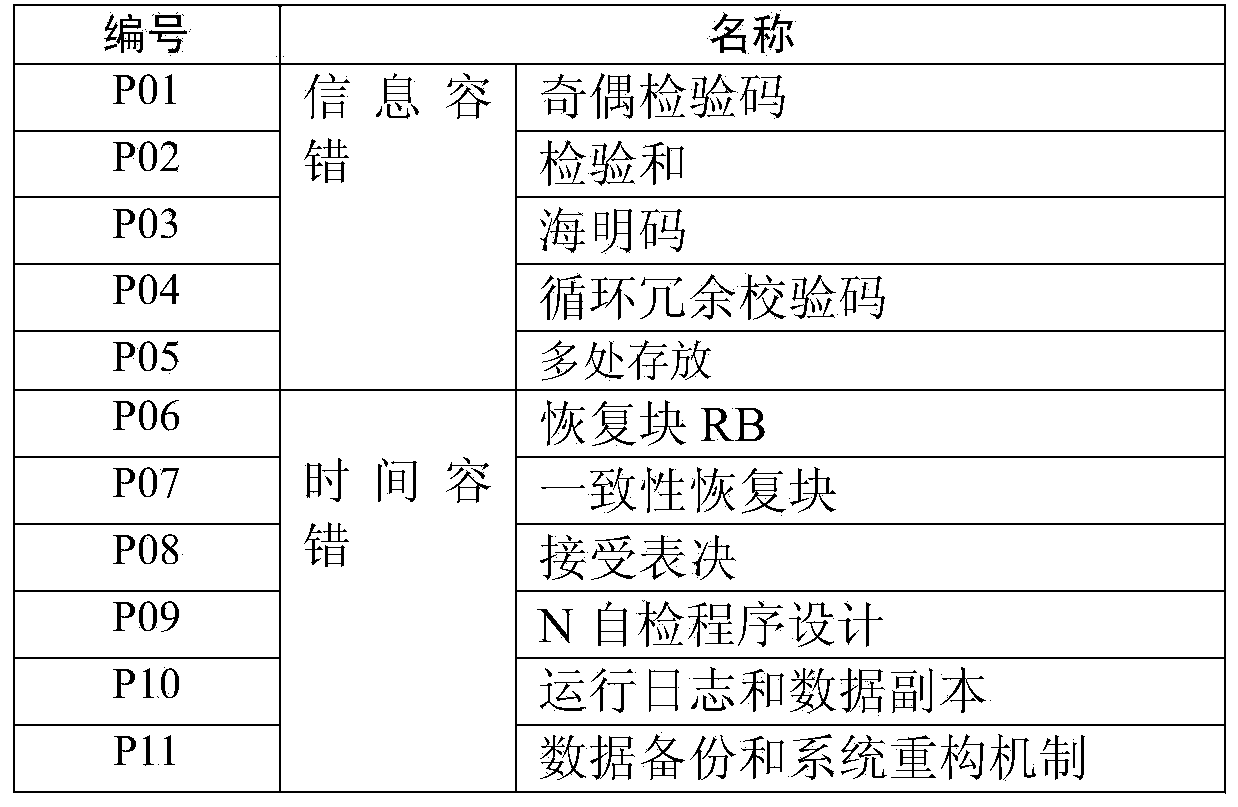
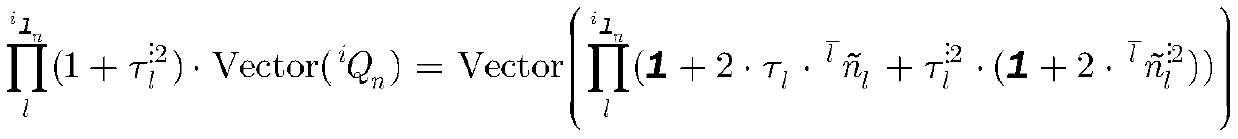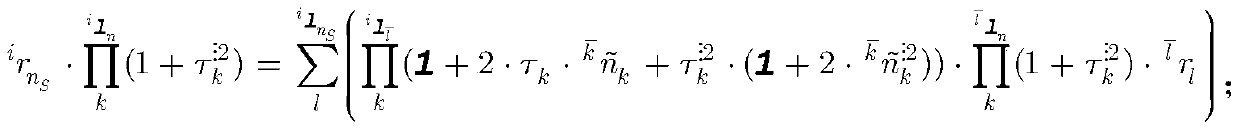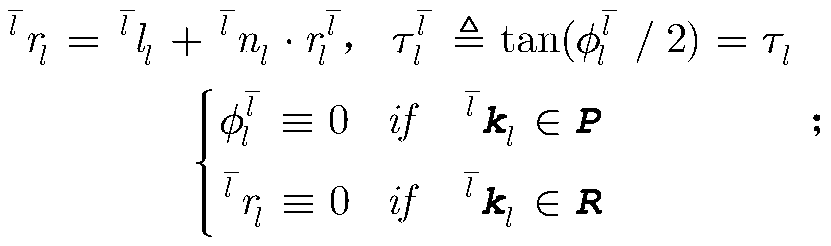Patents
Literature
82 results about "Pseudocode" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Pseudocode is an informal high-level description of the operating principle of a computer program or other algorithm. It uses the structural conventions of a normal programming language, but is intended for human reading rather than machine reading. Pseudocode typically omits details that are essential for machine understanding of the algorithm, such as variable declarations, system-specific code and some subroutines. The programming language is augmented with natural language description details, where convenient, or with compact mathematical notation. The purpose of using pseudocode is that it is easier for people to understand than conventional programming language code, and that it is an efficient and environment-independent description of the key principles of an algorithm. It is commonly used in textbooks and scientific publications that are documenting various algorithms, and also in planning of computer program development, for sketching out the structure of the program before the actual coding takes place.
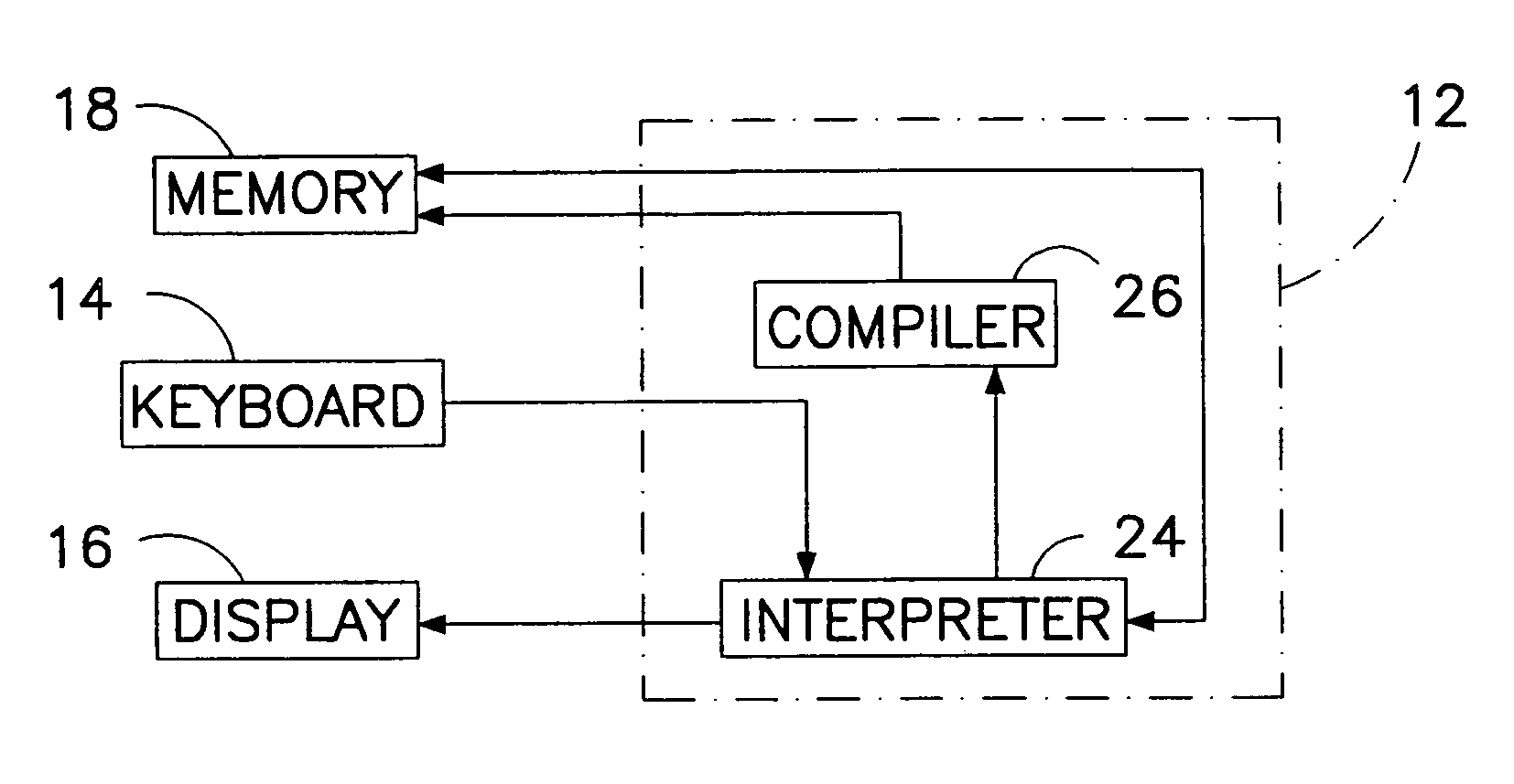
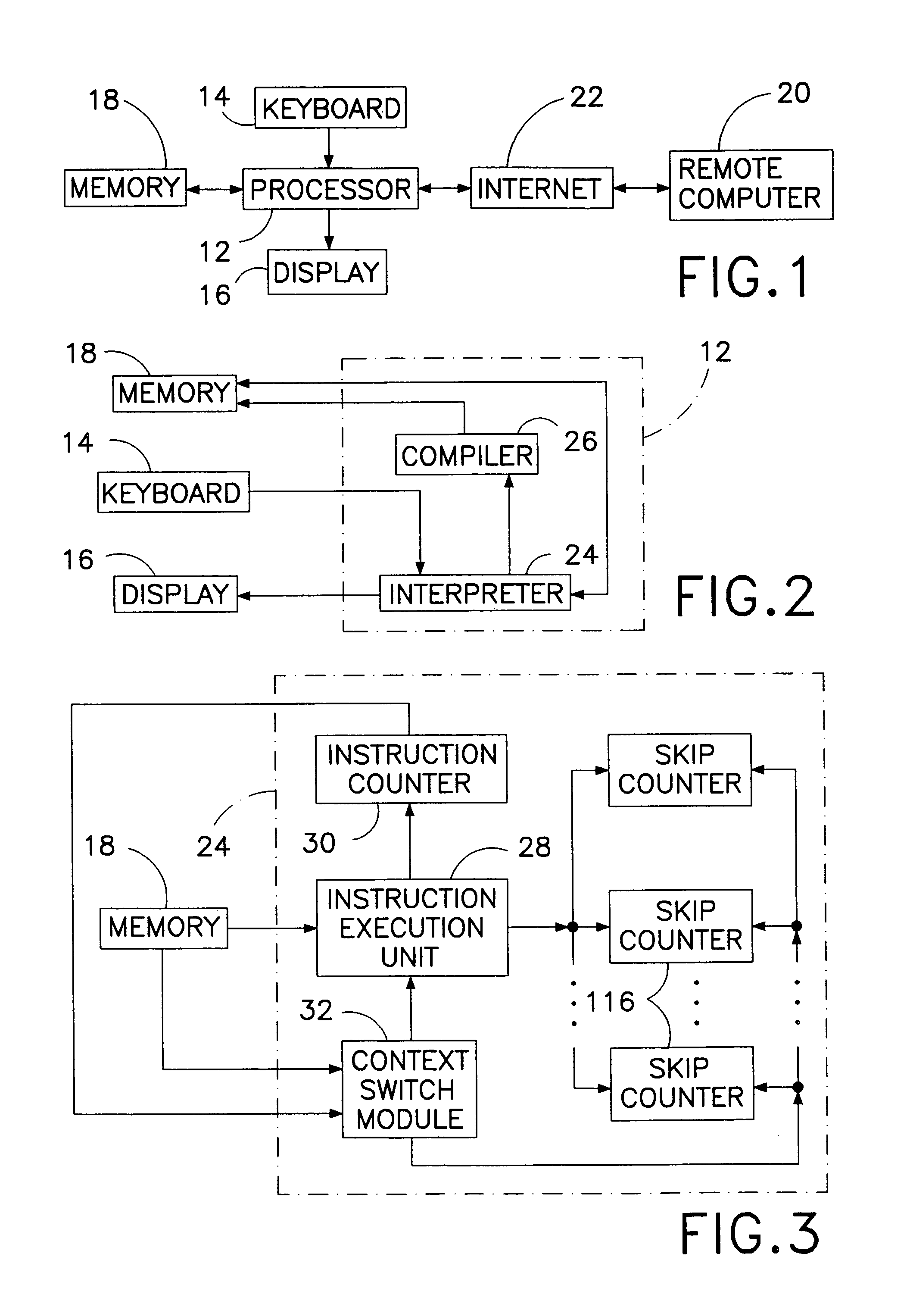
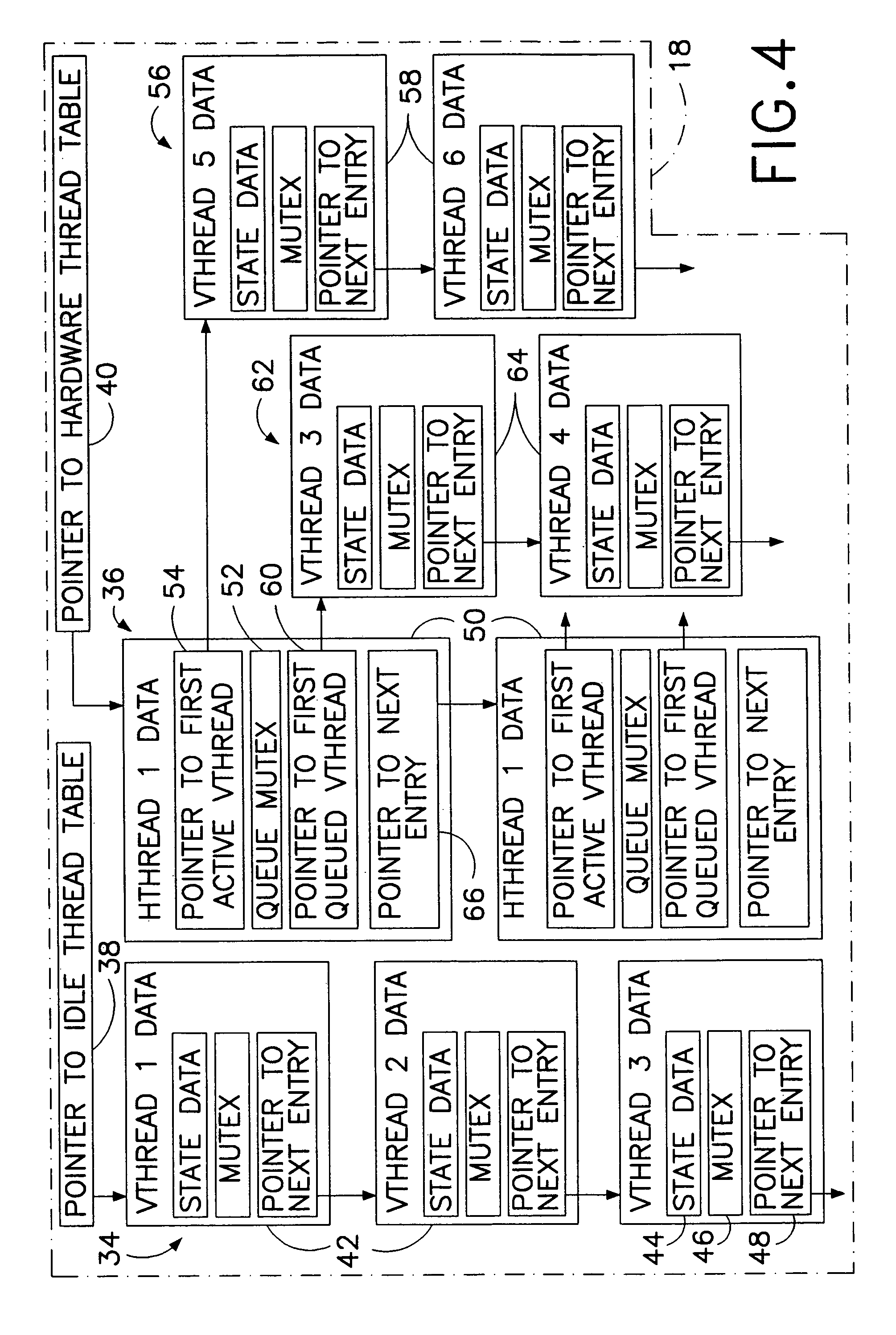
Computer multi-tasking via virtual threading using an interpreter
InactiveUS7234139B1Eliminate dependenciesDifferent operationalProgram initiation/switchingInterprogram communicationLocal variablePseudocode
In the operation of a computer, a plurality of bytecode or pseudocode instructions, at least some of the pseudocode instructions comprising a plurality of machine code instructions, are stored in a computer memory. For each of a plurality of tasks or jobs to be performed by the computer, a respective virtual thread of execution context data is automatically created. The virtual threads each include (a) a memory location of a next one of the pseudocode instructions to be executed in carrying out the respective task or job and (b) the values of any local variables required for carrying out the respective task or job. At least some of the tasks or jobs each entails execution of a respective one of the pseudocode instructions comprising a plurality of machine language instructions. Each of the tasks or jobs are processed in a respective series of time slices or processing slots under the control of the respective virtual thread, and, in every context switch between different virtual threads, such context switch is undertaken only after completed execution of a currently executing one of the pseudocode instructions.
Owner:CERINET USA
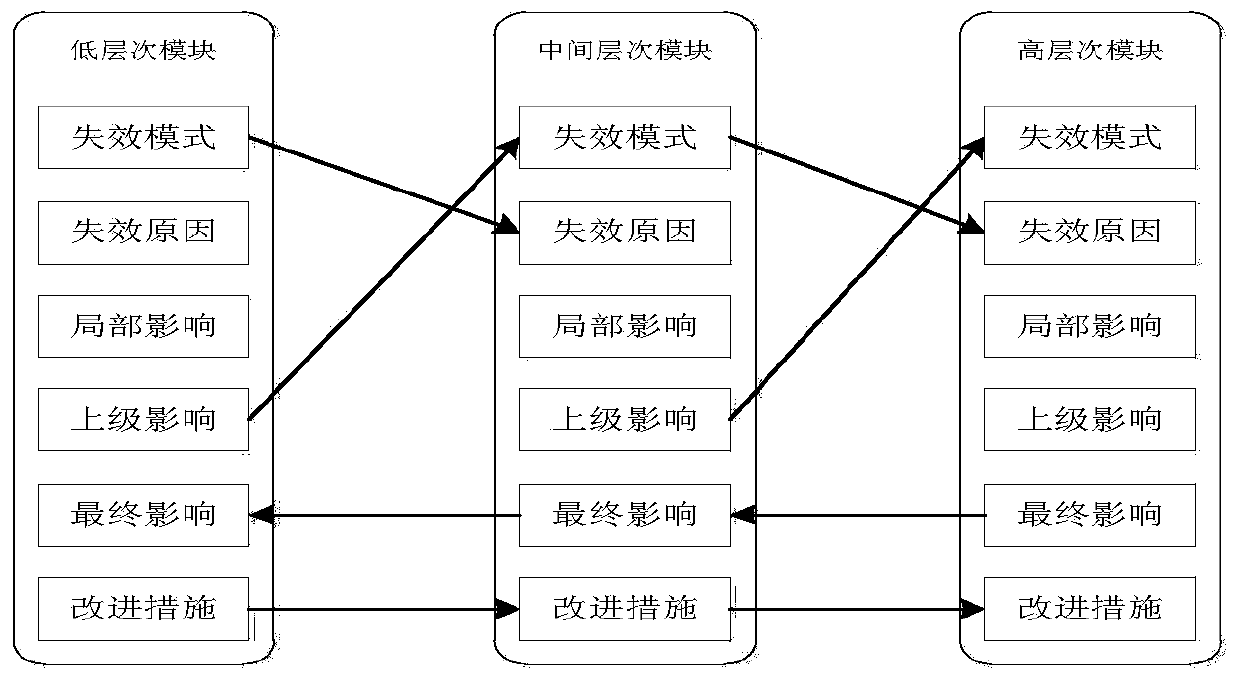
Software FMEA (failure mode and effects analysis) method based on level dependency modeling
InactiveCN103473400AMeet system level FMEAMeet detailed level FMEASpecial data processing applicationsInfluence propagationReachability
The invention discloses a software FMEA (failure mode and effects analysis) method based on level dependency modeling. The method includes 1, understanding an object to be analyzed completely and deeply as required, and determining an analyzing target; 2, establishing a system-grade level dependency model by utilizing outline design as a reference; 3, selecting a module to be analyzed and determine a failure mode thereof, analyzing a failure influence propagation path and a failure reason tracing path to determine a failure reason and the failure influence and provide improvements according to system-grade level dependency model reachability node analysis; 4, selecting a detailed-grade FMEA analyzing object according to a system-grade FMEA result; 5 establishing a detailed-grade level dependency model on the basis of detailed design or a pseudo-code of the selected object to be analyzed; 6, selecting key variables to be analyzed according to the detailed-grade level dependency model; 7, determining a specific failure mode of the key variables to be analyzed, and analyzing producing reasons and failure influences of the variables and providing improvements according to detailed-grade level dependency model reachability node analysis.
Owner:BEIHANG UNIV
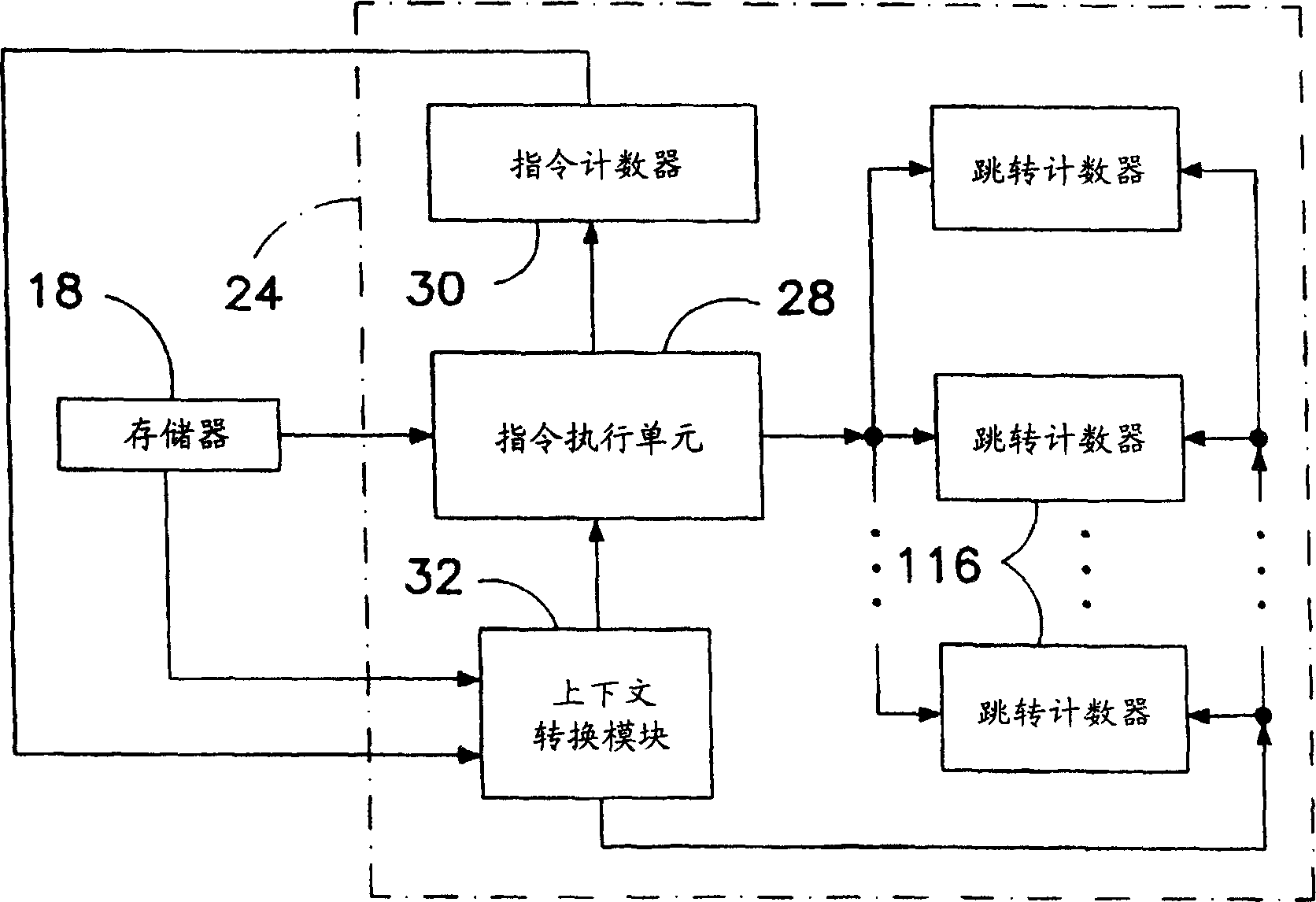
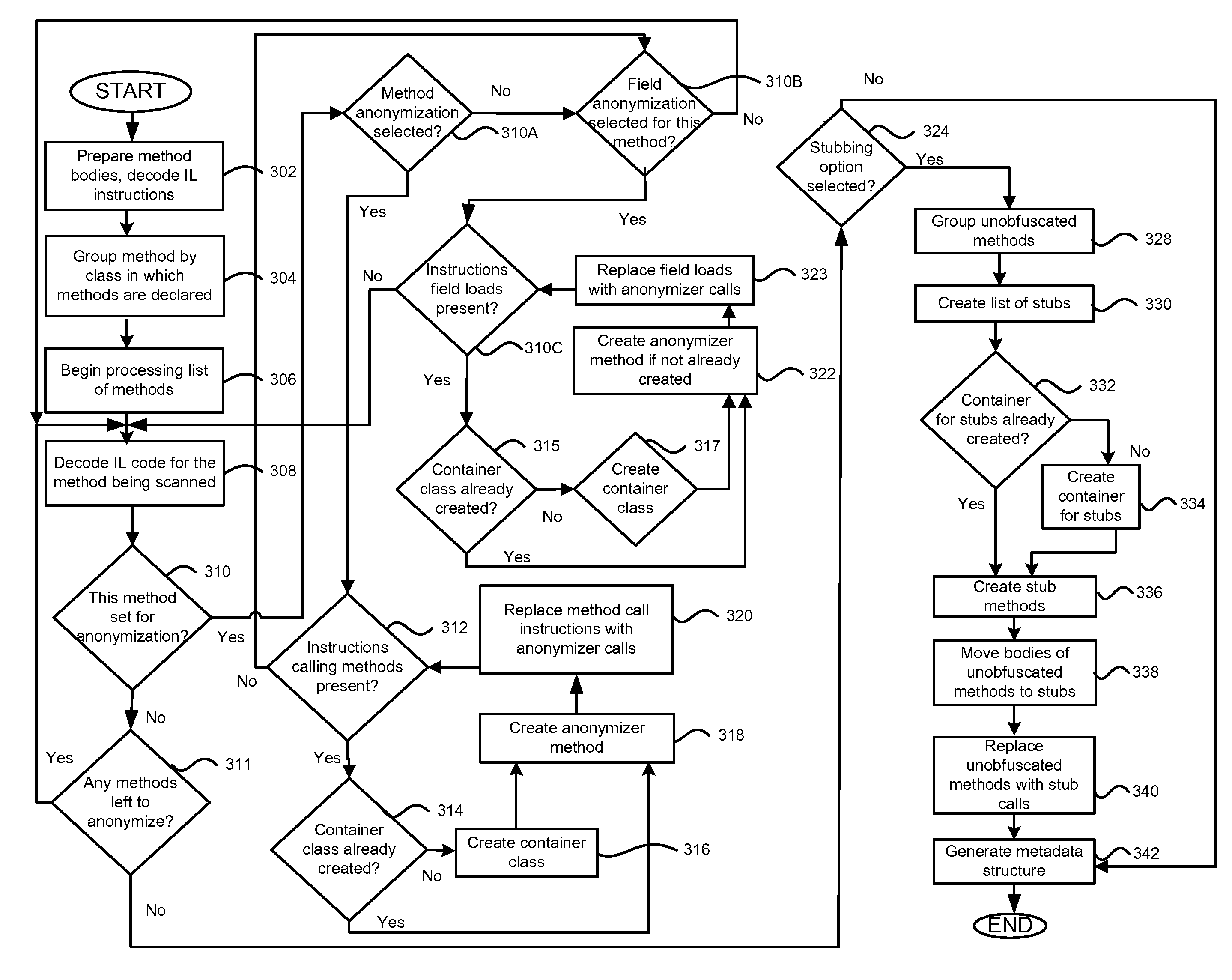
System and method for obfuscation of reverse compiled computer code
InactiveUS20070256061A1Difficult to assembleProgram controlProgram/content distribution protectionLoad instructionObfuscation
A method, system and computer program product for obfuscating pseudocode (e.g., p-code, IL-code, byte-code, etc.), including creating a class-container; declaring an anonymizer method in the class-container; identifying method call instructions in the pseudocode; replacing, in the pseudocode, method calls with calls of the anonymizer method; and in the anonymizer method, adding the method call instructions. All or some of the added method calls have the same name. Parameter types of the added calls can be replaced with an abstract type. Return types of the added calls can be replaced with an abstract type. The class-container is a global class, and includes calls to public method, or the class-container is a private nested class, and includes calls to private methods, or two separate class-containers can be used. Optionally, the invention can include identifying field load instructions in the pseudocode; replacing, in the pseudocode, field load instructions with calls of the anonymizer method; and in the anonymizer method, adding the field load instructions.
Owner:VICTOR Y VICTOROV
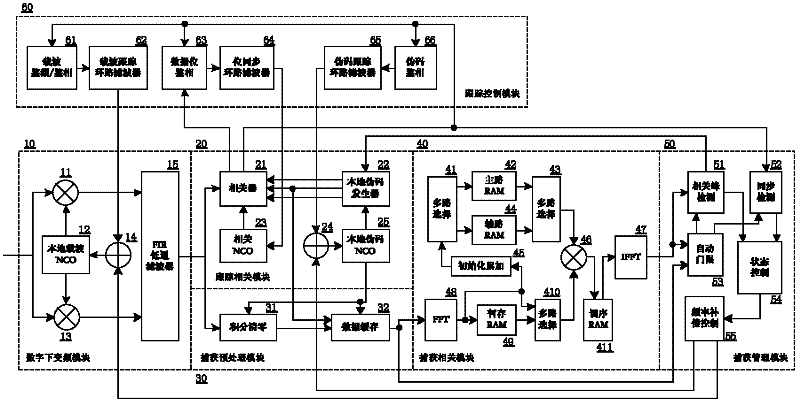
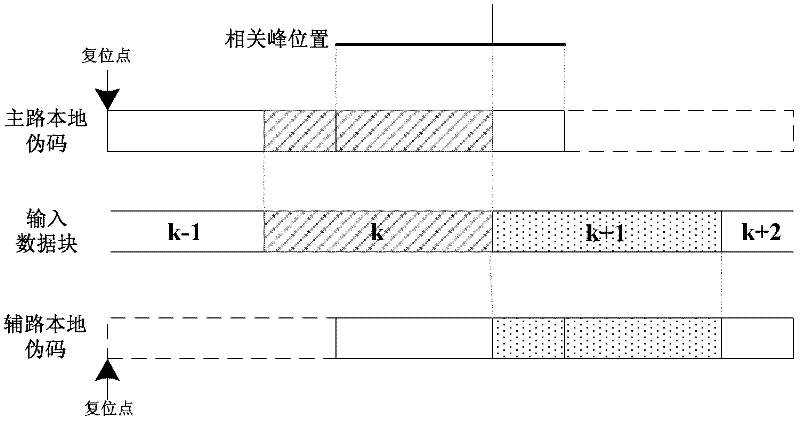
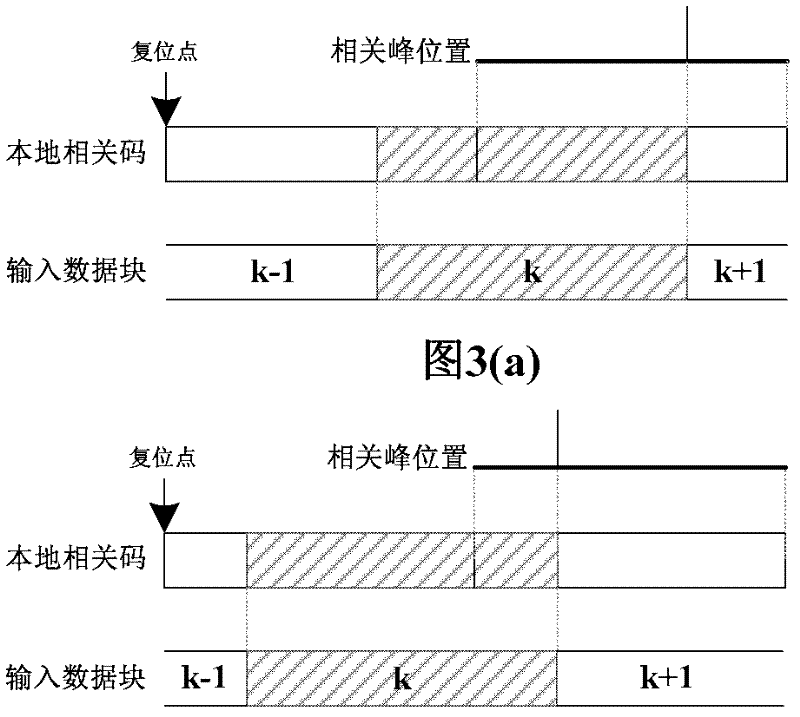
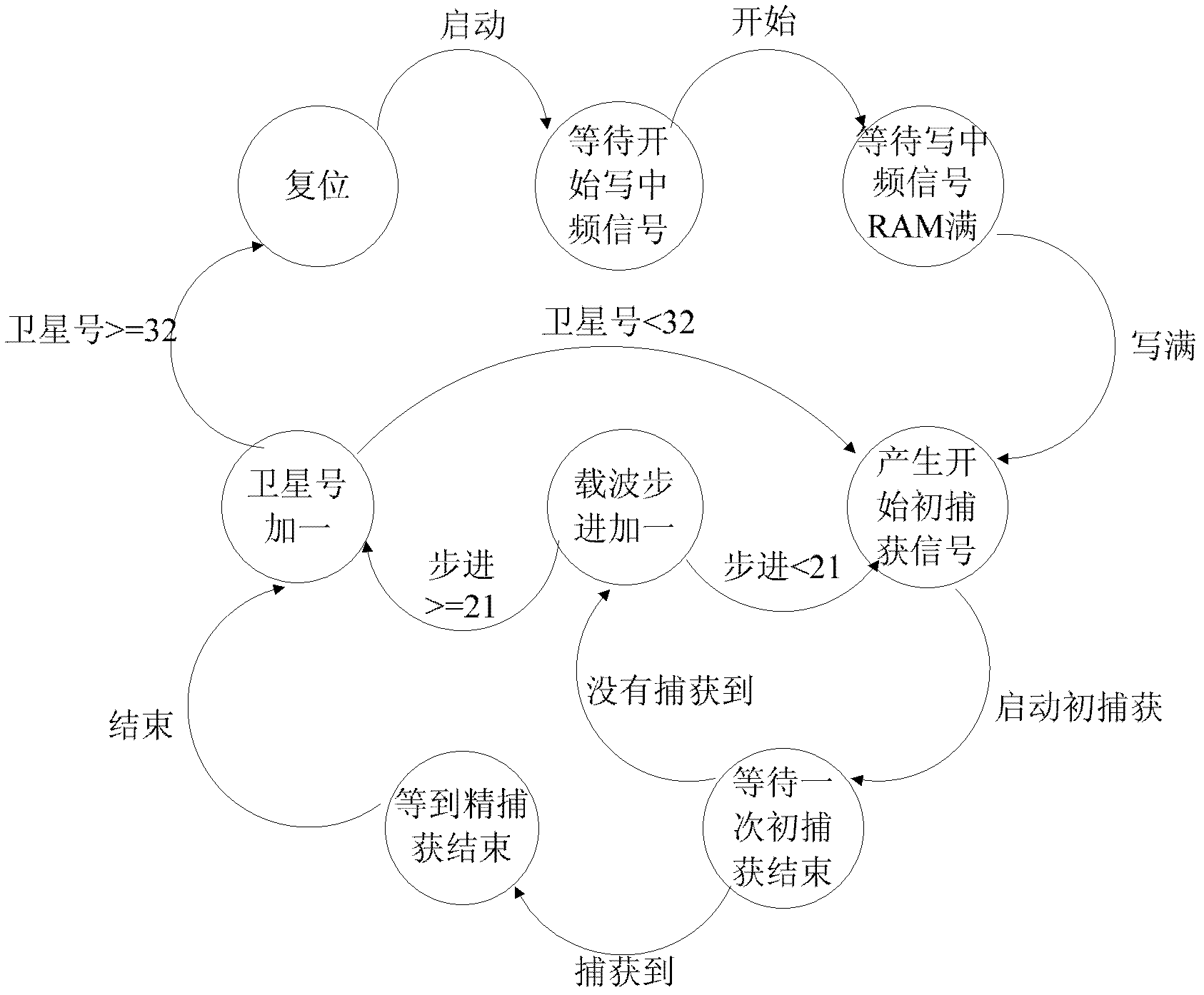
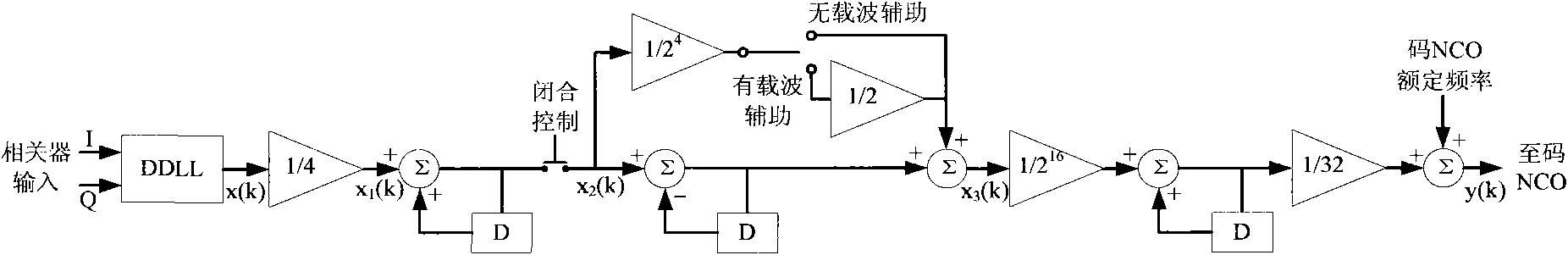
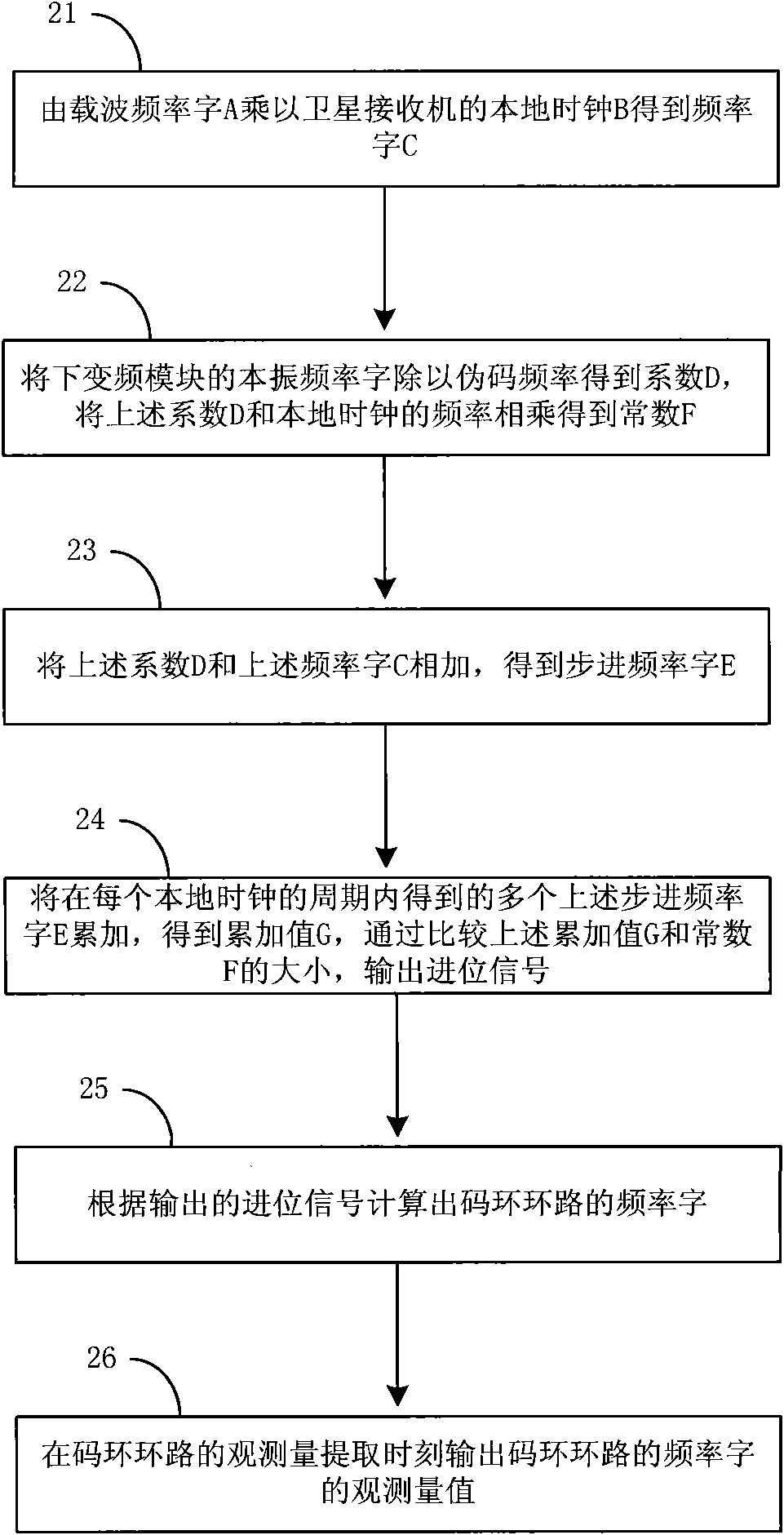
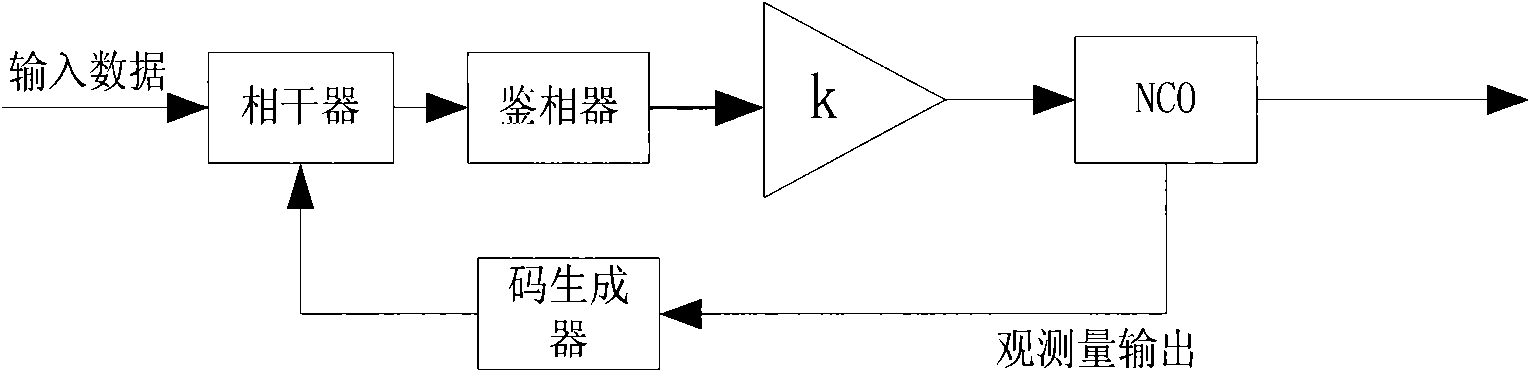
Universal pseudocode synchronization system of comprehensive satellite baseband equipment
ActiveCN102594393AFast captureReduce resource consumptionTransmissionDigital down conversionPseudocode
The invention relates to a universal pseudocode synchronization system of comprehensive satellite baseband equipment, and the system comprises six parts, i.e. a digital lower variable frequency module (10), a tracking related module (20), a capture pre-processing module (30), a capture related module (40), a capture management module (50) and a tracking control module (60), and completes the pseudocode capture, carrier tracking, pseudocode tracking and bit synchronization functions of remote control or range finding data in a test to a satellite according to a preset process; and the six parts are realized in a field-programmable gate array (FPGA). According to the universal pseudocode synchronization system of the comprehensive satellite baseband equipment, the parameters of the capture module are configured flexibly according to the test needs of the actual satellite, so that the quick capture and tracking of various remote control signal or range finding signal pseudocodes are realized, and the system has better practical value and wide application prospect in the technical field of comprehensive satellite baseband testing.
Owner:BEIHANG UNIV
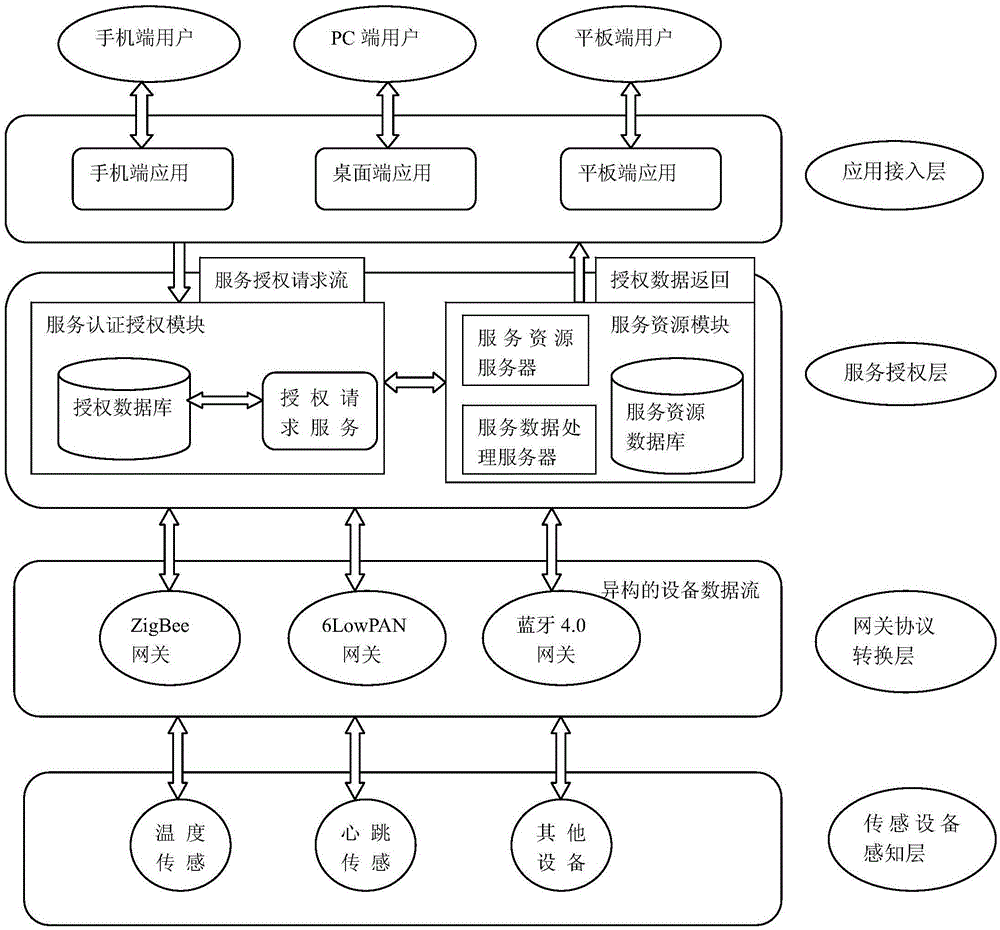
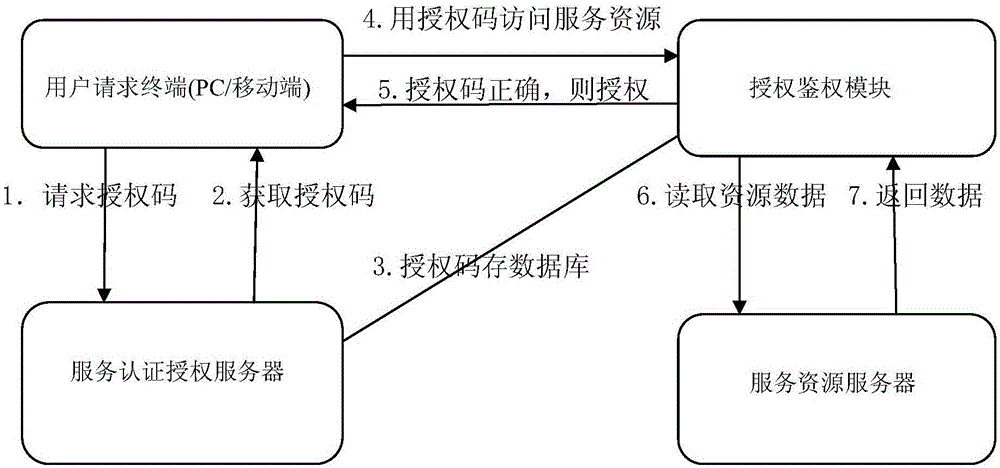
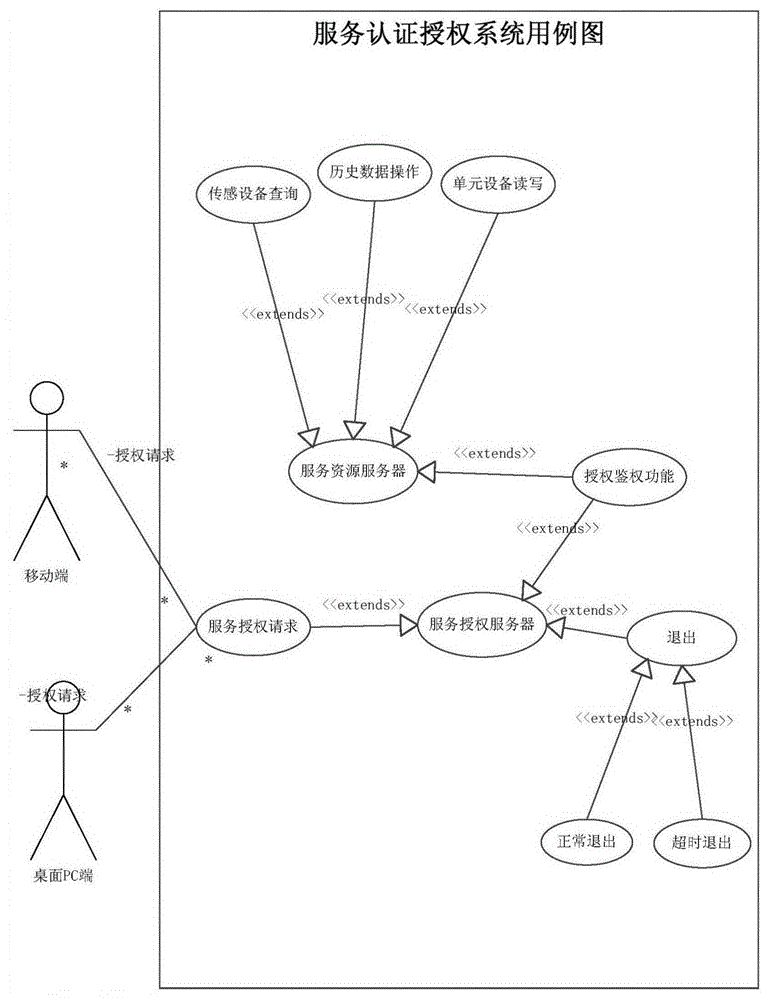
Smart service based open authorization access design method and system
ActiveCN105117657AAuthorization is controllableProtection securityDigital data protectionDigital data authenticationResponse processPseudocode
The invention discloses a smart service based open authorization access design method and system. The method comprises the following steps: step 1: describing relations among modules of a service authorization layer and a service authorization request process; step 2: according to the relations among the modules of the service authorization layer and the service authorization request process in the step 1, designing a service open authorization system and providing a service authorization access function; step 3: according to the steps 1 and 2, designing a service authentication and authorization state response required for service open authorization access and using a pseudocode for describing a service authentication and authorization state response process; step 4: according to the steps 2 and 3, designing a class of a service authentication and authorization module; step 5: according to the class of the service authentication and authorization module in the step 4, designing a required database table structure comprising a table name, a table field and a field type; and step 6: according to the steps, designing a service open authorization interface calling time sequence chart and describing a service open authorization interface calling realization process in a pseudocode form.
Owner:NANJING UNIV OF POSTS & TELECOMM
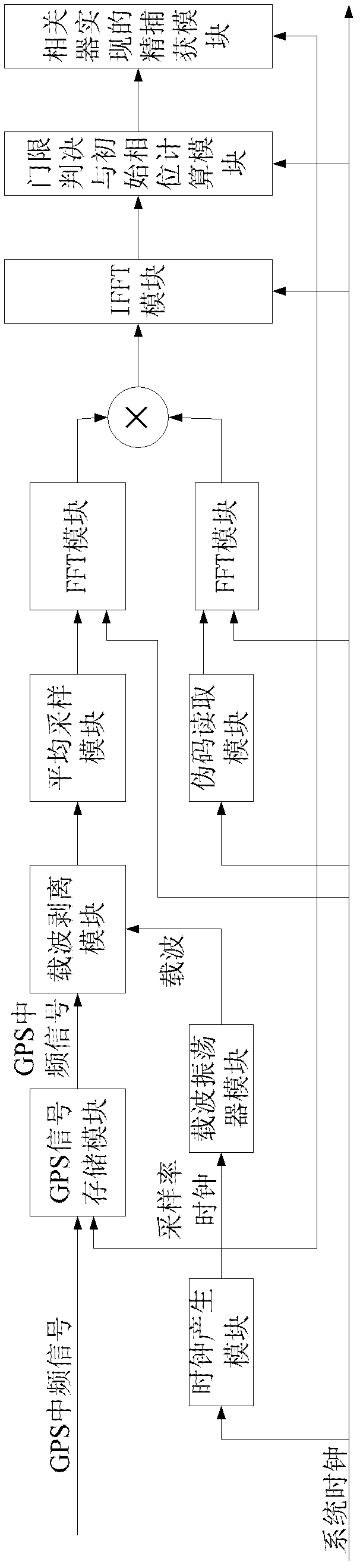
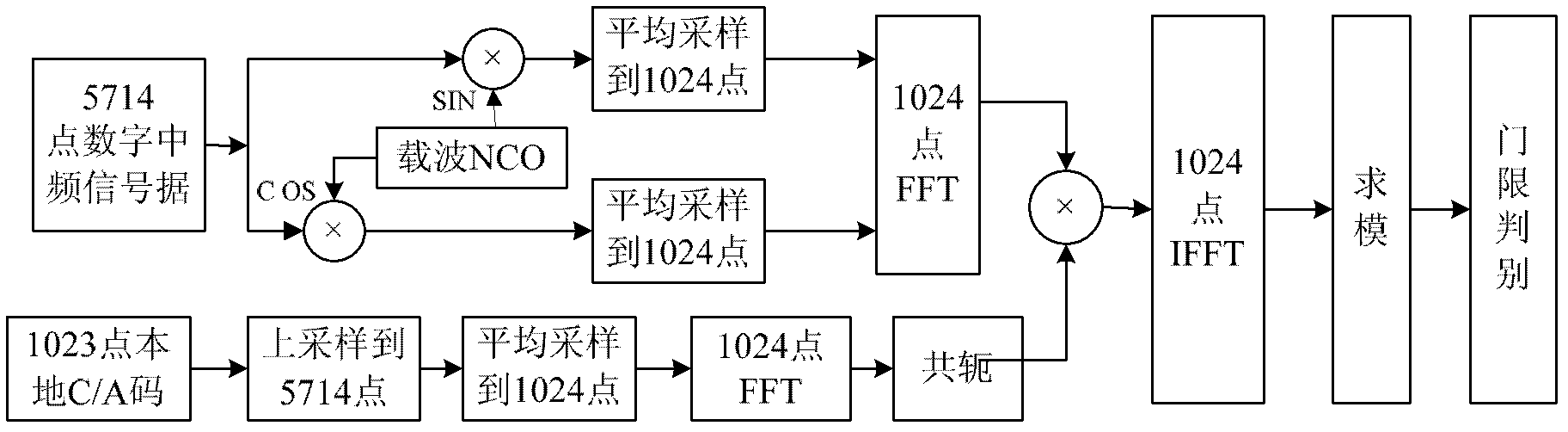
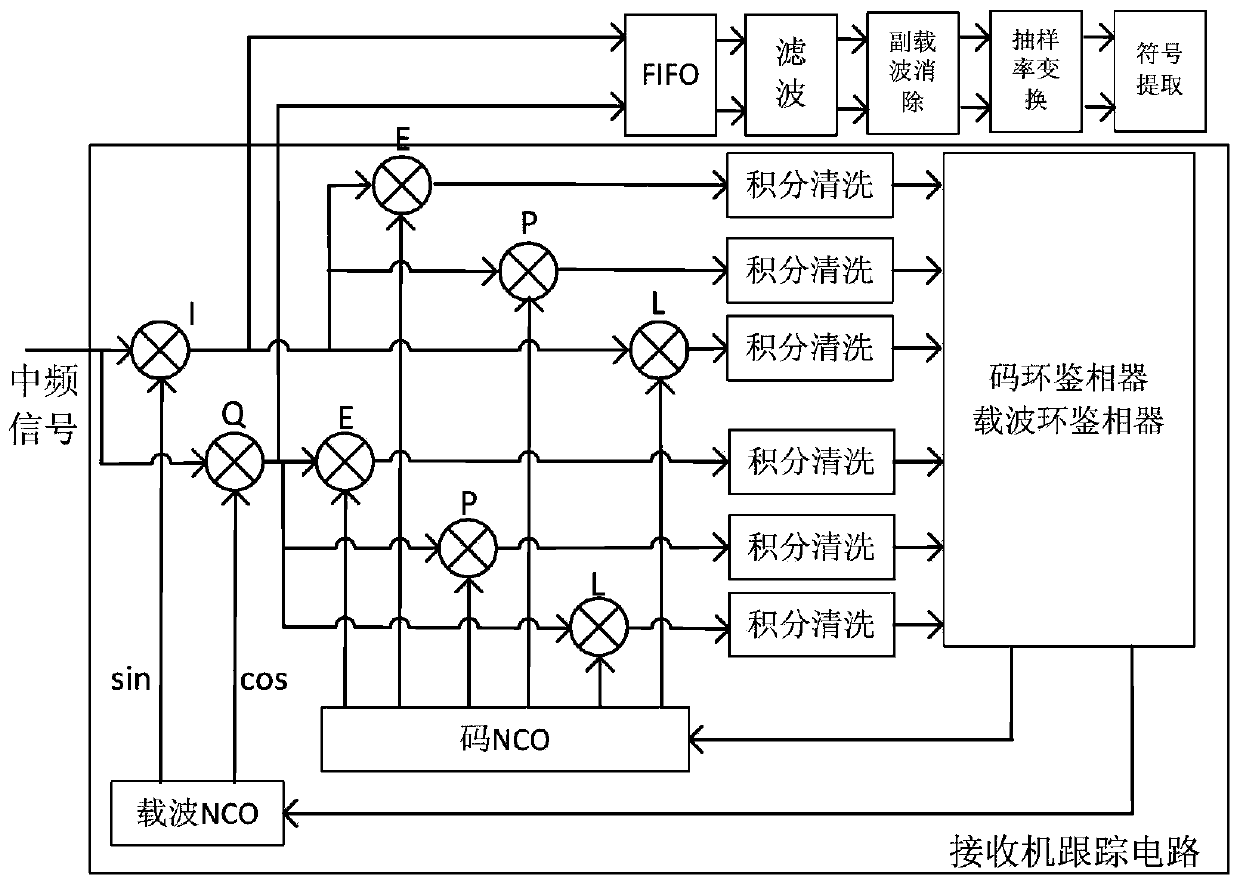
GPS (Global Positioning System) signal acquisition method based on FPGA (Field Programmable Gate Array) and GPS signal acquisition system
InactiveCN102353968AReduce computationReduce the number of data pointsSatellite radio beaconingPseudocodeCarrier signal
The invention discloses a GPS (Global Positioning System) signal acquisition method based on an FPGA (Field Programmable Gate Array), which comprises the following steps of: firstly, carrying out down sampling on a medium-frequency acquisition signal by adopting an average sampling method; taking data obtained by averaging the energy of a point during each sampling period as sample data subjectedto down sampling, wherein the averagely-sampled points meet 2FFT (Fast Fourier Transformation) operation; finishing initial acquisition of the GPS signal to obtain an initial phase range of a pseudocode and initial carrier frequency; and carrying out further fine acquisition by using a time domain correlation algorithm to obtain accurate initial phase of the pseudocode and carrier frequency. An FPGA hardware platform is set up in the acquisition system and is combined with a radio-frequency front-end chip of a GSP receiver; and the acquisition system comprises a clock generation module, a main control module realized by a state machine, a GPS signal storage module, a carrier oscillator module, a carrier stripping module, a pseudocode reading module, an average sampling module, an FFT(FastFourier Transformation) / IFFT (Inverse Fast Fourier Transform) module, a threshold decision and initial phase calculation module and a fine acquisition module realized by a correlator.
Owner:SOUTHEAST UNIV
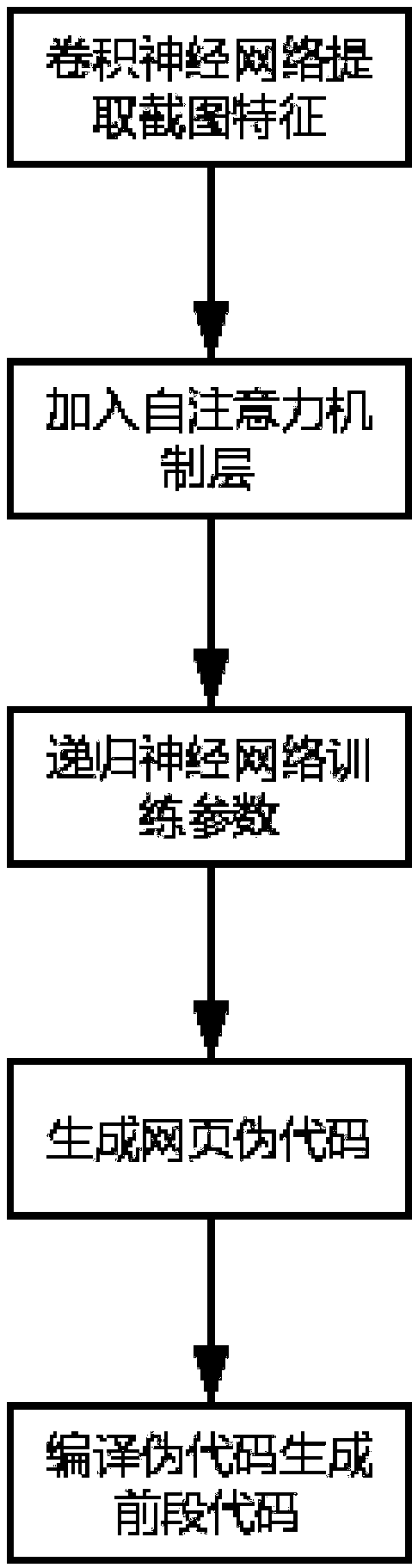
Method for generating a web page screenshot code based on a neural network and a self-attention mechanism
InactiveCN109522017AEasy to identifyConvenience to followCharacter and pattern recognitionNeural architecturesPseudocodeTheoretical computer science
The invention discloses a method for generating a web page screenshot code based on a neural network and a self-attention mechanism, which comprises the following steps: extracting key features from web page screenshots of several platforms through a convolution neural network; generating a web page screenshot code based on the web page screenshots of several platforms through a convolution neuralnetwork. By applying the self-attention mechanism, carrying out associated learning operation on the key features obtained in step S1 and the web page code to enhance the attention of the text to itsown information; learning The processed image features and web page codes through the loop neural network, and acquiring the corresponding network parameters. Generating a pseudo code of a web page screenshot using the network parameters obtained in step S4; compiling The pseudo code in step S4 further to obtain the final generated web screenshot code. The invention can better identify the features in the web page screenshot, can better pay attention to the syntax associated with the front and back in the code text and match with the generated web page screenshot features, has high practicalvalue, and can help the developer of the front section to improve the development efficiency.
Owner:SUN YAT SEN UNIV
Spatial decomposition methods using bit manipulation
ActiveUS20040201584A1Increase speedEnhance analytical option3D-image rendering3D modellingDecompositionPseudo-code
The invention relates to image decomposition strategies and computer-based methods for implementing them. In one method of the invention, the ordering of tetrahedral shapes that define or approximate an image is performed in such a way that neighboring tetrahedral shapes can be identified, located and efficiently used. In one aspect, a binary location code array is used to represent an image and the method for identifying the neighbor shape employs a bit manipulation step in code or pseudo-code for operating a computer. In this aspect, the invention allows one to move between adjacent tetrahedra, and any data corresponding to the tetrahedra, in constant time.
Owner:BINARY SIMPLEX
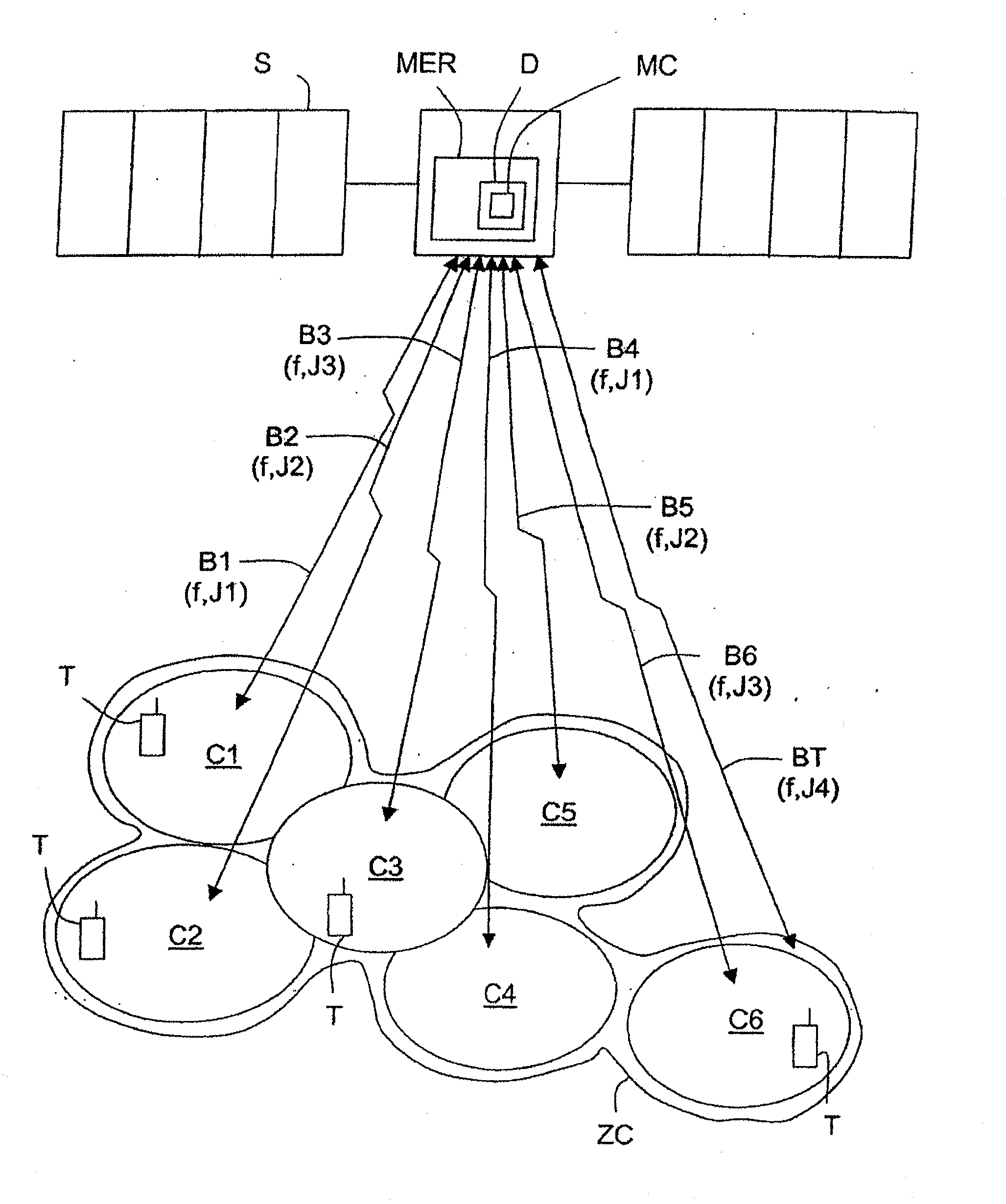
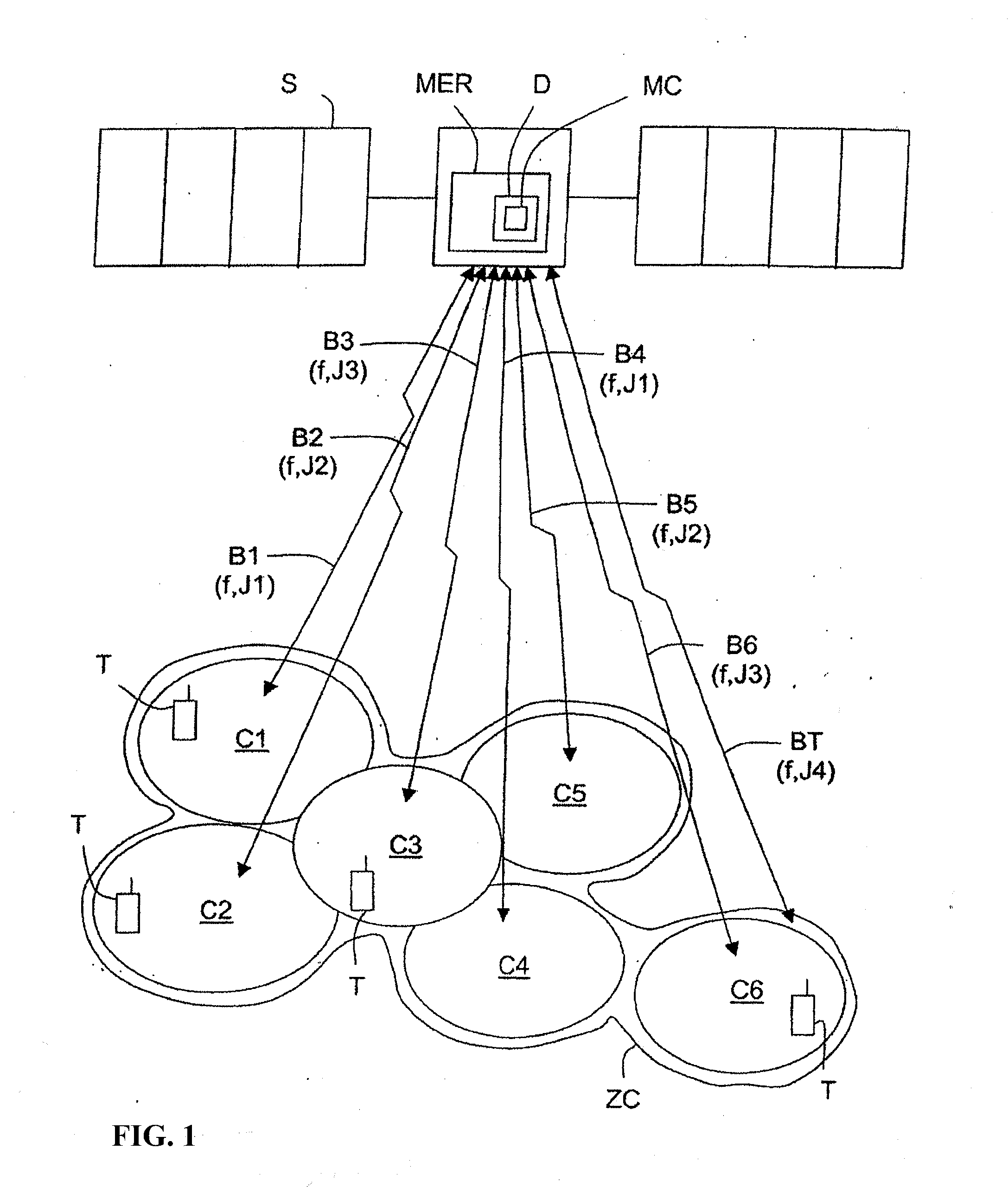
Device and Method for Processing Data by Modulating Sets of Spreading Pseudocodes as a Function of Data Destination Cells for a Multi-Beam Communication Satellite
InactiveUS20080298439A1Good conditionCode division multiplexRadio transmissionPseudocodeCarrier signal
A device (D) is dedicated to the processing of data by spread spectrum coding for a multi-beam communication satellite (S), each beam (B1-B6) of which is associated with a terrestrial cell (C1-C6) contained in a satellite coverage zone (ZC). This device (D) comprises coding means (MC) charged i) with associating, on the one hand, sets of pseudo-spreading codes (J1-J4), differing pairwise, with adjacent cells of the zone (ZC) and with signalling channels common to the collection of cells (C1-C6) of this zone (ZC), and on the other hand, identical sets of pseudo-spreading codes with non-adjacent cells of the zone, the sets (J1-J4) being chosen from among sets resulting from the subdivision of a collection of pseudo-spreading codes, and ii) when data have to be broadcast in a cell (C1) and / or common information data have to be broadcast in the collection of cells, with modulating pseudo-spreading codes belonging to the set (J1) associated with this cell (C1) with the data to be broadcast, then with modulating a carrier, whose frequency (f) is the same for all the beams (B1-B6) of the satellite (S), with the modulated pseudo-spreading codes so that the modulated carrier is broadcast towards the cell (C1) or the collection of cells (C1-C6) by means of the associated beam (B1).
Owner:THALES SA
Method and device for implementing computer multi-tasking via virtual threading
Owner:CATHARON PRODIONS
System and method for obfuscation of reverse compiled computer code
InactiveUS7937693B2Program controlProgram/content distribution protectionLoad instructionObfuscation
A method, system and computer program product for obfuscating pseudocode (e.g., p-code, IL-code, byte-code, etc.), including creating a class-container; declaring an anonymizer method in the class-container; identifying method call instructions in the pseudocode; replacing, in the pseudocode, method calls with calls of the anonymizer method; and in the anonymizer method, adding the method call instructions. All or some of the added method calls have the same name. Parameter types of the added calls can be replaced with an abstract type. Return types of the added calls can be replaced with an abstract type. The class-container is a global class, and includes calls to public method, or the class-container is a private nested class, and includes calls to private methods, or two separate class-containers can be used. Optionally, the invention can include identifying field load instructions in the pseudocode; replacing, in the pseudocode, field load instructions with calls of the anonymizer method; and in the anonymizer method, adding the field load instructions.
Owner:VICTOR Y VICTOROV
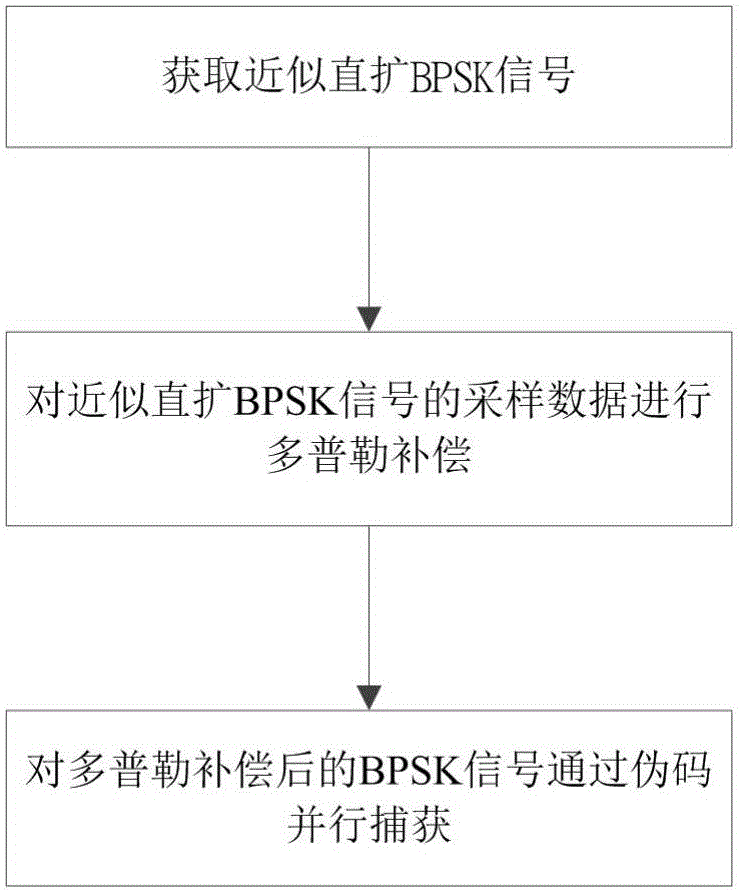
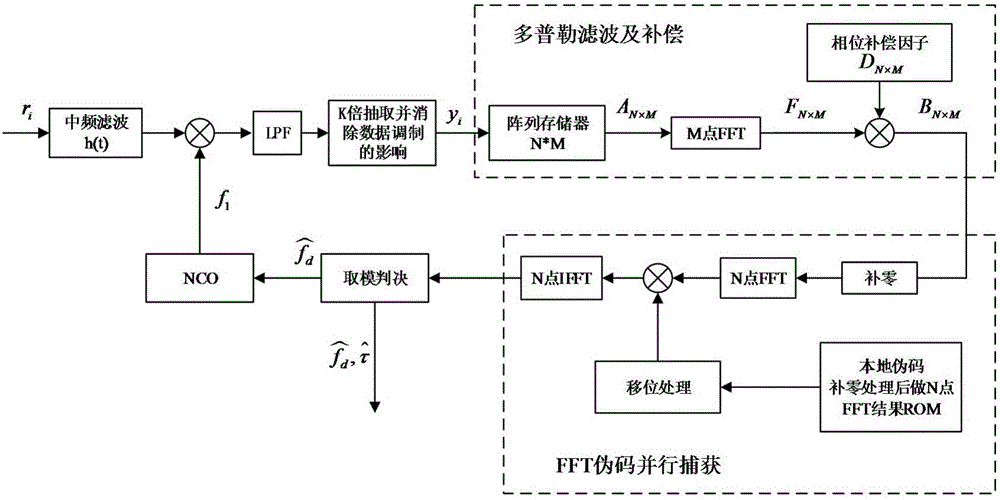
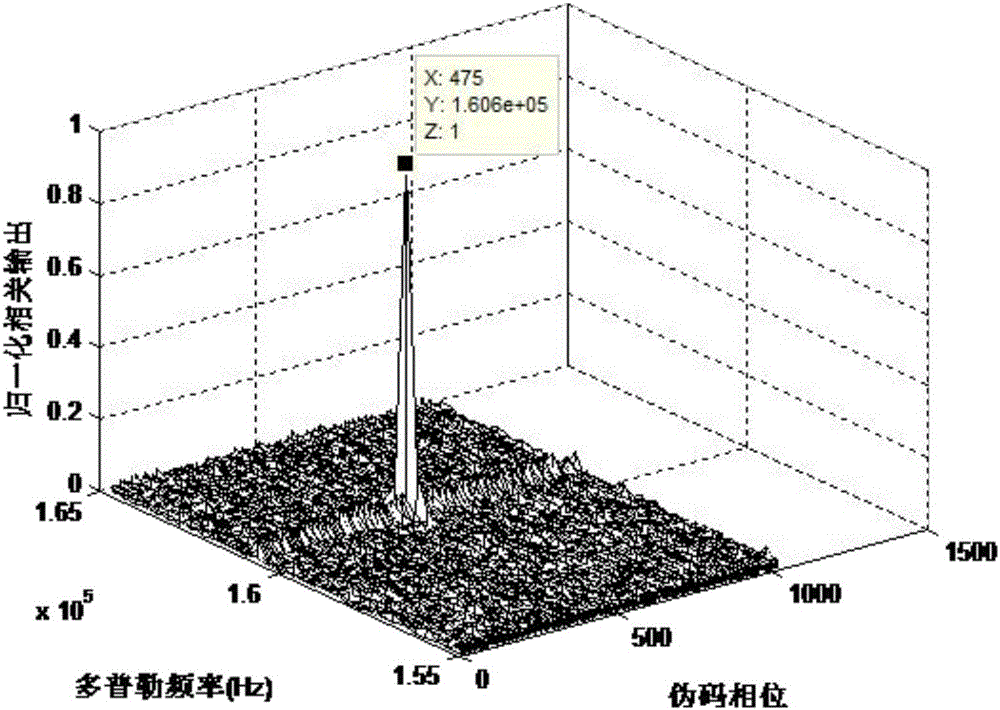
Pseudocode-Doppler combined capturing method of direct sequence spread spectrum MSK signal
ActiveCN105790788AReduce complexitySolve complex problemsTransmissionSignal-to-noise ratio (imaging)Pseudocode
The invention provides a pseudocode-Doppler combined capturing method of a direct sequence spread spectrum MSK signal. The method comprises the following steps of converting the direct sequence spread spectrum MSK signal to an appropriate direct sequence spread spectrum BPSK signal through intermediate-frequency matching processing; performing Doppler compensation on sampling data of the appropriate direct sequence spread spectrum BPSK signal; capturing the code phase error, the Doppler channel and Doppler displacement value of the BPSK signal after Doppler compensation through a pseudocode parallel capturing method, and acquiring a Doppler frequency offset according to the Doppler channel and the pseudocode displacement value. The pseudocode-Doppler combined capturing method can realize capturing of the direct sequence spread spectrum MSK signal in a high dynamic condition and furthermore finishes combined estimation for the pseudocode phase and the Doppler frequency offset. On the condition of relatively low signal-to-noise ratio, not only is relatively low Doppler frequency offset estimation error realized, but also high pseudocode phase capturing performance is obtained, thereby ensuring relatively good coarse synchronization of a received signal before entering a signal tracking processing module.
Owner:NANJING UNIV OF SCI & TECH
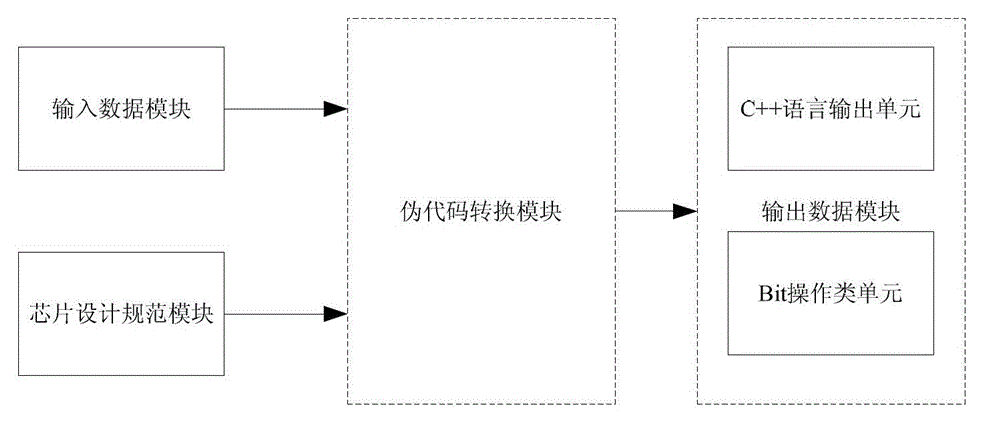
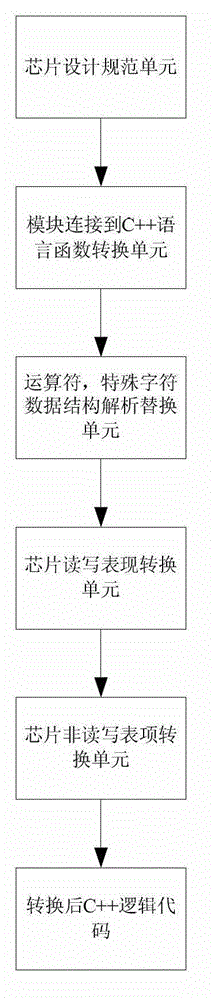
System and method for converting pseudocode into programming language
ActiveCN103336706AImprove test efficiencyFunctional verificationProgram controlMemory systemsPseudocodeSoftware language
The invention discloses a system and a method for converting a pseudocode into a programming language. The system comprises a data input module, a chip design specification module, a pseudocode conversion module and a data output module, wherein the data output module comprises a programming language output unit and a Bit operation type unit, and after the data input module and the chip design specification module are converted by the pseudocode conversion module, the programming language output unit outputs the generated programming language, and converts the pseudocode into a software language capable of being used directly by matching with the Bit operation type unit complying with the programming language. According to the system and the method, the conversion time from the pseudocode to the software language is shortened greatly, the functionality and the logicality of chip design logic can be verified efficiently, and the efficiency of chip testing is improved.
Owner:苏州盛科科技有限公司
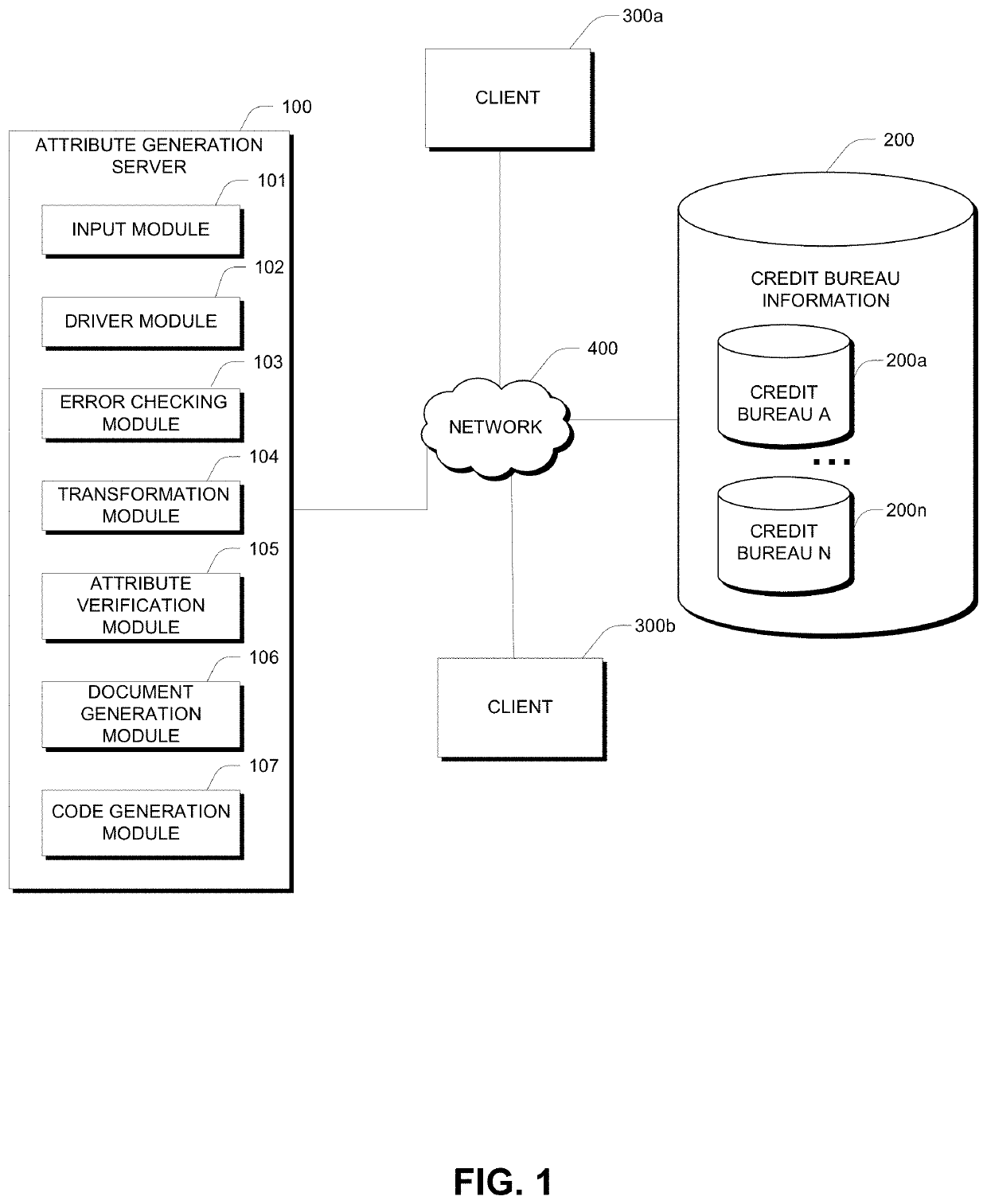
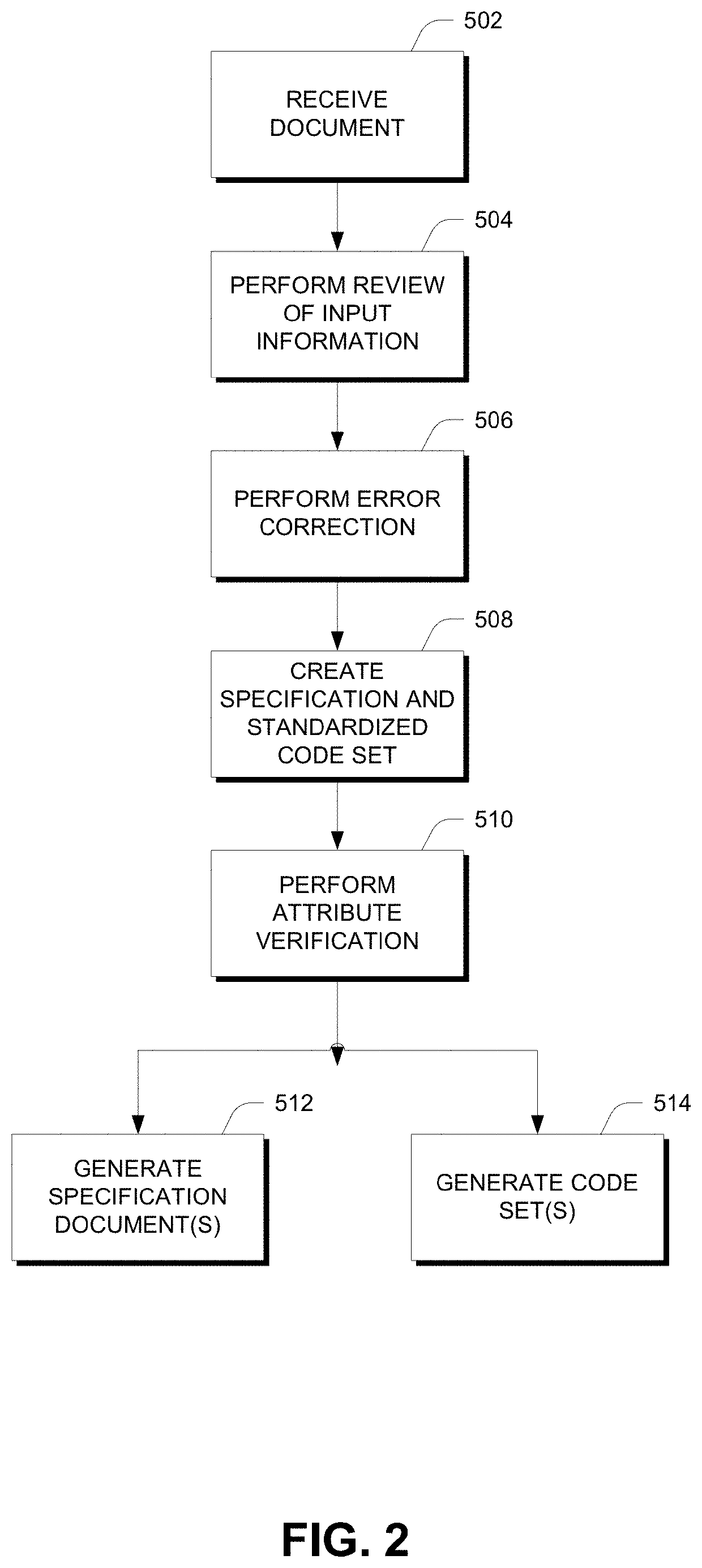
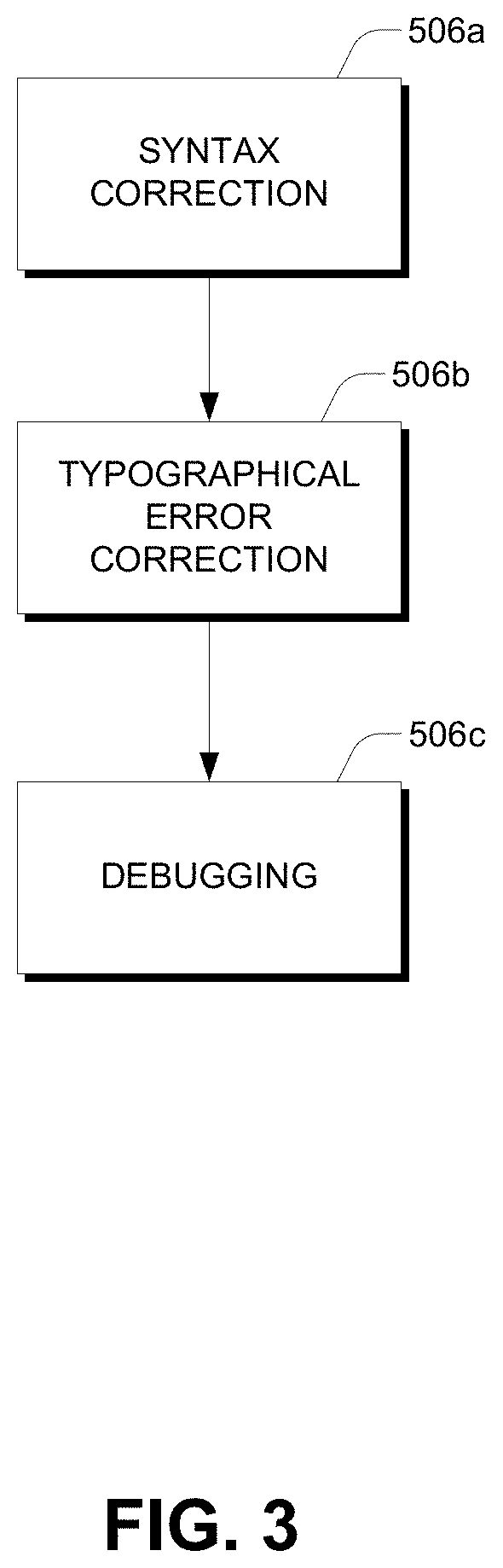
Automatic generation of code for attributes
One embodiment of a system for automatically generating code for attributes includes a credit bureau data that store stores credit bureau convention information and an attribute generation system that communicates with the credit data store to detect rules associated with respective credit bureaus. The system may include an input module which receives, from a user system, a document comprising pseudo-code defining attributes including credit bureau specific logic; an error checking module which automatically performs error checking and provides error correcting information on the document; an attribute verification module which parses the document to identify attributes and automatically retrieves rules associated with the respective credit bureaus; a document generation module which generates an attribute specification document based on the retrieved rules as applied to the attributes in the document; and a code generation module which generates an executable code set based on the retrieved plurality of attributes and credit bureau specific rules.
Owner:EXPERIAN INFORMATION SOLUTIONS
Search algorithm and verification method for swarm robots based on physarum polycephalum foraging
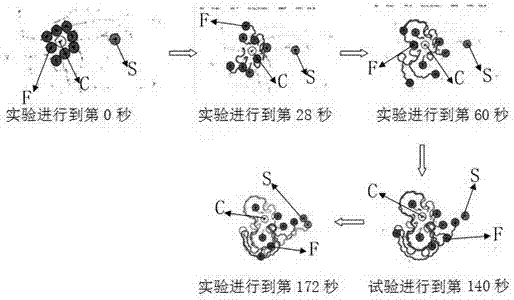
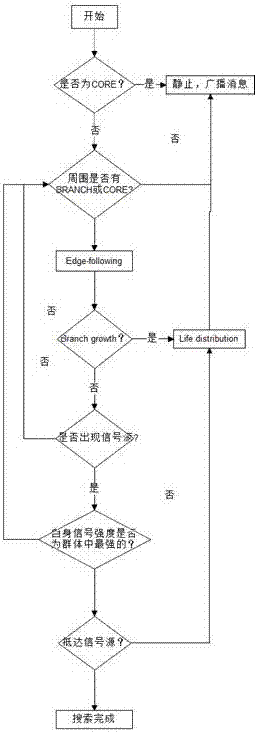
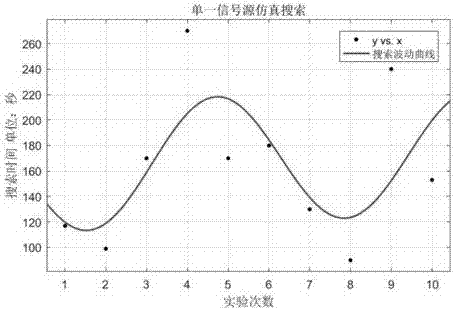
ActiveCN107066705AThe effect conclusion is goodImprove efficiencyGeometric CADDesign optimisation/simulationSearch problemPseudocode
The invention relates to the technical field of multi-agent genetic algorithms, in particular to a search algorithm and a verification method for swarm robots based on physarum polycephalum foraging. The swarm robots are divided into three types of robots which are named as CORE, BRANCH and FORAGER; operation processing steps of data comprise four phases, namely an initialization phase, a dispersion search phase, an edge search phase and a signal source attracting phase. According to the search algorithm and the verification method disclosed by the invention, search calculation is performed by adopting a mode of controlling the swarm robots to execute simulation of the physarum polycephalum foraging by pseudocodes; simulated experiment verification for a single signal source and multiple signal sources is realized by a simulation experiment platform; demonstration and verification of the single signal source are realized in a hardware simulation experiment, and thus better effects and conclusions for coverage search in a situation of limited communication radius of the robot are obtained by the algorithm disclosed by the invention, and a simple algorithm which less depends on robot communication and adapts to area coverage searching is realized; the algorithm has higher efficiency and application value for the area coverage searching.
Owner:DONGGUAN UNIV OF TECH +1
Modulation identification and blind pseudo-code sequence estimation of MC-CDMA signals
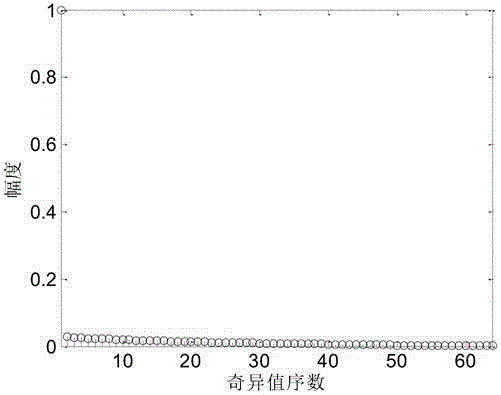
InactiveCN105871764AImproved noise immunityImprove noise immunityModulation type identificationCode division multiplexSingular value decompositionPrior information
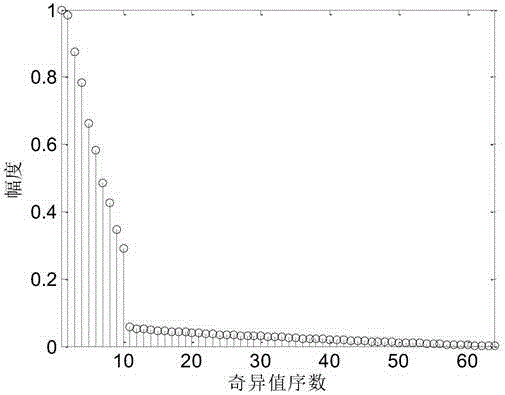
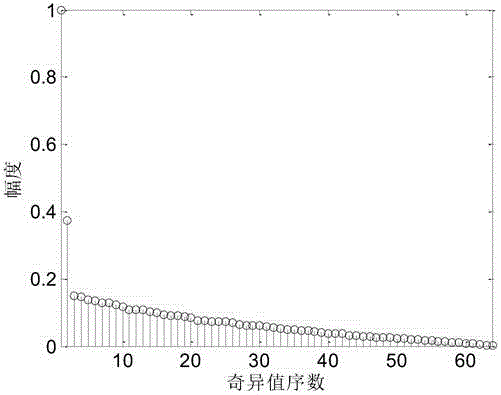
The invention claims a singular value decomposition-based MC-CDMA signal modulation identification and pseudo-code sequence estimation method, which belongs to the technical field of signal processing. By removing the cyclic prefix first, then constructing the matrix and performing singular value decomposition on it, the signal categories can be distinguished according to the number of eigenvalues. Since the number of eigenvalues of a single-user MC-CDMA signal is always 1, it has nothing to do with the size of the construction matrix, so it is easy to distinguish from it. In the case of known prior information such as modulation type and pseudo-code period, the pseudo-code sequence is estimated by the left singular vector. For complex problems such as classifier design, the algorithm has the advantage of less calculation for the estimation of pseudocode sequences. The method can effectively distinguish MC-CDMA and MC-DS-CDMA signals, and at the same time blindly estimate the pseudo-code sequence of the MC-CDMA signal, which is of great significance for the subsequent processing of the signal and the analysis of subtle features.
Owner:CHONGQING UNIV OF POSTS & TELECOMM
Multiplexed navigation signal pseudo code extraction method
ActiveCN110208832AShorten development timeAvoid the effects of extractionSatellite radio beaconingMultiplexingFrequency spectrum
The invention discloses a multiplexed navigation signal pseudo code extraction method. The method utilizes the existing navigation receiver to realize real-time extraction of each component pseudo code of a multiplexed signal. According to the multiplexed navigation signal pseudo code extraction method based on a navigation receiver technology, the receiver is firstly adopted to realize carrier synchronization and pseudo code synchronization of a known civilian code signal; and then, by using multiplexed signal I / Q orthogonality and spectral separation characteristics, navigation signal pseudocode extraction is realized. Compared with demodulation methods based on BPSK, QPSK, BPSK-LIKE and the like, the method disclosed in the invention can avoid the influences of receiver losing lock onpseudo code extraction and has great advantages and feasibility. In addition, as no additional signal synchronization circuit is required, the development time can be greatly saved.
Owner:NO 54 INST OF CHINA ELECTRONICS SCI & TECH GRP
Method for capturing pseudocode under non-Gaussian channel
The invention provides a method for capturing pseudocode under a non-Gaussian channel, which comprises the following steps: after being processed by the operations of carrier wave striping and pseudocode dispreading treatment, a received signal is converted into two observed quantities Xi and Xiof two I / Q branches; after being processed by the operation of squaring, the two observed quantities are added to the quadratic term gammaof a dispersion coefficient, and the obtained result is respectively divided by the two observed quantities of the I / Q branches to obtain reciprocal values so that the value of statistical quantity of each branch at a single time can be obtained; the values from 1 to M time (the variable of i) are sequentially processed by the steps of accumulation addition and square; and finally, the values of the two branches are added to each other to obtain and compare the statistical quantity with the threshold so as to judge whether a signal is captured or not, and the phase position of the local pseudocode is slid to carry out the operations of secondary judgment and comparison until the signal is captured under the circumstance that the statistical quantity is lower than the threshold. Proved by the result of comparison of performance simulation of the pseudocode capturing method of the invention and the traditional pseudocode capturing method, the detection performance of the pseudocode capturing method of the invention is drastically improved under the non-Gaussian noise environment, and the more obvious the pulse characteristic is, the more obvious the advantage of the detector designed by the invention can be.
Owner:如皋市生产力促进中心
High-dynamic spread spectrum signal fast acquisition algorithm
The invention discloses a high-dynamic spread spectrum signal fast capture algorithm, which comprises the following steps of: 1, capturing a signal R1, obtaining a signal Rt after delay time t, and performing autocorrelation operation on the signal R1 and the signal Rt of the delay time t based on an FFT Doppler offset estimation technology; 2, performing autocorrelation operation on the signal R1and the signal Rt of the delay time t of the signal R1 by using FFT, processing a result, and performing frequency offset analysis to obtain a Doppler frequency change rate. According to the algorithm disclosed in the invention, the Doppler frequency change rate is obtained through frequency offset analysis and calculation; the signal frequency offset reconstruction signal is compensated according to the Doppler frequency change rate k to obtain a signal without the frequency change rate; then, the pseudo code phase can be obtained only through one-time pseudo code capture, Doppler and pseudocode limiting serial stepping search is not needed, meanwhile, the capture threshold is compared and analyzed, the local carrier signal frequency and the pseudo code phase are modified according to the comparison result, and rapid capture of the high-dynamic spread spectrum signal is achieved.
Owner:南京天际砺剑科技有限公司
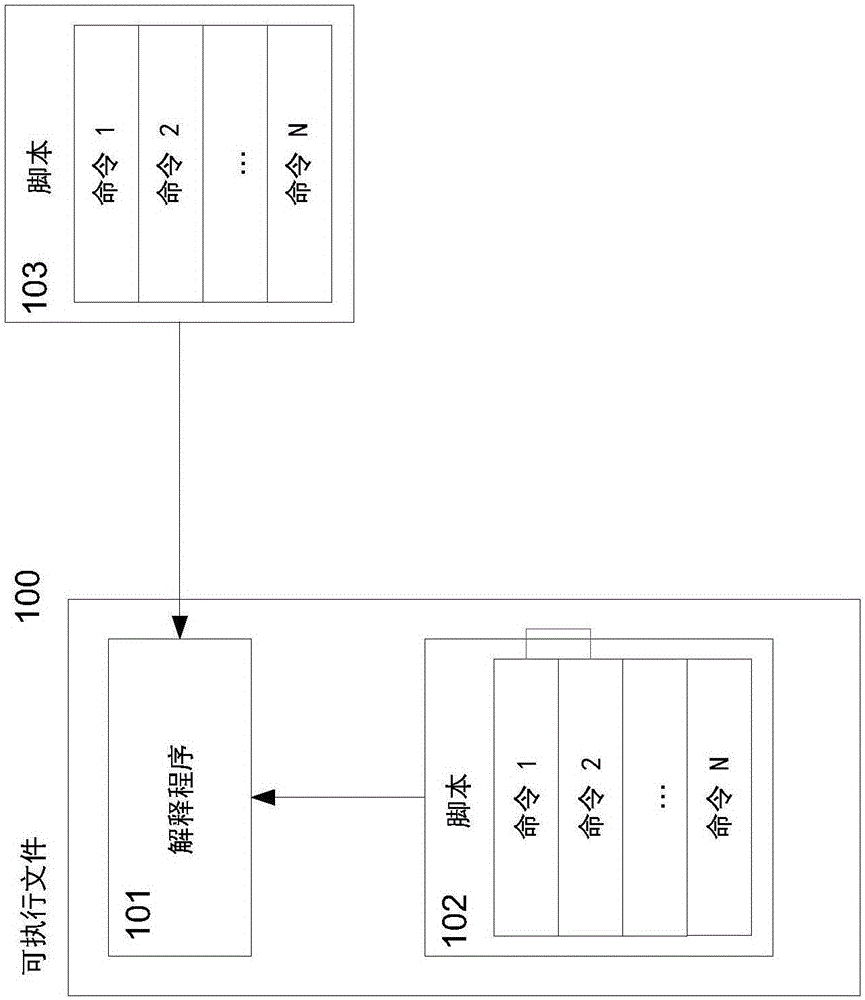
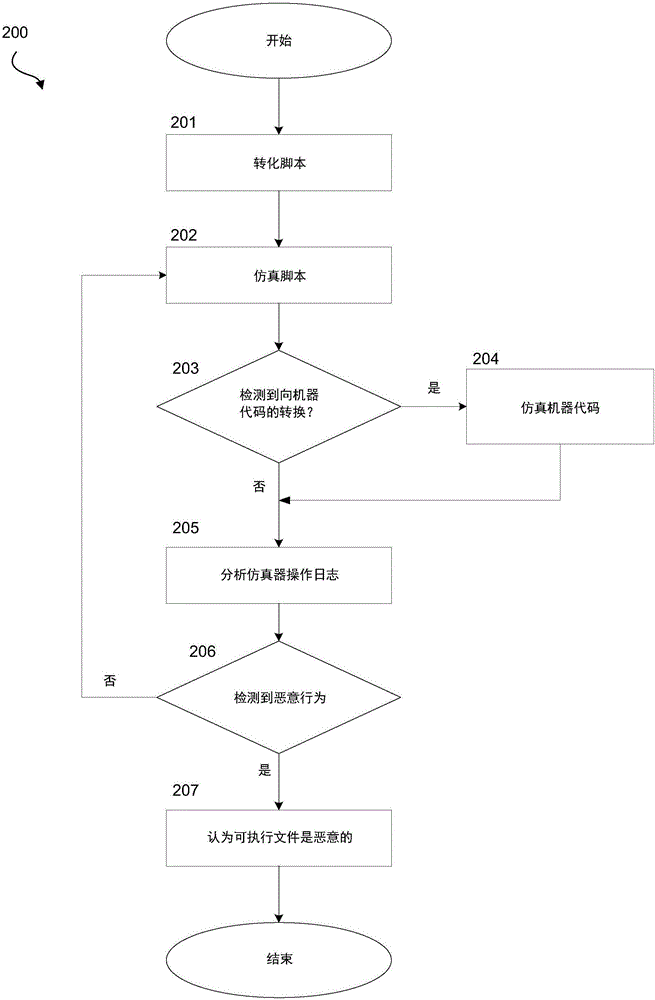
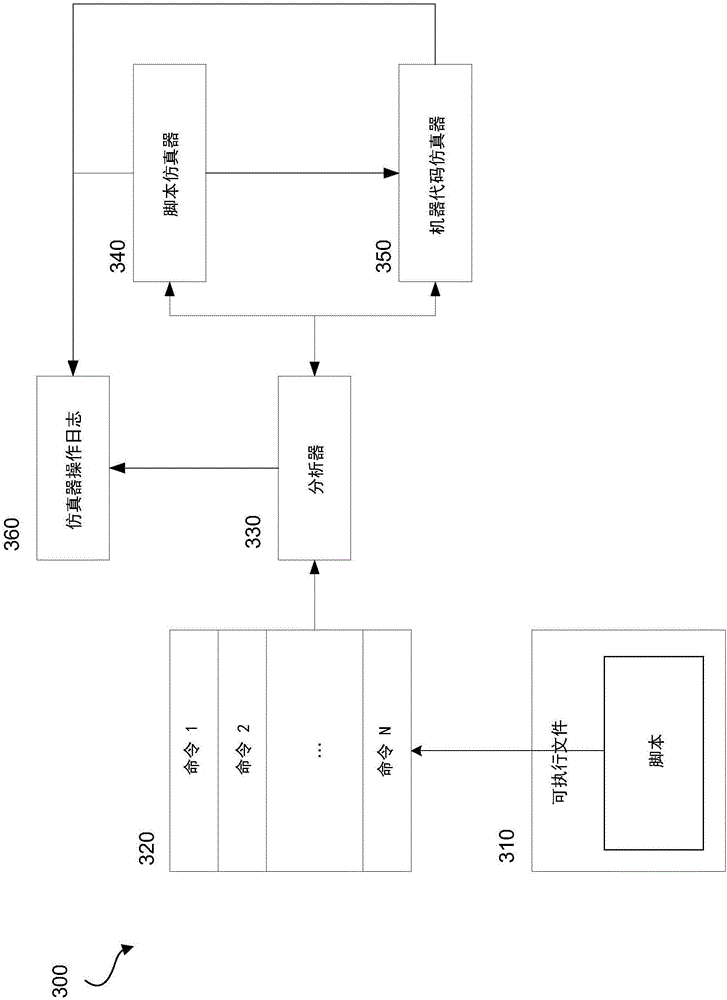
Systems and methods for detecting malicious executable files
ActiveCN106228069APlatform integrity maintainanceProgram/content distribution protectionScripting languagePseudocode
Systems and methods to detect malicious executable files having a script language interpreter by combining a script emulator and a machine code emulator. A system includes an analyzer configured to convert a script into pseudocode and monitor an emulation process of the pseudocode, a script emulator configured to sequentially emulate the pseudocode and write emulation results to an emulator operation log, and a machine code emulator configured to emulate the pseudocode if a transition from pseudocode to machine code is detected by the analyzer, such that the analyzer can analyze the emulator operation log to determine if the executable file is malicious.
Owner:AO KASPERSKY LAB
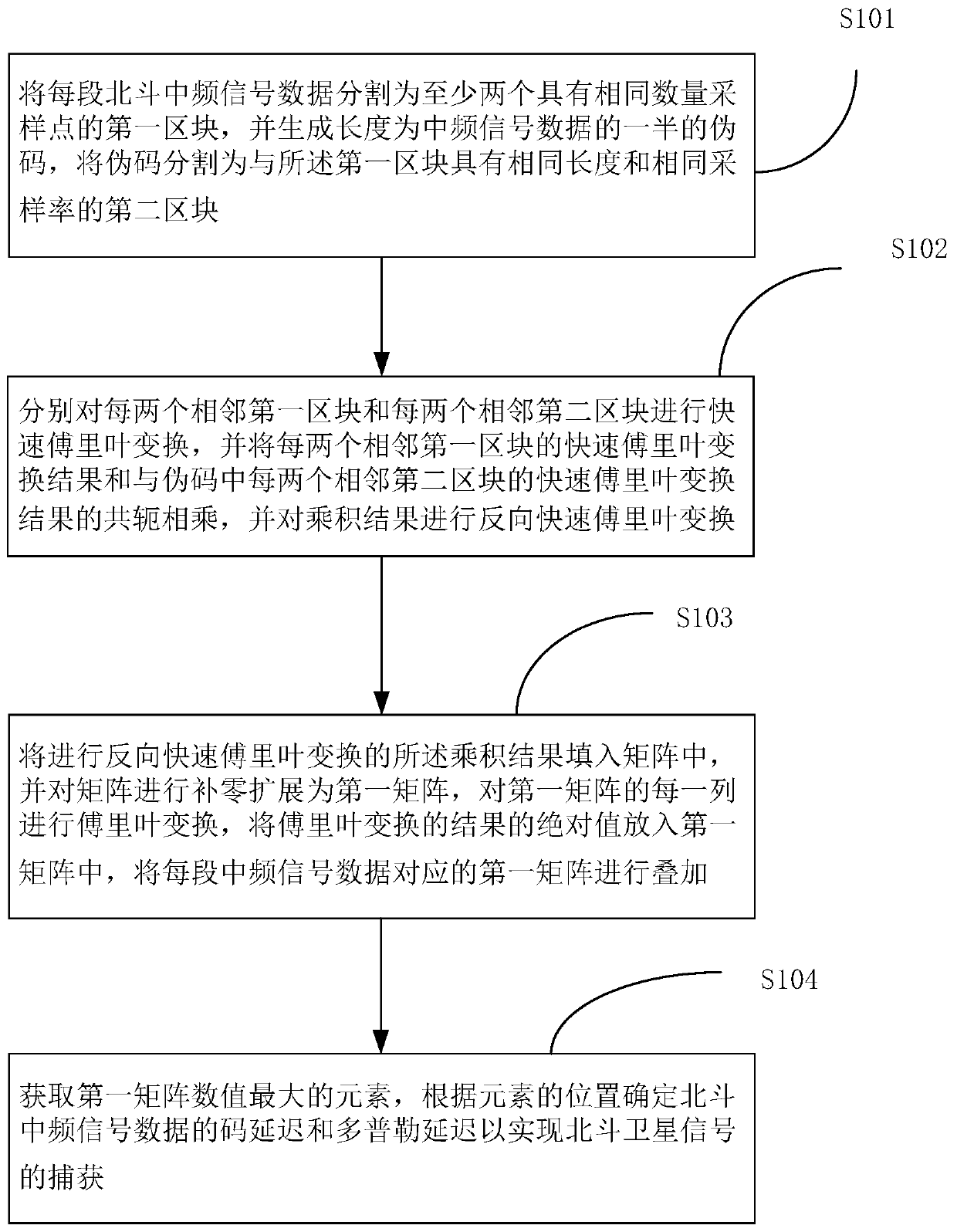
Beidou satellite signal capturing method and device
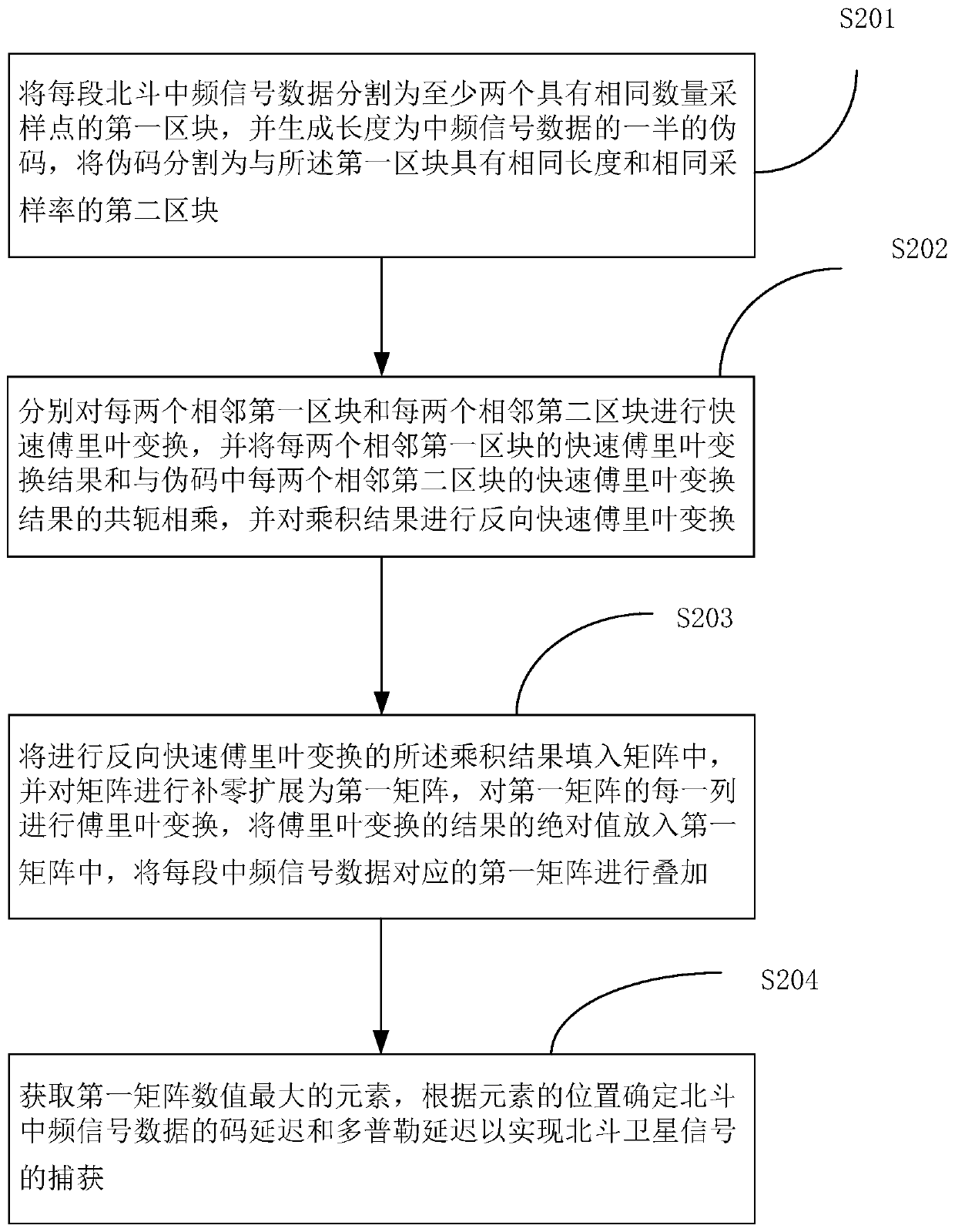
PendingCN111257913AImprove capture efficiencyShort capture timeSatellite radio beaconingFast Fourier transformIntermediate frequency
The invention provides a Beidou satellite signal capturing method and device. The method comprises steps of segmenting Beidou intermediate frequency signal data into a first block, generating a pseudocode, and segmenting the pseudo code into a second block; respectively carrying out fast Fourier transform of the first block and the second block, multiplying the result of the first block by a conjugate of the result of the second block, and carrying out reverse fast Fourier transform of a product result; filling the product result into a matrix, carrying out zero padding expansion to form a first matrix, carrying out Fourier transform of each column of the first matrix, taking an absolute value, and superposing the first matrixes; and capturing a Beidou satellite signal according to the element with the maximum numerical value of the first matrix. The method is advantaged in that the satellite signal capturing time is short, hardware resource requirements are few, precision is high, advantages of a Beidou system constellation can be used for preferentially capturing Beidou satellite signals, capturing of other constellations is assisted, and satellite signal capturing efficiency isimproved.
Owner:交通运输部长江通信管理局 +2
Hardware implementation method for generating B1C signal pseudorandom noise code
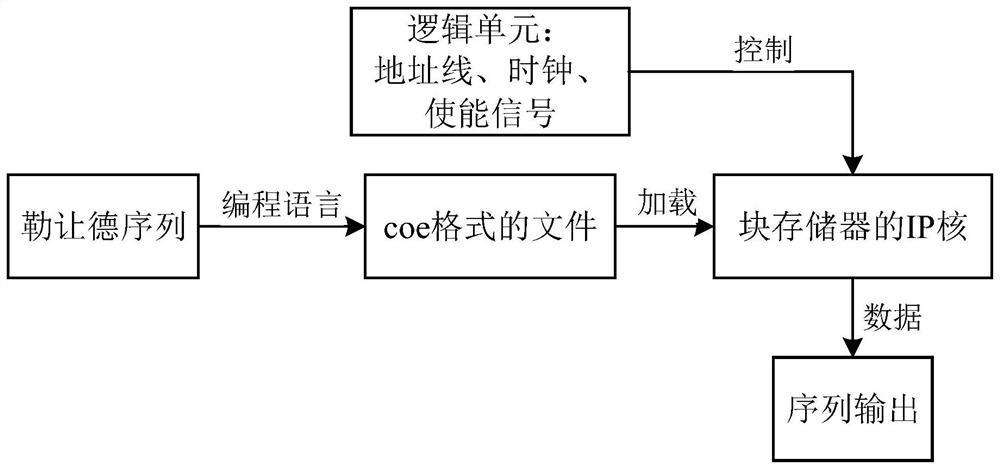
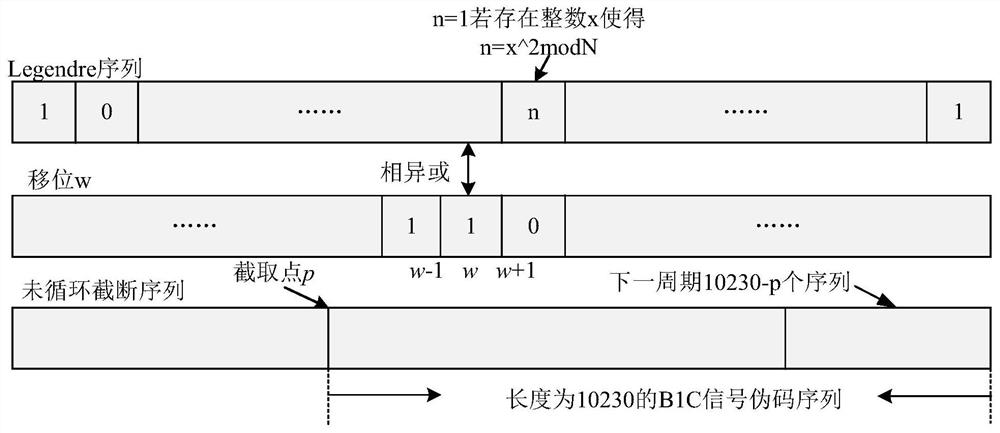
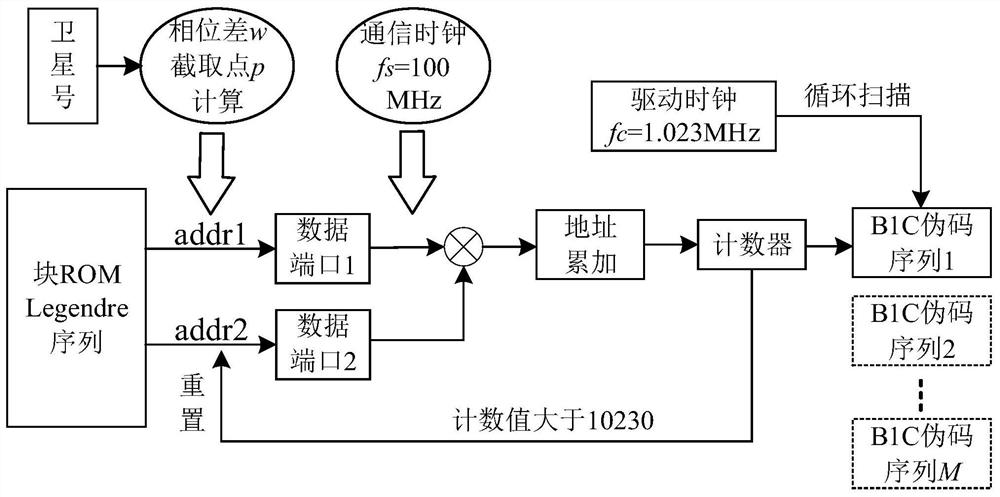
PendingCN111694029AAchieve real-time outputSimple structureSatellite radio beaconingComputer hardwareComputer architecture
The invention provides a hardware implementation method for generating a B1C signal pseudorandom noise code, which is characterized by comprising the following steps of: 1, designing a Legendre hardware output implementation method based on a block memory; 2, designing a hardware circuit scheme based on block ROM shared B1C pseudo-random noise code output; and 3, proposing a scheme of multi-channel time division multiplexing of the block memory in the FPGA, and realizing a multi-channel output method of the sequence. The invention aims to solve the problem that a multichannel B1C signal pseudocode generator occupies too many hardware resources, a multichannel B1C pseudo-random noise code output hardware design based on an FPGA and a time division multiplexing algorithm is provided. A specific design scheme and a simulation result are given, multichannel output of the B1C signal pseudo-random noise code of the low-power Beidou navigation receiver is realized, and the problems that thegenerated pseudo code sequence occupies too much hardware resources and the circuit structure is complex are solved.
Owner:HARBIN ENG UNIV
A Dynamics Modeling Method of Multi-axis Robot Based on Axis Invariant
ActiveCN108972558BImprove computing efficiencyImprove stabilityProgramme controlProgramme-controlled manipulatorPseudocodeModelSim
The present invention proposes a multi-axis system dynamics modeling and calculation principle based on axis invariants, and realizes the iterative display of multi-axis systems with tree chains, closed chains, joints with friction and stickiness, and moving bases. Dynamics modeling, the established model has an elegant chain symbol system, has the function of pseudocode, and realizes complete parameterization including "topology, coordinate system, polarity, structural parameters, mass inertia, etc.". This principle can be implemented as a circuit, as code, directly or indirectly, partially or fully within the multi-axis machine system. In addition, the present invention also includes an analysis and verification system constructed on these principles for designing and verifying multi-axis machine systems.
Owner:居鹤华
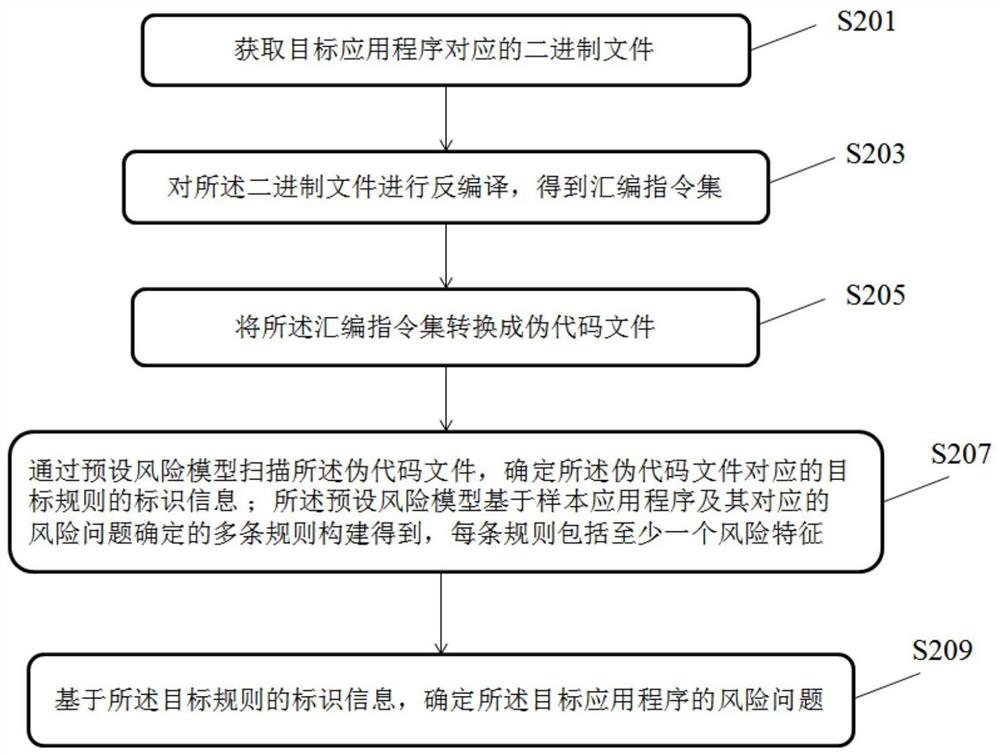
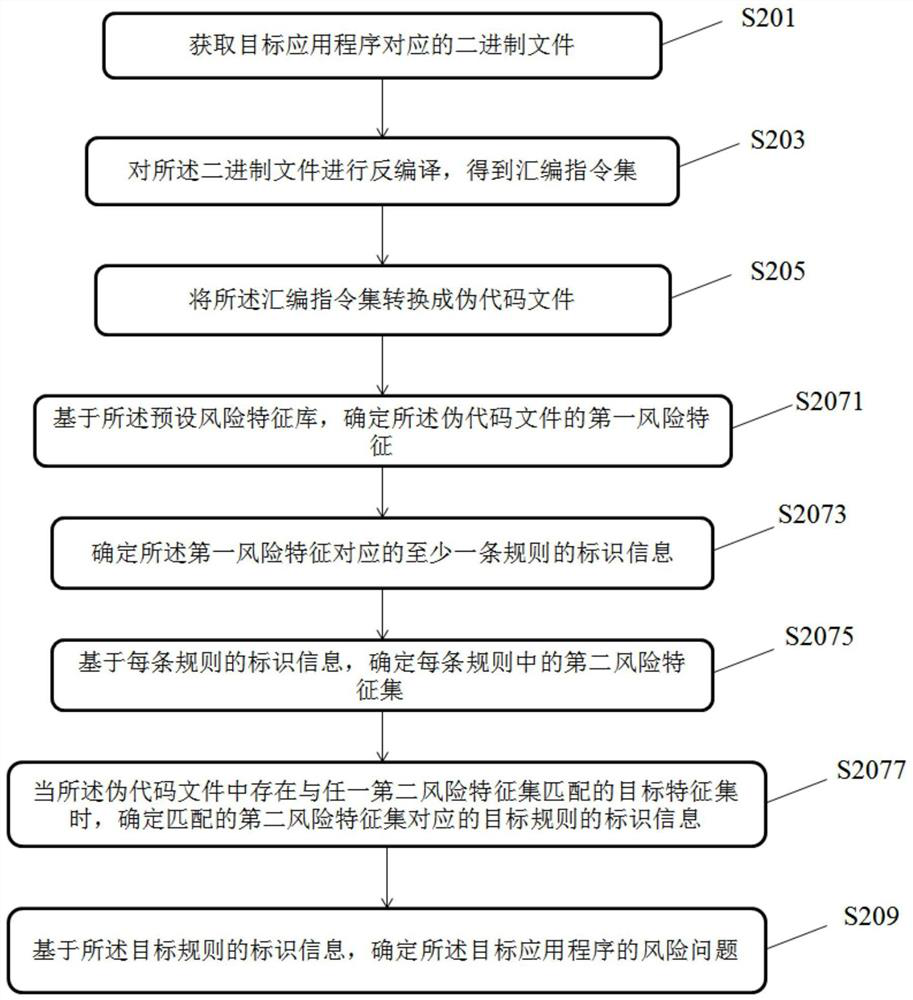
Risk problem determination method and device for application program and storage medium
PendingCN112711424AWide coverageAvoid risk warningDecompilation/disassemblyProgram documentationPseudocodeApplication procedure
The invention discloses an application program risk problem determination method and device and a storage medium. The method comprises the steps: acquiring a binary file corresponding to a target application program; decompiling the binary file to obtain an assembly instruction set; converting the assembly instruction set into a pseudo code file; scanning the pseudo code file through a preset risk model, and determining identification information of a target rule corresponding to the pseudo code file, wherein the preset risk model is constructed based on a sample application program and a plurality of rules determined by corresponding risk problems, and each rule comprises at least one risk feature; and determining a risk problem of the target application program based on the identification information of the target rule. By means of the technical scheme, the risk problems existing in all the application programs can be comprehensively and accurately detected.
Owner:TENCENT TECH (SHENZHEN) CO LTD
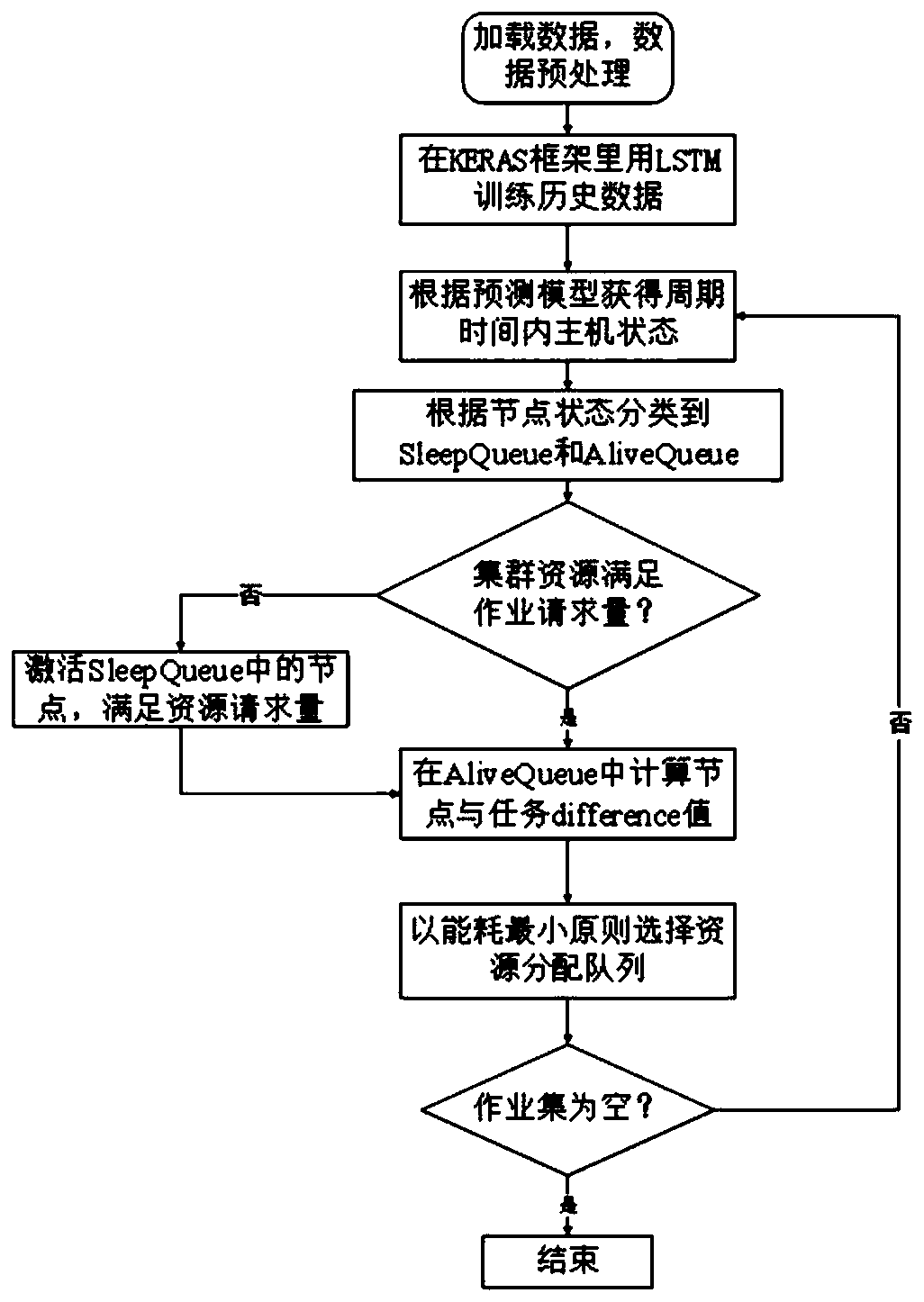
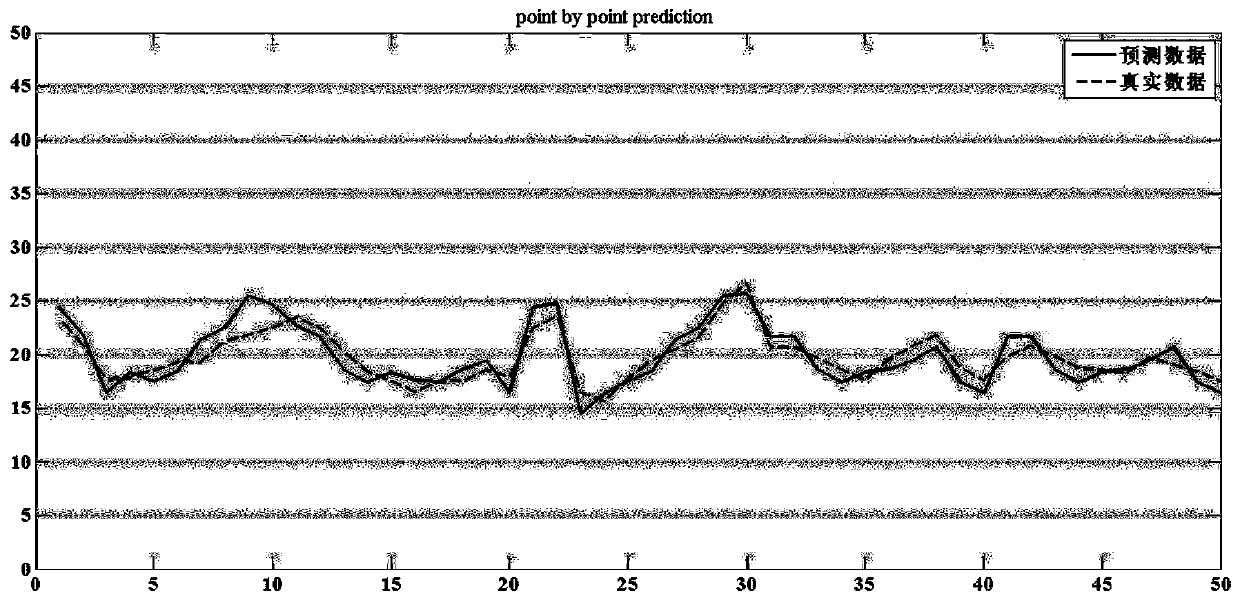
A Job Scheduling Method Based on Cluster Node Load Status Prediction
InactiveCN110096349BPractical significance of energy saving effectReduce the number of active nodesProgram initiation/switchingResource allocationPrediction algorithmsData set
The invention discloses a job scheduling method based on cluster node load status prediction, which belongs to the field of information technology processing. The invention proposes a job scheduling algorithm based on cluster node load status prediction. The load state of the prediction algorithm is divided into active node queues and dormant node queues; then the dormant nodes are dynamically activated according to the amount of resources required by the calculation to achieve the purpose of dynamically adjusting the cluster size; then the algorithm flow and algorithm steps are described. and the pseudo-code implementation of the algorithm, and then analyzed the energy-saving effect of the algorithm; and introduced the process of experimental verification, including the design of the experiment, the selection of data sets, and finally quantitatively analyzed the experimental results, proving the application's The method has a practical energy-saving effect.
Owner:SHANDONG UNIV OF SCI & TECH
Vulnerability detection method and device, equipment and storage medium
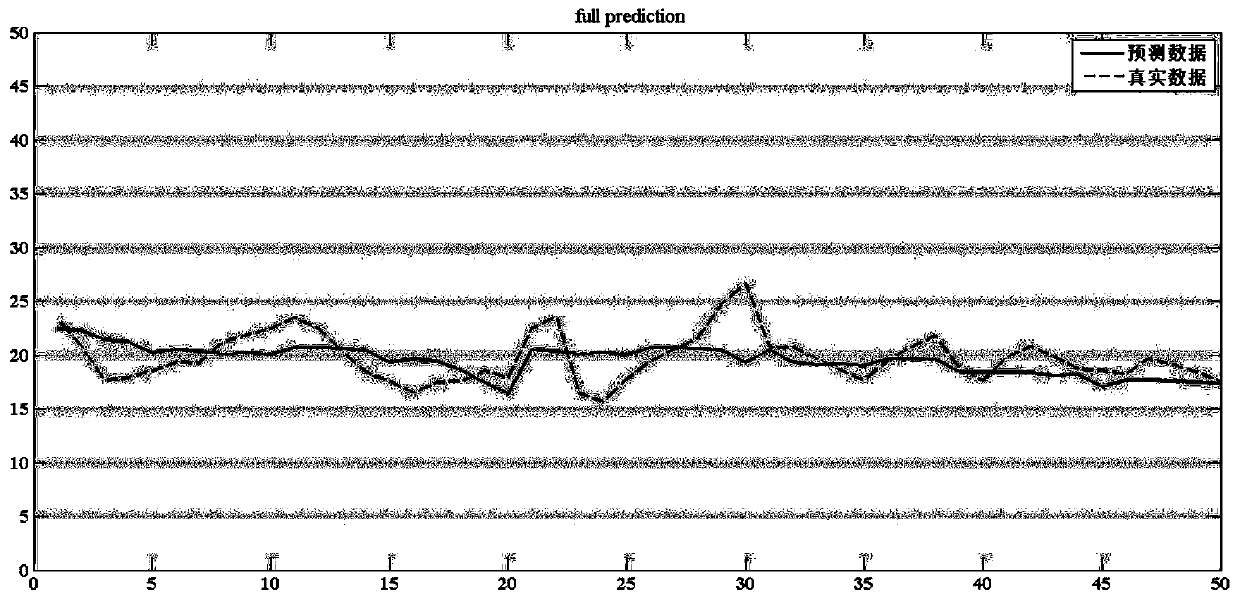
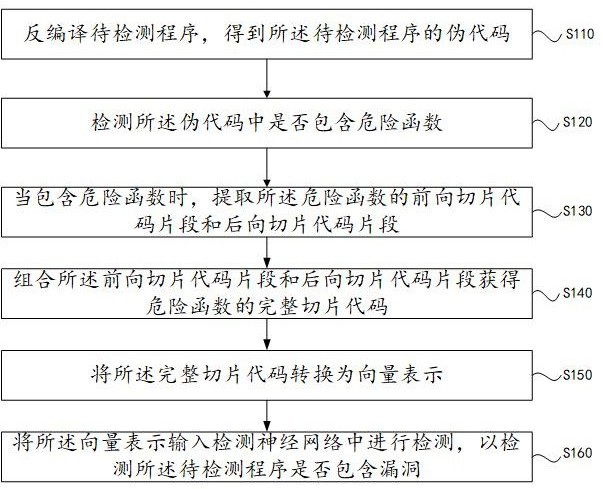
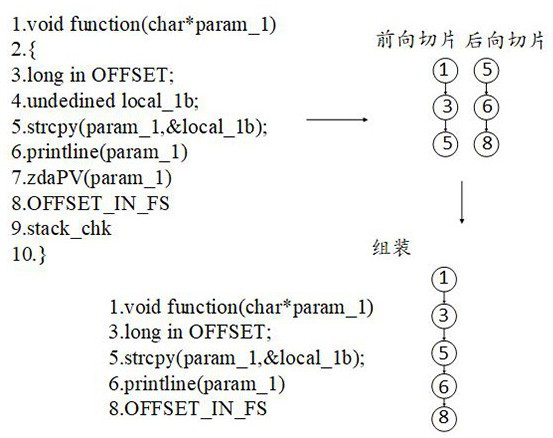
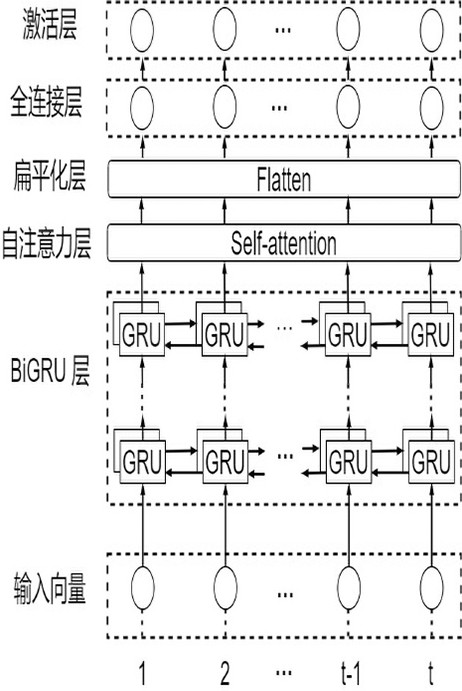
InactiveCN113297584AMitigate High False Positive EffectsAutomated Feature ExtractionPlatform integrity maintainanceNeural architecturesFeature extractionPseudocode
The embodiment of the invention provides a vulnerability detection method and device, equipment and a storage medium, and relates to the technical field of network information security, and the method comprises the following steps: firstly, decompiling a binary code of a to-be-detected program into a pseudo code; detecting a dangerous function in a pseudo code, then taking the dangerous function as a slice point, extracting a slice code related to the calling of the dangerous function, then converting the slice code into vector representation, and finally taking the vectorized slice code as input, and judging whether a program to be detected contains vulnerabilities or not by detecting a neural network. The method can be used for cross-architecture and cross-platform binary code vulnerability recognition scenes, fine-grained detection of vulnerabilities is achieved on the binary code level, automatic feature extraction can be effectively achieved, the high false alarm influence caused by different compilation options and patch codes is relieved, and the method has extremely high accuracy and extremely low false alarm rate and missing report rate.
Owner:SICHUAN UNIV
Sequence labeling-based text relation extraction method
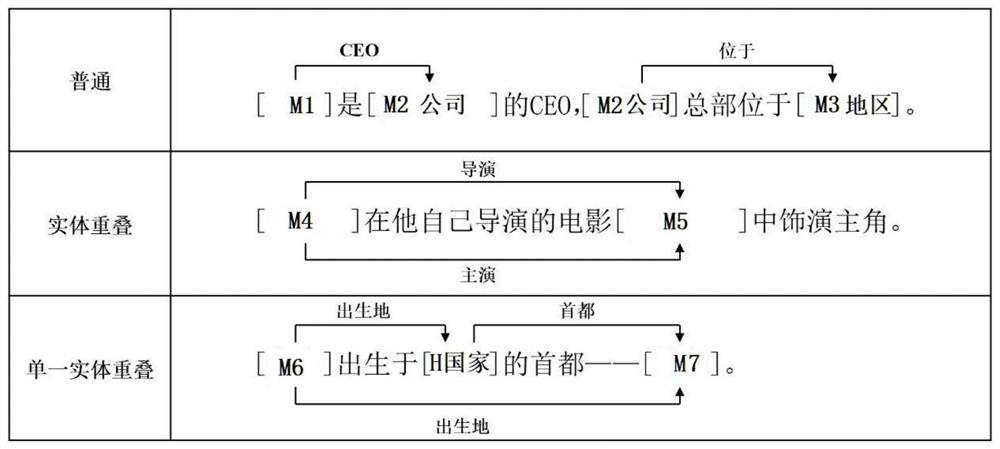
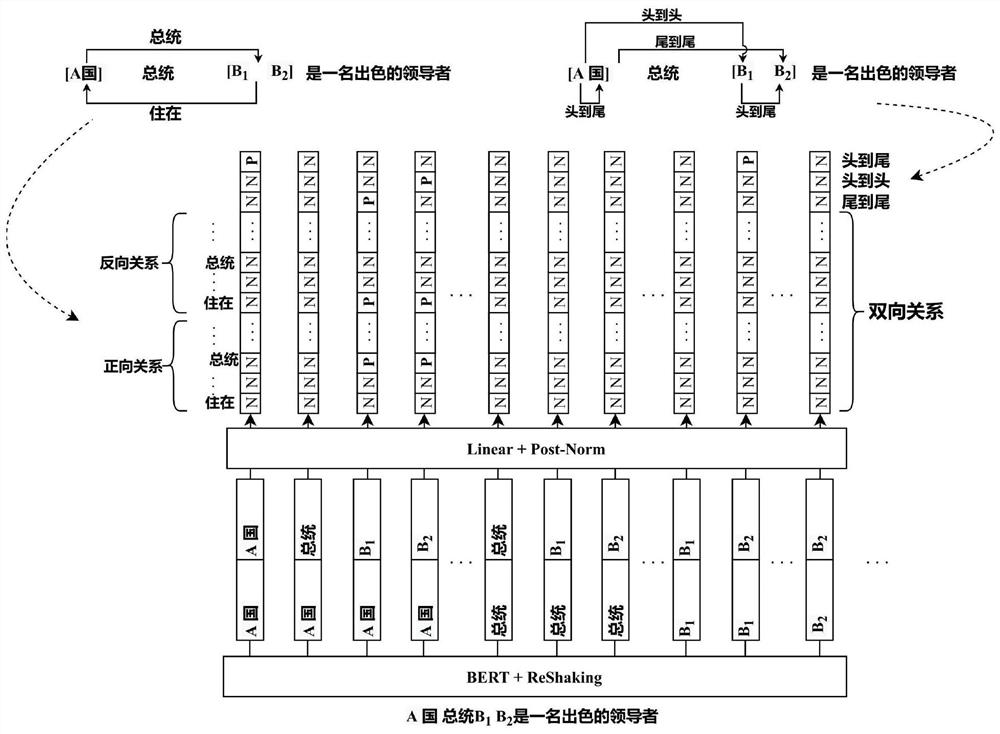
ActiveCN113191118ASolve the problem of entity overlapImprove accuracyCharacter and pattern recognitionNatural language data processingRelation classificationData set
The invention relates to the technical field of data processing, in particular to a sequence labeling-based text relation extraction method, which comprises the following steps of constructing a training data set similar to prediction data, and presetting all possible bidirectional entity relations and three fixed dependency relations; segmenting the input sentence into word sequences, and inputting the word sequences into a pre-training model to obtain a representation vector of a word in each sentence; forming a unique word pair sequence by using a mode similar to handshake for the word vector sequence; inputting the obtained vector pair sequence into a neural network classification layer; calculating loss and carrying out back propagation; judging the category of each word pair, and judging whether the word pair has the relation corresponding to the position or not; and decoding the final result by using the pseudo-code displayed in the drawing according to the corresponding relation, and finally obtaining all extracted triples. According to the method, two tasks including entity identification and relationship classification can be completed at the same time. And the extraction accuracy and the recall rate are remarkably improved and are greatly improved.
Owner:SHANDONG COMP SCI CENTNAT SUPERCOMP CENT IN JINAN
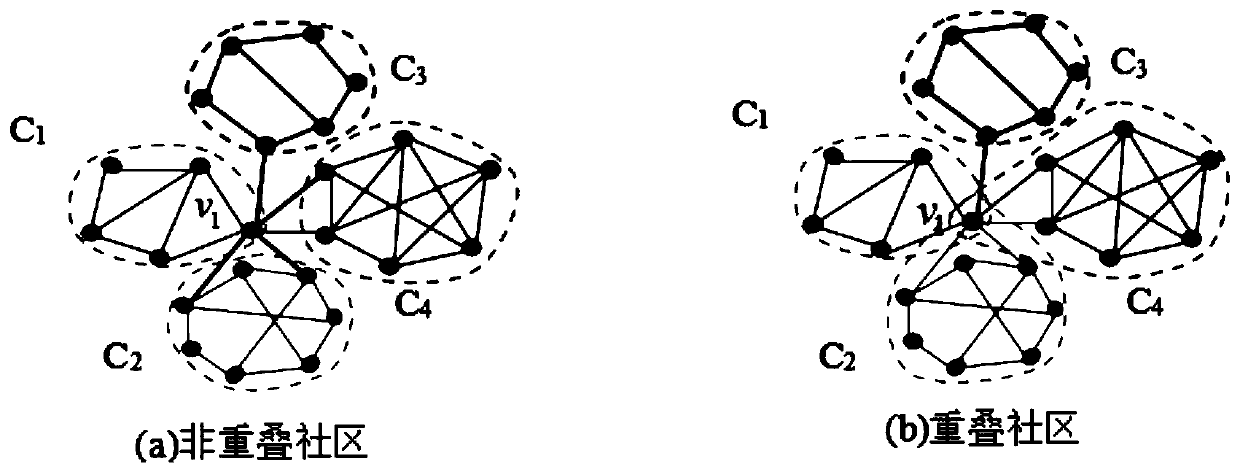
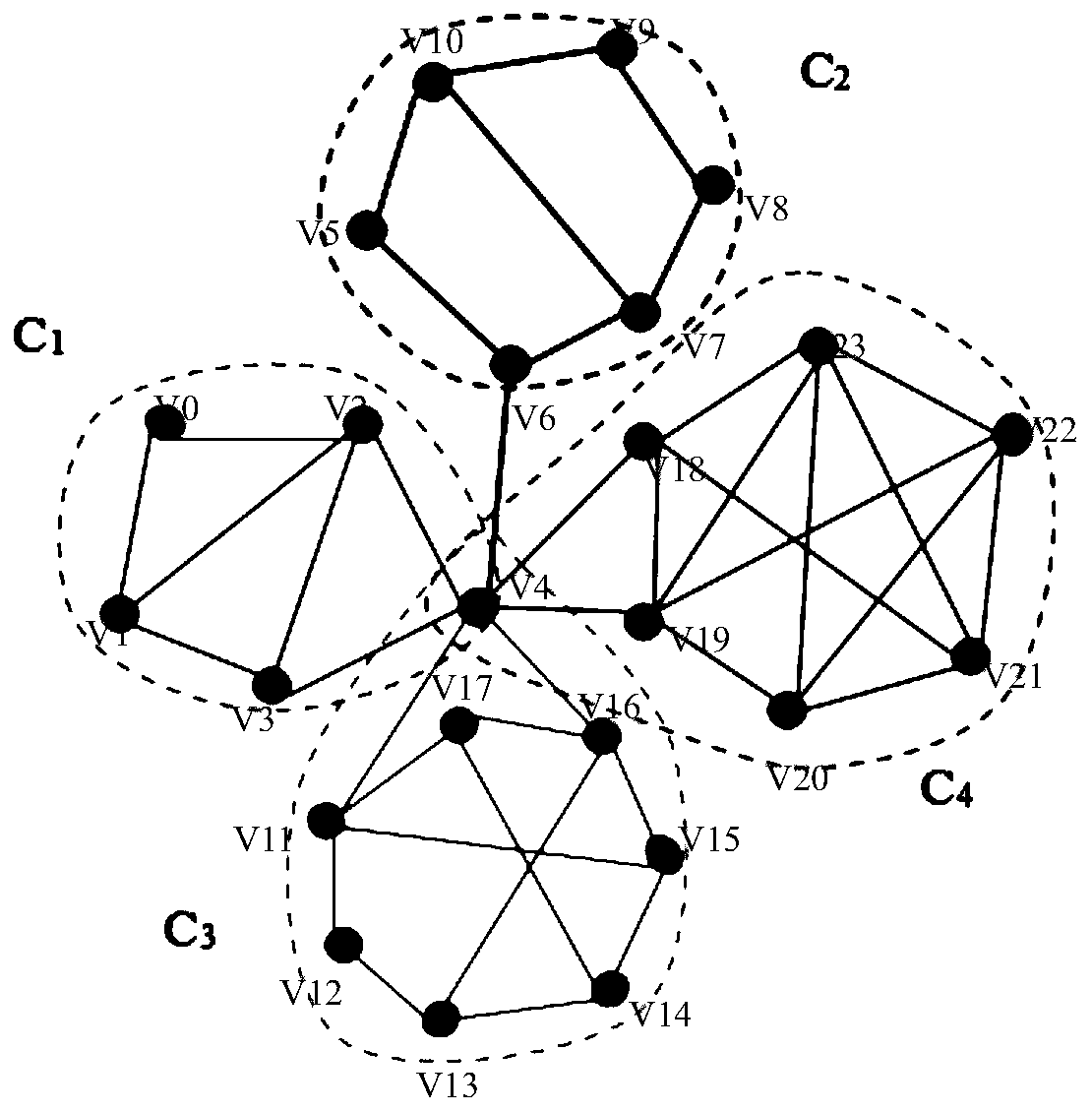
Method for measuring influence of social network
The invention discloses a method for measuring the influence of a social network, wherein the method is used for effectively selecting seed nodes. An algorithm 1 displays a pseudo code of a CCIM algorithm. Firstly, a network G (V, E) is divided into M communities through a community detection algorithm, then the influence of nodes is calculated, and a seed node with the maximum influence is found.For avoiding repeated calculation, incremental calculation of a marginal gain strategy is adopted. And after the seed node is selected, the overlapping influence is deleted and the influence of othernodes Is recalculated. And finally, the seed node propagates the influence in the network by using a specific diffusion model to maximize the influence range.
Owner:YUNNAN UNIV
A Forward Kinematics Modeling and Calculation Method of Multi-axis Robot System Based on Axis Invariants
ActiveCN108983705BImprove computing efficiencyImprove stabilityProgramme-controlled manipulatorNumerical controlPseudocodeTheoretical computer science
The invention proposes a multi-axis system forward kinematics modeling and solving method based on axis invariants. This method realizes inherently compact, real-time and functional reuse and simplified layering and complete parameter modeling and real-time calculation. It has the function of pseudo-code and symbol analysis, and can be set into circuits, codes, direct or indirect, partial Or do it all inside the multi-axis machine system. In addition, the present invention also includes an analysis and verification system constructed on these principles for designing and verifying multi-axis machine systems.
Owner:居鹤华
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com