Data encrypting method, data encrypting device, data deciphering method and data deciphering device
A data encryption and data technology, which is applied in the field of data processing, can solve complex problems, affect system performance, and cumbersome problems, and achieve the effect of effective data encryption
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
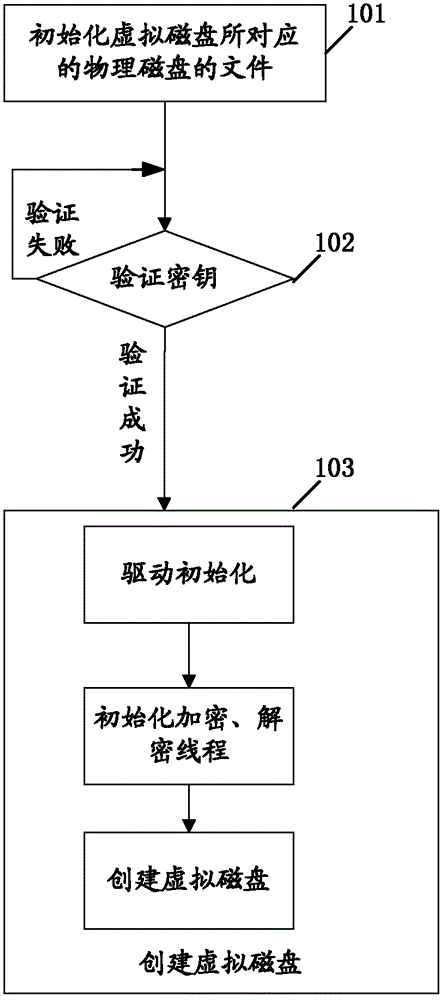
[0051] Embodiment 1 describes the data encryption method based on the virtual disk described above.
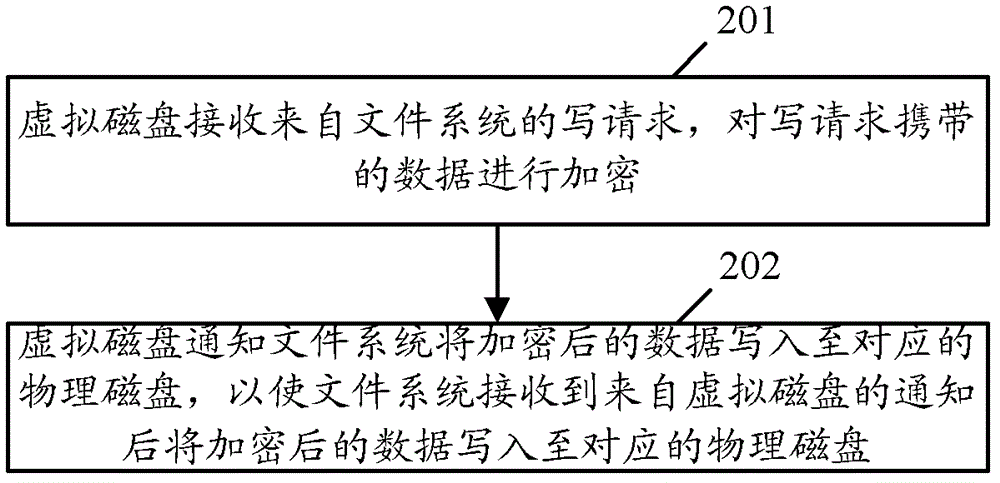
[0052] see figure 2 , figure 2 The basic flowchart provided for Embodiment 1 of the present invention. Such as figure 2 As shown, the process may include the following steps:
[0053] Step 201, the virtual disk receives a write request from the file system, and encrypts the data carried in the write request.
[0054] Step 202, the virtual disk notifies the file system to write the encrypted data to the corresponding physical disk, so that the file system writes the encrypted data to the corresponding physical disk after receiving the notification from the virtual disk.
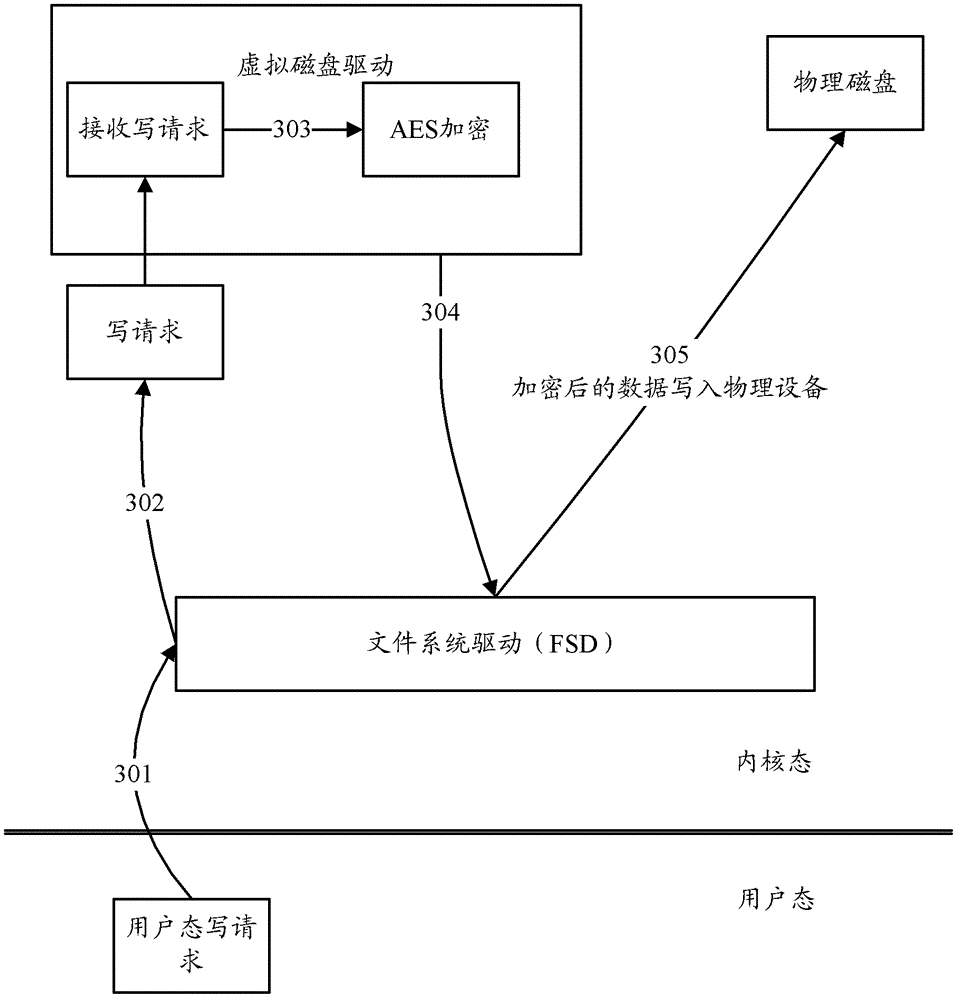
[0055] To make figure 2 The flow shown is more clear, and the following passes image 3 right figure 2 The flow shown is described in detail:
[0056] see image 3 , image 3 The detailed flowchart provided for Embodiment 1 of the present invention. Such as image 3 As shown, the process may inc...
Embodiment 2
[0089] Embodiment 2 is described below:
[0090] Example 2:
[0091] Embodiment 2 describes the data encryption method based on the virtual disk described above.
[0092] see Figure 5 , Figure 5 The basic flowchart provided for Embodiment 2 of the present invention. Such as Figure 5 As shown, the process may include the following steps:
[0093] Step 501, the virtual disk redirects the received read request from the file system to the physical disk, so that the file system obtains the data requested by the read request from the physical disk.
[0094] Step 502, the virtual disk receives the data acquired by the file system from the physical disk, decrypts the received data, sends the decrypted data to the file system, and the file system provides the decrypted data to the client.
[0095] To make Figure 5 The flow shown is more clear, and the following passes Figure 6 right Figure 5 The flow shown is described in detail:
[0096] see Figure 6 , Figure 6 The...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com