Multibit forensic watermark with encrypted detection key
A multi-bit, watermarking technology, applied in watermark detectors and computer-readable codes, extracting multi-bit watermarks, detecting keys, and watermark embedders, can solve problems such as leakage and detection of key theft, and achieve less investment. , high-throughput, performance-enhancing effects
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
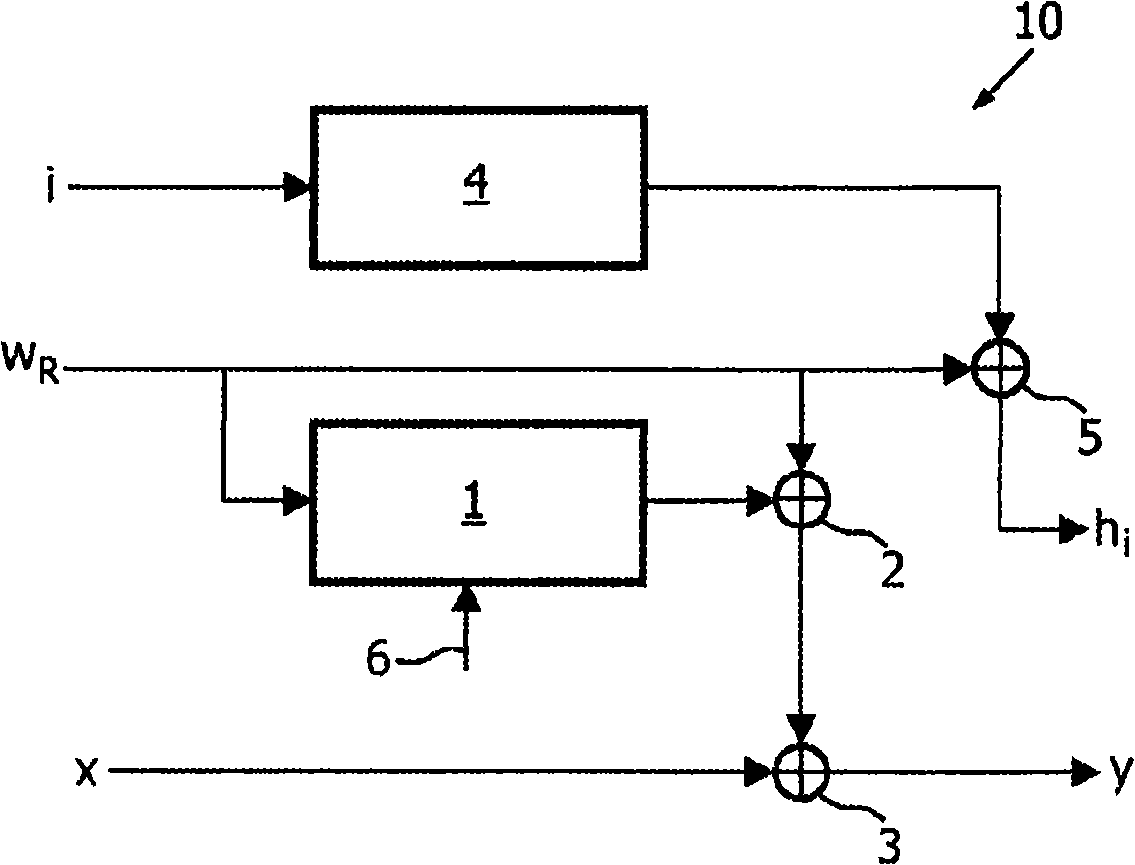
[0045] figure 1 A strategy 10 for embedding auxiliary data (shown here as a multi-bit payload) into the main signal x according to an embodiment of the invention is schematically shown. The input to the embedding process consists of the identification number i, the reference watermark w R and the main signal x. In one embodiment, the embedding of the auxiliary data may be performed at one or more computer systems, as a watermark embedder or encoder, for example at a computer system located at the content owner. The output of the embedding process includes the encryption key h i and the watermarked signal y. The encryption key is then distributed to users or clients either together with or separately from the watermarked signal y.
[0046] A master signal may be a signal to be distributed to clients or users of the signal. The signal may be distributed via a computer network, via an Electronic Content Distribution (ECD) application, via a record carrier such as a recordabl...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com