Vehicle CAN bus encryption method
A technology of CAN bus and encryption method, which is applied in the direction of bus network, data exchange through path configuration, digital transmission system, etc. It can solve the problems that data cannot be intercepted and the protection ability is not enough to ensure safety, so as to ensure the safety and security of vehicles sex-enhancing effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
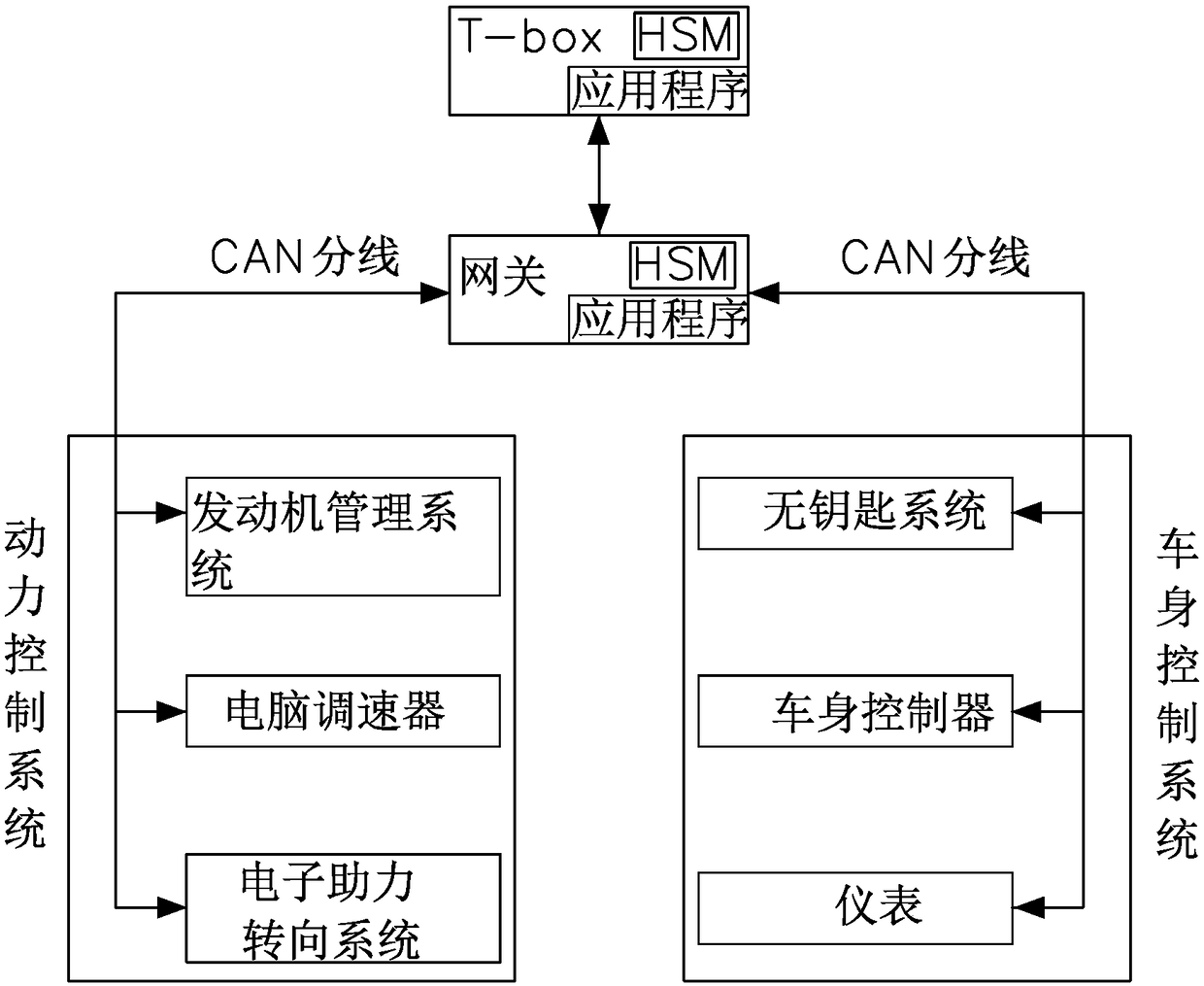
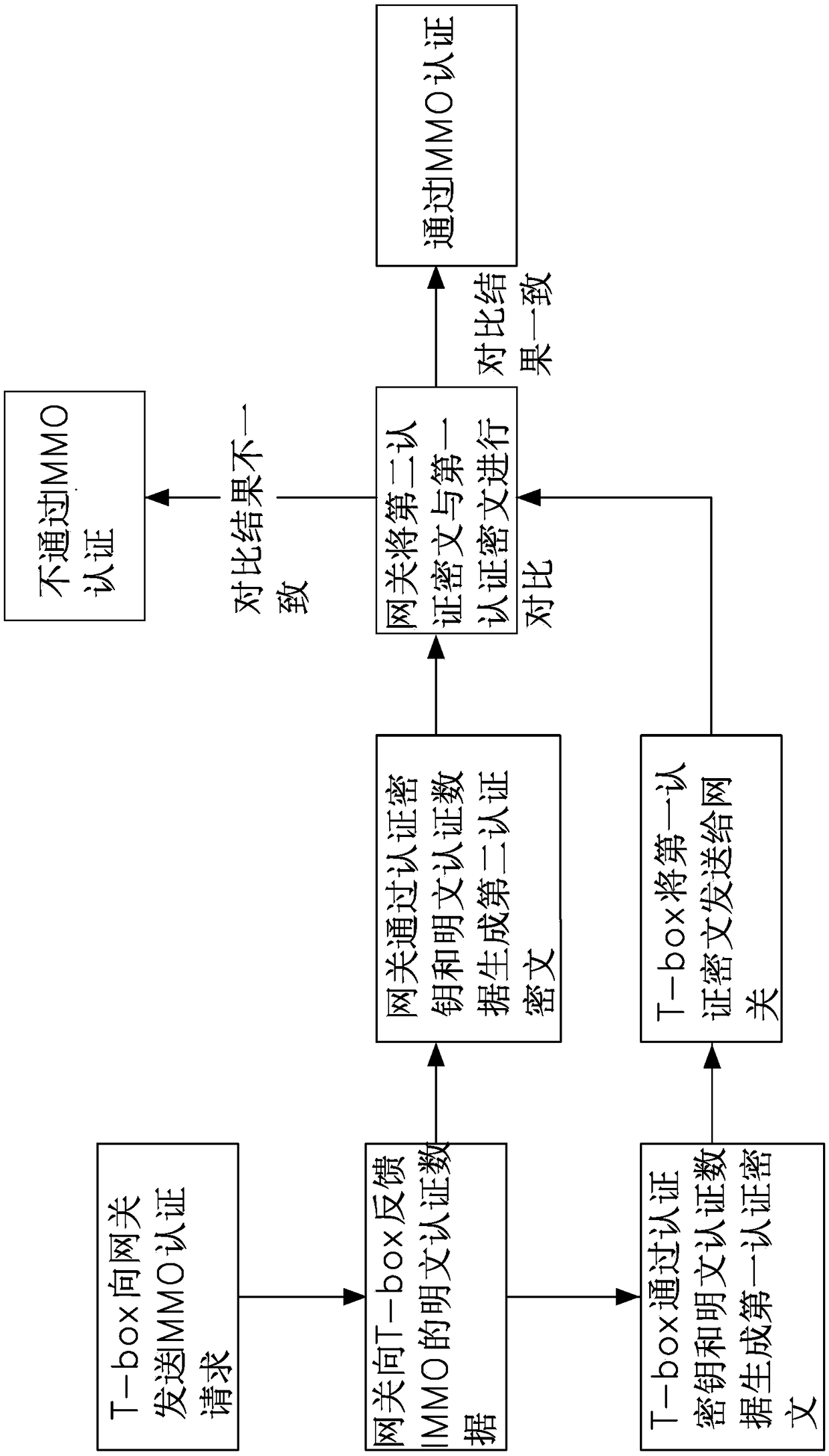
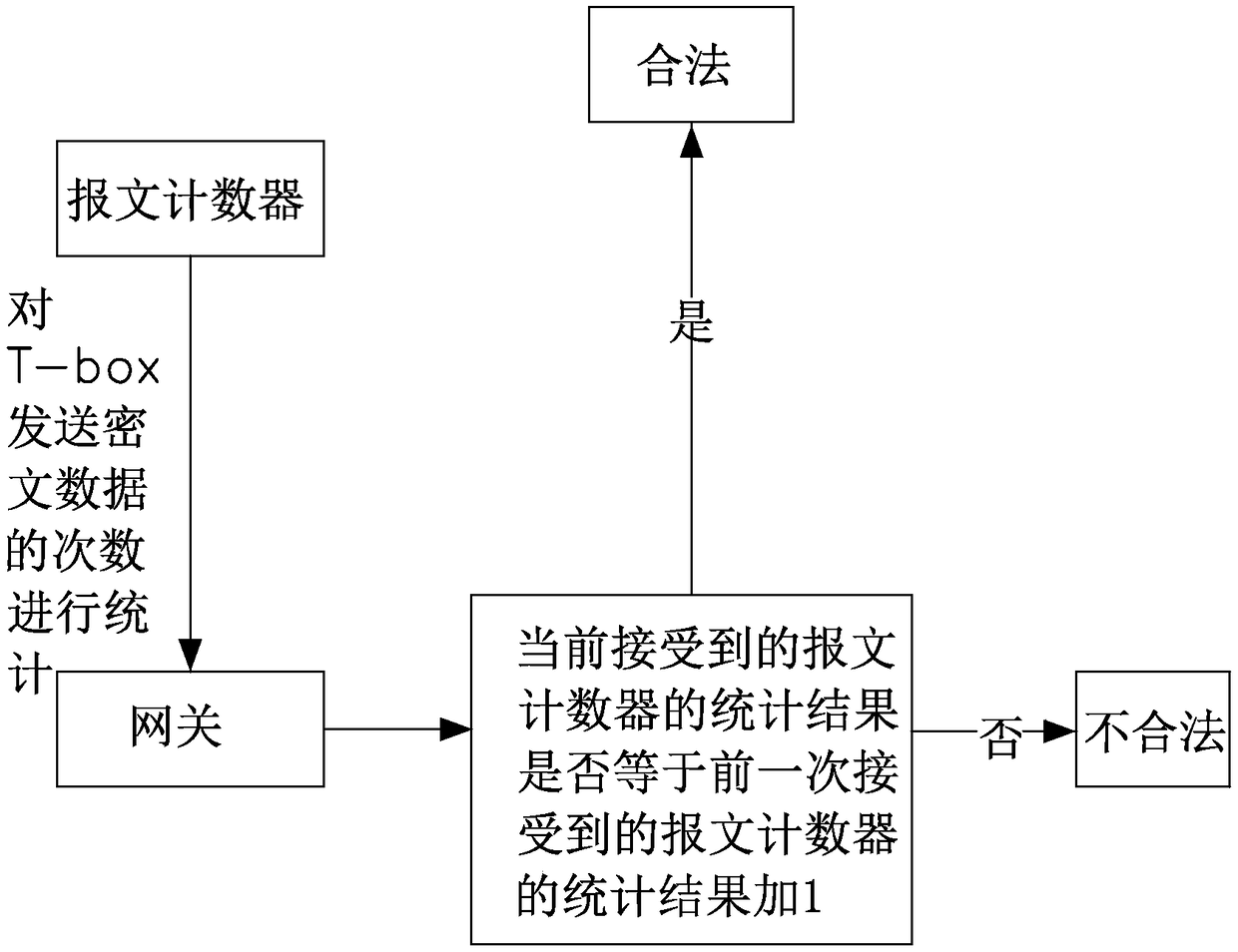
[0026] Please refer to Figure 1 to Figure 3 Shown, the preferred embodiment of a kind of vehicle CAN bus encryption method of the present invention comprises the following steps:
[0027] Step S1, generate the first authentication ciphertext through the T-box, and send the first authentication ciphertext to the gateway; the gateway generates the second authentication ciphertext, and compares the second authentication ciphertext with the first authentication ciphertext, And if the comparison results are consistent, pass the IMMO certification and enter step S2; if not, then fail the IMMO certification and end the process; IMMO certification is the first line of defense for the CAN bus;
[0028] Step S2, generating the plaintext data to be sent through the T-box, encrypting the plaintext data into ciphertext data and sending it to the gateway;
[0029] At the same time, a message counter is set on the T-box. The message counter is a counter with an 8bit capacity. When the T-bo...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com