Double-bit unidirectional circular linked list encryption and decryption method based on stream ciphers
A one-way circulation, encryption and decryption technology, applied in encryption devices with shift registers/memory, usage of multiple keys/algorithms, digital transmission systems, etc. , the method is simple, the effect is easy to achieve
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0049] In order to make the object, technical solution and advantages of the present invention clearer, the present invention will be described in detail below in conjunction with the accompanying drawings and specific embodiments. The game interface behavior control system of the present invention is suitable for the development of stand-alone games, mobile games, web games and other games, especially for the processing of game interface behaviors realized in controlling role-playing games.
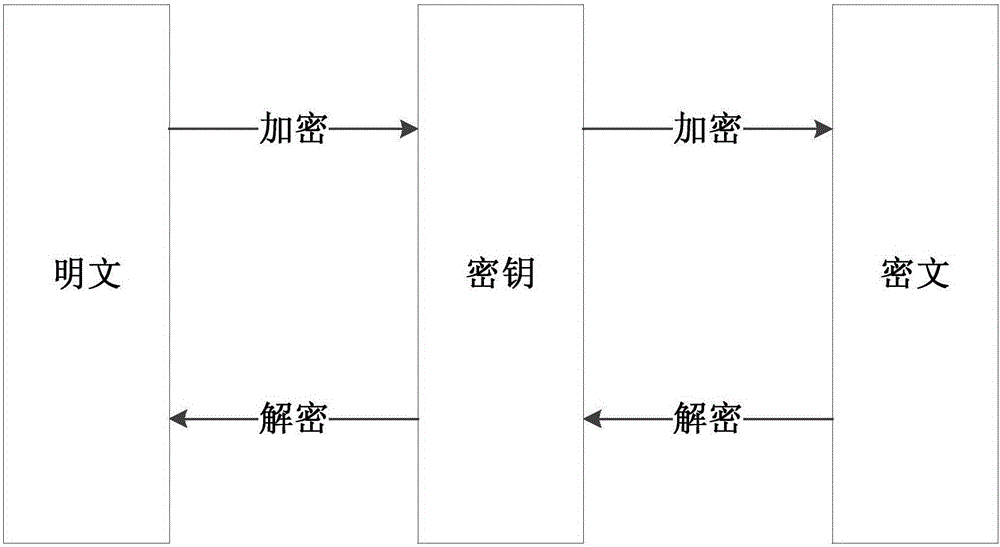
[0050] figure 1 Shown is a schematic diagram of encryption and decryption according to an embodiment of the present invention. The figure shows that the public key realizes the mutual conversion of plaintext and ciphertext, and the algorithm is the encryption or decryption algorithm and the corresponding restoration algorithm. Based on this figure, the encryption system quadruple (M (clear code), C (ciphertext), P (key), A (algorithm
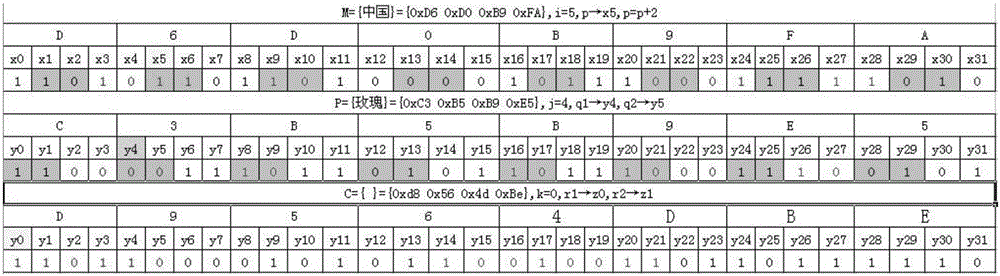
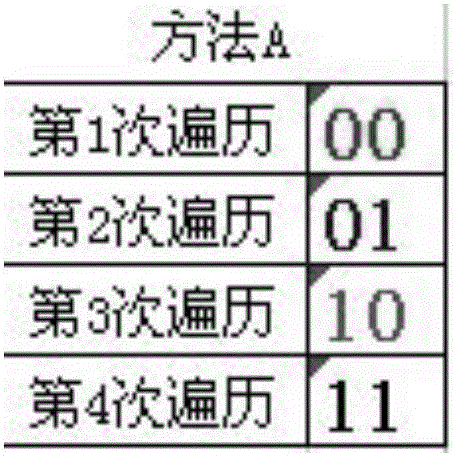
[0051] )). M, C, P, A sets have the following cha...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com