Data Bus Encryption Method Based on XOR Address
A bus encryption and data bus technology, applied in the field of data bus encryption based on address XOR, can solve the problem of inability to change the value of plaintext data, and achieve the effect of fast computing time, increasing difficulty, and resisting physical attacks
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
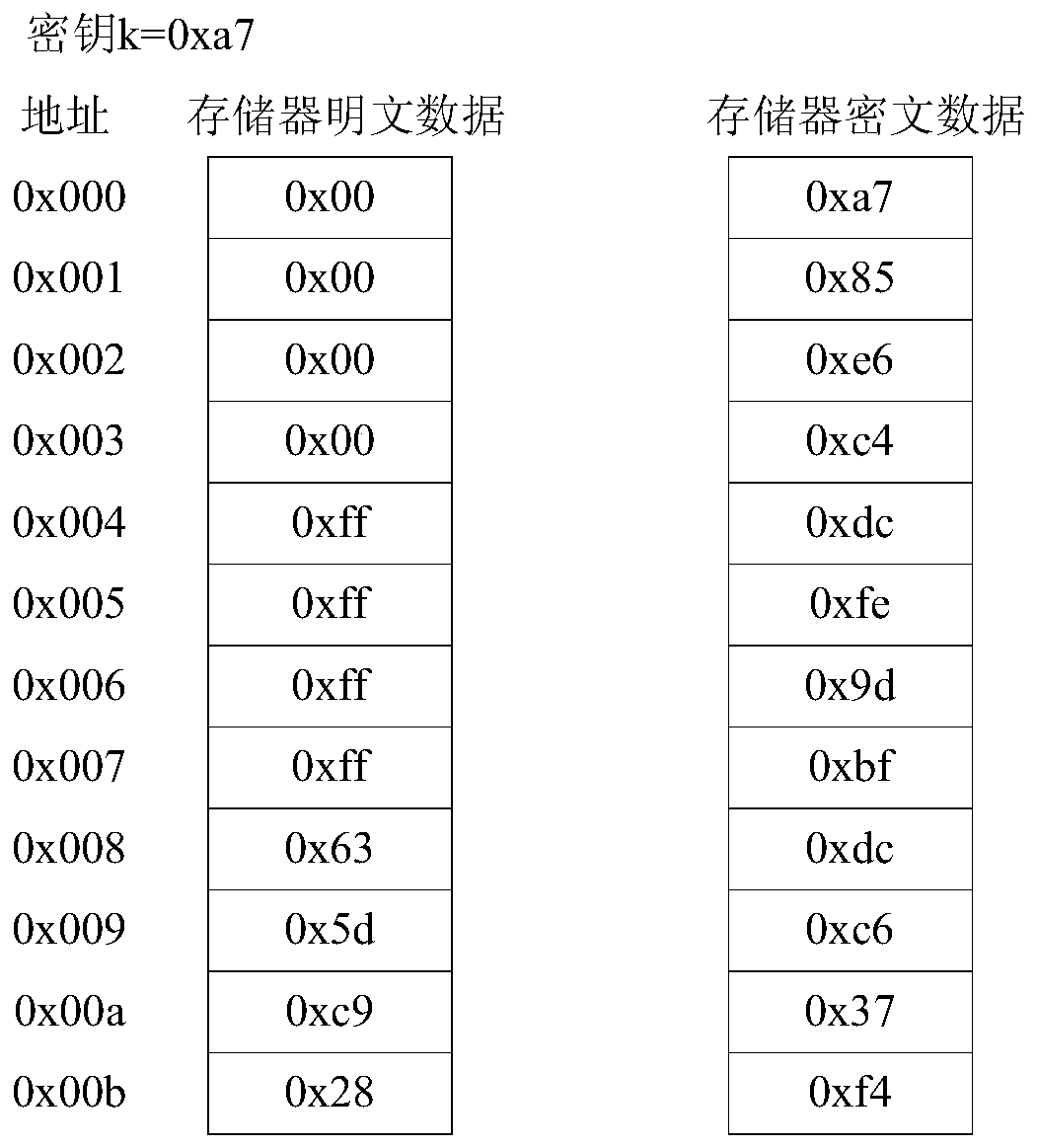
[0017] The data bus encryption method based on the XOR of the address is to make it difficult for an attacker to calculate the key by analyzing the ciphertext data in the memory so as to recover the plaintext. Each bit of the XOR key corresponding to the memory data is obtained by performing an XOR operation on a corresponding bit of the bus encryption key and a certain bit or bits of the memory address bus. Therefore, the XOR bus encryption keys corresponding to the data in different memory addresses are all different. Even if the plaintext data in different addresses are consistent, the ciphertext addresses obtained after the bus encryption operation are also different. This greatly increases the difficulty for an attacker to infer the correlation of plaintext data by observing the correlation of ciphertext data. In addition, even if the plaintext data happens to be "all 0" or "all 1", what is exposed to the attacker is only the bus encryption key XORed with the address. W...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com