Method for improving unpredictability of output of pseudo-random number generators
A counter, digital technology, applied in the field of nonlinear functions
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
example I
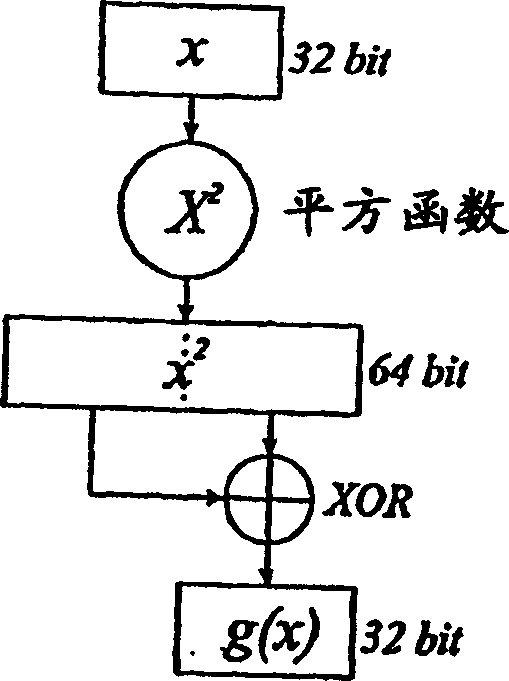
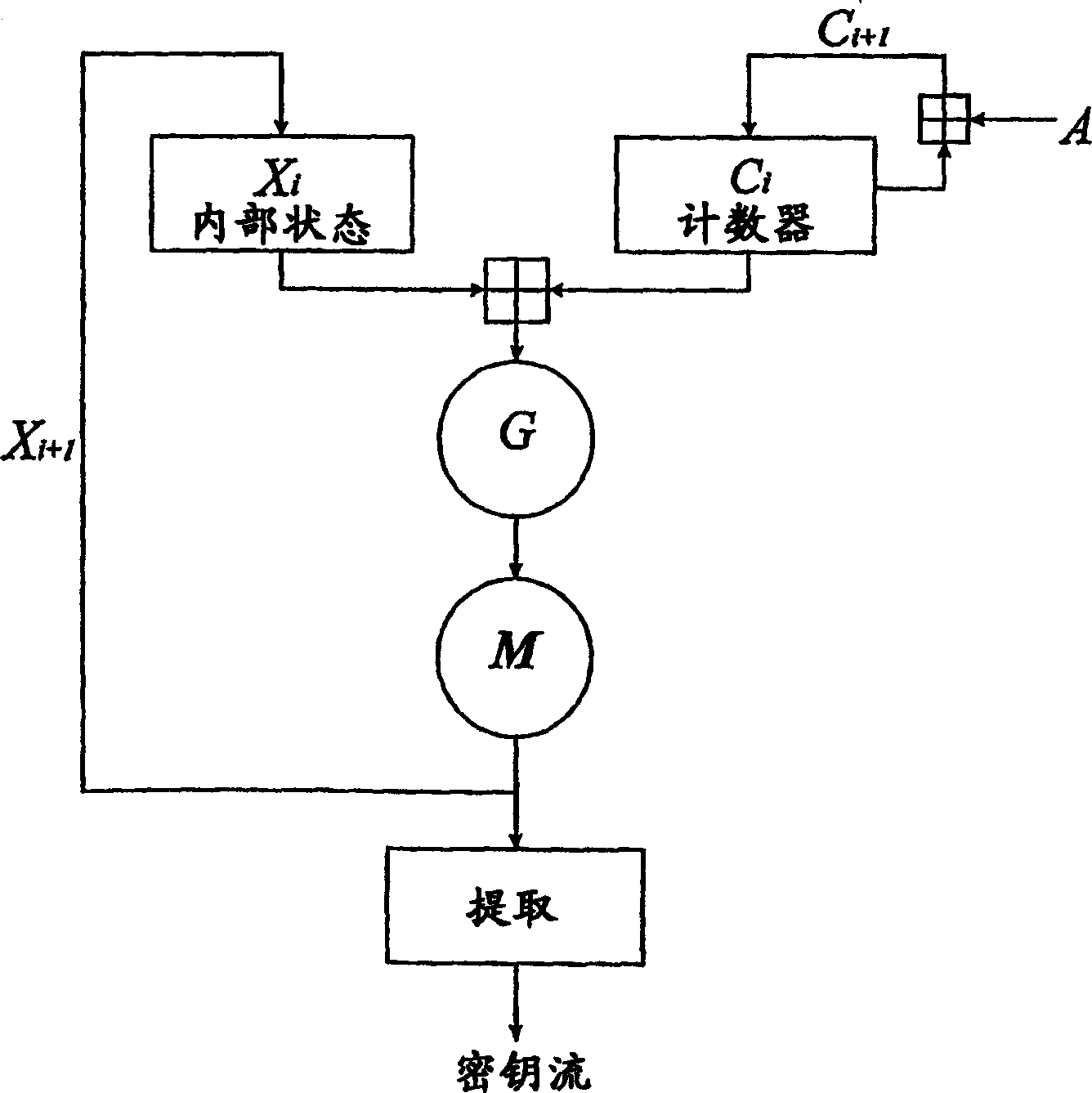
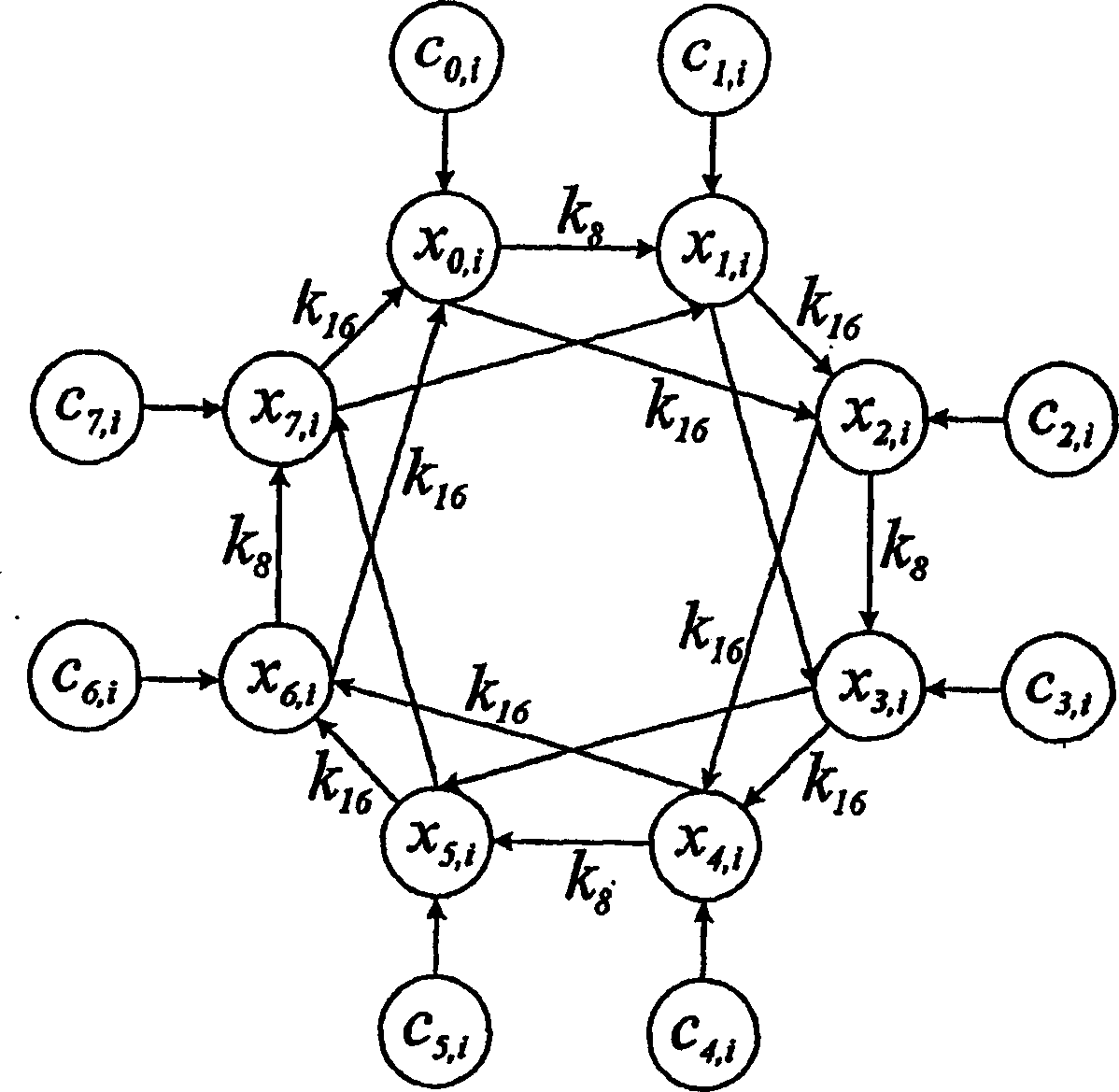
[0737] The following pseudocode program shows an example program for encrypting and decrypting data, one byte at a time. The program is based on Figure 20-27 flow chart to work. The program works with 32-bit registers. Figure 20 A method of encrypting a file containing data is shown. Figure 21-27 Corresponding to the functions appearing in the following pseudocode, they are related to the checking of periodic solutions and stream ciphers using the Lorenz system.
[0738] Pseudocode for the fixed-point library
[0739] FloatToFixedPoint: Convert a floating-point number X to a fixed-point number. The result of this function has the format S(a.b) or U(a.b).
[0740] fixedpoint FloatToFixedPoint(float X)
[0741] {
[0742] return X*2 b ; / / b is the number of bits after the decimal
[0743] / / separator in the fixed-point
[0744] / / representation of the result
[0745] }
[0746] FixedPointToFloat: Converts ...
example II
[0831] Table V shows one method disclosed herein (see Figure 1-5 ), and the encryption speeds of various existing encryption methods. The encryption speed provided by the method of the present invention is jointly published in Proceedings of Fast Software Encryption (FSE) 2003, Springer, Berlin, (2003) according to M.Boesgaard, M.Vesterager, T.Pedersen, J.Christiansen and O.Scavenius Measured by the algorithm described in the article "Rabbit: A New High-Performance Stream Cipher (Rabbit: A New High-Performance Stream Cipher)". The algorithm utilizes the MMX TM Instructions, implemented in assembly language.
[0832] Based on the measurements, the speeds were converted to an equivalent encryption / decryption speed of 947Mbit / sec on a 450MHz Pentium III processor.
[0833]
name
Appeared year
share
type
key
length
[bit]
Block
length
...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com