Data storage data processing method based on block chain
A processing method, block chain technology, applied in the direction of electronic digital data processing, data processing applications, special data processing applications, etc., can solve data leakage, malicious damage, hidden dangers of data security, etc., to increase reliability and ensure authenticity Sexuality, the effect of alleviating contradictions and conflicts
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
specific Embodiment approach 1
[0080] Specific Embodiments 1. The processing method of blockchain-based electronic deposit data described in this embodiment includes methods for uploading electronic data, methods for preserving electronic data, methods for querying electronic data, methods for downloading electronic data, and methods for electronic data Authorization method, electronic data comparison method and user point establishment method;
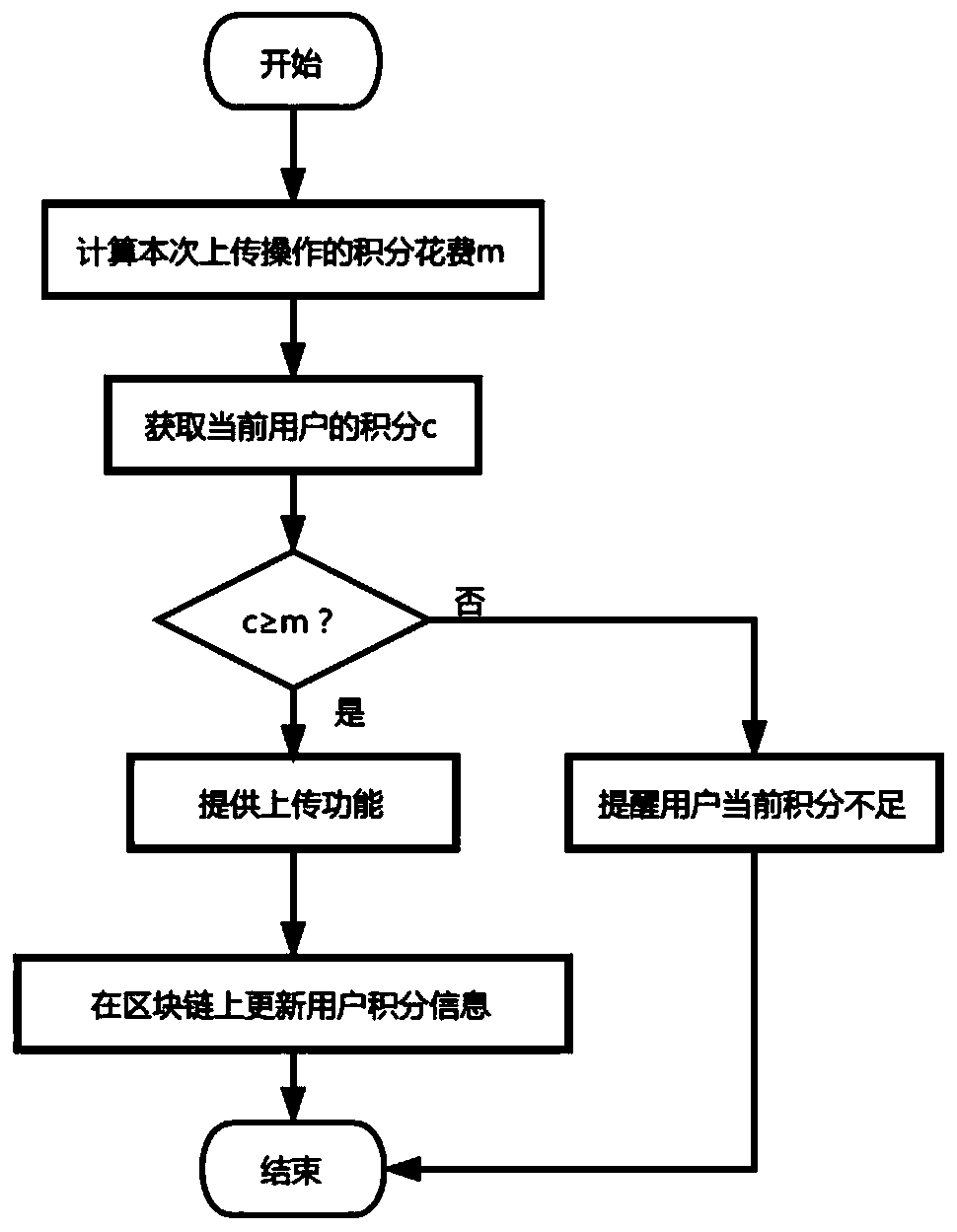
[0081] The method for uploading electronic data includes the following steps:
[0082] Step A1. Calculate the point cost m of this upload operation;
[0083] Step A2, obtaining the current user's points c;
[0084] Step A3, judging whether c is greater than or equal to m; if the judgment result is yes, then execute step A41; if the judgment result is no, then execute step A42;
[0085] Step A41, providing an upload function, and then performing step A5;
[0086] Step A42, reminding the user that the current points are insufficient; then end;
[0087] Step A5, u...
specific Embodiment approach 2
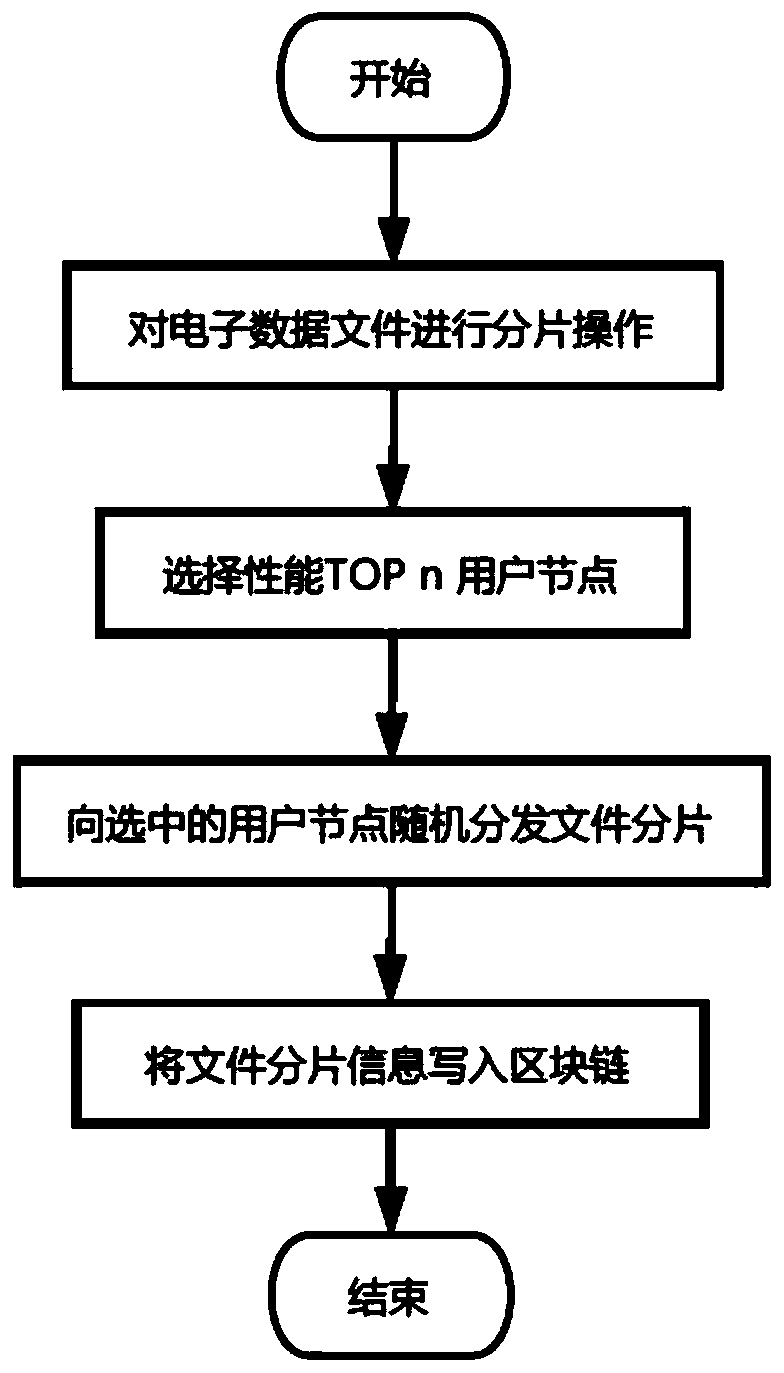
[0264] Embodiment 2. The difference between this embodiment and the blockchain-based data storage and data processing method described in Embodiment 1 is that the index idea is introduced in the process of writing the smart contract to constrain Different users' access rights to electronic data.
[0265] In the process of writing the smart contract, four structural variables of File, Record, Member and User are defined, which respectively store key information of electronic data files, key information of electronic data file fragmentation, and all relationships between user data and electronic data files . Based on the above four variables, writing of electronic data information, query of electronic data information, authorization of electronic data, update of user information and query of user information are programmed in sequence. Considering that the writing speed of Ethereum data is slow and it is easy to affect the user experience, an asynchronous request method (sendAs...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com