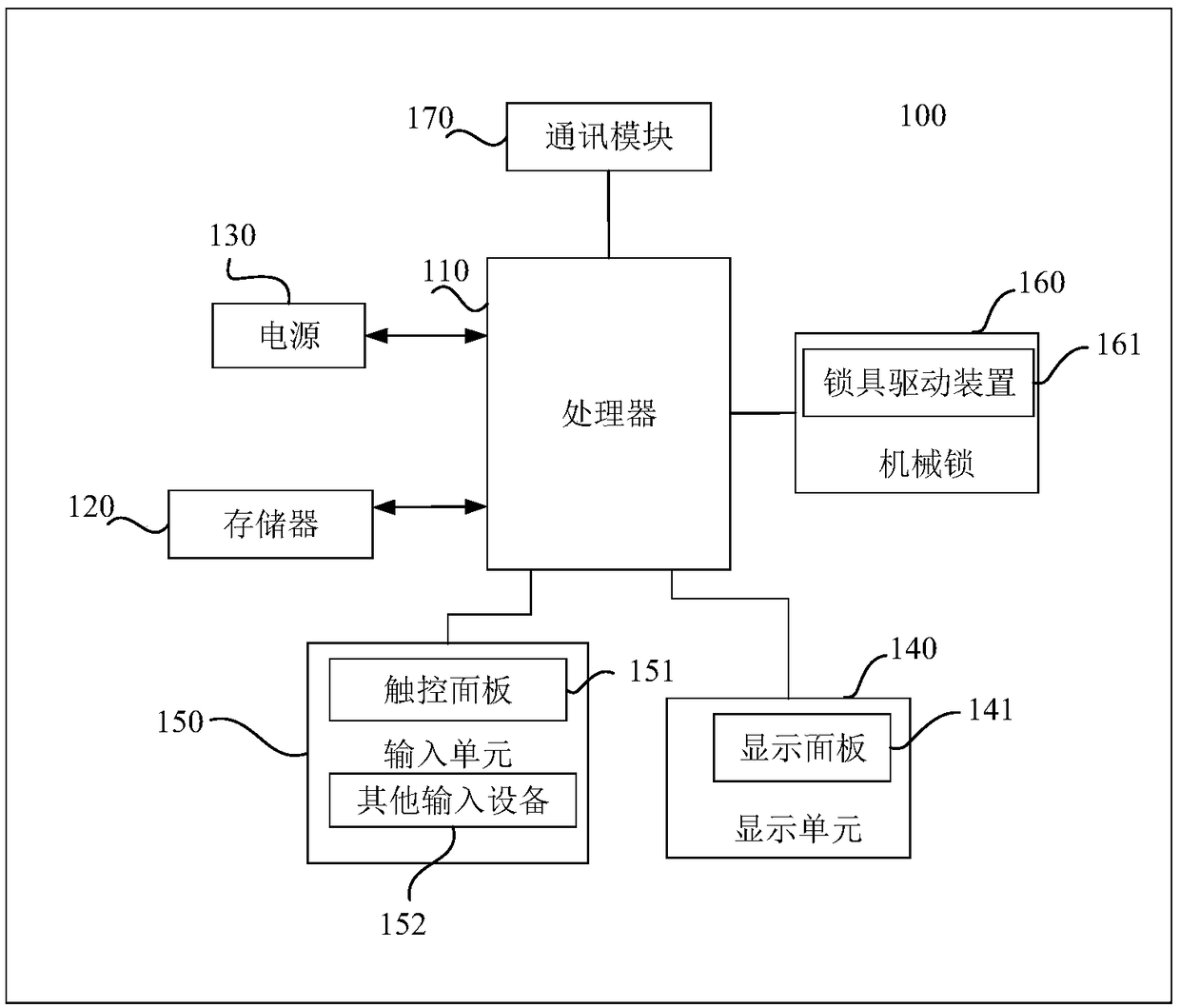
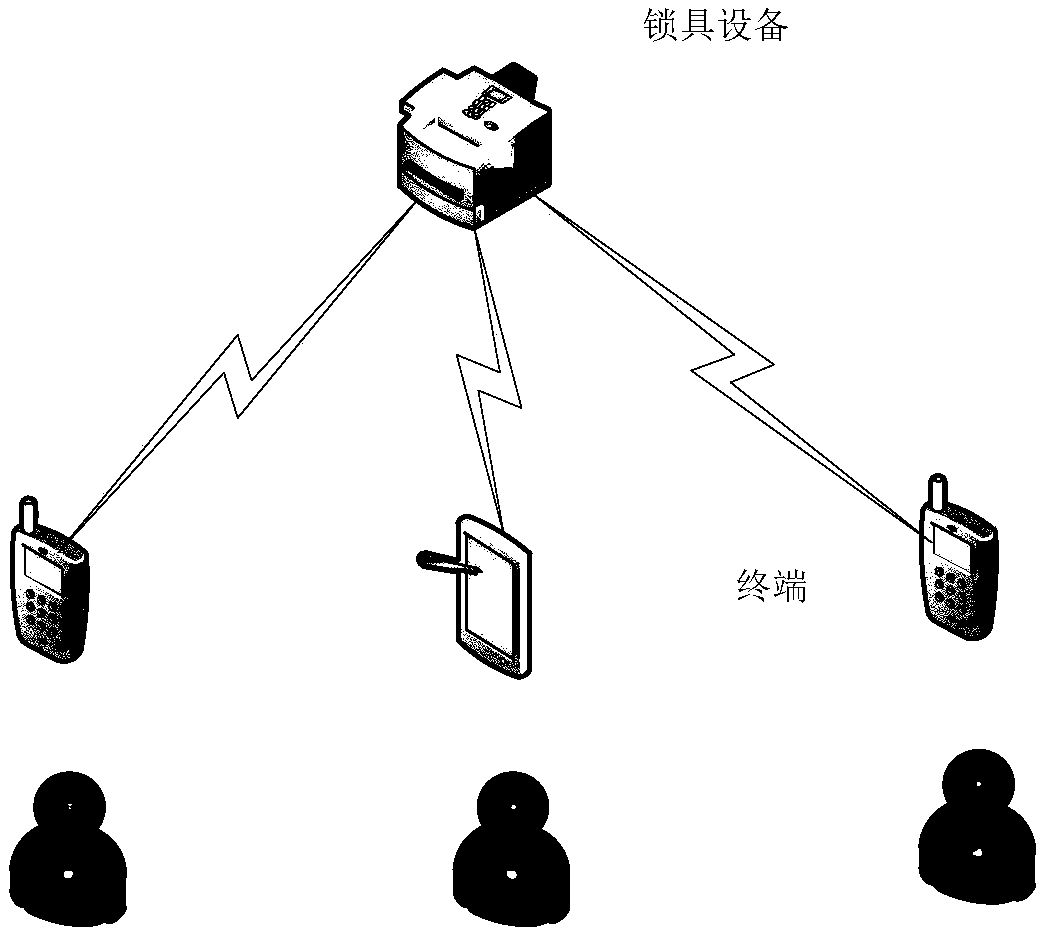
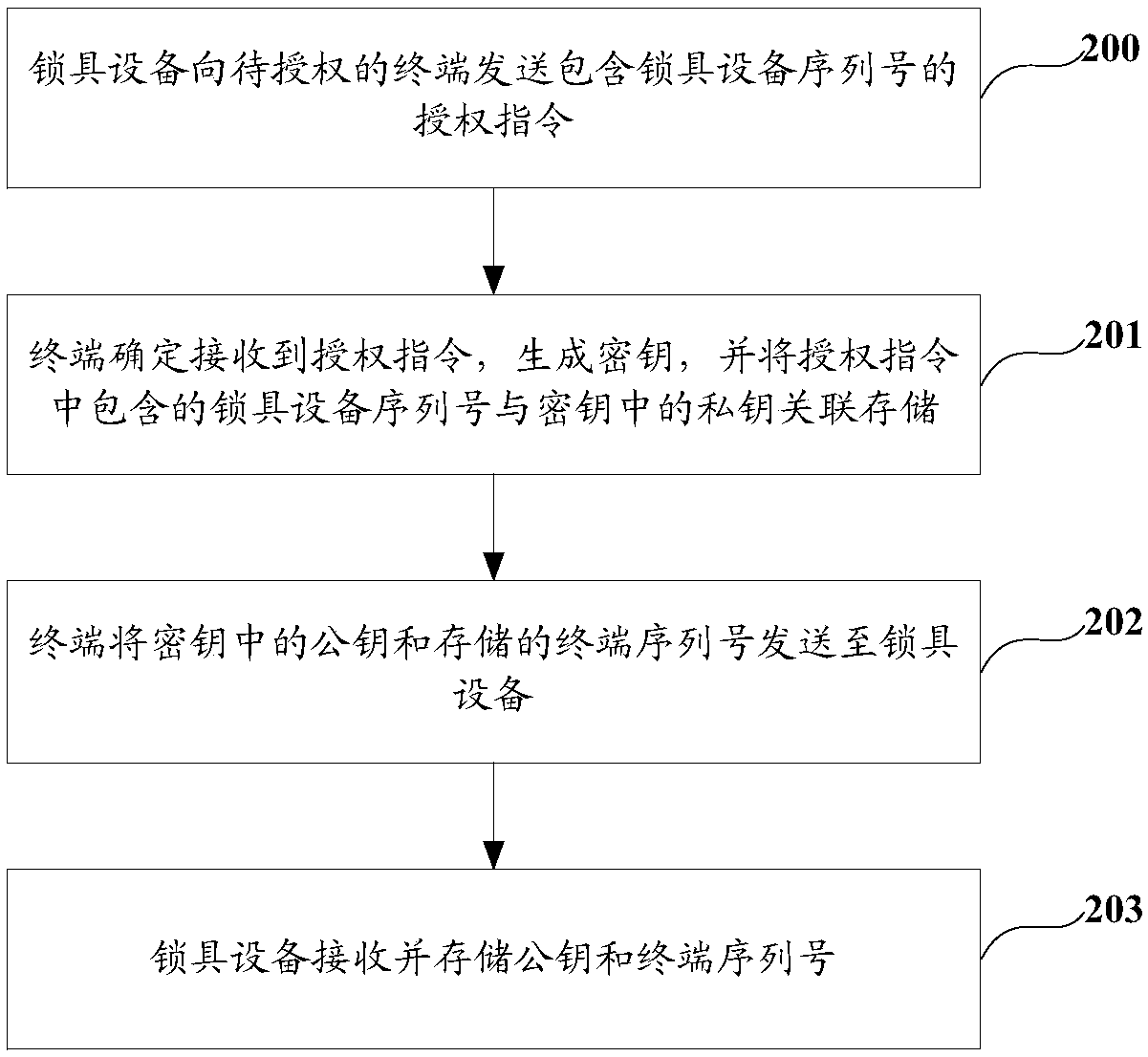
Serial numbers are used to identify specific machines and equipment by assigning a previously unused number to that particular device.
Method for fast configuring remote video monitoring system
InactiveCN103414881AEasy to deployEasy to set upClosed circuit television systemsTransmissionVideo monitoringPassword
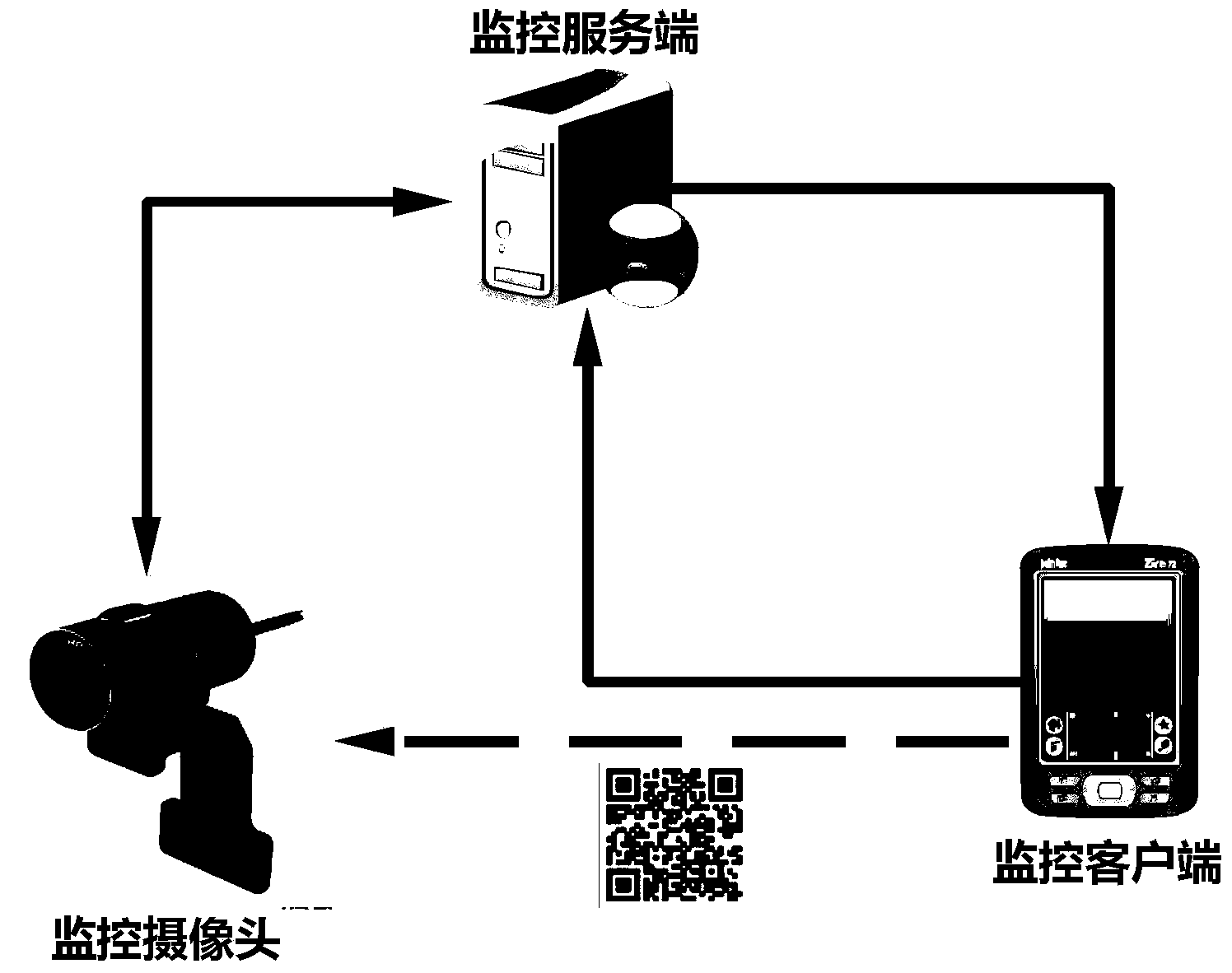
The invention discloses a method for fast configuring a remote video monitoring system. The method comprises the steps that (1) a wireless network access module is arranged on a monitoring camera; (2) currently available wireless networks are scanned by a monitoring client, a wireless network is selected and a wireless network password is input; (3) after receiving authentication information of the monitoring client, a monitoring server sends a safety verification code to the monitoring client; (4) the monitoring client converts an access point name, the password, the safety verification code and the authentication information to a two-dimension code picture, and the two-dimension code picture is placed in a shooting area of the monitoring camera; (5) the two-dimension code picture is shot through the monitoring camera and is analyzed, the monitoring camera has access to the wireless network, and an equipment serial number, the safety verification code and the authentication information of the monitoring camera are then sent to the monitoring server; (6) authentication is conducted on the monitoring client by the monitoring server according to information sent by the monitoring camera, and when the certification is passed, the monitoring camera and the monitoring client are bound to enter a monitoring module.
Owner:INST OF SOFTWARE - CHINESE ACAD OF SCI +1
Block chain architecture-based ecological environment monitoring system and implementation method thereof
ActiveCN106407481AEnsure integrityEnsure authenticityData processing applicationsGeneral water supply conservationEcological environmentTimestamp
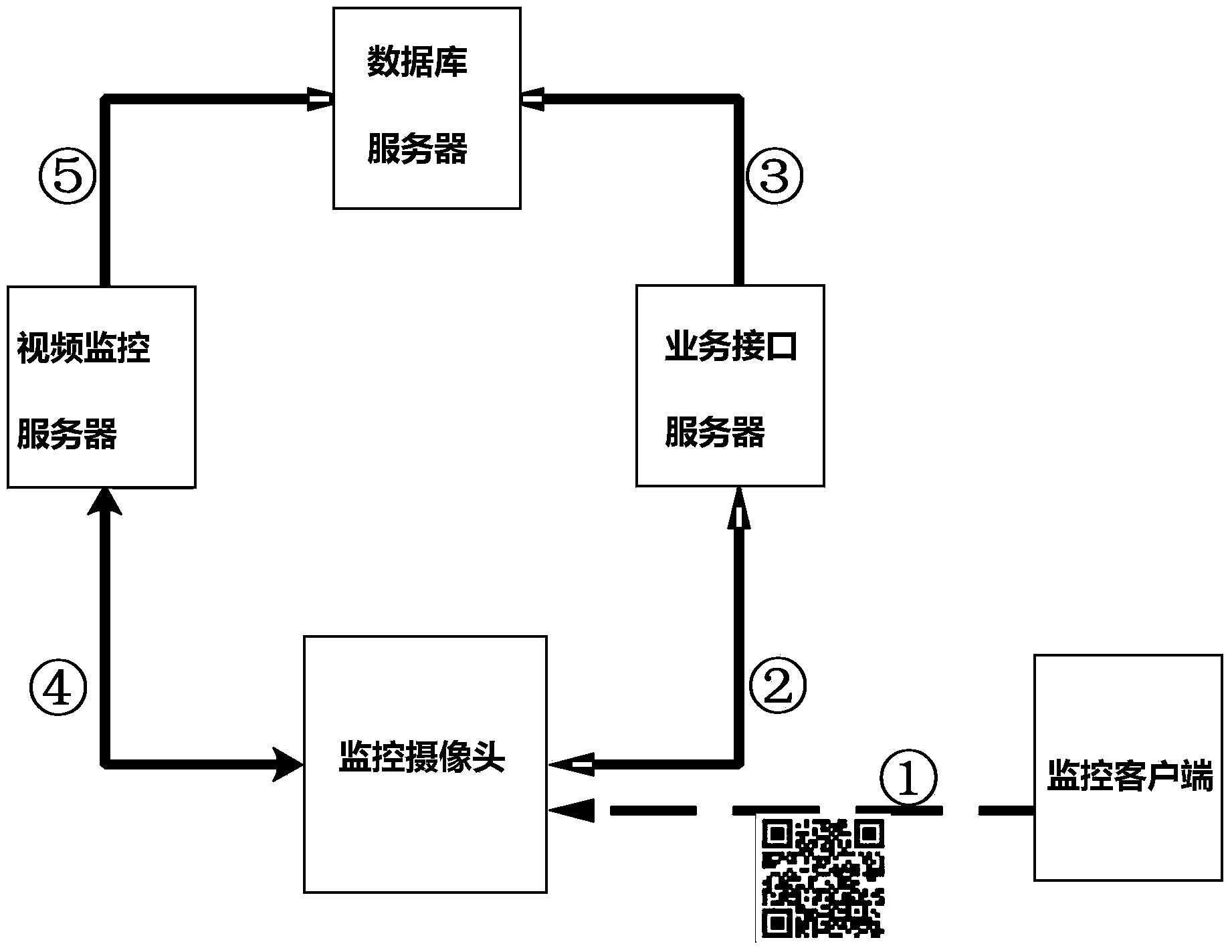
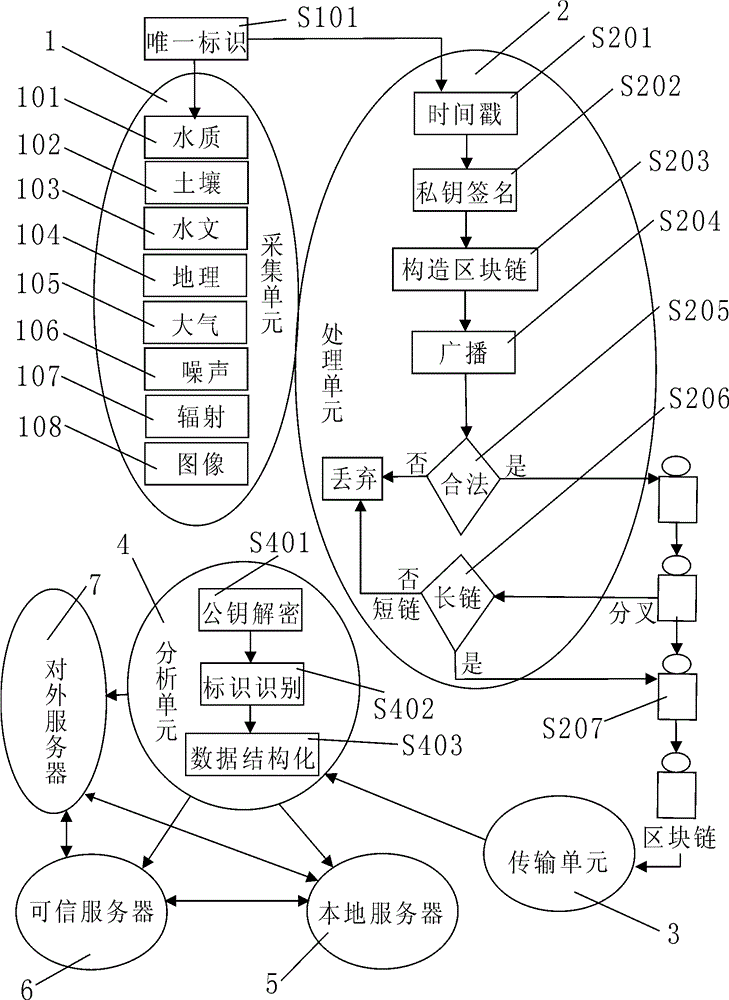
The invention relates to a block chain architecture-based ecological environment monitoring system, which comprises collection units, a processing unit, a transmission unit, an analysis unit, a local server, a trusted server and an external server, wherein each collection device has an inalterable device series number and is combined with geographic information to reform a unique identifier of a whole network; and meanwhile, a timestamp and a private key DSA signature are added to real-time monitoring data of each collection unit, and a new block which cannot be tampered and cannot be anonymous is constructed and added to a block chain. All participants in the network have copies of the block chain, the credibility of the data can be confirmed without check of any centralized mechanism, and meanwhile, ecological environment monitoring information and data are opened to the society, so that illegal acts of excess emission, data tampering or data falsification and the like can be effectively blocked; the integrity and the authenticity of the data are ensured; and the ecological environment monitoring uniformity and effectiveness are strengthened.
Owner:福州微启迪物联科技有限公司
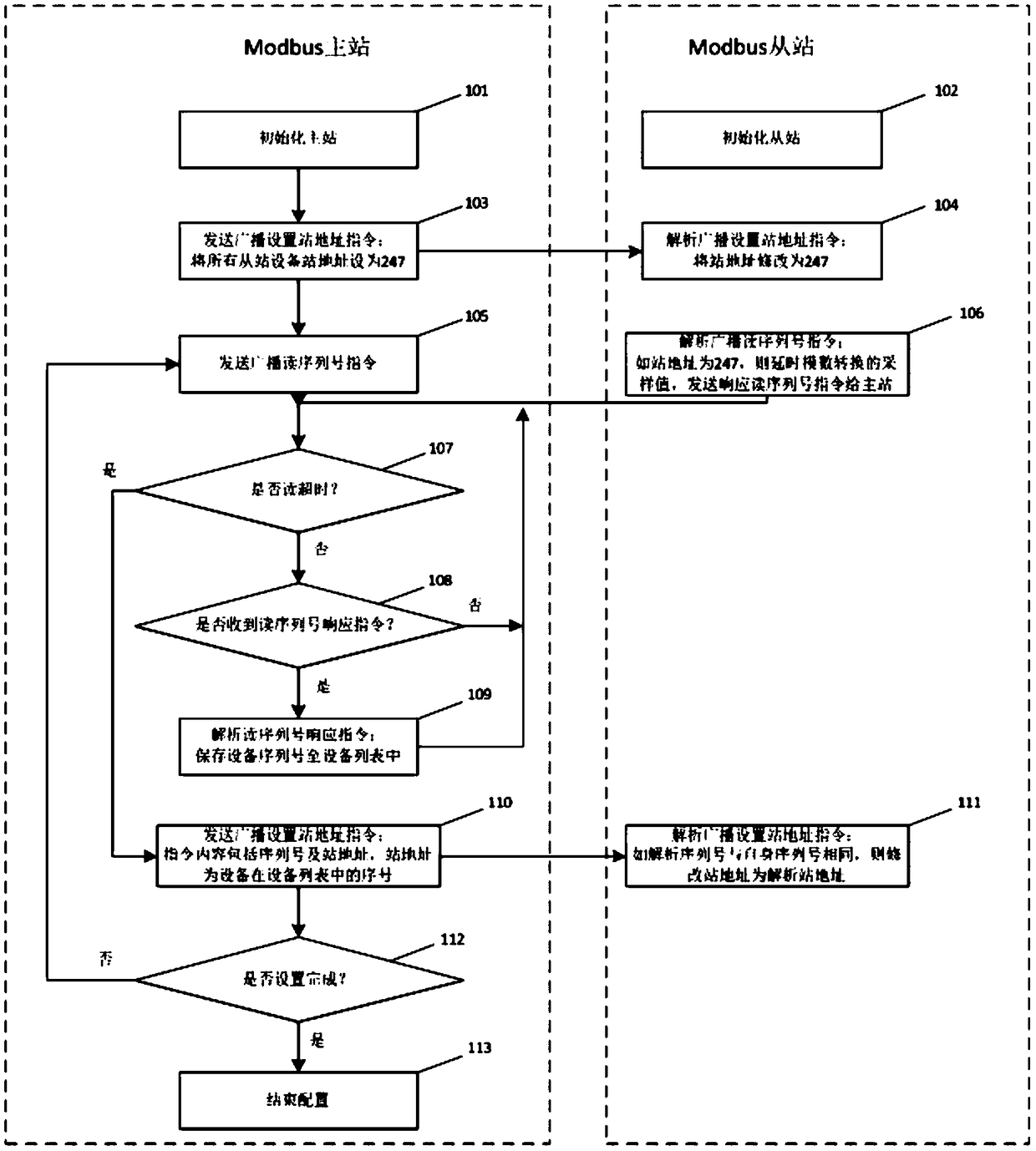
Address automatic allocation method, Modbus master station and Modbus slave station and system
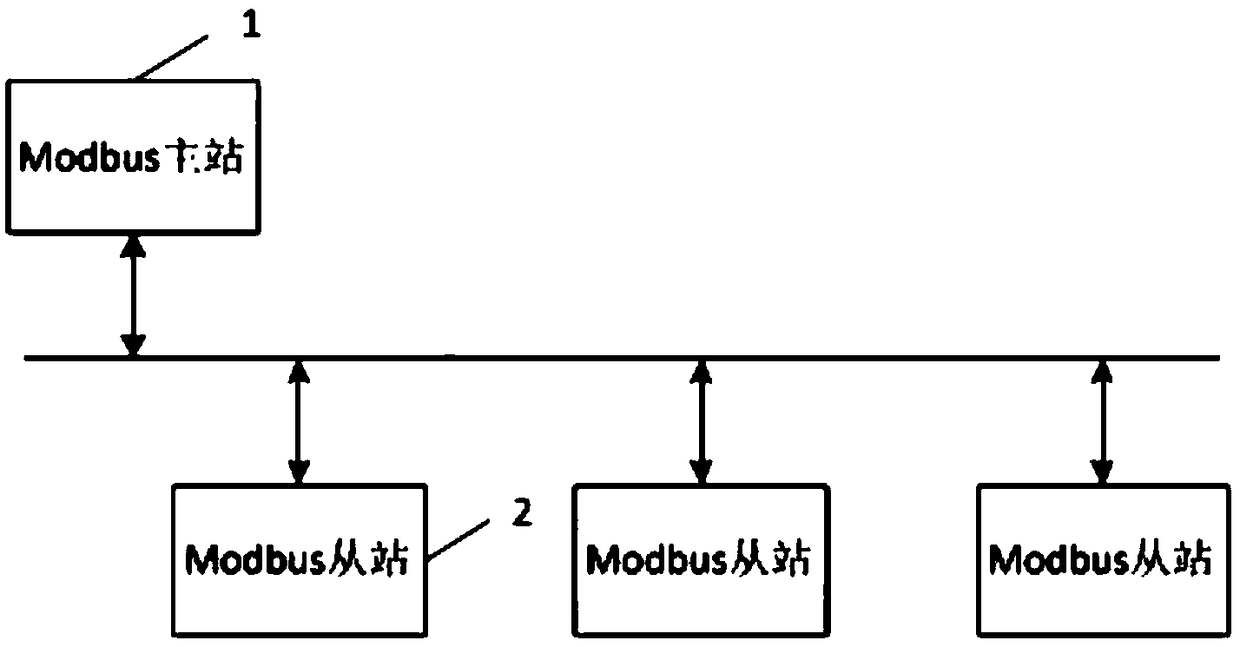
The invention discloses an address automatic allocation method. A Modbus master station sends broadcast address setting commands and sets station addresses of all Modbus slave station devices as the same fixed address; broadcast Modbus slave station device serial number read commands are sent; the Modbus slave station devices return messages responding to the Modbus slave station device serial number read commands; the Modbus master station broadcasts and issues slave station address setting commands carrying the slave station device serial numbers and the slave station addresses in sequence,according to a list of the received Modbus slave station device serial numbers; and the Modbus slave station devices analyze the slave station device serial numbers and the slave station addresses, and if the slave station device serial numbers are equal to own serial numbers, own slave station addresses are modified, thereby realizing address automatic allocation. The invention also provides an address allocation Modbus master station and Modbus slave station applicable to a Modbus protocol, and a system.
Owner:ZHEJIANG CHINT ELECTRIC CO LTD
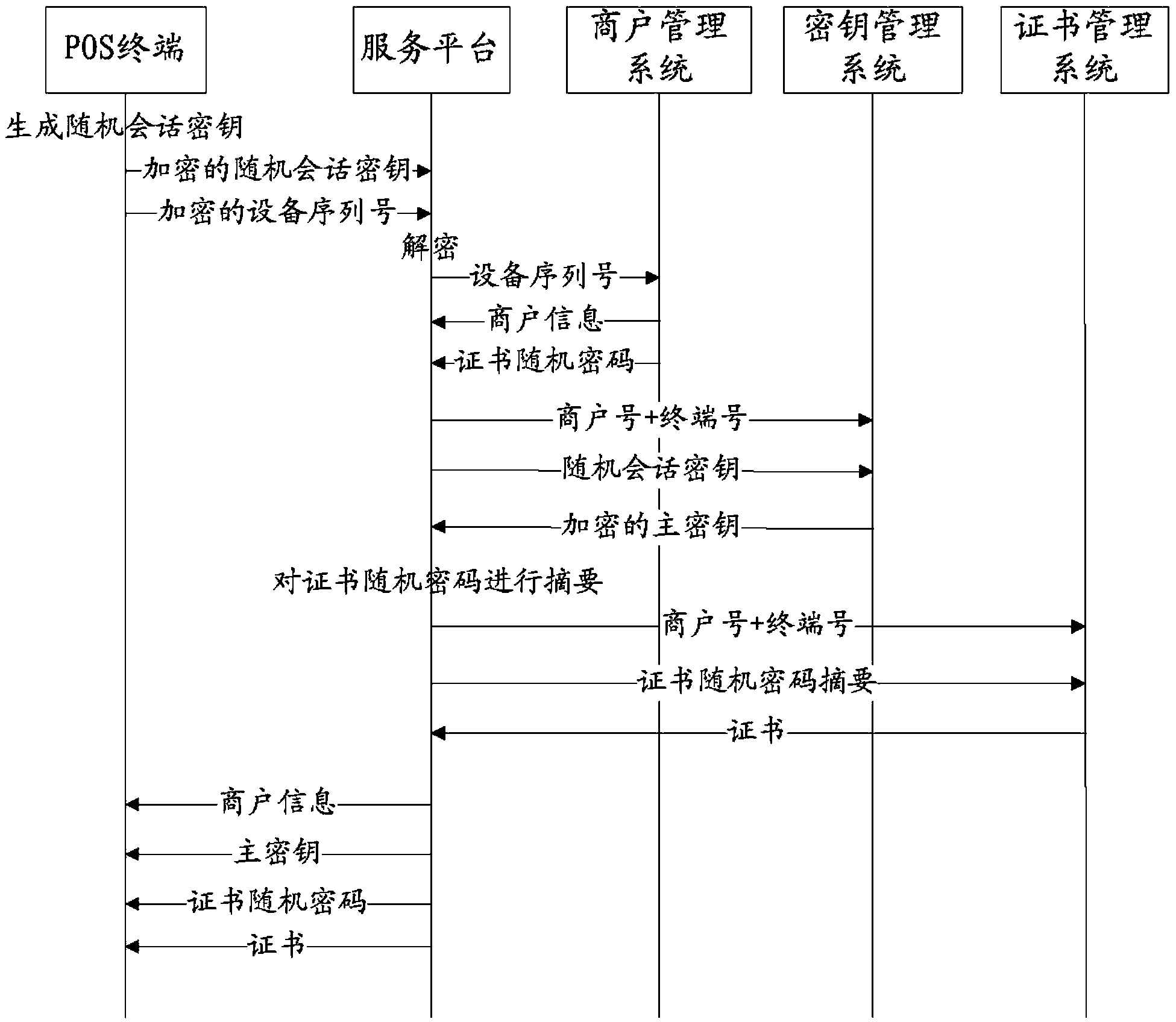
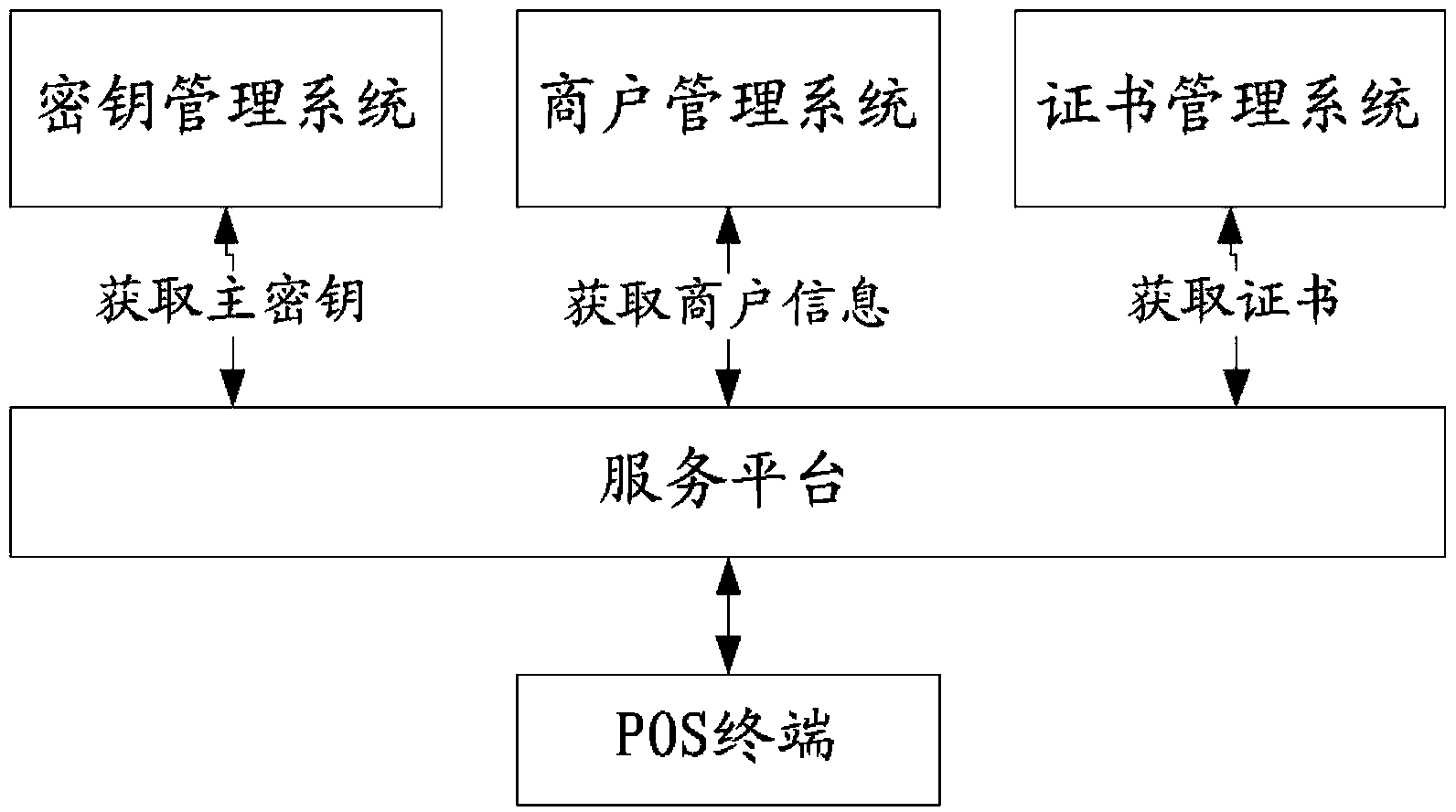
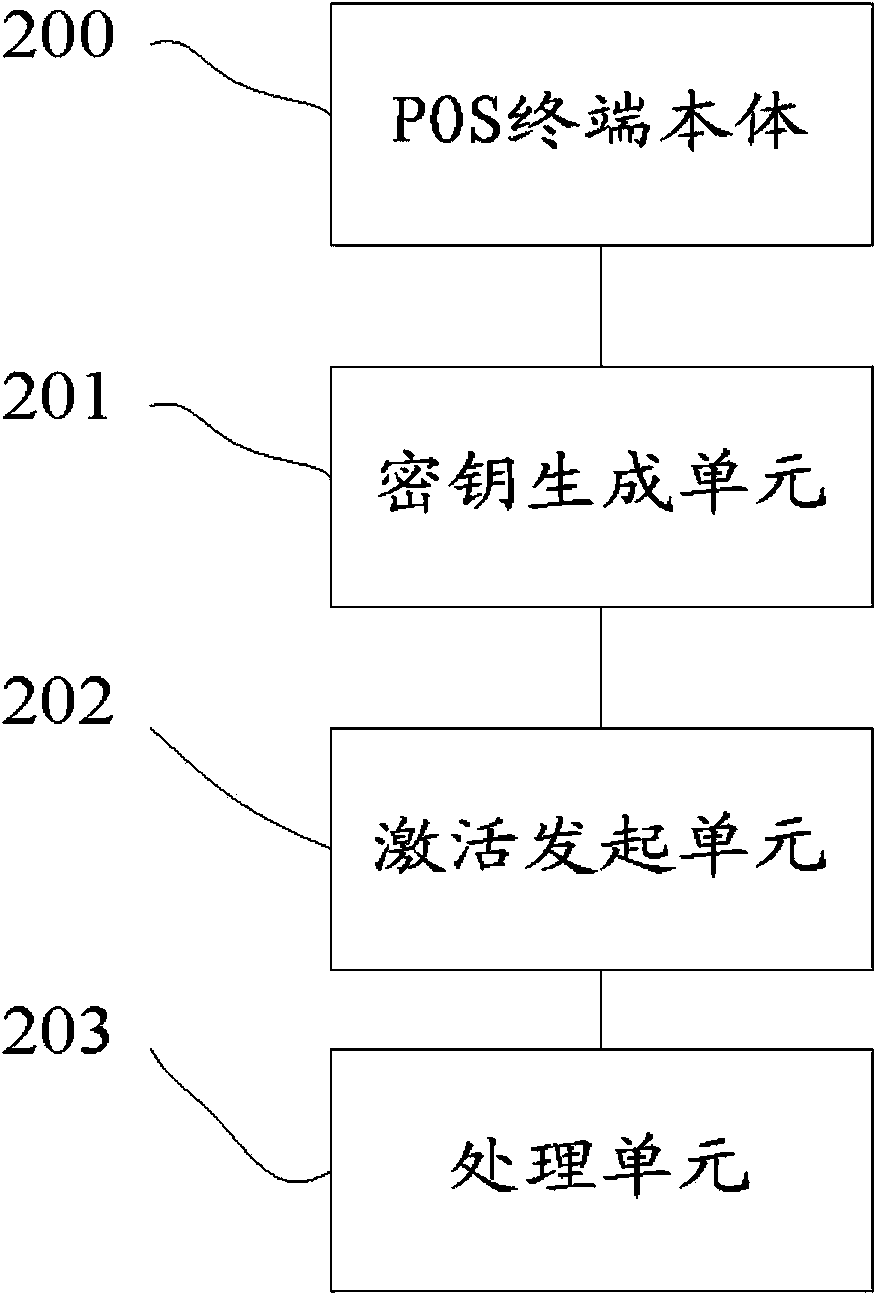
POS terminal and method, system and service platform for activating same
ActiveCN103595718AShorten the timeLow costKey distribution for secure communicationCash registersComputer terminalMaster key
The invention provides a POS terminal and a method, system and service platform for activating the POS terminal. The method includes the steps that the POS terminal sends a device serial number to the service platform, and after receiving the device serial number of the POS terminal, the service platform obtains commercial tenant information from a commercial tenant managing system according to the device serial number; after the commercial tenant information is obtained successfully, a master key of the POS terminal is obtained from a key managing system, and a terminal private key certificate is obtained from a certificate managing system; the obtained information is returned to the POS terminal; the information is used for completing activating operation for the POS terminal. By the adoption of the technical scheme, time and cost of installation personnel can be greatly reduced, the installation personnel even do not need to visit a commercial tenant and directly issue a device to the commercial tenant after the commercial tenant passes audits, the commercial tenant can complete terminal configuration operation by himself after getting the device, and the method is simple, rapid and suitable for large-scale device installation in batch.
Owner:LAKALA PAYMENT CO LTD
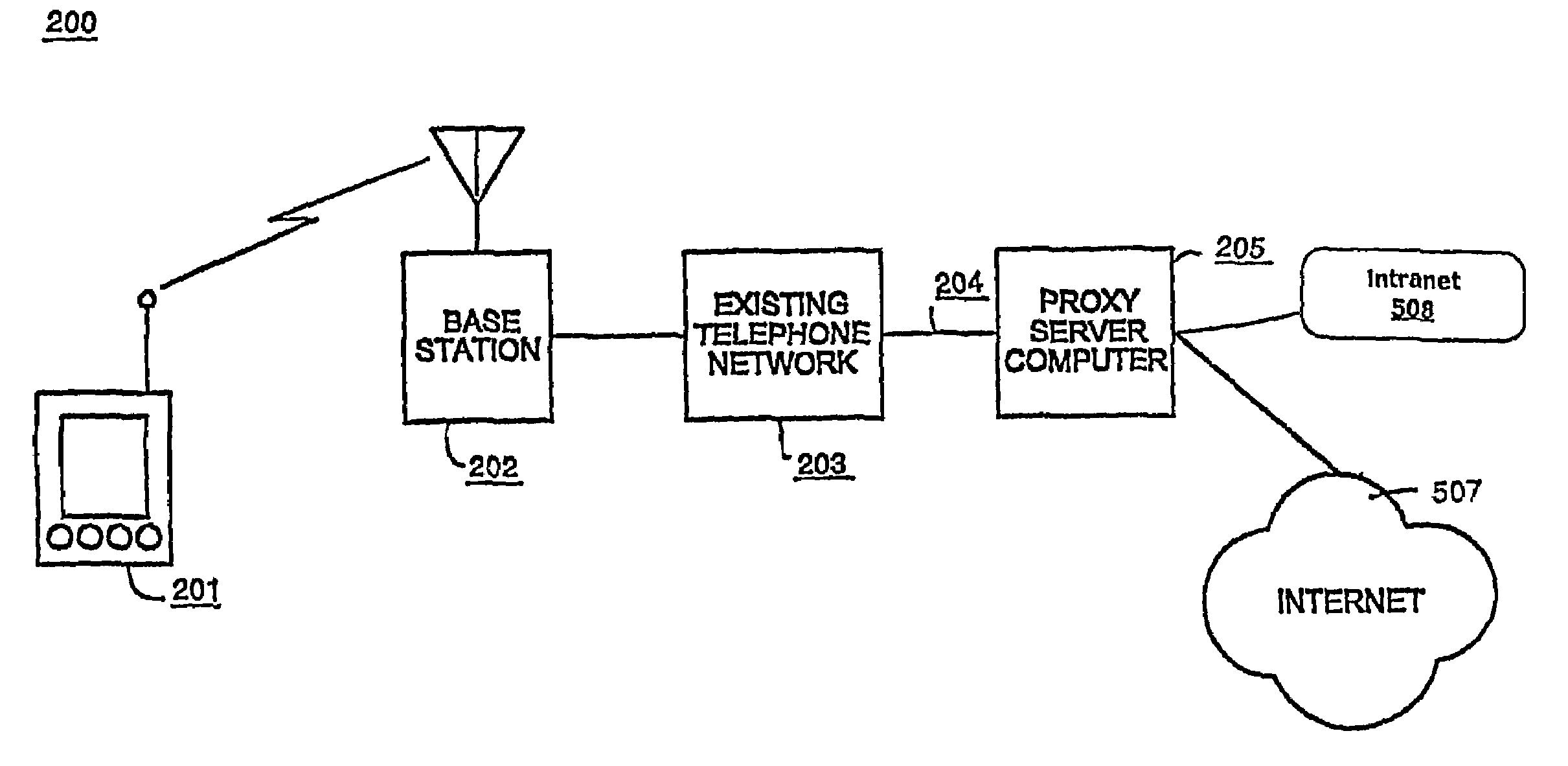
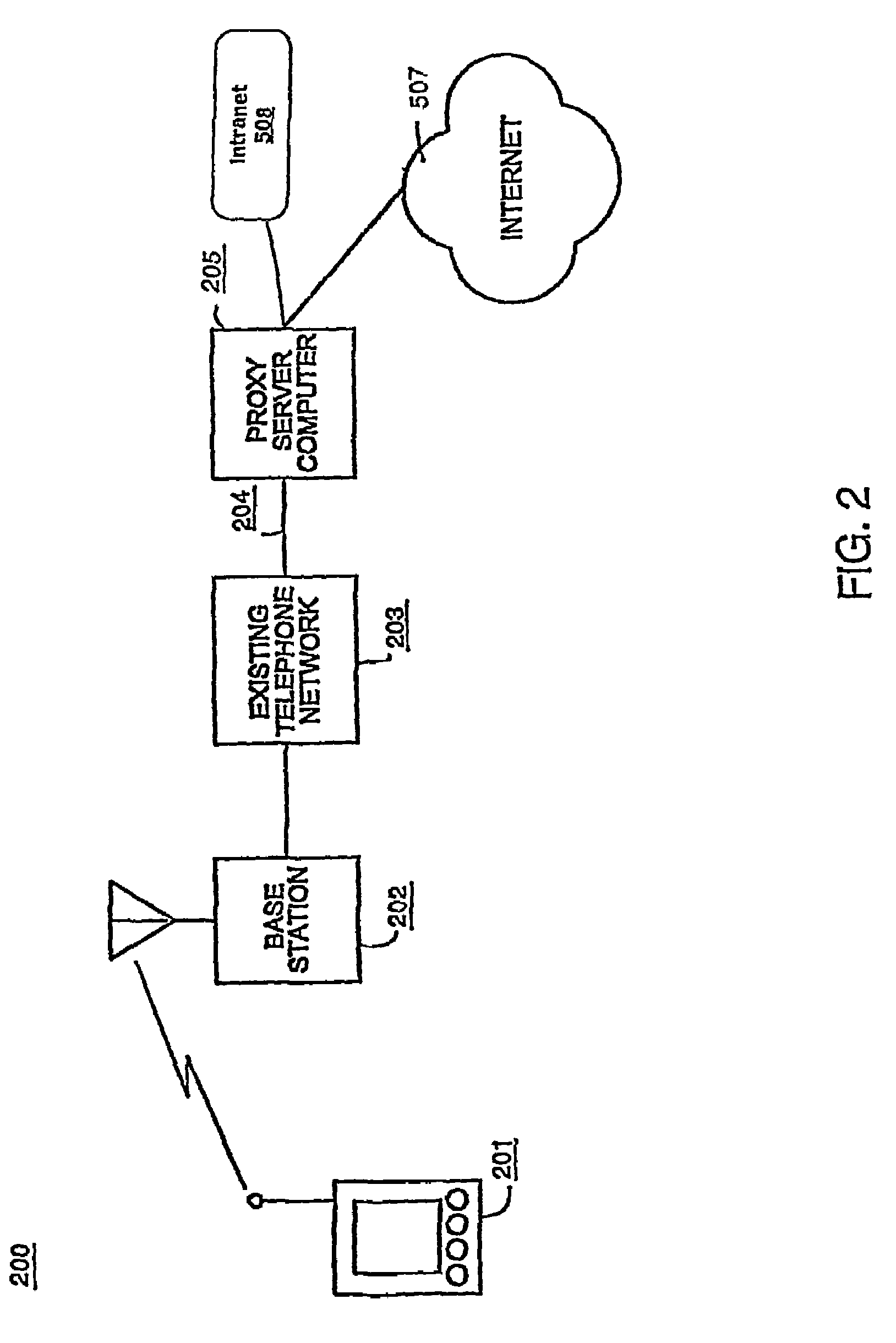
Secure authentication proxy architecture for a web-based wireless Intranet application
InactiveUS7184999B1Flexible and inexpensiveData processing applicationsDigital data processing detailsNetwork connectionApplication software
A method and server system for exchanging data between a wireless electronic device and another computer system. This system allows a wireless electronic device to securely communicate with an Intranet by verifying authentication parameters. The first authentication parameter is the device serial number and a password which authenticates the network connection. The second authentication parameter is a user name and password that authenticates the user's access to applications on the Intranet. The system uniquely integrates the authentication parameters into every query the wireless device makes to the Intranet to maintain the session between the wireless device and the Intranet. Beneficially, the authentication parameters are not stored on any particular network device and do not burden either the server or the wireless device with maintaining the session. In another embodiment of the present invention, the server system uses a link rewriter service for examining web pages generated by applications of the Intranet to identify links that target any application that is resident on the Intranet. The link rewriter uses a look up table in a database to rewrite the link to include a keyword that designates the targeted application and its Intranet server. The keyword is then used to route links to the Intranet and if a link is not resident on the Intranet, the query will be routed to the Internet.
Owner:QUALCOMM INC
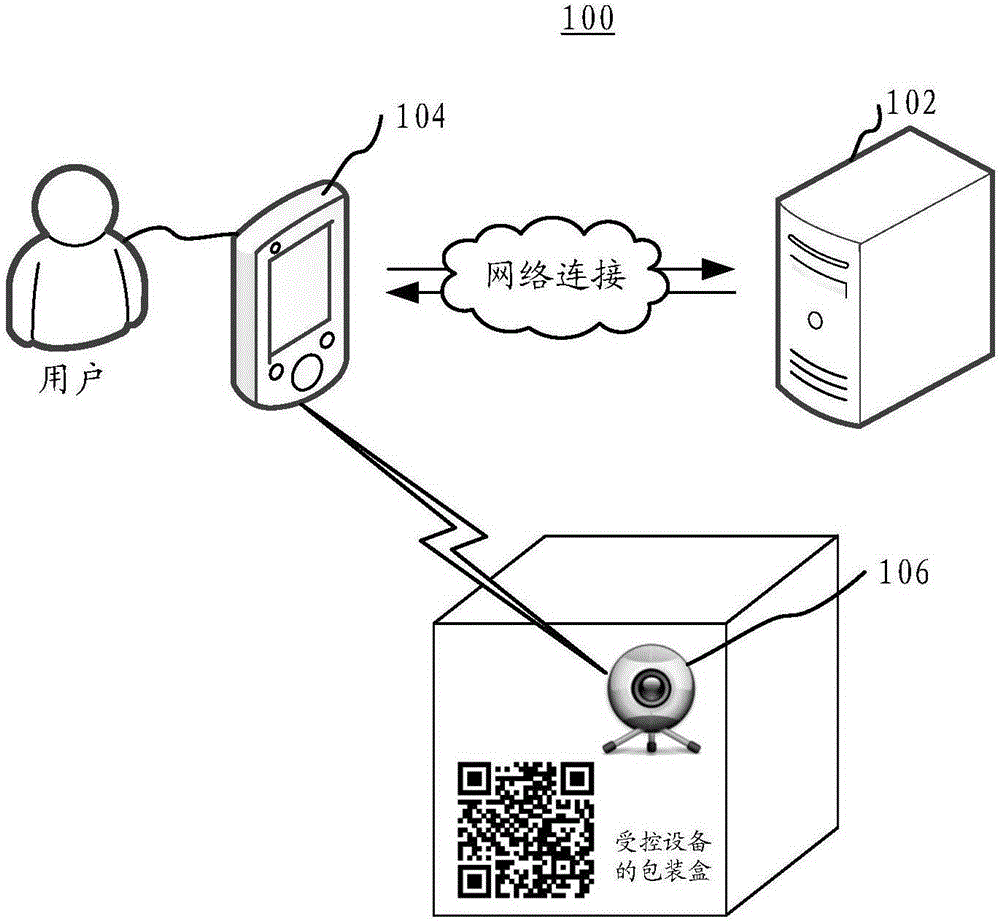
Device binding method and apparatus
ActiveCN106413124AThe binding relationship is validSimple and fast operationConnection managementDevice typeGraphics
The invention relates to a device binding method and apparatus. The method comprises the following steps of: scanning a graphics code corresponding to a controlled device and obtaining a device type identifier and a device serial number; querying a corresponding device connection mode according to the device type identifier; searching the controlled device corresponding to the device serial number according to the queried device connection mode in order to establish a connection; after the connection is established, uploading a user identifier and the device serial number to a thing-united open platform in order than the thing-united open platform establishes a binding relationship between the user identifiers and the device serial numbers. The device binding method and apparatus can automatically trigger a series of operation for binding devices only by scanning the graphic code, and the operation is simple and the operation convenience is improved.
Owner:TENCENT TECH (SHENZHEN) CO LTD
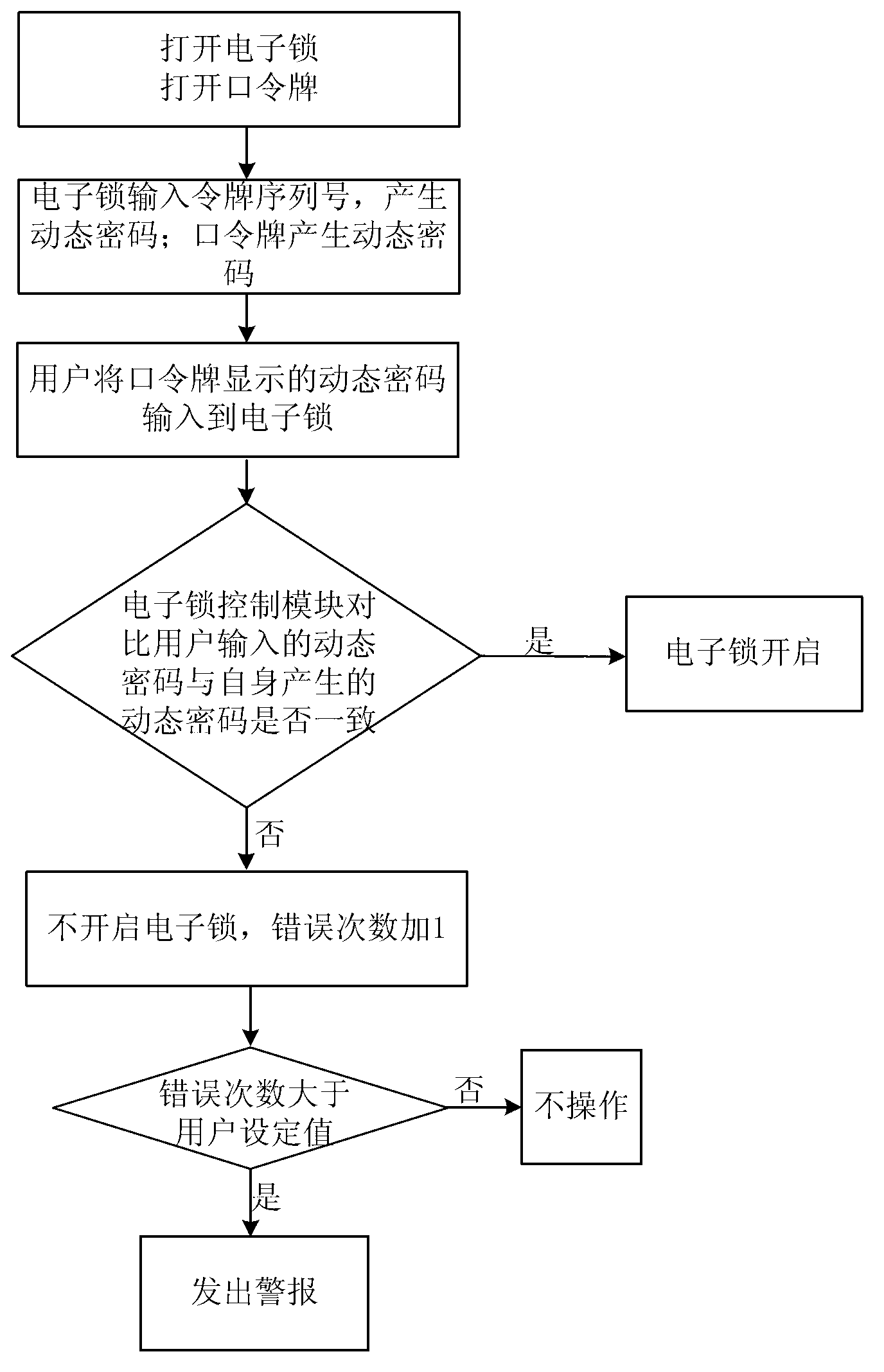
Dynamic electronic coded lock system and authentication method thereof
ActiveCN103218865AExtended service lifeImprove securityIndividual entry/exit registersPasswordUser input
The invention relates to a dynamic electronic coded lock system and an authentication method thereof. The system is composed of an electronic lock (1) and a plurality of password tokens (2) with different equipment sequence numbers. The authentication method comprises the following steps that: the electronic lock respectively accumulates and stores the application times of the password tokens according to the equipment sequence numbers; each password token accumulates and stores own application time; a dynamic password is calculated according to certain rules at the password token end on the basis of the equipment sequence numbers and the accumulated application times, and then is displayed; a dynamic password set is calculated according to the same rules of the password token end at the electronic lock end on the basis of the equipment sequence number corresponding to the password token in use and the allowable error range of the accumulated application times corresponding to the equipment sequence number, and a password input by a user is received; and an unlocking command is executed if the password input by the user is in the selectable dynamic password set, otherwise, the unlocking operation is ineffective. The system and method need no time benchmark, the service life and the security of the system can be prolonged and improved, and a hardware design is simplified.
Owner:孙添平
Hard-disc fan-area data enciphering and deciphering method and system
InactiveCN1936870AImprove securityPrevent leakageUnauthorized memory use protectionSecuring communicationProgrammable read-only memoryTransfer procedure
This invention discloses an encryption and decryption method for data in hardware. It consists of several steps: obtain the key by reading data from the ROM; obtain the original key by the expending mechanism; operate the logic address and the sequence number and shift the result to get the address key; encryption on the address key by the original key to form a key flow; encryption and decryption on transmitting data. This invention could enhance data security on storage device and protect them from missing.
Owner:ZHEJIANG XUNBO INFORMATION ENG
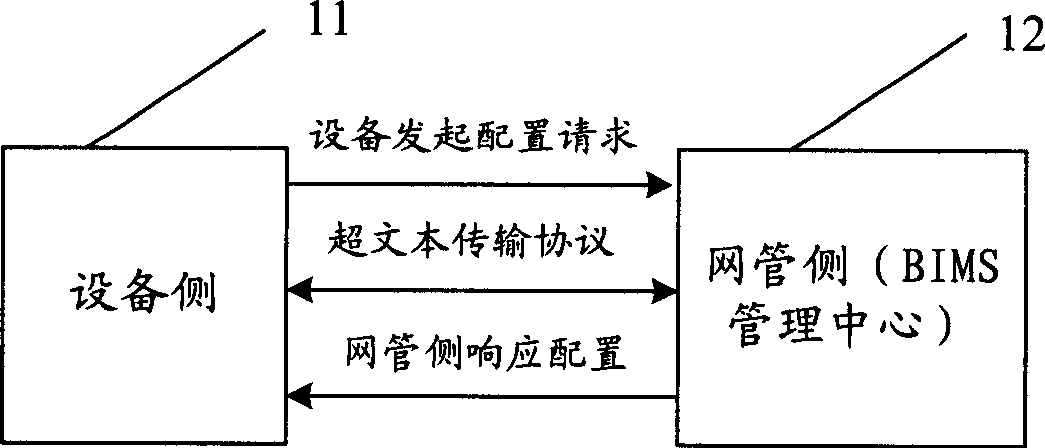
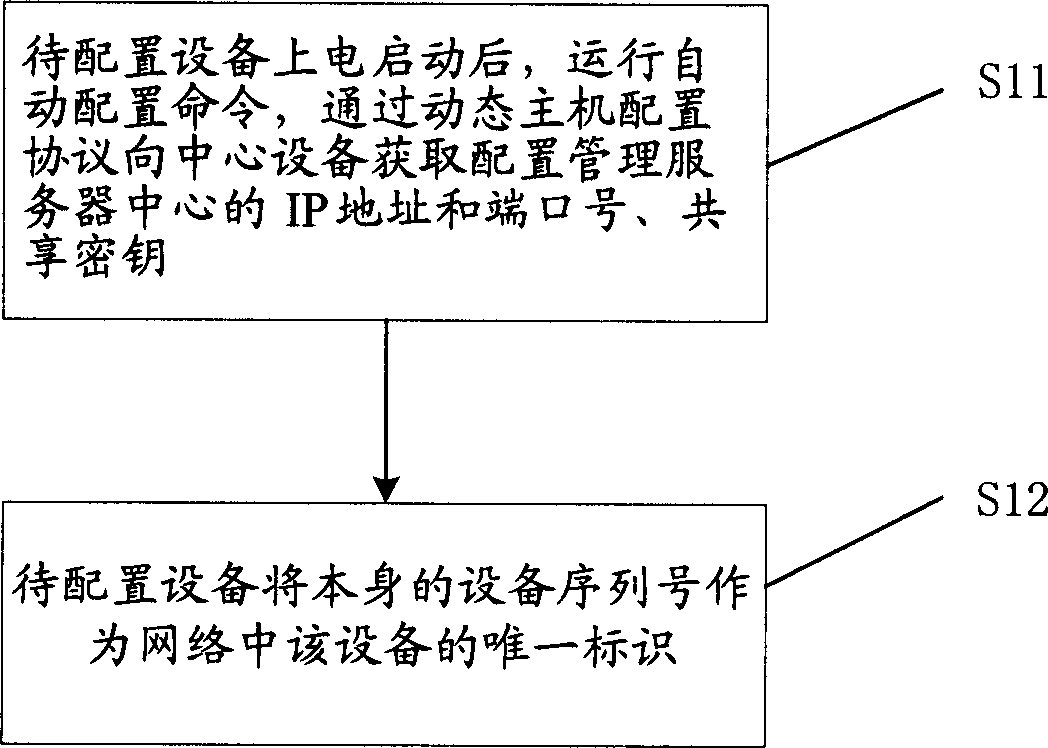
Method and system for automatically gaining configuration management server initial allocation
InactiveCN1791029ARealize zero configurationTroubleshoot initial configuration issuesData switching networksAuto-configurationIp address
The invention relates to a method to automatic acquire initial configuration of management server, which comprises: A. with acquirement unit, after starting, running the auto-configuration command to acquire the IP address and port number and share key of configuration management server center by dynamic host configuration protocol; B. with read unit connected to said acquirement unit, the configuring device uses self device SN as its unique label in network. This invention can solve problem that lots of branch devices need to repeat configure the initial configuration of management server.
Owner:NEW H3C TECH CO LTD
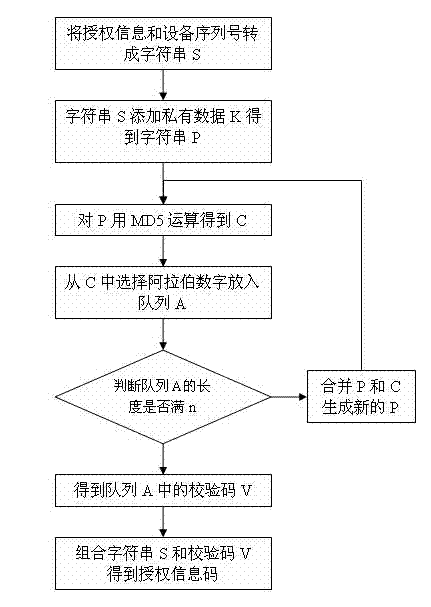
Equipment authorization use method and equipment for method
ActiveCN102831352AEnrich business scopeChanging the leasing business modelComputer security arrangementsElectric equipmentAuthorization
The invention discloses an equipment authorization use method and a device and equipment for the method. The method includes an equipment authorizing device and authorized equipment. The equipment authorizing device is used for generating and outputting an authorization information code; and the authorized equipment receives the authorization information code, and sets the authorization use time of the equipment according to the authorization information code. The interaction between the equipment authorization device and the authorized equipment is realized through the authorization information code. The authorization information code includes an equipment serial number, authorization information and authorization timeliness information, and the authorization information code is generated by converting above information into a character string and adding a check code. The check code is obtained by adding a private data to the above information and processing the information by MD5 (message-digest 5) algorithm, wherein the private data is a secrete data; the MD5 algorithm has non-repudiation; and the authorization information code has a timeliness, so that the authorization information code has certain security. The equipment authorization use method provided by the invention can be used for conducting trial and leasing business of electronic equipment.
Owner:NANJING TIANSU AUTOMATION CONTROL SYST
Device registration method and device registration device
ActiveCN106713518AReduce maintenance costsEasy to operateUser identity/authority verificationDevice typeThird party
The invention relates to a device registration method. The method comprises steps: a device registration request sent by a mobile terminal is received; a user identifier, a device type identifier and a device sequence number are extracted from the device registration request; according to the device type identifier and the device sequence number, corresponding signature data are pulled from a device-party server; according to the user identifier, the device type identifier and the signature data, a device account is generated; the device account is fed back to a controlled device corresponding to the device type identifier and the device sequence number through the device-party server; and a result of device registration success with the device account included is fed back to the mobile terminal. According to the device registration method provided by the invention, a third-party SDK (Software Development Kit) for supporting device registration does not need to be set specially for the controlled device, and the research cost and the maintenance cost for the controlled device are reduced.
Owner:TENCENT TECH (SHENZHEN) CO LTD +1
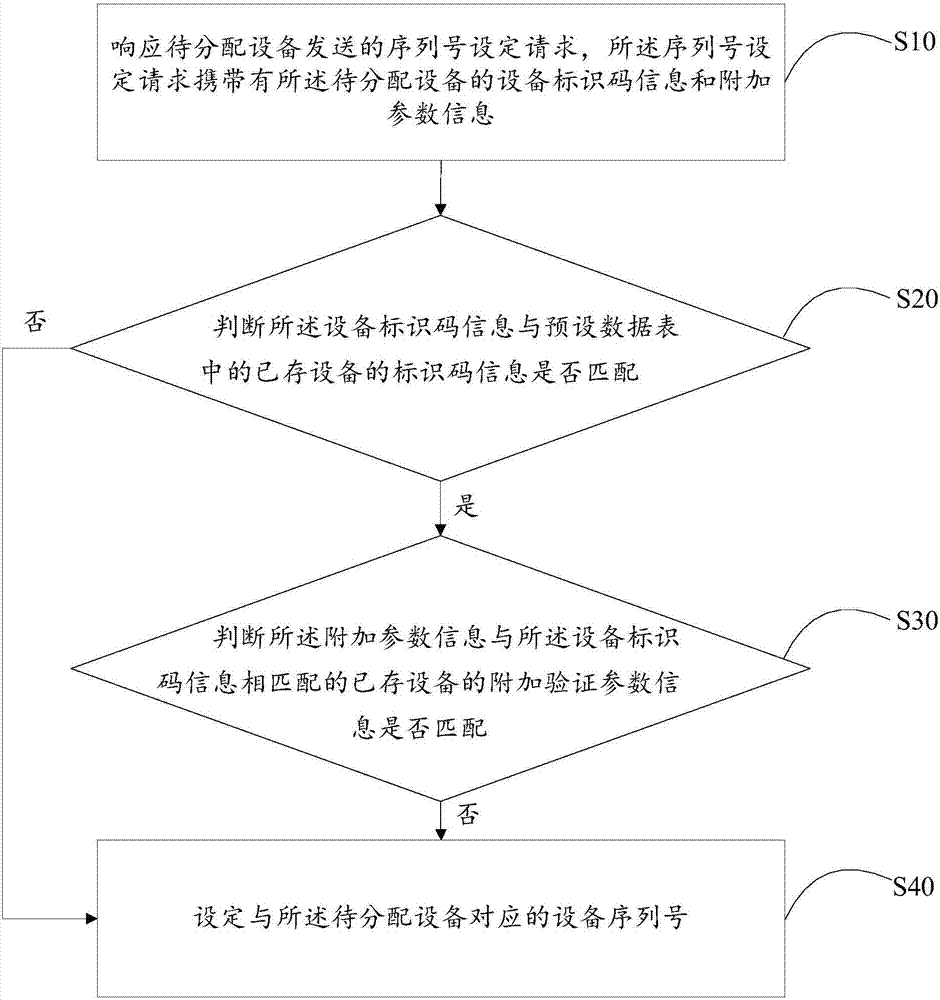
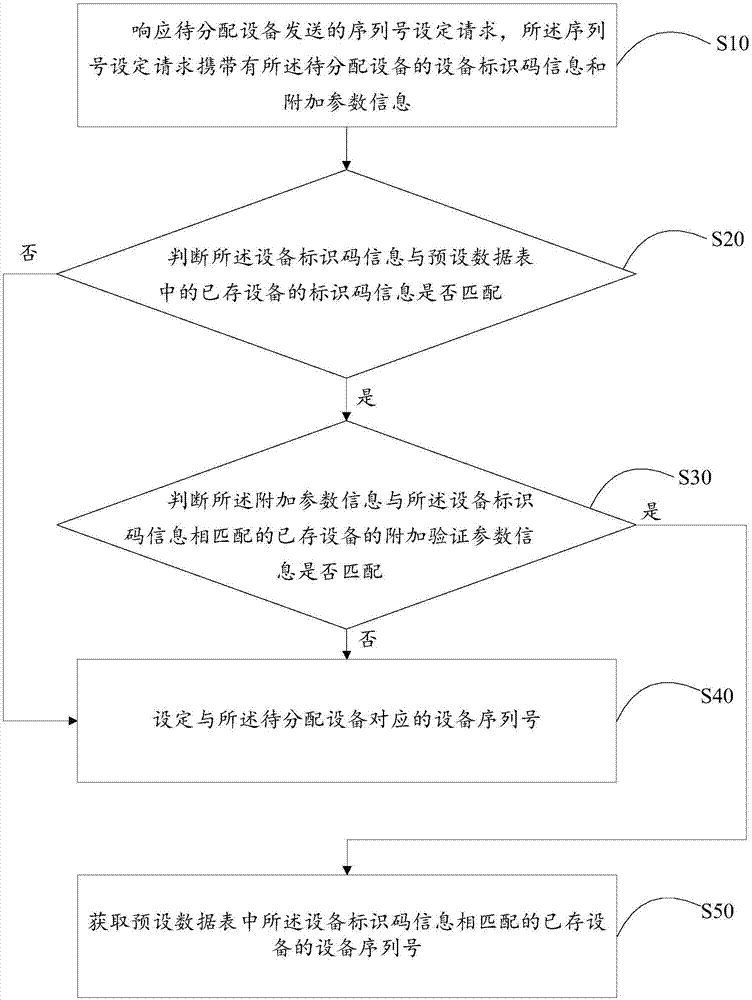
Equipment sequence number setting method and device and computer readable storage medium
ActiveCN107257392ASolve problems that are not uniqueTransmissionSoftware engineeringEquipment serial number
The invention discloses an equipment sequence number setting method and device and a computer readable storage medium. The method comprises the steps of: responding to a sequence number setting request sent by to-be-allocated equipment, wherein the sequence number setting request carries equipment identification code information and additional parameter information of the to-be-allocated equipment; judging whether the equipment identification code information is matched with identification code information of existing equipment in a preset data table; when the equipment identification code information is matched with the identification code information of the existing equipment in the preset data table, judging whether the additional parameter information is matched with additional verification parameter information of the existing equipment matched with the equipment identification code information; and when the additional parameter information is not matched with the additional verification parameter information of the existing equipment matched with the equipment identification code information, setting an equipment sequence number corresponding to the to-be-allocated equipment. The invention solves the problem of non-uniqueness of the equipment sequence number, which is cause by adopting single data to allocate the equipment sequence number currently.
Owner:SHENZHEN TCL NEW-TECH CO LTD
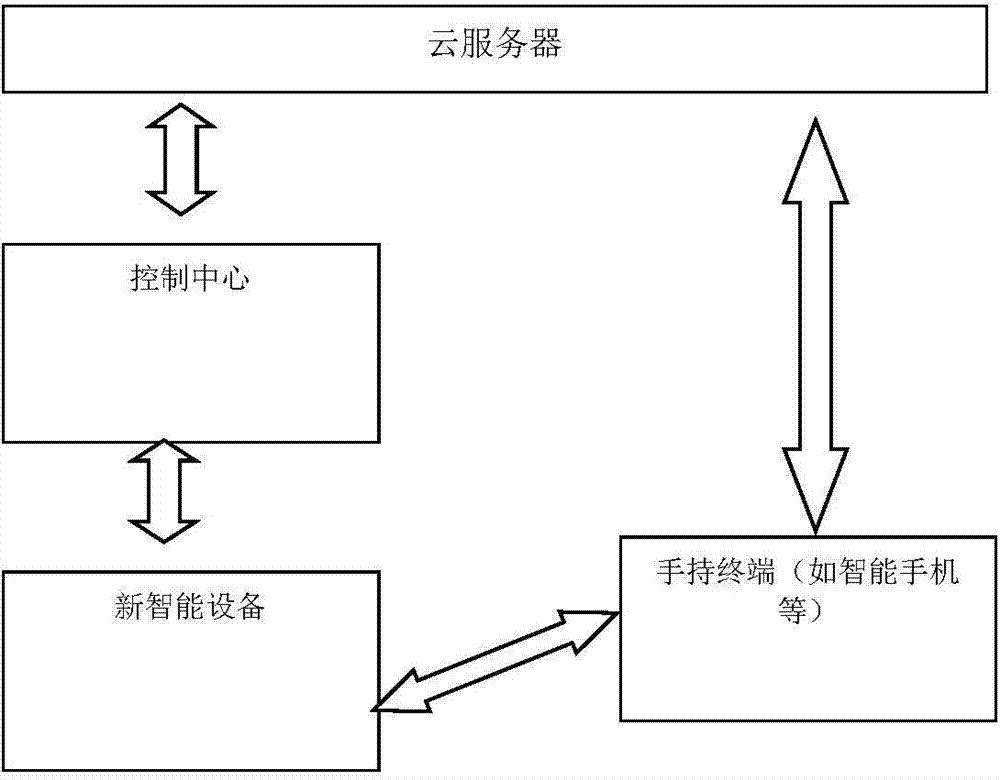
Intelligent household system and quick pairing method thereof
InactiveCN104777752AQuick identificationQuick pairing methodComputer controlProgramme total factory controlPairingIntelligent equipment
The invention relates to an intelligent household system and a quick pairing method of the intelligent household system. The intelligent household system comprises intelligent household equipment, a handheld terminal, a control center and a cloud server, wherein the intelligent household equipment generates a random code with a plurality of bits; the generated random code and an equipment sequence number are displayed on the equipment; the handheld terminal acquires and transmits a configuration command, the random code and the sequence number to the control center via the cloud server or directly; after the control center receives the configuration command, the random code and the sequence number, the control center enters into an equipment addition mode to search equipment for pairing; after the control center is paired with new intelligent equipment, the control center transmits the random code to the new intelligent equipment; the new intelligent equipment is matched with the random code; after matching succeeds, the new intelligent equipment transmits the sequence number to the control center; the control center accomplishes sequence number matching; and the pairing succeeds. Therefore, keys of the control center and the new equipment are not required to be pressed simultaneously; most work is accomplished in the handheld terminal; interference and safety problems of neighbouring multiple-equipment configuration are avoided at the same time; and marks such as a two-dimensional code are not required to be printed on a housing of the equipment any longer.
Owner:YUNDING NETWORK TECH BEIJING
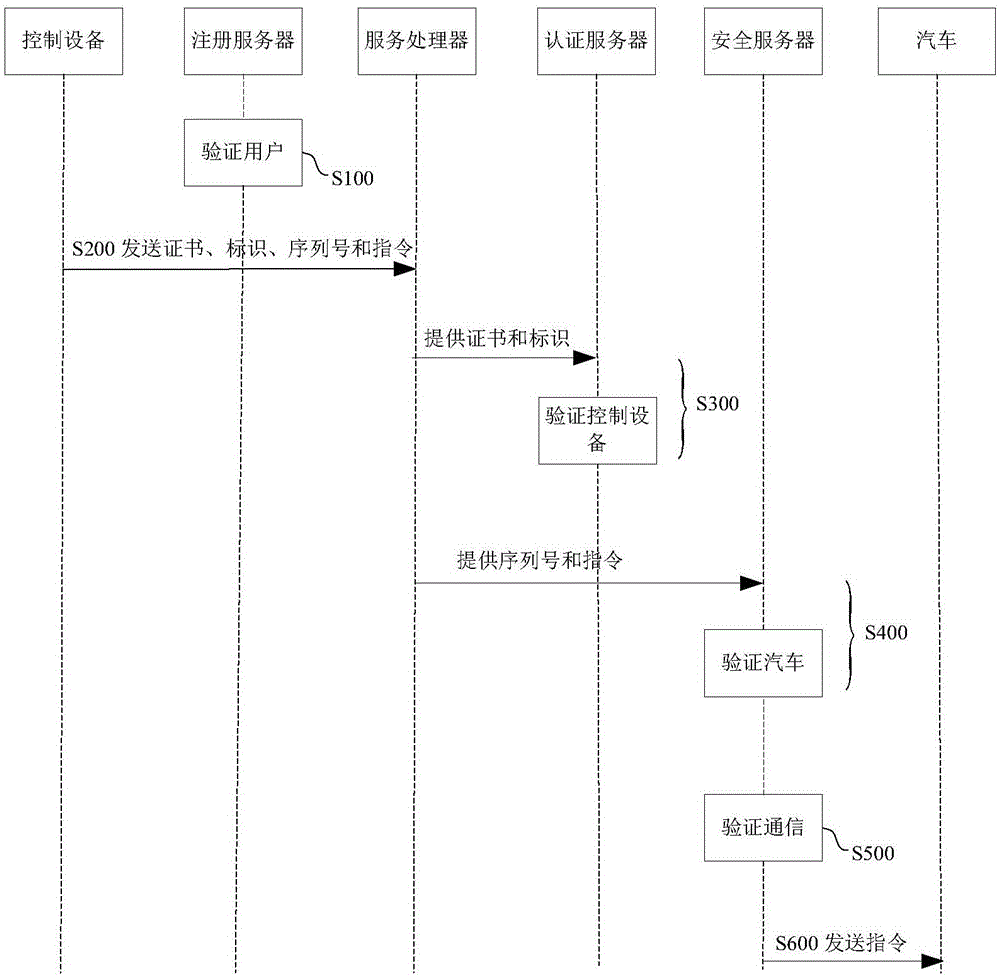
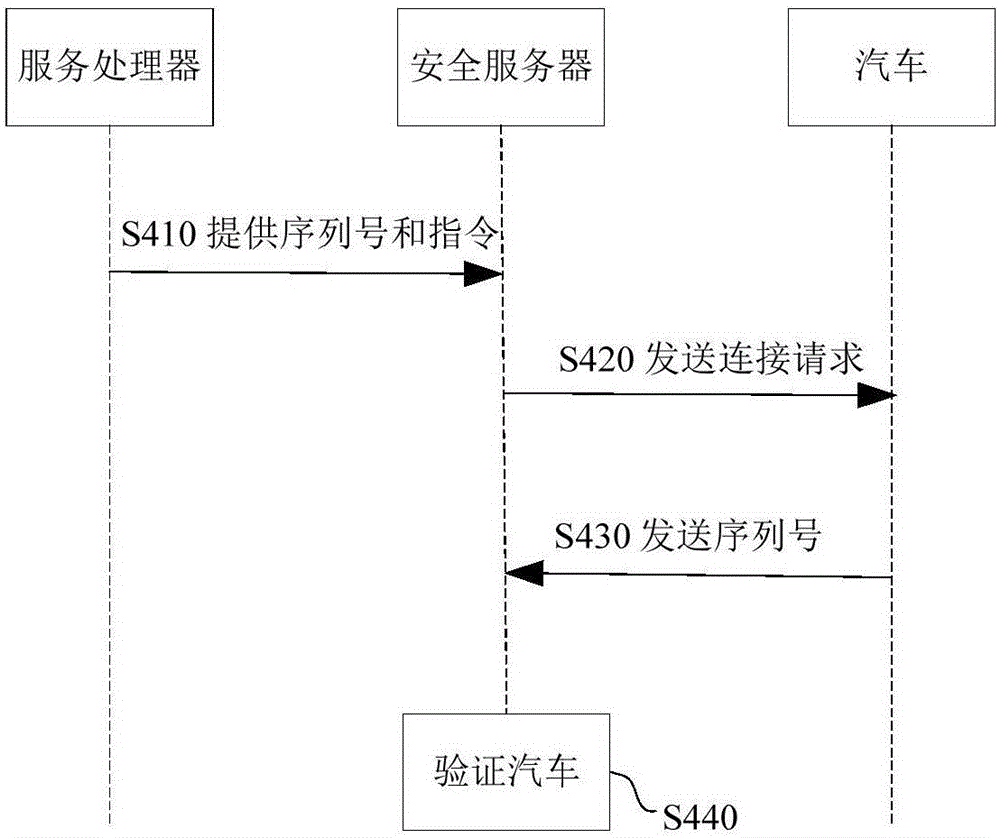
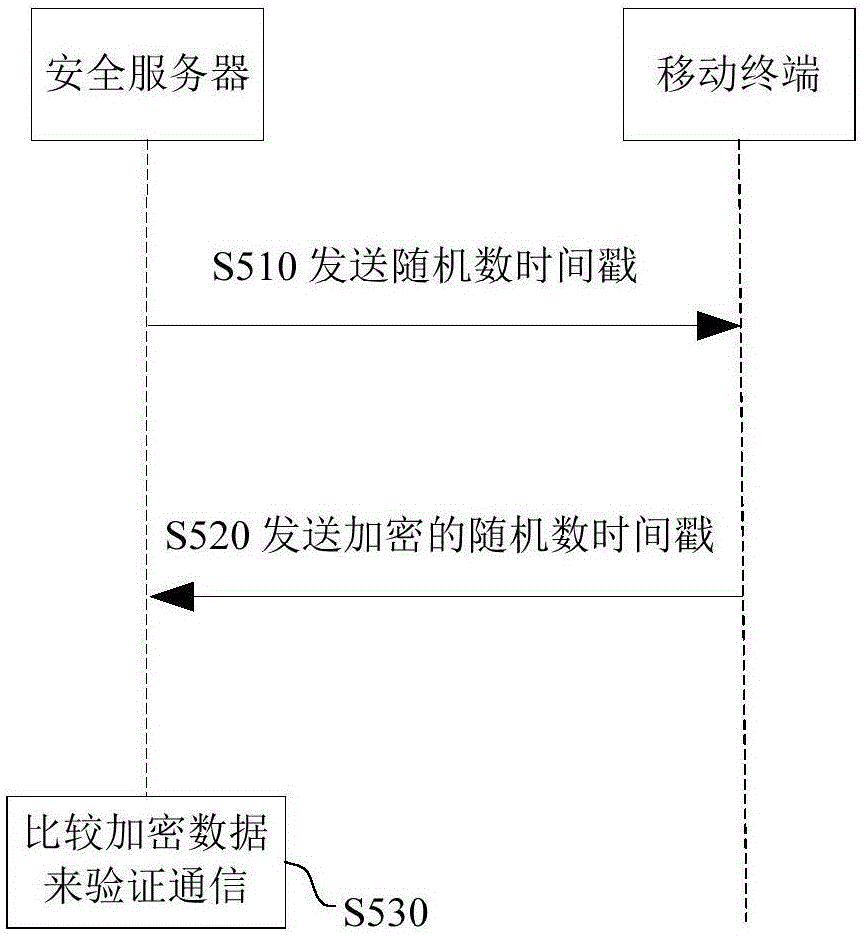
Authentication method for communicating with automobile through control equipment and system thereof
ActiveCN106257861AAvoid controlEnsure safetyUser identity/authority verificationAuthentication serverControl equipment
The invention provides an authentication method for communicating with an automobile through control equipment and a system thereof. The method comprises the steps that a registration server verifies whether the user of the control equipment is a legal user; the control equipment transmits a certificate, the identification information of the control equipment, the vehicle serial number or the vehicle-mounted equipment serial number of the automobile and an instruction used for controlling the automobile to a service processor; the service processor provides the certificate and the identification information of the control equipment to an authentication server, and the authentication server verifies whether the control equipment is legal control equipment; the service processor provides the vehicle serial number or the vehicle-mounted equipment serial number and the instruction used for controlling the automobile to a security server, and the security server verifies whether the automobile is a legally authenticated automobile according to the vehicle serial number or the vehicle-mounted equipment serial number; the security server verifies whether communication between the control equipment and the automobile is legal and secure by using a communication session overtime mechanism and a random number encryption mode; and the security server transmits the instruction used for controlling the automobile to the automobile so as to control the automobile to perform the instruction.
Owner:严俨
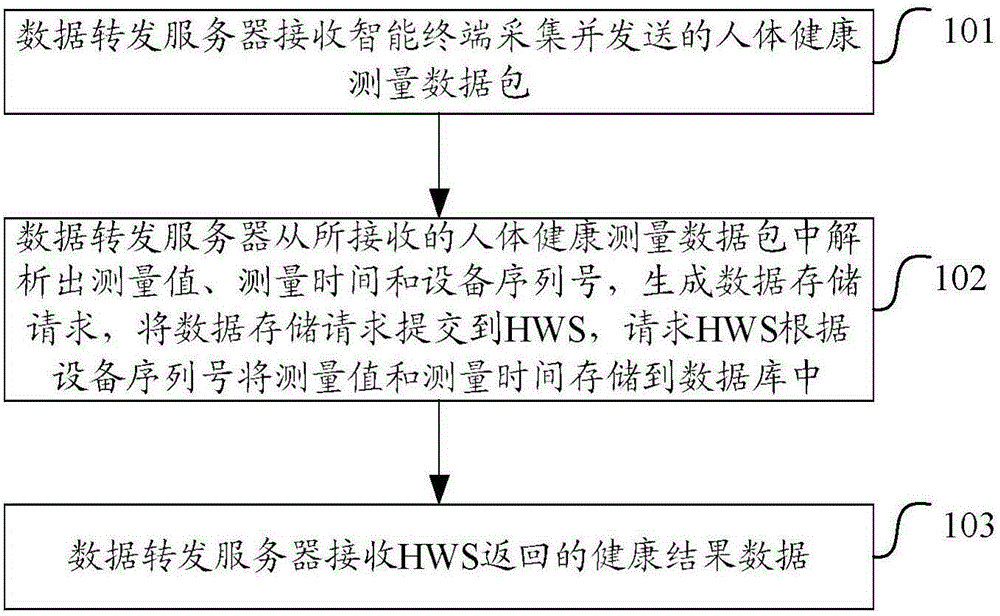
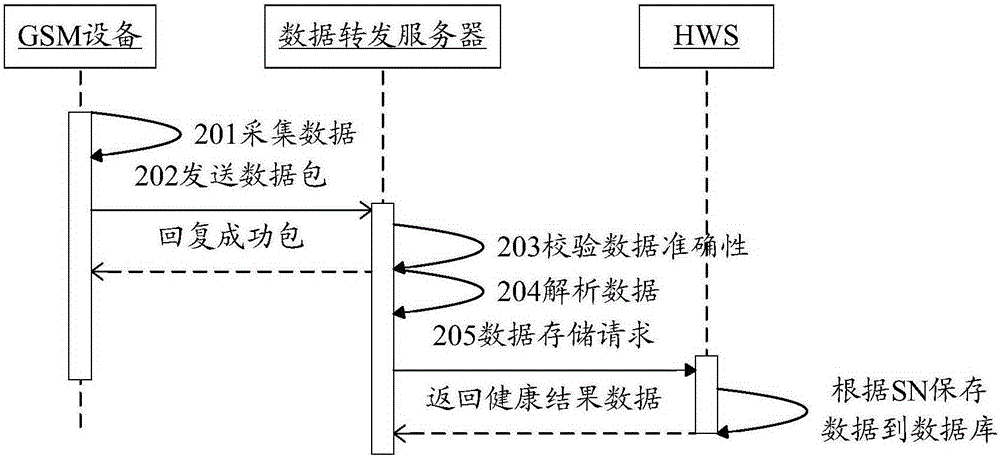
Data uploading method and data forwarding server
ActiveCN105187536ARealize acquisitionAchieve effectivenessTransmissionNetwork packetData acquisition
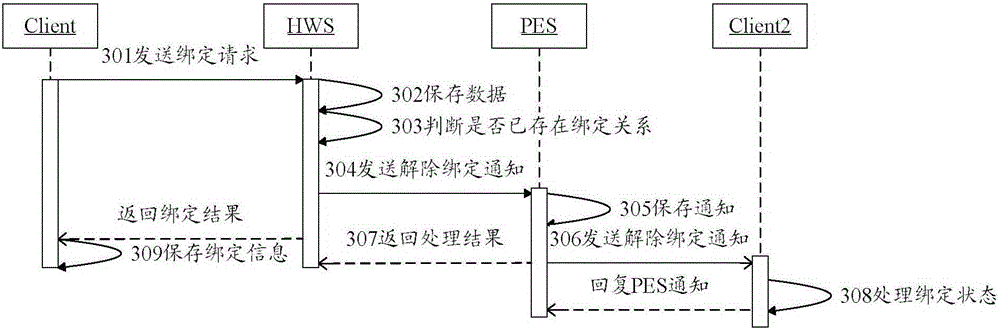
The invention discloses a data uploading method and a data forwarding server. The data uploading method comprises the steps that: the data forwarding server receives a human body health measured data packet acquired and sent by an intelligent terminal; the data forwarding server parse measured values, measurement time and equipment serial numbers out from the received human body health measured data packet, generates a data storage request, submits the data storage request to a network server HWS, and requests the HWS to store the measured values and the measurement time into a database according to the equipment serial numbers; and the data forwarding server receives health result data returned by the HWS. The data uploading method and the data forwarding server achieve the acquisition and effectiveness analysis of medical health data, and establish a set of safe, effective and standard medical health cloud big data acquisition platform.
Owner:GUIYANG LONGMASTER INFORMATION & TECHNOLOGY CO LTD
Method for encrypting and decrypting recorded program through HDCP key
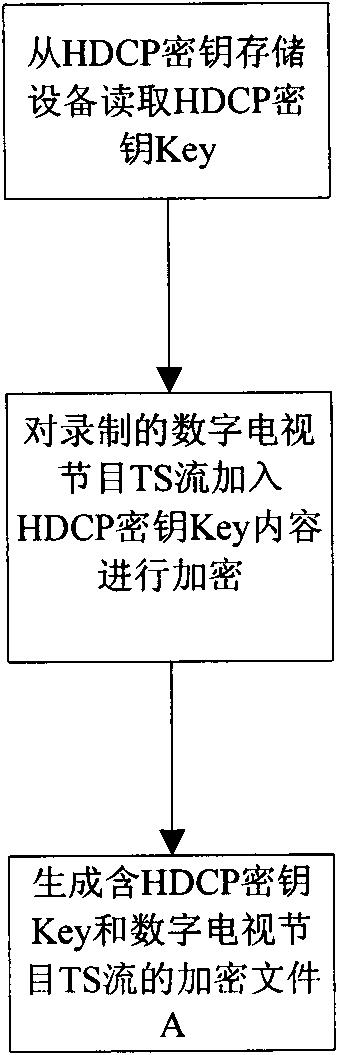
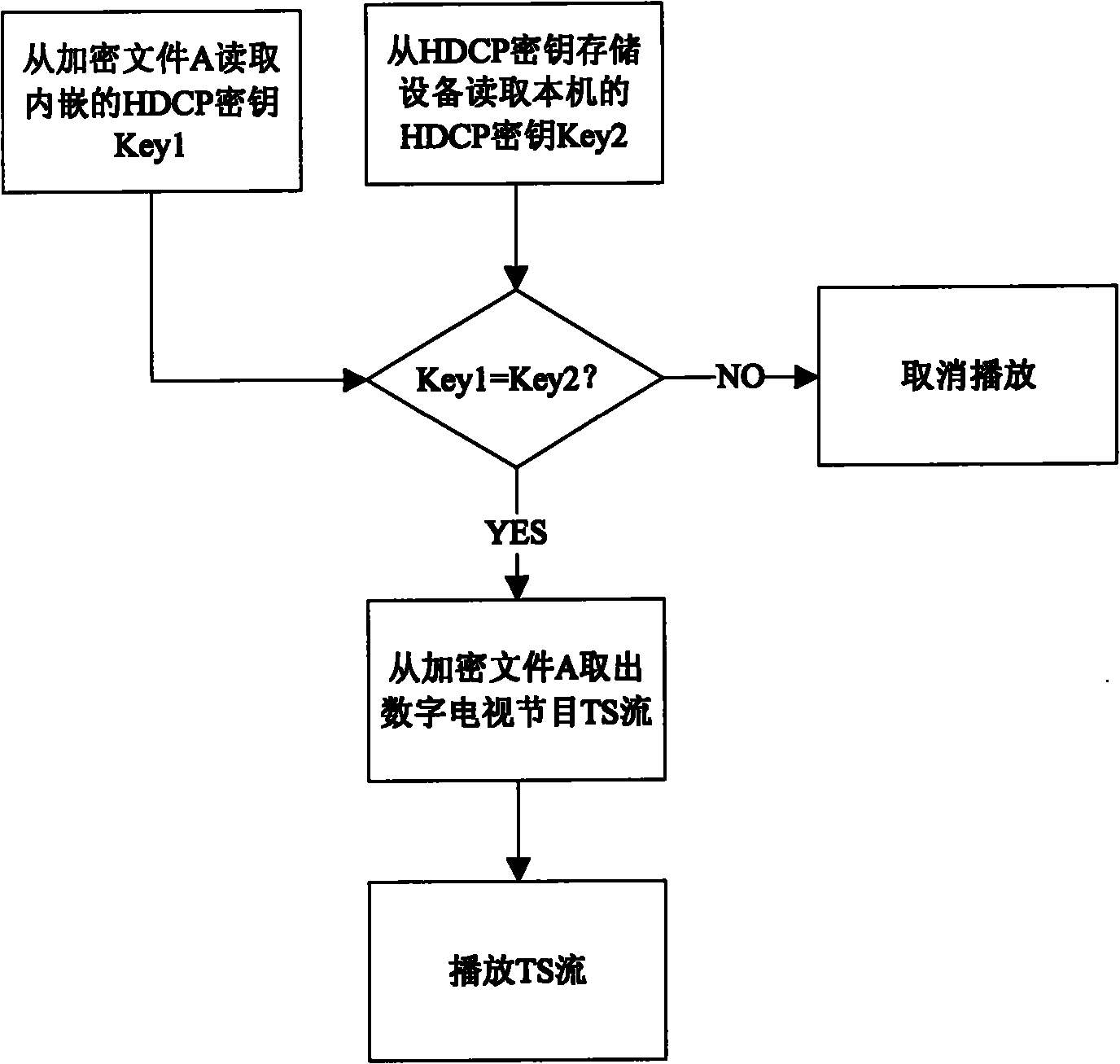
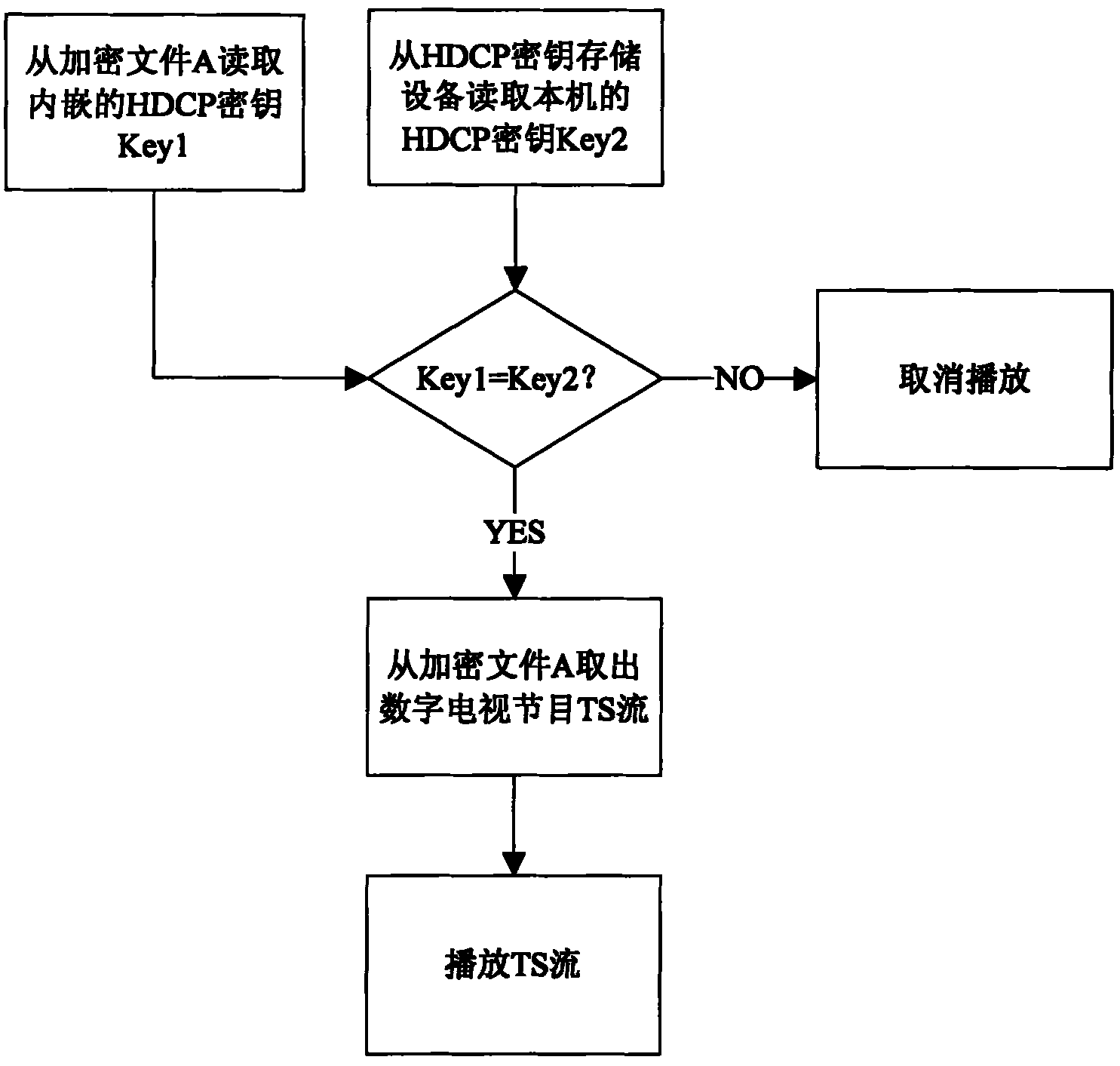
ActiveCN101931784AProtect interestsPulse modulation television signal transmissionAnalogue secracy/subscription systemsHigh bandwidthDigital content
The invention discloses a method for encrypting and decrypting a recorded digital television program through a high-bandwidth digital content protection (HDCP) key. In the method, encrypting and decrypting operation is performed on the recorded content by using the HDCP key carried by a high-definition multimedia interface (HDMI); and an equipment serial number, namely a key selection vector (KSV) is added during the encrypting and decrypting operation. Due to the uniqueness of the KSV carried by a television set or a set-top box, the recorded content is encrypted and decrypted, so that the digital program recorded through the digital television set or the digital set-top box can only be played on the digital television set or the digital set-top box per se.
Owner:KONKA GROUP
Method and device for safely having access to monitoring front-end device
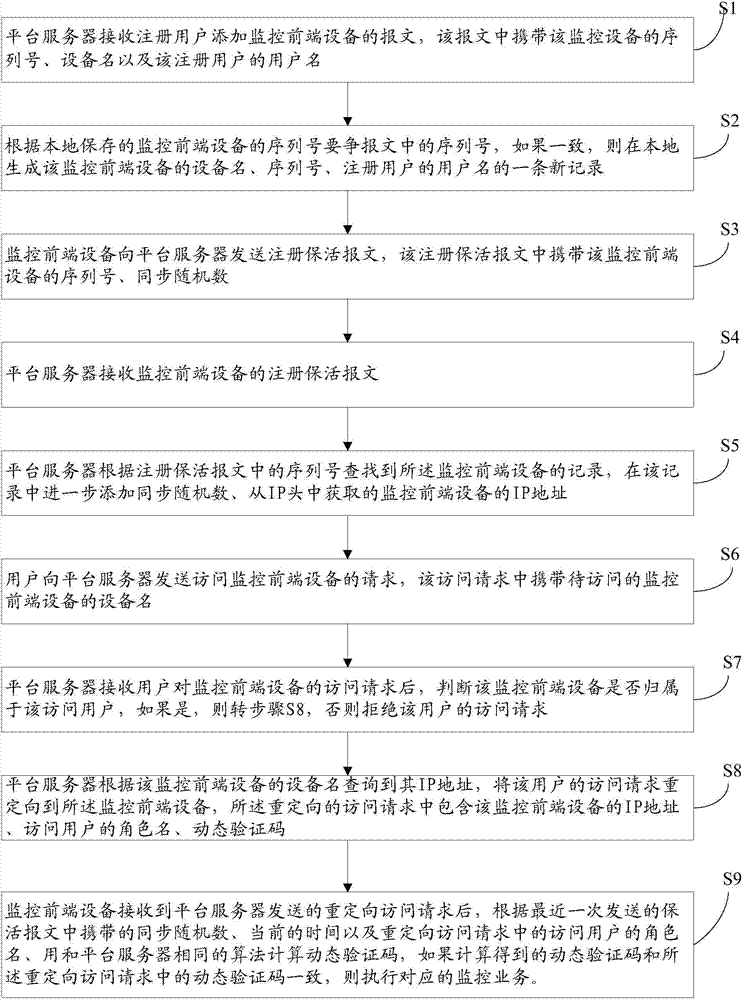
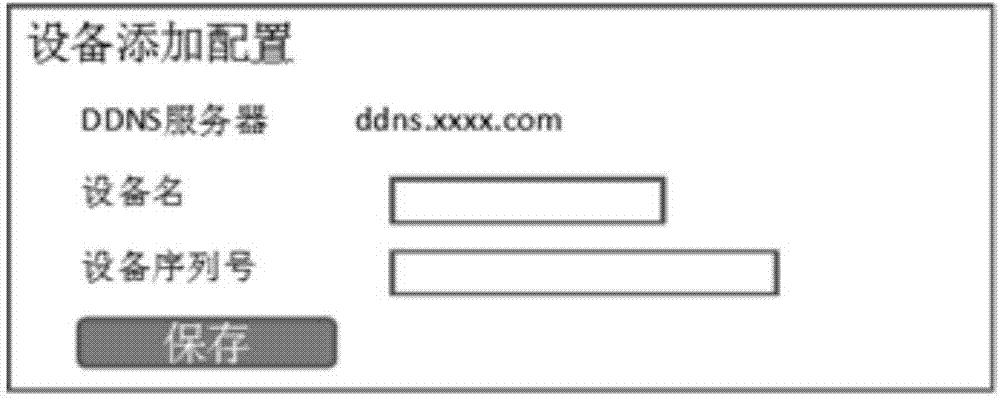
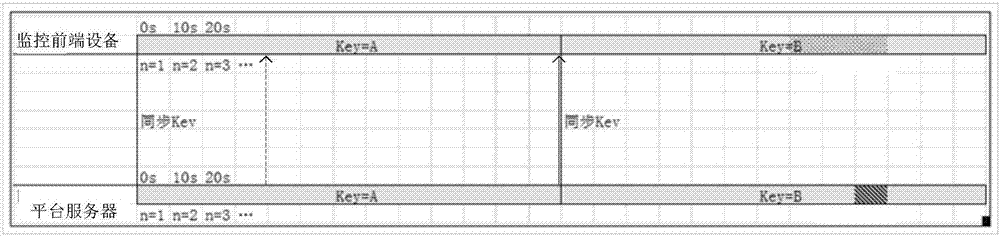
The invention provides a method for safely having access to a monitoring front-end device. The method comprises the first step of receiving a message for adding the monitoring front-end device on a platform server by a registered user; the second step of verifying the serial number in the added message according to the device serial number stored locally, wherein if consistent, a piece of new record including a device name, the serial number and a user name is generated locally; the third step of receiving a register keep-alive message of the monitoring front-end device; the fourth step of searching for the record according to the serial number of the register keep-alive message and adding the synchronous random number and the IP address of the monitoring front-end device; the fifth step of judging whether there is a device name of a device to be accessed under the name of the user or not after the access request of the user is received, wherein if yes, the sixth step is executed, and if not, the access request of the user is rejected; the sixth step of searching for the IP address of the device to be accessed and redirecting the access request of the user to the front-end device, wherein the redirected access request comprises the IP address, a user name and a dynamic verification code of the device. The method for having access to the monitoring front-end device is safe and reliable.
Owner:ZHEJIANG UNIVIEW TECH CO LTD
MAC address generation method and apparatus
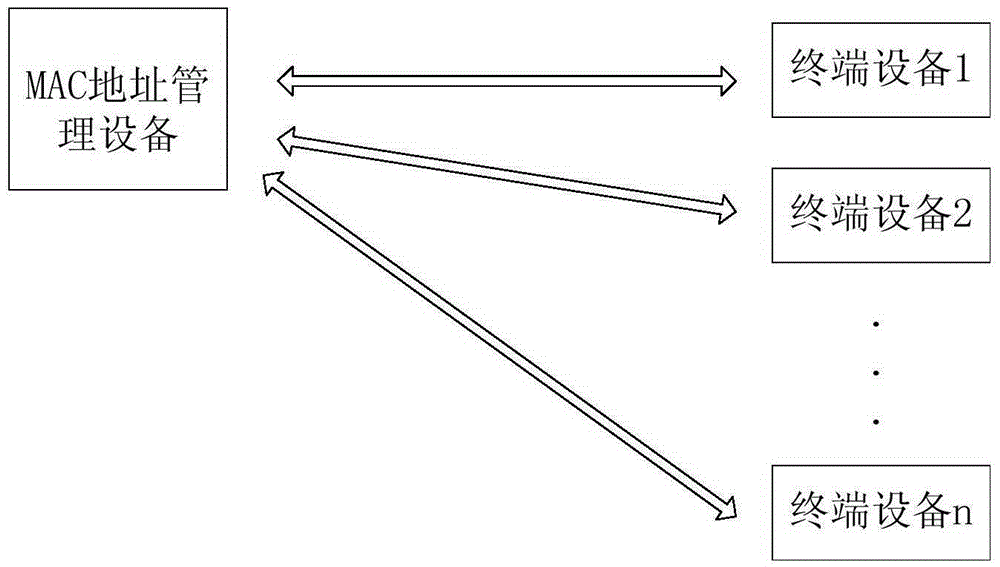
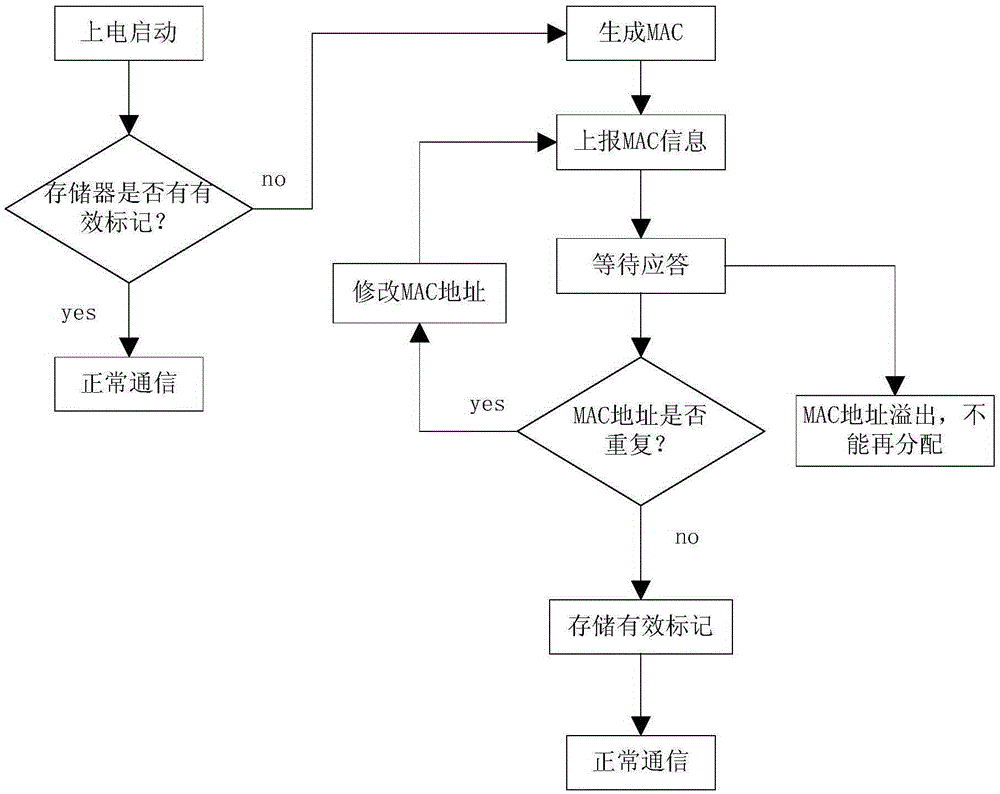
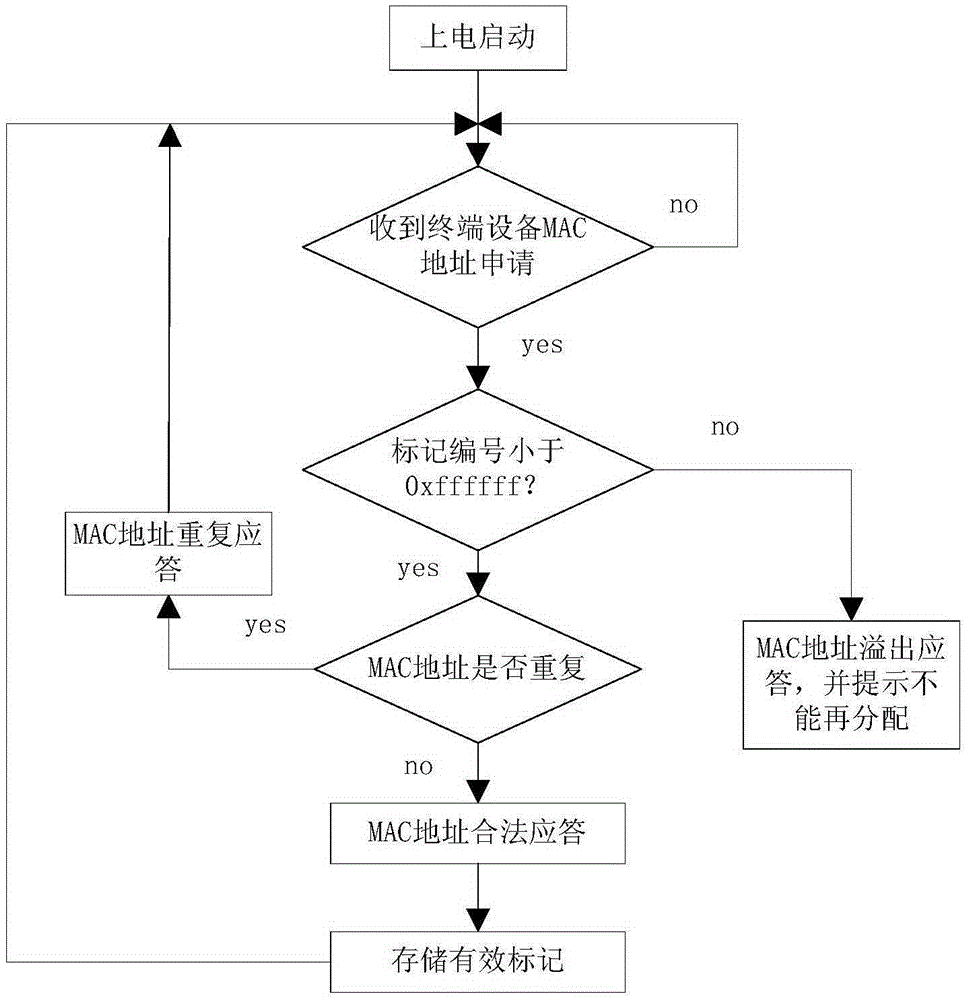
The invention discloses an MAC address generation apparatus, comprising a terminal device and an MAC address management device, wherein the terminal device automatically generates an initial MAC address by means of a device sequence number of a chip, the uniqueness of the MAC address is guaranteed to a certain extent by the particularity of the device sequence number, and by means of the communication with the MAC address management device, the MAC address management device judges to finish an allocation procedure of the MAC address. A unique MAC address is generated finally, and the MAC address is performed with CRC check with the device sequence number and is stored in a memory for starting, reading and verifying in the next startup. The MAC address is generated without excessive manual participation in the entire process, and the MAC address is always safe and unique within the service lives of the processor and the memory of the device. The apparatus and the device disclosed by the invention are used for automatically generating and allocating the MAC address and writing the unique MAC address in the memory at last, in order to improve the efficiency of overall volume production.
Owner:GUANGZHOU HUIRUI SITONG INFORMATION SCI & TECH CO LTD
Access control system and method of remote centralized authentication
ActiveCN103839318AImprove timelinessReduce waiting timeUser identity/authority verificationIndividual entry/exit registersApplication serverCommunication unit
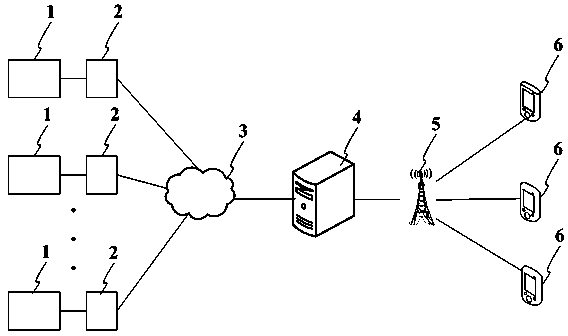
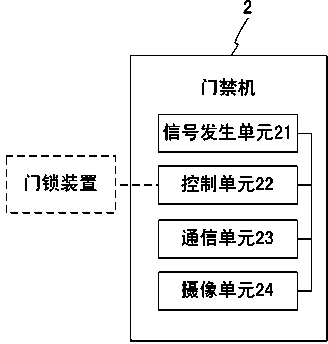
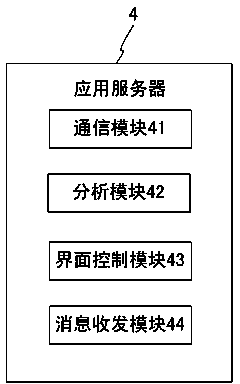
The invention relates to an access control system and a method of remote centralized authentication, belonging to the technical field of access control. The access control system comprises a plurality of door lock devices, a plurality of access control machines, an application server, a communication base station and a user mobile phone, wherein different access control machines are uniquely identified by using equipment serial numbers, and are communicated with the application server through a communication network, wherein each access control machine comprises a signal generating unit, a control unit, a communication unit and a camera unit, after a door opening request signal generated by the signal generating unit is analyzed and treated through the control unit, door opening request information is forwarded to the application server through the communication unit, and the application server comprises a communication module, an analysis module, an interface control module and a message receiving and transmitting module. According to the access control system, the practicability, the reliability and the safety of a remote centralized authentication mode in the access control system are further improved.
Owner:云南数金科技有限公司
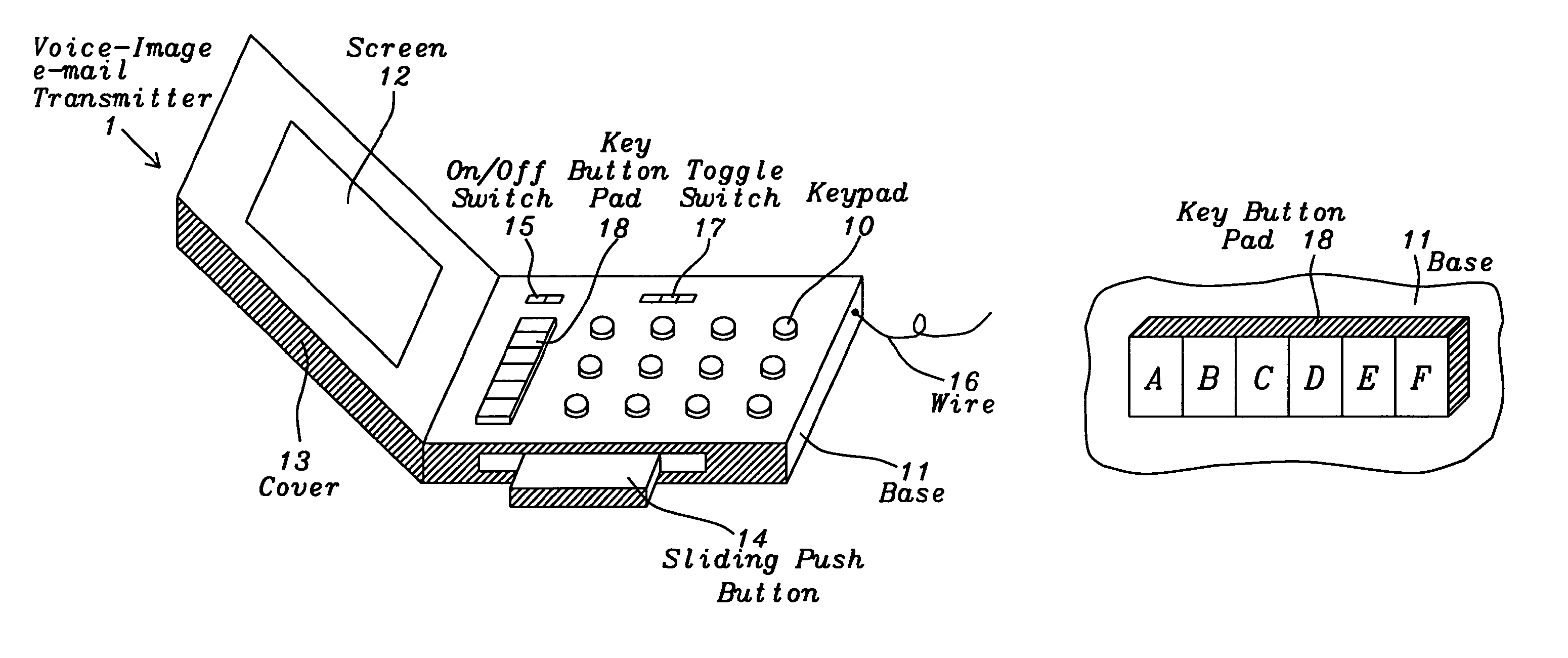
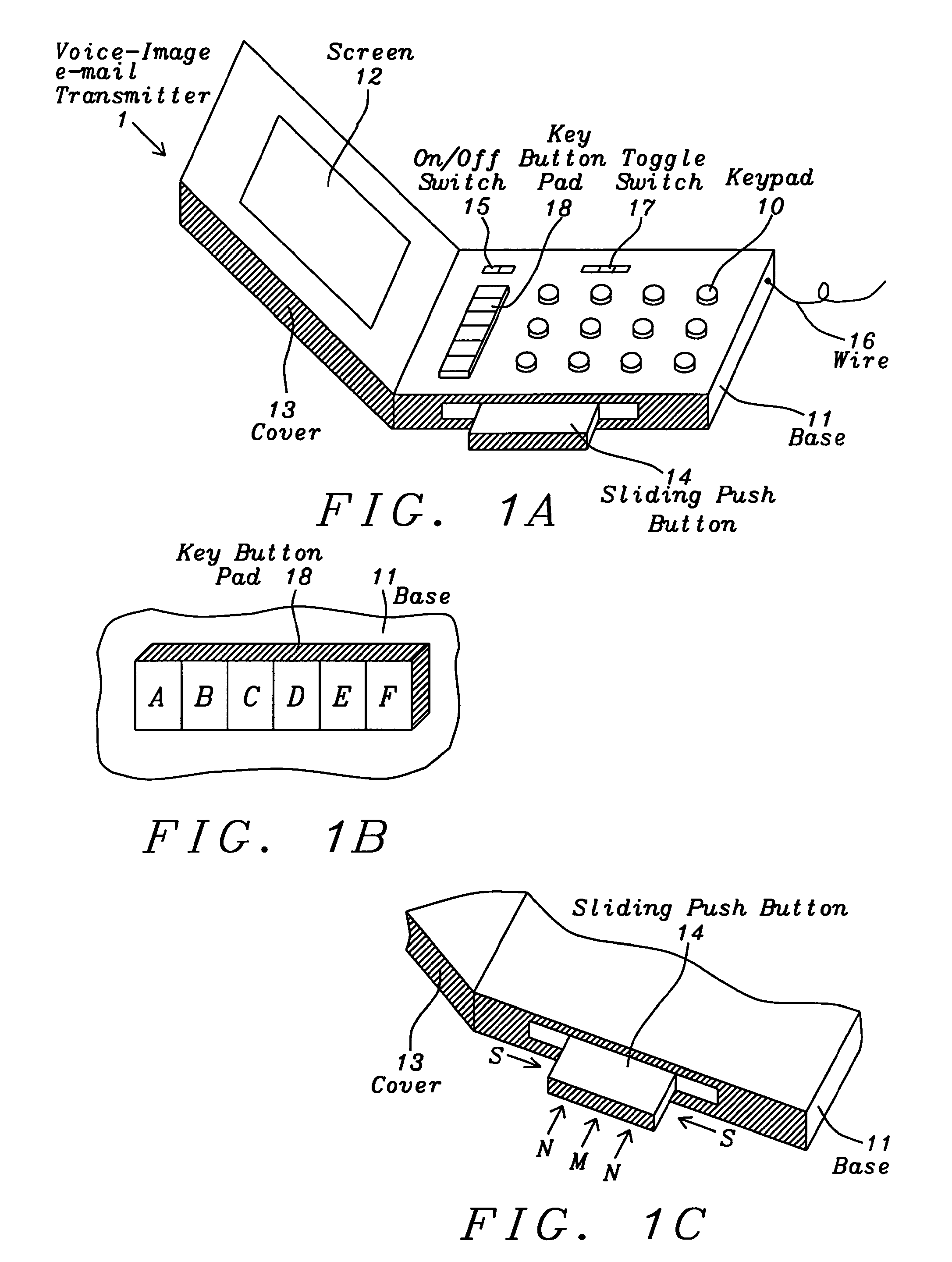
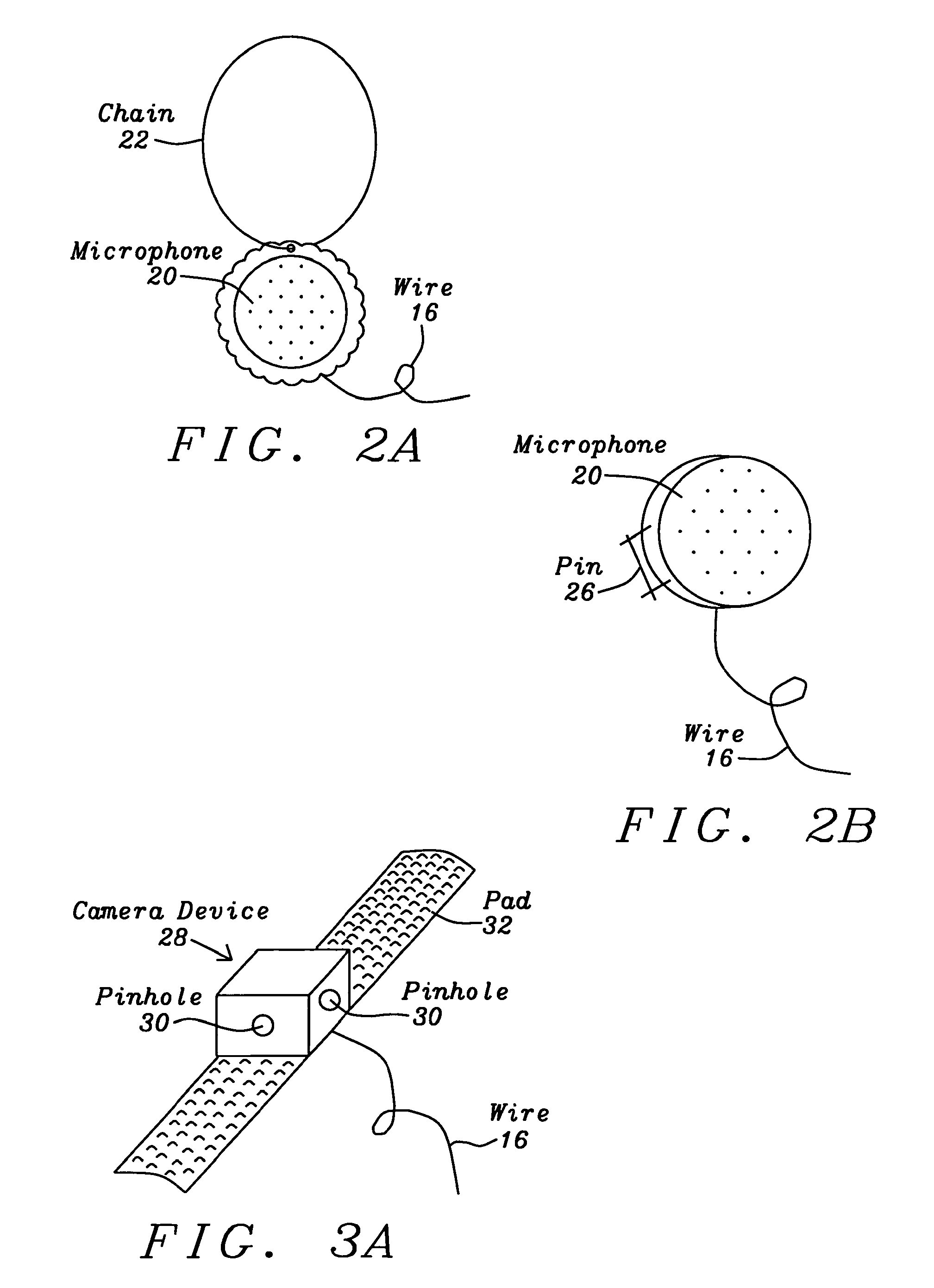
System and method for the emergency voice and image e-mail transmitter device
InactiveUS7751534B2Easy to parseReduce fearAutomatic call-answering/message-recording/conversation-recordingData switching networksEmail addressJPEG
Owner:SUN NICHOLAS
Protection method for secure cloud computing terminal
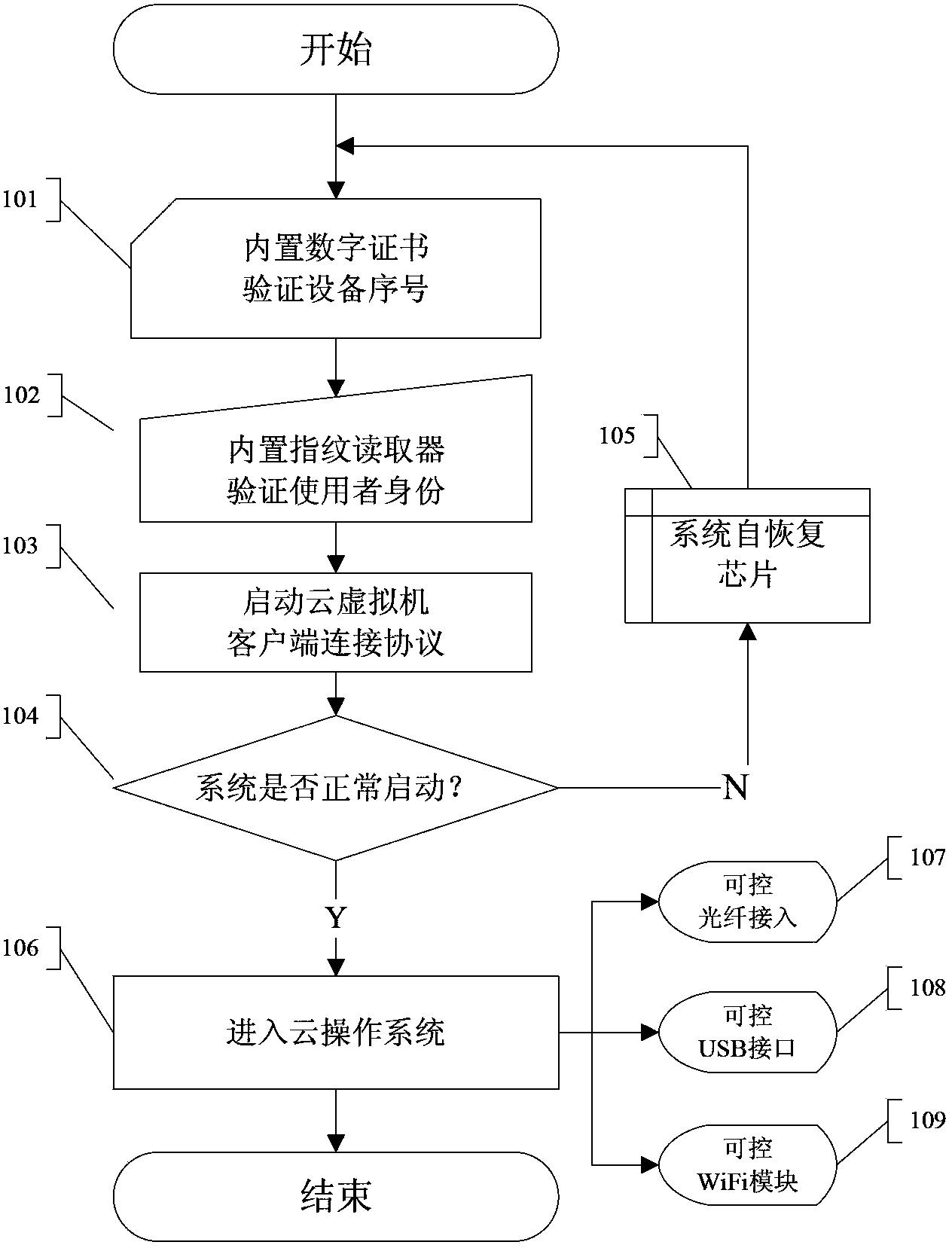
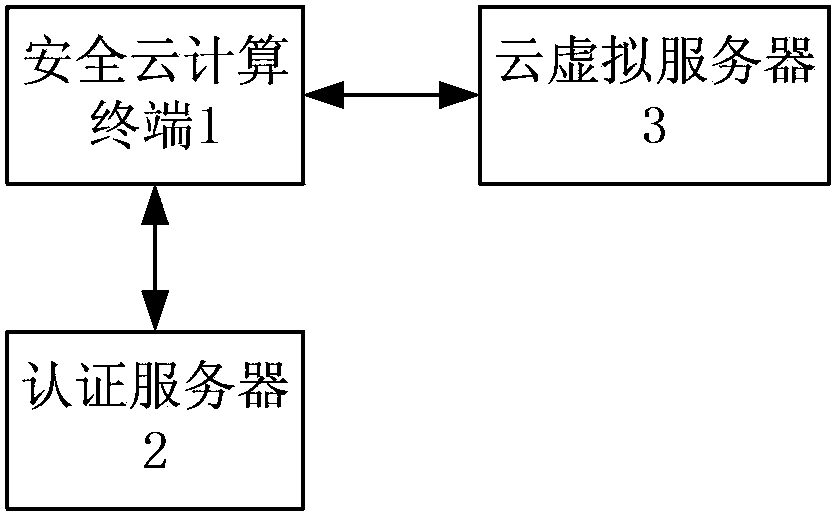
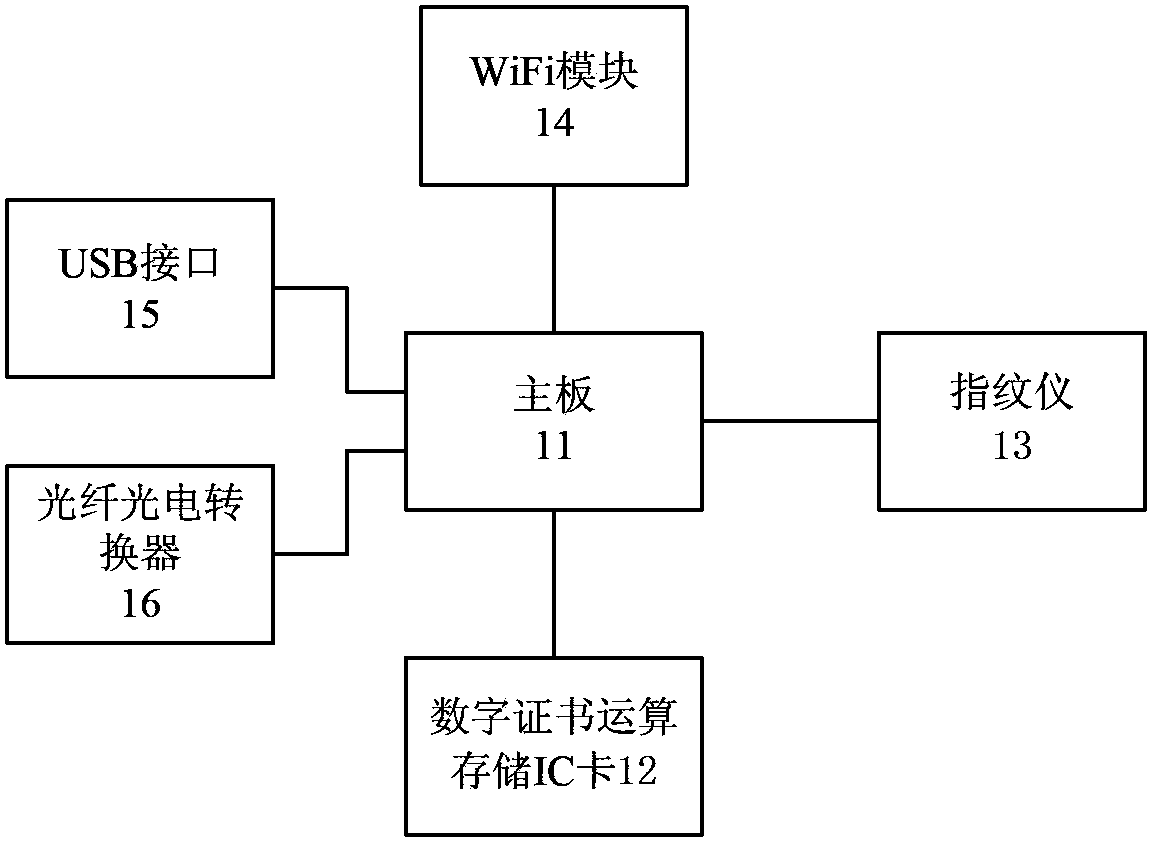
InactiveCN103780583AResolve the Leakage SituationAddress safety risk concernsUser identity/authority verificationControl signalClient-side
The invention relates to a protection method for a secure cloud computing terminal. The protection method comprises a first step in which a unique equipment serial number is generated by a digital certificate computing storage IC module arranged inside the secure cloud computing terminal; a second step in which a user identity is verified by a fingerprint reader arranged inside the secure cloud computing terminal; a third step in which the secure cloud computing terminal is connected with a virtual cloud server via a client connection protocol to start a remote cloud virtual machine; a fourth step in which normal starting is judged, if yes, the sixth step is carried out, and if not, the fifth step is carried out; a fifth step in which initial setup is restored by the secure cloud computing terminal, and the first step is carried out; and a sixth step in which the secure cloud computing terminal is connected to a cloud operation system, and the start / stop state of a WiFi module, a USB interface and an optical photoelectric converter can be controlled via controllable signal output and input interfaces. Compared with the prior art, the protection method for a secure cloud computing terminal has the advantages that the problem that the user information is revealed duo to weak secure cloud computing terminal protection measures can be effectively solved and the like.
Owner:SHANGHAI JUNYUE INTELLIGENT TECH
Equipment authorization method, device and system
InactiveCN105187438ARealize offline authorization operationAuthorization operation implementationTransmissionComputer moduleAuthorization
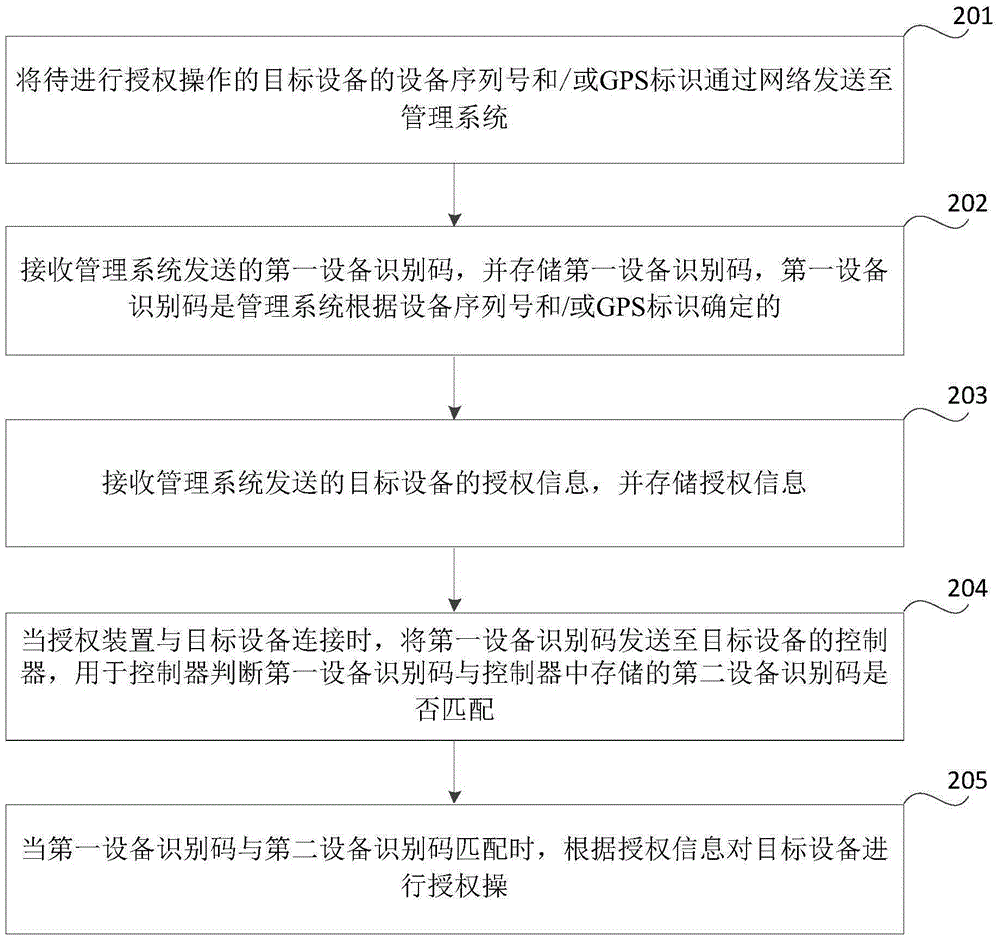
The invention provides an equipment authorization method, device and system. The method comprises the following steps that: an authorization device transmits an equipment serial number and / or GPS (Global Position System) identifier of target equipment to a management system through a network; the management system determines a matched first equipment identification code and transmits the matched first equipment identification code to the authorization device according to the equipment serial number and / or GPS identifier; the authorization device receives the first equipment identification code and stores the first equipment identification code; when the authorization device is connected with the target equipment, the authorization device transmits the stored first equipment identification code to a controller of the target equipment; the controller judges whether the first equipment identification code is matched with a second equipment identification code stored in the controller or not; and when the first equipment identification code is matched with the second equipment identification code, the authorization device performs authorization operation on the target equipment according to authorization information. Through adoption of the equipment authorization method, device and system, authorization operation of the equipment can be realized under the situation that GPS signal intensity is low or GPS signals are unavailable or the equipment is not provided with any GPS module.
Owner:BEIQI FOTON MOTOR CO LTD
Ad-Hoc network communication manager and networking method thereof and Ad-Hoc network communication system
PendingCN109450662AFast networkingQuick associationSingle network parallel feeding arrangementsSystems intergating technologiesCommunication interfaceUnit device
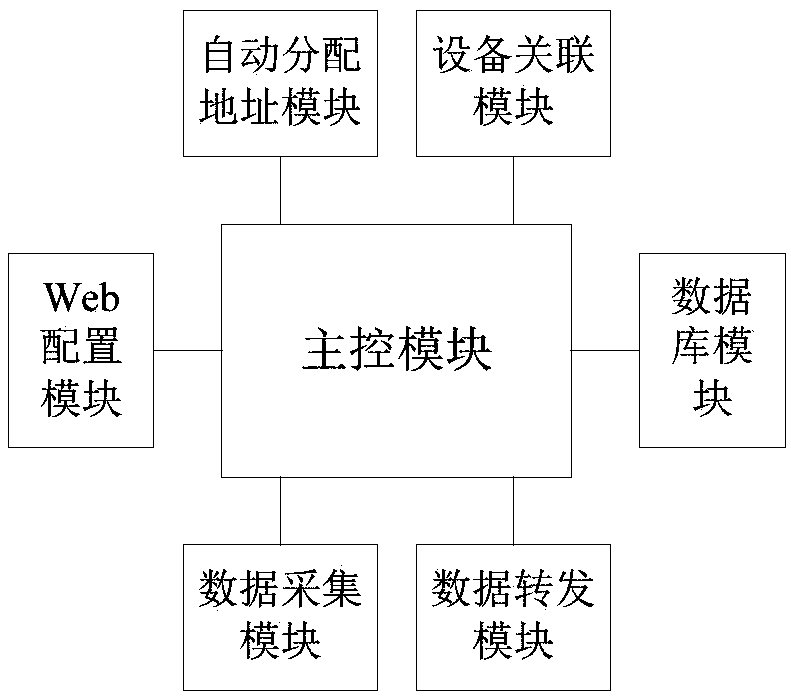
The invention relates to an Ad-Hoc network communication manager and a networking method thereof and a photovoltaic megawatt house Ad-Hoc network communication system. The Ad-Hoc network communicationmanager is connected and communicated with multiple networking devices, the networking devices comprise basic unit devices and branch devices, the basic unit devices are connected with a main controlmodule through communication interfaces, and the branch devices are connected with the basic unit devices; and the Ad-Hoc network communication manager configures device parameters of each networkingdevice through a Web configuration module and stores the device parameters to a database module, and an automatic address allocation module sends broadcast commands according to channels configured by the Web configuration module, automatically allocate different addresses to the devices sequentially according to the order of responses returned by received reading sequence numbers and sequentially broadcasts and sends address setting commands carrying device sequence numbers and device communication addresses for self networking. The networking method is a networking method for the Ad-Hoc network communication manager, and the photovoltaic megawatt house Ad-Hoc network communication system adopts the Ad-Hoc network communication manager.
Owner:ZHEJIANG CHINT ELECTRIC CO LTD
Method and apparatus for binding equipment
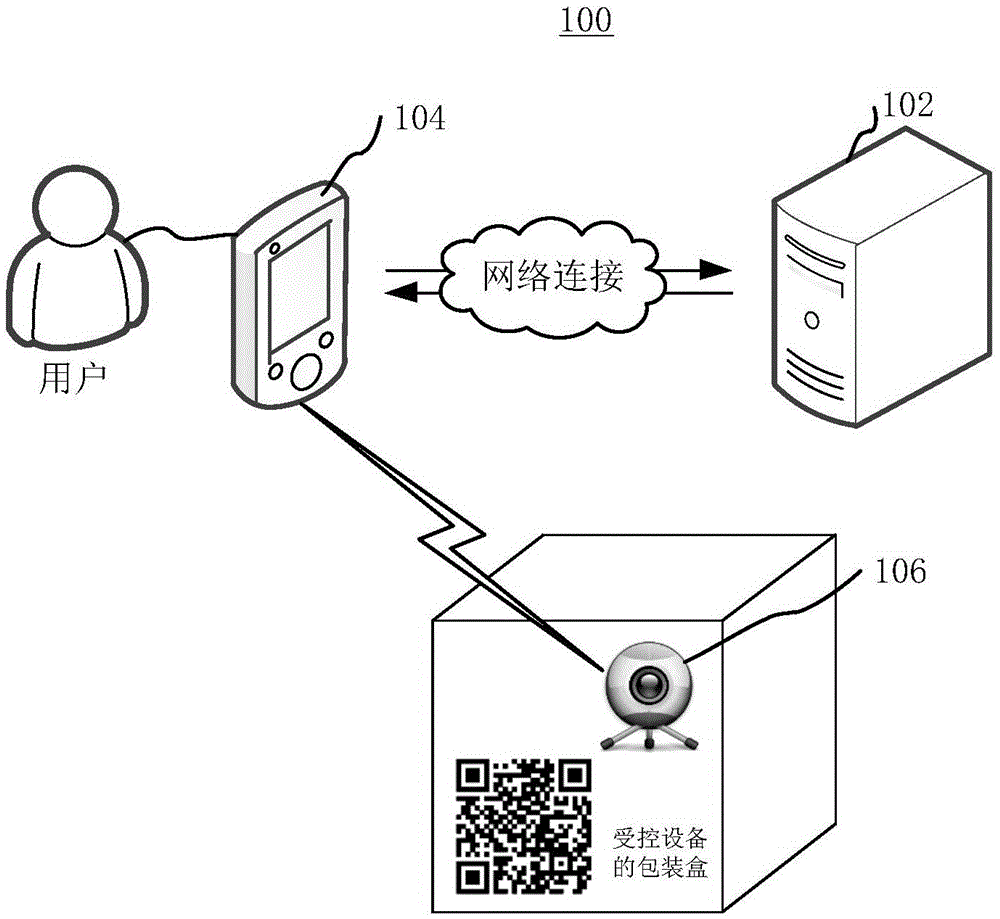
ActiveCN106559388ASimple and fast operationImprove operational convenienceTransmissionGraphicsImage code
The invention relates to a method and apparatus for binding equipment wherein the method comprises the following steps: scanning the image code corresponding to a piece of controlled equipment so as to obtain the serial number of the equipment; uploading the user identification and the serial number of the equipment to a server so that when the server establishes the binding relationship between the user identification and the serial number of the equipment, a binding record is generated and saved for the equipment corresponding to the user identification wherein the equipment binding recording includes the serial number of the equipment; drawing from the server the list of the equipment binding record corresponding to the user identification; and selecting from the list the equipment binding record and announcing the server so that the server could re-establish the binding relationship between the user identification and the serial number of the equipment in the selected equipment binding record. The method and apparatus for binding equipment provided by the invention bind equipment through the scanning of image code, which can effectively avoid the condition that equipment cannot be bonded due to the loss of image code.
Owner:TENCENT TECH (SHENZHEN) CO LTD
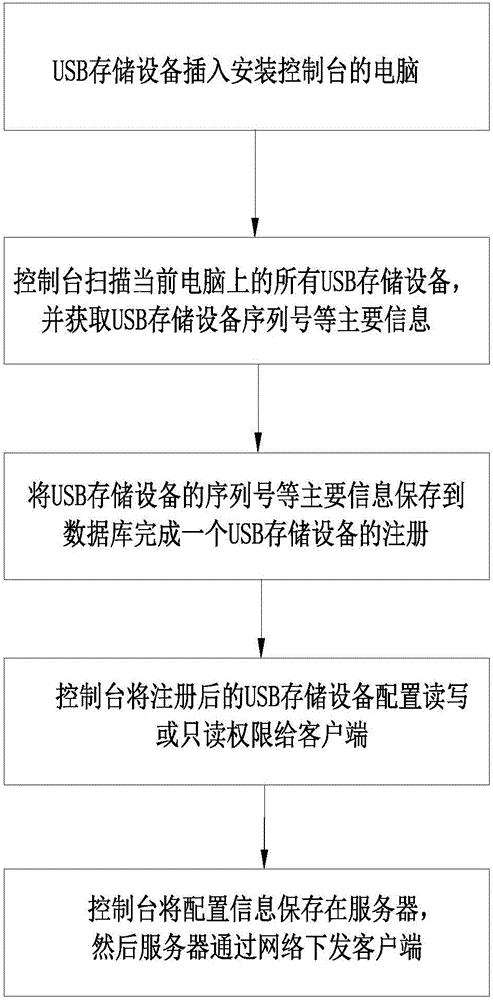
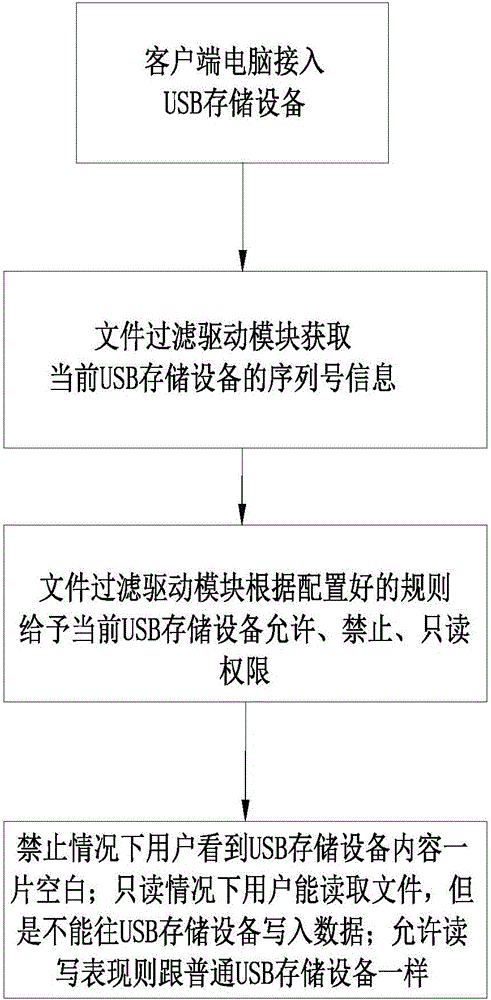
Method and system for limiting USB (universal serial bus) storage device through file filter driving
ActiveCN106203187AImprove general performanceIncrease flexibilityInternal/peripheral component protectionData acquisitionComputer module
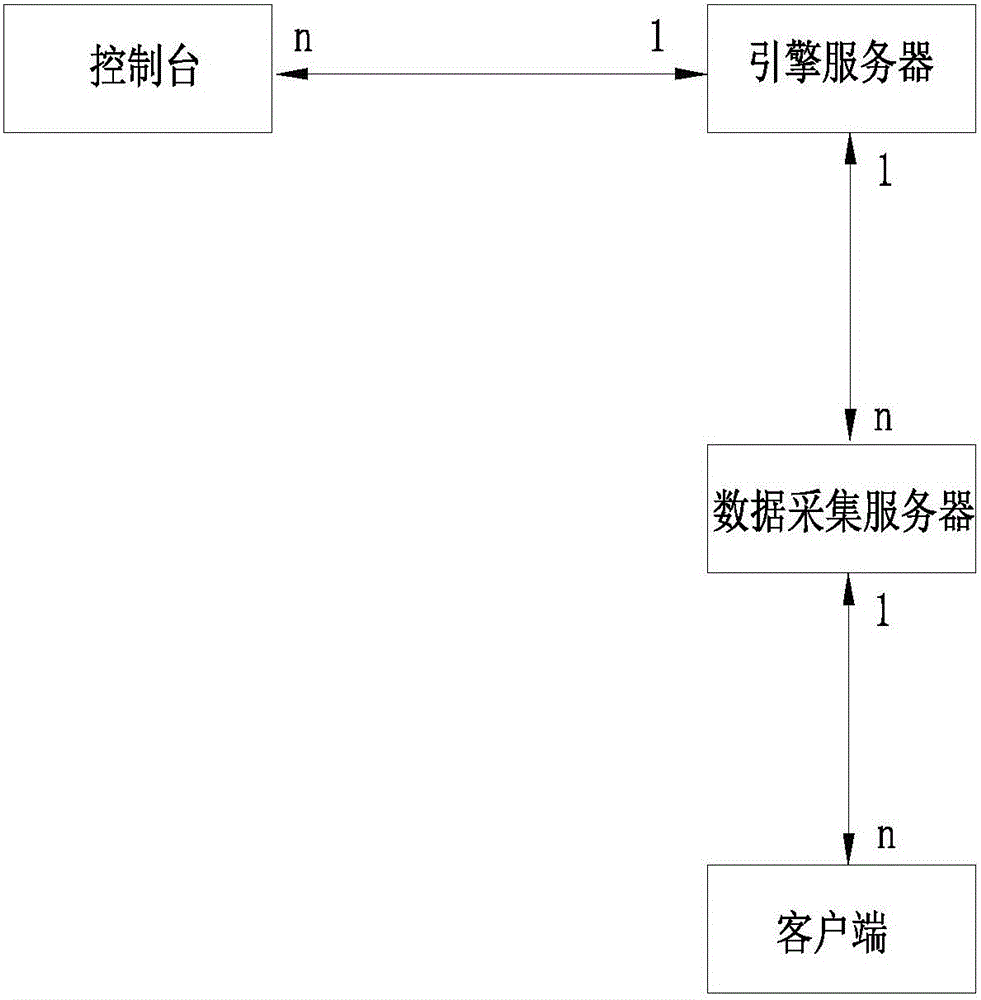
The invention relates to a method for limiting a USB (universal serial bus) storage device through file filter driving. The method comprises steps as follows: a policy configuration is saved, and when the USB storage device is inserted in a computer, the serial number of the currently mounted USB storage device is detected; information of the saved policy configuration is acquired; whether the serial number of the USB storage device is used legally is judged according to the policy configuration, and a permission is given to the USB storage device. A system for limiting the USB storage device through file filter driving comprises an engine server, a control console, a data acquisition server and a client side, wherein the engine server is connected with the control console and the data acquisition server, and the data acquisition server is connected with the client side. With the method and the system, use of the USB storage device can be limited universally and flexibly through a file filter driving module, the method and the system take effect on the USB storage device, and other types of USB devices cannot be limited.
Owner:厦门天锐科技股份有限公司
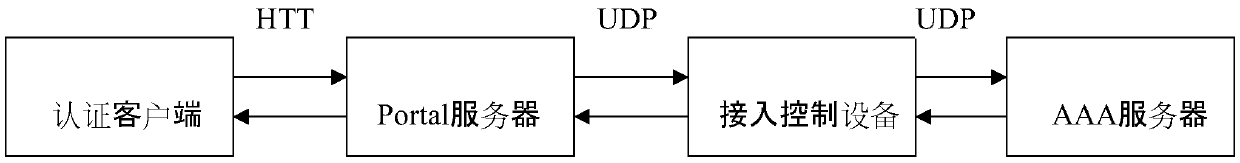
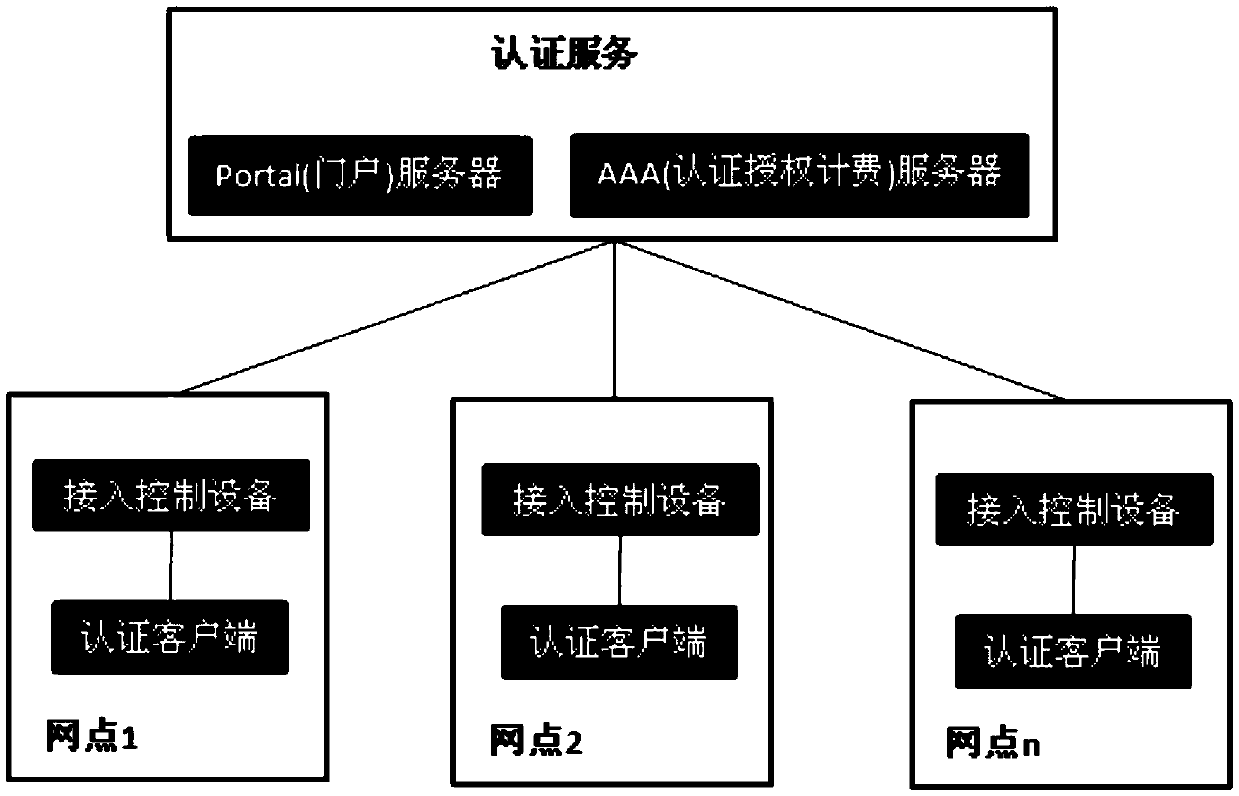
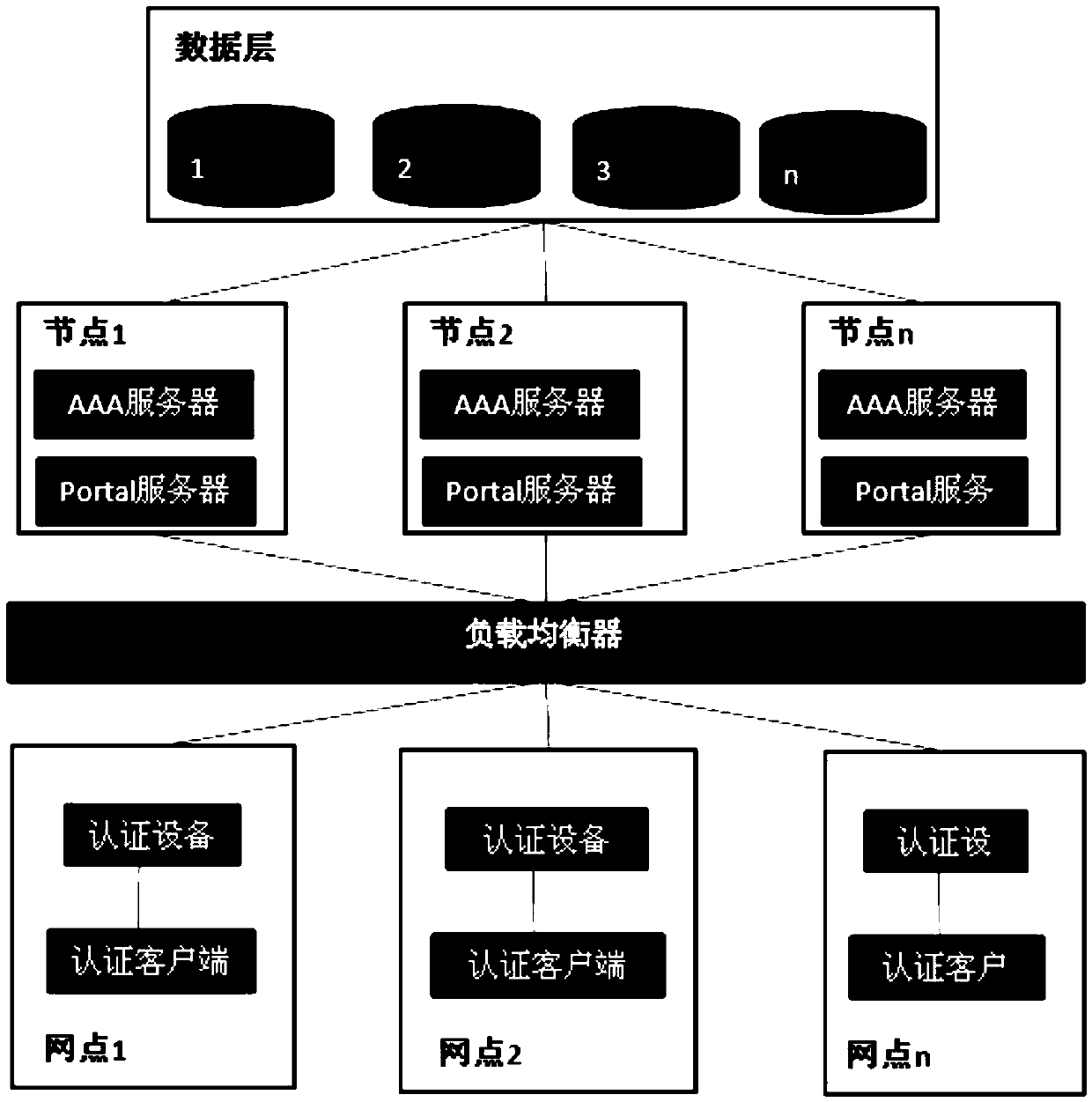
Authentication service cluster-based portal keep-alive system, method, authentication system and method
ActiveCN105516171ASolve the problem that it cannot be sent to the access control device normallyTransmissionIp addressCluster based
The invention relates to a WLAN security access technology and discloses an authentication service cluster-based portal keep-alive system, method, authentication system and method. The objective of the invention is to solve a problem that a portal message cannot be normally sent to access control equipment due to inconsistency of access control equipment keep-alive and load portal service nodes. The portal keep-alive system of the invention includes access control equipment which continuously sends keep-alive messages carrying equipment serial numbers to a load balancer through NAT equipment, the NAT equipment which performs NAT conversion on source IP addresses and source ports in the keep-alive messages, transmits converted IP addresses and ports to the load balancer, and stores mapping relations of the IP addresses and port numbers before and after conversion, the load balancer which balances the keep-alive messages onto a certain portal service node, and the portal service node which stores the equipment serial numbers, the IP addresses and port numbers after the NAT conversion, and the correlation relationship of the IP address of the portal service node which receives the keep-alive messages after receiving the keep-alive messages. The systems and methods of the invention are suitable for portal authentication in enterprise authentication service clusters.
Owner:MAIPU COMM TECH CO LTD
System, method and chip for hardware detection of illegal software user, computer system having hardware detection chip thereof and a software registration center
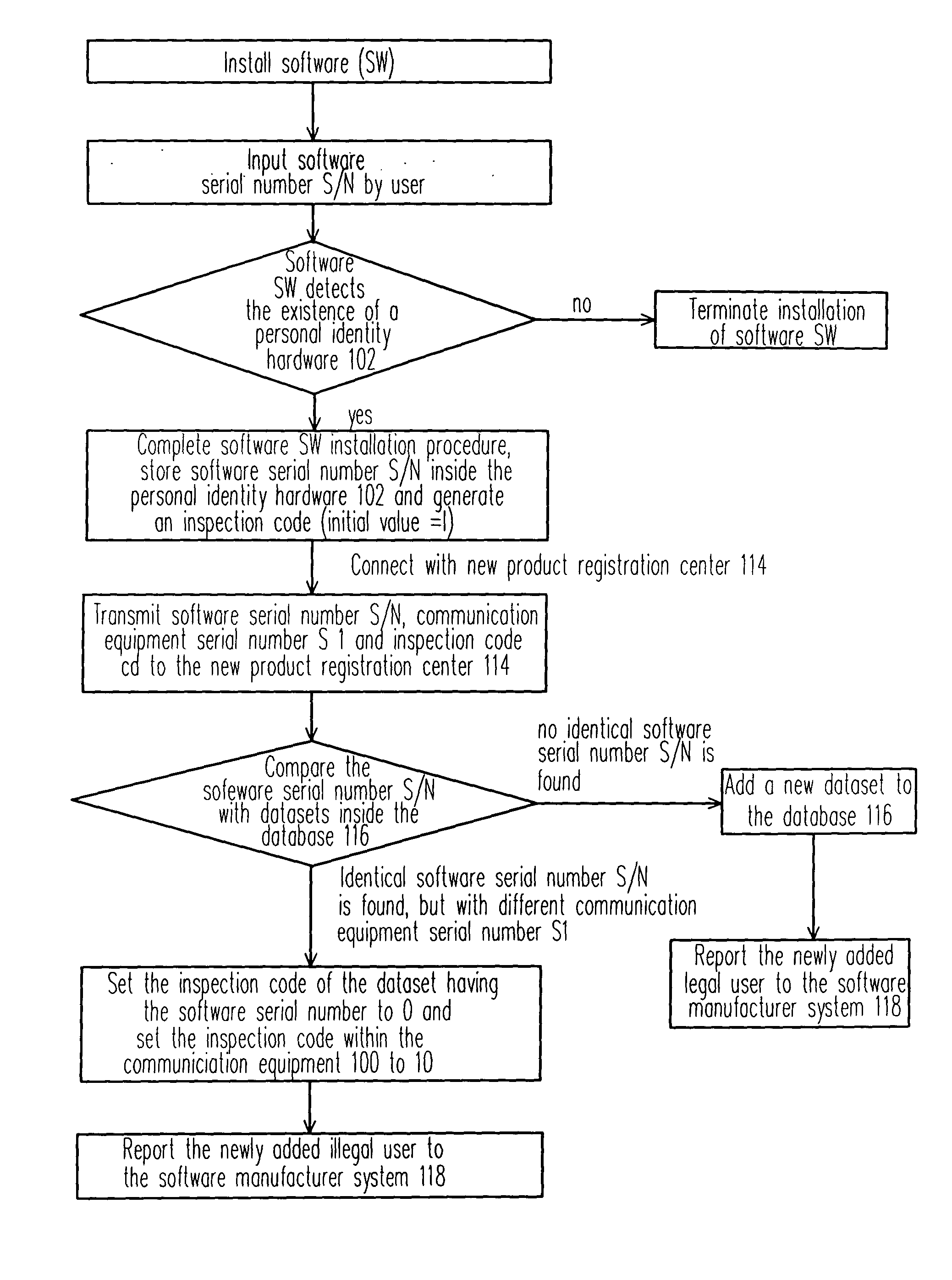
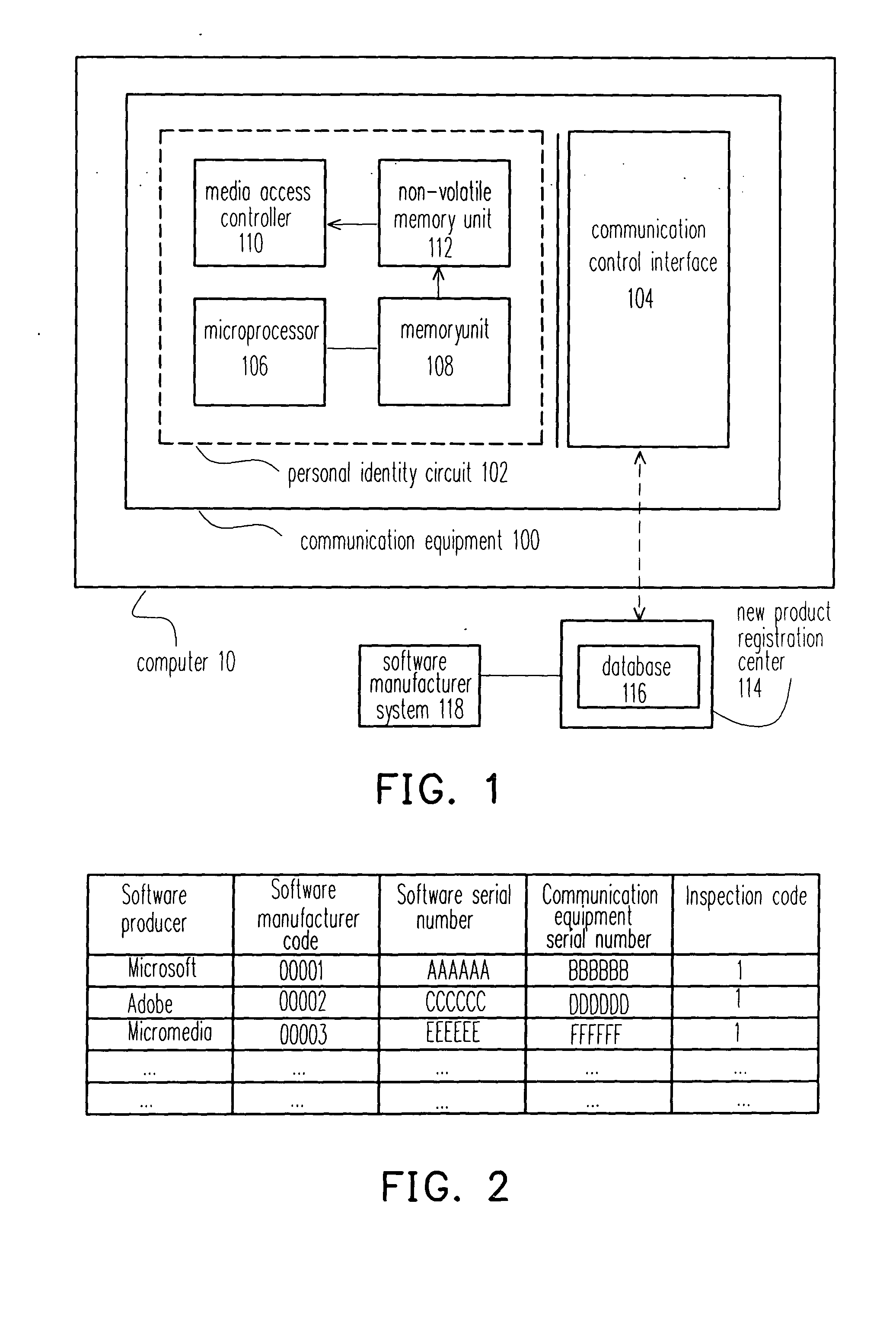
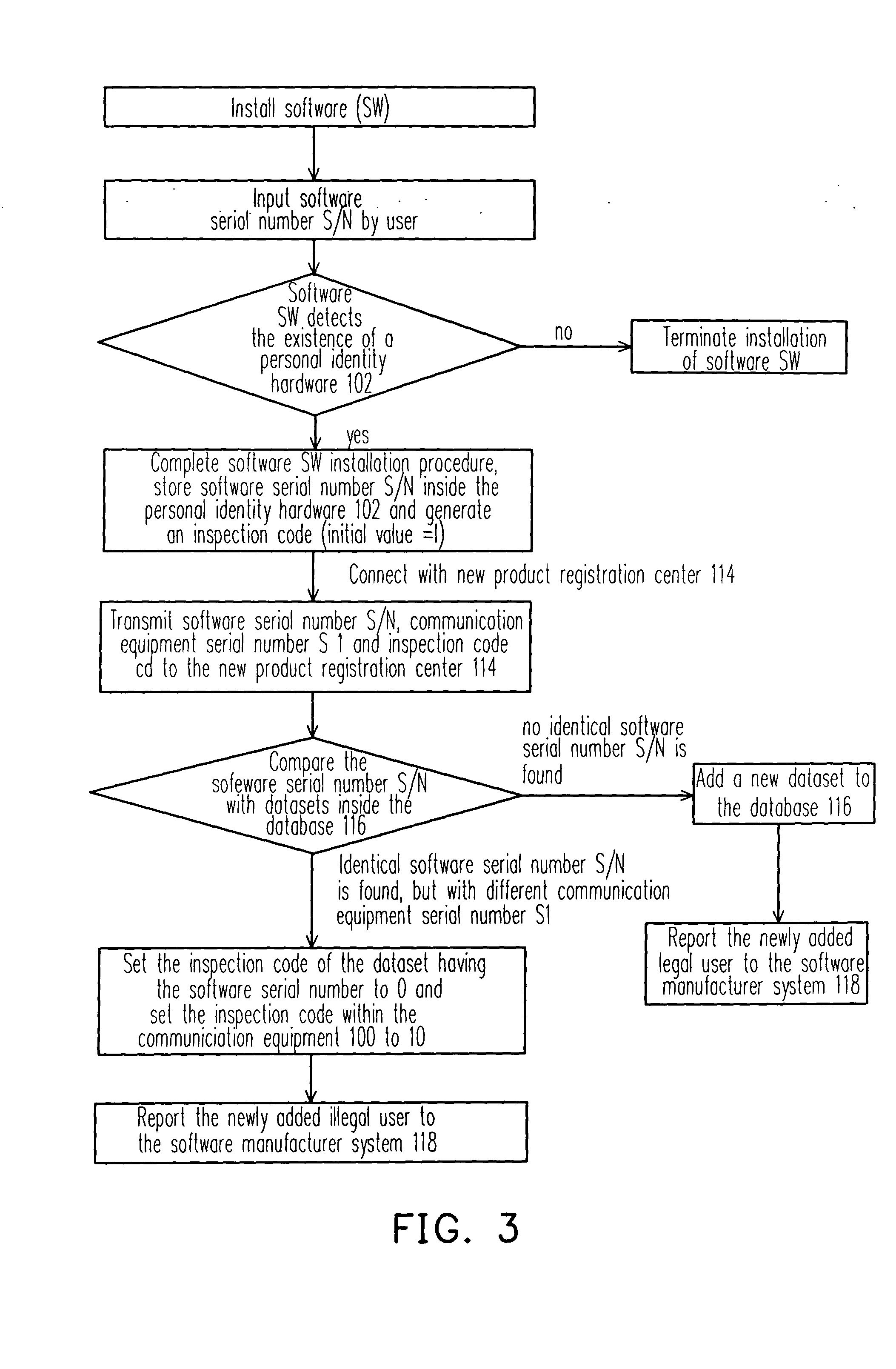
InactiveUS20050050347A1Prevent illegal useProtect intellectual propertyDigital data processing detailsAnalogue secracy/subscription systemsProtection systemComputer science
A software copyright protection system, method, chip and peripheral subsystem is provided. In one aspect of this invention, a smart security identity (SID) integrated circuit (IC) is used for registering a legal user. To become an authorized users of a particular software program, a software serial number and a communication equipment serial number must be submitted to the smart SID IC in a registration process to obtain a legal inspection code. The smart SID IC not only serves as a hardware serial number built-in module, but also reports to the software producer any illegal software registration attempts.
Owner:UNITED MICROELECTRONICS CORP
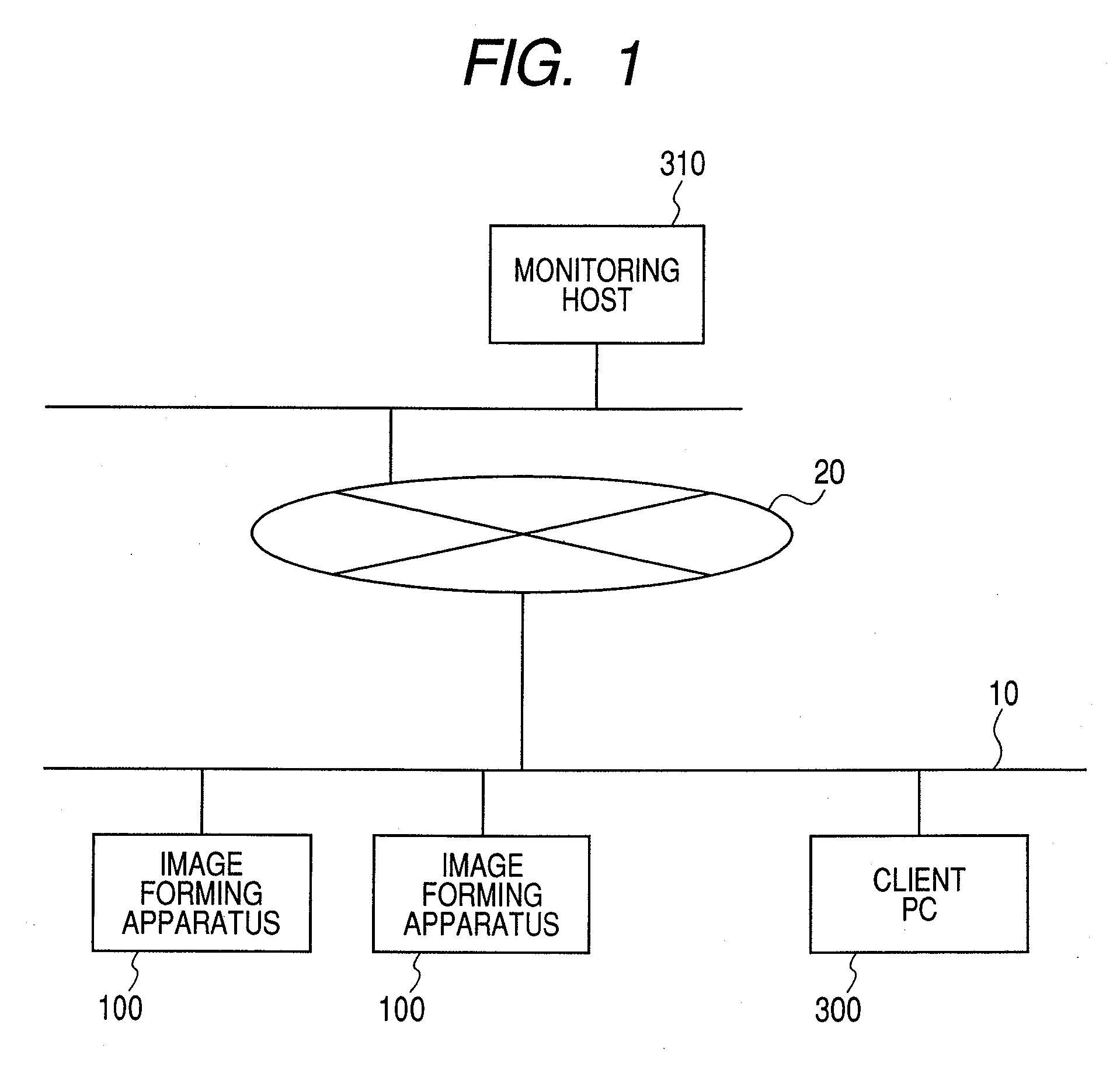
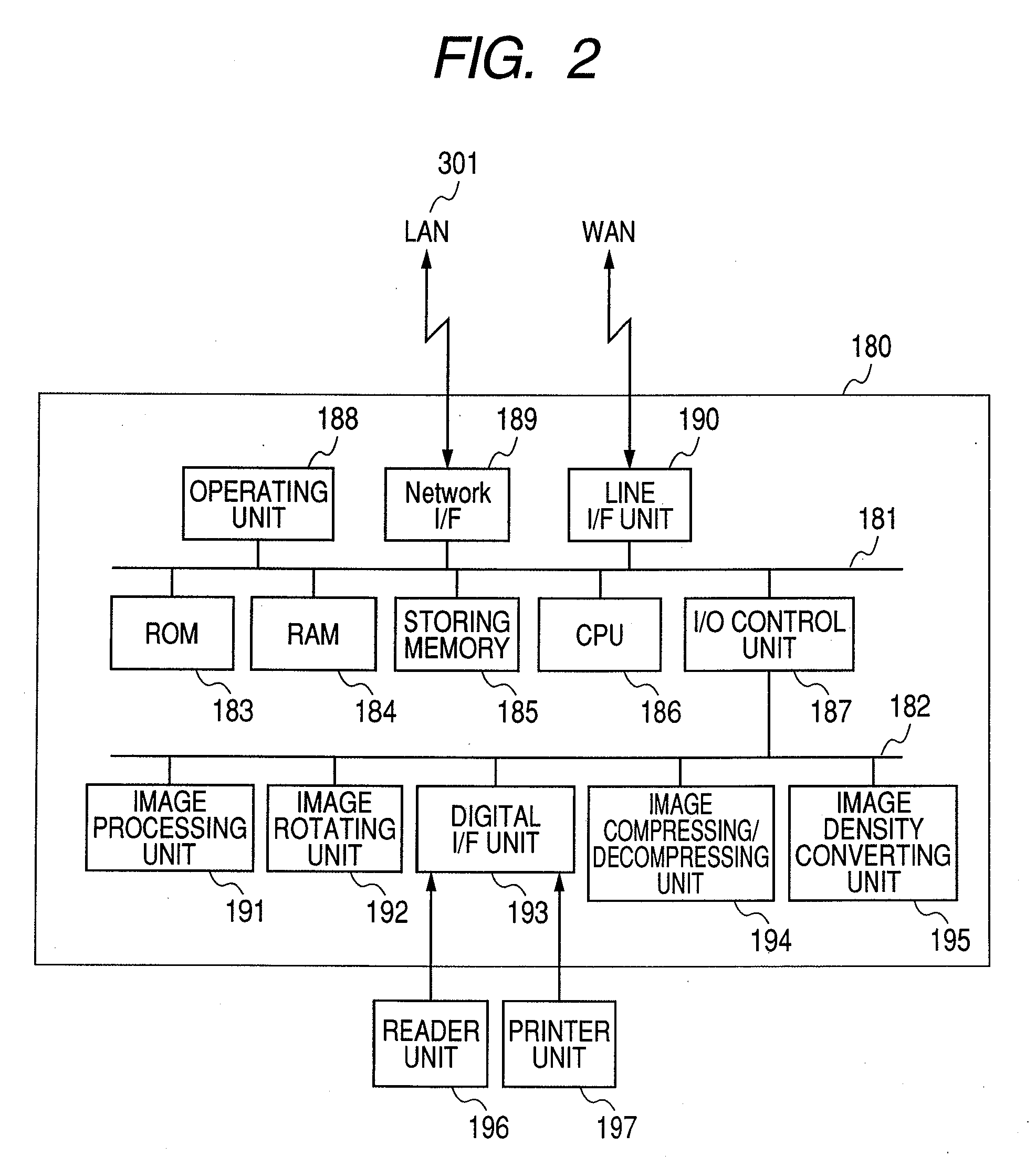
Monitoring host apparatus, image forming apparatus, and access control method for access to their web pages
InactiveUS20080155095A1Safety is assuredDigital computer detailsDigital data authenticationHardware structurePassword
The invention intends to realize access authentication by a simple method by an existing hardware construction while assuring a security when the user accesses a monitoring service display screen of a monitoring host from a client PC. In the invention, when a WEB page provided by a monitoring host apparatus is browsed from a WEB page for the administrator provided by an image forming apparatus, a device serial number of the image forming apparatus is used for the authentication, thereby omitting the authenticating operation using a log-in / account. Thus, a troublesomeness for the user or the administrator of the monitoring host to manage the log-in / account and a password can be omitted.
Owner:CANON KK
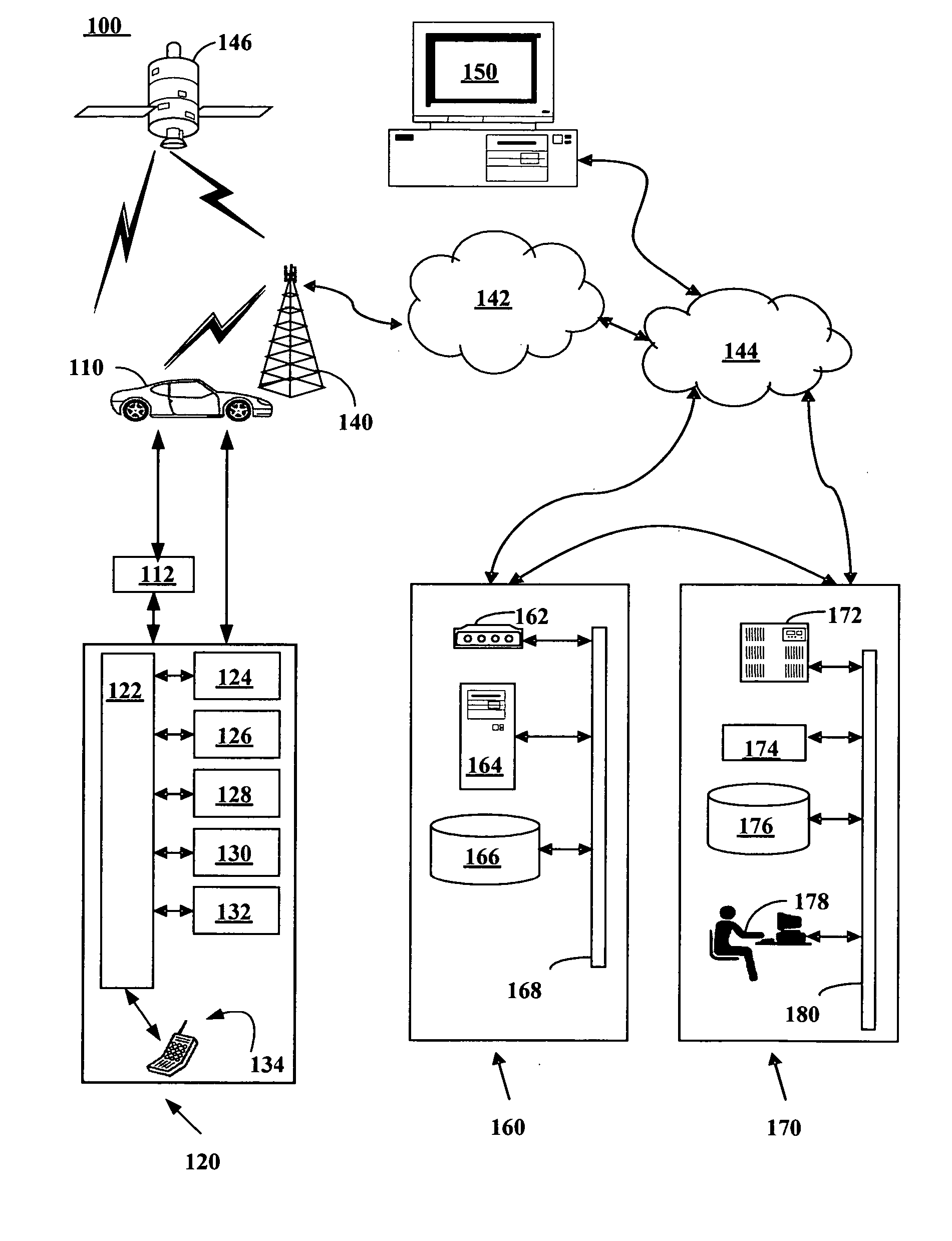
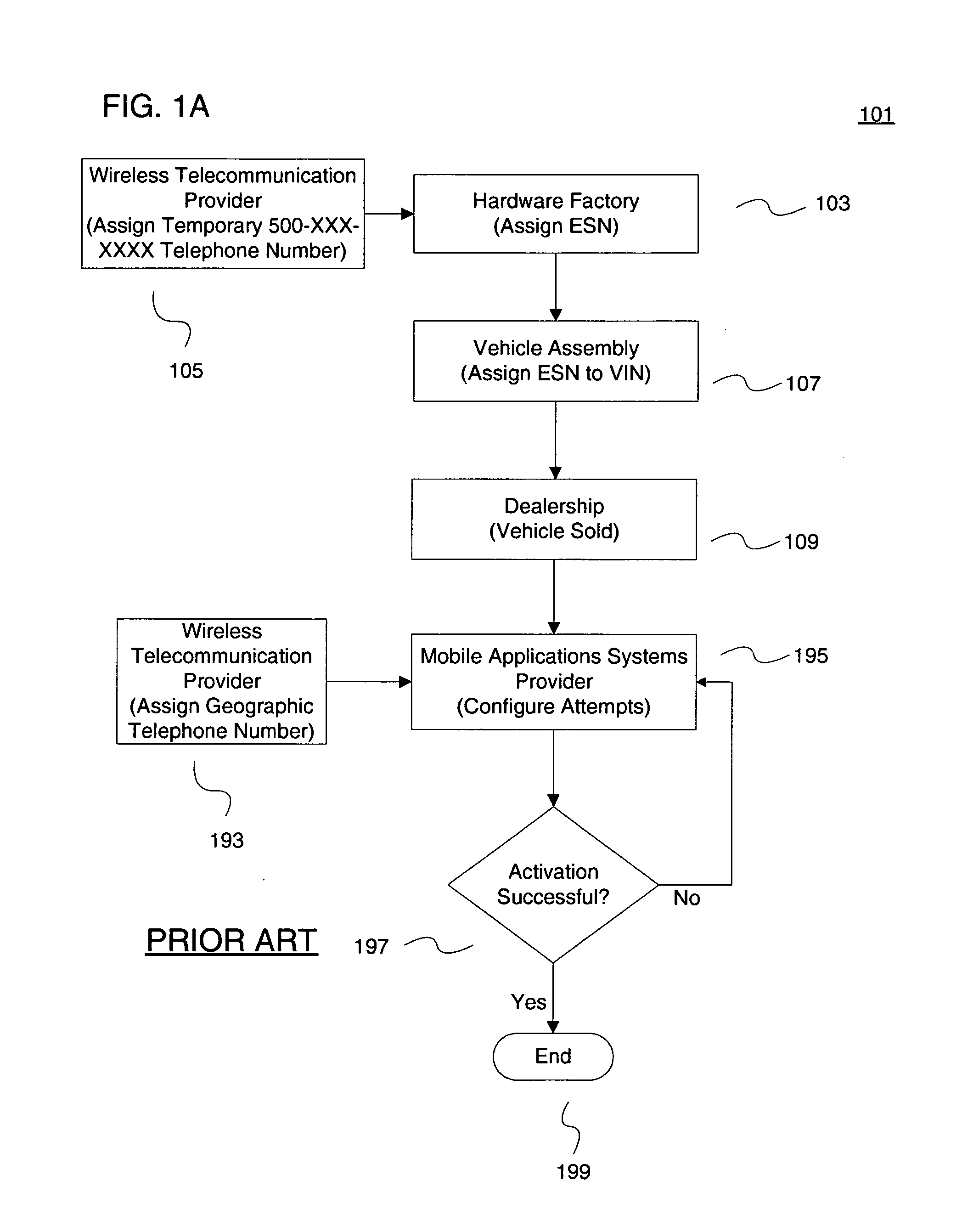
Method and system for routing toll-free calls to wireless devices
InactiveUS20070093250A1Special service for subscribersRadio/inductive link selection arrangementsMobile deviceComputer science
A method, computer readable medium and system for routing toll-free calls to wireless devices. One aspect of the invention provides a method, computer readable medium and system for receiving a non-translated telephone call at a wireless carrier including determining a serial number associated with the call based solely on a phone number associated with the call and routing the call from the wireless carrier to a mobile device based on the determination. Another aspect of the invention provides a method and computer readable medium for providing a communication number to the mobile device including receiving a non-geographic phone number, providing an equipment serial number unique to a mobile device, linking the phone number to the equipment serial number in a database, storing the phone number and equipment serial number to the mobile device and assigning the mobile device to a subscriber.
Owner:GENERAL MOTORS COMPANY
Equipment unlocking method and device, terminal equipment and medium
InactiveCN109150509ASimplify tedious stepsReduce maintenance costsKey distribution for secure communicationIndividual entry/exit registersGraphicsTerminal equipment
The invention discloses an equipment unlocking method and device, terminal equipment and a medium and belongs to the technical field of computers. The method comprises a step of outputting a graphic authentication code generated based on a random number and a lock equipment serial number, a step of receiving verification information returned by a terminal based on a scanned graphic authenticationcode, wherein the verification information is obtained by encrypting a private key pair random number set based on a corresponding lock equipment serial number, a terminal serial number and a number of unlocking times, a step of decrypting the verification information by using a stored public key to obtain the random number, the terminal serial number and the number of unlocking times, and a stepof carrying out information verification based on the random number, the terminal serial number and the number of unlocking times included in the verification information, and executing an unlocking operation when the verification is successful. In this way, remote data processing by a server is not required, the cumbersome steps of the information verification are simplified, and the maintenancecost of equipment unlocking is reduced.
Owner:BEIJING HAITAI FANGYUAN HIGH TECH
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com