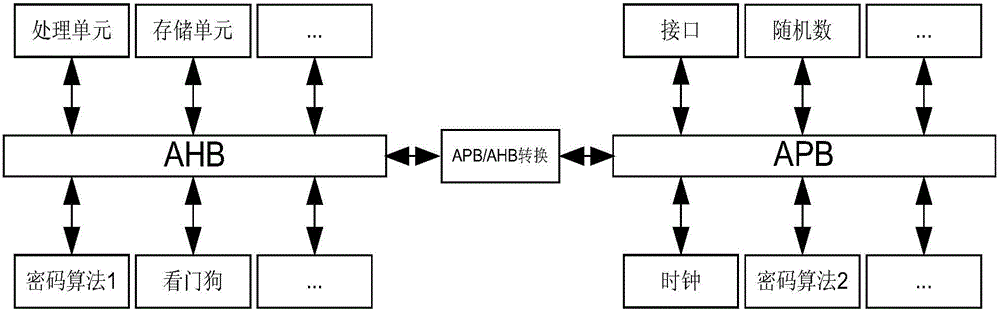
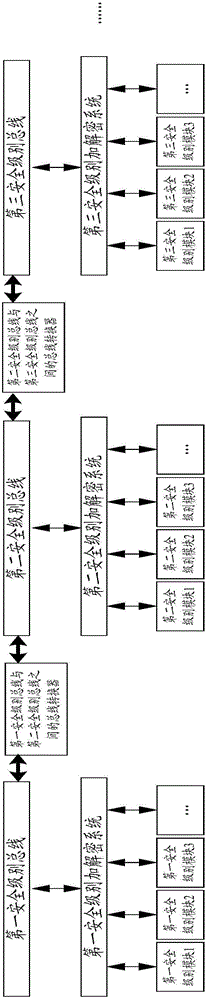
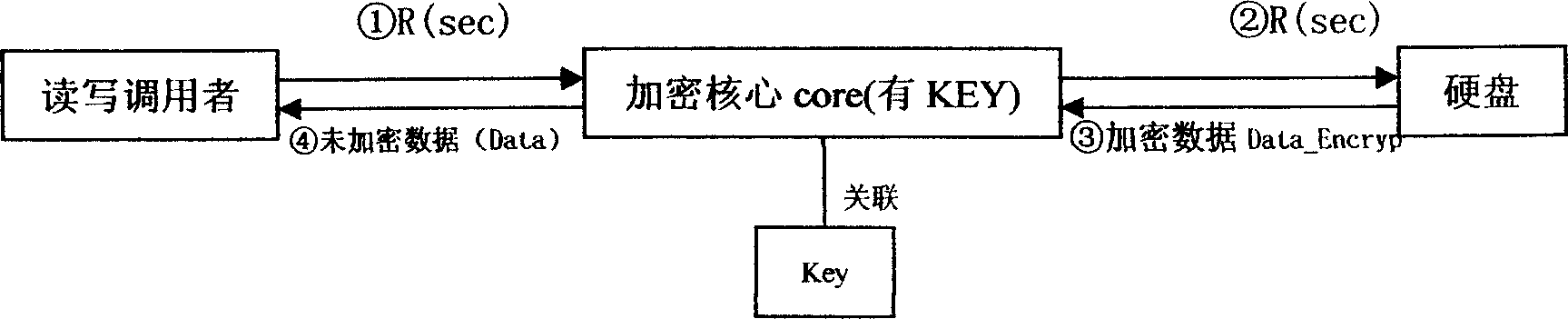
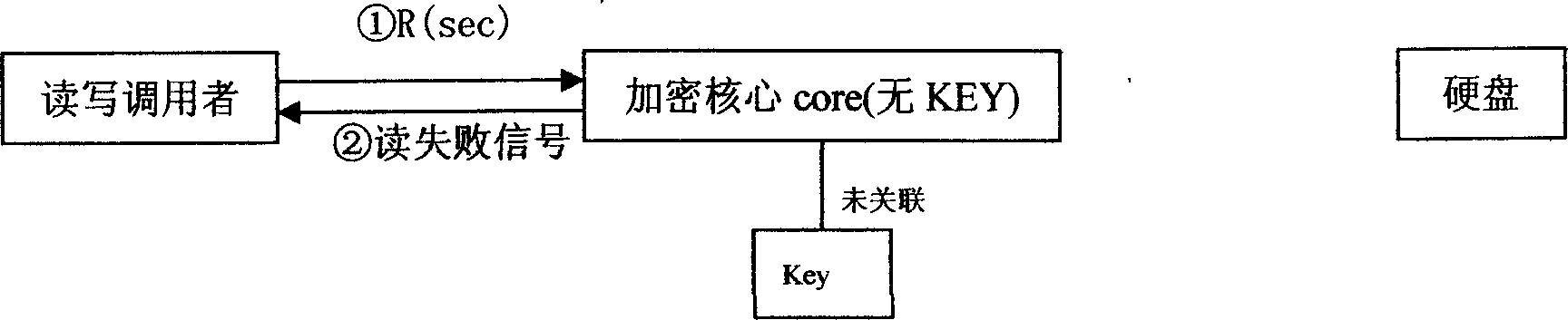
Patents
Literature
31 results about "Bus encryption" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Bus encryption is the use of encrypted program instructions on a data bus in a computer that includes a secure cryptoprocessor for executing the encrypted instructions. Bus encryption is used primarily in electronic systems that require high security, such as automated teller machines, TV set-top boxes, and secure data communication devices such as two-way digital radios.
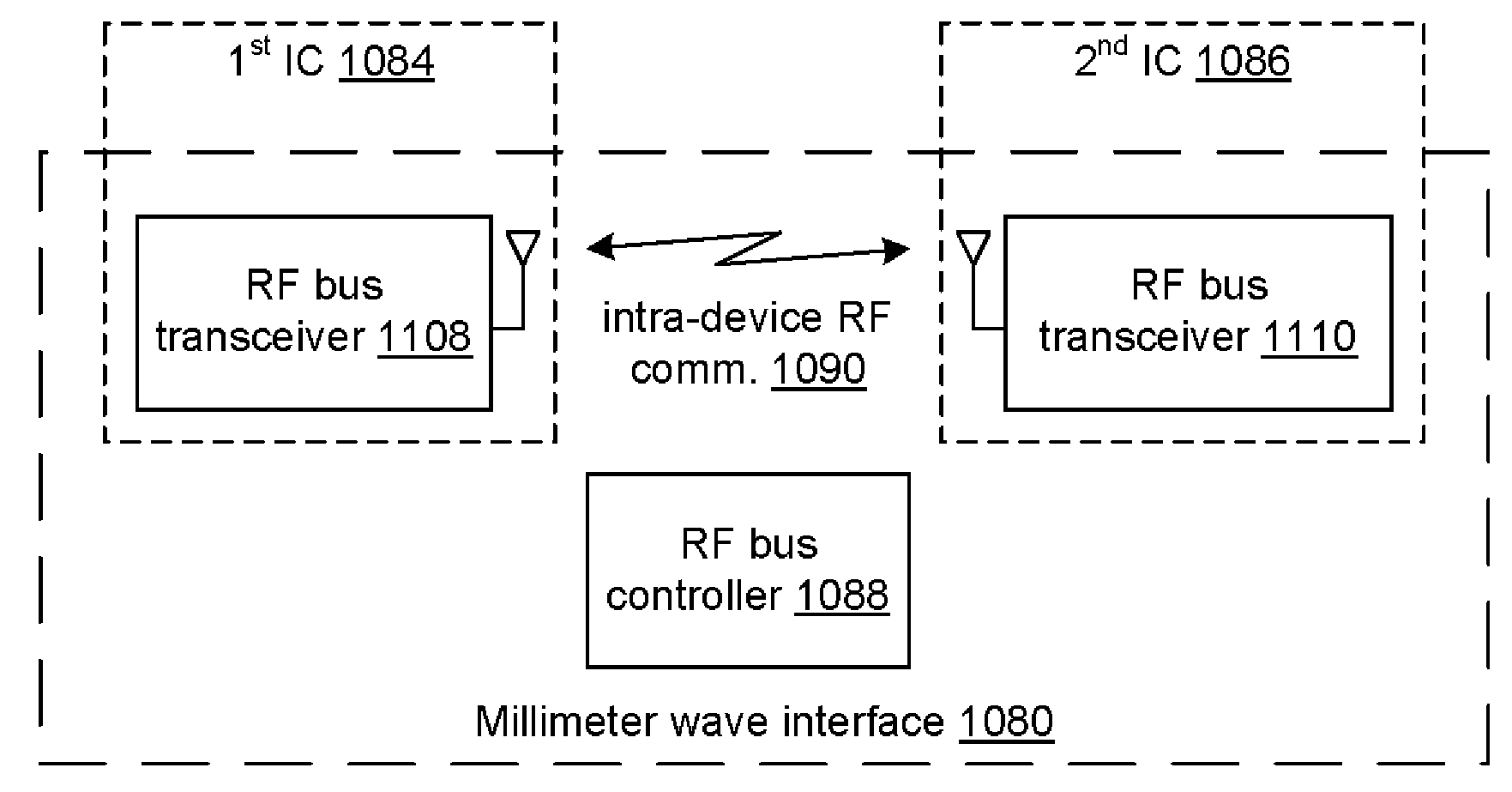
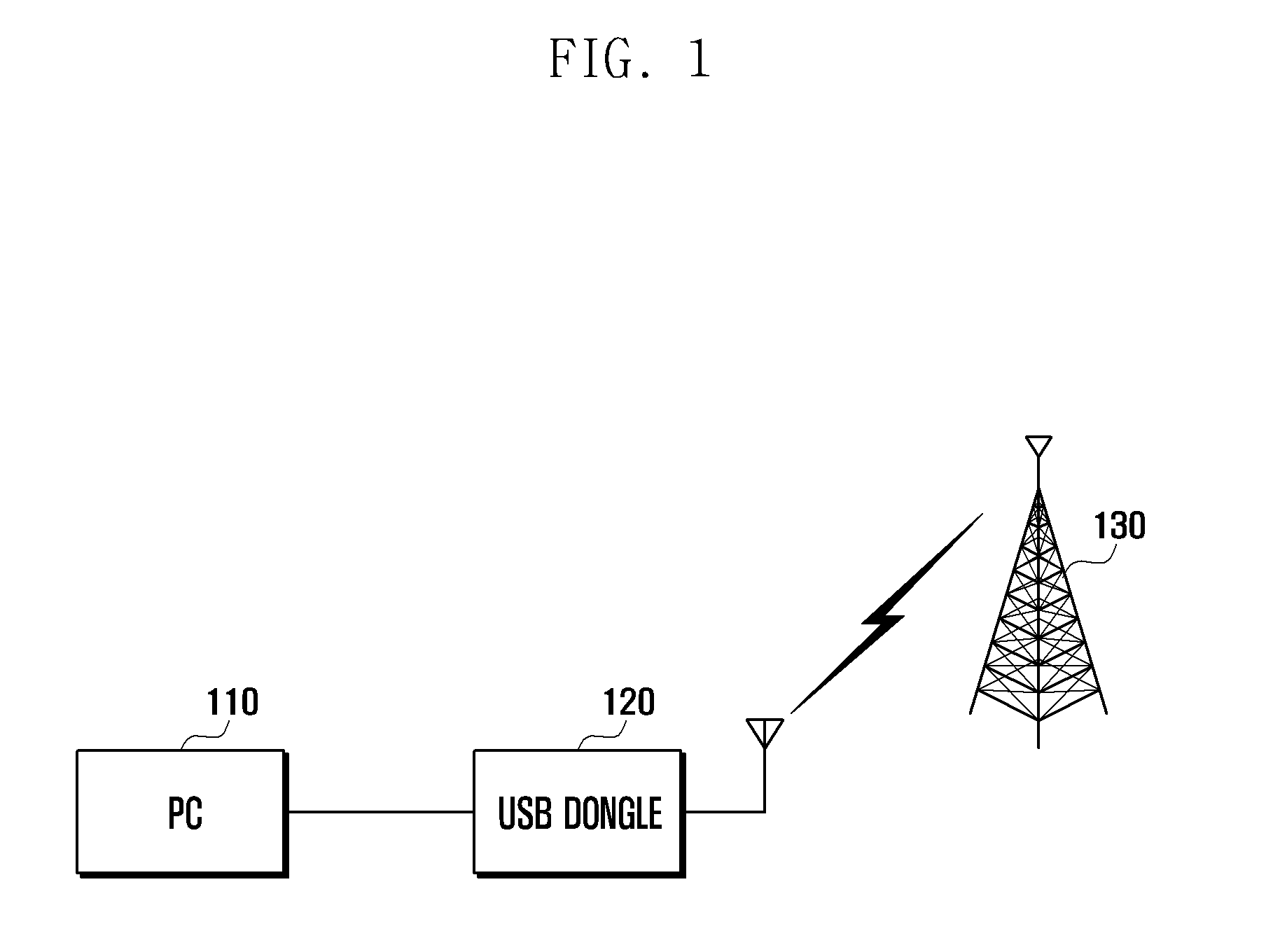
Universal serial bus dongle device with wireless telephony transceiver and system for use therewith
A universal serial bus (USB) dongle device includes a wireless telephony transceiver that receives an inbound RF signal and that generates inbound data based on the inbound RF signal and receives outbound data and that generates an outbound RF signal in response thereto. A USB plug is connectable to a host device. A USB controller circuit formats the inbound data in the USB format for communication to the host device and to recover the outbound data from outbound data received in the USB format from the host device. A millimeter wave interface includes a first millimeter wave transceiver coupled to the wireless transceiver and a second millimeter wave transceiver coupled to the USB controller circuit that wirelessly communicates the inbound data and the outbound data between the wireless telephony receiver and the USB controller circuit.
Owner:AVAGO TECH INT SALES PTE LTD
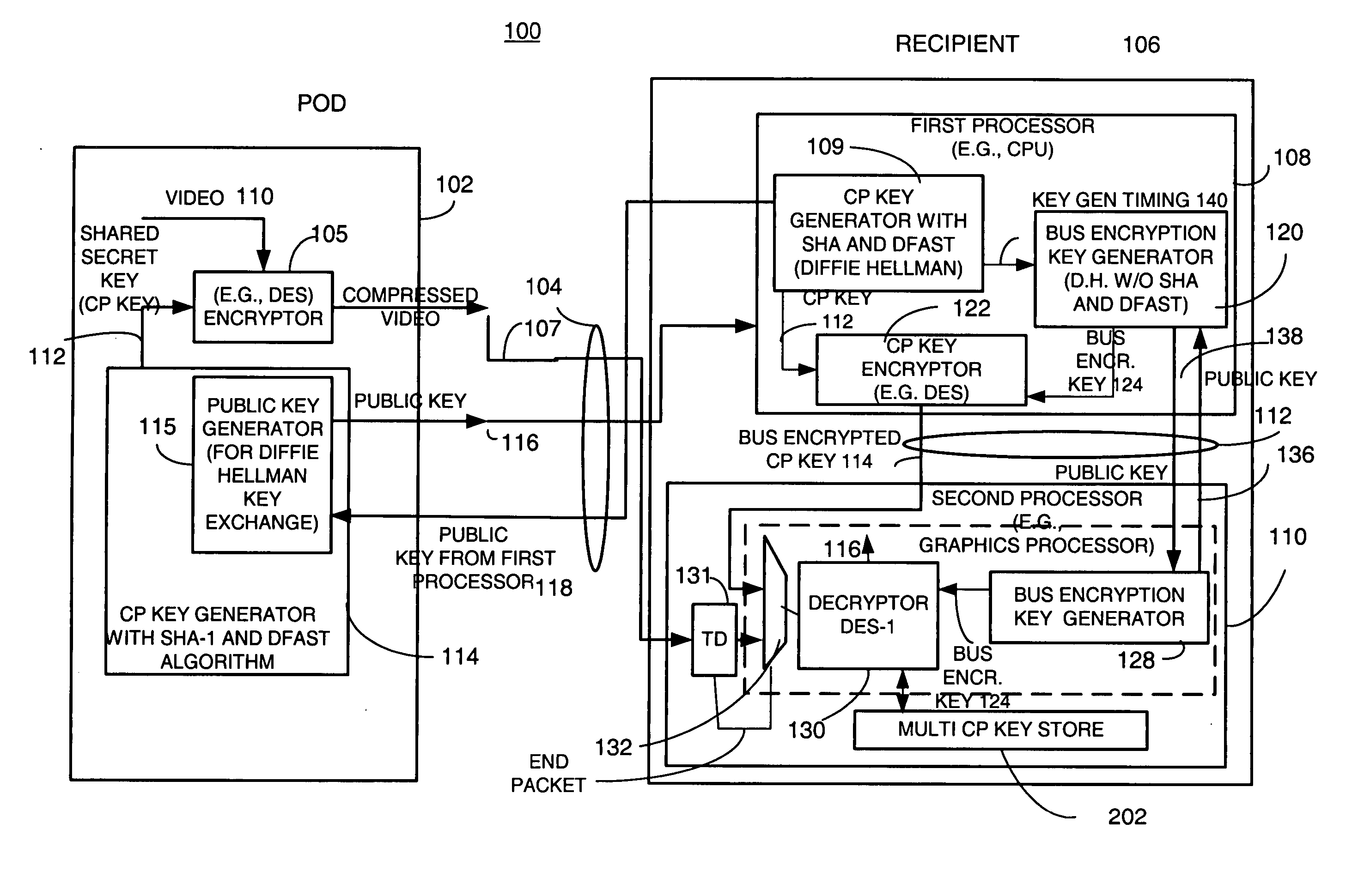
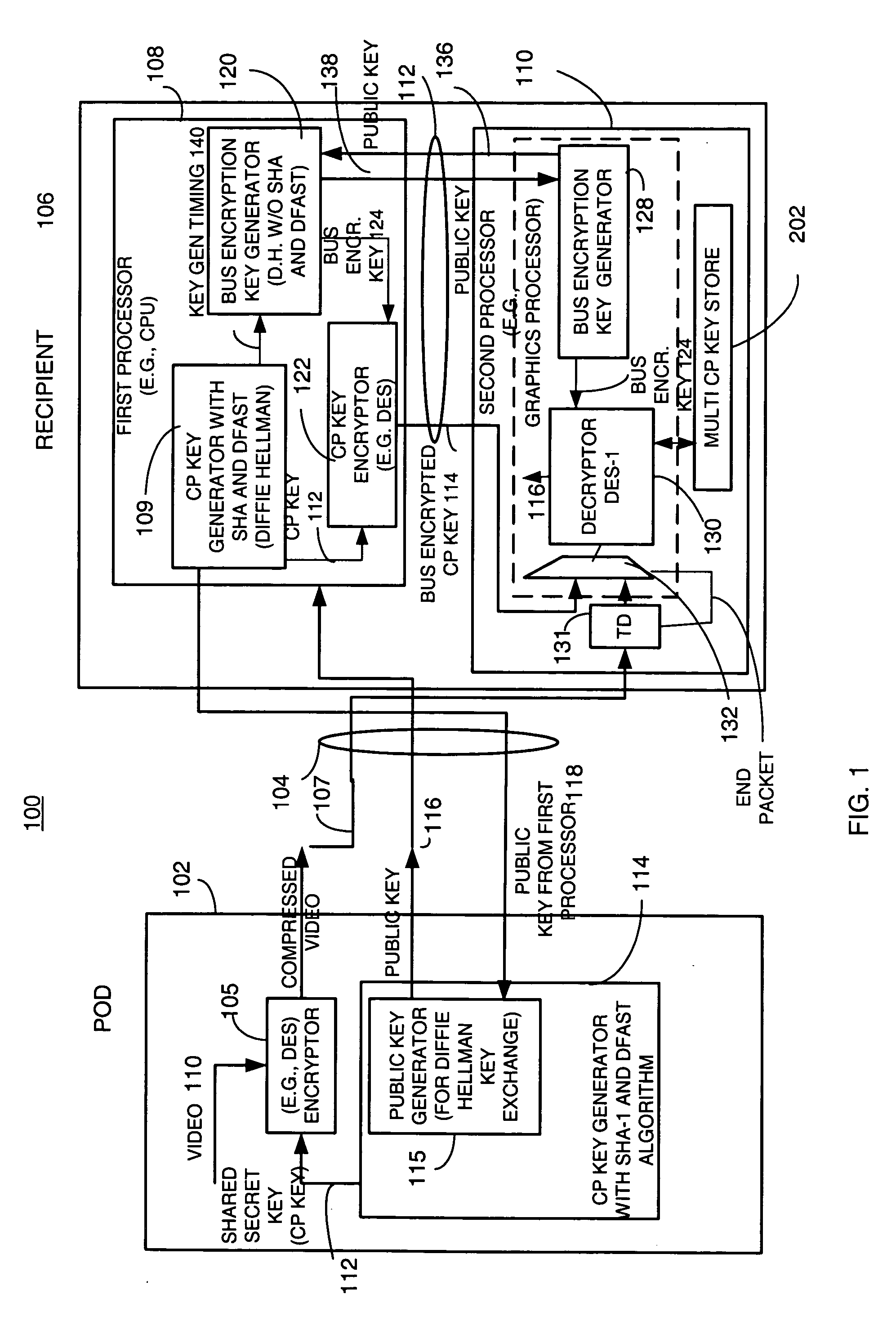
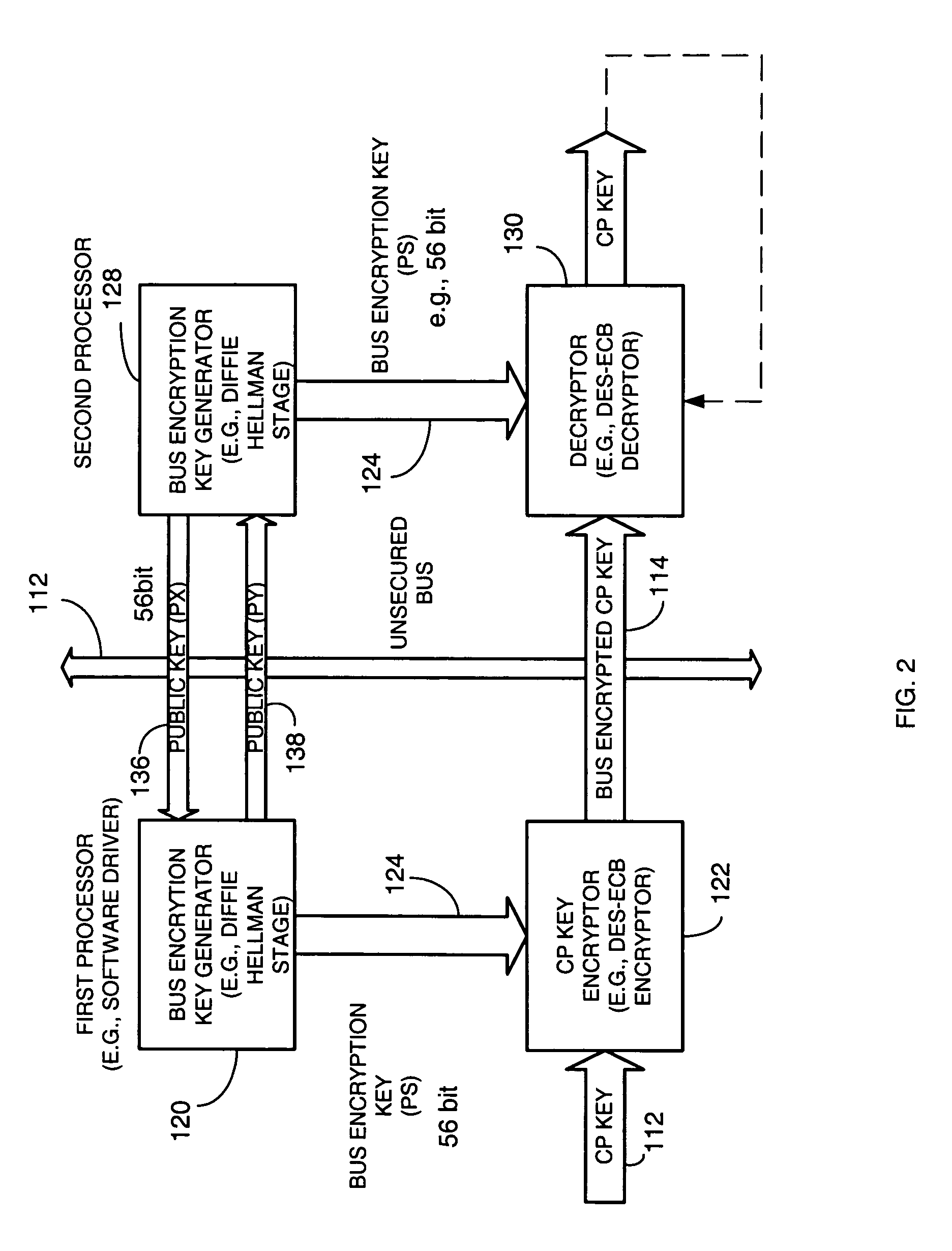
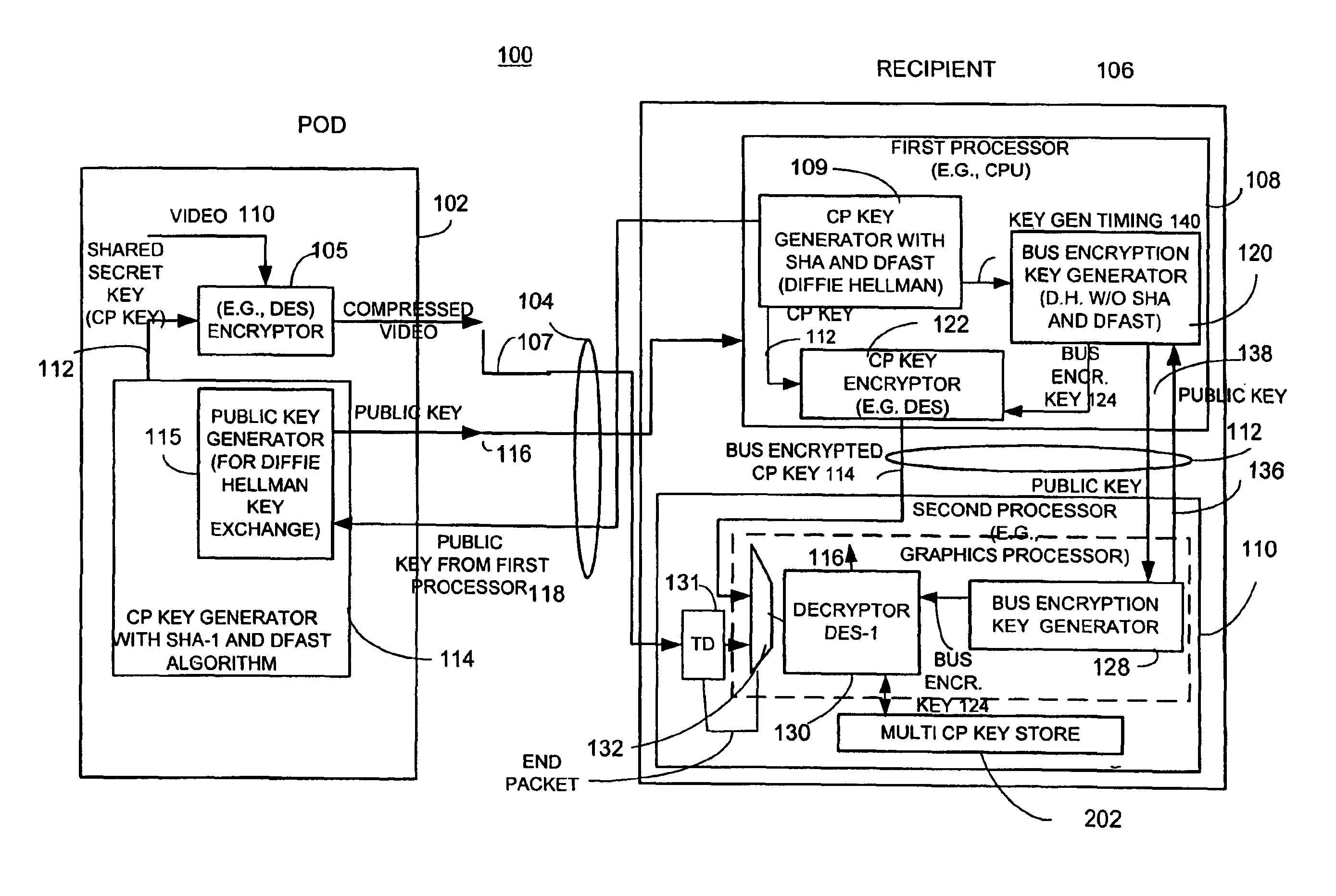
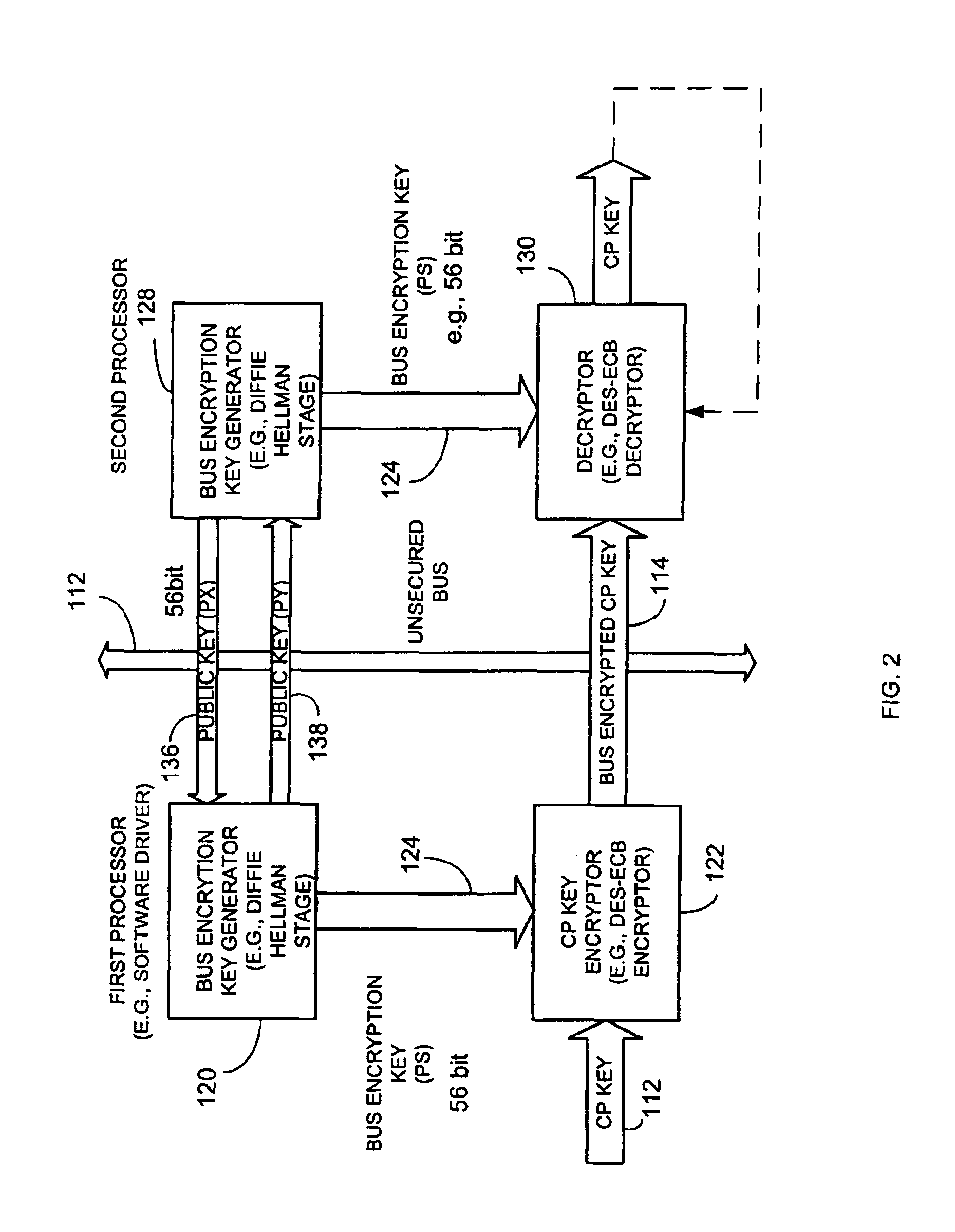
Method and apparatus for providing a bus-encrypted copy protection key to an unsecured bus
InactiveUS20050265547A1Key distribution for secure communicationPublic key for secure communicationComputer hardwareGraphics
A copy protection (CP) key used by a sending source, such as a POD, to encrypt content such as audio and / or video information is derived by a first key generator associated with a first processor and is locally encrypted by the first processor using a locally generated bus encryption key to produce a bus encrypted CP key that is sent over a local unsecure bus to a second processor, such as a graphics processor. The second processor decrypts the bus encrypted copy key using a decryption engine to obtain the CP key. The second processor receives the encrypted content and in one embodiment, also uses the same decryption engine to decrypt the encrypted content. The first and second processors locally exchange public keys to each locally derive a bus encryption key used to encrypt the CP key before it is sent over the unsecure bus and decrypt the encrypted CP key after it is sent over the bus. The locally exchanged public keys are shorter in length than those used between the CPU and POD to produce the original CP key.
Owner:ATI TECH INC
Universal Serial Bus Dongle Device with Millimeter Wave Transceiver and System for use Therewith
InactiveUS20090006675A1Substation equipmentElectric digital data processingBus encryptionTransceiver
A universal serial bus (USB) dongle device includes a first wireless millimeter wave transceiver that receives an inbound RF signal, that generates inbound data based on the inbound RF signal, that receives outbound data and that generates an outbound RF signal in response thereto. An antenna is coupled to transmit the outbound RF signal and to receive the inbound RF signal. A USB interface communicates the inbound data to the host device and receives the outbound data from the host device.
Owner:AVAGO TECH WIRELESS IP SINGAPORE PTE
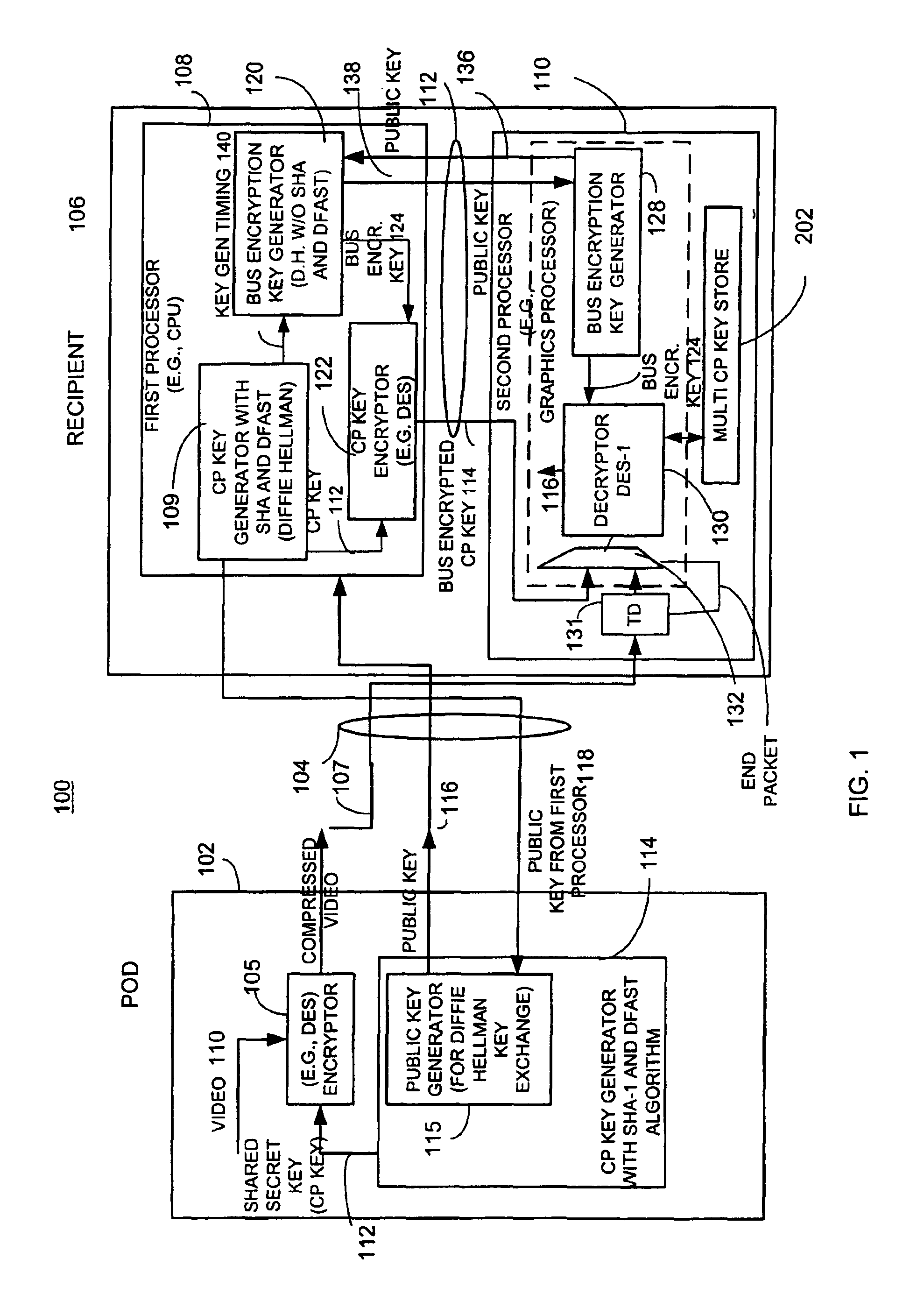
Method and apparatus for providing bus-encrypted copy protection key to an unsecured bus
InactiveUS6934389B2Key distribution for secure communicationPublic key for secure communicationComputer hardwareGraphics
A copy protection (CP) key used by a sending source, such as a POD, to encrypt content such as audio and / or video information is derived by a first key generator associated with a first processor and is locally encrypted by the first processor using a locally generated bus encryption key to produce a bus encrypted CP key that is sent over a local unsecure bus to a second processor, such as a graphics processor. The second processor decrypts the bus encrypted copy key using a decryption engine to obtain the CP key. The second processor receives the encrypted content and in one embodiment, also uses the same decryption engine to decrypt the encrypted content. The first and second processors locally exchange public keys to each locally derive a bus encryption key used to encrypt the CP key before it is sent over the unsecure bus and decrypt the encrypted CP key after it is sent over the bus. The locally exchanged public keys are shorter in length than those used between the CPU and POD to produce the original CP key.
Owner:ATI TECH INC
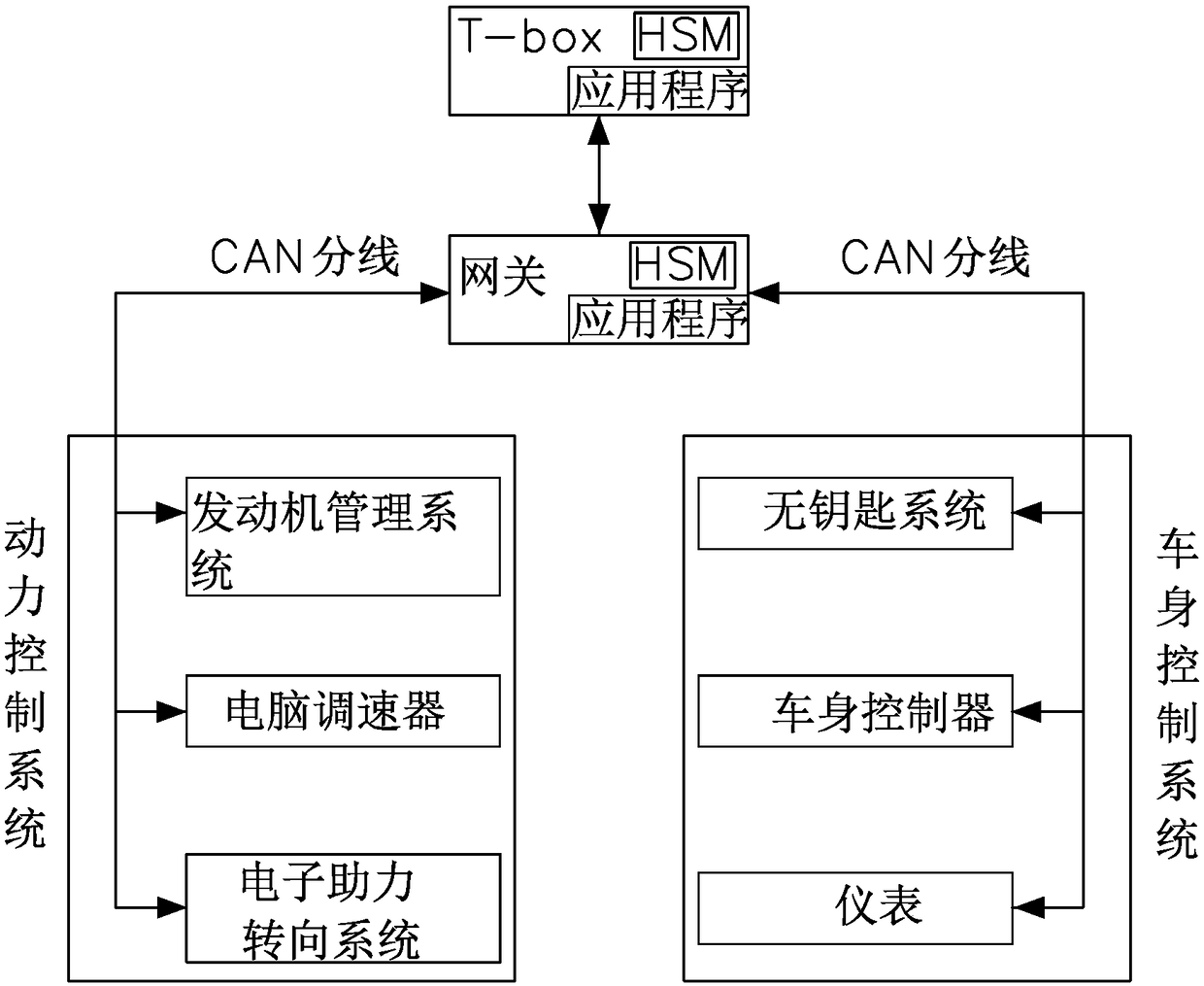
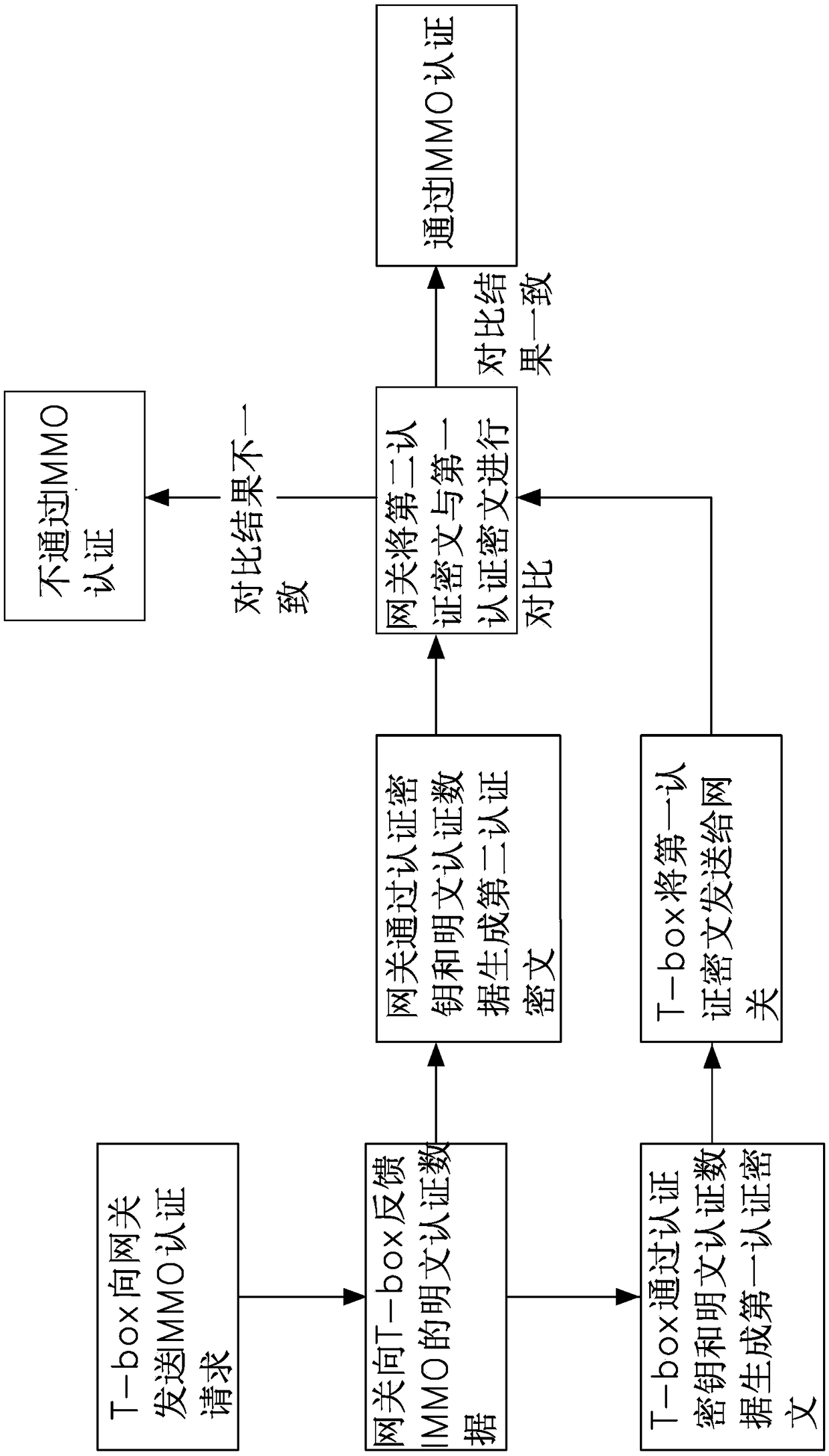
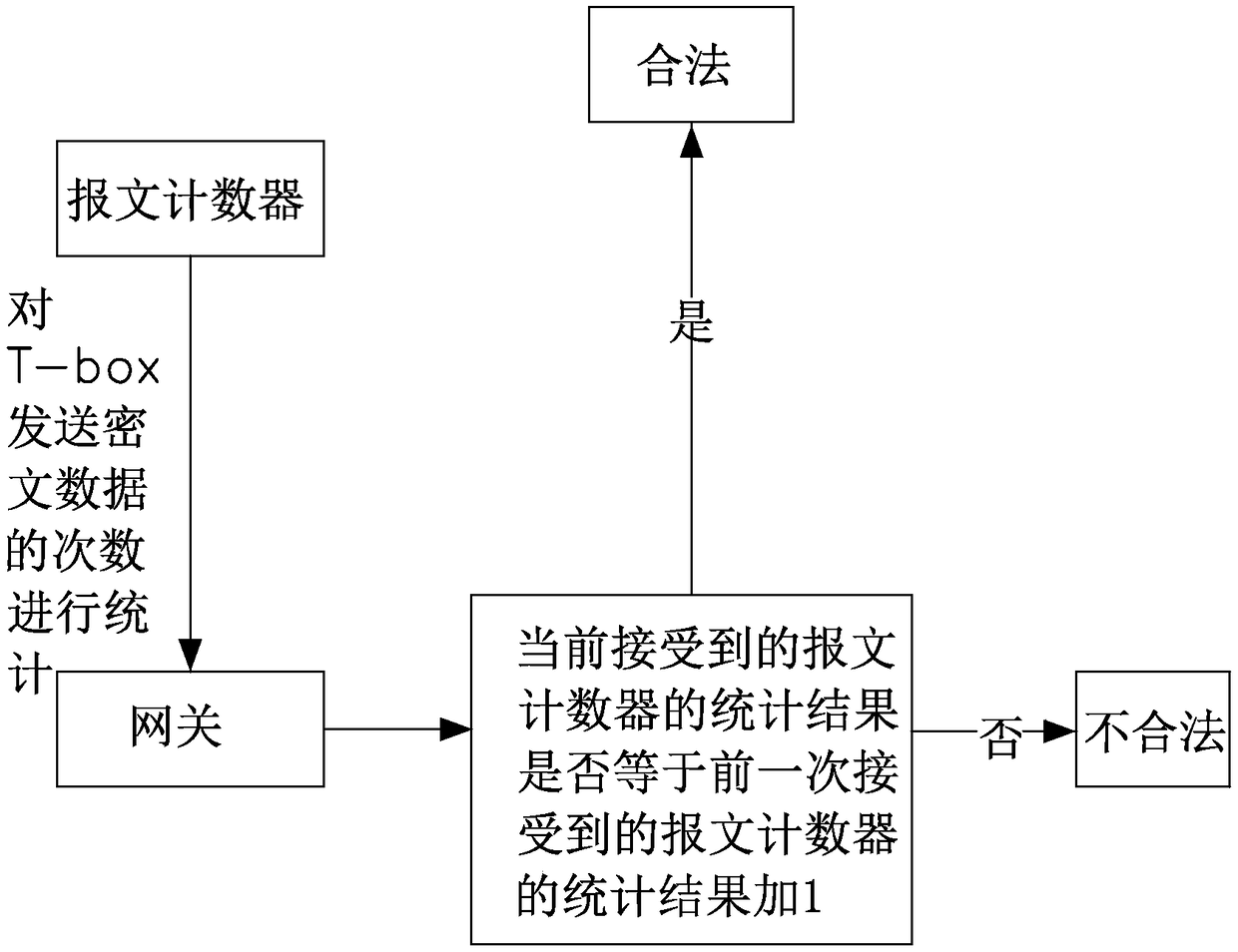
Vehicle CAN bus encryption method
The invention provides a vehicle CAN bus encryption method. The method comprises the following steps: firstly performing IMMO authentication on T-box, wherein the T-box sends a message to a gateway through a bus CAN under the condition that the IMMO authentication is passed; performing hardware encryption and decryption on the message sent by the T-box through a HSM of the T-box and the HSM of thegateway, wherein the a message counter is arranged on the T-box to count the sent message, and the gateway detects the message counter; judging that the message is legal when the message conforms tothe set rule, and decrypting the message when the message is legal, and then sending the decrypted message to other CAN branches of the vehicle. The vehicle CAN bus encryption method provided by the invention has the advantages that the triple encryption method of IMMO authentication, the HSM hardware encryption and the message counter judgment is applied by adopting the way of combining the software encryption and hardware encryption, the security of the vehicle CAN bus is greatly improved, the Hacker intrusion is prevented, and the travelling security is improved.
Owner:SOUEAST
Hierarchical bus encryption system
ActiveCN105790927AImprove securityImprove speed performanceAcutation objectsSynchronising transmission/receiving encryption devicesBus encryptionComputer module
The invention relates to the technical field of system security, and especially relates to a hierarchical bus encryption system. The system is used for solving the problems that data transmission of a security module and an ordinary module is not physically isolated and buses are not utilized reasonably and fully according to the security of each module. The system comprises at least two buses of a first bus and a second bus, an encryption and decryption system corresponding to each bus, at least one signal processing module corresponding to each bus, and a bus converter coupled between the first bus and the second bus. Through adoption of the system provided by the embodiment of the invention, the data transmitted on the buses is encrypted data, even through an attacker obtains the bus data through a probe attack, a secret key is difficult to break, and the anti-attack capability of the system can be improved.
Owner:HUAWEI TECH CO LTD
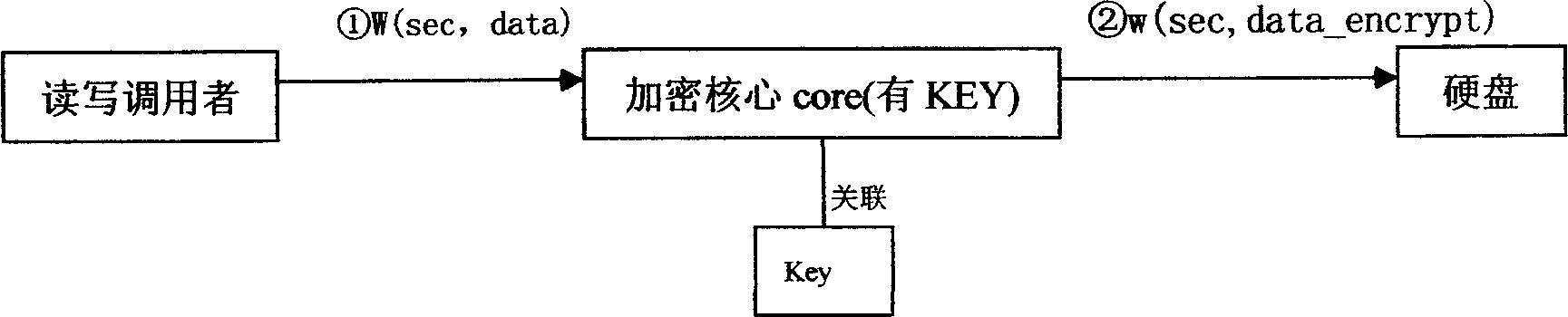
Enciphered protection and read write control method for computer data
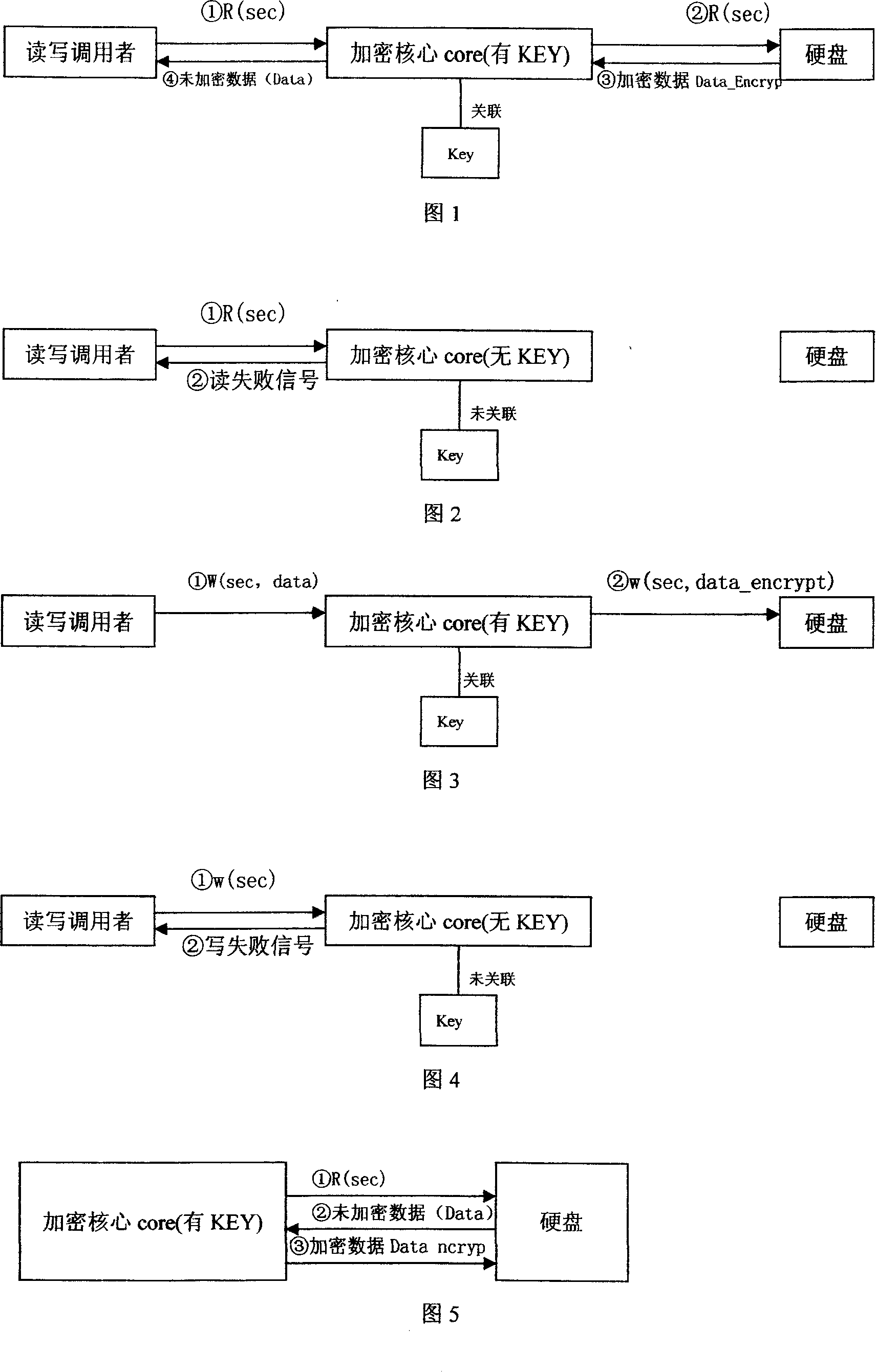
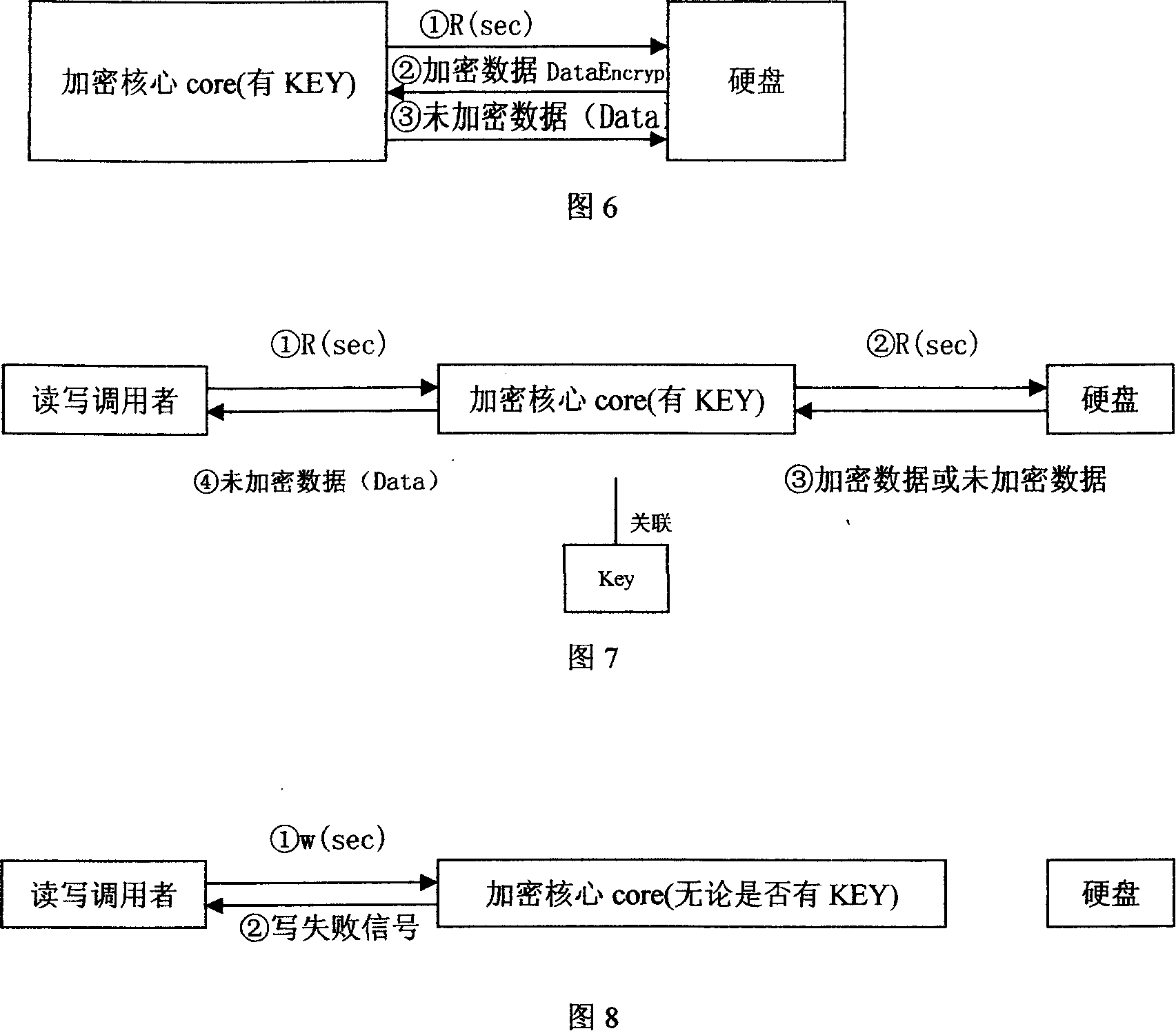
InactiveCN1725196APrevent leakageAvoid destructionDigital data processing detailsUnauthorized memory use protectionDECIPHERBus encryption
This invention relates to a computer data cipher protection and a read / write control method, which applies a generate method combining a serial bus ciphering dog or software identity certification with the sector stage read / write interception to realize cipher to hard disk data, which utilizes the sector stage read / write interception method to intercept all read / write operations, carries out cipher / decipher conversion in the cipher core under the condition of existing related identity certification to realize the cipher to disk data and read / write control.
Owner:陆峰
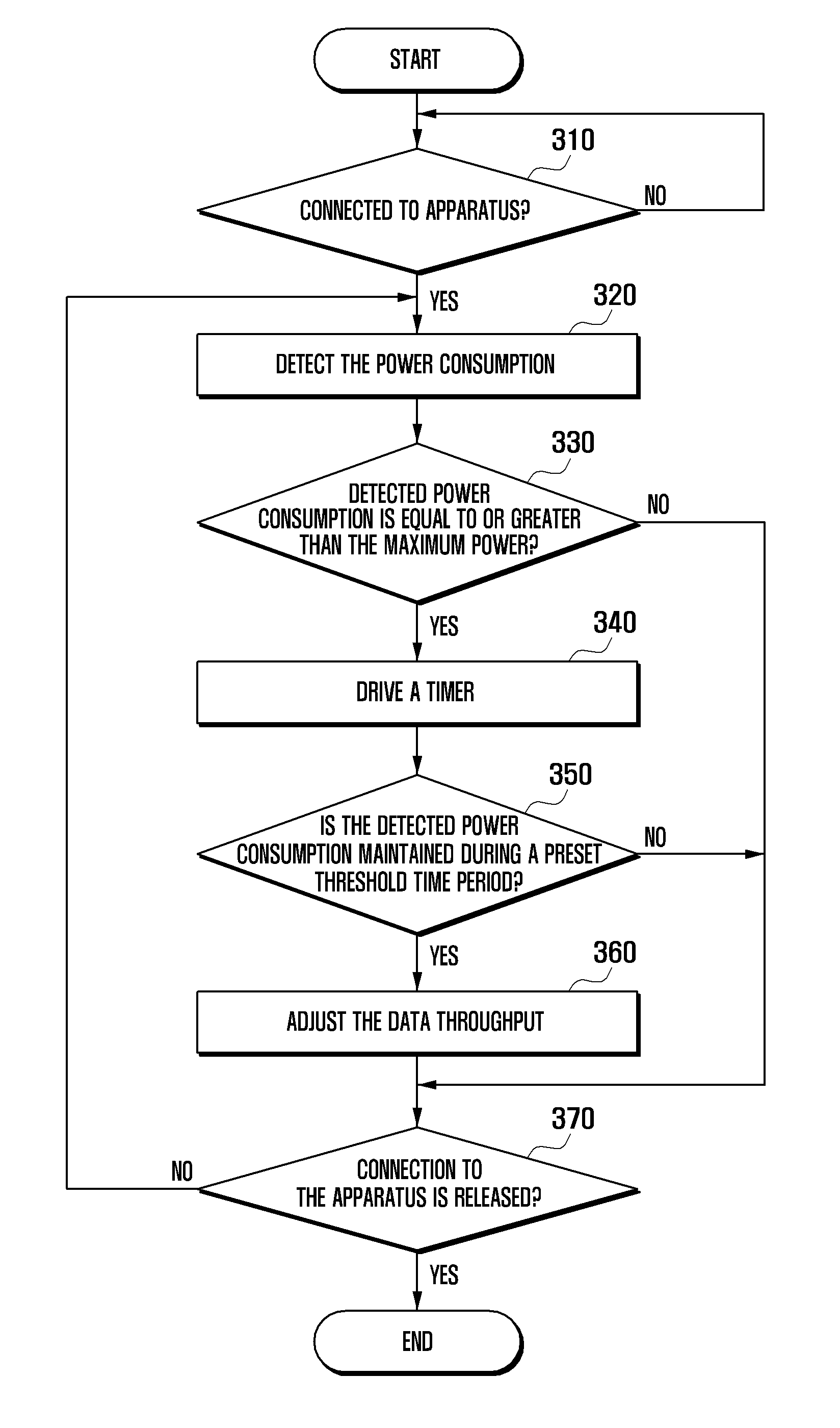
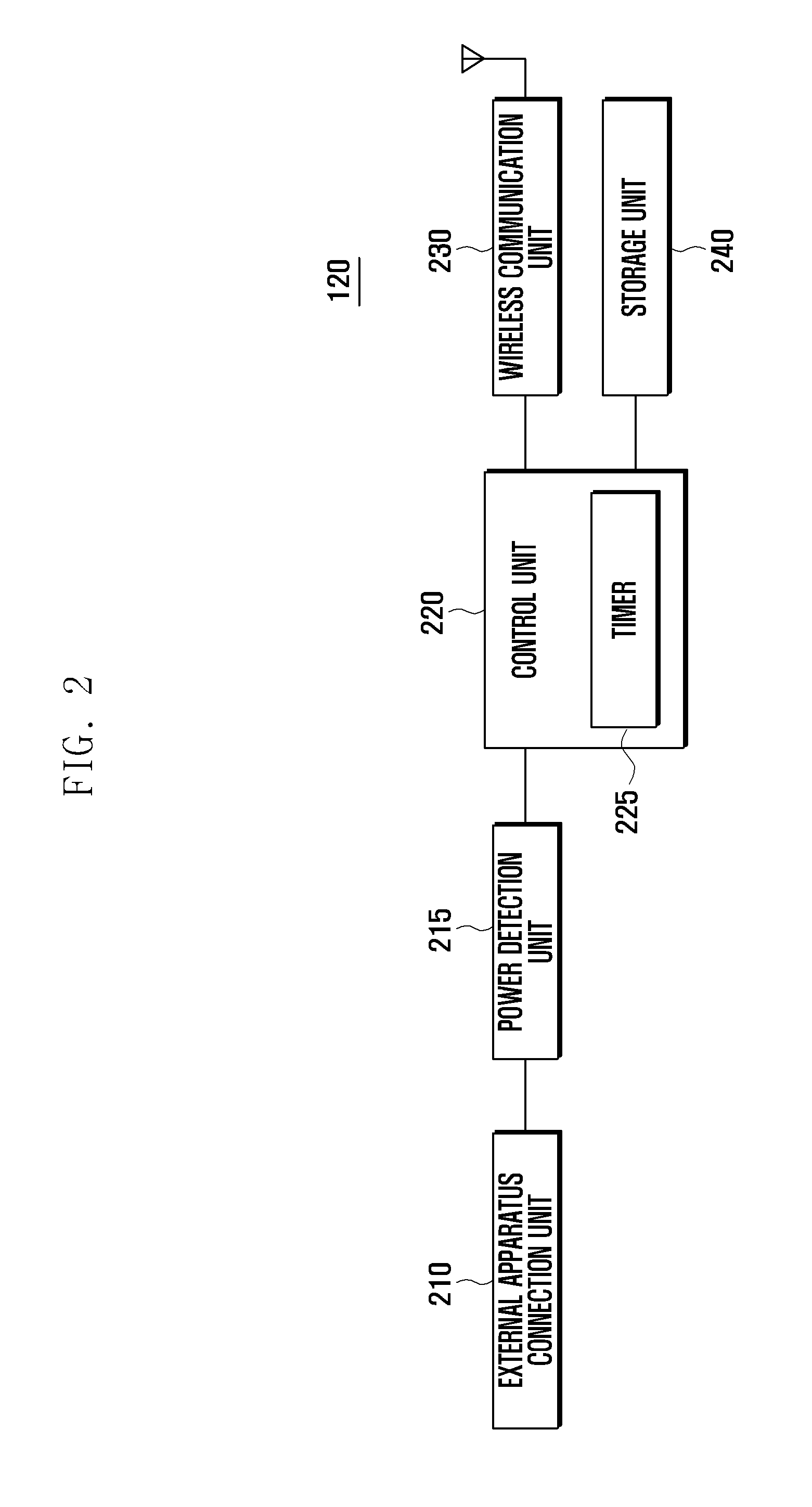
Universal serial bus dongle and method of controlling power thereof
InactiveUS20120096299A1Reduce data throughputEnergy efficient ICTPower managementControl powerBus encryption
An apparatus and method of controlling power of a Universal Serial Bus (USB) dongle are provided. The method includes detecting power consumption of the USB dongle when the USB dongle is connected with an apparatus to perform a communication function, determining whether the detected power consumption is equal to or greater than a maximum power, and lowering a data throughput when the detected power consumption is equal to or greater than the maximum power.
Owner:SAMSUNG ELECTRONICS CO LTD
Random number generator configured to combine states of memory cells
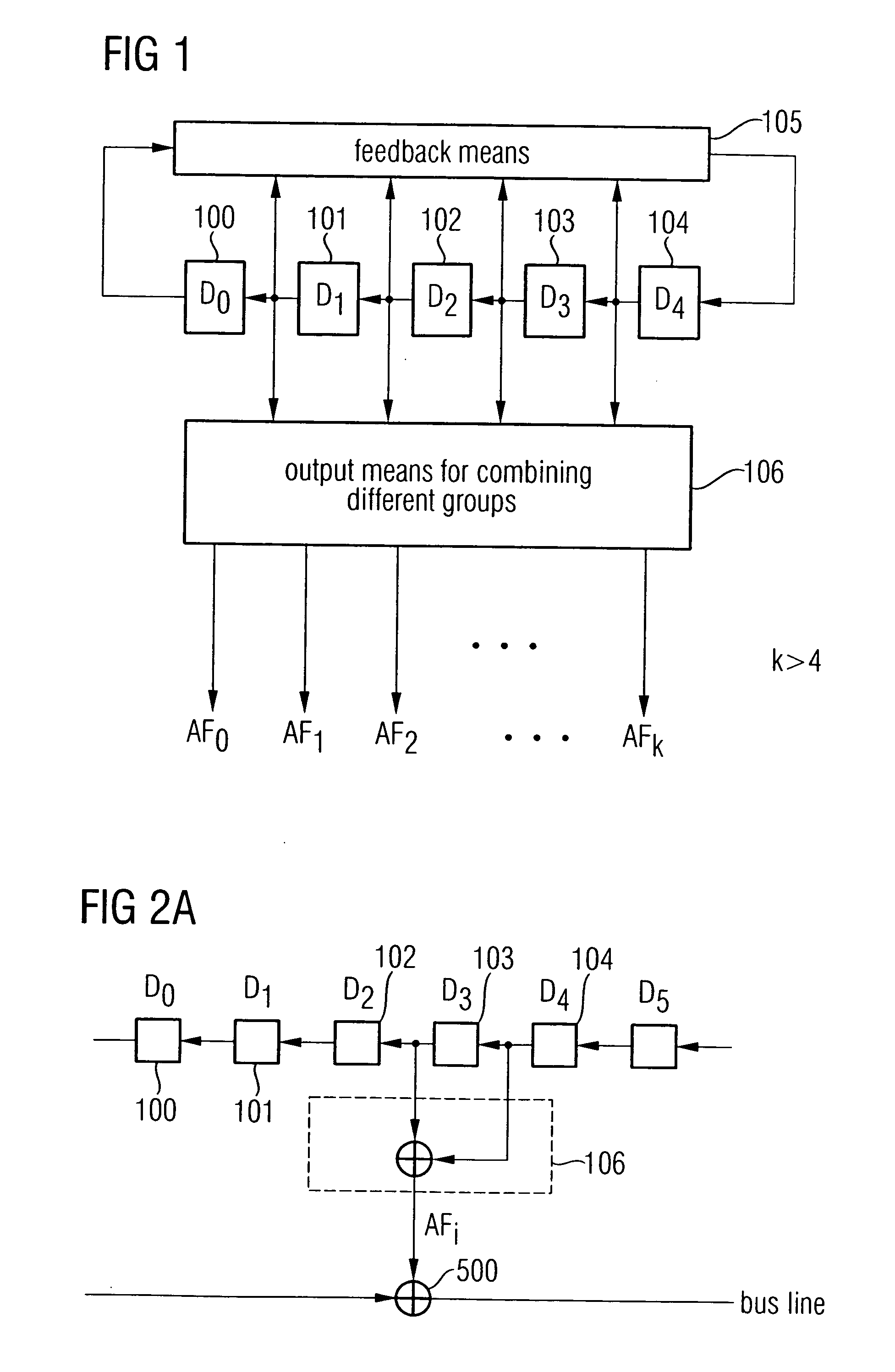
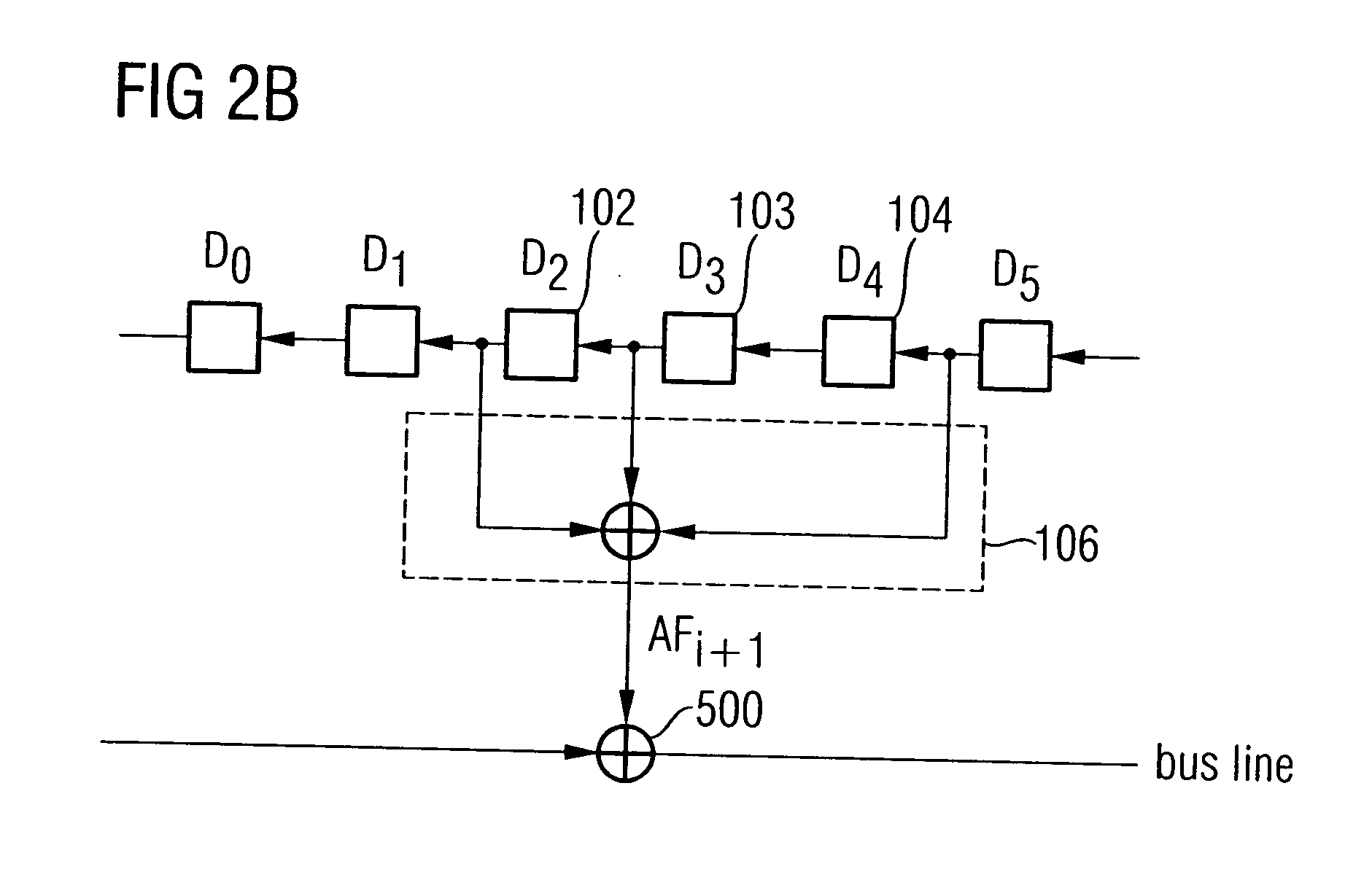
ActiveUS7979482B2Safe and efficientRandom number generatorsEncryption apparatus with shift registers/memoriesComputer hardwareMemory cell
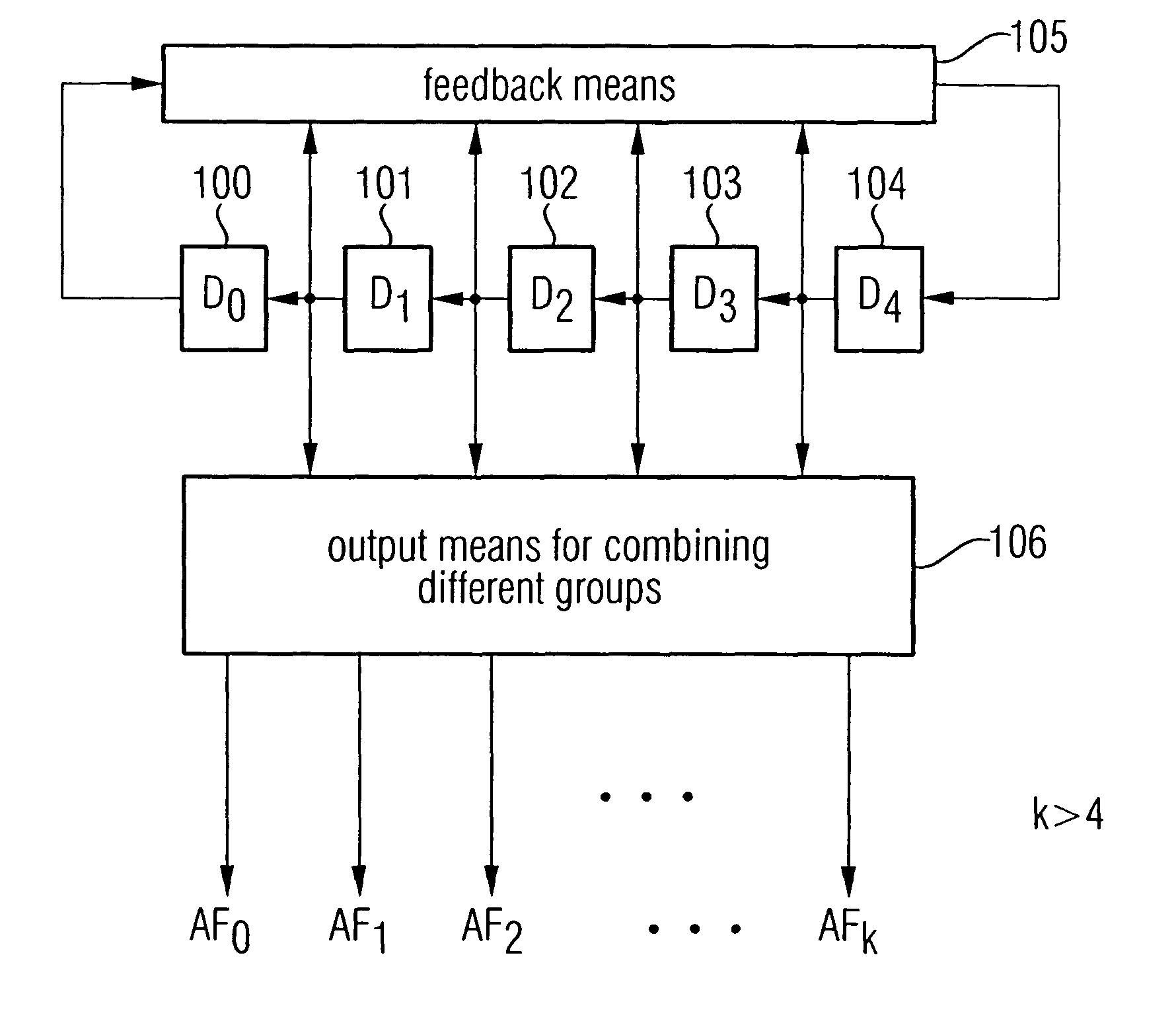
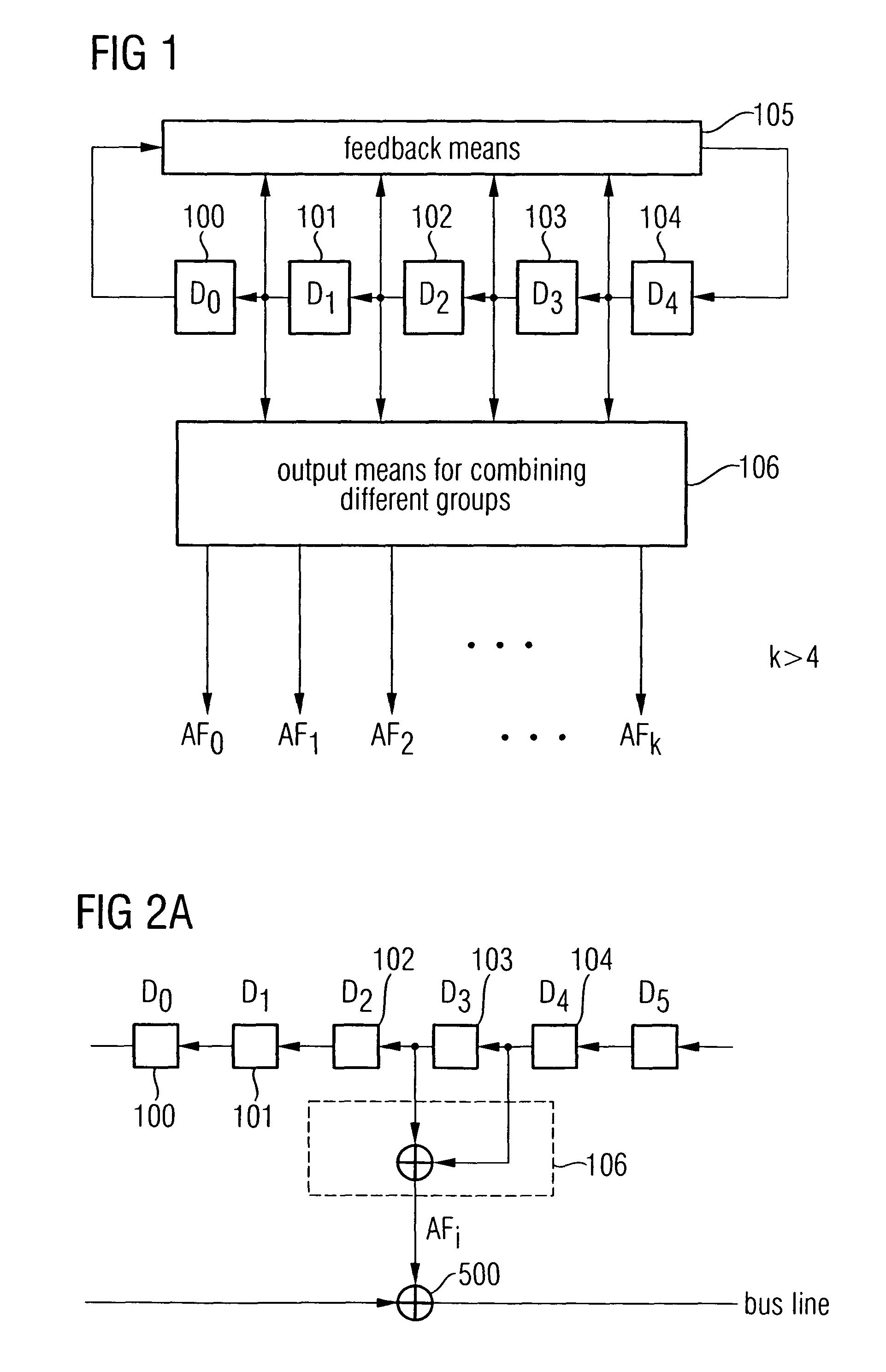
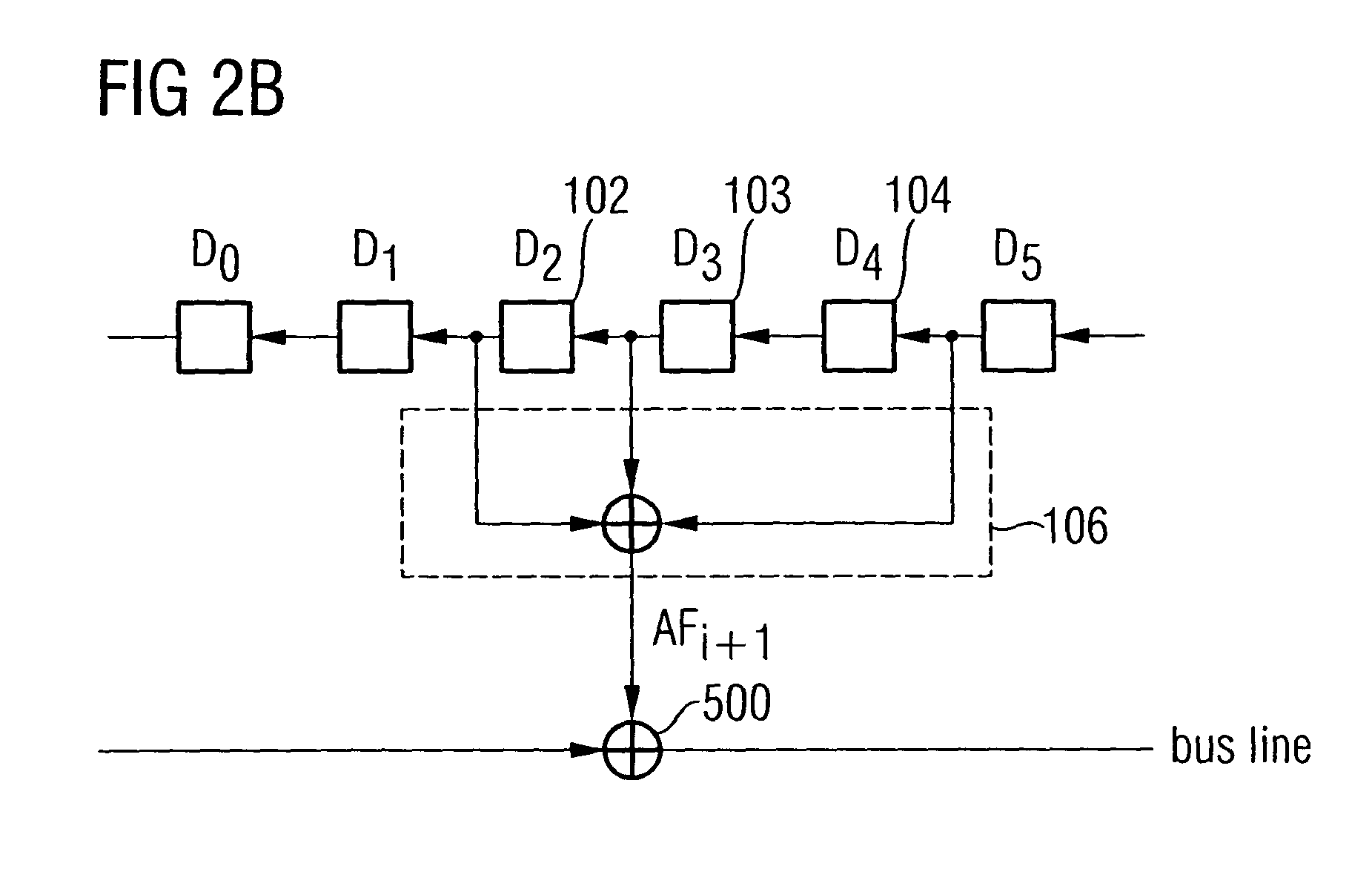
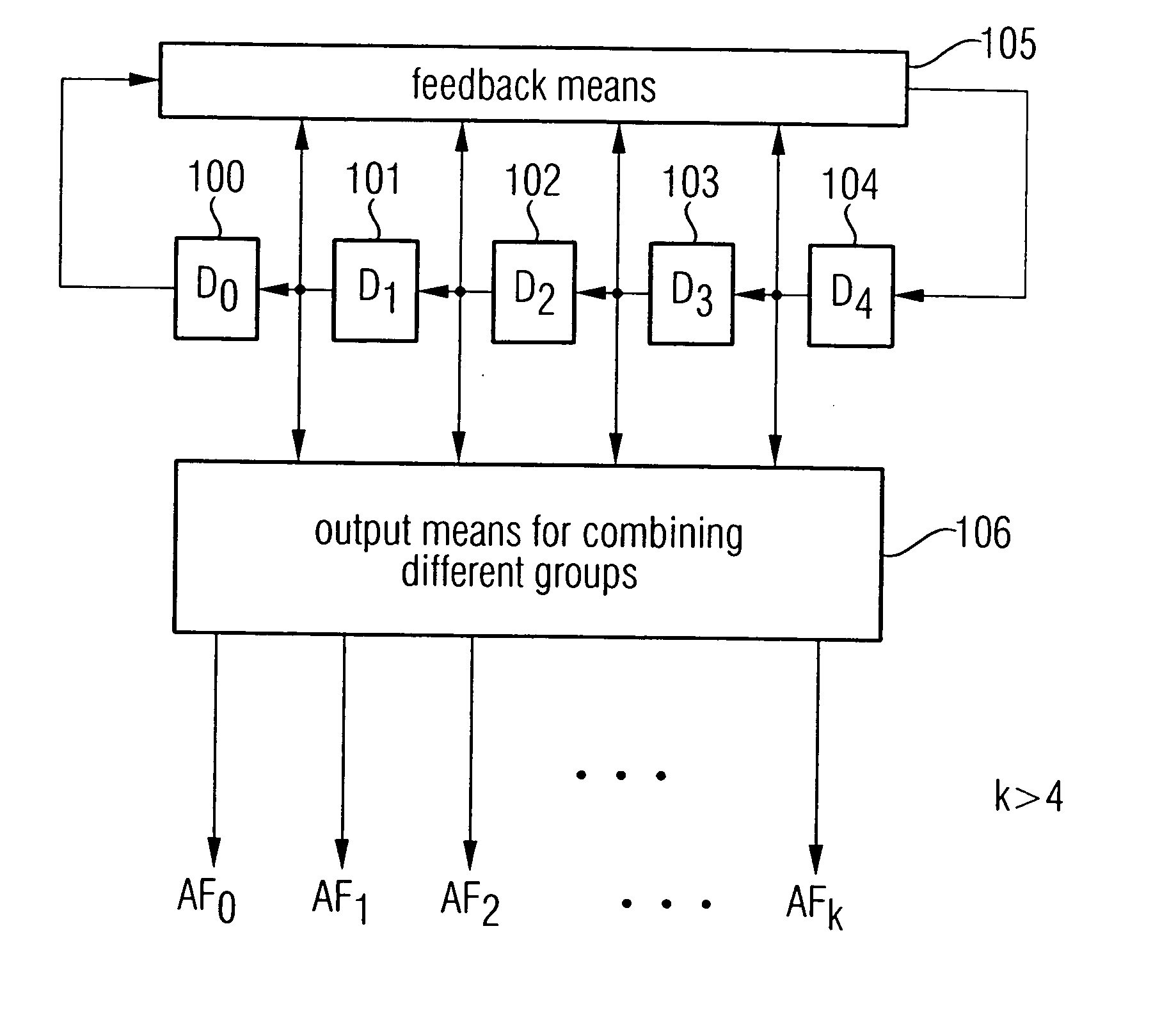
A random number generator includes a plurality of memory cells arranged in a series, a feedback processor for generating a feedback signal and for feeding the feedback signal into one of the memory cells, and a random number outputter formed to combine states of a group of at least two memory cells to obtain an output sequence. Sequences strongly differing from one another, the number of which is greater than the number of memory cells, can be generated by generating several output sequences AF0, AF1, AF2, . . . , AFk by combining states of different memory cells such that a safe and efficient bus encryption is achievable.
Owner:INFINEON TECH AG
Random number generator and method for generating random numbers
ActiveUS20050207207A1Safe and efficientRandom number generatorsEncryption apparatus with shift registers/memoriesBus encryptionNumber generator
A random number generator includes a plurality of memory cells arranged in a series, a feedback processor for generating a feedback signal and for feeding the feedback signal into one of the memory cells, and a random number outputter formed to combine states of a group of at least two memory cells to obtain an output sequence. Sequences strongly differing from one another, the number of which is greater than the number of memory cells, can be generated by generating several output sequences AF0, AF1, AF2, . . . , AFk by combining states of different memory cells such that a safe and efficient bus encryption is achievable.
Owner:INFINEON TECH AG
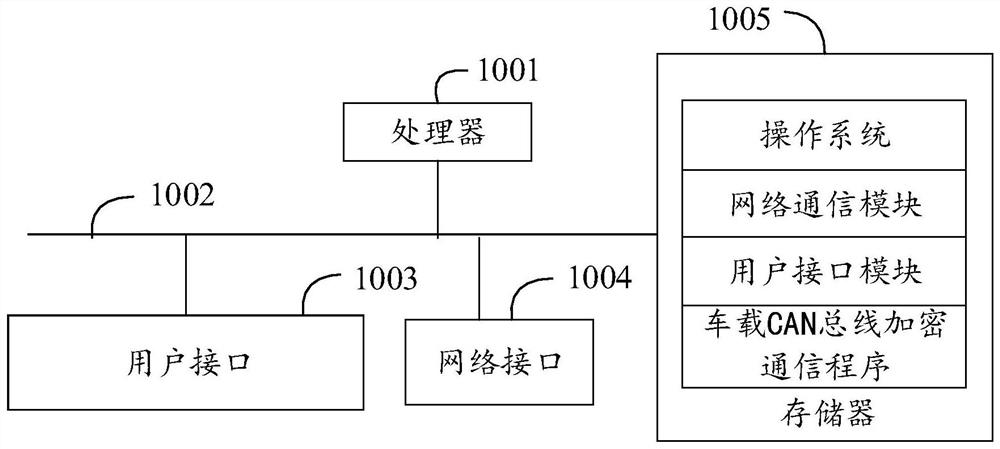
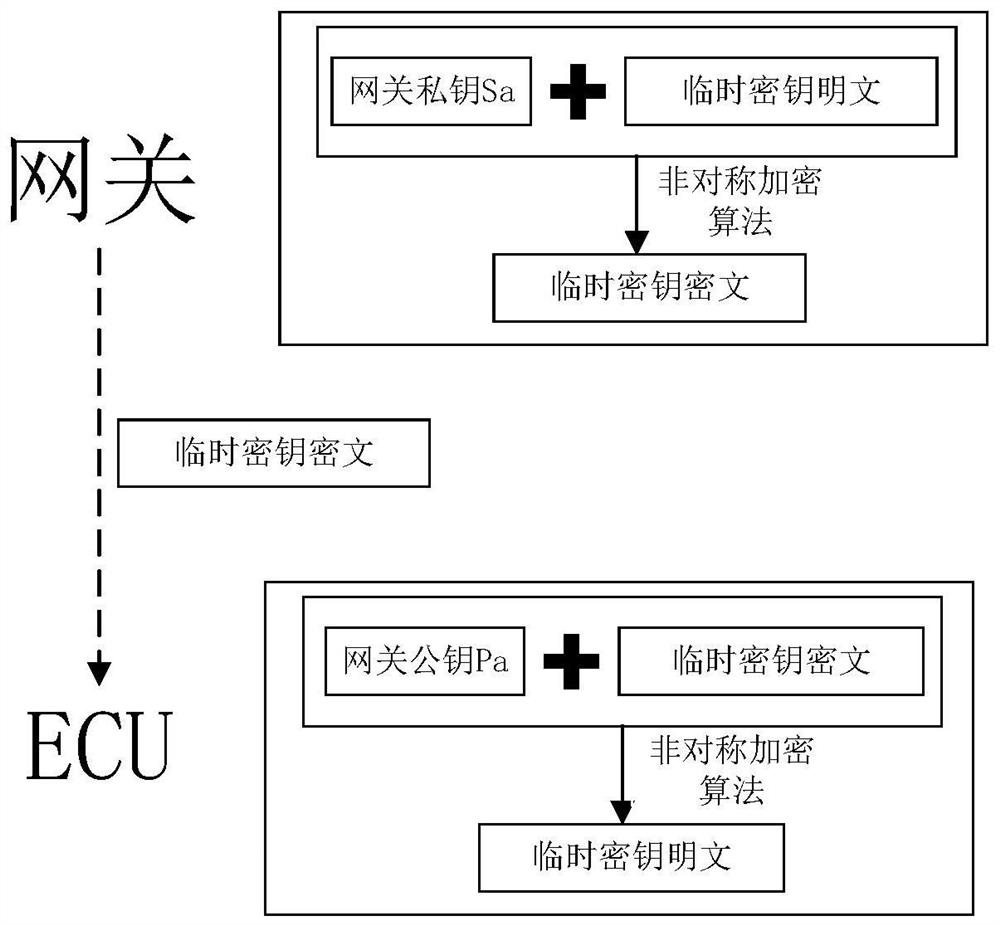
Vehicle-mounted CAN bus encryption communication method, control device and readable storage medium
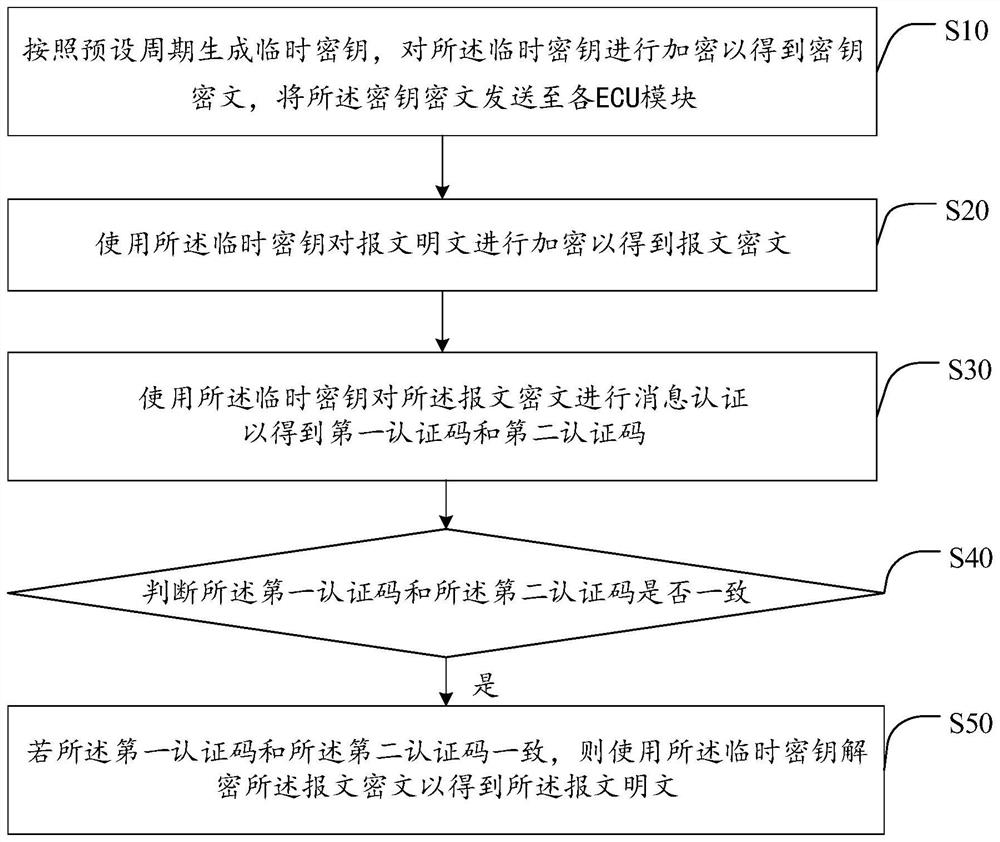
The invention discloses a vehicle-mounted CAN bus encryption communication method, a control device and a readable storage medium, and the vehicle-mounted CAN bus encryption communication method comprises the following steps: generating a temporary key according to a preset period, encrypting the temporary key to obtain a key ciphertext, and sending the key ciphertext to each ECU module through a vehicle-mounted CAN bus; encrypting a message plaintext by using the temporary key to obtain a message ciphertext; performing message authentication on the message ciphertext by using the temporary key to obtain a first authentication code and a second authentication code; judging whether the first authentication code is consistent with the second authentication code or not; and if the first authentication code is consistent with the second authentication code, decrypting the message ciphertext by using the temporary key to obtain the message plaintext. By implementing the method and the device, the confidentiality, the integrity and the authenticity of the message data are ensured, the effect of preventing the message replay attack is achieved, and the safety of the vehicle-mounted CAN bus communication is ensured.
Owner:SAIC-GM-WULING AUTOMOBILE CO LTD
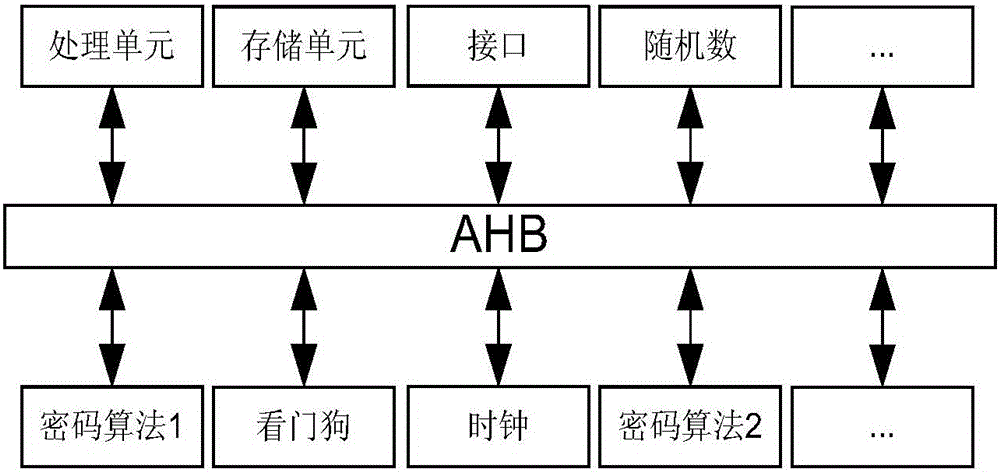
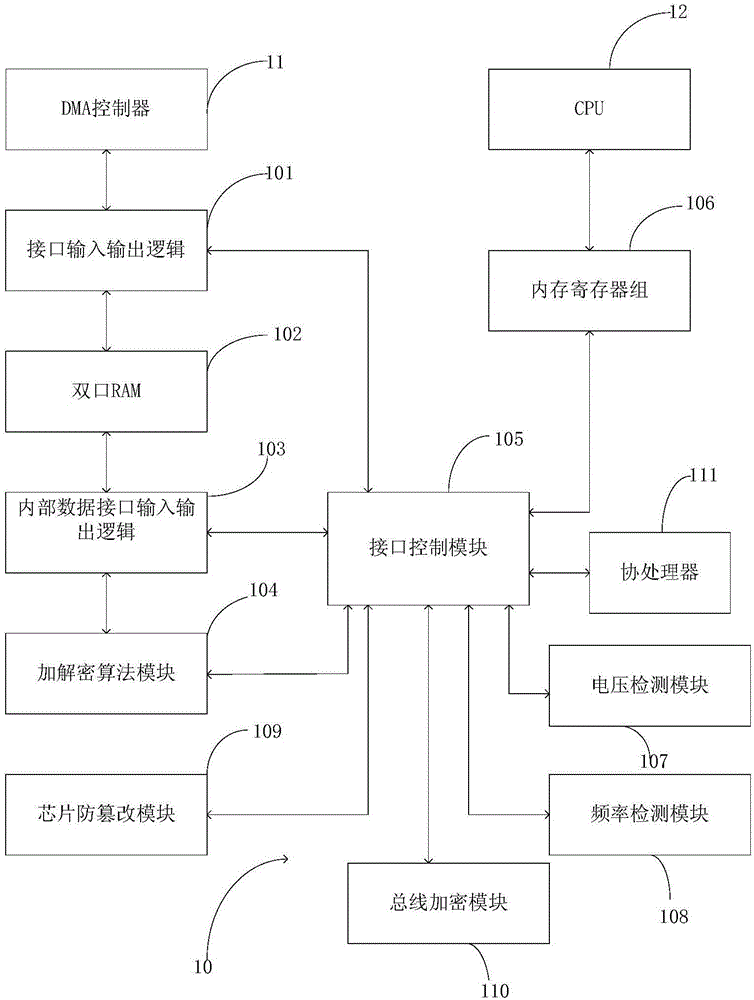
Circuit system security protection chip
The invention discloses a circuit system security protection chip. The chip comprises interface input and output logic, a dual-port RAM, internal data input and output logic, an encryption algorithm module, an interface control module, an internal register bank, a voltage detection module, a frequency detection module, a chip tamper-proofing module, a bus encryption module and a hardware 3DES algorithm coprocessor, wherein the control module is in bidirectional connection with the internal data input and output logic, the encryption algorithm module, the internal register bank and a DMA controller, and signals flow in two directions; the signal input end of the control module is connected with the signal output end of the interface input and output logic; the voltage detection module is used for resisting attacks by high and low voltages; the frequency detection module is used for resisting attacks by high and low frequencies; the chip tamper-proofing module is used for designing a unique serial number of the chip; the bus encryption module is provided with a metallic shield protective layer and used for self-destruction of internal data after external attacks are detected. Operation of the encryption chip and input of external data can be basically performed at the same time, and high speed of data flow read-write in a DMA burst read-write mode can be fully utilized to increase the data encryption and decryption speed of the chip.
Owner:深圳市华曦达科技股份有限公司
Data security protection method of computer
InactiveCN105809043AEnsure safetyEasy to useDigital data protectionDigital data authenticationData informationBus encryption
The invention discloses a data security protection method for a computer, which establishes a safe storage space for storing user data and controls the access authority of the safe storage space; the safe storage space is a protected partition isolated from other spaces on a hard disk , it is only allowed to be operated through the underlying unified extensible firmware interface UEFI; the method of sector-level read-write interception combined with the universal serial bus dongle USB‑KEY or software identity authentication is used to realize the encryption of hard disk data. The invention encrypts and decrypts the sent instructions and important user data information in the safe storage space of the hard disk multiple times, and issues a trusted authorization certificate between the sending and receiving parties of the instructions to perform legality authentication, effectively avoiding hacker interception software interception In addition, the present invention is easy to use and can control the reading and writing of data in the designated area, so that users can implement diversified protection schemes for different data according to their own needs.
Owner:LISHUI VOCATIONAL HIGH SCHOOL
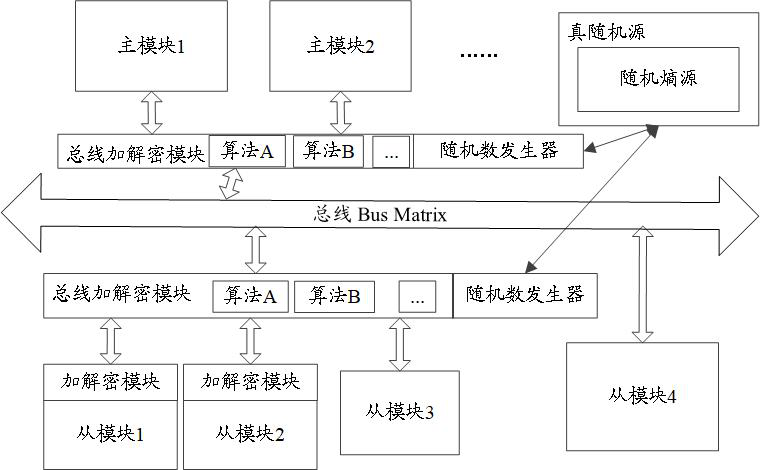
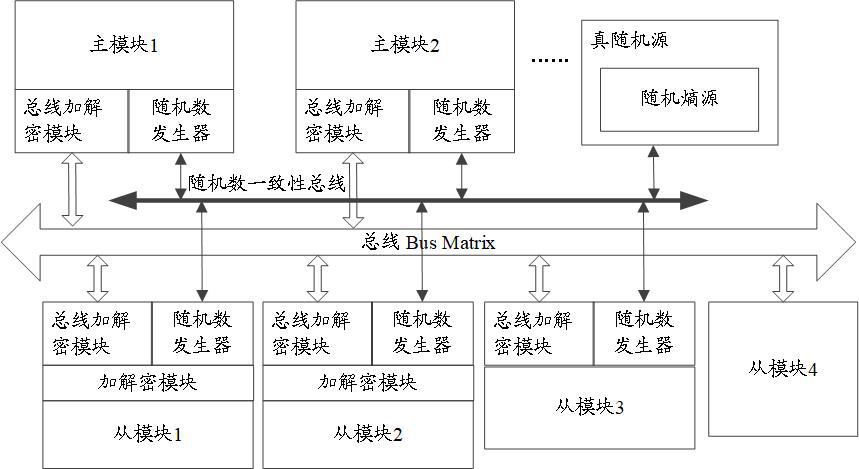
Bus data protection method and device, storage medium and chip
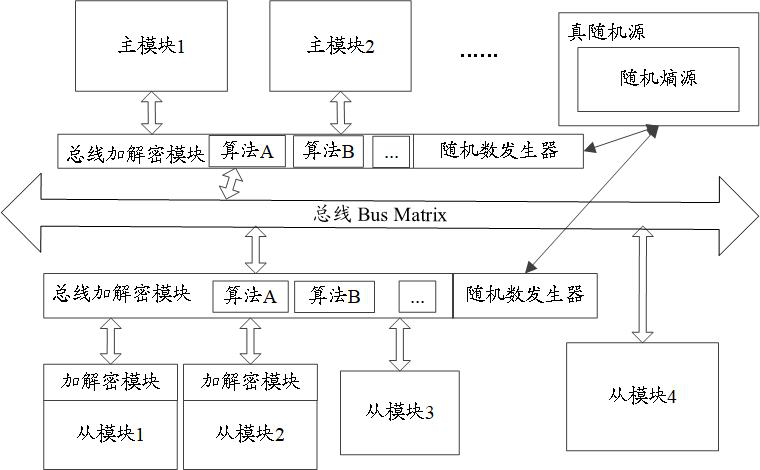
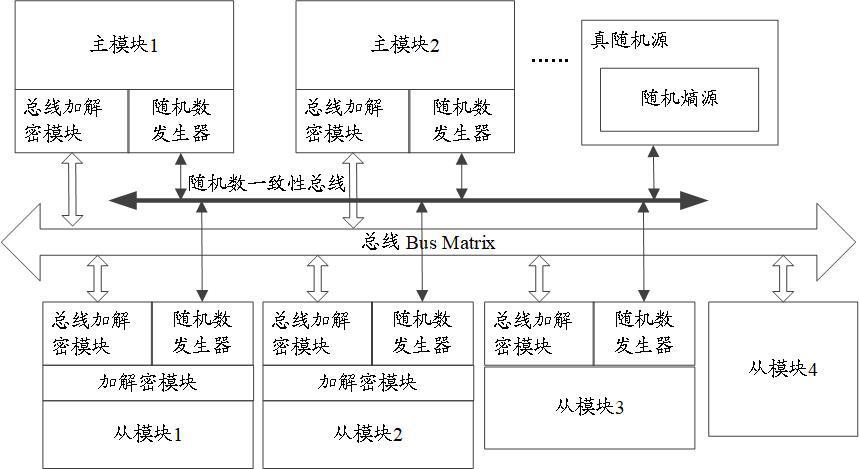
ActiveCN111814212AImprove securityReduce overheadDigital data protectionInternal/peripheral component protectionComputer hardwareBus encryption
The invention discloses a bus data protection method and device, a storage medium and a chip, and belongs to the technical field of chip security. The method comprises the following steps that: when afirst module is a master module, a second module is a slave module and the first module performs a write operation on the second module, or when the first module is the slave module, the second module is the master module and the second module performs a read operation on the first module, the first module sends sensitive data to a bus encryption module; the bus encryption module acquires a firstrandom number, and sends encrypted data obtained by encrypting the sensitive data according to the first random number to a bus; the bus sends the encrypted data to a bus decryption module; and the bus decryption module obtains a second random number and sends sensitive data obtained by decrypting the encrypted data according to the second random number to the second module, and the second randomnumber is the same as the first random number. According to the bus data protection method and device, the storage medium and the chip of the embodiments of the invention, the consistency of random numbers can be ensured, the security and accuracy of data transmission are improved, and the overhead of bus bit width is reduced.
Owner:NANJING SEMIDRIVE TECH CO LTD
CAN bus data encryption and decryption method and device
ActiveCN110247760AImprove securityAvoid economic lossKey distribution for secure communicationBus networksBus encryptionByte
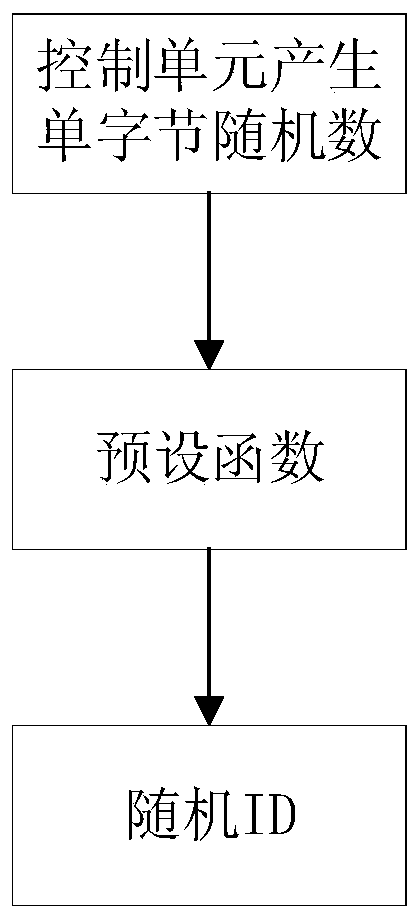
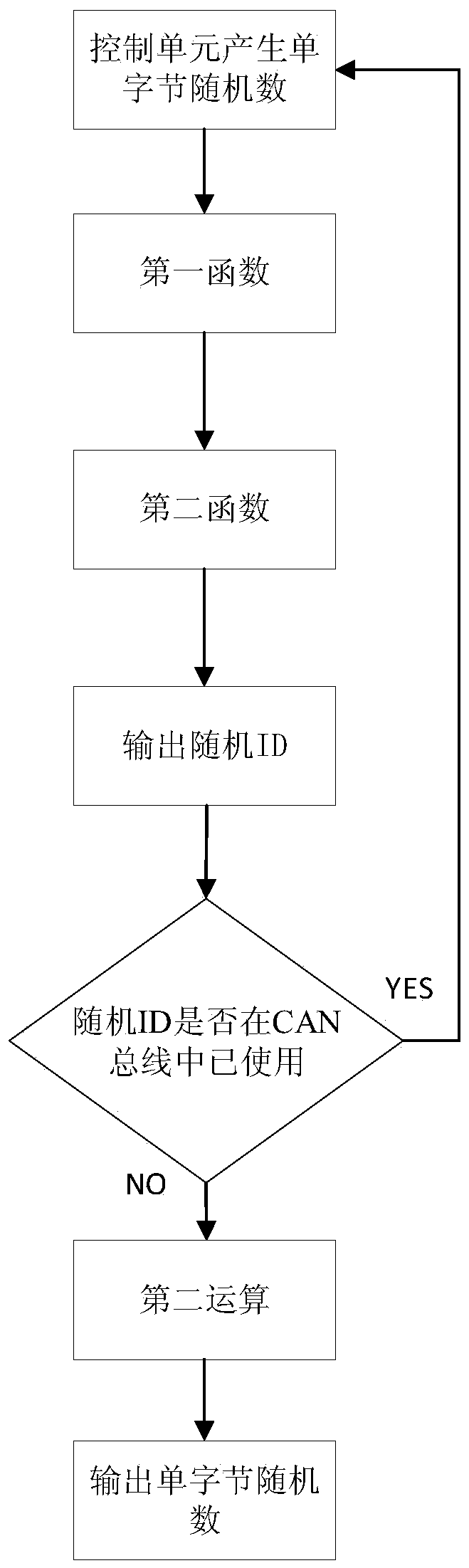
The invention provides a CAN bus data encryption and decryption method and device, and the method comprises the steps: generating a single-byte random number through a control unit, and enabling the range of the single-byte random number to be 1-255, processing the single-byte random number by a preset function to obtain a random ID with an ID domain of 29 bits, wherein the preset function is a reversible function, and the random ID for sending the encrypted data is random each time, data security is improved, the economic loss caused by modification of important parameters (hours, GPS parameters) of a service and leasing unit is avoided, at least two random IDs can be sent each time, and the true value exists in one random ID, so that the possibility that the CAN bus data is tampered is reduced, and the data security is greatly improved.
Owner:XCMG EXCAVATOR MACHINERY
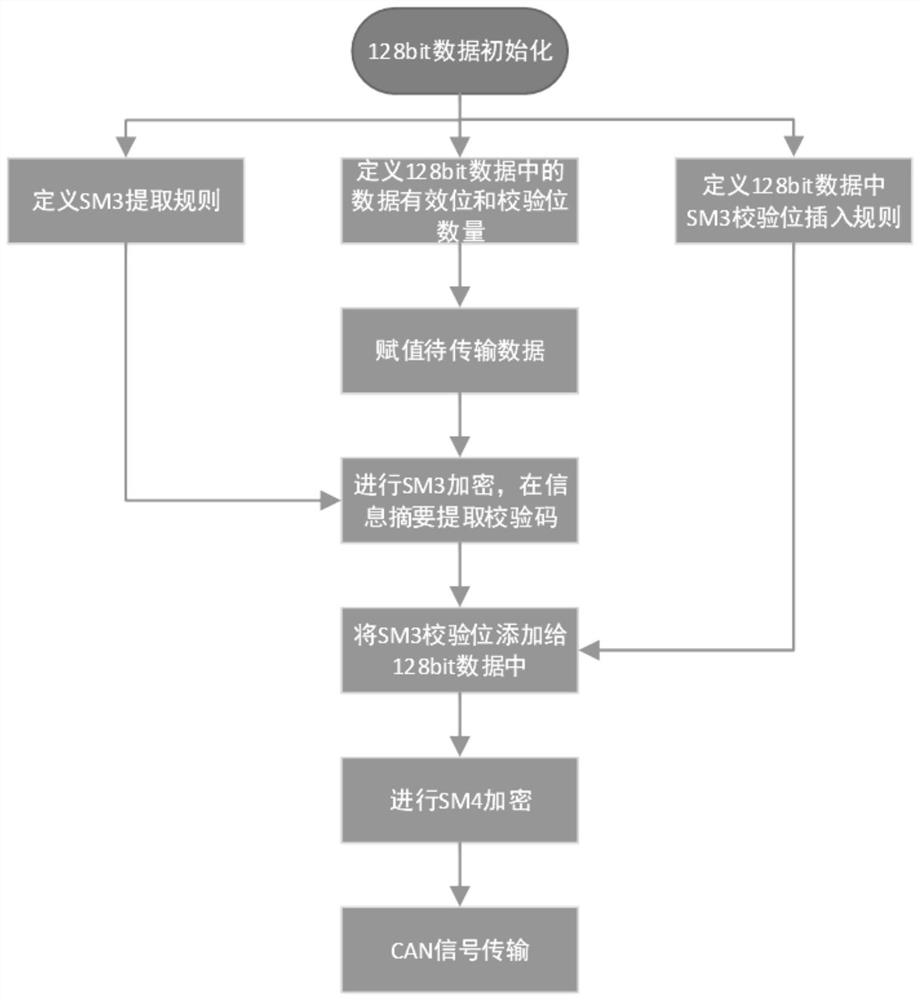
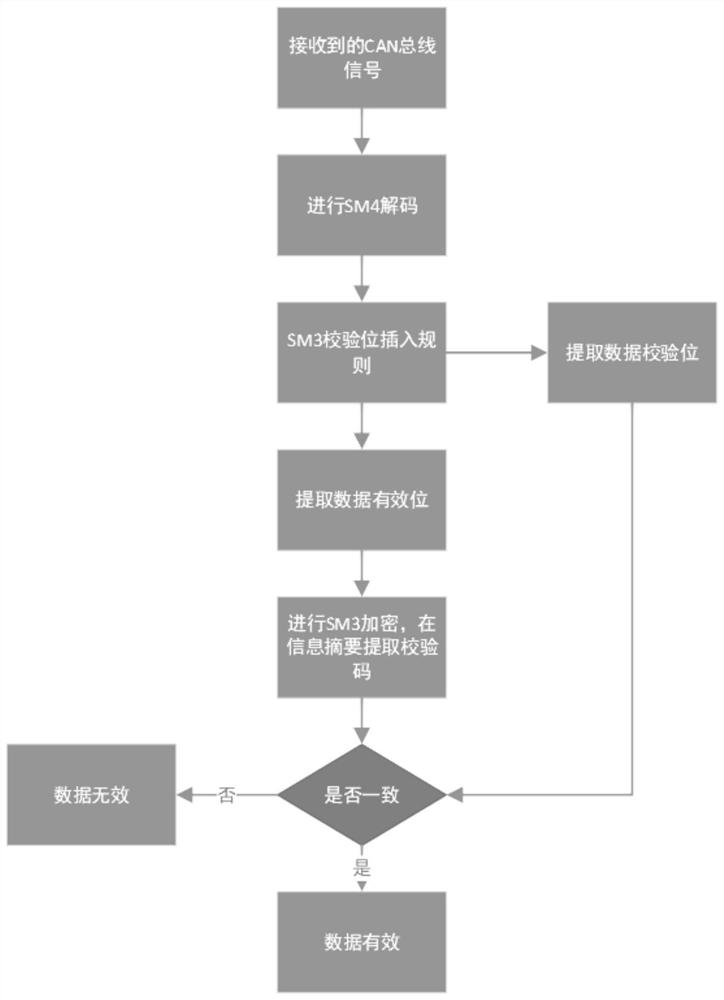
CAN bus encryption method for encrypting data by applying encryption algorithm
In order to solve the problem that a CAN bus encryption mode is easy to crack in the prior art, the invention provides a CAN bus encryption method for encrypting data by using an encryption algorithm.The method is characterized in that the following steps: performing SM3 algorithm operation on original data to generate a hash value; extracting a plurality of bits of data from the hash value, combining the data with the original data to form 128 bits of combined data, and performing SM4 algorithm operation on the combined data to encrypt the combined data; finally, realizing the decryption ofSM3 and SM4 algorithms on the FPGA platform, and completing the data interaction between software and hardware by utilizing an AXI bus. The encryption system is constructed by adopting SM3 and SM4 password symmetric encryption and decryption algorithms, an encryption method is provided for bus data, information verification can also be realized, and the security, reliability and anti-cracking capability of CAN bus data are improved.
Owner:GUANGDONG UNIV OF TECH
A kind of car CAN bus encryption method
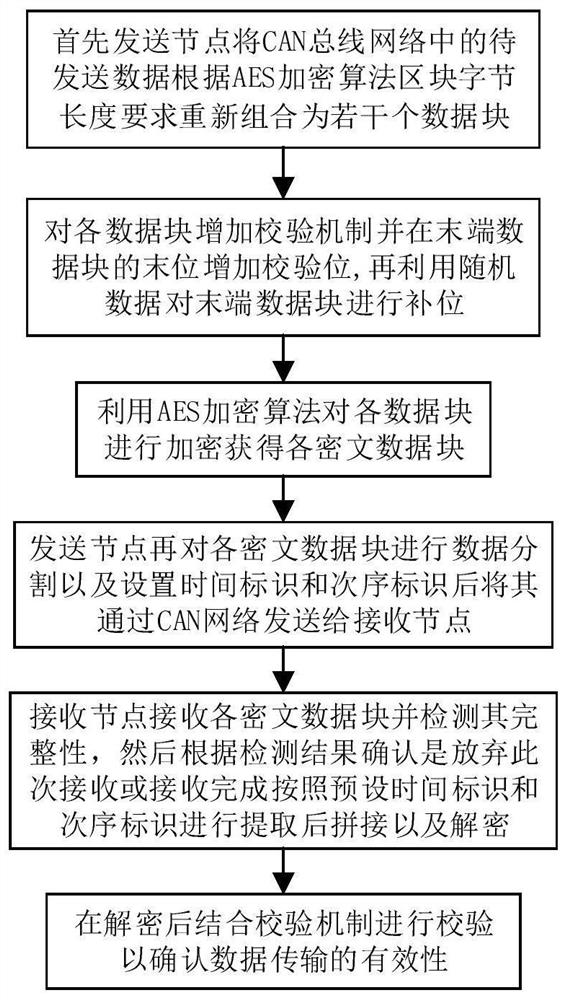
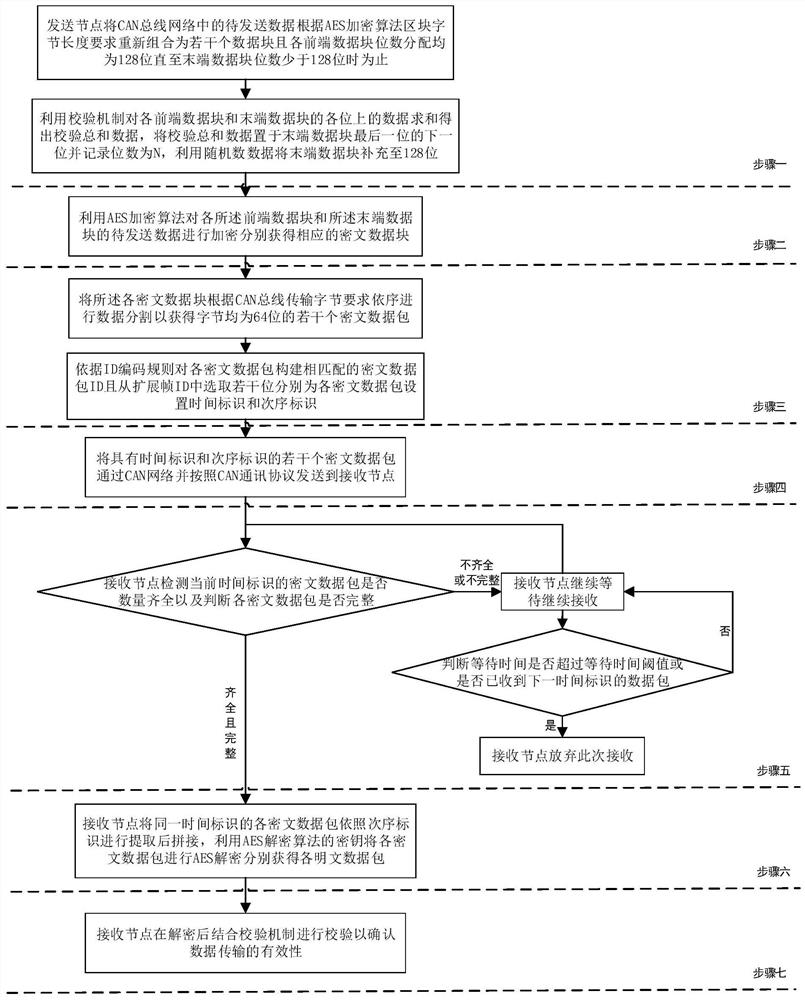
ActiveCN110545257BEnsure safetyReduce communication loadEncryption apparatus with shift registers/memoriesBus networksCiphertextCheck digit
The invention relates to a method for encrypting an automobile CAN bus. Firstly, a sending node reassembles the data to be sent in the CAN bus network into several data blocks according to the block byte length requirements of the AES encryption algorithm, and adds a verification mechanism to each data block. And add a check digit at the end of the end data block, and then use random data to fill the end data block, use the AES encryption algorithm to encrypt each data block to obtain each ciphertext data block, and then send the node to each ciphertext data After dividing the block into data and setting the time mark and order mark, it is sent to the receiving node through the CAN network. The receiving node receives each ciphertext data block and checks its integrity. The time mark and the order mark are set to be extracted, spliced and decrypted, and after decryption, combined with the verification mechanism for verification to confirm the validity of the data transmission, which improves the efficiency of data transmission and ensures the security of data information transmission on the car.
Owner:BEIJING HANGSHENG NEW ENERGY TECH CO LTD
Method and device for storing data on a record medium and for transferring information
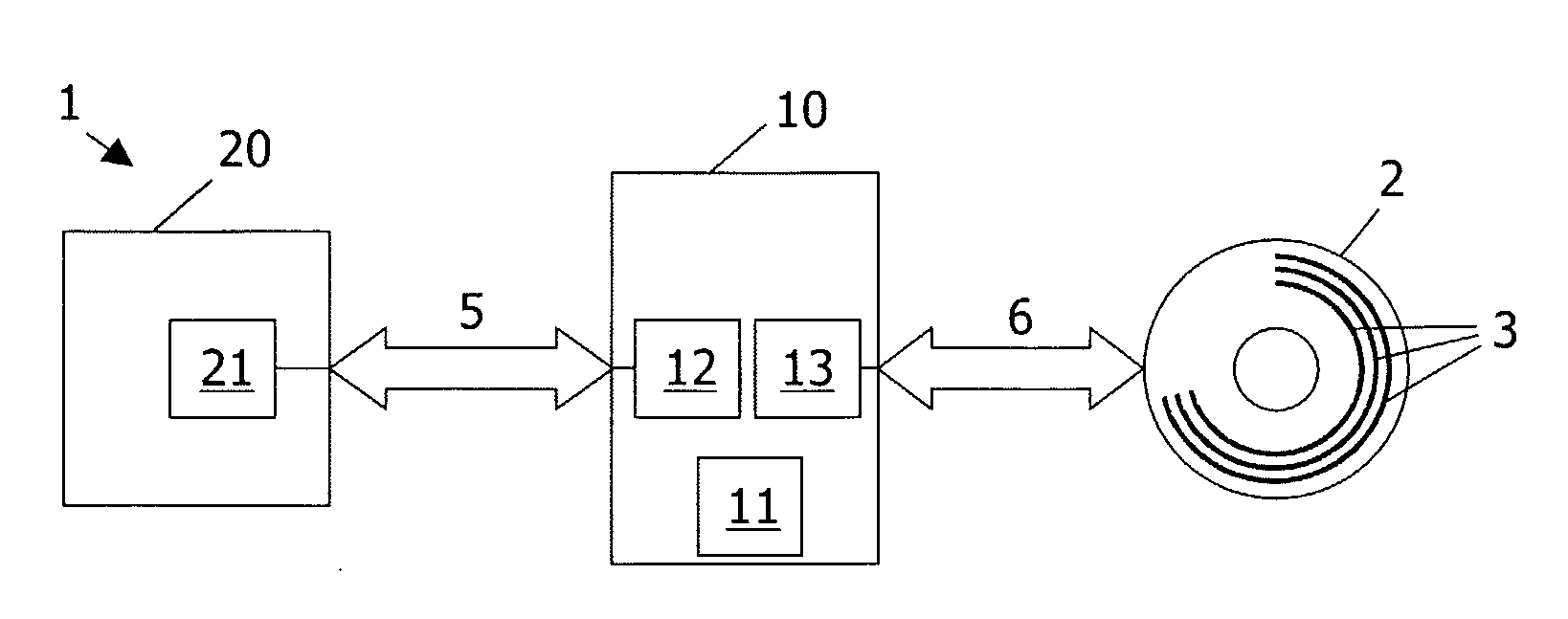
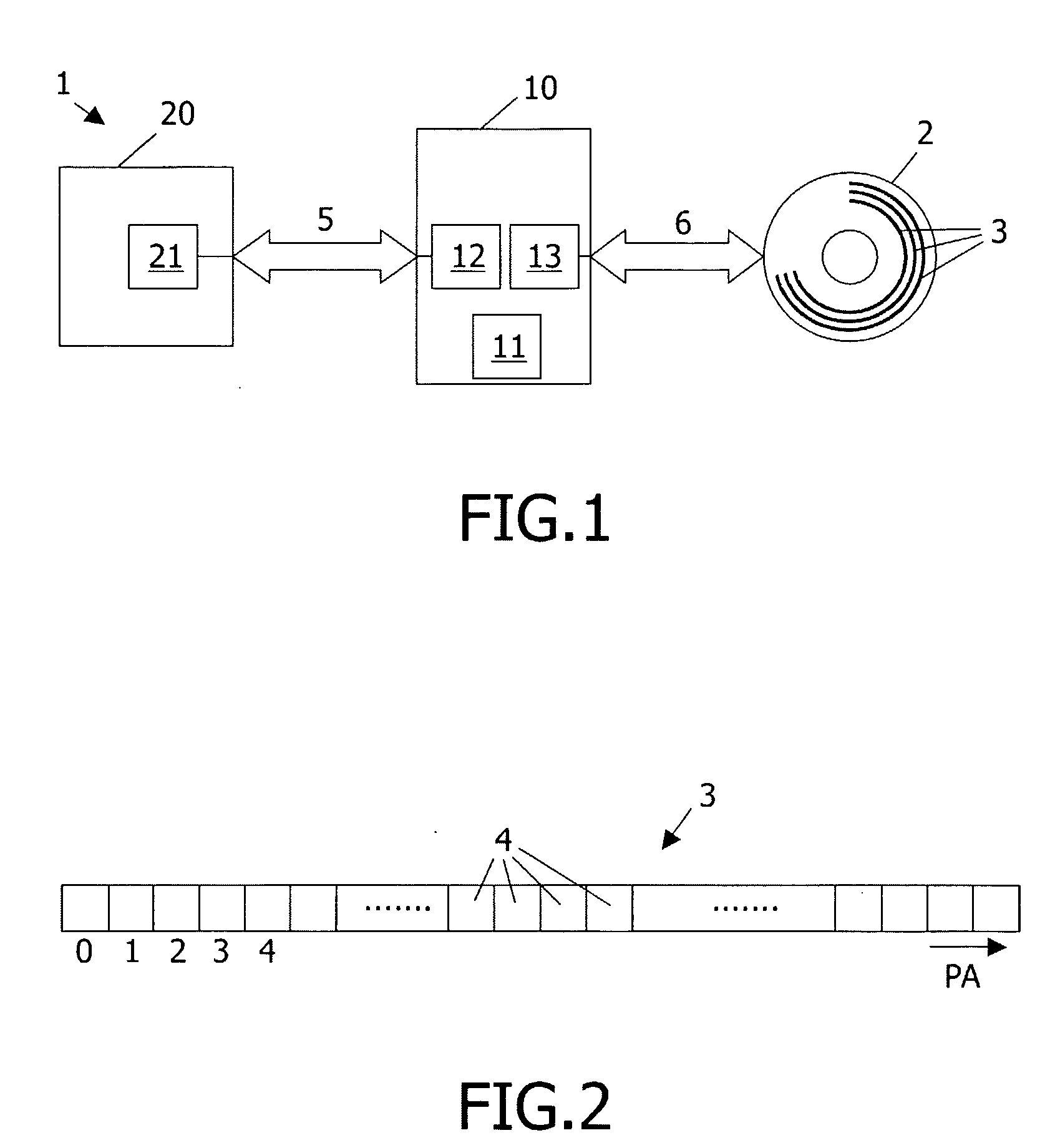
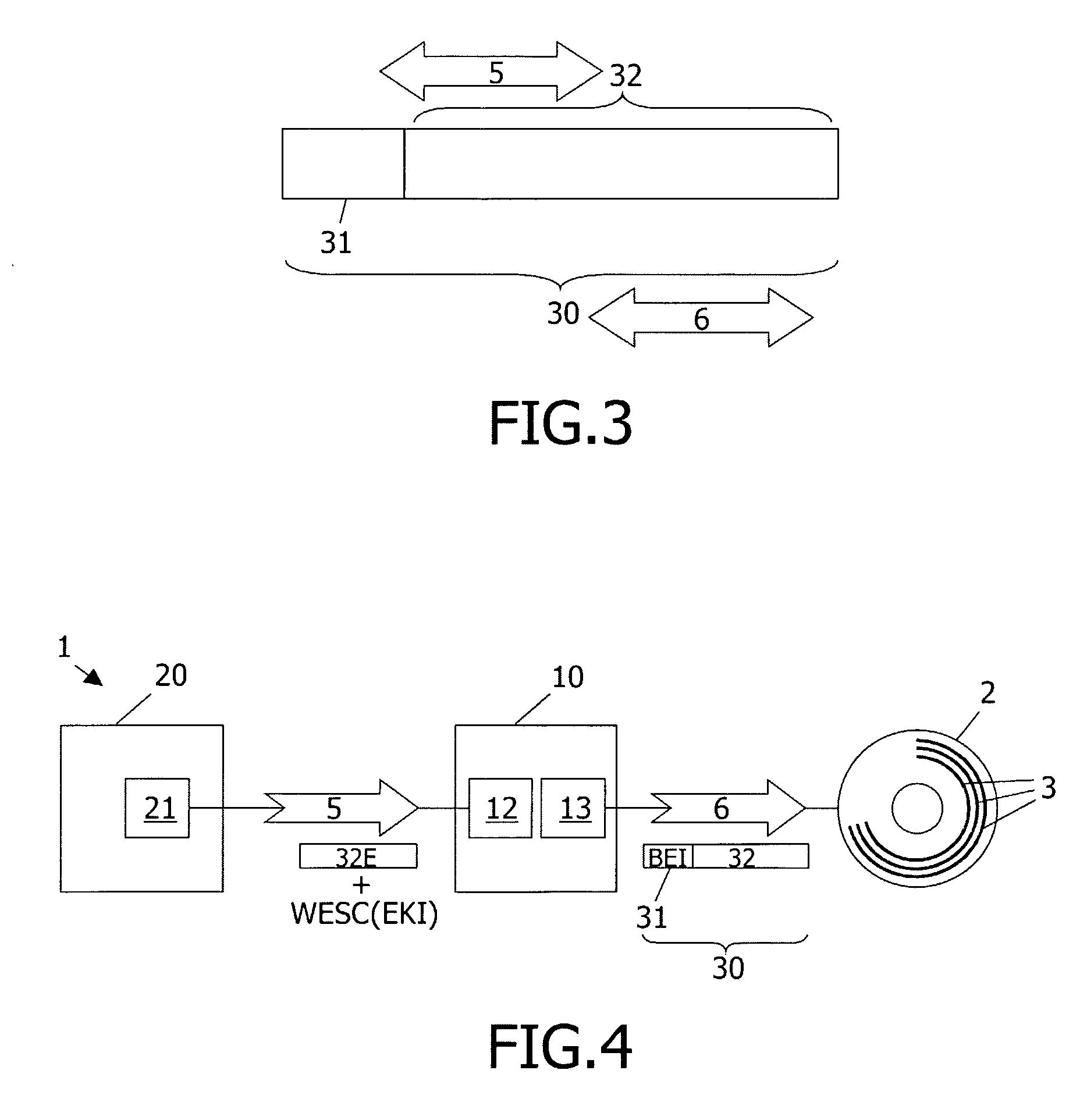
InactiveUS20090185467A1Not possibleCombination recordingRecord information storageComputer hardwareBus encryption
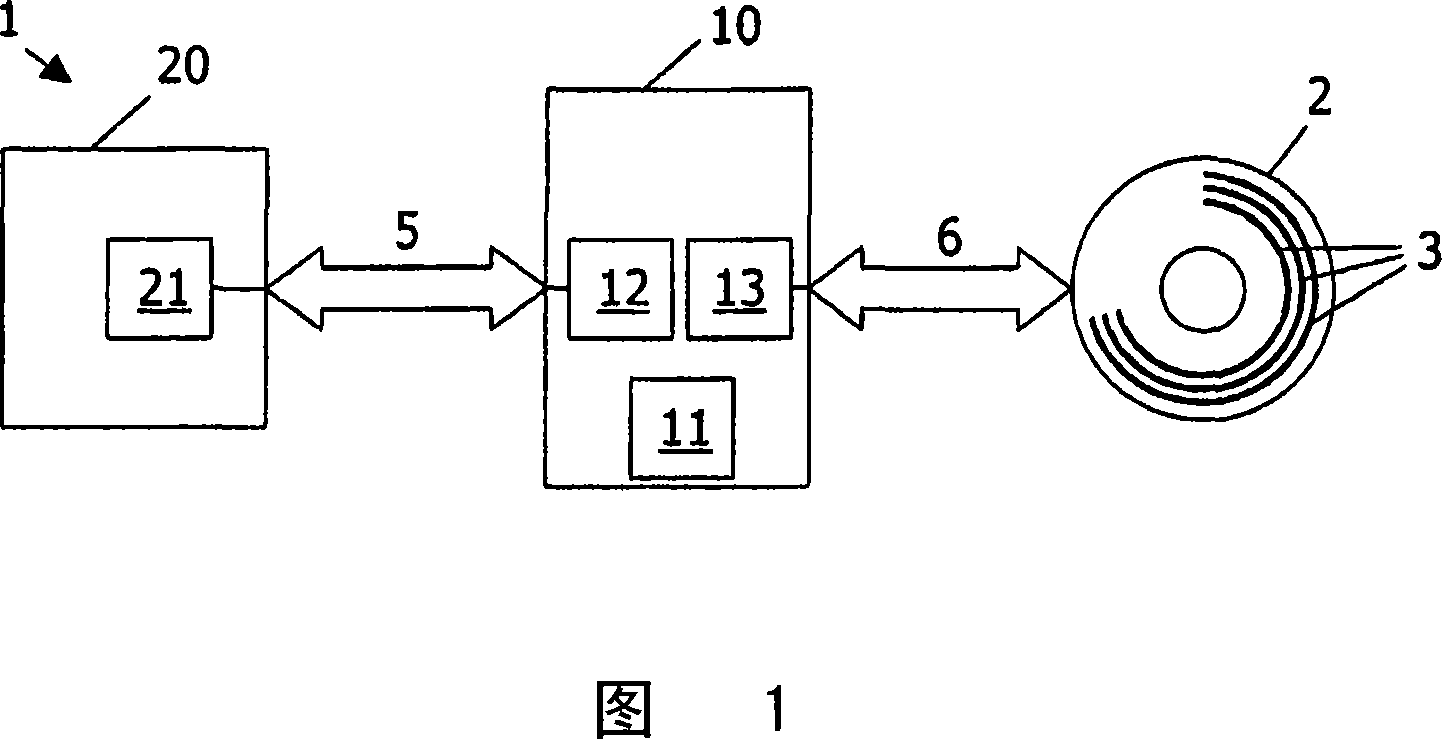
Data storage system (1) comprises: an optical disc (2) having a storage space (3) for receiving sectors of data; a disc drive (10), suitable for writing information to the disc; a host (20), capable of cooperating with the drive; the host being designed to send to said drive a write encrypted sector command WESC(EKI) for commanding said drive to write one or more bus-encrypted sectors to said disc, WESC(EKI) including an encryption key identifier EKI; the drive being designed, in response to receiving said WESC(EKI), to evaluate the value of EKI, and, if the value of EKI indicates a bus-encrypted user data portion (32E), to decrypt this user data portion, to generate a header portion (31) with bus encryption information BEI, to combine this header portion with the decrypted user sector portion (32) to make a data sector (30), and to write the data sector (30) to the disc.
Owner:KONINKLIJKE PHILIPS ELECTRONICS NV
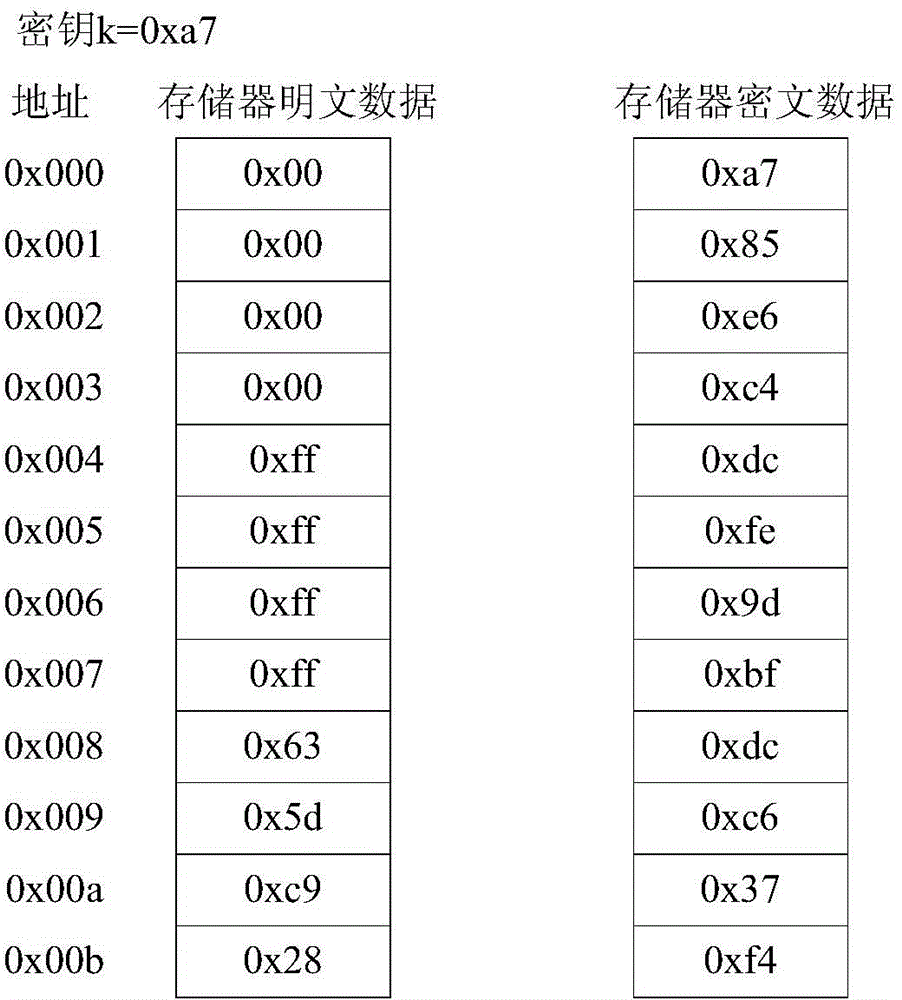
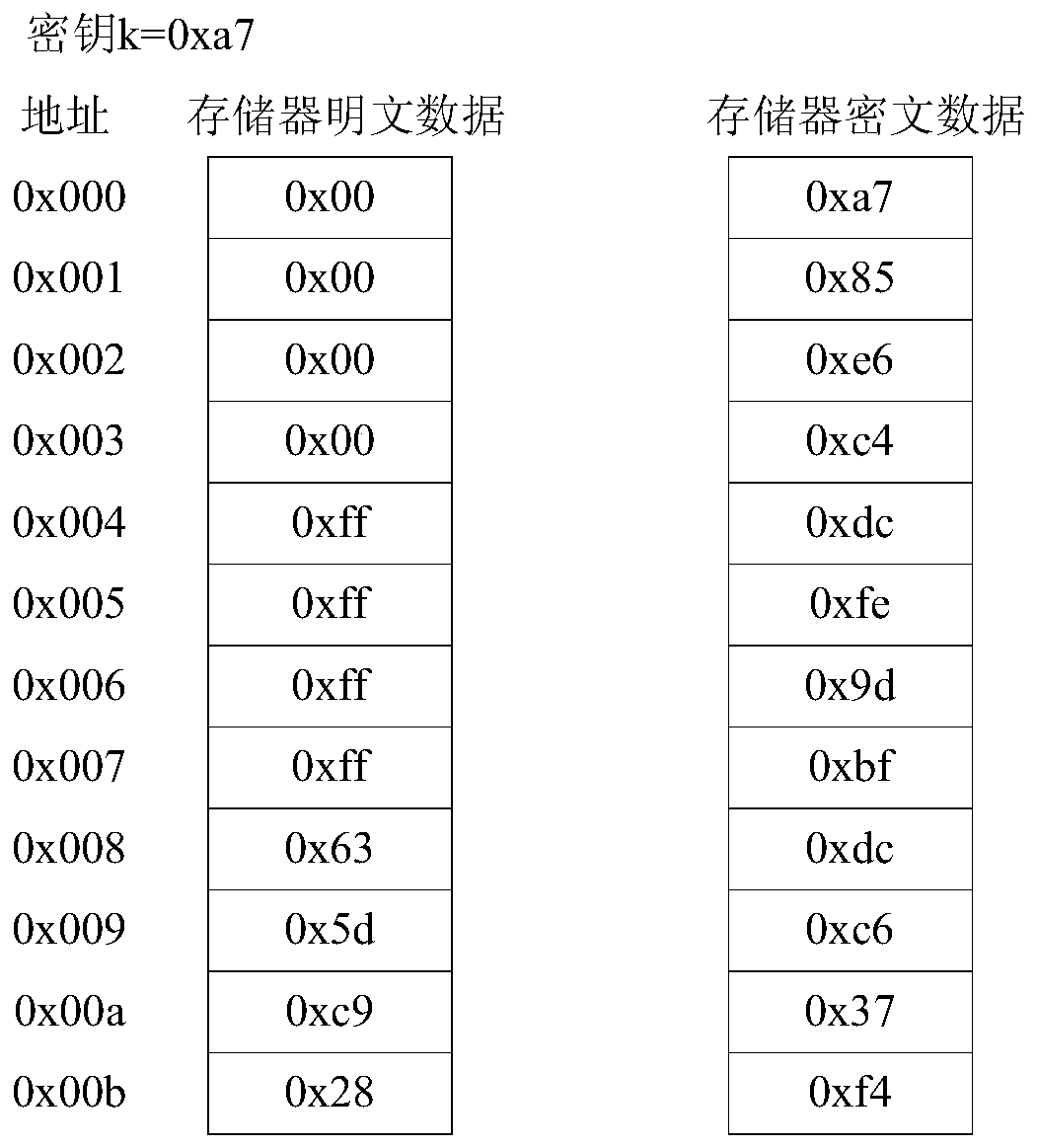
Address XOR based data bus encryption method
ActiveCN105743652AReduce correlationIncrease the difficultyEncryption apparatus with shift registers/memoriesUser identity/authority verificationMemory addressPlaintext
The invention discloses an address XOR based data bus encryption method. A bus encryption key after XOR is obtained by performing XOR operation on each bit of the bus encryption key with a certain bit or multiple bits of a memory address bus. Cryptograph data is obtained by performing XOR on the bus encryption key after address XOR with memory plaintext data. XOR keys corresponding to plaintext data in each address are different, and thus attackers cannot restore plaintexts easily by reckoning the keys through analyzing the cryptograph data. The method provided by the invention can fend off physical attacks of memory data, effectively improve the system security and also substantially improves the computation speed.
Owner:SHANGHAI HUAHONG INTEGRATED CIRCUIT
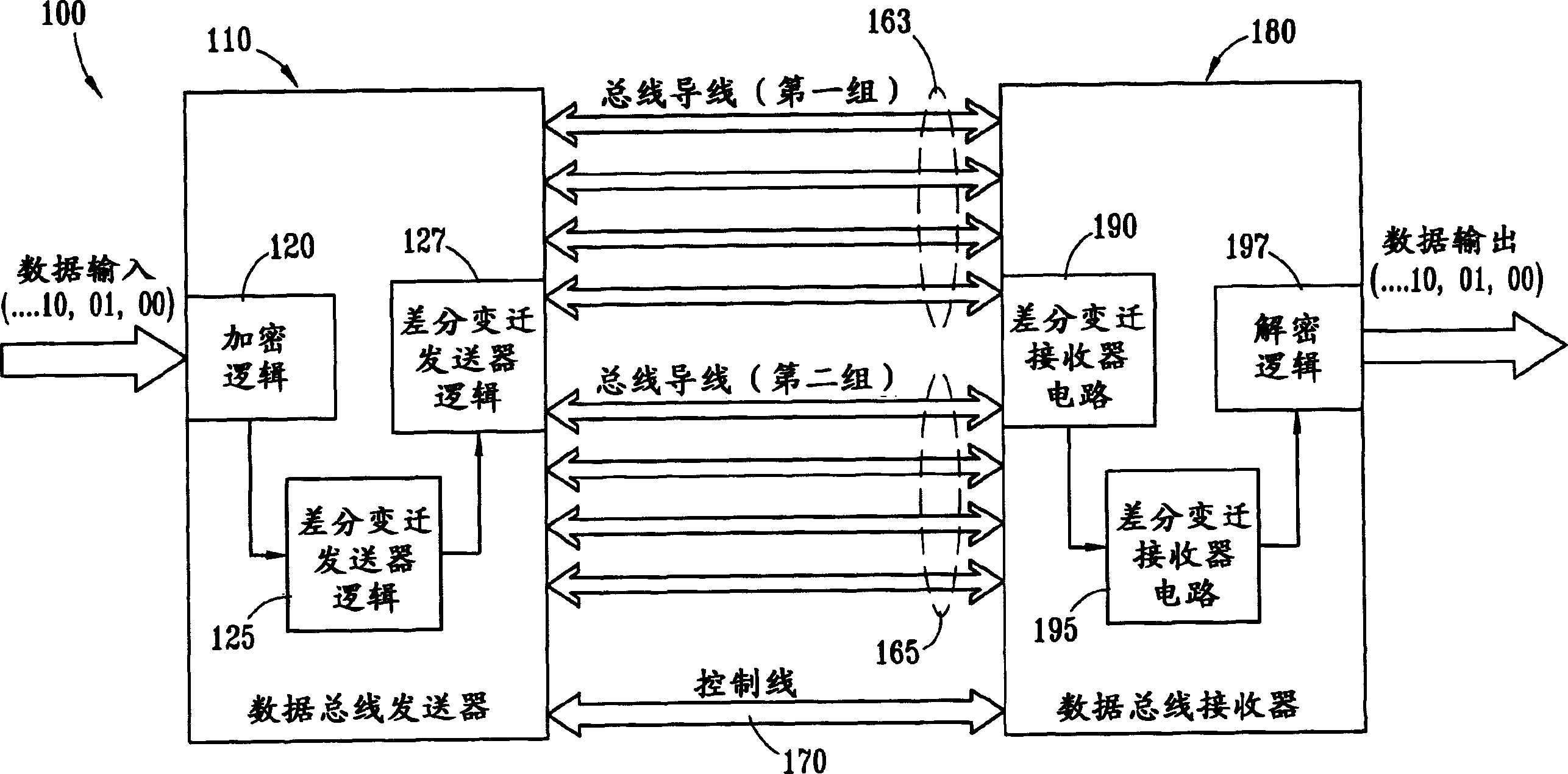
Method and system for encrypting bus using improved difference transition code
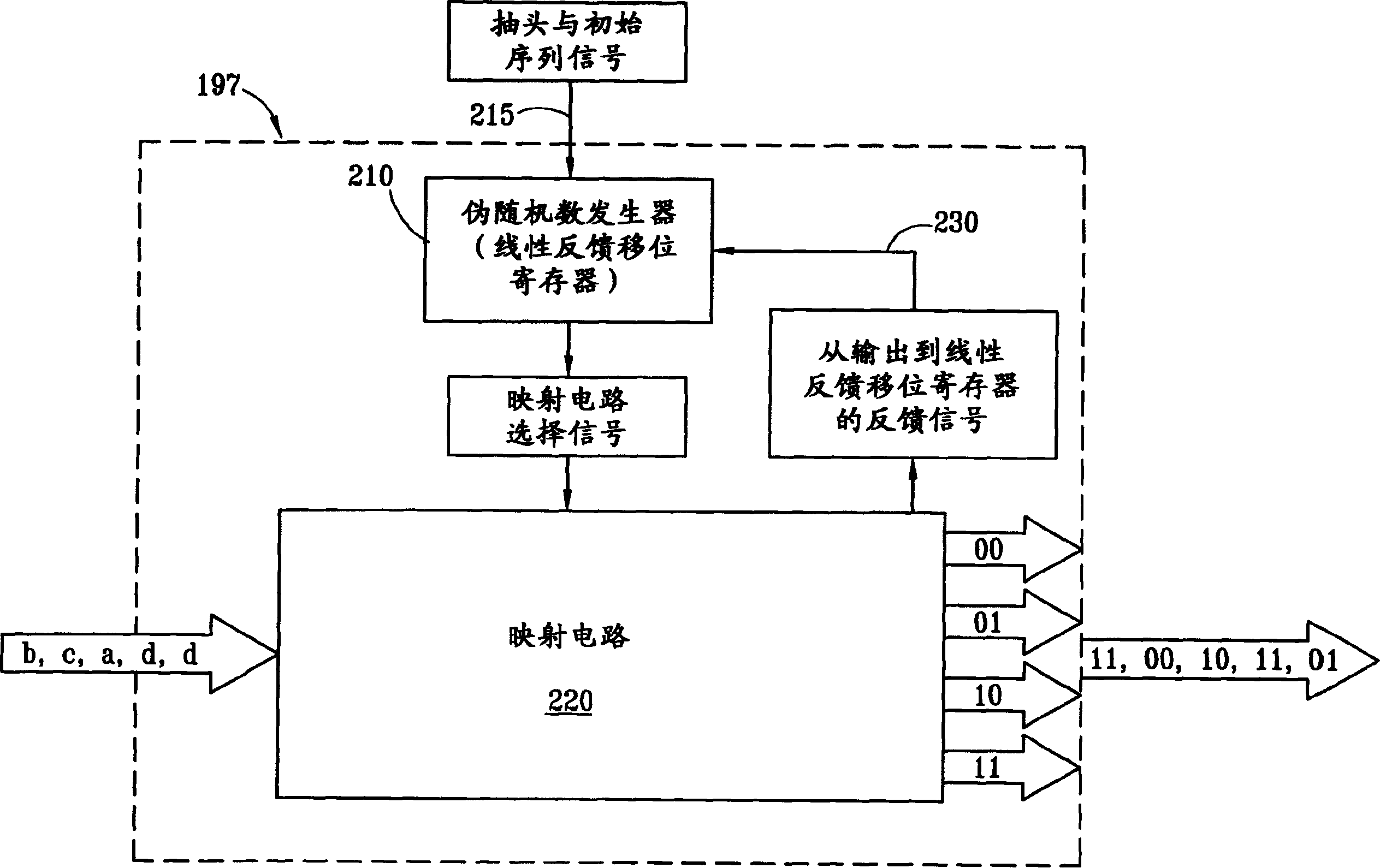
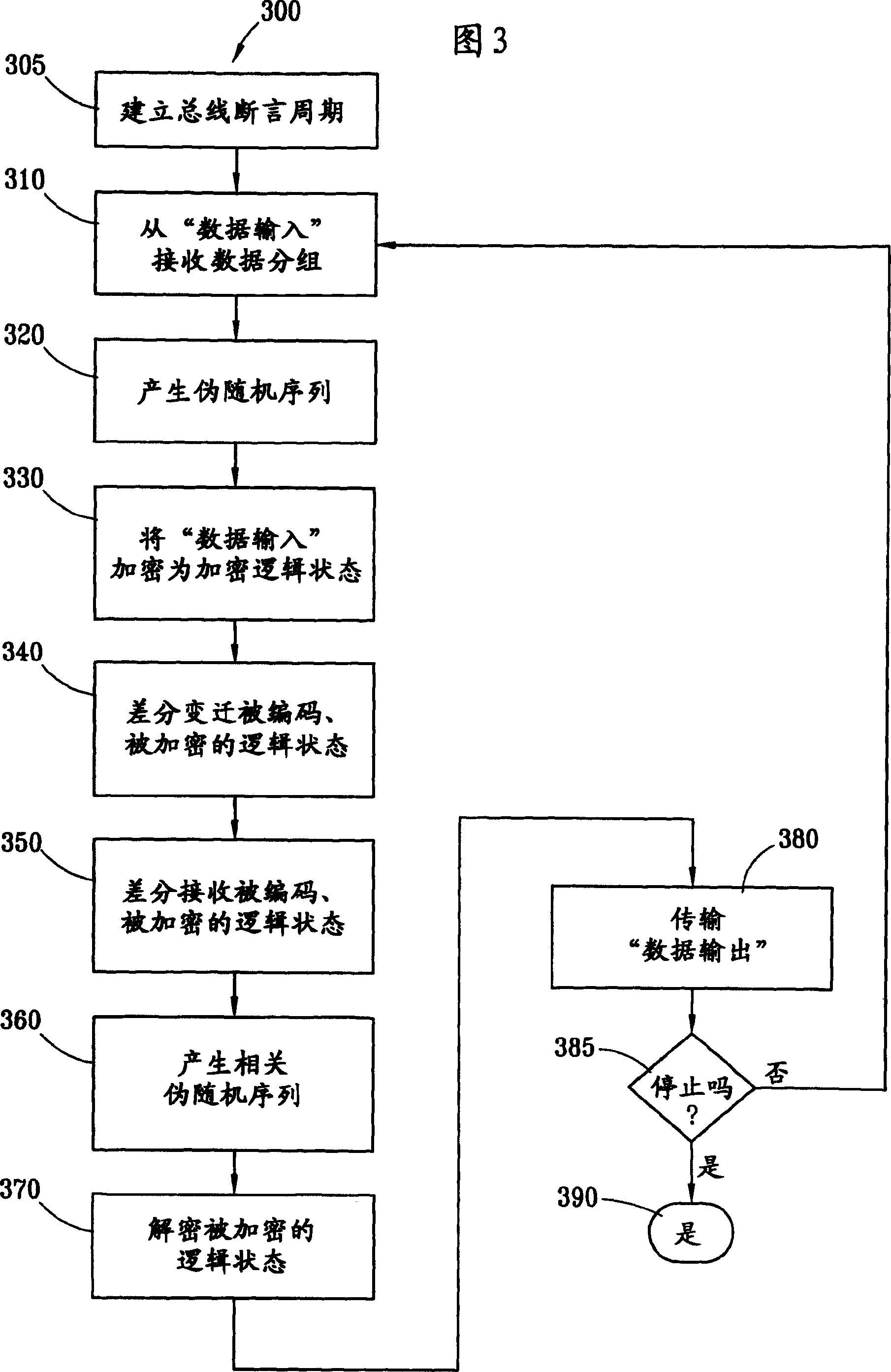
InactiveCN1492339AData stream serial/continuous modificationCoding/ciphering apparatusBus encryptionENCODE
The present invention provides data encryption for a differential bus employing transitional coding. The present invention maps, encodes and encrypts input data as a logic status for a given bus transfer cycle. The mapping, encoding and encrypting of the input data changes from bus transfer cycle to bus transfer cycle. The mapping, encoding and encrypting is a function of a pseudo-random number. A logic status is differentially transmitted from a bus transmitter to a bus receiver, to be mapped, decrypted and decoded as the corresponding output data.
Owner:IBM CORP
CAN bus encryption method and device, engineering machinery and storage medium
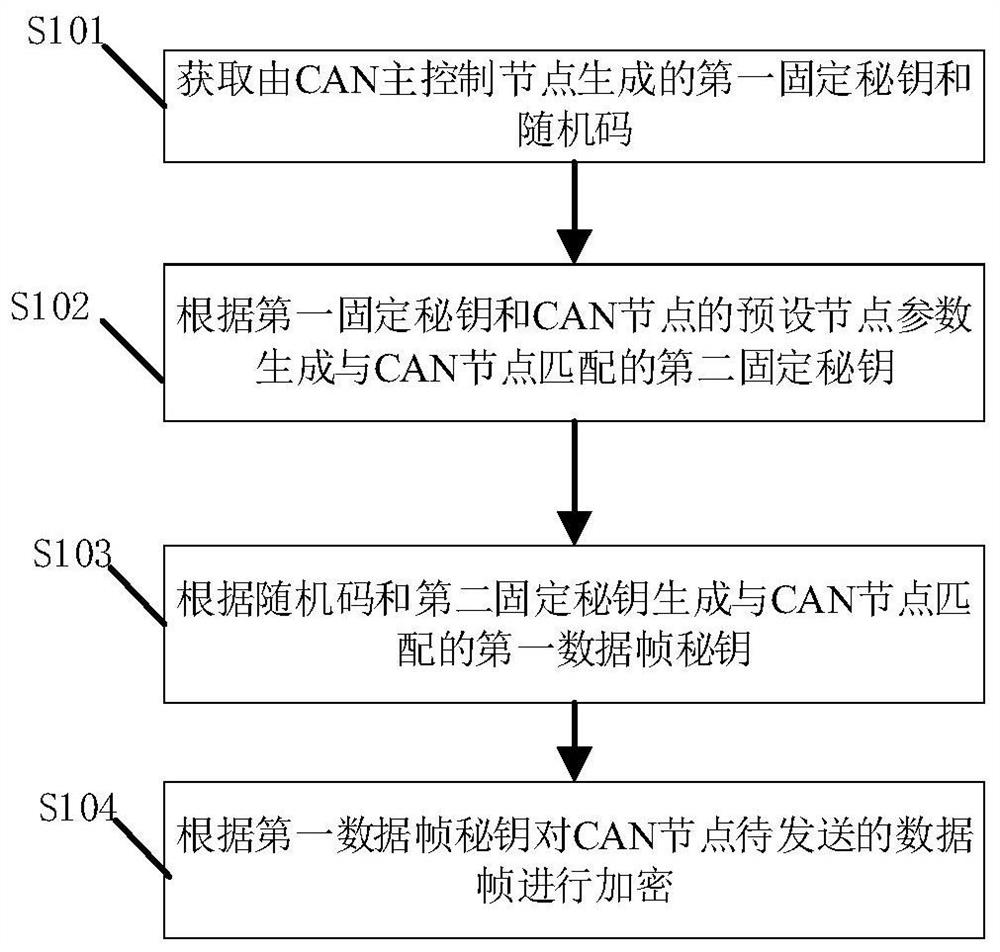
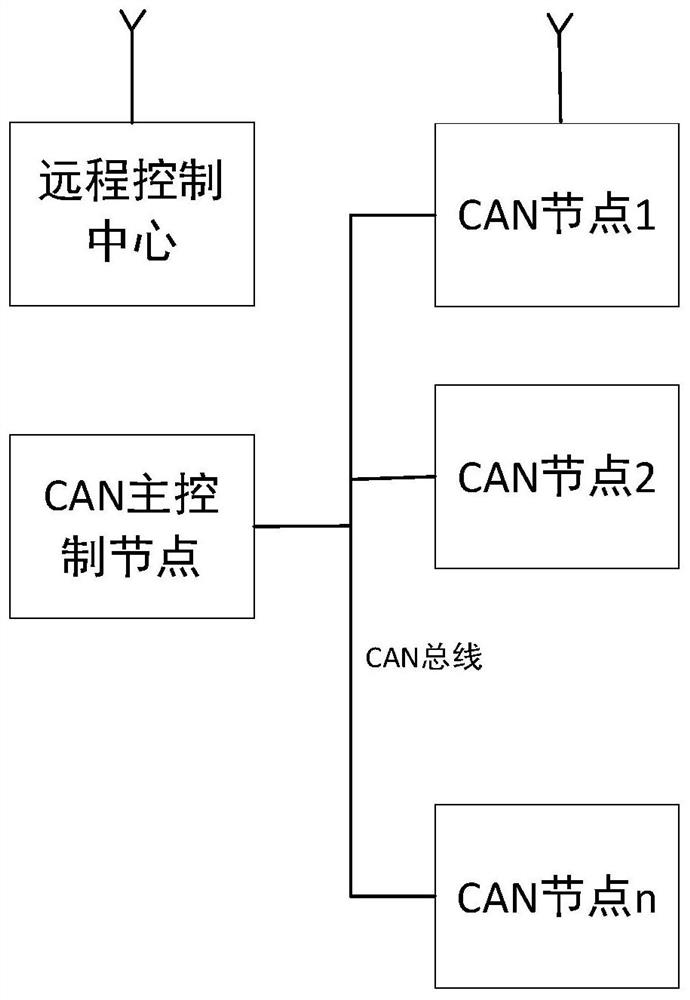
ActiveCN113098860AKey distribution for secure communicationBus networksComputer hardwareBus encryption
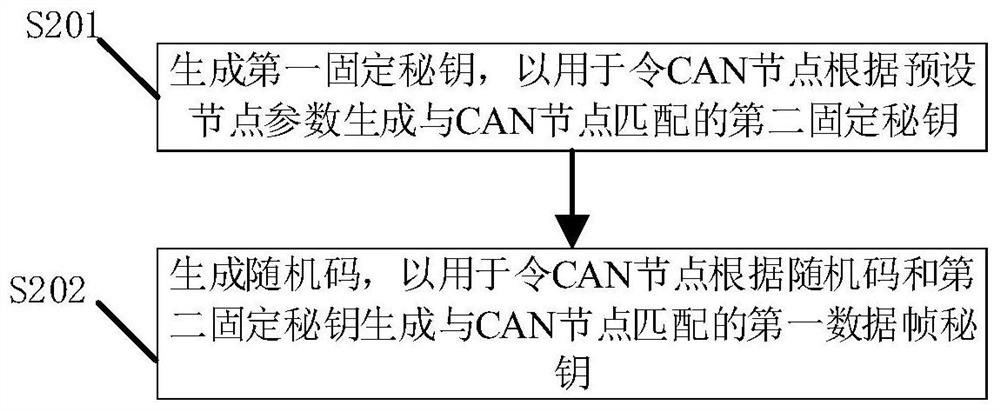
The invention provides a CAN bus encryption method and device, engineering machinery and a storage medium. The CAN bus encryption method comprises the following steps: acquiring a first fixed key and a random code generated by a CAN main control node; generating a second fixed secret key matched with the CAN node according to the first fixed secret key and a preset node parameter of the CAN node; generating a first data frame secret key matched with the CAN node according to the random code and the second fixed secret key; and encrypting a data frame to be sent by the CAN node according to the first data frame secret key. The invention has the beneficial effect that the security after data encryption can be improved under the condition of ensuring the running speed of the CAN node.
Owner:SANY AUTOMOBILE HOISTING MACHINERY
Method and device for storing data on a record medium and for transferring information
InactiveCN101031968ARecord information storageInternal/peripheral component protectionComputer hardwareBus encryption
Data storage system (1) comprises: an optical disc (2) having a storage space (3) for receiving sectors of data; a disc drive (10), suitable for writing information to the disc; a host (20), capable of cooperating with the drive; the host being designed to send to said drive a write encrypted sector command WESC(EKI) for commanding said drive to write one or more bus-encrypted sectors to said disc, WESC(EKI) including an encryption key identifier EKI; the drive being designed, in response to receiving said WESC(EKI), to evaluate the value of EKI, and, if the value of EKI indicates a bus-encrypted user data portion (32E), to decrypt this user data portion, to generate a header portion (31) with bus encryption information BEI, to combine this header portion with the decrypted user sector portion (32) to make a data sector (30), and to write the data sector (30) to the disc.
Owner:KONINKLIJKE PHILIPS ELECTRONICS NV
Data Bus Encryption Method Based on XOR Address
ActiveCN105743652BReduce correlationIncrease the difficultyEncryption apparatus with shift registers/memoriesUser identity/authority verificationComputer hardwareMemory address
The invention discloses an address XOR based data bus encryption method. A bus encryption key after XOR is obtained by performing XOR operation on each bit of the bus encryption key with a certain bit or multiple bits of a memory address bus. Cryptograph data is obtained by performing XOR on the bus encryption key after address XOR with memory plaintext data. XOR keys corresponding to plaintext data in each address are different, and thus attackers cannot restore plaintexts easily by reckoning the keys through analyzing the cryptograph data. The method provided by the invention can fend off physical attacks of memory data, effectively improve the system security and also substantially improves the computation speed.
Owner:SHANGHAI HUAHONG INTEGRATED CIRCUIT
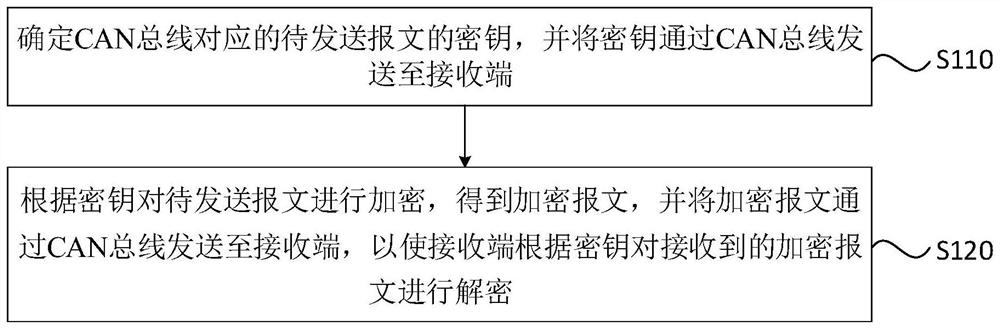
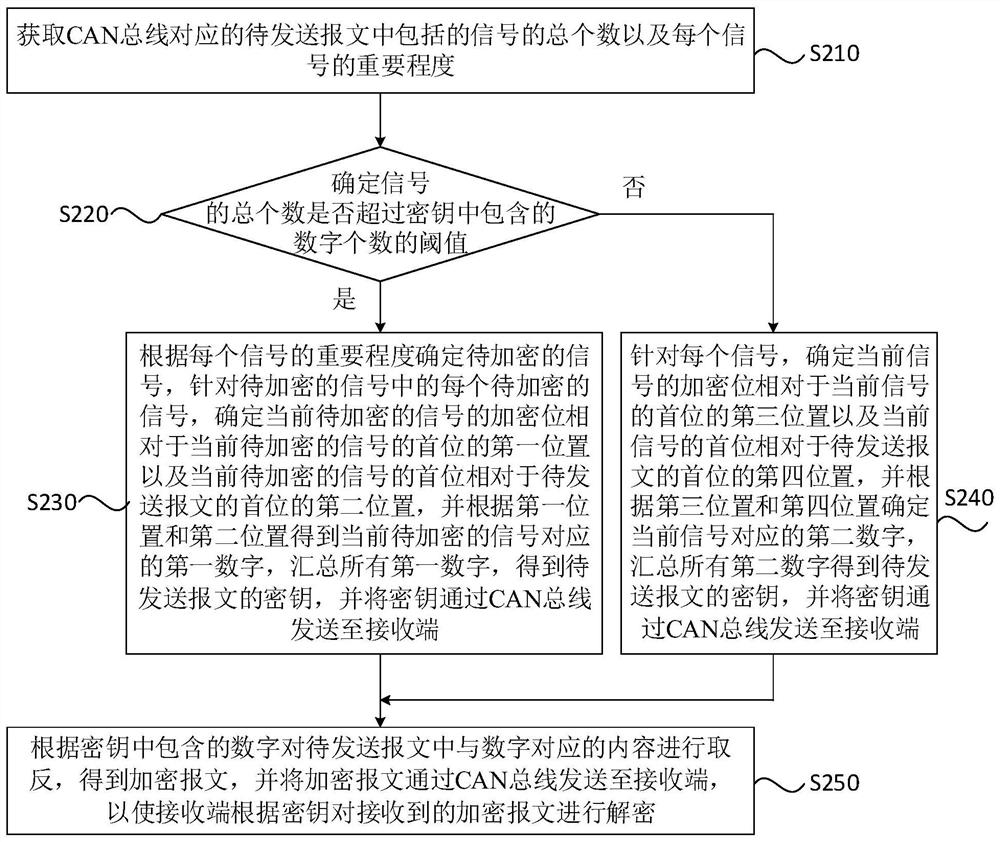
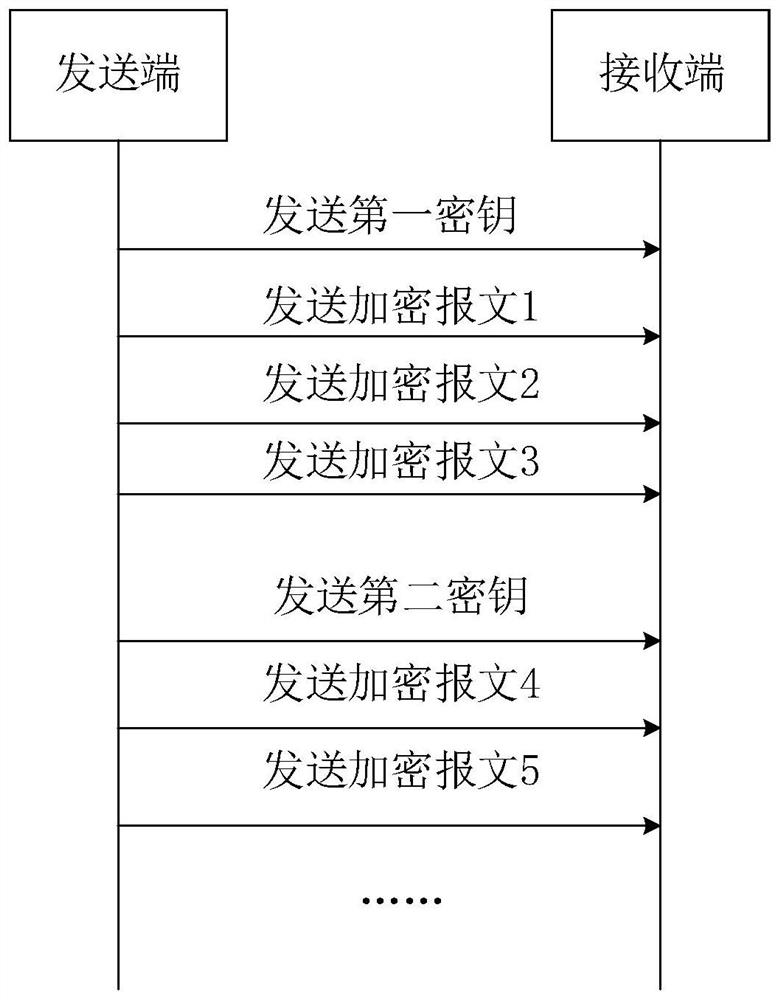
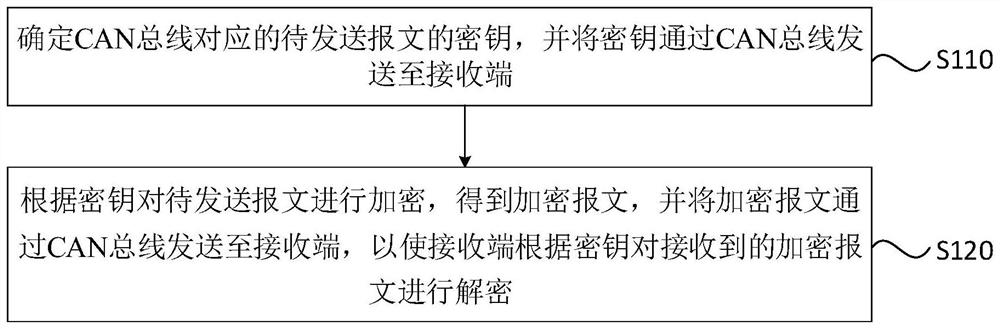
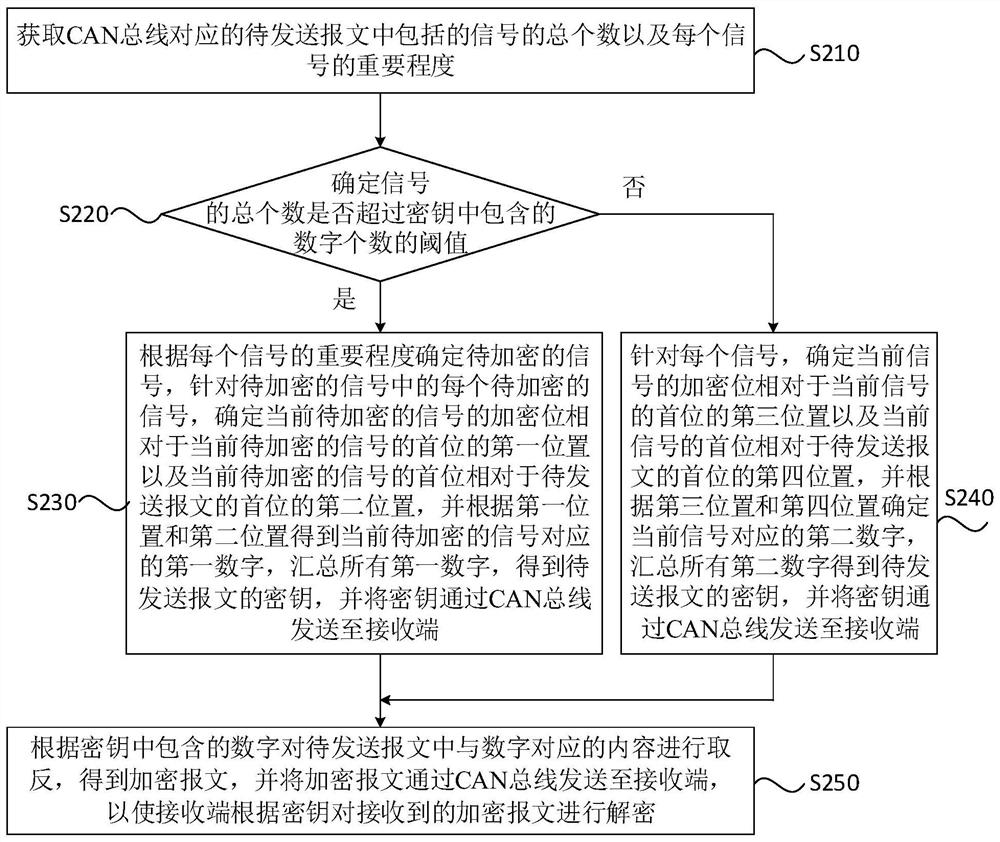
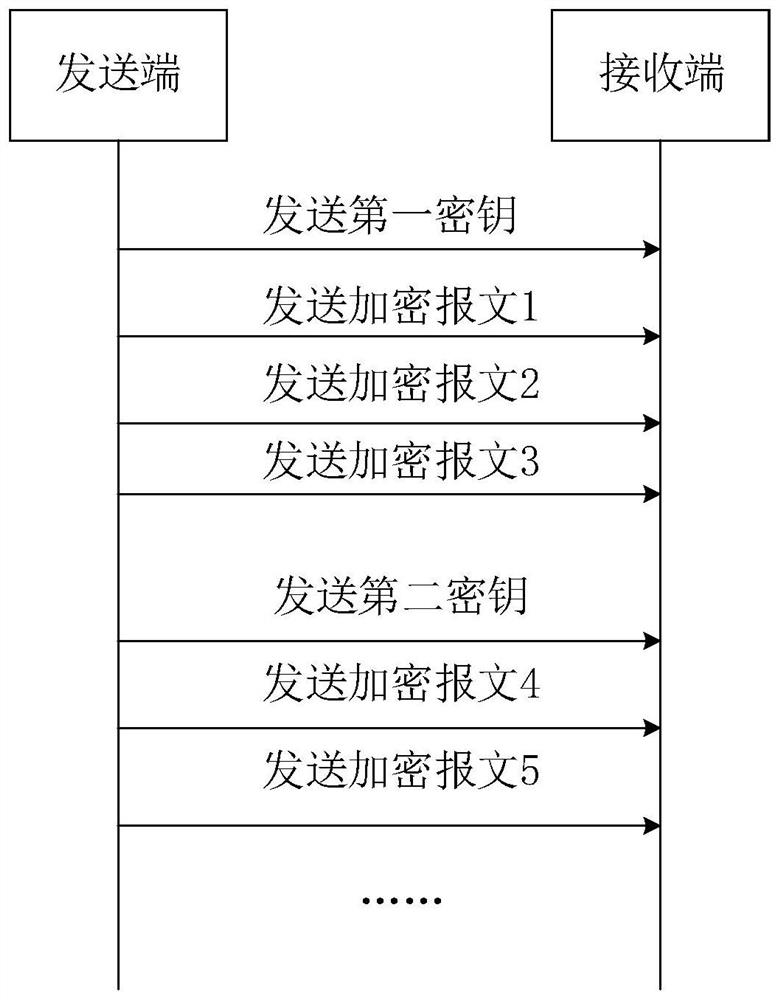
A controller area network bus encryption method, device, equipment and medium
ActiveCN113285956BEncryption is simple and fastImplement encryptionSecuring communicationBus networksArea networkBus encryption
Embodiments of the present invention disclose a method, device, device and medium for encrypting a controller area network bus. The method includes: determining the key of the message to be sent corresponding to the CAN bus of the controller area network, and sending the key to the receiving end through the CAN bus; encrypting the message to be sent according to the key to obtain the encrypted message, The encrypted message is sent to the receiving end through the CAN bus, so that the receiving end decrypts the received encrypted message according to the key. The technical solutions provided by the embodiments of the present invention can simply and quickly implement CAN bus encryption through the interaction between the sending end and the receiving end, without the need to process the messages to be sent corresponding to the CAN bus, reducing network load and processor load. burden.
Owner:CHINA FIRST AUTOMOBILE
Controller local area network bus encryption method, device, equipment and medium
ActiveCN113285956AEncryption is simple and fastImplement encryptionBus networksArea networkBus encryption
The embodiment of the invention discloses a controller local area network bus encryption method and device, equipment and a medium. The method comprises the following steps: determining a key of a message to be sent corresponding to a controller area network (CAN) bus, and sending the key to a receiving end through the CAN bus; and encrypting the message to be sent according to the key to obtain an encrypted message, and sending the encrypted message to the receiving end through the CAN bus, so that the receiving end decrypts the received encrypted message according to the key. According to the technical scheme provided by the embodiment of the invention, through interaction between the sending end and the receiving end, CAN bus encryption can be simply and quickly realized, the to-be-sent message corresponding to the CAN bus does not need to be processed, and the network load and the burden of a processor are reduced.
Owner:CHINA FIRST AUTOMOBILE
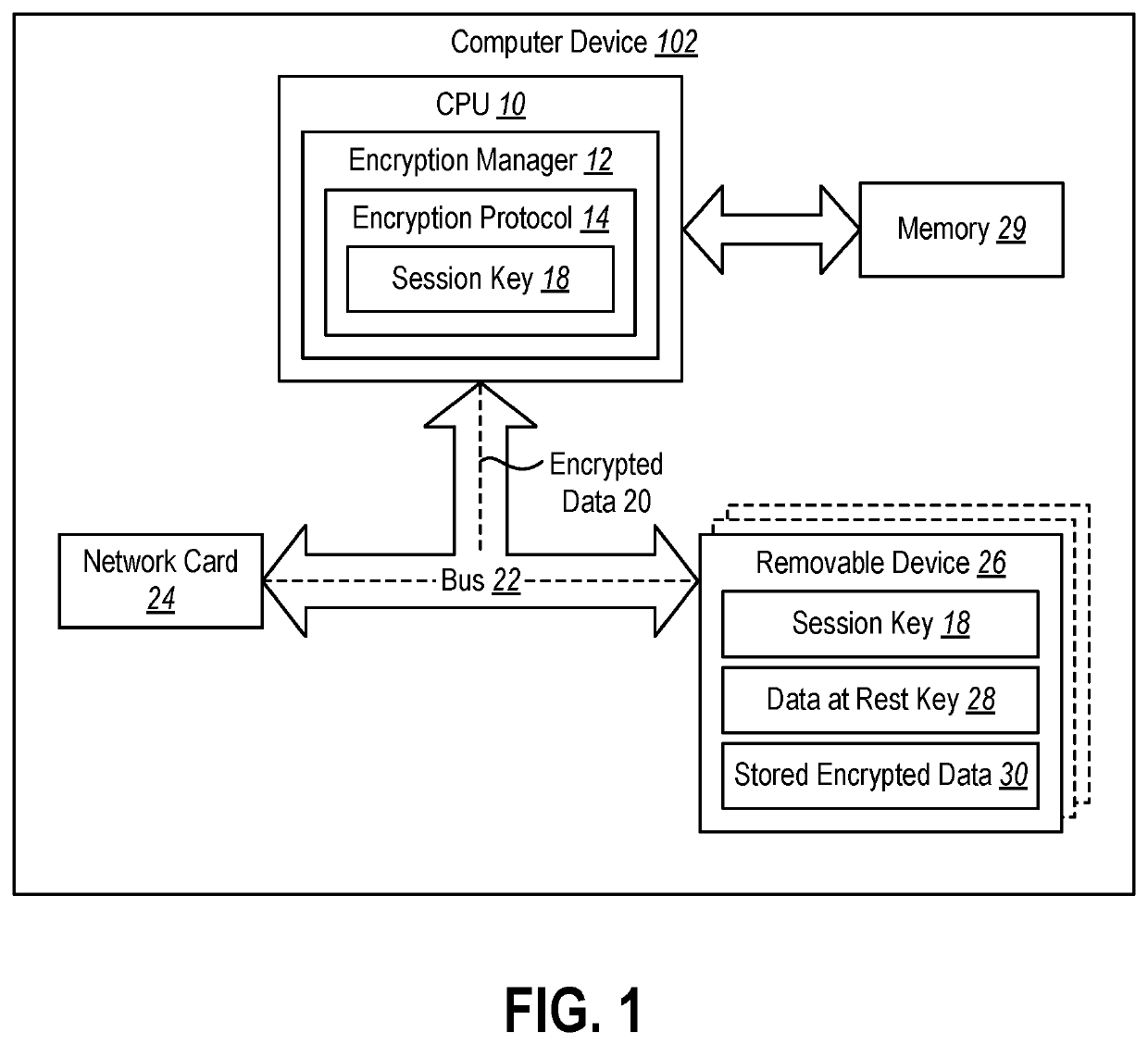
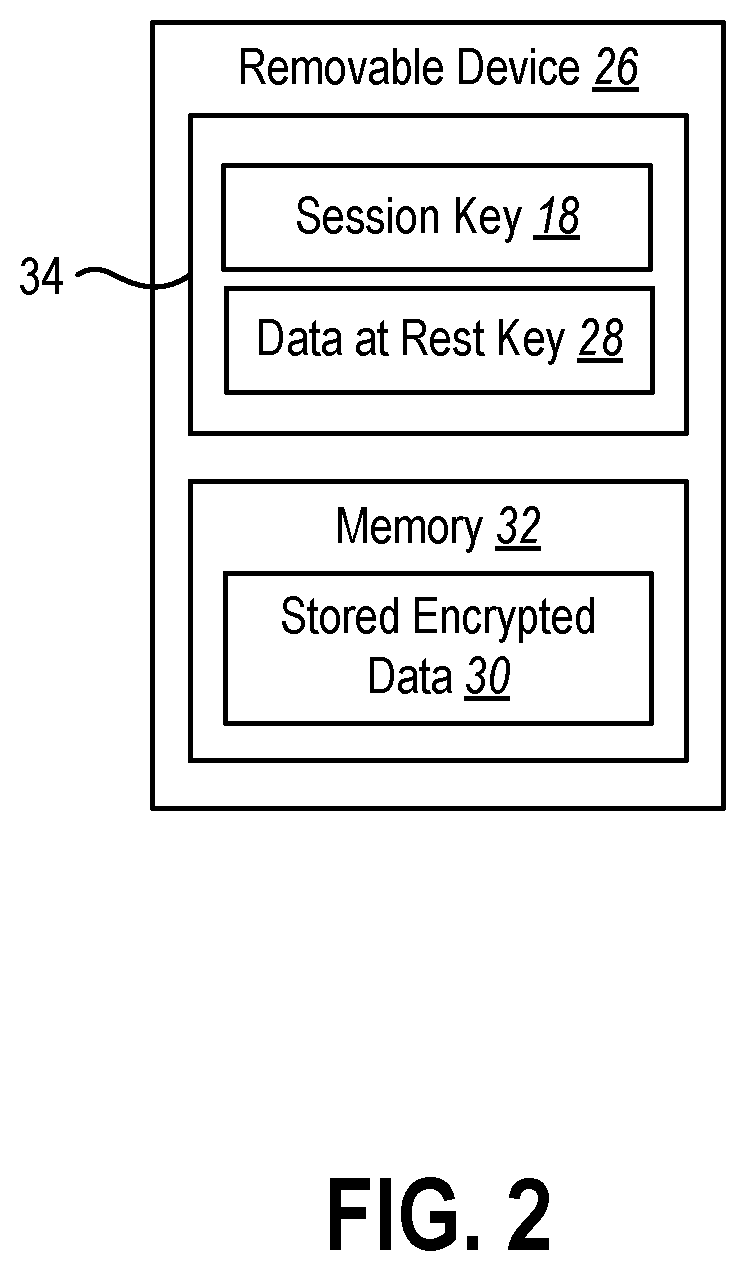
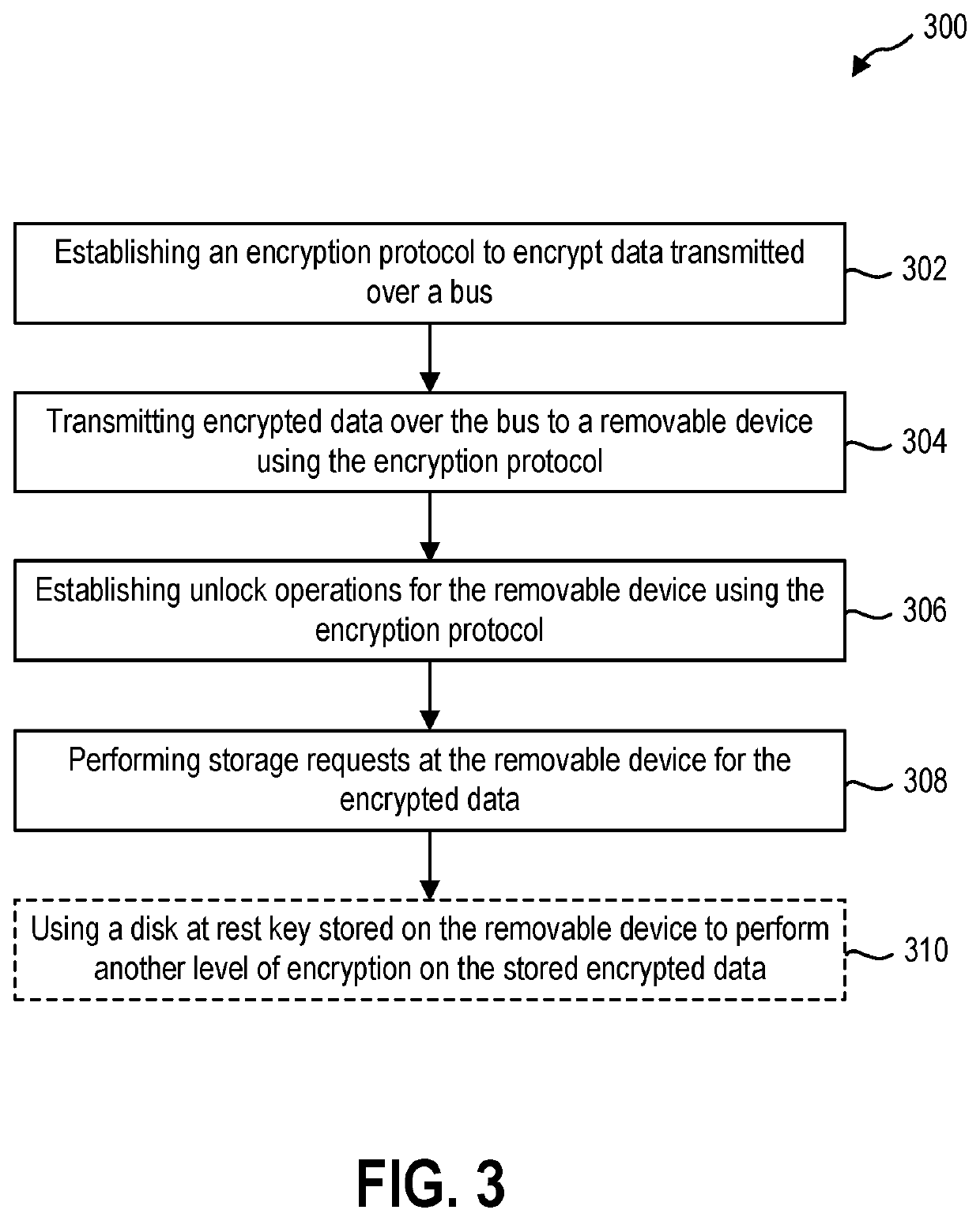
Protecting device detachment with bus encryption
PendingUS20210264064A1Well formedKey distribution for secure communicationMultiple keys/algorithms usageAttackBus encryption
The present disclosure relates to devices and methods for protecting data from physical attacks. The devices and methods may establish an encryption protocol to encrypt data transmitted over a bus to one or more removable devices in communication with a computer device. The devices and methods may use the encryption protocol to communicate with the removal devices and perform storage requests at the removal devices. The devices and methods may also perform another layer of encryption on the data stored at the removal devices using a data at rest key stored on the removal devices.
Owner:MICROSOFT TECH LICENSING LLC
Bus data protection method, device, storage medium and chip
ActiveCN111814212BImprove securityReduce overheadDigital data protectionInternal/peripheral component protectionComputer hardwareBus encryption
The application discloses a bus data protection method, device, storage medium and chip, belonging to the technical field of chip security. The method includes: when the first module is a master module, the second module is a slave module, and the first module performs a write operation to the second module, or, when the first module is a slave module, the second module is a master module, and the second When the second module performs a read operation to the first module, the first module sends the sensitive data to the bus encryption module; the bus encryption module obtains the first random number, and sends the encrypted data obtained by encrypting the sensitive data according to the first random number to the bus; The bus sends the encrypted data to the bus decryption module; the bus decryption module obtains the second random number, and sends the sensitive data obtained by decrypting the encrypted data according to the second random number to the second module, and the second random number is the same as the first random number . The embodiment of the present application can ensure the consistency of random numbers, improve the security and accuracy of data transmission, and reduce the overhead of bus bit width.
Owner:NANJING SEMIDRIVE TECH CO LTD
Enciphered protection and read write control method for computer data
InactiveCN100378689CPrevent leakageAvoid destructionDigital data processing detailsUnauthorized memory use protectionDECIPHERBus encryption
This invention relates to a computer data cipher protection and a read / write control method, which applies a generate method combining a serial bus ciphering dog or software identity certification with the sector stage read / write interception to realize cipher to hard disk data, which utilizes the sector stage read / write interception method to intercept all read / write operations, carries out cipher / decipher conversion in the cipher core under the condition of existing related identity certification to realize the cipher to disk data and read / write control.
Owner:陆峰
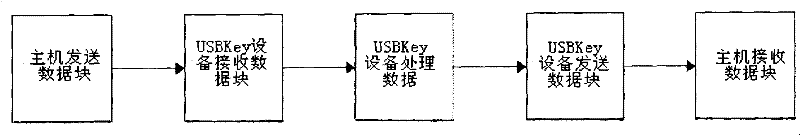
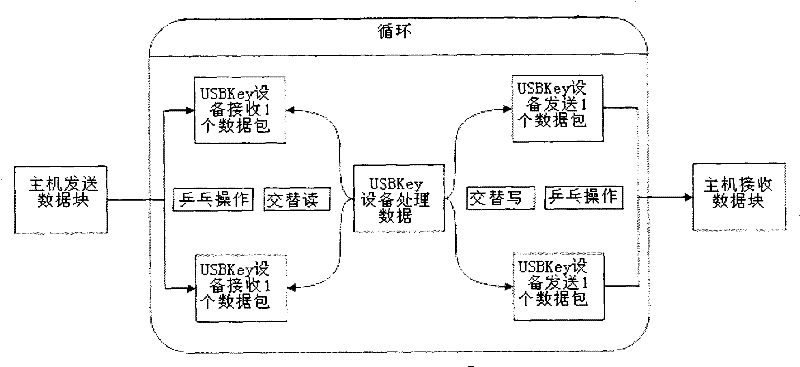
Method for improving throughput of grouping algorithm on general serial bus encryption lock
ActiveCN101655894BFast transmissionEasy to handleDigital data protectionInternal/peripheral component protectionNetwork packetBus encryption
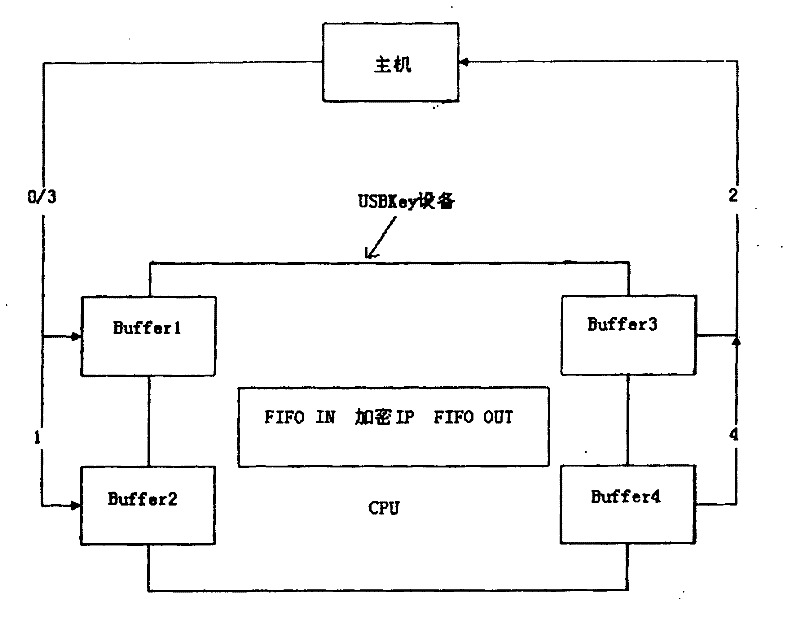
The invention discloses a method for improving throughput of grouping algorithm on a USBKey device, comprising steps of: application program on the host transmitting data block to a device drive program, at same time, the application program requesting to read response data from the device drive program; the device drive program transmitting the data block to the USBKey device, at same time, the device drive program requesting to read the response data; the USBKey device receiving a USB data packet, and sending to an encryption IP to be encrypted, simultaneously receiving a next USB data packet; the USBKey device sending the encrypted USB data pocket into an output buffer area, then sending to the host simultaneously sending another USB data pocket to an encryption IP to be encrypted; thehost receiving encrypted USB data packet, and placing in the device drive program, until data of the data block are completely processed. The invention may effectively improve data transmission speed.
Owner:SHANGHAI HUAHONG INTEGRATED CIRCUIT
Encryption method and device for nonvolatile memory in security chip
PendingCN110795775AGuaranteed removalHigh encryption strengthEncryption apparatus with shift registers/memoriesInternal/peripheral component protectionCiphertextBus encryption
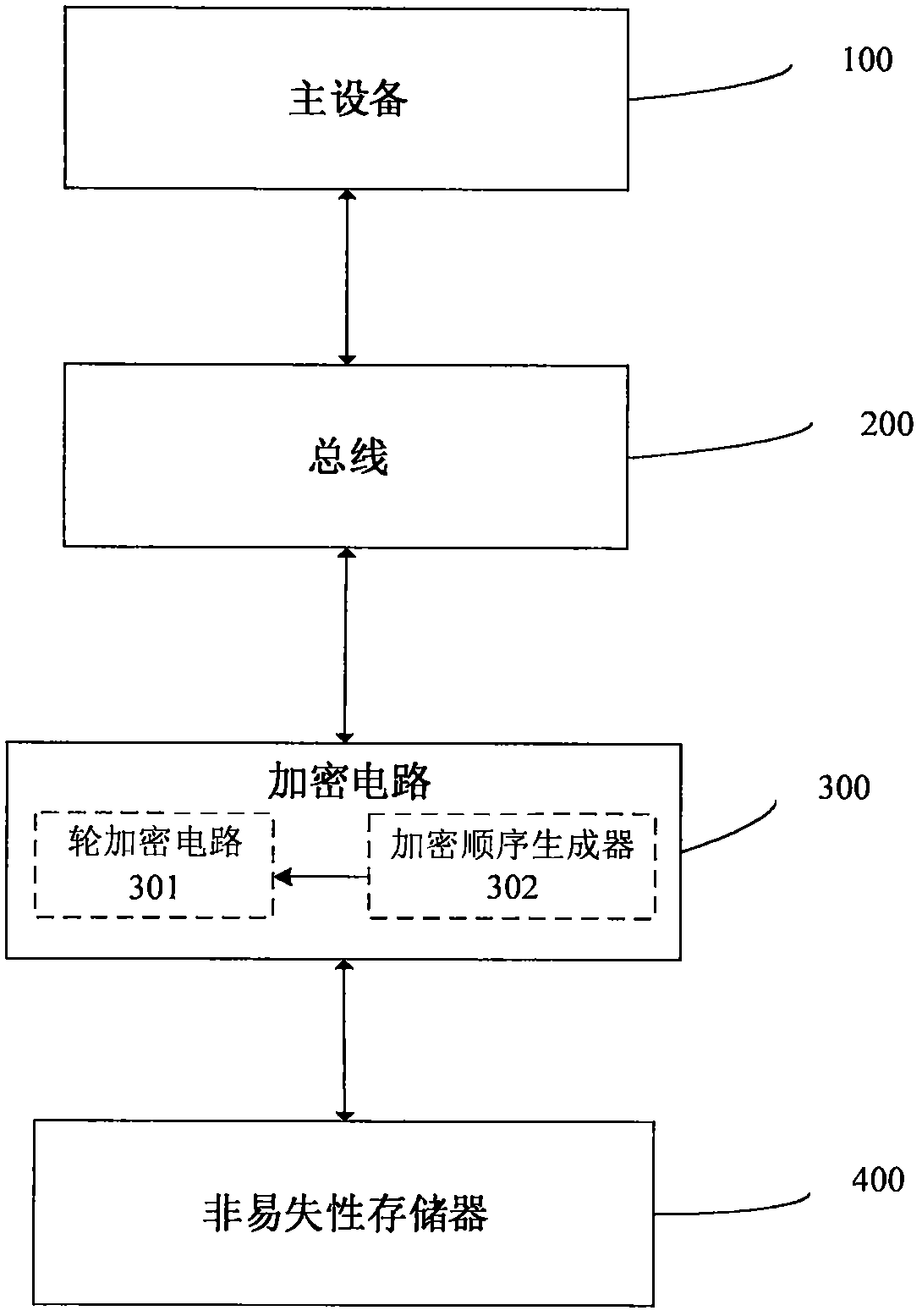
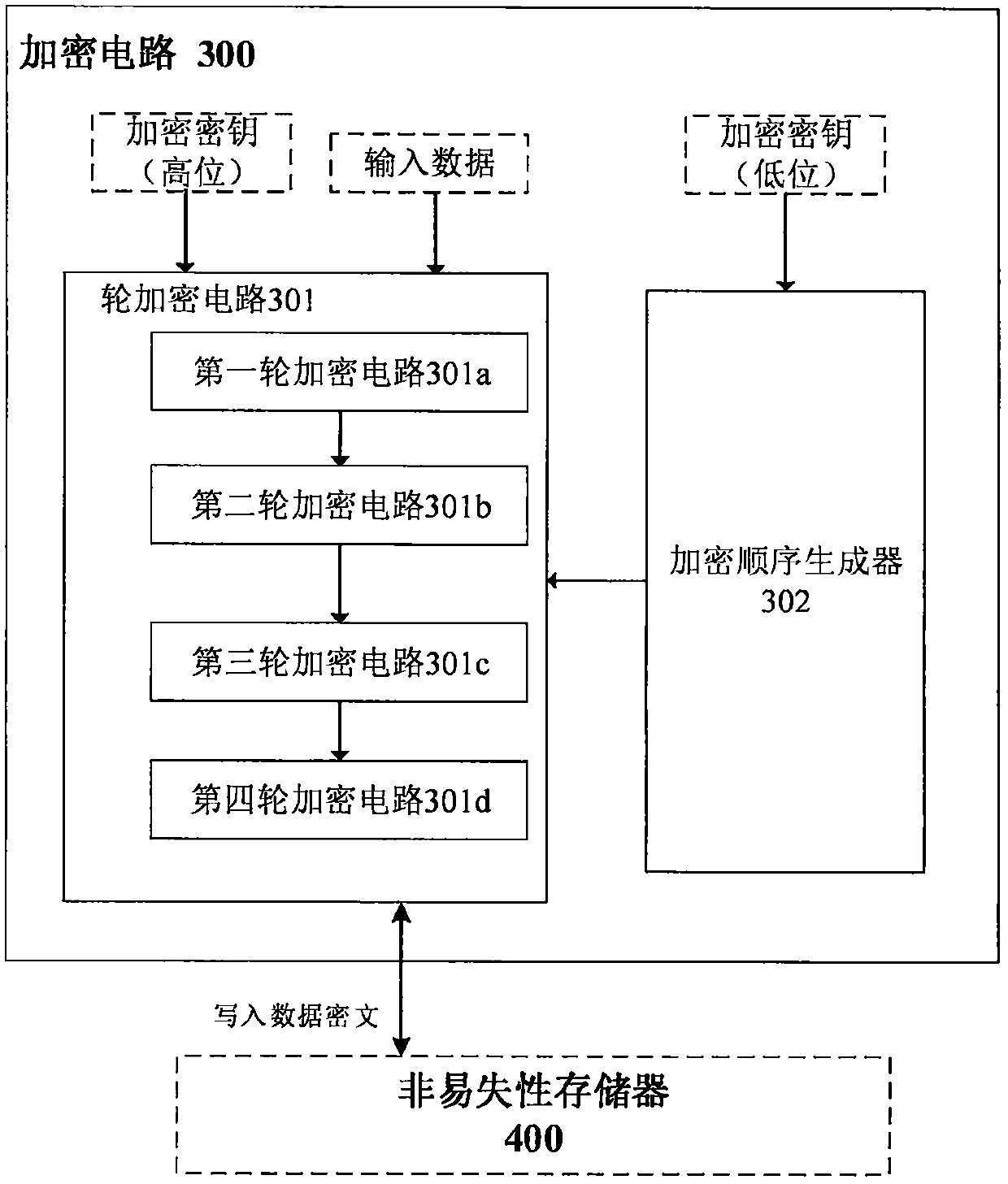
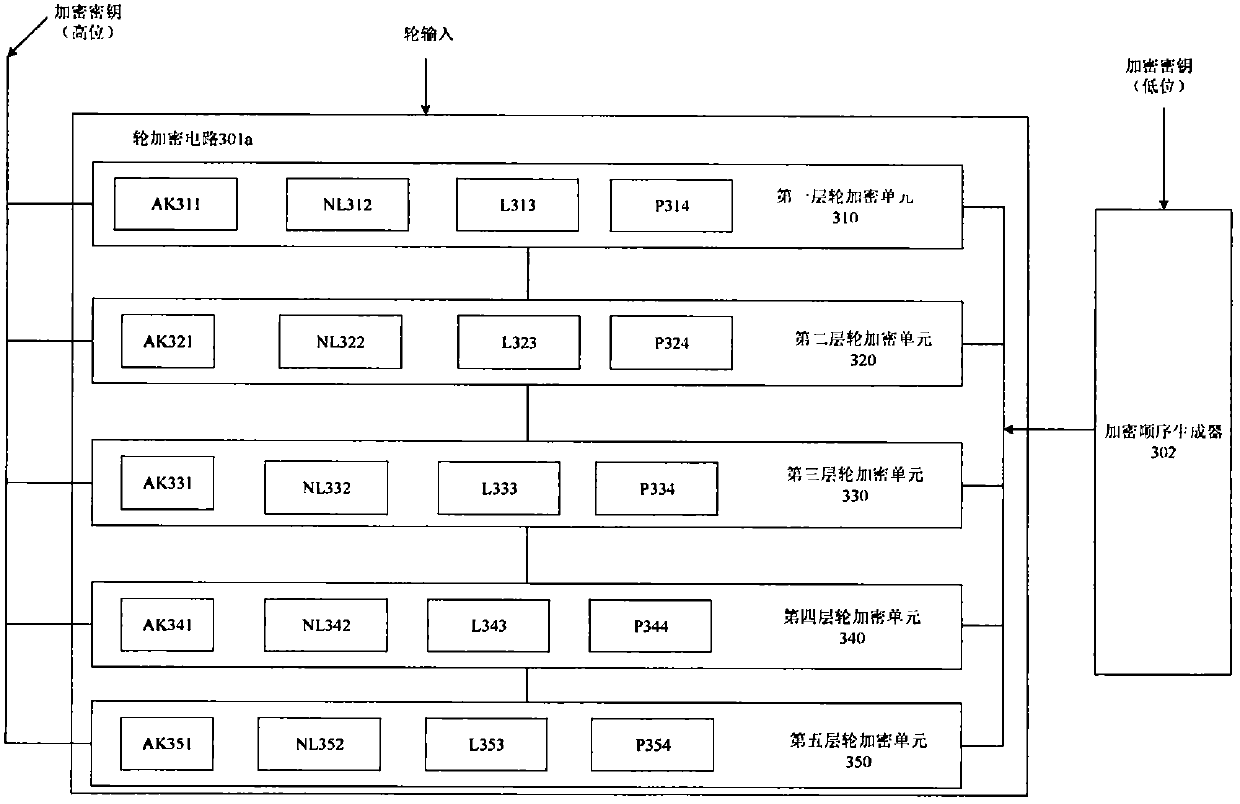
The invention provides an encryption method and device for a nonvolatile memory in a security chip. The encryption device for the nonvolatile memory of the security chip comprises main equipment, a bus, an encryption circuit and a nonvolatile memory, wherein the encryption circuit comprises four round encryption circuits and an encryption sequence generator, each round encryption circuit is divided into five layers of round encryption units, and each layer of round encryption unit comprises a key addition operation unit, a nonlinear operation unit, a linear operation unit and a replacement operation unit; when the round encryption circuit executes encryption, the first round encryption circuit begins to execute encryption, the other round encryption circuits sequentially encrypt in sequence, ciphertext obtained after encryption processing is completed is input into the nonvolatile memory, and the encryption process is completed. According to the method, a 2-4 rounds of symmetric algorithm structure is utilized, and the encryption strength and speed are improved within a small round number; meanwhile, the encryption method comprises a nonlinear mask transformation method, and it isguaranteed that no plaintext exists in the whole data migration process.
Owner:BEIJING TONGFANG MICROELECTRONICS
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com