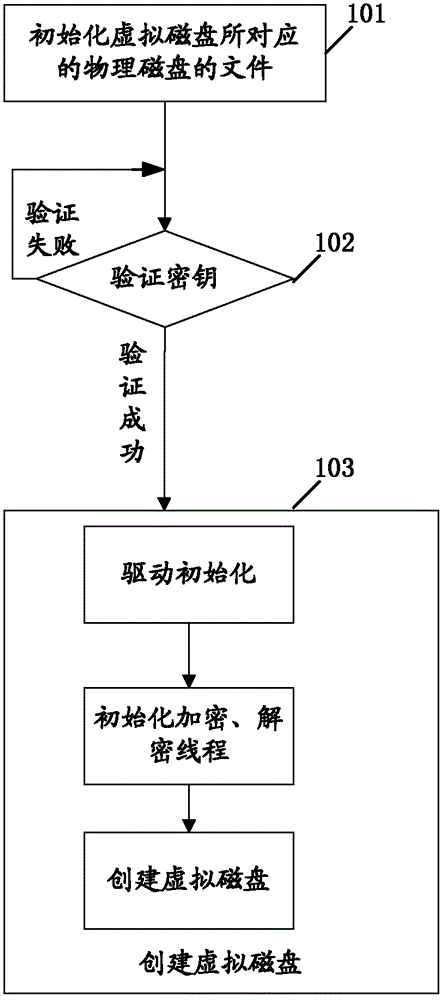
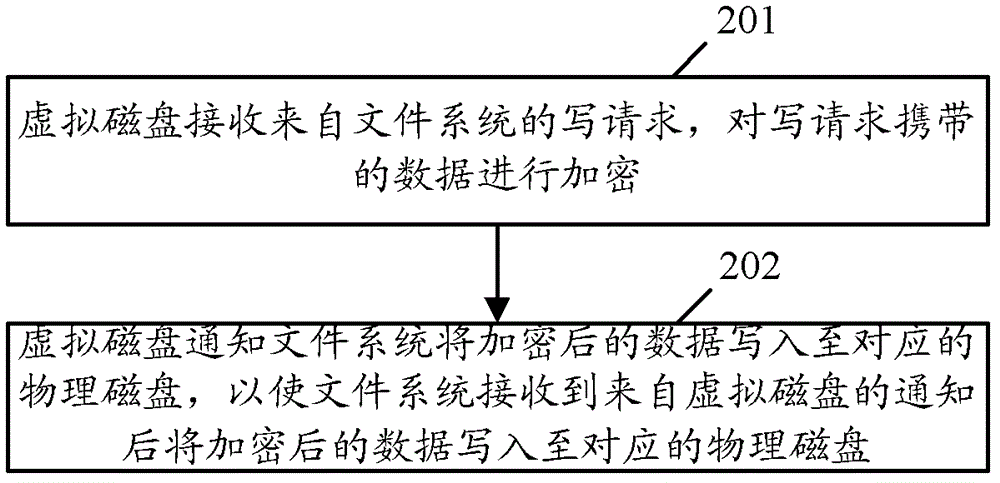
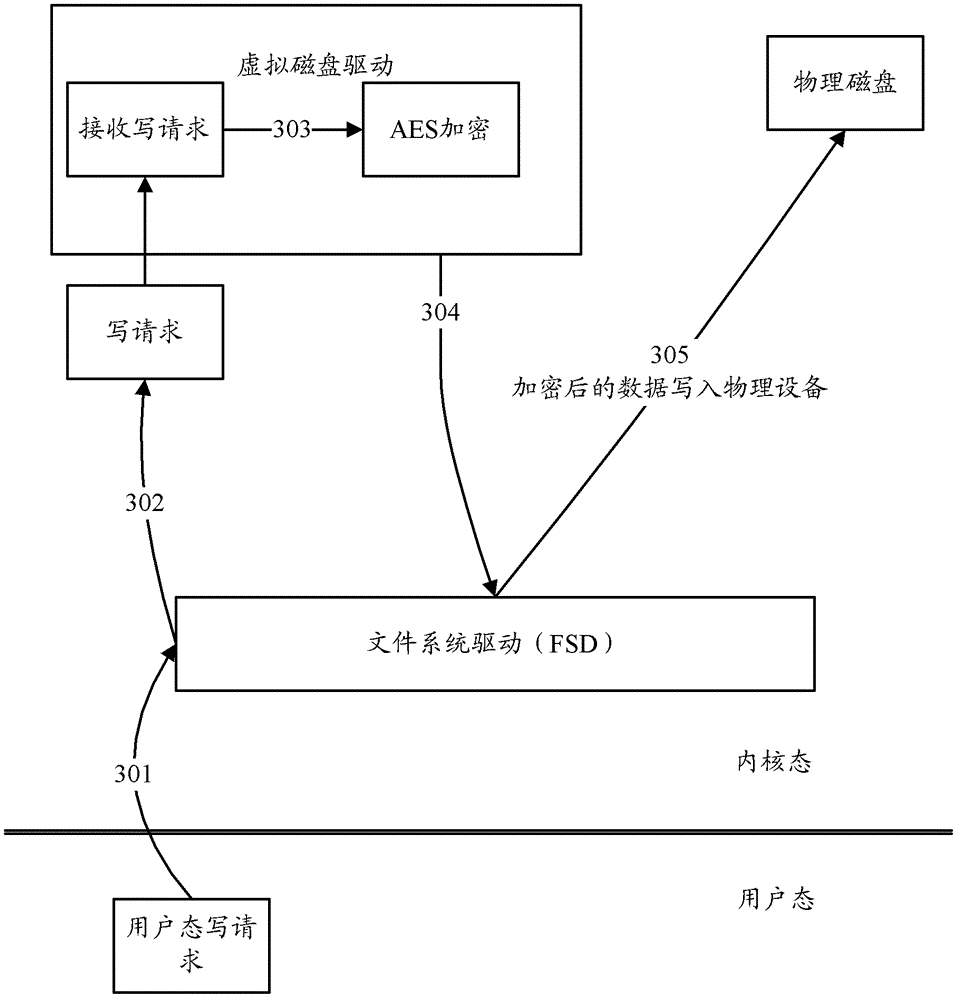
Patents
Literature
34results about How to "Encryption is valid" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
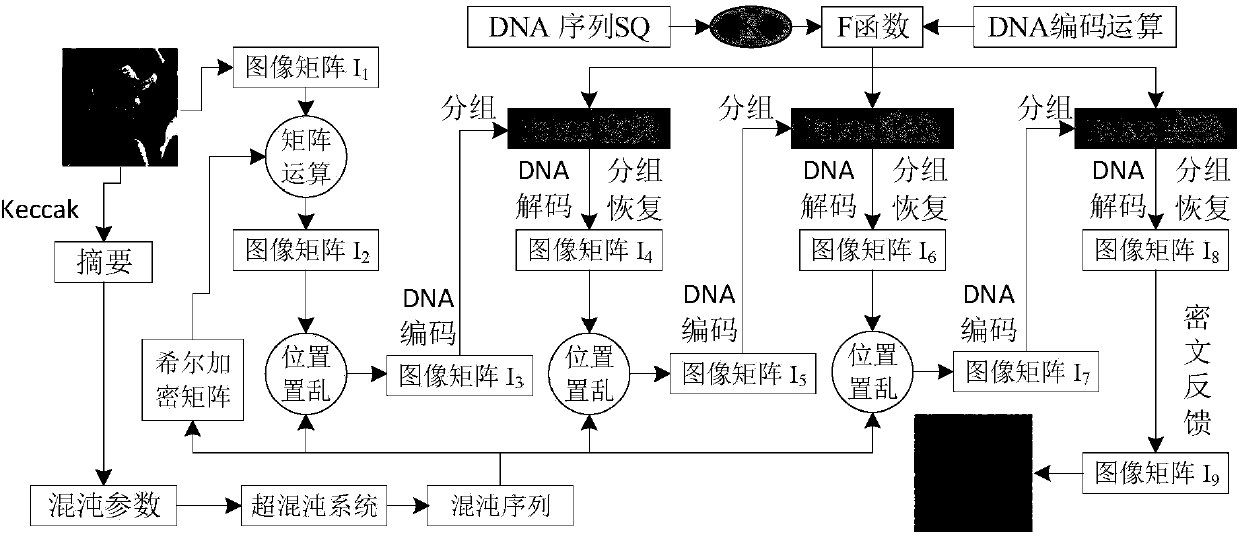
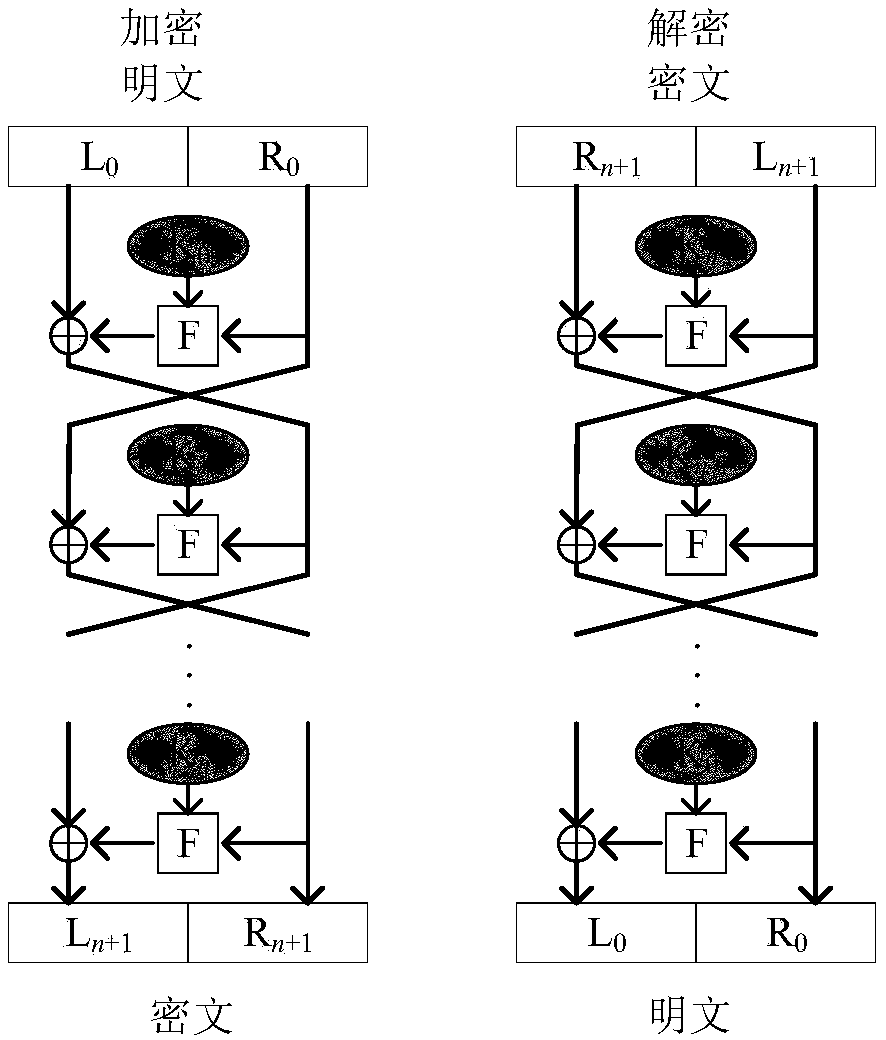
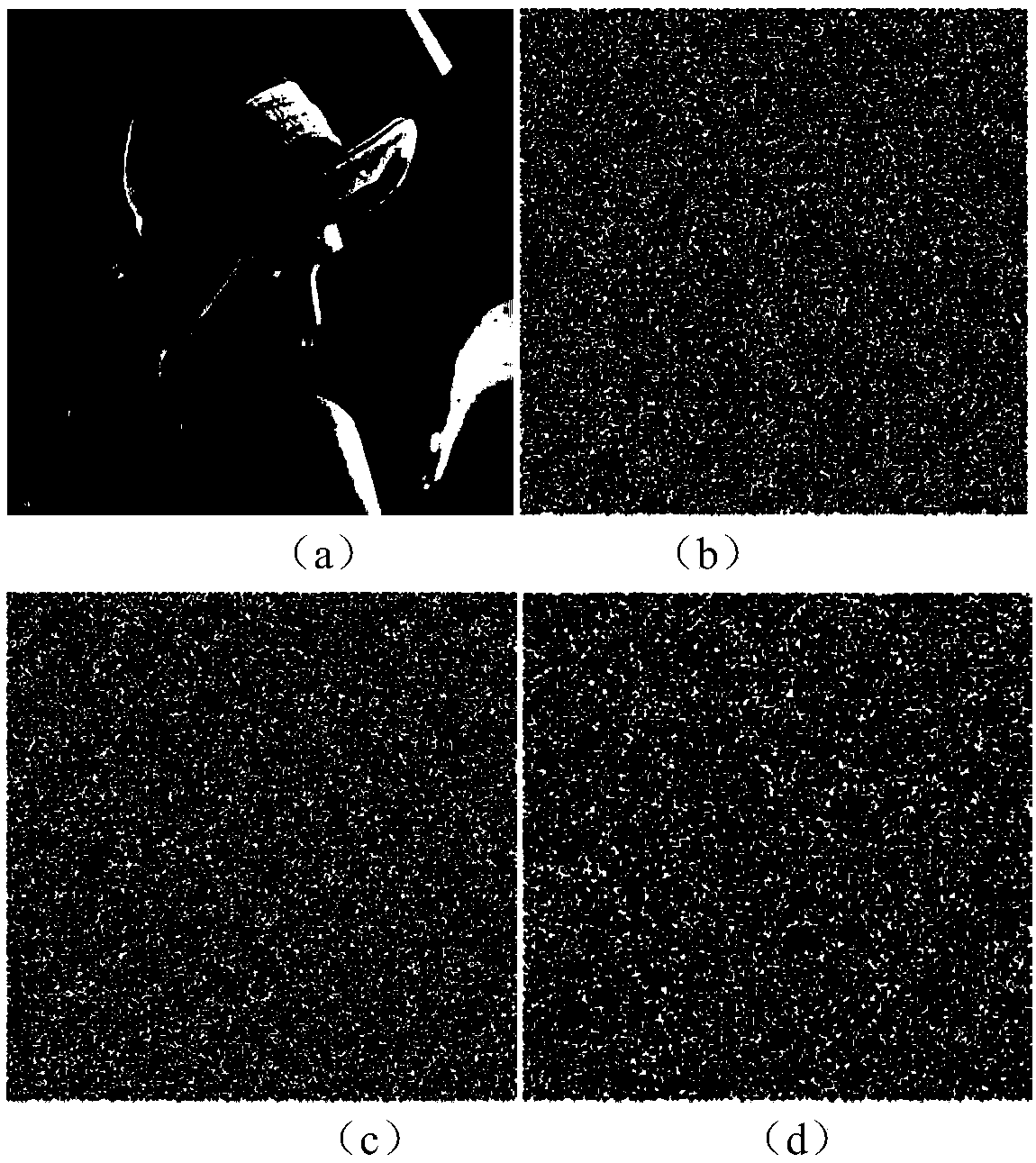
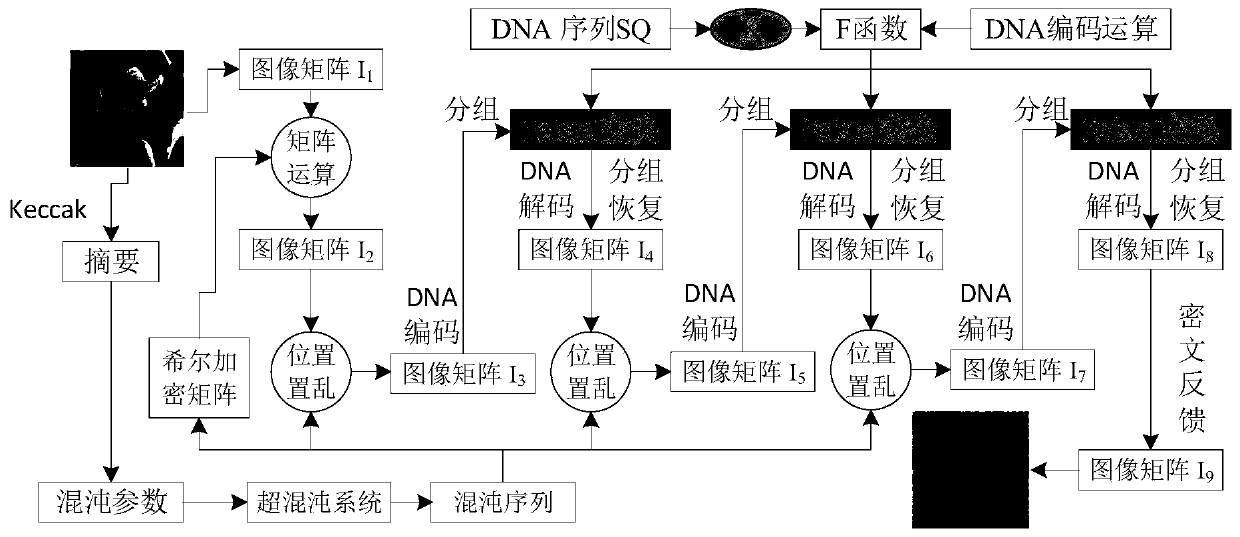
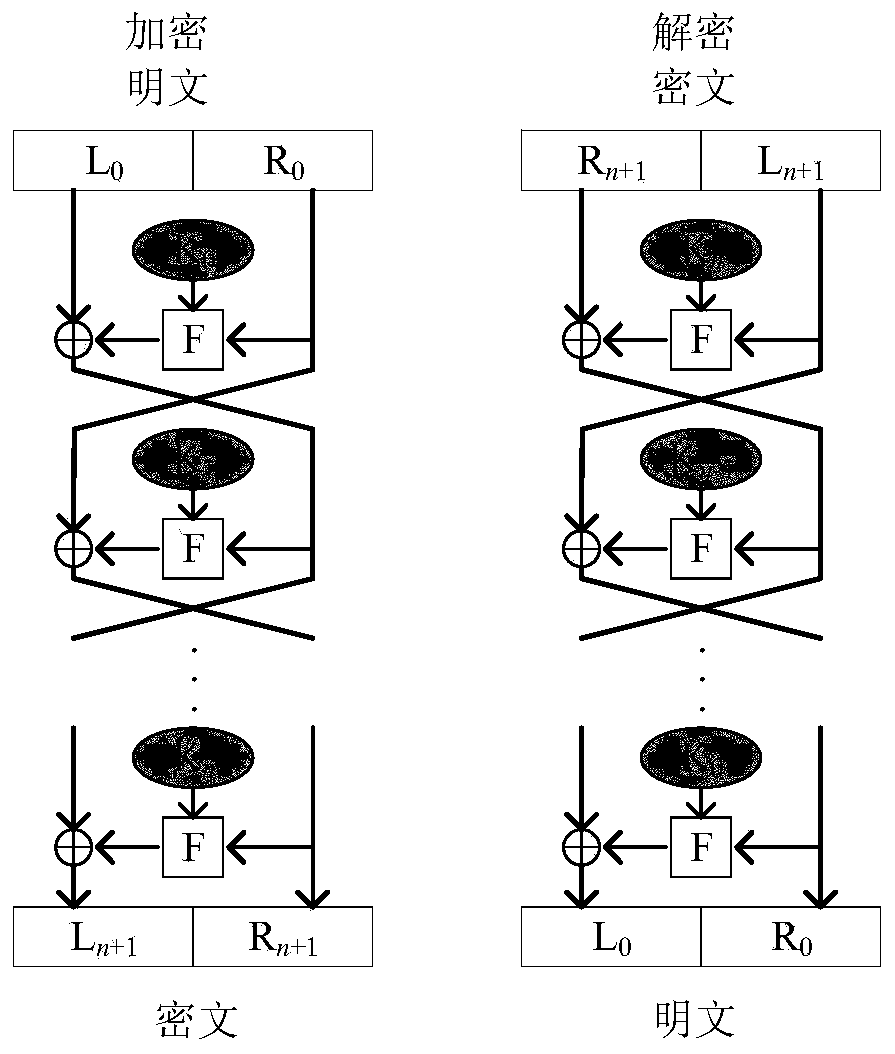
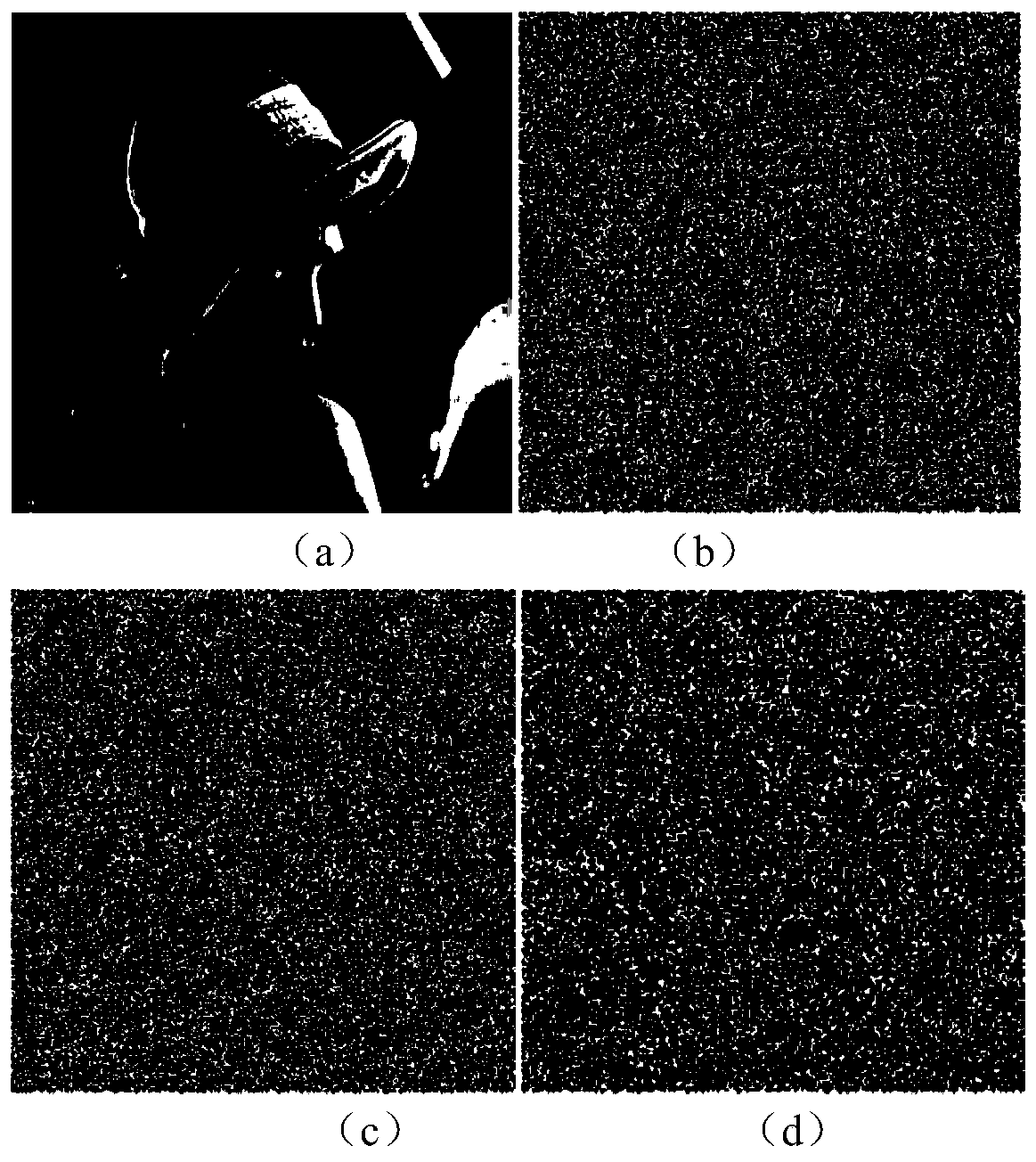
Image encryption method based on Feistel network and dynamic DNA encoding
ActiveCN108365947AStrong randomnessStrong resistance to attackKey distribution for secure communicationSecuring communication by chaotic signalsPlaintextCiphertext
The invention provides an image encryption method based on a Feistel network and dynamic DNA encoding. The method comprises the following steps: computing a Hash value of an original plaintext image by using a Keccak algorithm, and taking the Hash value as an initial value of a hyper-chaotic Chen system, generating a Hill encryption matrix by using a chaotic sequence generated by the hyper-chaoticChen system so as to replace pixels of an original image; realizing image pixel value diffusion by using the DNA encoding operation as a F function of the Feistel network, and a DNA sequence base asa key of the Feistel network; and performing further diffusion through ciphertext feedback. Through three turns of chaotic scrambling-DNA encoding-Feistel conversion-DNA decoding, the ciphertext randomness and attack resistance are stronger, the scrambling conversion of the image pixel location and the diffusion of the pixel value are realized, and the encryption turn is reduced due to repeated scrambling and DNA encoding and decoding. Through the image encryption method provided by the invention, the image can be effectively encrypted, the plaintext sensitivity is strong, the plaintext attack, the differential attack and the statistical attack can be effectively resisted
Owner:ZHENGZHOU UNIVERSITY OF LIGHT INDUSTRY
Image encryption method and device
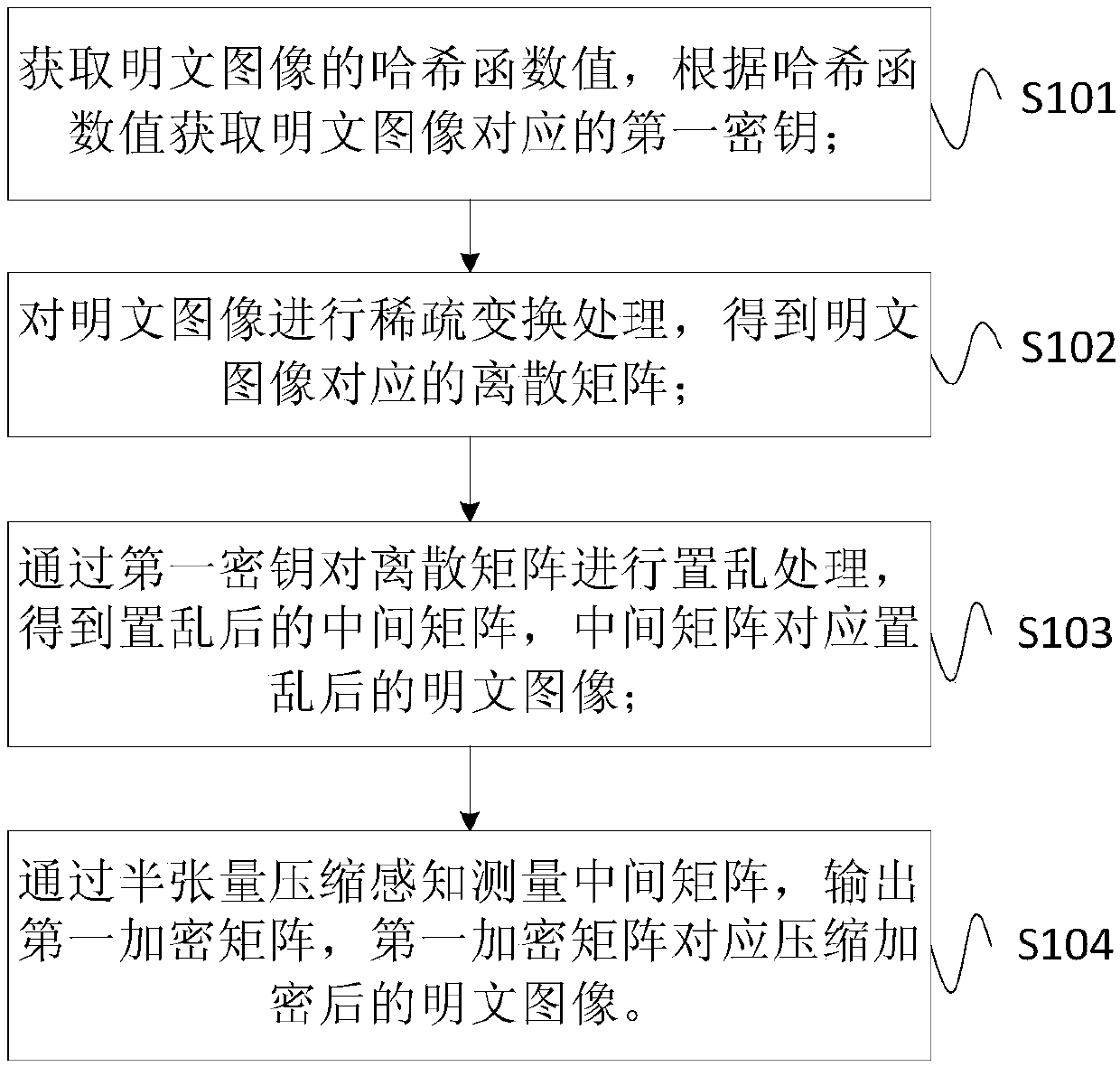
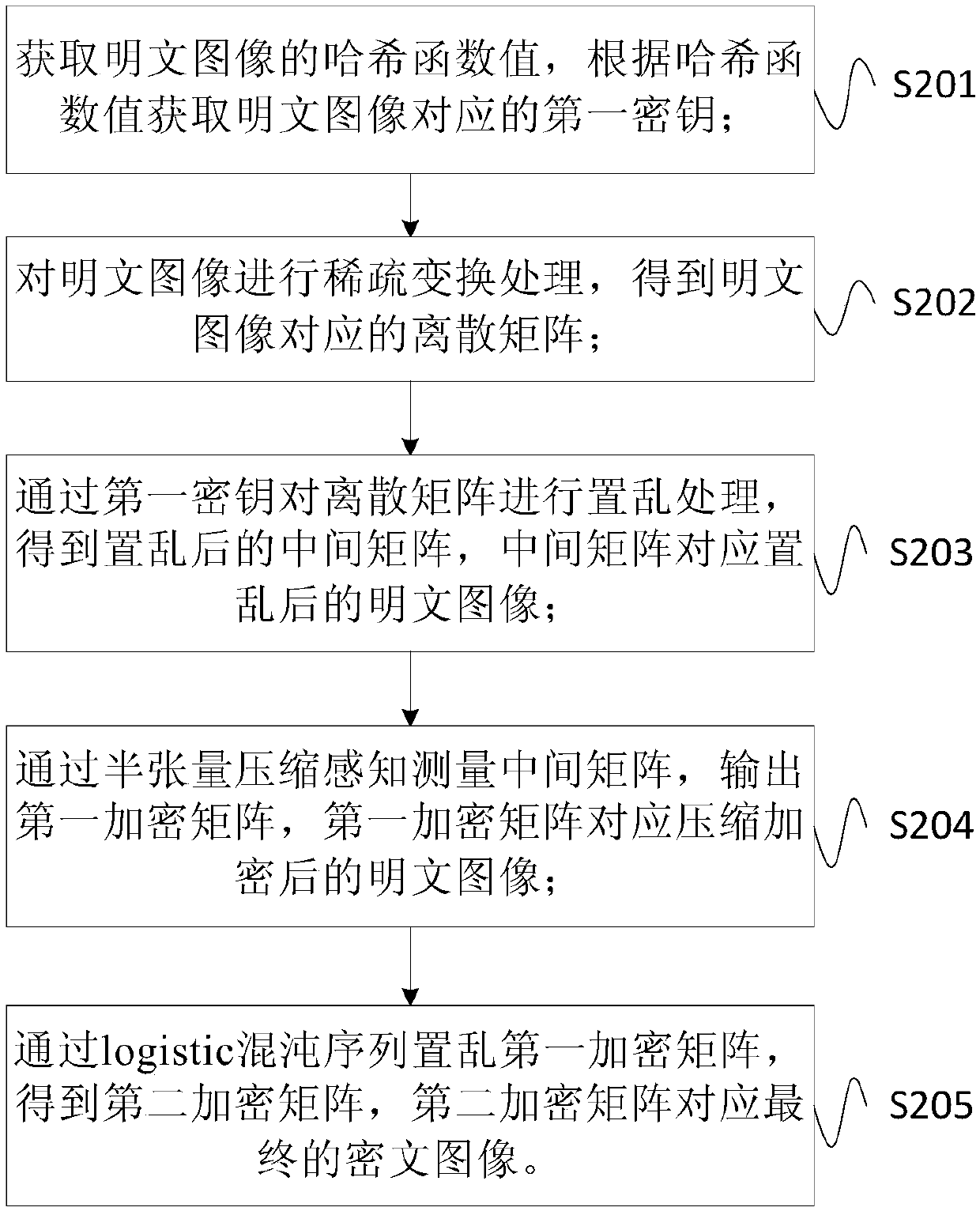
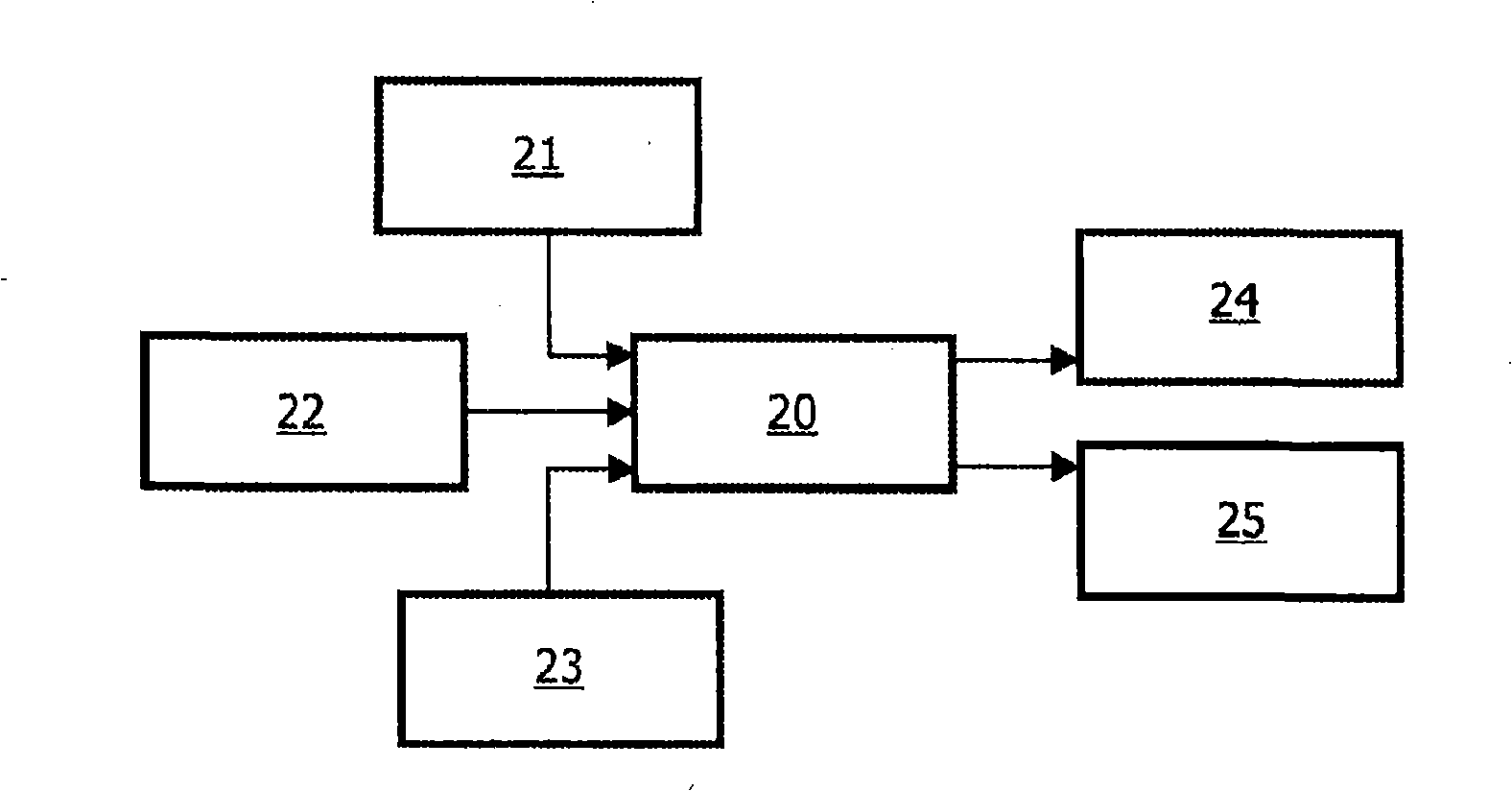
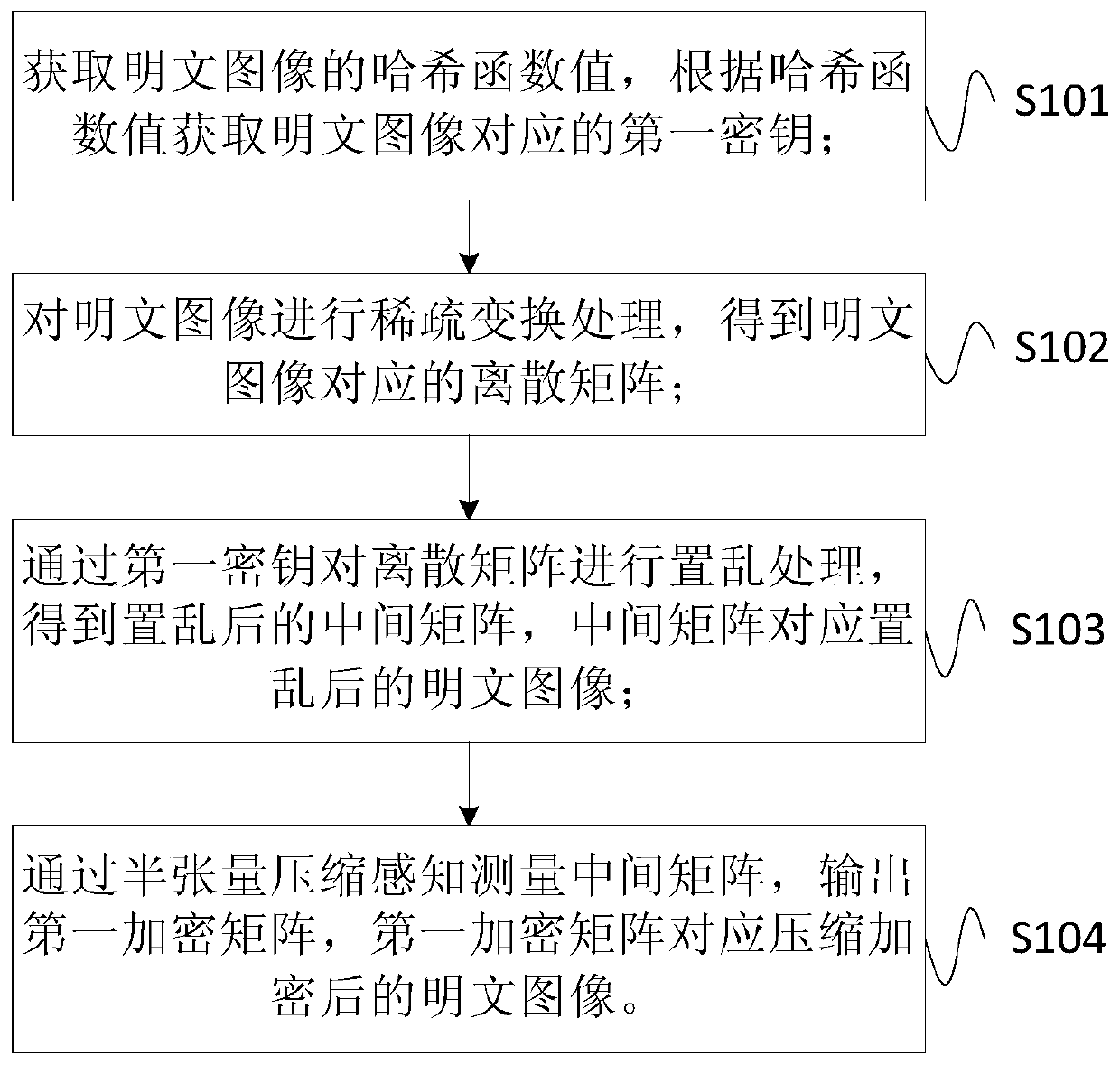
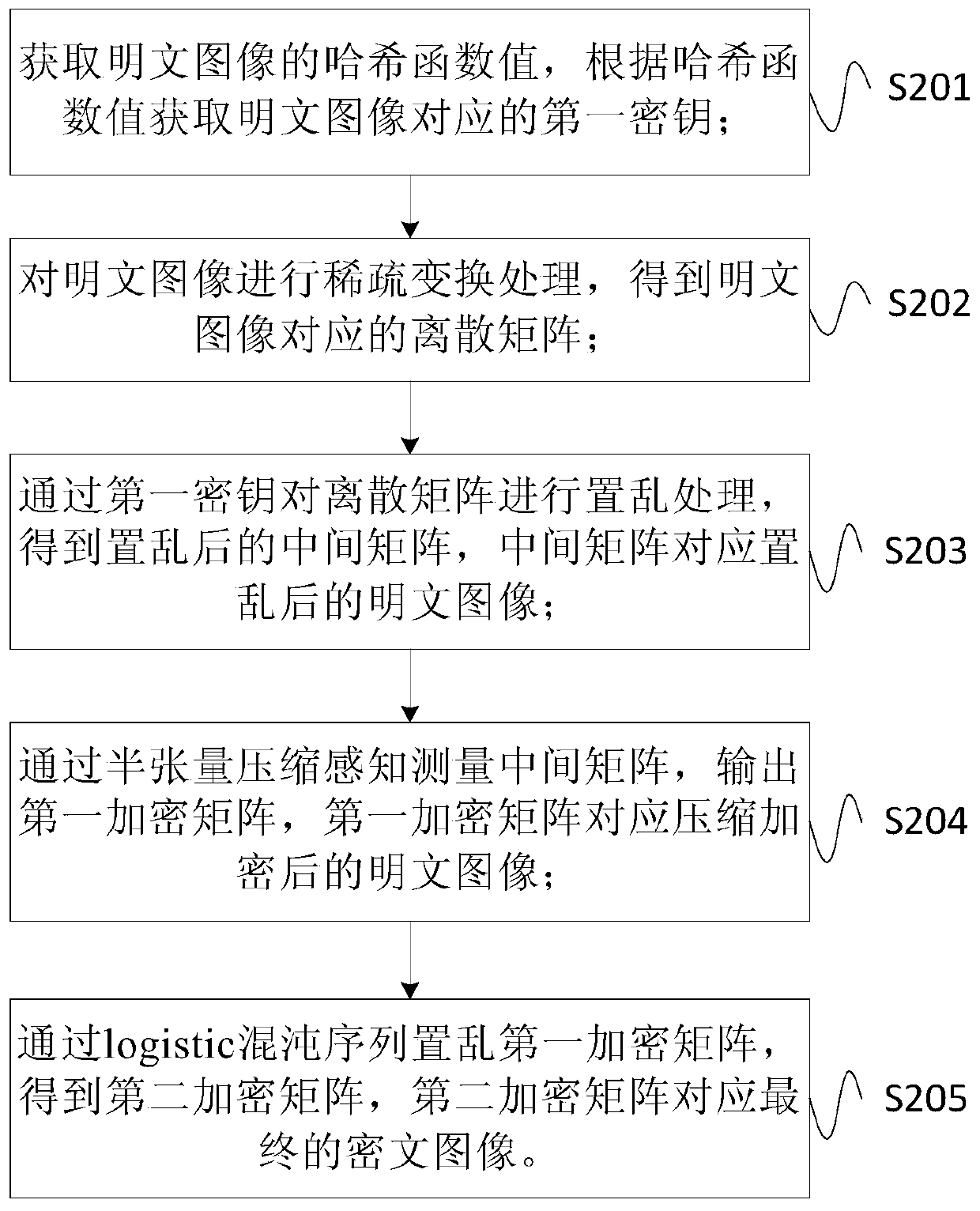
ActiveCN107770405AEncryption is validImplement compression processingEncryption apparatus with shift registers/memoriesSecuring communication by chaotic signalsPlaintextHash function
The invention provides an image encryption method and device. The method comprises the following steps: acquiring a Hash function value of a plaintext image, and acquiring a first key corresponding tothe plaintext image according to the Hash function value; performing sparse transformation processing on the plaintext image to obtain a discrete matrix corresponding to the plaintext image; performing scrambling processing on the discrete matrix through the first key to obtain a scrambled intermediate matrix, wherein the intermediate matrix corresponds to the scrambled plaintext image; and measuring the intermediate matrix by means of half-tensor compressed sensing, and outputting a first encrypted matrix, wherein the first encrypted matrix corresponds to the compressed and encrypted plaintext image. Through adoption of the method provided by the invention, the storage and transmission amounts of image data during transmission are reduced effectively.
Owner:BEIJING UNIV OF POSTS & TELECOMM
Internet of ships intelligent shore-based interaction device based on Beidou
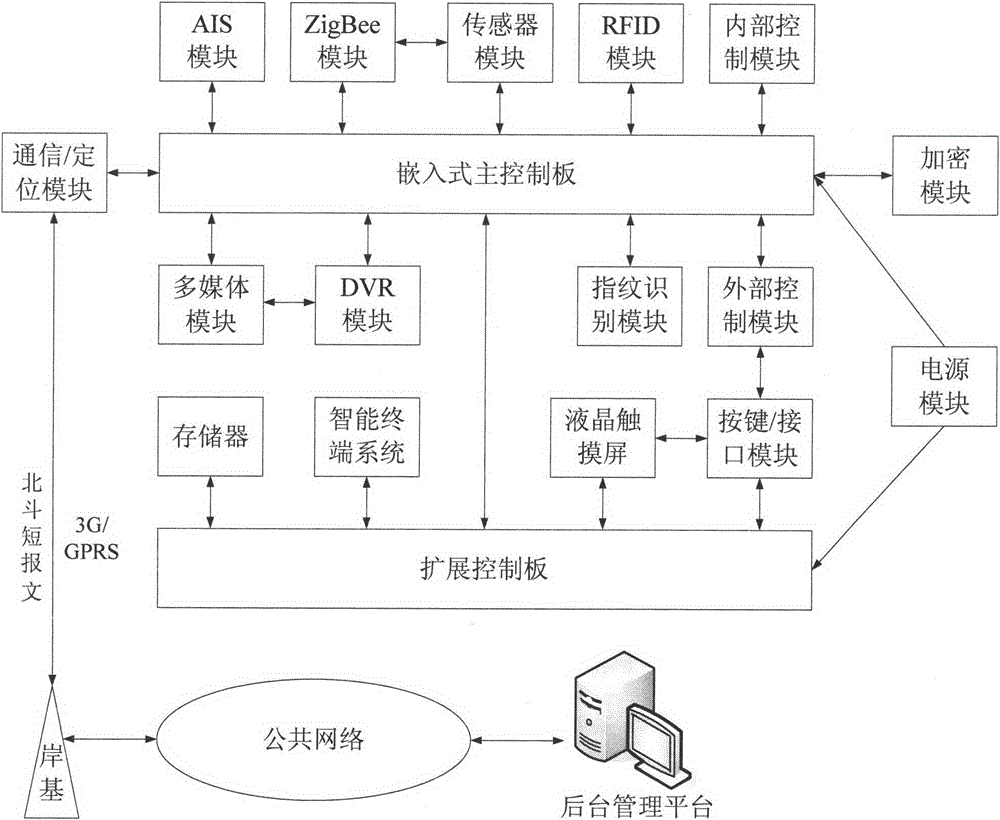
ActiveCN104933897ASimple internal structureLow failure rateTransmission systemsMarine craft traffic controlThe InternetInteraction device
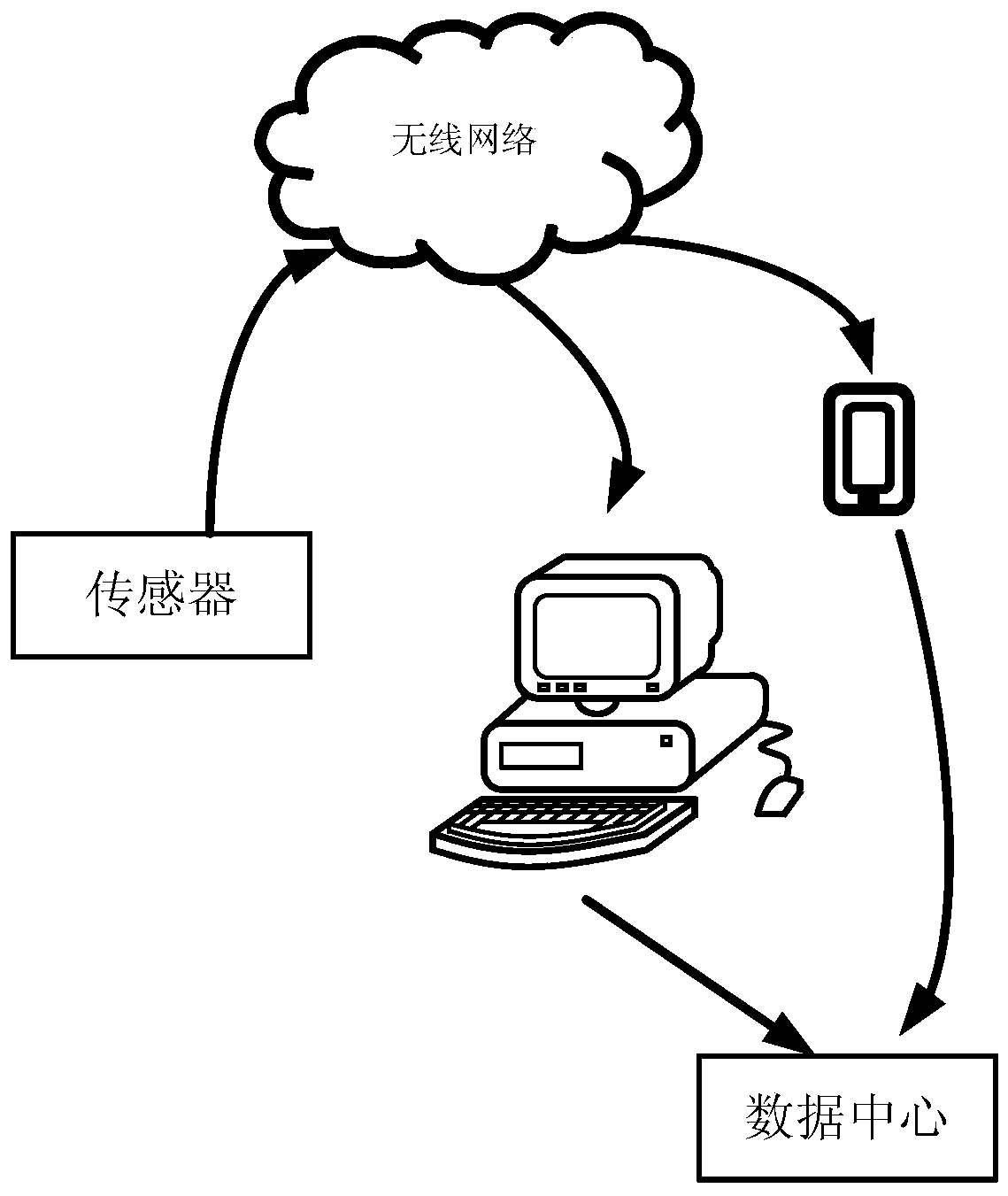
The invention discloses an Internet of ships intelligent shore-based interaction device based on Beidou, and the device comprises an embedded-type main control board, an extended control board, a communication / positioning module, an AIS module, a ZigBee module, a sensor module, an RFID module, an internal control module, an encryption module, a power module, an external control module, a fingerprint recognition module, a DVR module, a multimedia module, a storage unit, an intelligent terminal system, a liquid crystal touch screen, and an interface module. The embedded-type main control board is connected with the extended control board. The power module is connected with the main control board and the extended control board. The communication / positioning module achieves interaction with shore-based equipment through a Beidou message or a 3G / GPRS signal. The device employs the technology of multimode positioning, the technology of sensing, the technology of wireless networking communication and the technology of safety encryption, achieves a function of inland river gate report, a function of visualized emergency command scheduling and a function of shipping electronic business, and prompts the building and development of inland river Internet of ships.
Owner:林兴志
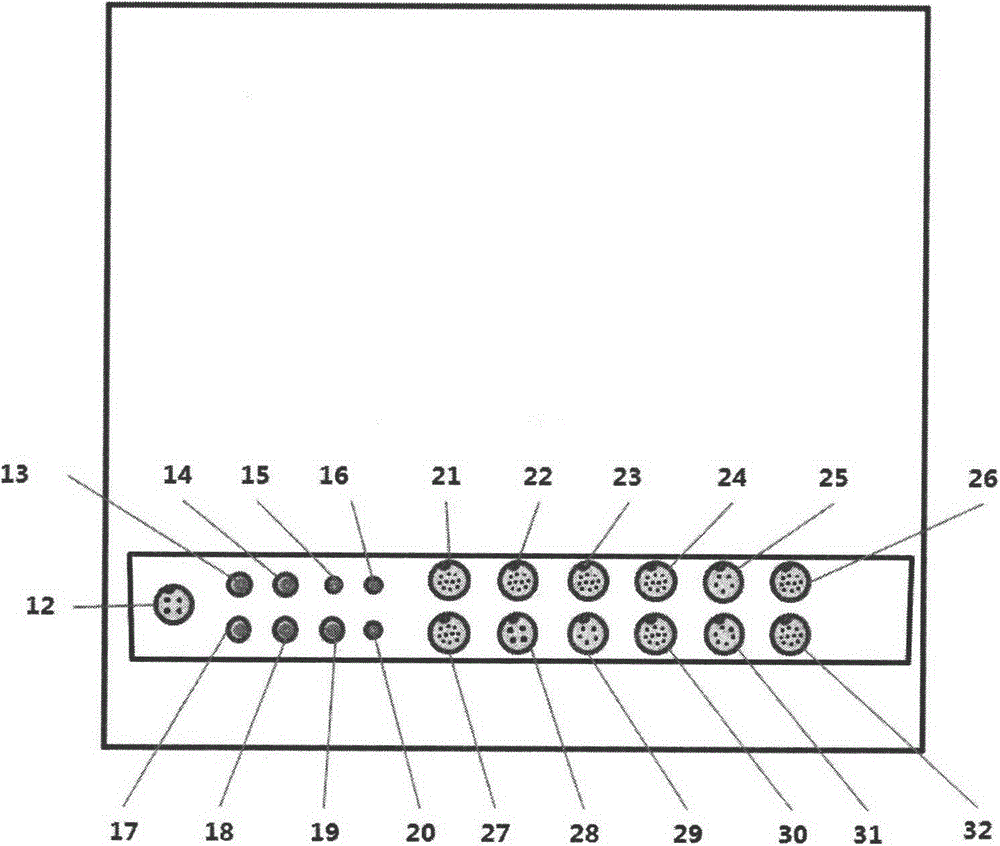
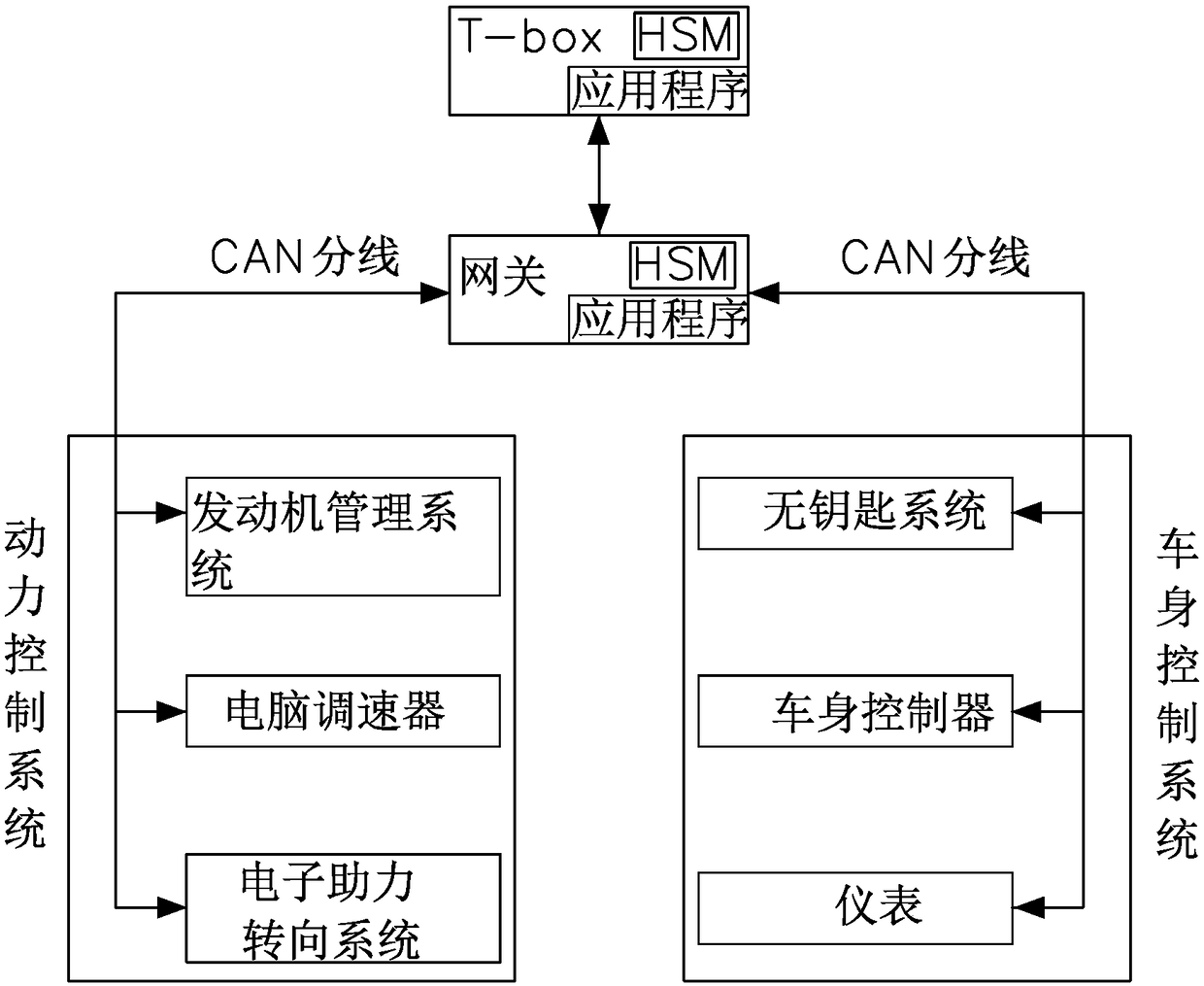
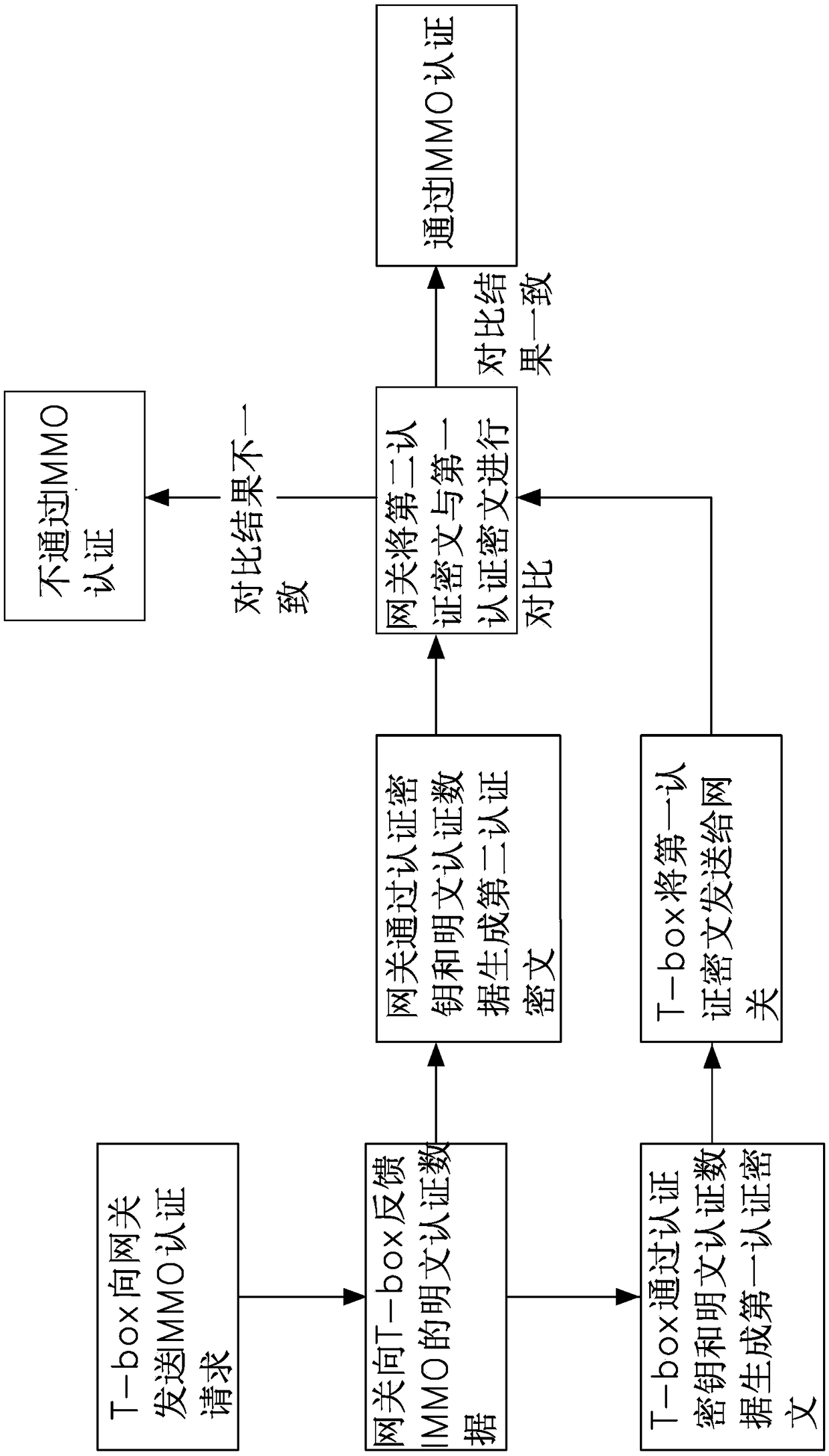
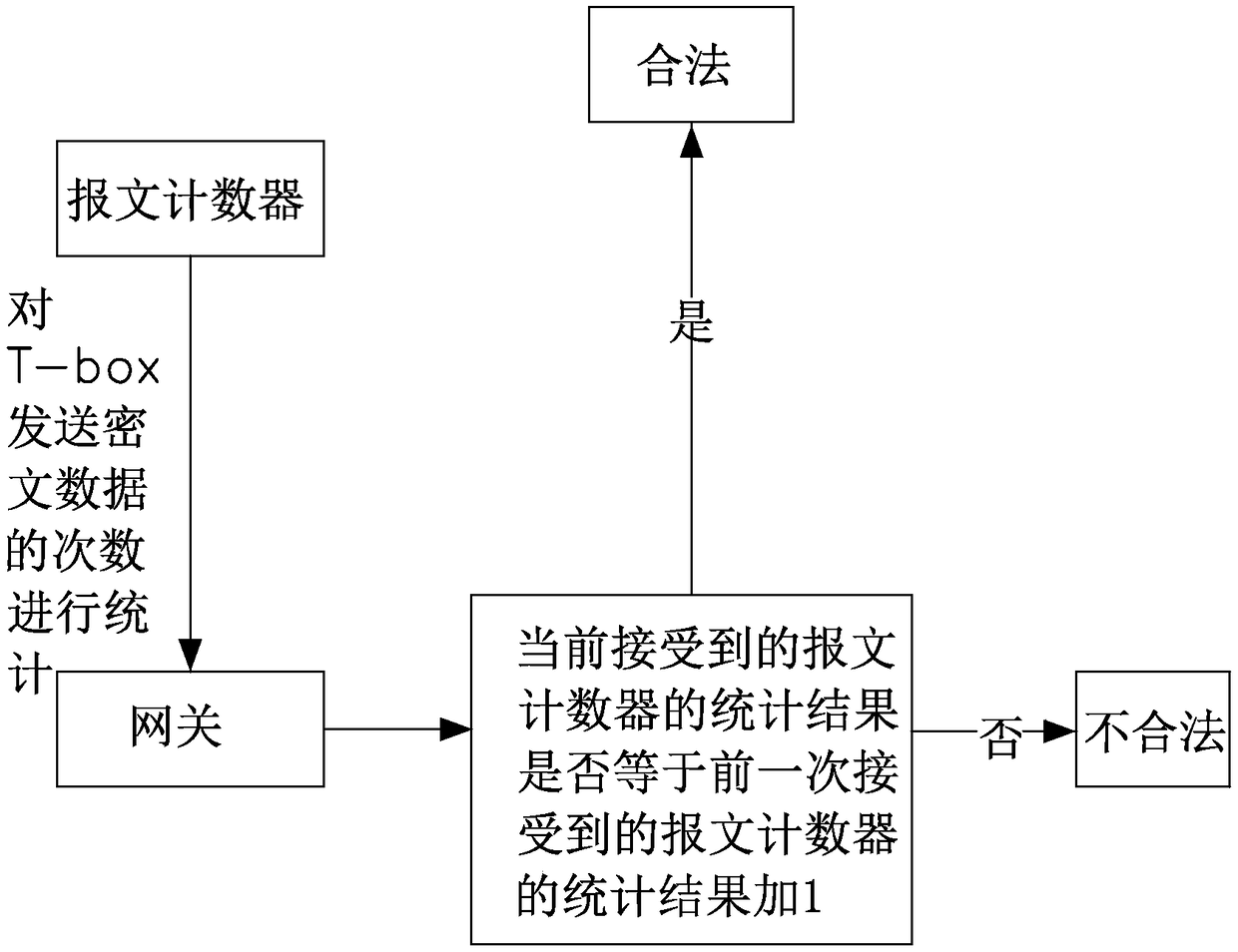
Vehicle CAN bus encryption method
The invention provides a vehicle CAN bus encryption method. The method comprises the following steps: firstly performing IMMO authentication on T-box, wherein the T-box sends a message to a gateway through a bus CAN under the condition that the IMMO authentication is passed; performing hardware encryption and decryption on the message sent by the T-box through a HSM of the T-box and the HSM of thegateway, wherein the a message counter is arranged on the T-box to count the sent message, and the gateway detects the message counter; judging that the message is legal when the message conforms tothe set rule, and decrypting the message when the message is legal, and then sending the decrypted message to other CAN branches of the vehicle. The vehicle CAN bus encryption method provided by the invention has the advantages that the triple encryption method of IMMO authentication, the HSM hardware encryption and the message counter judgment is applied by adopting the way of combining the software encryption and hardware encryption, the security of the vehicle CAN bus is greatly improved, the Hacker intrusion is prevented, and the travelling security is improved.
Owner:SOUEAST
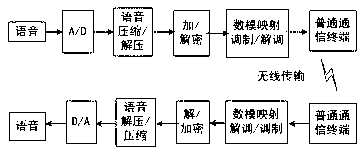
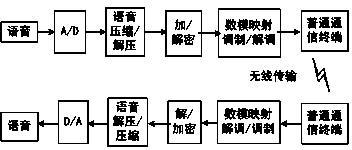
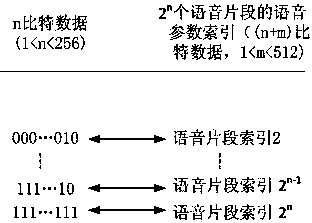
System and implement method thereof for secret communications based on public communication network voice channel
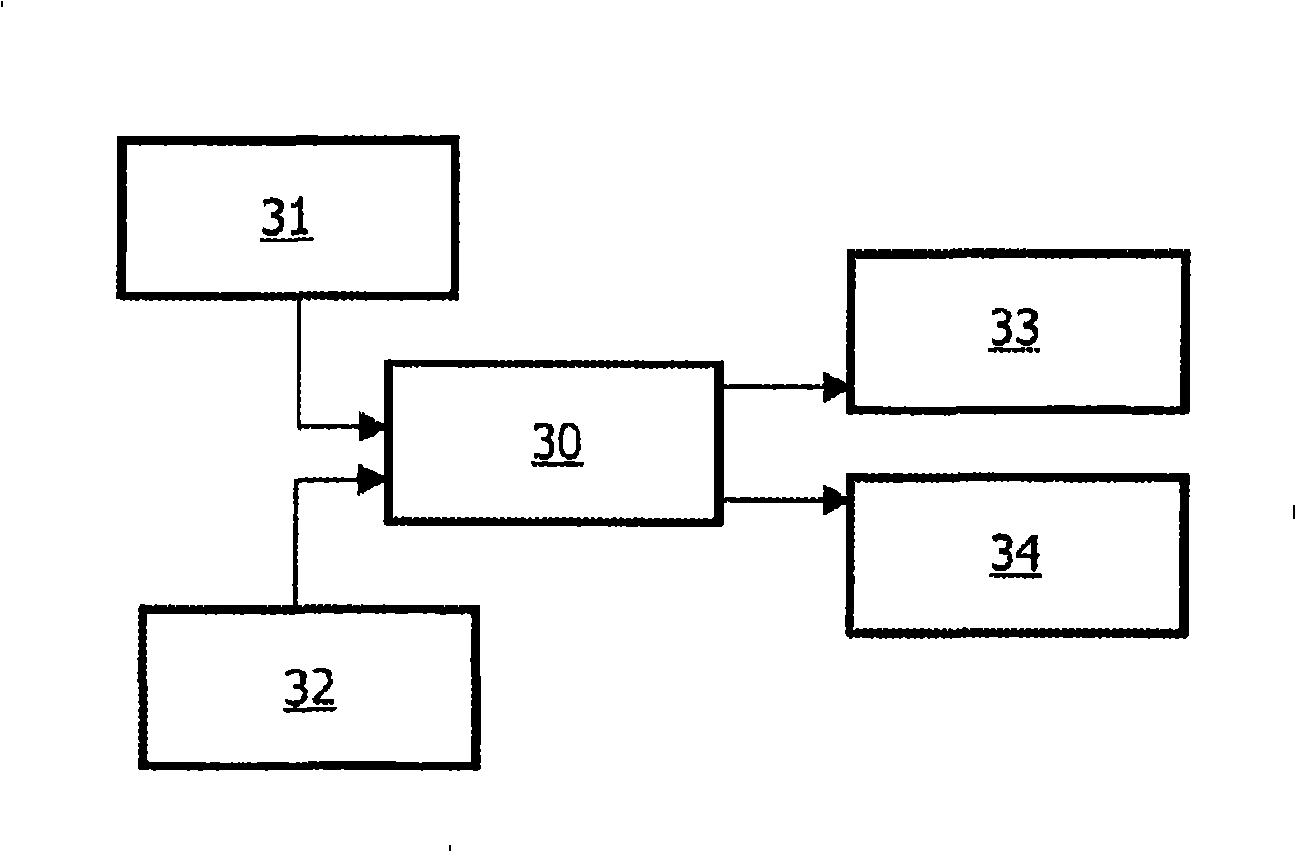
InactiveCN103000181AEncryption is validMeets requirementsSpeech analysisSecuring communicationComputer hardwareVoice communication
The invention discloses a system and an implement method thereof for secret communications based on a public communication network voice channel. The system and the implement method thereof for the secret communications based on the public communication network voice channel mainly solve the problem in an existing technology that a voice encryption method of a public communication network is low in reliability, difficult in technique and not convenient to implement. The system for the secret communications based on the public communication network voice channel comprises a power source, and further comprises a processor connected with the power source, and a storage, a digital / analog conversion module, a voice compression / decompression module, an encryption / decryption module, and a digital analogy mapping modulation / demodulation module all connected with the processor. By adopting the scheme, the system and the implement method thereof for the secret communications based on the public communication network voice channel achieve a purpose of conveniently and reliably keeping voice communications confidential, and have high practical value and promotional value.
Owner:CHENGDU LINGGUANG QUANTUM TECH
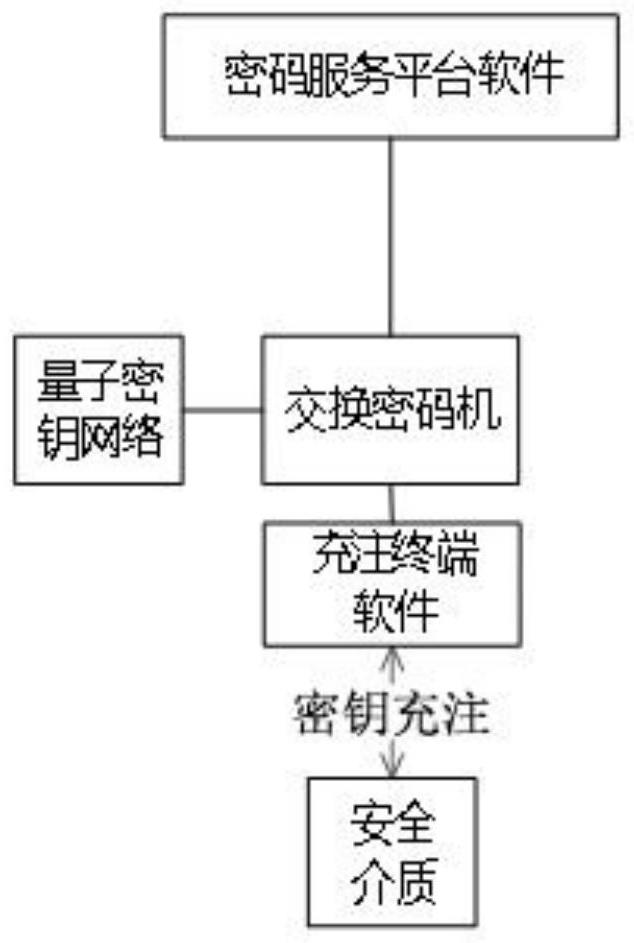
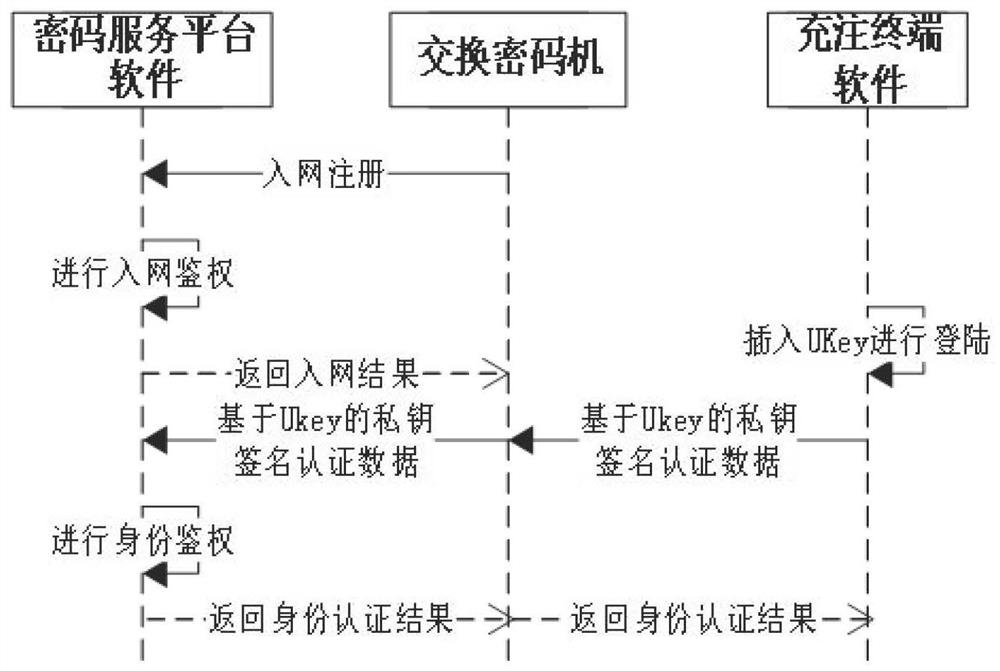
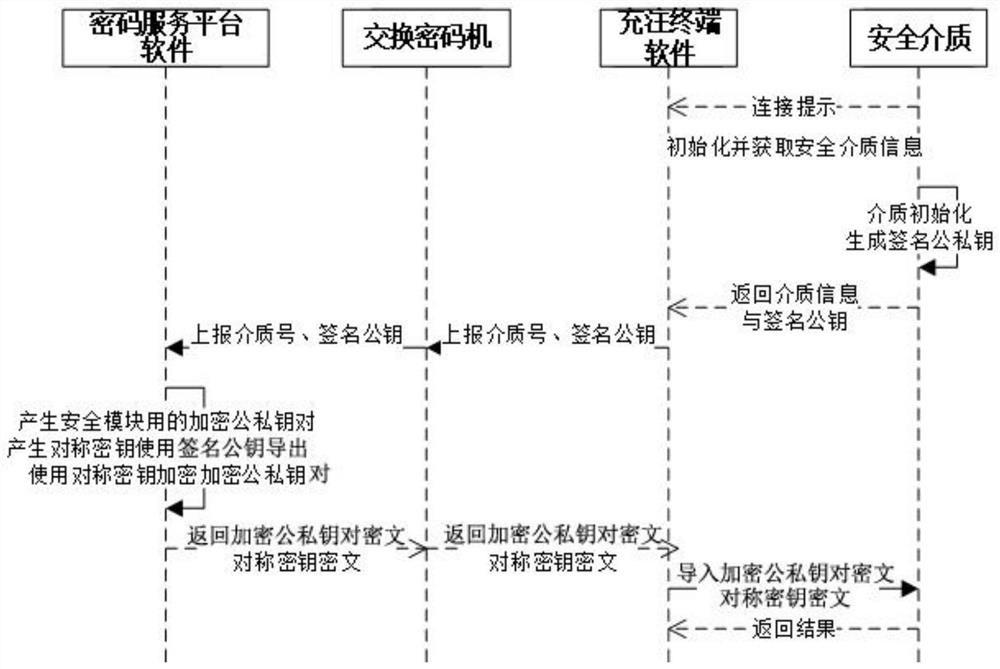
Quantum key charging method of communication terminal
PendingCN114095167AEnsure safetyEncryption is validKey distribution for secure communicationUser identity/authority verificationKey exchangeCiphertext
The invention relates to communication encryption, in particular to a quantum key charging method of a communication terminal. The method comprises the steps that connection relationships among a charging terminal, a quantum random number generator, an exchange cipher machine and a cipher service platform are established; the cipher service platform initializes a security medium in a communication terminal through the exchange cipher machine and the charging terminal; the quantum random number generator generates a charging key, and the exchange cipher machine generates an encryption key to encrypt the charging key; the charging terminal obtains the charging key based on a key obtaining token, and the exchange cipher machine encrypts the encryption key through a card public key and returns a charging key ciphertext and an encryption key ciphertext to the charging terminal; and the charging terminal imports the charging key ciphertext and the encryption key ciphertext into the security medium, the security medium returns a charging result to the charging terminal, and the charging terminal finishes key charging of the security medium. According to the technical scheme provided by the invention, the defects that an application range is limited and a quantum key is likely to be stolen in a quantum key charging process can be effectively overcome.
Owner:安徽国盾量子云数据技术有限公司
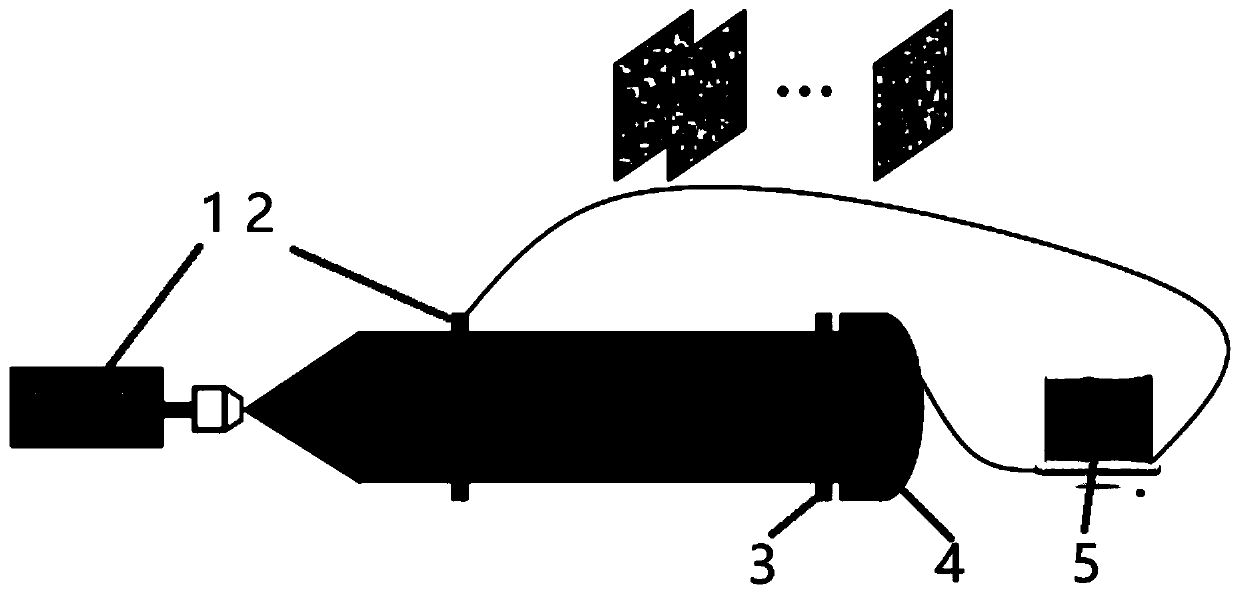
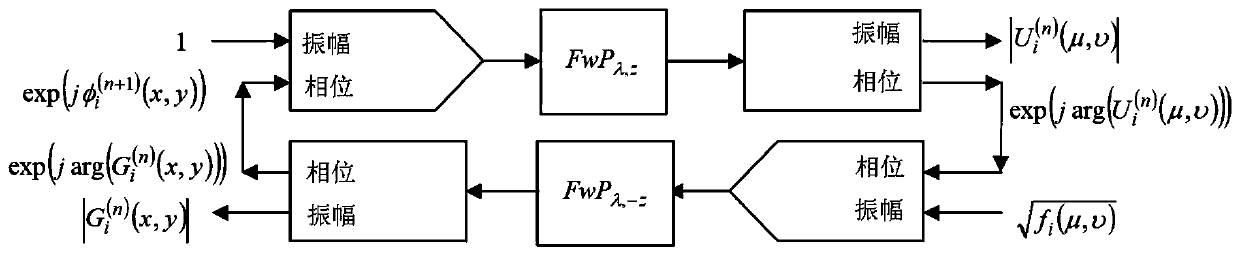
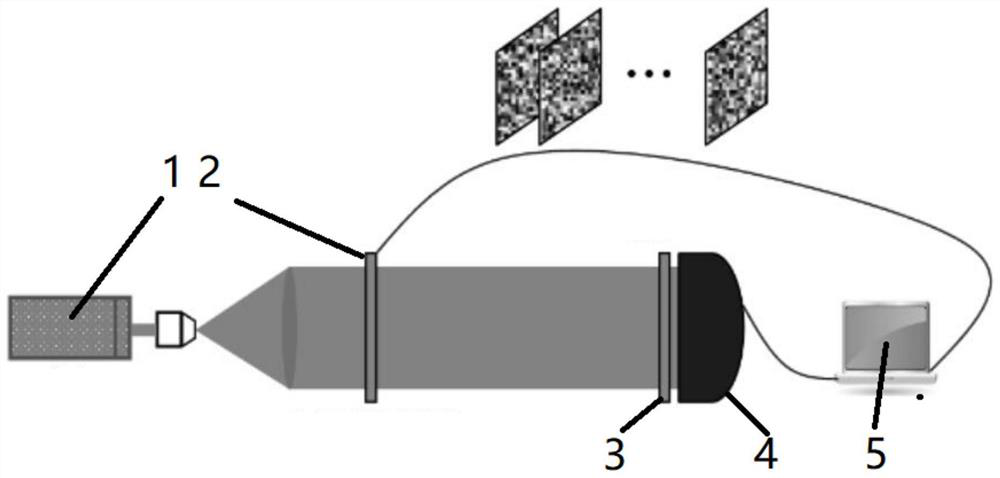
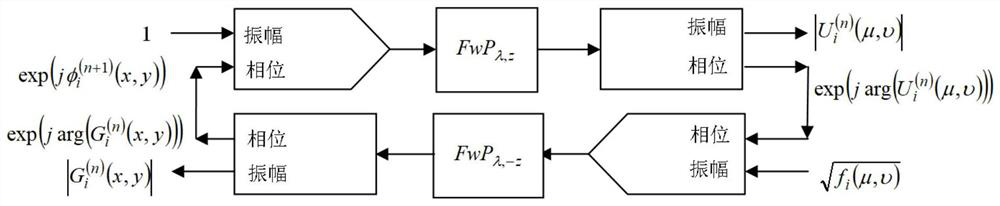
Optical image encryption method for calculating ghost imaging by using phase iterative algorithm
ActiveCN110348232AFast convergenceReduce in quantityDigital data protectionFresnel diffractionEncryption
The invention discloses an optical image encryption method for calculating ghost imaging by using a phase iterative algorithm, which comprises the following steps of: 1) performing collimation illumination on a laser beam, and sequentially inputting a group of different random phase masks into a spatial light modulator; wherein the wave is modulated by a pure phase mask, and the generated random speckle pattern passes through the object at the axial distance from the plane of the spatial light modulator; 2) wherein a transmission function T ([mu]m, v) of the object, Ii ([mu]m, v) = | Ei ([mu]m, v) | 2 being a speckle pattern, Ei ([mu]m, v) being a free space propagation field of the pure phase mask and (mu, v) representing lateral coordinates of the object plane; performing, for each purephase mask embedded in the spatial light modulator, by using Fresnel diffraction; and 3) correlating the intensity distribution collected by the barrel detector with the speckle pattern derived from the known pure phase mask. The method provided by the invention is simple and easy to implement and high in accuracy.
Owner:XIAN UNIV OF TECH
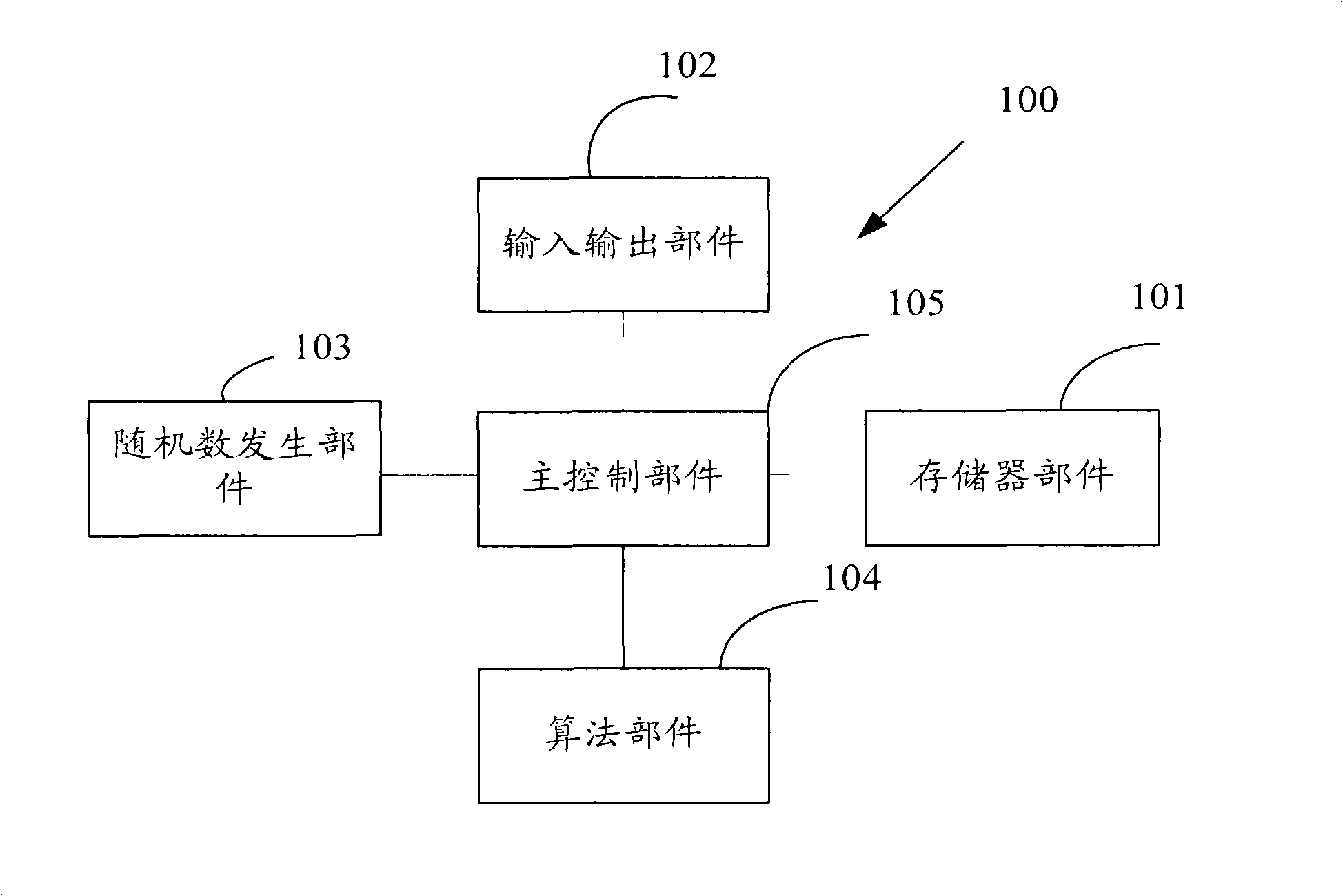
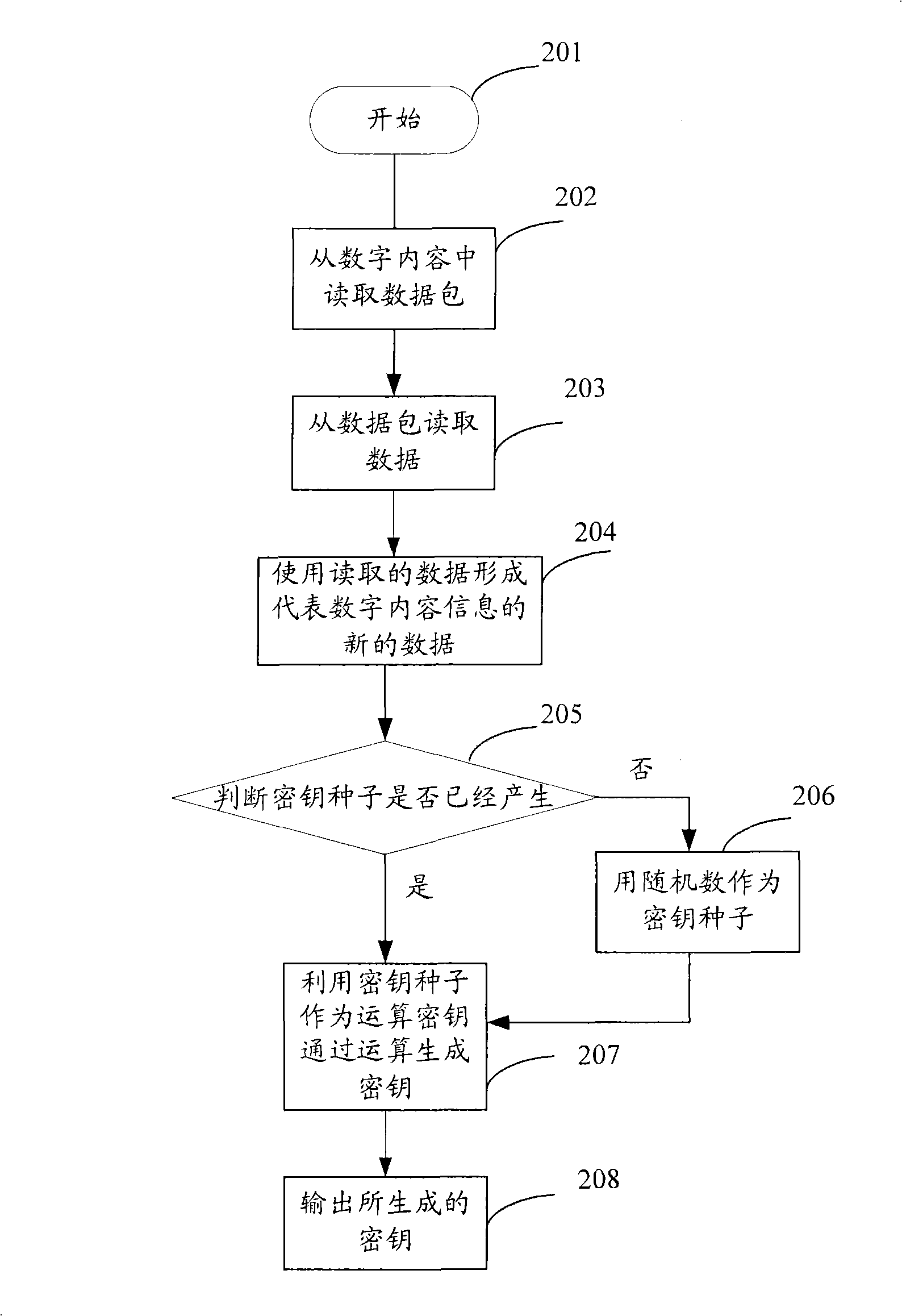
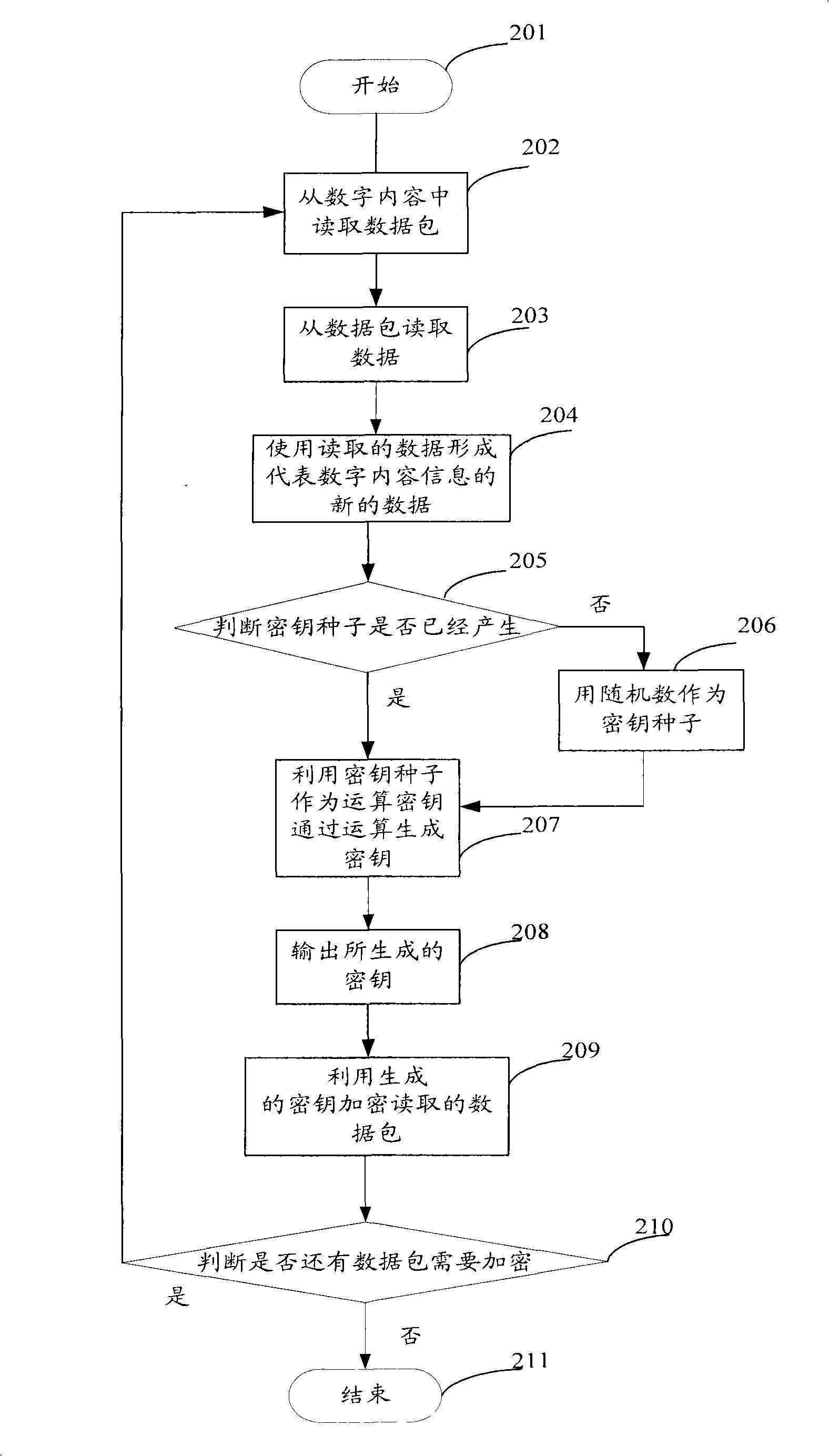
Cryptographic key generation device, method and data encryption method based on digital contents
InactiveCN101296074AEncryption is validEnsure safetySecuring communicationComputer hardwareCryptographic key generation
The invention provides a device and a method for generating a cipher code based on digital contents and a data encrypting method. The cipher code generating device comprises a memory component, a random number generating component, an arithmetic component, an input and output component and a main control component which is respectively connected with the memory component, the random number generating component, the arithmetic component and the input and output component so as to control the operation of the components. Randomness and safety of cipher code generating can be met and the data can be effectively encrypted by using the cipher code generating device and the cipher code generating method based on the cipher code generating device and the data encrypting method of the invention, thus guaranteeing the security of the digital contents and maintaining the security and reliability of the data communication.
Owner:BEIJING ANPU BODA SCI & TECH
An optical dft-s-ofdm secure transmission system based on digital chaos
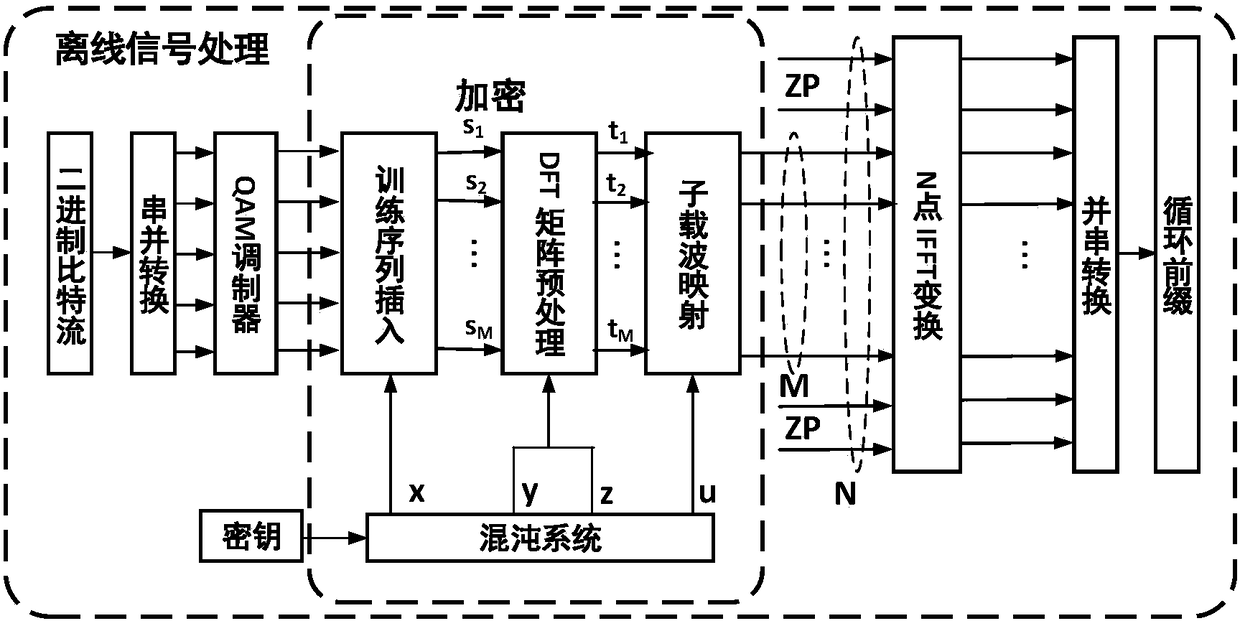
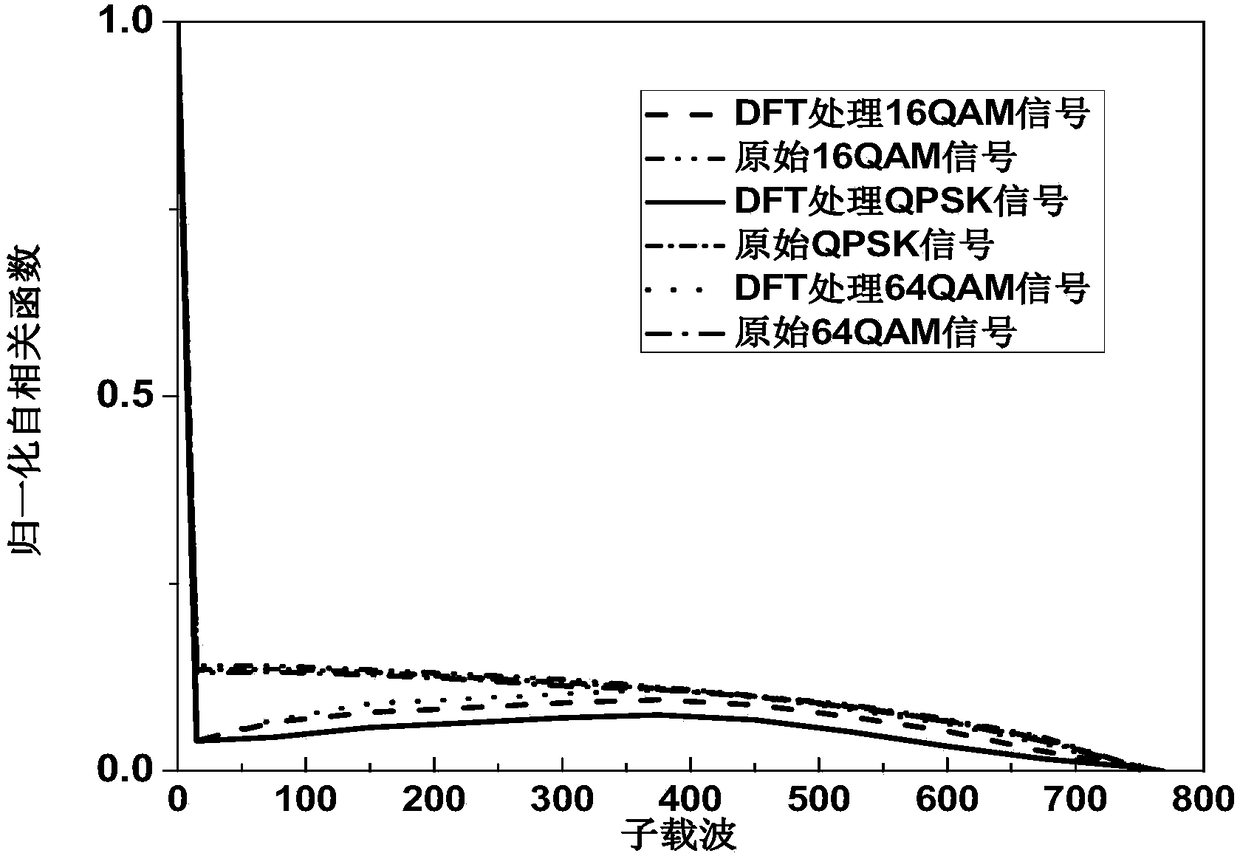
InactiveCN105933103BImprove transmission qualityImprove bit error rate performanceSecuring communication by chaotic signalsElectromagnetic transmission optical aspectsTransceiverDFT matrix
The invention discloses a light DFT-S-OFDM secure transmission system based on a digital chaos. The system comprises three encryption steps all together, i.e., insertion of an OFDM synchronous training sequence, DFT matrix signal preprocessing and subcarrier mapping, wherein an OFDM synchronous training sequence and a subcarrier mapping mode are both generated by a chaotic system, DFT matrix element parameters m and n are generated by the chaotic system, by use of initial value sensitivity and pseudo randomness of the digital chaos, encryption processing is performed on DFT-S-OFDM signals, and thus secret transmission is realized. On one hand, since a security system secret key space is huge, the security of high-speed information transmission can be effectively enhanced, and at the same time, since a DFT matrix can substantially reduce a peak average power ratio (PAPR) of OFDM signals, the performance of the transmission system is also improved; and on the other hand, since multiple iteration optimization and multiple discrete Fourier transformation operation are unnecessary in a DFT matrix signal processing system, the whole system has the following advantages: the system architecture is simple, the calculation amount is small, the transceiver cost is low, and transmission of sideband information is unnecessary.
Owner:SHANGHAI JIAOTONG UNIV
Digital image encryption method, decryption method and system based on chaotic system
PendingCN114157408ALarge dynamic propertiesStrong dynamic propertiesSecuring communication by chaotic signalsChaotic systemsDigital image
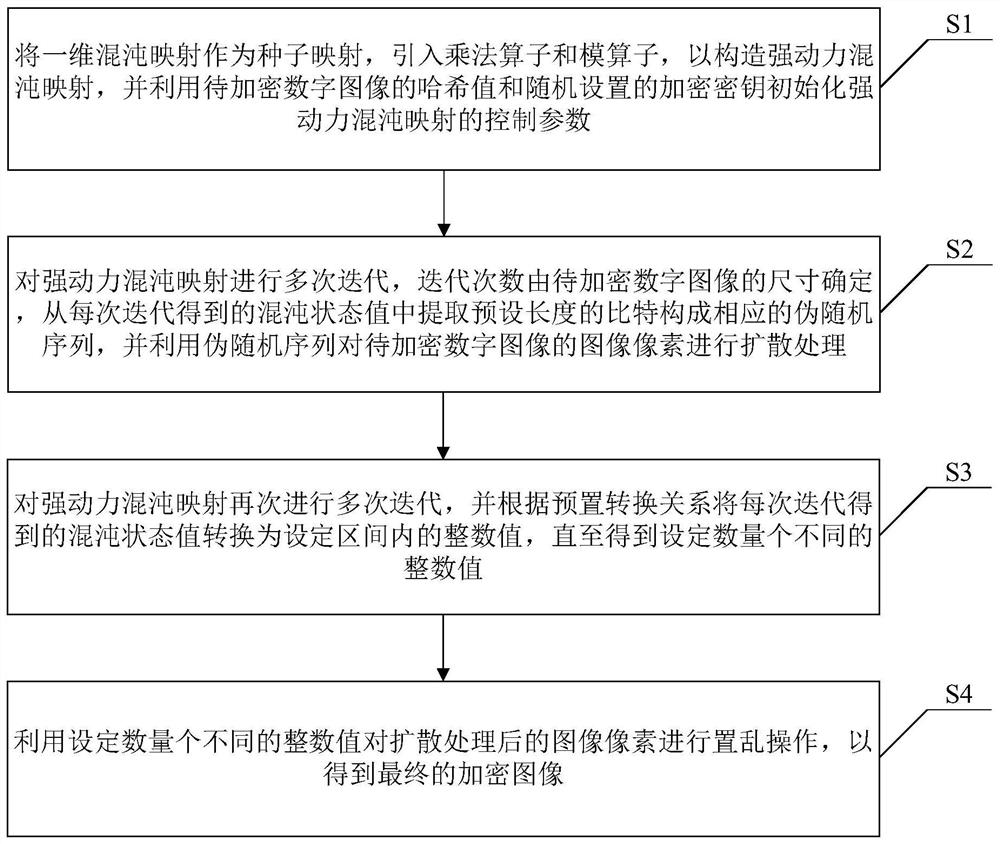
The invention discloses a digital image encryption method, decryption method and system based on a chaotic system, and belongs to the field of chaotic image encryption, and the encryption method comprises the steps: taking a one-dimensional chaotic mapping as a seed mapping, introducing a multiplication operator and a modular operator, constructing a strong dynamic chaotic mapping, initializing a control parameter of strong dynamic chaotic mapping by using the hash value of the digital image to be encrypted and the encryption key; iterating the strong dynamic chaotic mapping for multiple times, extracting bits with a preset length from a chaotic state value obtained by each iteration to form a corresponding pseudo-random sequence, and diffusing image pixels of the digital image to be encrypted by using the pseudo-random sequence; and performing multiple iterations on the strong dynamic chaotic mapping again, converting a chaotic state value obtained by each iteration into an integer value in a set interval until a set number of different integer values are obtained, and performing scrambling operation on image pixels after diffusion processing to obtain a final encrypted image. And the digital image is encrypted safely and effectively.
Owner:HUAZHONG UNIV OF SCI & TECH
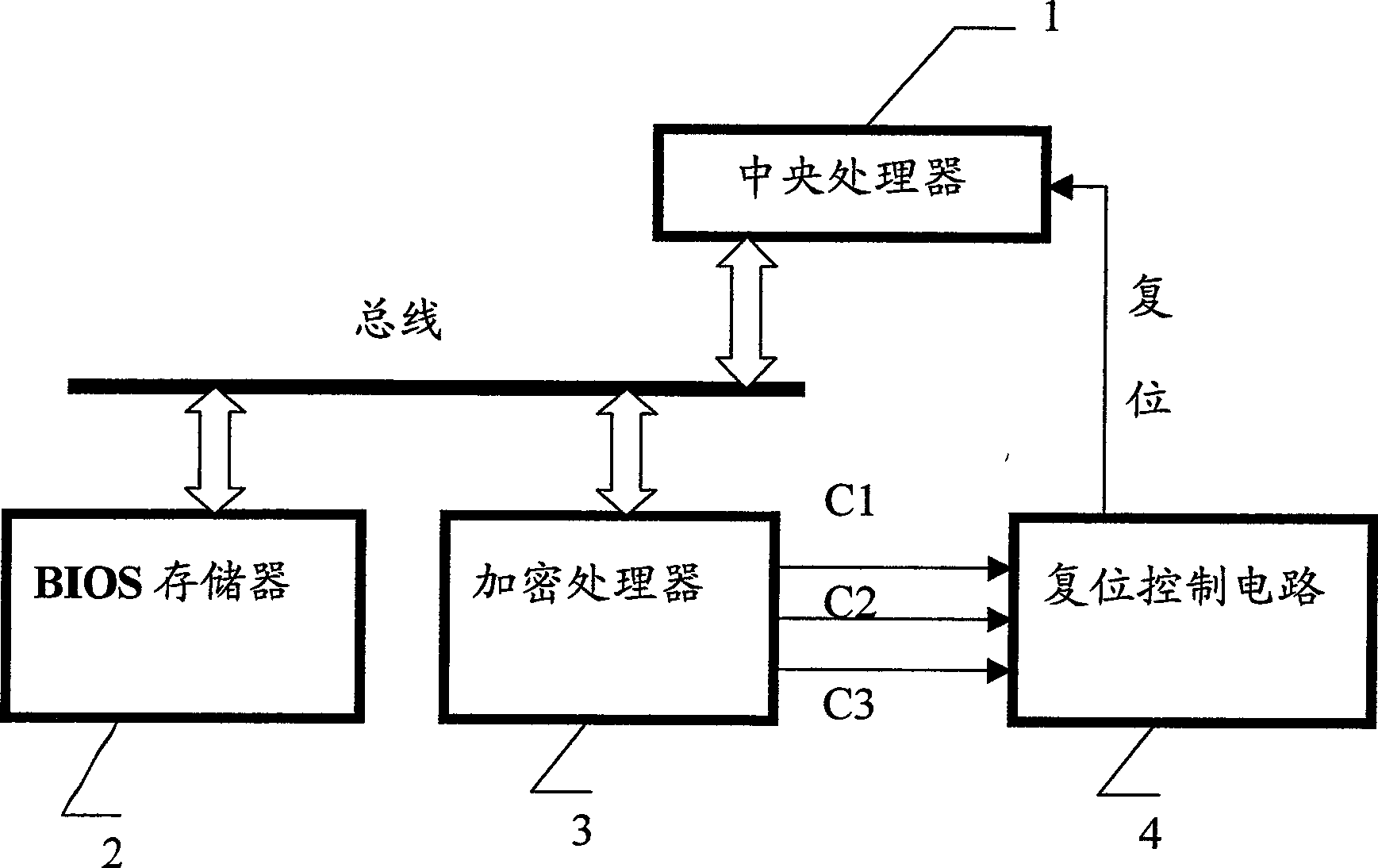
Encryption system for computer mainboard and encryption method thereof
InactiveCN100495335CEncryption is validPrevent illegal useData resettingProgram loading/initiatingPasswordEmbedded applications
The invention relates to an encryption system and its encryption method of the computer main board, which is composed of the CPU, the BIOS memory, the encryption processor and the reset controlling circuit. The BIOS memory and the encryption processor are connected to the CPU via the bus. The password check-up program is added to the BIOS start-up procedure stored in the BIOS memory. By this means, the encryption processing to the main board is implemented when the computer's main board starts up. The reset controlling circuit is connected to the encryption processor and the CPU. The encryption processor transfers signals to the reset controlling circuit and force the circuit to generate the reset signal to the CPU to reset the computer's main board. The invention effectively encrypts the main board of the computer and the embedded system.
Owner:EVOC INTELLIGENT TECH
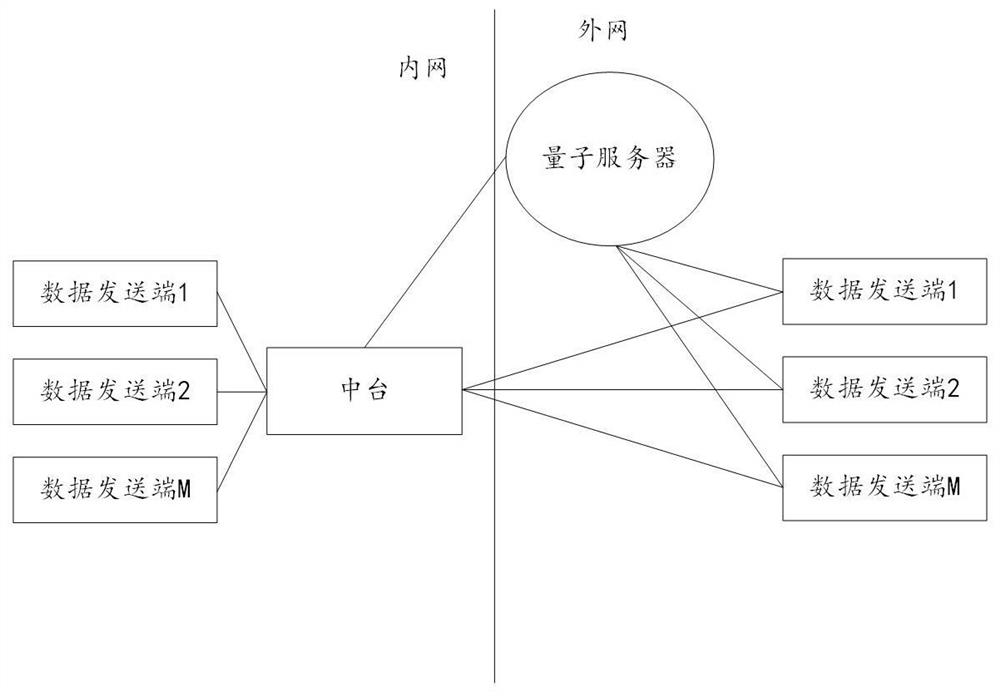
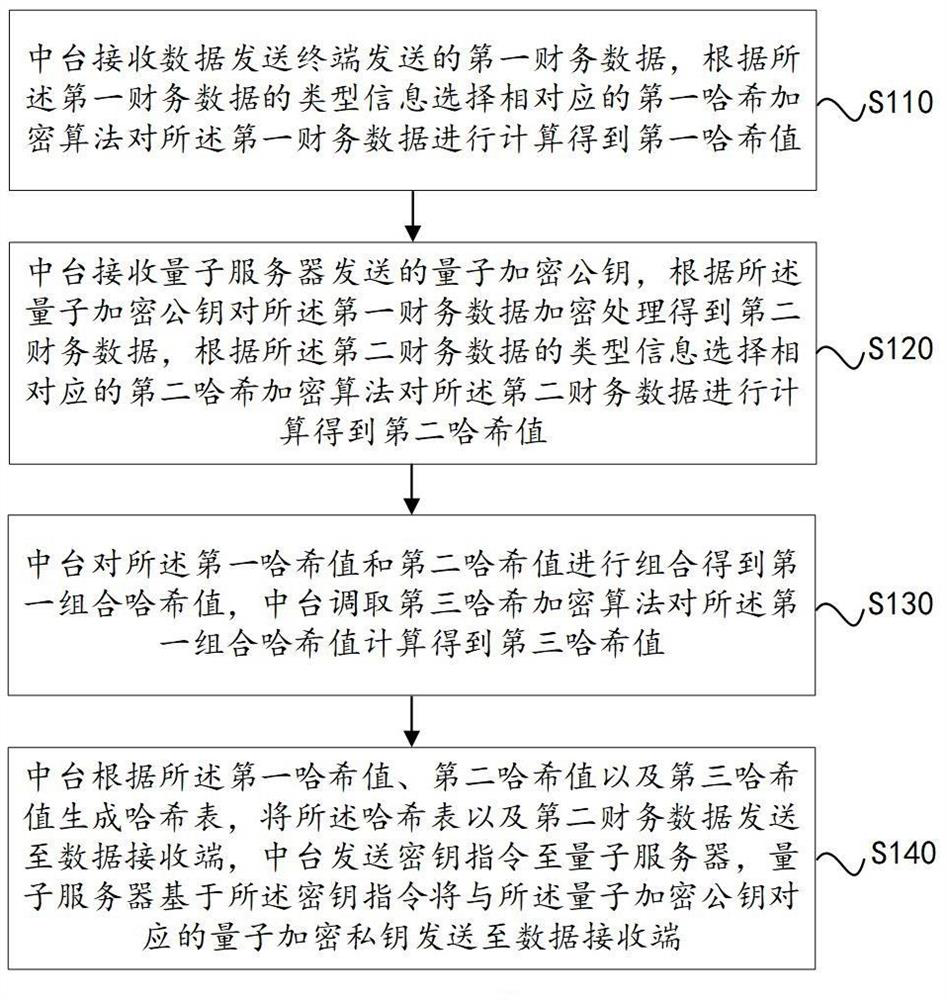
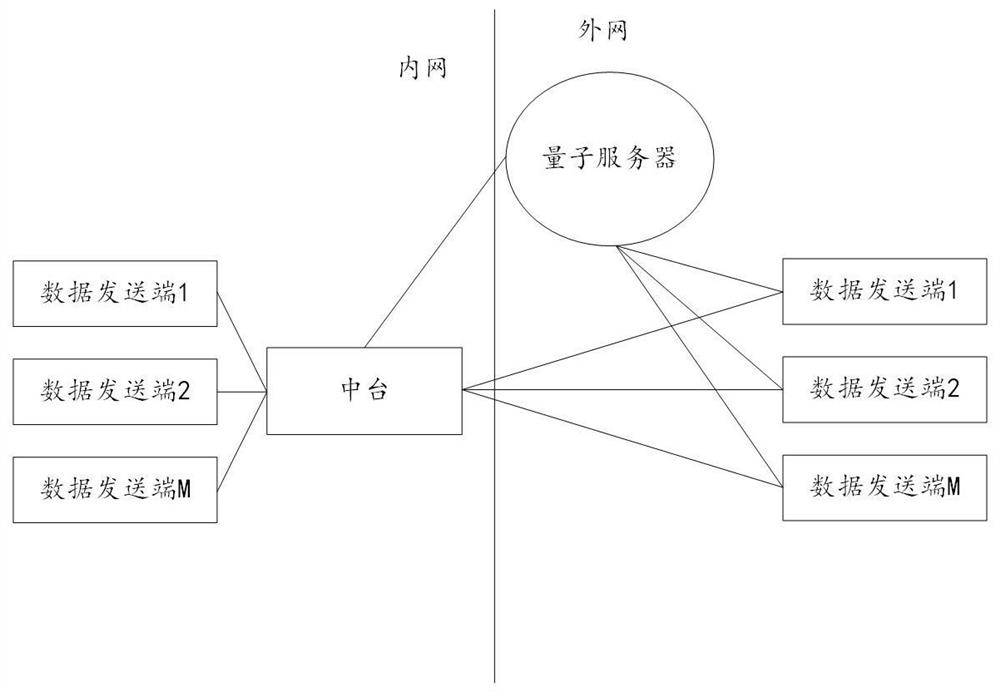
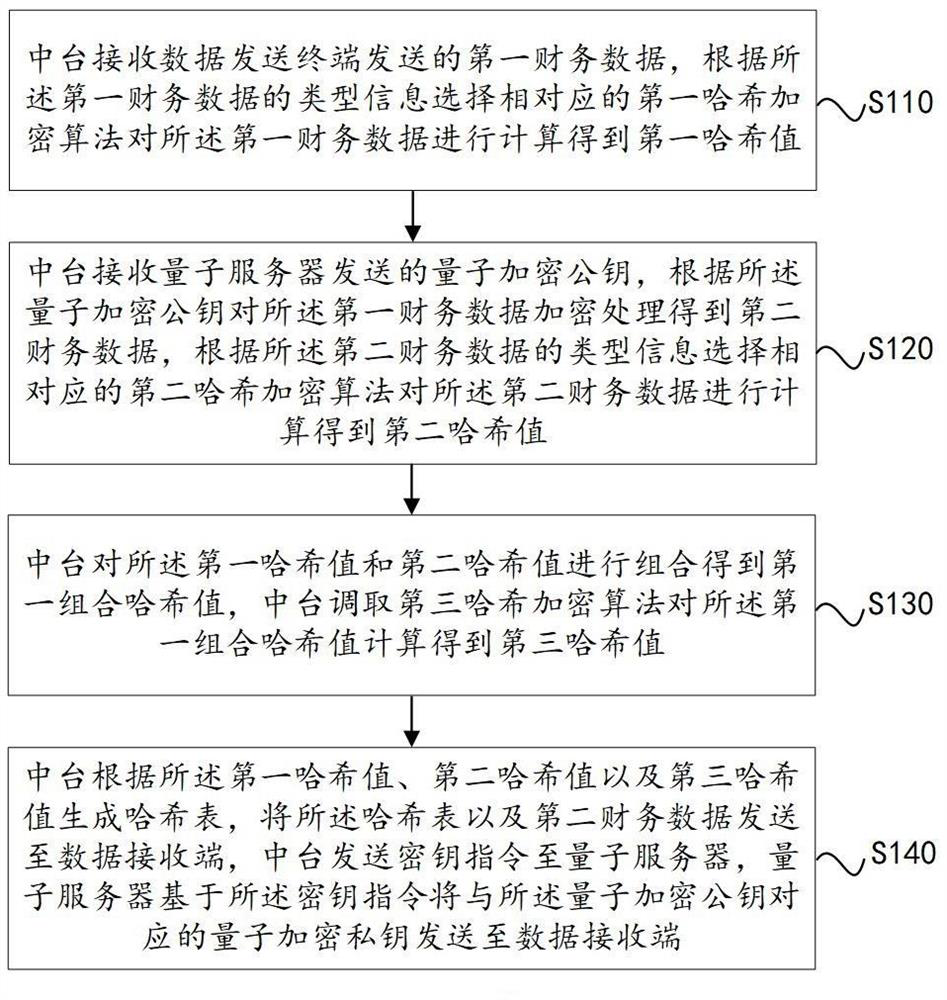
Intelligent sharing financial platform and system based on Hash encryption algorithm and quantum key
The invention provides an intelligent sharing financial platform and system based on a Hash encryption algorithm and a quantum key, and the method comprises the steps: receiving first financial data transmitted by a data transmitting terminal through a middle platform, according to the type information of the first financial data, selecting a corresponding first Hash encryption algorithm to calculate the first financial data to obtain a first Hash value; the middle station receives the quantum encryption public key sent by the quantum server, encrypts the first financial data according to the quantum encryption public key to obtain second financial data, and calculates the second financial data according to a second Hash encryption algorithm to obtain a second Hash value; the middle table combines the first Hash value and the second Hash value to obtain a first combined Hash value, and calls a third Hash encryption algorithm to calculate the first combined Hash value to obtain a third Hash value; and the middle table generates a hash table according to the first hash value, the second hash value and the third hash value, and sends the hash table and the second financial data to a data receiving end.
Owner:STATE GRID ZHEJIANG ELECTRIC POWER
System and implement method thereof for secret communications based on public communication network voice channel
InactiveCN103000181BEncryption is validMeets requirementsSpeech analysisSecuring communicationVoice communicationComputer module
The invention discloses a system and an implement method thereof for secret communications based on a public communication network voice channel. The system and the implement method thereof for the secret communications based on the public communication network voice channel mainly solve the problem in an existing technology that a voice encryption method of a public communication network is low in reliability, difficult in technique and not convenient to implement. The system for the secret communications based on the public communication network voice channel comprises a power source, and further comprises a processor connected with the power source, and a storage, a digital / analog conversion module, a voice compression / decompression module, an encryption / decryption module, and a digital analogy mapping modulation / demodulation module all connected with the processor. By adopting the scheme, the system and the implement method thereof for the secret communications based on the public communication network voice channel achieve a purpose of conveniently and reliably keeping voice communications confidential, and have high practical value and promotional value.
Owner:CHENGDU LINGGUANG QUANTUM TECH
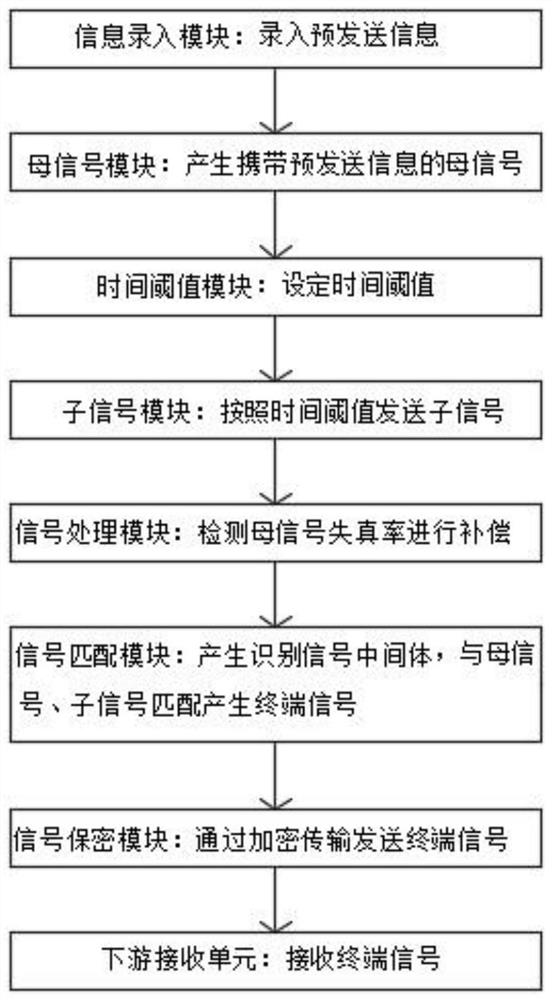
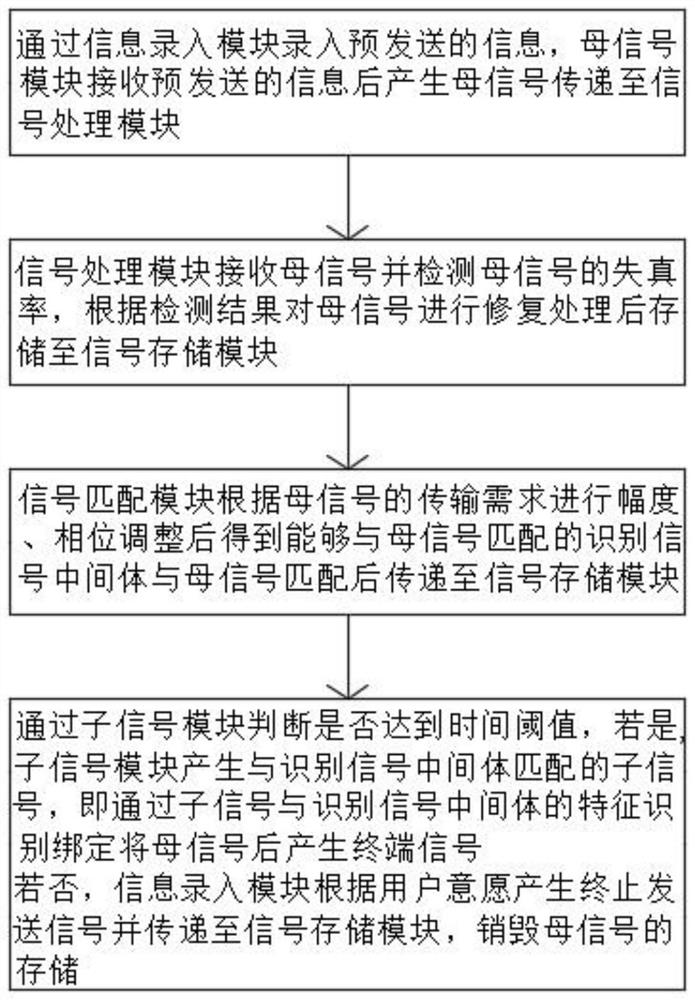
RabbitMQ-based delayed braking system and braking method thereof
PendingCN114615222AImprove communication latencyIncrease delaySecuring communicationHigh level techniquesTelecommunicationsControl engineering
The invention relates to the technical field of network communication, and particularly discloses a delay braking system based on RabbitMQ and a braking method thereof. Comprising an upstream transmitting unit, a RabbitMQ server and a downstream receiving unit which are in signal connection in sequence, and the upstream transmitting unit comprises a mother signal module used for receiving pre-transmitted information and generating a mother signal. According to the invention, through the feature identification mode of the mother signal and the sub-signal and the determined matching transmission of the sub-signal to the mother signal under the time threshold, the terminal signal is generated to complete the instant messaging process, the communication delay is improved on the premise of not influencing the communication conversation, the braking instruction can be given to the sent information, and the communication efficiency is improved. The fault-tolerant rate of information input and sending is increased, misunderstanding is reduced, and social harmony is facilitated.
Owner:航天科工通信技术研究院有限责任公司
An Image Encryption Method Based on Feistel Network and Dynamic DNA Coding
ActiveCN108365947BStrong randomnessStrong resistance to attackKey distribution for secure communicationSecuring communication by chaotic signalsPlaintextCiphertext
Owner:ZHENGZHOU UNIVERSITY OF LIGHT INDUSTRY
DVD encryption optical disk burning method
InactiveCN106169299AEncryption is validPrevent direct copyingRecord information storageRecording signal processingComputer hardwareEncryption
A method for burning an encrypted DVD disc belongs to the technical field of electronic products. The method is novel and the working principle is clear. When pirates use software such as Nero to copy the entire disc of the encrypted disc, they encounter continuous data reading errors in the burnt area. causing replication to fail. When trying to copy encrypted files separately from the master disk, a parameter error occurs and the data cannot be read to other storage devices, so as to avoid further illegal copying. Since the customer's data is located outside the area corresponding to the encrypted directory, and the area burnt by this method will not damage the customer's data, the master disc formed through the above steps will not be affected in any way during normal use.
Owner:WUHU ZHENHUA RONGKE INTELLIGENT TECH
Multibit forensic watermark with encrypted detection key
The invention relates to embedding auxiliary data in the form of a multibit payload in a host signal, and encrypting the associated detection key. Moreover, the invention relates to extracting the auxiliary data in the form of the multibit payload from a data signal. Auxiliary data is embedded in a host signal by the following steps. First a reference watermark is provided, subsequently an encrypted detection key associated only with the reference watermark is generated. The encrypted detection key may be a scrambled version of the watermark. In a further step, the multibit watermark is generated and a multibit payload is encoded into the reference watermark. Finally, the multibit watermark is embedded into the host signal.
Owner:KONINKLIJKE PHILIPS ELECTRONICS NV
A method for encrypting and decrypting printed text in invisible office
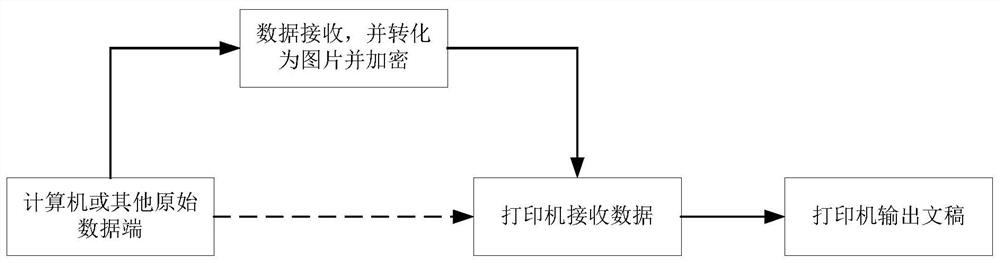
ActiveCN113012018BConsume less resourcesEasy to useImage enhancementImage analysisHidden dataInterference resistance
The invention provides a text encryption and decryption method for invisible office printing, which can realize strong anti-interference ability, consume very little hardware resources, and have less requirements on the text itself. The present invention proposes a relatively simple and feasible hidden data encryption method. The algorithm is relatively simple. By performing invisible encryption on the document, the time, place, person, unit information and other content can be effectively embedded in the document. Once the document is illegally leaked, it can quickly Effectively locate and query leaking units or personnel. The hardware consumes very little resources; there are few requirements for the text itself, and only a small amount of text or characters can be used to encrypt information; this method has strong anti-interference ability and can effectively resist the impact of text printing on encryption; high concealment , is not easy to be found, which is beneficial to query or trace after the event; there is no visible change to the original manuscript, which is conducive to the use and reading of the manuscript.
Owner:中船汉光科技股份有限公司
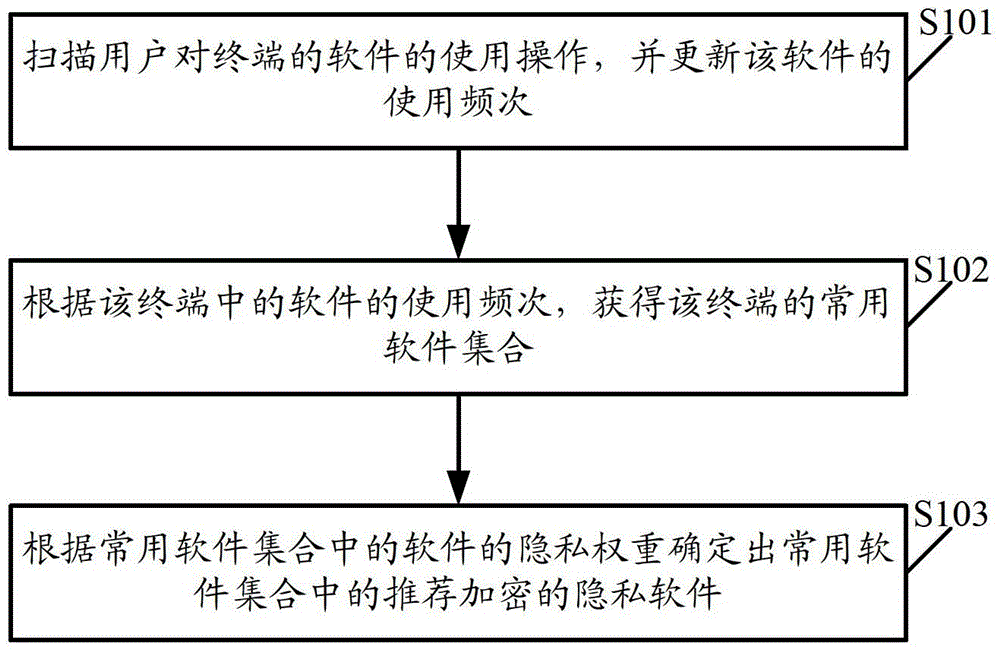
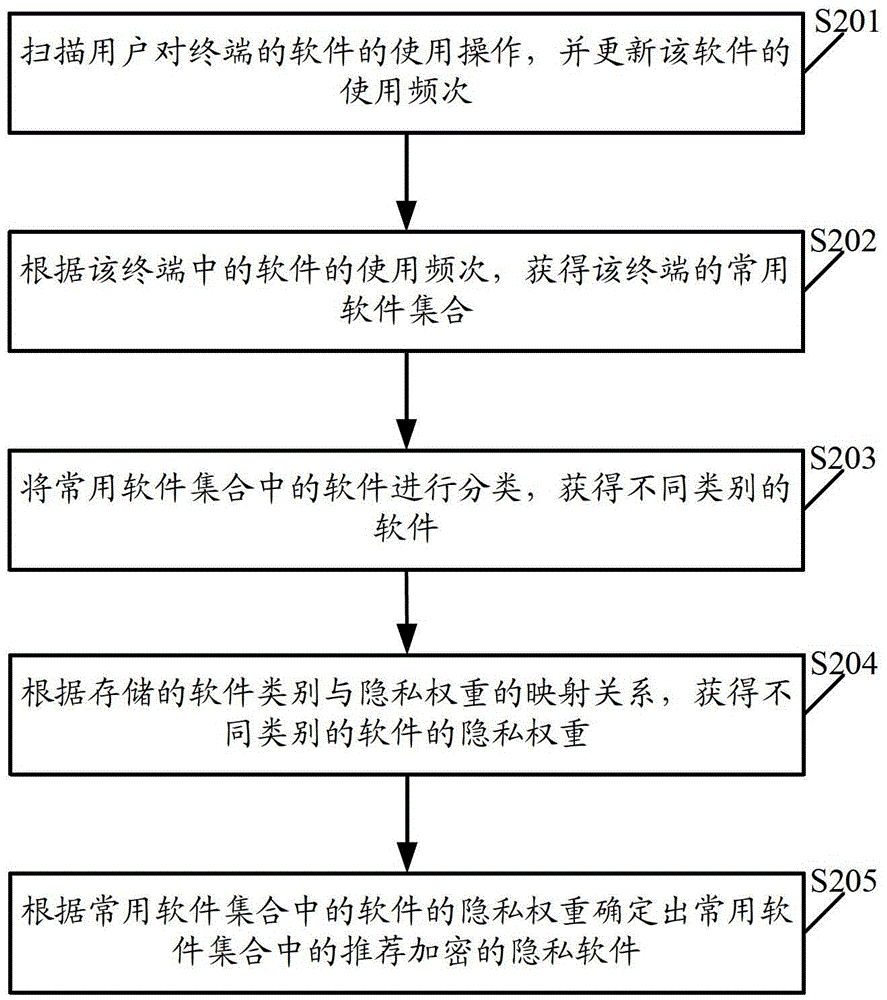
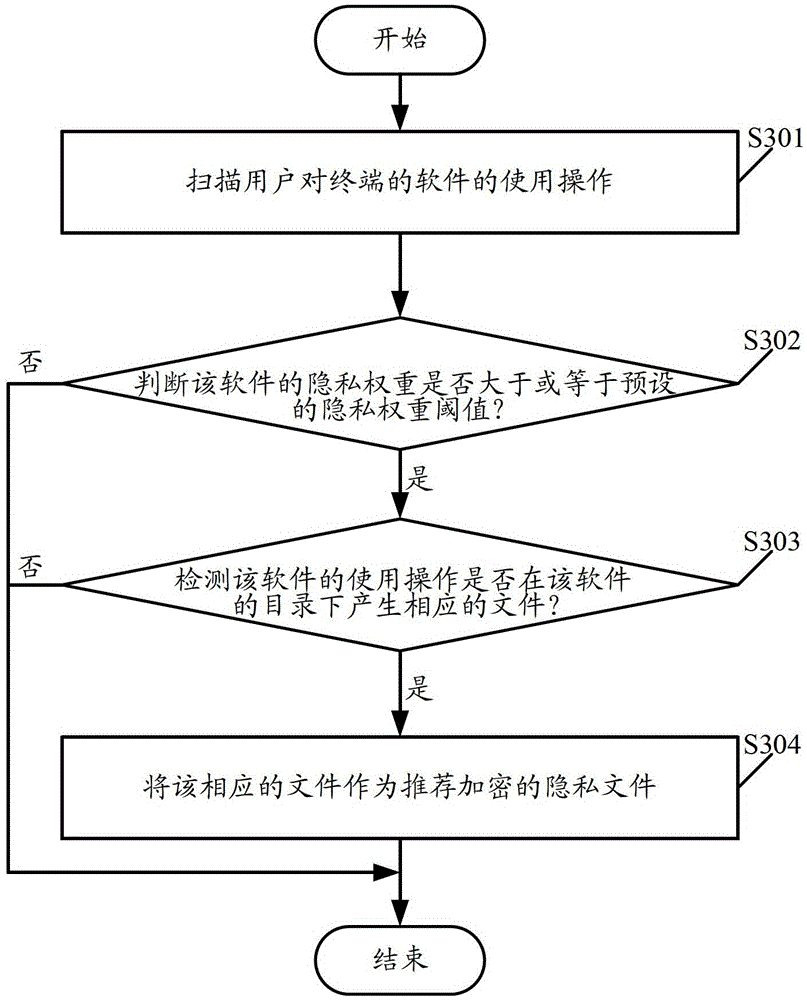
An encryption recommendation method, device, and terminal
ActiveCN104217169BFast encryptionEncryption is validDigital data protectionInternet privacyThe Internet
The present invention relates to the field of Internet technology, and discloses an encryption recommendation method, device, and terminal. The method includes: scanning user operations on terminal software, and updating the frequency of use of the software; according to the frequency of use of the software in the terminal, obtaining The commonly used software collection of the terminal; determine the recommended encrypted privacy software in the commonly used software collection according to the privacy weight and frequency of use of the software in the commonly used software collection; or include: scanning the user's use of the terminal software; judging the privacy of the software Whether the weight is greater than or equal to the preset privacy weight threshold; if the privacy weight of the software is greater than or equal to the preset privacy weight threshold, check whether the use of the software generates corresponding files in the software directory; The corresponding files are recommended as encrypted privacy files. Implementing the embodiments of the present invention can quickly and effectively recommend encrypted private files or private software to users.
Owner:TENCENT TECH (SHENZHEN) CO LTD
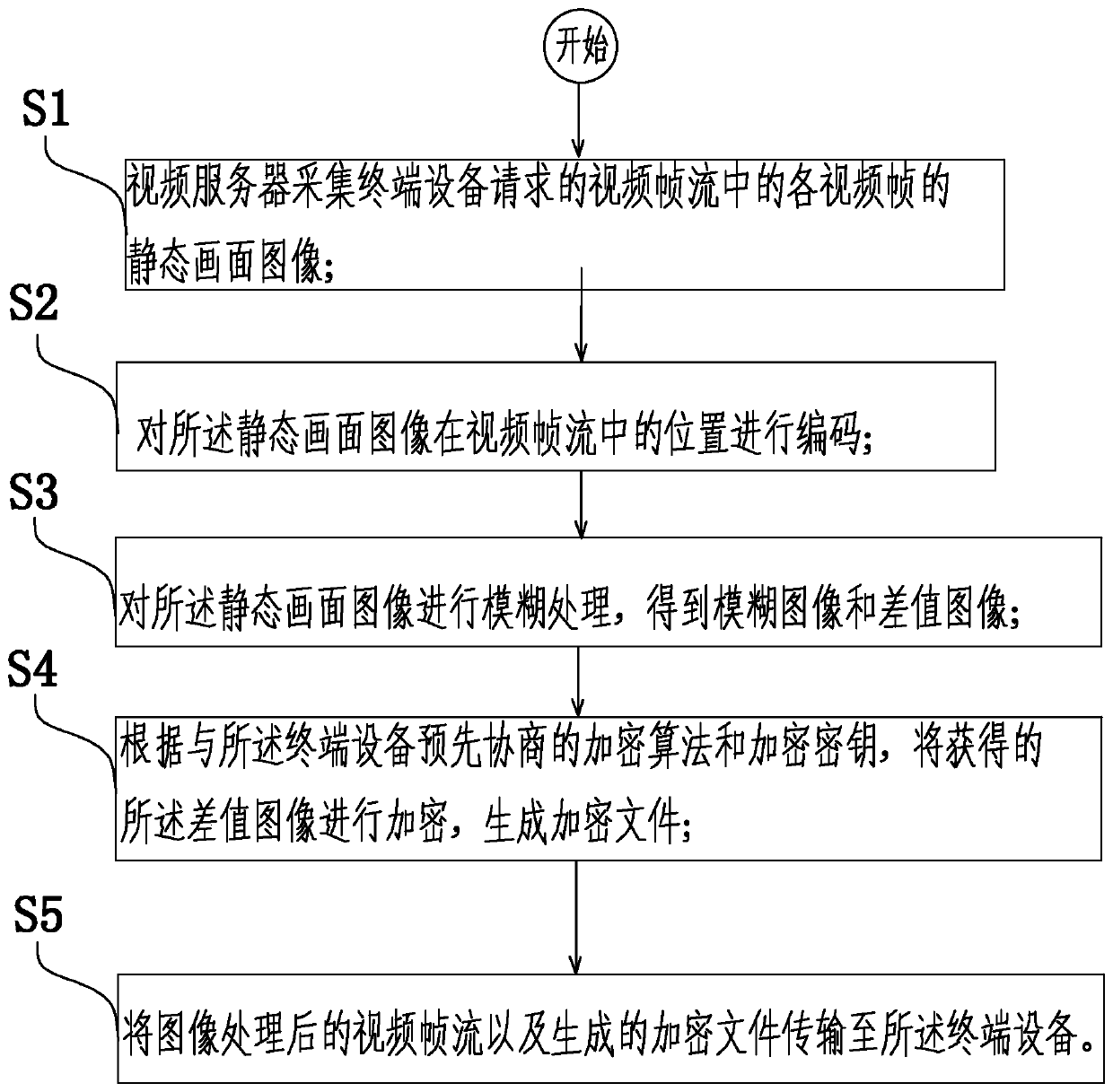
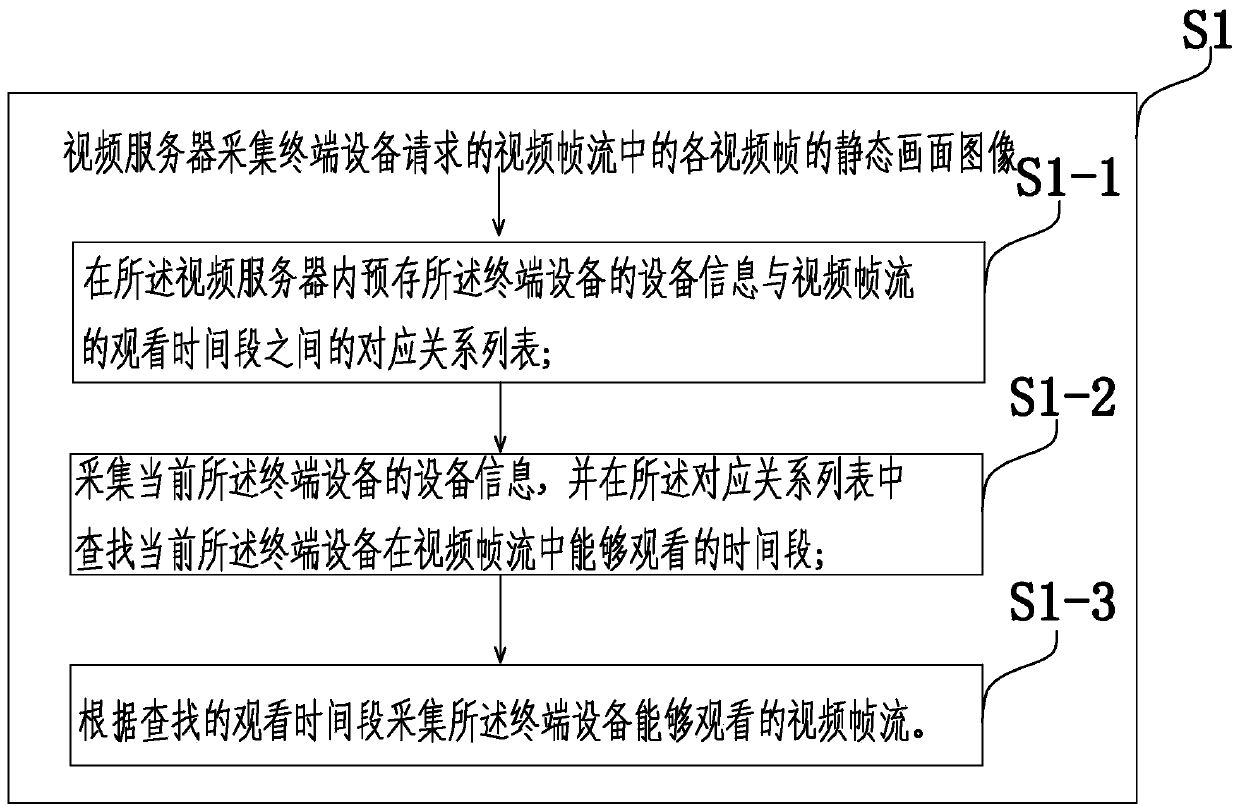
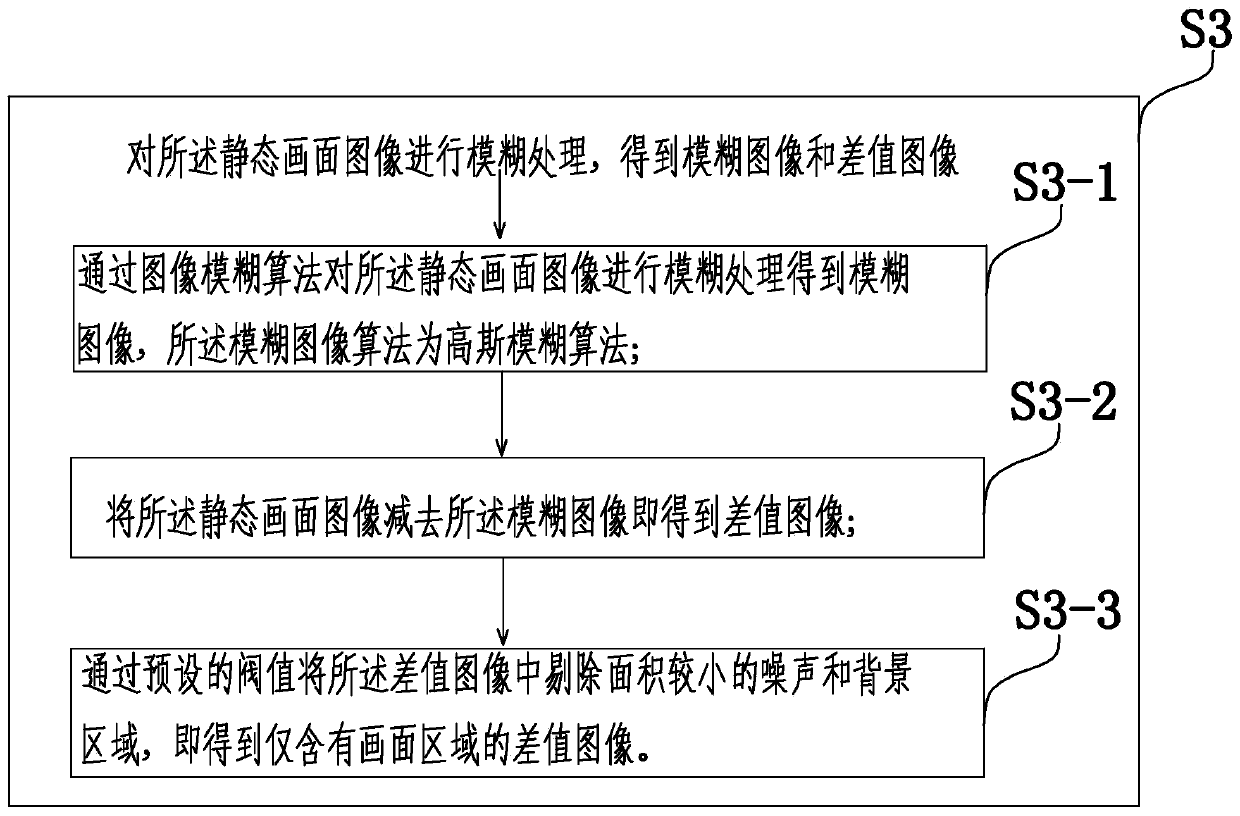
A video frame stream processing method and video server
ActiveCN106791923BOvercoming defects such as the effect of encryptionEncryption is validSelective content distributionVideo transmissionTerminal equipment
The invention provides a processing method of a video frame stream, a video server and a terminal device. The processing method comprises the following steps of collecting, by the video server, a static menu image of each video frame in the video frame stream which is requested by the terminal device; coding the position, in the video frame stream, of the static menu image; carrying out fuzzy processing on the static menu image, so as to obtain a fuzzy image and a difference image; according to an encryption algorithm and an encryption key which are previously negotiated with the terminal device, encrypting the obtained difference image, and generating an encrypted file; transmitting the video frame stream of which the image is processed and the generated encrypted file to the terminal device. According to the processing method, the video server and the terminal device, which are provided by the invention, the static menu image of the video frame is subjected to the fuzzy processing to obtain the fuzzy image and the difference image; the difference image is encrypted; other persons are prevented from directly checking or obtaining a clear image of a video frame image; the effective encryption on a video is realized; the transmission safety of the video is improved.
Owner:ZHONGGUANG REDIANYUN TECH CO LTD
Method for performing national secret encryption by using RDMA PSN
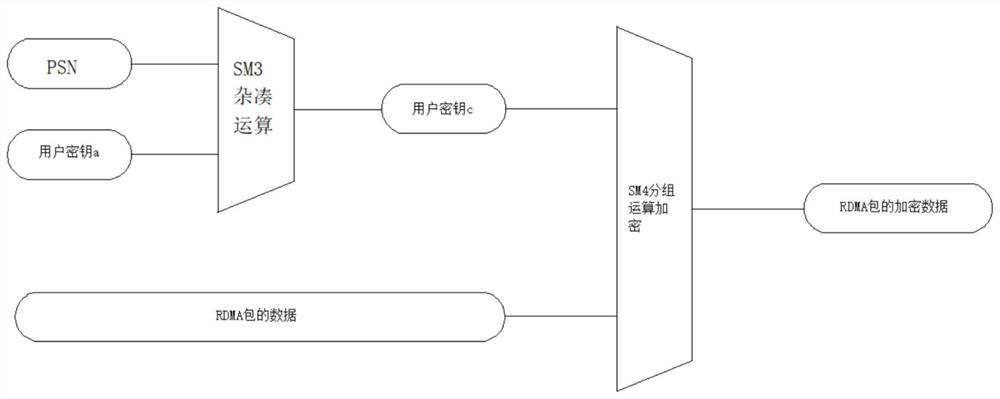
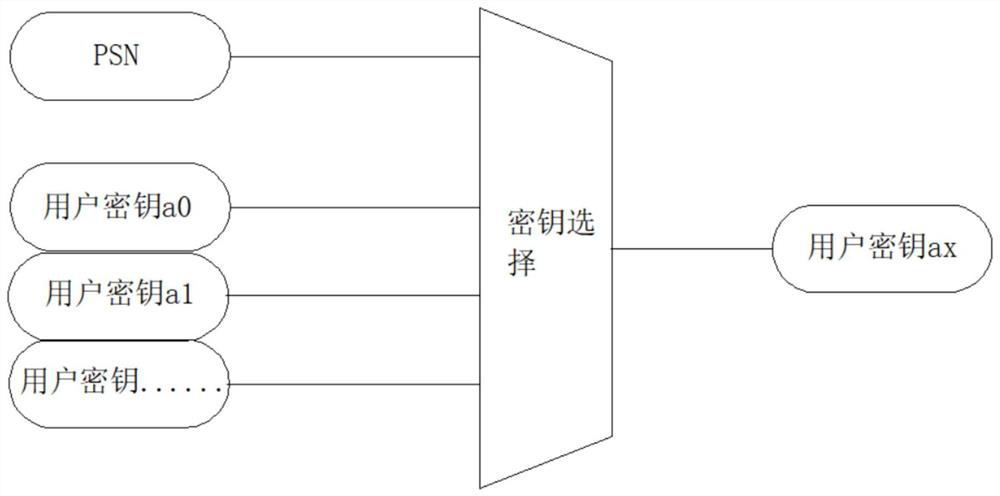
PendingCN113542234AEncryption is validGood data protectionKey distribution for secure communicationConfidentialityPassword
The invention relates to the field related to data security, in particular to a method for performing national secret encryption by using RDMA PSN, which comprises an encryption step and a decryption step, and comprises the following steps of: encrypting a data part in RDMA by using SM4, superposing the PSN and a KEY_A of the RDMA, and obtaining a key encryption key KEYB by using a low 128 bit of an SM3 password hash operation result, thereby effectively encrypting the data in the RDMA; meanwhile, when the user needs to switch the key KEYA, assigning which PSN starts to use a new key KEYA at the same time, so that the effect of switching the key without interrupting transmission is achieved, data are better protected, the key can be circularly and automatically switched according to the PSN, the data are better protected, and the confidentiality is improved.
Owner:上海芯易恒联科技有限公司
Data secret keeping method
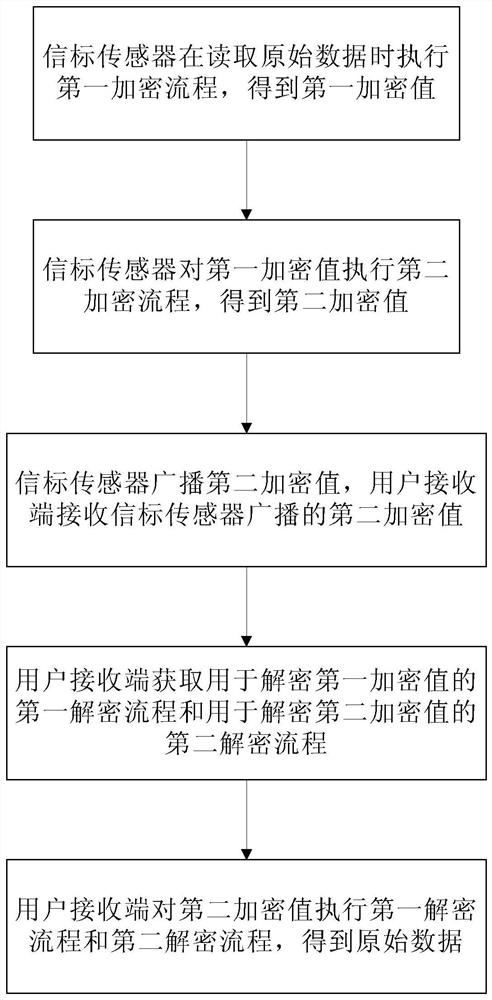
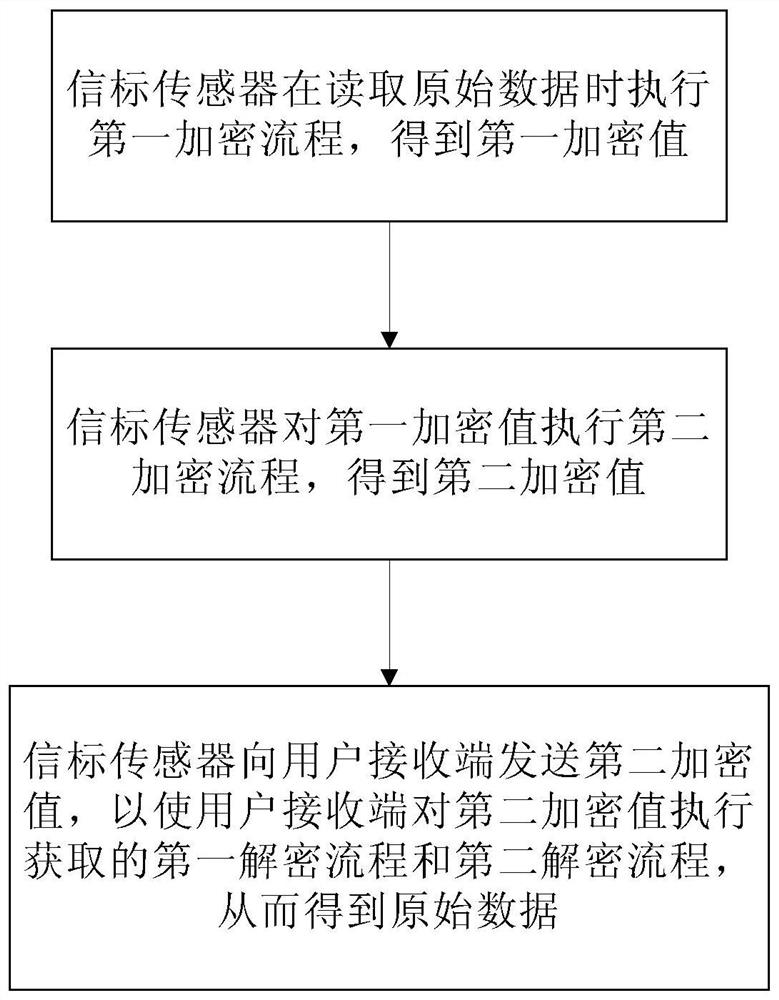
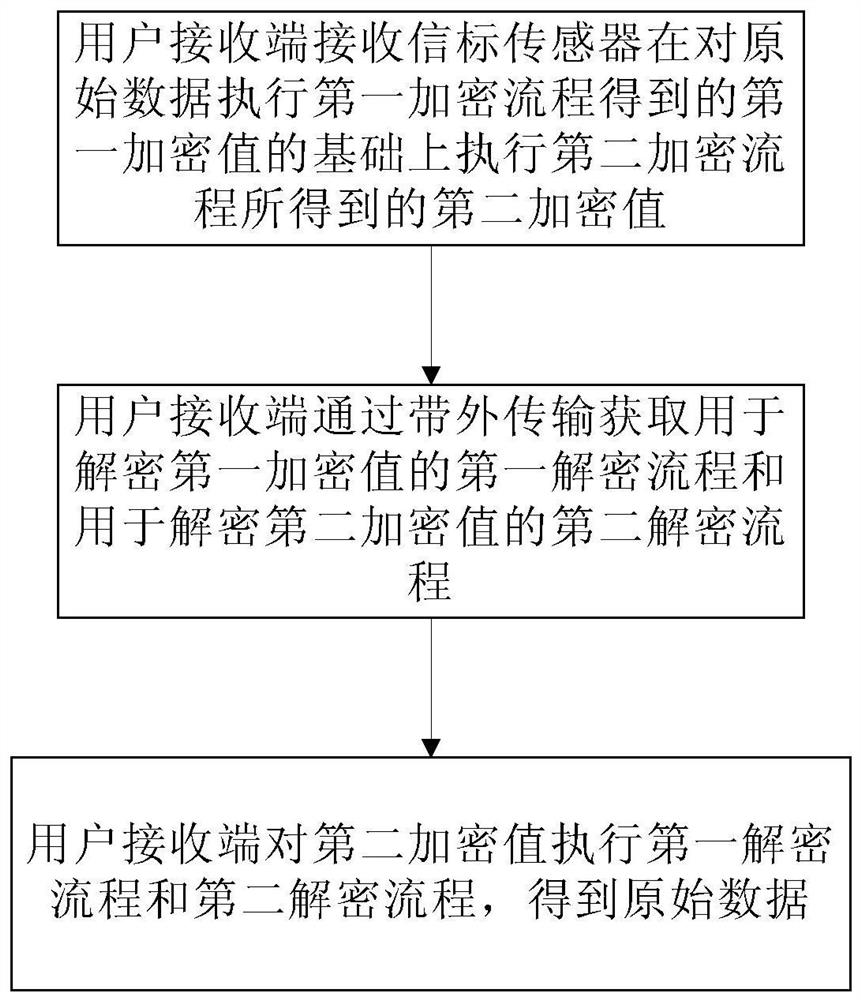
ActiveCN114051240AEncryption is validImprove communication securityParticular environment based servicesBroadcast service distributionCommunications securityOriginal data
According to a data secret keeping method, original data are encrypted through simple hardware and a low-energy-consumption encryption mode, and a decryption process is obtained from a cloud end through out-of-band transmission, so that other terminals cannot interpret the original data even if intercepting broadcasted data, and effective encryption of one-way communication data of a beacon sensor is realized; the communication security of the beacon sensor is improved on the premise that no extra hardware is needed and no power consumption needs to be improved.
Owner:HI P SHANGHAI HOUSING APPLIANCE
Data encrypting method, data encrypting device, data deciphering method and data deciphering device
ActiveCN103020537BEncryption is reliableEncrypted securityRecord information storageDigital data protectionFile systemData decryption
Owner:TENCENT CLOUD COMPUTING BEIJING CO LTD
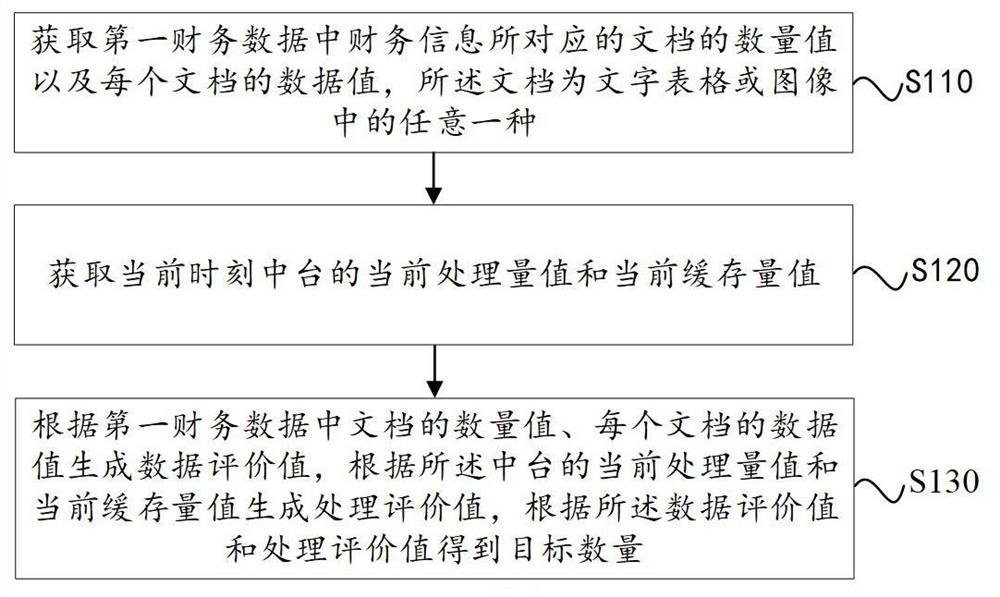
Smart Shared Financial Platform and System Based on Hash Encryption Algorithm and Quantum Key
The invention provides an intelligent sharing financial platform and system based on a hash encryption algorithm and a quantum key, comprising: a middle station receives first financial data sent by a data sending terminal, and selects a corresponding financial data according to the type information of the first financial data The first hash encryption algorithm calculates the first financial data to obtain the first hash value; the middle station receives the quantum encryption public key sent by the quantum server, and encrypts the first financial data according to the quantum encryption public key to obtain For the second financial data, calculate the second financial data according to the second hash encryption algorithm to obtain a second hash value; the middle station combines the first hash value and the second hash value to obtain a first combined hash value value, the middle station calls the third hash encryption algorithm to calculate the first combined hash value to obtain the third hash value; the middle station calculates the third hash value according to the first hash value, the second hash value and the third hash value; A hash table is generated from the value, and the hash table and the second financial data are sent to the data receiving end.
Owner:STATE GRID ZHEJIANG ELECTRIC POWER
Optical Image Encryption Method for Computational Ghost Imaging Using Phase Iterative Algorithm
ActiveCN110348232BReduce in quantityEasy to storeDigital data protectionSpatial light modulatorGhost imaging
The invention discloses an optical image encryption method for calculating ghost imaging by using a phase iterative algorithm, which comprises the following steps of: 1) performing collimation illumination on a laser beam, and sequentially inputting a group of different random phase masks into a spatial light modulator; wherein the wave is modulated by a pure phase mask, and the generated random speckle pattern passes through the object at the axial distance from the plane of the spatial light modulator; 2) wherein a transmission function T ([mu]m, v) of the object, Ii ([mu]m, v) = | Ei ([mu]m, v) | 2 being a speckle pattern, Ei ([mu]m, v) being a free space propagation field of the pure phase mask and (mu, v) representing lateral coordinates of the object plane; performing, for each purephase mask embedded in the spatial light modulator, by using Fresnel diffraction; and 3) correlating the intensity distribution collected by the barrel detector with the speckle pattern derived from the known pure phase mask. The method provided by the invention is simple and easy to implement and high in accuracy.
Owner:XIAN UNIV OF TECH
Image encryption method and device
ActiveCN107770405BEncryption is validImplement compression processingEncryption apparatus with shift registers/memoriesSecuring communication by chaotic signalsHash functionComputer vision
The invention provides an image encryption method and device. The method comprises the following steps: acquiring a Hash function value of a plaintext image, and acquiring a first key corresponding tothe plaintext image according to the Hash function value; performing sparse transformation processing on the plaintext image to obtain a discrete matrix corresponding to the plaintext image; performing scrambling processing on the discrete matrix through the first key to obtain a scrambled intermediate matrix, wherein the intermediate matrix corresponds to the scrambled plaintext image; and measuring the intermediate matrix by means of half-tensor compressed sensing, and outputting a first encrypted matrix, wherein the first encrypted matrix corresponds to the compressed and encrypted plaintext image. Through adoption of the method provided by the invention, the storage and transmission amounts of image data during transmission are reduced effectively.
Owner:BEIJING UNIV OF POSTS & TELECOMM
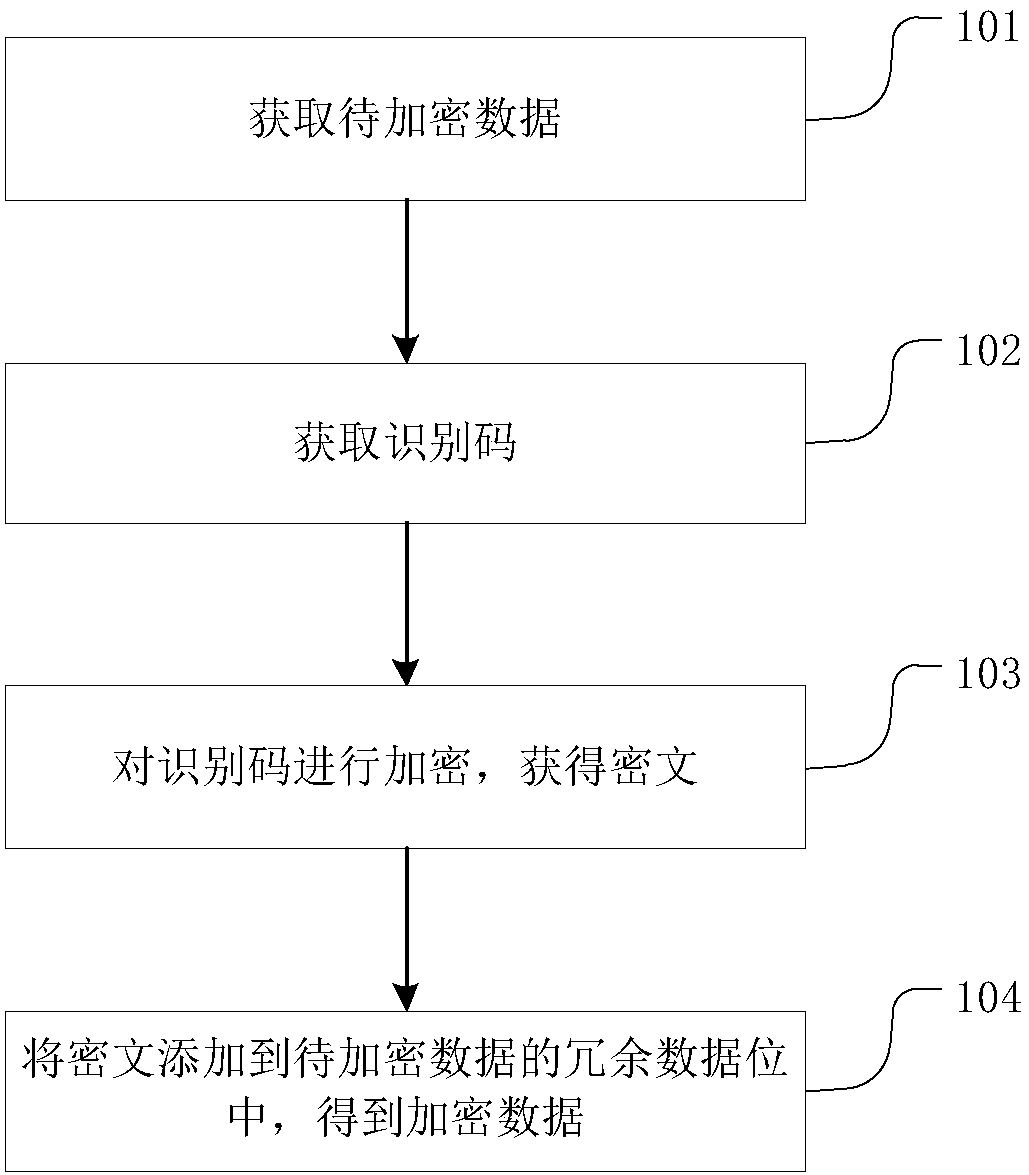
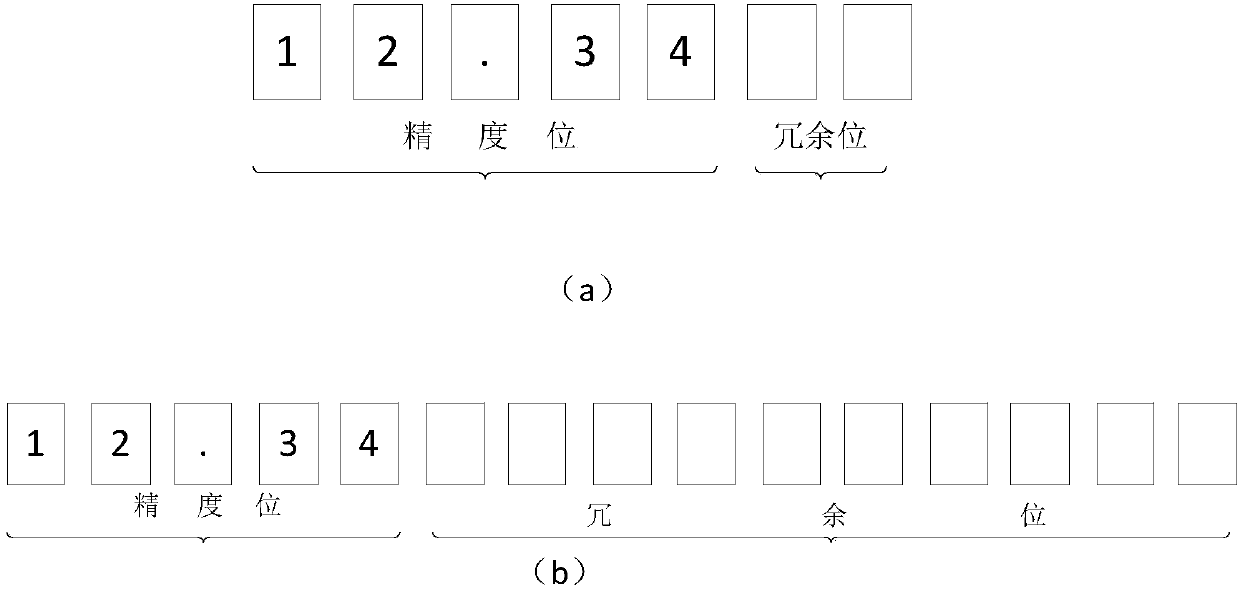
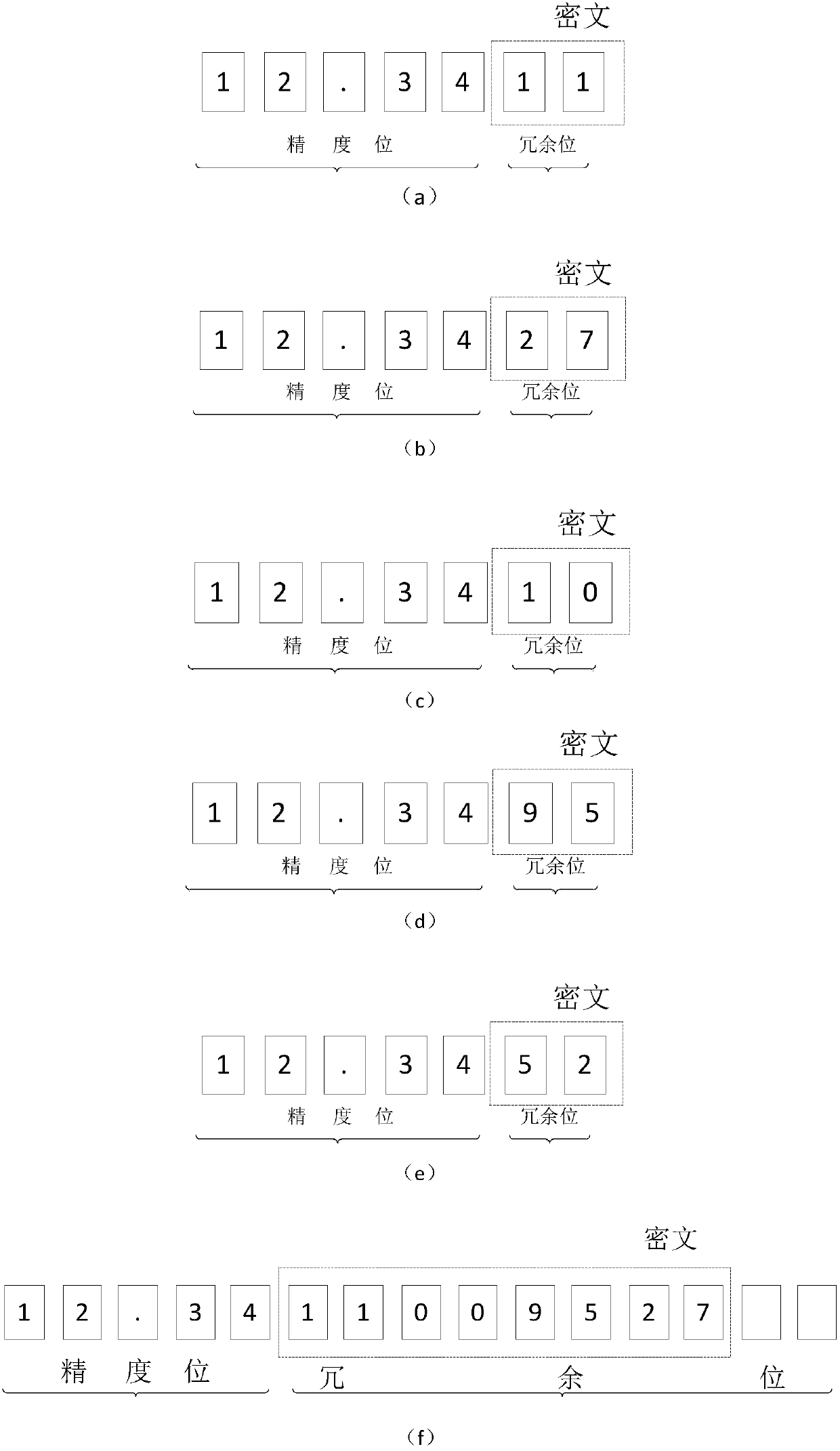
Data redundancy encryption method and device, redundancy encryption data identification method and device and storage medium
InactiveCN110321718AEncryption is validAccuracy is not affectedDigital data protectionProgram/content distribution protectionComputer hardwareCiphertext
The invention belongs to the technical field of information security, and relates to a data redundancy encryption method, a redundancy encryption data identification method and device, and a storage medium. The data encryption method comprises the following steps: acquiring to-be-encrypted data; obtaining an identification code; encrypting the identification code to obtain a ciphertext; and addingthe ciphertext into the redundant data bit of the to-be-encrypted data to obtain encrypted data. In addition, the invention also provides a method for identifying the data obtained by the encryptionmethod. Through the data encryption and identification method provided by the invention, piracy can be effectively prevented; meanwhile, evidence obtaining and right protection after the data is stolen are also facilitated; in addition, the data encryption bit is located on the invalid bit of the data, so that the data precision is not influenced.
Owner:BEIJING LINKING MEDICAL TECH CO LTD
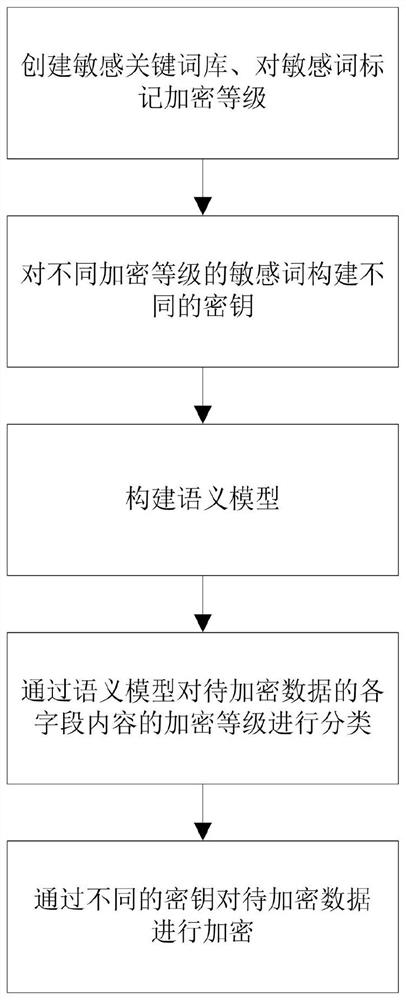
Data encryption method and device for different sensitive fields
PendingCN114139185APrevent leakageEncryption is validRandom number generatorsDigital data protectionTheoretical computer scienceEngineering
The invention relates to a data encryption method and device for different sensitive fields, and the method comprises the steps: (1) creating a local sensitive keyword library, and marking encryption levels for sensitive words in the local sensitive keyword library; step (2), constructing different secret keys for sensitive words with different encryption levels in the local sensitive keyword library; step (3): receiving to-be-encrypted data, and classifying encryption levels of each field content of the to-be-encrypted data through the trained semantic model to obtain a classification result; and step (4), according to the classification result, encrypting the to-be-encrypted data through the different keys. According to the invention, data can be effectively encrypted, and data privacy leakage is prevented.
Owner:上海健交科技服务有限责任公司
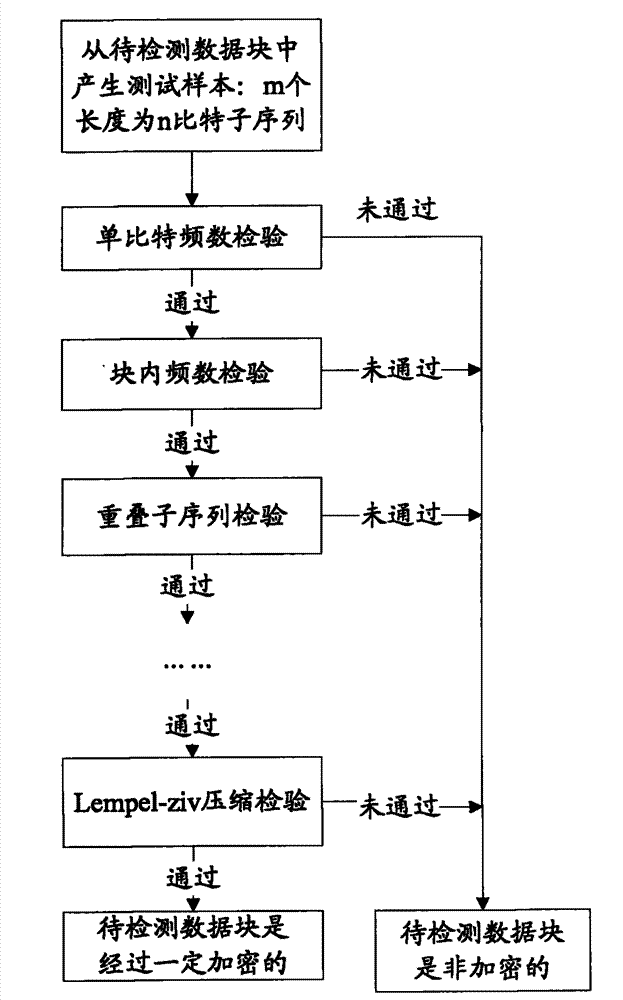
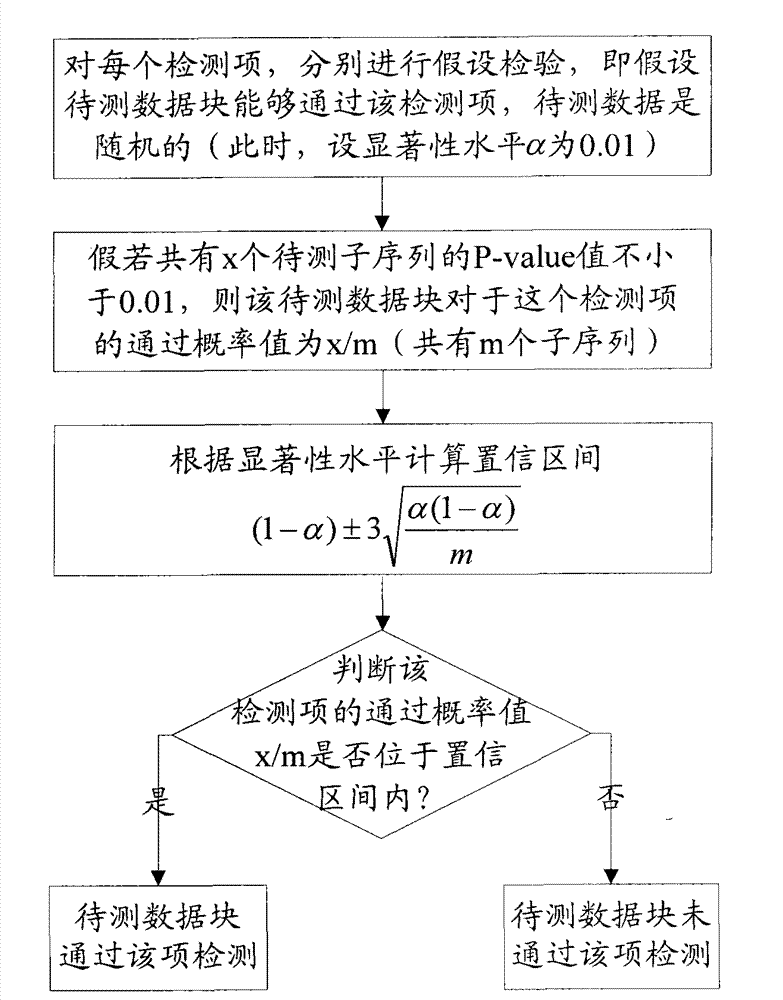
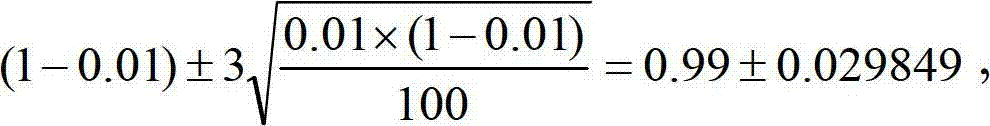
Randomness analysis-based data encryption function detection method
InactiveCN101888282BNovel methodEncryption is validError preventionEncryption apparatus with shift registers/memoriesComputer scienceData sequences
The invention discloses a randomness analysis-based data encryption function detection method, which comprises the following steps of: (1) generating a detection sequence: dividing a data sequence to be detected into a plurality of data subsequences to be detected according to the set conditions; (2) executing randomness detection: aiming at each item in 16 items of 8 classes of a randomness testmethod, and respectively performing randomness detection on the plurality of data subsequences to be detected; and (3) analyzing detection results: in the process of executing all detection items, ifany data subsequence does not pass any item of the randomness detection, judging that the data sequence to be detected is a nonrandom sequence, namely the data to be detected is not encrypted, and ifthe data subsequences pass the detection of all detection items, judging that the data to be detected has been subjected to a certain degree of encryption processing. The randomness analysis-based data encryption function detection method has the advantages that the test method is novel, and test angles are comprehensive and cover a plurality of aspects of the data sequence randomness; and the statistic test principle is adopted for detection, so the operation is simple and convenient and that whether the data is encrypted in an information system can be effectively and accurately judged.
Owner:BEIJING UNIV OF POSTS & TELECOMM
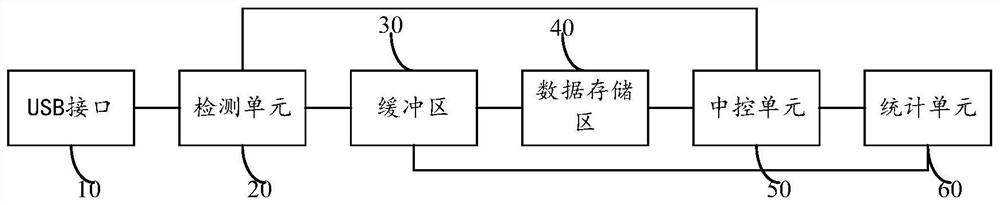
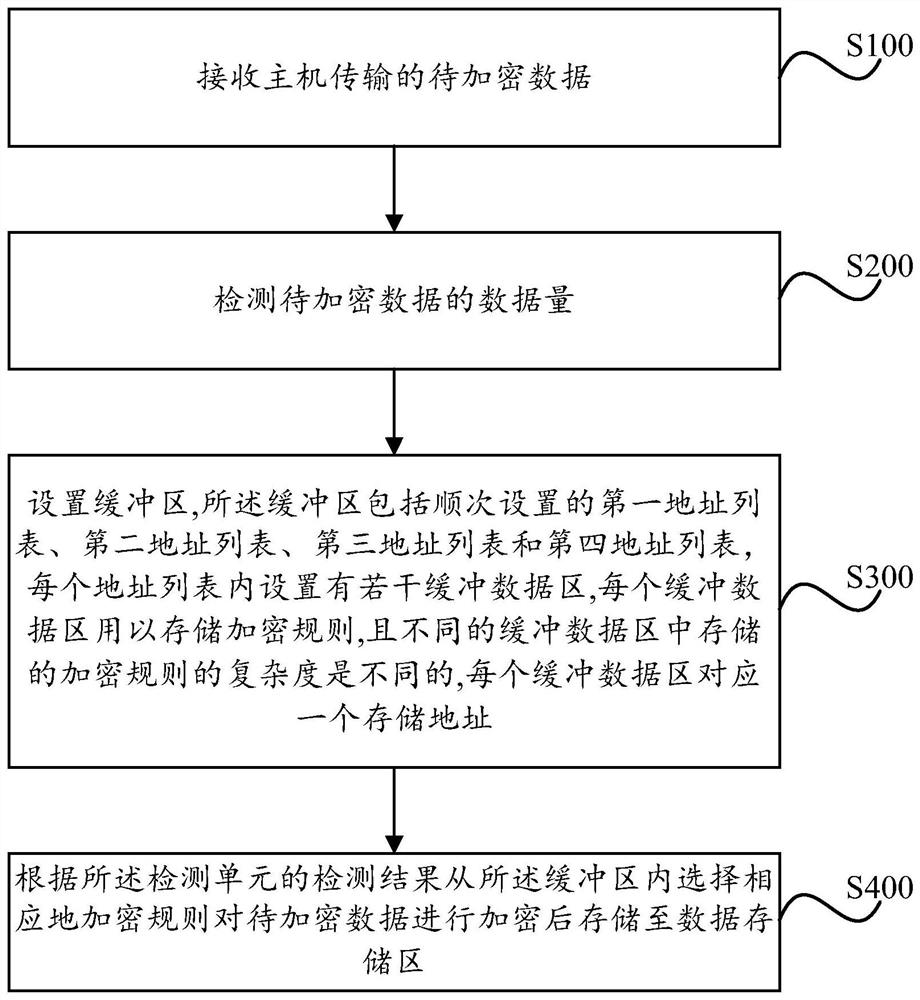
Encrypted U disk and authorization method
ActiveCN113420339BEncrypted intelligenceAvoid exposureDigital data protectionInternal/peripheral component protectionStorage securityEngineering
The invention relates to an encrypted U disk and an authorization method, wherein the encrypted U disk includes a USB interface for receiving data to be encrypted transmitted by a host; a detection unit for detecting the amount of data to be encrypted; a buffer, the buffer includes a The first address list, the second address list, the third address list and the fourth address list set up next time, the data storage area is used to store the encrypted data; the central control unit is connected with the detection unit, the buffer and the data respectively The storage areas are respectively connected to select corresponding encryption rules from the buffer area according to the detection results of the detection unit, encrypt the data to be encrypted and store it in the data storage area. By partitioning the addresses in the cache area, the encryption rules in different address partitions are selected according to the actual data volume to encrypt the data to be encrypted, making the data encryption more intelligent, and realizing the storage speed and speed of data storage. Storage security is double guaranteed.
Owner:广东全芯半导体有限公司
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com