Encipher method and system for B2B data exchange
A technology of data exchange and encryption method, applied in transmission systems, public keys for secure communication, user identity/authority verification, etc. And other issues
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0019] Firstly, the relevant technologies utilized in the present invention are introduced.
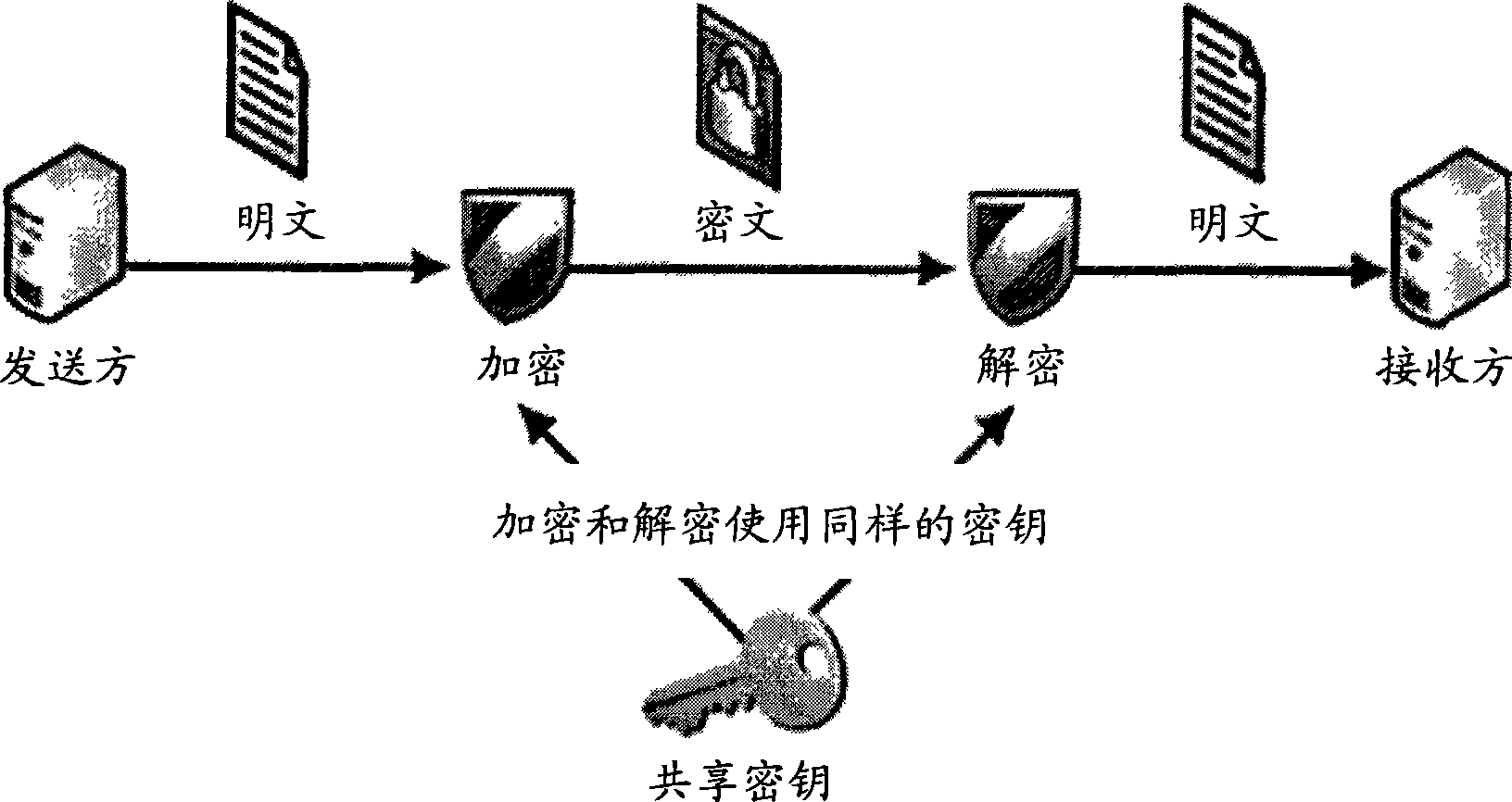
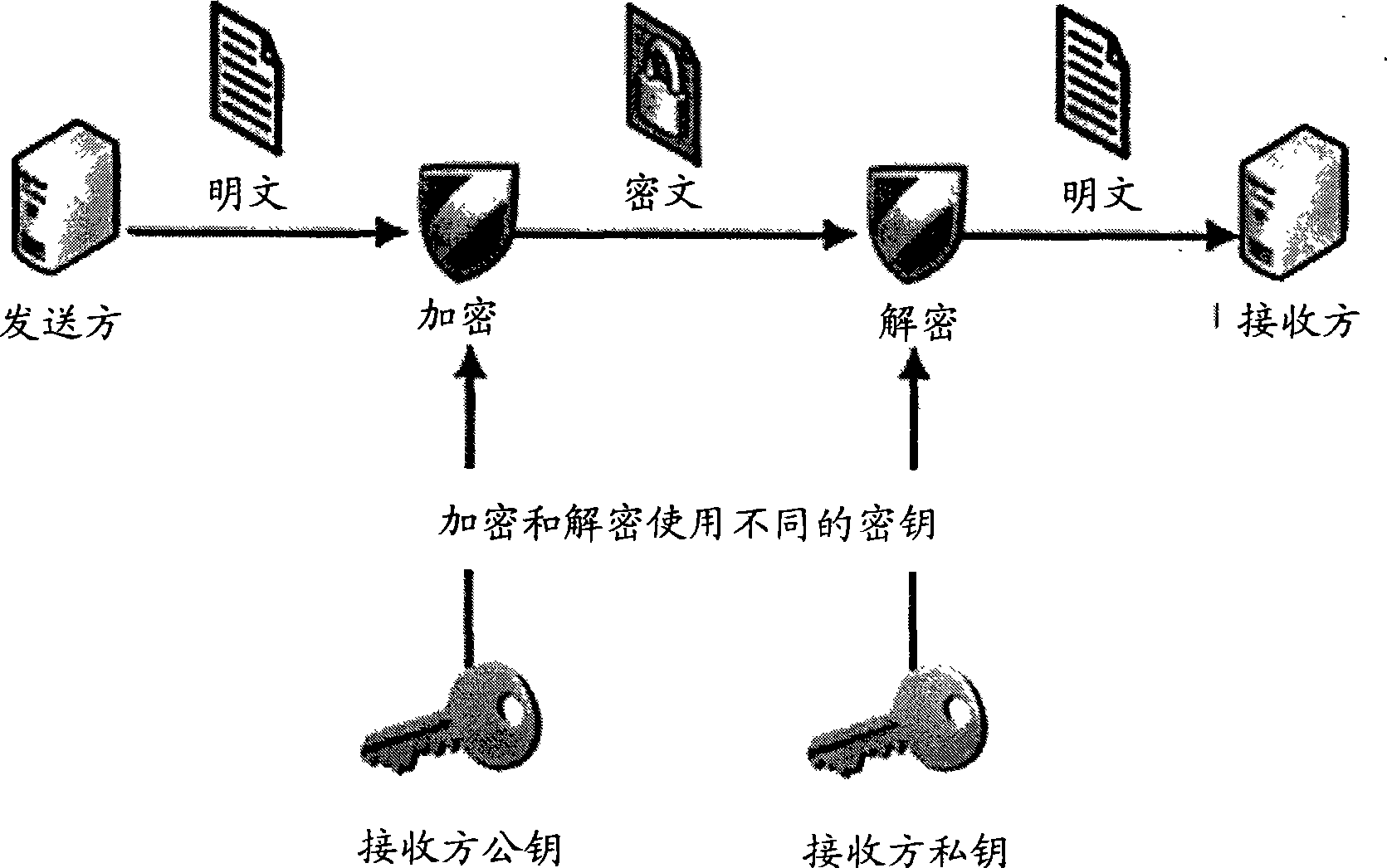
[0020] Digital certificate: An authoritative electronic document containing user identity, public key, validity period and many other relevant information digitally signed by the private key paired with the public key, is an electronic ID card of an entity on the Internet. The public key and private key contained in the digital certificate can be considered as an encryption / decryption algorithm certificate. The public key part can be obtained and circulated publicly, while the private key part is stored in the physical medium in a secret way, and is guaranteed by the relevant technology of the physical medium. The private key is unique in the real world and cannot be copied.
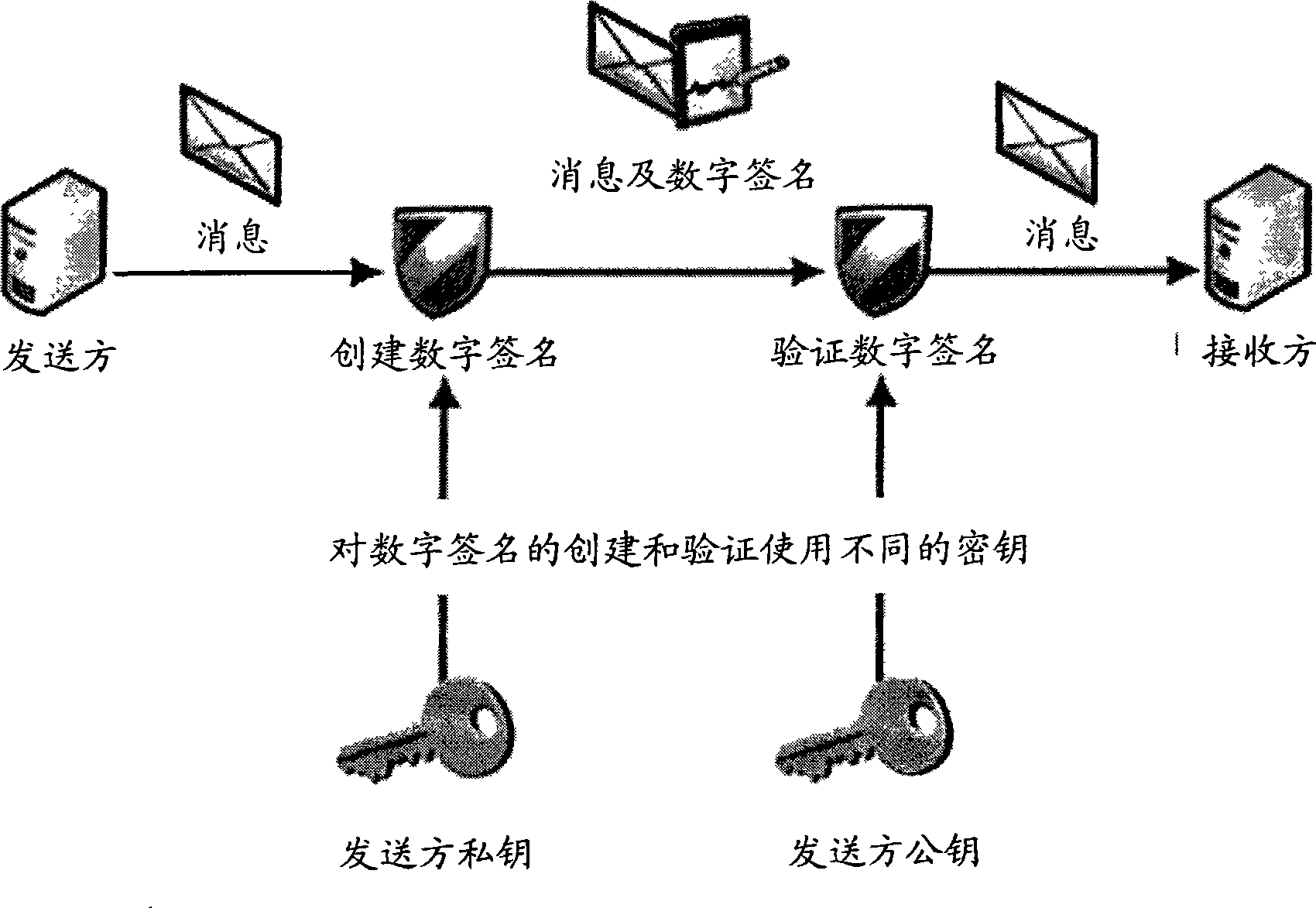
[0021] Digital signature: An information technology process based on digital certificates, similar to traditional handwritten signatures to ensure the non-repudiation of information. refer to image 3 As shown...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com