Patents
Literature
166results about How to "Safety is assured" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Method and apparatus using geographical position and universal time determination means to provide authenticated, secure, on-line communication between remote gaming locations
InactiveUSRE39644E1Facilitates denialAccurately determineSecret communicationApparatus for meter-controlled dispensingGeolocationThe Internet
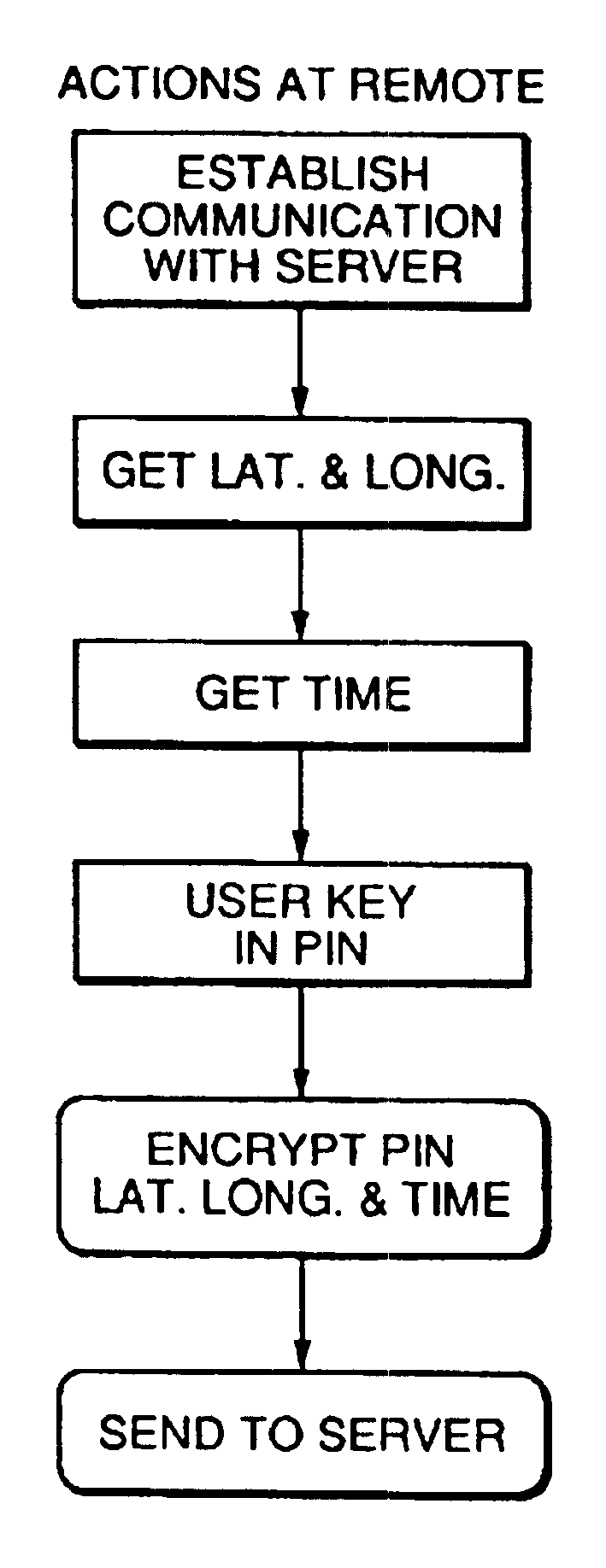
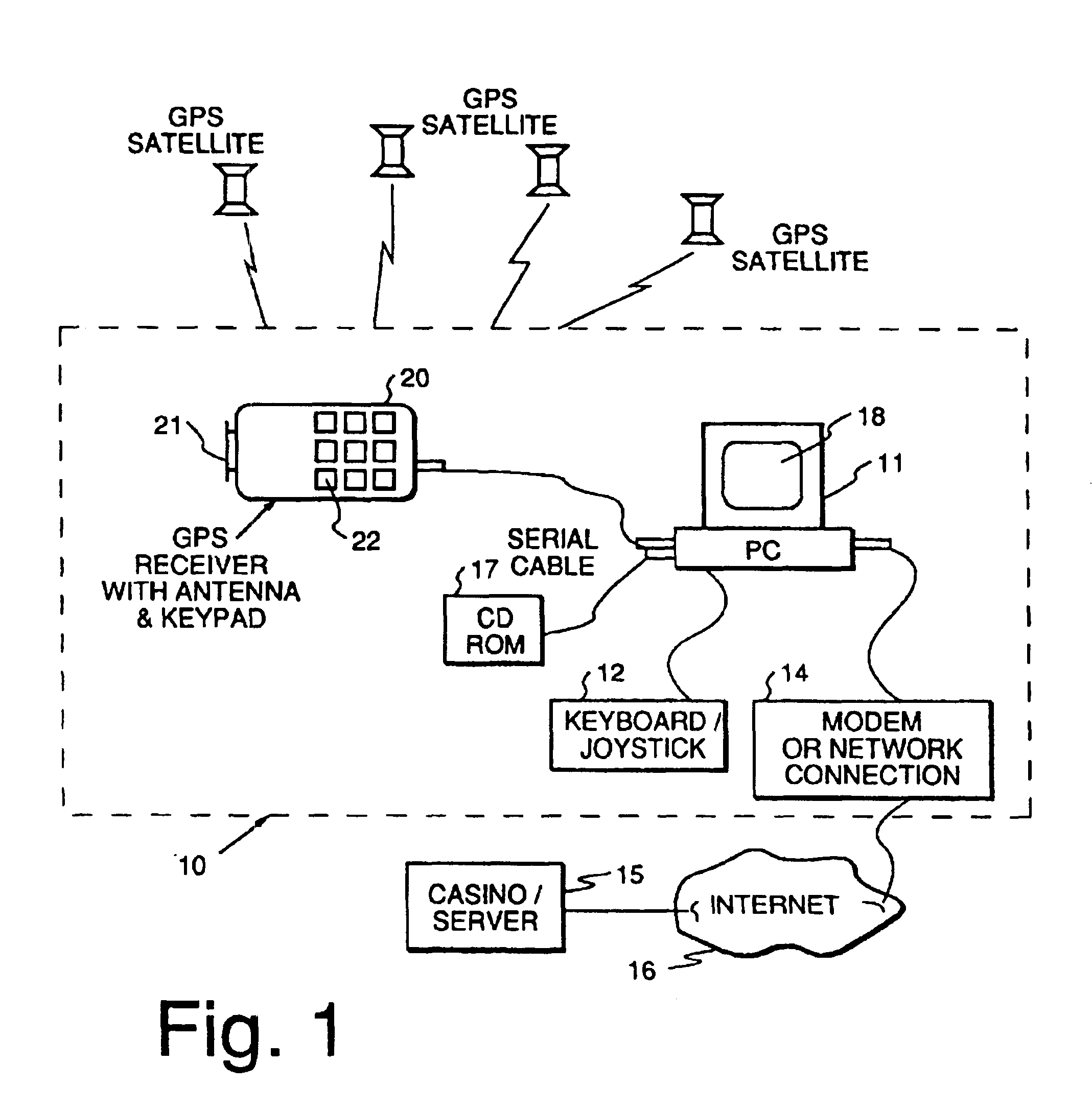
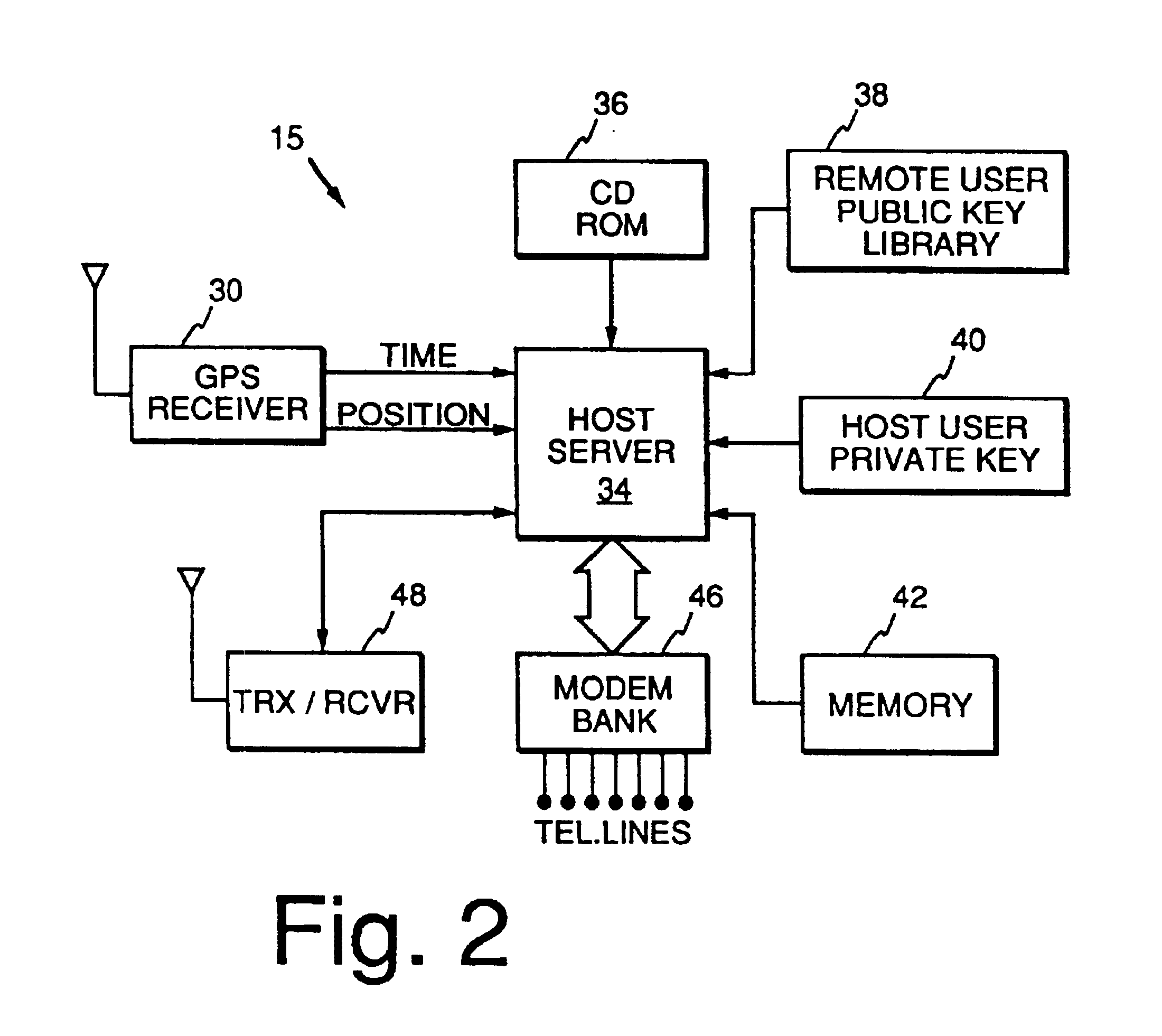
Method and apparatus for providing authenticated, secure, on-line communication between remote locations including a user terminal adapted to enable a player in one location to remotely communicate via a communications medium such as the Internet with a gaming host in another location. Location of the remote user terminal, the host server and universal time are determined using means for accessing signals generated by geostationary navigational transmitters, such as in the global positioning satellite (GPS) system. Player authentication (identity verification) is determined by use of a personal identification number (PIN) and an electronic signature verification service. Security of communication is accomplished through use of a public-key / private-key encryption system. The remote user terminal may be comprised of one or more discreet components adapted to be used with a laptop or desktop personal computer (PC), or may be embodied in a stand alone or self-contained single unit that is portable and communicates via radio waves, telephone lines or the Internet to a host server.
Owner:IGT
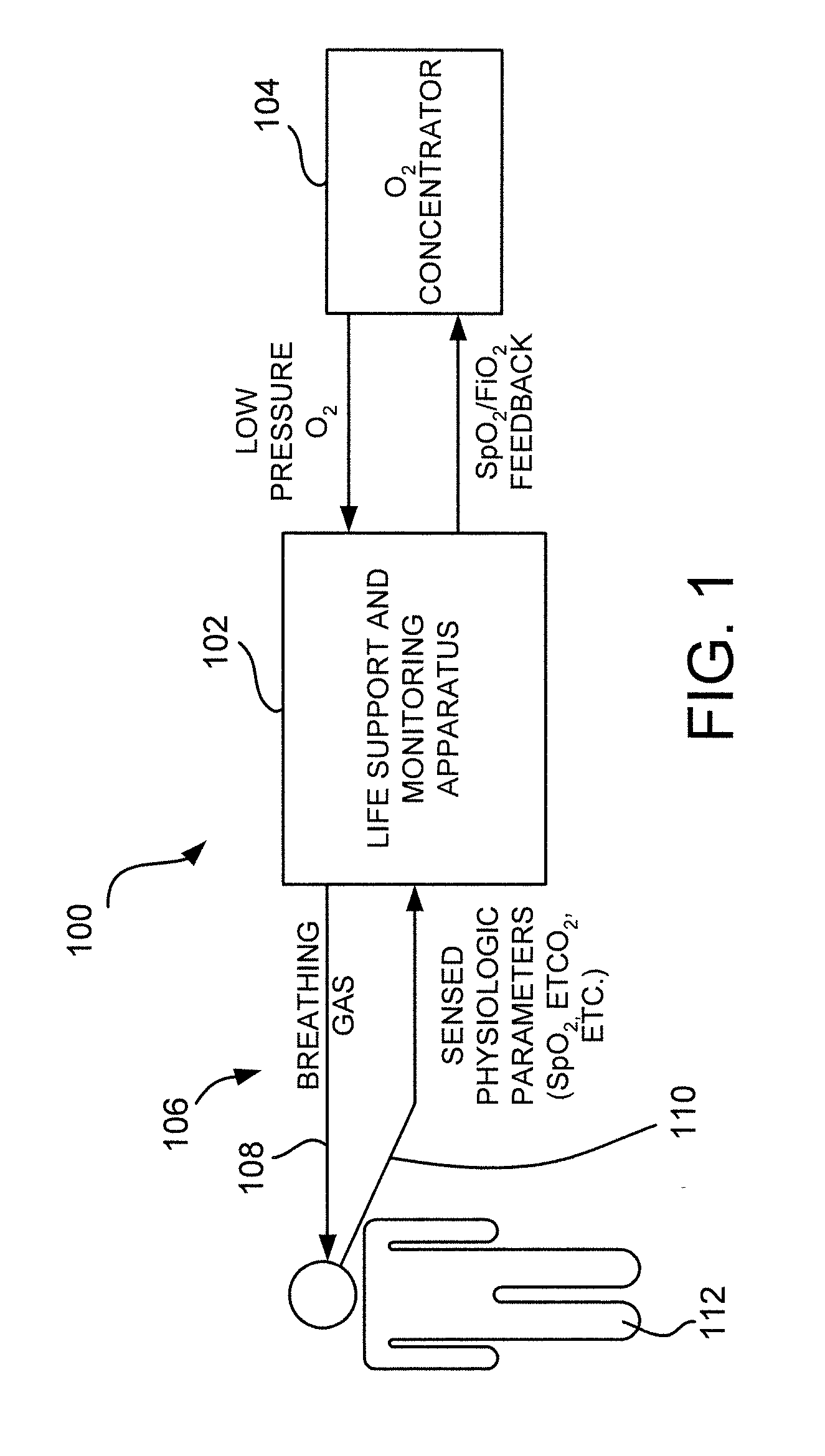
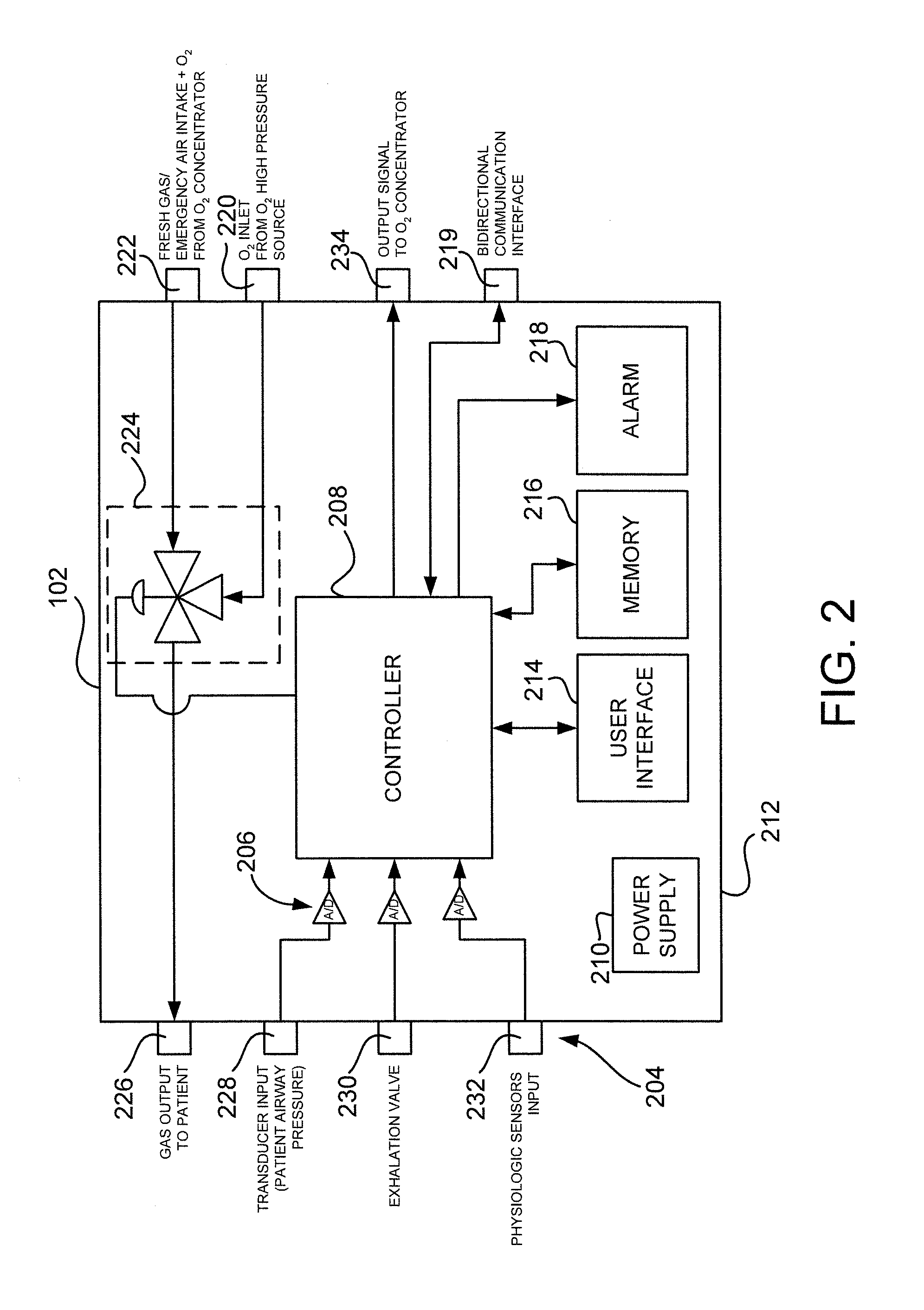
Life support and monitoring apparatus with malfunction correction guidance
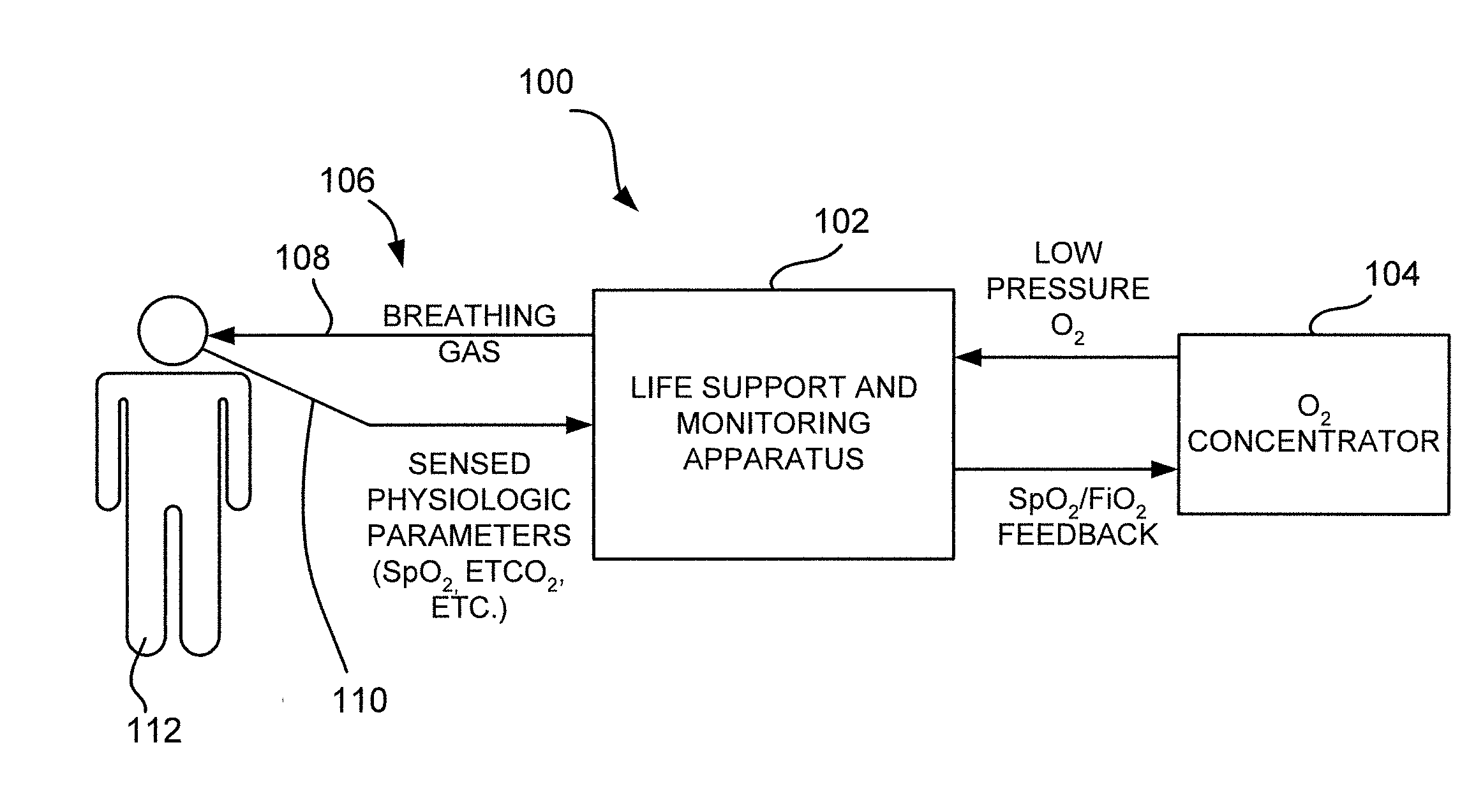
ActiveUS20100292544A1Safety is assuredRespiratorsOperating means/releasing devices for valvesBasic life supportRoot cause
A life support and monitoring apparatus with malfunction correction guidance is provided. The life support and monitoring apparatus of the present disclosure identifies the root cause or potential cause of a fault / failure and then prompts an operator to take appropriate steps to assure the continuance of life support and critical physiologic monitoring. When multiple faults / failures exist, the apparatus automatically prioritizes them based on risk to the patient and prompts the operator to do the most appropriate intervention to assure patient safety.
Owner:ZOLL MEDICAL CORPORATION
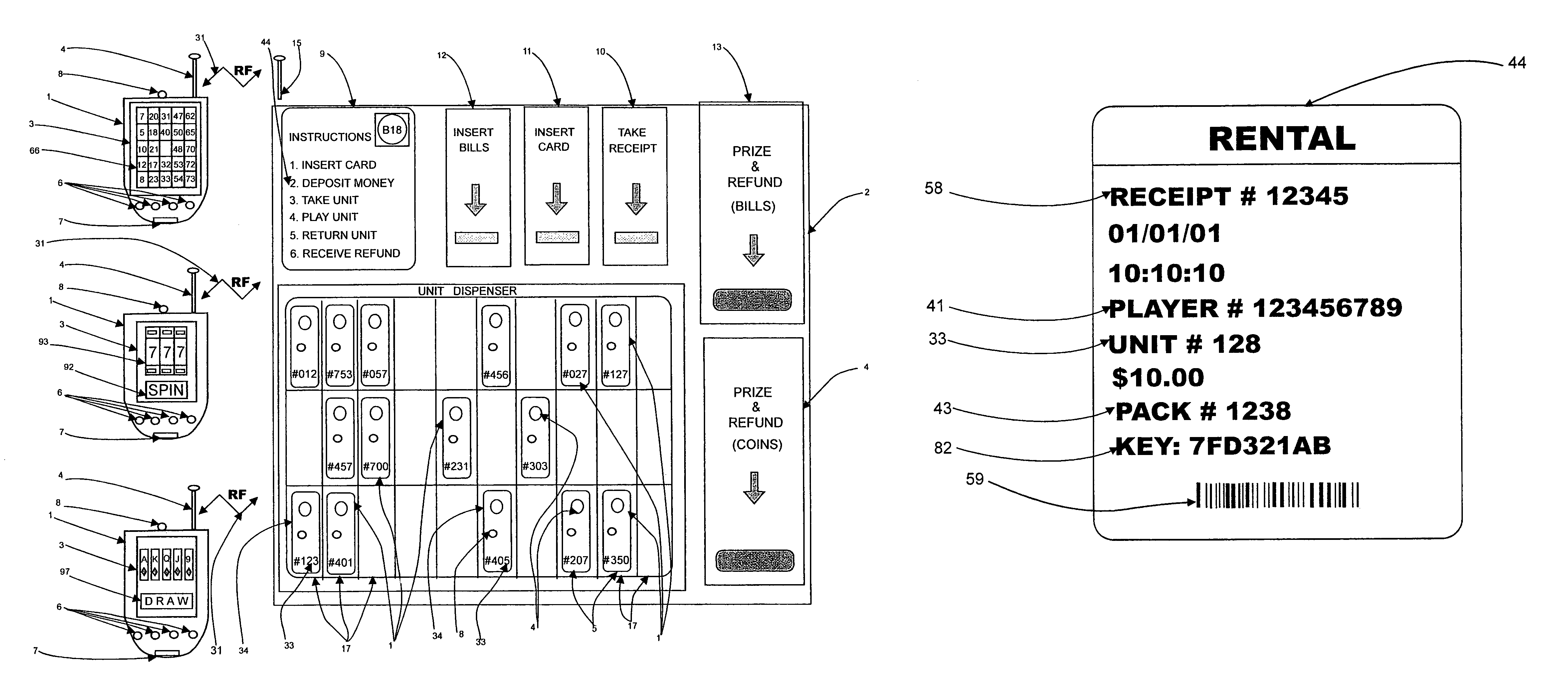
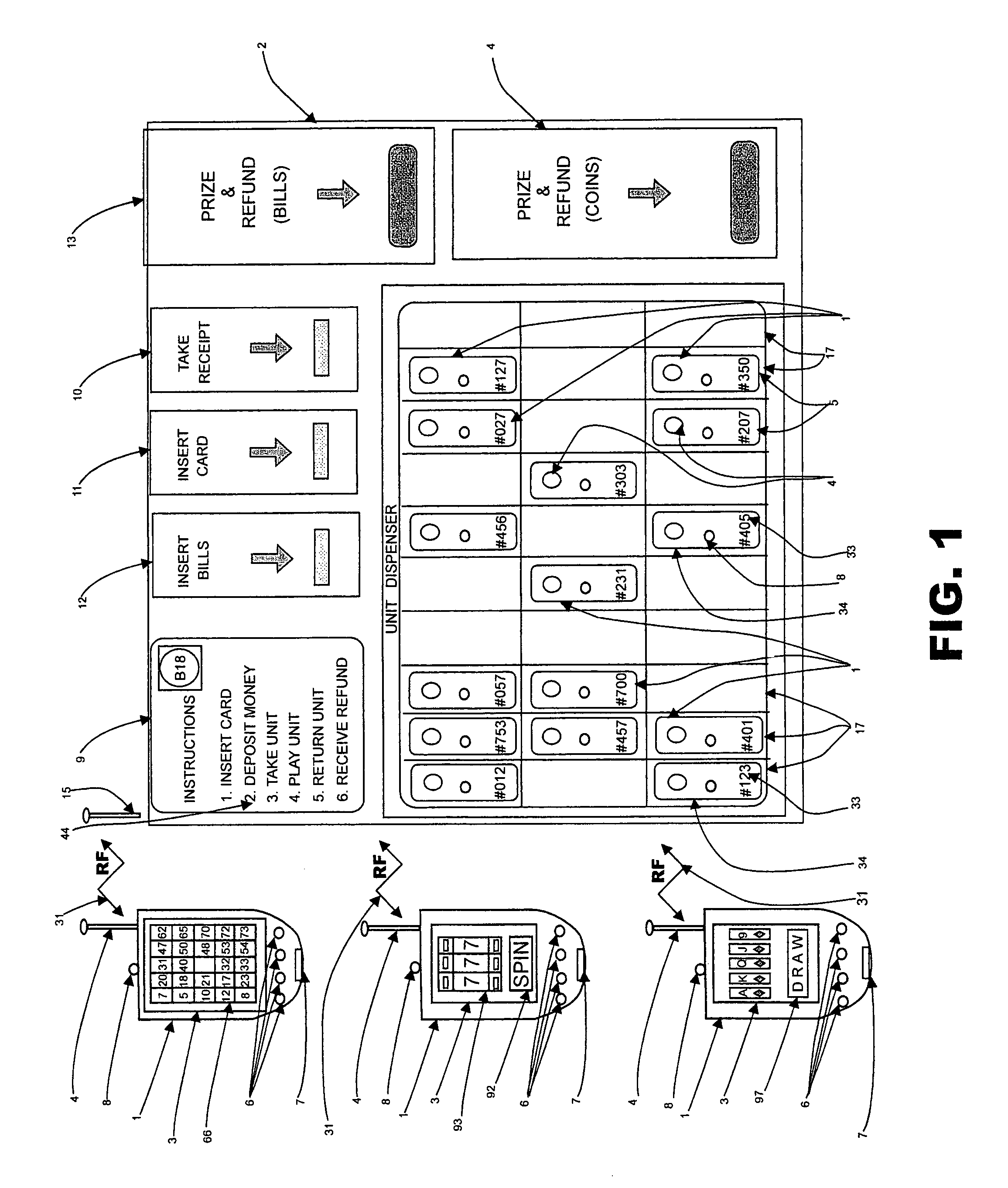
Wireless wagering system
InactiveUS7611407B1Automate processingReduce labor costsBoard gamesCard gamesWired communicationRadio channel
A casino game is implemented on the basis of a wireless mobile player unit adapted to play poker, slots, bingo and other casino games. The unit obtains random game outcomes from a central computer over a radio channel utilizing a data encryption technique relying on an authentication key. The authentication key is downloaded into the unit from the central computer via a secure wired communication channel while the unit is stored, recharged and locked in a dispensing kiosk controlled by the central computer. A player rents the unit from the kiosk, plays it throughout the casino and returns the unit to the kiosk to obtain prizes and / or bonus points earned. The central computer tracks the inventory of the units in the kiosk and on the casino floor.
Owner:FORTUNET
Optical Power Beaming to Electrically Powered Devices
InactiveUS20100012819A1Reduce reflectionAvoid possible injuryPhotometry using reference valueElectromagnetic wave systemHot zoneOptical power
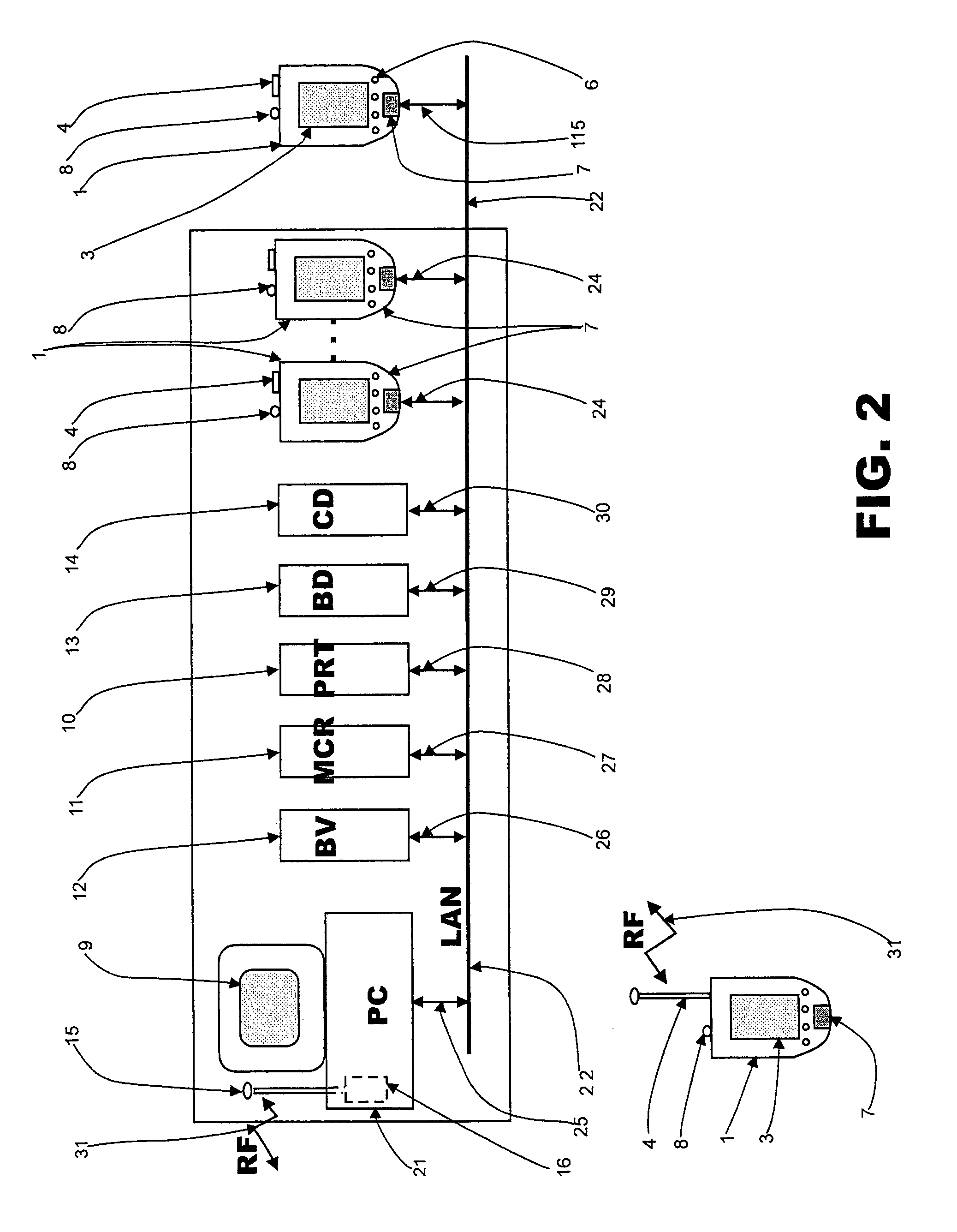
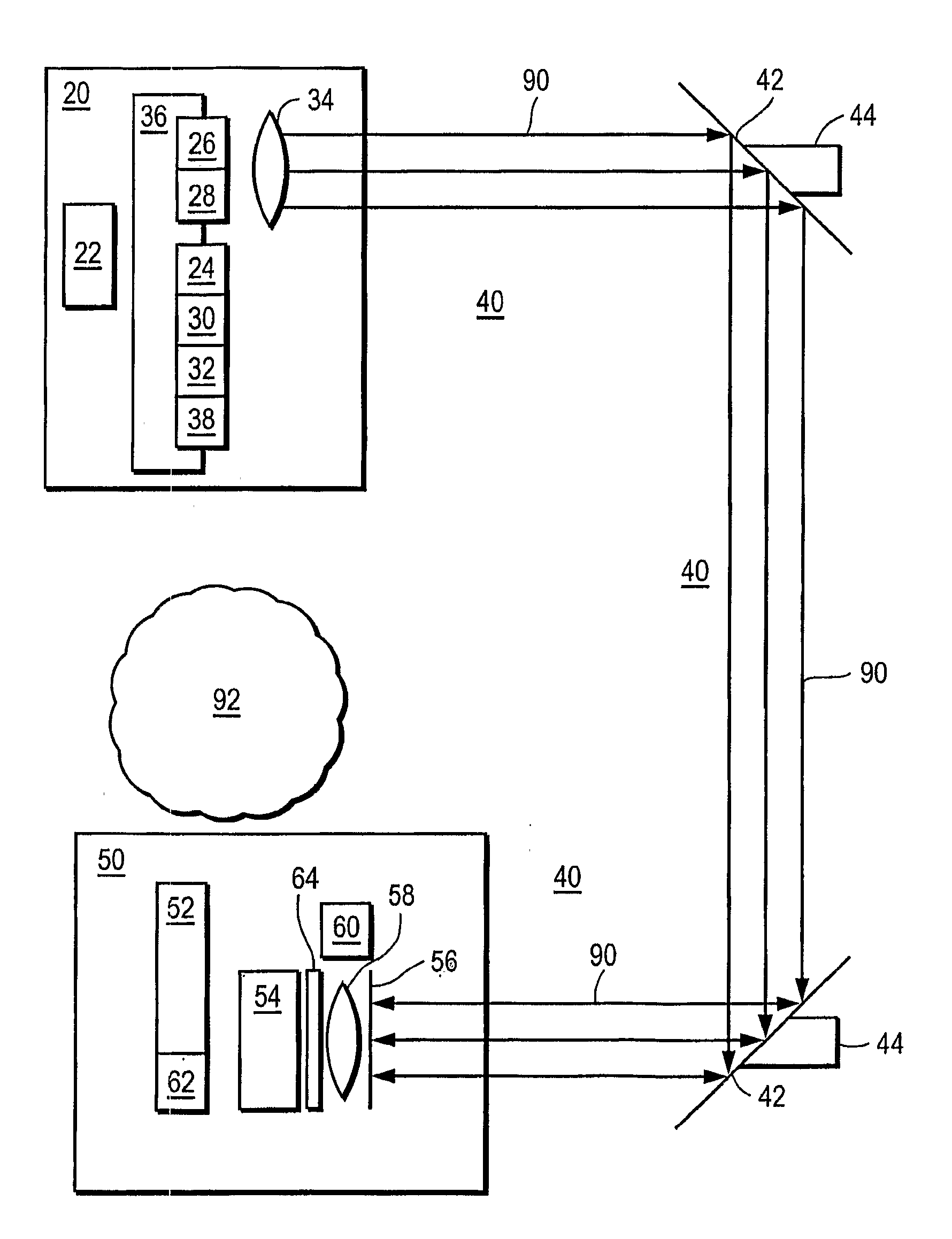
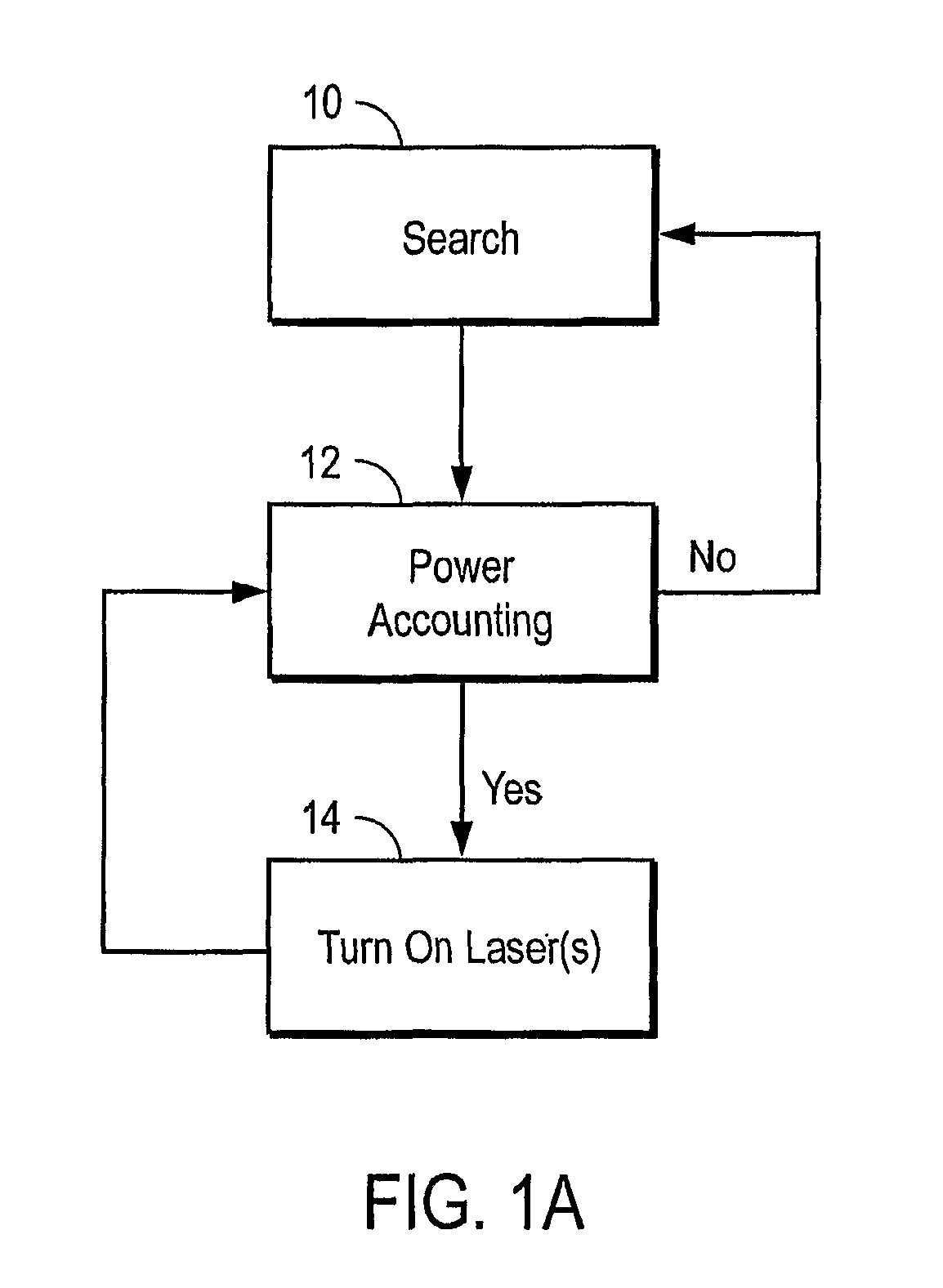
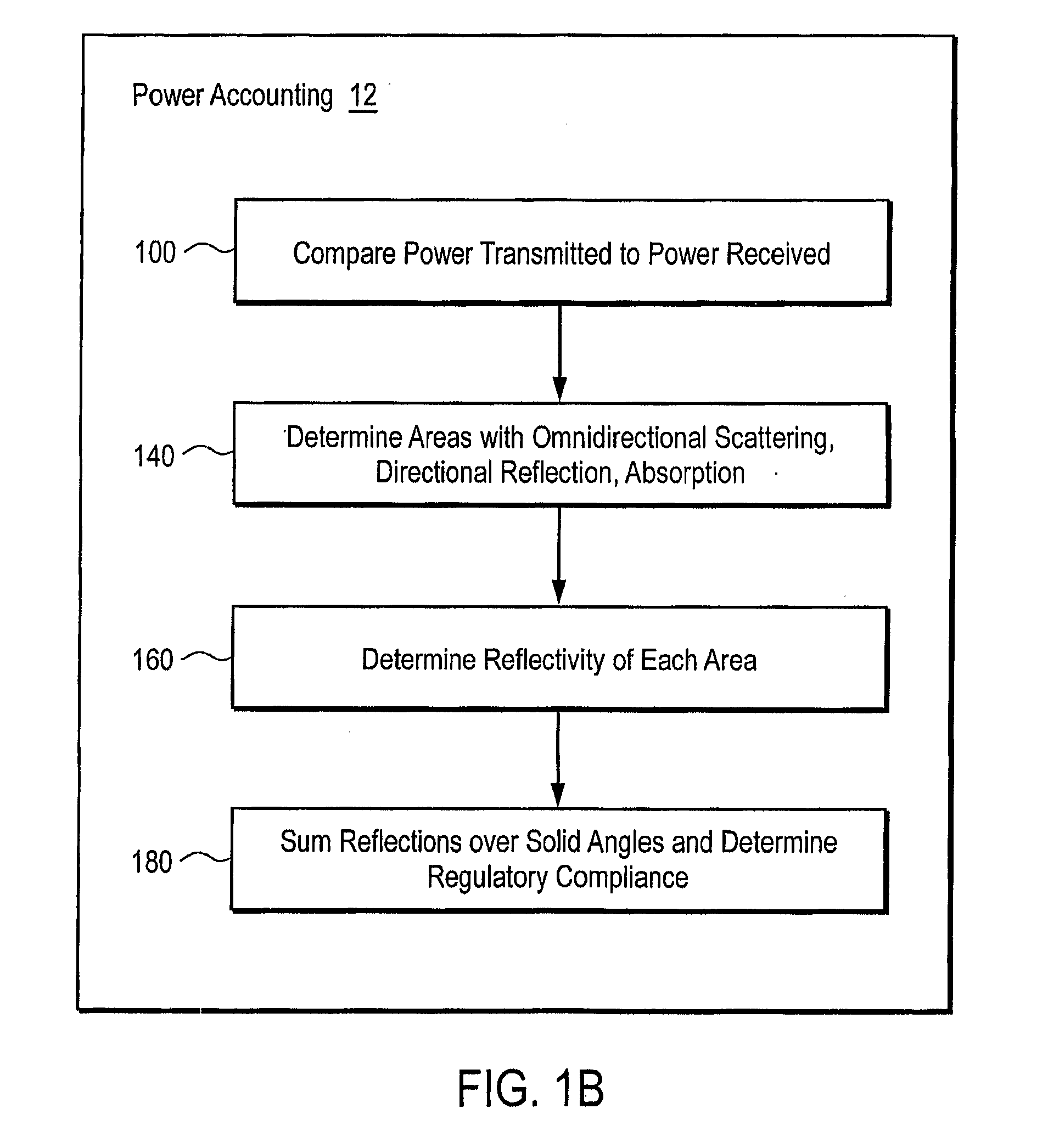
In one embodiment, a transmitter assembly containing a light source is electrically powered. The light source receives electrical power and converts the electrical power to an optical power beam that is directed through free space to an optical-to-elect power converter for a device. The optical-to-electric power converter converts the optical power beam to electrical form, thus providing electrical power to a device. A safety subsystem assures that the emission beyond the hot zone between the transmitter and receiver do not exceed regulatory levels.
Owner:GRAHAM DAVID S
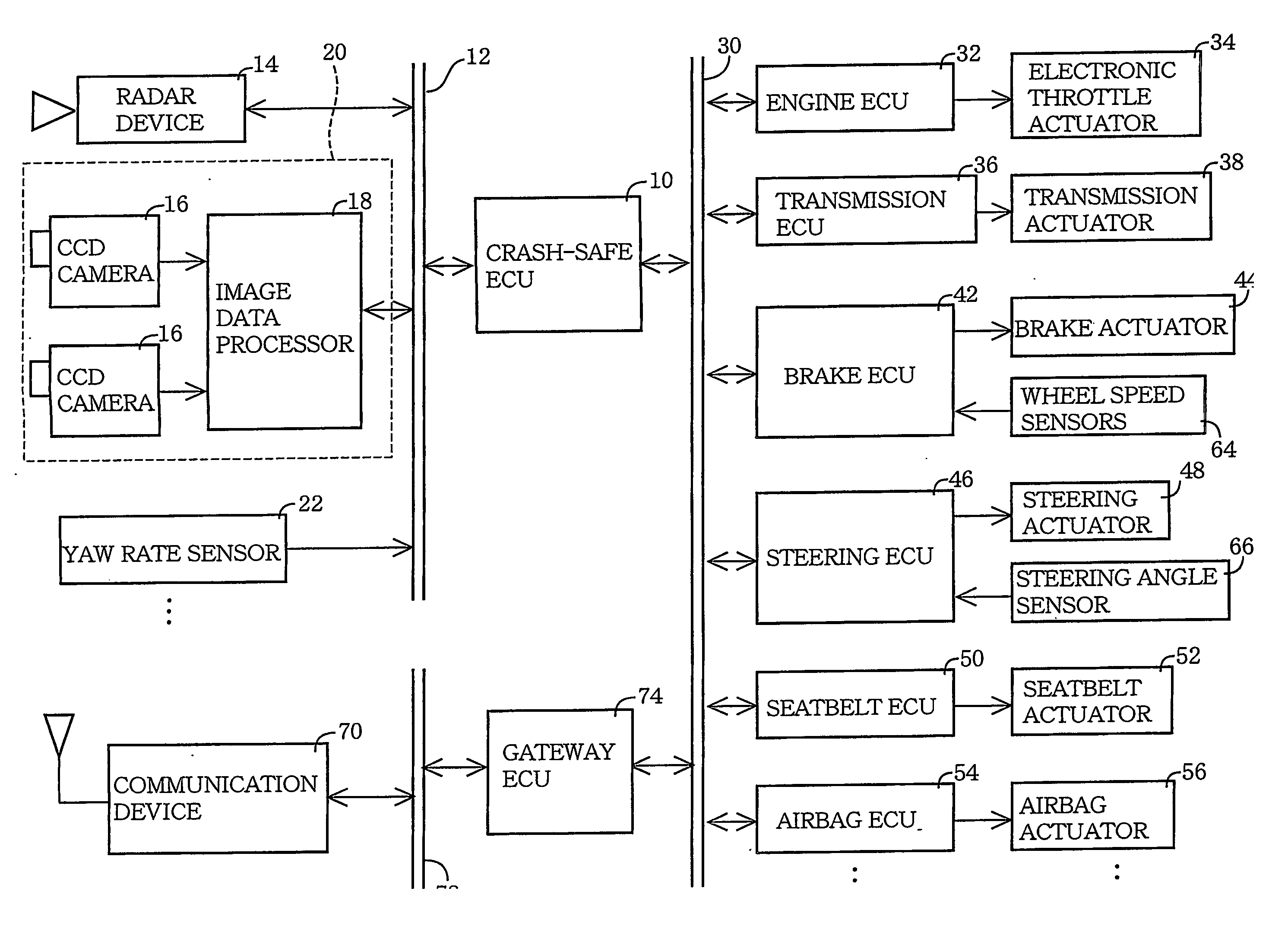
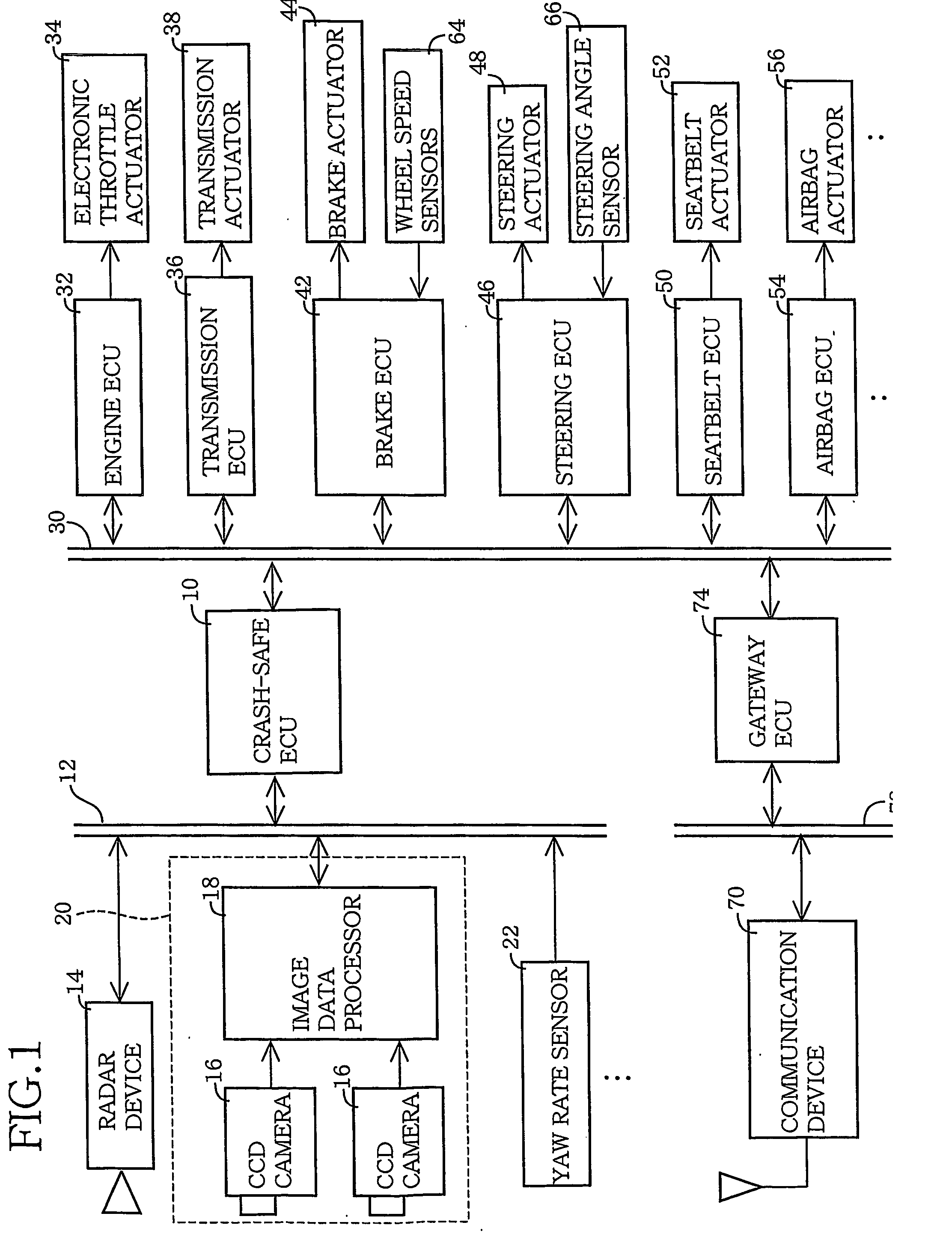
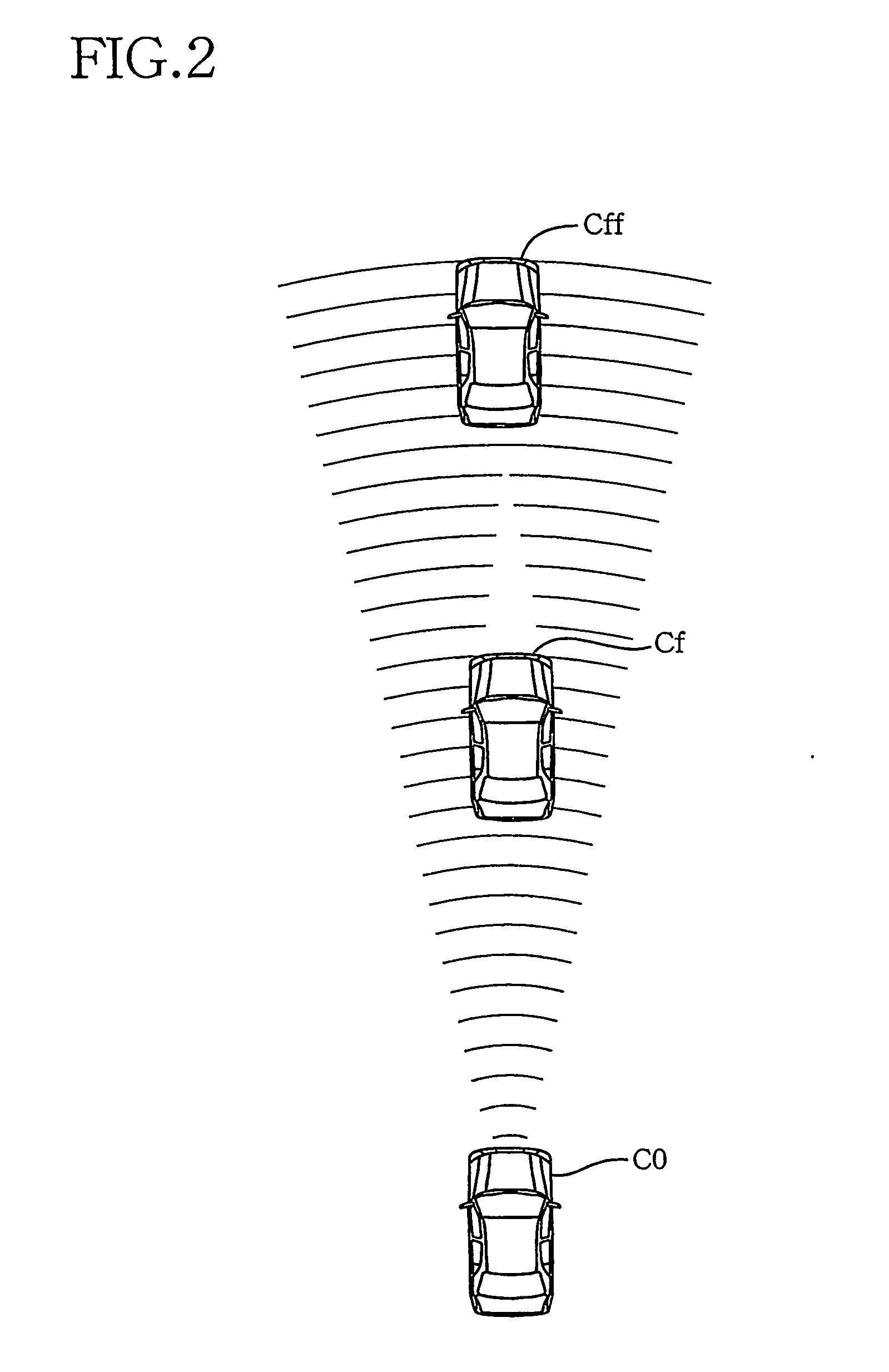
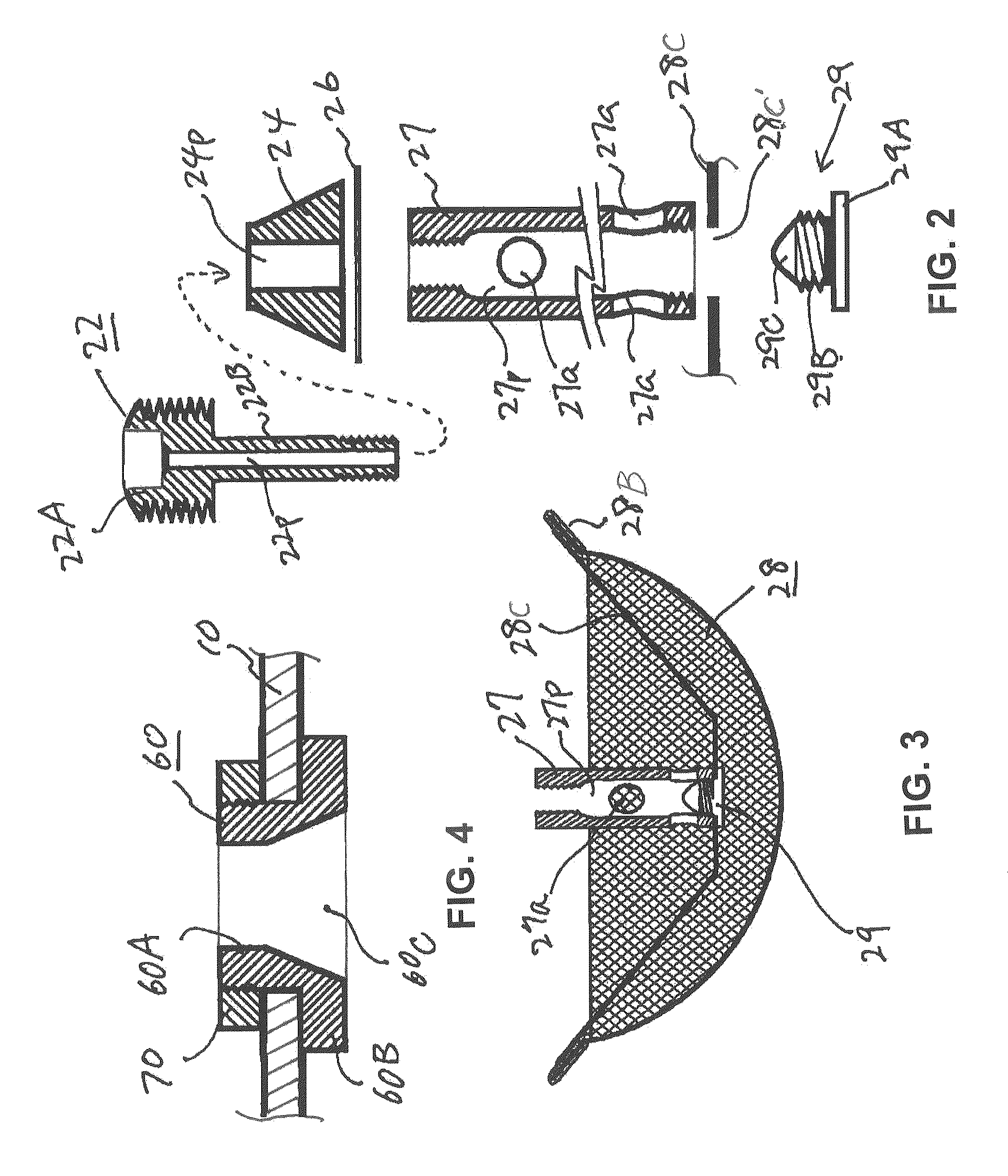
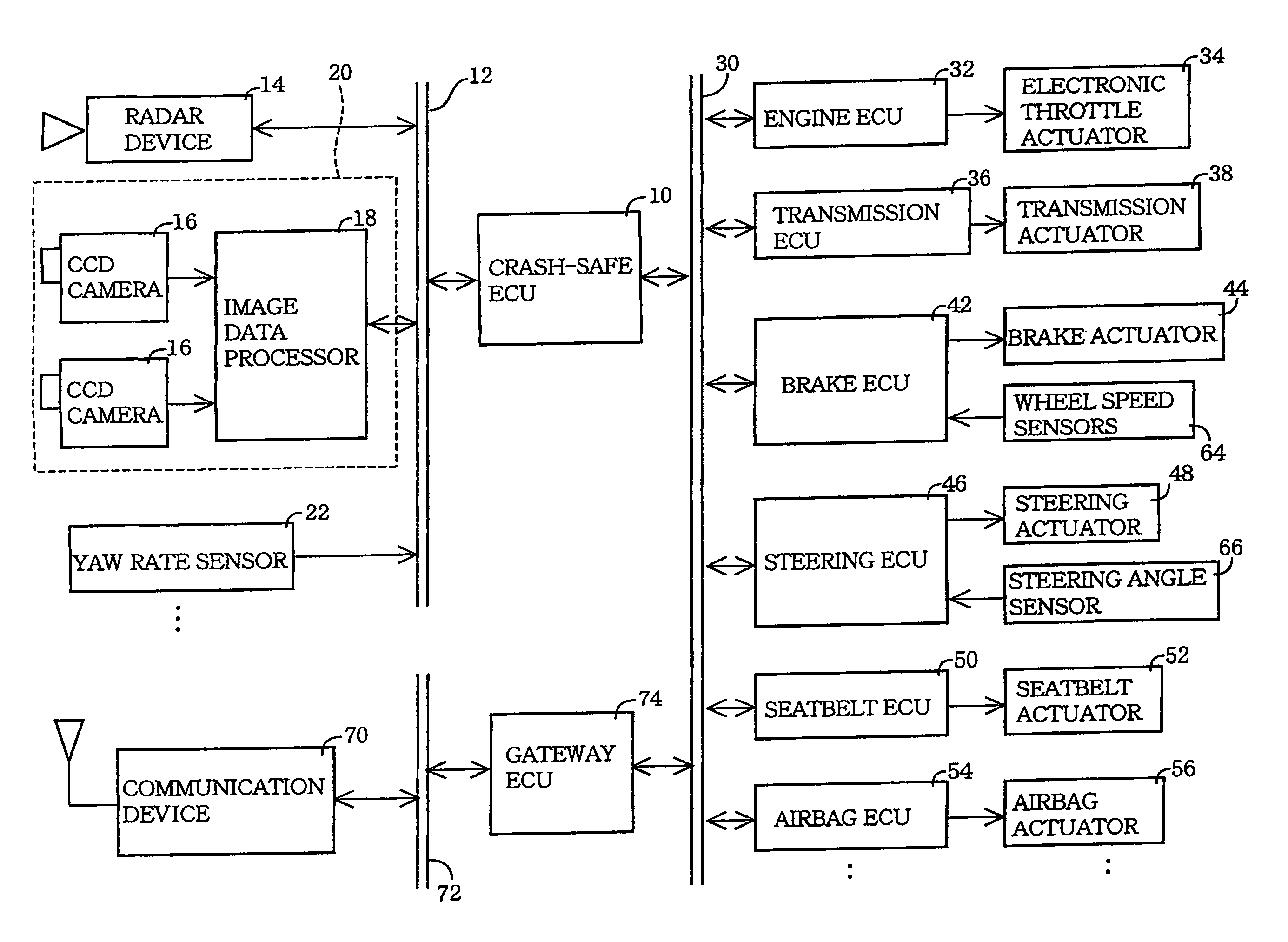
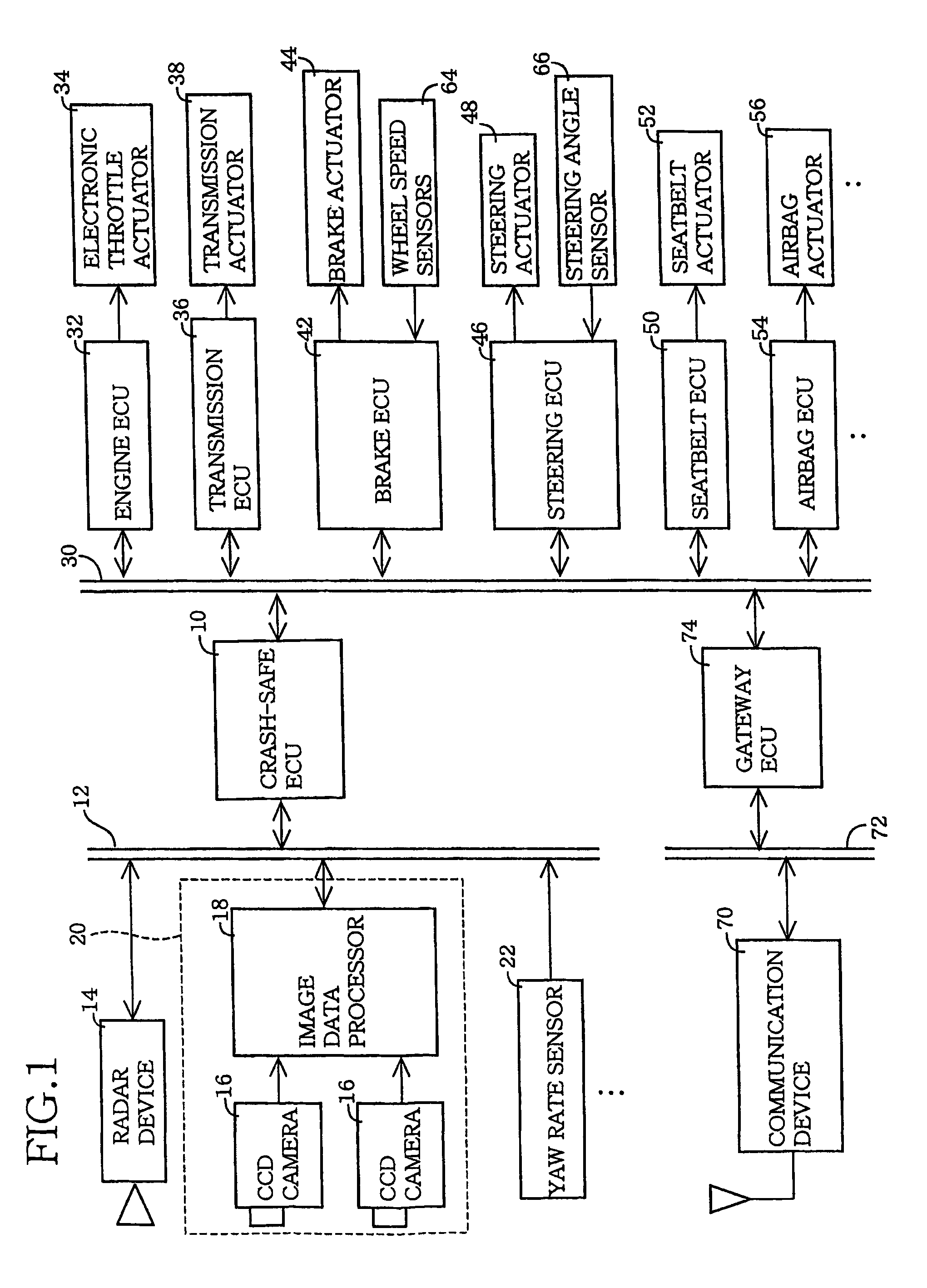
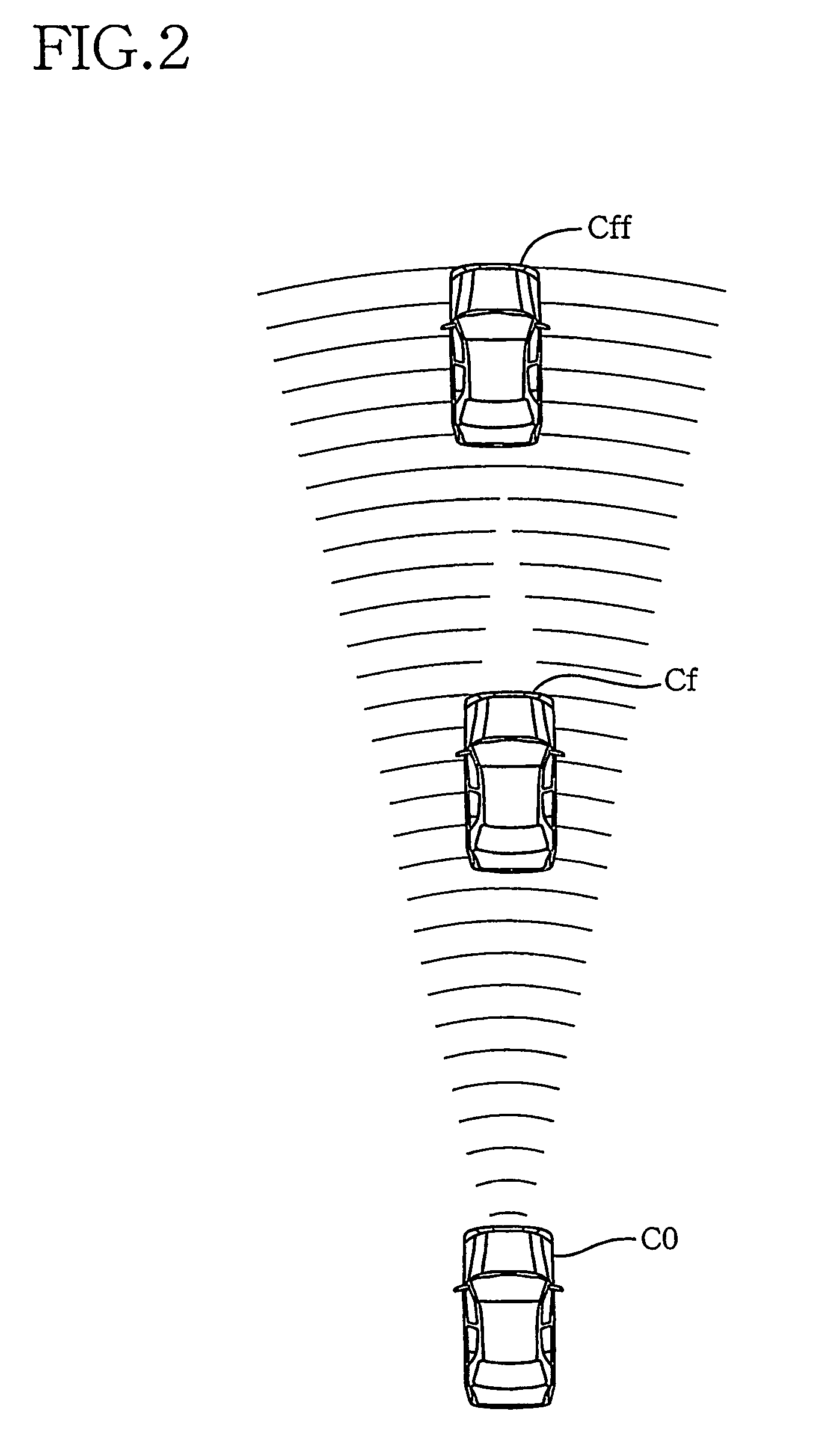
Crash-safe vehicle control system
InactiveUS20060155469A1Safety is assuredAccurate identificationDigital data processing detailsPedestrian/occupant safety arrangementRelevant informationControl system
A crash-safe vehicle control system for controlling operating devices of an own vehicle such as a vehicle decelerating device and an occupant protecting device, on the basis of information on at least one preceding object existing in front of the own vehicle. The vehicle control system is arranged to effect at least one of a non-first-preceding-object-information-dependent control and a width-related-information-dependent control. The non-first-preceding-object-information-dependent control is a control of the operating devices on the basis of non-first-preceding-object information detected by the present system per se, in the presence of a high possibility of crashing of the own vehicle with a first preceding vehicle existing immediately in front of the own vehicle. The non-first-preceding-object information relates to at least one non-first preceding object each existing in front of the first preceding vehicle. The width-related-information-dependent control is a control of the operating devices on the basis of at least one of width-related information relating to a width and a widthwise position of each specific object selected from the above-indicated at least one preceding object.
Owner:TOYOTA JIDOSHA KK
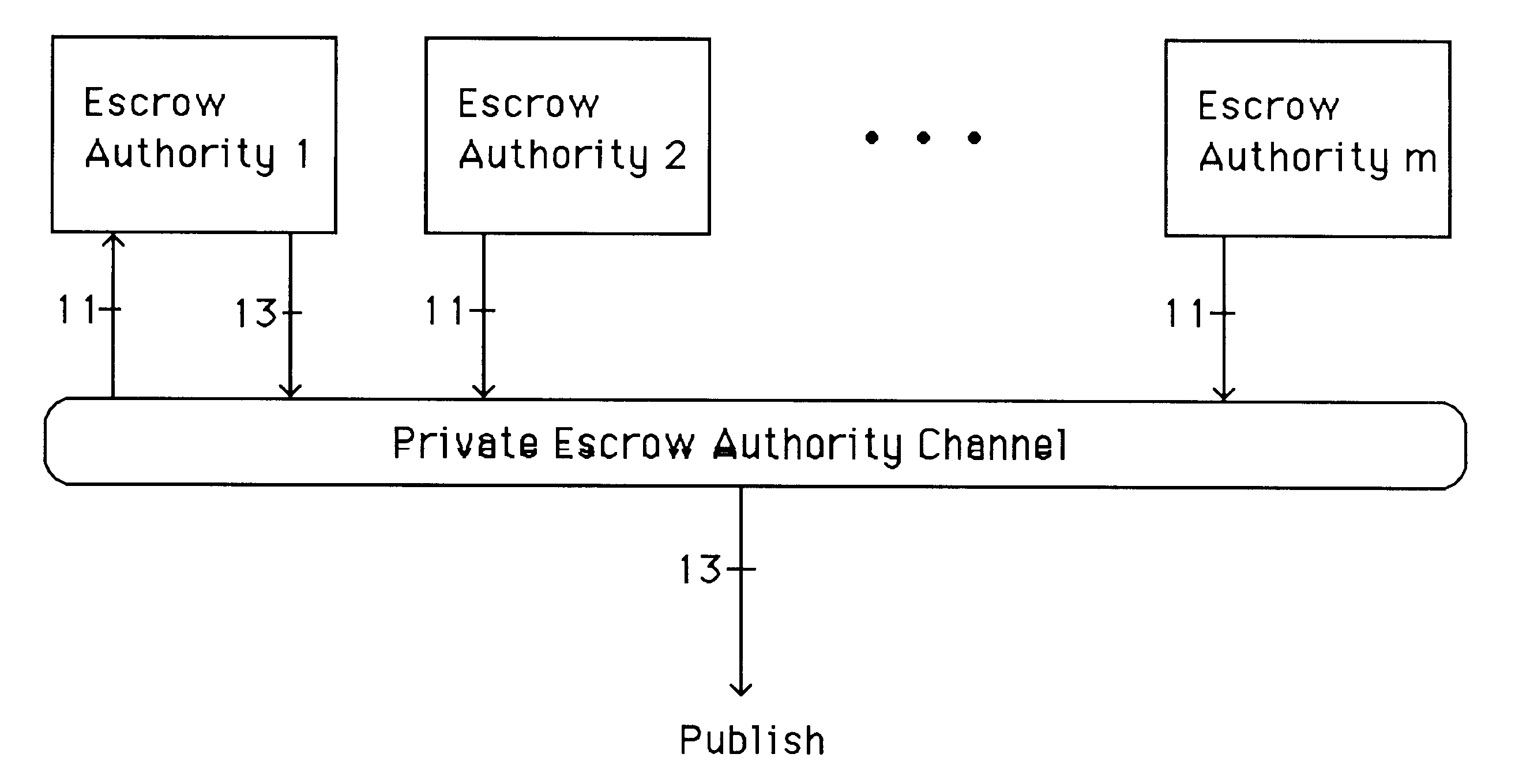
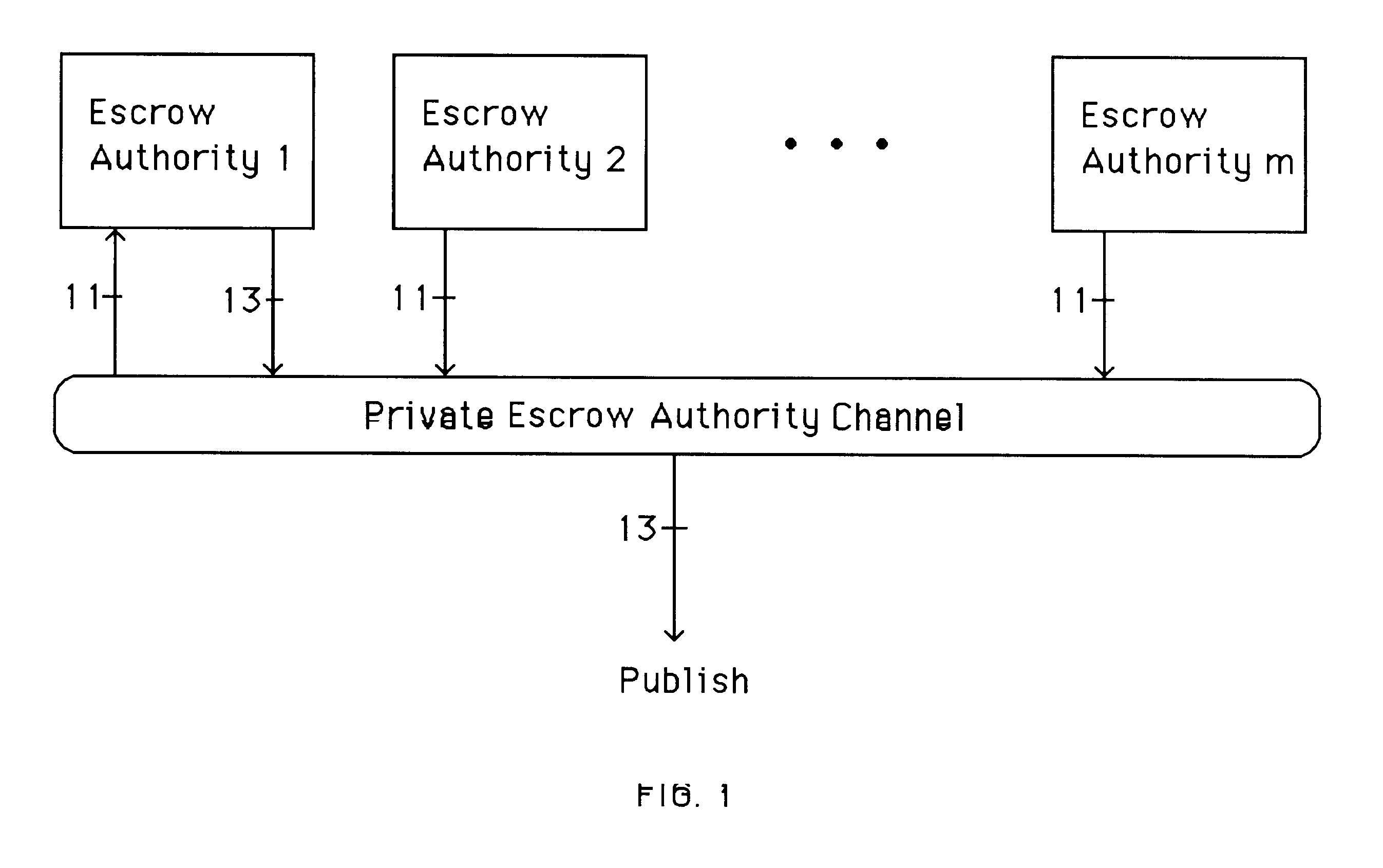
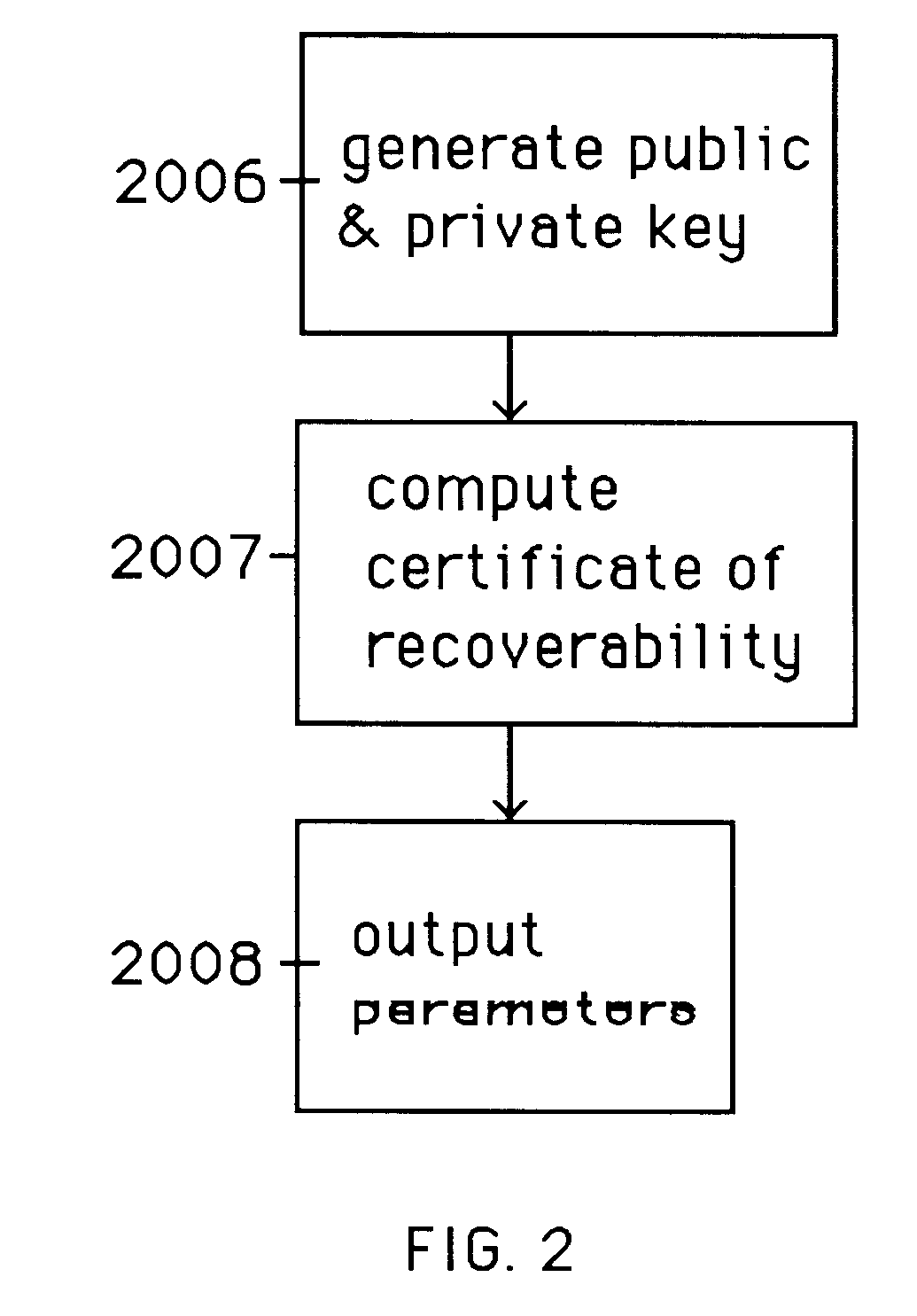
Auto-recoverable and auto-certifiable cryptostem using zero-knowledge proofs for key escrow in general exponential ciphers
InactiveUS6282295B1Fast and easy disseminationEasy to handleKey distribution for secure communicationPublic key for secure communicationTrusted authorityValidation methods
A method is provided for an escrow cryptosystem that is essentially overhead-free, does not require a cryptographic tamper-proof hardware implementation (i.e., can be done in software), is publicly verifiable, and cannot be used subliminally to enable a shadow public key system. A shadow public key system is an unescrowed public key system that is publicly displayed in a covert fashion. The keys generated by the method are auto-recoverable and auto-certifiable (abbrev. ARC). The ARC Cryptosystem is based on a key generation mechanism that outputs a public / private key pair, and a certificate of proof that the key is recoverable by the escrow authorities. Each generated public / private key pair can be verified efficiently to be escrowed properly by anyone. The verification procedure does not use the private key. Hence, the general public has an efficient way of making sure that any given individual's private key is escrowed properly, and the trusted authorities will be able to access the private key if needed. Since the verification can be performed by anyone, there is no need for a special trusted entity, known in the art as a "trusted third party". The proof and verification method involves one party proving to a second party that a third party can gain access to an encrypted value. In addition, the system is designed so that its internals can be made publicly scrutinizable (e.g., it can be distributed in source code form). This differs from many schemes which require that the escrowing device be tamper-proof hardware. The system is efficient and can be implemented as a "drop-in" replacement to an RSA or ElGamal cryptosystem. The system is applicable for lawenforcement, file systems, e-mail systems, certified e-mail systems, and any scenario in which public key cryptography can be employed and where private keys or information encrypted under public keys need to be recoverable. The system security relies solely on the security of cipher systems involved whose security has been extensively studied in the past.
Owner:CRYPTOPEAK SECURITY LLC
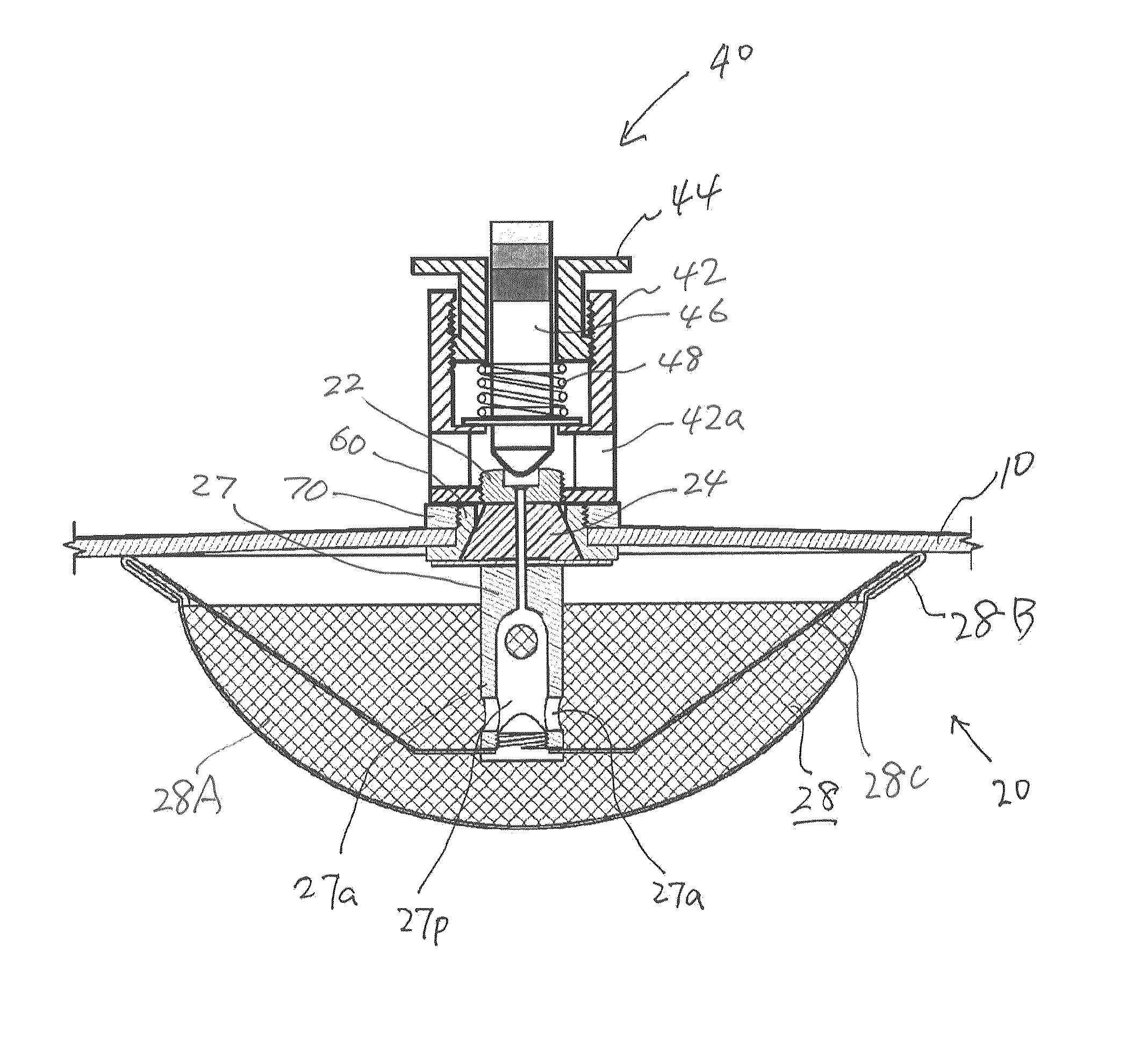
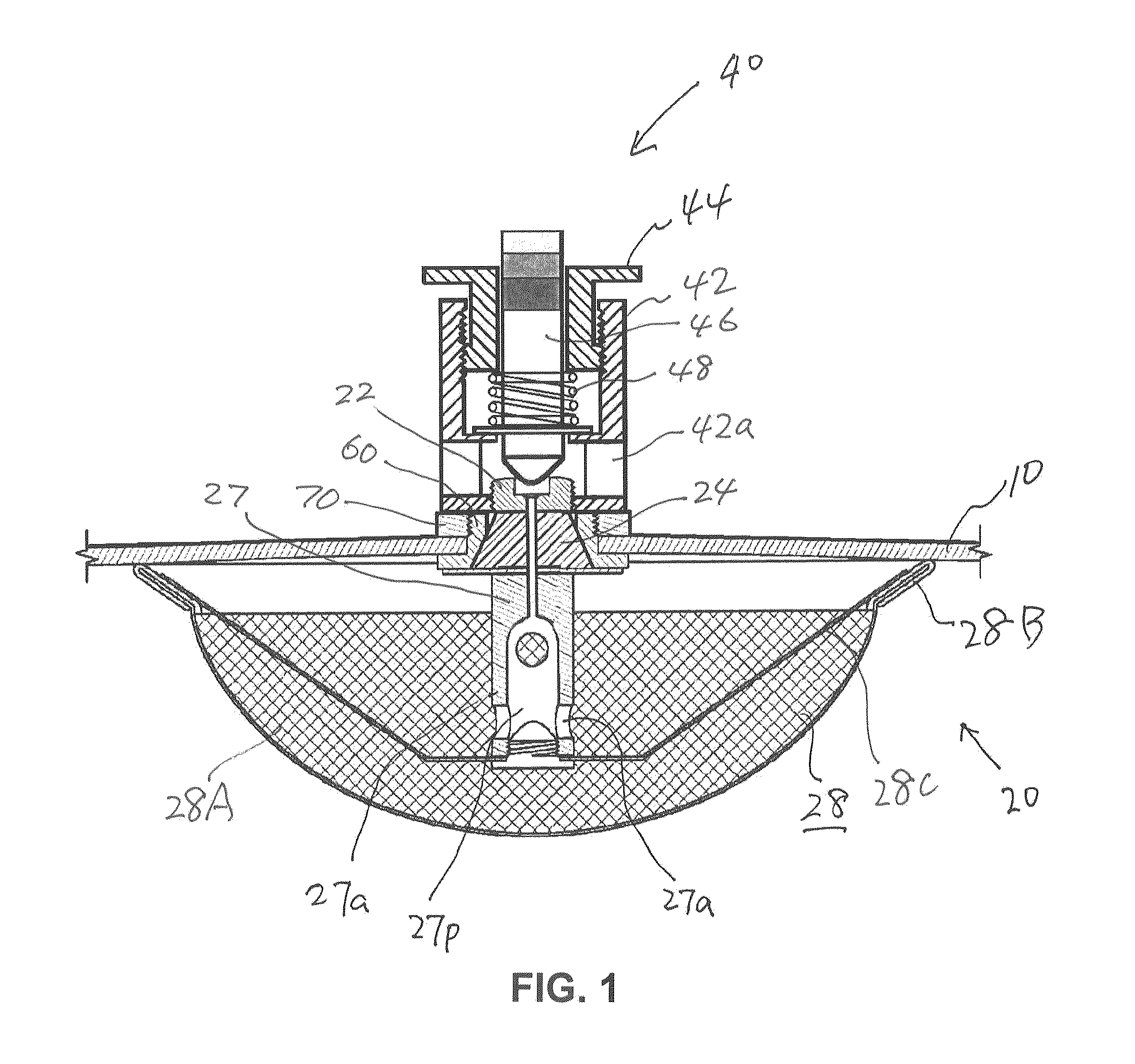
Pressure release valve assembly for pressure cooker
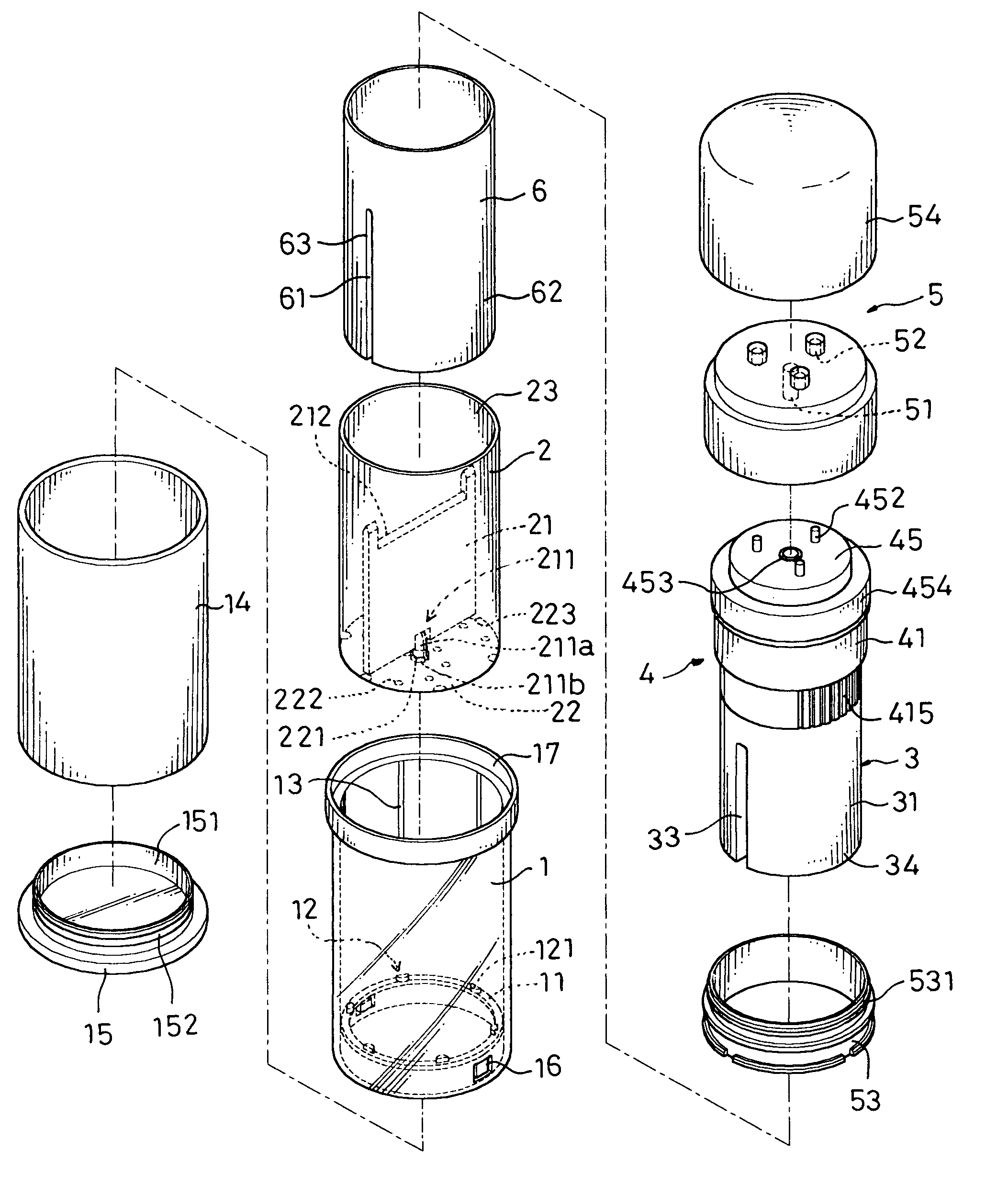
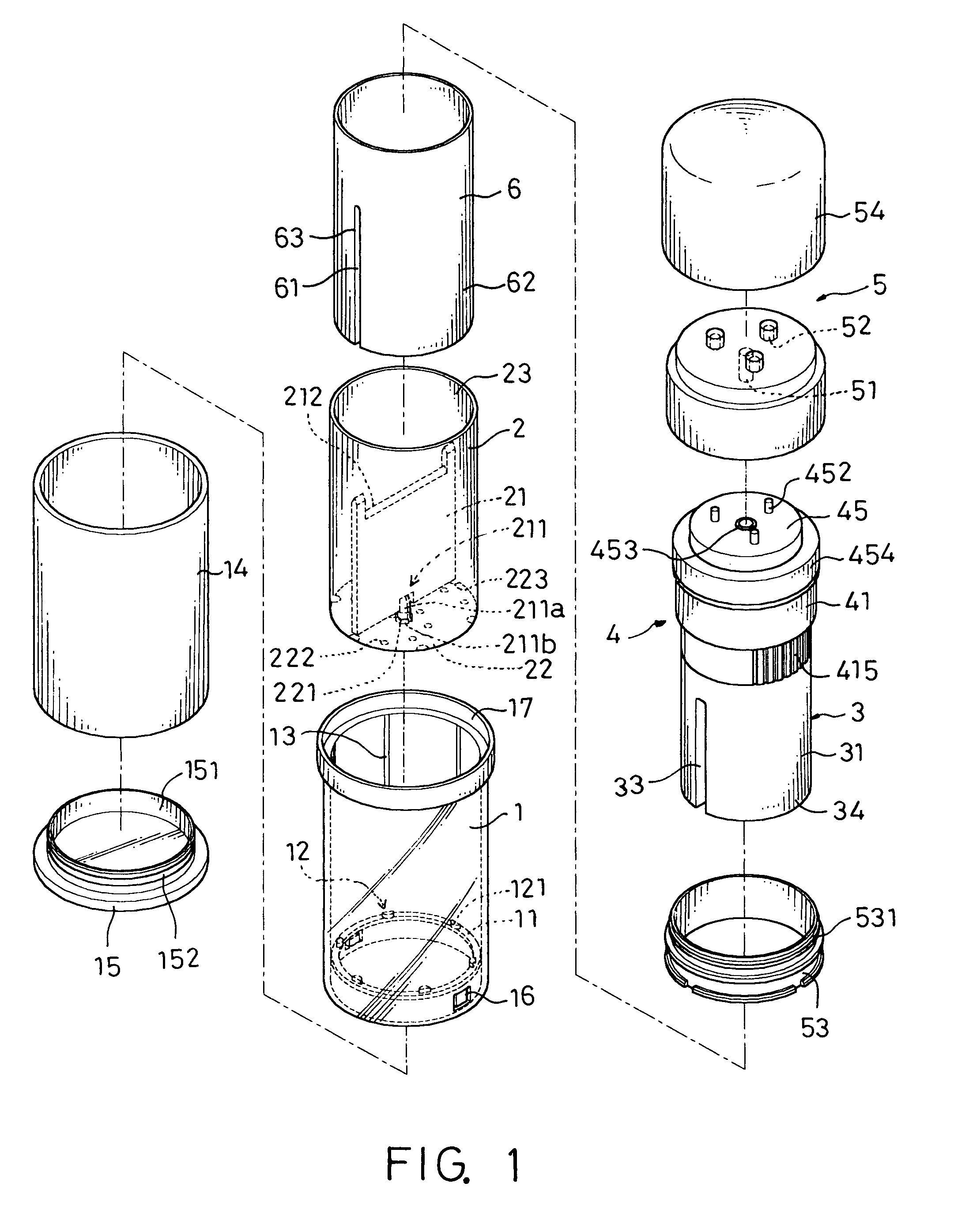
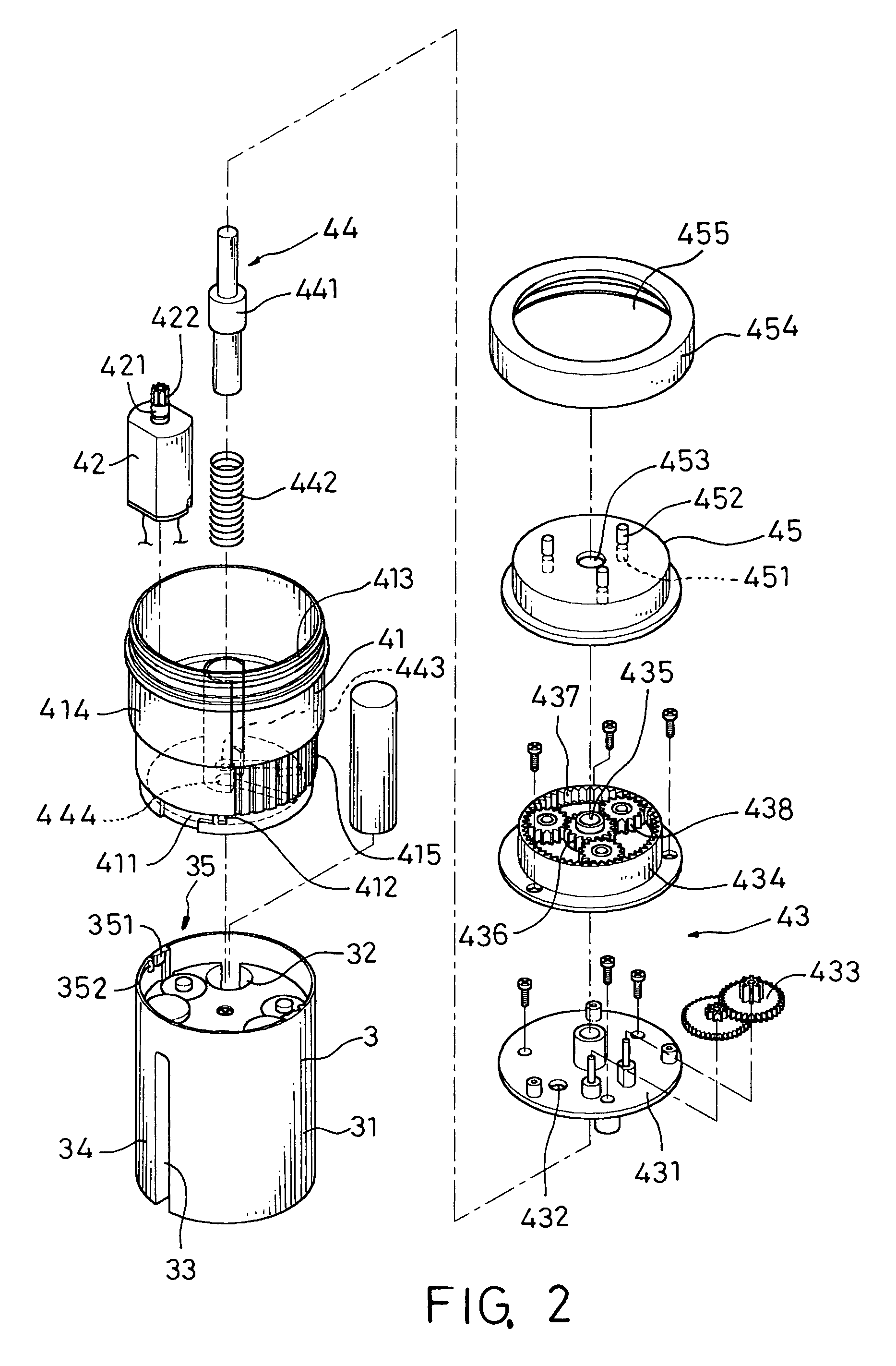
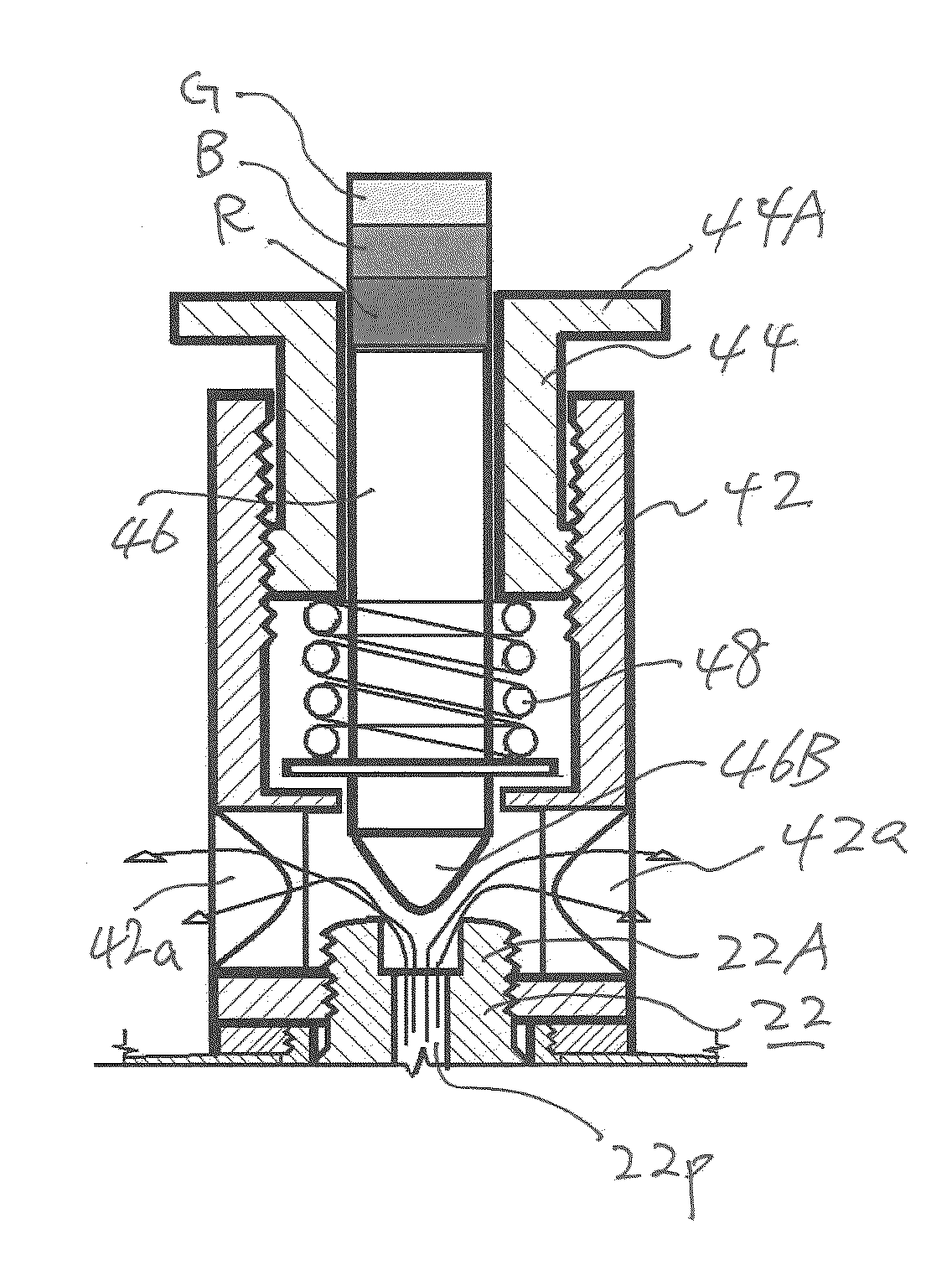
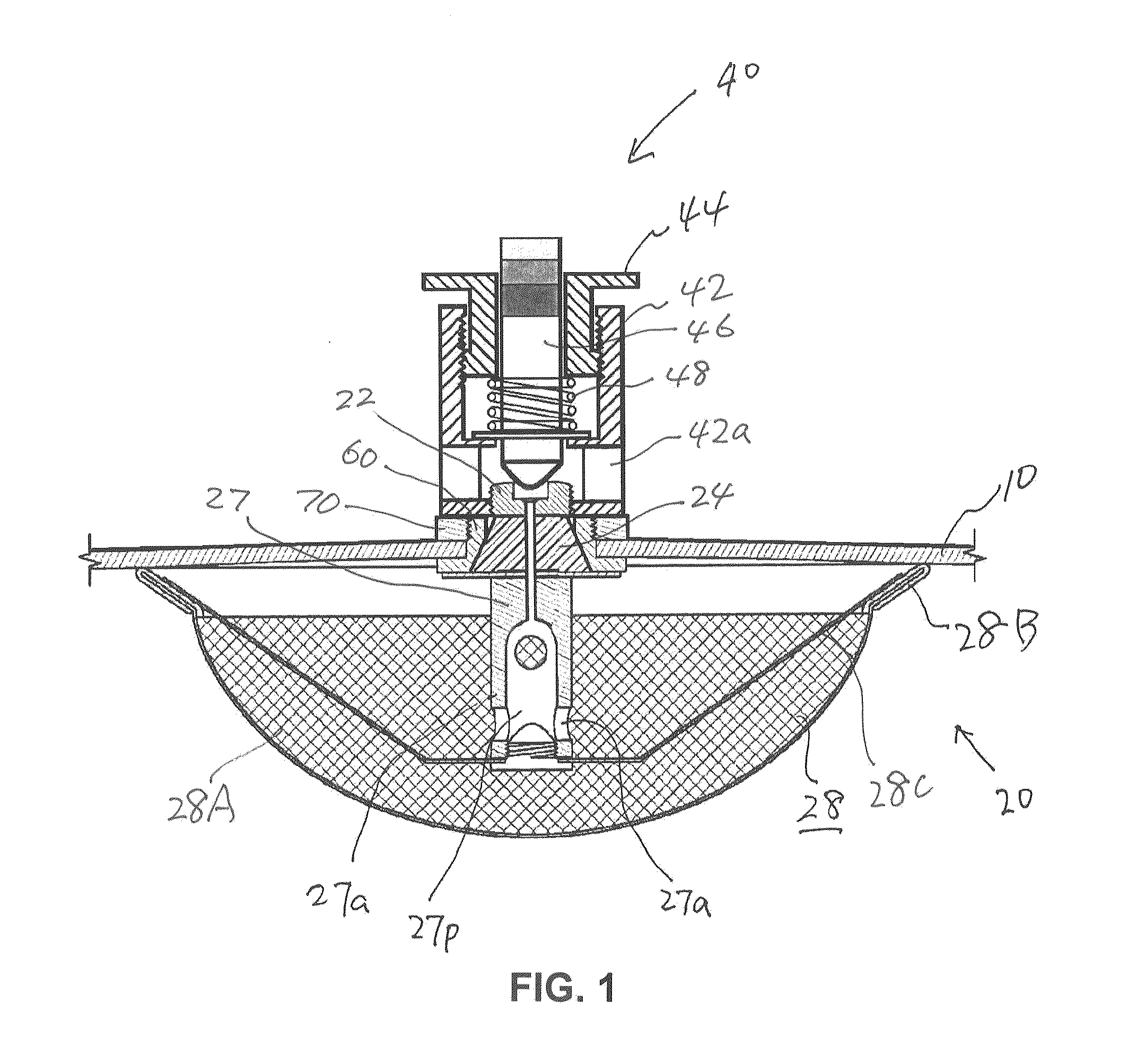
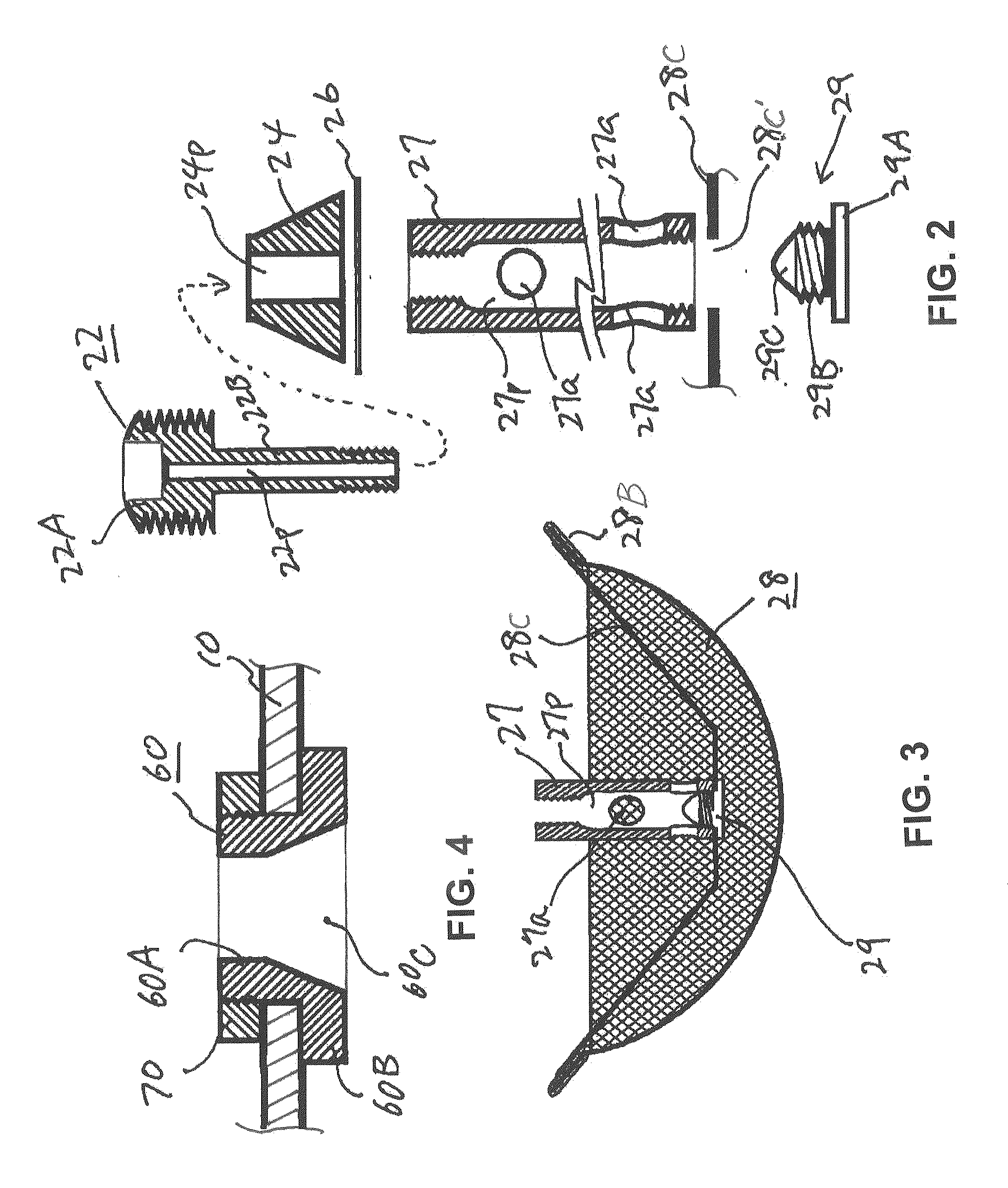
ActiveUS8869829B2Easy to useSafety is assuredCooking-vessel lids/coversCheck valvesEngineeringPressure controlled ventilation
A pressure release valve assembly for a pressure cooker including a pressure intake unit provided inside of (or under) the lid of a pressure cooker and a pressure control unit connected to the pressure intake unit and provided outside of the lid. The pressure intake unit includes a pressure outlet tube, a connecting plug substantially in a truncated conical shape and connected to the pressure outlet tube with the connecting plug in between, a pressure intake tube connected to the pressure outlet tube, and a filtering cap attached to the pressure intake tube; and the pressure control unit includes a cylindrical pressure release casing, a tubular pressure control element threadedly connected to the inside of the pressure release casing, a valve plunger provided inside the tubular pressure control element, and a pressure spring installed between the pressure control element and an externally expanding supporting flange of the valve plunger.
Owner:HASEGAWA TOM HIROSHI
Nonaqueous electrolytic solution and lithium secondary batteries
ActiveUS20040121239A1Not inhibit overchargeImprove battery performanceOrganic electrolyte cellsLi-accumulatorsSolventBiphenyl compound
In order to manufacture a lithium secondary battery having excellent performances in safety under overcharge condition, cycle property, electric capacity, and storage endurance, 0.1 wt. % to 10 wt. % of a tert-alkylbenzene compound is favorably incorporated into a non-aqueous electrolytic solution comprising a non-aqueous solvent and an electrolyte, preferably in combination with 0.1 wt. % to 1.5 wt. % of a biphenyl compound.
Owner:UBE IND LTD
Crash-safe vehicle control system
InactiveUS7613568B2Safety is assuredAccurate identificationDigital data processing detailsPedestrian/occupant safety arrangementControl systemEngineering
A crash-safe vehicle control system for controlling operating devices of an own vehicle such as a vehicle decelerating device and an occupant protecting device, on the basis of information on at least one preceding object existing in front of the own vehicle. The vehicle control system is arranged to effect at least one of a non-first-preceding-object-information-dependent control and a width-related-information-dependent control. The non-first-preceding-object-information-dependent control is a control of the operating devices on the basis of non-first-preceding-object information detected by the present system per se, in the presence of a high possibility of crashing of the own vehicle with a first preceding vehicle existing immediately in front of the own vehicle. The non-first-preceding-object information relates to at least one non-first preceding object each existing in front of the first preceding vehicle. The width-related-information-dependent control is a control of the operating devices on the basis of at least one of width-related information relating to a width and a widthwise position of each specific object selected from the above-indicated at least one preceding object.
Owner:TOYOTA JIDOSHA KK
Two-way caster bench
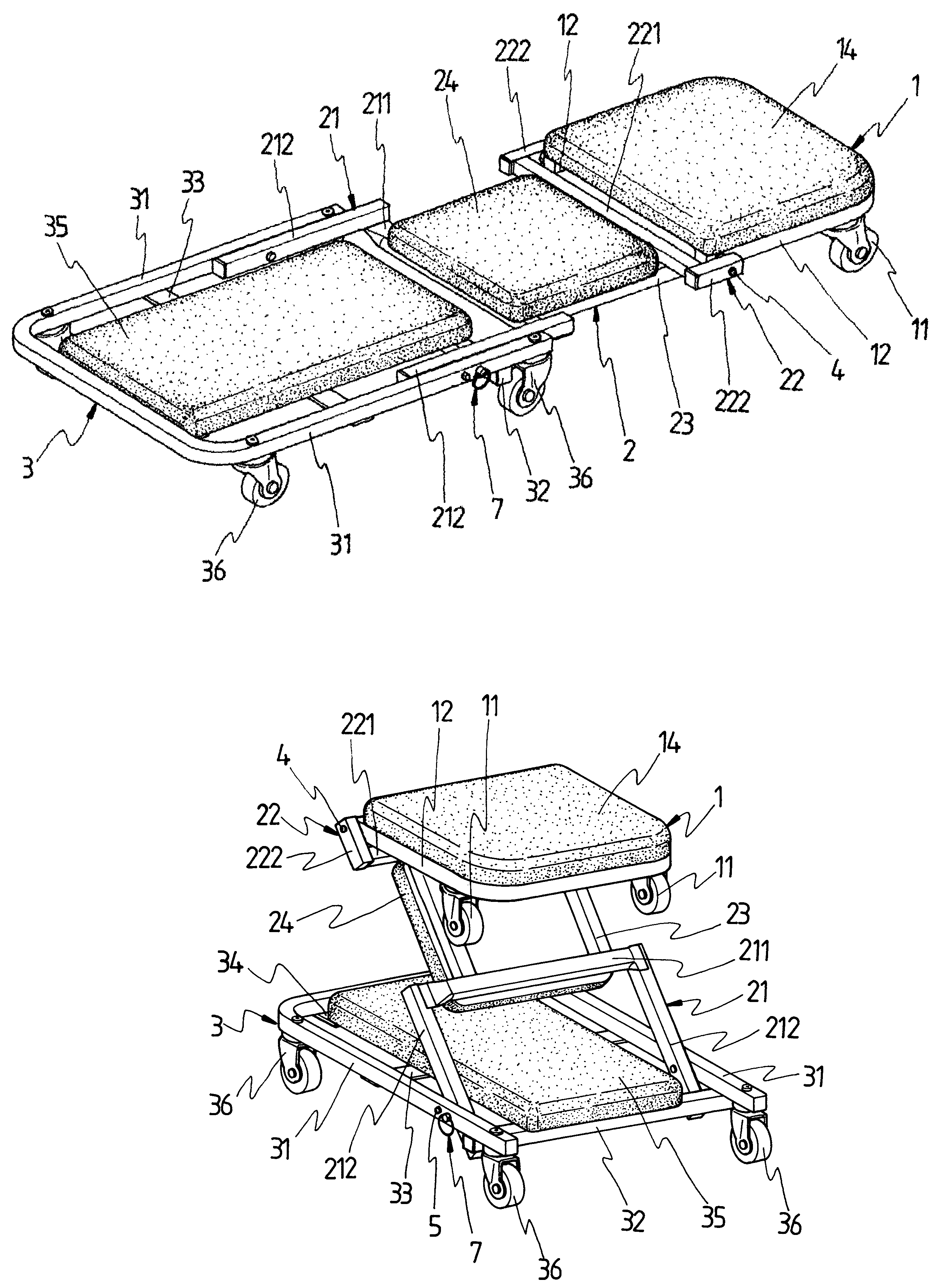
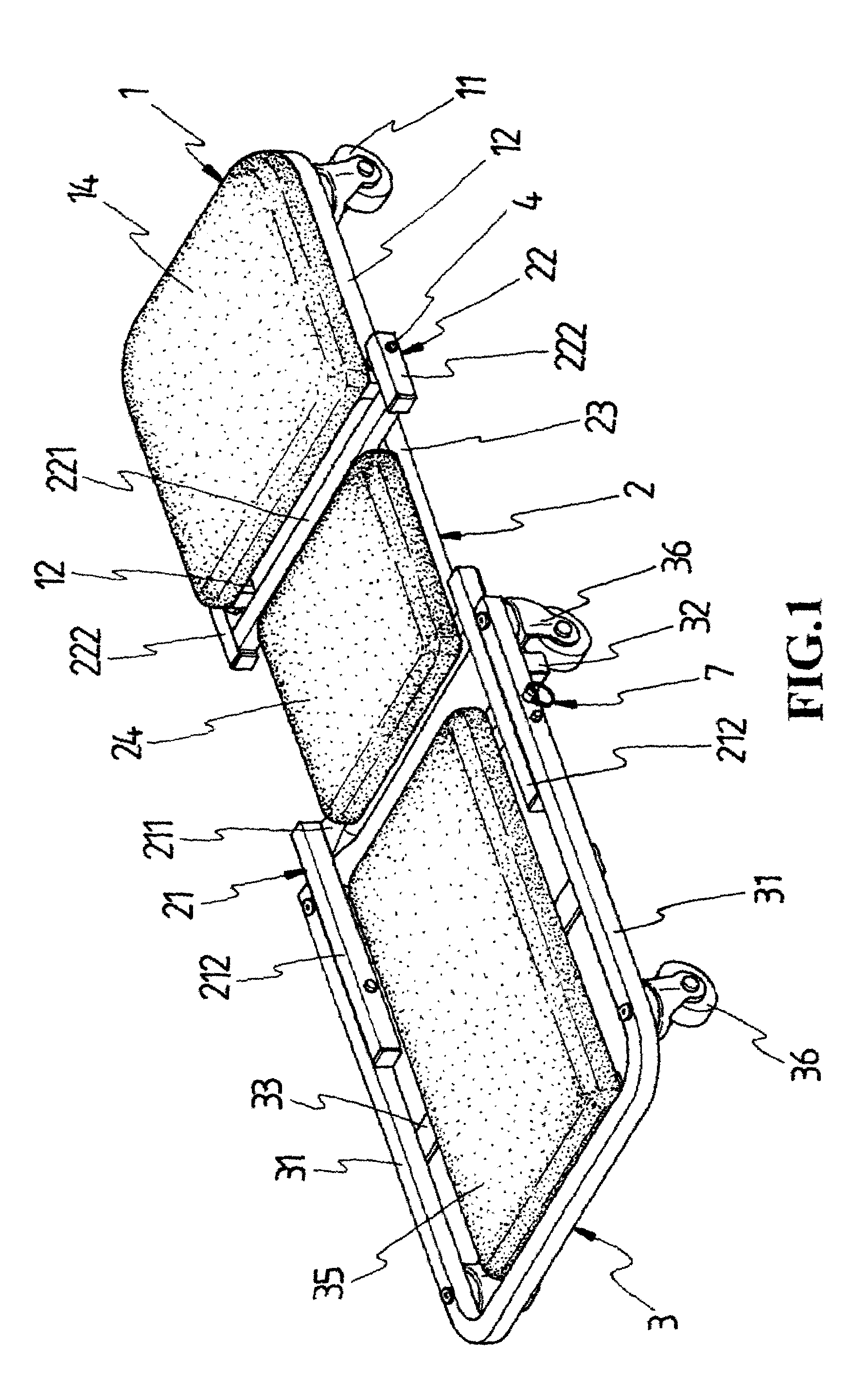
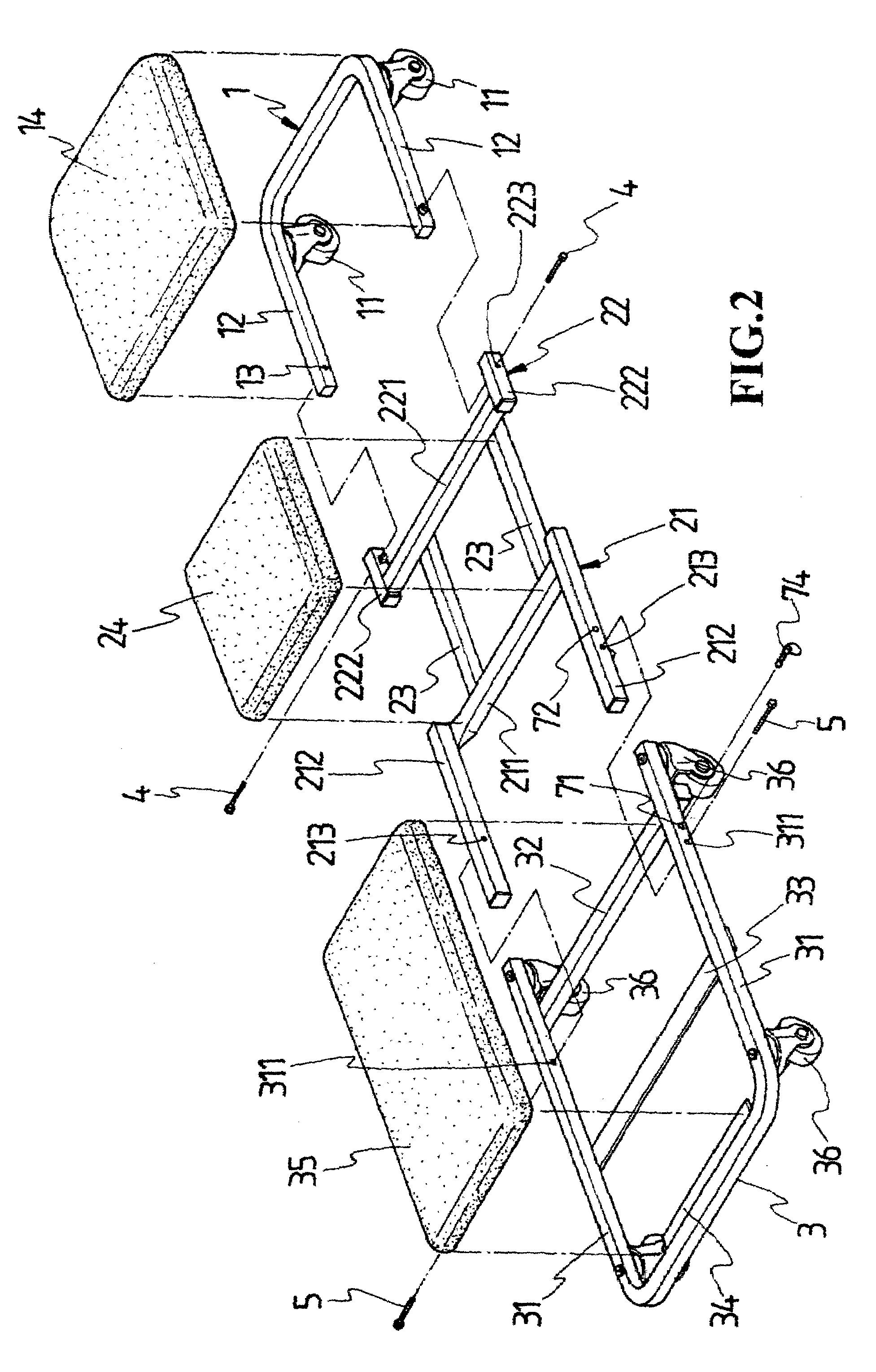
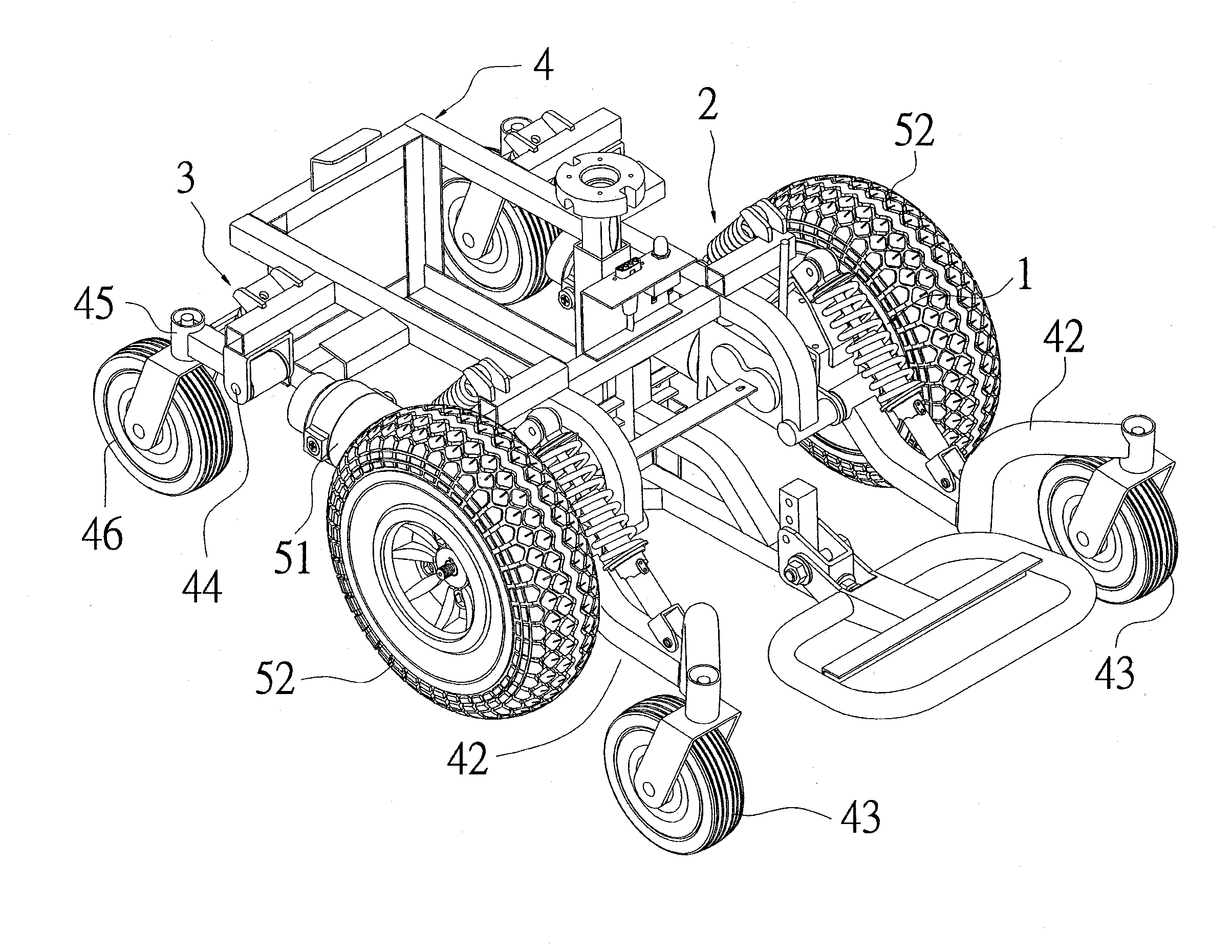
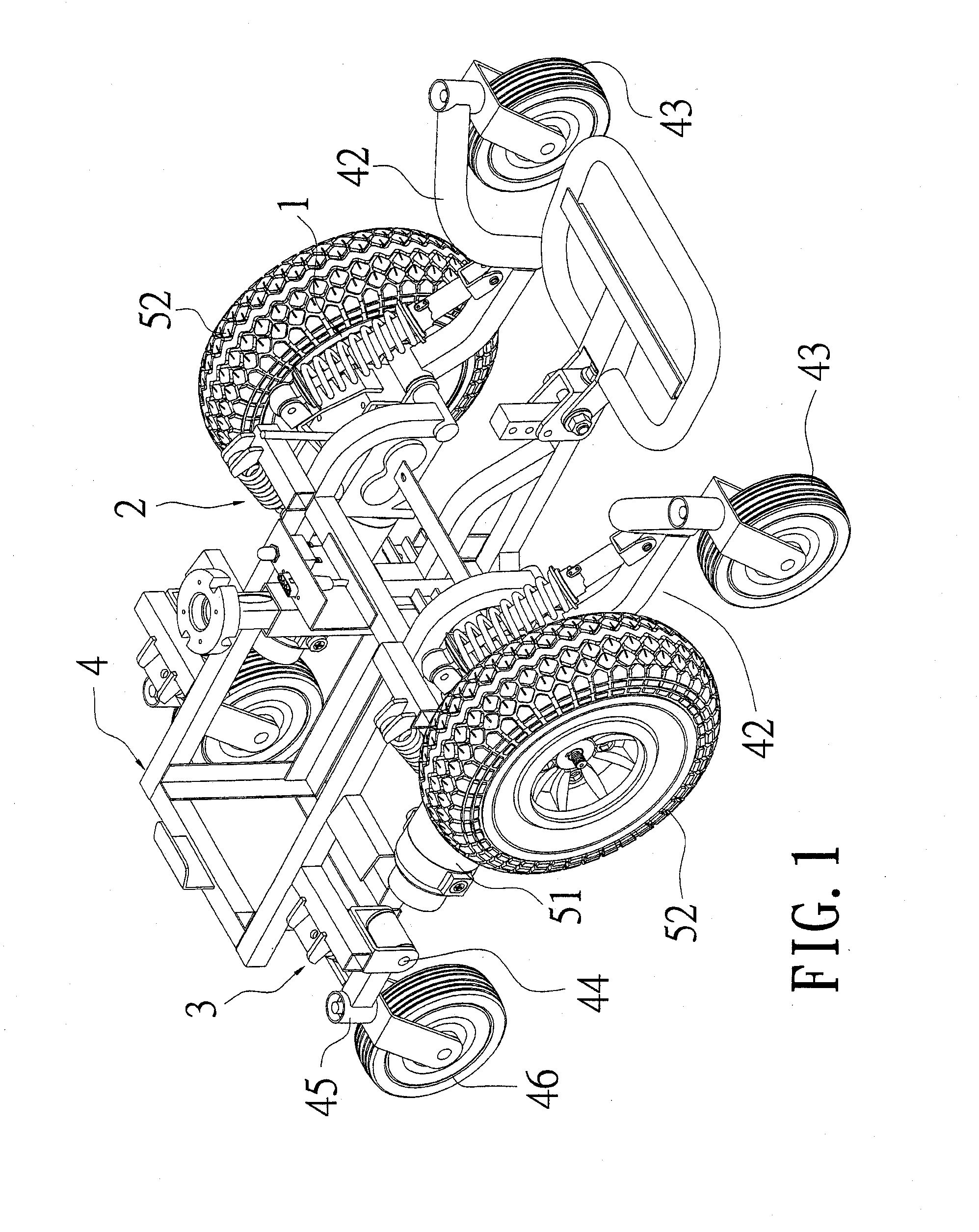
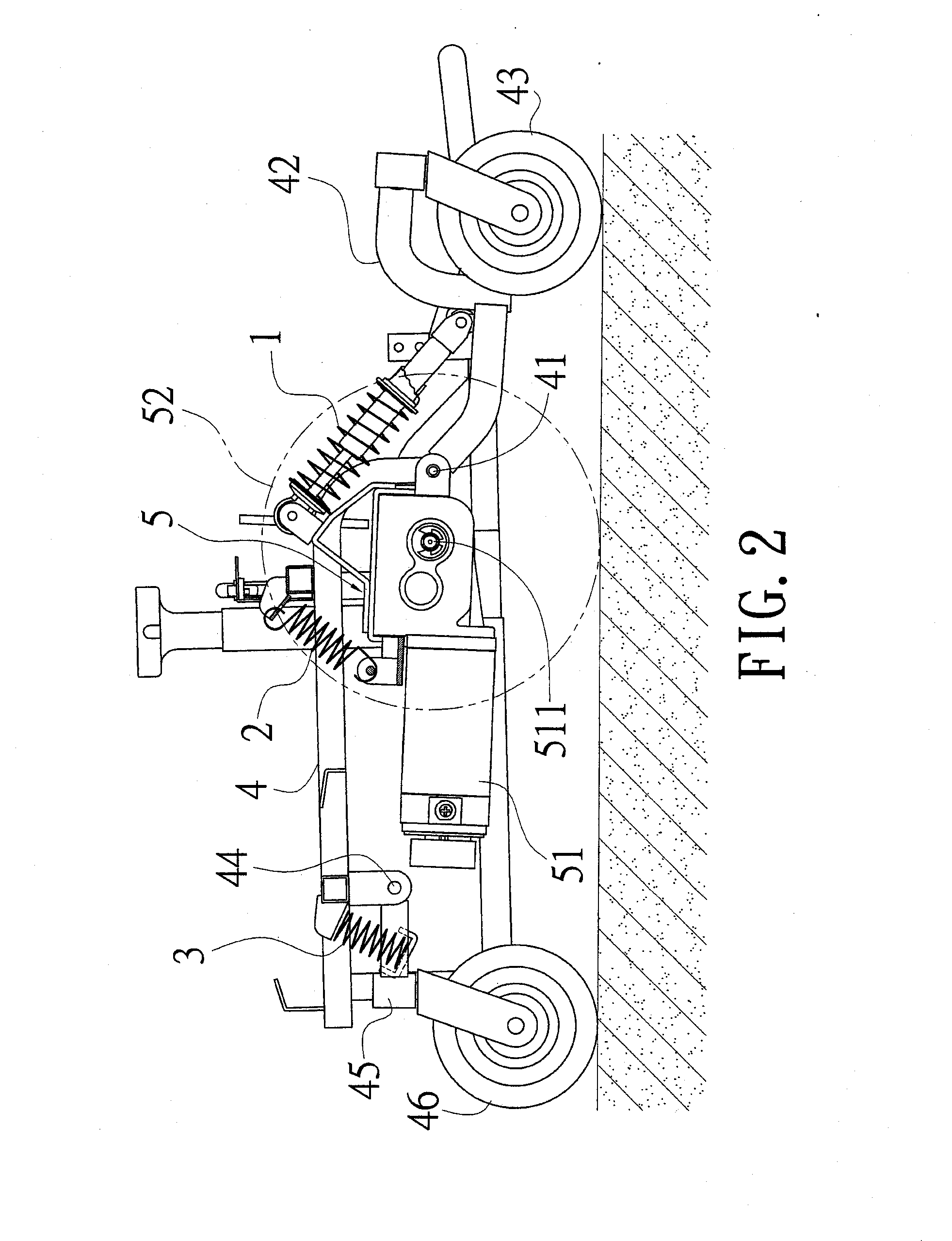
InactiveUS6969077B2Safety is assuredCarriage/perambulator with multiple axesHand carts with one axisEngineeringCaster
A two-way caster bench comprises a front chair frame, a middle chair frame and a rear chair frame. The front chair frame is a U-shaped frame having a predetermined number of casters installed underneath, whose free ends are pivotally connected with the middle chair frame. The middle chair frame is composed of two U-shaped frames connected by a pair of connecting bars, with the free ends facing outwardly. One U-shaped frame is for a pivotal connection to the front chair frame, and another is for a pivotal connection to the rear chair frame. The rear chair frame is also a U-shaped frame having a predetermined number of casters installed underneath, the bottom of which is provided with a transverse bar for supporting the middle chair frame as it is folded toward the rear chair frame. Each of the chair frames is provided with a cushion.
Owner:SHINN FU
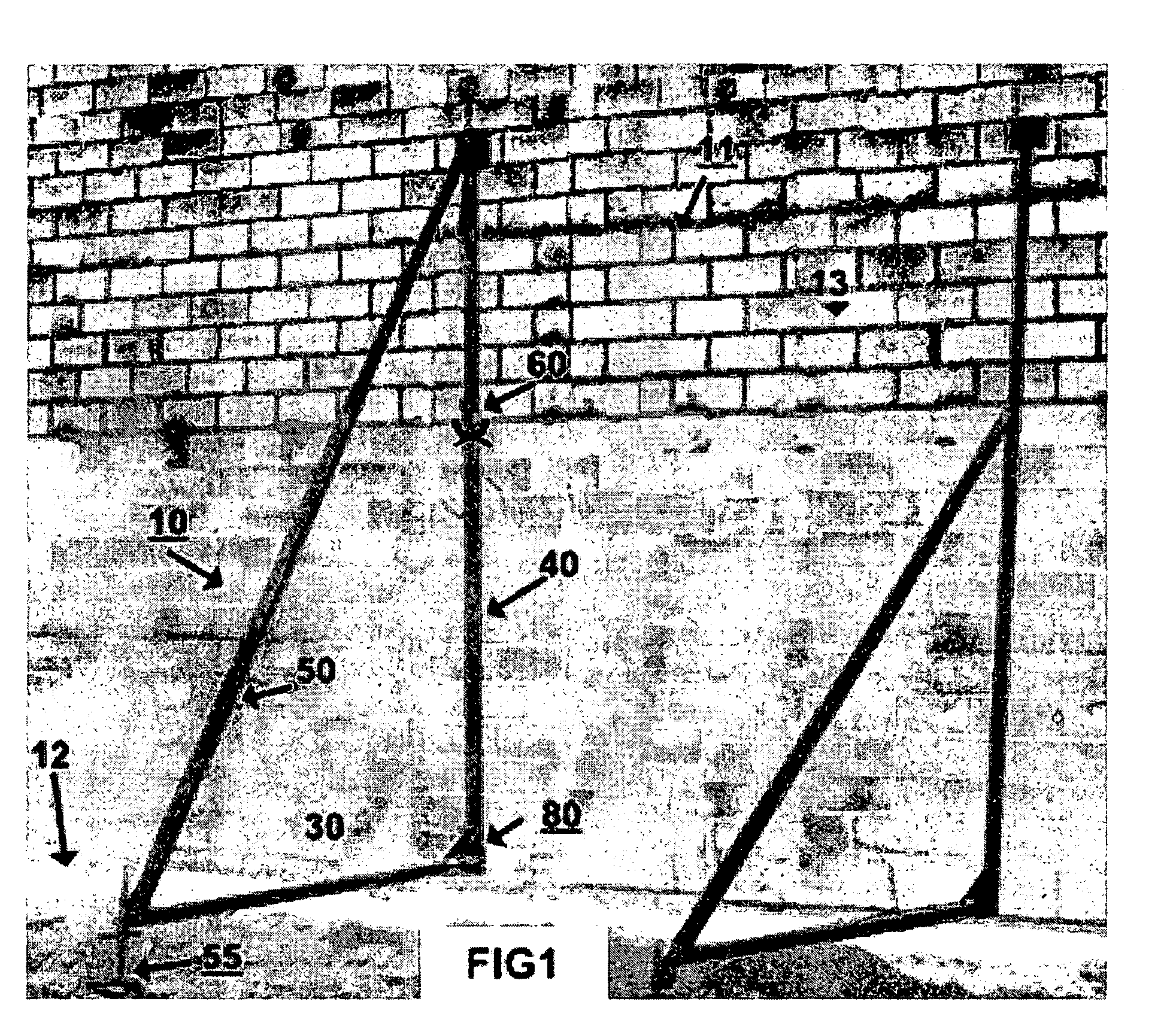
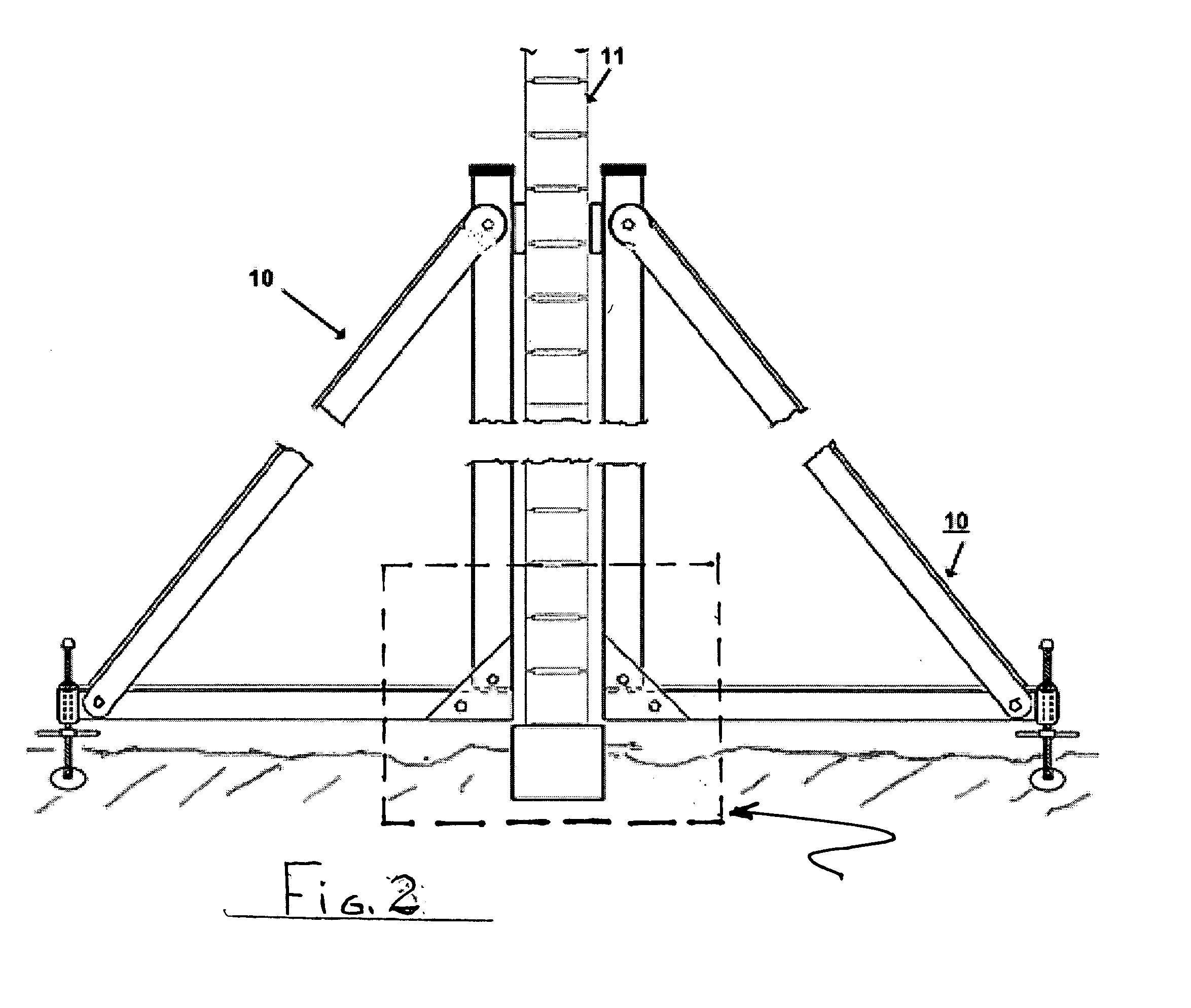
Method and adjustable apparatus for masonry wall bracing
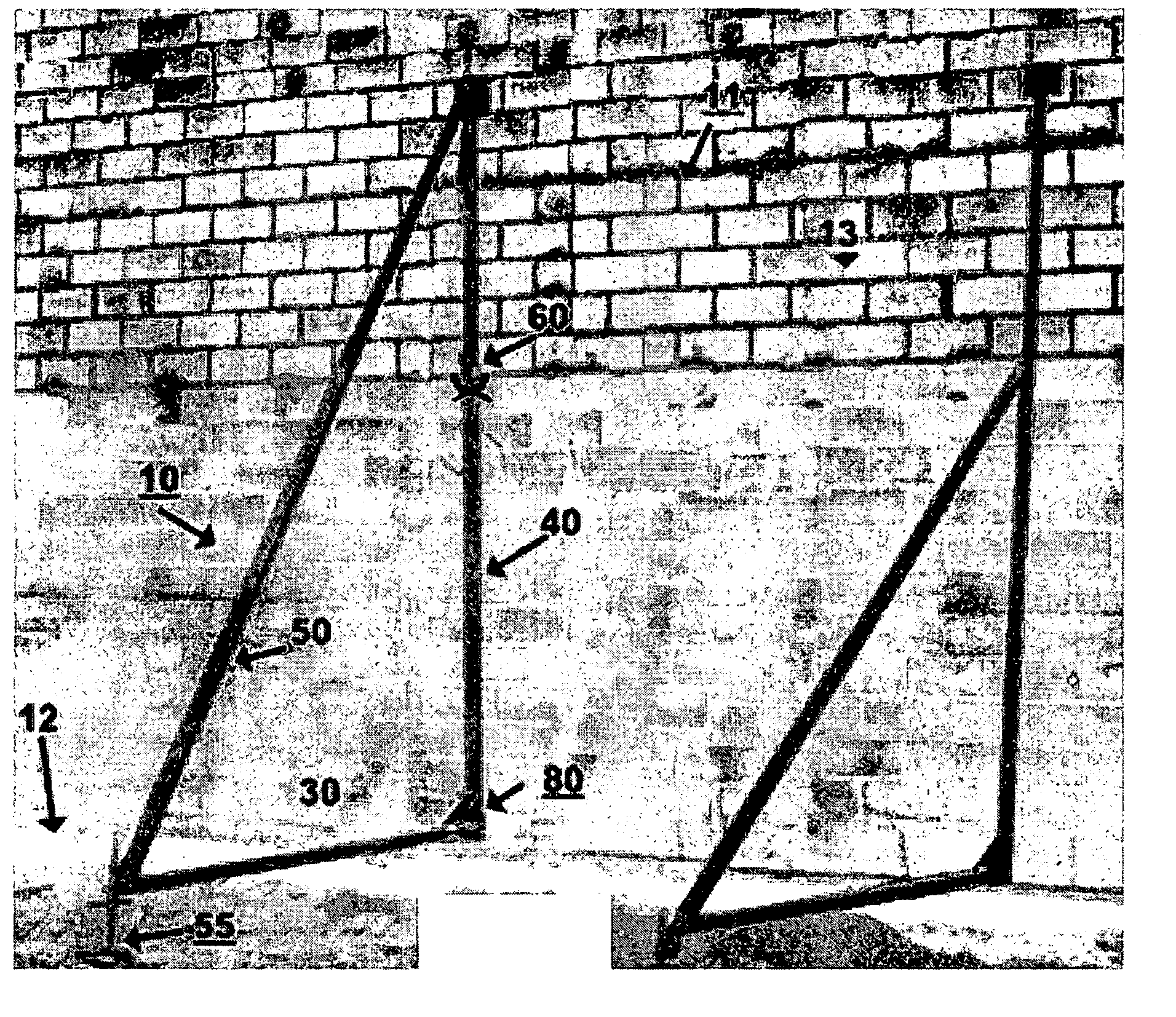
InactiveUS20050072059A1Reduce deathReduce injuriesBuilding roofsCeilingsEngineeringMechanical engineering
Adjustable apparatus for bracing one or both sides of a wall being fabricated from masonry blocks and having an opening near the base of the block wall. Bracing system includes strong rigid members assembled in the form of a right angle brace set having stiff vertical, horizontal and diagonal members, a connector having a length sufficient to extend through the opening affixed at a right angle location of one or both of the brace sets. A pair of such braces—back to back, and spaced on opposite sides of a wall—are interconnected together via this connector. Selected brace members telescope to accommodate increases in wall height and a manually adjustable outrigger screwjack at the remote end of the horizontal member eliminates reliance on prior art deadmen.
Owner:HODSDON EDWIN R +1
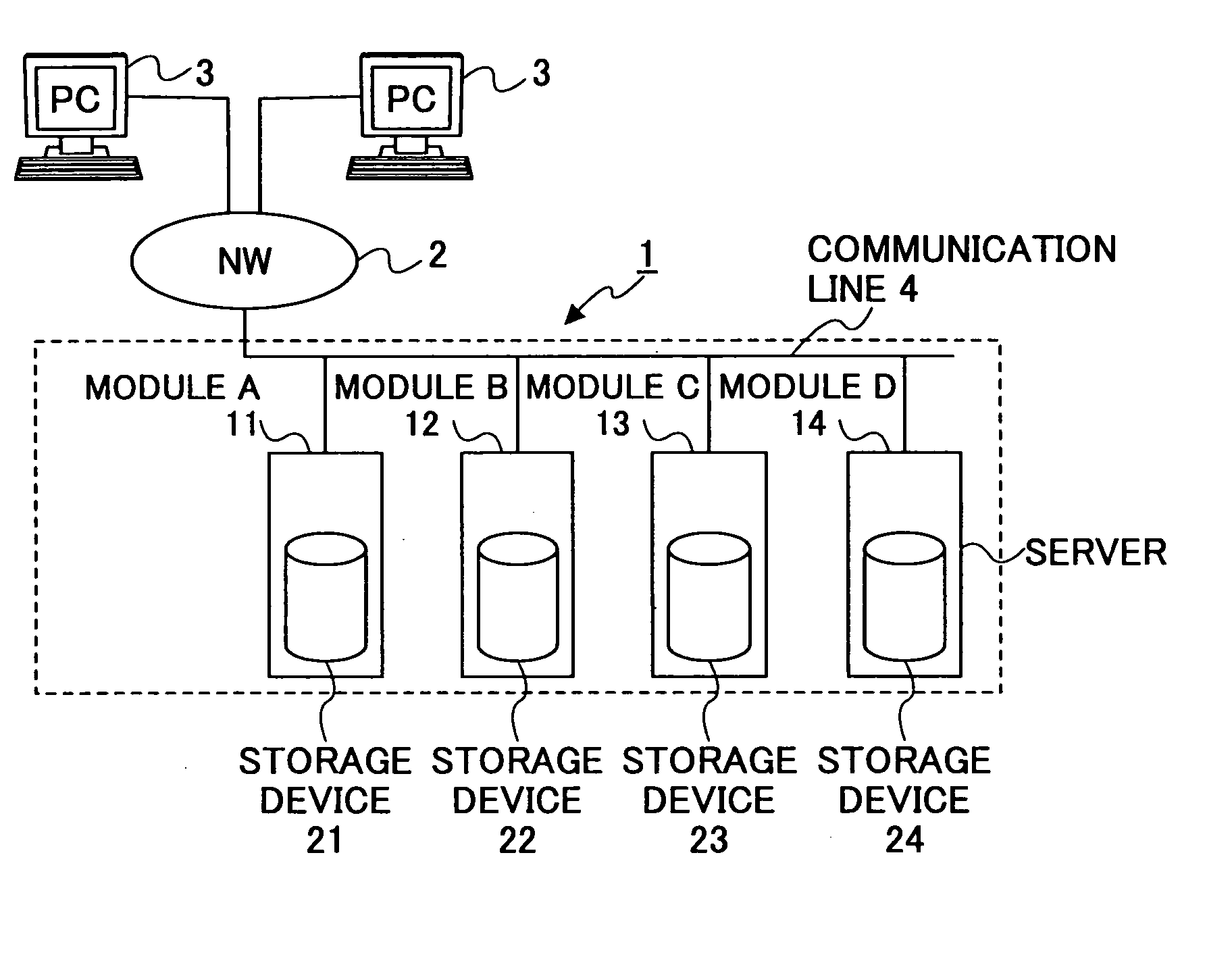
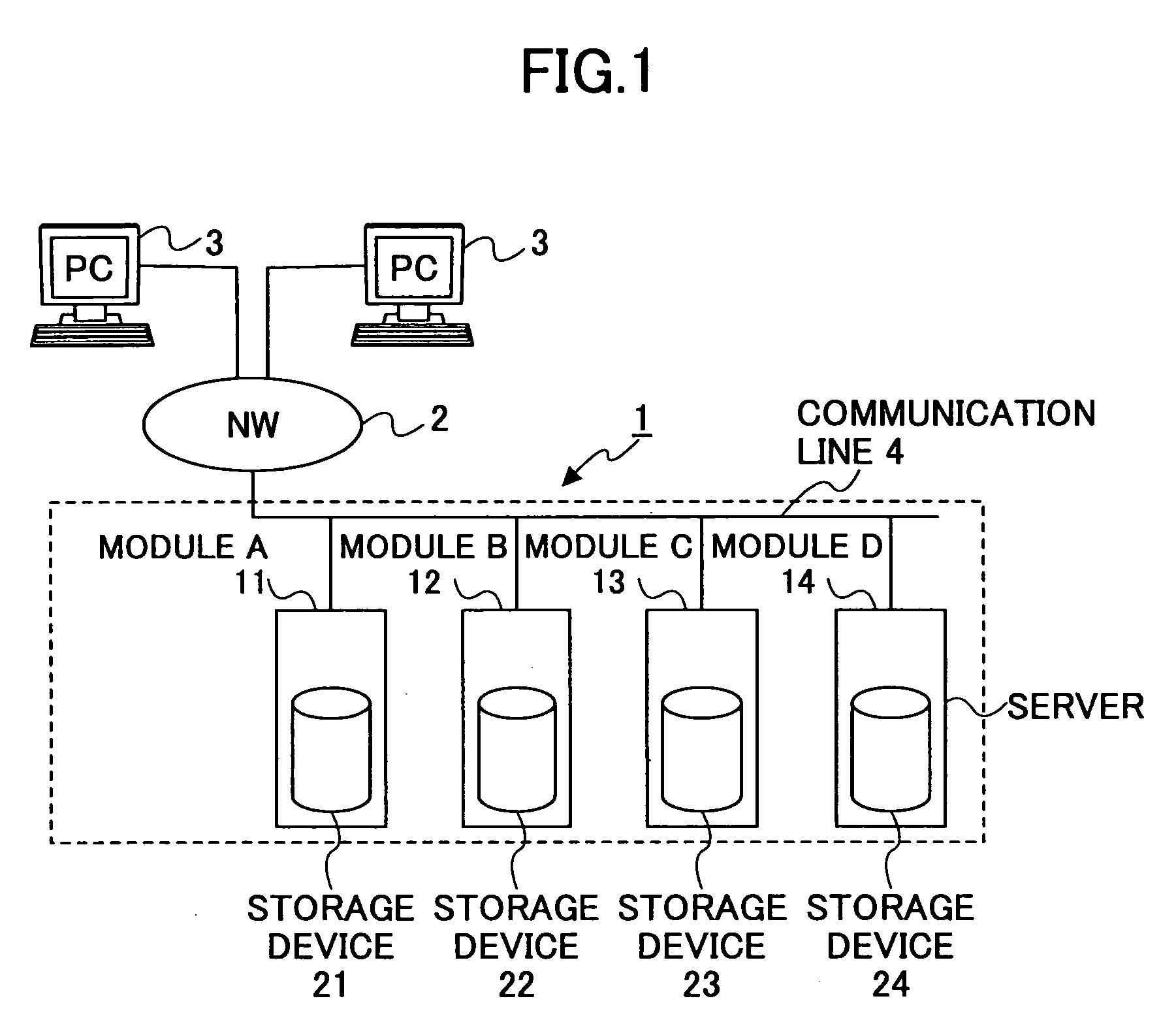
Storage system
InactiveUS20050235109A1High use efficiencySafety be assureInput/output to record carriersMemory adressing/allocation/relocationInformation storageFunctional module
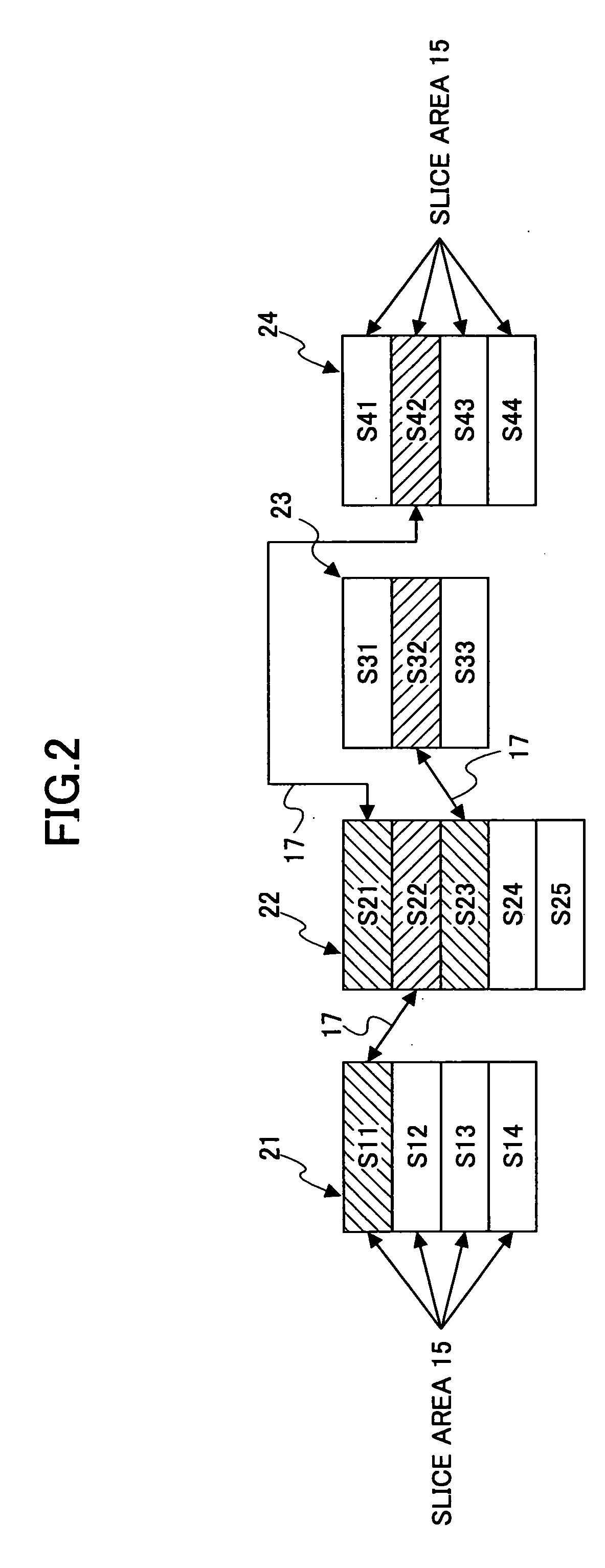
A storage system is disclosed that stores data across plural storage devices. The storage system includes plural modules. Each of the modules includes a storage device including a data storage section that has plural slice areas to store data elements one in each, and a control-information storage section that stores control information of the plural slice areas, a communications-function section having a function of sending and receiving the data elements stored in the slice areas in the data storage section. The modules communicate with each other to replicate the data element stored in the slice area into an unused slice area in another module so as to have data redundancy.
Owner:FUJITSU LTD
Battery-powered manual machine tool
InactiveUS6889439B2Quickly availableProtection from vibrationMetal sawing devicesMetal sawing accessoriesHand heldPower tool
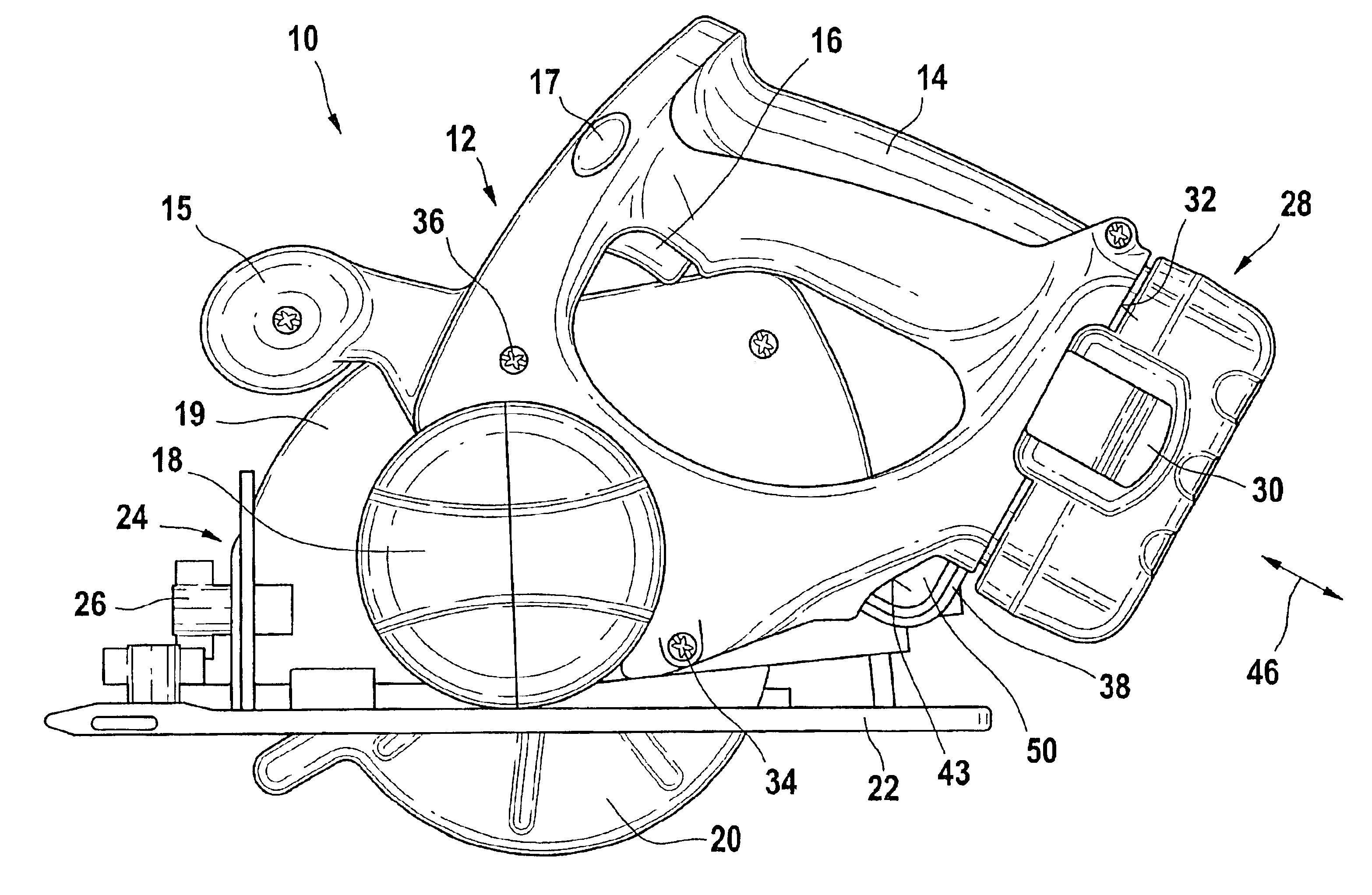
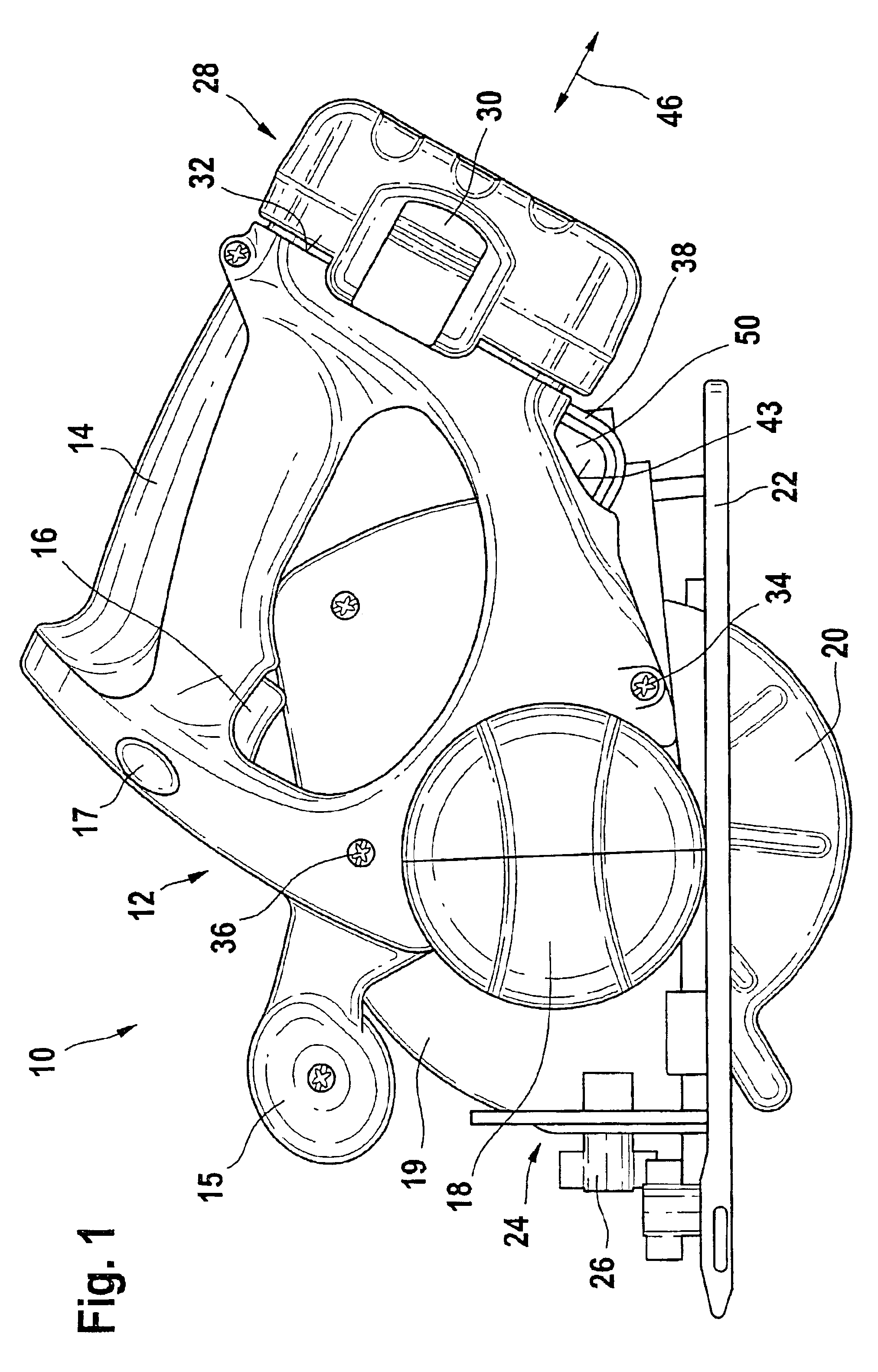
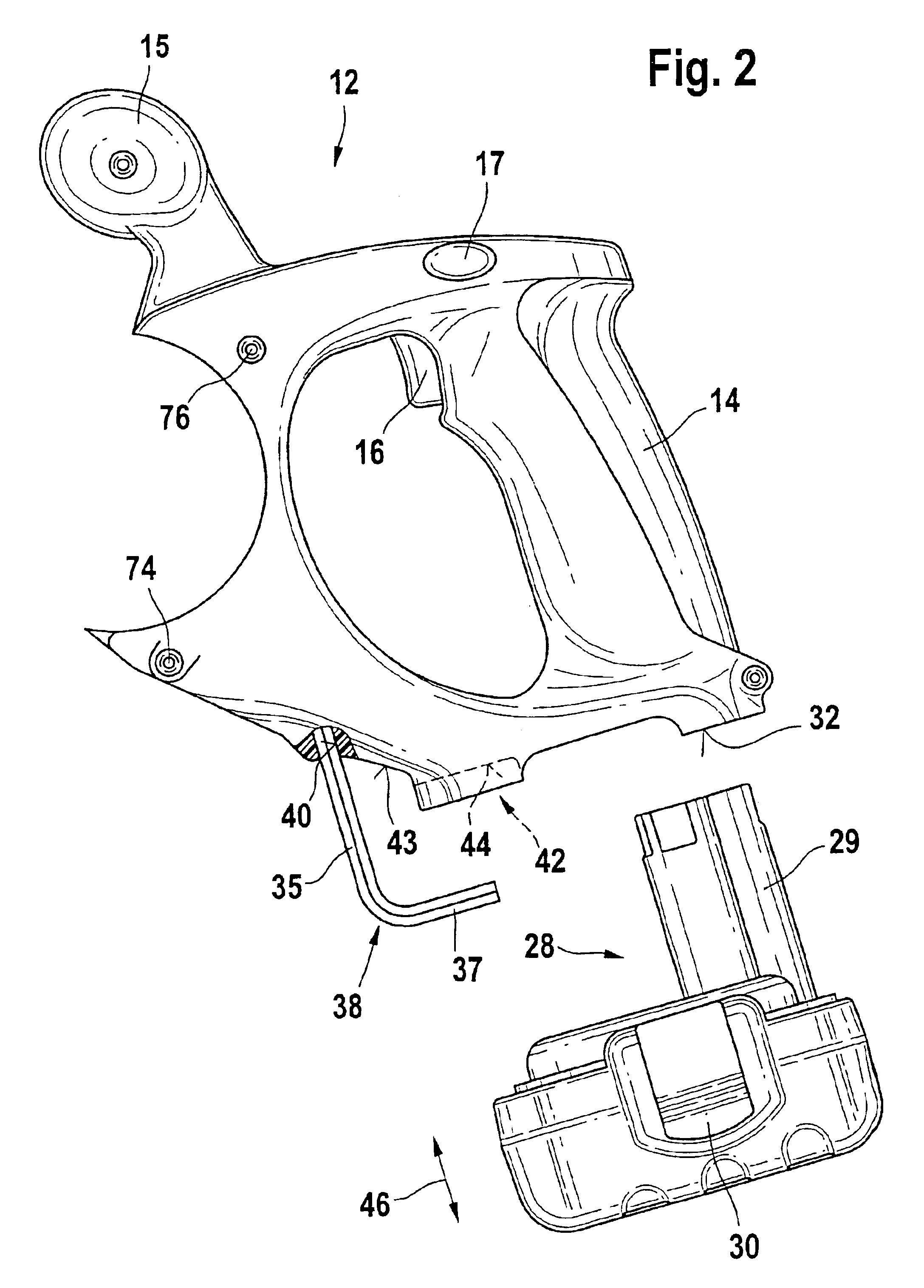
A battery-operated hand power tool (10), in particular a power saw (101), having a housing (12) into which a battery pack (28) can be detachably inserted in captive fashion, and between the battery pack (28) and the housing (12), an elongated auxiliary tool (38) is stored, in particular for releasing the tool, preferably the saw blade, is made more secure and convenient to manipulate by disposing the auxiliary tool (38) in such a way that it is visible from outside and is easy to feel, and in particular can be reached through.
Owner:ROBERT BOSCH GMBH
Suspension system for electric wheelchair
InactiveUS20110253464A1Easily slidSafety is assuredElectric propulsion mountingWheelchairs/patient conveyanceEngineeringSlip resistance
A suspension system for an electric wheelchair is revealed. A pivot on a front end of a wheelchair frame pivotally connects a front wheel frame and a drive set frame. A front suspension system is disposed between the front wheel frame and a drive set frame. The front wheel frame is assembled with front wheels, the drive set frame is disposed with a drive set and a drive wheel is arranged at a power output end of the drive set. Moreover, an auxiliary suspension device is arranged between the drive set frame and the frame while a rear end of the frame is disposed with rear wheels. Thereby the electric wheelchair has good stability and slip-resistance, not easily overturned or slid by interaction between the front and the auxiliary suspension devices while driving through concave surfaces or convex surfaces. Therefore the safety of users seated in wheelchairs is assured.
Owner:FREERIDER CORP
Remote control vehicle with UV sterilizer
InactiveUS7380627B2Good for healthQuality improvementLighting and heating apparatusAutomatic initiationsControl signalUv disinfection
A remote control vehicle includes a cart, an ultraviolet radiation tube and a remote control device. The cart has a video device, a control signal antenna and a video signal antenna. The control signal antenna and the video signal antenna are disposed by the video device. The remote control device is used to send out control signals to the control signal antenna so as to control the motions of the cart. In use, users place the cart in an air conduit of an air conditioning system and steer it with the remote control device so that the cart may reach every part in the air conduit. Also, the ultraviolet radiation tube is activated to kill all the bacteria and microorganisms in the air conduits. Such that, the users will not be exposed to the ultraviolet radiation emitted by the tube, and hence the safety of use is assured.
Owner:NAT TAIPEI UNIV OF TECH
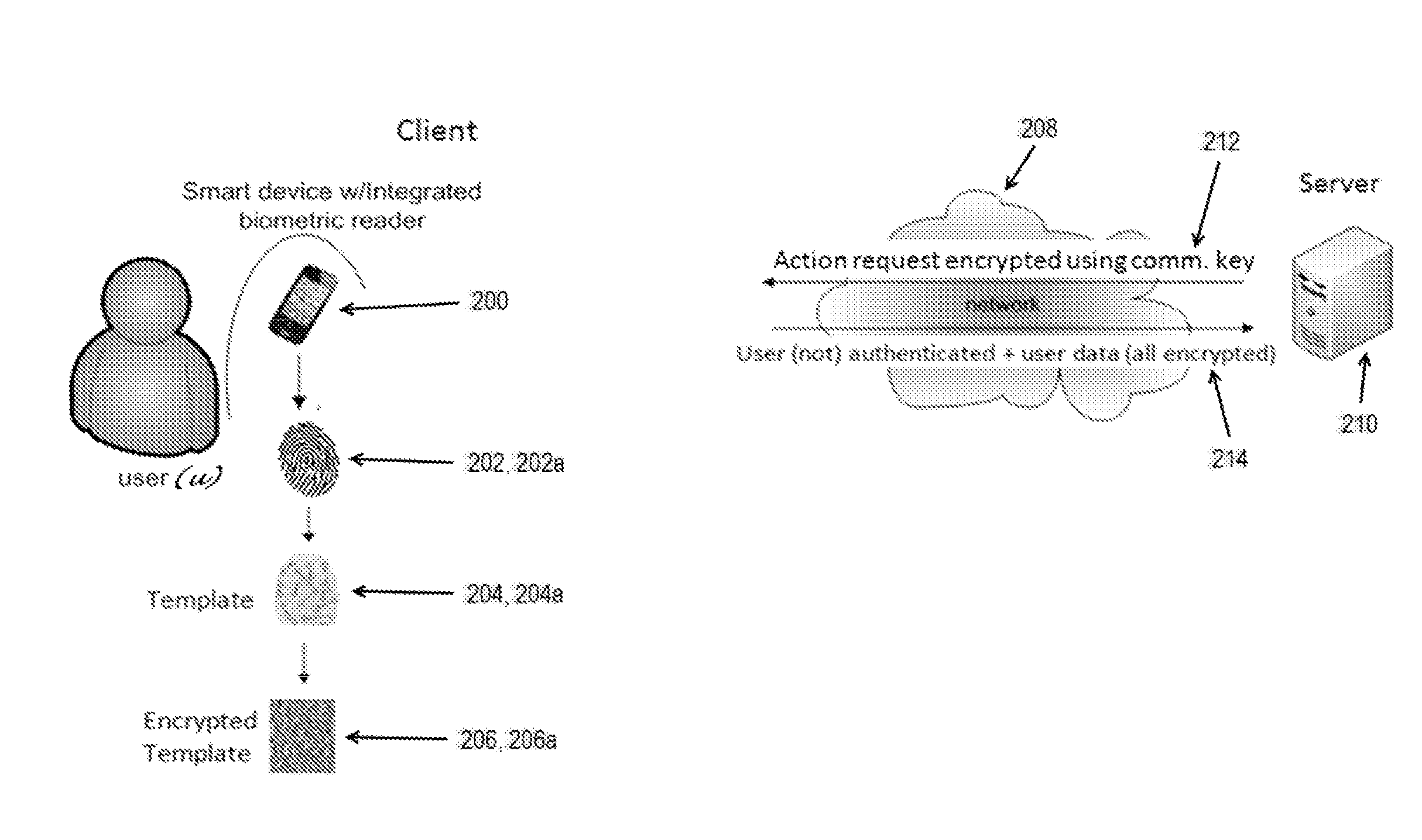
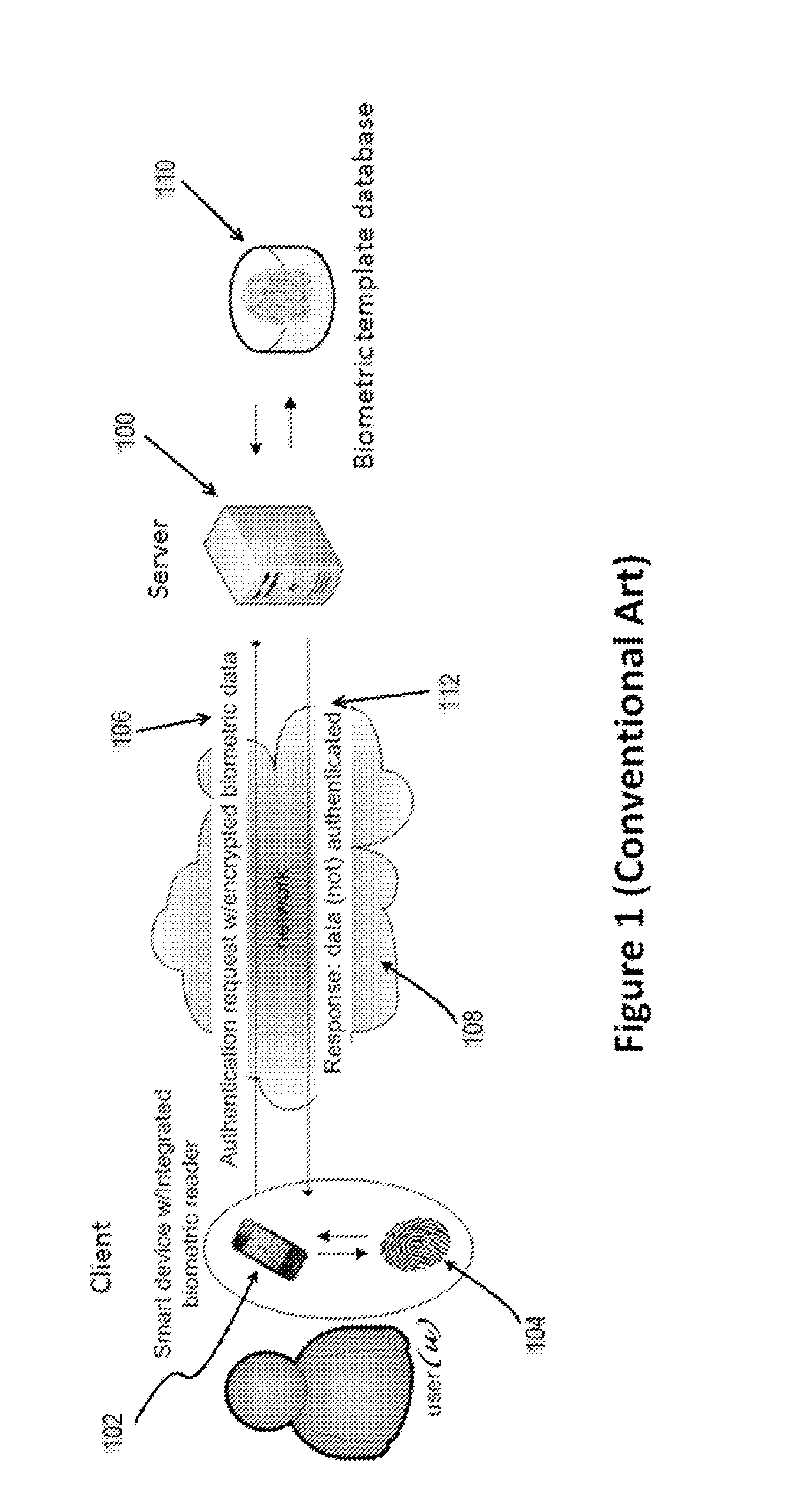
Biometric verification with improved privacy and network performance in client-server networks
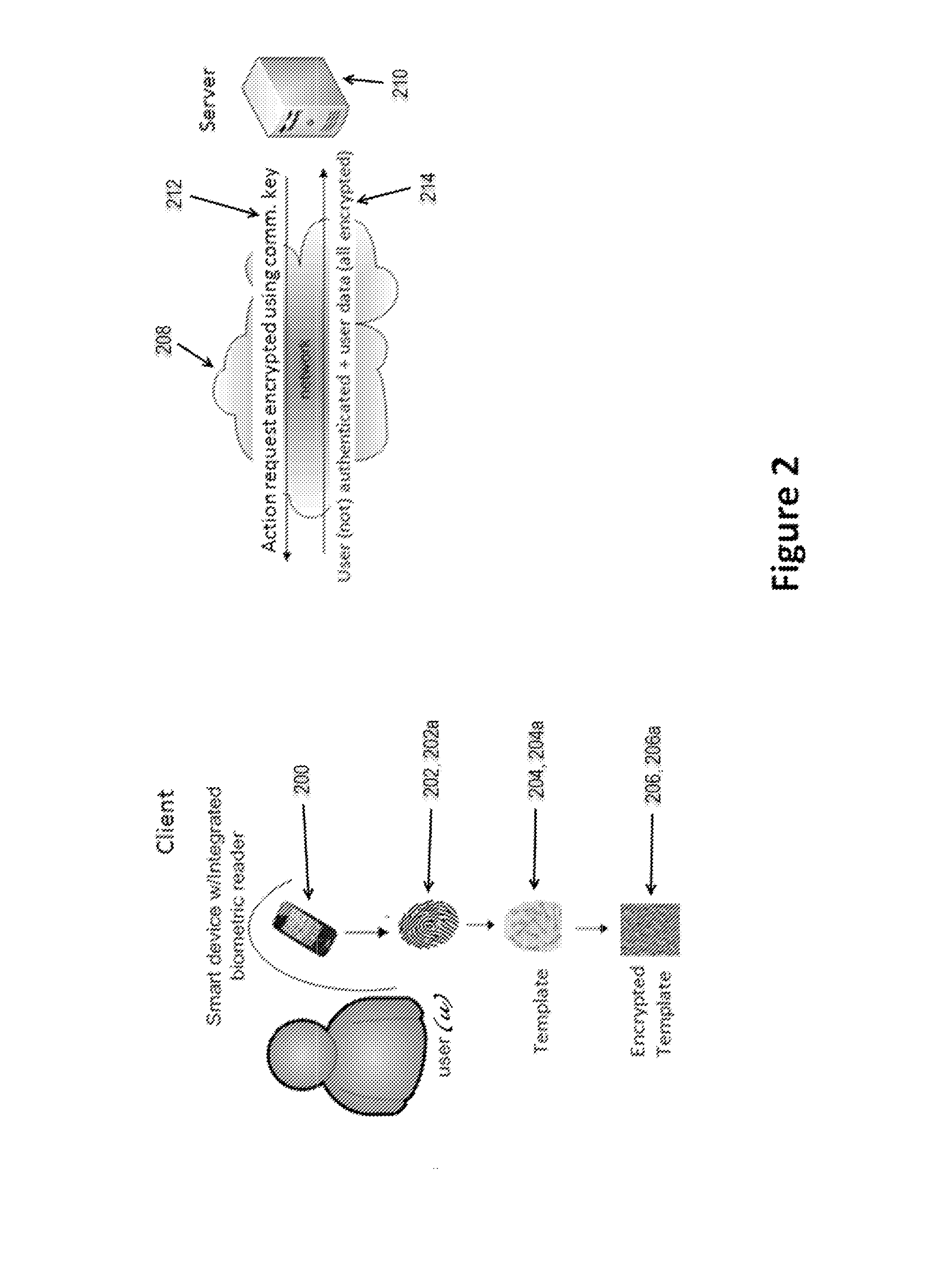
ActiveUS20140337635A1Safety be assureSafety is assuredDigital data authenticationTransmissionClient-sideNetwork performance
The present invention relates to improving the privacy of biometric information used in biometric authentication of identity by retaining all biometric information corresponding to a given user, and conducting all transactions related thereto (i.e., the actual authentication process) on a client (i.e., user) side of the system, thereby maximizing the user's control over biometric information corresponding to himself and preventing the storage of biometric templates on third-party servers outside of the control of the concerned individual. In a particular example of the present invention, security for the biometric information is further enhanced by encrypting the biometric template (used as a comparison reference during authentication, as is known) stored on the client side and completely destroying an original unencrypted version of the template. Also specified is secure storage of encryption keys for encrypting biometric data at the client. In yet a further example of the present invention, authentication is preferably conducted using the encrypted biometric templates.
Owner:KONVALINKA IRA
Automated banking machine and monitoring method
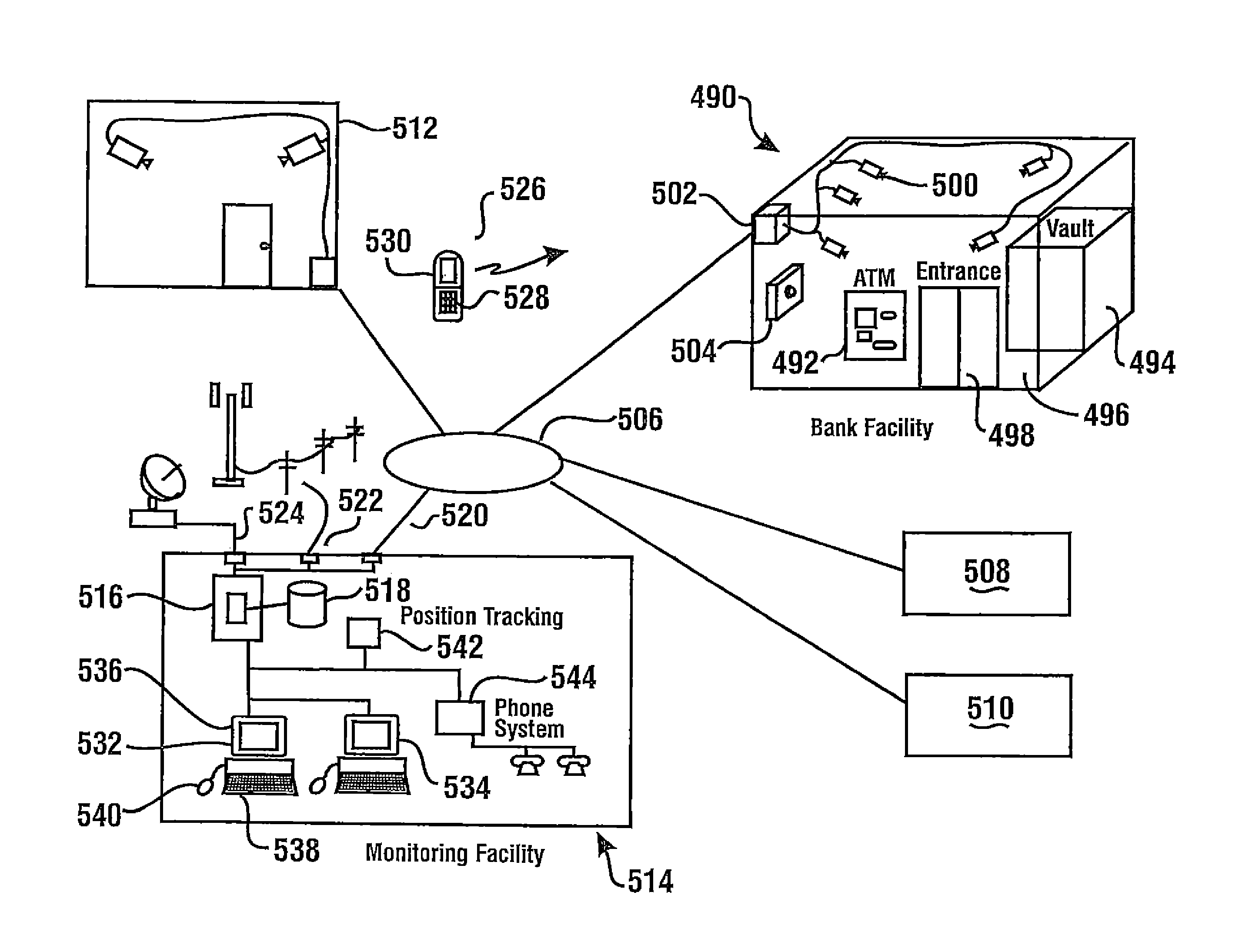
InactiveUS8474704B1Programmed more readilyEasy programmingComplete banking machinesFinanceData recordsFinancial transfer
An automated banking machine is part of a banking system that can operate to cause financial transfers responsive to data read from data bearing records, including user cards. The machine is in operative connection with a system operable to capture images related to activity that is conducted at or adjacent to the machine. The machine is positioned at a banking facility having a vault and an entrance. A plurality of cameras are positioned at the facility. Captured images can be analyzed at a remote monitoring center. The monitoring center can operate to assure that employees or customers of the banking facility can safely enter and / or exit the banking facility.
Owner:SECURITAS ELECTRONICS SECURITY INC
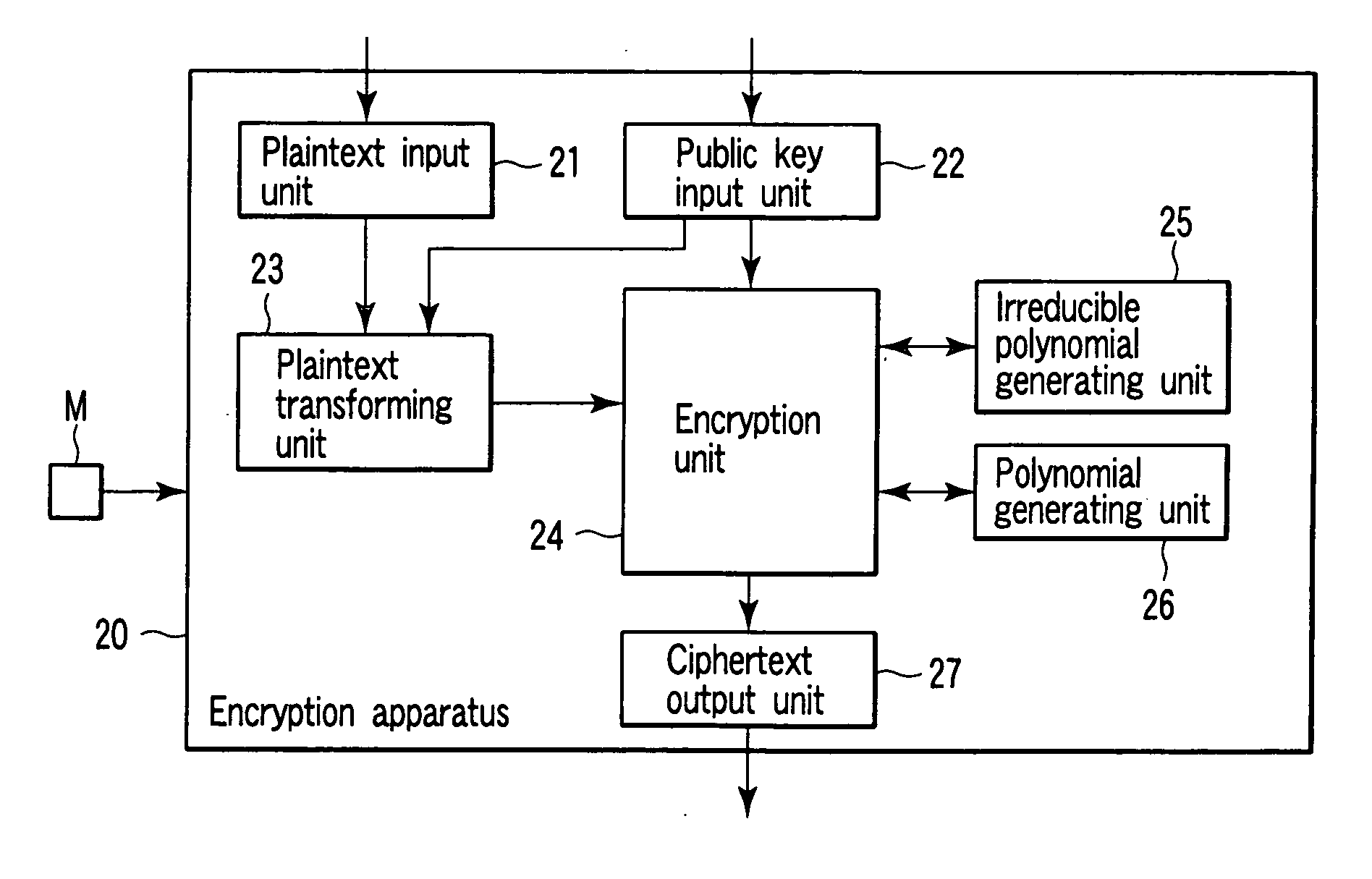
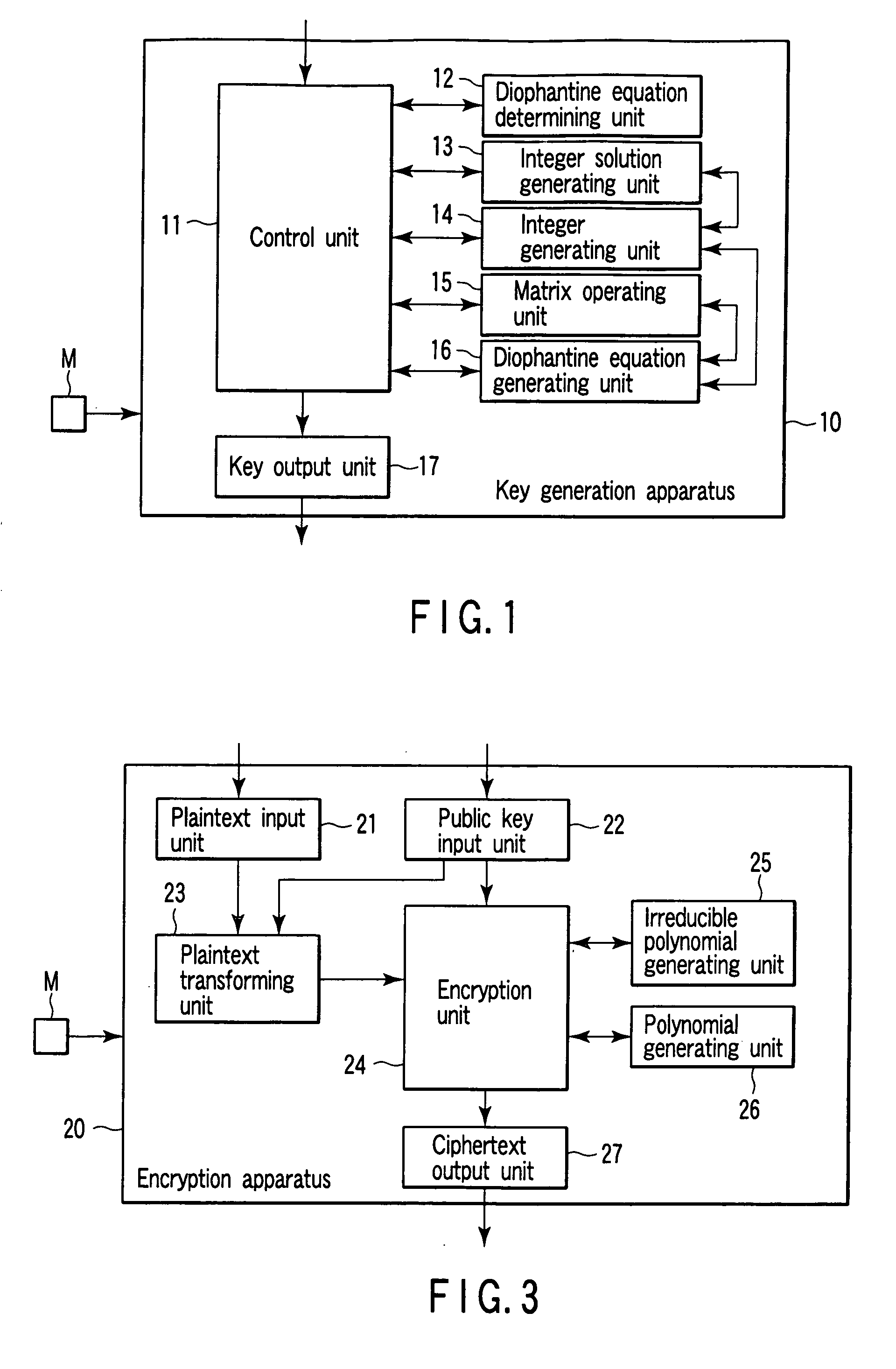
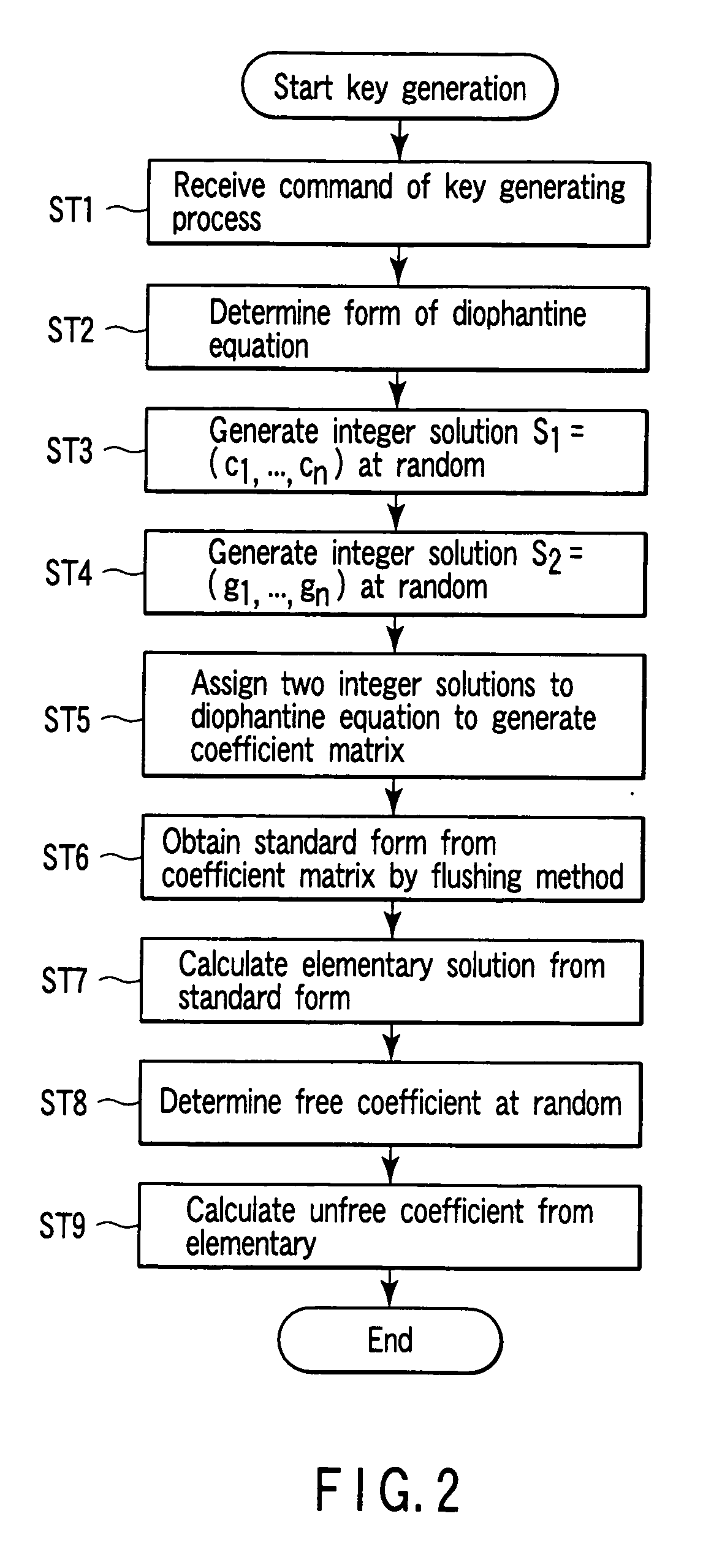
Encryption apparatus, decryption apparatus, key generation apparatus, program and method therefor
InactiveUS20060251247A1Safety is assuredQuantum computersPublic key for secure communicationQuantum computerKey generation
According to one aspect of the present invention, a public-key encryption method which can assure security even though a quantum computer appears, which can be securely realized by an existing computer, and which may be realized in a low-electric-power environment can be constituted. More specifically, one spect of the present invention uses an integer solution of a diophantine equation as a private key. In this manner, an encryption apparatus, a decryption apparatus, or a key generation apparatus of a public-key encryption method using a problem that calculates an integer solution of a diophantine equation having no general solution algorithm as the basis of security is realized. Therefore the above problem can be solved.
Owner:KK TOSHIBA
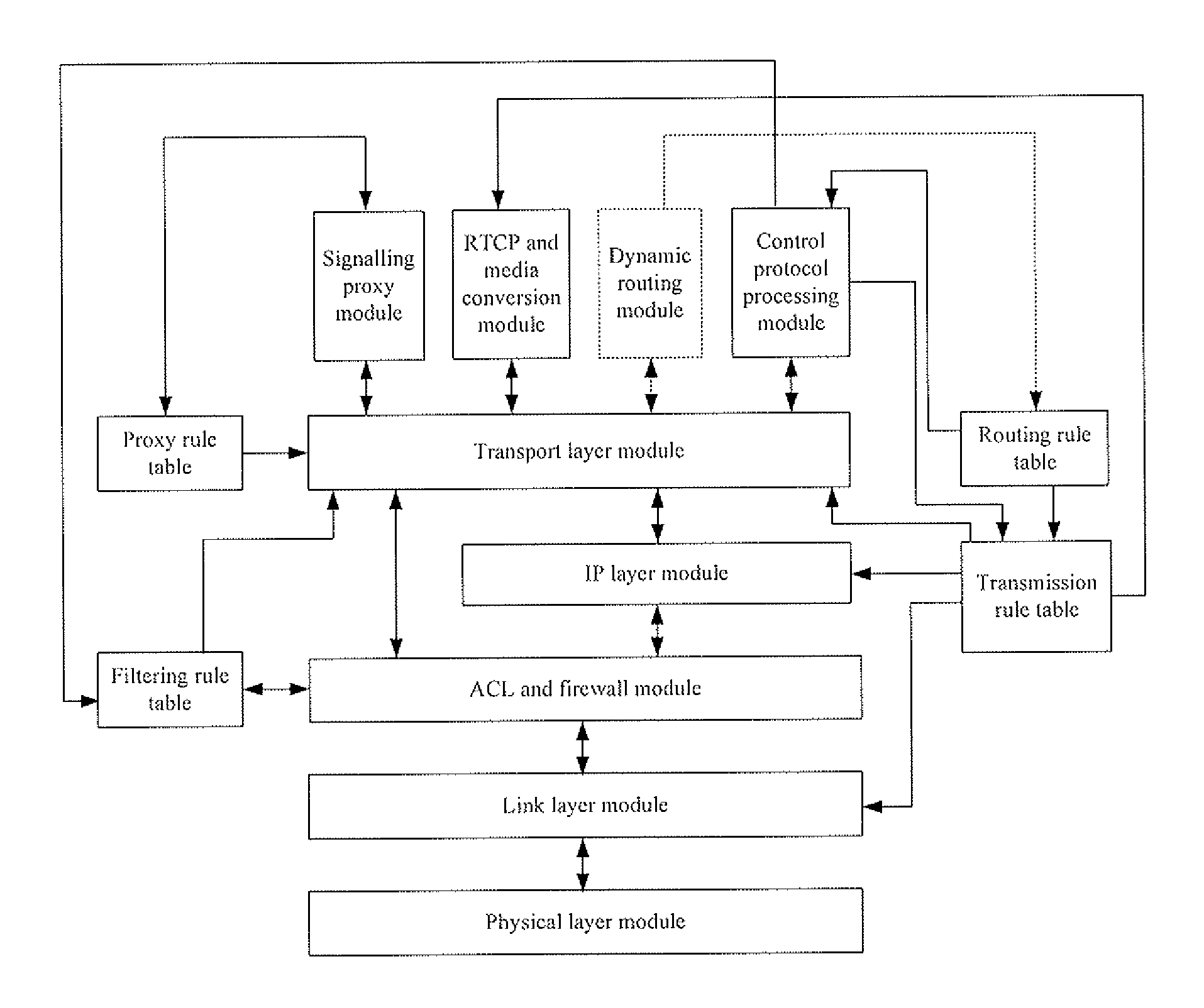
IP inter-working gateway in next generation network and method for implementing inter-working between IP domains
ActiveUS20070211738A1Reduce complexityLow investmentTime-division multiplexData switching by path configurationTransport layerProtocol stack
Owner:HUAWEI TECH CO LTD
Heating and blowing apparatus
InactiveUS7644511B2Efficient dischargeStable conditionDrying gas arrangementsAir heatersIon emissionElectrical and Electronics engineering
Owner:MATSUSHITA ELECTRIC WORKS LTD
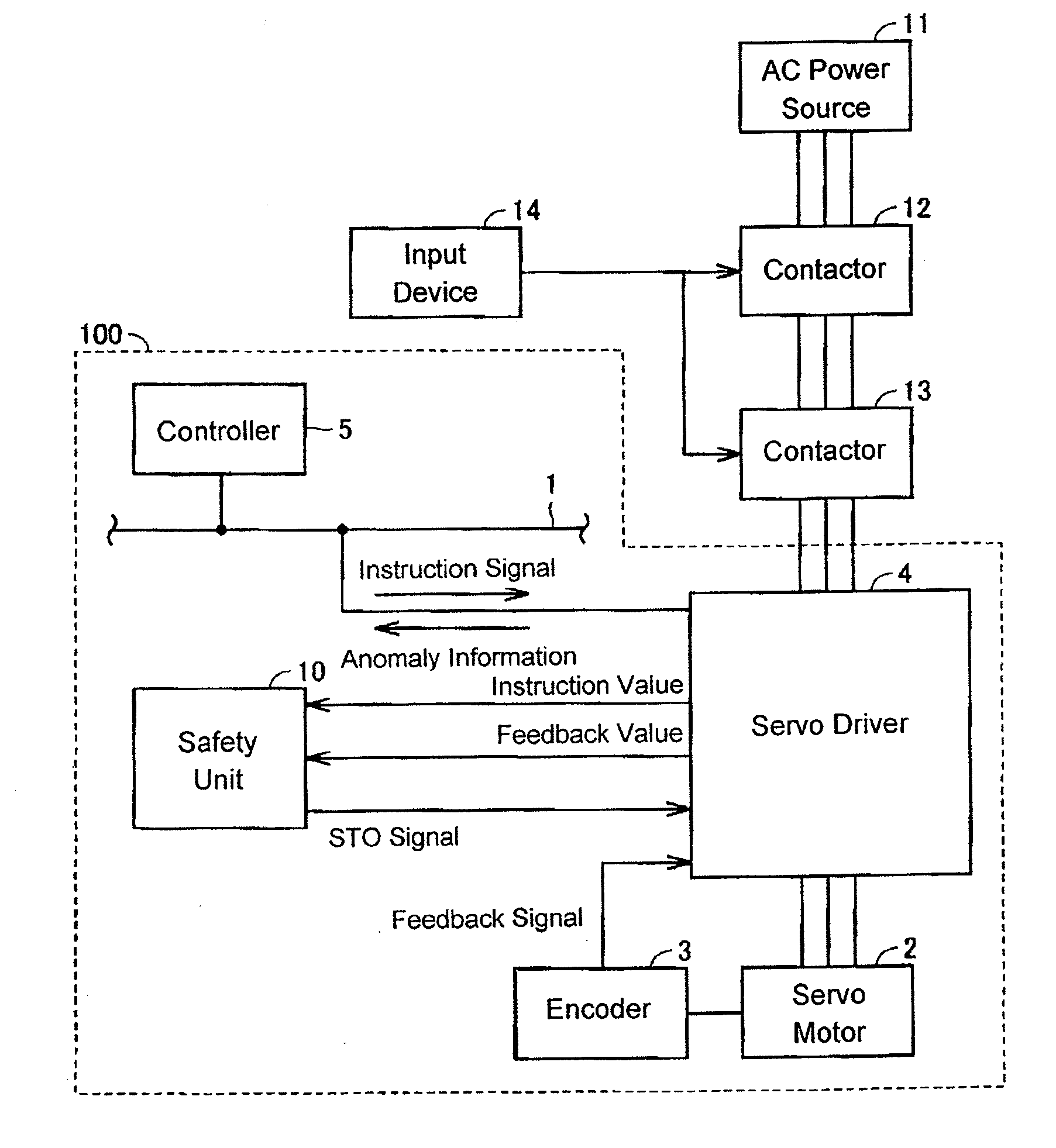
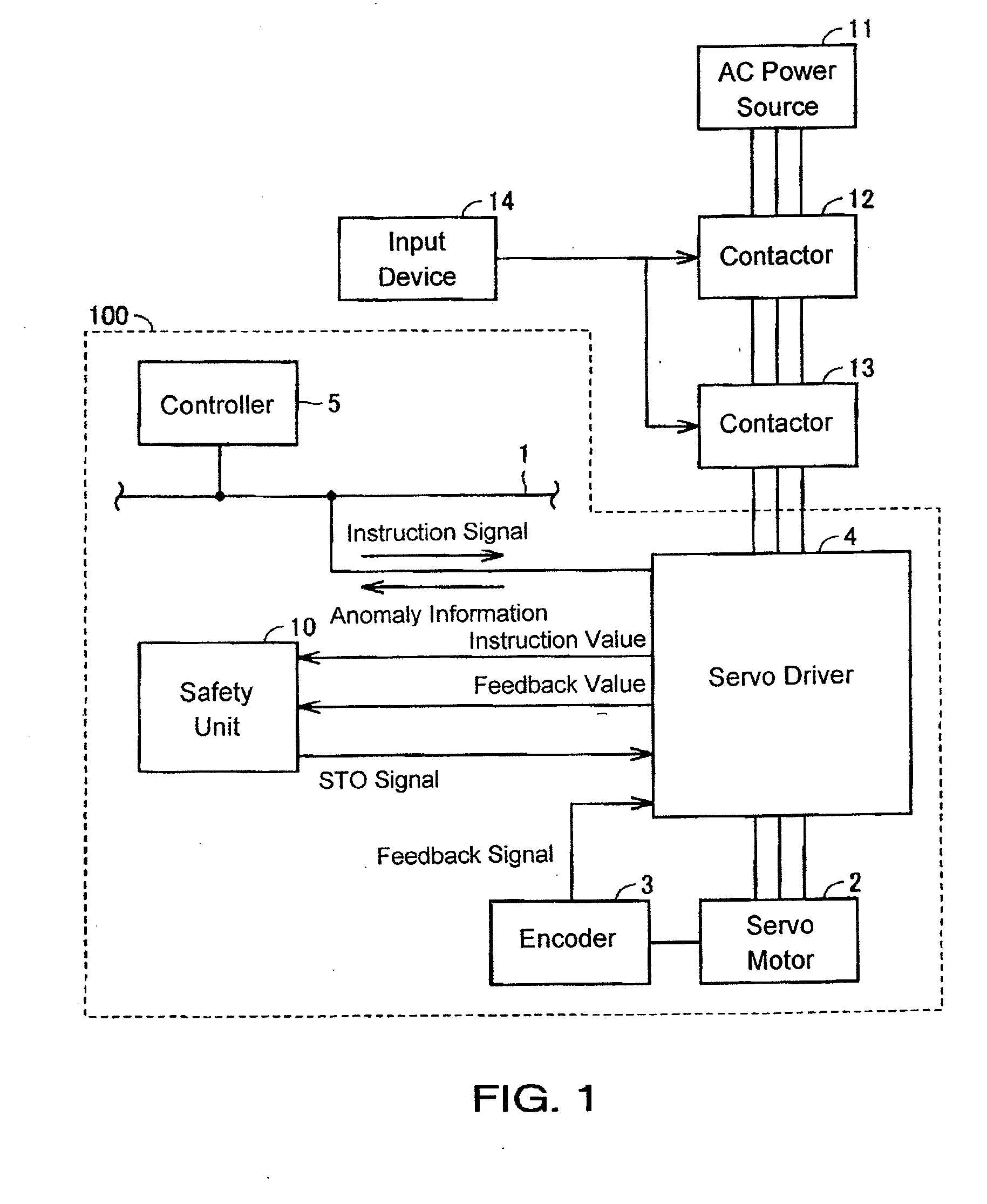
Servo system, servo motor driving device, safety unit and method for controlling servo system
ActiveUS20110221377A1Safety is assuredSafety of the servo system can be assuredSafety arrangmentsElectric motor controlElectricityMotor drive
A servo driver sets an instruction value for an operation of a servo motor based on an instruction signal from a controller. The servo driver sends the instruction value and a feedback value obtained based on a feedback signal to a safety unit. When at least one of the instruction value and the feedback value sent by the servo driver has an abnormal value, an STO signal is generated and sent to the servo driver. When the STO signal is input to the servo driver, the servo driver stops the supply of electricity to the servo motor.
Owner:ORMON CORP
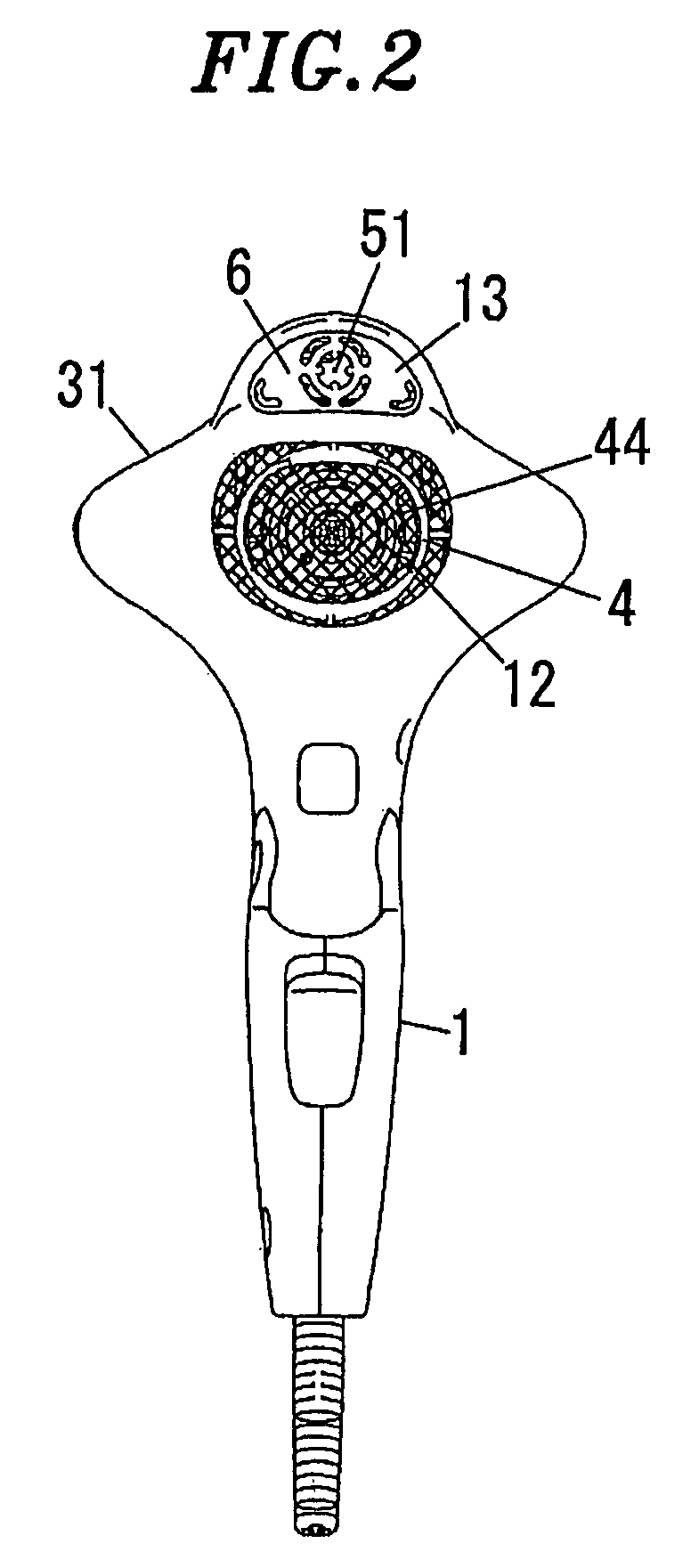
Numerical control machine tool
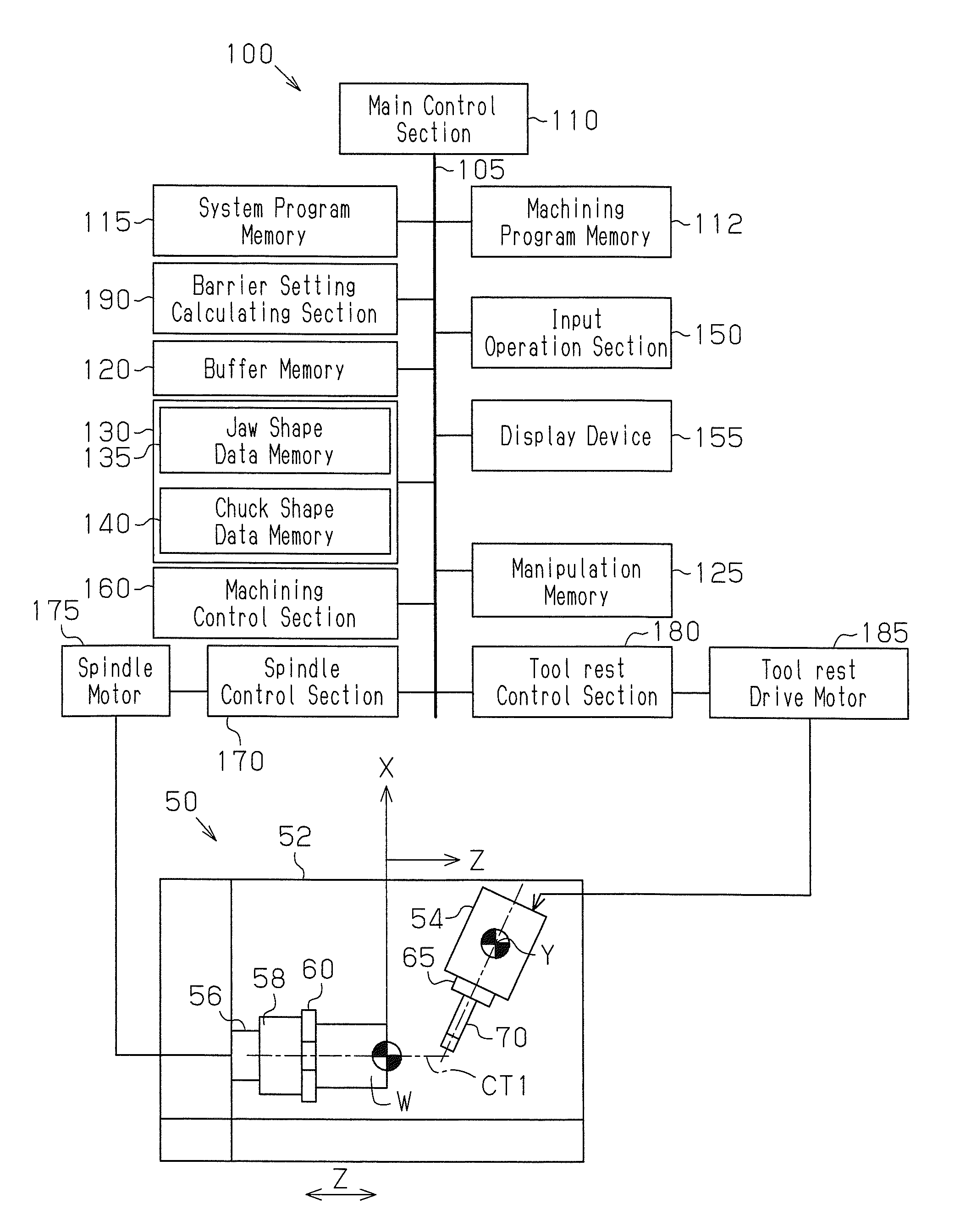
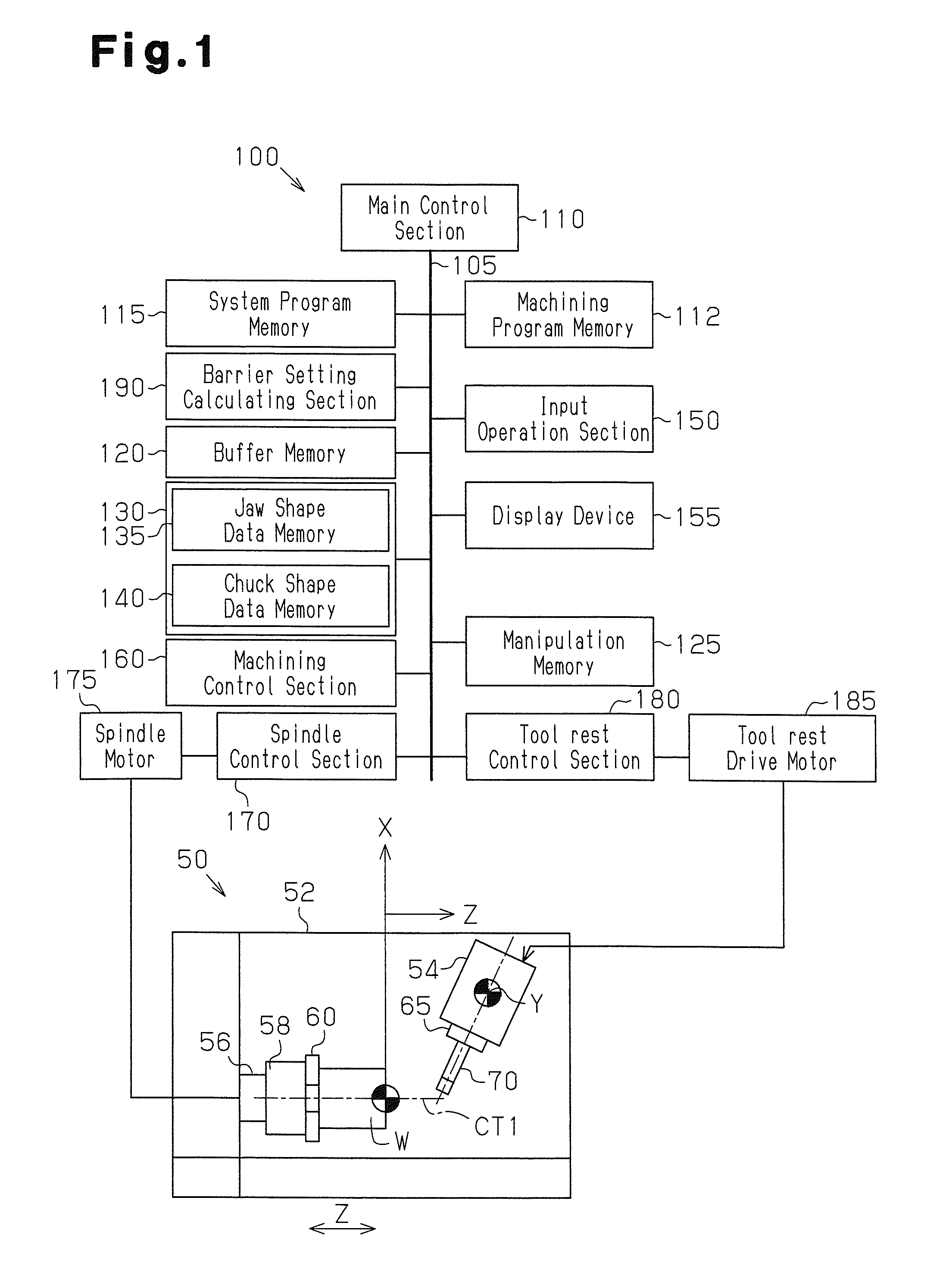
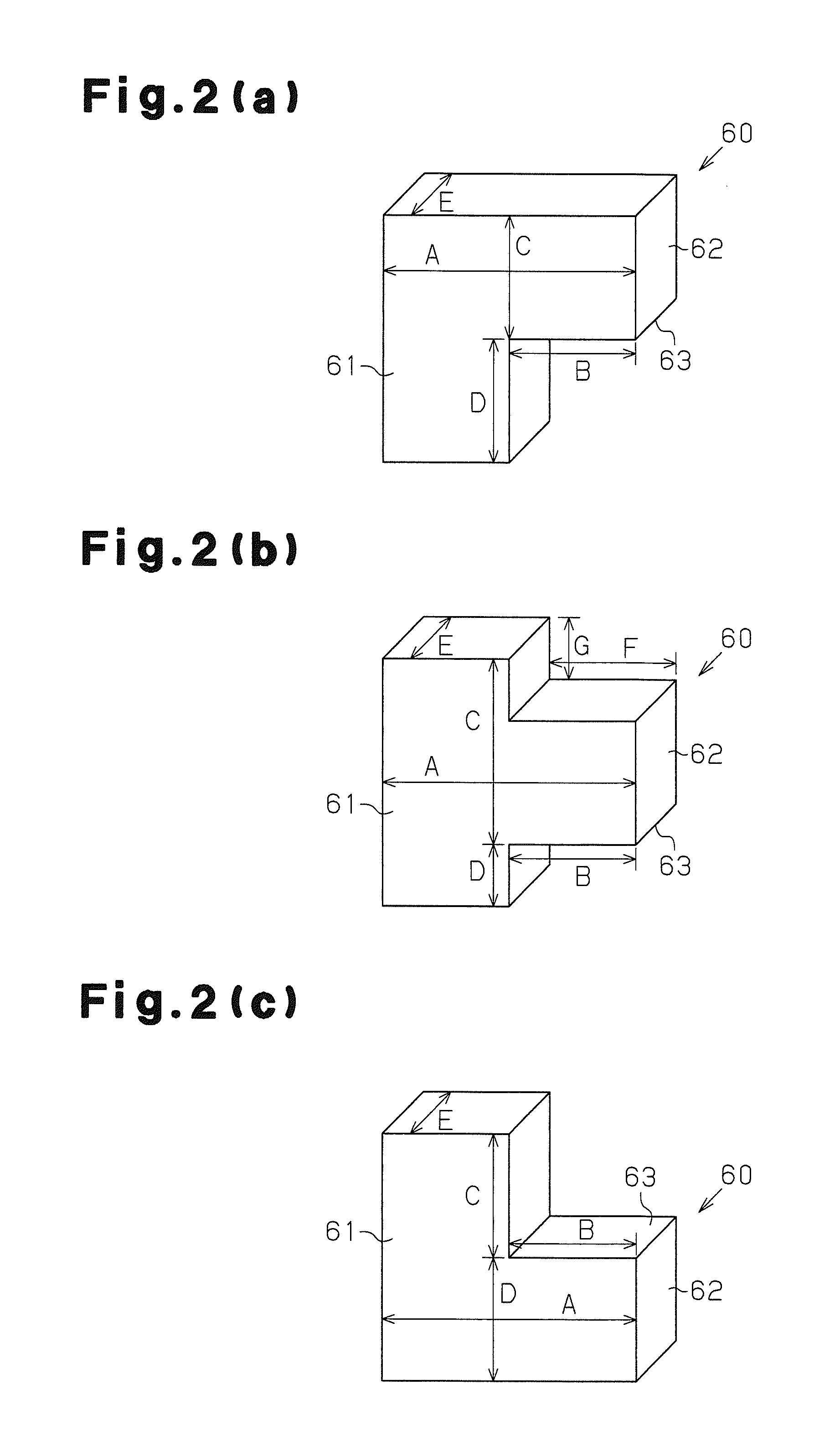
ActiveUS20120239182A1Safety is assuredIncrease the burdenProgramme controlSpecial data processing applicationsTouch panelMachine control
An NC control unit 100 includes a touch panel display device 155 through which a barrier canceling command is input and a machining control section 160 that performs an interference check for interference between a milling tool 70 and a chuck 58 and jaws 60. When the machining control section 160 determines that interference occurs and stops movement of a tool rest 54, the machining control section 160 writes the barrier canceling command that commands cancelation of the interference check for a process of a machining program where the interference has been determined based on manipulation of the display device 155. When the machining program including the barrier canceling command is carried out to machine subsequent workpieces, the machining control section 160 omits the interference check for the process corresponding to the barrier canceling command.
Owner:YAMAZAKI MAZAK KK
Wireless remote-control model
InactiveUS20080220687A1Improve securityEasy maintenanceToy aircraftsRemote-control toysRemote controlNormal conditions
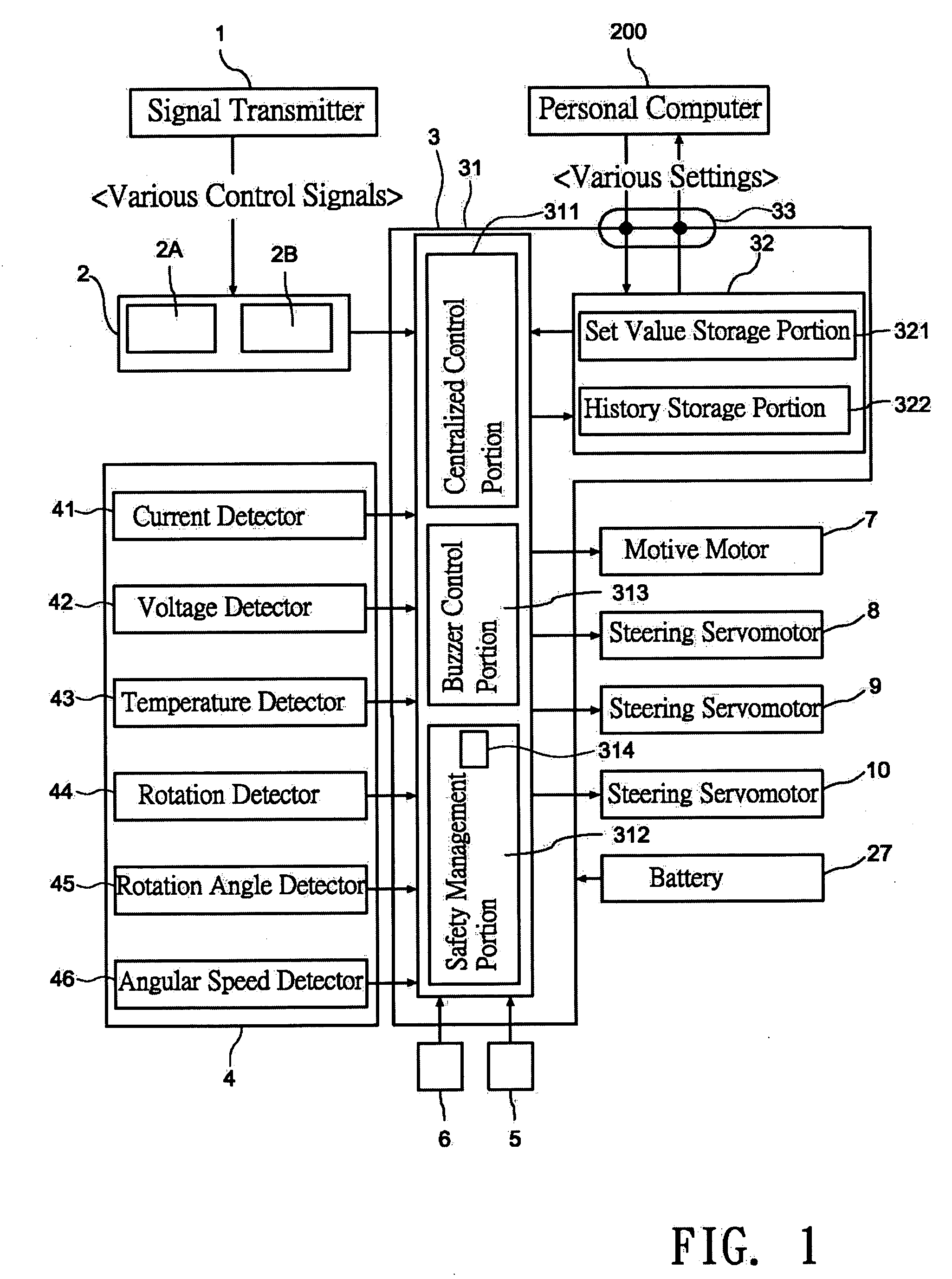
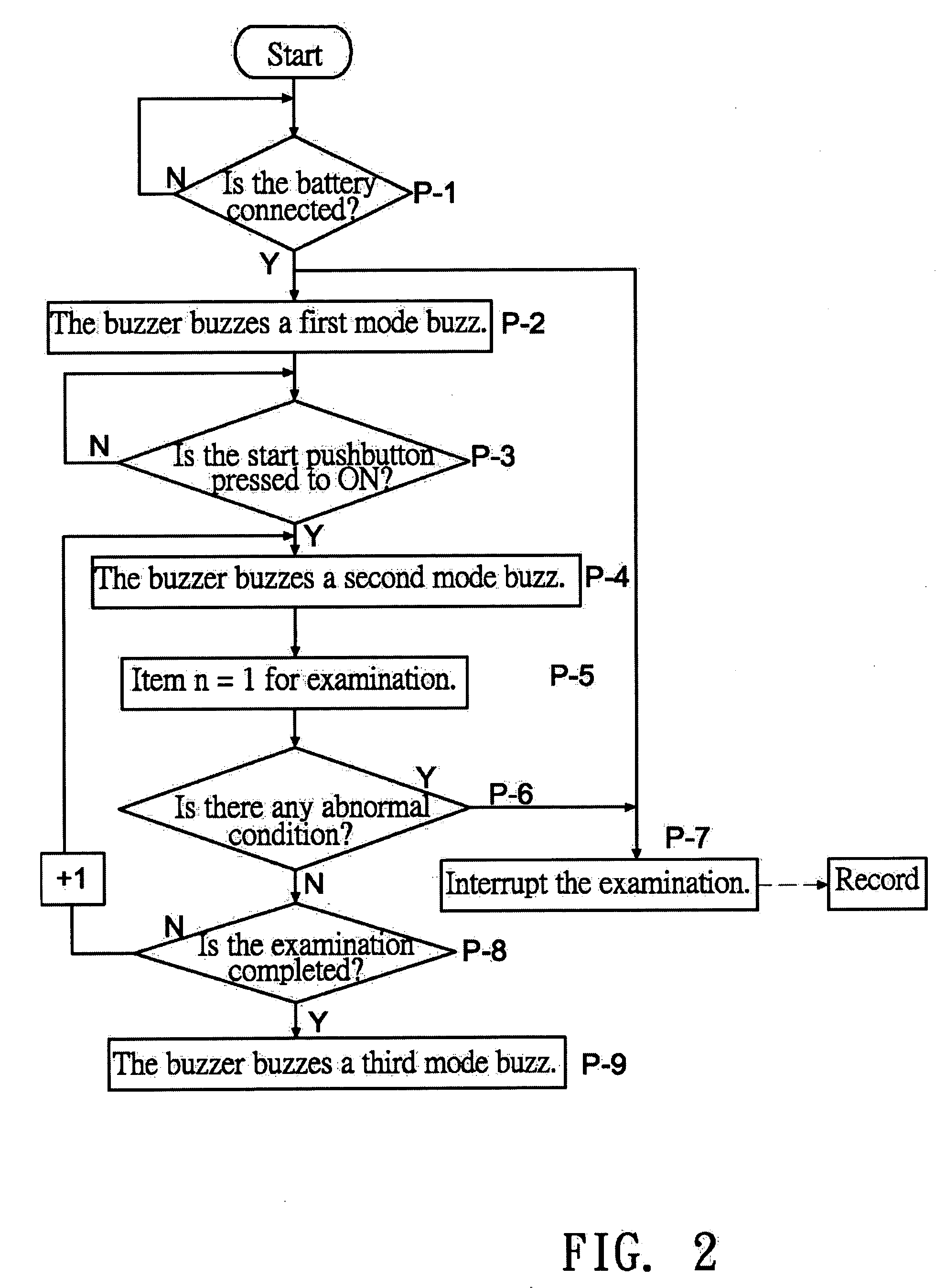
A wireless remote-control model includes a safety management portion having a central control device, and the safety management portion includes a determination portion, such that when a battery is connected correctly, a first mode buzz signal instruction is sent to a buzzer control portion for indicating that the battery is connected. If the battery is connected correctly and a start pushbutton is pressed during an examination period, or a second mode buzz signal instruction is sent to the buzzer control portion for indicating that the operation is started, or a third mode buzz signal instruction is sent to the buzzer control portion for indicating that a power motor is at a driving idle state when the examination determines a normal condition, so as to assure the safety of an operator (or a user) as well as the safety of the wireless remote-control model itself.
Owner:THUNDER TIGER
Headrest for vehicles
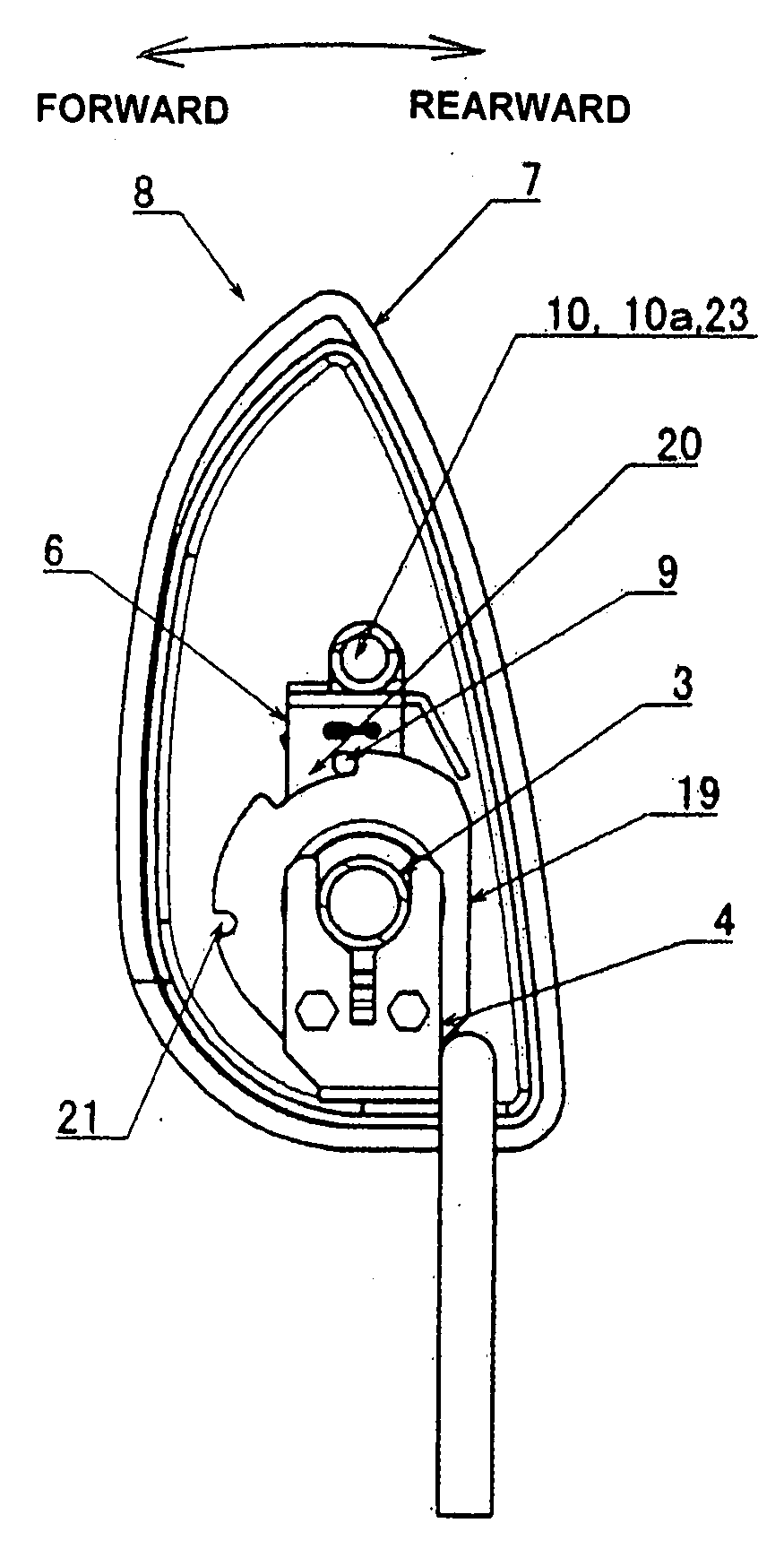
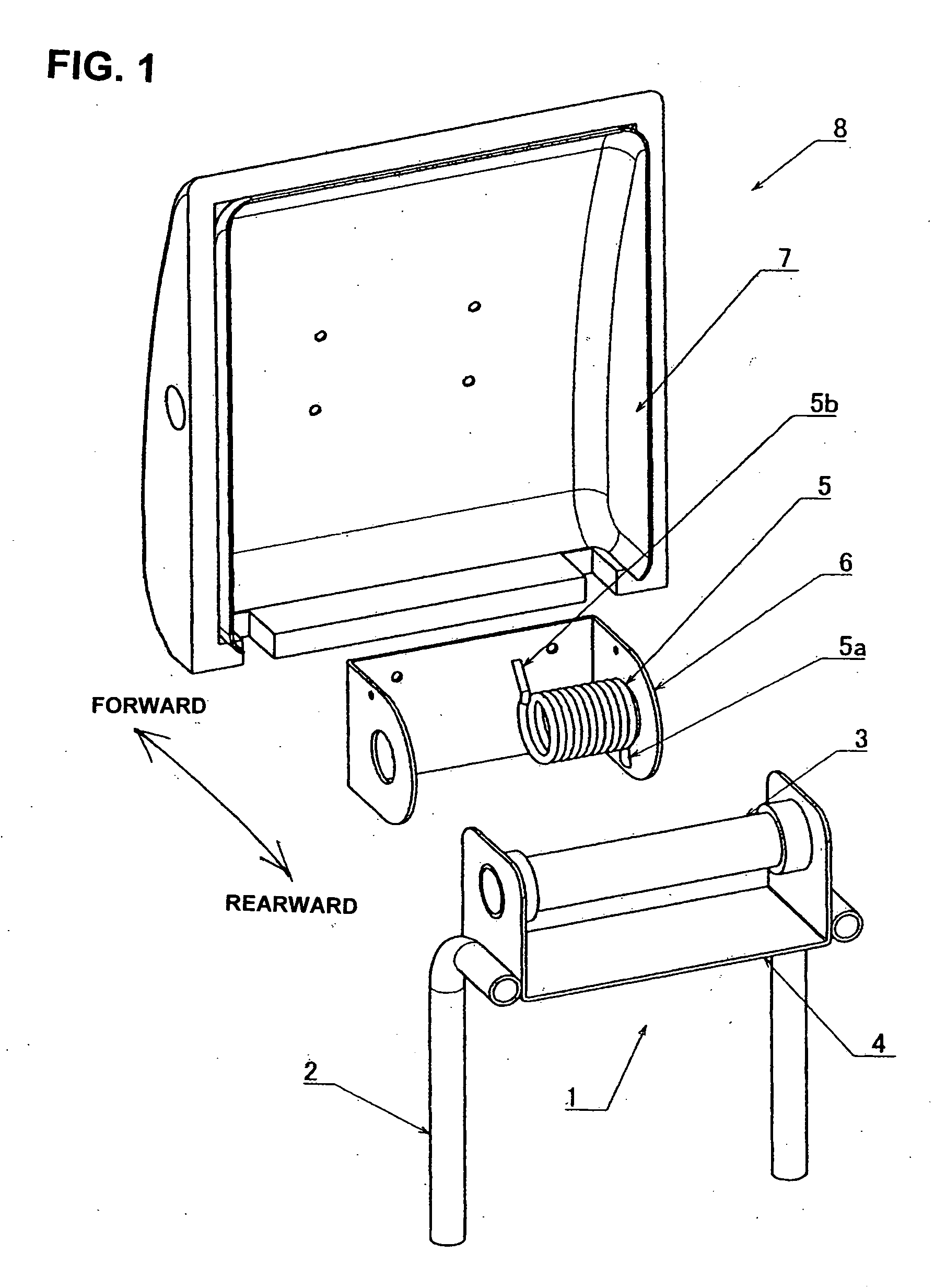
ActiveUS20080277989A1Easy to adjustReduce fatigueOperating chairsDental chairsCoil springEngineering
A headrest for vehicles including a stationary plate secured to the seat back of a vehicle; an attachment shaft supported by the stationary plate; a coil spring wound on the attachment shaft and having a fixed end and a free end with its inner diameter being smaller than the outer diameter of the attachment shaft; and a headrest base plate attached to the stationary plate so as to turn forward and rearward. The fixed end of the coil spring is fixed to the base plate so as to secure the attachment shaft to the base plate or the fixed end of the coil is fixed to the stationary plate so as to secure the attachment shaft to the base plate, and the winding direction of the coil spring is set in a direction that tightens the spring when the base plate is turned rearward, thus restricting this rearward turning.
Owner:BIZEN HATSUJO
Headrest for vehicles
A headrest for vehicles including a stationary plate secured to the seat back of a vehicle; an attachment shaft supported by the stationary plate; a coil spring wound on the attachment shaft and having a fixed end and a free end with its inner diameter being smaller than the outer diameter of the attachment shaft; and a headrest base plate attached to the stationary plate so as to turn forward and rearward. The fixed end of the coil spring is fixed to the base plate so as to secure the attachment shaft to the base plate or the fixed end of the coil is fixed to the stationary plate so as to secure the attachment shaft to the base plate, and the winding direction of the coil spring is set in a direction that tightens the spring when the base plate is turned rearward, thus restricting this rearward turning.
Owner:BIZEN HATSUJO
Nonaqueous electrolytic solution and lithium secondary batteries
InactiveUS7294436B2InhibitionBattery safetyOrganic electrolyte cellsLi-accumulatorsElectric capacitySolvent
Owner:UBE IND LTD
Electric rotary grater
InactiveUS6966510B2Quickly gratesExtended service lifeCoffee millsSpice millsEngineeringMechanical engineering
An electric rotary grater including an external cylinder and a roller being sheathed into the external cylinder and having a stirring plate connected to a blocking edge of the external cylinder. A chamber is defined each on both sides of the stirring plate which is connected to a grater disc having a plurality of grater holes. A power device having a power source disposed in a housing, and a pillar groove transversally disposed outside the housing into which the stirring plate is inserted and a housing pillar on both sides of the pillar groove. A transmission device being connected to the power device and having a motor, a retardation mechanism and a press switch in the housing. A top cover presses on a driven set assembly to make planet gears of the retardation mechanism run in idle and the housing and shell to rotate and thus driving the roller to rotate.
Owner:PAI
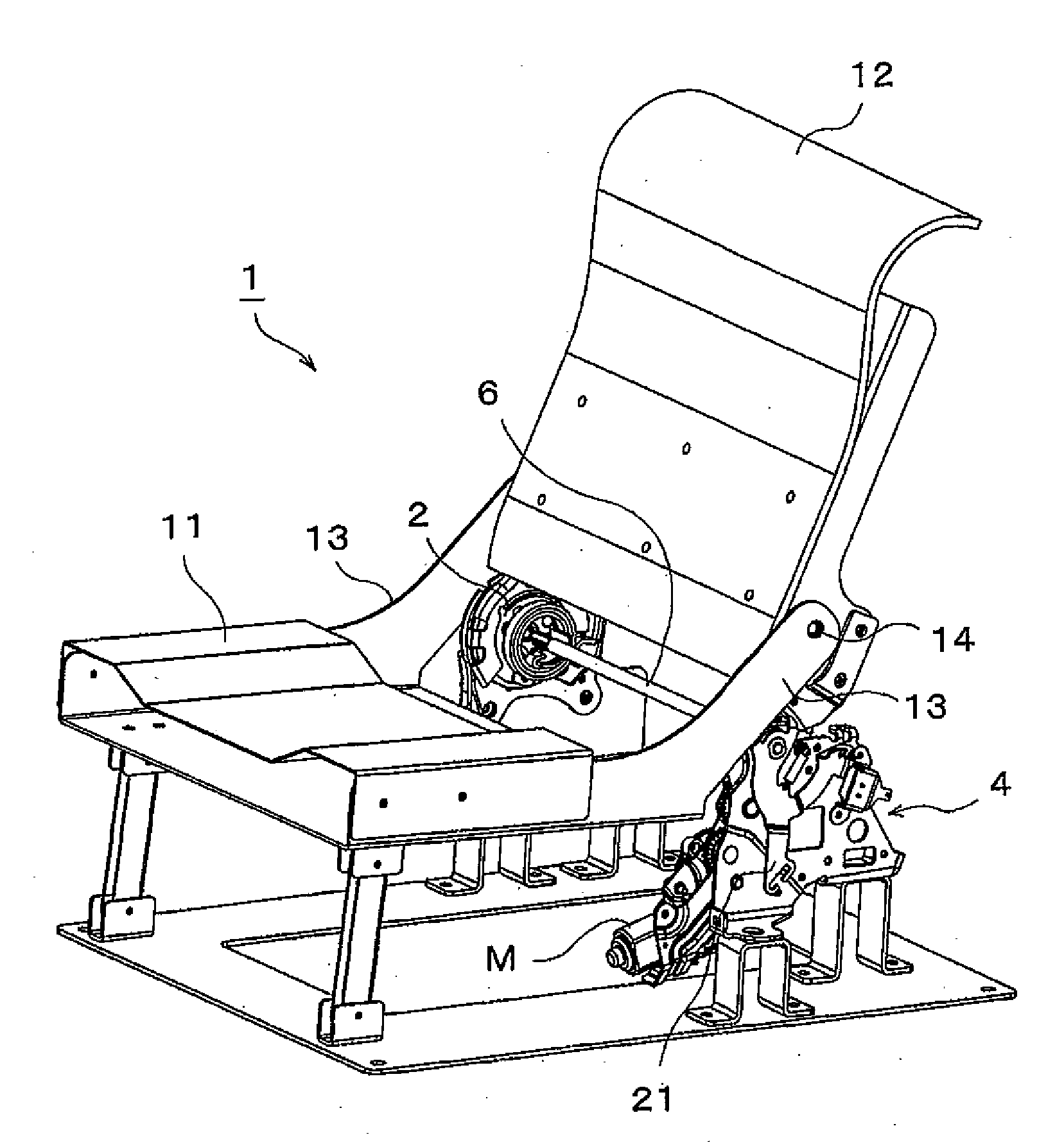
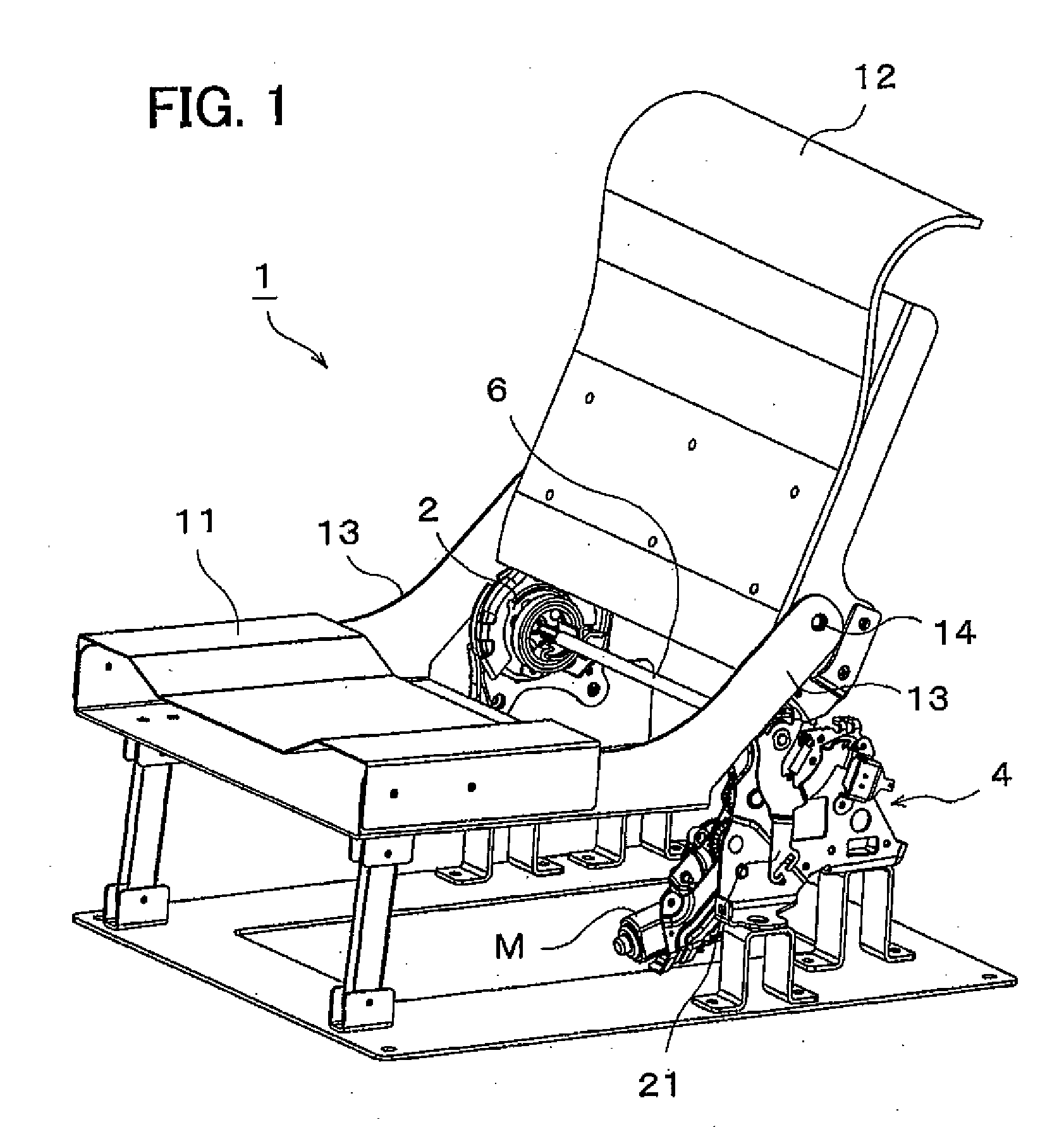
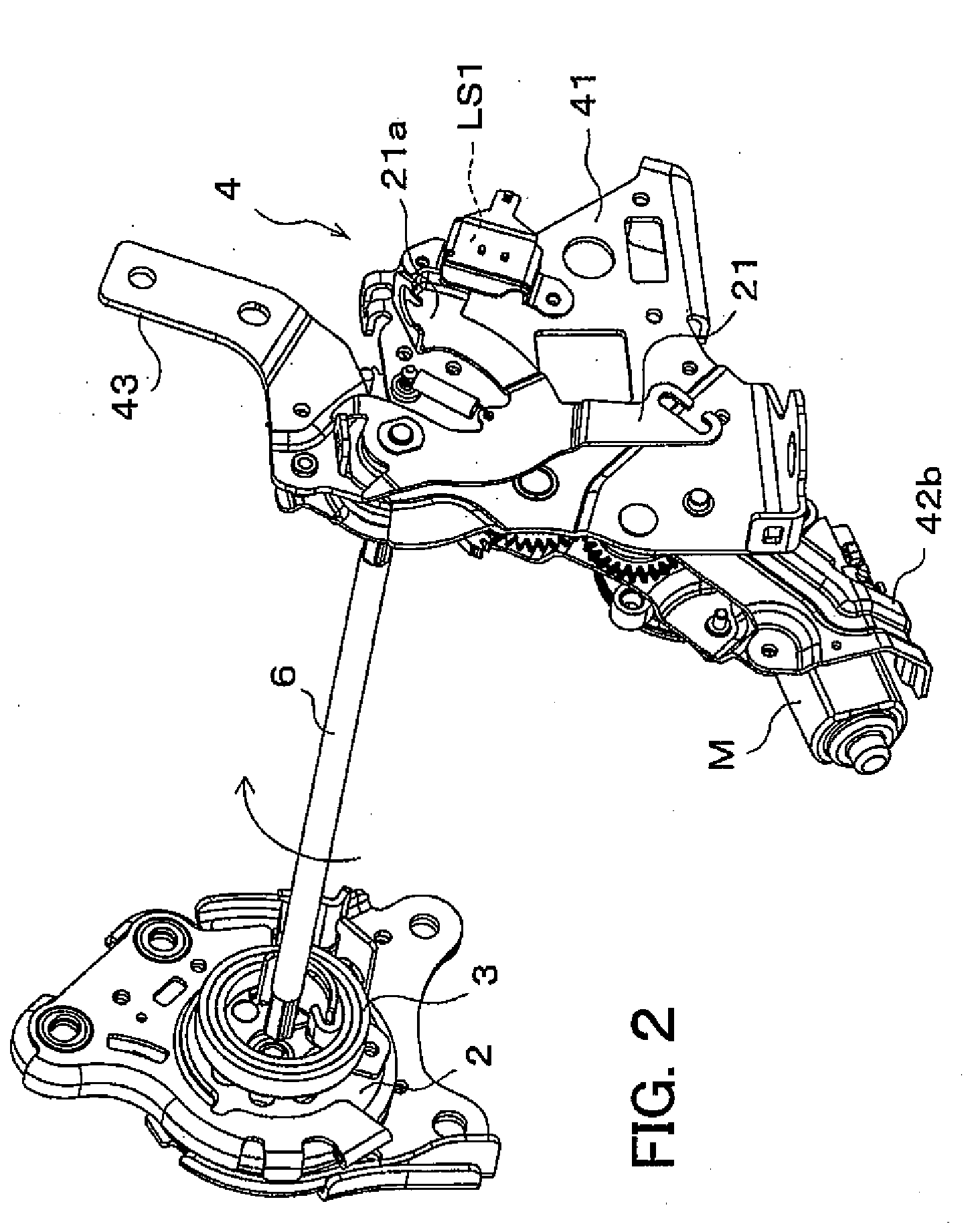
Seat apparatus
A seat apparatus includes a reclining device and a power assist mechanism coupled to the reclining device through a coupling rod. The power assist mechanism includes a motor; a seat back-side bracket which is tiltably provided to move the seat back; an operational gear which is turnable depending on a rotational direction of the motor; a rod gear provided integrally with the coupling rod; and a lever gear having a gear part capable of being engaged with the rod gear and an engaging part capable of being engaged with the operational gear. The lever gear transmits the turning of the operational gear to the rod gear.
Owner:IMASEN ELECTRIC IND
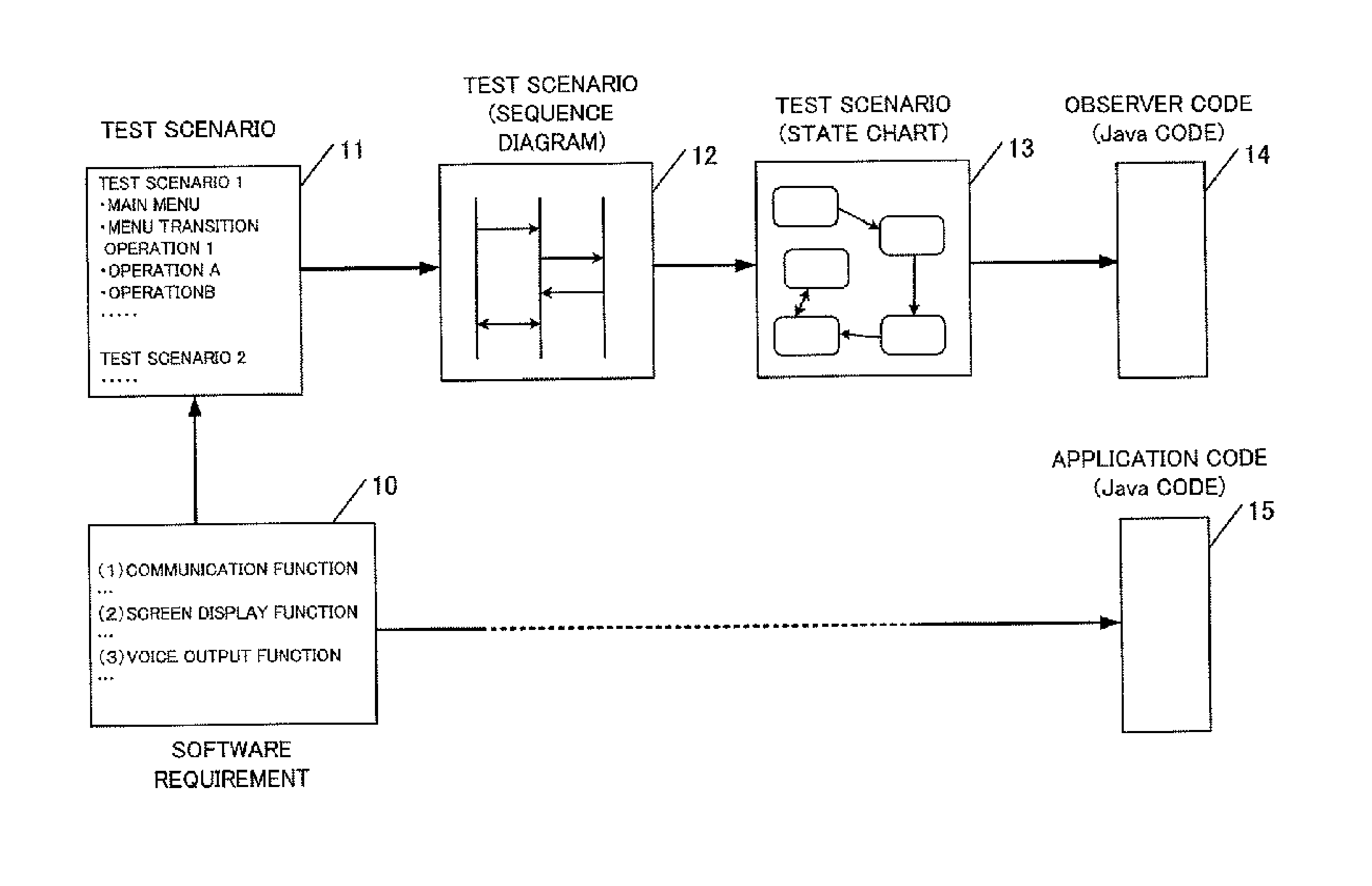
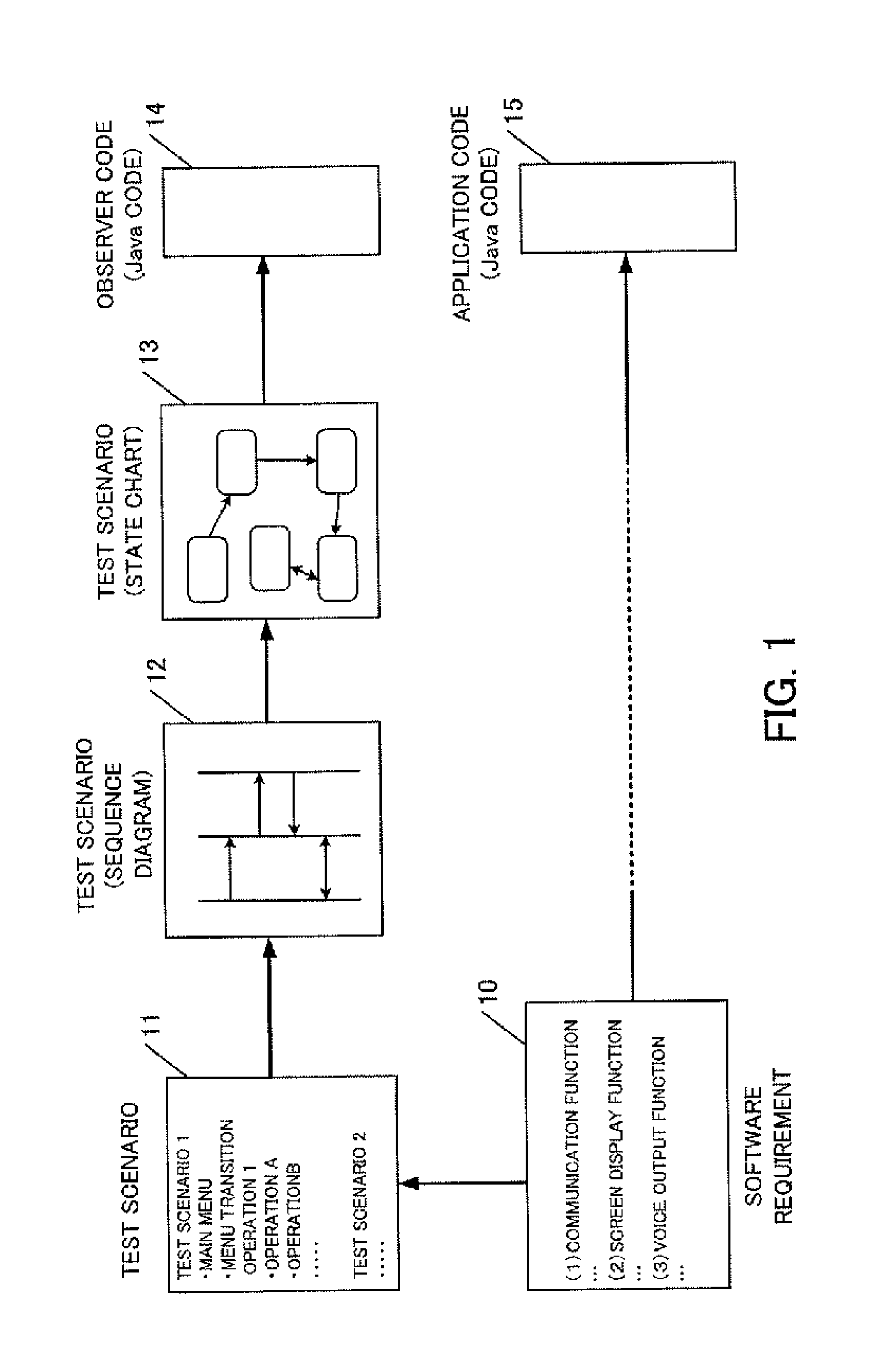
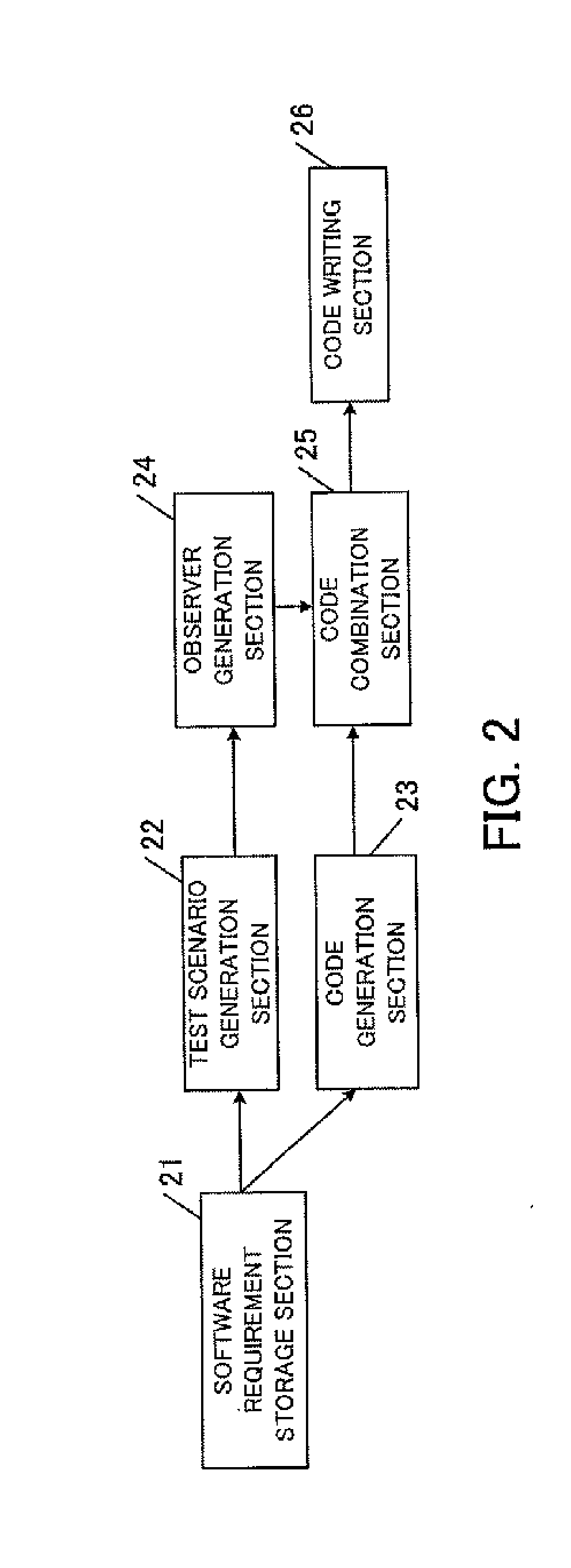
Computer having self-monitoring function and monitoring program
A computer comprises an input unit configured to acquire an input operation; a first program execution unit configured to execute a computing program performing a computation based on the input operation acquired by the input unit; a test scenario storage unit configured to store a plurality of test scenarios for the computing program; and a second program execution unit configured to execute a monitoring program determining whether or not the input operation acquired by the input unit corresponds to any of the plurality of the stored test scenarios.
Owner:TOYOTA JIDOSHA KK +1
Pressure Release Valve Assembly for Pressure Cooker
ActiveUS20130199633A1Easy to useSafety is assuredCheck valvesEqualizing valvesEngineeringPressure controlled ventilation
Owner:HASEGAWA TOM HIROSHI
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com