Equipment unlocking method and device, terminal equipment and medium
A device and terminal technology, applied in the computer field, can solve problems such as high maintenance costs and cumbersome steps, and achieve the effect of reducing maintenance costs and simplifying cumbersome steps
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
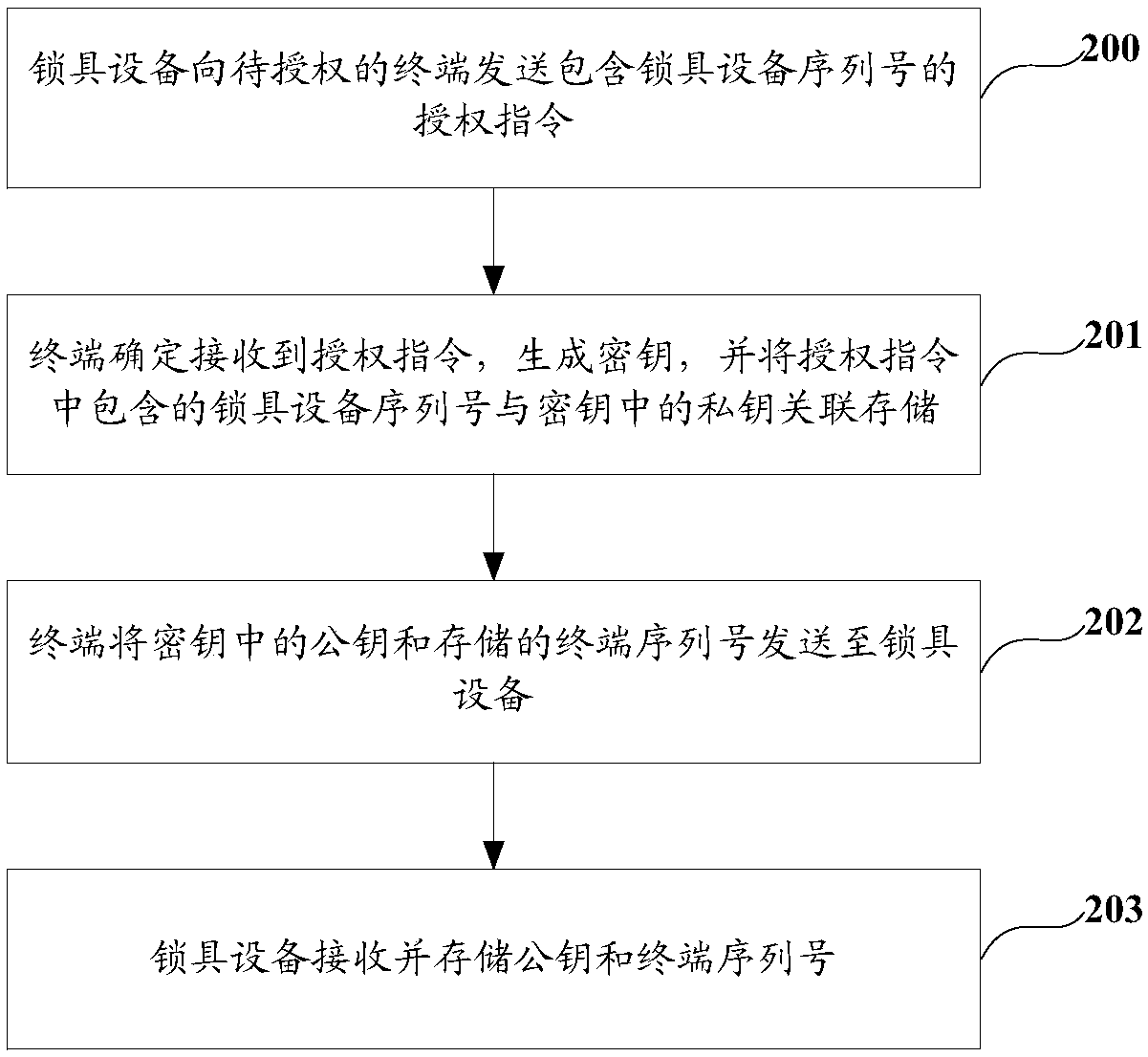
[0044] In order to simplify the cumbersome steps of information verification when verifying and unlocking the lock device through verification information, and reduce the maintenance cost of information verification for device unlocking, the embodiments of the present application provide a device unlocking method, device, terminal device and medium.
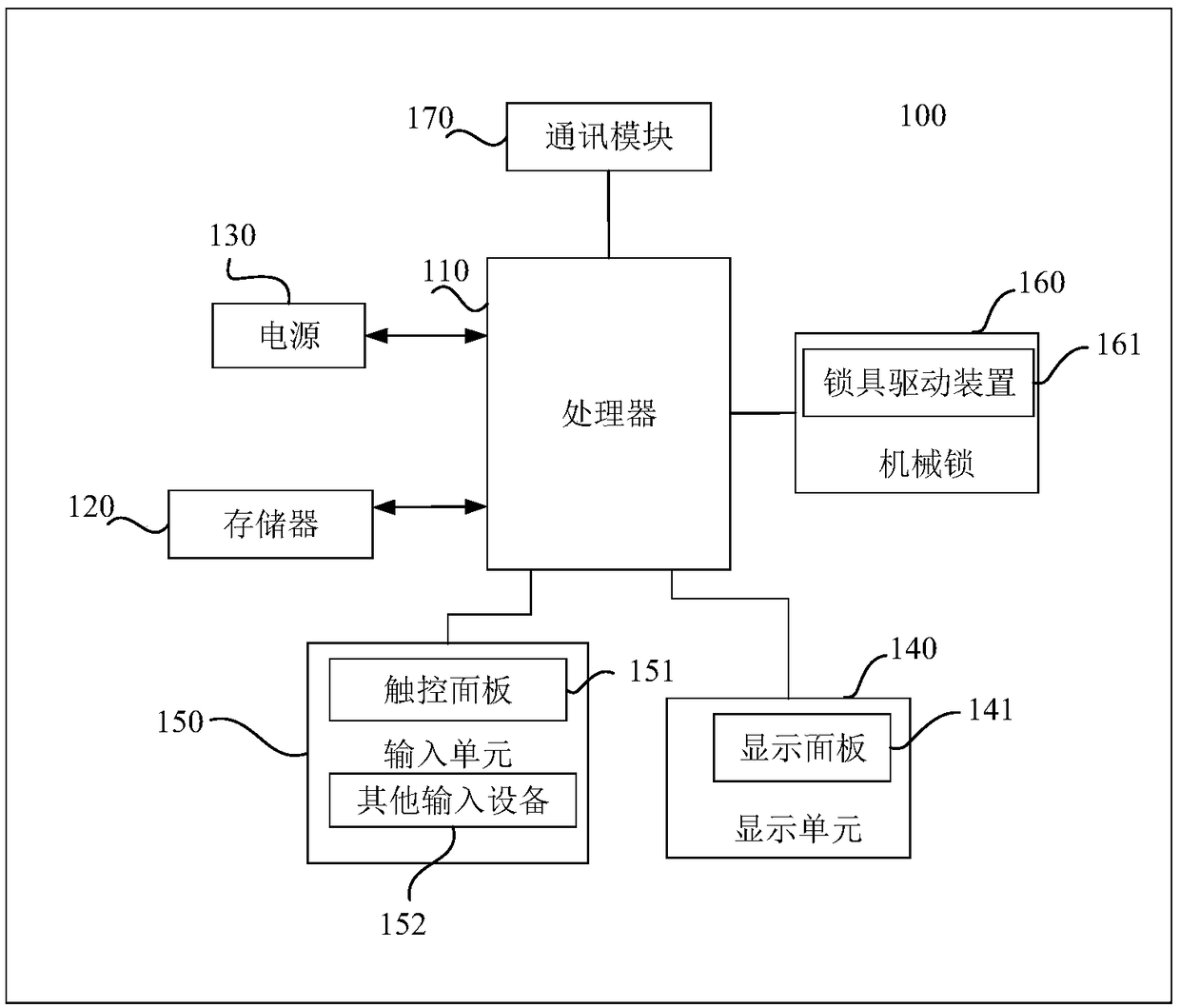
[0045] refer to Figure 1a Shown is a schematic structural diagram of a lock device provided in this application. The lock device 100 includes: a processor 110 , a memory 120 , a power supply 130 , a display unit 140 , an input unit 150 , a mechanical lock 160 and a communication module 170 .
[0046] The processor 110 is the control center of the lock device 100. It uses various interfaces and lines to connect various components, and executes various functions of the lock device 100 by running or executing software programs and / or data stored in the memory 120, thereby controlling the lock. The device is monitored as a whole.
...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com