Implementation method for integrated security protection subsystem of mobile office system
A technology for security protection and implementation methods, applied in transmission systems, security devices, wireless communications, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
specific Embodiment approach
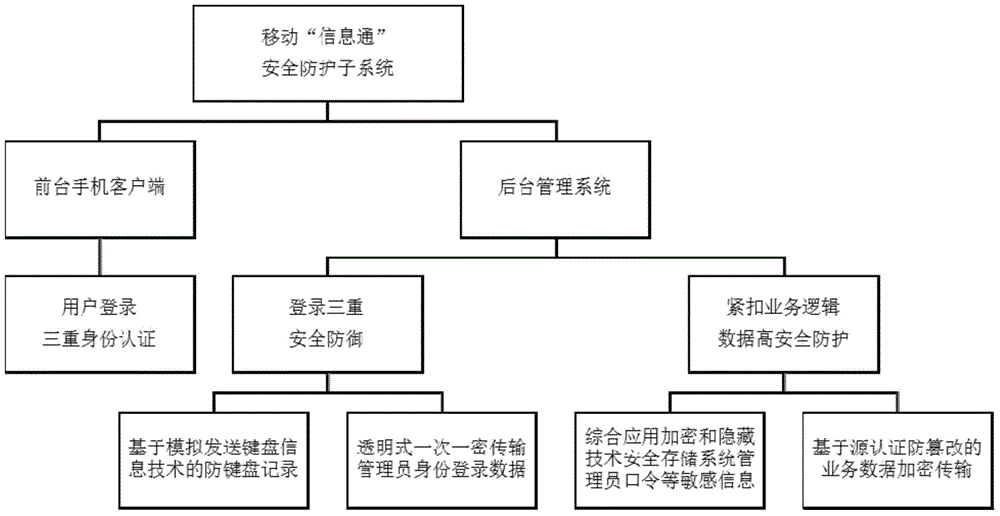
[0072] Such as figure 1 As shown, the implementation method of the integrated security protection subsystem in a mobile office system includes the triple identity authentication of the mobile client, the triple security defense of the background management system login, and the security protection closely linked to the business logic data. The specific implementation method adopts the following technical solutions:
[0073] Step 1. Three-factor authentication for smartphone user login
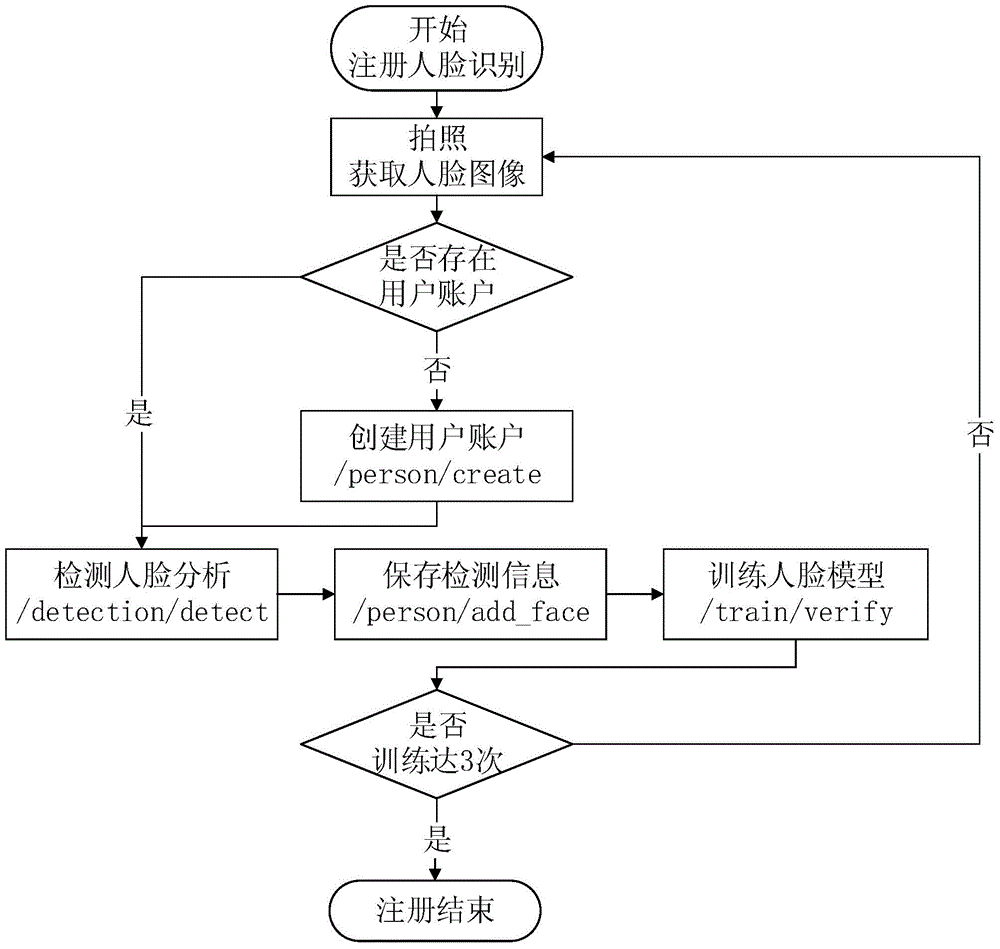
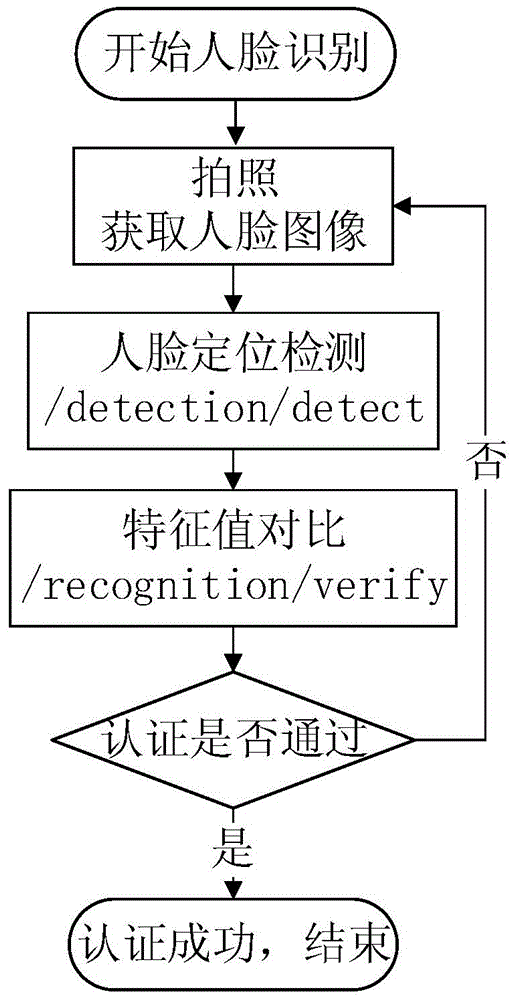
[0074] Such as figure 2 and image 3 As shown, in order to enhance the security of mobile client login control, effectively verify legitimate users, ensure effective access control of information systems, and at the same time protect the privacy of legitimate users and prevent others from stealing privacy, the triple identity authentication for user login includes password authentication. , face recognition authentication, pattern password authentication.
[0075] 1-1. Password authenticat...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com