Component method for encrypting data safety conveying channel
A transmission channel and encrypted data technology, applied in the direction of digital data protection, electronic digital data processing, computer security devices, etc., can solve the problems of data encryption function and countermeasures
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0064] A component method for encrypted data security transmission channel, the steps of which are as follows:
[0065] (1) Decryption stage 1;
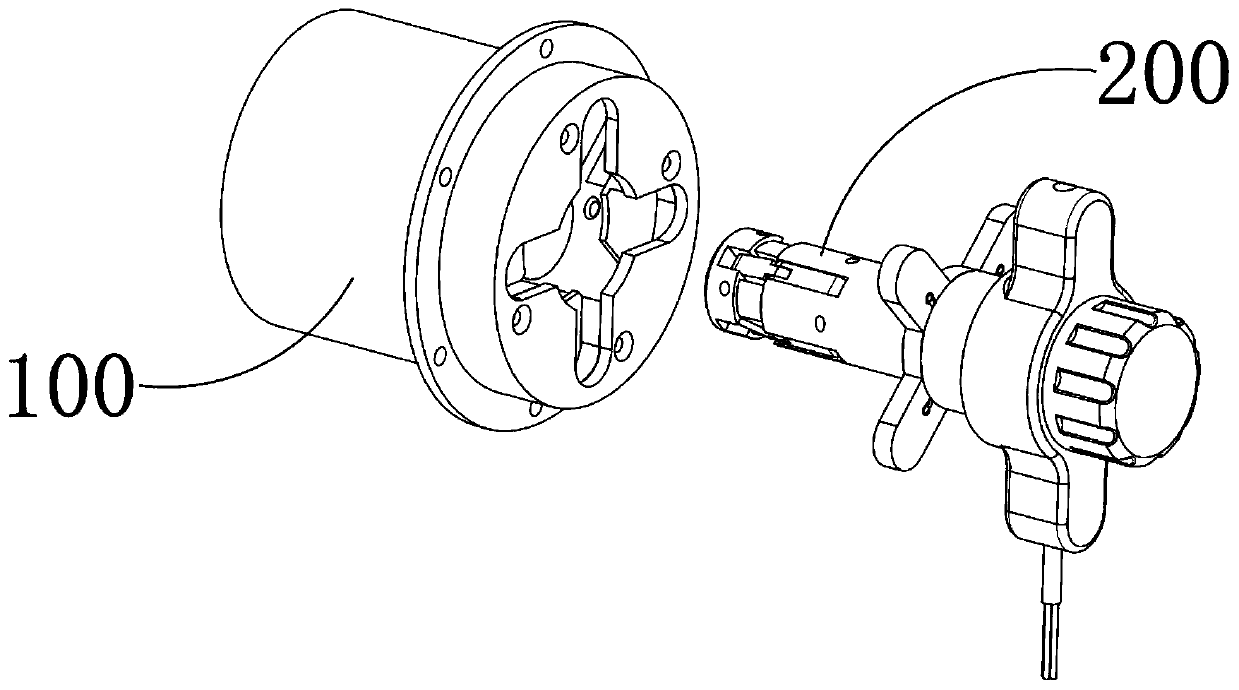
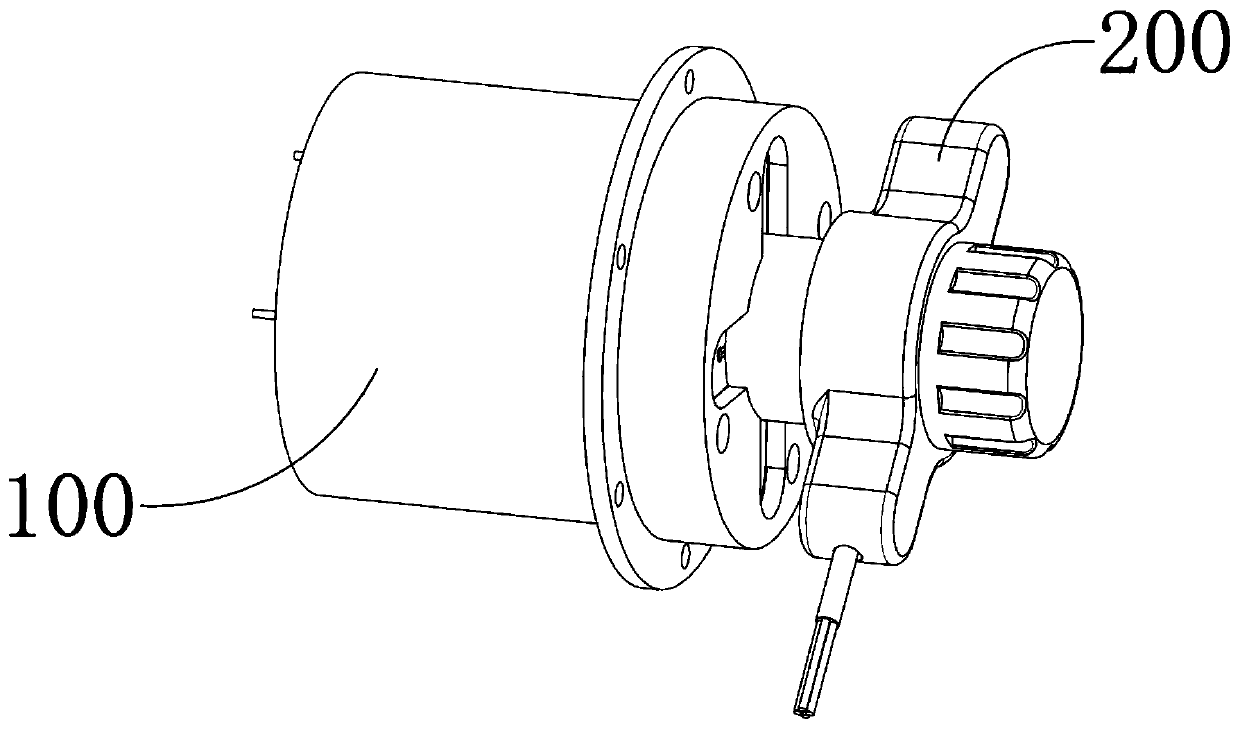
[0066] S1: In the process of encrypted data transmission, the plug-in device 200 is inserted into the installation cylinder 110 along the socket 117, the decryption mechanism 1 210 in the plug-in device 200 matches the encryption mechanism 120, and the encryption mechanism 120 decrypts and internally conduction;
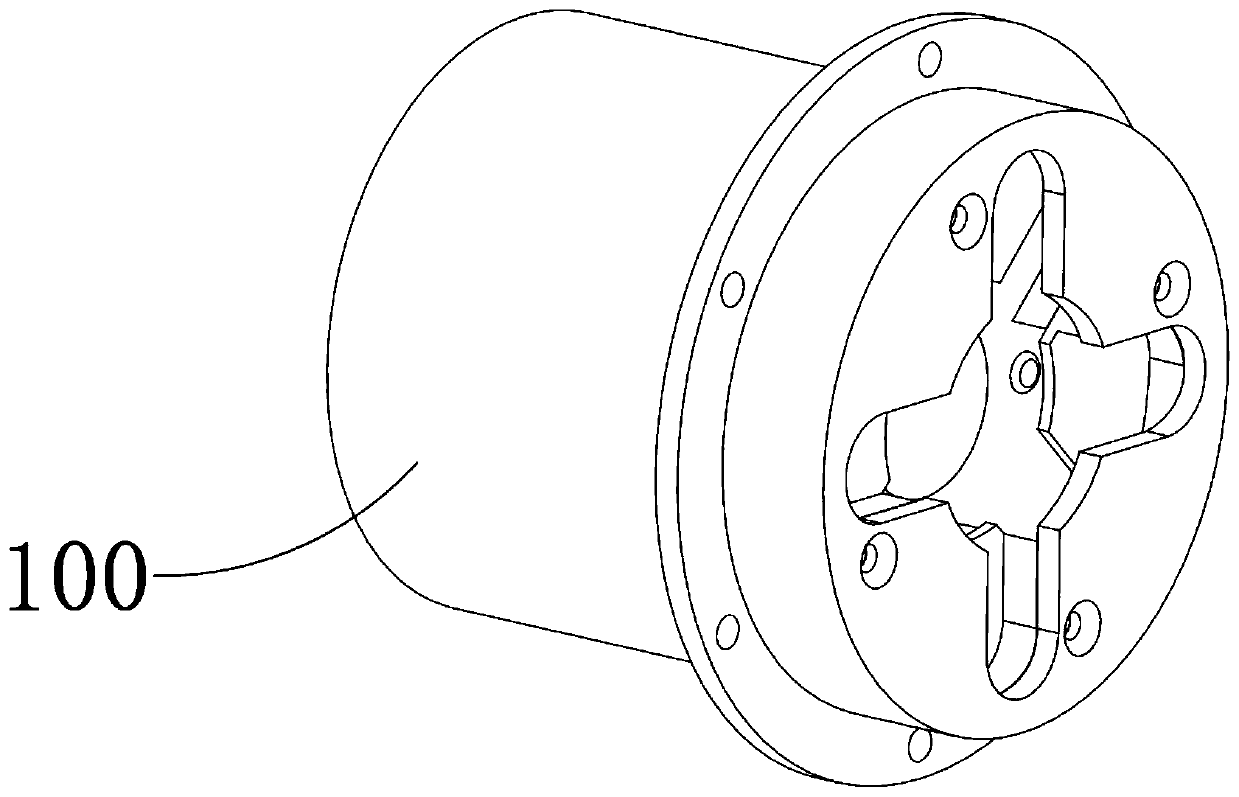
[0067] The insulating installation cylinder 110, the first encryption mechanism 120, the second encryption mechanism 130, the output contact 140 and the output wire 150 arranged on the outer surface of the installation cylinder 110 together constitute the transmission device 100, and the input end of the output wire 150 establishes data with the memory The connection is turned on, the output terminal is connected to the output contact 140, the encryption mechanism one 120 and the encryption mechanism two 130 are internally...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com