Data redundancy encryption method and device, redundancy encryption data identification method and device and storage medium
An encryption method and data redundancy technology, applied in the field of information security, can solve problems such as the difficulty for data owners to prove the source of stolen data, the difficulty of data forensics, and the inability to track the source of data to be encrypted, so as to facilitate proof and rights protection, prevent The effect of piracy
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
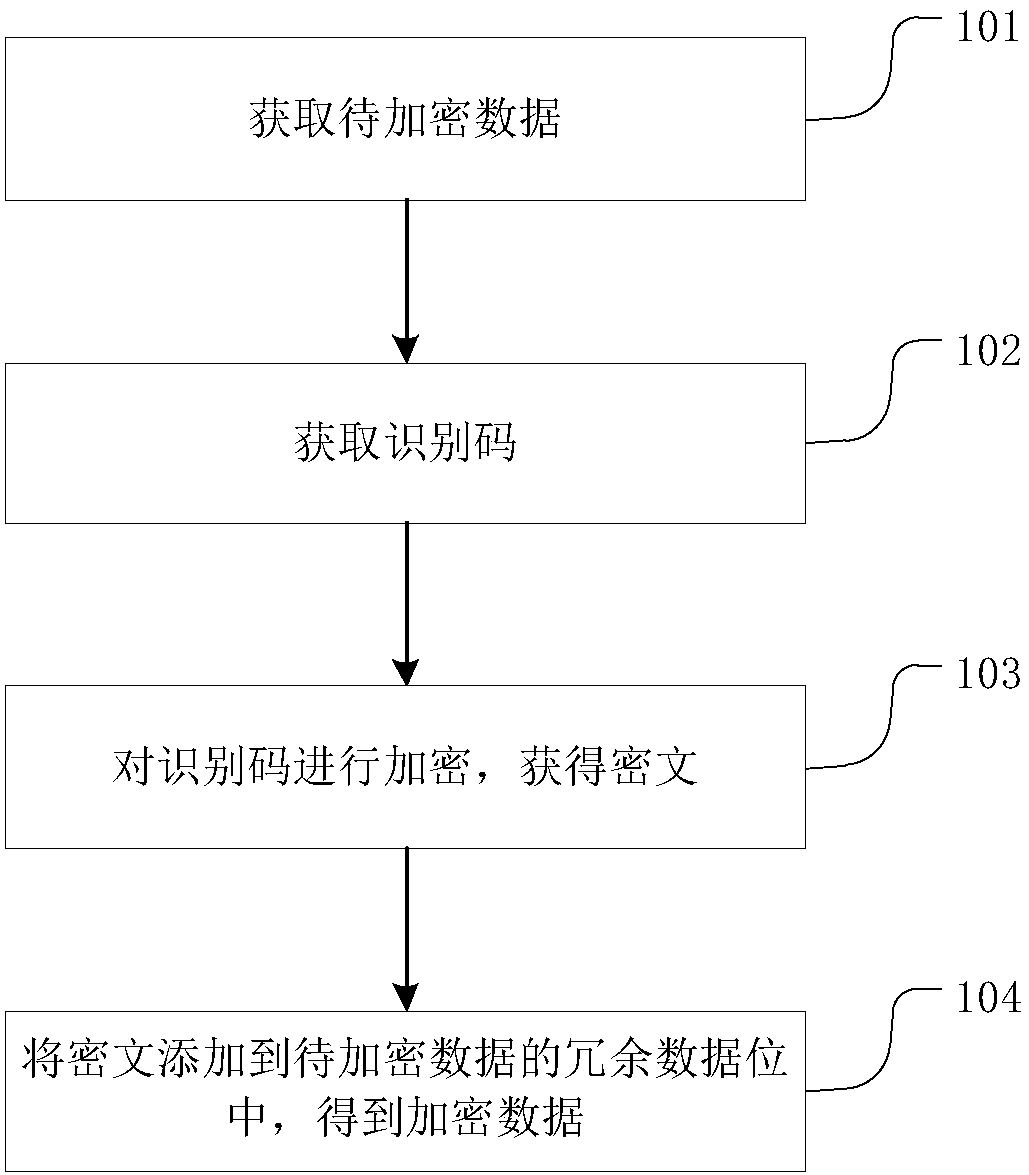
[0058] refer to figure 1 , a data redundancy encryption method suitable for execution in a computing device, comprising the following steps:
[0059] Obtain the data to be encrypted 101;
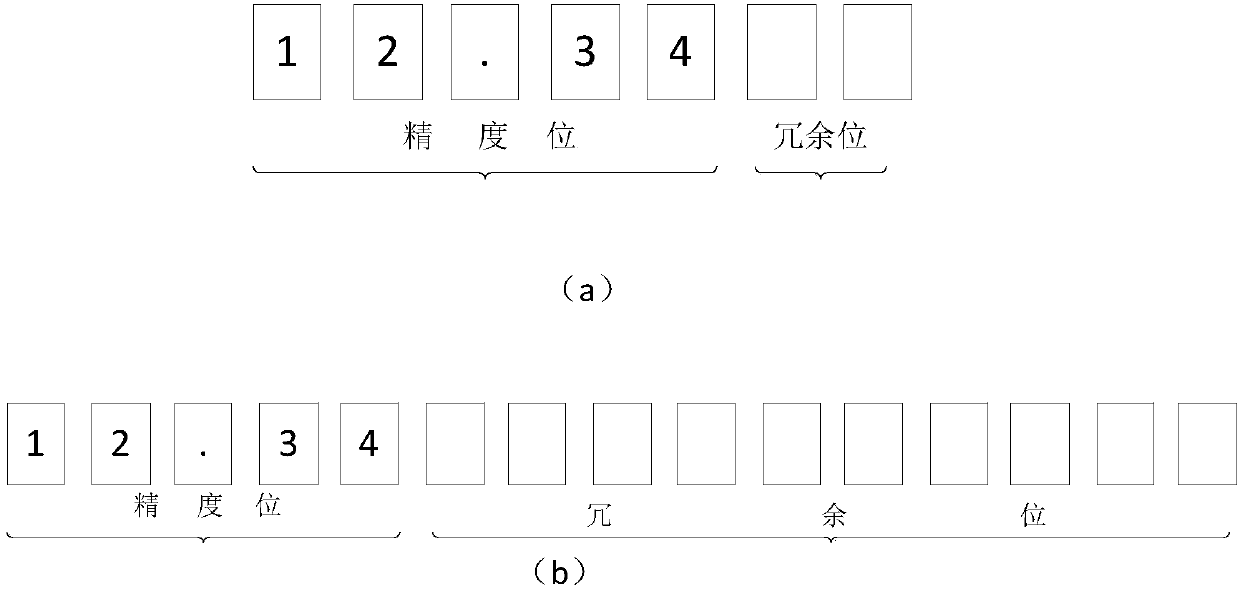
[0060] In a preferred embodiment of the present invention, when the data to be encrypted contains non-digital data, the non-digital data can be converted into digital data by standard ASCII codes, and then encrypted; those skilled in the art should understand that the encrypted The data in a database can be a single piece of data, or several pieces of data or some or all of the data in the database.
[0061] Obtain the identification code 102;
[0062] Wherein the identification code is a combination of numbers or a random number with an identification function. Wherein, the random numbers in this embodiment are pseudo-random numbers or quasi-random numbers. Therefore, the random number of the present invention can be reproduced by combining the random seed and the method of generating t...
Embodiment 2
[0079] An embodiment of the present invention also provides a computing device, including:
[0080] one or more processors;
[0081] storage; and
[0082] One or more programs, wherein the one or more programs are stored in said memory and configured to be executed by one or more processors, the one or more programs include instructions for a data redundancy encryption method, the method comprising Follow the steps below:
[0083] (1) Obtain the data to be encrypted;
[0084] (2) Obtain the identification code;
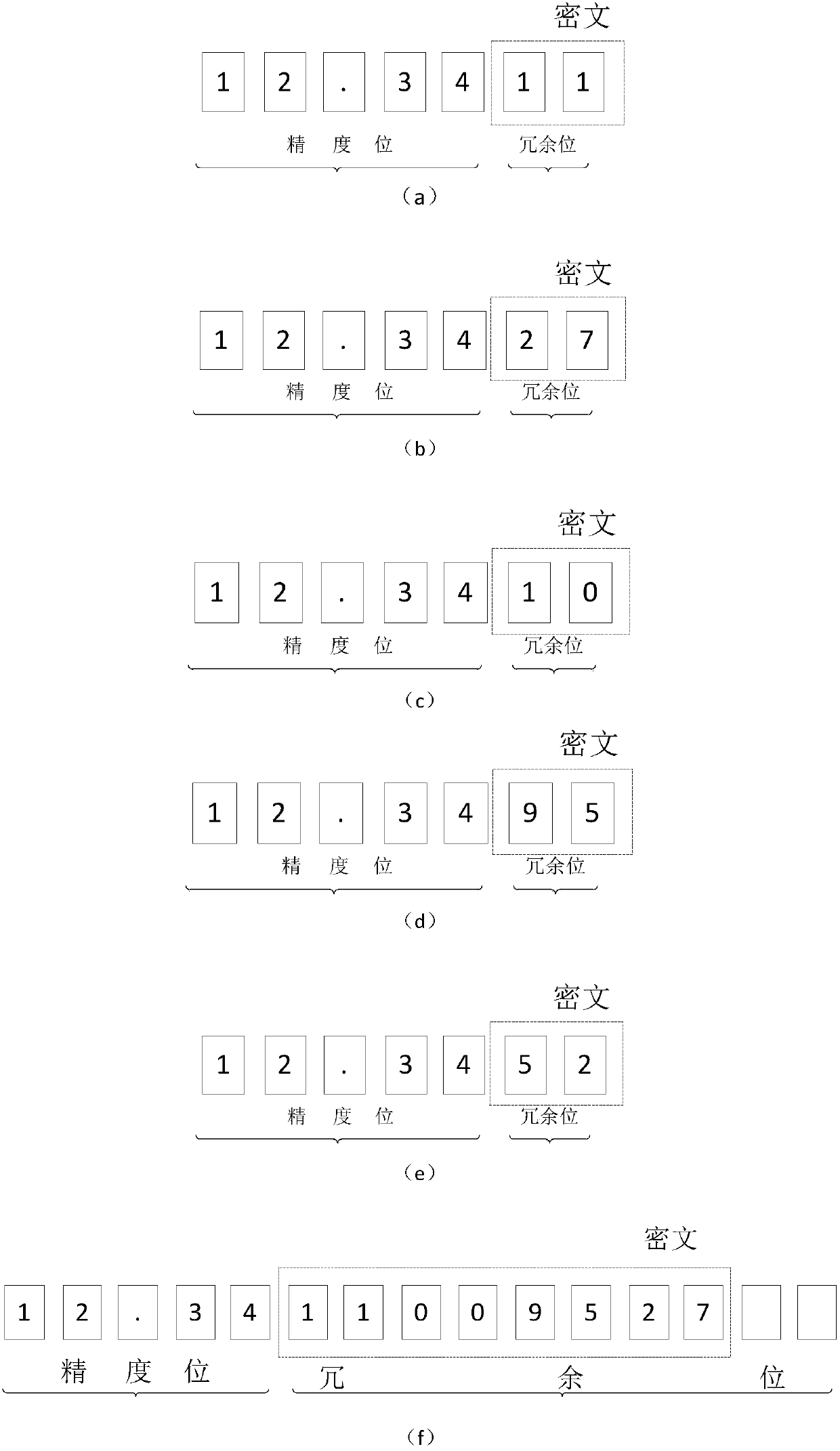
[0085] (3) Encrypt the identification code to obtain the ciphertext;
[0086] (4) Add the ciphertext to the redundant data bits of the data to be encrypted to obtain the encrypted data.
[0087] Depending on the desired configuration, a processor may be any type of processing including, but not limited to, a microprocessor (μP), microcontroller (μC), digital information processor (DSP), or any combination thereof. A processor may include one or more levels of ca...
Embodiment 3
[0090] The present invention also provides a computer-readable storage medium storing one or more programs, wherein the one or more programs include instructions, and the instructions are adapted to be loaded by the memory and execute the data redundancy encryption method, the method includes the following step:
[0091] (1) Obtain the data to be encrypted;
[0092] (2) Obtain the identification code;
[0093] (3) Encrypt the identification code to obtain the ciphertext;
[0094] (4) Add the ciphertext to the redundant data bits of the data to be encrypted to obtain the encrypted data.
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com