Optical image encryption method for calculating ghost imaging by using phase iterative algorithm
An iterative algorithm, optical image technology, applied in computing, computer security devices, instruments, etc., can solve the problem of inconvenient storage and transmission, and achieve the effect of convenient storage and transmission of keys, reducing the number, and encrypting grayscale images
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0019] The present invention will be described in detail below in conjunction with the accompanying drawings and specific embodiments.
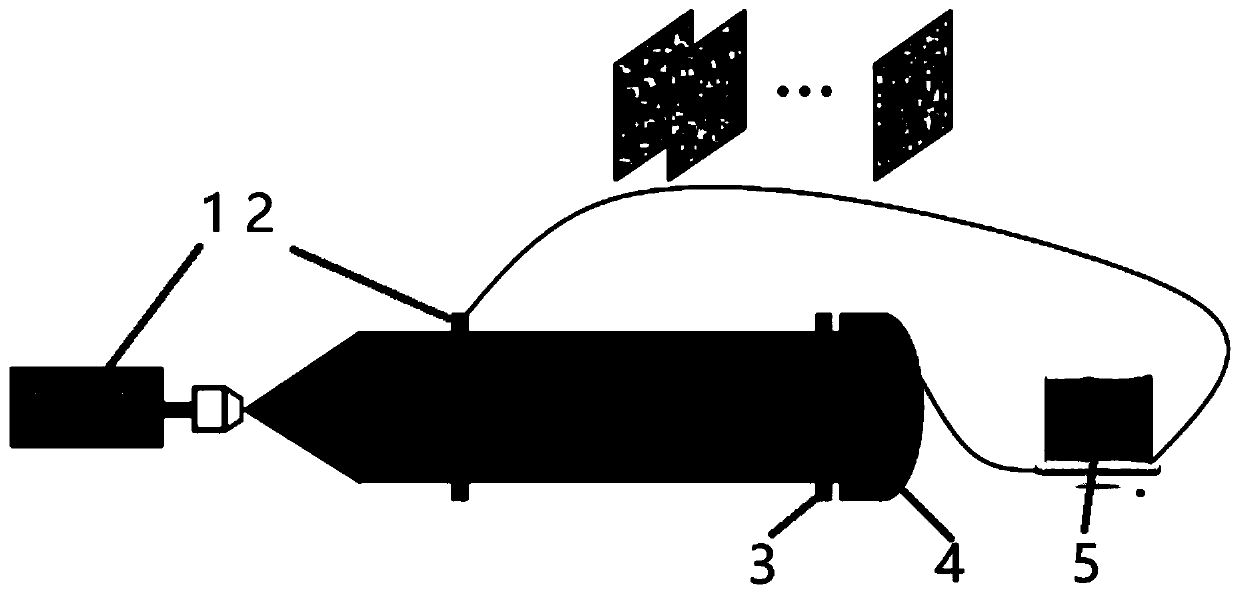
[0020] In order to improve the quality of reconstructed images with fewer measured intensities, the present invention proposes an optical image encryption for high-quality computational ghost imaging using an iterative phase retrieval algorithm, and the corresponding schematic diagram is set as figure 1 As shown, the structure is that a laser 1 , a spatial light modulator 2 , an object 3 , a barrel detector 4 and a controller 5 are placed in sequence along the axis, and the barrel detector 4 communicates with the spatial light modulator 2 through the controller 5 .
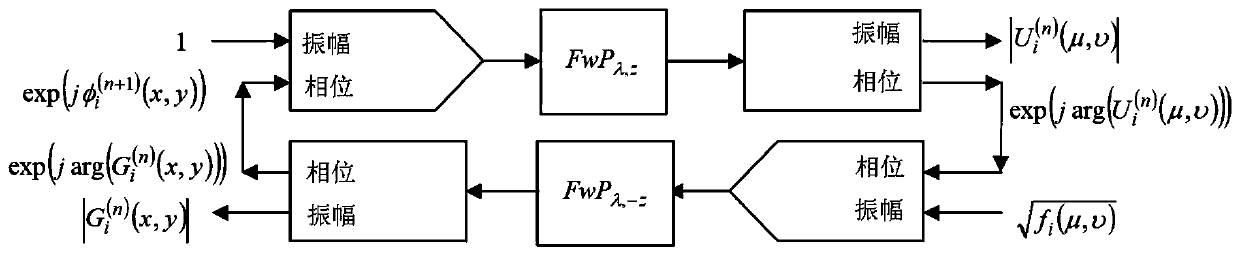
[0021] The method of the present invention adopts the above-mentioned configuration, referring to figure 2 , follow the steps below to implement:
[0022] Step 1: The laser beam is collimated and a set of different random phase masks is sequentially input into the spatial light...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com