Hard-disc fan-area data enciphering and deciphering method and system
A data encryption and sector-level technology, which is applied in the field of storage security in computer technology, can solve problems such as low security and slow encryption/decryption speed, and achieve the effects of improving security, increasing difficulty, and increasing flexibility
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0045] The present invention will be further described below in conjunction with the accompanying drawings and specific embodiments.
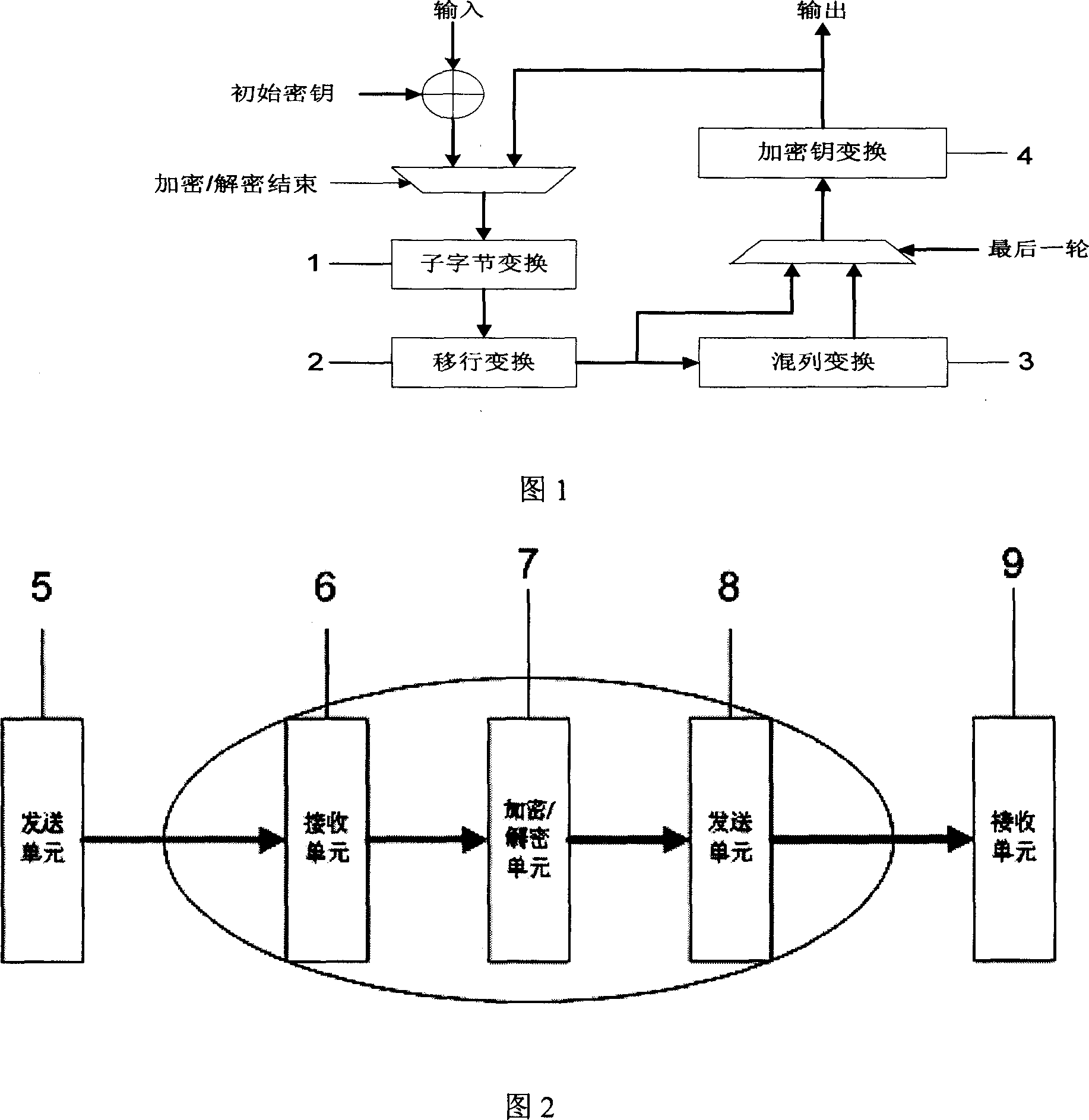
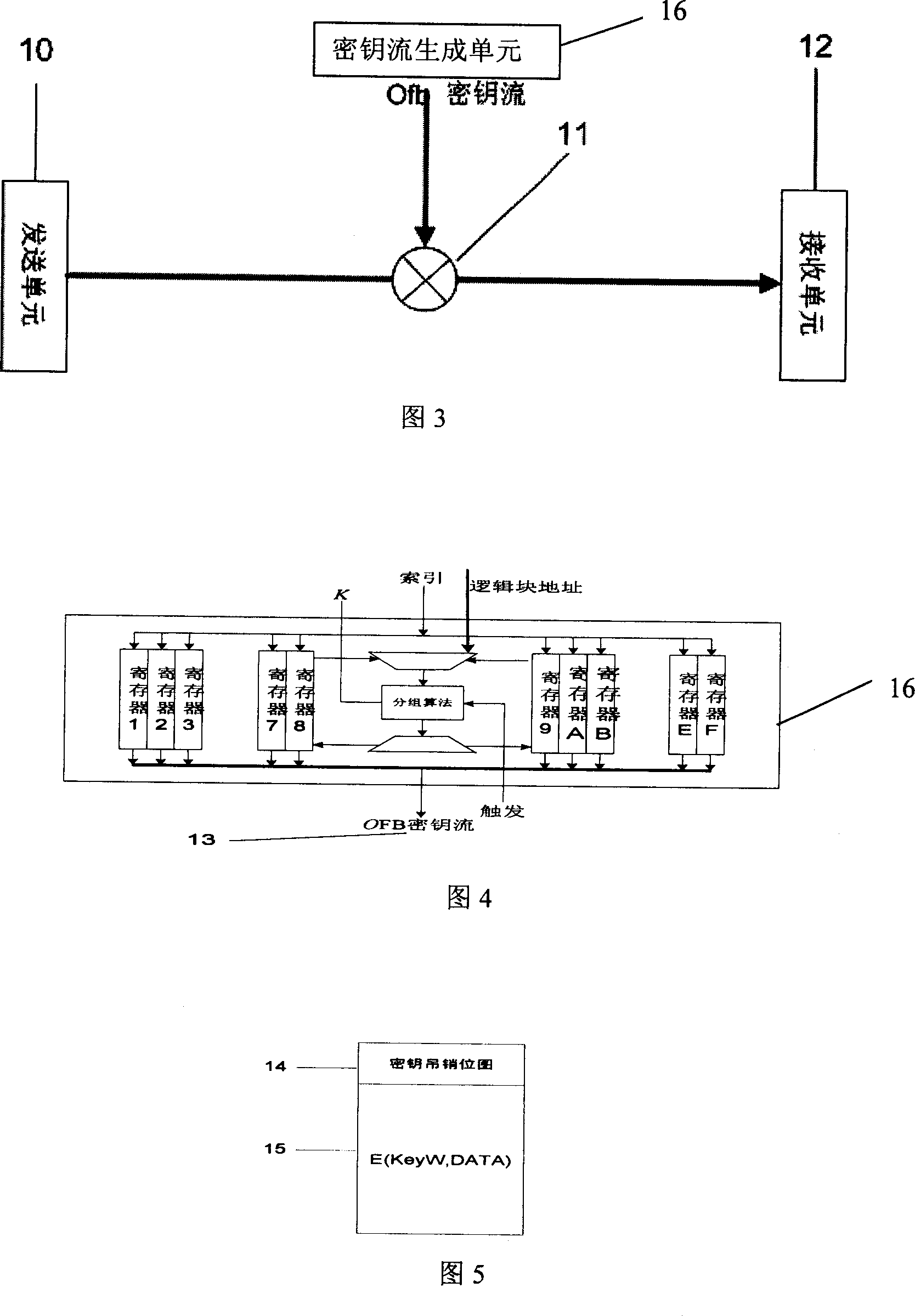
[0046] In general, storage systems can be divided into application layer, operating system layer, storage protocol and device model layer, and physical layer. The hard disk sector-level data encryption method of the present invention realizes encryption and decryption of data at the device model layer and the physical layer of the storage protocol.
[0047] The hard disk sector-level data encryption method of the present invention includes an improved AES encryption algorithm, a data transmission method that synchronizes data transmission and data encryption / decryption, and an online key revocation mechanism based on a key revocation bitmap , a low-density encryption method and a key strategy based on I2C bus.
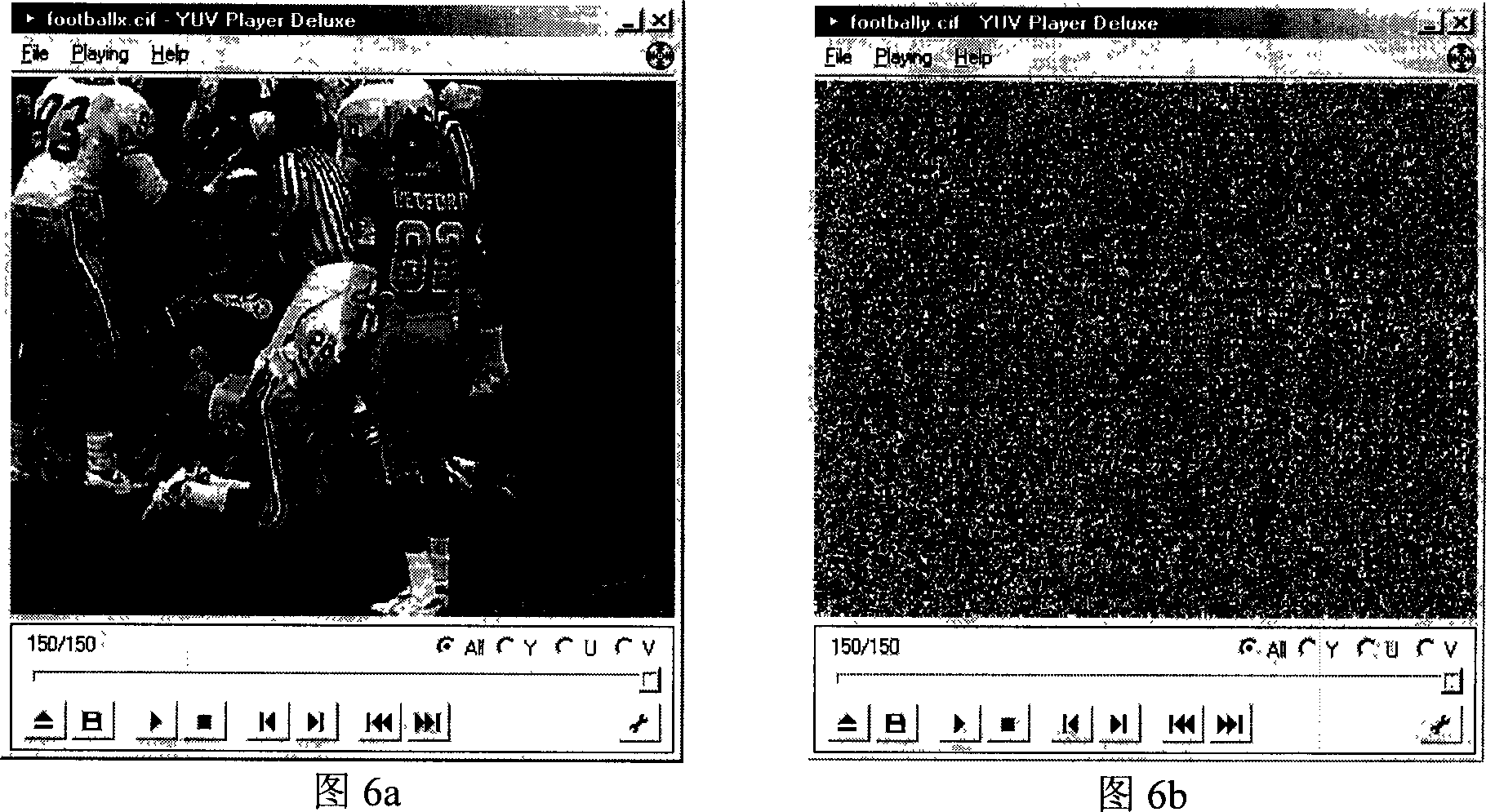
[0048] The hard disk sector-level data encryption and decryption method of the present invention realizes the encryption and decrypti...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com