Encryption-decryption method and terminal of data pack based on network transmission
A network transmission and data packet technology, which is applied in the encryption and decryption method of data packets and the terminal field, can solve problems such as potential safety hazards, increased network communication traffic, and loss of synchronization of key tables, so as to achieve high security and avoid network communication traffic. Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
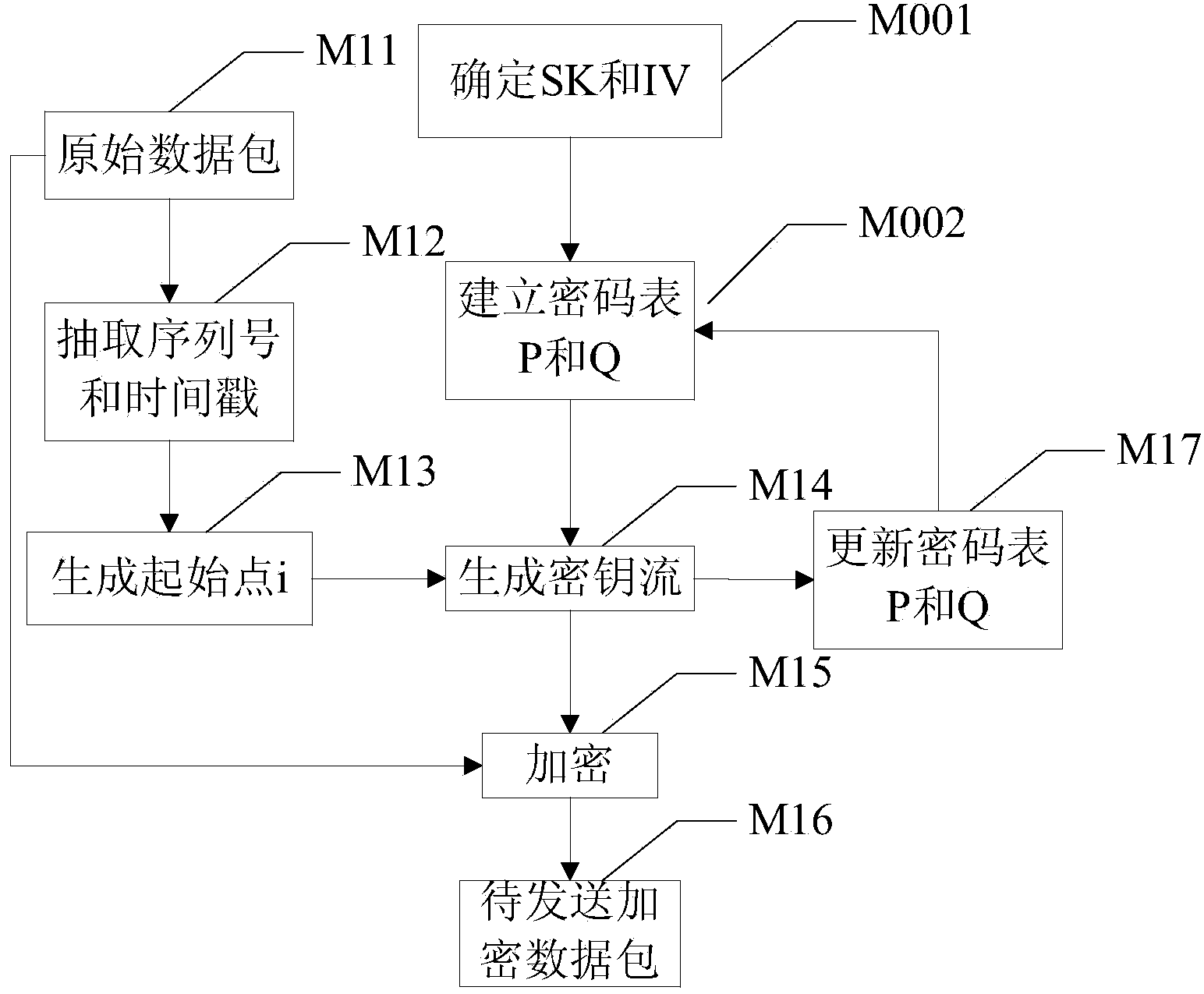
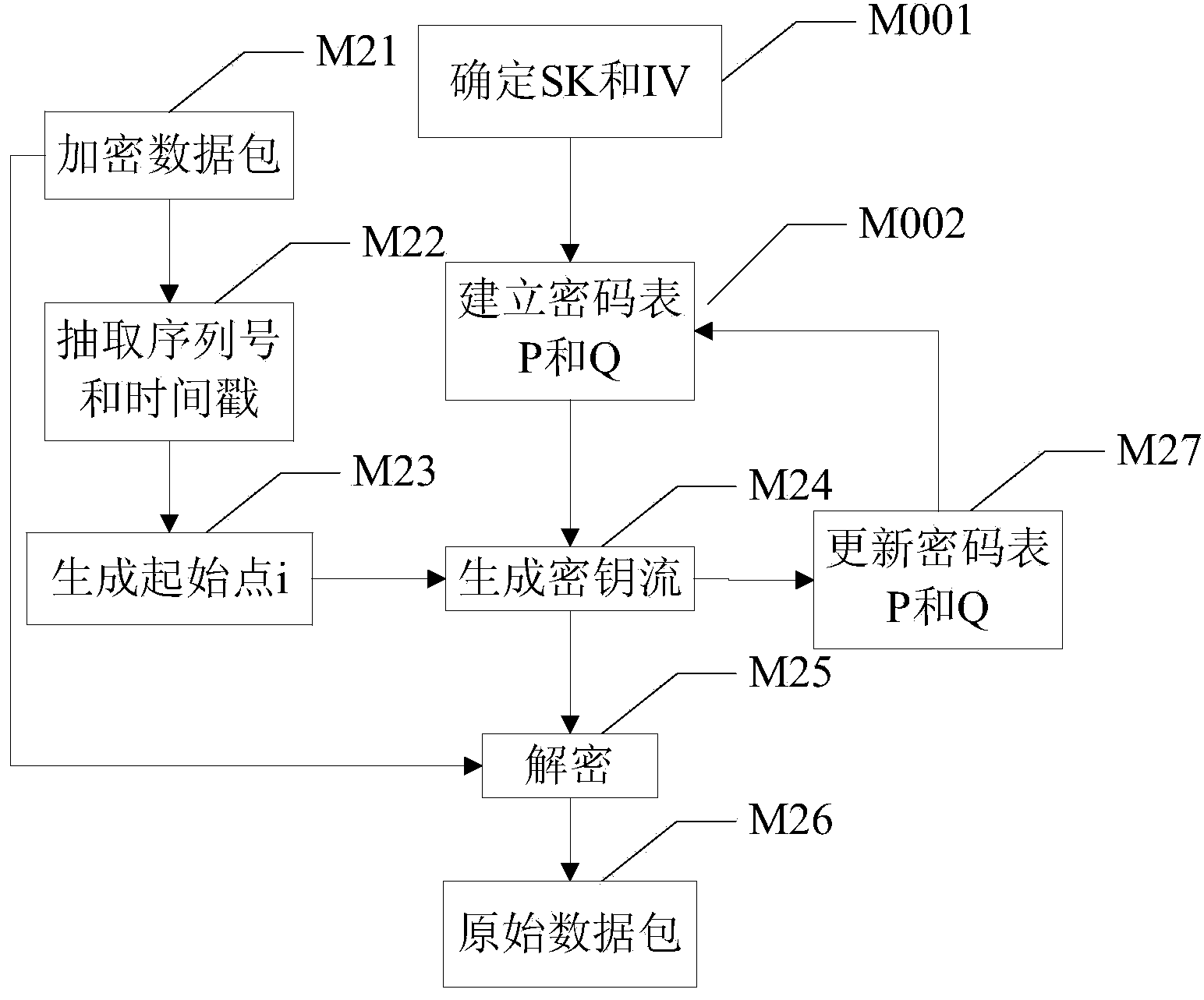
[0045] A specific implementation of the method for encrypting and decrypting data packets based on network transmission in the present invention can be referred to Figure 1-a and Figure 1-b , the specific steps include:
[0046] M001. Determine session key SK and random initialization vector IV.
[0047] The communication parties negotiate the session key SK and the 256-bit random initialization vector IV based on a specific security mechanism during the session initialization phase. The so-called session key SK and random initialization vector IV are commonly used by both communication parties to establish their respective communication password tables. Therefore, before the communication parties establish voice communication, they need to negotiate the relevant parameters of the call. It is easy to understand that since both communication parties have the same session key SK and random initialization vector IV, any one of the communication parties can determine the sessio...
Embodiment 2
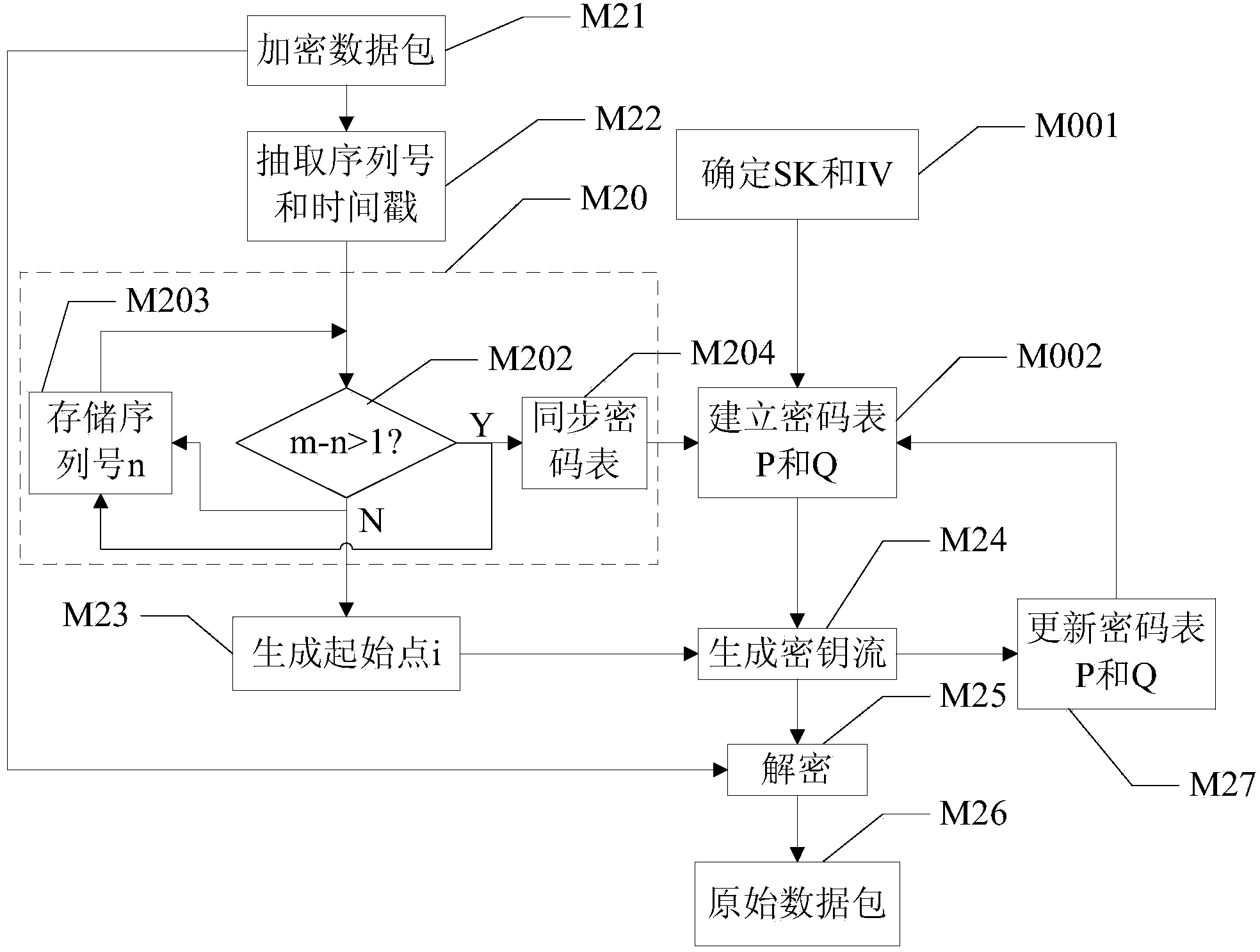
[0101] Due to unavoidable factors such as the network, in the communication process, it is inevitable that some data packets will not be received by the receiving end, which is called packet loss in this application. Due to the occurrence of packet loss, not only the lost data will be lost, but also the second update cannot match the first update. This is because the password table at the sender is updated every time a data packet is encrypted, so that the subsequent decryption does not match the encryption at the sender, causing errors in subsequent communications.
[0102] The method provided in this embodiment can effectively synchronize the second update when packet loss occurs. Please refer to figure 2 The difference between this embodiment and Embodiment 1 is that in the decryption process at the receiving end, after receiving the encrypted data packet, the receiving end also performs a packet loss synchronization processing flow M20, which specifically includes the fo...
Embodiment 3
[0119] A specific implementation of the encryption and decryption terminal suitable for VoIP media transmission in the present invention can be referred to image 3 , the encryption and decryption terminal in this embodiment can be used to execute the encryption and decryption methods involved in the above embodiments. The specific structure includes:
[0120] A key and initial vector acquisition unit 301, configured to determine a commonly used session key SK and a random initial vector IV when both communicating parties initiate a session;
[0121] A password table generating unit 302, configured to generate password tables P and Q according to the session key SK and the random initialization vector IV;
[0122] A data packet obtaining unit 311, configured to obtain an original data packet, the so-called original data packet is an unencrypted data packet;
[0123] The starting point extracting unit 312 extracts the first starting point according to the header information s...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com