Protection method for secure cloud computing terminal
A cloud computing and secure technology, applied in electrical components, user identity/authority verification, transmission systems, etc., can solve the problems of cloud terminal security protection, information loss, data theft, etc., and solve security risks. The effect of identity loss, great business value and social value
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
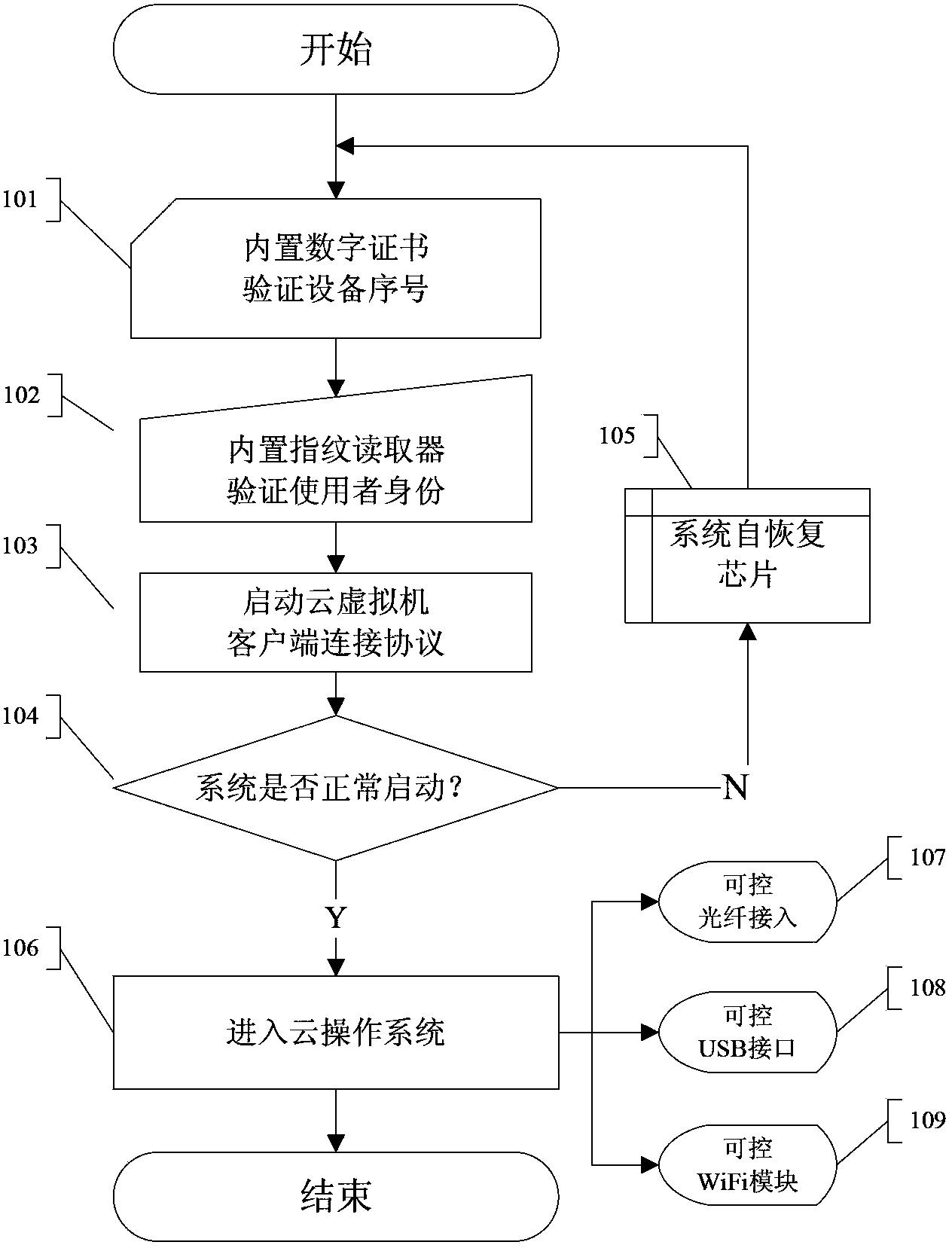
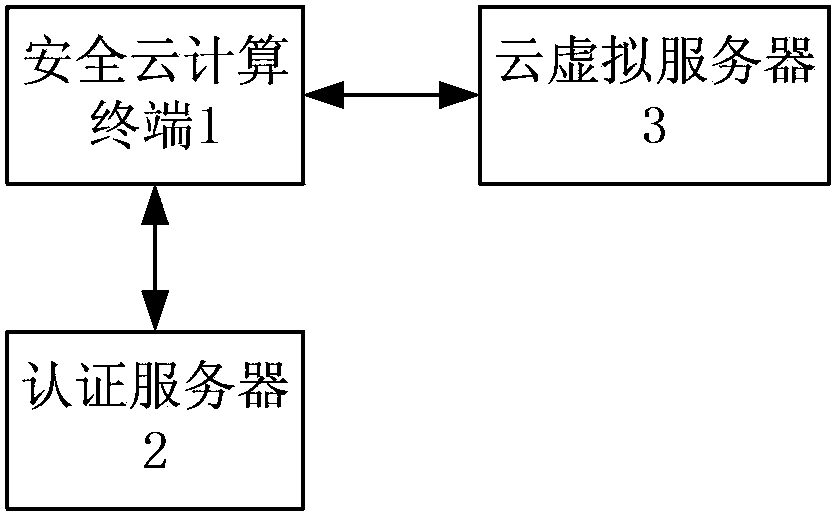
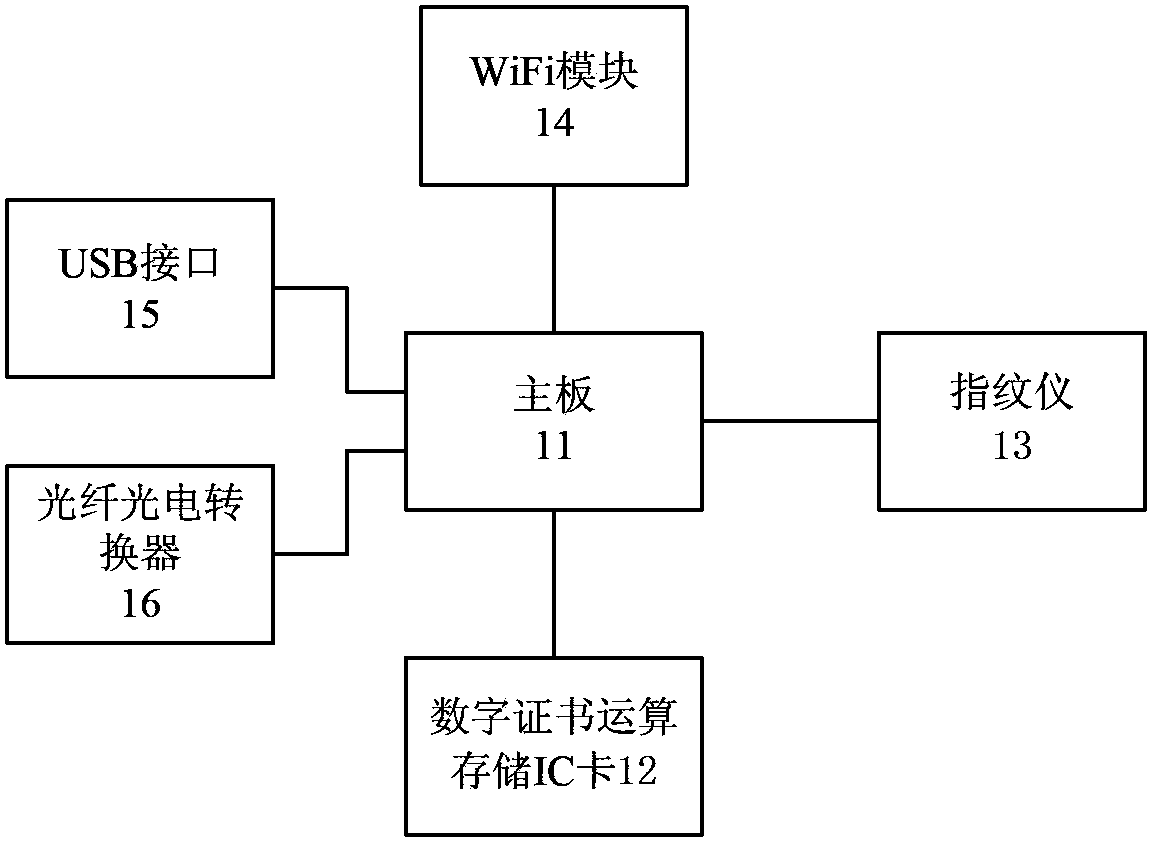
[0027] like Figure 1-Figure 3 As shown, a protection method for a secure cloud computing terminal, the secure cloud computing terminal 1 includes a main board 11, a digital certificate operation and storage IC module 12, a fingerprint device 13, a WiFi module 14, a USB interface 15 and a fiber-optic converter 16 , the secure cloud computing terminal 1 is respectively connected to the authentication server 2 and the cloud virtual server 3, and the protection method adopts a combination of multiple security authentication and protection facilities on a low-power, micro-volume cloud terminal through a unified security policy , so that the data and user information of the cloud terminal are effectively protected, and the specific steps of the protection method are as follows:
[0028] In step 101, the built-in digital certificate operation storage IC module 12 generates a unique device serial number, and then executes step 102.
[0029] In step 102 , the built-in fingerprint dev...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com