Efficient and energy-saving link safety method in wireless sensor network
A wireless sensor, high-efficiency and energy-saving technology, applied in security devices, wireless communication, energy-saving ICT, etc., can solve the problem of reduced utilization of network resources, reduce computing load, prevent replay attacks and denial of service attacks, and improve availability Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
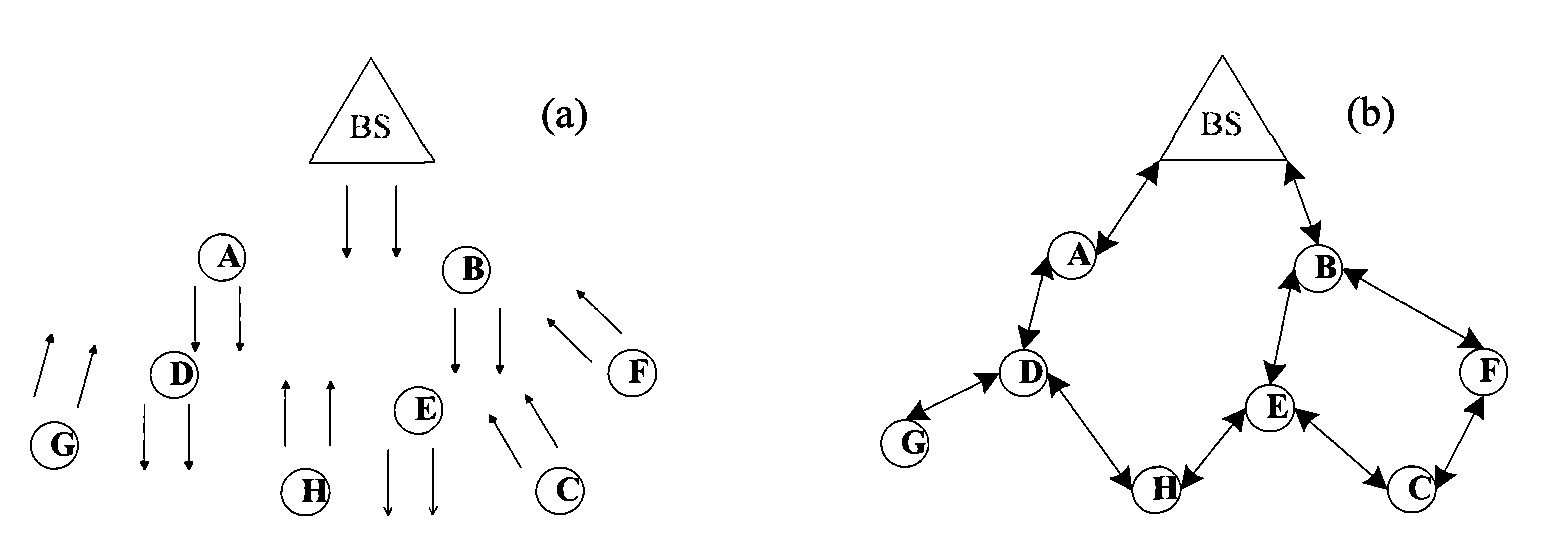
[0053] The wireless sensor network in this embodiment (the network topology diagram is as follows Figure 4 As shown) is composed of 8 MICAz sensor nodes and 1 base station (the base station is composed of 1 MICAz processor / radio frequency board connected with 1 MIB520USB PC gateway) from Crossbow Company in the United States, using the MoteView client monitoring software installed The IBM PC aggregates the data collected by the sensor nodes, including temperature (unit: Celsius), relative humidity (unit: %), and illumination (unit: lumens per square meter) data. The encryption algorithm used in the embodiment is the RC5 algorithm.
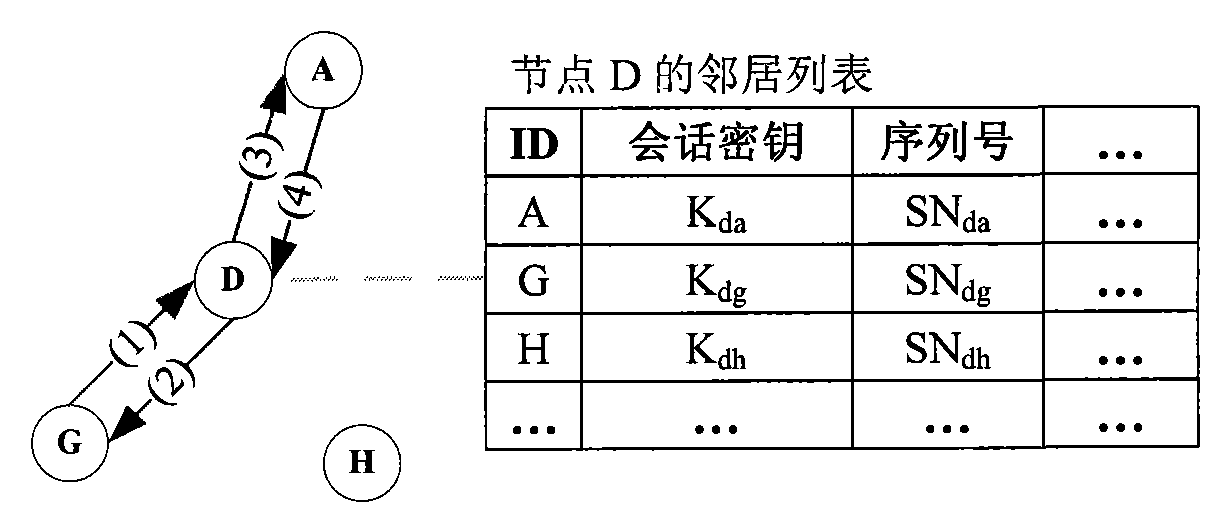
[0054] 1. Neighbor list establishment phase
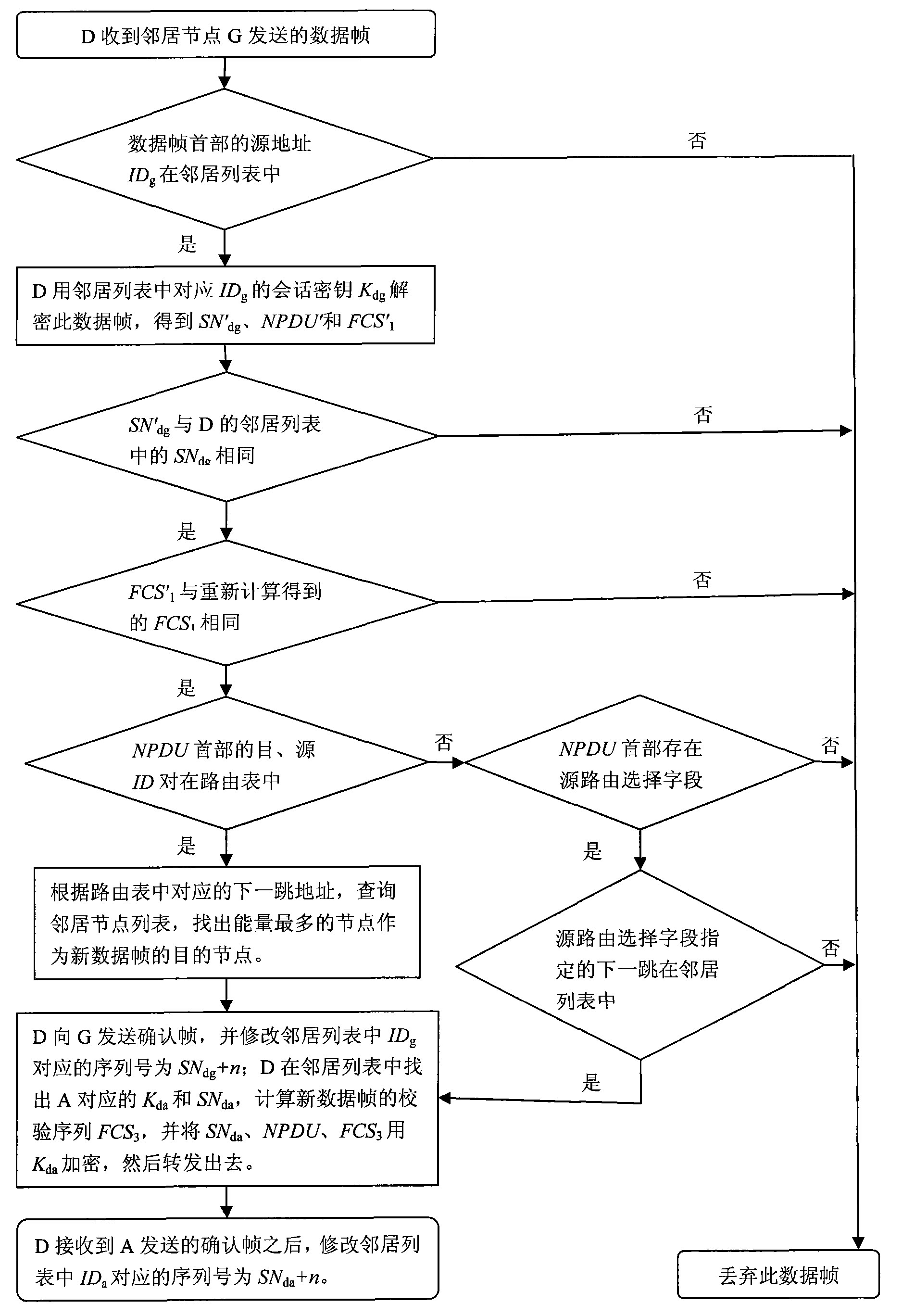
[0055] In the initialization phase of the network, each node needs to form a route to the base station, and each node also establishes a neighbor relationship and a neighbor list accordingly during the route formation process. This embodiment adopts Figure 4 The shown method gets the route and buil...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com