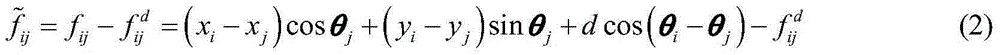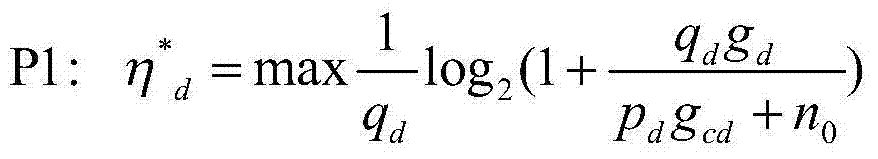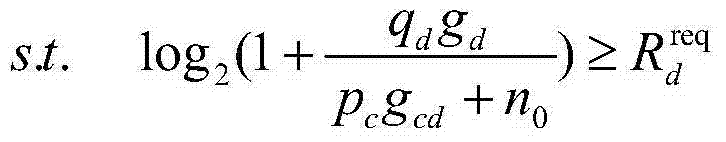Patents
Literature
318results about How to "Reduce communication load" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Analyzer, a system and a method for defining a preferred group of users
InactiveUS20090055435A1Reduce in quantityReduce communication loadMarketingSpecial data processing applicationsKnowledge managementSocial web
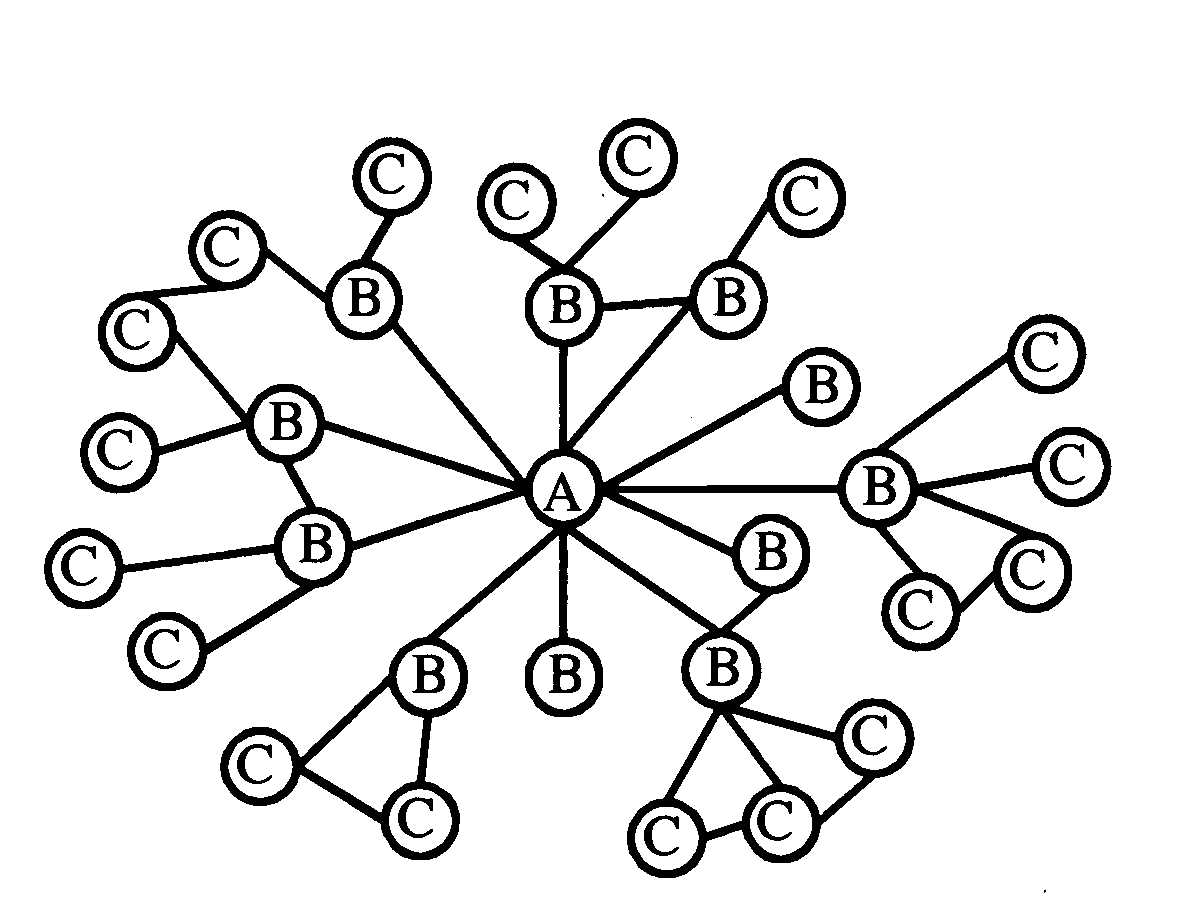
The present invention relates to an analyzer, a system, a method, and a computer-readable medium for defining a preferred group of users, wherein the group is defined in the following way. The analyzer receives data from a data network node, which may be e.g. a (plurality of) data-base(s). After receiving the data, there is determined a social network of the users and a set of parameters for each user. The set of parameters may comprise e.g. an innovator score, a repeat user score and a social influence score. After the above determination, there is determined the preferred group of users based on the social network and the set of parameters. The information (or indication) of the preferred group of users may be utilized in various marketing activities (e.g. product launch or churn management).
Owner:XTRACT
Intelligent water resource control platform based on cloud computing and expert system
InactiveCN103489053AReduce communication load and data processing volumeIncrease the number of accessResourcesCloud computingData transmission systems
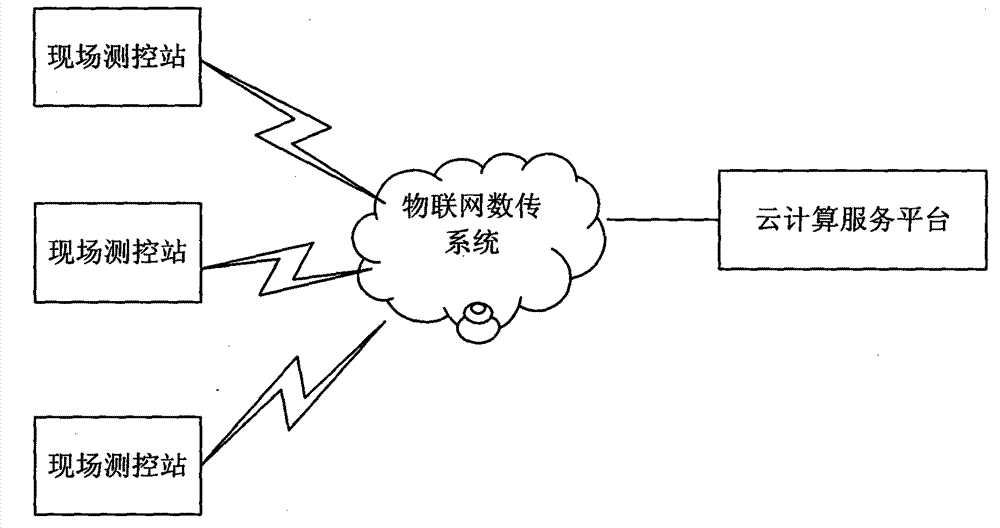
The invention discloses an intelligent water resource control platform based on cloud computing and an expert system. The platform comprises a site measurement and control station, an internet of things data transmission system and a cloud computing service platform, and is characterized in that the control platform carries out automatic real-time collection on water resource information of a water supply water source, underground water, a water intake, a boundary control fracture surface and a sewage draining exit and site equipment operating condition information through the site measurement and control station, and real-time data preprocessing is achieved by means of an additionally installed site intelligent controller; internet of things data transmission equipment is adopted in the internet of things data transmission system to sent data of the measurement and control station to the cloud computing platform, and data support is provided for water resource management and advanced applications; the cloud computing service platform achieves real-time monitoring on water resources, monitoring on operating condition and remote on-line maintenance on site monitoring equipment and applications on water resource service, and a water resource decision is utilized to support the expert system to achieve assessment, early warning and emergency commanding of the water resources. The cloud computing and the Internet of things technology are applied to the platform, so measurement and control data are timely and efficiently processed, the intelligent computing technology is applied so that intelligent assessment and early warning of the water resources can be achieved, and safety of the water resources is guaranteed to a great extent.
Owner:湖南云控科技有限公司 +1
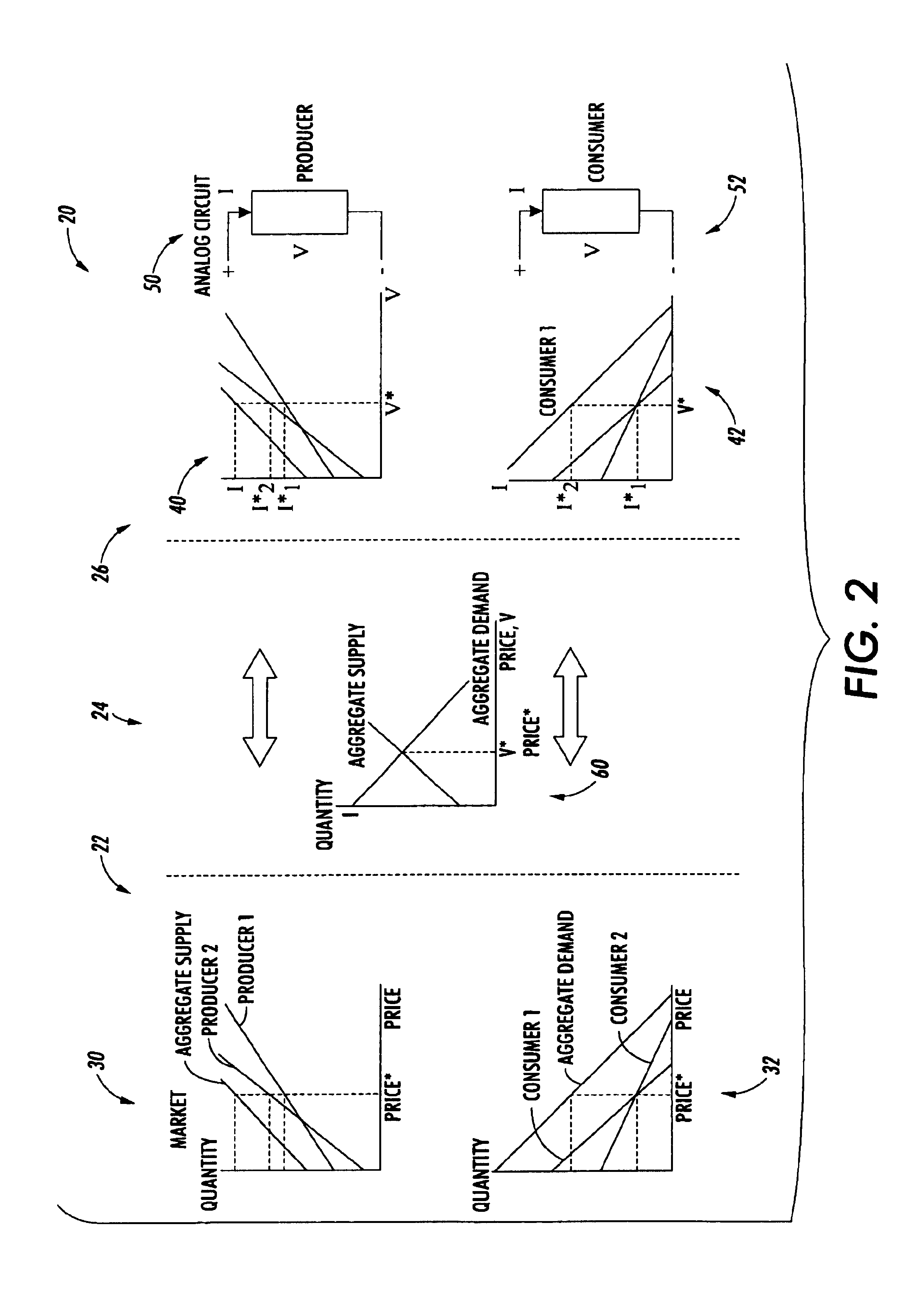
Distributed control of non-linear coupled systems with a single output
InactiveUS6915267B2High bandwidthInexpensively connectionMarket predictionsDigital computer detailsConsumer unitControl system
The present invention encompasses a control system and method for systems of producing and consuming units. The method of the invention includes the steps of setting each producing unit to have an output responsive to an analog signal representative of a market price, and connecting each producing unit to a marketwire, with the changes in the analog signal on the marketwire representing changes in the market price resulting from inputs from the consuming units and the output response of each producing unit.
Owner:XEROX CORP
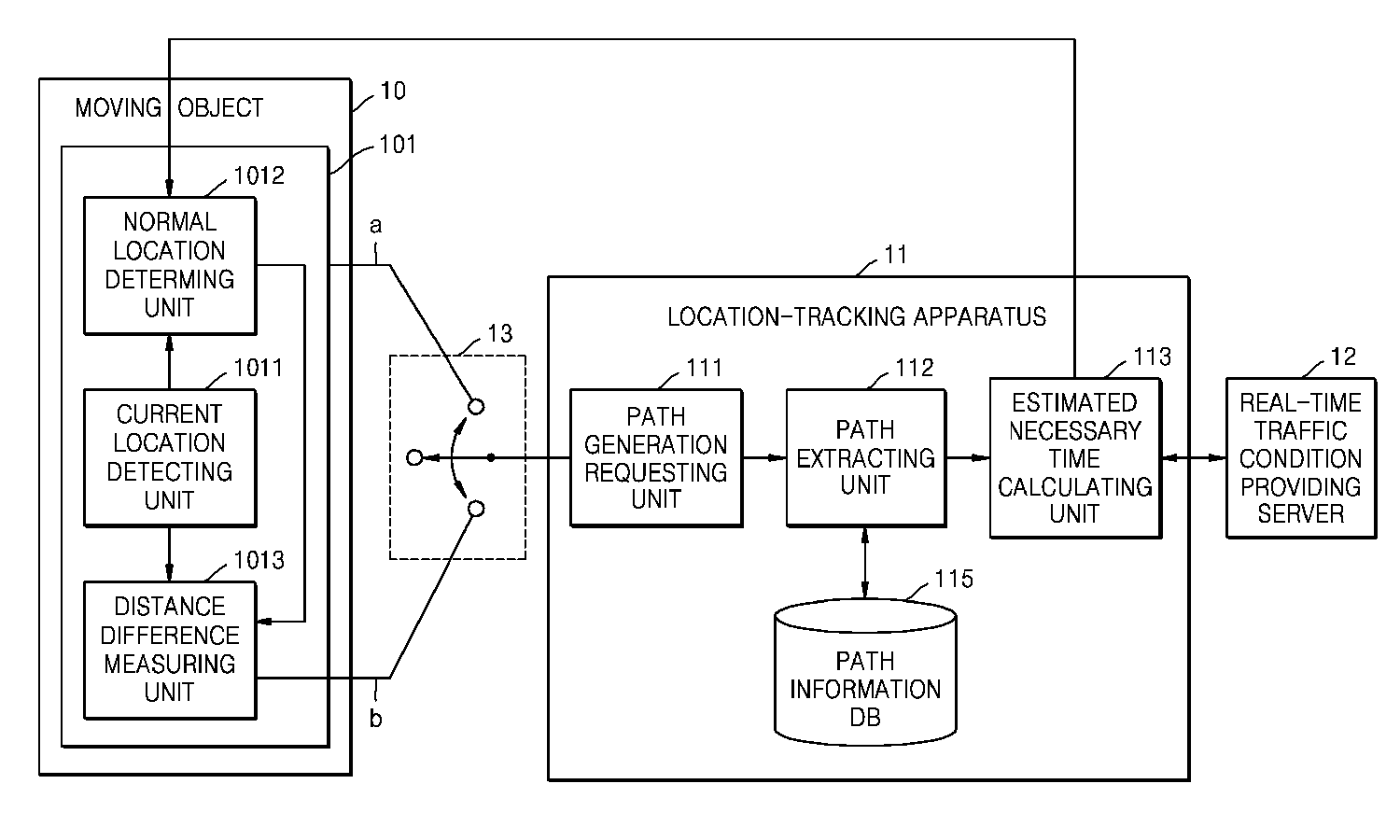
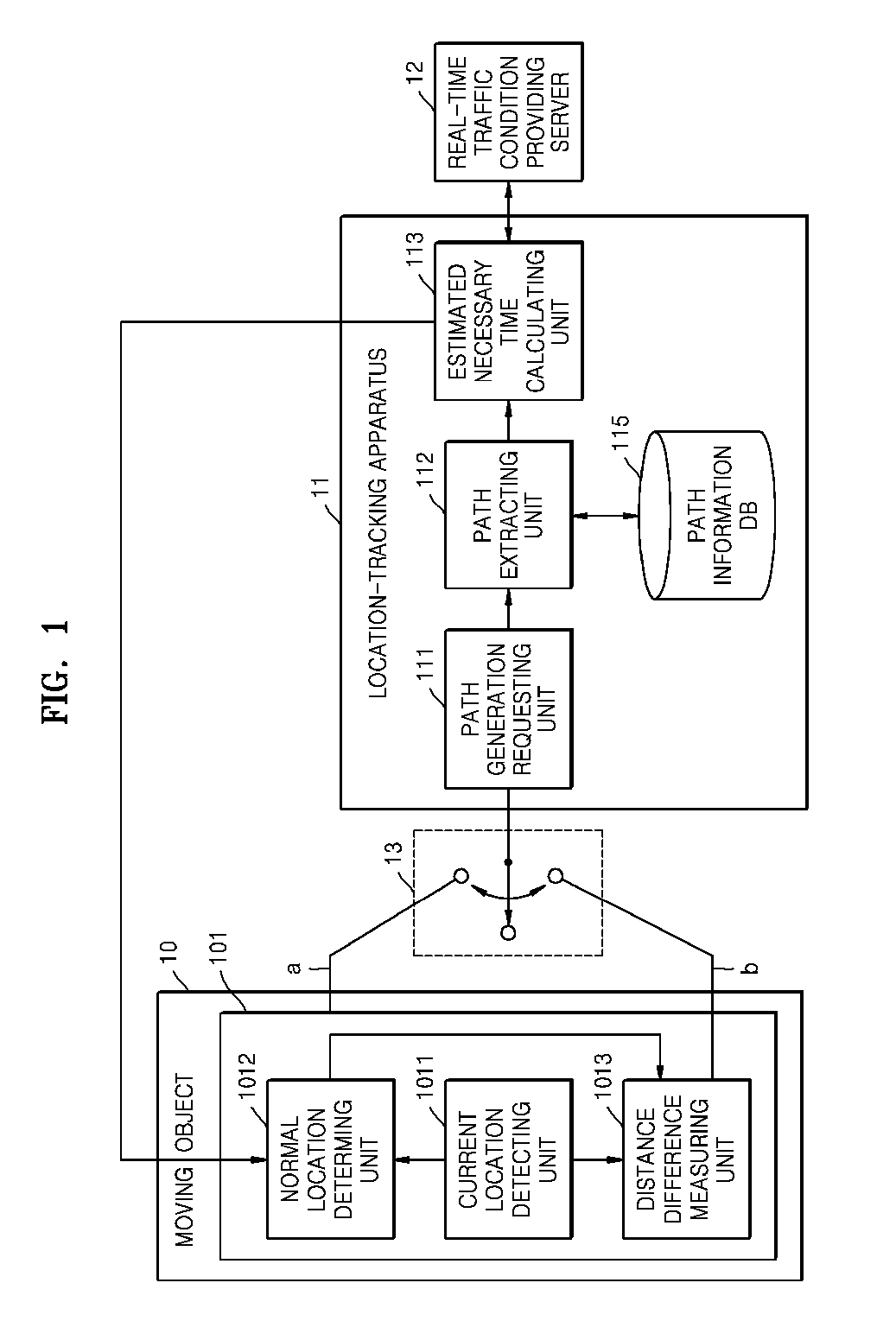
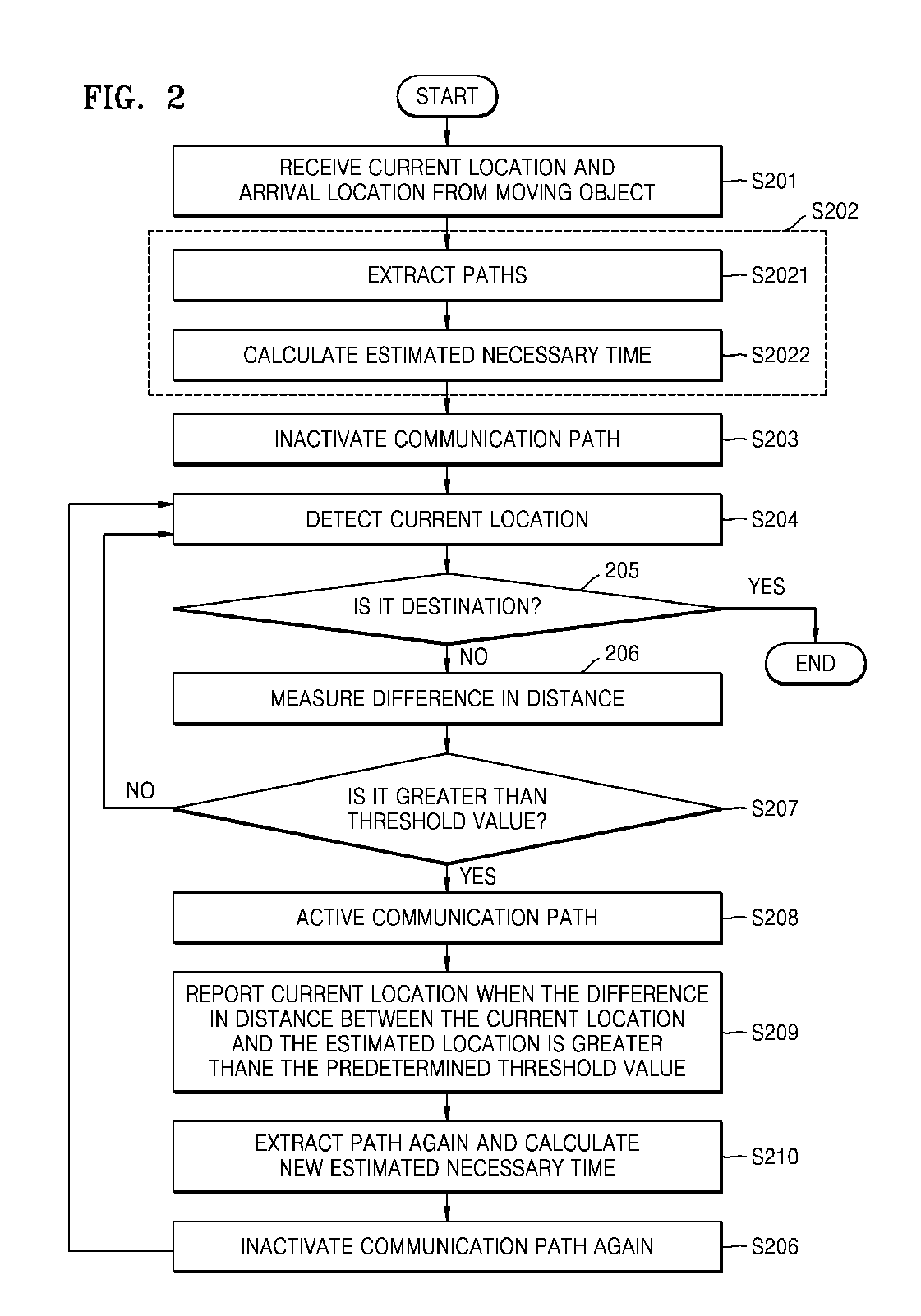
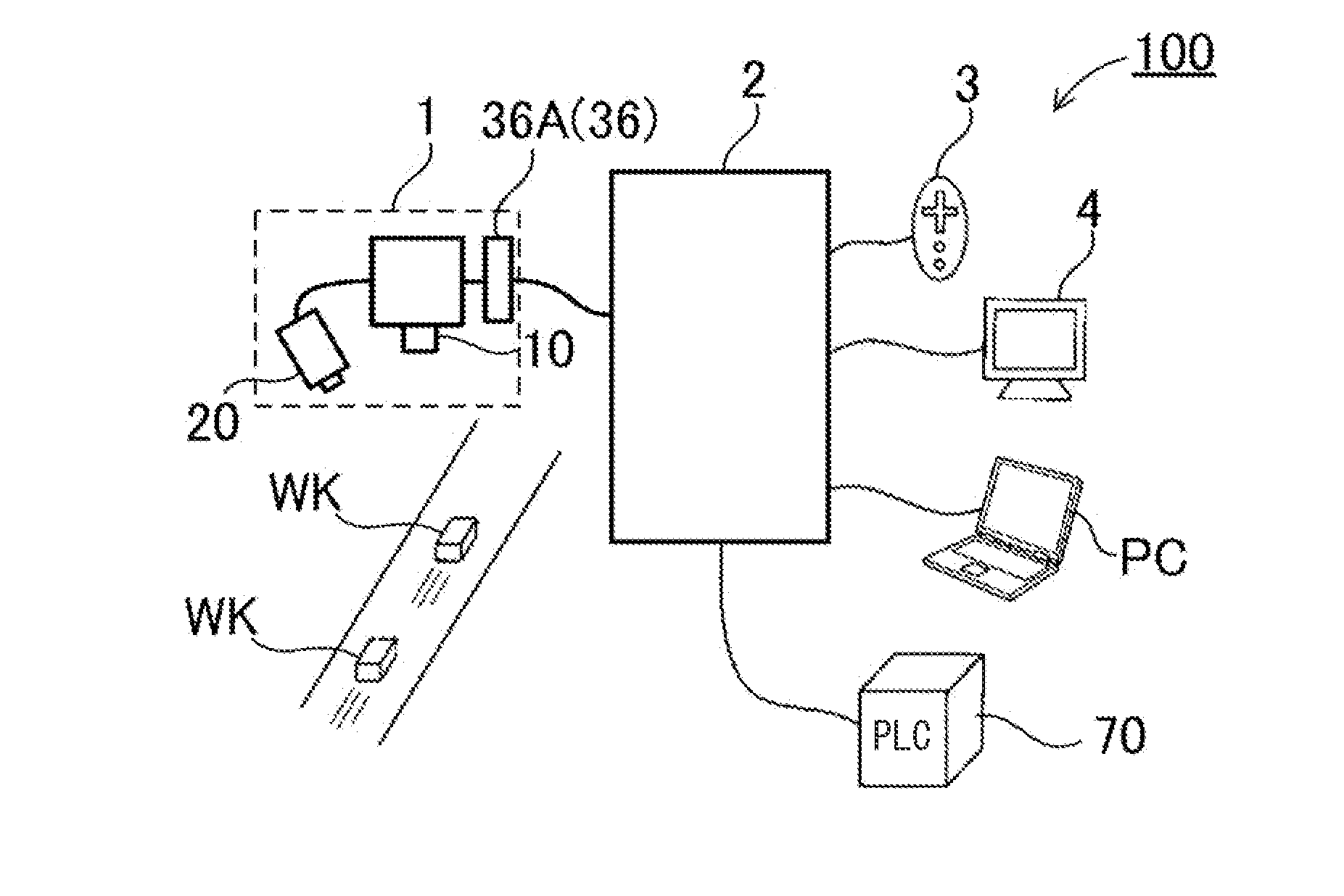
System and method for reducing communication load of apparatus for tracking moving object
ActiveUS20090018768A1Reduce communication loadReduce communication frequencyInstruments for road network navigationRoad vehicles traffic controlComputer terminalComputer science
Provided are a system and a method for reducing a communication load of an apparatus for tracking a moving object. The system includes: an estimated necessary time calculating unit receiving a current location and an arrival location of the moving object from a terminal included in the moving object, calculating estimated necessary time for the moving object to reach the arrival location, and transmitting the estimated necessary time to the terminal; and a communication path on-off controlling unit activating a communication path for the terminal to receive the estimated necessary time from the estimated necessary time calculating unit, and inactivating the communication path when the terminal receives the estimated necessary time through the communication path.
Owner:ELECTRONICS & TELECOMM RES INST
Automatic driving automobile control system and method and microcontroller
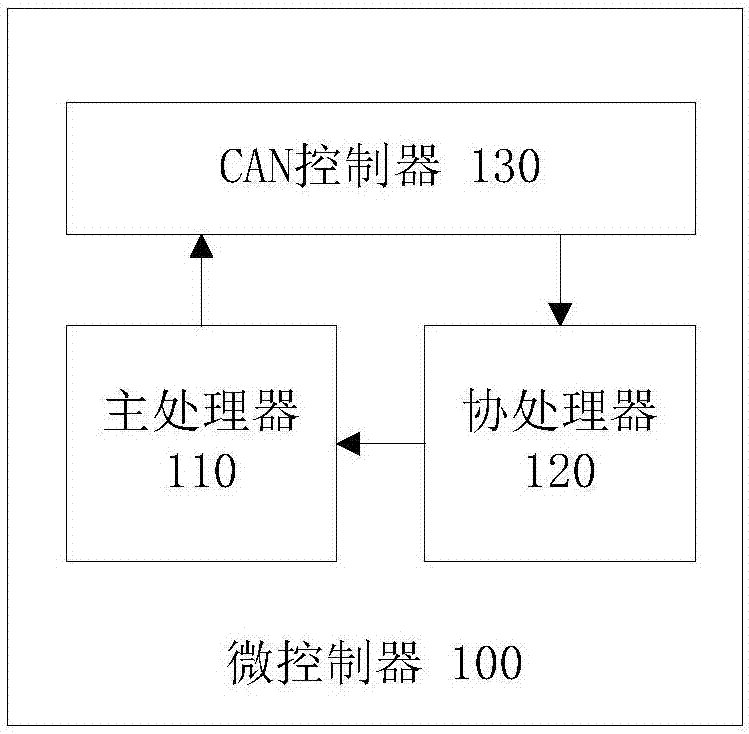
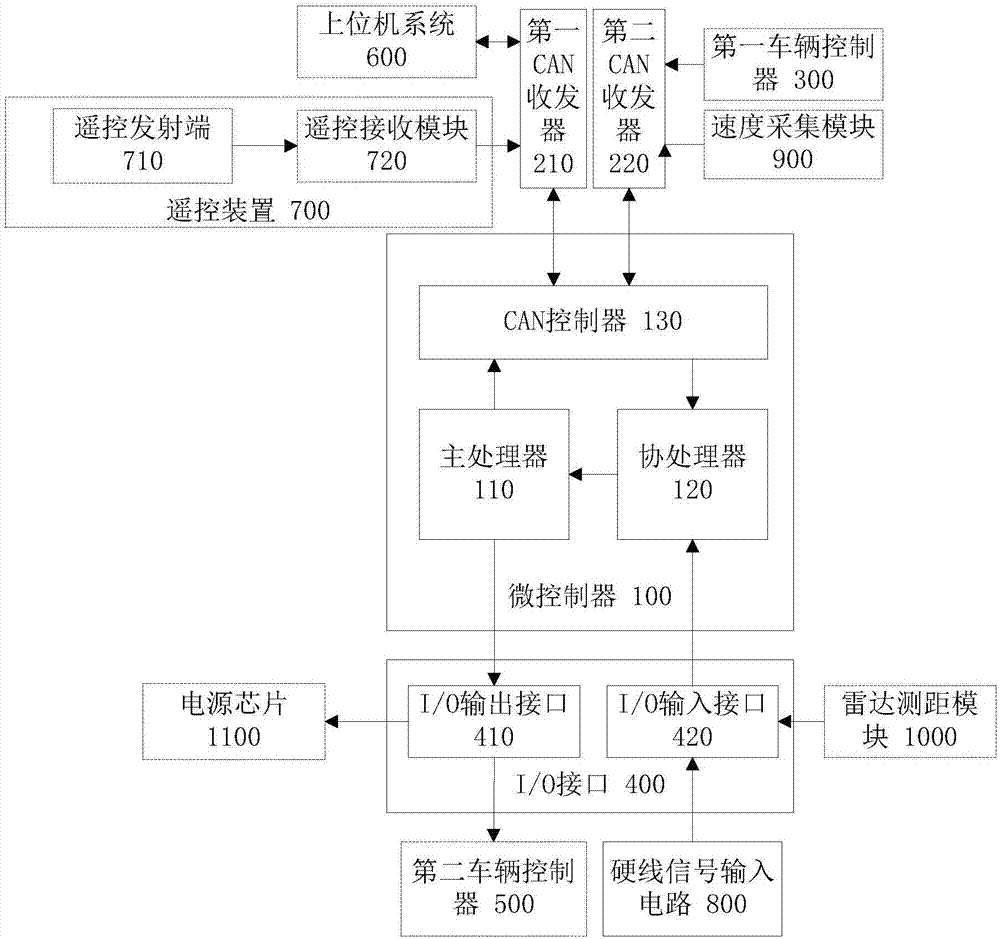
PendingCN107219797AReduce communication loadImprove communication efficiencyProgramme controlComputer controlMicrocontrollerCoprocessor
The invention provides an automatic driving automobile control system and method and microcontroller. The microcontroller comprises a main processor, a coprocessor and a CAN controller. The CAN controller is connected with the coprocessor and the main processor in a communication way to receive a CAN message and forward the CAN message to the coprocessor. The coprocessor interrupts receiving of the CAN message and the I / O input signal forwarded by the CAN controller and analyzes the CAN message and the I / O input signal so as to obtain corresponding control information and transmit the control information to the main processor. The main processor processes the control information so as to obtain a corresponding control output instruction to be transmitted to a second automobile controller used for controlling acousto-optic performance, starting and electrical parking of the automatic driving automobile or transmitted to a second automobile controller used for controlling driving of the automatic driving automobile. The communication load between the upper computer system and the microcontroller can be reduced and the communication efficiency between the upper computer system and the microcontroller can be enhanced.
Owner:GUANGZHOU AUTOMOBILE GROUP CO LTD
Communication load reducing method and computer system
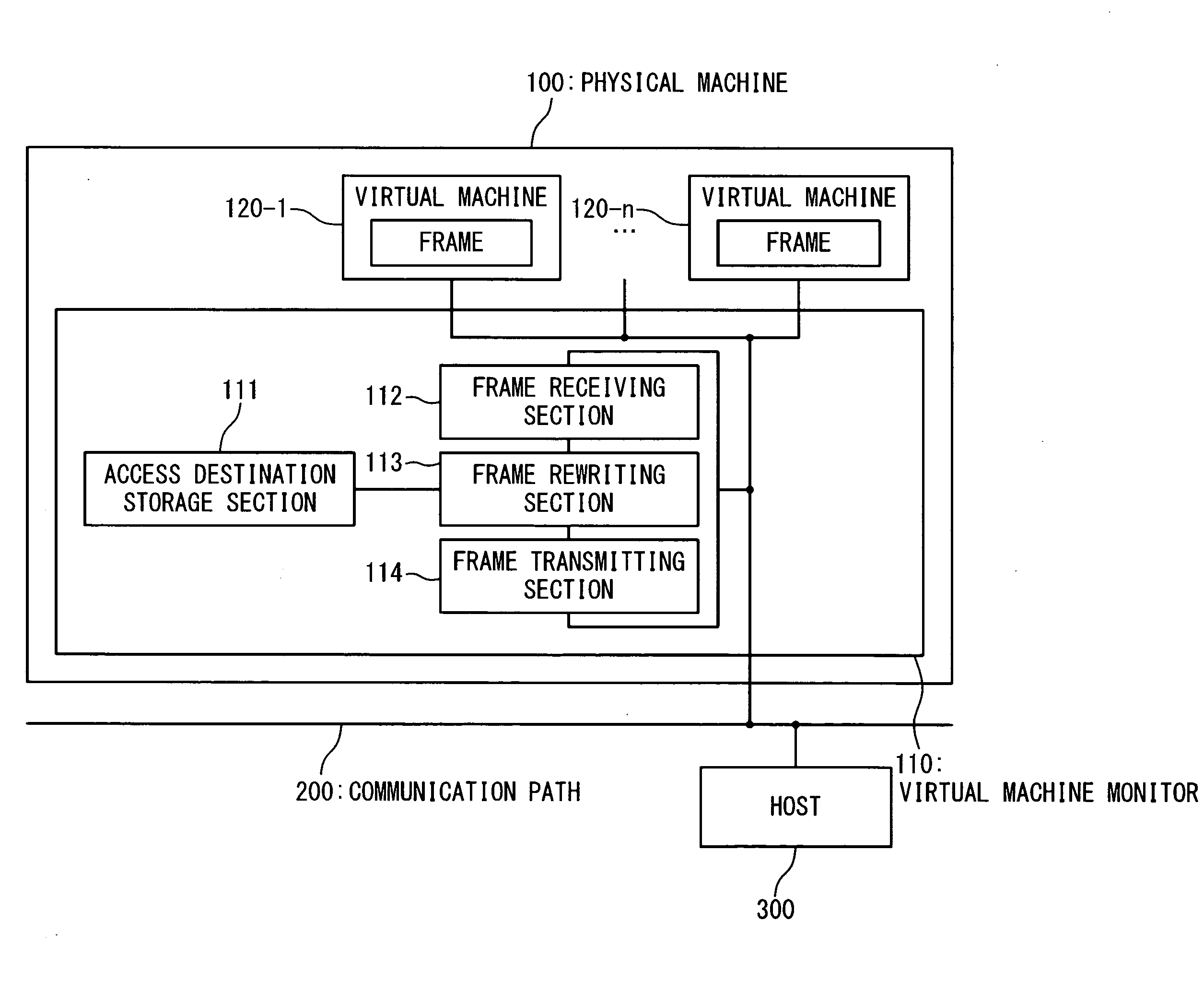
InactiveUS20080028071A1Reduce communication loadSuppress generationMultiple digital computer combinationsTransmissionComputerized systemTerminal equipment
A computer system connected to a network includes a terminal apparatus configured to detect an access destination on the network, acquire a destination data of the access destination, and generate a frame having the destination data for the access destination; and a monitoring apparatus configured to hold the destination data, and to produce at least one unicast frame to the access destination based on the destination data of the frame received from the terminal apparatus. The monitoring apparatus issues an access destination registration request to the terminal apparatus, and acquires the destination data from the terminal apparatus. The terminal apparatus holds a data indicative of reception of the access destination registration request from the monitor apparatus and notifies the destination data to the monitoring apparatus if the data indicative of the reception of the access destination registration request is stored when receiving a reply from the access destination.
Owner:NEC CORP
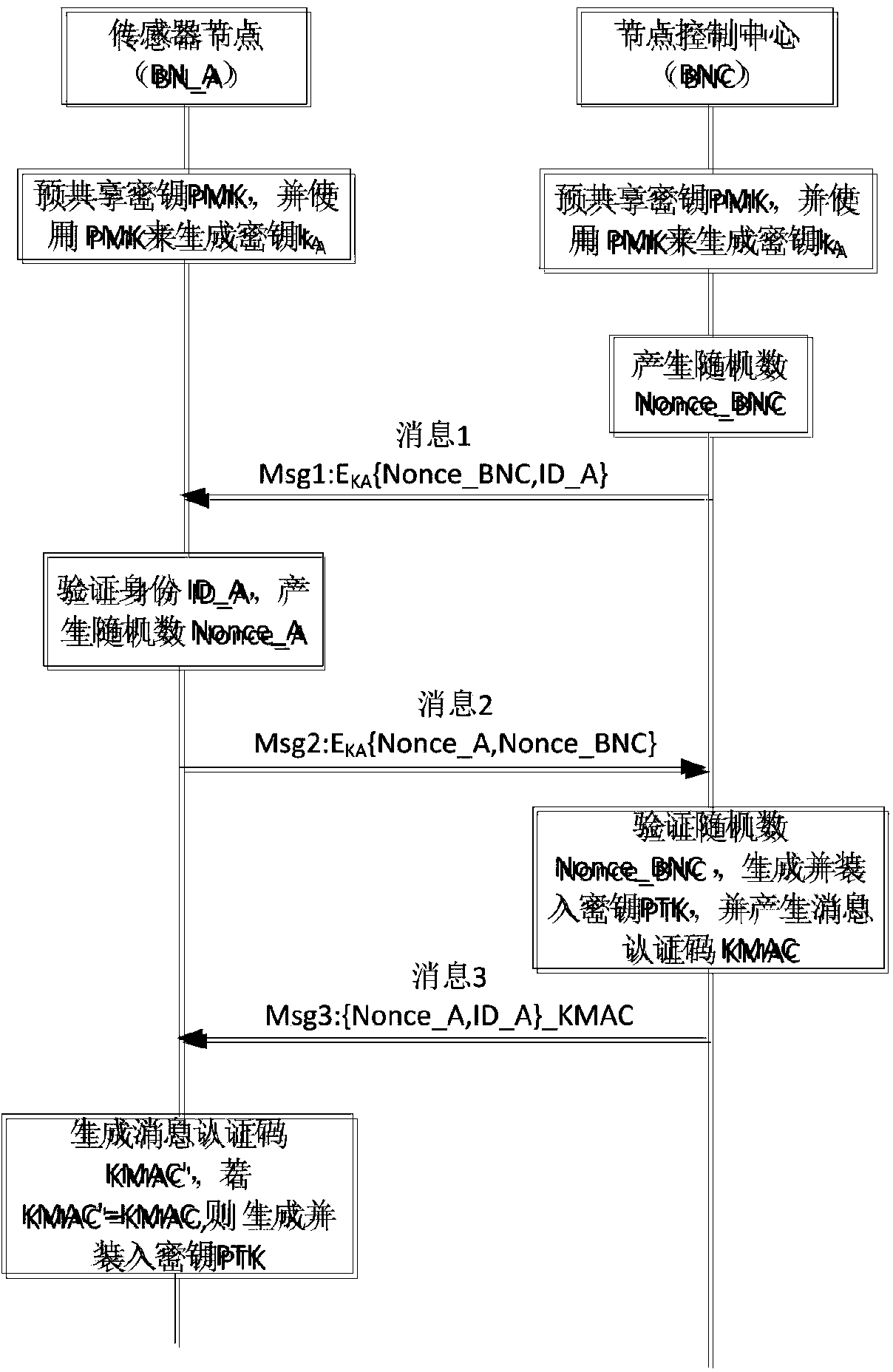
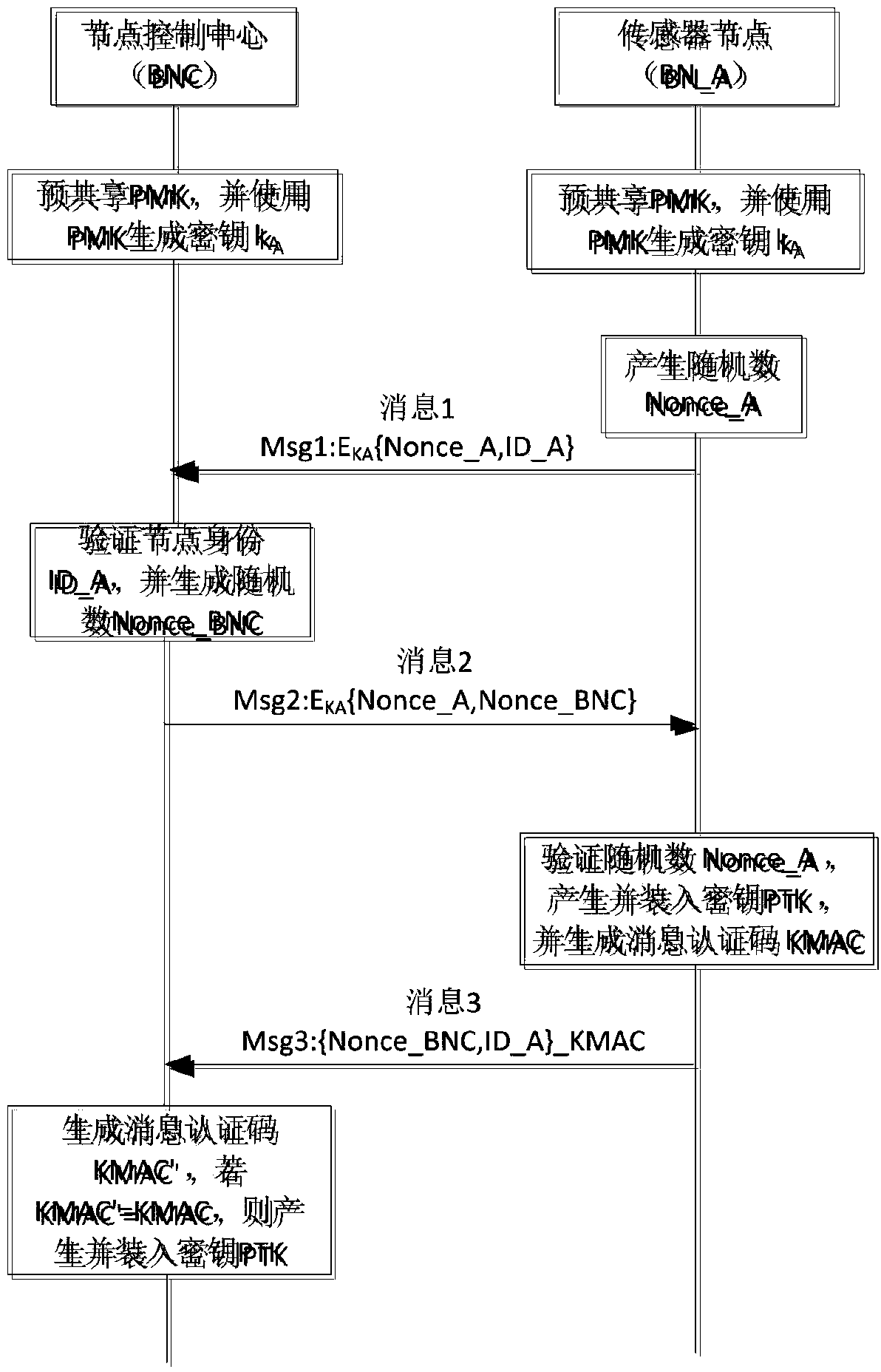
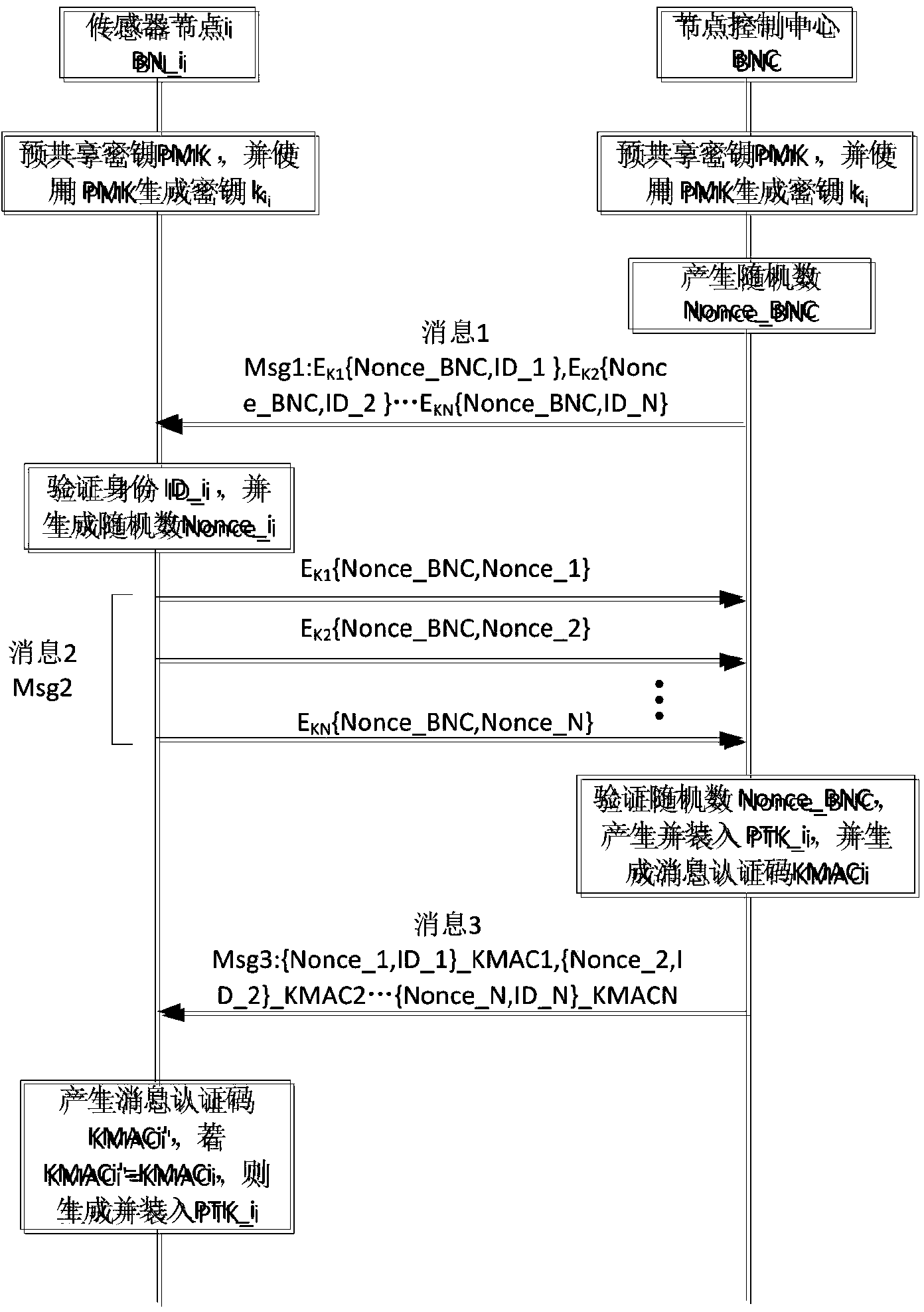
Efficient and energy-saving link safety method in wireless sensor network
InactiveCN101820619APrevent replay attacks and denial of service attacksImprove usabilityEnergy efficient ICTSecurity arrangementFrame check sequenceLine sensor
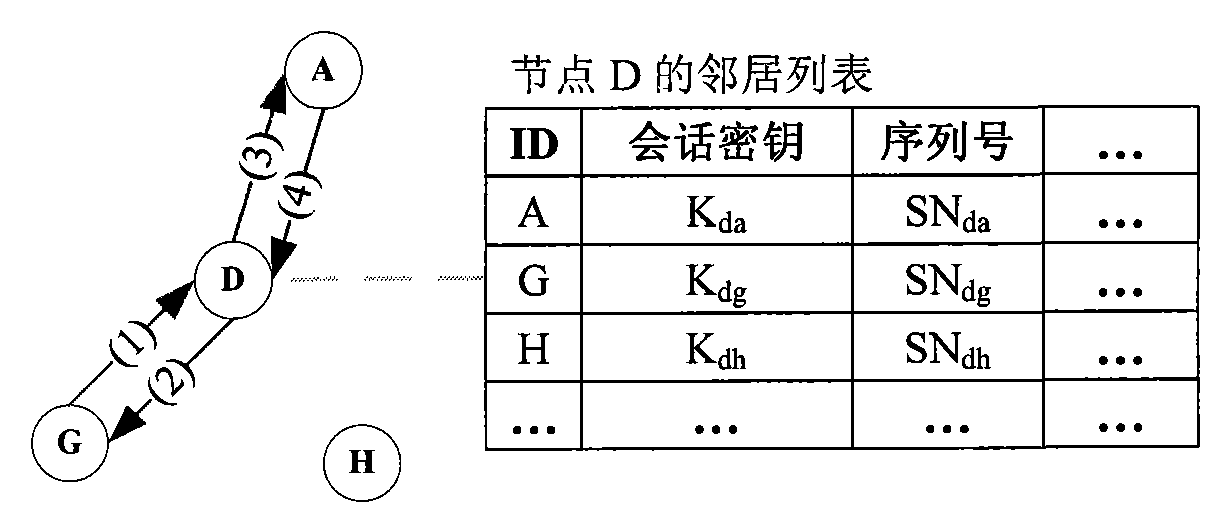
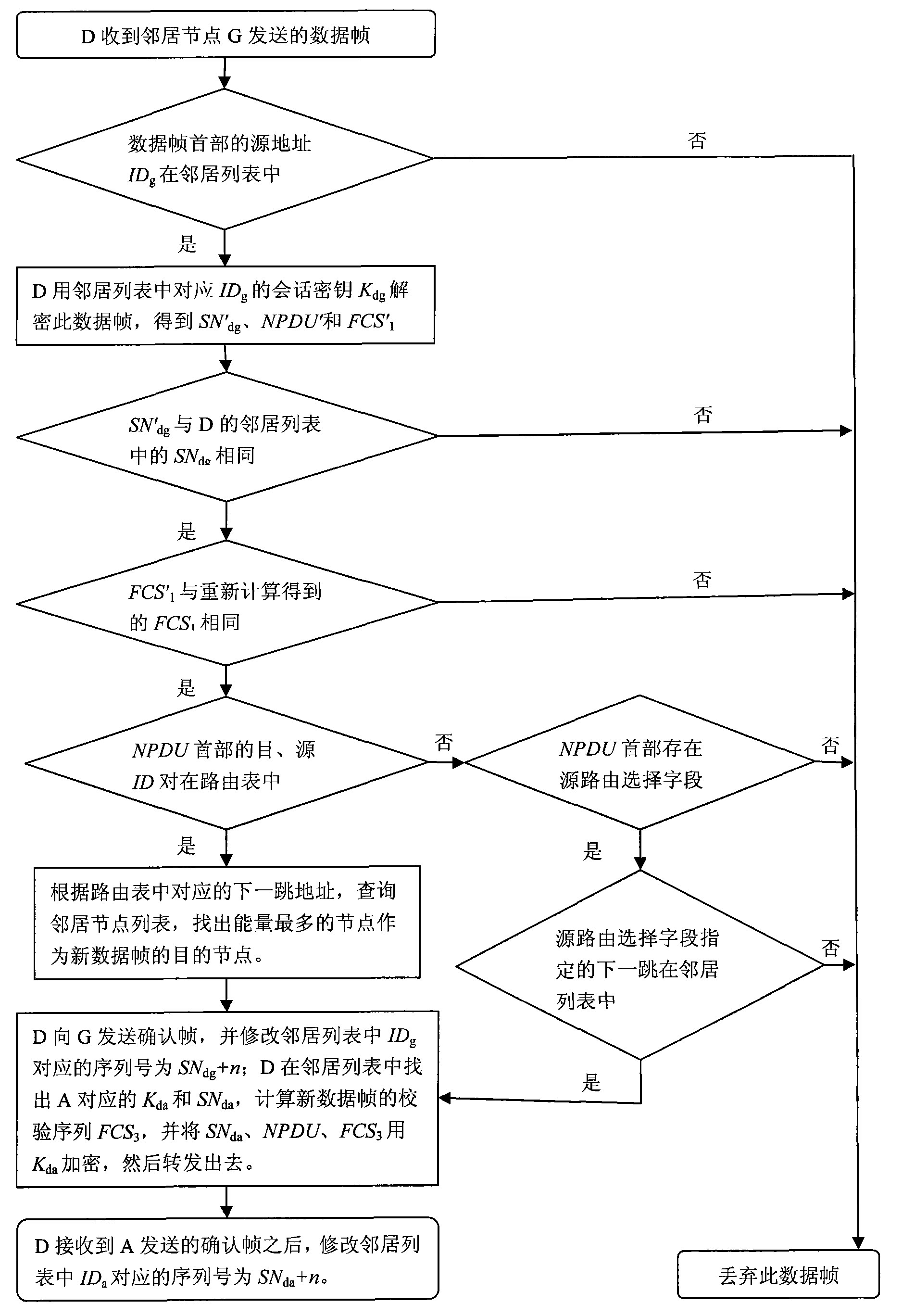
The invention relates to an efficient and energy-saving link safety method in a wireless sensor network, belonging to the cross technical field of a wireless sensor network and information safety. The invention establishes a neighbor list in which parameters used by the link safety method are stored. The invention adopts a method of encrypting sequence number fields at the header of a data frame, frame check sequence fields and a network grouping part together, can prevent malicious nodes from intercepting and analyzing flow of data of the wireless sensor network, and can confront active attacks of replay, denial of service, and the like initiated by the malicious nodes. The invention carries out link encryption under the condition of not changing the IEEE 802.15.4 general-purpose data frame structure, thus being simple and easy in use. The whole scheme comprises three stages of establishing the neighbor list, forwarding data and maintaining the neighbor list. Because the neighbor list has ingenious design, the three stages ensure that the sensor nodes have low expenses on computation, communication and storage, thus the invention is very suitable for the wireless sensor network with limited resources.
Owner:BEIJING UNIV OF TECH
Three-Dimensional Image Processing Apparatus, Three-Dimensional Image Processing Method, Three-Dimensional Image Processing Program, Computer-Readable Recording Medium, And Recording Device
ActiveUS20150022638A1Reduce data transfer loadReduce the amount of data transferredImage enhancementImage analysisImaging processingComputer science
A head section includes: a light projecting part for projecting incident light as structured illumination of a predetermined projection pattern; the image capturing part for acquiring reflected light that is projected by the light projecting part and reflected on an inspection target, to capture a plurality of pattern projected images; a distance image generating part capable of generating a distance image based on the plurality of pattern projected images captured in the image capturing part; a head-side storage part for holding the distance image generated in the distance image generating part; and a head-side communication part for transmitting the distance image held in the storage part to the controller section. The controller section includes: a controller-side communication part for communicating with the head-side communication part; and an inspection executing part for executing predetermined inspection processing on the distance image received in the controller-side communication part.
Owner:KEYENCE
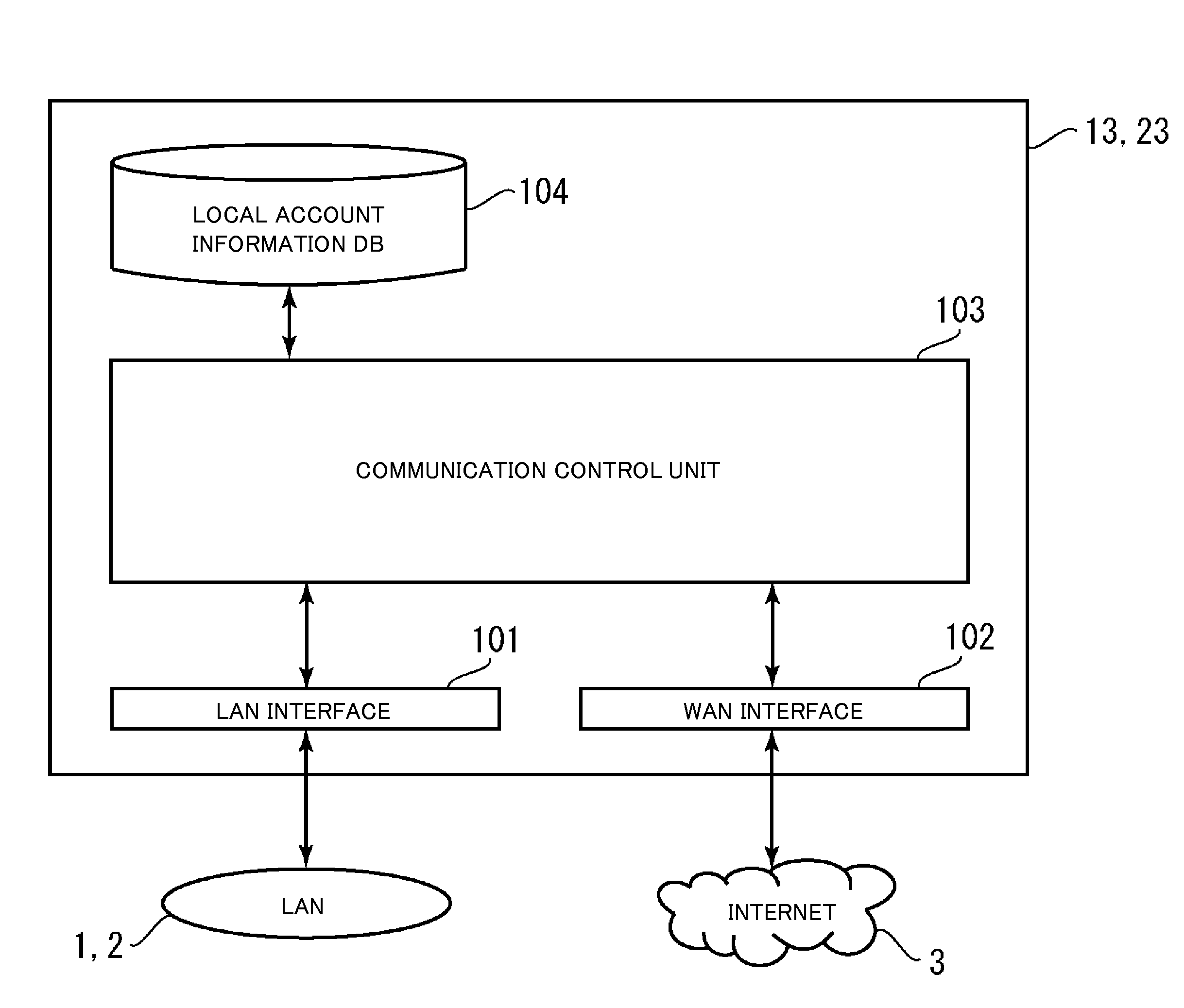
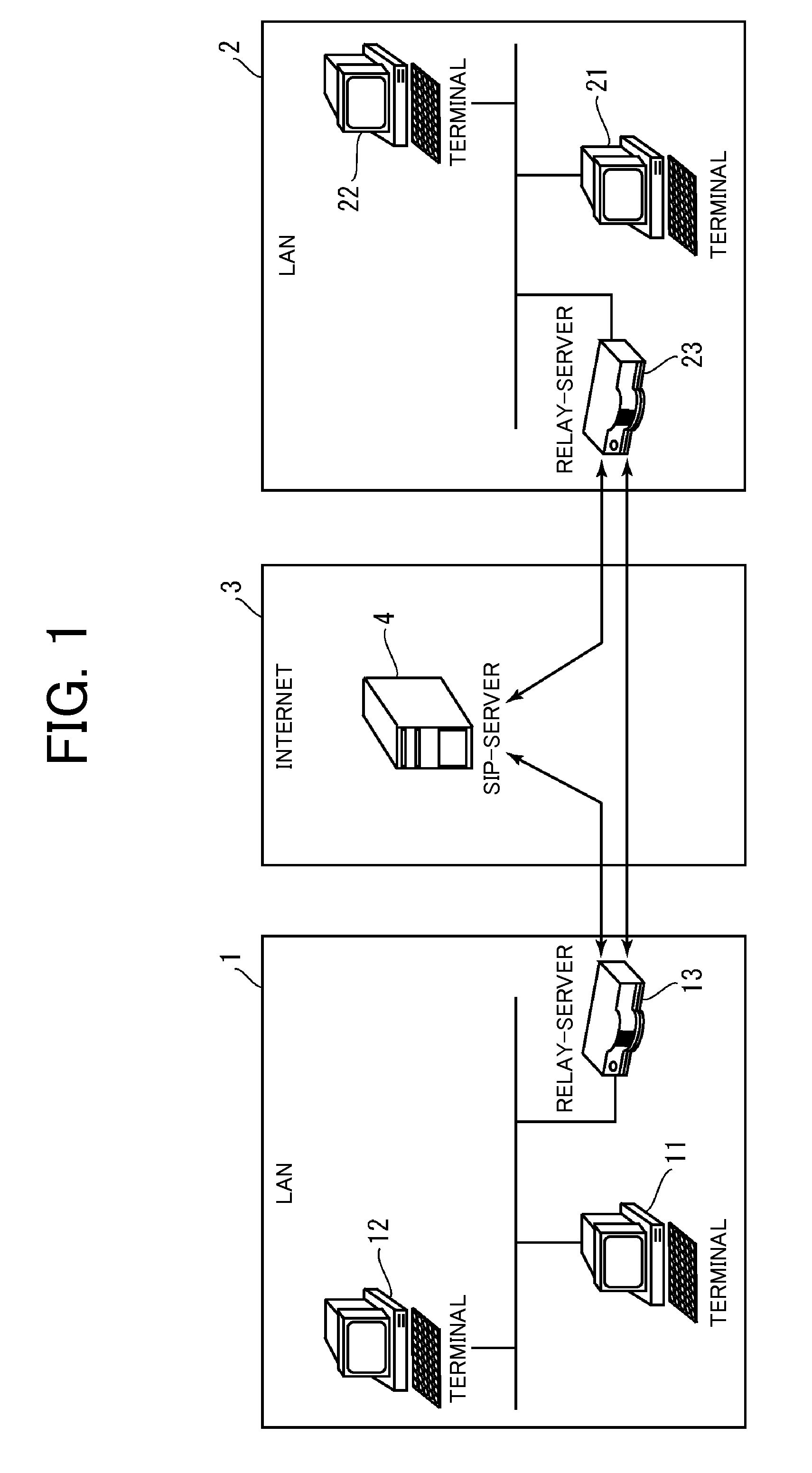
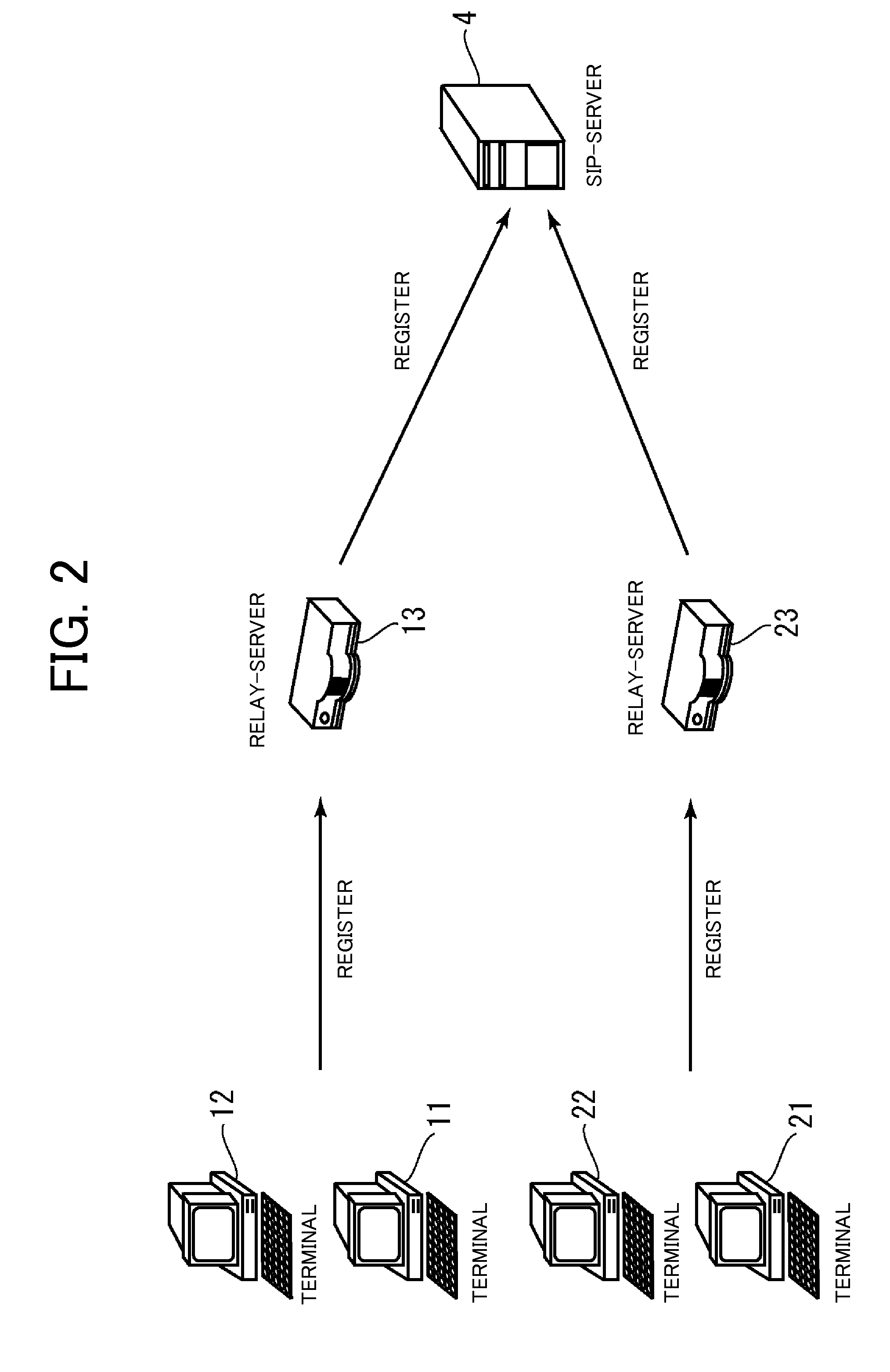
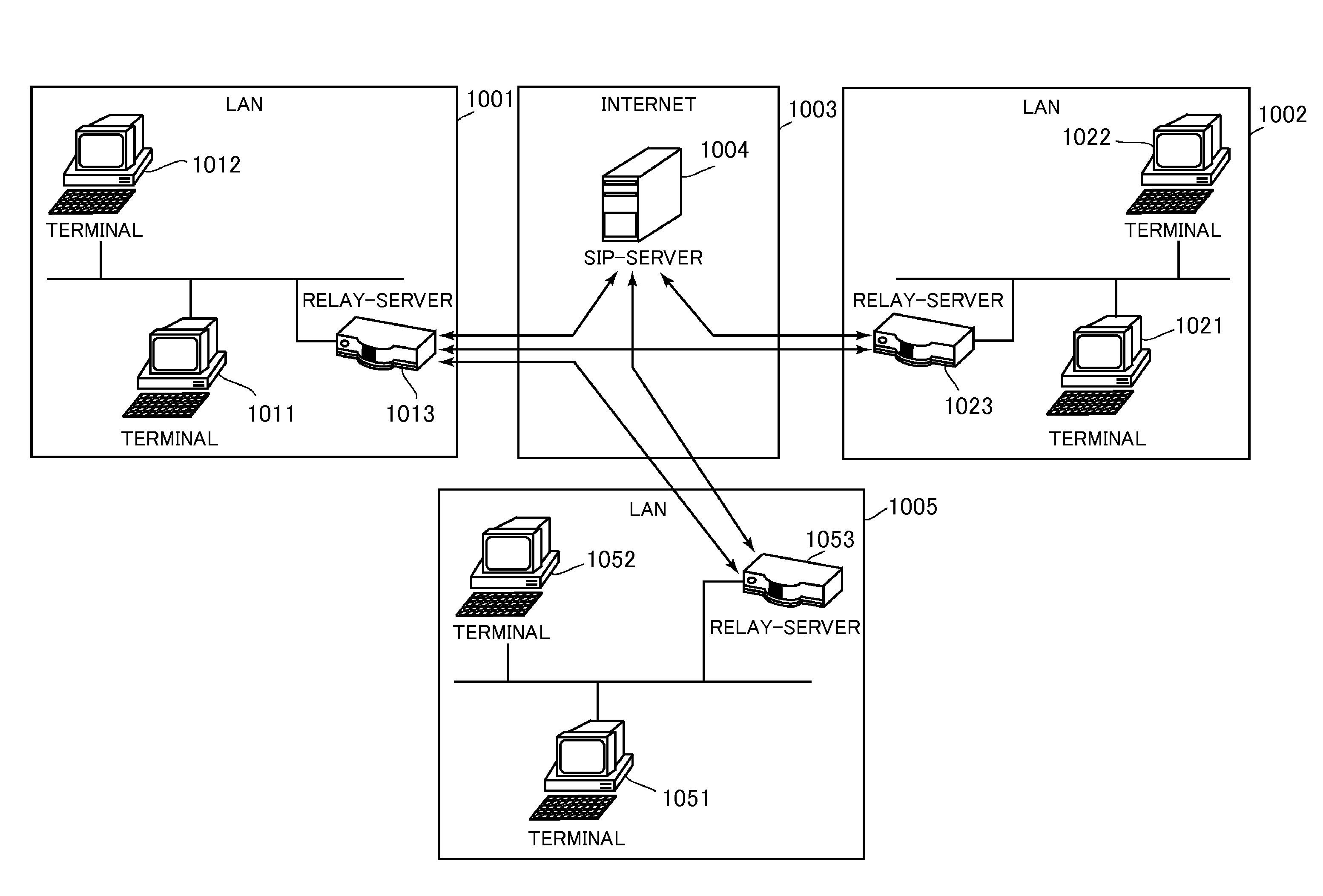
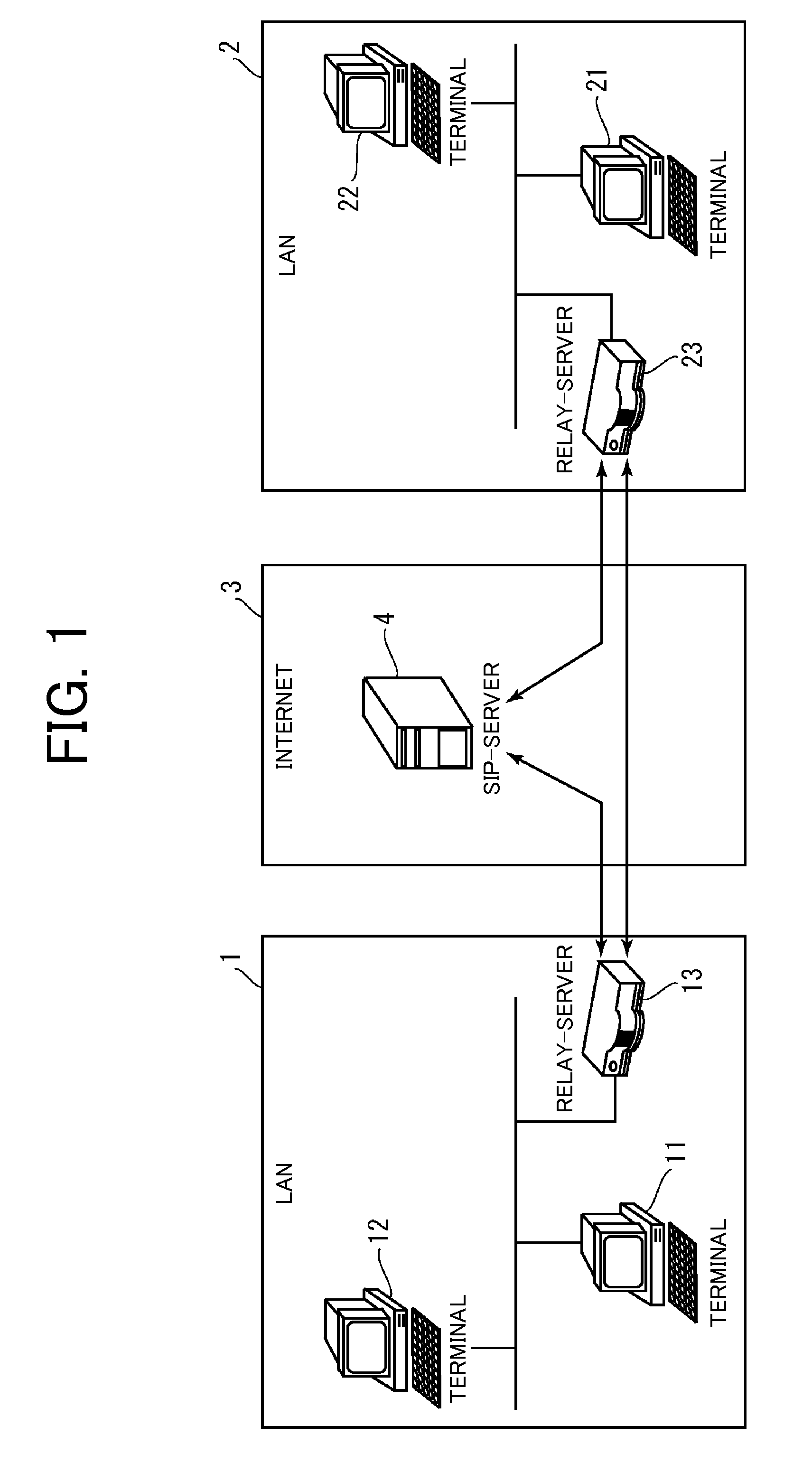
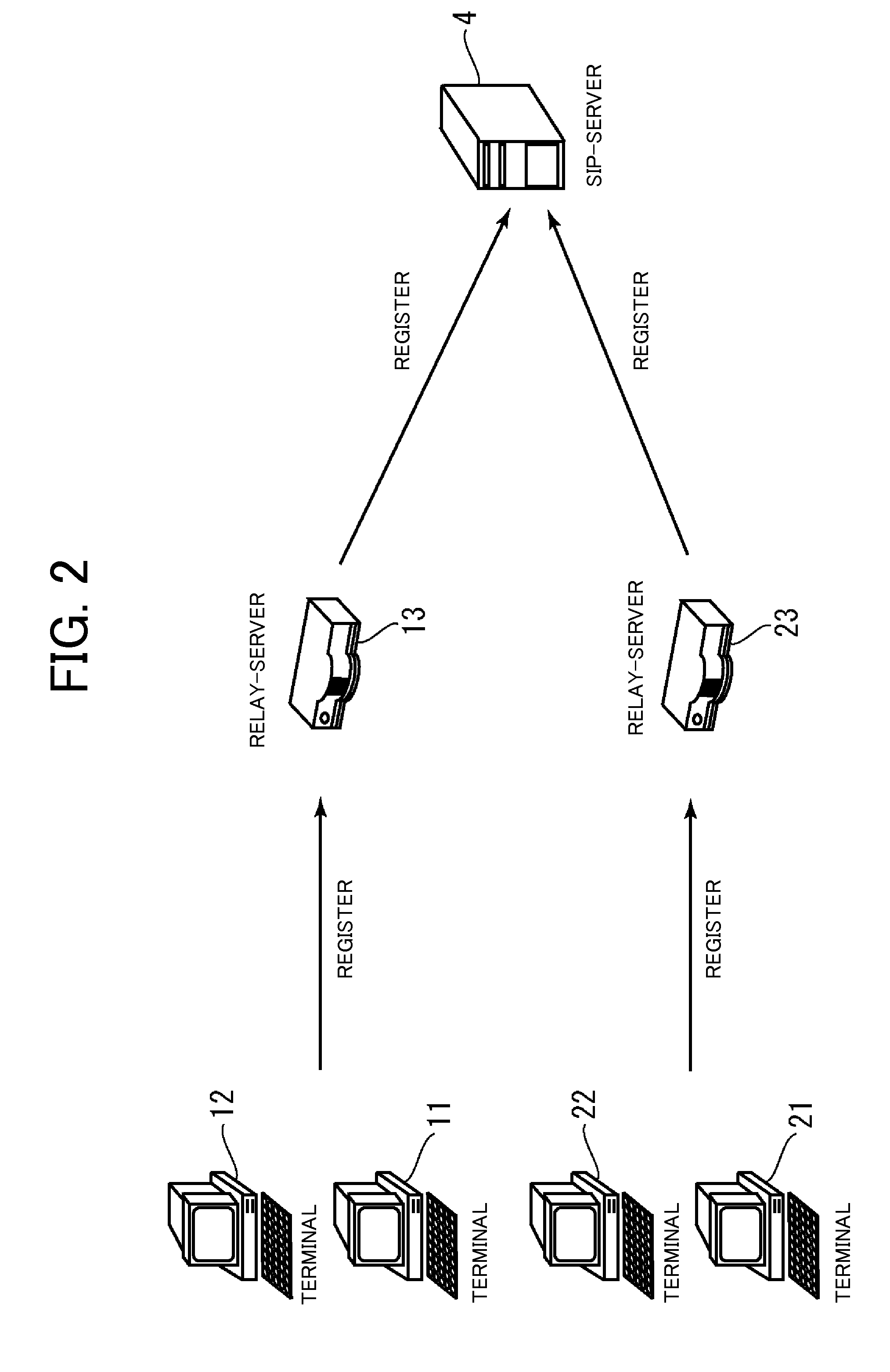
File server device
ActiveUS20080089349A1Reducing server loadReduce loadData switching by path configurationMultiple digital computer combinationsServer loadFile server
Communication is established between communication terminals arranged in different LANS while realizing dynamic response to reduction in server load, movement of communication terminal, and the like. A relay server is arranged in a LAN and can communicate with an SIP server arranged in a WAN. For instance, a first relay server exchanges account information of the communication terminals in the respective LAN with a second relay server. If exchanged account information is changed in one relay server, the account information after the change is notified to the other relay server. One relay server determines the other relay server based on the exchanged account information and relays communication data between the communication terminals through the other relay server.
Owner:MURATA MASCH LTD
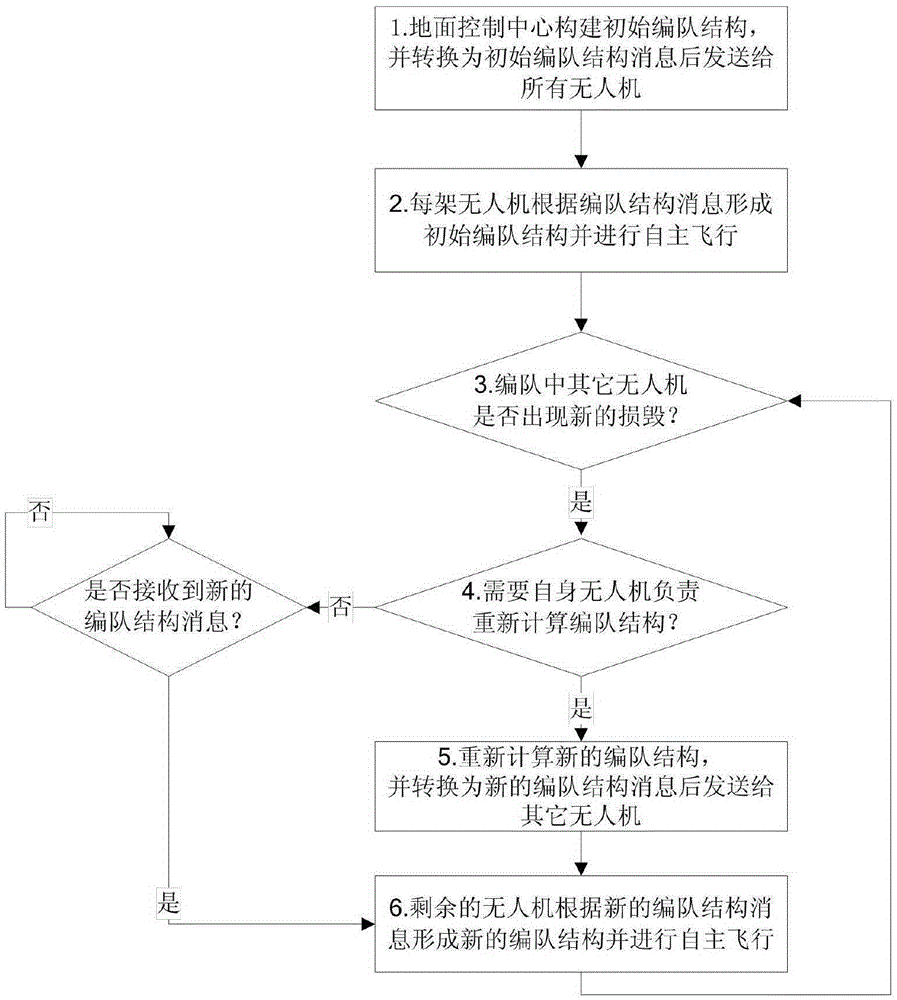
Distributed fault-tolerant management method of multi-UAV formation structure
ActiveCN105353766AImprove reliabilityImprove robustnessPosition/course control in three dimensionsComputer scienceFlight formation
Owner:HEFEI UNIV OF TECH
Method for operating a communication system and objects for such a system
InactiveUS20030112124A1Improve availabilityDecrease loadPower managementEnergy efficient ICTEngineeringRemote object
Abstract of Disclosure Method and arrangement for operating a communication system for communication between a central station (10) and one or a plurality or remote objects (20 to 25), as well as such an object, wherein at least one object is operated in a battery saving mode in which it is switched alternatively between a wake period for conducting communication between the object and the central station and a sleep period in which communication is inactive. Each object is designated a predetermined first time (t0) and a time interval (Dt), wherein each object initiates the wake periods at times t0+n (Dt) with n=0, 1, 2, ... and wherein the time interval is longer than the wake period.
Owner:VOLVO TECH
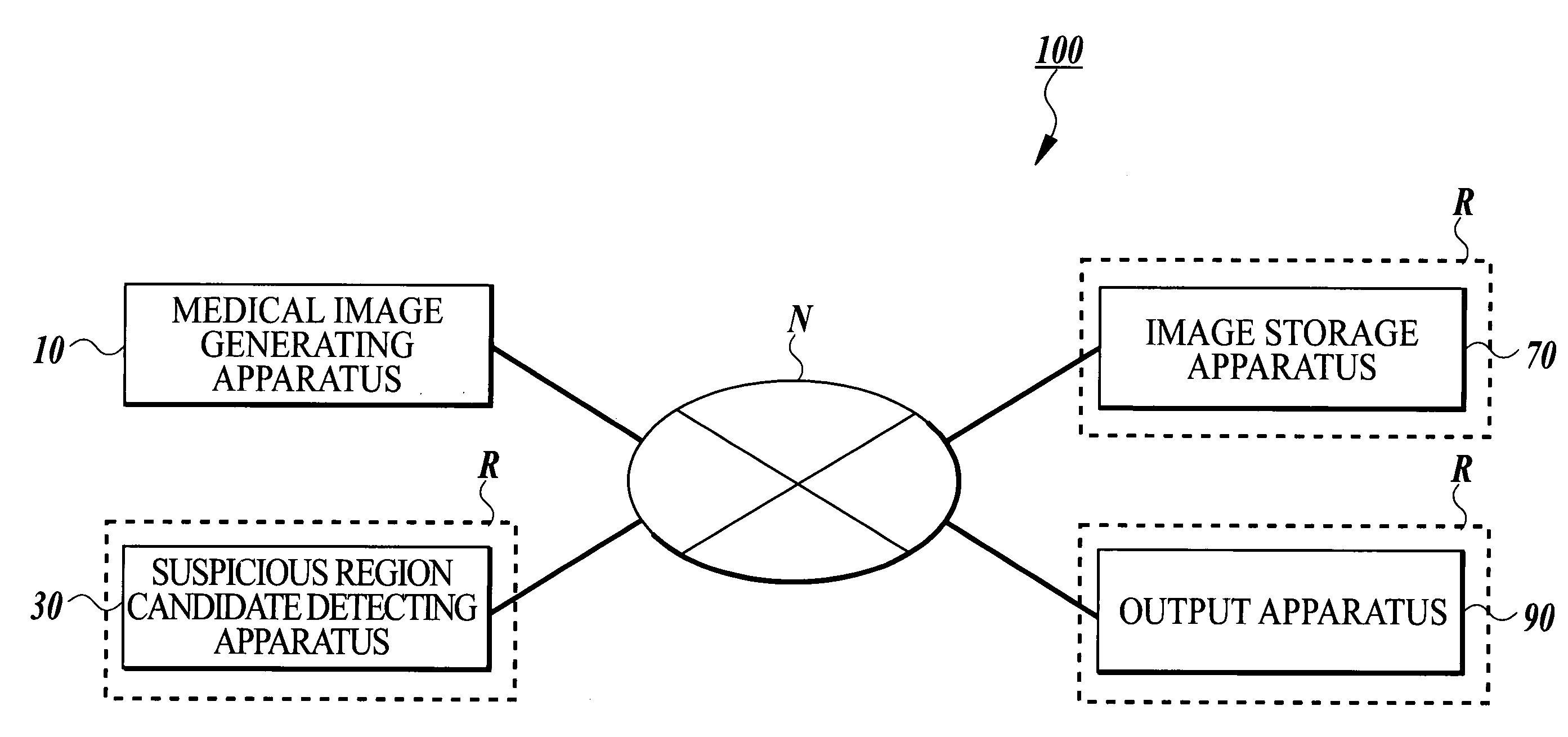
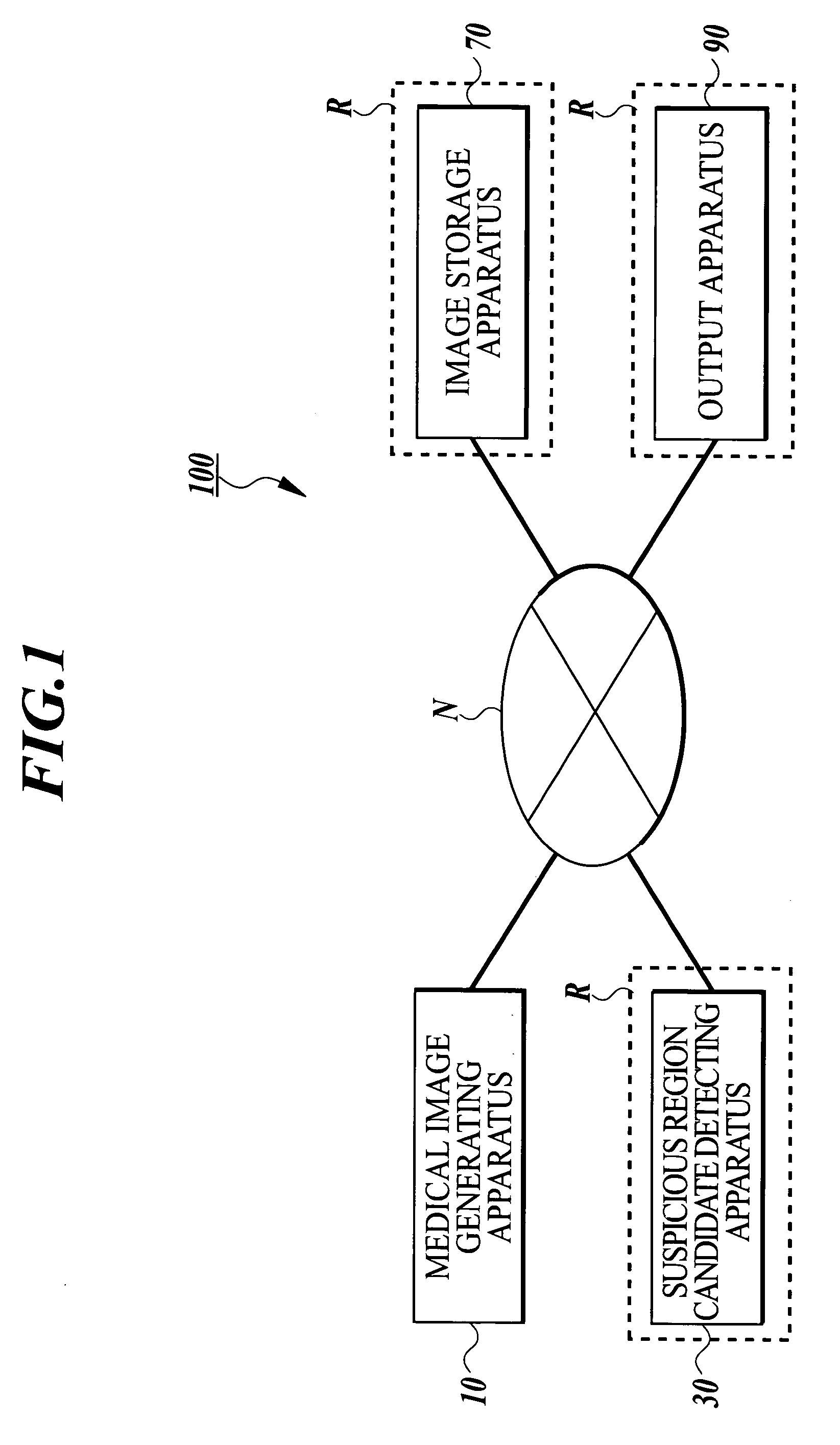
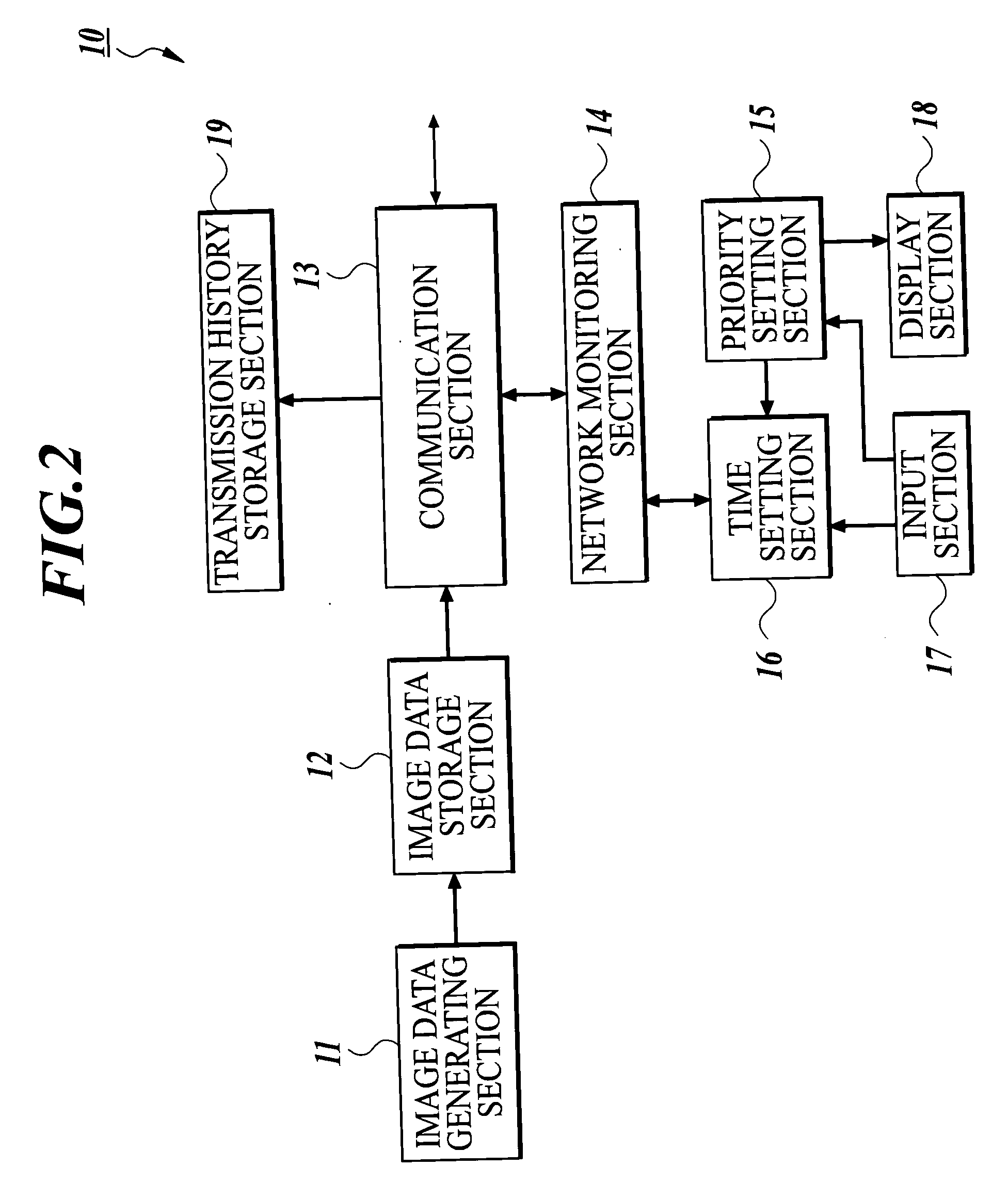
Medical image processing system
InactiveUS20040146190A1Improve image processing efficiencyReduce communication loadUltrasonic/sonic/infrasonic diagnosticsImage analysisComputer hardwareImaging processing
A medical image processing system including a medical image generating apparatus for generating medical image data of a radiographed subject; a suspicious region candidate detecting apparatus for detecting a suspicious region candidate from the generated medical image data, the detecting apparatus being connected with the generating apparatus through a communication network; a network monitoring section for monitoring a communication load of the communication network; and a time setting section for setting an image transmission time for transmitting the medical image data from the generating apparatus to the detecting apparatus on the basis of a monitoring result of the communication load. The generating apparatus transmits the medical image data to the detecting apparatus at the set image transmission time.
Owner:KONICA MINOLTA INC
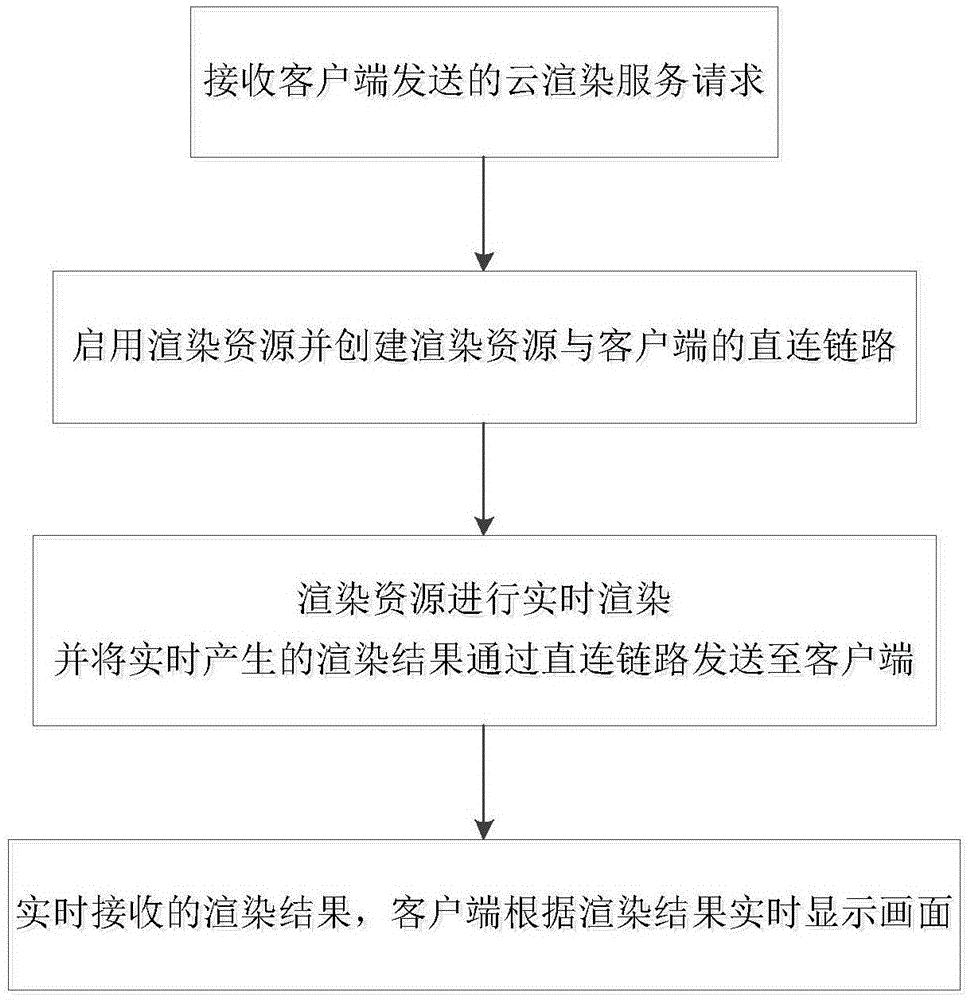
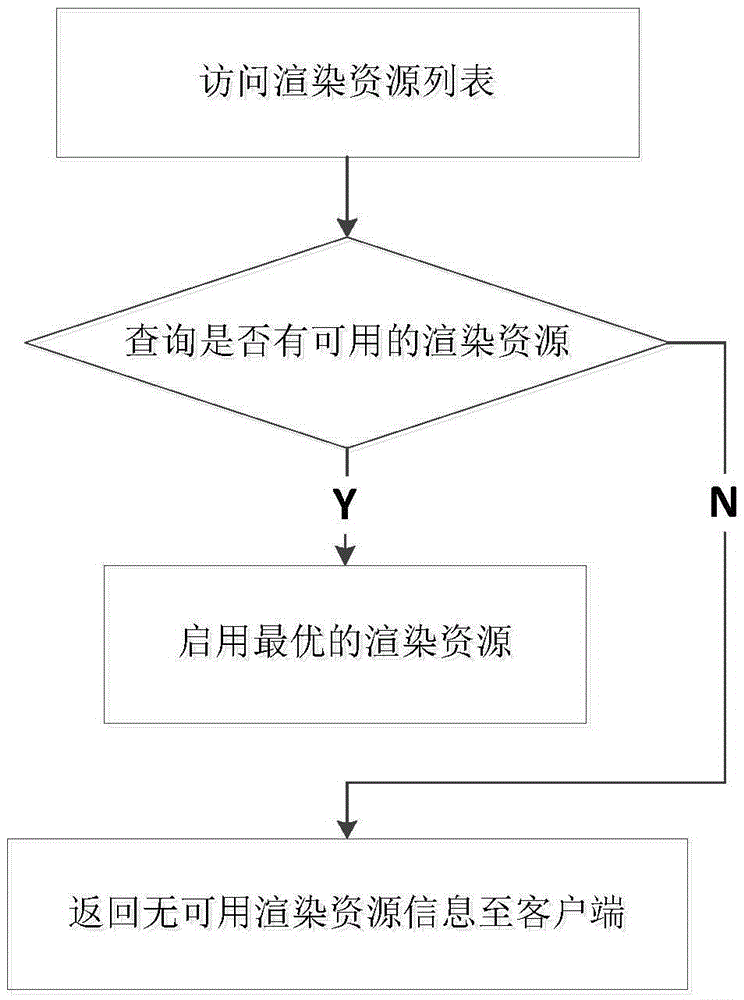
Cloud computing based real-time off-screen rendering method, apparatus and system
ActiveCN105488837ALower latencyReduce communication loadTransmission3D-image renderingComputer graphics (images)Time delays
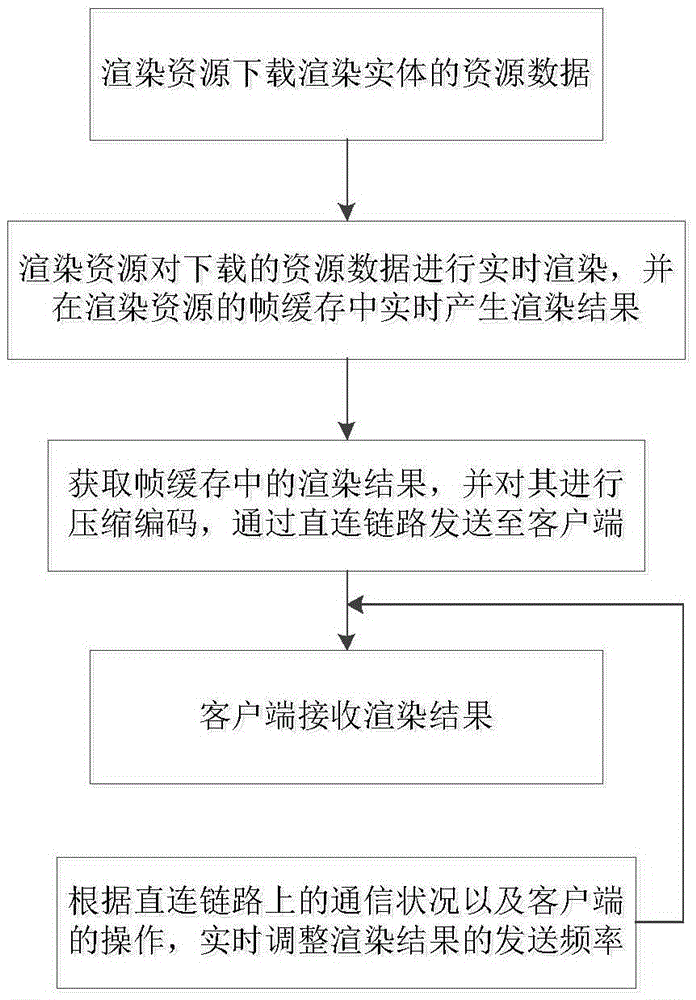
The invention discloses a cloud computing based real-time off-screen rendering method, apparatus and system. The method comprises: receiving a cloud rendering service request sent by a client; enabling a rendering resource and creating a direct connection link of the client and the rendering resource, so that the rendering resource can directly process the cloud rendering service request; performing real-time rendering by the rendering resource and directly sending a rendering result generated in real time to the client; and enabling the client to receive the rendering result in real time and display a picture according to the rendering result. Numerous client devices that are online at the same time can be supported, massive rendering service requests of the client devices can be born, and all online rendering tasks are independent mutually, so that the communication load of a cloud end is reduced and the time delay of a cloud rendering service is shortened.
Owner:成都云创互联信息技术有限公司
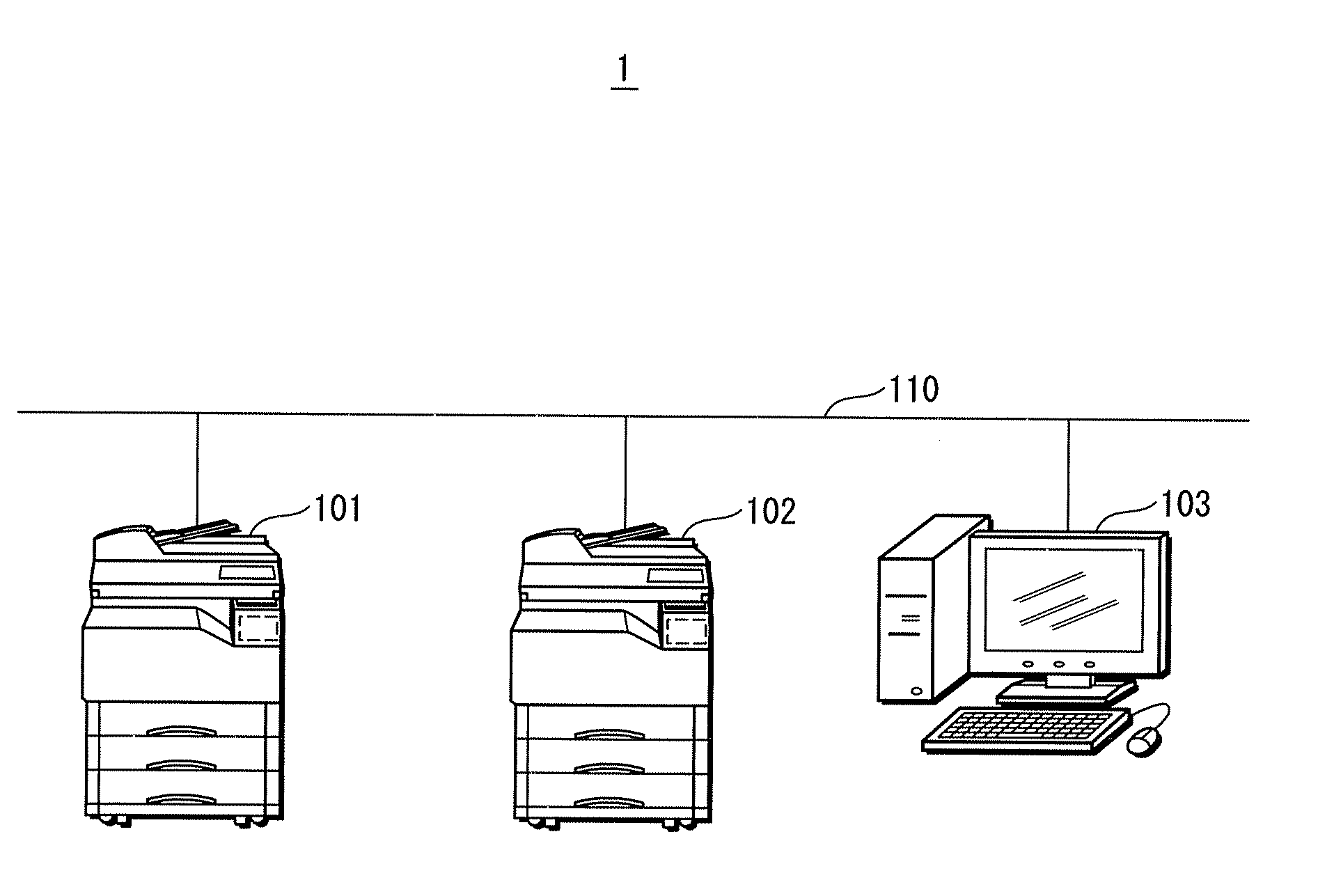
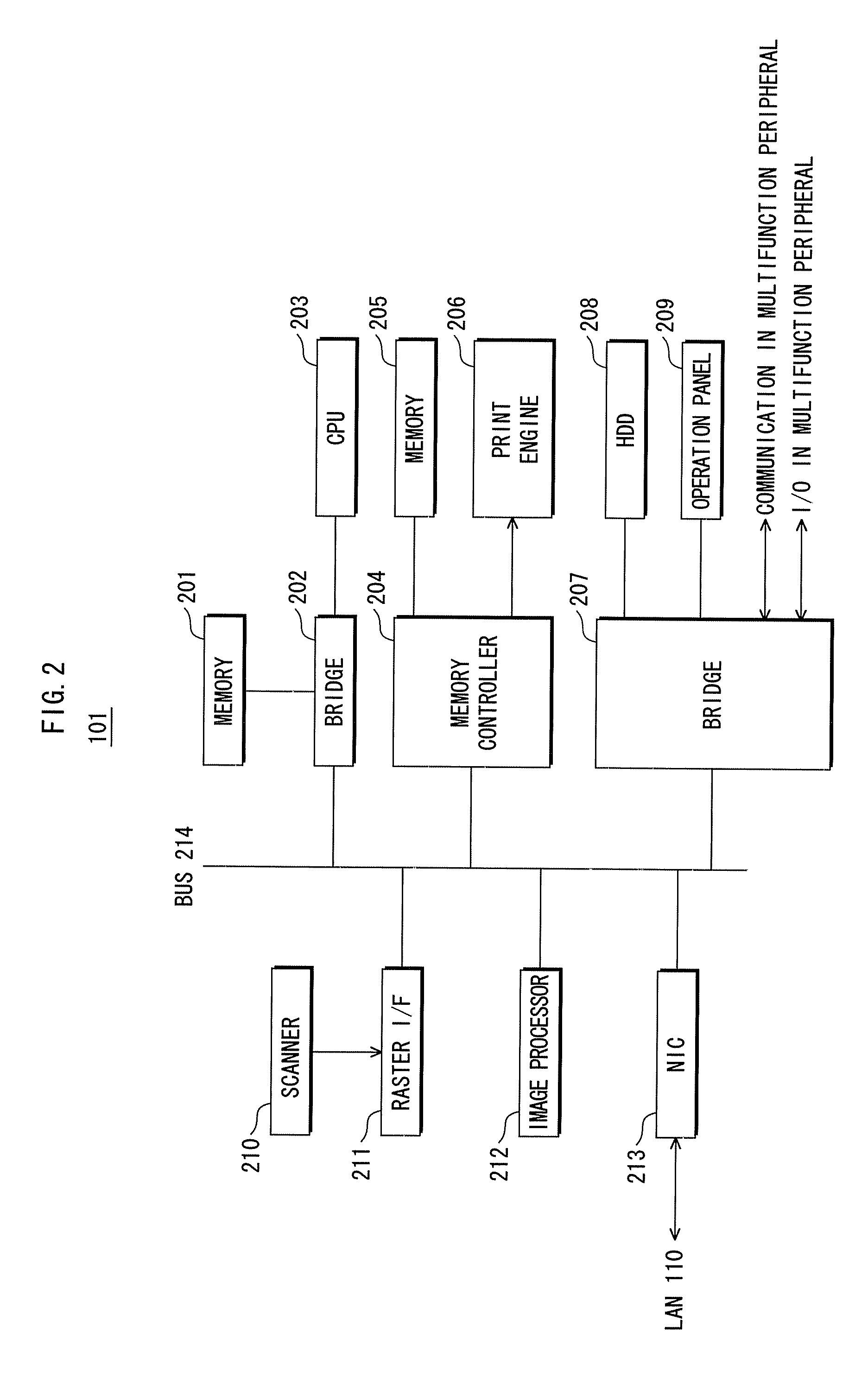
Printing system, image forming apparatus, processing method thereof, and program
ActiveUS20130003125A1Reduce communication loadVisual presentation using printersDigital output to print unitsImage formationComputer science
An image forming apparatus that stores print data transmits identification information for identifying itself to another image forming apparatus that includes a notification image forming apparatus is storing print data. When printing print data, the image forming apparatus requests a list of image forming apparatuses in which print data is stored from the another image forming apparatus. The image forming apparatus requests a list of print data from image forming apparatuses corresponding to the received.
Owner:CANON SALES CO
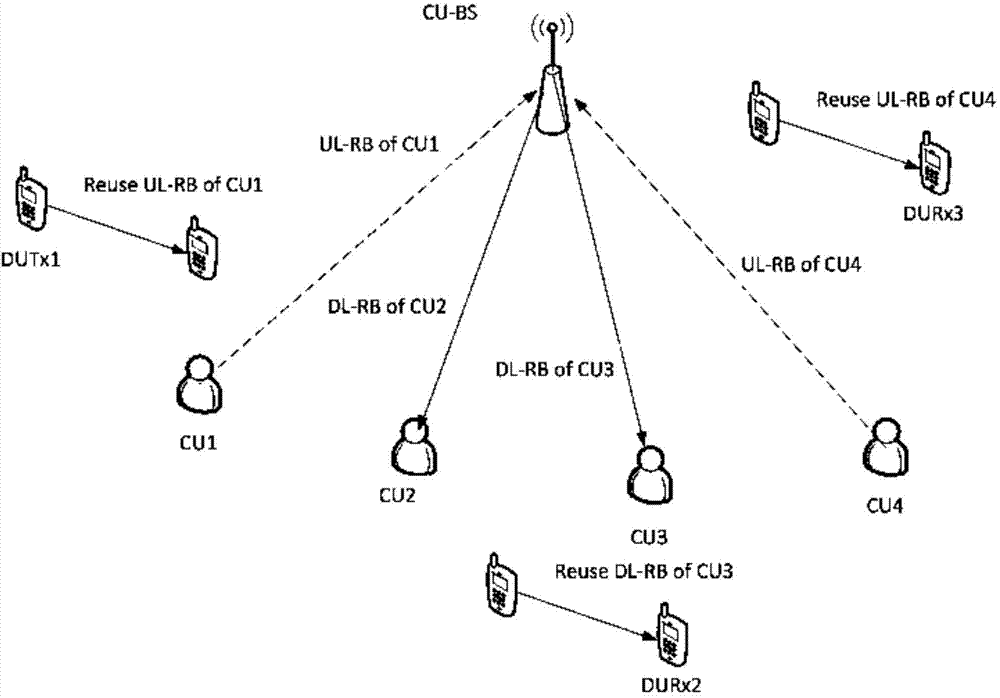
Distributed power control method based on energy efficiency optimization in D2D communication
ActiveCN103716869AReduce communication loadIncrease profitEnergy efficient ICTPower managementResource utilizationMulti variable
A distributed power control method based on energy efficiency optimization in D2D communication comprises the following steps: (1) a D2D user and a cellular user realize D2D user energy efficiency optimization on the basis of ensuring user transmission quality through a user distributed transmission power control method, wherein the optimization problem is described as a multi-variable non-convex optimization problem; (2) the problem P1 is converted into a single-user transmission power control optimization problem; and (3) the users carry out power control and optimize the user energy efficiency in a transmission power range in order to guarantee the minimum quality service. The distributed power control method based on energy efficiency optimization in D2D communication, provided by the invention, is capable of reducing the communication load of a base station, improving the spectrum utilization rate, enhancing the scalability and security and improving the resource utilization rate.
Owner:ZHEJIANG UNIV OF TECH
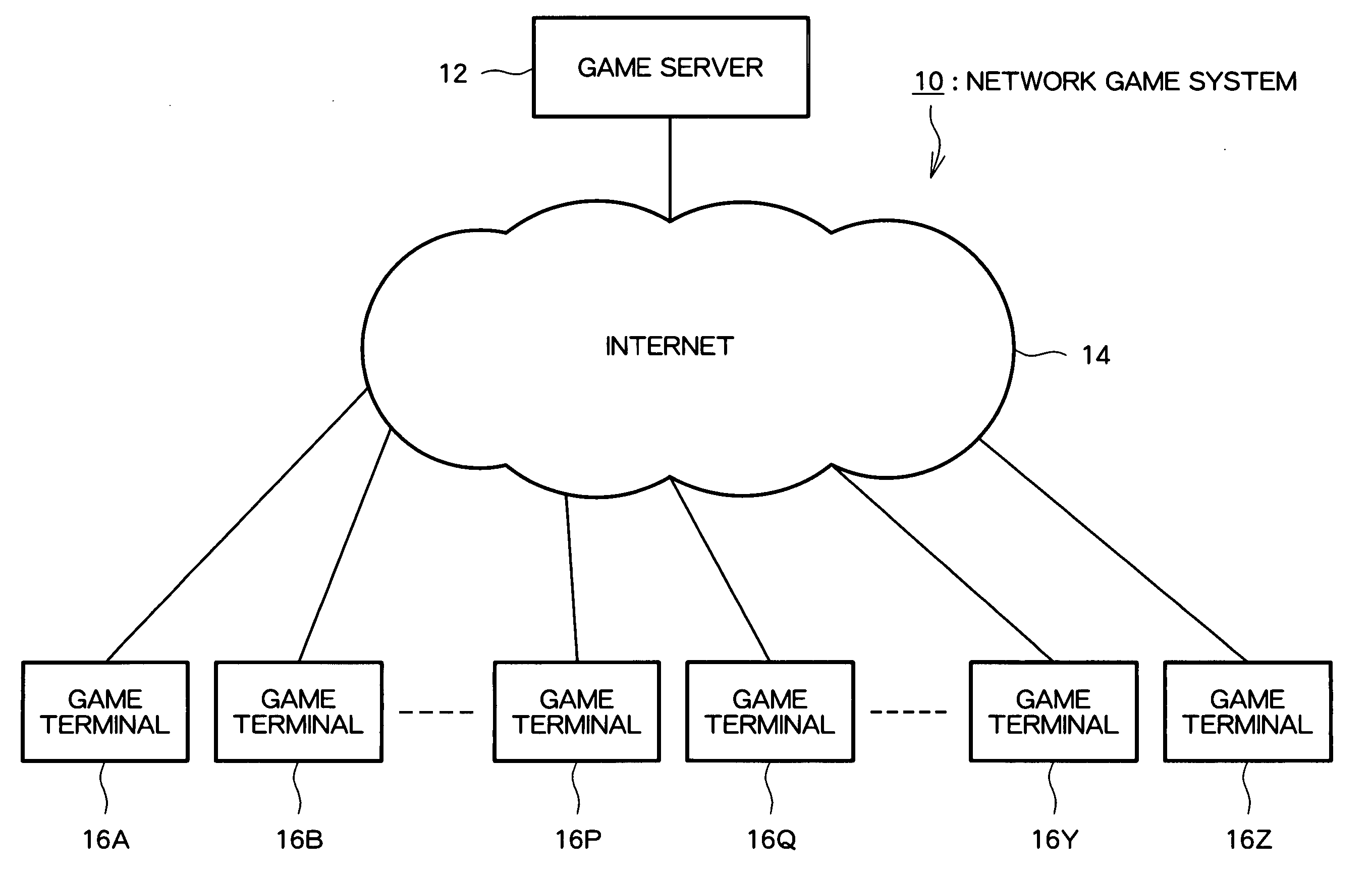
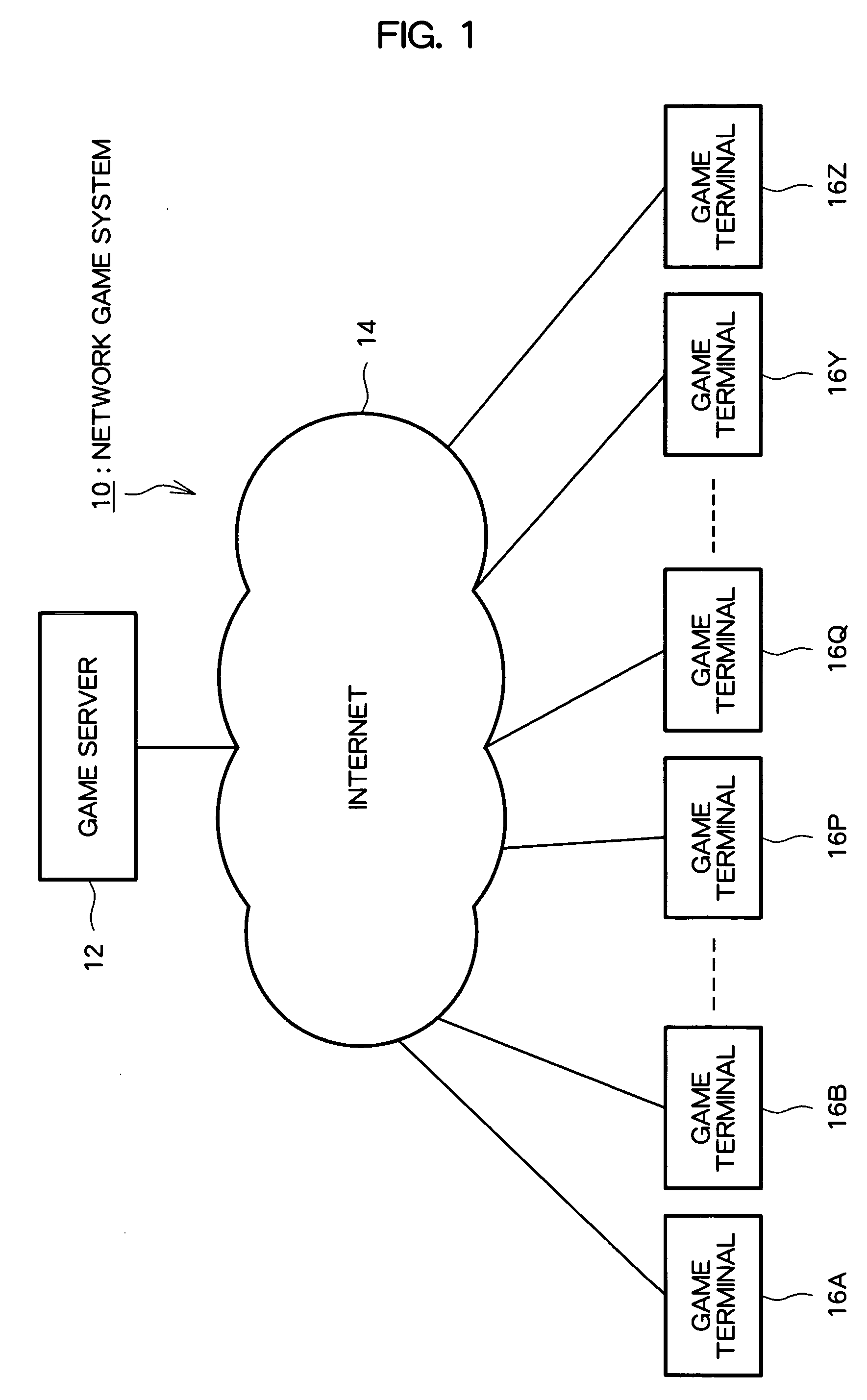
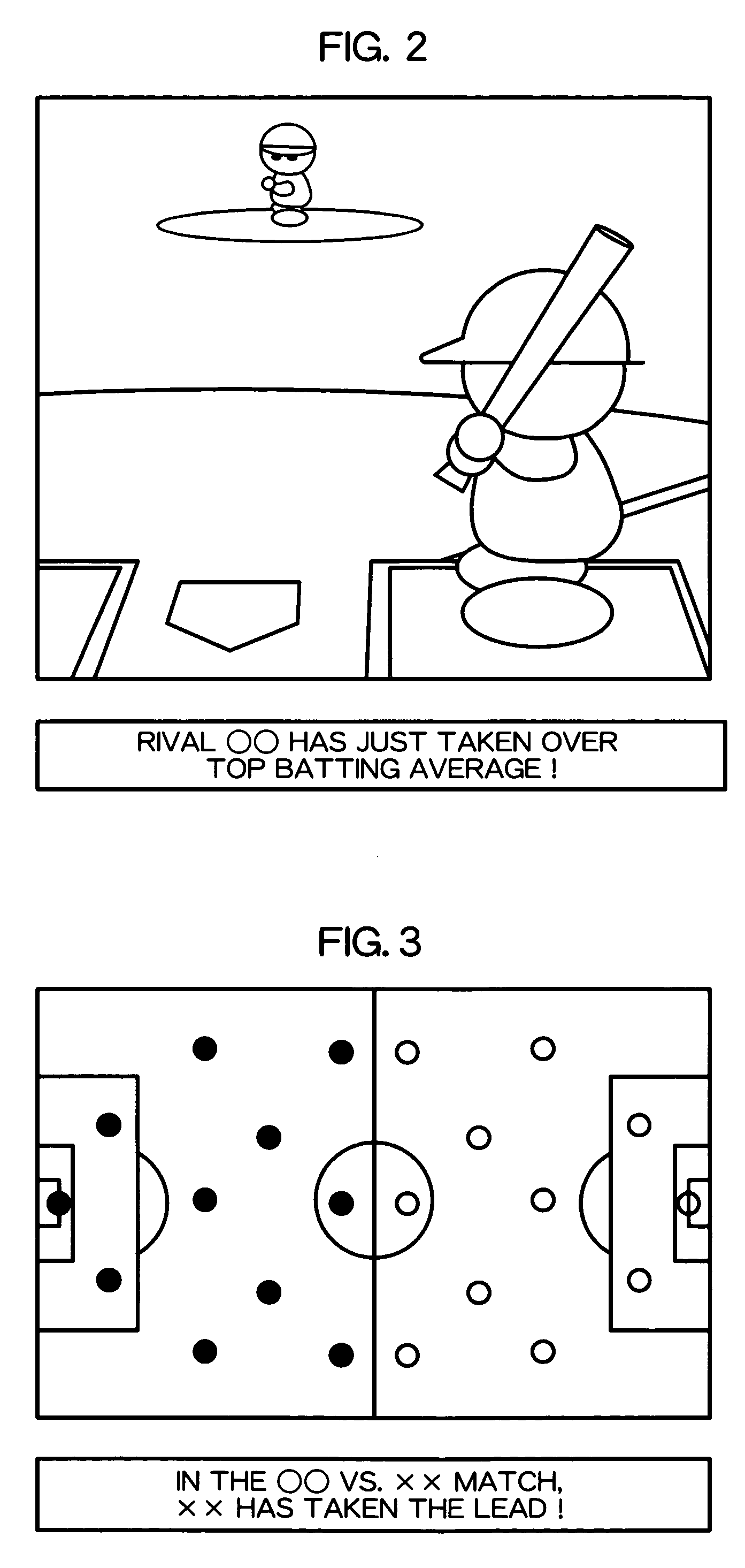
Game system, game system control method, and program
InactiveUS20050282635A1Reduce communication loadImprove representationVideo gamesSpecial data processing applicationsPairingGame server
A network game system capable of representing a sense of the existence of players other than the immediate contest opponent, with a light communication load. In a game system for serving multiple contest games, a game server (12) used together with multiple game terminals includes a contest pairing determination part (22) for determining contest pairings in contest games; a contest game start command part (32) for transmitting a contest game start command to game terminals corresponding to contest pairings determined by the contest pairing determination part (22); a parameter change command destination determining part (26) for, when in a contest game executed by game terminals in accordance with the contest game start command a predetermined game event such as a point-scoring occurs, receiving event details data expressing details of the predetermined game event and determining destinations of parameter change commands corresponding with the event details data; and a parameter change command part (36) for sending the parameter change commands to the destinations determined by the parameter change command destination determining part (26).
Owner:KONAMI DIGITAL ENTERTAINMENT CO LTD
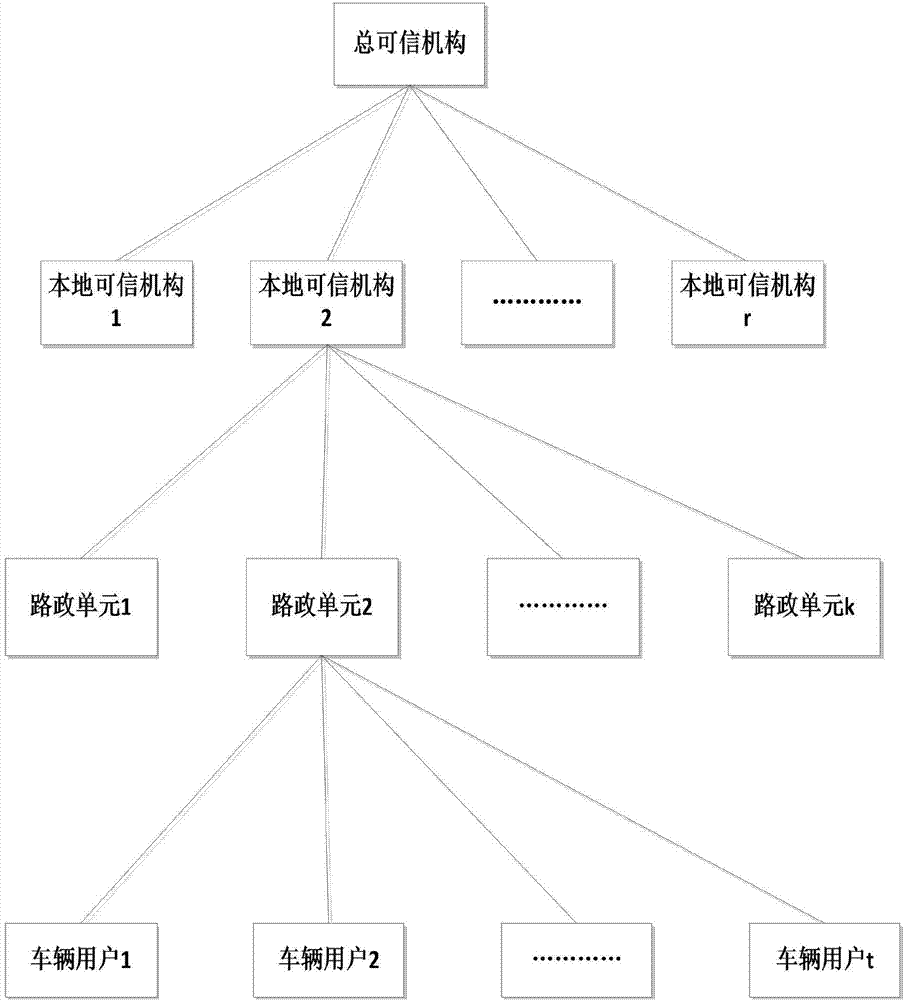
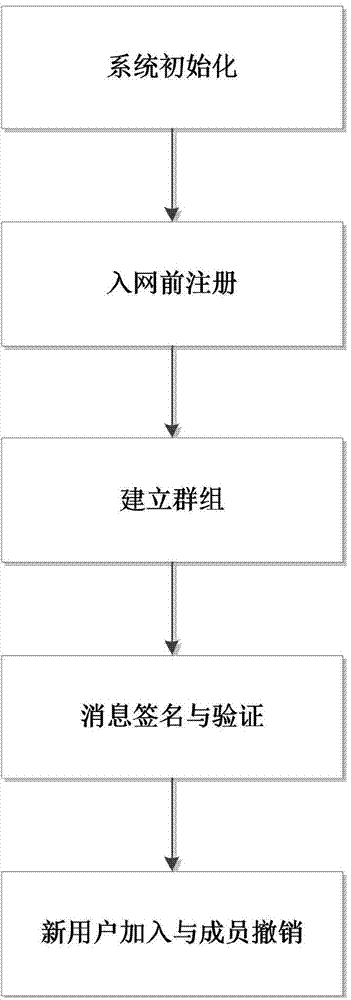
Group signature method with efficient revocation in vehicle networking
ActiveCN104753683AImprove real-time update efficiencyEfficient undoUser identity/authority verificationIn vehicleBroadcasting
The invention discloses a group signature method with efficient revocation in vehicle networking with an aim to mainly solve the problem that revocation of group members affects key pairs of group members without revocation in the prior art. According to the technical scheme, the group signature method includes: 1, initiating a system and generating parameters and public key pairs of a general trusted mechanism, a local trusted mechanism and a road administration unit; 2, vehicle users registering in the local trusted mechanism before access to the networking and receiving blind certificates; 3, the road administration unit establishing groups, the vehicle users in the jurisdictional scope submitting the blind certificates and joining in the groups after identity legitimacy is verified; 4, after the group members join in the groups, subjecting messages to signing and broadcasting, and anybody verifying the messages; 5, when new users join in the groups or in case of revocation of the members, the road administration unit calculating and publishing new public keys. With the method, efficient and safe joint and revocation in the road administration in the vehicle networking and anonymity of the users to the road administration can be realized, and track on user mobile trajectories is avoided.
Owner:XIDIAN UNIV
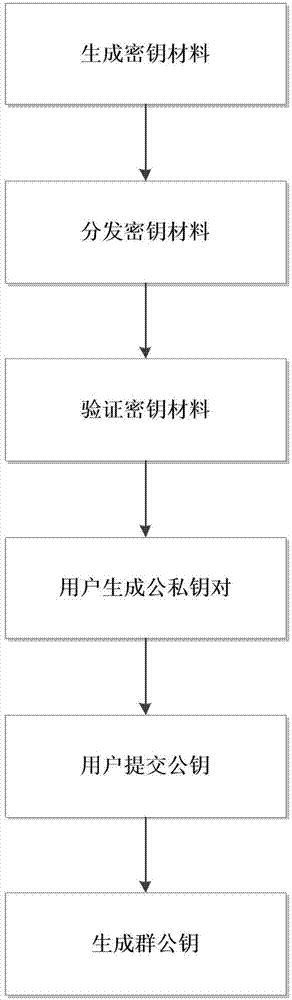
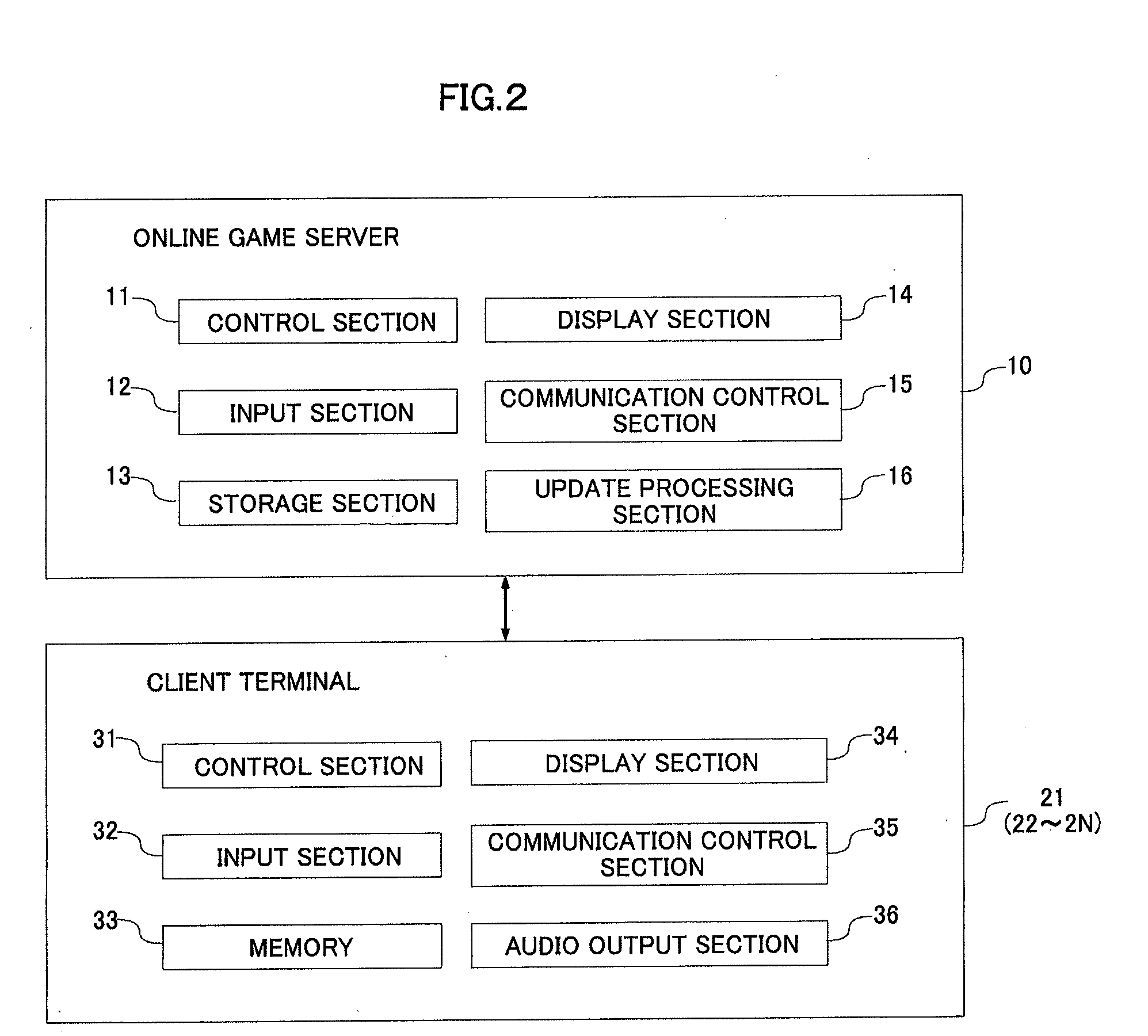
Online game system and online game program
ActiveUS20090137321A1Reduce communication loadAvoid mistakesData processing applicationsVideo gamesComputer terminalGame server
In an online game server, an updater updates at least one of a game program and game data for server stored in a storage section in accordance with an update operation for data to be utilized when to execute a sub game other than a main game in an online game. Updated portion data are a shared library format that can be utilized in the client terminal. A transmitter transmits updated data including at least the updated portion data to the client terminal. In a client terminal, a rewriter rewrites at least one of a game program and game data for client stored in a memory. In the case where there is a specification operational input by a player, a controller controls progress of the online game using the game program or the game data for client without carrying out communication with the online game server.
Owner:SQUARE ENIX HLDG CO LTD
WSN (Wireless Sensor Network) abnormity detection method and system based on artificial immunization and k-means clustering
InactiveCN105791051AImprove search efficiencyPrecise positioningPower managementNetwork topologiesAnomaly detectionArtificial immune algorithm
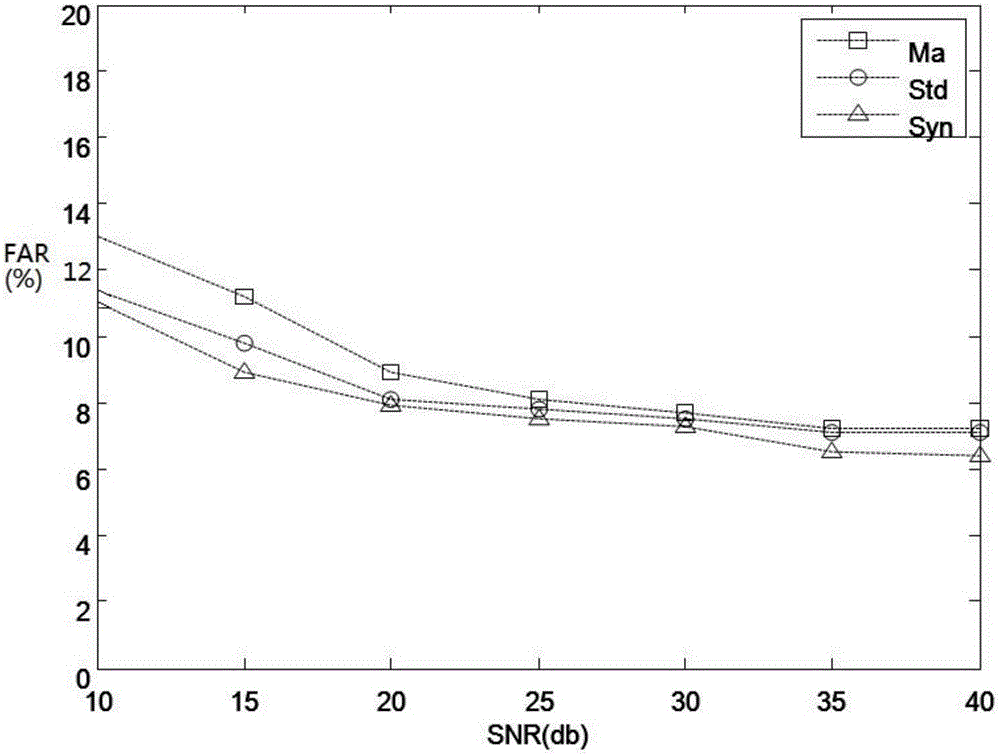
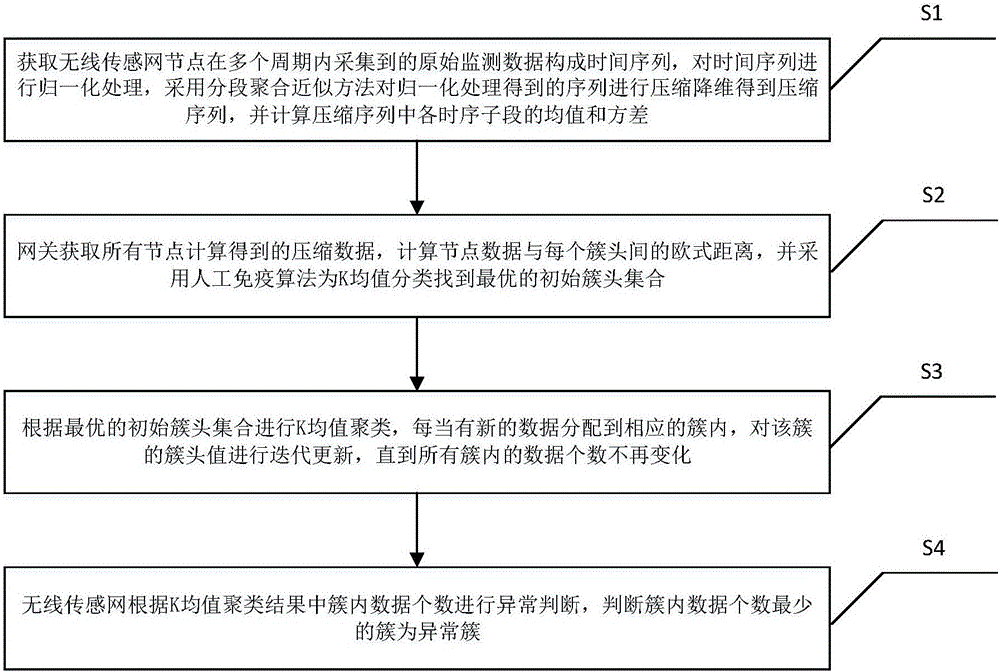
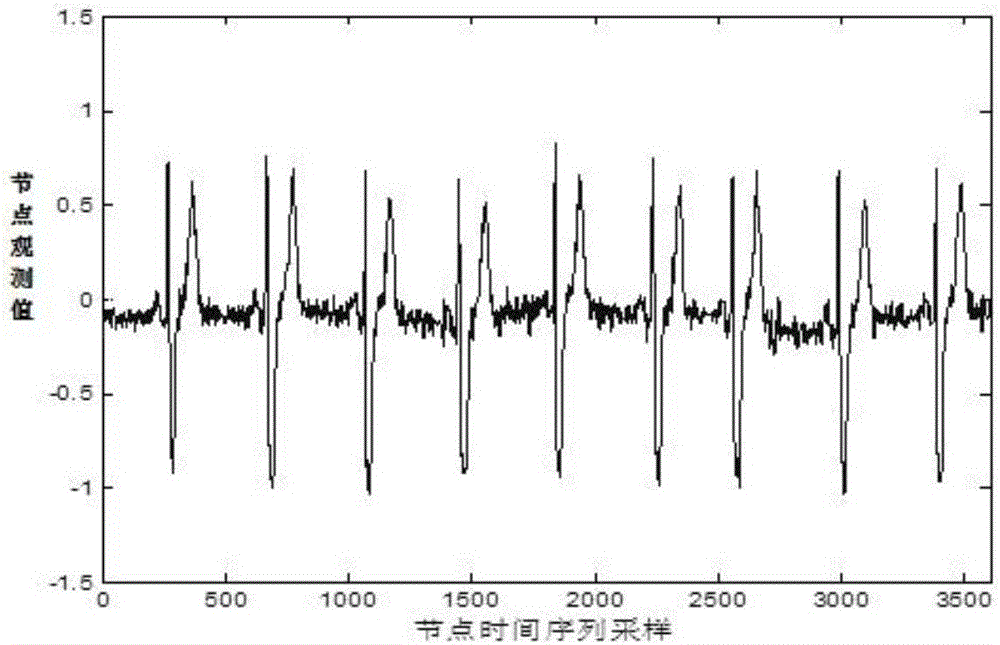
The invention discloses a WSN abnormity detection method and system based on artificial immunization and k-means clustering. The method comprises that S1) original monitoring data collected by WSN nodes is obtained to form a time sequence, the time sequence is normalized, compression and dimension reduction are carried out on the normalized sequence, and the mean value and variance of each sequential segments in the compressed sequence are calculated; S2) the Euclidean distance between node data and each cluster head is calculated, and an artificial immunization algorithm is used to search an optimal initial cluster head set for K-means classification; S3) whenever new data is distributed into a corresponding cluster, iterative update is carried out on the cluster head value of the cluster till the amount of all data in the cluster does not change; and S4) the WSN determines abnormity according to the amount of data in the cluster in a K-means clustering result. According to the invention, abnormity information in monitoring data can be discovered accurately, the instantaneity and reliability of abnormity event detection of the WSN are improved, and energy and communication bandwidth of the WSN are greatly reduced.
Owner:CHINA UNIV OF GEOSCIENCES (WUHAN)
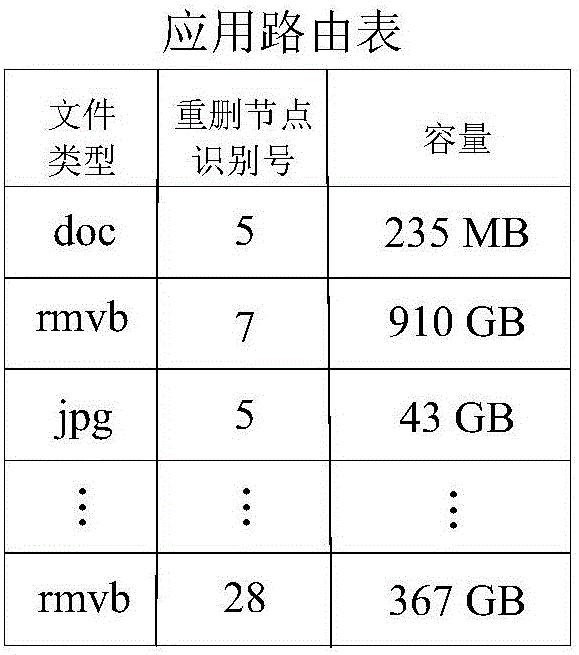
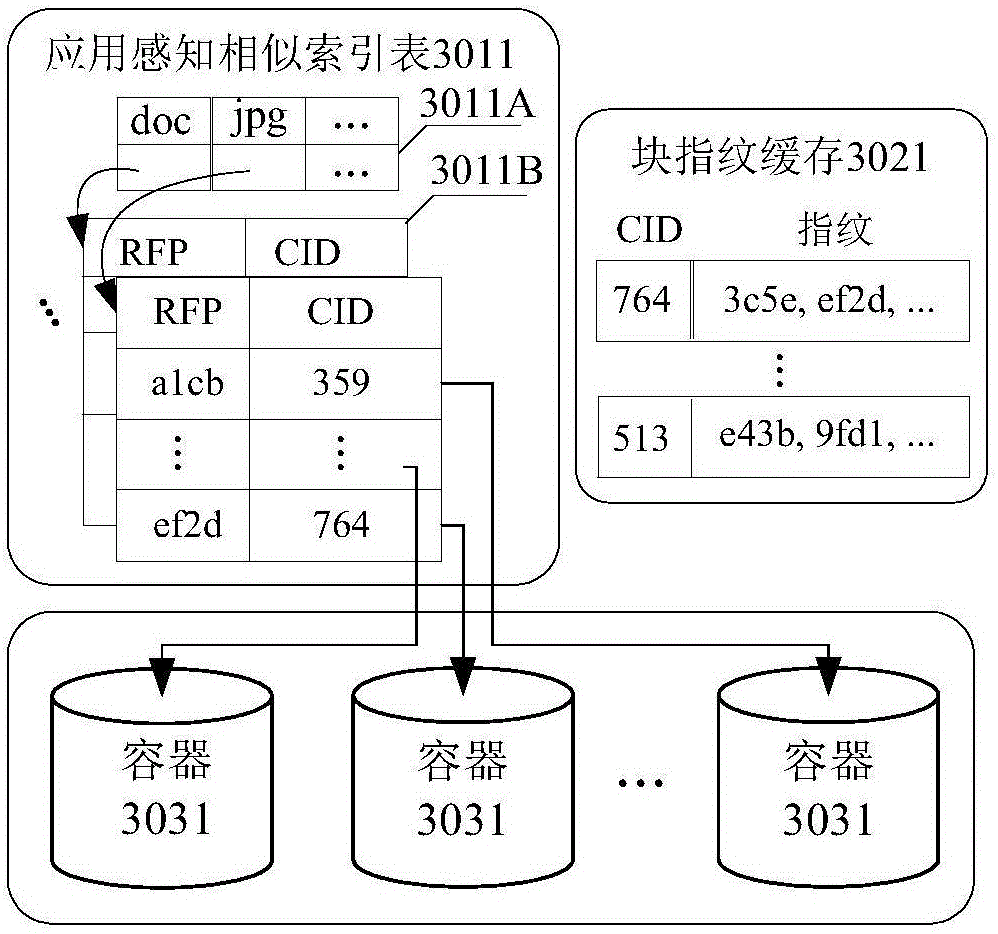
Application sensitive big data de-duplication storage system and method
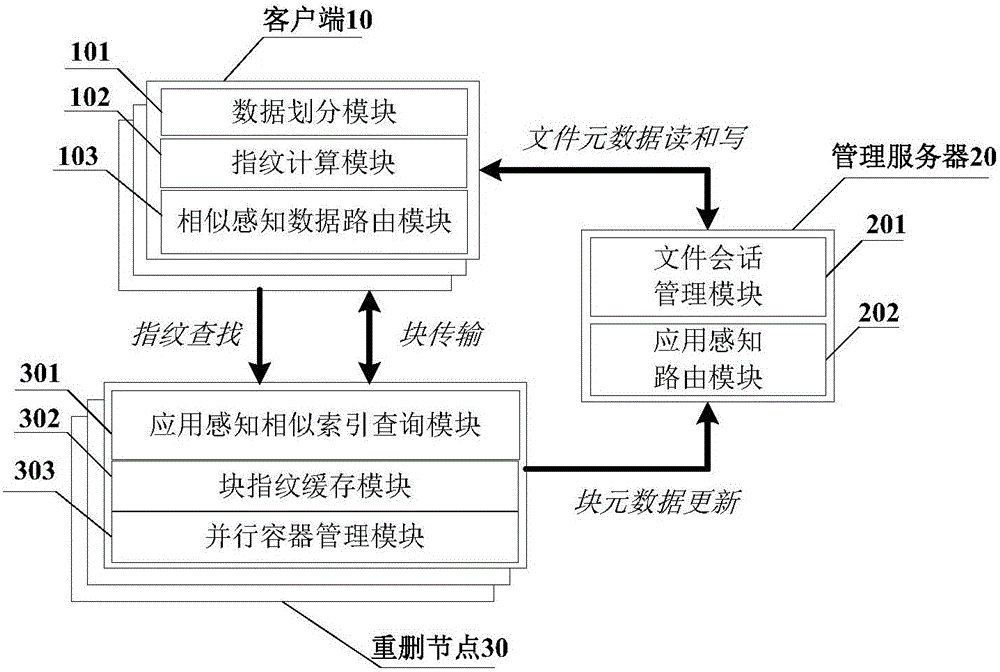
ActiveCN106066896AReduce communication loadImprove scalabilitySpecial data processing applicationsNetwork communicationLoad capacity
The invention discloses an application sensitive big data de-duplication storage system and method. The system comprises clients interconnected on the basis of a computer network, a management server and de-duplication nodes. The clients and the management server determine a de-duplication node list for application file storage through an application sensitive routing method, and the clients and the de-duplication nodes determine target de-duplication nodes from the de-duplication node list through a similar sensitive routing method. The system also comprises super blocks used for storing application files. The application files are stored and managed through the system, so that the application files same in type can be stored in the same de-duplication nodes, the load capacity of network communication can be effectively reduced, the improvement on the de-duplication rate and the improvement on the storage throughput rate of each de-duplication node are also facilitated, and the network expandability is enhanced.
Owner:PLA UNIV OF SCI & TECH
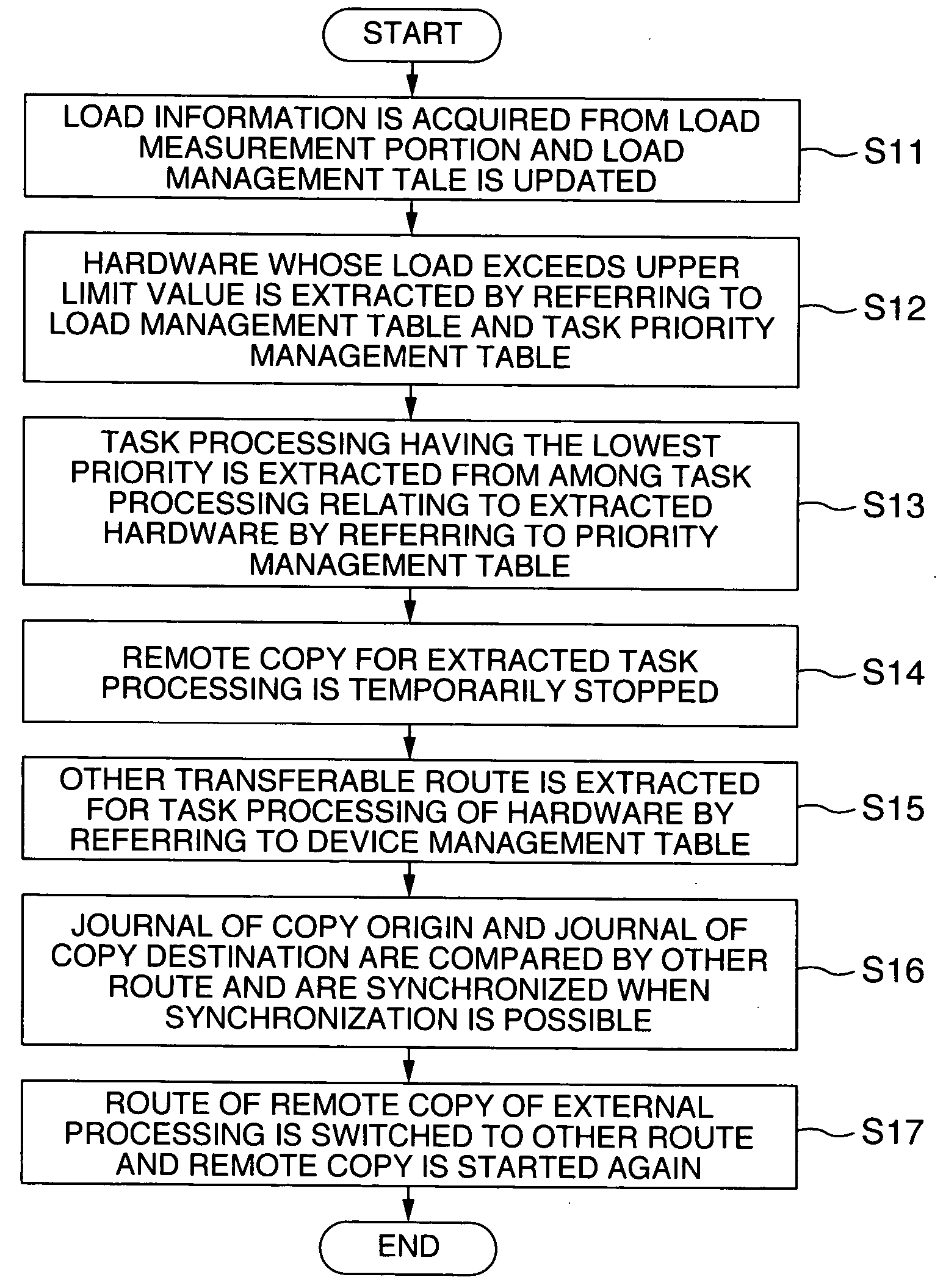
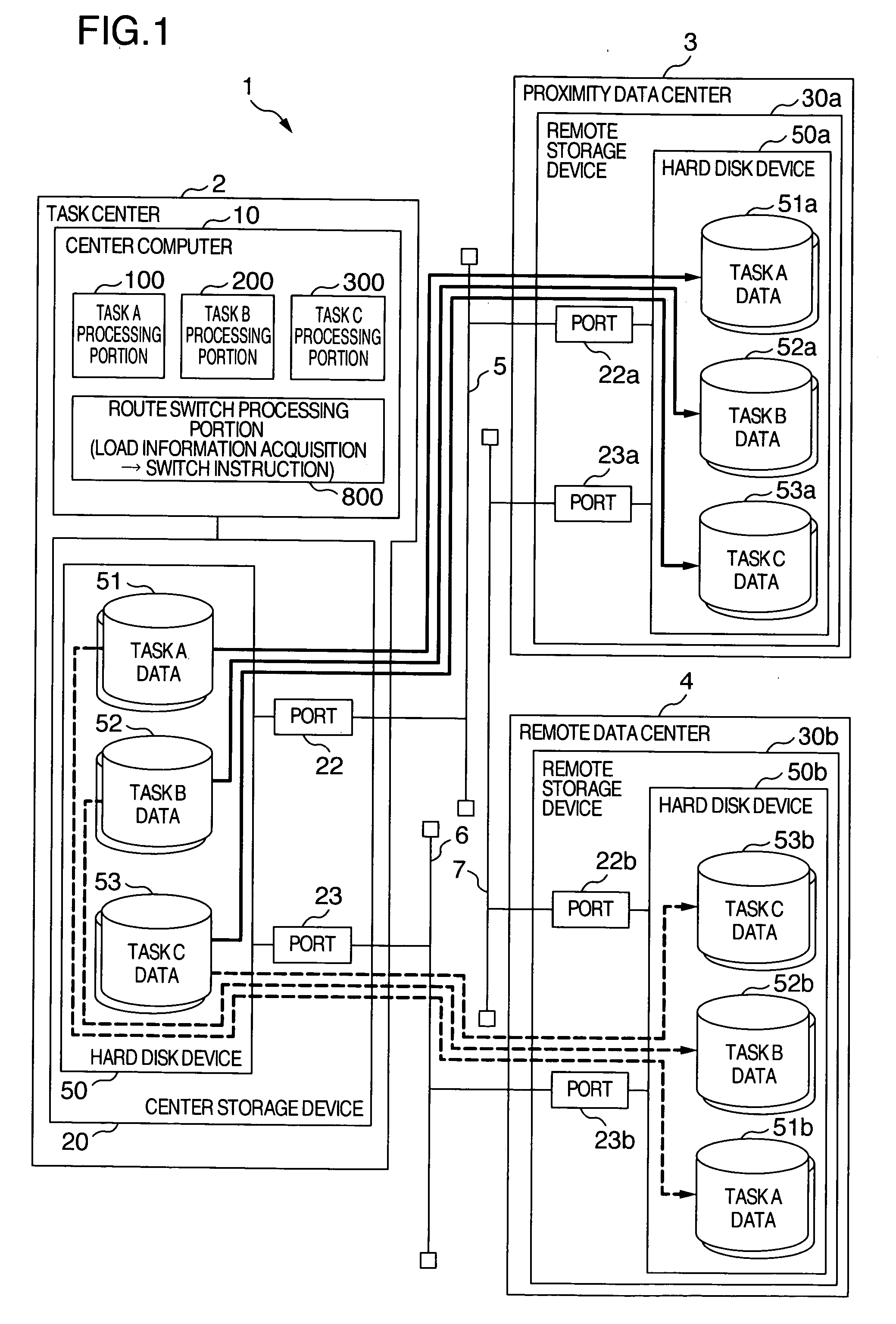
Remote copy storage device system and a remote copy method
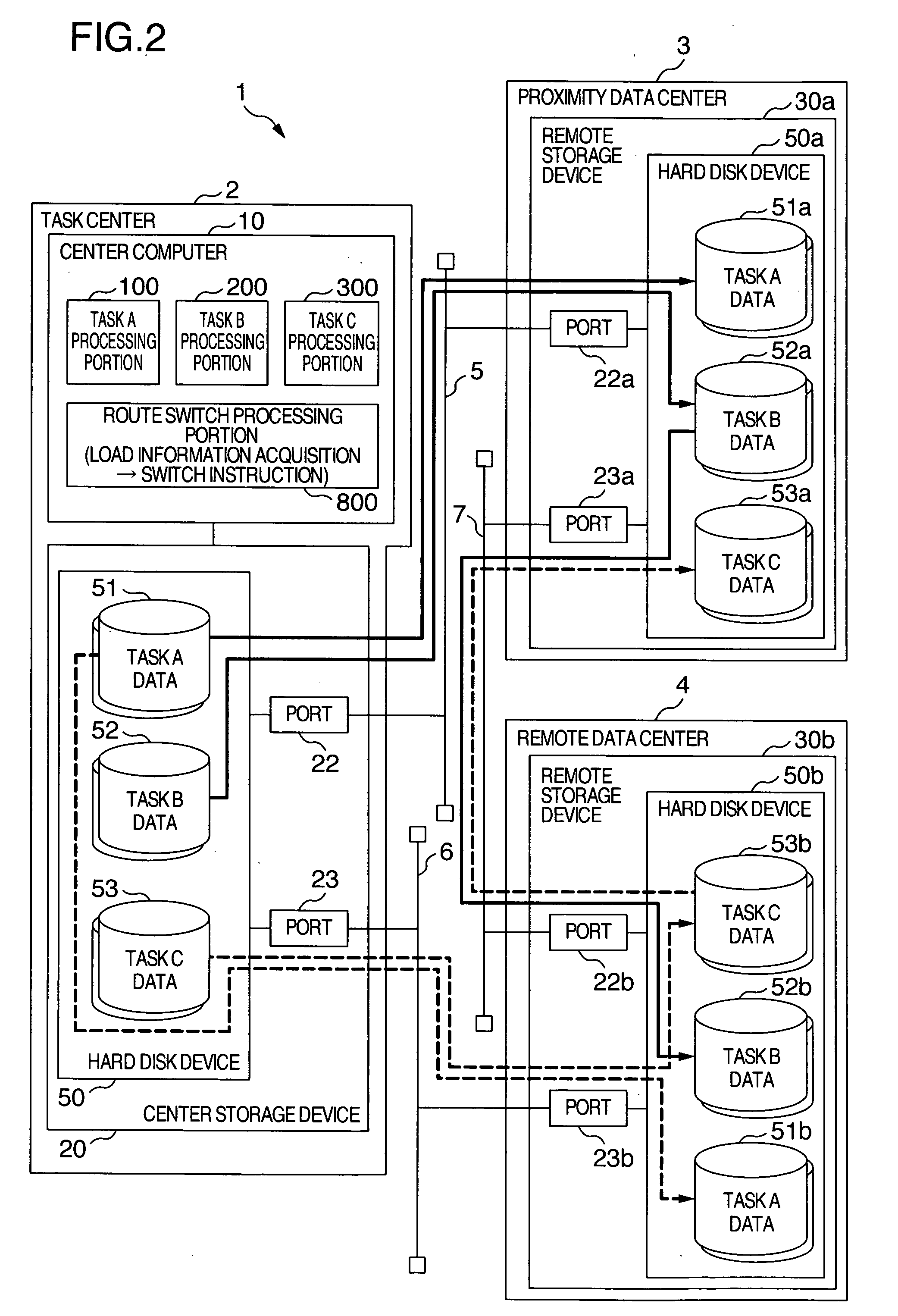
InactiveUS20070118840A1Reduce communication loadReduce loadInput/output to record carriersMultiprogramming arrangementsLoad measurementThroughput
Overload of communication lines and the drop of through-put of task processing in a center computer is prevented. The center computer executes a plurality of task processing, writes the execution result to a center storage device and remote copies the same data to a plurality of remote storage devices. At this time, the center computer acquires loads of communication lines through load measurement portions and stops the execution of a part of the task processing involved with the transmission of the copy data through the communication line when its load exceeds a predetermined threshold value. When the center storage device and the remote storage devices switch the transmission route of the copy data to other route, the center computer starts again the execution of the task processing previously stopped and starts again the remote copy.
Owner:HITACHI LTD
Vehicle-mounted diagnosis processing method and terminal based on wearable equipment
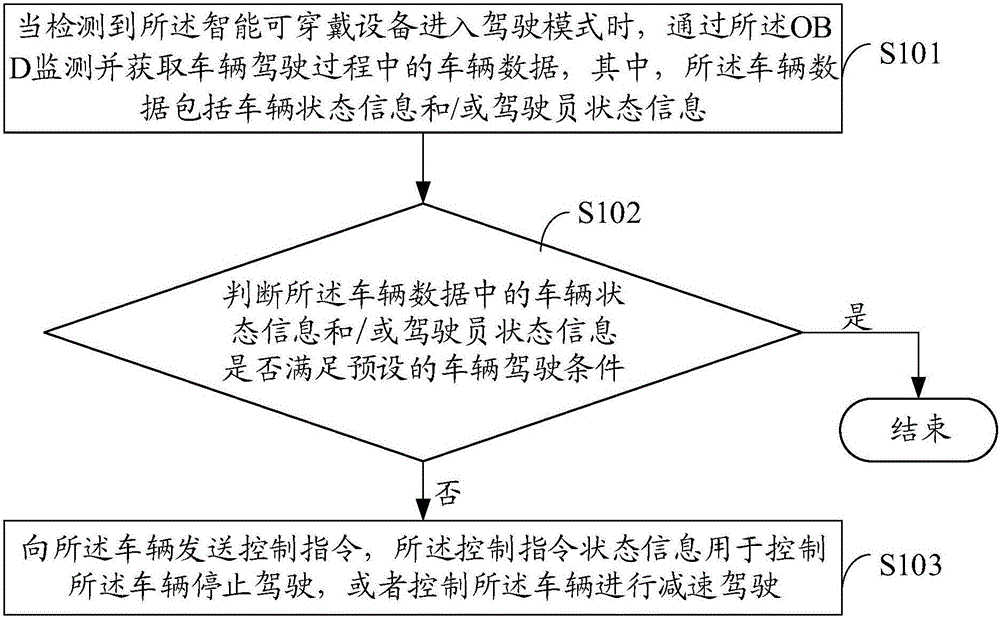
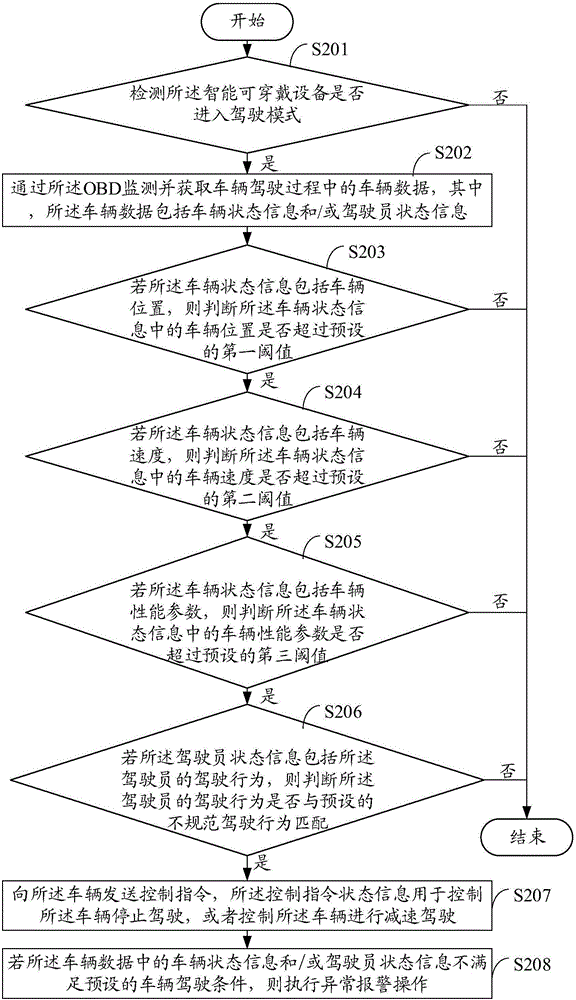
InactiveCN105959021AReduce communication loadReduce dependenceProgramme controlComputer controlIn vehicleComputer terminal
The embodiment of the invention provides a vehicle-mounted diagnosis processing method and terminal based on wearable equipment. The intelligent wearable equipment is provided with a built-in vehicle-mounted diagnosis system OBD. The method comprises the steps: monitoring and obtaining the vehicle data in a driving process through the OBD when the intelligent wearable equipment is monitored to enter in a driving mode, wherein the vehicle data comprises vehicle state information and / or driver state information; judging whether the vehicle state information and / or driver state information in the vehicle data meet / meets a preset vehicle driving condition or not: transmitting a control instruction to the vehicle if the vehicle state information and / or driver state information in the vehicle data do / does not meet the preset vehicle driving condition, wherein the control instruction is used for controlling the vehicle to stop, or controlling the vehicle to reduce the speed. According to the invention, the method can reduce the communication load and dependence of the vehicle, and improves the safety of the vehicle in a driving process.
Owner:LAUNCH TECH CO LTD
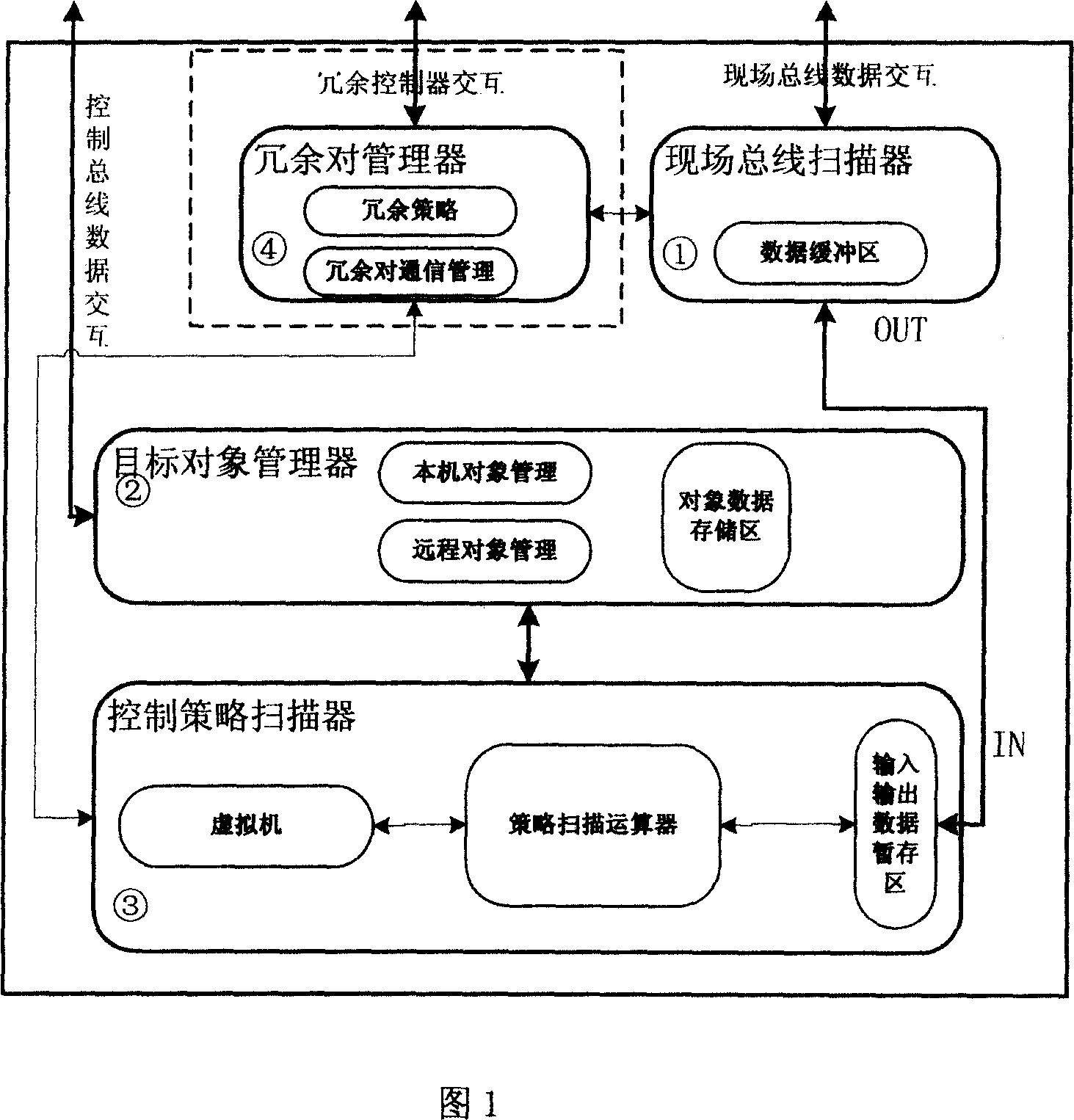
General industrial controller
ActiveCN1945480AReduce communication loadGuaranteed redundancyTotal factory controlProgramme total factory controlControl functionControl bus
The invention discloses a general industrial controller, including a general industrial computer, a control bus and a controller. The controller includes site bus scanners, target manager, control strategy scanners and redundancy couple manager. The site bus scanner realizes the reception and sending of the real-time data on control bus. The target manager conducts a transparent visit to all the real-time data on all the nodes of control bus and can regulate the number of nodes. The control strategy scanner makes each node use different general industrial computer to operate according to different functions, and manages on-line and schedules each control function block. The redundancy couple manager realizes the mutual interaction between the two machines for hot standby, to judge their own state and other state to inform each other, and switch when necessary, and transmit the data for the inverse calculations of guard machine function block.
Owner:NANJING SCIYON AUTOMATION GRP
File server device arranged in a local area network and being communicable with an external server arranged in a wide area network
ActiveUS8316134B2Reduce loadIncrease loadData switching by path configurationMultiple digital computer combinationsFile area networkFile server
Communication is established between communication terminals arranged in different LANS while realizing dynamic response to reduction in server load, movement of communication terminal, and the like. A relay server is arranged in a LAN and can communicate with an SIP server arranged in a WAN. For instance, a first relay server exchanges account information of the communication terminals in the respective LAN with a second relay server. If exchanged account information is changed in one relay server, the account information after the change is notified to the other relay server. One relay server determines the other relay server based on the exchanged account information and relays communication data between the communication terminals through the other relay server.
Owner:MURATA MASCH LTD
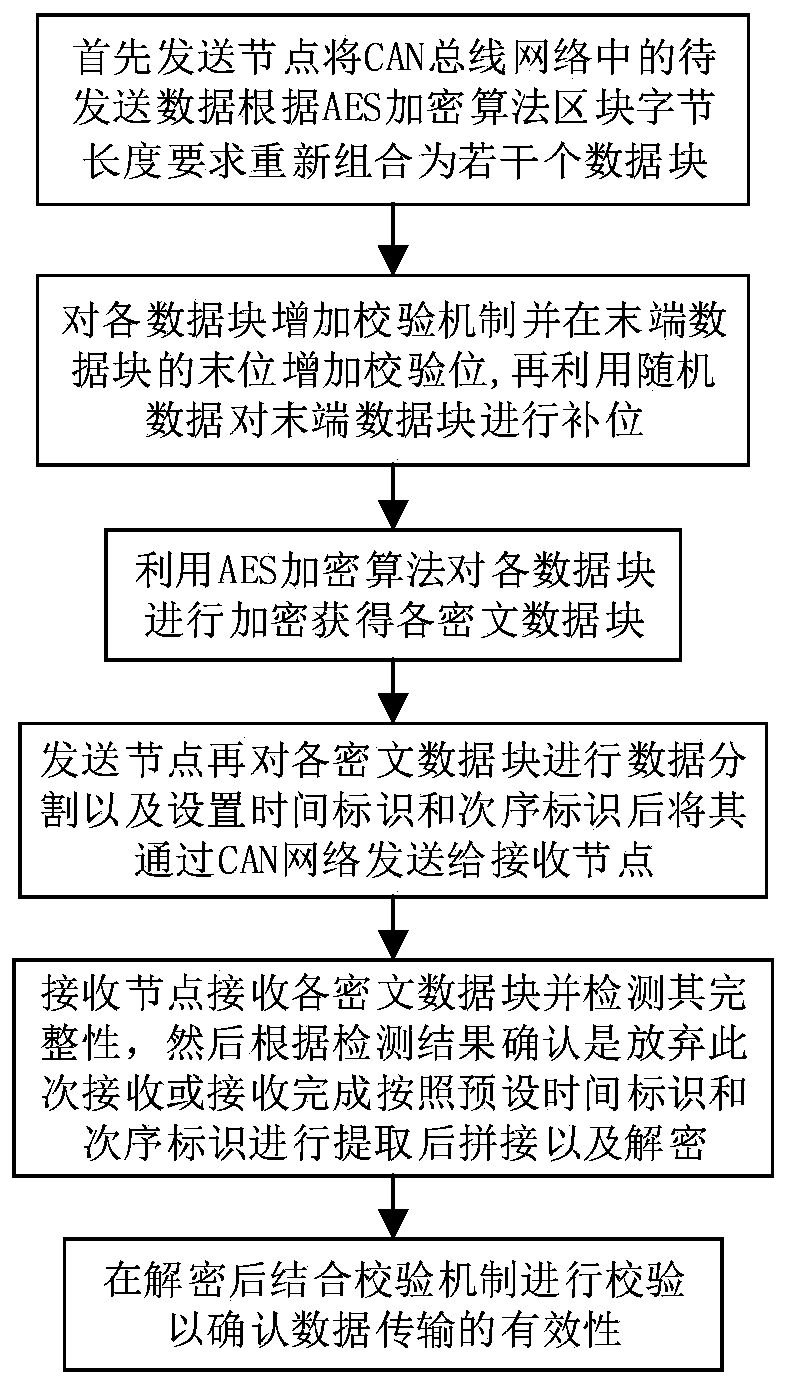
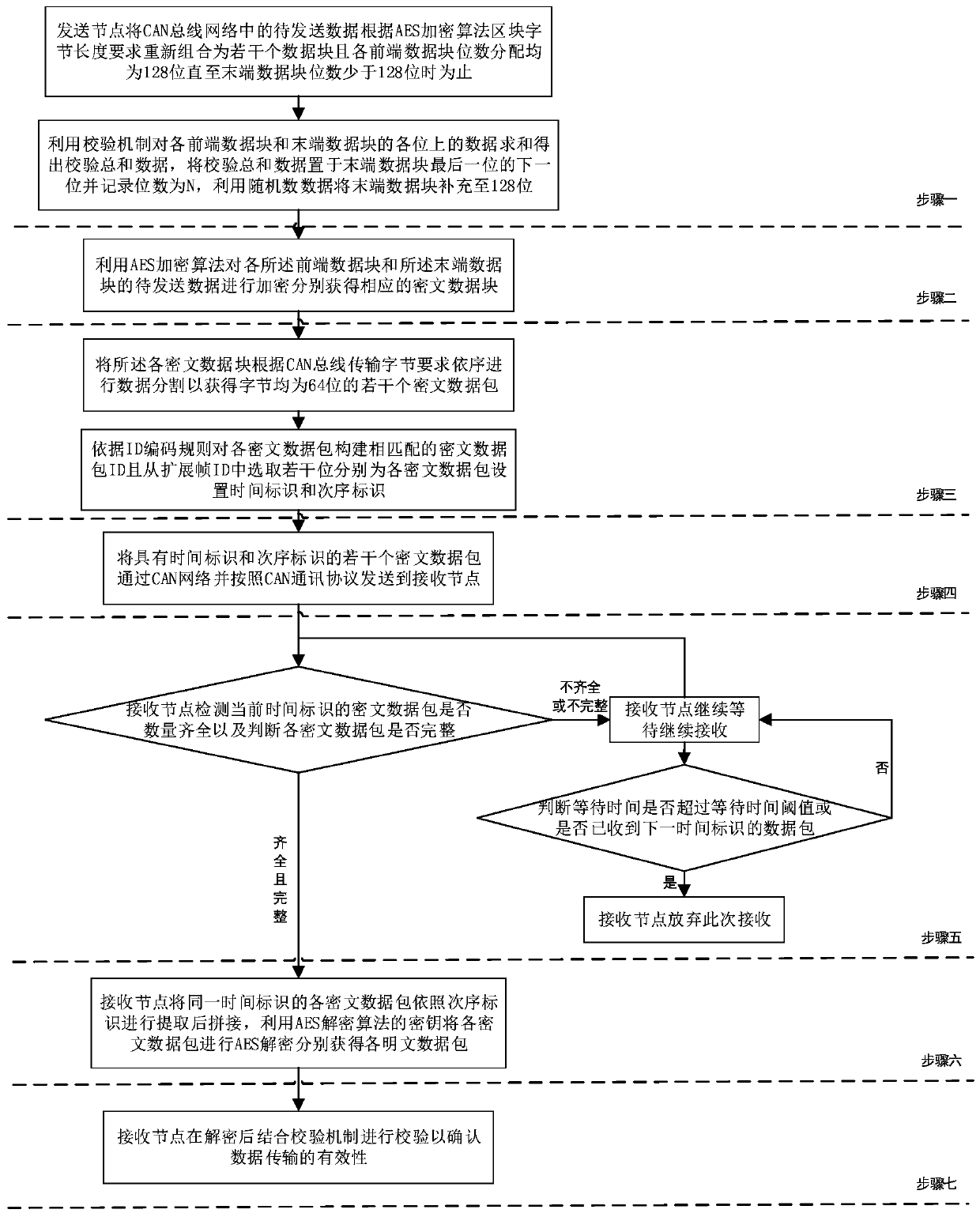
Automobile CAN bus encryption method
ActiveCN110545257AEnsure safetyReduce communication loadEncryption apparatus with shift registers/memoriesBus networksCiphertextData information
The invention relates to an automobile CAN bus encryption method. The method includes: firstly enabling a sending node to recombine to-be-sent data in a CAN bus network into a plurality of data blocksaccording to an AES encryption algorithm block byte length requirement; adding a check mechanism to each data block and adding a check bit to the tail of the tail end data block; carrying out bit compensation on the tail end data block by utilizing random data; encrypting each data block by using an AES encryption algorithm to obtain each ciphertext data block; enabling the sending node to perform data segmentation on each ciphertext data block, set a time identifier and an order identifier and send the ciphertext data blocks to the receiving node through the CAN network; enabling the receiving node to receive each ciphertext data block and detect the integrity of each ciphertext data block; according to the detection result, confirming that that it is discarded that this time of receiving is completed or splicing and decryption are conducted after extraction is conducted according to the preset time identifier and the sequence identifier, carrying out verification in combination witha verification mechanism after decryption to confirm the effectiveness of data transmission. The data transmission efficiency is improved, and the safety of data information transmission on an automobile is guaranteed.
Owner:BEIJING HANGSHENG NEW ENERGY TECH CO LTD
Wireless body area network security access method
ActiveCN104301888AEnable secure accessReduce communication delayShort range communication serviceSecurity arrangementHand shakesAccess method
The invention discloses a wireless body area network security access method. Two interaction modes, namely, the unicast mode and the multicast mode, are set; two launching modes are set, and in other words, a network coordinator launches hand shaking and sensor nodes launch hand shaking; thus, when a certain part is injured and the blood pressure suddenly rises or in other words, the measurement indexes of a certain or some sensor nodes exceed the corresponding index limitations, the corresponding sensor nodes actively launch the hand shaking process, the situations of patients are rapidly fed back to medical staff, and patients are helped in time. According to the method, dynamic negotiation of a user conversation key is achieved through enhanced four-step hand shaking, hand shaking information is reduced, all the information is encrypted, the unicast access mode and the multicast access mode are set, and the remote access problem is solved through a multi-hop method. The method has the advantages that the access efficiency of a large number of sensing nodes is high, security is high, and the energy consumption is low, and the method can be used for the access of the sensing nodes in a wireless body area network and the dynamic negotiation of the user conversation key.
Owner:XIDIAN UNIV
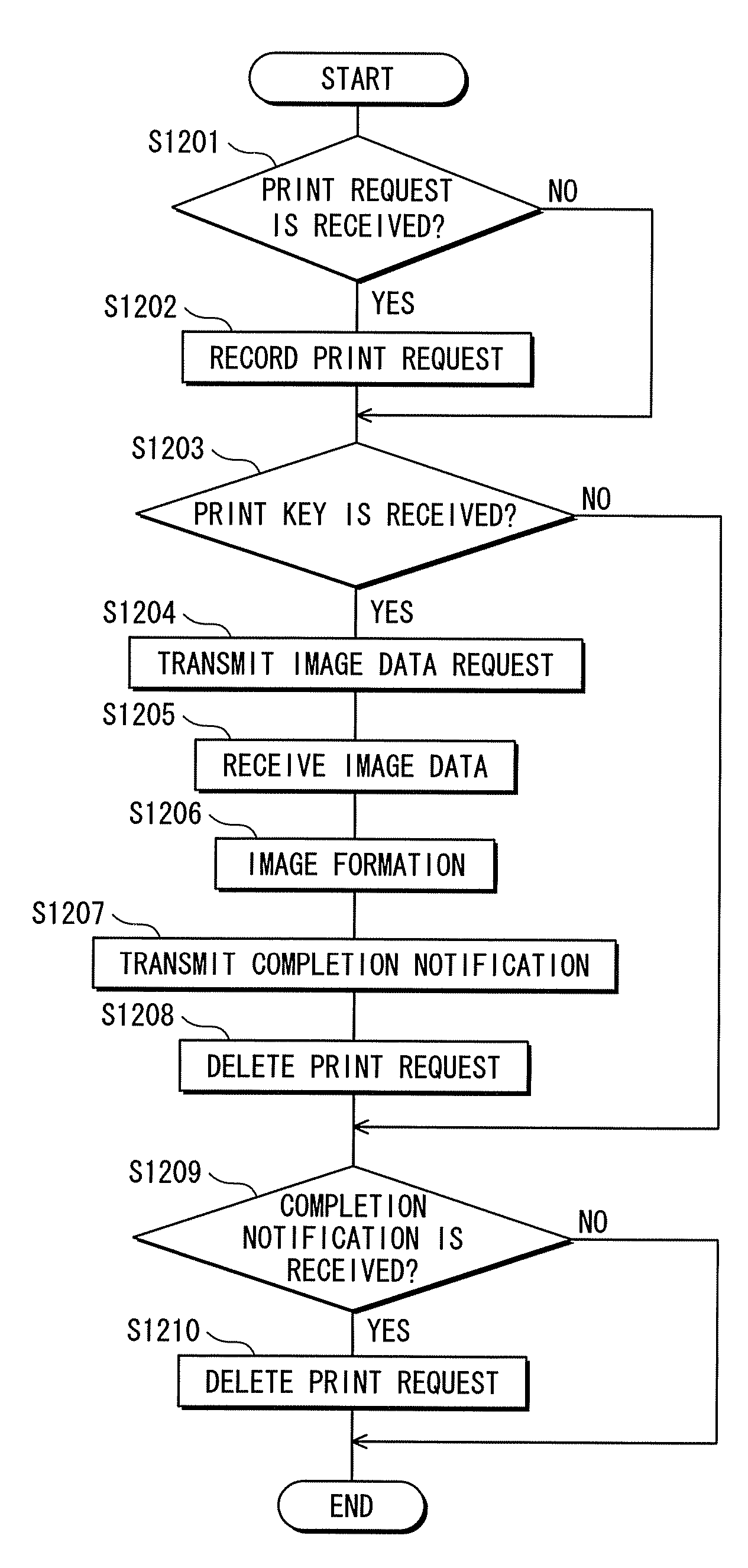
Image Processing System
ActiveUS20080291489A1Wasted storage areaPrevent confidentialityDigital computer detailsComputer security arrangementsImaging processingPersonal computer
After a print request is made from a personal computer to a multifunction peripheral, when a user who logs into the multifunction peripheral instructs an execution of the print request in the multifunction peripheral, the multifunction peripheral requests the personal computer to transmit image data. Then, the personal computer transmits the requested image data to the multifunction peripheral. The multifunction peripheral executes the printing using the received image data. When the printing is completed, the multifunction peripheral transmits a completion notification indicating that the printing is completed to the personal computer. When receiving the completion notification, the personal computer transmits a completion notification having the same content as the received completion notification to the multifunction peripheral.
Owner:KONICA MINOLTA BUSINESS TECH INC
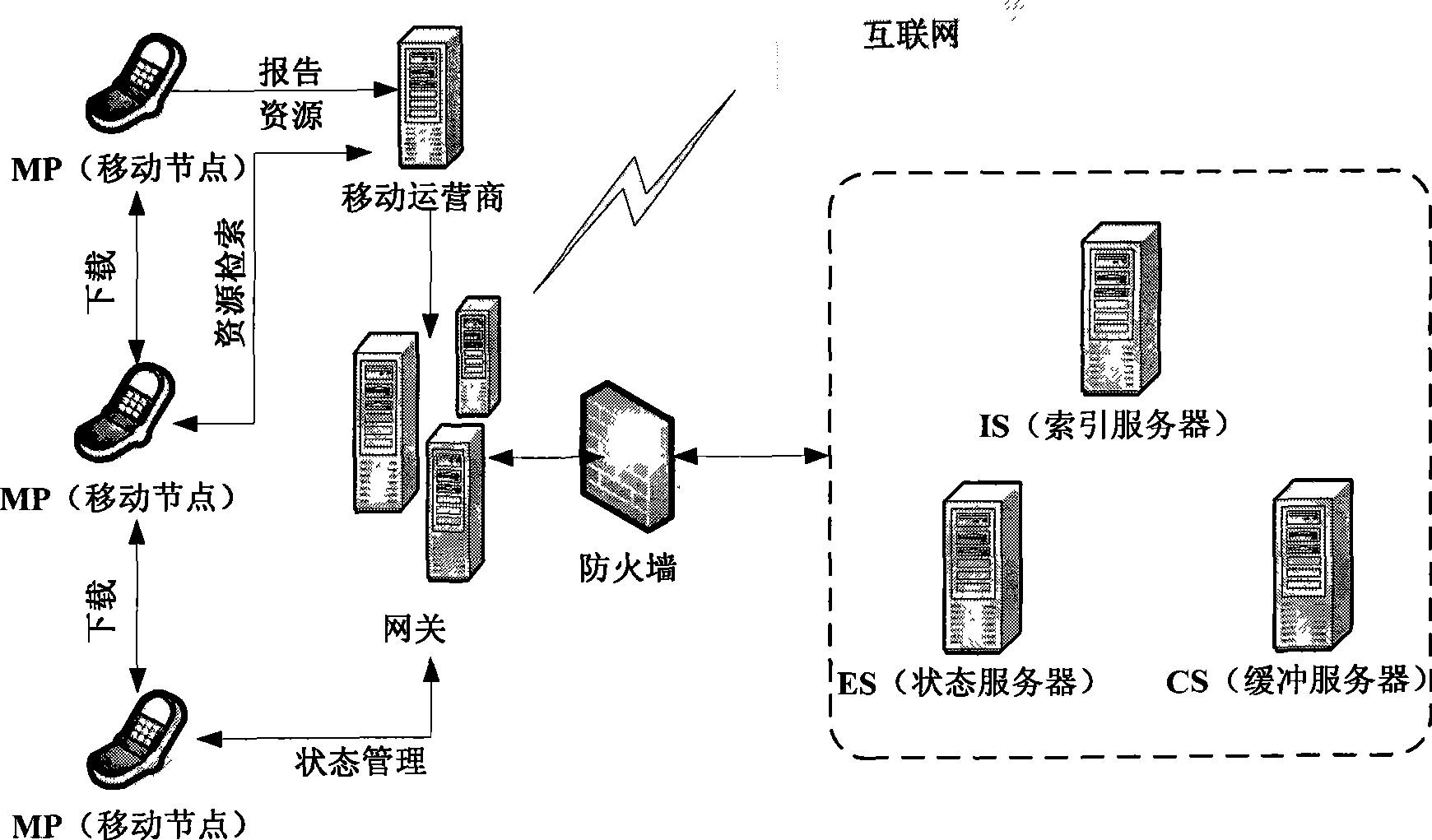
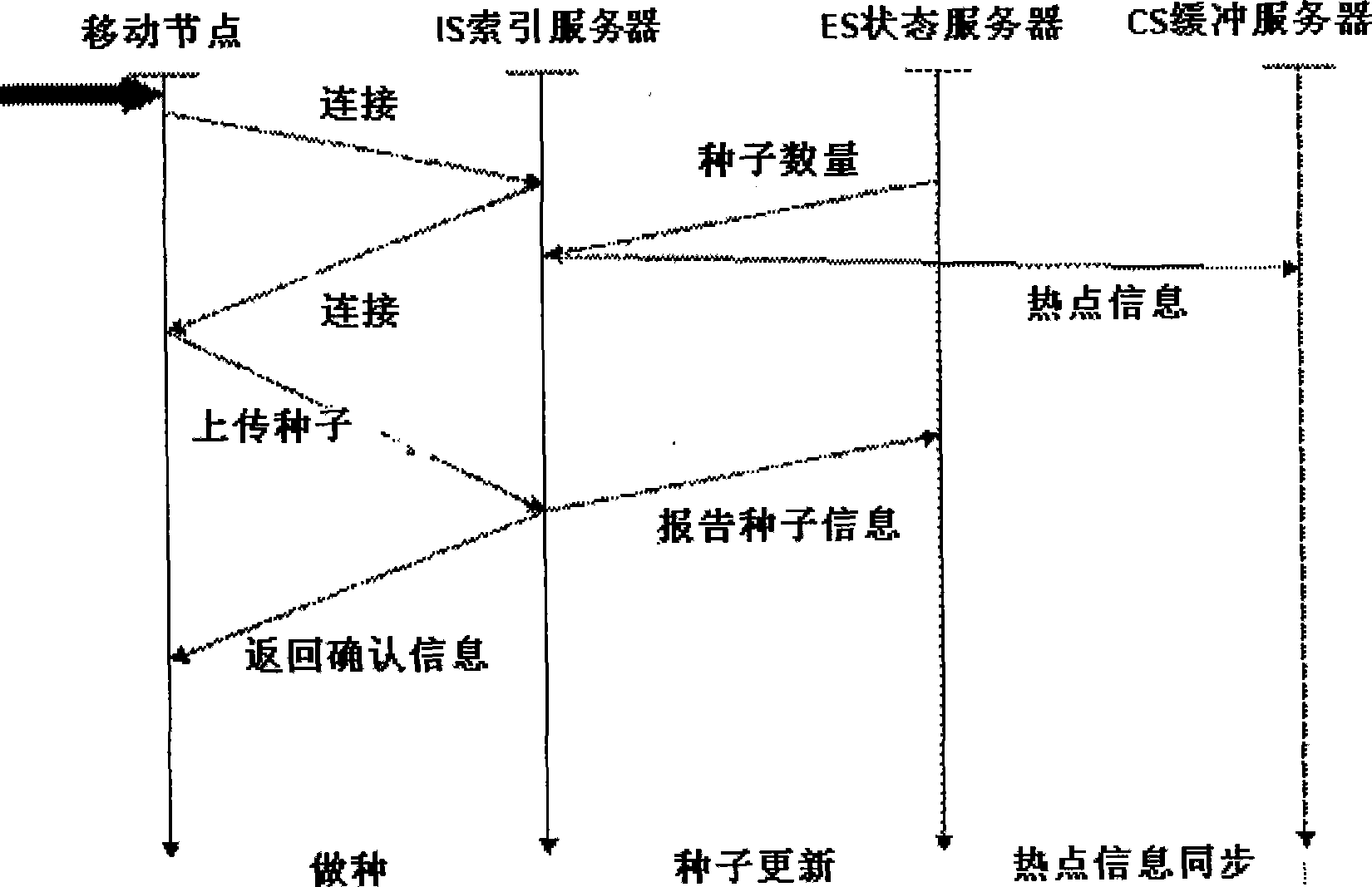
Data file transmission method for mobile phone system
The invention relates to a method for data file transmission between mobile communication equipments. The invention is to transmit data file in P2P style using mobile phone. First, user for providing uploading information divides the file into several portions or blocks, then different user downloads different block of the file, one of the user downloads a certain block of the file then uses the block for providing downloading service for other user; the method is similar to BT downloading of computer system. In the inventive method, the more people downloads, the more the servers; the more people downloads, the more people uploads; and the speed is faster.
Owner:广州飞锐网络科技有限公司
Application service network access method and system based on identifier
ActiveCN102739687AReduce message lengthReduce communication loadUser identity/authority verificationApplication serverService networks
The invention discloses an application service network access method based on an identifier, wherein the method comprises the following steps: in the process of accessing the client end in the application server, an indentifying server obtains certificates of a client end and an application server according to identifiers of the client and the application server, and then verifies the identifications of the client and the application server; after the authentication of the client and the application server are passed, the client end and the application server consult obtain a message identifying password; and the client and the application server perform the secrecy transmission of the application service data according to the message identifying password. The invention further discloses an application server system. According to the application service network access method and the system based on the identifier, unified authentication is carried out in the application server and the client in the mass application service network, so the client can access different application servers by the same identifier so as to facilitate users greatly.
Owner:GCI SCI & TECH
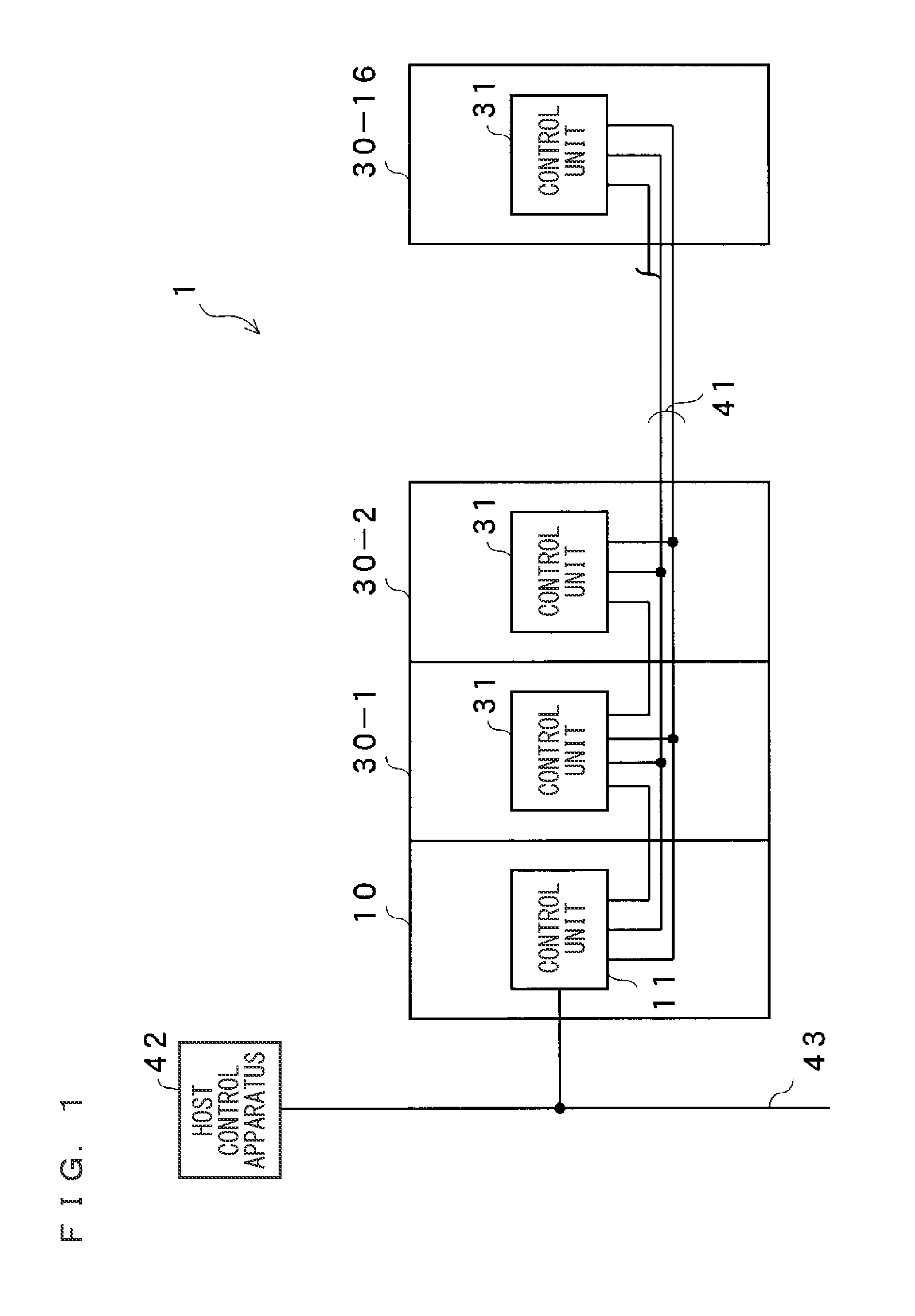
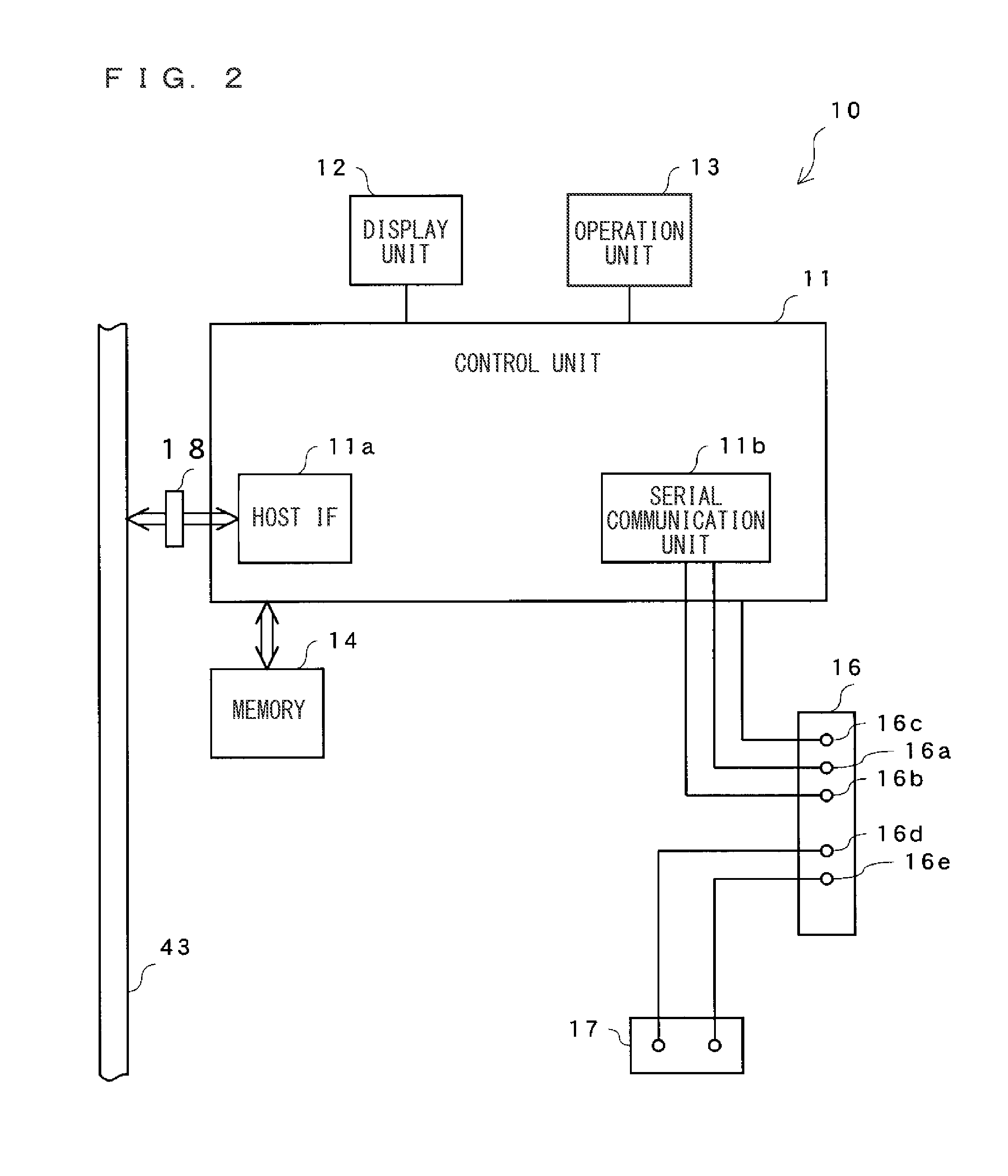
Connected Sensor System, Network Unit, And Sensor Unit
InactiveUS20110018688A1Easy to useReduce communication loadTesting/calibration apparatusElectric testing/monitoringComputer hardwareComputer science
The present invention provides a connected sensor system which can be easily used by the user and which can give an external input to each sensor unit without making the wiring complicated, and also provides a network unit and a sensor unit used for the connected sensor system. A cyclic communication memory of a network unit is arranged with an external input request region, and an external input signal is stored to a corresponding memory in a host control apparatus. By performing cyclic communication between the network unit and the host control apparatus, the external input signal is stored to the cyclic communication memory of the network unit. Accordingly, the external input signal is transmitted to each sensor unit connected to the network unit, and each sensor unit executes the external input function.
Owner:KEYENCE
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com