Authentication and cipher key negotiation method of mobile communication system
A mobile communication system and key negotiation technology, which is applied in the field of authentication and key negotiation of mobile communication systems, can solve problems such as security defects, and achieve the effect of increasing difficulty and reducing security risks
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
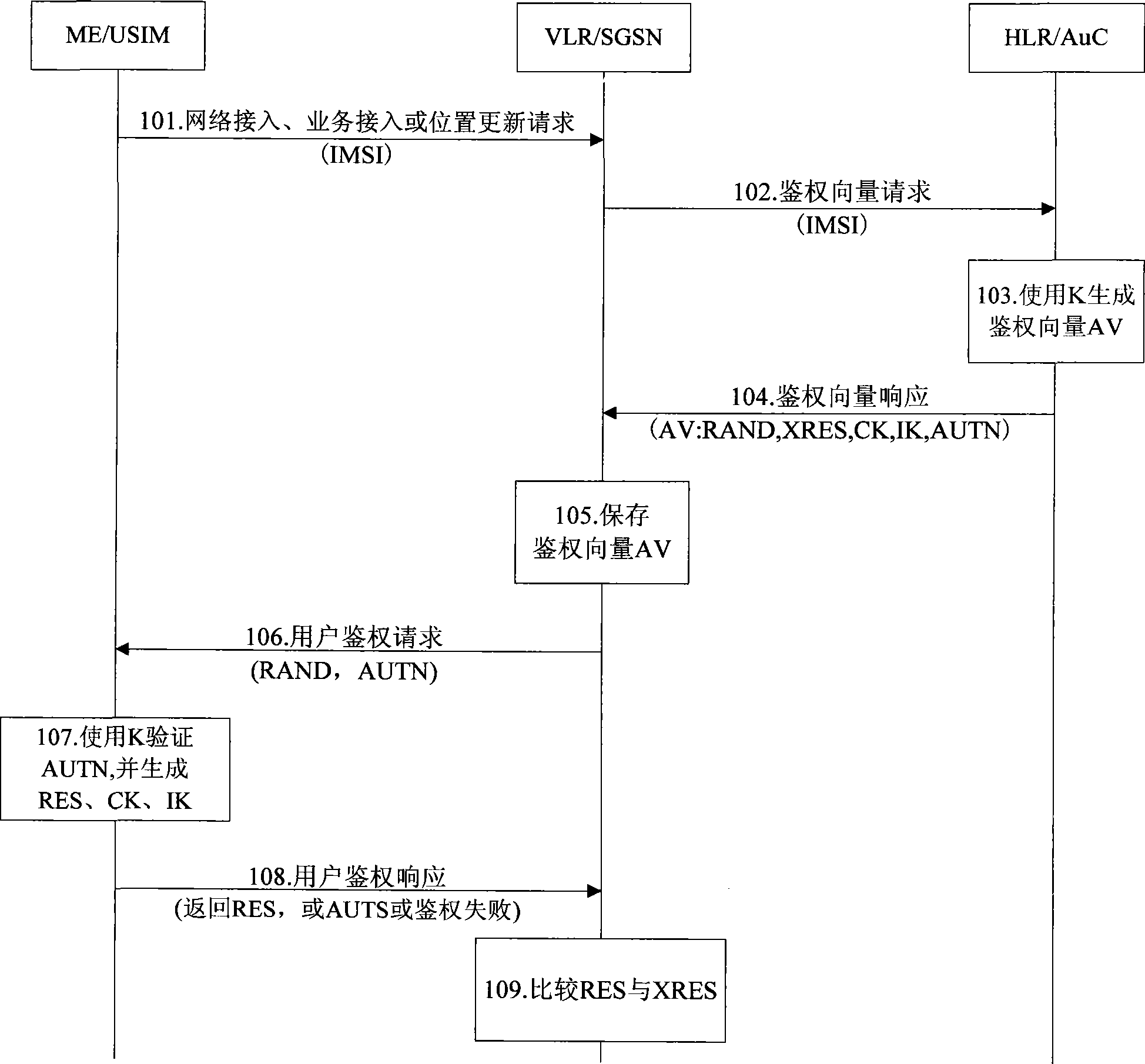
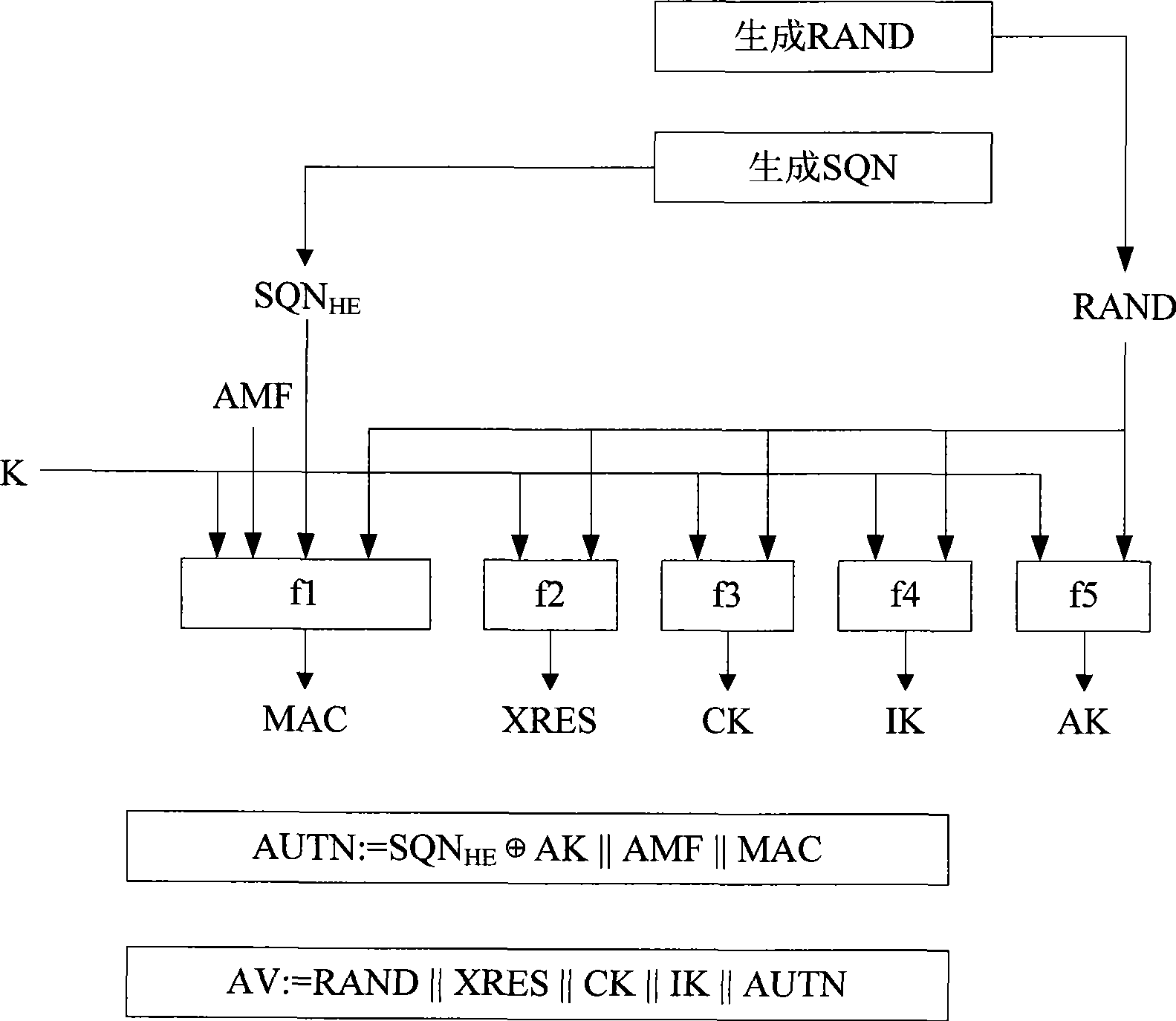
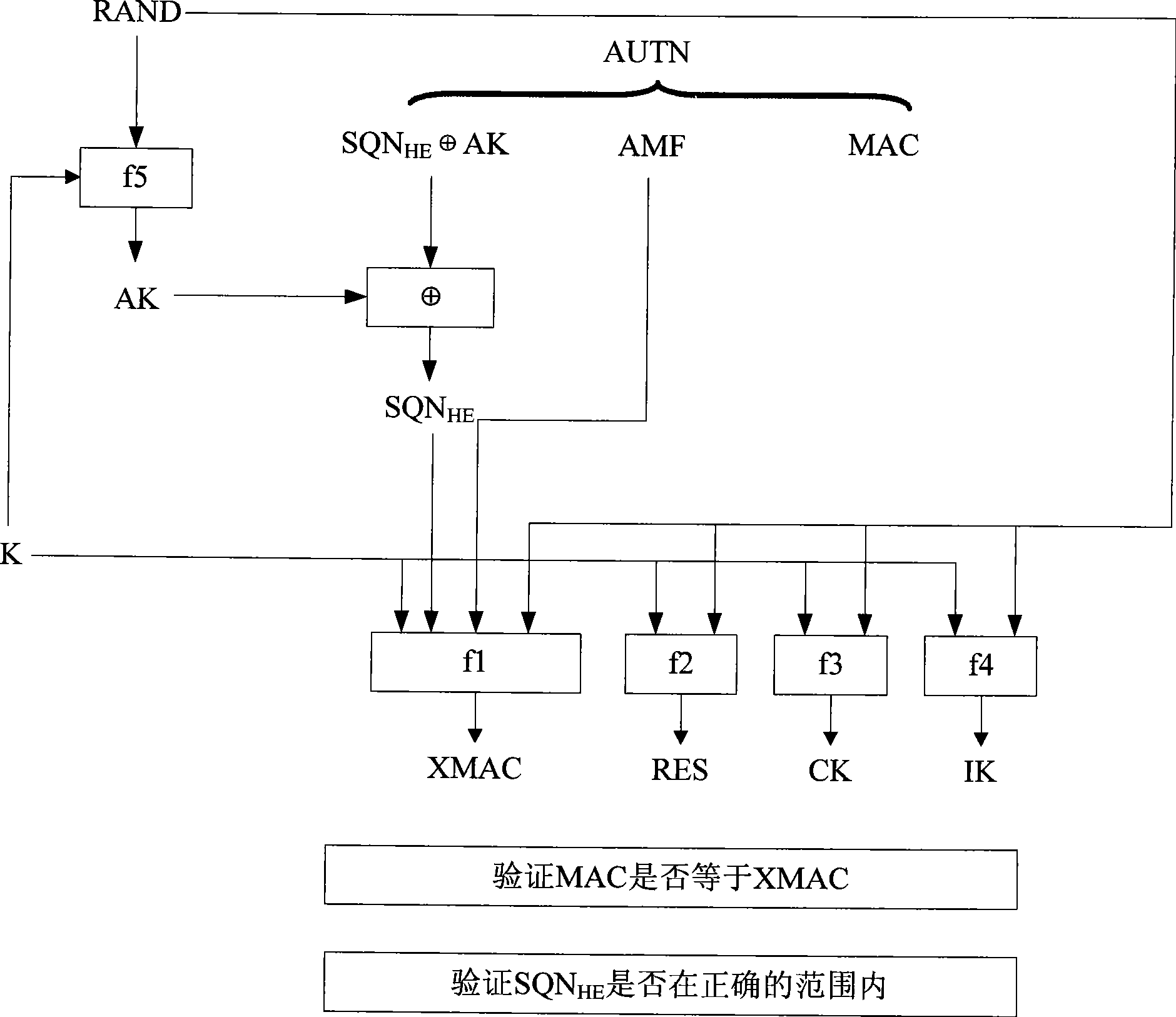
[0075] Based on the above analysis, the present invention proposes a one-time pad AKA enhanced authentication method: that is, each time an authentication request is made, the HLR / AuC on the network side will use the authentication root key K, random numbers RAND and SQN to derive A relatively independent ephemeral key K * , then by K * Calculate and generate the authentication vector AV.
[0076] According to the principle of cryptography, although K * It is not a completely independent random number, but compared with the existing AKA authentication mechanism, the one-time pad AKA enhanced authentication method of the present invention can greatly increase the difficulty of deciphering the authentication key, thereby reducing the authentication root key The security risk of the key being deciphered.
[0077] The present invention will be described in detail below with reference to the drawings and embodiments.
[0078] Figure 4 It is a flow chart of the AKA enhanced au...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com