Method for password protection for constructing unidirectional hash function based on infinite dimension ultra-chaos
A one-way hash function and password protection technology, applied in the field of information security, can solve problems such as easy collisions
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0049] The present invention will be described in detail below in conjunction with the accompanying drawings and specific embodiments.
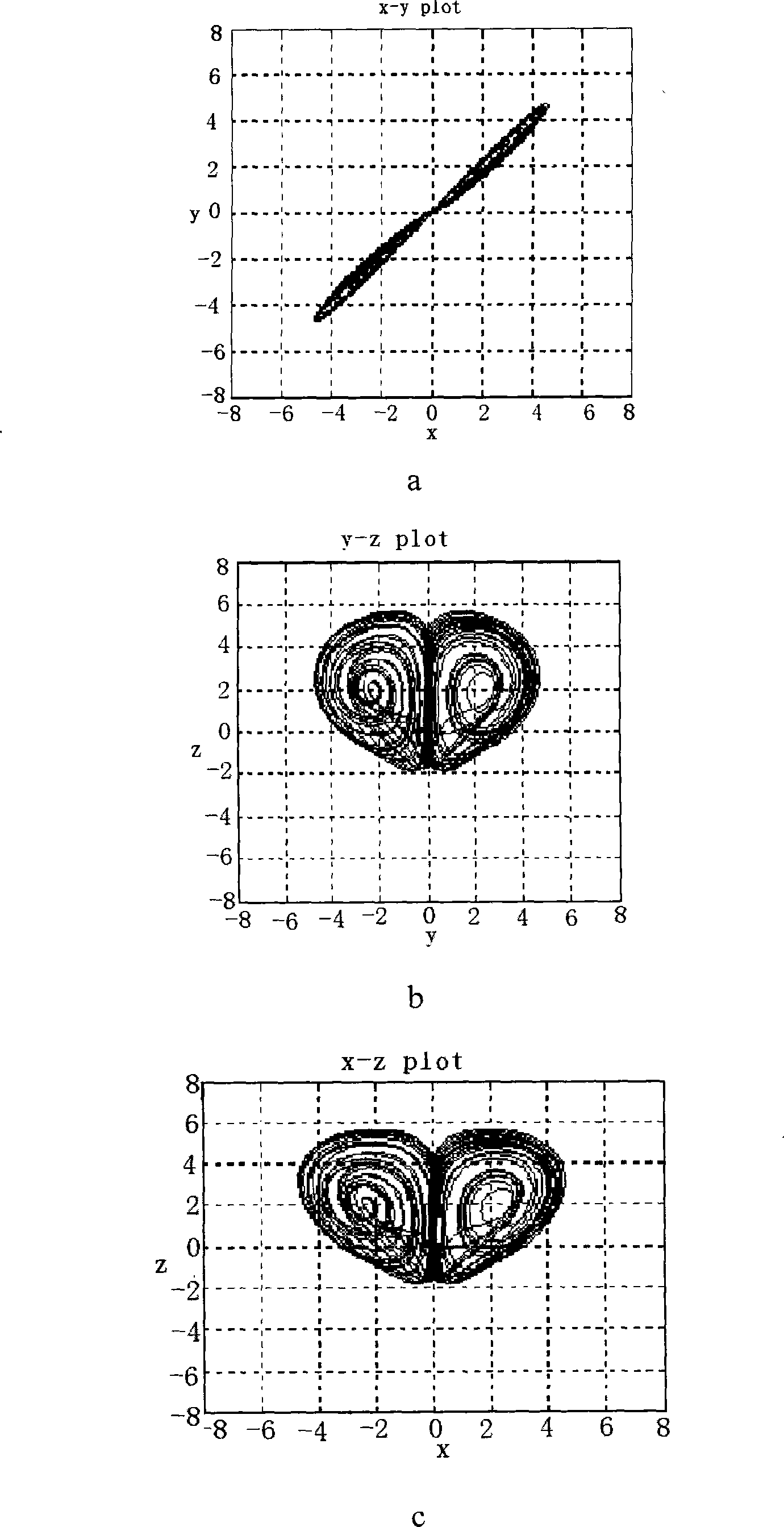
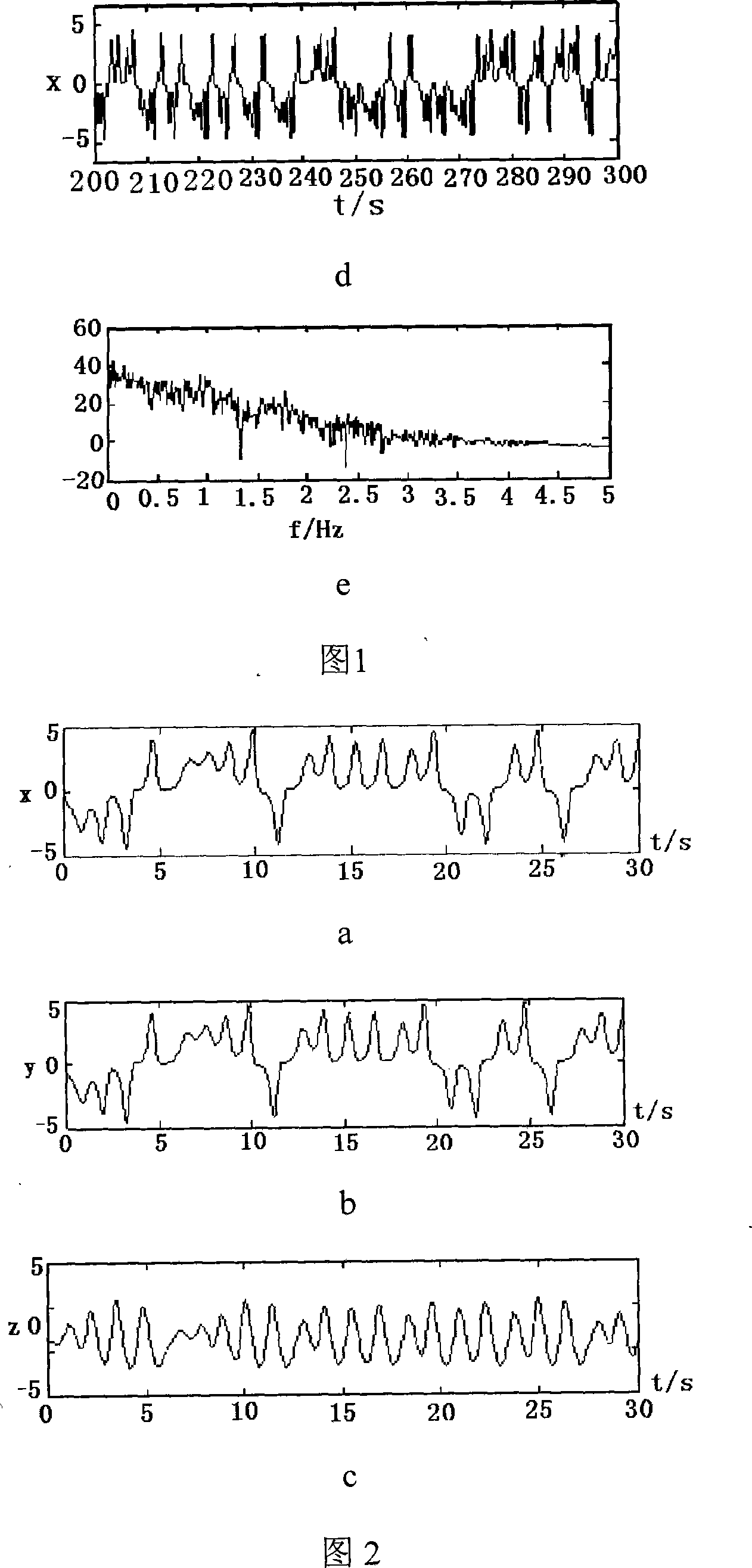
[0050] The invention first constructs a high-performance one-way hash function by using hyper-chaos and key flow, and then uses the function to encrypt passwords.
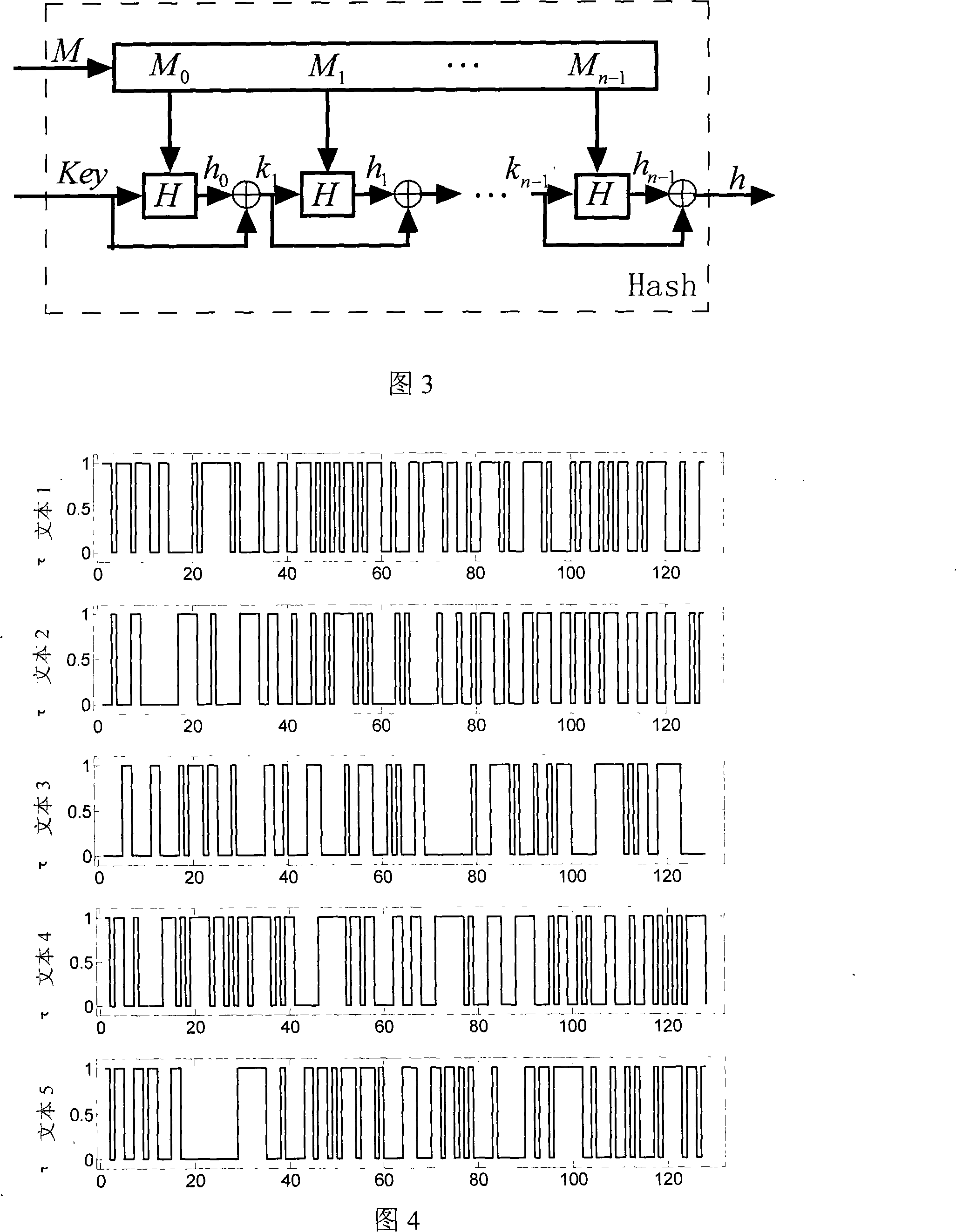
[0051] The plaintext (the password to be protected) and the key are used as the initial values of two hyperchaotic Chen systems with delayed feedback, and the evolution is carried out for a certain period of time according to the chaotic dynamic characteristics of the two systems, and the final result of the evolution is quantified, and the The quantized value is substituted into the key stream for iteration to realize the confusion and diffusion of plaintext and key information, and based on the cipher block chaining method, a 128-bit hash value of plaintext of any length is generated, and the hash value of the password to be authenticated is combined with the hash value of the ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com