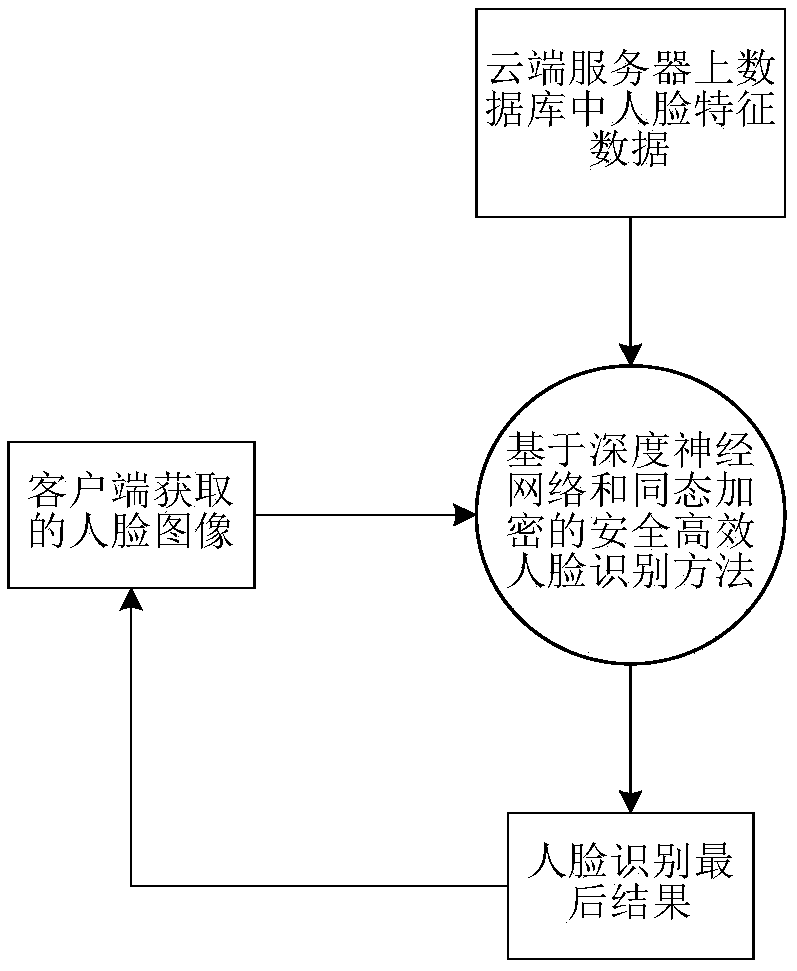
A secure and efficient face recognition method based on depth learning and homomorphic encryption
A homomorphic encryption and deep learning technology, applied in homomorphic encryption communication, neural learning methods, character and pattern recognition, etc., can solve the problem that the SCiFI scheme is no longer safe, and achieve the effect of reducing data volume and simplifying calculations
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0046] The present invention will be described in further detail below in conjunction with the accompanying drawings and specific embodiments.
[0047] Overall process:
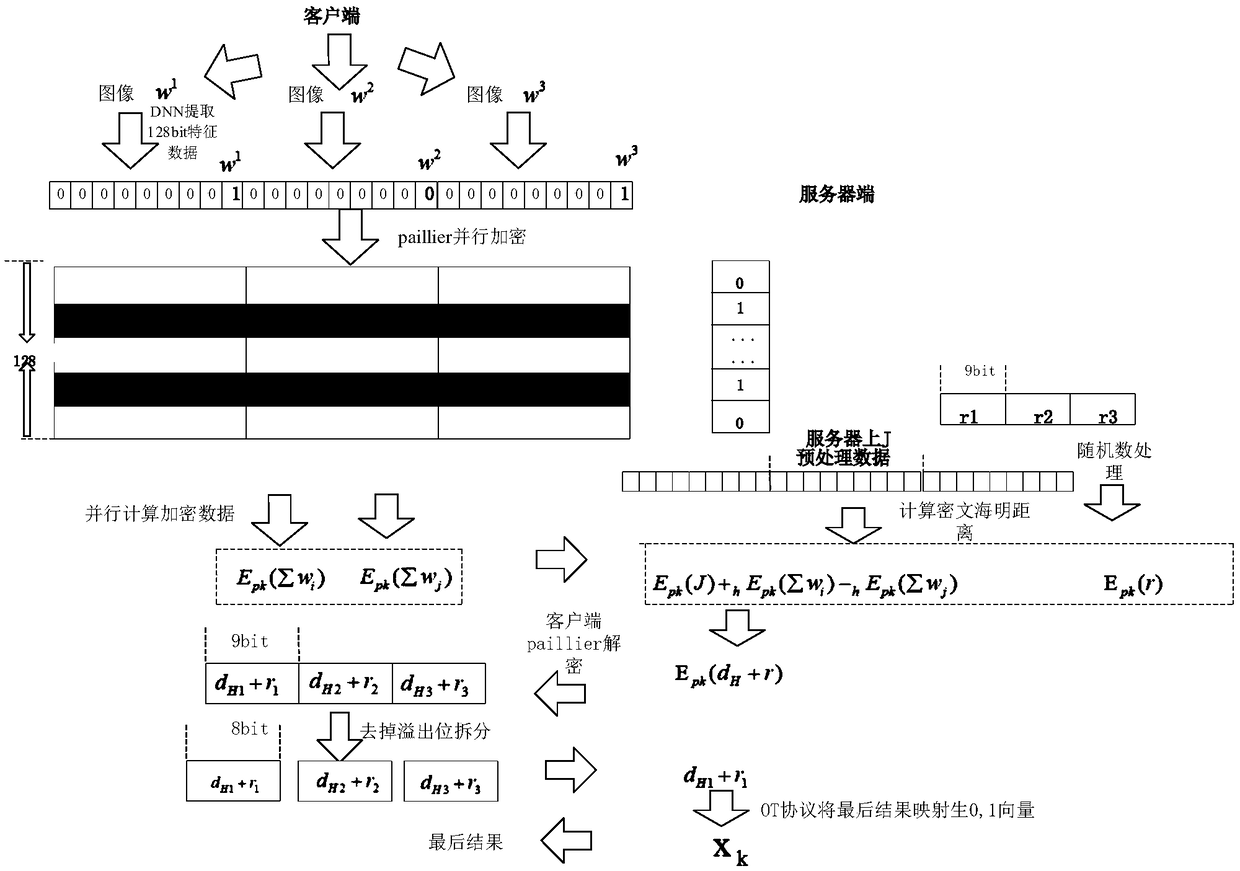
[0048] The client has the encrypted public key and the decrypted private key, and the index i that it wants to look up the data in the server. The server has an encrypted public key and a face recognition threshold t. A uniform threshold is set for faces in the entire database through experiments. exist figure 2 where i and j represent the indexes of 0 and 1 in the server-side vector v, respectively. For the extracted 128-bit feature vector, J is the number of 1 in the server-side vector v, which is less than or equal to 128, w i with w j is a vector value in the client, + h represents the multiplication operation, - h stands for subtraction, d H is the Hamming distance, r is a random number, X k is the corresponding 0,1 vector;
[0049] client:
[0050] After the client acquires the face image, it...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com